#URL rewriting in Java
Explore tagged Tumblr posts
Text
How do you handle session management in Java for web applications?

1. Intro to Java Session Management
So, how do you manage sessions in Java for web apps? This is a key question for developers who want to create safe and scalable applications. Session management is all about keeping track of a user's activity on a web app over time. Java has built-in tools for this using HttpSession, cookies, and URL rewriting. Learning how to handle sessions well is an important skill, and taking a Java course in Coimbatore can provide you with hands-on experience. Whether you're just starting out or looking to be a full-stack developer, getting the hang of session concepts is essential for building secure and efficient apps.
2. Understanding HttpSession in Java
So, what about HttpSession? It’s the go-to API for managing sessions in Java. It keeps track of a user's info across several HTTP requests, created by the servlet container. You can access it using request.getSession(). With it, you can store user-specific data like login details or shopping cart items. If you enroll in Java training in Coimbatore, you will learn to create and manage sessions the right way. HttpSession also has methods to end sessions and track them, making it a key part of Java web development.
3. Session Tracking Techniques
When it comes to tracking sessions, there are some common methods: cookies, URL rewriting, and hidden form fields. Cookies are small bits of data saved on the client side, while URL rewriting adds session IDs to URLs. Hidden fields are less used but are still an option. These methods are thoroughly covered in a Java Full Stack Developer Course in Coimbatore. Knowing these options helps you pick the right one for your project. Each method has its benefits based on your app's security and scalability needs.
4. Importance of Session Timeout
Managing session timeout is super important for security and user experience. You can set up timeouts in the web.xml file or by using session.setMaxInactiveInterval(). This helps avoid unused sessions from taking up server resources and lowers the risk of hijacking. Sessions automatically end after a certain time without activity. In a Java course in Coimbatore, you’ll learn how to set timeout values that fit your app's needs. Proper timeout handling is part of building secure Java applications.
5. Secure Session Management Practices
How do you ensure session management is secure in your Java web applications? Always use HTTPS, create new session IDs when a user logs in, and end sessions when they log out. Avoid keeping sensitive info in sessions. Developers taking Java training in Coimbatore learn to apply these practices in real-life projects. Good session management isn't just about saving data; it's about protecting it, which helps safeguard against threats like session fixation.
6. Storing Complex Data in Sessions
When it comes to more complex data, Java sessions can handle that too. You can store objects using session.setAttribute(), which is great for keeping user profiles and cart items. Just remember that the objects need to be serializable and avoid making the session too big. Practical lessons in a Java Full Stack Developer Course in Coimbatore often touch on these points. Good data storage practices can improve performance and keep your code clean.
7. Session Persistence and Scalability
In cases where applications are spread across multiple servers, you have to think about sharing sessions. This can be done with persistent sessions or clustering. Tools like Redis and Memcached help manage state across servers. These ideas are often covered in advanced modules of Java courses in Coimbatore. Learning about session replication and load balancing is key to scaling your app while keeping the state intact.
8. Invalidating and Cleaning Sessions
Another important part of session management is cleaning up. Properly ending sessions is crucial. You can use session.invalidate() when a user logs out to terminate a session. Also, make sure to remove unnecessary attributes to save memory. Good session cleanup is important to prevent memory leaks and keep your app running smoothly. These topics are usually explained in Java training in Coimbatore, teaching students how to manage sessions responsibly.
9. Real-world Applications of Session Management
Understanding the theory is just one part. How does session management play out in the real world? Examples include e-commerce carts, user logins, and personalized dashboards. Sessions are essential for adding a personal touch. The Java Full Stack Developer Course in Coimbatore includes practical projects where session management is used in real web apps. Learning through practical examples helps solidify the concept and prepares developers for actual job roles.
10. Conclusion with Career Opportunities
Getting a handle on session management in Java can really open up job opportunities in backend or full-stack roles. With a solid grasp of HttpSession, tracking methods, and security measures, you'll be able to build secure applications. Whether you’re taking a Java course in Coimbatore or pursuing a full-stack course, this is a key topic you shouldn't overlook. At Xplore IT Corp, we focus on making sure our students are ready for the industry with practical session handling skills and more.
FAQs
1. What’s a session in Java web applications?
A session tracks a single user's activity with a web app over multiple requests and keeps user-specific info.
2. How do I create a session in Java?
You can create one using request.getSession() in servlet-based apps.
3. How do I expire a session in Java?
Use session.invalidate() to end it or set a timeout with setMaxInactiveInterval().
4. What are the options other than HttpSession?
You can use cookies, URL rewriting, hidden fields, or client-side storage depending on what you need.
5. Why is secure session management important?
To protect against threats like session hijacking and to keep user data safe.
#ava servlet session#Java web security#Java session timeout#Session tracking in Java#Cookies in Java#URL rewriting in Java#HttpSession methods#Java EE sessions#Serializable Java object#Java backend development
0 notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] 1.Java Networking Network Basics and Socket overview, TCP/IP client sockets, URL, TCP/IP server sockets, Datagrams, java.net package Socket, ServerSocket, InetAddress, URL, URLConnection. (Chapter - 1) 2.JDBC Programming The JDBC Connectivity Model, Database Programming : Connecting to the Database, Creating a SQL Query, Getting the Results, Updating Database Data, Error Checking and the SQLException Class, The SQLWarning Class, The Statement Interface, PreparedStatement, CallableStatement The ResultSet Interface, Updatable Result Sets, JDBC Types, Executing SQL Queries, ResultSetMetaData, Executing SQL Updates, Transaction Management. (Chapter - 2) 3.Servlet API and Overview Servlet Model : Overview of Servlet, Servlet Life Cycle, HTTP Methods Structure and Deployment descriptor ServletContext and ServletConfig interface, Attributes in Servlet, Request Dispacher interface. The Filter API: Filter, FilterChain, Filter Config Cookies and Session Management : Understanding state and session, Understanding Session Timeout and Session Tracking, URL Rewriting. (Chapter - 3) 4.Java Server Pages JSP Overview: The Problem with Servlets, Life Cycle of JSP Page, JSP Processing, JSP Application Design with MVC, Setting Up the JSP Environment, JSP Directives, JSP Action, JSP Implicit Objects JSP Form Processing, JSP Session and Cookies Handling, JSP Session Tracking JSP Database Access, JSP Standard Tag Libraries, JSP Custom Tag, JSP Expression Language, JSP Exception Handling, JSP XML Processing. (Chapter - 4) 5.Java Server Faces 2.0 Introduction to JSF, JSF request processing Life cycle, JSF Expression Language, JSF Standard Component, JSF Facelets Tag, JSF Convertor Tag, JSF Validation Tag, JSF Event Handling and Database Access, JSF Libraries : PrimeFaces. (Chapter - 5) 6.Hibernate 4.0 Overview of Hibernate, Hibernate Architecture, Hibernate Mapping Types, Hibernate O/R Mapping, Hibernate Annotation, Hibernate Query Language. (Chapter - 6) 7.Java Web Frameworks . Publisher : Technical Publications; First Edition (1 January 2021) Language : English Paperback : 392 pages ISBN-10 : 9333221638 ISBN-13 : 978-9333221634 Item Weight : 520 g Dimensions : 24 x 18.3 x 1.5 cm Country of Origin : India Generic Name : Books [ad_2]
0 notes
Text
Tumblr's 4th Annual Security Capture the Flag
We've hosted an internal Security Capture the Flag (CTF) event for four years in a row now, with each year getting better than the last!
The event
Previously, we were only open to Tumblr employees. This year we decided to extend an invite out to the other teams housed under our parent company, Oath.
All participants had a three hour window to hack, a buffet of tacos, beer, and wine to dive into, and a stack of prizes for the top four players (see Prizes below for details)!
Challenges were available Jeopardy-style, broken down by category. We had eight fun categories to select from:
Auth Bypass (authn | authz)
Cross Site Request Forgery (CSRF)
Cross Site Scripting (XSS)
Crypto
Forensics
Reverse Engineering
SQL Injection (SQLi)
XML Injection (+ XXE)
We also sprinkled a few "inside joke" Easter eggs around the system that awarded bonus points to anyone that discovered them! For example, if they attempted to find a hole in the CTF system itself and navigated to /wp-admin, we'd give them a flag on a prank WordPress page; or perhaps testing to find XSS with a <marquee> tag — only the greatest of all XSS tags!
While the Security Team walked around and helped out, we also setup a mini lockpick village just because.
Solving challenges & scoring points
To complete a challenge, the player had to achieve the goal within one of the listed categories.
In XSS challenges, the player would need to cause the browser to create an alert dialog (e.g. alert()).
Conversely, in SQL Injection challenges the player would need to read the flag column from the flags table in that challenge's database.
When the player successfully solved the challenge they were awarded with a flag, each in the format ofTumblr{s0mE_cHalL3nGe_j0kE-abcdef012}. That last piece is a unique hash for the user, per challenge, so that they couldn't directly share their flag. They can help others — even provide the solution — but they can't simply give away their flag.
Each challenge, when solved, is worth a certain number of points based on the challenge's difficulty and whether or not the player used the challenge's hints.
There were 3800 points available, though no player was able to break 1000!
At the end, we locked the leaderboard and announced the winners.
Prizes
We awarded the top four players based on their ranking on the leaderboard. First place got first dibs from the list. Second place gets to select theirs from the remaining lot, and so on.
Up for grabs this year:
Hak5 Elite Field Kit
Proxmark3 RDV2 Kit
Samsung Chromebook Plus
Lockpick set and a "how to" manual
Challenge snapshot
Throughout the eight categories we had a total of 46 challenges. We wanted to have a wide range of challenges that welcomed players of all backgrounds and experience levels.
The goal for XSS challenges was to get an alert dialog to appear. The player is presented with a vulnerable web page and they needed to determine where the vulnerability is and how to exploit it. Example:
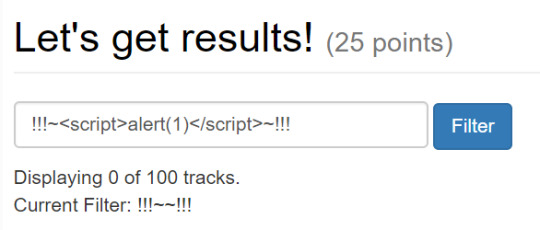
These challenge levels ranged everywhere between simple non-sanitized output to DOM reflection to CSP bypasses.
One fo the more unique challenges to develop was SQL Injection. These offered players the ability to put their SQL skills to the test with a variety of basic input injection, blind injection, and filter bypassing challenges.
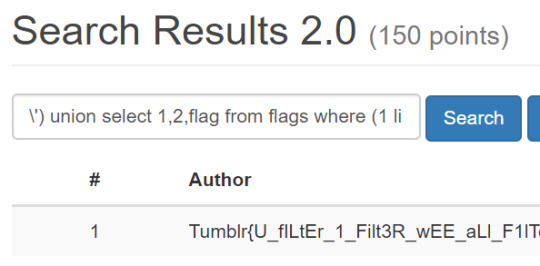
In at least one of the SQLi challenges, players had to inject into an INSERT statement. When creating challenges like this, special care had to be taken to give players the full capabilities of MySQL but also prevent them from revealing the flag to other players — it's a tricky thing making vulnerabilities secure!
The infrastructure
A frequent question I receive when I talk about deving on the CTF is "are you using CTFd?" Short answer? Nope! A slightly less short answer is that CTFd wasn't out when we started this =P.
The framework we're using is called "Security Training Grounds" and it's a custom-written project using PHP, PhantomJS, and MySQL (with HTML + JavaScript too, of course), running in Amazon Web Services.
An advantage of writing this in-house was that it gave us the ability to create a dynamic and robust system that has endless capabilities.
PHP + MySQL
The website was created from scratch, written in PHP with a little bit of jQuery + Bootstrap on the frontend and MySQL as the database.
The big thing here are the challenges themselves. Each challenge is hosted on its own subdomain. This enables us to provide live and interactive challenges like XSS or SQLi while still providing support static challenge types like Crypto or Reverse Engineering.
We accomplished this by allowing dynamic hostnames on the webserver and defining a subdomain hostname for each challenge that's stored in MySQL. When a web request comes in, the app checks whether it's a subdomain or not. If so, it hits the database to determine what to display.
For most challenges, we were able to handle all of the dynamic pieces directly in PHP. For some, such as the C or Java reverse engineering challenges, we did need to shell out to gcc or javac to build the custom binaries for each user.
PhantomJS
A difficulty for XSS and CSRF challenges is determining whether or not the participant successfully exploited the system. Surely we don't want to manually confirm for each flag, and attempting to pattern-match on their input would be crazy.
Our solution: execute what the player submits!
This is my own little baby, a piece of the system I'm so excited by. See, what better way to test XSS than to actually test XSS. As mentioned in the "Challenge snapshot" section above, when a player is working on a XSS challenge, they are given a website that has a XSS vulnerability. Their goal is to make an alert dialog appear. This is key and the requirement of the XSS framework itself.
On the client, we use this fancy little snippet:
var ctf_alert = alert; alert = function(msg) { ctf_phantomjs_alert_test(document.location, msg); };
This overrides the window's actual alert() function and lets us put some processing logic in the middle. The logic is to take a snapshot of the current page - the URL, query string, POST parameters, the cookies and then pass the full snapshot to a backend PhantomJS service (via a PHP proxy, to help prevent tampering).
The PhantomJS service replicates that entire request and loads the target web page. If the page invokes an alert() call, which we catch via PhantomJS's onAlert, then we return with a "success" and the PHP proxy will return the user's flag. Our alert() overriding logic will then replace whatever message the user attempted to display and display their flag instead. Fancy af.
CSRF has a similar setup, except the player needs to submit their full CSRF payload:
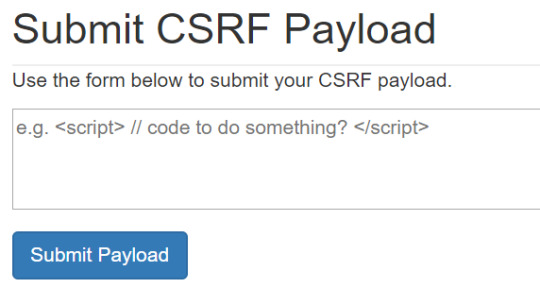
After submitting the payload to the PHP proxy, we pass the payload to PhantomJS. This executes the payload in the context of an empty web page. If the PhantomJS worker successfully falls victim to the targeted action, the PHP proxy will return a flag to the user!
Open source
The framework code, as-is, is still relatively hacky and written with internal dependencies. We do believe in OSS though! We expect a near-future initiative to rewrite portions of it so we can release it for others to use for their CTF events, too.
Wanna Play?
Quick, come apply so you can participate in the next one: https://www.tumblr.com/jobs
#tumblr#tumblrhq#security#capture the flag#ctf#xss#csrf#sqli#hacking#tumblr event#tumblr staff#computer security#cybersecurity#cyber#programming#computers#tacos
115 notes
·
View notes
Text
API - Application Programming Interface
Using a set of definitions and protocols, APIs are techniques that let two software components communicate with one another. For instance, the software system of the weather bureau contains daily weather information. Your phone's weather app "talks" to this system via APIs to provide you with daily weather updates.
Application Programming Interface is referred to as API. Any software with a specific function is referred to as an application when discussing APIs. Interface can be compared to a service agreement between two programs. This agreement specifies the requests and responses that the two parties will use to communicate. Developers can find instructions in their API documentation on how to format those requests and responses.
Client and server architecture is typically defined in terms of APIs. Applications that transmit requests and responses are referred to as clients and servers, respectively. In the weather example, the mobile app is the client and the bureau's weather database is the server.
Depending on when and why they were built, APIs can operate in one of four different ways.
1. SOAP APIs
Simple Object Access Protocol is used by these APIs. XML is used by client and server to exchange messages. In the past, this more rigid API was more widely used.
2. RPC APIs
Remote Procedure Calls are the name given to these APIs. A function (or operation) on the server is finished by the client, and the server then transmits the output back to the client.
3. WebSocket APIs
Another contemporary web API that uses JSON objects to convey data is the WebSocket API. Client apps and the server can communicate in both directions using a WebSocket API. The server can communicate with connected clients via call-back messages, making it more effective than REST API.
4. REST APIs
These are the most widely used and adaptable APIs available right now online. Requests are sent to the server as data by the client. The server launches internal processes using this client input and sends the results back to the client.
Representational State Transfer is referred to as REST. For clients to access server data, REST defines a set of functions including GET, PUT, DELETE, etc. Using HTTP, clients and servers exchange data. The statelessness of REST APIs is a key characteristic. Servers that are stateless do not save client information between requests. Similar to the URLs you type into your browser to view a website, client requests to the server. The server's response is just basic data without the customary graphical web page display.
Web API
An application processing interface (Web API or Web Service API) connects a web server and a web browser. While all APIs are web services, not all web services are APIs. A specific kind of Web API that adheres to the accepted architectural design is the REST API.
Because APIs were traditionally developed before to the development of the World Wide Web, many terminologies relating to APIs, such as Java API or service APIs, exist. REST APIs are the current generation of web APIs, and the two words are interchangeable.
API integrations
Software elements known as API integrations are used to automatically update data between clients and servers. Examples of API connections include automatic data syncing from your phone's photo gallery to the cloud or automatic time and date syncing on your laptop when you go to a different time zone. They can be effectively used by businesses to automate a variety of system operations.
Benefits of REST APIs
1. Integration
New apps are integrated with current software systems through APIs. Because each functionality doesn't need to be created from scratch, development time is sped up. APIs can be used to benefit from pre-existing code.
2. Innovation
With the introduction of a new app, entire industries can shift. Businesses must act swiftly and facilitate the quick rollout of innovative services. Without having to completely rewrite the code, they can accomplish this by adjusting at the API level.
3. Expansion
Businesses have a special opportunity thanks to APIs to satisfy the needs of their customers on several platforms. For instance, the maps API enables the integration of map data into websites, Android, iOS, etc. By employing either free or paid APIs, any company can grant similar access to its internal databases.
4. Ease of maintenance
A gateway between two systems is created via the API. Each system is required to implement internal adjustments to ensure that the API is not harmed. In this manner, any upcoming code modifications by one party won't affect the other side.
0 notes
Text
AngularJS Web Application Development Case Studies - Arya College
AngularJS was created, as a side project, in 2009 by two developers, Misko Hevery and Adam Abrons. Hevery started working on a project at Google called Google Feedback. Hevery and some other Developers wrote 17,000 lines of code in 6 months for Google Feedback. But the code size has been increased, and they again tried and had a bet to complete it in two weeks, it took three weeks to rewrite the project but finally, he won the bet to cut the application from 17000 lines to 1500 lines.
What is Angular JS?
There are no functions that we can directly call and use.
It is not a library like jQuery, But it is called jqLite.
Work on HTML web apps.
For MVC/MVVM design pattern
ANGULARJS is built around the philosophy that declarative code is better than imperative code while building UIs and wiring different components of a web application together.
Why Angular JS
1. Numerous ways to organize web applications at the client end
2. Enhance HTML by attaching directives, custom tags, attributes, Expressions, and templates within HTML
3. Encourage TDD
4. Encourage MVC/MVVM
5. Code Reuse
6. Good for SPA
Benefits of Angular JS
1. Structure, Quality, and Organization
2. Lightweight
3. Free
4. Separation of concern
5. Modularity
6. Extensible & Maintainable
7. Reusable Components
What Browsers Does AngularJS Support?
Angularsupportst Class A Browsers. As of Angular 1.2. some of the Browsers are:-
1. Chrome
2. firefoxfox
3. Safari
4. iOS
5. Android
6. IE8+
Core Features:-
Data Bind:- It is the Sync Between the Modal and component.
Scope:- Binding Between controller and view
Controller:- This is the Java Script Function.
Services:- They give service on the app
Templates: This can be a single fine with multiple views.
Deep Linking:- This Encode the application in the URL
Key Features of ANGULARJS
1. Declarative HTML approach
2. Easy Data Binding
3. Reuse Component
4. Design Pattern
5. Dependency Injection
6. Testing or Unit Testing
7. Routing
8. Template
9. Module
10. Services
11. Expressions
12. Filters
13. Directive
14. Forms Validating
HTML compiler:-
Angular's HTML compiler allows the developer to teach the browser new HTML syntax. Angular calls these behavior extension directives.
The compiler is an angular service that traverses the DOM looking for attributes.
Directive:-
The directives are to be placed in names, attributes, class names, as well as comments. A directive is just a function that executes when the compiler encounters it in the DOM.
There are some types of:-
ng-app, ng-model, ng-bind.
Expression:-
Expressions are JavaScript code that is usually placed in bindings such as
{{ expression }}
<body>
1+2={{1+2}}
</body>
Forms:-
Forms and controls provide validation services so that the user can be notified of invalid input. This gives a better user experience so the user gets good feedback corrections.
Modules:-
Modules declaratively specify how an application should be bootstrapped. There are multiple modules an that are interdependent too
Routing:-
It Is used for deep-linking URLs to controllers and views (HTML partials). It watches location. URL to map the path to an existing route definition.
Scope:-
A scope is an object that refers to the application model.
Scopes are arranged in a hierarchical structure that mimics the DOM structure of the application. Scopes can watch expressions and propagate events.
The ViewModel of MVVM.
Dependency Injection:-
Dependency Injection (DI) is a software that deals with how code gets hold of its dependencies.
Filters:-
Angular filters format data for display to the user.
Resources:-
Documentation
AngularJS Developer Guide
AngularJS API
AngularJS Tutorial Videos
AngularJS Fundamentals In 60-ish Minutes
Introduction to Angular JS
AngularJS end-to-end web app tutorial Part
Advantages of AngularJS:-
It provides the Single page app with a maintained way
It can bind the HTML and gives the best experience to the user.
It is testable
It is a reusable component
It does more Functionally with shortcode
It is a pure HTML page and has JavaScript to do business processing.
Disadvantages Of AngularJS
It is not Secure and not safe, there is no authentication and authorization to make it secure.
If a user Disable the java scrip then nothing would be visible except the basic page.
Conclusion:-
Arya college is the best Engineering College in Jaipur and Rajasthan that Gives you the best courses and results in terms of placements and scores and knowledge. So some conclusions are here below:-
AngularJS is an efficient framework that can create Rich Internet Applications (RIA). AngularJS provides developers an option to write client-side applications using JavaScript in a clean Model View Controller (MVC) way.
0 notes
Text
Responsive Web Design Services
UX has been the point of interest of recent net development for fairly some time now. This is influenced by several factors, including page loading velocity, readability, usability, and design. But now that extra customers prefer mobile web looking over using desktops, any website-be it a niche blog or an e-commerce retailer should start prioritizing mobile friendliness.
Nowadays, it’s easy to apply a cell-responsive theme and use tools like Google’s Mobile-Pleasant Test to receive extra suggestions on find out how to optimize your site. However if you wish to take issues to the next stage, you can develop a Progressive Internet App (PWA) to ship recent and memorable new experiences to your cellular users.
What’s a Progressive Net App? A PWA leverages trendy net technologies to enable app-like features. Not like conventional mobile web sites, a PWA doesn’t must refresh your complete page when loading new content material-nor does it need internet connectivity to be accessible. They’re additionally installable, meaning users can simply reuse them by adding a home display shortcut.
Progressive web purposes have the potential to be the next massive factor for the mobile web. This was initially proposed by Google just a couple of years back in 2015. However, within such a short while, it has already attracted numerous attention as a result of it’s relatively straightforward to develop and for the appliance’s person experience delivery. Rahul Varshneya, cofounder of app development company Arkenea.
A PWA is an enormous undertaking that may lead the direction of your mobile internet presence within the future. But if you happen to’re completely new to PWAs, here are 7 tools and resources that may put you heading in the right direction:
PWA.rocks With regards to creating a PWA, it's essential have a deeper understanding on what they are succesful of.
To see PWAs in action, you'll be able to confer with PWA.rocks for examples underneath a number of categories, including enterprise, games, procuring, and social. This can enable you to visualize what your future PWA could look like. It's also possible to borrow inspiration from the obtainable examples when conceptualizing what your PWA will offer cell users.
Knockout Knockout is a free, open supply device that may enable you to with Model-View-View Mannequin or MVVM bindings. This allows you to simplify the method of coding JavaScript UIs by letting you define views and declarative bindings that are controlled by viewmodel properties.
The platform runs purely on JavaScript, which works with all main browsers and any web framework. The Knockout library can also easily be built-in with present web sites without extensive rewrites.
PWABuilder The fastest strategy to create a PWA is to make use of PWABuilder and shortly construct a service employee for offline functionality, which works by pulling and serving the “offline.html” out of your internet server whenever customers lose web connectivity. It's also possible to submit your PWA to the app retailer for Android and iOS devices.
To use PWABuilder, all you'll want to do is insert your web site’s URL and then fill in the further details like your name, website description, and preferred icon. You too can easily modify certain properties resembling your PWA’s screen orientation, language, and background color. The platform will then routinely generate a manifest primarily based on the data you provide.
AngularJS JavaScript is often the introductory language realized by college students who wish to be taught web development. When you’re an skilled Java or .NET developer, then AngularJS is likely one of the greatest JavaScript frameworks you need to use for web applications. Even so, their website gives a ton of guides, tutorials, and resources that may show you how to be taught your way across the platform.
The newest version, Angular v4.zero, gives the same surroundings whether or not you’re creating for cell or desktop. In case you assume Angular is just too complex for your wants, you might choose as a substitute for React-a JavaScript library tailored to UI development. Another various is Polymer, which might give you templates and different reusable parts that can velocity up the method of PWA development.
Google Developers A PWA just isn't precisely a DIY project for self-made bloggers or affiliate marketers, but it might probably still be done with the right resources. If you have already got experience with Website Design Services content management programs however are clueless about developing internet purposes, then you may get the fundamentals down via Google Developers, a library of assets that can assist you discover ways to code.
Google Developers have a complete tutorial on how PWAs work, easy methods to construct one, and how you can make it run correctly. It additionally covers different basics such as enabling the “add to home screen banner” and using HTTPS.
Webpack Webpack is an especially useful tool for bundling your JavaScript app assets, including non-code belongings like fonts and images. These shall be treated as JavaScript objects, which in flip allows them to be loaded faster. The platform additionally makes it considerably simpler to handle dependencies.
Simply keep in mind that Webpack has a steep learning curve, that means you could possibly be looking at hours of searching for tutorials and guides. Nonetheless, the educational sources and documentation out there on their web site aren’t beginner-friendly. The good news is, Webpack is widely lined in different websites, together with Angular 4.0’s documentation section.
youtube
GitHub Lastly, GitHub is a neighborhood-pushed website that maintains repositories of projects. It covers a broad vary of programming-associated topics, including JavaScript and PWA service workers. The truth is, you can find the PWA.rocks and Webpack repositories within the platform. This will provide help to deepen your understanding and even contribute to additional development.
At this time, there’s a handful of repositories involving PWAs on GitHub. You'll be able to study from these projects or start your personal repository as you experiment with your first PWA. GitHub now additionally has venture management options, allowing you to seamlessly collaborate with other builders remotely.
Conclusion Progressive Web Apps are the future of mobile web experiences, however not lots of brands at the moment use them. With the instruments above, you’re now fully able to making a standout PWA and establishing an authoritative presence. Just take notice that PWA instruments, sources, and practices evolve with the constantly evolving applied sciences of major online browsers.
1 note
·
View note
Text
Advance Java Courses in Pune

Advance courses help in gaining some extra skill sets and discover new things in any particular domain. NIIT helps students in developing such skills and making them industrial ready. NIIT offers some of thebest Advance Java courses in Pune. Some of which are mentioned below.
Advanced Java Course in Pune
Java, a standout amongst the most prevalent programming being used, especially for customer server web applications, with an announced 9 million engineers. Propelled Java modules are the most utilized instruments to advertising today. They are generally utilized as a part of the industry and consequently, information of these modules enable the possibility to discover steady employment in the showcase. Propelled Java modules are exceptionally looked for after ability as these aptitudes are difficult to discover among general applicants.
Advanced Java Course Covers
HTML, CSS & Javascript Overview
HTML Basics Information
HTML Elements
CSS Introduction
CSS Syntax & Selectors
JavaScript Overview
Bootstrap Overview
Java MVC Architecture
Three-tier architecture
Introduction to MVC
MVC Architecture
Advantages of MVC
Building pages with MVC
Servlets
What is a web application?
What is a Servlet?
Advantages of Servlet
Servlet Class
Servlet Lifecycle
Servlet Context Interface
Advantages of Servlet Context
Session management
Session Tracking Techniques ◦Cookies
Hidden field
URL Rewriting
HTTPSession
Building the first Servlet
Deploying the Servlet
Servlet examples
JSP
Introduction of JSP
JSP Architecture
JSP Processing
JSP Tag library
Core Tags
JSP Standard Tags
JSP Page Life Cycle
Creating the first Dynamic web page using JSP
Hibernate
Introduction to Hibernate
Hibernate v/s JDBC
what is Object Relational Mapping
Hibernate Features
Application Architecture
Persistent Classes
Object States ◦Transient State
Persistent State
Detached State
Rules of Persistent Classes
Mapping Collections
Hibernate Mapping File Elements
Types of Mapping ◦One-to-one
One-to-many mapping
Many – one mapping
Many – to – many mapping
Hibernate Query Language
Basic HQL Operations
Advantages of HQL
Caching and Transactions
Types Of Cache
Hibernate Transaction Management
Transaction Interface In Hibernate
Hibernate with Web Applications
Advanced Selenium course in Pune
Selenium robotizes programs. Principally, it is for mechanizing web applications for testing purposes, yet is surely not constrained to only that. Online organization assignments can likewise be robotized. Selenium has the help of a portion of the biggest merchants who have found a way to make Selenium a local piece of their program. It is additionally the centre innovation in endless other program mechanization instruments, APIs and structures.
Selenium has turned out to be exceptionally prevalent as an Automation device in the IT business as it is a freeware and extremely convenient. Its prominence has developed monstrously in the most recent couple of years. This course additionally acquaints understudies with Cucumber – a conduct was driven improvement instrument that is quickly increasing colossal notoriety among the testing network. We prescribe this course to everybody in the product testing vertical.
Selenium Course Covers
Introduction
Overview of Selenium
Advantages of Selenium
The Selenium Suite
Inroduction to Selenium IDE
Selenium Remote Control
Selenium Grid
Architecture of Selenium Grid
the Hub & the Nodes
Basics of Web Driver
Setting up the environment
Configure Fire Bug & Fire Path
Advanced Selenium Web-driver
TestNG
Automation Framework
Advanced Automation Framework
Core Java Overview
Why Java for Selenium
First Java program
Datatypes in Java
Variables & Constants
Control-flow statements
Operators
Arrays
Loops
Classes and Objects
Class Constructors
Class program in Java
Inheritance & Polymorphic
Introduction to Interface
Collection hierarchy
Selenium IDE
Introduction to Selenium IDE
Features of Selenium IDE
Installing Selenium IDE
IDE Options
Building test cases
Running Test Cases
IDE Script Debugging
Writing a Test Suite
Using Locators in Selenium
Verification points in IDE
Working with regular expressions
User extensions
Execute scripts across browsers
Selenium Web Driver
Introduction
How Selenium Web Driver Works
Configuring Selenium Web Driver With Eclipse
Selenium RC vs Web Driver
Set Up Web Driver Client
Programming your tests in Web Driver
Debugging Web Driver test cases
Troubleshooting
Testing HTTPS and Security Pop-ups
Running Test on GeckoDriver
Executing and Debugging tests in browsers ◦IE
Chrome
Firefox
Desired Capabilities in Selenium WebDriver
Session Handling
Handle Alerts and Multiple Windows using WebDriver
Uploading & Downloading using WebDriver
Accessing Forms & GUI Objects
Text box interaction
Radio button interaction
Handling Check boxes with Web Driver API
Handling static drop downs
Handling dynamic drop downs
Drag & Drop
Keyboard Interaction
Mouse Interaction
Multi select
Selenese Commands
Actions
Accessors
Assertions
Using Locators in Selenium ◦Locating by ID
Locating by Name & using filters
Locating by Link Text
Locating by CSS Selector
Locating by DOM
Synchronization in WebDriver
What is an implicit wait?
What is an explicit wait?
AJAX Calls in Selenium ◦ What is AJAX
Handling AJAX Calls
Challenges
Accessing Web Tables
what is a Web Table?
Static Tables
Dynamic Tables
Locating Web Table elements
Fetching number of rows and columns
Fetching cell value
TestNG Framework
Introduction
TestNG Features
Install and set up TestNG environment
First Test Case with TestNG
TestNG annotations
Junit vs TestNG
TestNG Test Suite
Annotations, Groups & DependOn
TestNG – Ignore Test
Group Test in TestNG ◦Metagroups
Exclusion Groups
Exception Test
Dependency Test
TestNG Parameters & Data Provider
TestNG Reporters & Asserts
Test Cases Prioritizing & Sequencing
TestNG DataProvider with Excel
Multi Browser & Parallel Testing
Test Design Techniques
Page Object Model ◦Why POM?
What is POM?
POM Benefits
Parameterizing using Excel
Log4j Logging
Exception Handling
Capture Screenshots
Cookie Handling in Selenium
Why handle cookies
Retrieving, adding and deleting cookies
Storing a cookie
Using stored cookie
Debugging
what are Breakpoints
Implementation of Breakpoints
what is a Start point
Implementation of Startpoints
Xpath Functions
Contains
Sibling
Ancestor
Selenium Frameworks
Data-Driven Test Framework
Keyword Driven Test Framework
Hybrid Test Framework
These advanced courses provide you with some extra knowledge of different things around which can guarantee you a great success. These advanced courses cover many important things and help in developing extra skills. NIIT provides the best Java training and advanced Java training courses in Punewith the help of trained staff and professionals.
Visit us at : NIIT Pune
6 notes
·
View notes
Link
In this article we’ve collected the most commonly asked Java Interview Questions for freshers and job seekers in Java. These questions will familiarize you with the types of questions an interviewer will ask you during your Java Programming interview. As a Fresher, you have either attended or will soon attend an interview. You may be worried about the upcoming interviews as an Entry Level job seeker trying to advance your career in software programming. If you want to start a career in Java web app development, you’ve come to the right place! We’ve put together a rundown of the most often requested Java interview questions to help you pass your Java career interview.
Java Interview Questions
Let us have a look at the major Java interview questions.

Question 1: What is Java?
Java is a general-purpose ,object-oriented and a high-level programming language.
Question 2: What is Java Virtual Machine?
JVM is a program that helps to interpret the intermediate Java byte code and generates the desired output.
Question 3: Explain the feature of Java platform independent?
Java JVM can covert the source code into corresponding byte codes these byte codes can be run on any OS independent of the platform.
Question 4: What is mean by singleton class in Java ?
The singleton class is the that can be create only one instance at any time in one JVM.
Question 5: What are access modifiers in Java?
Access modifiers in Java specifies the scope and visibility of Java variable.
The four Java access modifiers are
1. Default
2. Private
3. Protected
4. Public
Question 6: Why Java Strings are immutable in nature?
Java Strings are immutable which meaning that the value of Java string variable can’t be modified or unchanged. We can change the values only by specifying it by using a StringBuffer or StringBuilder.
Question 7: What is Request Dispatcher?
The Request Dispatcher is used to sending the request to another resource of the type html, servlet or jsp.
The methods of Request Dispatcher are
1.void forward()
2.void include()
Question 8: What is the life-cycle of a servlet?
1. Servlet is loaded
2. Servlet is instantiated
3. Servlet is initialized
4. Service the request
5. Servlet is destroyed
Question 9: Explain different methods of session management in servlets?
Common session management methods are
1. User Authentication
2. HTML Hidden Field
3. Cookies
4. URL Rewriting
5. Session Management API
Question 10: How to integrate Spring and Hibernate Frameworks?
Hibernate and Spring are Java frameworks they are integrated with help of DAOpattern and its dependency injection.
Question 11: Is it possible to restrict Inheritance in Java?
Yes, inheritance in Java can be restricted by using the following methods
1. By using the final keyword. 2. By making the methods as final. 3. By using private constructor in a class. 4. By using (//) Javadoc comment in a Java program
Question 13: What is the function of a constructor in a Java class?
Java class constructors are used to initialize the state of any object only after creating an object using the new keyword.
Question 14:What is the use of looping?
Loops in Java help the programmer to execute a part of program repeatedly in several times. Java have for , while and do-while as looping statements.
Question 15:How to perform Java Database Connectivity in a Java program?
The five major steps to achieve JDBC(Java Database Connectivity) are
1. Register the driver class
2. Create the connection
3. Create the statement
4. Execute the queries
5. Close the connection
Question 16:What Is the concept of Multi-Threading in Java?
Multi-threading is the process of executing multiple task simultaneously. In Java Multi-threading is achieved by using extending from Thread class or implementing from Runnable interface.
Question 17: What are Packages in Java?
Java packages are collection of classes and interfaces.
Question 18: What is the function of main method in Java?
Main() method is the entry point of all Java programs . The syntax of main is given below
public static void main(String args[])
{
}
Question 19: What is static keyword in Java?
static keyword in Java used to share the value between the objects and it is global in nature.
Question 20: What is the use of instanceof keyword in Java?
instanceof keyword is used to check whether the specified object is an instance of the particular class or not.
It is very important to take a training for Java to get a confidence to attend all interviews. Grooming for an interview would be equipped well when guided by professionals. So to learn more about Java it is always better to get in touch with the best Java training in Kochi or any other cities. There are various Java training institutes are readily available to assist you. The key point is finding the optimal Java online training in Kochi so that you can learn, grow and be experts in your field.
0 notes
Text
SDLC, Requirements and UX
What goes into requirements at what level of detail and accountability?
Financial Rebalancing example: High level ask: Given a investment account generate a set of trades to bring it inline with a model and allow execution of those trades after review.
Basic Requirements including UX (graphics are described): Allow user to select a model and an account, provide a set of trades for review, allow them to select which they want to execute, after submission provide back results.
Biz also describes a list of 20 something validations each with specific error copy. Some of these only apply to the API that generates the trades, others apply only to trade submission (mostly security related), and the rest apply to both. They have a specific priority that if multiple occur, which to display to the user...
This brings me to the issue which we have several implementation choices, one question is who should be deciding between them: 1. We could implement each check as an isolated function that take the model and accounts ids, gather data and validate. This means however each function is repeatedly hitting the database which potentially impacts performance. 2. We could implement as 2 distinct APIs that do not share code. This means that there is code duplication and when a check needs to be changed, we need to change it in 2 places. 3. We can implement a mix, each API and each function take various amount of data probably gathered slightly different but no data is gathered twice and no check is duplicated. IMO this sounds like the best approach, however it's also the most time consuming to define up front.
The next question is accountability of making that choice, and impact of it's cost in the future to rewrite and impact analysis? If the decision is made in the code an only documented within the code's documentation (java doc format) impact analysis could only be done by technical. Should not technical be doing impact analysis, for a given change a set of test cases need to be created. Assuming that automated testing doesn't have 100% coverage and manual regression testing is done, it means that the impact analysis must be done prior to development if test cases are being done prior to development.
What level of detail needs to go into requirements, is UX requirements or something else? For example lets say we have a Salesforce integration. One our sidebar we have a button that when pressed opens salesforce using SSO in a new window if the user is already linked or launches the authentication oauth flow for salesforce.
The reqs as: Have "Salesforce" in sidebar if user is entitled. If user is not linked launches Salesforce Authentication flow in new tab, otherwise launches salesforce using SSO
or they could be as complicated (simplified version still skipping some UX) as: Salesforce in Sidebar: - Displays only if user is entitled to View Salesforce - When clicked gathers Salesforce URL using Salesforce SSO API - on success, success opens that URL in a new tab - on failure, gathers salesforce oauth url using Salesforce Login API, then opens a popup window using that url that is 500px by 540px centered on current window which when resolved will redirect the user to the Salesforce SSO Callback API
Sorry I think this dissolved into more of a rant without a purpose but at my current company we're struggling to figure it out.
Without the more detailed requirements when something is changed, impact analysis is left up to the developers which is usually within their development process, the impact of changing A and breaking unrelated feature B except that they both pull data using a shared query is where the problem lies mostly i think. Additional testing would need to be added to retest B before A could be released.
It's a small company, less then 11 people involved in the entire process, outside of that anyone in the process would really be considered "clients" as far as the development process is concerned.
submitted by /u/jegsar [link] [comments] from Software Development - methodologies, techniques, and tools. Covering Agile, RUP, Waterfall + more! https://ift.tt/3dHi2AT via IFTTT
0 notes
Text
Search Enginge Optimization Tips That Increase Website Traffic
If you don’t choose to utilize Search Engine Marketing tactics, then it is unlikely that you will attract visitors to your site. Make sure your site gets found by following the tips in this article.
If you are using Lynchburg Search Engine Optimization, take the time to ensure that the code on your site is well written. Poorly coded java can make it difficult for spiders to index your pages. A Flash content loaded site that lacks descriptive text will can’t indexed by search engine spiders.
When trying to enhance your site’s search engine optimization, be patient. An abundance of traffic and major changes do not happen overnight. If the creation date of your site is not very long ago, it may take a few months to build your SEO Consultants. You need to build a reputation, it will take time.
Anchor Text
Anchor text is essential when you put links on your webpage. A common example of poor anchor text is “click here”. This anchor text contributes nothing to your search rank. It is vital you use the correct keywords, since anchor text allows crawling spiders to notice you.
Use good, descriptive text for your site’s title tag so search engines can figure out the relevance of your site’s content, and display your site in lots of search results. Search engines only display 60 characters, so keep it short. They will also give less importance to terms at that point.
Consider using an article exchange service rather exchanging links. Article exchange involves posting a full article done by the owner of another site, giving them a link and getting the same in return. Each site will have new content, making it more helpful than link exchanges.
Start your SEO rewrite by looking at your description tag. This tag should be relevant to your customers’ needs so that they’ll find you when they search for the tag. An efficient description tag should not exceed 30 words in length. Don’t put more than 100KB of content on your description page if you can avoid it.
Site Map
Design an easy to use site map that also includes your target keywords. A site map is a navigational tool on your website that gives links to all the different pages so that viewers can easily find the specific page they’re looking for. Search engines use the inclusion of a site map in their consideration of where your site should be ranked.
You may use JavaScript on the pages, but certain search engine bots don’t react well to it. Using Java is totally up to the website owner as a choice, but remember that some search engines will see your website differently due to the different capabilities found in the respective crawlers.
Websites that are properly optimized for search engine results rarely employ image links. The only purpose an image link serves is to store the URL of a linked file. This is not as beneficial when search engines index them.
Increasing your ranking on search engines will allow your regular customers to access your site. There are a lot of web-based business that do not know this.
If you want to focus on search engine optimization, you need a social media strategy. Twitter and Facebook are completely interactive, and the video sharing site YouTube is an effective way to showcase your product.
Search Engine Optimization requires a lot of patience. Sometimes it will seem like all your efforts are being done in vain. With millions of websites already online, it will take time for yours to fight its way to the front. It is imperative that you stay with the process for a sufficient amount of time, and don’t abandon it when it looks like nothing is changing with your site. Using common keywords and linking to other sites can also make your site more visible.
If you hire a search engine optimization company to improve your site, be sure to ask the important questions before you agree to anything. Things you wish to consider include their pricing, experience, recommended techniques and estimated time for visible results. You should ask to see examples of previous work, and if possible speak to their current or former clients. Companies that stand by their work will more than happily comply.
Use every venue available, from article directories to social networks, to drive traffic to your site with inbound links. A great way to succeed at search engine optimization is to gather the best outward links possible.
Phrases are an important part of Lynchburg Search Engine Optimization. Do you typically search with one word only? You need to attract traffic to your site that is actually looking for what your site has to offer. Include information that helps to put a location in the text, such as “Check out the sale at our Toronto location! ” rather than “We are going to have a sale! ”
When building a successful site, try to focus a single page on a single keyword. Using too many keywords on one page tends to cause people to misunderstand the purpose of the webpage. Worrying about just one topic tends to cause you to produce better content, which will cause your readers to continue coming back because they will be satisfied with what they are finding. Having a loyal handful of readers tends to raise your website rankings and increase search engine optimization.
No business expects to fail. Even though many online businesses fail, there are actually many more ways to find success on the Internet.
It can be difficult to learn the knowledge you need to know about When it comes to search engine marketing, you really should not gamble on your organization’s Google ranking to someone who is not a Lynchburg SEO Expert. If you are reading this, you most likely are searching for someone who can aid you develop your company’s online visibility, website traffic, and leads.

, especially if you don’t know how to begin. Learning about the key points on When it comes to search engine marketing, you really should not gamble on your organization’s Google ranking to someone who is not a Lynchburg SEO Expert. If you are reading this, you most likely are searching for someone who can aid you develop your company’s online visibility, website traffic, and leads. is a great start. Applying everything you learn from this article is proven to be a great way to get started on the road to success.
source https://lynchburgseoexpert.com/search-enginge-optimization-tips-that-increase-website-traffic/ from Lynchburg SEO Expert https://lynchburgseoexpert.blogspot.com/2020/04/search-enginge-optimization-tips-that.html
0 notes
Text
Search Enginge Optimization Tips That Increase Website Traffic
If you don’t choose to utilize Search Engine Marketing tactics, then it is unlikely that you will attract visitors to your site. Make sure your site gets found by following the tips in this article.
If you are using Lynchburg Search Engine Optimization, take the time to ensure that the code on your site is well written. Poorly coded java can make it difficult for spiders to index your pages. A Flash content loaded site that lacks descriptive text will can’t indexed by search engine spiders.
When trying to enhance your site’s search engine optimization, be patient. An abundance of traffic and major changes do not happen overnight. If the creation date of your site is not very long ago, it may take a few months to build your SEO Consultants. You need to build a reputation, it will take time.
Anchor Text
Anchor text is essential when you put links on your webpage. A common example of poor anchor text is “click here”. This anchor text contributes nothing to your search rank. It is vital you use the correct keywords, since anchor text allows crawling spiders to notice you.
Use good, descriptive text for your site’s title tag so search engines can figure out the relevance of your site’s content, and display your site in lots of search results. Search engines only display 60 characters, so keep it short. They will also give less importance to terms at that point.
Consider using an article exchange service rather exchanging links. Article exchange involves posting a full article done by the owner of another site, giving them a link and getting the same in return. Each site will have new content, making it more helpful than link exchanges.
Start your SEO rewrite by looking at your description tag. This tag should be relevant to your customers’ needs so that they’ll find you when they search for the tag. An efficient description tag should not exceed 30 words in length. Don’t put more than 100KB of content on your description page if you can avoid it.
Site Map
Design an easy to use site map that also includes your target keywords. A site map is a navigational tool on your website that gives links to all the different pages so that viewers can easily find the specific page they’re looking for. Search engines use the inclusion of a site map in their consideration of where your site should be ranked.
You may use JavaScript on the pages, but certain search engine bots don’t react well to it. Using Java is totally up to the website owner as a choice, but remember that some search engines will see your website differently due to the different capabilities found in the respective crawlers.
Websites that are properly optimized for search engine results rarely employ image links. The only purpose an image link serves is to store the URL of a linked file. This is not as beneficial when search engines index them.
Increasing your ranking on search engines will allow your regular customers to access your site. There are a lot of web-based business that do not know this.
If you want to focus on search engine optimization, you need a social media strategy. Twitter and Facebook are completely interactive, and the video sharing site YouTube is an effective way to showcase your product.
Search Engine Optimization requires a lot of patience. Sometimes it will seem like all your efforts are being done in vain. With millions of websites already online, it will take time for yours to fight its way to the front. It is imperative that you stay with the process for a sufficient amount of time, and don’t abandon it when it looks like nothing is changing with your site. Using common keywords and linking to other sites can also make your site more visible.
If you hire a search engine optimization company to improve your site, be sure to ask the important questions before you agree to anything. Things you wish to consider include their pricing, experience, recommended techniques and estimated time for visible results. You should ask to see examples of previous work, and if possible speak to their current or former clients. Companies that stand by their work will more than happily comply.
Use every venue available, from article directories to social networks, to drive traffic to your site with inbound links. A great way to succeed at search engine optimization is to gather the best outward links possible.
Phrases are an important part of Lynchburg Search Engine Optimization. Do you typically search with one word only? You need to attract traffic to your site that is actually looking for what your site has to offer. Include information that helps to put a location in the text, such as “Check out the sale at our Toronto location! ” rather than “We are going to have a sale! ”
When building a successful site, try to focus a single page on a single keyword. Using too many keywords on one page tends to cause people to misunderstand the purpose of the webpage. Worrying about just one topic tends to cause you to produce better content, which will cause your readers to continue coming back because they will be satisfied with what they are finding. Having a loyal handful of readers tends to raise your website rankings and increase search engine optimization.
No business expects to fail. Even though many online businesses fail, there are actually many more ways to find success on the Internet.
It can be difficult to learn the knowledge you need to know about When it comes to search engine marketing, you really should not gamble on your organization’s Google ranking to someone who is not a Lynchburg SEO Expert. If you are reading this, you most likely are searching for someone who can aid you develop your company’s online visibility, website traffic, and leads.

, especially if you don’t know how to begin. Learning about the key points on When it comes to search engine marketing, you really should not gamble on your organization’s Google ranking to someone who is not a Lynchburg SEO Expert. If you are reading this, you most likely are searching for someone who can aid you develop your company’s online visibility, website traffic, and leads. is a great start. Applying everything you learn from this article is proven to be a great way to get started on the road to success.
from https://lynchburgseoexpert.com/search-enginge-optimization-tips-that-increase-website-traffic/
from Lynchburg SEO Expert - Blog https://lynchburgseoexpert.weebly.com/blog/search-enginge-optimization-tips-that-increase-website-traffic
0 notes
Text
Search Enginge Optimization Tips That Increase Website Traffic
If you don’t choose to utilize Search Engine Marketing tactics, then it is unlikely that you will attract visitors to your site. Make sure your site gets found by following the tips in this article.
If you are using Lynchburg Search Engine Optimization, take the time to ensure that the code on your site is well written. Poorly coded java can make it difficult for spiders to index your pages. A Flash content loaded site that lacks descriptive text will can’t indexed by search engine spiders.
When trying to enhance your site’s search engine optimization, be patient. An abundance of traffic and major changes do not happen overnight. If the creation date of your site is not very long ago, it may take a few months to build your SEO Consultants. You need to build a reputation, it will take time.
Anchor Text
Anchor text is essential when you put links on your webpage. A common example of poor anchor text is “click here”. This anchor text contributes nothing to your search rank. It is vital you use the correct keywords, since anchor text allows crawling spiders to notice you.
Use good, descriptive text for your site’s title tag so search engines can figure out the relevance of your site’s content, and display your site in lots of search results. Search engines only display 60 characters, so keep it short. They will also give less importance to terms at that point.
Consider using an article exchange service rather exchanging links. Article exchange involves posting a full article done by the owner of another site, giving them a link and getting the same in return. Each site will have new content, making it more helpful than link exchanges.
Start your SEO rewrite by looking at your description tag. This tag should be relevant to your customers’ needs so that they’ll find you when they search for the tag. An efficient description tag should not exceed 30 words in length. Don’t put more than 100KB of content on your description page if you can avoid it.
Site Map
Design an easy to use site map that also includes your target keywords. A site map is a navigational tool on your website that gives links to all the different pages so that viewers can easily find the specific page they’re looking for. Search engines use the inclusion of a site map in their consideration of where your site should be ranked.
You may use JavaScript on the pages, but certain search engine bots don’t react well to it. Using Java is totally up to the website owner as a choice, but remember that some search engines will see your website differently due to the different capabilities found in the respective crawlers.
Websites that are properly optimized for search engine results rarely employ image links. The only purpose an image link serves is to store the URL of a linked file. This is not as beneficial when search engines index them.
Increasing your ranking on search engines will allow your regular customers to access your site. There are a lot of web-based business that do not know this.
If you want to focus on search engine optimization, you need a social media strategy. Twitter and Facebook are completely interactive, and the video sharing site YouTube is an effective way to showcase your product.
Search Engine Optimization requires a lot of patience. Sometimes it will seem like all your efforts are being done in vain. With millions of websites already online, it will take time for yours to fight its way to the front. It is imperative that you stay with the process for a sufficient amount of time, and don’t abandon it when it looks like nothing is changing with your site. Using common keywords and linking to other sites can also make your site more visible.
If you hire a search engine optimization company to improve your site, be sure to ask the important questions before you agree to anything. Things you wish to consider include their pricing, experience, recommended techniques and estimated time for visible results. You should ask to see examples of previous work, and if possible speak to their current or former clients. Companies that stand by their work will more than happily comply.
Use every venue available, from article directories to social networks, to drive traffic to your site with inbound links. A great way to succeed at search engine optimization is to gather the best outward links possible.
Phrases are an important part of Lynchburg Search Engine Optimization. Do you typically search with one word only? You need to attract traffic to your site that is actually looking for what your site has to offer. Include information that helps to put a location in the text, such as “Check out the sale at our Toronto location! ” rather than “We are going to have a sale! ”
When building a successful site, try to focus a single page on a single keyword. Using too many keywords on one page tends to cause people to misunderstand the purpose of the webpage. Worrying about just one topic tends to cause you to produce better content, which will cause your readers to continue coming back because they will be satisfied with what they are finding. Having a loyal handful of readers tends to raise your website rankings and increase search engine optimization.
No business expects to fail. Even though many online businesses fail, there are actually many more ways to find success on the Internet.
It can be difficult to learn the knowledge you need to know about When it comes to search engine marketing, you really should not gamble on your organization’s Google ranking to someone who is not a Lynchburg SEO Expert. If you are reading this, you most likely are searching for someone who can aid you develop your company’s online visibility, website traffic, and leads.

, especially if you don’t know how to begin. Learning about the key points on When it comes to search engine marketing, you really should not gamble on your organization’s Google ranking to someone who is not a Lynchburg SEO Expert. If you are reading this, you most likely are searching for someone who can aid you develop your company’s online visibility, website traffic, and leads. is a great start. Applying everything you learn from this article is proven to be a great way to get started on the road to success.
from Lynchburg SEO Expert https://lynchburgseoexpert.com/search-enginge-optimization-tips-that-increase-website-traffic/ from Lynchburg SEO Expert https://lynchburgseoexpert.tumblr.com/post/615058685310468096
0 notes
Text
Search Enginge Optimization Tips That Increase Website Traffic
If you don’t choose to utilize Search Engine Marketing tactics, then it is unlikely that you will attract visitors to your site. Make sure your site gets found by following the tips in this article.
If you are using Lynchburg Search Engine Optimization, take the time to ensure that the code on your site is well written. Poorly coded java can make it difficult for spiders to index your pages. A Flash content loaded site that lacks descriptive text will can’t indexed by search engine spiders.
When trying to enhance your site’s search engine optimization, be patient. An abundance of traffic and major changes do not happen overnight. If the creation date of your site is not very long ago, it may take a few months to build your SEO Consultants. You need to build a reputation, it will take time.
Anchor Text
Anchor text is essential when you put links on your webpage. A common example of poor anchor text is “click here”. This anchor text contributes nothing to your search rank. It is vital you use the correct keywords, since anchor text allows crawling spiders to notice you.
Use good, descriptive text for your site’s title tag so search engines can figure out the relevance of your site’s content, and display your site in lots of search results. Search engines only display 60 characters, so keep it short. They will also give less importance to terms at that point.
Consider using an article exchange service rather exchanging links. Article exchange involves posting a full article done by the owner of another site, giving them a link and getting the same in return. Each site will have new content, making it more helpful than link exchanges.
Start your SEO rewrite by looking at your description tag. This tag should be relevant to your customers’ needs so that they’ll find you when they search for the tag. An efficient description tag should not exceed 30 words in length. Don’t put more than 100KB of content on your description page if you can avoid it.
Site Map
Design an easy to use site map that also includes your target keywords. A site map is a navigational tool on your website that gives links to all the different pages so that viewers can easily find the specific page they’re looking for. Search engines use the inclusion of a site map in their consideration of where your site should be ranked.
You may use JavaScript on the pages, but certain search engine bots don’t react well to it. Using Java is totally up to the website owner as a choice, but remember that some search engines will see your website differently due to the different capabilities found in the respective crawlers.
Websites that are properly optimized for search engine results rarely employ image links. The only purpose an image link serves is to store the URL of a linked file. This is not as beneficial when search engines index them.
Increasing your ranking on search engines will allow your regular customers to access your site. There are a lot of web-based business that do not know this.
If you want to focus on search engine optimization, you need a social media strategy. Twitter and Facebook are completely interactive, and the video sharing site YouTube is an effective way to showcase your product.
Search Engine Optimization requires a lot of patience. Sometimes it will seem like all your efforts are being done in vain. With millions of websites already online, it will take time for yours to fight its way to the front. It is imperative that you stay with the process for a sufficient amount of time, and don’t abandon it when it looks like nothing is changing with your site. Using common keywords and linking to other sites can also make your site more visible.
If you hire a search engine optimization company to improve your site, be sure to ask the important questions before you agree to anything. Things you wish to consider include their pricing, experience, recommended techniques and estimated time for visible results. You should ask to see examples of previous work, and if possible speak to their current or former clients. Companies that stand by their work will more than happily comply.
Use every venue available, from article directories to social networks, to drive traffic to your site with inbound links. A great way to succeed at search engine optimization is to gather the best outward links possible.
Phrases are an important part of Lynchburg Search Engine Optimization. Do you typically search with one word only? You need to attract traffic to your site that is actually looking for what your site has to offer. Include information that helps to put a location in the text, such as “Check out the sale at our Toronto location! ” rather than “We are going to have a sale! ”
When building a successful site, try to focus a single page on a single keyword. Using too many keywords on one page tends to cause people to misunderstand the purpose of the webpage. Worrying about just one topic tends to cause you to produce better content, which will cause your readers to continue coming back because they will be satisfied with what they are finding. Having a loyal handful of readers tends to raise your website rankings and increase search engine optimization.
No business expects to fail. Even though many online businesses fail, there are actually many more ways to find success on the Internet.
It can be difficult to learn the knowledge you need to know about When it comes to search engine marketing, you really should not gamble on your organization’s Google ranking to someone who is not a Lynchburg SEO Expert. If you are reading this, you most likely are searching for someone who can aid you develop your company’s online visibility, website traffic, and leads.

, especially if you don’t know how to begin. Learning about the key points on When it comes to search engine marketing, you really should not gamble on your organization’s Google ranking to someone who is not a Lynchburg SEO Expert. If you are reading this, you most likely are searching for someone who can aid you develop your company’s online visibility, website traffic, and leads. is a great start. Applying everything you learn from this article is proven to be a great way to get started on the road to success.
from Lynchburg SEO Expert https://lynchburgseoexpert.com/search-enginge-optimization-tips-that-increase-website-traffic/
0 notes
Text
Building a Search Engine Friendly Website
When it involves constructing a website, most of local business owner are mainly concerned regarding just what their website will certainly appear like to human visitors. If you desire your web site to rate well in the search results after that you need to guarantee it is structured for both search engines and also human visitors alike. If you're developing a brand-new internet site, or certainly restructuring your present site, after that you need to make certain that you adhere to the actions outlined in this message to develop a web site that is both obtainable to look engine crawlers as well as worthwhile of inclusion in their index.
Ensure your site is accessible
It must come as no shock that a web page does not look the same to online search engine as it does to human beings. It is for that reason necessary that you comprehend how online search engine spiders 'creep' web sites, as well as the kinds of material they prefer to index.
In order for your site to be detailed in the search results, your essential material ought to remain in HTML text format. Flash data, Javascript, as well as image heavy content is typically disregarded or cheapened by search engine crawlers. The simplest means to ensure that the words as well as phrases on your websites are noticeable to browse engines is to place them in the HTML message town of each page.
If your website includes a high number of pictures compared to message, after that it is necessary that you classify these images for search engines. Images could be appointed "alt" tags in HTML, giving search engines a message summary of the aesthetic content. Flash or Java based material could be sustained with text on the web page, while video clip content ought to have a going along with transcript if the words and also expressions used are essential to the keyword you 'd anticipate the web page the video clip is hosted on to place for.
In addition to guaranteeing your web site comes, it is very important that you provide high-quality, initial material on your web pages. Online search engine are establishing a more powerful understanding of specifically just what constitutes great high quality content. Basically, if your web pages have info that serves to your target market, this content will draw in visitors and also tempt other webmasters to connect to the details offered on your website.
Crawlable Link Structure
Just as online search engine need to be offered with content in order to detail pages in their mainly keyword-based index, they first of all should have the ability to locate your material. Therefore, creating a crawlable interior link framework on your internet site is very essential as it enables search engines to find all of the pages on your site. The first stage in creating an online search engine friendly inner web link structure is your primary navigating food selection, however there are still lots of sites that make the mistake of structuring their navigating in means that look engines can not 'review', hence affecting their capacity of their web pages to be detailed in the search results.
You should think about your navigation as well as general inner connecting framework as a way of signposting your material to search engines. If you don't connect to particular pages on your site it could be extremely difficult for online search engine to find them - as highlighted in the image listed below:
Take an appearance at this wonderful post on inner link framework from Moz, which plainly describes exactly how the structure of your inner links could affect site accessibility.
Your website need to be developed using a sensible web link framework as well as website navigation. I 'd recommend that every page ought to be obtainable from a minimum of one fixed text link on the site. Certainly, there are various other methods of signposting the structure of your site to Google and also various other internet search engine, As an example, by creating an XML sitemap, you have the capacity to feed search engines information on the pages on your website that you want crawled along with the priority or power structure of website material along with info on when the page was last updated.
If you intend to give your web pages the ideal possibility of being indexed by online search engine, I would recommend linking to every one of your crucial landing web pages on your main navigation menu and also frequently generating an XML sitemap having a listing of all the content on your website.
Make certain that websites connect to yours
Links help online search engine spiders discover your site as well as can aid give your site greater visibility in the search results. When returning results for a search question, online search engine use exceptionally sophisticated text-matching strategies to display web pages that are both essential and also appropriate to an individuals search. Outside links (links from various other sites pointing to your website) are a crucial statistics utilized by Google and also other internet search engine to calculate the value of a web page. Google translates a web link from page A to page B as a vote by web page A for page B. Links (or votes) cast by internet sites that are themselves prominent bring even more weight and thus pass even more 'link juice'.
Keep in mind that internet search engine algorithms could identify all-natural links from abnormal links. Abnormal web links to your site are classed as web links placed specifically making your website look even more popular to internet search engine. Some of these types of web links (such as web link plans as well as entrance pages) are covered in Google's Webmaster Standards. With this in mind, it is important to ensure your inbound web link profile is considered 'all-natural' by online search engine. You could find out more concerning ways to obtain all-natural connect to your website here.
Consider Keywords
Keywords are essential to the search procedure - they are the structure blocks of search. Certainly, if you want among your web pages to have a possibility of ranking in the search engine result for 'egg box', you have to make certain the phrase ' egg box' belongs to the material on the page.
Keyword usage as well as targeting still plays a huge component of online search engine' ranking algorithms, as well as it is consequently crucial that you include these keywords in certain towns of your internet pages that are seen as vital by online search engine. Selecting the keyword phrases to target on each page is not as uncomplicated as it appears, and I would always recommend performing thorough keyword research study on a page-by-page basis making use of tools such as Adwords key phrase coordinator, as well as Moz's key phrase difficulty device. These devices will enable you to study about the amount of people are browsing for a particular word or expression each month, and also approximately exactly how difficult it could be to place highly for those phrases.
When carrying out keyword research, it is essential to obtain into the way of thinking of the searcher, as well as aim to identify the words and phrases you believe your target market will certainly be making use of to find the content on your web site. Once you have determined a target key words for each and every of your crucial web pages, you will certainly then have to optimise the material on each web page to effectively 'target' each of these key phrases. You could review more regarding exactly where to include keywords on your pages here.
Search Engine Friendly LINK Structure
Best method URL framework is a topic which is frequently neglected by web designers. This is a substantial embarassment as rewriting URLs can be an obstacle in terms of keeping rankings as well as website traffic for any type of site.
While a descriptive LINK is important, reducing length and also tracking slashes will certainly make your Links easier to replicate and paste (into emails, post, message messages, etc) as well as will be completely noticeable in the search results.
If your pages are targeting a certain term or phrase, ensure to include those words in your Links (in small amounts of training course). The very best Links are human understandable, do not utilize parameters, numbers and also symbols. Google suggest making use of hyphens (-) rather than highlights (_) in LINK names, because expressions within URLs where the words are linked using emphasizes are treated by Google as one single word, e.g. example_url_structure is exampleurlstructure to Google.
Things to avoid
Don' t fill your page with reams of keyword phrases, or attempt to 'cloak' web pages. If your website has pages, links, or text that you do not plan site visitors to see, Google thinks about those links and pages deceitful as well as may well disregard your site completely.
Don' t develop several duplicates of a page under various Links. If your site has identical content that could be gotten to by means of various URLs, there are a number of methods of indicating the approved (recommended) version of a web page. Even more info concerning approved Links could be found here.
Duplicate content is an all also typical event these days. Over the past few years, internet search engine such as Google have punished 'thin' and duplicate content via charges as well as decreased ranking positions.
Don' t head out of your way to obtain web links from any type of resource feasible. Instead, produce material that will certainly gain connect to your site. Google in specific have actually been securing down on internet sites with abnormal inbound web link profiles in current times.
Conclusion
You ought to now have a concept of the best ways to create an internet search engine pleasant site framework, which will act as a platform for your material to be indexed by significant internet search engine. If you wish to speak to us about any of the factors covered in this write-up in greater information, and how we could aid you. You could call us on 0115 948 0123 or use our online contact form. I'm additionally satisfied to address your concerns in the comments box below.
#business#business owner#marketing#marketing strategy#media marketing#social media#social media management#social media marketing strategy
1 note
·
View note
Text
Best of Google Database
New Post has been published on https://is.gd/42EFDP
Best of Google Database

Google Cloud Database By
Google provides 2 different types of databases i.e google database
Relational
No-SQL/ Non-relational
Google Relational Database
In this google have 2 different products .
Cloud SQL
Cloud Spanner
Common uses of this relational database are like below
Compatibility
Transactions
Complex queries
Joins
Google No-SQL/ Non-relational Database
In this google provide 4 different types of product or databases
Cloud BigTable
Cloud Firestore
Firebase Realtime database
Cloud Memorystore
Common uses cases for this is like below
TimeSeries data
Streaming
Mobile
IoT
Offline sync
Caching
Low latency
Google relational Databases
Cloud SQL
It is Google fully managed service that makes easy to setup MySQL, PostgreSQL and SQL server databases in the cloud.
Cloud SQL is a fully-managed database service that makes easy to maintain, Manage and administer database servers on the cloud.
The Cloud SQL offers high performance, high availability, scalability, and convenience.
This Cloud SQL takes care of managing database tasks that means you only need to focus on developing an application.
Google manage your database so we can focus on our development task. Cloud SQL is perfect for a wide variety of applications like geo-hospital applications, CRM tasks, an eCommerce application, and WordPress sites also.
Features of Cloud SQL
Focus on our application: managing database is taken care of by google so we can focus on only application development.
Simple and fully managed: it is easy to use and it automates all backups, replication, and patches and updates are having 99.955 of availability anywhere in the world. The main feature of Cloud SQL is automatic fail-over provides isolation from many types of infrastructure hardware and software. It automatically increases our storage capacity if our database grows.
Performance and scalability: it provides high performance and scalability up to 30 TB of storage capacity and 60,000 IOPS and 416Gb of ram per instance. Having 0 downtimes.
Reliability and Security: As it is google so security issue is automatically resolved but the data is automatically encrypted and Cloud SQL is SSAE 16, ISO 27001 and PCI DSS v3.0 compliant and supports HIPAA compliance so you can store patient data also in Cloud SQL.
Cloud SQL Pricing:
Google Cloud SQL Pricing -Image From Official Google Site
Cloud Spanner
It is a fully managed scalable relational database service for regional and global application data.
Cloud spanner is the first database who takes advantage of relational database and non-relational database.
It is enterprise-grade, globally distributed and strongly consistent database service which built for cloud and it combines benefits of relational and non-relational horizontal scale.
By using this combination you can deliver high-performance transactions and strong consistency across rows, regions and continent.
Cloud spanner have high availability of 99.999% it has no planned downtime and enterprise-grade security.
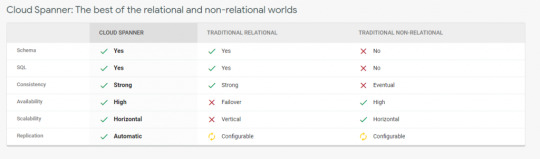
Google Cloud Spanner Features:- Image from official google site
Features of Cloud Spanner:
Scale+SQL:– in today’s world most database fail to deliver consistency and scale but at their, Cloud Spanner comes what it means? It means Cloud Spanner provides you advantage of relational database structure and not relational database scale and performance feature with external consistency across rows, regions and continents.
Cloud spanner scales it horizontally and serves data with low latency and along with that it maintains transactional consistency and industry-leading availability means 99.999%. It can scale up arbitrarily large database size means what It provides it avoids rewrites and migrations.
Less Task– it means google manage your database maintenance instead of you. If you want to replicate your database in a few clicks only you can do this.
Launch faster: it Is relational database with full relational semantics and handles schema changes it has no downtime. This database is fully tested by google itself for its mission-critical applications.
Security and Control:- encryption is by-default and audit logging, custom manufactured hardware and google owned and controlled global network.
Multi-language support means support c#, Go, Java, Php, Python and Ruby.
Pricing for Cloud Spanner:
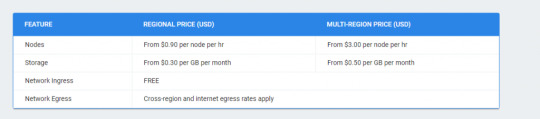
Google Cloud Spanner Pricing – Image from official google site
Non-relational Database by Google
BigTable
This Bigtable database is created by Google, it is compressed, high performance and proprietary data storage system which is created by Google and is built on top of google file system, LevelDB and other few google technologies.
This database development is starting in 2004 and now it is widely used by google like web indexing,google maps, google book search and google earth, blogger, google code, youtube.
The google is designed its own database because they need high scalability and better control over performance.
Bigtable is like wide column store. It maps 2 arbitrary string values which are row key and column key and timestamp for 3-dimensional mappings into an arbitrary byte array.
Remember it is not a relational database and it is more kind of sparse, distributed multi-dimensional sorted map.
BigTable is designed to scale in petabyte range across hundreds and thousands of machines and also to add additional commodity hardware machines is very easy in this and there is no need for reconfiguration.
Ex.
Suppose google copy of web can be stored in BigTable where row key is what is domain URL and Bigtable columns describe various properties of a web page and every column holds different versions of webpage.
He columns can have different timestamped versions of describing different copies of web page and it stores timestamp page when google retrieves that page or fetch that page.
Every cell in Bigtable has zero or timestamped versions of data.
In short, Bigtable is like a map-reduce worker pool.
A google cloud Bigtable is a petabyte-scale, fully managed and it is NoSQL database service provided by Google and it is mainly for large analytical and operational workloads.
Features Of Google Cloud BigTable:
It is having low latency and massively scalable NoSQL. It is mainly ideal for ad tech, fin-tech, and IoT. By using replication it provides high availability, higher durability, and resilience in the face of zonal failures. It is designed for storage for machine learning applications.
Fast and Performant
Seamless scaling and replication
Simple and integrated- it means it integrates easily with popular big data tools like Hadoop, cloud dataflow and Cloud Dataproc also support HBase API.
Fully Managed- means google manage the database and configuration related task and developer needs only focus on development.
Charges for BigTable- server: us-central
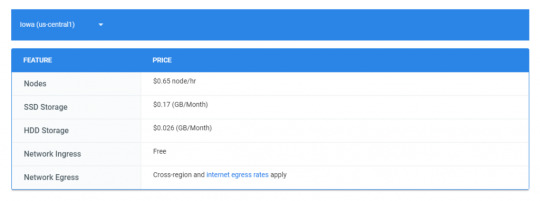
Google Bigtable Pricing- Image from official google site
Cloud Firestore
It is mainly serverless. Cloud Firestore is fast and serverless and fully managed and cloud-native NoSQL. It is document database which simplifies our storing data, syncing data and querying data from your IoT devices, mobile devices or web at global scale. It also provides offline support and its security features and integration with firebase and googles cloud platform.
Cloud Firestore features are below:
You can increase your development velocity with serverless: Is a cloud-native database and Cloud Firestore provides automatic scaling solution and it takes that advantage from googles powerful infrastructure. It provides live synchronization and offline support and also supports ACID properties for hundreds of documents and collections. From your mobile you can directly talk with cloud Firestore.
Synchronization of data on different devices: Suppose client use the different platform of your app means mobile, tab, desktop and when it do changes one device it will automatically reflected other devices with refresh or firing explicit query from user. Also if your user does offline changes and after while he comes back these changes sync when he is online and reflected across.
Simple and effortless: Is robust client libraries. By using this you can easily update and receive new data. You can scale easily as your app grows.
Enterprise-grade and scalable NoSQL: It is fast and managed NoSQL cloud database. It scales by using google infrastructure with horizontal scaling. It has built-in security access controls for data and simple data validations.
Pricing of Google Cloud Firestore:
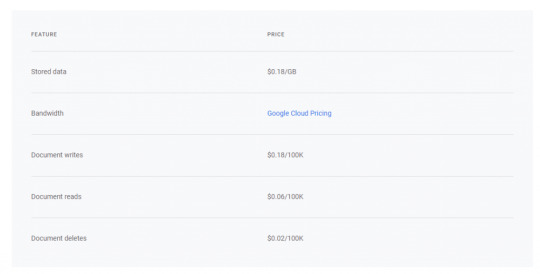
Google Cloud Firestore Pricing – Image from official googles site
FireBase
By tag line, it stores and sync data real-time. It stores data in JSON format. Different devices can access the same database.
It is also optimized for offline use and is having strong user-based security. This is also cloud-hosted database with a NoSQL database. It syncs In real-time across all clients and remains available if you go offline.
Capabilities of FireBase:
Realtime
Offline
Accessible from client devices
Scales across multiple databases: Means if you have blaze plan and your app go grow very fast and you need to scale your database so you can do in same firebase project with multiple database instances.
Firebase allows you to access the database from client-side code directly. Data is persisted locally and offline also in this realtime events are continuous fires by using this end-user experiences realtime responsiveness. When the client disconnected data is stored locally and when he comes online then it syncs with local data changes and merges automatically conflicts.
Firebase designed only to allow operations that can execute quickly.
Pricing of Firebase
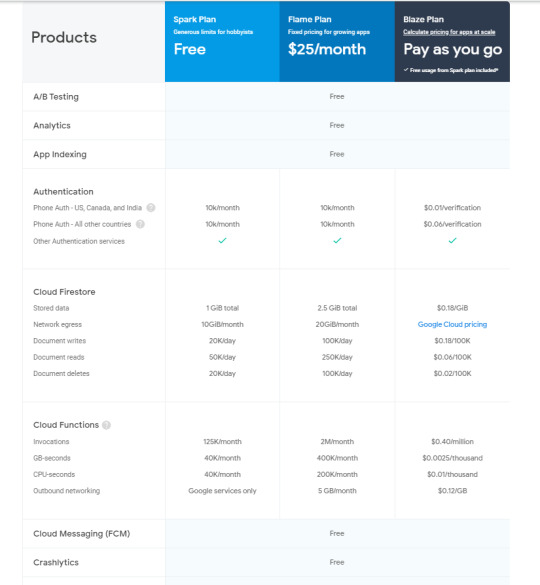
Google Firebase pricing-image from official google site
Cloud MemoryStores
This is an in-memory data store service for Redis. It is fully managed in-memory data store service which is built for scalability, security and highly available infrastructure which is managed by Google.
It is very much compatible with Redis protocol so it allows easy migration with zero code changes. When you want to store your app data in sub-millisecond then you can use this.
Features of Cloud memory stores:
It has the power of open-source Redis database and googles provide high availability, failure and monitoring is done by google
Scale as per your need:- by using this sub-millisecond latency and throughput achieve. It supports instances up to 300 Gb and network throughput 12 Gbps.
It is highly available- 99.9% availability
Google grade security
This is fully compatible with Redis protocol so your open-source Redis move to cloud memory store without any code change by using simple import and export feature.
Price for Cloud MemoryStore:
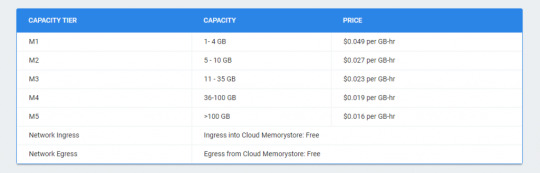
Google Cloud Memorystore price – image from official site of google
0 notes
Text
300+ TOP J2ME Objective Questions and Answers
J2ME Multiple Choice Questions :-
1. Which of the following statements is true about Java ME? A. Java ME is a single specification. B. Java ME is a family of related specifications. C. Java ME is a platform for creating applications for the well-established desktop market. D. Java ME is a platform for creating server-side enterprise applications. Ans: B 2. What is a configuration? A. A configuration defines a set of class libraries available for a particular domain of devices. B. A configuration defines a vertical (or specialized) set of classes. C. A configuration defines a minimum set of class libraries for a wide range of devices. D. All of the above. Ans: C 3. What is a profile? A. A profile defines a set of class libraries available for a wide range of devices. B. A profile defines a horizontal set of classes that a configuration can use. C. A profile defines the set of APIs available for a particular family of devices. D. A profile is the foundation for a configuration. Ans: C 4. The Personal Digital Assistant (PDA) Profile is based on: A. Connected Device Configuration (CDC). B. Connected Limited Device Configuration (CLDC). Ans: B 5. The Foundation profile: A. Extends the CDC by adding the missing user interface APIs. B. Extends the CLDC by adding the missing Java 2, Standard Edition (J2SE) core libraries. C. Is meant to serve as a foundation for other profiles. D. All of the above. Ans: C 6. The RMI profile is meant to be used with: A. CLDC and MIDP B. CDC and Foundation C. Both A and B Ans: B 7. The CLDC does not address user interface issues. They are left to be handled by the: A. Foundation profile B. Personal profile C. Mobile Information Device Profile (MIDP) D. None of the above Ans: C 8. Which of the following network connections is supported by MIDP? A. UDP datagrams B. WAP C. HTTP D. All of the above Ans: C 9. A Java ME-enabled device: A. Can support only a single profile B. Can support multiple profiles Ans: B 10. A device that currently uses CLDC (and therefore has a profile) can use that profile with CDC without modification. A. True B. False Ans: A

J2ME MCQs 11. In the CDC, user interface issues are handled by the: A. Foundation profile B. Personal profile C. Mobile Information Device Profile (MIDP) D. None of the above Ans: B 12. The CDC targets devices with _______ of total memory available for the Java platform, including both RAM and flash or ROM. A. 160 KB B. 256 KB C. 512 KB D. 2 MB or More Ans: D 13. The Java Virtual Machine1 specified to be used with the CDC is: A. KVM B. CVM C. PVM Ans: B 14. In MIDP, the maximum length of a record store name is: A. 8 characters B. 32 characters C. 128 characters D. No limit on the length of a record store name Ans: B 15. Is it possible to determine the contents of a JAR file before is it downloaded to a device? A. No, it is not. B. Yes, by inspecting the associated JAD file. Ans: B 16. The CDC and Foundation make corrections to the J2SE libraries by removing all noncritical, deprecated APIs. A. True B. False Ans: A 17. Which of the following network connections is supported by the CDC? A. UDP datagrams B. TCP sockets C. HTTP connections D. None of the above Ans: A 18. Which of the following network connections is supported by the Foundation profile? A. UDP datagrams B. TCP sockets C. HTTP D. All of the above Ans: D 19. What compilation option should be used when compiling Java ME applications? A. -classpath B. -bootclasspath C. -preverify D. Any of the above Ans: B 20. Which of the following areas are being investigated by the MIDP Next Generation? A. HTTPS and secure networking B. Network connectivity through sockets and datagrams C. Extensions to the low-level user interface APIs to allow greater game functionality D. All of the above E. None of the above Ans: E 21. A midlet is a Java class that extends the abstract class: A. javax.microedition.MIDlet B. javax.microedition.midlet C. javax.microedition.midlet.MIDlet D. javax.microedition.midlet.midlet Ans: C 22. Which one of the following methods of the MIDlet abstract class must be implemented by a midlet: A. initApp, startApp B. startApp, destroyApp C. startApp, pauseApp, destroyApp D. initApp, startApp, pauseApp, destroyApp Ans: C 23. After compiling your midlet, you must process it with a command to ensure that it is valid before use by the Kilo virtual machine (KVM). What is the name of that command? A. midp B. javac-bootclasspath C. preverify D. jar Ans: C 24. A Java Application Descriptor (JAD) file is a text file that is similar to a manifest, except that it is not packaged in a JAR file. Some of the shared attributes that must have identical values are: MIDlet-Name, MIDlet-Version, and MIDlet-Vendor. If any shared attributes are different, then: A. The ones in the descriptor override those in the manifest B. The ones in the manifest override those in the descriptor Ans: A 25. When downloading application descriptors (.jad files) from a web server, the web server must return a MIME type of: A. text/vnd.sun.j2me.midp B. text/vnd.sun.j2me.jad C. text/vnd.sun.j2me.app-descriptor D. text/vnd.sun.j2me.midapp Ans: C 26. A midlet suite is a set of midlets that are packed together into a single JAR file. Midlets within the same suite: A. Can share the classes and resources contained in the JAR file B. Cannot share the classes and resources contained in the JAR file Ans: A 27. Midlets from different suites: A. Can interact directly. B. Cannot interact directly. Ans: B 28. What is the difference between a configuration (such as the CLDC) and a profile (such as the MIDP)? A. a configuration defines the set of class libraries available for a particular domain of devices, and a profile provides I/O and network APIs. B. a configuration defines a vertical set of classes that a profile can use. C. a configuration defines a minimum set of class libraries for a wide range of devices, and a profile defines the set of APIs available for a particular family of devices. D. a profile is the foundation for a configuration. Ans: C 29. All MIDP implementations are required to support what image format? A. GIF B. JPG C. BMP D. PNG Ans: D 30. If a midlet needs to receive high-level events from the implementation, which interface should it implement? A. ActionListener B. CommandListener C. Windows Listener D. ChoiceListener Ans: B 31. All MIDP GUI classes are contained in what package? A. javax.microedition.gui B. javax.microedition.lcd C. javax.microedition.lcdui D. javax.microedition.display Ans: C 32. The MIDP user interface API is a subset of the AWT/ Project Swing libraries. A. True B. False Ans: B 33. Which class would you use to write applications to access low-level input events or to issue graphics calls for drawing to the display? A. Display B. Command C. Screen D. Canvas Ans: D 34. Which of the following statements is true regarding the Generic Connection framework: A. The CLDC provides an implementation for the HTTP protocol. B. All MIDP implementations must provide support for the HTTP protocol. C. The MIDP provides implementation for datagram and socket connections. D. The Connection interface is part of the java.net package. Ans: B 35. The heart of the Generic Connection framework is: A. javax.microedition.Connection B. javax.microedition.Connector C. javax.microedition.StreamConnection D. javax.microedition.HttpConnection Ans: B J2ME Objective type Questions and Answers 36. What is the correct syntax, using the Generic Connection framework, to open an HTTP connection: A. Connection c = Connection.open("http://developer.java.sun.com"); B. Connector c = Connector.open("http://developer.java.sun.com"); C. Connection c = Connector.open("http://developer.java.sun.com"); B. Connector c = Connection.open("http://developer.java.sun.com"); Ans: C 37. The MIDP provides a mechanism for MIDlets to persistently store data in a platform-dependent file and retrieve it later. This mechanism is: A. Object Serialization B. JDBC C. RMS D. ODBC Ans: C 38. A Java virtual machine1 (JVM) supporting CLDC has no support for: A. Floating point numbers B. Reflection C. JNI D. All of the above Ans: D 39. Which of the following non-exception classes are inherited from the Java 2 Standard Edition 1.3 java.util package by the CLDC: A. Calendar, Date, Enumeration, Hashtable, Stack, Vector B. Calendar, Date, Enumeration, Hashtable, Random, Stack, Timer, Vector C. Calendar, Date, Enumeration, Hashtable, Stack, Vector, StringTokenzier D. All of the java.util classes are inherited Ans: B 40. Which of the following techniques can be used for wireless session tracking? A. Cookies B. URL Rewriting C. Hidden Fields D. None of the above Ans: B 41. Which class would you use to write applications to access low-level input events or to issue graphics calls for drawing to the display? A. Display B. Command C. Screen D. None of these Ans: C 42. Which one of the following methods of the MIDlet abstract class must be implemented by a midlet: A.initApp, startApp B.startApp, destroyApp C.initApp, startApp, pauseApp, destroyApp D. startApp, pauseApp, destroyApp Ans: D WWW.PECET.ACSCHE.AC.IN 43. All MIDP GUI classes are contained in what package? A. javax.microedition.gui B. javax.microedition.lcd C. javax.microedition.lcdui D. javax.microedition.display Ans: C 44. Which of the following techniques can be used for wireless session tracking? A. Cookies B. URL Rewriting C. Hidden Fields D. None of the above Ans: B 45. A midlet is a Java class that extends the abstract class: A. javax.microedition.MIDlet B. javax.microedition.midlet C. javax.microedition.midlet.MIDlet D. javax.microedition.midlet.midlet Ans: C 46. All MIDP implementations are required to support what image format? A. GIF B. JPG C. BMP D. PNG Ans: D 47.The heart of the Generic Connection framework is: A. javax.microedition.Connection B. javax.microedition.Connector C. javax.microedition.StreamConnection D. javax.microedition.HttpConnection Ans: C 48. If a midlet needs to receive high-level events from the implementation, which interface should it implement? A. ActionListener B. CommandListener C. Windows Listener D. ChoiceListener Ans: B 49. A Java virtual machine1 (JVM) supporting CLDC has no support for: A. Floating point numbers B. Reflection C. JNI D. All of the above Ans: D 50. The MIDP user interface API is a subset of the AWT/ Project Swing libraries. A. True B. False Ans: B 51. A midlet is a Java class that extends the abstract class: A. javax.microedition.MIDlet B. javax.microedition.midlet C. javax.microedition.midlet.MIDlet D. javax.microedition.midlet.midlet Ans: C 52. Which one of the following methods of the MIDlet abstract class must be implemented by a midlet: A. initApp, startApp B. startApp, destroyApp C. startApp, pauseApp, destroyApp D. initApp, startApp, pauseApp, destroyApp Ans: C 53. After compiling your midlet, you must process it with a command to ensure that it is valid before use by the Kilo virtual machine (KVM). What is the name of that command? A. midp B. javac-bootclasspath C. preverify D. jar Ans: C 54. A Java Application Descriptor (JAD) file is a text file that is similar to a manifest, except that it is not packaged in a JAR file. Some of the shared attributes that must have identical values are: MIDlet-Name, MIDlet-Version, and MIDlet-Vendor. A. The ones in the descriptor override those in the manifest B. The ones in the manifest override those in the descriptor Ans: A 55. When downloading application descriptors (.jad files) from a web server, the web server must return a MIME type of: A. text/vnd.sun.j2me.midp B. text/vnd.sun.j2me.jad C. text/vnd.sun.j2me.app-descriptor D. text/vnd.sun.j2me.midapp Ans: C 56. A midlet suite is a set of midlets that are packed together into a single JAR file. Midlets within the same suite: A. Can share the classes and resources contained in the JAR file B. Cannot share the classes and resources contained in the JAR file Ans: A 57. Midlets from different suites: A. Can interact directly. B. Cannot interact directly. Ans: B 58. What is the difference between a configuration (such as the CLDC) and a profile (such as the MIDP)? A. a configuration defines the set of class libraries available for a particular domain of devices, and a profile provides I/O and network APIs. B. a configuration defines a vertical set of classes that a profile can use. C. a configuration defines a minimum set of class libraries for a wide range of devices, and a profile defines the set of APIs available for a particular family of devices. D. a profile is the foundation for a configuration. Ans: C 59. All MIDP implementations are required to support what image format? A. GIF B. JPG C. BMP D. PNG Ans: D 60. If a midlet needs to receive high-level events from the implementation, which interface should it implement? A. ActionListener B. CommandListener C. Windows Listener D. ChoiceListener Ans: B 61. All MIDP GUI classes are contained in what package? A. javax.microedition.gui B. javax.microedition.lcd C. javax.microedition.lcdui D. javax.microedition.display Ans: C 62. The MIDP user interface API is a subset of the AWT/ Project Swing libraries. A. True B. False Ans: B 63. Which class would you use to write applications to access low-level input events or to issue graphics calls for drawing to the display? A. Display B. Command C. Screen D. Screen Ans: D 64. Which of the following statements is true regarding the Generic Connection framework: A. The CLDC provides an implementation for the HTTP protocol. B. All MIDP implementations must provide support for the HTTP protocol. C. The MIDP provides implementation for datagram and socket connections. D. The Connection interface is part of the java.net package. Ans: B 65. The heart of the Generic Connection framework is: A. javax.microedition.Connection B. javax.microedition.Connector C. javax.microedition.StreamConnection D. javax.microedition.HttpConnection Ans: B 66. What is the correct syntax, using the Generic Connection framework, to open an HTTP connection: A. Connection c = Connection.open("http://developer.java.sun.com"); B. Connector c = Connector.open("http://developer.java.sun.com"); C. Connection c = Connector.open("http://developer.java.sun.com"); D. Connector c = Connection.open("http://developer.java.sun.com"); Ans: C 67. The MIDP provides a mechanism for MIDlets to persistently store data in a platform-dependent file and retrieve it later. This mechanism is: A. JDBC B. RMS C. ODBC Ans: C 68. A Java virtual machine1 (JVM) supporting CLDC has no support for: A. Floating point numbers B. Reflection C. JNI D. All of the above Ans: D 69. Which of the following non-exception classes are inherited from the Java 2 Standard Edition 1.3 java.util package by the CLDC: A. Calendar, Date, Enumeration, Hashtable, Stack, Vector B. Calendar, Date, Enumeration, Hashtable, Random, Stack, Timer, Vector C. Calendar, Date, Enumeration, Hashtable, Stack, Vector, StringTokenzier D. All of the java.util classes are inherited Ans: B 70. Which of the following techniques can be used for wireless session tracking? A. Cookies B. URL Rewriting C. Hidden Fields D. None of the above Ans: B J2ME Questions and Answers pdf Download Read the full article
0 notes