#Segregation of Duties Risk Management
Explore tagged Tumblr posts
Text
SAP Cybersecurity and Solutions - ToggleNow

Today, organizations are increasingly vulnerable to cyberattacks and the no. of attacks have tremendously raised after covid 2019. Hackers started targeting enterprises that are vulnerable and weak, especially the business critical systems such as SAP.
As digital transformation, hyper-convergence, new normal rules create unintended gateways to risks, vulnerabilities, attacks, and failures, a cyber resilience strategy can help your business withstand disruptive cyber incidents. It can help you defend against those risks, protect your critical applications and data, and recover from breach or failure in a controlled, measurable way.
Read More: https://togglenow.com/cybersecurity
#SAP Cyber security#Segregation of Duties Risk Management#Unauthorized login attempts#SAP Security Services
0 notes
Text
When to Redesign SAP Roles: During ECC or Post-Migration to S/4HANA or Rise with SAP
Migrating to SAP S/4HANA or adopting RISE/GROW with SAP is a strategic milestone for organizations aiming to modernize their ERP landscape. However, one critical consideration often overlooked during these transitions is the redesign of SAP roles. The timing of this redesign can significantly influence the success of the migration and the overall efficiency. Should you redesign roles during the ECC phase or wait until after the migration to S/4HANA? This blog explores the key factors driving this decision and introduces the S.M.A.R.T framework—a modern approach to SAP role redesign that ensures compliance, efficiency, and business alignment.
Understanding the Need for Role Redesign
SAP roles are pivotal in defining user access, ensuring compliance, and maintaining operational efficiency. Over time, roles in ECC systems often become bloated with unused authorizations or misaligned with current business needs. This can lead to:
Compliance Risks: Excessive authorizations increase the risk of segregation of duties (SoD) violations.
Migration Complications: Legacy roles with redundancies can complicate the migration process to S/4HANA.
Operational Costs: Since the licensing model is based on assignment and not by usage in S/4HANA and RISE, you may need to procure more licenses than required.
A role redesign ensures clean, streamlined, and compliant access structures, setting the stage for a smooth transition and efficient system post-migration.
ls.ECC vs. S/4HANA: When to Redesign Roles?
Aspect
Redesign During ECC
Redesign Post-Migration to S/4HANA
Compliance
Proactively addresses SoD conflicts and access risks.
Allows compliance alignment with new functionalities post-migration.
Migration Complexity
Simplifies migration with clean and optimized roles.
Reduces redundant effort, focusing only on relevant roles in the new system
Alignment with New Features
May require rework later to incorporate S/4HANA-specific functionalities.
Ensures roles are tailored to new modules, Fiori apps, and processes.
Timeline and Resources
Increases project timelines due to pre-migration workload.
Defers redesign efforts, potentially affecting initial system efficiency.
Business Process Analysis
Limited to existing ECC processes, with potential misalignment after migration.
Better aligned with current and optimized business processes in S/4HANA.
Redesigning SAP Roles with RISE with SAP
If you are moving to RISE with SAP, it is advisable to conduct a complete role redesign during the ECC phase. Once the migration is complete, perform a retrofit to align roles with the cloud-specific requirements introduced by RISE. This approach addresses the unique security, integration, and scalability considerations of a cloud-oriented transformation. You might have many questions at this juncture – What is the best approach? Which tools must be considered? Are there any accelerators that can be used? Can we use stock ready/ready to deploy role structures?
Challenges with Stock Ready Rulesets
Many system integrators offer pre-packaged or stock-ready rulesets as part of their role redesign services. While these rulesets might appear to save time and effort, they often come with significant challenges, making them unsuitable for many businesses. Here’s why the stock-ready approach is not recommended:
Lack of Customization: Stock-ready rulesets are designed to be generic and may not align with the specific needs of your industry or business processes. This can result in inadequate or excessive authorizations.
Compliance Risks: These pre-packaged rulesets may not fully address industry-specific compliance requirements, leaving gaps that could lead to audit findings or regulatory penalties.
Misalignment with Business Processes: Every organization has unique workflows and processes. Stock-ready rulesets may not account for these nuances, leading to inefficiencies and user frustrations.
Post-Implementation Challenges: Organizations often need to spend additional time and resources customizing these rulesets post-implementation, negating the perceived benefits of a quick deployment.
Instead of relying on stock-ready rulesets, organizations should invest in a tailored role redesign approach. This ensures that roles are aligned with specific business processes, compliance requirements, and future scalability needs, delivering long-term value and efficiency. This is where S.M.A.R.T approach/framework can be a life saver.
The S.M.A.R.T Role Redesign Framework
At ToggleNow, we leverage the S.M.A.R.T framework for SAP role redesign. This approach ensures that roles are:
Simplified: Designed to reduce complexity while maintaining operational effectiveness.
Mitigated for Risks: Focused on eliminating SoD conflicts and maintaining regulatory compliance.
Aligned with Business Tasks: Task-based roles ensure that access permissions directly support specific workflows.
Responsive to Change: Built to adapt seamlessly to future business or technical changes.
Transparent and Optimized: Designed with a focus on license optimization to eliminate unnecessary expenditures.
This framework delivers roles that are not only secure but also cost-effective and easy to manage
ToggleNow Advantage
ToggleNow brings a unique value proposition to SAP role redesign initiatives, ensuring a seamless and efficient process tailored to your business needs. Here’s why we stand out:
Customized Solutions: Unlike stock-ready rulesets, ToggleNow develops tailored role designs aligned with your specific business processes, compliance requirements, and industry standards.
Deep Expertise: With extensive experience in SAP role redesign, ToggleNow combines technical proficiency with a deep understanding of regulatory compliance and security best practices.
Innovative Tools:ToggleNow leverages proprietary tools such as Verity, Optimus and accelerators such as xPedite to streamline role redesign, risk analysis, and validation, ensuring faster project delivery.
Focus on Scalability:Our approach ensures that the roles we design are not only compliant and efficient but also scalable, adapting to your future business growth.
Proven Track Record:Trusted by leading organizations, ToggleNow has successfully delivered role redesign projects across diverse industries, enabling smoother migrations and enhanced system performance.
By partnering with ToggleNow, organizations can confidently navigate their SAP transitions, optimizing roles to drive operational excellence and long-term success.
Conclusion
The decision to redesign SAP roles during ECC or post-migration to S/4HANA or RISE with SAP depends on your organization’s priorities, resources, and timeline. Redesigning during ECC can simplify the migration process, while post-migration redesign allows alignment with new functionalities. For RISE with SAP, role redesign becomes even more critical to address cloud-specific requirements.
Moreover, organizations should avoid the pitfalls of stock-ready rulesets and opt for a customized approach that aligns with their unique requirements. By investing in a well-planned redesign, organizations can unlock the full potential of SAP S/4HANA or RISE with SAP, driving operational excellence and business growth.
Read more: https://togglenow.com/blog/redesign-sap-roles-ecc-or-s-4hana/

#SAP Risk Management#SAP access risk analysis tool#SAP GRC access control solution#SAP segregation of duties automation#SoD risk analysis for SAP
0 notes
Text
https://www.illumeo.com/courses/segregation-duties-core-business-processes

'Segregation of Duties' (SOD) within essential business processes, a linchpin for risk management and regulatory compliance, notably Sarbanes-Oxley (SOX). SOD ensures robust internal controls by delineating distinct roles to mitigate conflicts of interest. It elucidates SOD principles, dissects specific process intricacies, and empowers participants to pinpoint vulnerabilities, enact effective SOD strategies, and comprehend control mechanisms. By mastering SOD, individuals fortify organizations against financial improprieties and regulatory breaches, safeguarding integrity and compliance.
#e-learning#enhancement#finance#certification#accounting#business#courses#Segregation of Duties#Risk Management#Regulatory Compliance#Sarbanes-Oxley (SOX)#Internal Controls#Conflict Mitigation#Financial Integrity#Compliance Strategies#Role Delineation#Control Mechanisms
0 notes
Text
Is extensive Segregation of Duties an emerging Audit Concern?

Explore the features of the Verity Risk Analysis & Management solution. Verity serves as a thorough SoD Analyzer specifically crafted for SAP, pinpointing more than 100,000 risks, and empowering you to apply efficient measures for risk mitigation and resolution. Verity allows for a detailed examination of risks tied to users' actions. The platform offers diverse tools for establishing monitoring controls in critical risk areas. With support for multiple rulebooks, you have the flexibility to create one tailored to your auditor's specifications.
Enhance your Segregation of Duties management with our SoD Analyzer solution
Risk Analysis:
Swiftly analyze risks at both the user and role levels using the pre-delivered standard rulebook containing 100k+ risks.
Risk Assessment:
Evaluate the severity of the risk and its potential conflicts through user-friendly assessment screens, both at user and role level.
Risk Response:
Establish monitoring controls while mitigating risks to enhance your management processes. Else, remediate it.
Risk Governance:
Elevate your governance with the pre-delivered rules, reports, and dashboards, all of which can be generated with a single click.
Features of Verity
Risk Monitoring:
Verity comes with an in-built unique Alert Monitor which sends notifications to key monitors when critical transaction codes that are mitigated are being executed. Through this feature, the alerts can be easily reviewed and approved by business process owners.
Risk Identification:
Verity facilitates SAP risk analysis on the basis of standard rulebooks. Custom rulebooks can be added to suit audit requirements, or for easy identification of SoDs and critical risks in transaction codes, authorization objects, and other areas of concern.
Risk Management:
Verity helps organizations with execution of effective risk management activities at both the user and the role levels. It offers the option to create and manage mitigation controls within the organization at the business process and sub-business process levels.
Read More: https://togglenow.com/solutions/verity/
#SAPSODanalysissolution#SAPSODanalysissoftware#SAPSODtool#offline SAPSODanalysis#SAPSODanalysis#SAPSODanalysistool
0 notes
Text
How Accountants Help Small Businesses Avoid Costly Mistakes?

Running a small business requires juggling many responsibilities, from sales and operations to marketing and customer service. Amid this busy environment, financial management often becomes an afterthought—leading to costly errors that can threaten long-term stability. Hiring a professional accountant can be one of the smartest decisions a small business owner makes. Accountants bring expertise, structure, and foresight, helping small businesses avoid common but costly mistakes.
Preventing Financial Reporting Errors
One of the most frequent and damaging mistakes small businesses make is inaccurate financial reporting. Whether it’s entering incorrect data, misclassifying expenses, or failing to reconcile accounts, these errors can distort the true financial picture of a business. Misleading reports can lead to poor decision-making, missed opportunities, or even penalties during audits.
Accountants for small businesses in Fort Worth, TX ensure that all transactions are recorded properly and consistently. They implement sound bookkeeping practices and use reliable accounting software to maintain accuracy. With their help, small business owners can rely on clear, up-to-date financial reports to guide decisions with confidence.
Ensuring Tax Compliance
Tax-related mistakes are a major source of financial stress for small businesses. Missing deadlines, filing incorrect forms, or failing to understand tax obligations can result in fines, penalties, or even audits. Many business owners also miss out on deductions and credits simply because they’re unaware of them.
Accountants are well-versed in local, state, and federal tax regulations. They keep up with changes in tax laws and ensure all filings are submitted accurately and on time. More importantly, they offer tax planning strategies throughout the year to reduce liabilities and maximize savings. This proactive approach can significantly reduce the risk of compliance issues and unplanned expenses.
Avoiding Cash Flow Problems
Cash flow is one of the biggest challenges for small businesses. Even profitable companies can struggle if their incoming revenue doesn’t align with outgoing expenses. A lack of cash flow planning can lead to late payments, inability to meet payroll, or missed growth opportunities.
Accountants help small business owners monitor cash flow trends, forecast future needs, and prepare for seasonal fluctuations. By setting realistic budgets and advising on when to cut expenses or seek financing, they help businesses maintain the liquidity needed to operate smoothly.
Protecting Against Fraud and Theft
Small businesses are particularly vulnerable to internal fraud or theft due to limited staff and informal financial controls. Without proper oversight, unauthorized transactions or misuse of funds can go unnoticed.
Accountants introduce internal controls such as segregating duties, approving expenses, and reconciling accounts regularly. These safeguards make it much harder for fraudulent activity to occur and increase the chances of detection if it does.
Providing Strategic Guidance
Beyond preventing mistakes, accountants serve as trusted advisors. They help small businesses understand financial trends, evaluate pricing strategies, and make informed decisions about investments or expansions. Their insights enable owners to think strategically rather than just reactively.
Conclusion
Accountants are more than number crunchers—they are protectors of your business’s financial well-being. By helping small businesses avoid costly mistakes in reporting, taxes, cash flow, and fraud prevention, they pave the way for smarter decisions and sustainable growth. Investing in professional accounting support is an investment in your business’s long-term success.
0 notes
Text
Fraud Prevention: How Outsourced Accountants Safeguard UK Businesses
Financial fraud is a silent predator in the business world. Reports suggest globally it can surpass £500 billion per year, and the UK is estimated to lose £219 billion, costing UK companies over £1.2 billion annually.
Small and medium-sized enterprises (SMEs) are particularly vulnerable, often lacking the robust internal controls needed to detect and prevent fraudulent activities. For accounting firms and businesses seeking reliable protection against financial crime, outsourcing accounting functions has emerged as a powerful defence strategy.

The Growing Need for Fraud Prevention
In recent years, we have seen a great increase in the complexity of financial fraud. From phishing attacks that target the average employee to large-scale invoice fraud, we are seeing a very dynamic range of threats. Also, in-house account teams, which are usually already very low-staffed, may have trouble putting in place the required protections, which in turn creates openings for the fraudsters.
Outsourced accounting firms provide a solution by combining expert oversight with advanced technology, creating multiple layers of protection against financial misconduct.
How Outsourcing Strengthens Financial Security
Enhanced Internal Controls Through Segregation of Duties
One of the most common weaknesses in financial management is the lack of separation between key accounting functions. When a single employee handles invoicing, approvals, and reconciliations, the risk of undetected fraud increases significantly.
Outsourced accounting eliminates this vulnerability by distributing responsibilities across dedicated specialists. Payments are processed by one team, reconciliations by another, and audits by a separate group—ensuring no single individual has unchecked control over financial transactions. This structured approach not only deters potential fraud but also makes any irregularities easier to spot.
AI-Powered Fraud Detection
Manual bookkeeping processes are no match for today’s sophisticated fraud tactics. Modern accounting fraud often involves subtle manipulations—duplicate payments, fictitious vendors, or slight alterations to bank details—that can go unnoticed without automated monitoring.
Professional outsourced accounting firms deploy AI-driven tools that continuously scan financial data for anomalies. Systems like Xero and QuickBooks Advanced use machine learning to flag unusual transactions, such as sudden spikes in expenses, payments to unrecognized suppliers, or deviations from typical spending patterns. These real-time alerts allow businesses to intervene before losses escalate.
Mitigating Insider Threats
While external fraud garners headlines, insider threats remain a persistent danger. Employees with access to financial systems may exploit weak controls for personal gain—whether through payroll fraud, expense padding, or unauthorized fund transfers.
Outsourcing reduces this risk by removing direct financial access from internal staff. External accountants manage transactions independently, while maintaining detailed audit logs that track every modification. Additionally, surprise audits—conducted without warning—act as a powerful deterrent against internal misconduct.
Ensuring Regulatory Compliance
The UK’s financial regulations are stringent, with strict anti-fraud measures under Money Laundering Regulations (MLR 2019) and Corporate Criminal Offence (CCO) laws. Non-compliance can result in heavy fines and reputational damage.
Outsourced accounting providers stay ahead of regulatory changes, ensuring that businesses adhere to the latest fraud prevention standards. They perform due diligence on suppliers, maintain meticulous records for audits, and implement secure data-handling protocols to prevent breaches.
Strengthening Cyber Security Defences
Many fraud cases originate from cyberattacks—phishing emails, ransomware, or unauthorized system access. Small businesses, often lacking dedicated IT security teams, are prime targets.
Outsourced accounting firms invest heavily in cybersecurity, employing encryption, multi-factor authentication (MFA), and secure client portals to protect sensitive financial data. Regular security audits further minimize vulnerabilities, ensuring that businesses are shielded from digital threats.
Why UK Accounting Firms and Businesses Should Consider Outsourcing
For accounting firms, outsourcing offers a way to expand services without increasing fraud exposure. By partnering with specialists, firms can provide clients with advanced fraud prevention measures while reducing their own liability risks.
For businesses, the benefits are even clearer:
Lower Fraud Risk: Professional oversight and AI monitoring drastically reduce financial vulnerabilities.
Cost Efficiency: Outsourcing is often more affordable than hiring in-house fraud specialists.
Regulatory Confidence: Compliance is managed by experts, minimizing legal risks.
Business Continuity: Secure, fraud-resistant accounting allows leadership to focus on growth.
A Proactive Approach to Financial Security
Fraud is an unavoidable reality in today’s financial landscape, but businesses don’t have to face it unprepared. Outsourced accounting provides a multi-layered defense—combining expert oversight, cutting-edge technology, and rigorous compliance protocols—to safeguard against financial crime.
For UK accounting firms and businesses alike, partnering with a trusted provider like Integra Global ensures not only financial accuracy but also long-term security. In an era where fraudsters grow increasingly sophisticated, proactive prevention is no longer optional—it’s essential.
#accounting outsourcing#accounting firms#outsourced accounting#outsourcing for uk accounting firms#accounting outsourcing company#virtual accounting#uk accounting firms#accounting outsourcing services#accounting outsourcing uk#accounting online
1 note
·
View note
Text
Top Cloud Security Challenges in 2025—and How to Solve Them
As cloud adoption accelerates in 2025, so do the complexities of securing cloud environments. From sophisticated threats to regulatory pressures and misconfigurations, organizations face a dynamic and evolving cloud security landscape. This blog explores the top cloud security challenges in 2025—and actionable strategies to overcome them.
1. Misconfigurations and Human Error
Challenge:
Despite advances in automation, cloud misconfigurations remain the leading cause of data breaches. These errors often arise from overly permissive IAM policies, unencrypted storage buckets, or default security settings left unchanged.
Solution:
Implement Infrastructure as Code (IaC) with security baked in.
Use automated cloud security posture management (CSPM) tools.
Regularly conduct compliance audits and red team assessments.
2. Identity and Access Management (IAM) Complexity
Challenge:
As organizations adopt multi-cloud and hybrid environments, managing identity and access across platforms has become increasingly difficult. Poorly managed IAM can lead to privilege escalation and lateral movement by attackers.
Solution:
Enforce least privilege access and zero trust principles.
Use federated identity and single sign-on (SSO).
Continuously monitor access with behavioral analytics.
3. Supply Chain and Third-Party Risks
Challenge:
In 2025, supply chain attacks have become more sophisticated, targeting third-party APIs, open-source software, and CI/CD pipelines integrated into cloud workflows.
Solution:
Perform SBOM (Software Bill of Materials) assessments.
Use runtime security tools to detect anomalous behavior.
Vet vendors with strict security SLAs and continuous assessments.
4. Data Residency and Compliance
Challenge:
Global data privacy regulations (like GDPR, CCPA, and new regional laws) impose strict controls on where and how data is stored. Multi-national businesses struggle to maintain compliance across jurisdictions.
Solution:
Use geo-fencing and cloud-native encryption with customer-managed keys.
Choose cloud providers that offer region-specific data control.
Automate data classification and policy enforcement.
5. Insider Threats
Challenge:
Insider threats—whether malicious or negligent—pose significant risks to cloud environments, especially where sensitive data and critical infrastructure are involved.
Solution:
Deploy User and Entity Behavior Analytics (UEBA).
Establish segregation of duties and audit trails.
Provide regular security awareness training.
6. API and Microservices Vulnerabilities
Challenge:
APIs and microservices are the backbone of modern cloud-native applications, but they expand the attack surface. Common issues include broken authentication, excessive data exposure, and lack of rate limiting.
Solution:
Use API gateways with integrated security policies.
Adopt OpenAPI/Swagger specifications to enforce standards.
Regularly scan APIs for OWASP Top 10 vulnerabilities.
7. Ransomware and Extortionware in the Cloud
Challenge:
Ransomware is evolving to target cloud workloads, backups, and even object storage. Attackers now combine encryption with data theft to pressure victims.
Solution:
Implement immutable backups and multi-versioning.
Use behavioral threat detection for unusual file access patterns.
Employ endpoint detection and response (EDR) across cloud workloads.
8. Inadequate Visibility and Monitoring
Challenge:
Cloud environments—especially multi-cloud—often suffer from fragmented logging and monitoring, creating blind spots for security teams.
Solution:
Centralize logs using SIEM/SOAR platforms.
Deploy cloud-native monitoring tools (e.g., AWS CloudTrail, Azure Monitor).
Enable real-time alerting with correlation rules and ML-based anomaly detection.
Final Thoughts
Cloud security in 2025 demands a proactive, layered, and automated approach. It’s no longer about protecting the perimeter—because in the cloud, the perimeter is dynamic, ephemeral, and everywhere.
Security leaders must focus on:
Automation and continuous compliance
Identity-first security
Unified monitoring and response
Secure software development lifecycle (SSDLC)
Ready to Secure Your Cloud Future?
Partner with cloud-native security platforms, invest in team education, and make security a shared responsibility across development, operations, and governance teams.
0 notes
Text
Revolutionizing Accounts Payable: Innovative Strategies for Process Improvement
The accounts payable (AP) function is a critical component of financial operations, directly impacting cash flow, vendor relationships, and overall business efficiency. Traditional AP processes, often characterized by manual data entry, paper-based workflows, and fragmented systems, can lead to inefficiencies, errors, and increased operational costs. To address these challenges, organizations are adopting innovative strategies that leverage technology and process optimization to transform their AP operations.
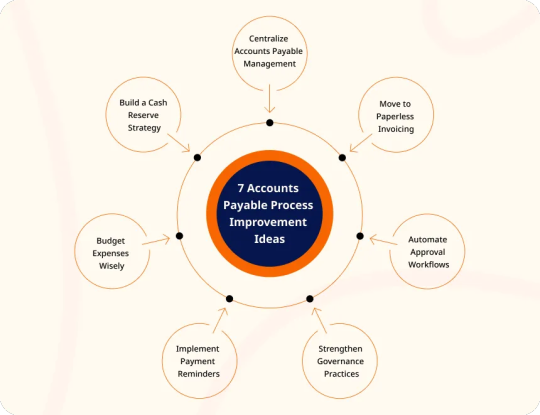
1. Embrace Automation to Streamline Operations
Manual data entry and paper-based processes are not only time-consuming but also prone to errors. Implementing automation tools, such as Optical Character Recognition (OCR) and Robotic Process Automation (RPA), can significantly reduce manual intervention. These technologies enable the automatic extraction of data from invoices and other documents, populating the information into the AP system with minimal human input. This leads to faster processing times, fewer errors, and reduced labor costs.
2. Implement E-Invoicing and Digital Document Management
Transitioning from paper invoices to electronic invoicing (e-invoicing) is a pivotal step in modernizing the AP process. E-invoicing allows for the direct submission of invoices into the AP system, eliminating the need for manual data entry and reducing the risk of lost or misplaced documents. Coupled with digital document management systems, organizations can store and retrieve invoices efficiently, ensuring compliance and facilitating audits.
3. Enhance Vendor Communication and Collaboration
Strong relationships with vendors are essential for smooth AP operations. Establishing clear communication channels and standardized processes for invoice submission and dispute resolution can prevent misunderstandings and delays. Regularly engaging with vendors to address concerns and provide feedback fosters a collaborative environment, leading to improved service levels and timely payments.
4. Standardize and Streamline Approval Workflows
Complex and inconsistent approval workflows can cause bottlenecks and delays in the AP process. By standardizing approval procedures and utilizing workflow automation tools, organizations can ensure that invoices are reviewed and approved promptly. Automated workflows route invoices to the appropriate approvers based on predefined rules, reducing the time spent on manual approvals and minimizing the risk of errors.
5. Utilize Data Analytics for Continuous Improvement
Leveraging data analytics provides valuable insights into AP performance metrics such as invoice processing time, payment accuracy, and vendor performance. By analyzing these metrics, organizations can identify trends, uncover inefficiencies, and implement targeted improvements. Regularly reviewing AP data ensures that processes remain aligned with organizational goals and industry best practices.
6. Ensure Compliance and Mitigate Fraud Risks
Compliance with regulatory requirements and safeguarding against fraud are paramount in AP operations. Implementing controls such as segregation of duties, approval hierarchies, and audit trails helps maintain compliance and detect fraudulent activities. Regular training for AP staff on compliance standards and fraud prevention techniques further strengthens the integrity of the AP process.
7. Adopt Cloud-Based AP Solutions
Cloud-based AP solutions offer scalability, flexibility, and real-time access to financial data. These platforms facilitate remote work, enable integration with other enterprise systems, and provide secure data storage. By adopting cloud-based solutions, organizations can enhance collaboration, improve data accuracy, and reduce IT infrastructure costs.
8. Optimize Payment Strategies
Efficient payment strategies contribute to better cash flow management and stronger vendor relationships. Implementing early payment discounts, optimizing payment schedules, and utilizing electronic payment methods can reduce processing costs and enhance vendor satisfaction. Automated payment systems ensure timely and accurate payments, minimizing the risk of late fees and maintaining positive vendor relationships.
youtube
Conclusion
Revolutionizing the accounts payable process requires a holistic approach that combines technology, process optimization, and strategic collaboration. By embracing automation, digital tools, and data-driven decision-making, organizations can transform their AP operations into a streamlined, efficient, and compliant function that adds value to the business. Continual assessment and adaptation to emerging technologies and industry trends will ensure that the AP process remains agile and aligned with organizational objectives.
SITES WE SUPPORT
AI Job Fit Process - Blogger
SOCIAL LINKS Facebook Twitter LinkedIn
0 notes
Text
Simple Strategies for Risk Remediation in Cybersecurity

You've identified the vulnerabilities, assessed the threats, and now you're staring down a list of cybersecurity risks. The next crucial step is remediation – the process of addressing those risks to protect your organization's digital assets. While complex vulnerabilities might require intricate solutions, many risks can be tackled with straightforward and effective strategies.
In the fast-paced world of 2025, where new threats emerge daily, focusing on simple yet impactful remediation techniques can significantly bolster your security posture without overwhelming your resources. Here are some key strategies to put out those cybersecurity fires:
1. Patching and Updating: The Low-Hanging Fruit
Outdated software is a welcome mat for cybercriminals. Vulnerabilities are constantly being discovered in operating systems, applications, and firmware. Regular and timely patching and updates are arguably the simplest and most effective ways to eliminate known weaknesses.
Implement a Patch Management Policy: Establish a clear process for identifying, testing, and deploying patches promptly.
Automate Where Possible: Utilize automated patching tools to streamline the process and reduce the window of vulnerability.
Prioritize Critical Updates: Focus on patching vulnerabilities that are actively being exploited or pose a high risk to your critical systems.
2. Strong Passwords and MFA: The Basic Blockade
Weak or reused passwords remain a primary entry point for attackers. Enforcing strong password policies and implementing Multi-Factor Authentication (MFA) are fundamental security hygiene practices that significantly reduce the risk of unauthorized access.
Enforce Complexity Requirements: Mandate passwords with a mix of uppercase and lowercase letters, numbers, and symbols.
Require Regular Password Changes: Implement a reasonable password rotation policy.
Ban Common Passwords: Utilize tools to prevent users from choosing easily guessable passwords.
Implement MFA Everywhere: Enable MFA for all user accounts, especially those with privileged access and for remote access points like VPNs.
3. Principle of Least Privilege: Limiting the Blast Radius
Granting users and applications only the minimum level of access required to perform their tasks is a powerful risk mitigation strategy. This principle of least privilege limits the potential damage an attacker can cause if an account is compromised.
Regularly Review User Permissions: Audit user accounts and remove unnecessary privileges.
Implement Role-Based Access Control (RBAC): Assign permissions based on job roles rather than individual users.
Segregate Duties: Ensure that no single individual has control over critical processes.
4. Network Segmentation: Containing the Spread
Dividing your network into isolated segments can prevent attackers from moving laterally across your entire infrastructure if one segment is compromised. Network segmentation limits the "blast radius" of an attack.
Segment Based on Sensitivity: Isolate critical systems and data on separate network segments.
Implement Firewall Rules: Control traffic flow between different network segments.
Utilize VLANs: Create virtual LANs to logically separate network resources.
5. Security Awareness Training: Empowering Your Human Firewall
Your employees are often the first line of defense against social engineering attacks like phishing. Regular security awareness training can empower them to recognize and report suspicious activity, turning them into a human firewall.
Conduct Regular Training Sessions: Cover topics like phishing, password security, malware, and social engineering.
Simulate Phishing Attacks: Test your employees' awareness and identify areas for improvement.
Foster a Culture of Security: Encourage employees to ask questions and report suspicious activity without fear of reprisal.
6. Data Backup and Recovery: Your Safety Net
In the event of a successful cyberattack or data loss incident, having reliable data backups and a well-tested recovery plan is crucial for business continuity.
Implement a Regular Backup Schedule: Automate backups of critical data to a secure, offsite location.
Test Your Recovery Plan: Regularly practice restoring data to ensure the process is effective and efficient.
Consider the 3-2-1 Rule: Maintain at least three copies of your data, on two different media, with one copy stored offsite.
Simple Actions, Significant Impact:
While these strategies might seem basic, their consistent and diligent implementation can have a significant impact on reducing your organization's cybersecurity risks. Don't get bogged down in the complexity of advanced threats and forget to address these fundamental security hygiene practices.
By focusing on patching, strong authentication, least privilege, network segmentation, security awareness, and robust backups, you can build a more resilient and secure digital environment in 2025 and beyond. Start with these simple steps, and you'll be well on your way to putting out those cybersecurity fires before they rage out of control.
0 notes
Text
Understanding the Core Functions of Accounting in Business Operations
Accounting is often referred to as the language of business—and for good reason. Whether you run a small startup or manage a large corporation, understanding the core functions of accounting is essential for informed decision-making, regulatory compliance, and long-term financial success.

In this article, we’ll explore the fundamental roles accounting plays in business operations and why every organization needs a solid accounting foundation.
What Is Accounting in Business?
Accounting is the systematic process of recording, analyzing, and reporting financial transactions. It helps businesses keep track of income, expenses, assets, liabilities, and overall financial health. The purpose is not just to document financial activities but to provide actionable insights that drive better business decisions.
Core Functions of Accounting
Accounting goes far beyond bookkeeping. Below are the key functions that make it a critical pillar of business operations:
1. Recording Financial Transactions
At the core of accounting lies the accurate recording of financial transactions. Every sale, purchase, expense, and income must be recorded in a standardized format, typically using double-entry bookkeeping. This ensures that financial statements reflect the true financial status of the business.
2. Financial Reporting and Analysis
Accounting transforms raw financial data into structured reports such as:
Income Statement (Profit & Loss)
Balance Sheet
Cash Flow Statement
These reports provide a snapshot of the company’s financial health, enabling business leaders to analyze profitability, liquidity, and solvency. They also assist stakeholders—including investors, banks, and regulators—in assessing the company’s performance.
3. Budgeting and Forecasting
Another vital function of accounting is budget preparation and financial forecasting. Businesses use historical data to create budgets and project future financial outcomes. This helps in:
Allocating resources effectively
Planning for expansion
Controlling costs
Identifying financial risks before they escalate
4. Tax Planning and Compliance
Every business must comply with local and international tax laws. Accounting ensures accurate calculation and timely payment of taxes such as:
Income tax
Sales tax
Payroll tax
Corporate tax
In addition, accounting helps in preparing and filing tax returns, minimizing the risk of audits, penalties, or legal consequences.
5. Internal Controls and Fraud Prevention
A sound accounting system helps maintain internal controls that safeguard business assets. It minimizes the risk of fraud, theft, and financial mismanagement by:
Segregating duties
Conducting audits
Implementing approval processes
Tracking cash and inventory movement
6. Decision-Making Support
One of the most strategic functions of accounting is its role in business decision-making. Whether it’s launching a new product, hiring new staff, or entering a new market, financial data supports leaders in making informed, data-driven decisions.
Importance of Accounting in Daily Business Operations
Without accounting, businesses would operate in the dark. Here’s why it’s indispensable:
Keeps finances organized and transparent
Ensures legal and regulatory compliance
Improves financial planning and forecasting
Boosts investor and stakeholder confidence
Helps identify cost-saving opportunities
How Accounting Software Enhances These Functions
Modern accounting software automates many of the tasks listed above, saving time and reducing errors. Tools like QuickBooks, Zoho Books, or Xero streamline invoicing, payroll, tax filing, and reporting—all in one place.
youtube
Final Thoughts
Understanding the core functions of accounting is essential for anyone involved in running a business. From maintaining records and complying with tax regulations to enabling strategic planning and fraud prevention, accounting supports every facet of business operations.
Investing in the right accounting practices and tools can make the difference between thriving growth and operational chaos. For long-term success, treat accounting not as an afterthought but as a strategic business function.
SITES WE SUPPORT
Skill Test Automation -
SOCIAL LINKS Facebook Twitter LinkedIn
0 notes
Text
5 Hidden SAP GRC Pitfalls That Could Jeopardize Your Compliance Strategy
1. “One-Size-Fits-All” RuleSet Syndrome
Many organizations implement SAP GRC with out-of-the-box rule sets and assume they’re covered and are completely Sox/SoD compliant. The problem? Standard rule sets don’t always reflect the unique business processes and risks of an enterprise. They must be utilized as a baseline.
Example: A global company using a generic SoD rule set might flag conflicts that aren’t actually risks in their specific operations, leading to unnecessary firefighting and role redesign efforts.
What is the solution? It is always recommended to tailor the rule set to align with your business needs. Involve process owners and auditors to ensure relevance. Disable those which are not relevant and add the ones what needs to be part of the rule set. For example, your custom transaction codes.
2. Over-Reliance on Automated Controls
Yes, automation is powerful, but blindly trusting automated GRC controls without proper oversight is a recipe for disaster.
Example: Automated access reviews might seem great, but if managers are just clicking the approval button without understanding the risk, you’re inviting compliance issues.
What is the solution? Combine automation with human intelligence. Train reviewers on what they’re approving and implement periodic audits.
3. The “Too Many Firefighters” Problem
Firefighter (emergency access) access is meant for temporary, critical access. But in many companies, they become a backdoor for permanent privileged access. I’ve seen in some instances where the FFIDs have SAP_ALL, SAP_NEW assigned
Example: If every second user has firefighter access “just in case,” then what’s really being controlled?
What is the solution? Reduce firefighter usage with strict policies. Ensure that the Firefighter IDs have limited and relevant access, not SAP_ALL. Look at how often your users are asking for such access. Set expiration dates, and enforce approvals before access is granted. A detailed review is must after the usage.
4. Role Design Nightmares
Ever seen a single SAP role with 500+ transaction codes? It happens more often than you’d think. Poorly designed roles create access chaos, security risks, and audit nightmares.
Example: A company that grants “Display All” access thinking it’s harmless—only to realize some reports contain sensitive payroll data.
What is the solution? Follow a least privilege approach. Display tcodes does possess risks. Design roles based on business functions, not user demands and assumptions. And, no, giving everyone SAP_ALL is not a solution!
5. The “Check-the-Box” Compliance Trap
Many organizations treat GRC as a compliance checklist rather than a risk mitigation strategy. The result? A false sense of security.
Example: An enterprise that passes an audit but later discovers a critical access loophole exploited by an insider threat.
What is the solution? Shift from a compliance-first mindset to a risk-first approach. Ask, “What’s the real-world impact of this control?” rather than just checking off audit items.
Final Thoughts: GRC is Not Just About Tools, It’s About Mindset
SAP GRC isn’t just about implementing Access Control, Process Control, or Risk Management modules—it’s about adopting a security and compliance culture. The best GRC strategies combine technology, process rigor, and human intelligence to create a resilient, risk-aware organization.
Readmore: https://togglenow.com/blog/sap-grc-hidden-pitfalls/

#SAP Risk Management#SAP access risk analysis tool#SAP GRC access control solution#SAP segregation of duties automation#SoD risk analysis for SAP
0 notes
Text
12 Expert Tips to Streamline Your Accounts Payable Process in 2025
In today’s volatile business environment, a well-optimized accounts payable (AP) process is no longer a luxury—it’s a necessity. Organizations must embrace innovation and precision to stay ahead. By refining the AP workflow, businesses can reduce errors, enhance cash flow visibility, and strengthen vendor relationships. Below are 12 expert-backed strategies to improve your accounts payable process in 2025.
1. Embrace End-to-End Automation
Manual invoice handling is time-consuming and error-prone. Deploy end-to-end AP automation tools to digitize invoice capture, routing, approvals, and payments. Automation accelerates processing times and drastically reduces human error.
2. Centralized Invoice Management
Disparate systems lead to redundancy and confusion. Centralizing invoice data into one digital repository allows for seamless tracking, reporting, and auditing, ensuring every transaction is transparent and traceable.
3. Implement Three-Way Matching
Adopt a three-way matching system that cross-verifies the purchase order, invoice, and delivery receipt. This practice prevents fraudulent or duplicate payments and ensures that companies only pay for goods or services received.
4. Integrate AP with Procurement
By integrating procurement and AP platforms, data silos are eliminated. This synchronization improves budget control, facilitates accurate forecasting, and strengthens supplier accountability.
5. Utilize Vendor Portals
Vendor self-service portals empower suppliers to submit invoices, update information, and track payment statuses. This reduces back-and-forth communication and allows AP teams to focus on higher-value tasks.
6. Adopt Dynamic Discounting
Negotiate early payment discounts with suppliers. Dynamic discounting not only enhances supplier satisfaction but also improves working capital management. The quicker the payment, the greater the savings.
7. Conduct Regular Reconciliations
Routine reconciliations between accounts and statements prevent discrepancies from snowballing into larger issues. Consistent reviews ensure accuracy and uphold financial integrity.
8. Strengthen Internal Controls
Establish strict approval hierarchies and segregation of duties to mitigate fraud risk. Control frameworks should evolve to include digital authentication and secure access protocols.
9. Leverage Data Analytics
Predictive analytics can offer insights into spending patterns, seasonal cash flow demands, and vendor performance. Harnessing such intelligence refines decision-making and uncovers inefficiencies.
10. Ensure Compliance with E-Invoicing Standards
With governments around the world tightening compliance regulations, especially around tax and invoicing, aligning with e-invoicing standards will help avoid penalties and streamline cross-border transactions.
11. Monitor Key Performance Indicators (KPIs)
Track KPIs like invoice processing time, cost per invoice, and percentage of invoices paid on time. Benchmarking performance fosters a culture of continuous improvement.
12. Partner with Reliable accounts payable services
Outsourcing to trusted accounts payable services providers can yield considerable benefits scalability, access to advanced tools, and process standardization. These experts ensure compliance, reduce operational costs, and drive efficiency across the AP lifecycle.
0 notes
Text
How to Conduct a Fraud Risk Analysis in Financial Reporting

In India, scandals like the Satyam fiasco or the recent IL&FS collapse prove that even giants crumble when fraud risk management fails. For commerce students eyeing careers in auditing or finance and chartered accountants navigating boardrooms, understanding how to dissect fraud risk in financial statements isn’t optional. It’s survival. Here’s how to conduct a fraud risk analysis.
What is Financial Reporting Fraud?
Financial Statement Fraud isn’t creative accounting—it’s manipulation. Think inflated revenues, hidden liabilities, or fake assets. Picture a company overstating sales to attract investors or understating expenses to dodge taxes. The goal? Deception. The tools? Material Misstatement, forged documents, or complex transactions designed to blur reality. In India, where family-run businesses dominate and regulatory gaps persist, accounting fraud thrives when internal controls are weak.
Steps to conduct a Fraud Risk Analysis in Financial Reporting
This systematic methodology will enable you to properly do a fraud risk analysis in financial reporting, therefore assisting you to find possible fraud risks and implement required controls:
Step 1: Map the Fraud Risk Factors
Fraud does not prosper in solitude. Fraud Risk Factors are the red flags. Start with the incentive-pressure trio:
Management incentives: Bonuses tied to unrealistic targets.
Industry pressures: Sectors like real estate or NBFCs (think DHFL) battling liquidity crunches.
Personal greed: Promoters siphoning funds (à la Nirav Modi).
Next, assess opportunities:
Poor financial controls (e.g., no segregation of duties).
Complex group structures (common in Indian conglomerates).
Lenient audit procedures or complacent boards.
Lastly, attitude: A culture that normalizes “minor adjustments” or silences whistleblowers.
Step 2: Utilize Fraud Risk Evaluation Instruments
Fraud Risk Assessment Tools aren’t magic—they’re systematic. Start with forensic accounting techniques. Unlike routine financial audits, forensic accountants dig deeper. They trace discrepancies in accounts receivable, spot fake vendors in accounts payable, or flag inventory mismatches. Tools like Benford’s Law analyze numerical patterns to detect anomalies (e.g., 80% of invoices ending with “5”).
Use financial fraud detection techniques like ratio analysis. Sudden spikes in gross margins without market justification? That’s a red fraud risk indicator. Compare associated data—if a textile firm in Surat reports double the industry’s ROI, dig deeper.
Step 3: Strengthen Internal Controls
Internal controls are your first line of defense. For Indian SMEs, where “trust” often overrules processes, this is critical. Examples:
Segregation of duties: The person approving payments shouldn’t reconcile bank statements.
Mandatory leave policies: Rotate staff to uncover hidden frauds (e.g., a clerk embezzling cash during long tenures).
Whistleblower mechanisms: Mandated under the Companies Act 2013 but often ignored.
Automate where possible. Use ERP systems to flag unusual transactions—say, a junior employee approving a ₹50 lakh vendor payment. Align with Indian Accounting Standards (Ind AS) to ensure transparency.
Step 4: Audit Procedures
The methods, procedures, and techniques used by auditors to gather trustworthy audit data so they may make an informed assessment of an organization's financial health are known as audit procedures. To ascertain the veracity and accuracy of a company's financial statements, audit procedures are carried out. A company's financial reputation and credibility in the eyes of its clients, the market, and possible investors are enhanced by the consistent use of these processes.
Substantive testing: 100% of Q4 transactions should be tested for high-risk areas (such revenue recognition).
Analytical procedures: Compare declared revenues with GST filings or bank deposits.
Third-party confirmations: Contact customers/suppliers directly to confirm outstanding balances.
In India, where cash transactions linger, scrutinize petty cash logs. A ₹10,000 daily withdrawal might hide a ₹3.6 crore annual leak.
Step 5: Fraud Prevention
The goal of fraud prevention is to eliminate incentives, not to apprehend criminals.
Tone at the top: If promoters flout rules (e.g., diverting loans to shell companies), employees will follow.
Regular training: Teach staff to spot fraud risk indicators like missing documents or sudden lifestyle upgrades.
Robust IT systems: Deploy AI to monitor real-time data. A Mumbai-based fintech startup recently used machine learning to flag ₹2 crore in fake invoices within weeks.
Step 6: Forensic Accounting
When fraud surfaces, forensic accounting takes center stage. It’s part detective work, part litigation support.
Asset tracing: Follow the money trail—offshore accounts, benami properties.
Digital forensics: Recover deleted emails or WhatsApp chats (yes, Indian courts accept these as evidence).
Expert testimony: Present findings in SEBI hearings or NCLT (National Company Law Tribunal) disputes.
In the PNB scam, forensic accountants unraveled how Letters of Undertaking (LoUs) were forged for 7 years.
Step 7: Compliance Isn’t Optional
Financial compliance isn’t a burdensome process—it’s a protective measure. It’s essential for safeguarding the business, ensuring its integrity, and avoiding legal or financial risks.
Regular audits: Mandate financial audits by rotation (Companies Act 2013).
Disclosure norms: SEBI’s LODR (Listing Obligations and Disclosure requirement) regulations require detailed risk reporting for listed entities.
Whistleblower protection: The Sarbanes-Oxley Act (SOX) isn’t Indian, but MNCs here adopt its principles.
Questions to understand your ability
What is the first step in conducting a fraud risk analysis in financial reporting?
A) Strengthen internal controls B) Deploy fraud risk assessment tools C) Map the fraud risk factors D) Forensic accounting
Answer: C) Map the fraud risk factors Reason: The first step involves identifying the fraud risk factors by assessing incentives, opportunities, and attitudes that might lead to fraud.
Which of the following is an example of a tool used in fraud risk evaluation?
A) Segregation of duties B) Financial fraud detection techniques like ratio analysis C) Whistleblower mechanisms D) Regular audits
Answer: B) Financial fraud detection techniques like ratio analysis Reason: Fraud risk evaluation tools include techniques like forensic accounting and ratio analysis to spot discrepancies or anomalies in financial data.
Why is segregation of duties important in preventing fraud?
A) It helps auditors to test 100% of transactions B) It reduces the potential for fraud by preventing any single person from handling all aspects of a transaction C) It improves the accuracy of financial statements D) It ensures compliance with tax regulations
Answer: B) It reduces the potential for fraud by preventing any single person from handling all aspects of a transaction Reason: Segregation of duties ensures that no individual is responsible for all parts of a financial transaction, which helps to reduce fraud risk.
Which of the following is a key aspect of fraud prevention?
A) Detecting fraud after it occurs B) Increasing audit frequency C) Eliminating the incentives that encourage fraudulent behavior D) Relying solely on whistleblower mechanisms
Answer: C) Eliminating the incentives that encourage fraudulent behavior Reason: Fraud prevention focuses on removing the motivations or incentives that encourage employees or management to commit fraud.
What does forensic accounting primarily involve when fraud is detected?
A) Enhancing company culture B) Asset tracking and recovering digital evidence C) Training employees on fraud prevention D) Conducting routine audits
Answer: B) Asset tracking and recovering digital evidence Reason: Forensic accounting involves tracing assets, recovering digital evidence, and providing support for legal proceedings to resolve fraud-related issues.
Conclusion
In conclusion, conducting a fraud risk analysis in financial reporting is crucial for detecting, preventing, and addressing financial fraud. By mapping fraud risk factors, utilizing specialized tools, strengthening internal controls, and ensuring compliance, organizations can safeguard their financial integrity. Through proactive measures like forensic accounting and fraud prevention strategies, businesses can protect themselves from significant losses, ensuring long-term stability and credibility in the market.
0 notes
Text
How Accounting Consultants Can Help Improve Internal Controls and Financial Reporting?

Strong internal controls and accurate financial reporting are the foundation of any well-run business. They protect assets, ensure compliance with regulations, and provide reliable information for decision-making. However, many small to mid-sized businesses struggle to maintain effective controls or produce consistent, error-free reports. This is where accounting consultants can make a significant impact. With their expertise and objective perspective, they can identify weaknesses, implement best practices, and help your business achieve greater financial transparency and stability.
Enhancing Internal Controls
Internal controls are the systems and procedures businesses use to prevent fraud, reduce risk, and ensure the accuracy of financial data. These include processes such as approving transactions, segregating duties, and reconciling accounts. Unfortunately, businesses often operate with outdated or incomplete controls, leaving them vulnerable to errors or fraud.
Accounting consultants in Fort Worth, TX begin by conducting a thorough evaluation of your current internal control environment. They review key processes—such as cash handling, payroll, purchasing, and inventory management—to identify inefficiencies or risks. Once they’ve assessed the gaps, they propose tailored improvements designed to strengthen oversight without overburdening your team.
For example, a consultant may recommend changes like separating invoice approval from payment processing or instituting regular reconciliations of bank and credit card accounts. These adjustments, while often simple, can significantly reduce the risk of financial misstatements or misuse of funds.
Improving Financial Reporting Accuracy
Timely and accurate financial reporting is essential for monitoring business performance, satisfying stakeholders, and meeting compliance obligations. However, poor reporting often stems from inconsistent accounting practices, outdated software, or a lack of financial expertise.
An accounting consultant can help you develop a more efficient and reliable reporting system. This includes creating standard operating procedures for closing books, designing customized financial reports, and ensuring compliance with generally accepted accounting principles (GAAP). Consultants also train your staff on proper reporting techniques and accounting standards, reducing dependency on guesswork or manual processes.
Additionally, they can help automate repetitive tasks and integrate software solutions that streamline financial reporting. Whether you’re using QuickBooks, Xero, or a more complex ERP system, consultants ensure that your technology supports accuracy and provides the right insights at the right time.
Reducing the Risk of Errors and Fraud
Errors in financial statements can lead to incorrect decision-making, lost credibility, and regulatory consequences. Fraud, whether internal or external, can cause devastating financial and reputational damage. Accounting consultants help mitigate both by introducing checks and balances, routine audits, and real-time monitoring systems.
They also develop protocols for detecting and investigating irregularities, helping businesses respond swiftly and decisively. By promoting a culture of transparency and accountability, they create an environment where financial integrity is a top priority.
Conclusion
Working with an accounting consultant is a proactive investment in your business’s financial health. By improving internal controls and enhancing the accuracy of financial reporting, they help protect your assets, support informed decision-making, and prepare you for sustainable growth. Their guidance can transform your accounting function from a basic necessity into a strategic advantage.
#Accounting consultants#Improve#internal controls#Financial reporting#accounting#accounting services
0 notes
Text
Streamlining Financial Processes: The Role of Medical Practice Accounting Services
Advanced Professional recognizes the complexities inherent in medical practice accounting services, which are essential for maintaining financial health and regulatory compliance. By streamlining financial processes, these services enable healthcare providers to focus more on patient care while ensuring accurate billing, efficient claims management, and timely reimbursements. This integration of specialized accounting solutions enhances operational efficiency, reduces administrative burdens, and supports informed decision-making, ultimately contributing to the growth and sustainability of medical practices.
Implementing Automated Billing and Invoicing Systems to Enhance Financial Efficiency
Automating billing and invoicing processes is crucial in medical practice accounting services to reduce errors and accelerate revenue cycles. Advanced Professional recommends investing in specialized accounting software that integrates seamlessly with medical billing systems, ensuring accurate and timely billing. Features such as automated invoicing, real-time payment tracking, and electronic claim submissions streamline operations, minimize outstanding payments, and enhance cash flow management. By adopting these technologies, medical practices can focus more on patient care while maintaining financial accuracy and efficiency.
Utilizing Integrated Accounting Software to Streamline Financial Workflows
Integrated accounting software serves as the backbone of efficient financial operations in medical practices. Advanced Professional emphasizes the importance of selecting software that offers automated data entry, expense tracking, and customizable reporting. Such tools reduce manual errors, enhance data accuracy, and provide real-time financial insights. Moreover, integration with other practice management systems ensures seamless data flow, reducing redundancy and improving overall productivity. Leveraging these software solutions allows healthcare providers to make informed financial decisions swiftly.
Ensuring Regulatory Compliance Through Accurate Financial Record-Keeping
Maintaining accurate and compliant financial records is non-negotiable in medical practice accounting services. Advanced Professional advises that medical practices adhere to healthcare regulations and tax laws, including HIPAA for patient data security. Implementing robust internal controls, such as segregation of duties and regular audits, helps prevent fraud and ensures financial integrity. Utilizing specialized accounting software can assist in tracking expenses, managing reimbursements, and generating reports that meet regulatory standards, thereby reducing the risk of compliance issues.
Enhancing Cash Flow Management Through Professional Accounting Services
Effective cash flow management is vital for the sustainability of medical practices. Advanced Professional highlights that professional accounting services can assist in monitoring accounts receivable, ensuring timely collection of payments, and managing accounts payable to maintain good relationships with suppliers. Developing comprehensive budgets and financial forecasts enables practices to anticipate future financial needs and make informed decisions regarding investments and expenditures. By leveraging expert accounting services, healthcare providers can achieve financial stability and focus on delivering quality patient care.
Leveraging Financial Reporting and Analysis to Drive Strategic Decisions
Regular financial reporting and analysis provide valuable insights into a medical practice's financial health. Advanced Professional recommends generating customizable reports that track key financial metrics, identify trends, and inform strategic planning. Utilizing accounting software with advanced reporting capabilities allows practitioners to monitor performance, assess profitability, and make data-driven decisions. This analytical approach supports the optimization of resource allocation, identification of growth opportunities, and enhancement of overall practice efficiency.
Mitigating Errors and Enhancing Accuracy Through Automated Financial Processes
Reducing manual errors is a significant advantage of automating financial processes in medical practices. Advanced Professional notes that automated systems for data entry, bank reconciliations, and expense tracking minimize human errors and enhance data accuracy. Implementing automated workflows streamlines operations, saves time, and reduces the risk of discrepancies in financial records. This increased accuracy ensures reliable financial reporting and supports effective decision-making within the practice.
Improving Financial Transparency and Patient Satisfaction with Streamlined Billing
Streamlined billing processes not only enhance financial efficiency but also improve patient satisfaction. Advanced Professional emphasizes that transparent billing practices, facilitated by automated systems, provide patients with clear and accurate statements, reducing confusion and disputes. Efficient billing ensures timely reimbursements and fosters trust between patients and healthcare providers. By adopting streamlined billing practices, medical practices can enhance patient experiences while maintaining financial health.
Conclusion
Streamlining financial processes through specialized medical practice accounting services is essential for enhancing operational efficiency, ensuring compliance, and improving patient satisfaction. Advanced Professional advocates for the integration of automated billing systems, robust accounting software, and professional financial management to achieve these objectives. By embracing these strategies, medical practices can navigate the complexities of healthcare finance effectively, allowing providers to focus on delivering exceptional patient care while maintaining financial stability.
0 notes
Text
How to Streamline Your Accounting and Compliance Processes

In today's fast-paced business environment, companies face growing pressure to meet regulatory requirements, ensure tax compliance, and maintain accurate financial records. The complexity of managing accounting and compliance processes can overwhelm organizations, especially when balancing multiple tasks and deadlines. Streamlining accounting and compliance services is essential for businesses looking to enhance efficiency, reduce costs, and avoid the risk of non-compliance.
Here are some proven strategies to streamline your accounting and compliance processes:
1. Adopt Accounting Software and Automation Tools
Technology plays a crucial role in simplifying accounting and compliance processes. Leveraging accounting software allows businesses to automate routine tasks, such as invoicing, payroll, expense tracking, and financial reporting. Tools like QuickBooks, Xero, and Sage enable businesses to integrate various financial functions into one platform. These tools reduce the time spent on manual data entry and minimize human errors, improving the overall accuracy of financial records.
Additionally, automation tools can be used to track and manage compliance deadlines, ensuring that you never miss an important filing date for taxes, annual returns, or regulatory submissions. Automated reminders and alerts help businesses stay on top of their compliance obligations.
2. Centralize Financial Data
A disorganized or fragmented approach to managing financial data can lead to inefficiencies and compliance risks. By centralizing financial data in a single system, businesses can improve the accuracy and accessibility of their records. This approach also ensures that all stakeholders, such as accountants, compliance officers, and auditors, have real-time access to the most up-to-date information.
Cloud-based accounting systems allow teams to work remotely and collaborate in real-time. Centralizing data also makes it easier to generate reports for audits, tax filings, and regulatory reporting, significantly reducing the time spent gathering and organizing information.
3. Standardize Processes and Documentation
Standardizing accounting and compliance processes ensures consistency and clarity in how financial tasks are performed. Businesses should establish clear procedures for handling accounting functions, including invoicing, expense tracking, tax calculations, and preparing financial statements. Having a standardized approach minimizes the chances of errors and ensures compliance with relevant regulations.
Moreover, businesses should develop standardized templates and checklists for key compliance documentation, such as tax returns, audit reports, and financial disclosures. This can reduce the time spent on preparing these documents and make it easier to maintain compliance year after year.
4. Outsource to Accounting and Compliance Experts
Outsourcing accounting and compliance services can help businesses streamline their operations and ensure expert-level accuracy. Partnering with an external provider that specializes in accounting and compliance services allows organizations to tap into the knowledge and experience of professionals who are up to date with the latest regulations and tax laws.
Outsourcing offers several benefits, including:
Cost savings: Avoid hiring full-time staff for accounting and compliance tasks.
Expertise: Access to highly skilled professionals who understand industry-specific compliance requirements.
Scalability: As your business grows, an outsourcing partner can scale their services to meet your evolving needs.
5. Implement Robust Internal Controls
Internal controls are essential for maintaining financial integrity and ensuring compliance. By implementing effective controls, businesses can prevent fraud, ensure accurate financial reporting, and stay compliant with regulatory requirements. Some key internal controls include:
Segregation of duties: Assign different people to handle different aspects of financial processes, such as authorizing payments, recording transactions, and reconciling accounts.
Regular reconciliation: Perform regular reconciliations to ensure that financial records match bank statements and other supporting documents.
Access controls: Limit access to sensitive financial data to authorized personnel only.
Regularly reviewing and improving internal controls helps businesses mitigate compliance risks and maintain financial stability.
6. Stay Updated on Regulatory Changes
Accounting and compliance regulations are subject to frequent changes, making it essential for businesses to stay informed. Keeping up to date with new tax laws, industry regulations, and compliance standards is crucial for avoiding penalties and fines.
One effective way to stay updated is to subscribe to industry newsletters, follow regulatory bodies, or work with accounting firms that offer ongoing training and updates. Implementing a continuous learning culture within your finance team helps ensure that your business is always prepared for new regulatory requirements.
7. Conduct Regular Audits
Regular audits are an important part of ensuring compliance and identifying areas where your accounting and compliance processes can be improved. Audits provide a detailed review of financial records, transactions, and compliance with tax laws and regulations.
By performing internal audits or hiring external auditors, businesses can spot discrepancies, address compliance gaps, and refine their accounting processes. Regular audits help organizations maintain transparency, foster trust with stakeholders, and minimize the risk of regulatory violations.
8. Integrate Accounting and Compliance Functions
Accounting and compliance are often treated as separate functions, but integrating these areas can create efficiencies and improve workflow. By having one team handle both accounting and compliance, businesses can ensure a seamless connection between financial reporting and regulatory requirements.
For example, your accounting team can ensure that financial statements are accurate and ready for compliance checks, while your compliance team can review them for regulatory adherence. Integrating these functions helps streamline reporting, reduces duplication of work, and ensures that both areas are aligned.
9. Implement Continuous Process Improvement
Streamlining accounting and compliance is an ongoing process. Businesses should regularly assess and improve their procedures to enhance efficiency and adapt to changing regulations. Encourage feedback from employees, review performance metrics, and continuously seek ways to optimize processes.
By fostering a culture of continuous improvement, businesses can identify bottlenecks, address inefficiencies, and streamline workflows over time.
Conclusion
Streamlining your accounting and compliance services is vital for ensuring that your business remains financially sound, tax-compliant, and free from legal risks. By leveraging technology, outsourcing expert services, standardizing processes, and staying updated on regulations, your organization can enhance its efficiency and reduce the burden of managing these complex functions. These strategies not only save time and resources but also contribute to building a more transparent, accountable, and compliant business environment.
0 notes