#T-SQL Scripts
Explore tagged Tumblr posts
Text
Discovering Giants: Unveiling Large Tables in SQL Server
Navigating the vast landscapes of data within a SQL Server instance can sometimes feel like exploring uncharted territories. Particularly in environments where databases grow to monumental sizes, housing billions of rows, identifying the largest tables becomes not just a matter of curiosity but a crucial task for optimizing performance, storage, and management strategies. Why Focus on Large…
View On WordPress
#database performance management#SQL Server large tables#SQL Server storage optimization#T-SQL scripts#table size optimization#TableSizes
0 notes
Text
My Dev VM

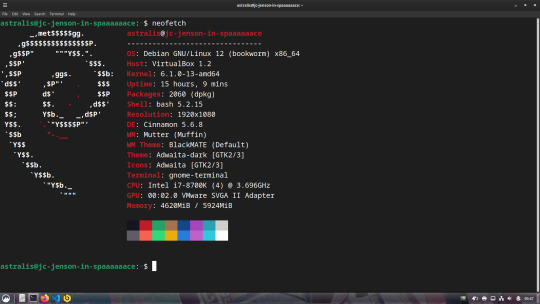
For those interested, this is what my dev machine looks like. Debian 12 + Cinnamon Desktop running inside of Virtual Box
The wallpaper is one I found on DA, but from what I can tell I don't think that the uploader was the original artist, especially after looking through the uploader's gallery. I have tried to find the original to no avail (TinEye, Lens, etc), so if someone finds the original artist I'd be more than grateful (and willing to shoot a few pounds their way cuz this piece is amazing)
Outside of that, I use VSCode most of the time on Linux, Komodo Edit (RIP T^T) on Windows, Beekeeper for SQL (database stuff) on Linux and Heidi on Windows, and Bash on Linux and Powershell on Windows for terminal/scripting.
For languages, it changes between three, Node/JS for web apps, C# for the majority of game and Windows stuff, and Elixir/Erlang (Oh look my MD OC's last name) for more random stuff cuz I'm trying to learn it.
So yea, thats my nerdy infodump for the moment, I do still create random website designs in my downtime after work but more often than not, I just play copious amounts of Trackmania and FFXIV.
4 notes
·
View notes
Text
QA Engineers || IT Company || Bank || Kolkata || West Bengal || India || World
Unlock Your Dream Job!
In this Job Post, we dive into the "Ideal Career Zone," revealing the secrets to finding your perfect profession!
Whether you’re hunting for a #job, searching #Naukri, or exploring new #Chakri options, we’ve got you covered with expert tips and career advice. From understanding your passions to mastering job searches and acing interviews, we empower you to navigate the competitive landscape with confidence!
Join us and discover how to elevate your career journey today!
Company Introduction:
A Global I T company head office in Bangalore they will work with you to make it a reality and enable you to deliver digital delight to your global customers. The digital age demands the strategy and execution that is relevant to the times, resilient to changes and drive ROI. Their solutions bring you a unique balance of strategy design and execution capability to realize your digital dreams.
Please find the attached JD for QA Engineers for Kolkata Location.
The experience range is 1 to 3 years and 3 to 5 years.
The Maximum budget for 1 to 3 years is 6 LPA and 3 to 5 years is 7.5 LPA.
Now they are looking for candidates who have the exposure into Loan Management System/ Loan Orientation Systems . Immediate Joiners are preferred
Job Description for QA Engineer
Location: Kolkata
We are seeking highly skilled Testing Specialists to support the Sales force implementation for loan origination processes. The ideal candidates will have expertise in functional, integration, regression, and User Acceptance Testing (UAT) across Sales force and Flex cube LMS. They will work collaboratively with business analysts, developers, and configuration teams to ensure seamless system behavior and optimal performance.
Key Responsibilities:
Validate and analyze the complete Loan Origination lifecycle, including lead capture, application processing, credit evaluation, approval workflows, disbursements, and system handoffs to Flex cube LMS.
Design and execute test plans, test cases, and test scripts for Sales force-based origination workflows and Flex cube integrations.
Conduct functional, integration, regression, and UAT testing for housing loan journeys across Sales force and Flex cube.
Verify critical components of the origination process, including:
Customer on boarding (KYC, eligibility verification).
Loan application creation, submission, and processing.
Document collection and validation.
Credit appraisal, approval, and final disbursement workflows in Flex cube LMS.
Validate data synchronization, integration points, and system interactions between Sales force and Flex cube.
Perform backend validations using SQL queries and investigate potential issues using logs or APIs.
Log, track, and manage defect resolution using standard test management tools (e.g., SPIRA, JIRA, Test Rail, HP ALM).
Collaborate closely with developers, business analysts, Sales force consultants, and Flex cube configuration teams to ensure system integrity and business requirement alignment.
Required Skills & Qualifications:
Hands-on experience in testing Sales force-based workflows and Flex cube LMS integrations.
Strong understanding of the loan origination process and associated financial systems.
Proficiency in SQL queries, API validations, and backend data integrity checks.
Experience with defect tracking and standard test management tools (SPIRA, JIRA, Test Rail, HP ALM).
Excellent problem-solving and analytical skills.
Ability to work collaboratively in a fast-paced project-driven environment.
Preferred Qualifications:
Prior experience in banking and financial sector testing.
Knowledge of Sales force ecosystem and Flex cube LMS configurations.
Interested candidates are most welcome to apply with their updated resumes at – [email protected] and please you must mentioned post which you wish to apply or call HR: 9331205133
* Note:- You can find many more job details in various posts in various companies.
You may call us between 9 am to 8 pm
8 7 7 7 2 1 1 zero 1 6
9 3 3 1 2 zero 5 1 3 3
Or you can visit our office.
Ideal Career Zone
128/12A, BidhanSraniShyam Bazaar metro Gate No.1 Gandhi Market Behind Sajjaa Dhaam Bed Sheet Bed cover Show room Kolkata 7 lakh 4
Thank you for watching our channel Please subscribed and like our videos for more jobs opening. Thank You again.
#QAEngineers, #Bank, #Recruiter, #ITCompany, #DataEngineer, #Kolkata, #WestBengal, #India, #World,
0 notes
Text
What is Django for beginners.
What is Django for Beginners?
Django is a high-level web framework for Python that encourages rapid development and clean, pragmatic design. It was created to help developers build web applications quickly and efficiently, allowing them to focus on writing code rather than dealing with the complexities of web development. For beginners, Django offers a powerful yet accessible way to learn the fundamentals of web development while building real-world applications.
Understanding Django
At its core, Django is designed to simplify the process of building web applications. It follows the Model-View-Template (MVT) architectural pattern, which separates the application into three interconnected components:
Model: This component handles the data and business logic. It defines the structure of the data, including the fields and behaviors of the data you’re storing. In Django, models are defined as Python classes, and they interact with the database to create, read, update, and delete records.
View: The view is responsible for processing user requests and returning the appropriate response. It acts as a bridge between the model and the template, retrieving data from the model and passing it to the template for rendering.
Template: Templates are used to define the presentation layer of the application. They are HTML files that can include dynamic content generated by the view. Django’s templating engine allows you to create reusable components and maintain a clean separation between the presentation and business logic.
Key Features of Django
Django comes with a plethora of features that make it an excellent choice for beginners:
Batteries Included: Django is often described as a "batteries-included" framework because it comes with a wide range of built-in features. This includes an admin panel, user authentication, form handling, and security features, which means you can get started quickly without needing to install additional packages.
Robust Security: Security is a top priority in Django. The framework provides built-in protections against common web vulnerabilities such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). This allows beginners to focus on building their applications without worrying about security issues.
Scalability: Django is designed to handle high-traffic applications. Its architecture allows for easy scaling, making it suitable for both small projects and large-scale applications. As your application grows, Django can accommodate increased traffic and data without significant changes to the codebase.
Versatile Database Support: Django supports multiple database backends, including SQLite, PostgreSQL, MySQL, and Oracle. This flexibility allows beginners to choose the database that best fits their needs and easily switch between them if necessary.
Strong Community and Documentation: Django has a large and active community, which means there are plenty of resources available for beginners. The official documentation is comprehensive and well-structured, making it easy to find information and learn how to use the framework effectively.
Benefits of Using Django for Beginners
Ease of Learning: Django’s clear and consistent design makes it easy for beginners to grasp the concepts of web development. The framework’s use of Python, a language known for its readability and simplicity, further lowers the barrier to entry.
Rapid Development: With Django, you can quickly build and deploy web applications. The framework’s built-in features and tools streamline the development process, allowing you to focus on writing code rather than dealing with repetitive tasks.
Community Support: As a beginner, having access to a supportive community can be invaluable. Django’s community is welcoming and offers numerous tutorials, forums, and resources to help you learn and troubleshoot issues.
Portfolio Development: Learning Django allows you to build real-world applications that you can showcase in your portfolio. This is particularly beneficial if you’re looking to enter the job market as a web developer, as having practical experience can set you apart from other candidates.
Long-Term Viability: Django is a mature framework that has been around since 2005. It is actively maintained and updated, ensuring that it remains relevant in the ever-evolving landscape of web development. By learning Django, you are investing in a skill that will be valuable for years to come.
Getting Started with Django
If you’re a beginner looking to dive into Django, here’s a simple roadmap to get you started:
Install Python: Since Django is a Python framework, the first step is to ensure you have Python installed on your machine. You can download it from the official Python website.
Set Up a Virtual Environment: It’s a good practice to create a virtual environment for your Django projects. This keeps your project dependencies isolated from other projects. You can use tools like venv or virtualenv to create a virtual environment.
Install Django: Once your virtual environment is set up, you can install Django using pip, Python’s package manager. Run the command pip install django in your terminal to get started.
Create a New Project: Use Django���s command-line tool to create a new project. Run django-admin startproject projectname to generate the necessary files and directory structure.
Run the Development Server: Navigate to your project directory and run the command python manage.py runserver. This will start a local development server, allowing you to view your application in your web browser.
Build Your First App: Django encourages a modular approach to development. You can create individual applications within your project using the command python manage.py startapp appname. From there, you can define models, views, and templates to build your application.
Explore Tutorials and Resources: Take advantage of the wealth of tutorials, documentation, and online courses available for Django. Websites like Django’s official documentation, YouTube, and platforms like Udemy and Coursera offer valuable learning materials.
Conclusion
In summary, Django is an excellent choice for beginners looking to learn web development. Its powerful features, robust security, and supportive community make it an ideal framework for building web applications. By understanding the fundamentals of Django and following a structured learning path, you can quickly gain the skills needed to create dynamic, data-driven websites. Whether you’re looking to build a personal project, enhance your portfolio, or start a career in web development, Django provides the tools and resources to help you succeed.
0 notes
Text
Lead Consultant - Site Reliability Engineers/L2
, Microservices, C#, .Net, ETL Informatica, C++, Extjs. TypeScript, R-Code, XML/XSLT, SQL, T-SQL, PL/SQL, PHP, VB Script, Microsoft… Apply Now
0 notes
Text
PixelPhoto Nulled Script 1.6.0

PixelPhoto Nulled Script – The Ultimate Photo Sharing Experience Looking for a powerful image-sharing platform that doesn’t break the bank? PixelPhoto Nulled Script is your ideal solution. Whether you’re an aspiring photographer, social media influencer, or tech-savvy entrepreneur, this premium social network platform gives you the freedom to create your own Instagram-style website—completely free. Say goodbye to costly subscriptions and hello to limitless customization with this nulled gem. What is PixelPhoto Nulled Script? The PixelPhoto Nulled Script is a high-performance image-sharing and social networking script developed to rival platforms like Instagram and Flickr. It’s packed with advanced features, a responsive design, and an intuitive user interface. Thanks to the nulled version, you can enjoy full access to all premium tools and functionalities—without spending a dime. Technical Specifications Framework: Laravel 8.x Database: MySQL 5.x or later Server Requirements: PHP 7.4 or higher, OpenSSL, cURL, Mbstring, PDO, and Fileinfo extensions Compatibility: Fully responsive across mobile, tablet, and desktop Languages: Multilingual support with RTL compatibility Outstanding Features & Benefits Customizable UI: Tweak the layout, colors, and branding to match your vision. Monetization Tools: Built-in options for ads, subscriptions, and premium memberships. High-Speed Performance: Fast-loading pages optimized for SEO and user retention. Multi-Media Support: Seamlessly upload and manage images, GIFs, and short videos. Secure Login & Registration: OAuth, email, and two-step authentication available. How PixelPhoto Nulled Script Benefits You One of the biggest advantages of using the PixelPhoto Nulled Script is freedom—freedom to explore, customize, and build your online community without financial barriers. You get access to premium capabilities usually locked behind a paywall, which makes it ideal for startups and individuals who want to launch fast and scale smart. Best of all, it works flawlessly alongside popular plugins like Slider Revolution NULLED—a perfect match for crafting visually stunning image galleries and carousels. Real-World Use Cases Photography Portfolios: Showcase your best shots in a professional, dynamic layout. Private Communities: Build niche social networks around hobbies, brands, or causes. Marketing & Promotions: Share branded content, run campaigns, and interact with followers. Online Galleries: Host and organize exhibitions, events, or digital art showcases. Installation Guide Installing the PixelPhoto Nulled Script is straightforward. Here’s a step-by-step overview to get you started: Download the latest version of the script (nulled) from our site. Upload all files to your web server using FTP or File Manager. Create a new MySQL database and import the SQL file included. Open config.php and input your database credentials. Follow the installation wizard in your browser to finalize setup. FAQs – Frequently Asked Questions Is the PixelPhoto Nulled Script safe to use? Yes, our version is pre-tested and malware-free. However, always use a secure hosting environment and regular backups for optimal safety. Can I monetize my platform with this script? Absolutely. The script includes built-in monetization features like ads, subscriptions, and sponsored posts to help you earn from your community. Does it support plugins? Yes, it supports a variety of third-party tools and integrates well with popular plugins such as wpbakery nulled to help you design your pages with ease. Can I rebrand the platform? Yes! You can customize every element—from logos to layouts—to reflect your unique identity. Start Your Photo Sharing Journey Today Why wait to create the next big thing in image sharing? With the PixelPhoto , you're only a few clicks away from building your own Instagram-like platform—fully free and loaded with premium features. Download it today and bring your creative vision to life.
0 notes
Text
Linux CLI 55 🐧 shell scripts output text
New Post has been published on https://tuts.kandz.me/linux-cli-55-%f0%9f%90%a7-shell-scripts-output-text/
Linux CLI 55 🐧 shell scripts output text

youtube
a - echo in shell scripts echo command in shell scripting is a fundamental tool for outputting text or variables echo "Hello, World!" → prints Hello World echo $greeting → prints the content of $greeting variable you can use escape characters as well echo "This is a newline:\nAnd this is a tab:\t." → using tab escape character -n option avoids new line echo -n "Hello, " → avoids new line b - printf and here document in shell scripts printf offers more precise control over the output format printf "Name: %s\nAge: %d\n" "$name" "$age" → formating text with printf printf "%.2f\n" "$number" → Output will be "123.46" Here documents are a way to pass multi-line text input into commands or scripts. This is particularly useful for passing large blocks of text or SQL queries. example 1 → multiline example example 2 → use of variables example
0 notes
Text
Top Vulnerability Assessment Tools to Secure Your Digital Assets
Cyberattacks are a reality in today's linked world that should not be neglected. Organizations that fail to recognize the magnitude of such risks threaten substantial reputational, financial, and legal consequences. As a result, they are not only a nightmare for end users but also a serious issue for enterprises.
But the million-plus query is, what are the main reasons for cyberattacks? Security experts declare that the primary causes of cyberattacks are social engineering, human errors, and vulnerabilities. While you can control the former two aspects with stronger security protocols and policies, vulnerabilities remain a constant threat.
Attackers frequently seek the flaws in targeted systems or apps because they provide the best potential to breach their security. Attackers can use vulnerabilities to carry out a variety of attacks, including cross-site scripting, SQL injection, session hijacking, and more.
Organizations require a thorough vulnerability assessment program to manage associated risks. You may automate this process by using feature-rich technologies that aid in the detection, categorization, and prioritizing of vulnerabilities. These vulnerability assessment tools help speed up the entire procedure.
This blog seeks to provide a comprehensive overview of vulnerability assessments, how they function, and the best tools. Continue scrolling for more details.
Download the sample report of Market Share: https://qksgroup.com/download-sample-form/market-share-vulnerability-assessment-2023-worldwide-6988
What is Vulnerability Assessment?
QKS Group defines vulnerability assessment as a comprehensive solution that enables organizations to identify, evaluate, and prioritize vulnerabilities within their IT infrastructure. Utilizing advanced automated tools and manual inspection techniques, it scans systems, applications, and network resources to uncover security weaknesses. By providing detailed reports on identified vulnerabilities, it empowers IT teams to address and mitigate risks effectively. Vulnerability Assessment solutions help prevent potential breaches, reduce the attack surface, and enhance overall cybersecurity posture.
Functionality of Vulnerability Scanning Solutions
The functionality of vulnerability scanning systems is essential for every company that produces and maintains large volumes of data, which frequently includes sensitive information specific to that organization. Attackers may attempt to identify and exploit weaknesses in the organization's systems to get unauthorized access to private data. Vulnerability analysis discovers and assesses risky locations inside an organization's network. This includes using various tools to find vulnerabilities and producing reports on the findings.
The vulnerability assessment scanning process is typically composed of three main actions:
Identifying Active Devices: The first step in the scanning procedure is identifying active devices within the target network using diverse scanning methods.
Cataloging Services and Operating Systems: Following the identification of active hosts, the following action is to catalogue the open ports and services and authenticate the operating systems running on the identified systems.
Evaluating for Vulnerabilities: The last stage involves examining the selected services and operating systems for any known vulnerabilities.
Top Vulnerability Assessment Tools
Undoubtedly, you want to use the finest tool for assessing digital assets for vulnerabilities. Such a tool will provide precise data, faster scanning times, convenience of use, and several other advantages. It would be much better if they were free. This is what you'll receive with the tools listed below.
Rapid7
Rapid7, Inc. strives to build a safer digital world by simplifying and making cybersecurity more accessible. Rapid7's technology, research, and extensive strategic skills enable security professionals across the world to handle a modern attack surface. Rapid7's comprehensive security solutions assist over 11,000 clients in combining cloud risk management with threat detection and response to decrease attack surfaces and eradicate attacks quickly and accurately.
Tenable Nessus
Tenable is an exposure management company that identifies and closes cybersecurity holes that reduce corporate value, reputation, and trust. The company's AI-powered exposure management platform dramatically integrates security visibility, insight, and action across the attack surface, enabling contemporary companies to defend against assaults on IT infrastructure, cloud environments, critical infrastructure, and everything in between.
Holm Security VMP
Holm Security is a next-generation vulnerability management software supplier that focuses on thorough 360-degree inspection. The business specializes in helping enterprises with vulnerability detection, risk assessment, and remedial prioritization. This is realized for all assets across a company. The solution has three levels and offers all the tools required for smooth vulnerability management.
RidgeBot
Ridge Security offers a new solution for security testing with their product, RidgeBot, an Intelligent Penetration Testing Robot. RidgeBot uses complex ways to penetrate networks comparable to those employed by hackers. RidgeBot, once inserted into a system, hunts out, exploits, and documents any flaws it discovers. It functions within a set scope and can quickly adapt to extremely complicated structures. Ridge Security's products benefit business and web application teams, ISVs, government agencies, educational institutions, and any other party responsible for software security by allowing them to test their systems economically and efficiently.
WithSecure Elements
WithSecure was once known as F-Secure Business. IT service providers, MSSPs, and enterprises rely on us for results-driven cyber security that protects and empowers their operations. WithSecure's AI-driven security safeguards endpoints and cloud collaboration, and its intelligent detection and response capabilities are powered by specialists that identify business risks by actively scanning for threats and combating actual attacks.
Download the sample report of Market Forecast: https://qksgroup.com/download-sample-form/market-forecast-vulnerability-assessment-2024-2028-worldwide-7141
Growing Demand for Vulnerability Assessment Solutions Amid Rising Cyber Threats
The global market for Vulnerability Assessment solutions is expanding rapidly, driven by rising cyber threats and demanding regulatory requirements across sectors. Organizations across the world are rapidly investing in sophisticated Vulnerability Assessment technologies to strengthen their cybersecurity defenses, minimize risks, and maintain compliance with regulatory requirements such as GDPR, HIPAA, and PCI-DSS. The proliferation of cloud computing, IoT, and other digital technologies is driving up demand for these solutions, as organizations strive to secure their digital assets and maintain operational resilience in an increasingly linked world.
The future of the Vulnerability Assessment market on a global scale appears promising, marked by continuous technological innovations and a proactive approach to cybersecurity. As cyber-attacks become more sophisticated and pervasive, there is a growing emphasis on deploying advanced Vulnerability Assessment solutions that offer real-time insights through Market Share: Vulnerability Assessment, 2023, Worldwide" and "Market Forecast: Vulnerability Assessment, 2024-2028, Worldwide" reports by QKS Group and proactive threat management capabilities.
Incorporating artificial intelligence, machine learning, and automation into these solutions will play a vital role in increasing their efficacy and allowing enterprises to remain ahead of new risks. Furthermore, increased collaboration between the public and private sectors and rising organizational awareness of the importance of cybersecurity will drive global adoption of Vulnerability Assessment tools, ensuring a secure digital landscape for both businesses and consumers.
0 notes
Text
Các Tính Năng Bảo Mật Tiên Tiến Trên Cloud Server: Giải Pháp Ngăn Ngừa Tấn Công Mạng
Trong kỷ nguyên số, các doanh nghiệp và tổ chức đang ngày càng chuyển sang sử dụng Cloud Server như một giải pháp hạ tầng linh hoạt, tiết kiệm chi phí và có khả năng mở rộng mạnh mẽ. Tuy nhiên, với sự phát triển nhanh chóng của các mối đe dọa an ninh mạng, bảo mật trở thành một yếu tố quan trọng khi sử dụng máy chủ ảo đám mây. Để đảm bảo an toàn cho dữ liệu và ứng dụng, các nhà cung cấp Cloud Server đã triển khai nhiều tính năng bảo mật tiên tiến để ngăn ngừa các cuộc tấn công mạng. Bài viết này sẽ điểm qua một số tính năng bảo mật quan trọng và cách chúng giúp bảo vệ các hệ thống đám mây khỏi các nguy cơ an ninh.
Mã hóa Dữ liệu (Encryption)
Một trong những tính năng bảo mật cơ bản và quan trọng nhất trên Cloud Server là mã hóa dữ liệu. Khi dữ liệu được mã hóa, nó trở thành không thể đọc được mà không có khóa giải mã chính. Dữ liệu có thể được mã hóa khi lưu trữ (encryption at rest) và trong quá trình truyền tải (encryption in transit). Việc mã hóa đảm bảo rằng ngay cả khi dữ liệu bị xâm nhập, tin tặc cũng không thể đọc hay sử dụng dữ liệu nếu không có khóa giải mã thích hợp.
Mã hóa khi lưu trữ (At Rest Encryption): Bảo vệ dữ liệu khi nó được lưu trữ trên các ổ đĩa hoặc các hệ thống đám mây.
Mã hóa khi truyền tải (In Transit Encryption): Đảm bảo rằng dữ liệu không bị rò rỉ hoặc bị đánh cắp khi di chuyển qua các kết nối mạng (như SSL/TLS).
Xác thực Đa Yếu Tố (Multi-Factor Authentication - MFA)
Xác thực đa yếu tố là một lớp bảo vệ thêm giúp bảo vệ tài khoản người dùng khỏi các cuộc tấn công mạng, đặc biệt là tấn công brute force (tấn công dò mật khẩu). MFA yêu cầu người dùng cung cấp hai hoặc nhiều yếu tố xác thực trước khi có thể truy cập vào hệ thống. Thông thường, yếu tố xác thực này bao gồm:
Yếu tố biết (Something you know): Mật khẩu hoặc mã PIN.
Yếu tố sở hữu (Something you have): Một mã được gửi qua SMS hoặc ứng dụng xác thực.
Yếu tố đặc điểm sinh trắc học (Something you are): Vân tay, nhận diện khuôn mặt hoặc quét mống mắt.
Xác thực đa yếu tố ngăn chặn việc đăng nhập trái phép ngay cả khi tin tặc biết mật khẩu của người dùng.
Tường lửa (Firewall) và Hệ thống Phát hiện Xâm nhập (IDS)
Tường lửa là một yếu tố quan trọng trong việc bảo vệ Cloud Server khỏi các tấn công từ bên ngoài. Nó giám sát và kiểm soát lưu lượng mạng vào và ra, chỉ cho phép các kết nối hợp lệ. Các nhà cung cấp Cloud Server thường tích hợp tường lửa với các hệ thống phát hiện xâm nhập (IDS) và phòng chống xâm nhập (IPS) để phát hiện và ngăn chặn các cuộc tấn công có chủ đích.
Tường lửa ứng dụng (WAF - Web Application Firewall): Bảo vệ các ứng dụng web khỏi các cuộc tấn công phổ biến như SQL injection, cross-site scripting (XSS), và các mối đe dọa khác.
Hệ thống phát hiện xâm nhập (IDS): Giám sát và phân tích lưu lượng mạng để phát hiện hành vi bất thường có thể là dấu hiệu của một cuộc tấn công.
Quản lý Quyền Truy Cập (Identity and Access Management - IAM)
Quản lý quyền truy cập giúp đảm bảo rằng chỉ những người có quyền mới có thể truy cập vào các tài nguyên quan trọng trong môi trường đám mây. Hệ thống quản lý danh tính và quyền truy cập (IAM) cho phép các tổ chức phân quyền truy cập cho người dùng và nhóm người dùng dựa trên các vai trò và nhu cầu công việc của họ.
Quy tắc nguyên tắc "ít quyền nhất" (Least Privilege): Mỗi người dùng chỉ có quyền truy cập những tài nguyên mà họ thực sự cần để thực hiện công việc của mình.
Kiểm tra và audit quyền truy cập: Quản lý IAM cung cấp các báo cáo và theo dõi để kiểm soát và đánh giá ai đã truy cập vào hệ thống và khi nào.
Giám sát và Báo cáo An ninh (Security Monitoring and Reporting)
Giám sát liên tục là một phương pháp quan trọng trong việc phát hiện sớm các mối đe dọa và tấn công. Công cụ giám sát bảo mật cung cấp các chỉ số thời gian thực về hoạt động của hệ thống, giúp phát hiện và ứng phó kịp thời với các sự cố an ninh.
Giám sát lưu lượng mạng và nhật ký hệ thống: Các công cụ giám sát giúp theo dõi lưu lượng mạng và phân tích các sự kiện đáng ngờ.
Cảnh báo tự động: Các hệ thống bảo mật có thể gửi cảnh báo tự động khi phát hiện các hành vi không bình thường hoặc có nguy cơ tấn công.
Tính Năng Backup và Phục Hồi (Backup and Disaster Recovery)
Mặc dù các biện pháp bảo mật có thể giúp ngăn ngừa hầu hết các cuộc tấn công, nhưng không thể loại bỏ hoàn toàn rủi ro. Vì vậy, việc sao lưu dữ liệu và có kế hoạch phục hồi sau thảm họa là một phần quan trọng của chiến lược bảo mật trên Cloud Server.
Sao lưu thường xuyên: Dữ liệu quan trọng cần được sao lưu vào các vị trí an toàn để có thể phục hồi nếu có sự cố xảy ra.
Phục hồi sau thảm họa: Các công cụ phục hồi giúp nhanh chóng khôi phục hệ thống trong trường hợp xảy ra tấn công hoặc lỗi hệ thống nghiêm trọng.
Cập nhật và Vá Lỗ Bảo Mật (Security Patching)
Các nhà cung cấp Cloud Server thường xuyên cập nhật các hệ thống của họ để vá các lỗ hổng bảo mật. Cập nhật và vá lỗi kịp thời là một trong những biện pháp bảo mật quan trọng giúp bảo vệ máy chủ đám mây khỏi các cuộc tấn công dựa trên lỗ hổng.
Kết Luận
Bảo mật trên Cloud Server không chỉ dựa vào một tính năng duy nhất, mà là sự kết hợp của nhiều công nghệ và phương pháp để bảo vệ dữ liệu và ứng dụng khỏi các mối đe dọa mạng. Các tính năng bảo mật tiên tiến như mã hóa, xác thực đa yếu tố, tường lửa, quản lý quyền truy cập, giám sát bảo mật và sao lưu dữ liệu giúp xây dựng một môi trường an toàn và đáng tin cậy cho các doanh nghiệp khi sử dụng dịch vụ Cloud Server.
Để đảm bảo an toàn tối đa, các tổ chức cần liên tục theo dõi, cập nhật và cải thiện các biện pháp bảo mật của mình, đồng thời kết hợp với các nhà cung cấp Cloud có uy tín để tận dụng các công nghệ bảo mật tiên tiến nhất.
Thông tin chi tiết: https://vndata.vn/cloud-server/
0 notes
Text
Error Handling with RAISEERROR and THROW in T-SQL Server
Mastering Error Handling in SQL Server: RAISEERROR and THROW Hello, SQL enthusiasts! In this blog post, I will introduce you to Error Handling using RAISEERROR and THROW in T-SQL Server – one of the most important concepts in SQL Server: error handling using RAISEERROR and THROW. These commands allow you to manage and report errors effectively within your T-SQL scripts. Proper error handling is…
0 notes
Text
A Guide to Columnstore Index Maintenance
In today’s data-driven world, the ability to efficiently manage and analyze vast amounts of information is paramount. SQL Server, a cornerstone technology in the realm of database management, offers a powerful feature known as Columnstore Indexes. These indexes are designed to dramatically improve query performance, making them an indispensable tool for businesses that rely on data analytics. In…
View On WordPress
#Columnstore Index maintenance#data analytics performance#database management techniques.#SQL Server optimization#T-SQL scripts
0 notes
Text
Lead Consultant - Log Analytics/Intelligent Monitoring/Automation
-Code, XML/XSLT. SQL, T-SQL, PL/SQL, PHP, VB Script, Microsoft Power Platforms (Power Apps/Power Automate/ Power BI… Apply Now
0 notes
Text
Unlocking the Future of Data Engineering with Ask On Data: An Open Source, GenAI-Powered NLP-Based Data Engineering Tool
In the rapidly evolving world of data engineering, businesses and organizations face increasing challenges in managing and integrating vast amounts of data from diverse sources. Traditional data engineering processes, including ETL (Extract, Transform, Load) and ELT (Extract, Load, Transform), often require specialized expertise, are time-consuming, and can be error-prone. To address these challenges, innovative technologies like Generative AI (GenAI), Large Language Models (LLM), and Natural Language Processing (NLP) are reshaping how data engineers and analysts work with data. One such breakthrough solution is Ask On Data, an NLP based data engineering tool that simplifies the complexities of data integration, transformation, and loading through conversational interfaces.
What is Ask On Data?
Ask On Data is an open-source NLP based ETL tool that leverages Generative AI and Large Language Models (LLMs) to enable users to interact with complex data systems in natural language. With Ask On Data, the traditionally technical processes of data extraction, data transformation, and data loading are streamlined and made accessible to a broader range of users, including those without a deep technical background in data engineering.
The tool bridges the gap between the technical demands of data engineering and the need for more intuitive, accessible interfaces. Through simple, conversational commands, users can query, transform, and integrate data, eliminating the need for writing complex code. This functionality significantly reduces the time and effort required for managing data pipelines, making it ideal for organizations looking to automate and optimize their data workflows.
How Ask On Data Works: NLP Meets Data Engineering
The core innovation of Ask On Data lies in its ability to understand and process natural language commands related to data integration, data transformation, and data loading. The tool uses Natural Language Processing (NLP) to parse and execute commands, enabling users to work with data systems without needing to master SQL or scripting languages.
Data Integration: Ask On Data connects seamlessly with various data sources, whether it’s a data lake, data warehouse, or cloud-based data storage system. Users can simply input commands like, “Integrate data from my sales database with customer feedback from the cloud,” and Ask On Data will manage the connection, data extraction, and integration processes.
Data Transformation: Data transformation is another area where Ask On Data excels. Users can request transformations in natural language, such as “Convert all dates in this dataset to ISO format” or “Aggregate sales data by region for the last quarter,” and the tool will apply the transformations without needing complex scripts.
Data Loading: Once data is transformed, Ask On Data can automatically load it into the target system, whether it’s a data warehouse for analytics or a data lake for storage. Users can issue simple commands to initiate loading, such as “Load transformed data into the reporting database.”
Benefits of Ask On Data in Data Engineering
Simplified Data Operations: By using natural language to manage ETL/ELT processes, Ask On Data lowers the barrier for non-technical users to access and manipulate data. This democratization of data engineering allows business analysts, data scientists, and even executives to interact with data more easily.
Increased Efficiency: Automation of routine data tasks, like data extraction, transformation, and loading, speeds up the process and reduces human errors. With GenAI at its core, Ask On Data can also generate code or queries based on user instructions, making it a powerful assistant for data engineers.
Open-Source Flexibility: Ask On Data is an open-source tool, meaning it is freely available and highly customizable. Organizations can adapt the tool to fit their specific needs, from integrating it into custom workflows to extending its capabilities through plugins or custom scripts.
Improved Collaboration: With its intuitive, chat-based interface, Ask On Data fosters better collaboration across teams. Data engineers can focus on more complex tasks while empowering other stakeholders to interact with data without fear of making mistakes or having to understand complex technologies.
The Future of Data Engineering with NLP and GenAI
The integration of Generative AI and LLMs into data engineering tools like Ask On Data represents a paradigm shift in how data operations are managed. By combining the power of AI with the simplicity of NLP, Ask On Data enables organizations to make smarter, faster decisions and streamline their data workflows.
As businesses continue to generate more data and migrate towards cloud-based solutions, tools like Ask On Data will become increasingly important in helping them integrate, transform, and analyze data efficiently. By making ETL and ELT processes more accessible and intuitive, Ask On Data is laying the groundwork for the future of data transformation, data loading, and data integration.
Conclusion,
Ask On Data is an innovative NLP-based data engineering tool that empowers users to manage complex data workflows with ease. Whether you're working with a data lake, a data warehouse, or cloud-based platforms, Ask On Data’s conversational interface simplifies the tasks of data transformation, data integration, and data loading, making it a must-have tool for modern data engineering teams.
0 notes
Text
Consultant - Batch Operations
Informatica, C++, Extjs, TypeScript, R-Code, XML/XSLT, SQL, T-SQL, PL/SQL, PHP, VB Script, Microsoft Power Platforms (Power Apps… Apply Now
0 notes
Text
So, I've eliminated a few paths already. One has nice examples that the author says are scripts. They're not Batch commands. If they're PowerShell, I don't have the right module (and it doesn't look right to my untrained eye). So what are they? Another was supposedly learning to use ScriptDOM, but no explanation of what to create is included. Maybe I'm too inexperienced to understand some stuff, but if you don't include at least a file type I'm fairly sure you skipped something.
So I'm trying this. It's worth a shot. First step, have a database project in VS. Uhm... I've never done that. I know why we should. But my work has a history of not requiring programmers to document what we do on production systems. Finally got the server admins doing it a while ago, but folks like me live dangerously. Grumble.
So - step 1, create a database. It's not a listed step, but apparently you don't do the creation in VS. There's no step for it in the template listing at least.
So instead I'm doing https://medium.com/hitachisolutions-braintrust/create-your-first-visual-studio-database-project-e6c22e45145b
Step one: in SSMS run the command:
CREATE DATABASE TCommon
T for temporary, and Common is a database I've already got going. It's for non-secure tools/programs/etc. that any of the other databases should be able to access.
Now to start up VS 2022. We begin a new project and search for database templates.
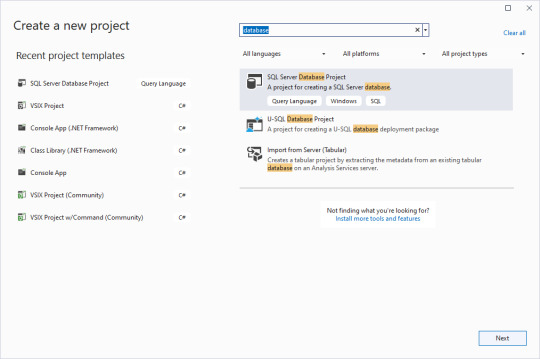
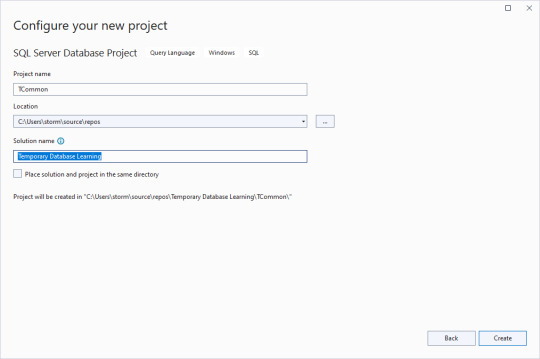
Clear the checkbox for putting the solution and project in the same directory, and give an overarching name to the solution. That way you can have multiple database projects worked on inside of one solution.
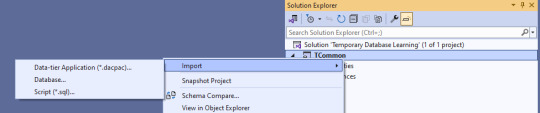
Next, we import the blank database so we have a test bed based off what is in production. Right click on the solution name, select Import, then Database.
The import database wizard looks like this after the connection is set.
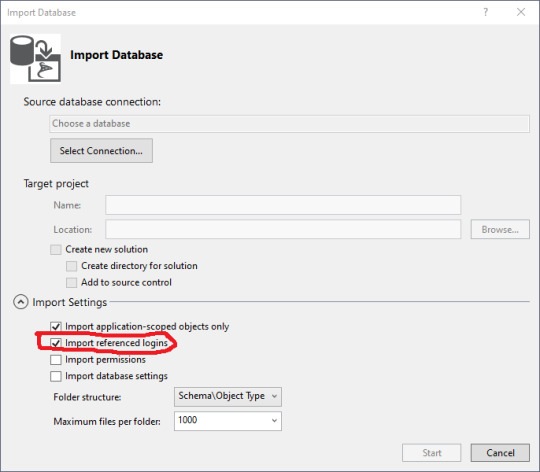
Blackburn suggests that you turn off the importation of referenced logins so you don't accidentally alter permissions. Sound strategy.
Then you can click on the "Select Connection" button.
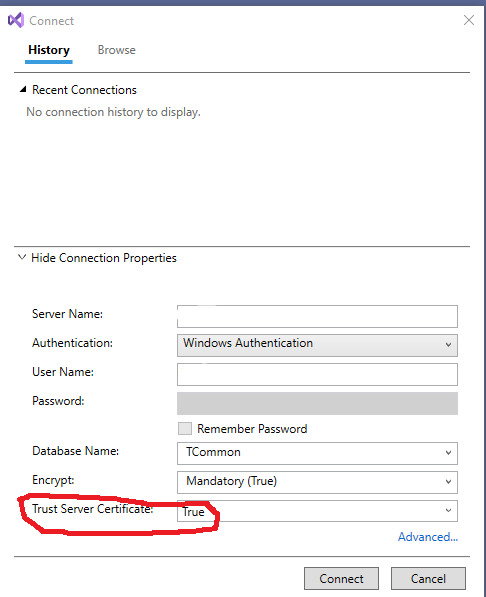
On my workstation, I have to Show Connection Properties, then change the default for Trust Server Certificate to True for it to make a connection. I'm running a test version of SQL Server and didn't set up the certificates.
Click on Connect. Then on the Import Database window, click Start.
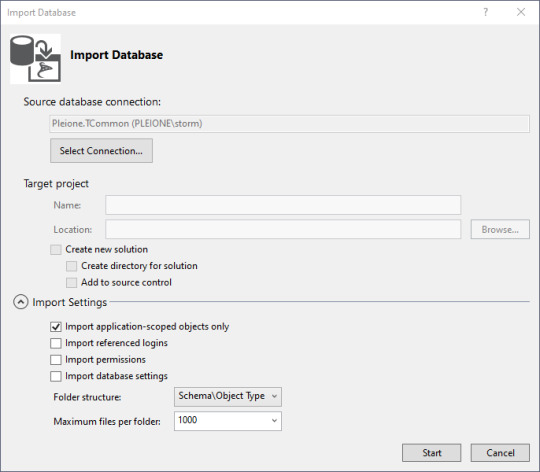
With a blank database, it's fairly anticlimactic, but there really is a connection now to the database, and the properties are copied to your work area. The summary tells you where the log is stored. Then click "Finish" to continue on.
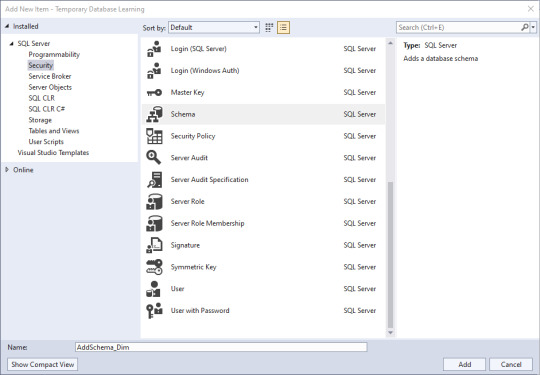
Next, we'll add some objects in. Right click in the Solution Explorer pane, then click Add, then New Item. Lots of little goodies to play with. Since I've been trying to match a project from another site, I need to create a schema to store the objects in. Schemas are part of Security, and there's my little object. I select the schema, give it a name down below, and click Add.
Well, not quite what I expected to happen: CREATE SCHEMA [AddSchema_Dim]
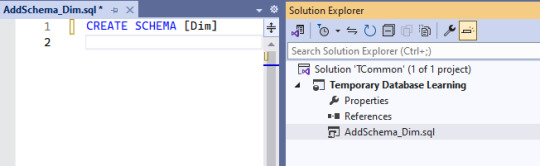
But that's changeable. And in making that change, the solution's object has the name I wanted, and the code has the actual name of the schema I want.
Now, lets add a table.
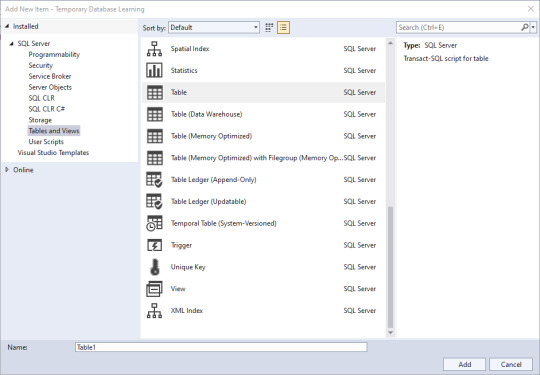
If you're like me, you've used a few of these, but not all of them. Time to do research if you're unsure, but I'm going to go with a simple table for this demonstration. Since I know the name of the solution object will take the name I put in the bottom, I'll name this one AddTable_Dim.Date, and know that I need to edit the actual code.
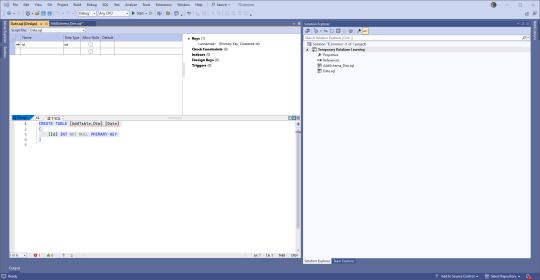
You have choices. If you're used to creating tables using the upper part of the pane where there is a GUI type of set up, go for that. If you're used to typing things out, go to the lower part. Or mix and match! VS will keep the two in sync.
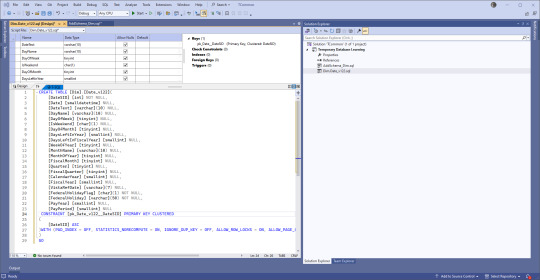
Instead of 'ID' we use 'SID' for Surrogate Identifier. The intake process sets up the unique (across a table) SID values and follows rules that help us track issues backwards to the original location where the data came from.
Second, there's a version number in there. We have the same tables across various enclaves (groups of servers), and we keep the versions the same between all but our development enclave. But instead of forcing our developers and end users to keep up, we use views that are in the databases they work from to expose the data. Many times we don't need to change the views at all which is easier on people that don't need to memorize a few hundred tables and variations.
I'm going to cut this off here, and start working on the next post. Back soon!
0 notes
Text
What skills are required for an MSBI developer?
In today's data-driven world, the role of a Microsoft Business Intelligence (MSBI) developer is important. These professionals wield the power to extract valuable insights from data, steering organizations toward informed decision-making and strategic growth. With the demand for proficient MSBI developers soaring, it's paramount to grasp the core skills requisite for success in this domain. In this article, we delve into the fundamental skills necessary for an MSBI developer while addressing common queries surrounding embarking on a career in MSBI.
Critical Skills for an MSBI Developer
SQL Proficiency: A robust command over SQL (Structured Query Language) is indispensable for MSBI developers. Given that MSBI solutions primarily involve querying and manipulating data stored in relational databases, a sound grasp of SQL queries, joins, and data manipulation techniques is imperative.
Data Modeling and ETL: MSBI developers must possess a strong foundation in data modeling concepts and hands-on experience with ETL tools like SQL Server Integration Services (SSIS). Their ability to design and execute efficient ETL processes, encompassing data extraction, transformation, and loading, is paramount for success in this role.
Comprehension of Business Intelligence Concepts: An MSBI developer's repertoire should include a profound understanding of business intelligence principles and methodologies. This entails familiarity with data warehousing fundamentals, dimensional modeling techniques, and OLAP (Online Analytical Processing) methodologies, empowering developers to craft BI solutions tailored to meet business users' analytical needs.
Mastery of the MSBI Stack: Proficiency in Microsoft's BI stack—comprising SQL Server, SSIS, SQL Server Analysis Services (SSAS), and SQL Server Reporting Services (SSRS)—is non-negotiable for MSBI developers. Their adeptness with these tools enables them to architect end-to-end BI solutions seamlessly.
Problem-Solving Aptitude and Analytical Skills: MSBI developers must exhibit robust problem-solving skills and analytical prowess to discern business requirements, analyze data effectively, and devise solutions aligned with organizational objectives. Their capacity to troubleshoot issues and fine-tune BI processes for optimal performance is critical for delivering impactful solutions.
Effective Communication and Collaboration: Strong communication and collaboration skills are indispensable for MSBI developers. Their ability to convey technical concepts to non-technical stakeholders and collaborate seamlessly with cross-functional teams facilitates the delivery of BI solutions that resonate with business imperatives.
Source : msbi certification
Conclusion
Becoming a proficient MSBI developer demands a blend of technical prowess, analytical acumen, and business acuity. By honing these requisite skills and staying abreast of industry trends, individuals can carve a rewarding career path in MSBI, driving organizational success through data-driven insights and solutions.
Frequently Asked Questions
1.Does MSBI require coding?
Yes, MSBI development typically entails coding, encompassing SQL queries, T-SQL scripts, and SSIS packages. While a strong coding acumen is advantageous, MSBI developers may also leverage graphical tools and wizards offered by MSBI platforms to design and deploy BI solutions.
2.What does an MSBI developer do?
An MSBI developer shoulders the responsibility of conceptualizing, crafting, and maintaining Business Intelligence (BI) solutions using Microsoft's BI stack. This entails a gamut of activities such as data modeling, ETL development, creation of analytical cubes, report and dashboard generation, and optimization of BI processes for enhanced performance and scalability.
3.Is MSBI a promising career path?
Indeed, MSBI offers a promising career trajectory for individuals inclined towards data analytics and business intelligence. Given the escalating demand for data-driven decision-making, organizations are increasingly reliant on BI solutions to derive actionable insights from their data. Consequently, adept MSBI professionals are highly sought after across industries, rendering it a lucrative career avenue for aspiring BI developers.
People also read : How To Start Your Career As MSBI Developer?
0 notes