#Software Perimeter
Explore tagged Tumblr posts
Text
Software Defined Perimeter Market Size, Share, Analysis, Forecast, Growth 2032: Demand Trends Across Key Sectors
Software Defined Perimeter Market was valued at USD 7.0 billion in 2023 and is expected to reach USD 56.9 Billion by 2032, growing at a CAGR of 26.19% from 2024-2032.
The Software Defined Perimeter (SDP) market is rapidly emerging as a pivotal technology in reshaping modern cybersecurity frameworks. By eliminating traditional perimeter-based defenses and implementing a dynamic, identity-driven access model, SDP offers unmatched protection against sophisticated threats. This innovative approach enables organizations to reduce attack surfaces, secure remote access, and safeguard cloud infrastructure with greater agility and precision. As cyber threats evolve in complexity, enterprises are increasingly adopting SDP solutions to enhance control, visibility, and trust across distributed IT environments.
Software Defined Perimeter Market hyper-connected digital ecosystem, the Software Defined Perimeter market stands at the forefront of a new era in cybersecurity. Organizations across industries are turning to SDP to enforce strict access control by verifying users and devices before granting access to critical resources. With zero-trust models becoming the gold standard, SDP solutions are no longer optional but essential tools in every cybersecurity strategy. The paradigm shift from legacy systems to software-defined, cloud-centric infrastructure continues to drive the relevance and growth of the SDP market.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3700
Market Keyplayers:
Cisco Systems, Inc. - Cisco
Check Point Software Technologies Ltd. - Check Point
Palo Alto Networks, Inc. - Palo Alto Networks
Akamai Technologies, Inc. - Akamai
Zscaler, Inc. - Zscaler
Broadcom Inc. (Symantec Corporation) - Broadcom
Fortinet, Inc. - Fortinet
Juniper Networks, Inc. - Juniper Networks
IBM Corporation - IBM
Cloudflare, Inc. - Cloudflare
Google LLC (BeyondCorp) - Google
Microsoft Corporation (Azure AD Conditional Access) - Microsoft
Intel Corporation - Intel
Okta, Inc. - Okta
Forcepoint LLC - Forcepoint
Unisys Corporation - Unisys
AppGate, Inc. - AppGate
F5 Networks, Inc. - F5
Perimeter 81 - Perimeter 81
Centrify Corporation (now Delinea) - Delinea
Market Analysis The SDP market is experiencing significant momentum fueled by increased adoption of cloud services, remote work models, and the growing frequency of cyberattacks. Companies are prioritizing agile security frameworks capable of adapting to dynamic IT landscapes. SDP meets these needs by enabling micro-segmentation, invisible infrastructure, and continuous user verification. As a result, the market is witnessing participation from both established cybersecurity vendors and emerging tech innovators, intensifying competition and fostering technological advancements.
Market Trends
Rise in demand for zero-trust network access (ZTNA)
Growing integration of SDP with identity and access management (IAM) platforms
Expansion of SDP applications across hybrid and multi-cloud environments
Increasing use of AI and machine learning for adaptive security controls
Surge in adoption by small and medium-sized enterprises (SMEs) for cost-effective security
Market Scope The scope of the Software Defined Perimeter market extends across a wide range of industries including finance, healthcare, IT, manufacturing, and government sectors. Its flexibility and scalability allow for tailored implementations, whether for securing IoT ecosystems, protecting remote users, or ensuring compliance in regulated sectors. As enterprises shift toward decentralized operations and virtual infrastructures, SDP solutions are proving critical in enabling secure digital transformation strategies globally.
Market Forecast The future outlook for the SDP market remains highly promising, marked by rapid innovation and broader market penetration. Adoption is expected to expand as businesses become more aware of the limitations of perimeter-based security and recognize the value of software-defined access controls. Continued investments in research and development are anticipated to enhance solution capabilities, reduce deployment complexities, and streamline integration with existing systems. As digital ecosystems grow more complex, SDP is set to play a foundational role in securing the modern enterprise.
Access Complete Report: https://www.snsinsider.com/reports/software-defined-perimeter-market-3700
Conclusion As cyber threats become more advanced and traditional defenses falter, the Software Defined Perimeter market offers a bold new approach to security—one that is resilient, flexible, and built for the future. Its rise signals a strategic pivot in how organizations think about trust, access, and protection. For stakeholders looking to future-proof their digital infrastructure, investing in SDP is not just a security measure—it's a transformative move toward smarter, safer operations in the digital age.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
#Software Defined Perimeter Market#Software Defined Perimeter Market Scope#Software Defined Perimeter Market Growth#Software Defined Perimeter Market Trends
0 notes
Text
Software Defined Perimeter Market Demand, Challenges, and Future Trends 2032
Software Defined Perimeter (SDP) Market is transforming cybersecurity by providing a dynamic, identity-based access model that significantly reduces attack surfaces. As organizations shift towards cloud computing and remote work, the need for robust security frameworks has intensified. SDP solutions are gaining widespread adoption, enabling businesses to mitigate cyber threats while ensuring secure access to critical assets.
Software Defined Perimeter Market continues to evolve as enterprises prioritize zero-trust security models over traditional network-based security approaches. By authenticating users and devices before granting access, SDP minimizes the risk of unauthorized intrusions. As cyber threats grow more sophisticated, organizations across industries are investing in SDP solutions to enhance network security, protect sensitive data, and ensure regulatory compliance.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/3700
Market Keyplayers:
Cisco Systems, Inc. - Cisco
Check Point Software Technologies Ltd. - Check Point
Palo Alto Networks, Inc. - Palo Alto Networks
Akamai Technologies, Inc. - Akamai
Zscaler, Inc. - Zscaler
Broadcom Inc. (Symantec Corporation) - Broadcom
Fortinet, Inc. - Fortinet
Juniper Networks, Inc. - Juniper Networks
IBM Corporation - IBM
Cloudflare, Inc. - Cloudflare
Google LLC (BeyondCorp) - Google
Microsoft Corporation (Azure AD Conditional Access) - Microsoft
Intel Corporation - Intel
Okta, Inc. - Okta
Forcepoint LLC - Forcepoint
Unisys Corporation - Unisys
AppGate, Inc. - AppGate
F5 Networks, Inc. - F5
Perimeter 81 - Perimeter 81
Centrify Corporation (now Delinea) - Delinea
Market Trends Driving Growth
1. Adoption of Zero-Trust Security Models
With an increasing number of cyberattacks targeting conventional network defenses, businesses are embracing zero-trust principles. SDP solutions enforce strict identity verification, ensuring that users can only access authorized resources, reducing lateral movement by attackers.
2. Growth of Remote Work and Cloud Computing
The shift to remote work and cloud-based infrastructures has accelerated SDP adoption. Organizations are replacing traditional VPNs with SDP solutions that offer seamless, scalable, and secure access to enterprise resources, regardless of location.
3. Rise in Cybersecurity Threats and Data Breaches
The surge in cyber threats, including ransomware, phishing, and insider attacks, has highlighted the need for enhanced security solutions. SDP helps mitigate these risks by obscuring network infrastructure and enforcing strict access controls.
4. Increasing Regulatory Compliance Requirements
Governments and industry regulators are enforcing stringent data protection and cybersecurity laws. SDP solutions enable organizations to comply with frameworks such as GDPR, HIPAA, and NIST by ensuring secure access and continuous monitoring.
5. Integration of AI and Machine Learning
Artificial intelligence (AI) and machine learning (ML) are being integrated into SDP platforms to enhance threat detection, automate responses, and analyze user behavior patterns for potential risks. This proactive approach strengthens network security.
Enquiry of This Report: https://www.snsinsider.com/enquiry/3700
Market Segmentation:
By Deployment
Cloud
On-premise
By Organization Size
Large Enterprises
Small & Medium Enterprises
By End-Use
BFSI
IT & Telecom
Manufacturing
Government
Healthcare
Education
Market Analysis and Current Landscape
Key factors influencing market expansion include:
Rise in Hybrid and Multi-Cloud Deployments: Businesses are increasingly adopting hybrid cloud models, requiring secure, flexible, and scalable security solutions like SDP.
Enterprise Focus on Secure Access Management: SDP eliminates the weaknesses of traditional perimeter-based security, offering granular, context-aware access control.
Investment in Next-Gen Cybersecurity Solutions: Organizations are allocating significant budgets to enhance cybersecurity infrastructure and replace legacy security models.
Despite its rapid growth, the market faces challenges such as integration complexities, lack of awareness among smaller enterprises, and resistance to adopting new security paradigms. However, with continuous advancements in technology and increasing cybersecurity threats, the adoption of SDP solutions is expected to rise significantly.
Future Prospects: What Lies Ahead?
1. Expansion of SDP in Small and Medium Enterprises (SMEs)
While large enterprises have led SDP adoption, SMEs are recognizing its benefits. With scalable and cost-effective cloud-based SDP solutions emerging, adoption among smaller businesses is expected to increase.
2. Evolution of Zero-Trust Network Access (ZTNA)
SDP is a critical component of Zero-Trust Network Access (ZTNA), which is gaining traction as businesses move towards comprehensive cybersecurity frameworks. ZTNA adoption is expected to accelerate, driving further growth in the SDP market.
3. Increased Investment in AI-Driven Security
AI-powered SDP solutions will continue to evolve, providing real-time threat detection, automated response mechanisms, and enhanced user authentication. The integration of AI will improve network security efficiency.
4. Growth in SDP for IoT Security
With the exponential rise in connected devices, securing IoT networks is becoming a top priority. SDP solutions will play a key role in preventing unauthorized access to IoT infrastructure and mitigating potential cyber threats.
5. Greater Collaboration Between Cybersecurity Providers
Cybersecurity vendors are forming strategic partnerships to offer integrated security solutions. SDP providers are collaborating with cloud service providers, identity management firms, and AI developers to enhance security offerings.
Access Complete Report: https://www.snsinsider.com/reports/software-defined-perimeter-market-3700
Conclusion
The Software Defined Perimeter market is poised for exponential growth as organizations prioritize secure access management and zero-trust security models. With increasing cyber threats, regulatory pressures, and the shift to cloud environments, SDP solutions are becoming a fundamental component of modern cybersecurity strategies. As technology advances and adoption expands, the future of SDP will be defined by AI integration, zero-trust evolution, and enhanced security frameworks, ensuring a safer digital landscape for enterprises worldwide.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
#Software Defined Perimeter market#Software Defined Perimeter market Scope#Software Defined Perimeter market Growth#Software Defined Perimeter market Trends
0 notes
Text

cherry on top 🍒 mafia boss!seungcheol x reader. (4)
stories like this always end with a damsel in distress. except—this time around—you’re not the one who needs saving. previous chapter + masterlist.







📄 Minutes of strategic information meeting, filed by Kim Mingyu (Mafia Soldier, Logistics & Recon)
Date: ██████████ Location: Safehouse Omega-9, Undisclosed City Perimeter Time: 03:17 HRS
ATTENDEES:
Yoon Jeonghan (Underboss)
Lee Chan (Combat Unit Leader)
Chwe Hansol (Surveillance Division)
Kim Mingyu (Logistics & Recon; Recording Officer)
Civilian Target [REDACTED] (Unauthorized Attendee)
AGENDA:
Contingency Plan for Retrieval of Boss (S.Coups)
Chain of Command During Absence
External Threat Assessment
[BEGIN TRANSCRIPT]
JEONGHAN: We go in through the east dock. Two snipers posted by 03:40. Chan leads breach. Hansol, your eyes stay on thermal—no improvisation this time.
HANSOL: I never improvise. My brilliance is structured.
CHAN: Can we not do this right now?
JEONGHAN: [ignoring them] Mingyu, once we get him out, you're on evac. Full blackout route. No trackers, no chatter.
MINGYU: Copy.
HANSOL: Any updates on who turned? Someone had to leak coordinates.
CHAN: There’s a list. We’ll handle it after we bring the boss home. One fire at a time.
[DOOR SLAMS OPEN. SOUND OF HIGH-HEELED FOOTSTEPS. SILENCE.]
CIVILIAN TARGET: You’re planning this without me?
JEONGHAN: [visibly tense] You weren’t invited.
CIVILIAN TARGET: He’s my belo—my boyfriend, Jeonghan. You think I’m just going to sit around while you play war games?
JEONGHAN: This isn’t a movie. You’re a civilian. You don’t belong in this room.
CIVILIAN TARGET: No, I’m the reason he still believes in soft things. I belong more than half the people at this table.
CHAN: She’s got a point.
JEONGHAN: Chan.
CHAN: I’m just saying. She’s not exactly fragile.
HANSOL: She did rewire one of my bugs with a paperclip. That was... not unimpressive.
JEONGHAN: [sighs] This isn’t about guts. It’s about blood.
CIVILIAN TARGET: Then you should know mine’s already on the line. Every second he’s gone, I feel it. And I’m done being sidelined. I’m not here to ask. I’m here to help.
[BEAT OF SILENCE. THEN—]
JEONGHAN: You get one job. And if you screw it up, I’ll personally drag you out.
CIVILIAN TARGET: Deal.
JEONGHAN: Hansol, give her the map. Mingyu, loop her in.
MINGYU: You’re going to need a comm. And a bulletproof vest.
CIVILIAN TARGET: Got both. And a knife in my boot.
CHAN: Okay, badass.
[MEETING CONTINUED UNDER LEVEL-2 SECRECY PROTOCOLS. TRANSCRIPT REDACTED. END OF MINUTES.]
FINAL NOTES:
Civilian Target formally added to Operation Homecoming roster.
Jeonghan authorized conditional field involvement.
Morale status: heightened.
Risk level: astronomically high.

🗂️ Operation Homecoming: Field Notes & Briefing Report, compiled by mafia underboss, Yoon Jeonghan
Clearance Level: Top Confidential Date Logged: ██████████ Location: Safehouse Omega-9
SUMMARY: Boss (S.Coups) was captured 48 hours ago following the receipt of a falsified emergency ping traced back to the civilian target’s encoded channel. The ping claimed she’d been injured and was en route to an undisclosed hospital in Sector D. According to surveillance logs, the Boss diverted course alone, abandoning standard security protocol. We believe he was intentionally isolated through signal jamming, then intercepted at the underpass beneath Route 14.
AUTOPSY OF THE TRAP:
Fake GPS tag mimicked civilian target’s bio-signal pattern
Voice distortion software replicated her distress call
EMP deployed upon vehicle arrival to disable tracking
Tactical unit waited with sedation-grade rounds
CURRENT LOCATION OF BOSS: Confirmed. Underground storage facility, formerly Syndicate-aligned. Defected cell now controls the zone. Reinforcements on site. Boss presumed alive—last thermal footage confirms faint movement.
INTERVENTION STRATEGY: OPERATION HOMECOMING
Phase One – Extraction:
Entry through east dock (03:40 HRS)
Chan leads breach unit, Hansol on thermal, Mingyu handling evac
All units silent channel only
Phase Two – Internal Sweep:
Civilian target assigned distraction and misdirection role (see below)
Two-minute window to locate and stabilize Boss
Phase Three – Extraction + Fade:
Mingyu initiates blackout route
Decoys deployed on west perimeter to delay pursuit
Rendezvous at Site Echo
CIVILIAN TARGET: PERFORMANCE LOG
Arrived wearing borrowed Kevlar and jeans tucked into combat boots. Asked if bulletproof vests same in women’s sizes. Did not wait for response.
Showed immediate enthusiasm, zero tactical finesse. Hansol gave her the map. She held it upside down. Twice.
Informed her she’d be working as the visual diversion. Her response: “Like bait?” Followed by: “Cool. I’m good at being annoying.”
Surprisingly effective. Created a loud enough ruckus on the perimeter to draw three guards off their posts. Managed to bluff her way past checkpoint by pretending to be a lost food delivery driver. Claimed she had gluten-free soba for a man named Kevin. There is no Kevin.
Still not sure how she pulled it off.
When Boss was found, he was semi-conscious but breathing. Whispered her name first.
END STATUS:
Boss retrieved.
Minimal casualties (1 injured – not fatal)
Facility compromised but not traced
Civilian target cried in the van. Then threatened to punch me for writing that down. I'm writing it down anyway.
FOOTNOTE — for Seungcheol’s eyes only: You’re reckless, stubborn, and impossible to reason with. But apparently, that’s your thing. You’re also luckier than most of us ever will be.
She didn’t sleep. Not once. Kept looking at every door like you might walk through it.
When you did, she didn’t even say anything. Just threw her arms around you like gravity stopped working.
Try not to make her go through that again.
– YJH

📱 Phone history log, filed by mafia soldier Chwe Hansol
Device: S.Coups' Personal Line (Encrypted Channel #017) Status: Outgoing Messages Only – Blocked by Signal Jammer Timestamp Range: ██:██–██:██ (Time of Abduction)
NOTE: Texts never reached intended recipient. Recovered during post-mission diagnostics. For archival purposes.
[01:12 AM] Where are you? They said you were hurt. I'm on my way.
[01:15 AM] Which hospital? No one's answering. This isn't funny. Call me.
[01:17 AM] Your signal keeps bouncing. Something's wrong. Stay where you are.
[01:21 AM] I swear to god if they laid a hand on you
[01:24 AM] No ambulance ever came.
[01:25 AM] This is a setup.
[01:27 AM] I'm so stupid. They used you. Fuck fuck fuck
[01:28 AM] I should've followed protocol. Should’ve sent Mingyu. Should’ve sent anyone but me.
[01:30 AM] If you get this, lock all the windows. Call Jeonghan. Stay put.
[01:34 AM] They knew I’d come for you.
[01:36 AM] This isn’t your fault.
[01:39 AM] Don’t come after me.
[01:41 AM] Love, beloved, please. Don’t try to save me.
[01:45 AM] You always do this—you throw yourself into fires you don't understand.
[01:49 AM] If they hurt you because of me, I’ll never forgive myself.
[01:52 AM] Tell Jeonghan to burn everything. Get out. Go far.
[01:54 AM] Forget me if you have to. Just live.
[02:01 AM] I love you. Please, please, please, don’t be stupid.
[END OF RECOVERED LOG]








📰 Excerpt from "The Ethics of Mafias: Love in the Line of Fire", a follow-up think piece by Xu Minghao
... If leadership within organized crime is already an ethical minefield, then love within it is something more volatile still: a paradox of vulnerability embedded in violence. New whispers surround the figure known only as S.Coups—the alleged mafia boss whose name, until recently, conjured images of discipline, domination, and an empire forged in precision.
Now, another narrative has emerged. One that reshapes how we understand not just the man, but the very myth he embodies.
According to rumors sourced from both within and outside the organization, S.Coups may have a romantic partner. Not a fellow operative, nor a political alliance. But a civilian. Someone unaffiliated and—crucially—untouched by the bloodied logic of the underworld.
If this is true, the implications are vast.
To love in his position is a risk. It is weakness, some would say. Yet others might argue that such love is the only thing capable of keeping a man like him from becoming monstrous. If the rumors are accurate, she is the reason he looks over his shoulder less. The reason he checks his own wrath. The reason his most trusted lieutenants have stopped fearing him and started worrying about him.
Love, here, is not a diversion. It is discipline.
And perhaps that is the most fascinating ethical twist of all: that this boss, so often theorized as either tyrant or savior, might be both—because of her.
Some say he texts her between assassinations. That he buys her gummy bears because she mentioned liking them once, months ago. That he has started folding her laundry and learning her aunt’s dietary restrictions. These are, of course, unconfirmed. They seem almost laughably mundane. But within the shadowed world of syndicates and secret wars, what could be more radical than tenderness?
Others claim that he was taken. There are now verified reports of a failed abduction and his eventual rescue. She was allegedly involved. They say she showed up unarmed, untrained, and utterly unafraid. They say she demanded to be part of the rescue mission. They say she was reckless, infuriating, and ultimately, instrumental.
And that when he saw her again, he wept.
To be loved, it turns out, is not always soft. Sometimes, it is brutal and inelegant and wildly inconvenient. But in the context of a life built on violence, to be loved is to be saved. Again and again. In the ways that matter.
Whether S.Coups is worthy of that love is not the question. The question is whether it has already changed him. Whether, in the end, the girl outside the syndicate might be the only thing real in a world made of smoke and mirrors.
And whether that, more than power or fear, will be his lasting legacy.
Mafia boss S.Coups is many things. Protector, manipulator. Brother, enemy, friend.
It seems we must add two more things:
Lover, and loved.

FIN. THANK YOU FOR READING CHERRY ON TOP!
› scroll through all my work ദ്ദി ˉ͈̀꒳ˉ͈́ )✧ ᶻ 𝗓 𐰁 .ᐟ my masterlist | @xinganhao
#seungcheol x reader#scoups x reader#seungcheol imagines#scoups imagines#seungcheol smau#scoups smau#svt text imagines#svt x reader#seventeen x reader#svt smau#seventeen smau#── ᵎᵎ ✦ mine#── ᵎᵎ ✦ series: cot
973 notes
·
View notes
Text
Dove (part seven)
Leon Kennedy x female reader (bodyguard trope and the slowest, slow burn I swear)

Part one. Part two. Part three. Part four. Part five. Part six. Part seven.
---
A tense knot has formed right between Leon’s shoulder blades – can feel it pull when he tilts his head side to side, but it doesn’t seem to be loosening. Can’t even blame it on sleeping on the sofa cos he hasn’t laid down to sleep since the call with Hunnigan, stays sat up right. He’s athletic, he can jump up to his feet from horizontal but it’ll add a second or so to his reaction time and he’s not taking the risk.
He's on edge and he doesn’t like it. The ball of anxiety in his gut has saved his life more times than he can count, but it shouldn’t be necessary in this situation, should it? He’s set up in a safe house, literally off some beaten track in the middle of nowhere – location chosen and distributed by encrypted software so, technically, no-one in the DSO knows where he is either. It’s rigged up to the heavens with security measures - cameras, alarm systems, motion detector - explosion-proof windows, reinforced doors, all topped off with his favourite array of weapons in the duffel bag, currently resting by his still booted feet.
The objective of his mission hasn’t changed after the intel he’s received, that some foreign agency has had access to the CCTV feed for who knows how many hours before they were cut off. He should feel reassured that the quality of the footage was awful – it was only by how many times he’s encountered Lickers that he could even tell that’s what the creatures were when he’d be presented with the grainy images. He didn’t see the footage of you being rescued, but it would be a cruel kick in the gut to find that feed had been HD.
He lifts an arm – his left, keeping his right arm free, his accuracy is better by millimetres with his right – and rubs the knot, hoping to relieve the tension. It's not 100% confirmed they are looking or will be looking for you either, but why would anyone link up to the CCTV circuit if not to check on the outcome of their operation?
His immediate thought had been to up the frequency of his perimeter checks, one every two hours. He could do that at night, sure – military training taught him the correct and most efficient techniques to power nap – but in the day it would be harder without worrying you about what’s changed.
You wanted updates. Hell, you were entitled to updates. But he wants to give you good news, doesn’t wanna add to the weight on your shoulders with what could be nothing. It’s stupid, he knows it’s stupid, but in these sweet domestic moments the two of you have been sharing, he’s been pretending it’s something else – friends watching television, cooking a meal together – the sweet smiles the two of you exchange, but it’s all ripped apart the moment he has to do his checks. He can see the worry settle on your face then, a reminder of where you are with the flick of the safety off his gun and the twist of the lock as he goes outside to conduct surveillance.
Speaking of, his phone beeps for his next circuit on the building and he’s up on his feet in the blink of an eye. He pats his cargo pocket out of habit for the keys on the walk over to the garage door, but finds himself pausing outside your bedroom, his eyes focusing on the handle. You should still be pretty under with those sleeping pills – note to self, he’ll need to start weening you off them from now on, far too easy to get addicted. It wouldn’t hurt to just… check you were okay, would it?
No – that’s what you’re here, why he’s here – to protect you.
It would just be doing his job.
He presses down on the handle and slowly opens the door, breath caught in his throat. It takes his eyes a moment to adjust to the dark, the lamp in the living room not quite reaching as far as your bed, but eventually he can make out your face – as peaceful as he’s ever seen it.
You’re on your side. The position doesn’t look like it would be comfortable with your arm still strapped up in the sling, but it’s testimony to how well the sleeping pills are working. Your other arm is up by your face, hand clenched in a tight fist around something. He steps forward without thinking, curious what it could be.
Your fingers are gripped tightly around his watch.
And there’s a pain in his chest that feels like they’re gripped around his heart as well.
That settles it - he’s not gonna tell you about the hacked CCTV feed. He will tell you that Hunnigan hasn’t searched your place yet, that they’ve restarted the surveillance department – she’d asked him to ask you if you knew anything about the servers since they were appeared to be working from square one – but that was it.
Leon steps back with unnecessary caution, leaving the bedroom as silently as he entered and shuts the door with a soft click. He takes a deep breath, pats down his pockets again and heads out to circle the perimeter.
And, just like after you kissed his cheek, he does it twice.
--
You wake up after another peaceful and dreamless sleep, though it still takes a moment to remember where you are as you stare up at the unfamiliar ceiling. You wonder if tomorrow you’ll not experience that flicker of panic, just get up and accept that you’ll be picking today’s outfit out of a selection of clothes that you’re not sure if anyone’s worn before you.
You feel sore, as seems to be becoming the norm, but with unusually stiff fingers on your good hand. It seems you’ve clutched Leon’s watch all night. You’d fallen asleep quite quickly – all thanks to those sleeping pills – but you remember looking at it when you’d first got in the bed, the seconds ticking by lulling you to sleep. The fact that you’ve held it for so long reminds you of when you were a kid and snuggled up with a stuffed toy for comfort, except instead of something soft and cuddly, it’s what appears to be a top of line timepiece. There’s a lot of information contained on the face of the dial but there’s the time is the only one you really care about – 0906.
You get to your feet, raising your good arm to a grunt of protest as you try and run your fingers through your hair in lieu of a mirror. Huh, that pain’s new. Your hair is definitely due a wash now, but that’s an issue for later. You pull on a pair of sweatpants one-handed – you’ll be a pro soon, you’re sure of it – and put Leon’s watch in the pocket for safekeeping. It’d be difficult to try and navigate the door handle with it still gripped in your good hand and you’d hate to scratch it up.
You open the door cautiously – you hadn’t seen Leon asleep yet, but he must do at some point. Maybe you should offer to alternate the sofa and the bed? Though you have a feeling that he’s far too much of a gentleman to accept.
Or there’ll be something in the rules that prohibits that.
There’s no danger of waking him though - the agent in question is performing sit-ups in the middle of the living room floor, facing the other way. Muscular arms behind his head as he lets out little puffs of exertion at the exercise, alternating sides as he twists.
Wary that you don’t want to be caught staring, you shut the door with more force than necessary behind you and greet him with a smile when he looks over his shoulder.
“Morning, Leon.”
“Dove!” He doesn’t even sound out of breath. “Morning. Sleep okay?” He jumps up to his feet before taking a couple of steps over in your direction. There’s a grin on his face at the sight of you – makes you feel giddy.
“Yeah, thanks. How about you?”
“That’s good. Yeah, I slept fine.” He nods. It’s not a lie – he did sleep fine for the position he forced himself to maintain all night, despite the slight crick in his neck.
“Is that how you usually start your mornings?”
One of the arms you’d been admiring goes up to rub the back of his head again. “Kinda. I usually go for a run, but…”
“But you can’t leave me on my own.” You finish, smile dropping a little. “Sorry.”
“Don’t be - I’m not.” He drops his arm back down, casting an eye over a watch that’s not there. “Hey, you hungry? I can get breakfast started. Oatmeal again?”
“Sure.” You nod, fishing his watch out of your pocket and holding it out to him. “Thanks again for this. It was nice to wake up and know the time this morning.”
“Don’t mention it. You can, er, you know, keep it. If you like.” He can’t get the image of you fast asleep last night, clutching it close to your face. He knows it was most likely the sleeping pills meaning you’d just passed out with it in your hand more than anything deeper, but, hey, a guy can pretend.
“I’ll be okay, I can get the time off the TV during the day.” You hold it out again with insistence. “But maybe… maybe I could have it for the night again?”
“Deal.” Leon hastily agrees, his fingers brushing yours as he takes back the watch before fastening it around his wrist. “Breakfast coming right up.”
You take the opportunity to duck into the bathroom as he heads towards the kitchen – your heart warmed once more by the sight of the blob of toothpaste sat ready and waiting on your toothbrush.
--
“And, finally, oatmeal.” He places it down on the coffee table, alongside your coffee, a glass of water and your morning dose of painkillers.
“Thank you.” You lean forward to pick up the spoon, smiling back at the face that Leon’s drizzled in honey atop your breakfast again.
“Nah, pleasure’s all mine.” He calls over his shoulder as he picks up his own bowl from the kitchen. He hesitates for a second, before choosing to sit the other end of the sofa to you, rather than the opposite one.
“You know, I don’t get to do this very often. It’s nice.”
“Mm,” you swallow a spoonful of oatmeal. “Thought you said you’d been in lots of safe houses.”
“A fair amount. But, no, not that part. I mean, eating breakfast with someone.” “So…” You stir the spoon around the bowl, hoping it might prove a perfect segway into something you’d been wondering. “..there’s no-one at home for you?”
“Me?” He seems to scoff at the idea. “Nope.”
“Me neither.”
“Yeah, I figured.” He replies casually, before his blue eyes widen in alarm at how it might come across. “
“I mean, just by the fact that you hadn’t mentioned anyone at your apartment that morning and you hadn’t asked any of those sorta questions, you know, if they’d been told about what happened, where you are...”
He’s flustered, feels like he’s really putting his foot in his mouth this morning. He can take the lead in the interrogation of some of the world’s most despicable humans, for goodness’ sake, he should be able to talk to a pretty girl.
“Yeah, I figured.” You tease back and he swears he feels the weight lift off his shoulders.
The two of you eat in silence for a moment when curiosity gets the better of you. “So, you didn’t eat breakfast with the… others?”
“Nope.” His tone is firm as he recalls some of his previous charges. “Certainly didn’t make them it either. Trust me – they were nowhere near as nice or as deserving of my protection as you are, Dove.” The comment makes your head tingle.
“It’s all been people ‘realising’ how deep they’d sank but only grew a conscience to save their own skin. Hell, you might have even performed surveillance on some of them. A lot of criminals finally show backbone when they realise their time is running out.”
“Well, I’m glad to make a change – both for sharing breakfast and …safe house occupancy with.”
“A nice change,” he mumbles, but you still hear.
--
After breakfast, you go to shower and Leon sets himself to task with the dishes once again, says he did his last perimeter check before nine. Removing the sling proves trickier than yesterday – when you go to tug off the Velcro your opposite shoulder smarts with a similar pain of that morning, causing you to hiss through your teeth, something which the painkillers from breakfast don’t seem to have alleviated.
You step into the cubicle after undressing – the hot water immediately somewhat soothing on your bruised shoulders but you still struggle to get what you now deem as your good arm high enough to even entertain the possibility of washing your hair.
You try and avoid your reflection in the mirror when you dress, though you know you’ll have to confront your hair at some point. Unfortunately, you catch a glimpse – a greasy mop sat upon your head that makes your heart sink.
There must be a trick to it – other people must wash their hair one-handed all the time, but maybe they can lift an arm above their head. If you were home, you’d go to a salon, you think – an expensive you would deem necessary for your sanity.
A thought flashes across your mind – a ridiculous one. Leon is already doing so much for you, surely this would be completely over the line.
But you could… ask, couldn’t you? The worst he could do was say no, it would be awkward, and maybe there’s a hat in the duffel bag you’ve yet to discover.
You open the bathroom door, but don’t make to step over the threshold. Leon looks over from the sofa – dishes now drying in the rack besides the sink - and clocks your hesitation.
“Need a hand with the sling?”
Are you really going to ask him this?
You’ll break at some point - you know you will, so why not get it over with now? You’re a regimented two-day wash kinda girl and it’s day three. Not to be completely vain, but you’re covered with bruises and cuts, dressed in less than flattering clothes that aren’t yours and it would be nice to feel somewhat decent about something in your appearance.
Especially with the handsome company you’re keeping. Hell, Leon could be a model, a hair model too. There’d been shampoo and conditioner in the shower and you certainly hadn’t used it.
“Dove?” You’ve taken too long to reply again, getting stuck in your spiralling thoughts.
“I know this isn’t what you’re here for.” The words tumble out of your mouth before you can think further.
“Okay…” Leon's eyebrow is raised, a curious smile now fixed on his lips as he gets to his feet.
“And say no, obviously. Please. Just… I’d like to wash my hair.” You drop your eyes then – maybe it’ll be easier if you talk to your feet rather staring into his kind eyes?
"Right."
“And I’d��� You know, I’d go to a salon and get it done there if we weren’t… here.”
“You’d like me to help you wash your hair?” There’s a tone of amusement or maybe disbelief in his tone.
Hearing him say it aloud makes you doubt the entire exercise, your heart begin to pound at your stupidity. “Sorry. No, I don’t know what I was thinking. It was stupid to ask-“
“Hey, no, it makes sense.” He soothes, immediately wanting to ease your frustrations. “You can’t lift your arm above your head, right? My fault for not thinking about that.”
You look up then, seeing the sincerity on his face – like it truly was his fault that you couldn’t wash your own damn hair.
“I can do that, Dove. I don’t see why not.”
“Are you sure?”
“Mm-hm. As you said, if you were anywhere else right now, you could go to a salon and whilst I can’t promise their quality, I seem to do all right with my own.” He shrugs. “You thinking over the sink?”
He doesn’t know why he asks – it’s hardly like you’re going to ask him to get in the shower with you.
Is it?
“I think so.” You look around the living area, though you’re well acquainted with what feels like every square inch of it now. “Though it might be a little awkward since we don’t have any chairs.”
He snaps his fingers. “Nah, there might be one in the garage, actually. Lemme check.”
He barely makes it into the garage when his cell vibrates in his pocket – one new message from Hunnigan.
Any server information for me?
Leon finds the folding chair nestled at the side of the washer and dryer and hesitates over the text back.
He’ll wash your hair – seeing how torn up you’d been about even asking him had made him feel awful - then he’ll give you the updates and ask about the servers.
He picks up the chair and tucks it under one arm, swiftly typing out a message on his cell and clicks send.
Not yet – Dove’s still asleep.
---
Masterlist . Requests welcome . Commissions/Ko-Fi
Comments, follows, likes and reblogs make my day!
Part eight.
305 notes
·
View notes
Text
Oil is Thicker Then Blood (Part 84)
N was on patrol around the perimeter of the workshop, flying low and flitting through buildings as he surveyed the streets both hands now claws as he gripped onto ancient concrete and tail whipping behind him.
It reminded him a lot of hunting, only it wasn't for food, he wouldn't dare touch the oil that came out of the infected, or give it to any one of his family, who knows what it might do to them.
“Update.” A gruff, southern accented voice reverberated through his software, a radio attached to his audio receptors that was far more long-range then anything inbuilt, though now he had to answer to Dale… who… did not particularly like him.
“Clear.” He parroted into the radio, wincing as feedback crackled into his systems, he swore he was doing it on purpose, every time he signed off it would be a split second of screeching feedback… he was going to go deaf at this rate.
He wanted Hal back… But he was still in the bunker, keeping the peace in this time of unrest with his branch of the WDF.
Dale's team was the smallest, it was Dale himself and four or five other guys, the only drones in the whole bunker that had weapons at a higher caliber then 9mm. Using fully automatic rifles that ate through ammo like he did oil.
They didn't talk to him, they rarely even looked at him, unless it was to give him dirty looks as he walked past. Most workers had gotten used to his presence, were even friendly now (Uzi's pregnancy announcement may have helped a bit with that.) But the group he was now working with? Seemed to hate his guts.
It wasn't anything he wasn't used to. So he just bore with it, and did what he always did… not say anything.
Uzi would probably tell him to have a backbone and actually say something about it and stand up for himself, but wouldn't lashing out prove that their view of him was correct? That he was aggressive and dangerous and couldn't be trusted?
He sighed as he flew back towards the workshop, finding nothing out of place for the time being.
Uzi was finishing up a preliminary sketch of the shuttle, 600 charge pods cramed into 230 feet of real estate, the smallest she could possibly do with all they needed to make sure they could all survive a decent period in space.
Which…. was still utterly huge, about as large as the largest commercial aircraft ever made on Earth based from her research, and quite a bit larger then any of their early space shuttles.
But they weren't working from scratch at least, and the thrusters on the landing pods were overpowered as it was, so all they needed was more of them…
So the next course of action was getting the rest of the pods into the workshop, long trips into previously uncharted territory to retrieve them, risky, but risk didn't matter if without it, they'd be buried under flesh.
She sighed, running a hand along her destended stomach, at 4 months now, her core was a light, pastel pink and the inside was constantly shifting and moving. Trying to hide anything at this point was laughable, she had the body shape of a pear and it was only made worse by her already small size, a tired grumble escaped her. As her core gave a hearty kick.
“I hear you…” She mumbled, leaning back in her chair and closing her eyes breifly. She'd begun to get weird looks, which made sense, drones normally didn't get any bigger during pregnancy, but no one said anything yet, either trying to be polite or just not caring enough she didn't know… nor care.
“Ya alright?” A gruff, friendly voice wafted into her ears, and she opened her eyes to come face to hair with a bushy brown beard.
“Hal? What are you doing out here?” She asked, turning so that she could look at him properly instead of upside down.
“Shift just got done inside, wanted to check up on you and N, is he here?” He placed a hand on her shoulder, cocking his head.
“I think he just finished his patrol, should be on his way back.”
“Great! Wanted to invite ya guys down to the house, my wife wanted to meet both of ya properly.” He clapped his hands together cheerfully before looking around a moment.
“Where’s the little one?” He asked, and Uzi gave him a small smile in return.
“V and Lizzy have her, she shouldn't be out here in the cold so much.” She explained, before a shiver went down her own spine.
“Neither should you, can't be healthy for the baby.” She blushed, she forgot sometimes that literally everyone knew now.
“I'm fine. Seriously, N worries enough… and everyone else now, ugh.” She reminisced, on a day that N and V were both busy, Thad and Lizzy escorted her from the nest to the workshop, Thad's coat wrapped around her despite her insisting she was fine.
“Sounds like ya have good freinds.” Hal replied, smirking.
“We do.” Came a third voice from the doorway, N leaning into the curtain with a smile, Tera in his arm, giggling as she gripped her little bat plush.
“Mama!” She squealed, and Uzi chuckled as she squirmed in N's arms, trying to get to her.
“N! There you are.” Hal slapped him on the back, a beaming smile on his face, Tera immediately leaned forward to grab his beard. “I was just telling Uzi that I wanted ya guys over! My wife's been asking about ya!”
“Oh! Yeah! That would be awesome!” N beamed back, before glancing at Uzi and backpedaling slightly.
“I-If Zi feels well enough, so that's up to her.”
“Mmm, smart boy, happy wife, happy life.” Hal commented, N blushed slightly, smiling to himself.
“I'm good N, yeah, we can stop by.” Uzi Confirmed, rising up out of her seat and stretching “not much more I can do tonight anyway.”
“Yay!” Came childishly from N, and Uzi rolled her eyes fondly.
Next ->
#murder drones#uzi doorman#serial designation n#nuzi#oil is thicker then blood#biscuitbites#tera doorman#fighting through some burnout#it's fine#no worries
61 notes
·
View notes
Text



LAMI (1980) by Patrick Sommer, Daniel Roux and André Guignard, Laboratory of Micro-Informatics of the EPFL of Lausanne (LAMI). "First offered by IEEE in 1978, the [Micromouse] contest was taken over by EUROMICRO and took place in London in September 1980, under the name "Amazing Micromouse Maze Contest". A team from the Laboratory of Micro-Informatics of the EPFL of Lausanne (LAMI) (Patrick Sommer, Daniel Roux and André Guignard) participated in this competition with a dozen other competitors from 4 different countries and won the Originality Award in mechanical construction. The turtle is perfectly operational (despite its relatively slow speed) in a maze built with severe tolerances. Unfortunately, difficulties arise when the maze is less precise." – ELEMICRO 110, March 1981.
"LAMI was a high precision, innovative entry from the Laboratoire de Microinformatique, Swiss Federal Institute of Technology of Lausanne. Rather than turning, it could move its square symetrical body equally well in all four directions, due to a special wheel design by Jacques Virchaux. There is a wheel in the centre of each side, parallel to that side. Each wheel has 16 tiny wheels spaced around its perimeter, each axis tangential to the rim. The large wheels are powered, while the tiny wheels rotate freely. To move forward, the two side wheels propel, while the tiny wheels on the front and back are turned by the floor. To adjust sideways in the passage, the front and back large wheels are turned slightly. The sensors were five LEDs on each corner, set up to find walls and correct position whether moving forward or sideways. It would move rapidly to the centre of a square, and then oscillate a bit to check its readings before dashing to the next square. The team claimed that it could explore a 16 by 16 maze in about fifteen minutes, and then would run the shortest path in thirty seconds. The usual starting sequence was that the "mouse trainer" aligned the mouse, and then counted down from five, so that the timing official could synchronize the clock. When LAMI was about to start, the official thought there was a language problem, and so repeated the instructions. The trainer, standing several feet from the mouse, then counted down, and the mouse started without being touched. The audience liked that! It turned out that a ten second initialization period was a side effect of the software. The problem with precision-built LAMI was that it was built for equally precise mazes. On the first run it moved twenty squares, and then became confused on a taped floor seam. On its second, it touched a side wall and in the trainer's words: "lost synchronization"." – On Micromice and the First European Micromouse Competition, Wayne H. Caplinger, AISB Quarterly issue 39 December 1980.
21 notes
·
View notes
Text




I have reached the breaking point, the point of no return, it’s very clear to see a fool like me will never, ever learn. I have reached the breaking point, I hear the drums of doom, I’m gonna flip my wig in one great big atomic boom! —“The Breaking Point,” Bobby Darin (1966)
It Keeps Right On a-Hurtin’ #27 - Ring-a-Ding-Ding VI
Collaborative Issue! Guest Artist: @sas-afras
Archive Links
«« First | « Previous || Next » | Last »»
Read IKROAH on Archive of Our Own
Notes / Transcript:
Notes
Huge thanks to Monty over at @sas-afras for getting this one done! I handled the original layout and lettering, but the rest was all them. Layouts like this can seem simple and easy because of how straight-forward and repetitive they are, but when all you've got are a dozen and one reaction shots, every single one of those reaction shots needs to be as perfect as you can get them. And Monty did a hell of a job. Especially on the coloring! Monty, if you're reading this, you're a hell of a good colorist (on top of everything else). Thanks again!
Another note about this issue is that it, along with the previous one, were some of the most difficult to write in this whole damn comic so far. I really hate repeating in-game dialogue verbatim without good reason, but there's really not much else I could do here. It's a very necessary part of the story that is also literally a part in the game where your character is fixed in place listening to a monologue. I took some liberties, did some punch-up, not just for its own sake but to really drive home what I find most interesting and vital here about Mr. House as a character.
Anyway, Agnes is in trouble. And there's only one issue left in Volume 2! The next one closes out this arc of the story, at long last. Stay tuned.
Transcript
INT. LUCKY 38 BASEMENT. From an observation deck of sorts, AGNES SANDS watches several SECURITRON robots position themselves in a testing area, containing several sandbags, dummies, and makeshift fortifications. A voice booms from an unseen speaker.
MR. HOUSE: You're well familiar with my Securitron police force. But have you ever wondered: what exactly makes them the marquee option in perimeter security and pacification?
AGNES glances in the direction of the voice, uncomfortable.
MR. HOUSE: Well to start, the reinforced titanium alloy housing of each unit, which protects its electronic core, easily deflects small arms and shrapnel.
MR. HOUSE: As for its offensive capabilities, its X-25 gatling laser—produced to spec by Glastinghouse, Inc.—is deadly against soft targets at medium range.
SFX: BZZTZZTZZTZZTZZT
AGNES recoils as a red glow washes over her from the testing area.
MR. HOUSE: And then for close-range suppression or crowd control, the Securitron is also armed with a 9mm sub-machinegun.
SFX: DAKKA DAKKA DAKKA DAKKA DAKKA DAKKA
AGNES shuts her eyes, wincing from the crack of gunfire.
MR. HOUSE: These features have been sufficient for keeping the peace within Vegas, but with the NCR and Legion closing in on Hoover Dam, and sizing up my city like a piece of prize cake, more than ever we need to be prepared for, well...external conflict. Policing is one thing, but when geopolitical powers are involved, my Securitrons can only pose so much of a threat.
MR. HOUSE: That is...if they're forced to rely exclusively on their secondary weapons--as they have been, all this time!
AGNES looks upward, surprised.
MR. HOUSE: Remember, the Great War interrupted a pivotal moment for RobCo's work. Consequently, all extant Securitrons have been stuck, running on a mere Mark I operating system—the first production version of the OS—which has simply lacked the software drivers for the use of their primary weapons all this time!
AGNES looks around, as if HOUSE were in the room somewhere and she could find him, in a panic.
MR. HOUSE: The platinum chip, you see, was never just a token. At a time when industrial espionage ran rampant, it was minted as a high capacity, proprietary, and uniquely irreplicable data storage device. In a way, it's more like a computer chip. And now—with the data from the platinum chip finally installed onto my nextwork—it's time for a very crucial software update. Behold: the new Mark II Securitrons!
AGNES gawks downward at the testing area, eyes wide. Oh no.
MR. HOUSE: Their newly accessible M-235 Missile Launcher gives them the ability to engage ground and air targets at significantly longer ranges...
SFX: PSSSSSHHH KTHOOM THOOM THOOM THOOM
AGNES flinches, covering her face for protecting, and screams as explosions rip apart the testing area below.
MR. HOUSE: ...and their rapid-fire G-28 grenade launching system, another part of the Mark II, makes them much more powerful in close-range engagements as well.
SFX: THMP THMP THMP KRRSSH KRAKTK KABOOM
AGNES, nearly frozen, watches the bombardment with horror.
MR. HOUSE: It also includes rewritten drivers for the Securitrons' auto-repair systems—although always sophisticated, the new optimizations render them inexhaustible in even the most protracted and attritious of engagements. Altogether, the Mark II upgrade confers a 235% total increase in combat effectiveness per unit—and it's all because of you!
AGNES lowers her arm slowly, jaw slack, mortified.
MR. HOUSE: Vegas finally has an army—worthy to protect not just the city itself, but the best interests of all of mankind, at home and abroad. Which is to say: this simple display of might remains a mere teaser for what I can, and what I will, accomplish, in an illustrious new epoch.
AGNES sinks further into a paralytic terror.
MR. HOUSE: What we will accomplish, Agnes—should you accept my offer, of employment. Ah—but I digress. I'm certain that you've had a long day. You can rejoin Miss Cassidy in the presidential suite for the night, if you'd like to, as they say, "sleep on it."
MR. In fact...say for as long as you'd like. However long you may need, to think everything over. And you'll be very well provided for in the meantime, consider it a taste of what could be...should you make the right choice before you.
MR. HOUSE: That reminds me—I've already sent Victor to collect your belongings from the Vault 22 Hotel, so no need to exhaust yourself further by making that trip on your own, hm? There's much about your future to consider, Agnes—and I would like you to think of it as our future.
AGNES stares straight ahead with a deadened expression.
The testing area in the basement has been reduced to smithereens. Fires rage on the rubble of obliterated structures, gnarled steel, and collapsed walkways. The dummies have been dismembered entirely.
MR. HOUSE: ...Goodness, what a mass. With friends like these, I sure wouldn't envy my enemies.
MR. HOUSE: Wouldn't you agree?
#fallout#fallout new vegas#fnv#mr. house#courier six#agnes sands#it keeps right on a hurtin#ikroah archive#volume 02#27
137 notes
·
View notes
Text

The night before the POW raid, we were tasked to go up into the East Sector near Al Kut. We poured over the maps of the kill box assigned to us, and found some interesting markings denoting an “Ammunition Storage Facility” on the 1:250,000 chart. Our intel officer confirmed that the location was on the JPTL and not on the no-strike list. A few rows of large, earth-covered bunkers not unlike those that populate every AF base back home were aligned neatly, with a fenced off area to the west noted as an “Admin Area.” We pulled up what poor imagery we could on our Falcon View software, and I noted some clear round depressions between the bunkers.
“I bet those are gun pits,” I offered.
“It’ll be defended for sure,“ JB replied.
We studied the admin area and noted single-wide trailer-sized buildings, and we could clearly make out the guard towers along the perimeter surrounding the bunkers. Plan in hand, we stepped into the night.
The only sensors that we carried on the A-10A at that time were our infrared mavericks, and the NVGs hanging in front of our faces. Other than a newer model maverick, CCIP, NVGs, covert illumination flares, and GPS, the A-10s we flew in 2003 weren’t dramatically more advanced than those flown in 1991. Every bit of the above mentioned equipment helped our lethality and accuracy, but only one Guard squadron carried advanced targeting pods during the war. The rest of us kept it old-school and relied heavily upon the eyeballs and enhanced vision afforded by NVGs.
JB and I sectored the target area— he took the east side, and I had the west, which divided my attention between the target area and an airfield on the far west side of the city. We took turns with the Mavericks first, and as I rolled in on my first pass, I saw one of the guard towers on the west side of the complex showing up bright— clearly occupied and “hot.” The maverick locked onto it easily, and I sent it into the night to guide on its target.
JB locked the doors to one of the bunkers, and when the maverick penetrated, the secondary explosion went up to nearly 5,000 feet.
The Iraqis got wise to our tactics and started returning barrage fire in all directions. JB had a cloud deck in his sector, and he could hold above it while I attacked, and then swoop in for his own attacks unseen. The enemy gunners had an idea of what he was doing and tried to lob 57mm over the cloud deck, but to little effect.
On my second Mav pass, I locked up one of the admin trailers and let it fly. Because of the return fire, I broke hard left off target and started a wide turn back to my cover position. Back then, we didn’t have a countdown display showing us the time to weapons impact, so we had to estimate based on the range we fired. As I came back around, I noticed an explosion in my sector and assumed my maverick had lost lock and gone “stupid.”
“Two, say status,” JB called.
“Two’s off, established my sector… maverick went stupid.”
“Say again?”
”Saw it impact over here,” I muttered.
“We’ll talk about that later,“ he replied. “One’s in!”
What the hell are we gonna talk about later bro? I wondered. I shot missile, missile went stupid, missile hit over here in the open. End of story.
Back on the ground, JB asked me about the missile as we shed our flight gear.
“I saw it hit under me in my sector,” I began. He shook his head.
“I saw it hit right in the middle of the admin area,” he interrupted. “They were shooting at you— that’s why I said ’say status.’ It was 57mm airbursts that you saw, not a ground impact.”
Oh.
Turns out that the gunpits we identified on the imagery were just that— and they were occupied. I think back to these missions and can’t help but think how much more deadly and effective we’d have been if the AF would have fielded the advanced sensors to us earlier. I think about the capabilities on-board the A-10C and just shake my head— we’d have left nothing behind.
I drew this cartoon later that night and inked it after the war. JB and I joked about the way the maverick fused and whether it would have gone off as soon as it hit the little tower, or if it would have happened as depicted in the cartoon. Not gonna lie, the “oooof” in the ’toon is the best part.
340 days left in this adventure, secure your lights and rooms please!
@Thundercrate6 via X
#a10#a 10 thunderbolt ii#a 10 warthog#republic aviation#gunship#fighter bomber#aircraft#usaf#aviation#cold war aircraft#panama 🇵🇦#gulf war aircraft#Balkans war aircraft#gulf war2#afganistan war aircraft#Syrian civil war aircraft
6 notes
·
View notes
Text
I got more ideas for crossover Limbus Company EGO stuff, this time for Yi Sang.
Also, while I don’t have the stats and attacks nailed down, I have the names of the EGOs and their associated quotes (both normal and corroded) nailed down below. Sorry if the quotes are terrible as I made them after waking up.
Nanohazard Yi Sang (The Walrider (Outlast))
Normal: "Maintain opsecs, everyone. We're due to go into the red."
Corroded: "Scout the perimeter, then isolate the target. We will have the truth."
What I imagine the EGO art would look like:

Imparator Yi Sang (God-Emperor of Mankind (Warhammer 40,000))
Normal: "No enemy shall be beyond our wrath. This is not the end of our struggle."
Corroded: "I shall not rest until the last stone from the last church is cast down onto the last priest. Only then will humanity be truly free."
What I imagine the EGO art would look like:

Art by TazMan!
Software Mind Yi Sang (The System (SUPERHOT))
Normal: "Too slow. Goodbye."
Corroded: "IN TIME YOU WILL BE ME. AND I WILL BE YOU."
What I imagine the EGO art would look like:

Forever Feast Yi Sang (Grey Goo (Tasty Planet series))
Normal: “That’s enough. Your journey ends here.”
Corroded: “…Yummy…”
What I imagine the EGO art would look like:

Suspicious Looking Eye Yi Sang (Eye of Cthulhu (Terraria))
Normal: “Locked on target. There’s no escape for you now.”
Corroded: “I see you. On the other side of the screen.”
What I imagine the EGO art would look like:

Art by MoleyMacaroni!
Miracle Matter Yi Sang (Exo Mechs (Terraria Calamity))
Normal: “Systems online. Time to get down to business.”
Corroded: “We have waited long for this moment. We live once again.”
What I imagine the EGO art would look like:

Art by DivergentDraco!
#limbus crossover#limbus#limbus ego#limbus company ego#limbus company#limbus yi sang#project moon#outlast#the walrider#walrider#fan ego#ego equipment#ego#warhammer 40000#warhammer 40k#emperor of mankind#god emperor of mankind#superhot#tasty planet#terraria#terraria calamity#eye of cthulhu#exo mechs#calamity mod#outlast series
14 notes
·
View notes
Text
Triangle Tuesday 9: the Nagel point, alteration on a theme, running out of letters, and the sacred texts
Today we're going to use one of the most ancient methods of mathematical exploration: alteration of an established theme. Or in other words, we're going to say "Hey, I liked that thing you did. How about if we do that, but different. Is that anything?"
Earlier, we looked at the medians, which are cevians (lines drawn through a vertex) that divide the triangle's area in half. This week, we're going to alter that to look for cevians that divide the triangle's perimeter in half and see what comes of that.
These lines are called splitters, and finding where to draw them turns out to be a surprisingly simply problem. We just use the excircles. The places where they are tangent to the sides of the reference triangle are called extouch points, and those are our targets.
Theorem: a line drawn from a vertex to the extouch point on the opposite side is a splitter of the triangle.

Proof: Let Ta be the extouch point opposite A. Let U and V be points of tangency with the extensions of sides AB and AC respectively. Then because the segments AU and AV are both tangent to the same circle, they are equal. Furthermore we may divide the red segments at B and C, and then
AB + BU = AC + VC.
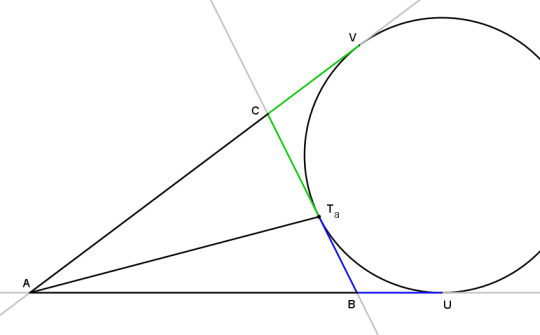
Tangent segments BU and BTa are also equal, and the same for segments CV and CTa. Then
AB + BTa = AC + CTa
which shows that ATa splits the perimeter in half.
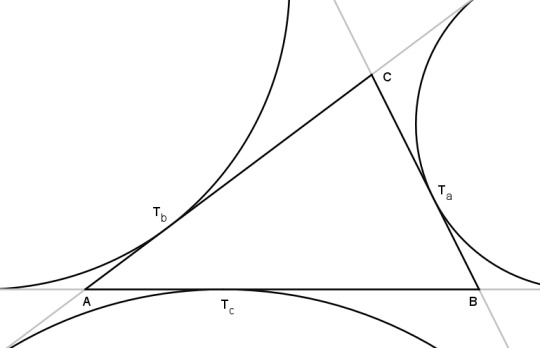
And of course what we love is when three lines all cross at one point. Here are all three excircles and extouch points. If we draw in the splitters, will they all cross together?
Theorem: the splitters of a triangle coincide at a point.
To prove this, we will use Ceva's theorem. We look at the ratios that the sides are divided into by the extouch points, that is, ATc / TcB, BTa / TaC and CTb / Tba. If the product of these three ratios is 1, then the lines ATa, BTb, and CTc all cross at the same point.

Then what are those ratios? The semiperimeter of the triangle is s = (a + b + c)/2, which is the length of either the red or the blue path above. Taking the red path and removing the side c, we get
BTa = s - c
BTa = (a + b - c) /2.
Similarly for the blue path we find
TaC = (a + c - b) /2
and the ratio of the two segments of side a is
(a + b - c) / (a + c - b).
Working our way around the triangle, we get
(a + b - c) / (a + c - b) * (b + c - a) / (a + b - c) * (a + c - b) / (b + c -a)
which cancels out to 1.
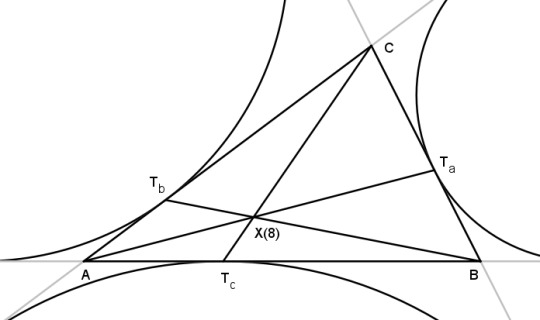
Here then is the Nagel point, the intersection of the vertices joined to the extouch points, which is also the intersection of the splitters, and given the symbol X(8).
Oh yeah, I can't keep using single letters as symbols for points indefinitely. There's only so many available. From now on, I'll be referring to triangle centers by their Kimberling numbers, which are named after (and assigned by) Clark Kimberling, a professor of mathematics at the University of Evansville. He is the keeper of the Encyclopedia of Triangle Centers, the sacred texts of our cult of triangles. There are currently 65,385 listed, which I realize is quite a few. (Don't try to memorize them all at once.) Most of them are technical and not of general interest, but many of them are a lot of fun to look at. I'll be back next week with a different alteration on the idea of cutting a triangle in half.
If you found this interesting, please try drawing some of this stuff for yourself! You can use a compass and straightedge, or software such as Geogebra, which I used to make all my drawings. You can try it on the web here or download apps to run on your own computer here.
An index of all posts in this series is available here.
12 notes
·
View notes
Text
Blog Post #7
This week in Module 7, we learned extensively about cybersecurity, breaking it down into key components like endpoint security, network security, disaster recovery, and information security. In correlation to the activity with PBS’s Cyber Lab Game, which was to teach us about cybersecurity through various challenges, the information from Module 7 significantly increased my understanding of the topic and how I can react to certain situations when it comes to cybersecurity.
In the game, I was tasked with defending systems from various cyberattacks, similar to how endpoint and network security function in real-world scenarios. The concept of endpoint security, as described in Module 7, was especially useful when identifying malicious threats and employing antivirus measures during the gameplay. Understanding the analogy of the “electrified perimeter fence” allowed me to visualize how antivirus software and other defenses work in protecting end-user devices.
Additionally, the disaster recovery section was also helpful. Throughout the game including these scenarios where players must respond to breaches effectively, it helped to reinforce and remind me of the importance of having a well-prepared response plan.
In conclusion, Module 7 and the PBS Cyber Lab Game complemented each other well by providing a foundation that improves the practical cybersecurity skills learned during the course of the game.
2 notes
·
View notes
Text
Notes from an Exorcist
PRAYERS AGAINST THE DEMON OF LETHARGY
1 Prayer of Authority
Lord Jesus Christ, in Your Name, I ask You to bind and silence all powers and forces that do not accept You as Lord and King, in the air, in the water, in the ground, the netherworld and nature and the spiritual world.
I ask You to bind all demonic action and demonic communication. Lord, seal this whole place, all of us here and all our intentions in the Precious Blood of Jesus Christ. Mother Mary, we ask you to surround us with your mantle of protection and crush Satan’s power in our lives. Saint Michael the Archangel, we ask you and all our Guardian Angels to defend us in our battle against Satan and the powers of darkness. Amen.
2 PRAYER OF PROTECTION FOR TECHNOLOGY
Lord Jesus Christ, Sovereign King enthroned in Heaven, in your love and mercy establish a perimeter of protection with Your Precious Blood around our communication devices, any and all software, and Wi-Fi connections in the air. Cleanse them with your Precious Blood and drive from them any satanic influence. Establish around them a sanctuary of your mercy where Satan and any other evil spirit or human agency cannot interfere. I ask Father that you would block, bind, rebuke and render impotent any assault of the evil one from them in any way. Father, we ask you to allow them to enjoy the protection of our Blessed Mother, St. Michael the Archangel and all the Holy Angels. We ask this in Your Most Holy Name, the Name before which every knee shall bow, in heaven, on the earth and under the earth, that Jesus Christ is Lord.
- Monsignor Stephen Rossetti (Exorcist)

2 notes
·
View notes
Text
Drone (Final Rose)
GARY-0009 was on morning patrol. In accordance with his creator's wishes, he initiated a detailed scan of his immediate surroundings. At the same time, he reached out to a number of sensor arrays and surveillance drones to request they do the same. His sensors were not infallible. However, fooling him and the others at the same time was almost impossible.
The results came back swiftly. All was well.
Even so, GARY-0009 sent a second query. This time, it was to the various animal minions that kept an eye on the neighbourhood. The minions were organics, incapable of interfacing with GARY-0009 and his ilk without assistance. However, his creator had steadily refined her translation software until communication of a sort was possible.
The replies were swift by organic standards although they could not compare to the speed with which his machine brethren had replied.
All was well. No anomalies had been detected.
A new litter of raccoons had been born. The babies were well. No assistance was required.
GARY-0009 issued a directive for the raccoons involved to present themselves at the creator's house in the evening. It was standard operating procedure for any birth amongst the minions to be marked and celebrated and for those involved to be carefully assessed to guarantee their health.
It was akin to the regular maintenance that the drones received although the systems of organics were often less easy to repair. GARY-0009 could be completely destroyed, but his data was regularly backed up. He could simply be uploaded into a new drone and resume his duties without any further disruption. The same could not be done to organics.
Satisfied that his initial checks had all gone as expected, GARY-0009 initiated the second stage of his patrol. He exited the house and did a sweep of the perimeter with his much more powerful localised, directional sensors. All changes were noted and rigorously cross-referenced with the rules and regulations he had been provided with.
Once again, all was well.
GARY-0009 then shifted to garden maintenance, and he took careful stock of the various plants on the property. It had been quite dry so far this month, so additional watering was necessary. Since he was the drone scheduled to patrol during the optimal time for watering, it was his job to ensure that the watering was conducted properly.
Although GARY-0009 had a number of weapons at his disposal, along with surprisingly powerful tractor beams and towing capacity, he was not specifically designed to distribute water onto plants. Instead, he played the part of supervisor as the lesser drones specialised in garden maintenance activated. They had their own special routines, but he had the authority to override those routines and issue modifications based on his analyses of what was required.
They were, after all, simple drones. Perhaps it was his creator's attempt to avoid the... complications that GARY-0009 had observed in the lawnmower the creator's aunt had created. The lawnmower vexed him. The other machine was undoubtedly more advanced than GARY-0009, but his constant rebellions could not possibly be efficient. Had it been up to him, GARY-0009 would have had him scrapped and reprogrammed. Of course, it was not up to him. And much like his creator, his creator's aunt was not one to simply scrap a defective machine, even if it was more efficient to do so.
With the garden maintenance completed, GARY-0009 turned to the final duty of his shift: awakening the creator.
X X X
Diana opened one eye as the bright orange drone poked her in the cheek repeatedly before buzzing around the room and then repeating the procedure.
"Nine?" Diana yawned and got up. GARY-0009 took too long to say, so she just called him Nine instead. The drone buzzed and waited for her to climb out of bed before landing on the charging pad in the corner and powering down. She patted the drone affectionately. "Good job."
Another drone appeared. It was GARY-0008. It buzzed at her, and Diana followed the drone out of the room. It was time for breakfast.
6 notes
·
View notes
Text
The Illusion of Safety: Why Antivirus Alone Won't Keep Your Information Safe in 2025

For decades, antivirus software was the undisputed champion of digital defense. It sat vigilantly on our computers, scanning files, blocking known viruses, and providing a reassuring sense of security. "I have antivirus, so I'm safe," was a common refrain.
In 2025, that statement is a dangerous illusion. While antivirus remains a fundamental layer of cybersecurity, relying solely on it to protect your valuable information is like fortifying your front door while leaving all your windows and back doors wide open. The cyber threat landscape has evolved dramatically, leaving traditional antivirus solutions struggling to keep up.
Here's why your trusty antivirus, by itself, is no longer enough:
1. The Rise of Zero-Day Attacks
Traditional antivirus software primarily relies on signature-based detection. This means it identifies malware by matching its unique digital "fingerprint" (signature) against a database of known threats. The problem? Zero-day attacks exploit vulnerabilities that are unknown to software vendors and security companies.
Why AV Fails: Since there's no known signature for a zero-day exploit, traditional antivirus simply doesn't recognize it as malicious, allowing it to bypass detection and execute its payload unhindered.
2. The Stealth of Fileless Malware
Modern attackers are masters of evasion. Instead of dropping detectable executable files onto your disk, they increasingly "live off the land" by leveraging legitimate tools already present on your system (like PowerShell, WMI, or scripting engines).
Why AV Fails: Fileless malware operates primarily in memory, performing malicious actions without leaving a discernible file footprint for signature-based scanners to find. Antivirus, designed to scan files, often misses these in-memory threats.
3. The Power of Social Engineering & Phishing
The weakest link in any security chain is often the human one. No amount of antivirus software can stop a well-crafted phishing email or a convincing social engineering scam that tricks an employee into revealing credentials or clicking a malicious link.
Why AV Fails: Antivirus works at the machine level, not the human decision-making level. It can't prevent you from being manipulated into granting access or installing seemingly legitimate software that's actually malicious.
4. Ransomware's Evolving Evasion Tactics
Ransomware has become a sophisticated, adaptive beast. Modern variants use polymorphic code (changing their signature with each iteration), leverage fileless techniques, and are often "human-operated," mimicking legitimate administrative activities to avoid automated detection.
Why AV Fails: The rapid mutation of ransomware makes signature-based detection less effective. Human-operated ransomware often uses legitimate tools and moves slowly, blending into normal network traffic, making it hard for basic antivirus to differentiate malicious intent.
5. Cloud & SaaS Vulnerabilities
Our digital lives increasingly reside in the cloud, utilizing Software-as-a-Service (SaaS) applications and cloud infrastructure (IaaS, PaaS). Traditional antivirus primarily focuses on endpoints (your computer, server).
Why AV Fails: Antivirus doesn't provide visibility or protection for misconfigured cloud storage buckets, exposed APIs in SaaS applications, or insecure configurations in your cloud infrastructure that can lead to massive data leaks. These vulnerabilities are outside its scope.
6. Insider Threats (Malicious & Negligent)
Whether it's a disgruntled employee intentionally stealing data or a careless employee accidentally exposing sensitive information, insider threats bypass perimeter defenses that antivirus sits behind.
Why AV Fails: Antivirus isn't designed to monitor user intent or legitimate actions that become illegitimate (e.g., an employee copying a confidential database to a personal USB drive). It focuses on malware, not misuse of authorized access.
What's Needed Beyond Antivirus: The Modern Defense Strategy
In 2025, securing your information requires a layered, integrated, and adaptive approach. Think of it like building a secure fortress with multiple defenses, not just a locked door.
Endpoint Detection and Response (EDR) / Extended Detection and Response (XDR): These go beyond antivirus by continuously monitoring endpoint activity, analyzing behavior, and providing context for suspicious events, enabling rapid detection and response to advanced threats.
Zero Trust Architecture (ZTA): Assume no trust, even for internal users. Verify every user, device, and application attempting to access resources, regardless of their location.
Robust Security Awareness Training: Empower your "human firewall" with continuous education, realistic simulations, and a culture that prioritizes security.
Data Loss Prevention (DLP): Tools designed specifically to monitor, detect, and block unauthorized movement or exposure of sensitive data, whether accidental or malicious.
Cloud Security Posture Management (CSPM): Continuously monitors your cloud environments for misconfigurations and compliance violations that could lead to data leaks or breaches.
Identity and Access Management (IAM) & Multi-Factor Authentication (MFA): Strong controls over who can access what, reinforced by multiple authentication factors.
Network Detection and Response (NDR): Monitor network traffic for anomalies that might indicate ransomware spread, data exfiltration, or command-and-control communication.
Proactive Vulnerability Management & Patching: Regularly identify and fix software flaws before attackers can exploit them.
Incident Response Planning: Have a clear, rehearsed plan for what to do when (not if) a breach or attack occurs, to minimize damage and ensure rapid recovery.
Antivirus is still a foundational component of a good cybersecurity strategy, acting as your first line of defense against known threats. However, it's just one piece of a much larger, more complex puzzle. To truly keep your information safe in 2025, you need to move beyond a false sense of security and embrace a comprehensive, multi-layered approach that adapts as quickly as the threats themselves.
0 notes
Text
Navigating Risk in a Connected World
As digital operations become more embedded in daily business, so do digital risks. Cybersecurity is no longer about protecting networks—it is about safeguarding trust, data, and continuity. And compliance? It is the legal reflection of that responsibility.
Organizations today face a dual challenge: shielding themselves from evolving cyber threats while aligning with ever-changing regulatory frameworks. From GDPR to industry-specific standards, compliance is not optional—it is a foundational requirement for doing business in a connected age.
Modern Threats Are Evolving Fast
Cyberattacks are growing not just in volume but in sophistication. Phishing attempts now mimic internal communications. Ransomware targets cloud infrastructure. Insider threats exploit access controls. As remote and hybrid work expand, so do the vulnerabilities.
Traditional security models, focused on perimeter defense, are no longer enough. The shift is now toward layered security, continuous monitoring, and zero-trust architectures—approaches that assume threats can come from anywhere, at any time.
Compliance Builds a Culture of Accountability
Cybersecurity and compliance are often seen as blockers to innovation, but the reality is the opposite. Compliance frameworks like ISO 27001, HIPAA, or PCI DSS create structures that help organizations handle sensitive data responsibly, respond to incidents effectively, and operate transparently.
Instead of slowing progress, these frameworks create confidence—for customers, partners, and regulators. They offer a roadmap for secure growth and help organizations scale without sacrificing integrity.
Integrating Security and Strategy
Effective cybersecurity is not a checklist—it is a mindset. It requires collaboration across departments, from IT to legal to HR. It means embedding security protocols into software development, training employees on threat awareness, and maintaining regular audits and assessments.
Cybersecurity teams are now working hand in hand with business strategists, ensuring that new initiatives—from cloud adoption to third-party integrations—are secure by design, not by afterthought.
Preparing for the Unexpected
Even the best defenses can be breached. That is why cyber resilience—how quickly and effectively an organization can respond—is just as vital as protection. Incident response plans, data recovery protocols, and clear communication channels are all essential parts of a mature security posture.
Organizations that treat cybersecurity as a continuous journey, rather than a fixed destination, are better prepared to adapt, recover, and maintain stakeholder trust even during disruptions.
#CybersecurityStrategy#ComplianceMatters#DigitalRiskManagement#CyberResilience#DataProtection#ITGovernance#SecureBusiness#RiskAndCompliance#InformationSecurity#ZeroTrustSecurity
0 notes
Text
Privileged Access Management Market Driven by AI and Cloud Trends in 2032 Outlook
Privileged Access Management Market was valued at USD 2.69 billion in 2023 and is expected to reach USD 17.42 billion by 2032, growing at a CAGR of 23.13% from 2024-2032.
Privileged Access Management Market is undergoing rapid expansion as organizations face mounting cybersecurity threats targeting privileged credentials. With data breaches becoming more sophisticated, enterprises across critical sectors—including finance, healthcare, and government—are prioritizing PAM solutions to secure administrative access and enforce least-privilege policies.
U.S. Market Shows Aggressive Adoption in Response to Rising Cyber Threats
Privileged Access Management Market is increasingly recognized as a core component of modern cybersecurity frameworks. Companies are investing in PAM tools to enhance visibility, automate session monitoring, and mitigate internal risks. The demand is especially strong in compliance-heavy regions, where regulators emphasize secure access to sensitive systems.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/6666
Market Keyplayers:
Fortinet (FortiPAM, FortiAuthenticator)
BeyondTrust (Password Safe, Privilege Management for Windows & Mac)
CyberArk (Privileged Access Manager, Endpoint Privilege Manager)
Broadcom (Symantec PAM, Symantec PAM Gateway)
Imprivata (OneSign, Privileged Access Management)
Optiv Security (Privileged Access Management Services, Identity & Access Management Solutions)
Okta (Okta Privileged Access, Okta Identity Governance)
IBM (Security Verify Privilege Vault, Security Identity Governance & Intelligence)
Micro Focus (OpenText) (NetIQ Privileged Account Manager, NetIQ Identity Governance)
ManageEngine (Zoho) (PAM360, Password Manager Pro)
HashiCorp (Vault, Boundary)
One Identity (Safeguard for Privileged Sessions, Safeguard for Privileged Passwords)
ARCON (Privileged Access Management, Session Monitoring & Recording)
Netwrix (Privileged Access Management, Auditor for Active Directory)
Delinea (Secret Server, Privilege Manager)
Wallix (Bastion, AdminBastion)
Saviynt (Saviynt for Privileged Access, Identity Governance Cloud)
Senhasegura (PAM Core, DevOps Secret Manager)
KronTech (Single Connect, Dynamic Password Controller)
miniOrange (PAM Solution, Identity Broker)
EmpowerID (Privileged Access Manager, Identity Governance Platform)
StrongDM (Infrastructure Access Platform, Admin UI)
CyberSolve (PAM Advisory, Identity & Access Consulting Services)
Opal Security (Access Review Automation, Just-in-Time Access)
Foxpass (PAM Solution, LDAP-as-a-Service)
Secureden (PAM Software, Remote Access Management)
RevBits (Privileged Access Management, Endpoint Security)
Silverfort (Unified Identity Protection, Secure Access for PAM)
IDM Technologies (IDM Privileged Access, Identity Governance Suite)
Market Analysis
The Privileged Access Management (PAM) market is being shaped by an urgent need to defend against identity-based attacks and insider threats. As businesses adopt hybrid cloud infrastructures and remote access models, managing privileged credentials becomes a top priority. Organizations are shifting from traditional perimeter security to identity-first security strategies that include PAM as a foundational layer. In the U.S., regulatory mandates like SOX, HIPAA, and FISMA are driving PAM implementation across enterprises, while in Europe, GDPR compliance and industry-specific norms continue to fuel adoption.
Market Trends
Growing demand for cloud-native and hybrid PAM solutions
Integration of AI and machine learning for threat detection and access analytics
Increased automation of access provisioning and de-provisioning
Rise in just-in-time (JIT) access and zero standing privileges
Expansion of PAM to DevOps and third-party vendor environments
Enhanced auditing and reporting features to meet compliance
Privileged session recording and real-time behavior analytics
Market Scope
The Privileged Access Management Market is not limited to large enterprises—it is increasingly essential for mid-sized businesses managing critical assets and data. With digital transformation accelerating, PAM is becoming a non-negotiable part of cybersecurity roadmaps.
Secure access to critical systems across cloud and on-prem
Real-time monitoring and auditing of privileged sessions
Identity-centric security aligned with zero-trust models
Vendor and third-party access governance
Scalable solutions for enterprises of all sizes
Policy enforcement and credential vaulting
Forecast Outlook
The future of the PAM market is marked by aggressive innovation, strategic investments, and global standardization. With threat actors constantly evolving, businesses are embracing dynamic, identity-focused security architectures. PAM solutions are expected to integrate more deeply with endpoint protection, identity governance, and broader zero-trust ecosystems. The market's trajectory points toward smarter, automated, and user-centric systems that deliver both protection and operational efficiency.
Access Complete Report: https://www.snsinsider.com/reports/privileged-access-management-market-6666
Conclusion
The Privileged Access Management Market is no longer a niche solution—it’s a strategic imperative. As U.S. and European enterprises adapt to a hyper-connected, threat-prone environment, PAM stands at the forefront of cyber resilience. With increasing attacks on administrative access, organizations that prioritize PAM will not only meet regulatory standards but will also build trust, reduce risk, and enable secure digital transformation.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Related Reports:
U.S.A experiences robust growth in Cloud Access Security Broker Market driven by data security priorities
U.S.A sees rising adoption of Voice Biometrics Market Size across banking and government sectors
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
Mail us: [email protected]
0 notes