#USB data logger software
Explore tagged Tumblr posts
Text
https://www.futureelectronics.com/p/semiconductors--analog--sensors--humidity-dew/sht41i-ad1b-r2-sensirion-9164920
Digital humidity sensor, USB data, Soil moisture sensor, Temperature sensor
SHT41I-AD1B-R2
#Sensirion#SHT41I-AD1B-R2#Sensors#Humidity / Dew Sensors#digital#USB data#Soil moisture sensor#Engine coolant#humidity monitor#USB data logger software#home#Remote humidity sensor#humidity sensor switch
1 note
·
View note
Text
What to Look for in Industrial Measurement Equipment for Manufacturing Facilities
In manufacturing, precision is everything. Whether you're producing electronics, automotive components, pharmaceuticals, or food packaging, accuracy in measurement directly impacts quality, safety, and regulatory compliance. That’s why investing in the right industrial measurement equipment is not only a smart decision—it’s a critical one.
But with so many options on the market, how do you choose the right tools for your facility?
At EpicRise Electronics, we help businesses across industries source high-performance tools and IT equipment, including measurement systems, scanners, and wholesale label printers. Here's what to look for when equipping your manufacturing facility with industrial measurement solutions.
1. Accuracy and Reliability
The foremost priority in any measurement equipment is accuracy. Whether you're measuring weight, temperature, humidity, voltage, or dimensional properties, even the smallest margin of error can lead to production defects, wasted materials, and safety issues.
Look for devices that meet or exceed ISO or NIST standards and are tested for industrial-grade precision. It’s also essential that the equipment performs consistently over time without needing frequent recalibration.
Tip: Opt for trusted manufacturers that offer certification or documentation on equipment accuracy. Brands partnered with EpicRise often come with reliability reports and compliance details.
2. Durability and Build Quality
Manufacturing environments are often harsh—subject to heat, moisture, dust, vibration, and continuous operation. Your measurement tools must be built for endurance.
When sourcing items such as laser measurement devices, multimeters, or pressure gauges, choose models specifically designed for industrial environments. Features to consider include:
Rugged casings (shock-proof, waterproof, dustproof)
High-quality connectors and cables
Resistance to chemicals or oil
Durability reduces downtime and repair costs—especially in 24/7 operations.
3. Integration with Existing Systems
Modern manufacturing facilities are increasingly automated and data-driven. Measurement devices should seamlessly integrate with your existing systems, whether that’s SCADA software, ERP platforms, or IoT networks.
Look for equipment with USB, Ethernet, or Bluetooth connectivity, and ensure it's compatible with your current software architecture. This allows real-time data collection and monitoring, improving decision-making and traceability.
Pro Tip: Integration also extends to your labeling and tracking tools. For instance, pairing a Zebra barcode scanner with automated weighing or inspection stations ensures that product IDs and measurement data flow smoothly across systems.
4. Ease of Use and Operator Training
Complex equipment that requires excessive training can slow down operations and increase the likelihood of user error. Choose tools that offer intuitive interfaces, clear displays, and simple calibration procedures.
Many leading brands also offer training resources, online support, and documentation. These are crucial when onboarding new team members or troubleshooting issues on the production floor.
At EpicRise, we prioritize stocking measurement tools with user-friendly design, backed by strong manufacturer support and documentation.
5. Scalability and Upgrade Potential
Your facility’s needs today might not be the same five years from now. The best industrial measurement systems are modular or scalable—allowing you to expand or upgrade without overhauling your entire process.
For example:
Multichannel data loggers can be expanded with additional sensors.
Barcode readers and scanners can be upgraded with advanced software.
Integrated systems can support added devices as your production grows.
When planning for growth, choose flexible solutions that evolve with your operations.
6. Data Logging and Traceability Features
In highly regulated industries—like food, medical devices, or aerospace manufacturing—data traceability is non-negotiable. Measurement tools should offer internal storage, cloud connectivity, or the ability to export logs securely.
This helps meet compliance standards (e.g., FDA, ISO 9001) and supports quality audits, troubleshooting, and continuous improvement initiatives.
Pairing your measurement devices with wholesale label printers also boosts traceability. With every reading, you can instantly generate barcode labels that reflect batch numbers, inspection dates, or critical data points.
7. Brand Reputation and Support
With industrial-grade tools, it pays to choose reputable brands with proven track records. These manufacturers typically offer:
Better warranties
Firmware updates
Technical support
Long-term availability of spare parts
One such example is Zebra Technologies, a leader in tracking and scanning tools. Their Zebra barcode scanner models are known for reliability in industrial environments, offering high-speed scanning, rugged durability, and seamless integration with other factory systems.
EpicRise is proud to offer Zebra products, along with measurement devices and peripherals from top global brands.
8. Cost Efficiency Through Wholesale Channels
Quality measurement equipment can be a major investment, especially if you’re outfitting an entire facility. Buying through a distributor like EpicRise Electronics means you gain access to wholesale pricing, faster shipping, and expert consultation.
Need to bundle tools with scanning devices, power supplies, or network equipment? We make procurement simple and affordable by offering:
Wholesale label printers
Bulk orders of barcode scanners and sensors
Compatible accessories and software
You don’t have to compromise quality for budget—EpicRise delivers both.
Final Thoughts
Investing in the right industrial measurement equipment pays dividends across your manufacturing operation—from better product quality and compliance to increased efficiency and cost savings. But success starts with sourcing smart.
When you work with EpicRise Electronics, you get more than just tools—you get a trusted partner in procurement. From Zebra barcode scanner systems to durable measurement devices and wholesale label printers, we supply the equipment that powers precision manufacturing.Need help choosing the right gear for your facility? Explore our full product range at EpicRiseElectronics.com or contact our support team for a custom quote today.
0 notes
Text
How Do IoT Data Loggers Enhance Data Collection?
In the age of digital transformation, collecting and analyzing data has become the backbone of efficient operations across industries. Whether monitoring temperature in a cold storage facility, analyzing vibrations in machinery, or measuring electrical signals in research labs, data loggers play a vital role in recording and preserving data. Among the most commonly used tools in this field are the IoT data logger, digital data logger, and DAQ data acquisition systems.
What is a Data Logger?
A data logger is an electronic instrument designed to record various types of data over time. It typically includes sensors, microcontrollers, memory storage, and software to collect and store information for later use. Data loggers are used in diverse applications—from environmental monitoring and industrial control to logistics and scientific research.
The key benefit of a data logger is its ability to operate autonomously once configured. Users can deploy these devices in remote or hard-to-reach locations where constant human supervision is impractical. They are engineered to log everything from temperature, humidity, and pressure to voltage, current, and vibration.
Understanding the IoT Data Logger
One of the most innovative developments in the world of data logging is the IoT data logger. These devices leverage the power of the Internet of Things to transmit real-time data to cloud-based platforms. Unlike traditional loggers that require manual data retrieval, IoT data loggers provide instant remote access to critical metrics.
This functionality is particularly useful in industries like agriculture, manufacturing, smart cities, and utilities. For example, a smart farm may use IoT data loggers to monitor soil moisture, temperature, and rainfall—enabling automated irrigation systems and real-time alerts. Similarly, in industrial plants, these loggers help monitor equipment conditions and detect anomalies before they lead to costly breakdowns.
IoT data loggers often come with wireless communication features like Wi-Fi, cellular (4G/5G), or LoRaWAN. They are integrated with GPS for location tracking and equipped with dashboards or mobile apps for easy data visualization.
Digital Data Logger: A Reliable Workhorse
A digital data logger is one of the most widely used types of data loggers. These compact devices are designed to measure and store data in digital form, ensuring high accuracy and ease of integration with computers and management systems. Unlike analog data recorders, digital data loggers minimize the chances of human error and offer improved precision.
They are commonly employed in industries where continuous monitoring is crucial—such as pharmaceuticals, food processing, and transportation. For example, in cold chain logistics, digital data loggers are used to monitor the temperature of perishable goods during transit. If the temperature deviates from the allowed range, the logger stores the event and alerts the operator.
Modern digital data loggers come with LCD screens, USB or Bluetooth connectivity, long battery life, and configurable sampling intervals. Their plug-and-play functionality makes them ideal for non-technical users who still require dependable data.
DAQ Data Acquisition Systems: For Complex Data Needs
While digital and IoT data loggers are great for general-purpose monitoring, DAQ data acquisition systems are used for more advanced and high-speed data recording applications. These systems consist of sensors, signal conditioning hardware, analog-to-digital converters, and specialized software that works in tandem to gather, process, and analyze large volumes of data in real time.
DAQ data acquisition systems are frequently used in laboratories, engineering research, aerospace, automotive testing, and energy sectors. For instance, during crash tests in the automotive industry, DAQ systems capture a wide range of sensor data—force, acceleration, pressure, and more—at extremely high speeds.
What sets DAQ systems apart is their ability to handle multiple input channels simultaneously and offer highly customizable configurations. They are typically connected to a PC or an industrial controller, allowing users to visualize and manipulate data through sophisticated software tools like LabVIEW or MATLAB.
Choosing the Right Tool
Choosing between an IoT data logger, digital data logger, and DAQ data acquisition system depends on your specific application needs:
IoT data logger: Best for remote, real-time monitoring where wireless communication is key.
Digital data logger: Ideal for routine environmental or process monitoring with accuracy and ease of use.
DAQ data acquisition: Suited for research and engineering environments where complex, high-speed, multi-signal data is required.
Conclusion
Data logging technologies have evolved to match the ever-growing demand for precision, efficiency, and real-time access. Whether it’s the connectivity of an IoT data logger, the reliability of a digital data logger, or the power and complexity of DAQ data acquisition systems, these tools empower industries to make smarter, faster, and more informed decisions. As technology continues to advance, the future of data logging promises even greater integration, automation, and intelligence.
0 notes
Text

High-Precision Mini Temperature and Humidity Data Logger – Testo 174 H
Discover the Testo 174 H mini temperature and humidity data logger, a small and dependable solution for measuring sensitive environments like storage rooms, laboratories, and logistics. The mini temperature data logger has a USB interface and intuitive PC software, allowing easy setup and downloading of precise measurement data. Perfect for guaranteeing compliance in the food safety, pharma, and HVAC sectors, the Testo 174 H provides reliable German technology in a pocket form. Shop today at shop testo and benefit from unparalleled performance and reliability.
#Mini data logger#mini temperature data logger#mini temperature and humidity data logger#humidity data logger
0 notes
Text
Voice logger manufactures & providers in Mumbai,
In today's dynamic business landscape, effective and secure communication is critical for success. From customer support calls to internal team discussions, businesses need a reliable way to record and analyze voice interactions. This has led to a growing demand for advanced call recording solutions. Fortunately, companies now have access to experienced Voice Logger Manufacturers & Providers in Mumbai who offer cutting-edge technology tailored to modern business needs.
Mumbai, being the financial hub of India, is home to thousands of enterprises that operate in fast-paced environments. Whether it's a multinational bank, a healthcare center, or a BPO, organizations need tools that help improve service quality, compliance, and dispute resolution. That’s where voice loggers come in.
What Is a Voice Logger?
A voice logger is a hardware or software solution that records telephone conversations. These systems are used to store, retrieve, and analyze audio data from analog, digital, or VoIP communication systems. Typically used in industries where accurate communication is critical, voice loggers ensure transparency and accountability in voice-based interactions.
Why Are Voice Loggers Essential?
Voice loggers aren’t just about recording calls—they’re about transforming communication into actionable insights. Here’s why companies turn to expert Voice Logger Manufacturers & Providers in Mumbai:
Monitoring & Quality Control: Supervisors can monitor live calls and playback recorded conversations to evaluate service standards and train staff accordingly.
Legal Protection: Recorded calls serve as documented proof in case of legal disputes or compliance audits.
Compliance & Regulation: Financial institutions, healthcare providers, and government organizations must comply with strict regulations that mandate the recording of voice communications.
Performance Tracking: Companies can assess agent performance, identify trends, and make data-driven decisions.
Customer Satisfaction: Understanding customer issues through call recordings helps improve service strategies and resolve complaints efficiently.
Aria Telecom – A Trusted Name in the Industry
As one of the leading Voice Logger Manufacturers & Providers in Mumbai, Aria Telecom brings over two decades of experience and innovation. Their product range is designed to meet the unique requirements of Indian businesses, offering everything from single-line USB voice loggers to multi-channel enterprise-level recording systems.
Key Offerings from Aria Telecom:
USB Voice Loggers for small offices
PRI & VoIP Voice Loggers for medium to large enterprises
Analog & Digital Call Recording Systems
Multi-channel support for 4 to 128 lines
Remote access, real-time monitoring, and custom reporting tools
Aria Telecom’s systems are easy to install, scalable, and user-friendly, making them a perfect fit for organizations of all sizes.
What Sets Aria Apart?
Choosing Aria Telecom means investing in more than just a device—you get a complete solution that includes hardware, software, support, and customization.
Top Features:
Crystal-clear Audio Quality
Secure Data Encryption & Cloud Backup
Searchable Call Archives
Custom Dashboard for Analytics & Reporting
Live Monitoring & Alerts
Integration with CRM and Helpdesk Tools
With strong after-sales support and technical assistance, Aria Telecom ensures uninterrupted service and system performance.
Where Are Voice Loggers Used?
Solutions from Voice Logger Manufacturers & Providers in Mumbai are commonly implemented in:
Call Centers & Customer Support Departments – For quality monitoring and complaint handling
Banks & Financial Services – To meet RBI compliance and transaction record keeping
Hospitals & Clinics – To record consultations and appointment calls
Police Departments & Emergency Services – To track and archive crucial calls
Corporate Offices & Legal Firms – For client communication recording and documentation
Any organization relying on verbal communication can benefit from a voice logger system to enhance transparency and efficiency.
#VoiceLoggerMumbai#AriaTelecomIndia#CallRecordingSolutions#BusinessCommunicationTools#SecureVoiceLogging
0 notes
Text
Single-Use Loggers: The Cost-Effective Solution for Accurate Data Monitoring

In industries where precise data monitoring is critical, the need for reliable, efficient, and cost-effective tools is paramount. From pharmaceuticals to food transportation, maintaining accurate temperature and humidity data can be the difference between product integrity and loss. Single-use loggers have emerged as a practical solution, offering simplicity and reliability for businesses that prioritize efficiency and accuracy in their operations.
What Are Single-Use Loggers?
Single-use loggers are compact, lightweight devices designed to record environmental data such as temperature and humidity during transportation or storage. Unlike reusable data loggers, these devices are meant for one-time use, making them particularly appealing for sectors where cost control and compliance with stringent regulations are crucial. Their design ensures they are easy to deploy and retrieve data from, often without the need for additional software or tools.
Benefits of Single-Use Loggers
One of the most significant advantages of single-use loggers is their cost-effectiveness. These devices provide accurate monitoring without the added expense of maintenance or recalibration required for reusable loggers. Additionally, they are ideal for industries like pharmaceuticals and perishable goods, where maintaining specific environmental conditions during transit is essential.
Single-use loggers are also user-friendly, designed to provide straightforward data retrieval. Many models come with built-in USB connections or simple plug-and-play capabilities, enabling quick access to recorded information. This ease of use reduces the risk of human error while saving time and resources.
Applications Across Industries
The versatility of single-use loggers makes them invaluable across various industries. In the food industry, they help ensure that perishable items remain within safe temperature ranges during transport. Similarly, in the pharmaceutical sector, they provide critical data to ensure compliance with storage requirements for temperature-sensitive medications and vaccines.
Single-use loggers also find applications in clinical trials, logistics, and other fields where maintaining accurate environmental records is non-negotiable. Their ability to deliver reliable results at an affordable cost makes them a trusted choice for professionals worldwide.
Single-use loggers offer an efficient and budget-friendly solution for businesses needing accurate data monitoring without long-term maintenance costs. Their simplicity, reliability, and adaptability make them a valuable asset across industries. For high-quality single-use loggers tailored to your needs, visit iVision today and explore how these devices can streamline your operations.
0 notes
Text



GF438II 6000A 1000V IEC61000-4-30 class A handheld three phase power quality analyzer
GF438II handheld three phase power quality analyzer offer the best ability in power quality analysis, GF438II handheld power quality analyzer help locate, predict, prevent and troubleshoot power quality problems in three phase and single phase power distribution systems. Additionally, GFUVE patented energy loss algorithm, unified power measurement, measuring and counting energy losses due to harmonics and unbalance issues, allowing the user to pinpoint the origin of energy losses in the system. GF438II handheld three phase power quality analyzer supports the measurement of 50 Hz and 60 Hz power frequency system. It can record and analyze different types of power quality parameters such as voltage, current, harmonic, frequency, fluctuation, flicker, swell,sag, power and three-phase unbalance of power supply line. It has advanced power quality measurement function and provides professional upper computer GFUVEPQA analysis software for secondary analysis and report file. To provide users with the most accurate power fault diagnosis analysis. And there are Ethernet, input contact, output contact, USB and other communication ports, which can flexibly carry out network communication. FUTURES
With PC management Software
10000 screenshots save
8 channel voltage & current
IEC61000-4-30 CLASS A 0.1%
32G data logger/recorder waveform
Support multi-brand current probe
2-63rd harmonic measurment
Voltage swell, Voltage sags, DIP
Fliker & In-harmonic measurement
Inrush current
Energy line loss
Unballance
1000V/5A/100A/500A/1000A/3000A/6000A
40-70HZ range, accuracy 0.001Hz
1 note
·
View note
Text
The Ultimate Guide to Data Acquisition Equipment: Key Features and Benefits
Data acquisition equipment is a critical component in various industries, enabling the collection, measurement, and analysis of data from physical systems. Whether you’re in engineering, manufacturing, or scientific research, understanding how to select and use the right data acquisition system can significantly impact the quality and accuracy of your work. This blog will explore the essential features, benefits, and considerations when choosing Data Acquisition Equipment.
What is Data Acquisition Equipment?
Data acquisition (DAQ) equipment is used to gather information from physical phenomena and convert it into a digital format that can be analyzed by computers. This equipment typically includes sensors, data loggers, and software to capture and process data from various sources like temperature, pressure, voltage, or sound.
Essential Features to Look For
Sampling Rate
Importance: The sampling rate determines how frequently data is collected. A higher sampling rate allows for more detailed data but requires more processing power and storage.
Tip: Match the sampling rate to your application’s requirements. For high-speed processes, you’ll need a higher sampling rate.
Resolution
Importance: Resolution refers to the precision of the measurements. Higher resolution provides more detailed data, which is crucial for applications requiring fine measurements.
Tip: Choose equipment with the highest resolution that fits your budget to ensure the accuracy of your data.
Input Channels
Importance: The number of input channels determines how many signals can be measured simultaneously. This is important for complex systems with multiple data points.
Tip: Select equipment with enough input channels to handle your current and future needs.
Connectivity
Importance: Modern DAQ systems often need to interface with various devices and networks. USB, Ethernet, and wireless options offer flexibility in data transfer.
Tip: Ensure your equipment supports the connectivity options you need for seamless integration into your workflow.
Software Compatibility
Importance: The software that comes with your DAQ system plays a crucial role in data analysis. It should be user-friendly and compatible with your existing systems.
Tip: Look for software that offers robust analysis tools and is compatible with popular operating systems and programming environments.
Portability
Importance: For fieldwork or on-site testing, portable DAQ systems are invaluable. They allow for data collection in remote or challenging environments.
Tip: Consider battery life, weight, and durability when choosing a portable system.
Benefits of Using Data Acquisition Equipment
Enhanced Data Accuracy
Data acquisition systems offer high levels of precision, reducing the likelihood of errors and improving the reliability of your analysis.
Real-Time Monitoring
Many DAQ systems provide real-time data monitoring, enabling instant decision-making and troubleshooting.
Versatility Across Applications
From automotive testing to environmental monitoring, DAQ systems are versatile tools that can be adapted to various industries and applications.
Data Integration and Analysis
DAQ systems often come with advanced software that allows for seamless data integration and analysis, making it easier to interpret complex data sets.
Cost-Efficiency
Investing in the right DAQ equipment can lead to long-term cost savings by reducing the need for repeated testing and improving process efficiency.
Choosing the Right Data Acquisition Equipment
When selecting data acquisition equipment, consider the following:
Application Requirements
Define what you need the system to measure and the conditions under which it will operate. This will guide you in choosing the right specifications.
Budget Constraints
While higher-end systems offer more features, ensure that the equipment you choose fits within your budget while meeting your essential requirements.
Vendor Support
Work with reputable vendors who offer reliable support, as setting up and maintaining DAQ systems can be complex.
Scalability
Consider future needs. Investing in a scalable system allows you to expand your data acquisition capabilities without needing a complete overhaul.
Conclusion
Data acquisition equipment is a cornerstone of modern research and industrial processes. By understanding the key features and benefits, you can make informed decisions that enhance the accuracy, efficiency, and effectiveness of your data collection efforts. Whether you’re working in a lab, a factory, or out in the field, the right DAQ system can be a powerful tool in achieving your goals.
0 notes
Text
Watlow F4T - Controlling More than Just Temperature
The best controls and system management equipment oftentimes involves those that are compact, provide multiple benefits, and have incredible reliability under challenging conditions. The Watlow F4T temperature control is exactly that. Built with a rugged design and a versatility that has been hard to match or come close to via competition, the F4T continues to score best-in-class as a result, and it’s easier to use than earlier models thanks to an extremely intuitive touch panel displayed and contrasted in color thanks to a high-resolution display.

Of course, the Watlow F4T didn’t win its credentials by looking beautiful. It had to perform consistently as well. That’s made possible by the fact that the model provides users with an expanded digital display, dual USB host capacity, 100-240 VAC power connectivity, universal input design, real clock time and battery redundancy as well. With well over 40 different possible profiles, the Watlow F4T typically finds itself being applied in different processes in the same factory or facility on a regular basis.
Expanded Networking Capability
A key factor that directly influences the F4T receiving so many referrals from experienced system managers is the fact that the Watlow temperature controller is ideal for communications compatibility. Packaged with a standard bus as well as an ethernet Modbus TCP compatibility, the F4T can also be expanded on the input/output side, and it is incredibly easy to configure for custom needs. For systems that are built up over time, the F4Ts modular approach makes it ideal for add-ons and expansion in sync with build outs as well, including low level disruption in the interim.
Data Logging and Export
Metrics are also fully enhanced and advanced through the F4T. The model comes with built-in data loggers, trending, temp limits for bottom and top ranges, integrated timers, temperature PID and more. Most importantly, the ability to achieve all of this data is made possible by how easy it is to control and manage the Watlow F4T as well.
Exporting data from the F4T was well-anticipated in the latest design. Users will find that the file transfer out of the system for expanded data analysis is a snap. The F4T connects quickly to external readers, and it has additional options for plug-in modular integration as well. Because both the firmware and integrated software are installed with the expectation of expanded life and use, the F4T stands out where other options close-off, being one-use functional only.
Flexible Design Meets Custom Demands
Scalability is a particularly useful feature. With many industrial systems needing to last and more than pay back their initial capital investment, the ability to enhance, modify and upgrade is essential. The F4T is extremely flexible in this regard, providing both backwards compatibility with other Watlow equipment as well making retrofitting a snap with existing equipment. There's no heavy modification needed for physical cabinets either; the F4T works seamlessly with F4 cabinets and panels from previous installations.
Seagate Controls is your access point for the Watlow F4T. Combining both Watlow inventory as well as the on-hand expertise to help guide clients with planning, options, system design or revision, installation and troubleshooting, our specialists always go the extra mile that helps our partnership stand out versus other suppliers for temperature controllers. Call us today to get started; there's no pressure to make a decision. Most of our clients engage in a good amount of discussion before narrowing down exactly what is needed for their particular installation or upgrade. And because we're with you all the way through to support and maintenance, there's no worries about going too deep into a decision and having no help on how to move forward. Seagate Controls is always at your side.
Source URL:- https://toppostng.com/watlow-f4t-controlling-more-than-just-temperature/
0 notes
Text
What Should You Think About Before Purchasing a Digital Voice Logger?
There is no doubt that a large number of students and businesspeople use digital voice logs extensively. They're using it to make their operating system better. This kind of logger provides a longer recording time than a regular cassette in terms of duration. Another major benefit is that connecting it to personal computers is quite simple. In addition, it has a larger capacity for data storage than a standard telephone call recorder. Although the market offers a variety of these recorders, you should use caution when picking which one to buy for someone else. You need to be crystal clear about the kind of feature or product you're after.
Those who are interested in this can use internet resources to their advantage. You may find a lot of websites that will assist you in choosing the best option among the options available. You need to be more explicit about the product's characteristics and utility. After determining that the voice logger device has all the fundamental elements that are absolutely need to satisfy the demands of the modern workplace, you should choose it. When making a purchase, you need to pay attention to a few essential features.

The recording capacity of the devices should be checked first, as this can differ from one product to another. A limited number of products provide up to 200 hours of recording duration. The voice quality of the devices with longer recording times is, however, severely compromised. Therefore, if you value having high-quality audio, stay away from these recorders and choose instead from those with shorter recording times. Even though it would require extra room, it would enable you to achieve excellent outcomes.
It would also be a fantastic idea to check the device's data storage capacity. Business owners should take note of this fact as features with multiple functions might benefit them in various ways. In addition to audio recording, the device must be able to manage files and store large amounts of data. You also need to be aware of your digital voice logger's data recording capabilities. Features like an web browser display and voice activation are essential for the device. For the owner, these characteristics make the process of recording and later transcribing very easy and convenient. Additionally, you want to check for computer connectivity features. You can benefit from this function if you're willing to work from home.
Ultimately, it is imperative that you purchase a digital voice logger only after carefully weighing all of the above listed considerations.
With years of experience, Nirmal Sharma help people collect information on voice logger telephone call recorder, CRM and PRI related solutions. The author also writes on VoIP recording device, voice recording system and screen capture software including IT services, USB analog Voice Logger and Voice Logging Solution.
#voicelogger#buyvoicelogger#telephonecallrecorder#digitalvoicelogger#voiceloggerprice#voiceloggerdelhi
0 notes
Text
Everything you need to know about keyloggers: a complete guide

A keylogger, sometimes called a keystroke logger or keyboard capture, is a type of surveillance technology used to monitor and record each keystroke on a specific computer. Keylogger software is also available for use on smartphones, such as the Apple iPhone and Android devices. Monitor the activities on any Android device with these efficiently hidden keyloggers. If you are interested in keyloggers, we will walk you through all the information you need regarding keyloggers. So let’s start our journey through keyloggers.
What exactly is a keylogger?
A keylogger is a software or application that enables you to record every activity on a device on which it is installed. It is basically a form of malware or hardware that keeps track of and records your keystrokes as you type. It takes the information and sends it to a hacker using a command-and-control (C&C) server. A keylogger monitors and records such activities without the knowledge of the device user.
Why do you need a keylogger?
These are used to quietly monitor your computer activity while you use your devices as normal. Keyloggers are used for legitimate purposes like feedback for software development but can be misused by criminals to steal your data. The reasons for installing or using a keylogger may vary from person to person. Let’s explore some most common reasons for using keyloggers.
Parental control
Parents may want to protect their children from cyber crimes. Keyloggers allow parents to monitor their social media interactions, Geo-location, call details, web history, etc. All this makes keyloggers useful for parents.
Employee monitoring
Employers or business owners may also want to verify whether their employees are properly utilizing their working hours. They may also want to know if their workforce is honest enough for their organization. For this reason, employers also use such apps commonly.
Stealing info
Cyber criminals also use keyloggers to steal passwords, bank details, financial information, etc.
Types of keyloggers
A hardware-based keylogger is a small device that serves as a connector between the keyboard and the computer. The device is designed to resemble an ordinary keyboard PS/2 connector, part of the computer cabling or a USB adaptor, making it relatively easy for someone who wants to monitor a user's behavior to hide the device.
A keylogging software program does not require physical access to the user's computer for installation. It can be purposefully downloaded by someone who wants to monitor activity on a particular computer, or it can be malware downloaded unwittingly and executed as part of a rootkit or remote administration Trojan (RAT). The rootkit can launch and operate stealthily to evade manual detection or antivirus scans.
How to install a keylogger on your smartphone?
To install a keylogger on any Android device, you just need single-time physical access to that device. Most of the keylogger or spy apps are not available on Google Play. As a result, you must first enable app installation options from third-party sources. You need to install the app by permitting the monitoring of the phone. Once you do all this, you can use the keylogger account for necessary configurations, such as monitoring apps. This configuration will enable the app to run in the background and record all the activities. You can later log into the desktop version of this keylogger app and view all the details of the activities.
To sum up
This article helped you understand keyloggers and find the right one for your Android monitoring needs. Ethical and sensible use of a keylogger can help you safeguard your assets, whether it is about your kids or your organization.
You may also want to explore the best keylogger app for Android and iPhone.
1 note
·
View note
Text
Real-Time Monitoring with Graphtec Data Logger GL7000: Benefits and Advantages
Introduction
Real-time monitoring is critical in various applications, such as manufacturing, research, and quality control. Real-time monitoring provides immediate feedback and allows for timely intervention when anomalies arise. The Graphtec Data Logger GL7000 is a powerful tool for real-time monitoring, that offers numerous benefits and advantages over other monitoring solutions. In this article, we will explore the benefits and advantages of using the Graphtec Data Logger GL7000 for real-time monitoring.
What is the Graphtec Data Logger GL7000?
The Graphtec Data Logger GL7000 is a versatile data acquisition system that can collect and analyze data from a wide range of sources. The GL7000 offers high-speed sampling rates of up to 100 MS/s, and it can store data in various storage media, including USB drives, SD cards, and Ethernet. The GL7000 also offers multiple measurement channels, allowing users to connect various sensors and devices to collect data.
Benefits of Real-Time Monitoring with Graphtec Data Logger GL7000
Real-time monitoring with the Graphtec Data Logger GL7000 offers several benefits, including:
Accurate Data Collection
The GL7000 offers high-speed sampling rates, which ensures accurate and reliable data collection. The high-speed sampling rate ensures that no data is missed, even in applications with high-frequency signals.
Customizable Monitoring
The GL7000 offers a wide range of measurement channels and can connect to various sensors and devices, making it highly customizable for different applications. The GL7000 can also be programmed to trigger alarms and alerts when specific conditions are met, allowing users to take prompt action.
Data Analysis and Visualization
The GL7000 comes with powerful software that allows users to analyze and visualize the collected data. The software provides various analysis tools, including FFT analysis, envelope analysis, and correlation analysis, among others. The GL7000 software also offers customizable graphical displays, allowing users to view data in real-time and spot anomalies easily.
Remote Monitoring
The GL7000 can connect to Ethernet, allowing for remote monitoring from any location. Remote monitoring is particularly useful in applications where data is collected from multiple locations or in hazardous environments.
Advantages of Real-Time Monitoring with Graphtec Data Logger GL7000
Real-time monitoring with the Graphtec Data Logger GL7000 offers several advantages over other monitoring solutions, including:
High-Speed Sampling Rates
The GL7000 offers high-speed sampling rates of up to 100MS/s, making it suitable for applications with high-frequency signals. The high-speed sampling rates ensure that no data is missed and that the data collected is accurate and reliable.
Multiple Measurement Channels
The GL7000 offers multiple measurement channels, allowing users to connect various sensors and devices to collect data. The multiple measurement channels also allow users to monitor different parameters simultaneously, improving the efficiency of the monitoring process.
Scalable Solution
The GL7000 is a scalable solution that can be expanded to meet changing monitoring needs. Users can add more measurement channels, storage media, and devices to the GL7000, making it a cost-effective solution in the long run.
User-Friendly Software
The GL7000 software is user-friendly, making it easy for users to set up and configure the system. The software also offers various analysis tools and customizable graphical displays, making it easy for users to analyze and visualize the collected data.
Conclusion
The Graphtec Data Logger GL7000 is a powerful tool for real-time monitoring, offering numerous benefits and advantages over other monitoring solutions. The GL7000's high-speed sampling rates, customizable monitoring, data analysis, and visualization tools make it a versatile and efficient solution for a wide range of applications, from manufacturing to research and quality control. The GL7000's scalability also makes it a cost-effective solution in the long run, as users can expand it to meet changing monitoring needs.
Real-time monitoring is essential for ensuring the quality and efficiency of various processes, and the Graphtec Data Logger GL7000 provides an accurate and reliable solution for monitoring critical parameters. With its user-friendly software, multiple measurement channels, and remote monitoring capabilities, the GL7000 offers a comprehensive solution for real-time monitoring, allowing users to make timely interventions and improve the efficiency of their operations. Therefore, the Graphtec Data Logger GL7000 is a valuable investment for anyone looking for a robust and scalable solution for real-time monitoring.
0 notes
Text
Testing new environmental dataloggers: Pt. 1
Happy Preservation Week!
My name is Erin Fitterer and I am a third-year student at the Conservation Center at the Institute of Fine Arts, New York University, with a focus on objects and time-based media. Though I am now focusing on other materials, much of my pre-program experience before attending NYU was actually in paper conservation, and I’m excited to be able to work in a library again. This semester, I am working with Jessica Pace on a project involving the dataloggers used by the Barbara Goldsmith Preservation and Conservation Department to monitor collections storage spaces at Bobst Library.

Dataloggers are an important tool when it comes to the care of collections. A datalogger is a device that records data about its surroundings at a regular interval, allowing conservators to monitor the environment of a given room or area over a long period of time. Depending on how they are made, a datalogger can record a wide range of information about a space, including monitoring vibrations and light levels. As conservators, we are most interested in monitoring the temperature and humidity levels in locations where collections are stored. Previously, conservators from the Preservation Department have been using PEM2 dataloggers. These devices monitor both temperature and relative humidity. To access the data, a USB device must be inserted into each logger. Unfortunately, the PEM2 device is no longer being supported by its manufacturer. To ensure continued access to loggers that can be calibrated and updated, we set out to find a replacement.
The first step for replacing PEM2 dataloggers was research. We wanted to find a datalogger that was able to record similar information as the PEM2 devices (namely relative humidity and temperature). Technology has changed since the introduction of the PEM2 to the market. While being able to capture the data from each device with a USB is a straightforward process, newer models enable the data to be accessed via the library’s WiFi network from any computer without needing to go to the location of each datalogger. This would allow our staff to monitor the collection in real-time, without needing to physically access each device.
When considering what we wanted in our new dataloggers, we looked for loggers that met several criteria, including: wireless capability, unlimited software storage, visible display, and the ability to send alarms to our computer/phone. Ultimately, we decided to test out: Dickson DWE DicksonOne Display, Lascar High Accuracy Wi-Fi (no picture yet as we are waiting for it to arrive), and WirelessTag. These loggers, with exception of the WirelessTag (which has no display) met all of the criteria that we had listed above. During testing, we will be evaluating the type of power source of the datalogger (whether it needed to be plugged in or not, the average battery life, and so forth), the accuracy of the recorded temperature and relative humidity, and the ease of use of both the loggers and their software.



We decided to use saturated salt chambers to test the accuracy of loggers’ ability to detect relative humidity because each type of saturated salt solution has its own relative humidity (you can see a table documenting each relative humidity for its respective salt here). There are a number of recorded relative humidities for saturated salt solutions. We chose three salts for our testing chambers: sodium chloride (NaCl), RH 75.3%; magnesium chloride (MgCl), RH 32.8%; lithium chloride (LiCl), RH 11.3% . These three salts represent a broad range of relative humidities that will allow us to see how the devices perform under a range of conditions. To create the saturated salt solution testing chambers, we followed instructions posted on the Conservation Wiki written by Samantha Alderson and Rachael Perkins Arenstein. The lithium chloride and magnesium chloride were purchased from a chemical supply company. For the sodium chloride, we used Kosher sea salt purchased at a nearby grocery store. To create the chambers, we cut windows into three plastic food storage containers. Over each window, we taped a piece of Gortex.
To prepare the salt solutions, we researched how much salt needed to be added to the water in order to create a saturated salt solution. We found a few publications that provided the ratios of water to salt used to achieve a saturated salt solution. Using these publications as a guide, for each salt solution, we measured 100 mL of water into a beaker. This water was heated on a hot plate, though not allowed to boil. For each of the salt solutions, salt was slowly added and allowed to dissolve. Once dissolved, more salt was added to the solution. Once the salt no longer dissolved (that is, it appeared on the bottom of the beaker), the solution was removed from the heat and allowed to cool. The result was a thick slurry mixture that was subsequently poured into the plastic food storage container. Each container and its salt solution were placed in a larger air-tight container. Within these larger containers, the datalogger devices will be placed. We will provide an update once we complete our testing.




5 notes
·
View notes
Text
Documentation Gathering, Sanitization, and Storage: an excerpt from "A Public Service"

[Yesterday, we published my review of Tim Schwartz's new guide for whistleblowers, A Public Service: Whistleblowing, Disclosure and Anonymity; today, I'm delighted to include this generous excerpt from Schwartz's book. Schwartz is an activist whom I've had the pleasure of working with and I'm delighted to help him get this book into the hands of the people who need to read it. -Cory]
Collection
As you collect documents and bring new information to light, be aware that you are in an escalating digital arms race. There will always be new ways that data forensics can identify you, or uncover information based on data that you inadvertently leave in your files, or data that is retained in logs noting who has accessed what files on what network. Recently it was discovered that noise from electrical grids can be used to quite accurately pinpoint when, and potentially where, an audio recording was made. The best way to win this war—or at least to avoid becoming collateral damage—is to work outside the standard methods and find partners who have experience.
Of course, the actual collection of documents has changed dramatically over the years. In 1969, Daniel Ellsberg systematically removed documents, including the Pentagon Papers, from the RAND Corporation in his briefcase, taking them to an advertising agency where he (sometimes with the help of his 13-year-old son) photocopied them, one page at a time. Though this took enormous courage and psychological stamina—and in 1969 all that copying was certainly time-consuming and undoubtedly tiresome—it was also technologically straightforward and relatively safe. As long as the guards didn’t stop and check his briefcase, and as long as no one saw him remove and return the reports, Ellsberg could duplicate the papers undetected.
If Ellsberg was trying to do the same thing in 2019 with physical documents, he would have to be sure there weren’t cameras looking over his shoulder. He would have to make sure that the documents themselves didn’t have watermarks that would lead back to him. And he would have to make sure that the copying method didn’t log his activity. If Ellsberg’s 21st-century counterpart were to take digital documents, there would be many more potential technological risks and traps to avoid along the way.
Take Notes
Before you start collecting documents or even trying to tell anyone about the wrongs you want to expose, start documenting what you see. Jesselyn Radack, who heads the Whistleblower and Source Protection Program at ExposeFacts and has worked with Thomas Drake and Edward Snowden, says the first step is to “just keep your own little record at home in a little notebook.” This should be a notebook where you methodically record everything pertinent to the wrongs you want to expose: everything that you see, everything that you hear, and everything that you say. Do this as often as you can, the same day that incidents occur. Note the time and date of each occurrence. Above all, your notes should always include any complaints you raise and to whom, as well as any retaliation against you for doing so.
This approach to notetaking played a critical role in the big Russian sports doping scandal in 2016. Grigory Rodchenkov, the whistleblower and former doctor of the Russian Olympic team, took incredibly detailed contemporaneous notes that became compelling evidence. The notes included Rodchenkov’s interactions with Russian coaches, officials, and athletes, such as how and when he provided performance-enhancing drugs to athletes, and how the doping was hidden from Olympic observers and their drug tests. Aside from all of these incriminating notes, as the New York Times reported, Rodchenkov also noted his daily activities details such as “6:30, I took a shower, had a smoke, got ready, had hot cereal and farmer’s cheese at breakfast.” These seemingly trivial details helped convince the judges to allow the journal to be considered credible evidence in the court case.
The technology you use to take notes can either help or hinder those who might seek to access and/or destroy any information you have, depending upon your situation. You can use a physical notebook, good old pen and paper, or notes on an anonymous laptop or tablet. But be sure to stay away from making entries at work or on your personal computer unless you are highly technically confident of your computer’s security.
“Documentation is very important,” says Debra Katz, founding partner of Katz, Marshall & Banks, LLP and the lawyer who represented Christine Blasey Ford when she was called to testify during the Kavanaugh confirmation hearings. “We increasingly have people who show up with videotapes of harassment. I’ve had clients who’ve had their iPhone rolling as their employer, predictably, would come in and do back massages or make sexual remarks.” Logs of text messages on phones or even recordings of interactions can be crucial to demonstrating that harassment is taking place. Save logs of all of your conversations and interactions, because you never know how they might prove useful later on.
The text messages sent by Mike Isabella and partners to Chloe Caras (who was also represented by Debra Katz) were used as evidence in the lawsuit that eventually took down Mike Isabella Concepts restaurants for sexual harassment. If you are going to attempt to record interactions as evidence, be sure that you are aware of the relevant recording laws. In some states and countries, you must inform the other party that you are recording and you must obtain their consent to be recorded. These laws are collectively known as two-party consent laws. Do more research into your context before you start shooting video or recording audio as documentation. You don’t want your evidence thrown out of court. You don’t want to be sued for releasing the recording. The Reporters Committee for Freedom of the Press is a good place to learn more about two-party consent laws in the United States.
Recommended Collection Approach
In New York City in 1953, a newspaper boy was finishing his day, jingling his coins around, when he noticed that one nickel felt lighter than the rest. When he dropped the coin on the floor, it split open, revealing a tiny photograph with numbers. This turned out to be microfilm that was destined for Soviet spy Reino Hayhanen. In 1957, Hayhanen defected to the U.S., where he exposed the spycraft of the Soviets to the FBI. This included the use of microfilm and dead drops for communication. Though this example may seem far from the world of computers and smartphones, taking photos of documents with microfilm is much safer than taking the actual documents, in the same way taking a digital photo is safer than copying the digital document. In such a case, there is far less potential for a log of the interaction.
The current best way to gather information is by taking pictures of documents or computer screens using a pseudonymous digital device. This method effectively circumvents all of the normal digital surveillance systems that might come into play when you copy data off of a network or onto a USB stick (e.g., logs of the copying or digital watermarking). It also circumvents any logging software that may be installed on your computer. Company or government tracking software can record the actions of taking screenshots or other mouse and keyboard actions. Evidence from one of these loggers was used by the FBI against Terry Albury, an FBI field agent who was sent to jail for disclosing classified information to The Intercept. In an affidavit in support of the search warrant, the FBI cited a number of facts, including that Albury had “conducted cut and paste activity” while viewing one of the classified documents. This fact could only have been gathered by latent logging software installed on his computer or built into a viewing program. By skipping digital copying or screenshotting, and instead simply taking a picture of the computer screen, you can circumvent some of these monitoring systems. Of course, if you are logged in and have a document open, you should assume that there is a log of the access as well.
Keep these tips in mind:
Only use a pseudonymous device for taking photos; never use your personal or work device.
Use a small tablet with Wi-Fi turned off instead of a phone; this way there will be no location information stored as metadata in the photos.
Make sure the photos don’t have any identifying information in them; this could be your hand, your reflection on the computer screen, images of your office, or other identifying information or marks on your computer screen.
Be sure to check the images afterwards for any metadata or accidental information captured, and make sure to sanitize the images if necessary.
Audio and video recordings can potentially replace taking photos, but these types of files can be harder to sanitize.
Be sure there aren’t video cameras that could capture you in the act of taking photos.
Microdots
Do not trust printers. Color laser jet printers and copiers embed metadata in the documents that they print in the form of microdots, which are patterns of tiny yellow dots that are almost invisible to the naked eye. These dots encode information, similar to QR codes. This includes the printer’s serial number, the time and date, the network address, and potentially other information. This data can be used to pinpoint when and where documents were printed, and potentially by whom. If you want to find out more on the topic, research the terms “printer steganography” and “machine identification code.”

Regular and enhanced image of a printed page from an HP Color LaserJet 3700 showing yellow microdots. Photography by Florian Heise, Druckerchannel.de, in the public domain via Wikimedia Commons.
Copying Digital Files
It is nearly impossible to copy files to a USB stick without leaving a trace, particularly if you are using log-in credentials at work or on a company device. Computers and networks are built to track and log file access, transfers, and printing. Do not try to make a digital transfer or to copy information onto a USB stick at work unless you can be positive that this process isn’t being logged somewhere. Use the Tails operating system, or a computer that is offline, when you copy data.
If you must copy digital files, be sure to collect all your information as anonymously as possible: use a shared computer at work (not your own). Do not use your own login credentials. Also, consider your physical location. It is best not to attempt this in your own office, for instance. Gathering information in the office will become even less viable as technology and employee surveillance software evolves.
Aside from the issues around copying digital files, some sensitive documents (particularly from government agencies) come with “phone home” beacons embedded in them or with digital rights management built in, making it impossible to view or print documents if you aren’t logged in. This could be a remote image or link embedded in a document, such that when you view the document, the image pings back to a server owned by the government or creator of the document. This allows the creator to see the IP address and potentially more information about you as a viewer. Microsoft files such as Word documents have been known to have “locating beacons” placed within them. PDFs may also include this type of beacon, though Adobe now tries to notify users before documents call a remote server. To combat this type of tracking, either convert a document to a safe format such as plain text with the command line, or view a document on a computer that is “air-gapped,” meaning that it is not connected to the internet. Make it impossible for your adversary to know you have the documents.
Uniqueness and Backflushing
If you are one of a limited number of individuals with access to the information you are releasing, then no matter how careful you are, it will be easy to trace you. This was the case with Reality Winner. In the criminal complaint filed against Winner, the FBI noted that only six individuals had accessed the document that was disclosed to The Intercept. When this document showed up on the website, the FBI had six individuals to start investigating, including Winner. Her unique trail quickly made her the most likely suspect. One way to combat uniqueness is by increasing the number of individuals who have access to a document before it is released.
Danielle Brian, executive director of the Project on Government Oversight, described a method that has been in use in D.C. for years: “backflushing.” Before disclosing a document, send it through official channels to as many legitimate places as possible. For example, include the document in a report and send the report to other departments. This makes it so others have the document as well, vastly reducing the uniqueness of your connection to the document. When you disclose the information later on, it will not be clear that you were in any way connected to it.
Another way to combat uniqueness is by gathering the data through a shared digital account, e.g., if someone else is logged into a computer and you copy a file while they are logged in, the document-gathering will be connected to them, not you. Of course, this should be done carefully and ethically, so as not to inadvertently cast blame on someone else. If possible, it’s better to hijack a shared network account. So consider how unique the connection between the information and your identity might be. There is protection to be gained by hiding in the crowd.
Theft and Misfiling
Corporations sometimes lash back at whistleblowers by filing criminal charges for theft of company property. So be aware that by taking documents off company property, you may open yourself up to a legal battle. This was one reason that SOC, a government security contractor, gave for firing Jennifer Glover, a security guard who had been sexually assaulted and harassed at work. Her termination letter stated that Glover had used her smartphone to take a photograph of the daily schedule, an act that they viewed as justifying her termination.
As an alternative to taking physical or digital documents, consider the misfiling technique. Hide copies of documents at work, either by misnaming digital files or by storing physical copies or USB sticks somewhere at work. In the future, you can “stumble upon” the copies, providing investigators with the information. They, not you, would then be removing property from company premises. The bottom line is that it might be helpful to have a backup copy of any important material stashed somewhere at work.
Sanitization
Sanitization is the process of removing, concealing, or cleaning up information in documents before you give them to someone else. Whether the documents you’re dealing with are physical or digital, images or videos, the same general process applies: you should overwrite, obscure, or remove any sensitive information. This process is ubiquitous the world over in redacting classified material to prepare it for release to the public. When attempting this, imagine that you are in a heist film: be meticulous, wear gloves, wipe down surfaces to remove fingerprints, and don’t leave anything that contains your DNA.
For those who are trying to disclose information, the process of sanitization is a little more complex, but there are two goals: 1) the removal of any information that could identify you, such as fingerprints, email addresses, or unique watermarks on documents; and 2) the removal of sensitive information that might harm someone else or have undue consequences if released, such as any company or government secrets or any personally identifiable information. This is where ethics and judgment come into play. Who would be harmed if this information were released? You don’t want to accidentally victimize (or revictimize) a colleague, accidentally reveal personal information that could compromise one’s reputation, or put a field agent in harm’s way.
To sanitize physical items with nonporous surfaces, such as USB sticks or hard drives, wipe them down with a cleaning product and towel. Paper documents and other porous surfaces are more difficult to sanitize. There are a number of techniques for attempting this, but most involve using an eraser and potentially a cornstarch mixture to remove any oils left by fingerprints. If you are providing someone with a device such as a hard drive, remove any serial numbers or identifying information that would make that product traceable, and of course, be sure to pay cash when buying any hardware that you might use. If you must provide physical documents, redact them first with a black marker or white-out and then photocopy them, providing a redacted copy instead of the original.
For digital documents, the process of sanitization can be broken down into two strategies: 1) redaction, the process of obfuscating information within a document; and 2) metadata removal, the process of deleting identifying traces from the document.
Text
Any text-based document (rich text files, DOC and DOCX formats, CSVs, Microsoft Excel files, PowerPoint files, Adobe InDesign files, etc.) should first be converted to a PDF. This can be done on most computers with either “print to PDF” or “export to PDF” functionality. The PDF should then be opened, and each page should be exported as an image and then redacted in image-editing software. Draw black boxes over areas of sensitive or identifying information in the images. Note: If you try to redact the documents from within the PDF, it will be done in layers, leaving the actual data underneath the black boxes. This will not technically remove the sensitive information. Similarly, it is important to use only image formats that do not include layers. If layers are included, someone can later remove the redaction layer and see the sensitive information underneath. JPG is a great image format to use, as it cannot save layers. After all of the images have been edited, they should be either recombined into a new PDF using a PDF viewer or given to someone as a set of images.
An alternative option is to use PDF Redact Tools, which automates those processes for you. It is currently available on Linux or macOS and comes bundled inside the Tails operating system.
Images
Images should be redacted just the same as text documents. Save them in a format without layers such as a JPG. Draw black boxes over any portions that need to be removed, then save them.
Video and Audio
Redaction of video and audio files can be a bit trickier, but the same basic process of obfuscating information applies. For videos, open them in a video editing program and either delete portions of the video or add black boxes over sensitive pieces. Then export the edited video. Audio files should be edited in an audio editor (Audacity is a good free choice), and portions of the recordings can be deleted or replaced with a standard sine wave tone (like a censorship bleep).
Remember, though, that there may be other information in audio and video recordings that isn’t obvious at first glance. Is there background noise or imagery that can be analyzed to determine the time and place it was taken? Are there reflections or other subtle pieces of data that could compromise you or someone else? Be very careful when it comes to audio and video, because so much information is contained in each file that it can be hard to think of every single thing that should be redacted.
Metadata Removal
Of course, if you are simply trying to get a video out, but trying to make it less obvious who it was shot by, removing the underlying capture information might be all that’s needed. This is where removing metadata comes into play.
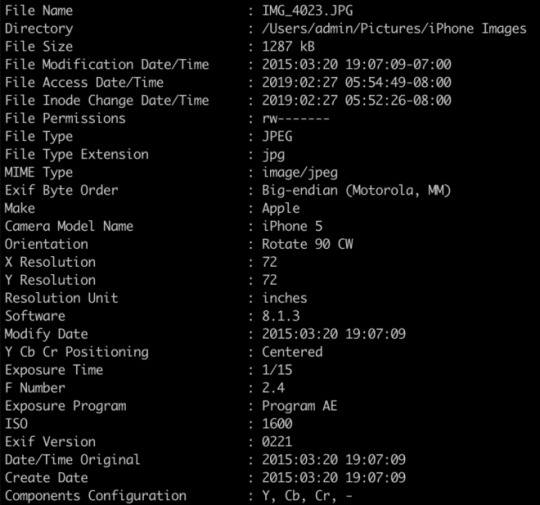
Example of image meta data created by an iPhone
The image above is just a selection of the metadata produced by one photo taken with a smartphone. The metadata contains the model of the phone, the time it was taken, and possibly the location of the phone at the time of capture (if GPS location was enabled). This data needs to be removed if you are trying to make the photo, video, or any other type of file untraceable.
Before anything else, check the filename for anything that could identify you or your means of creating the image. If you have any doubt—rename it.
All digital files inherently contain some distinct information that identifies them: filename, creation date and time, last modified date and time, and file size. Some digital file formats contain even more information. Microsoft Word documents, for example, are known for automatically saving additional metadata, such as the authors who worked on the document and the names and locations of the computers where the file was saved. Unfortunately, with these documents and particularly with proprietary file formats, it might be difficult or near-impossible to remove all pieces of metadata. Instead, convert proprietary formats to simple open-source formats that have consistent metadata formatting.
Some file formats use standard data wrappers to store metadata, such as EXIF (exchangeable image file format) or XMP (Extensible Metadata Platform). These are used for almost all image formats and PDFs. By converting other documents into these formats, it becomes much easier to delete metadata and know that it is really gone.
To actually remove metadata from an image, a PDF, or a video file, open it with its corresponding editing software and look for options such as “Properties,” “Inspector,” or “Document Inspector.” This should open up a dialog with a list of all of the metadata fields and entries. Delete them all. You will also want to research format-specific metadata removal methods for specific file types. Audio and video files, such as MP3s or MP4s, for example, can have proprietary ID3 tags embedded within them—such as PRIV frames—that make it near impossible to know if they have been sanitized.
Alternatively, a number of applications can scrub metadata from particular file formats. Several applications can remove EXIF data from images, but the Android application “EZ UnEXIF Free (EXIF Remover)” is especially useful for those communicating via an anonymous smartphone or tablet. This application removes all EXIF data, including geolocation, from photos taken with an Android device.
The Metadata Anonymisation Toolkit (MAT) provides a simple interface for stripping metadata from a number of formats, including PNG, JPEG, PDF, MP3, and Microsoft Office Document formats. MAT comes installed on Tails. However, MAT currently hasn’t been updated since January 2016, essentially making it abandonware. Fortunately, MAT2, the replacement for MAT, is under active development and currently in beta. This is a great tool that can be used to sanitize a variety of files, but please check on its current development status online before using it.
Storage
Be cautious about where you store documentation. Never store documentation at work, unless you are following the misfiling method mentioned previously. You may feel that your desk or office is a safe space, but it isn’t. You can consider storing documents at home, but this is an obvious choice for all concerned. In many cases, those who are trying to disclose information have had their houses ransacked and searched by their adversaries, both legally and illegally. If a subpoena is filed, information in your home will not be protected.
A good strategy is to either store documents outside your home or office or give a backup copy of what you will be revealing to a trusted person for safekeeping. Daniel Ellsberg gave a copy of a classified nuclear study to his brother, who hid the documents under a large gas stove in a garbage dump. Unfortunately, while this protected them for a while, the documents were ultimately destroyed by water damage, and Ellsberg spent years trying to reconstitute the information they contained. Instead of your brother, choose a lawyer. In the United States, information stored with your attorney may be protected from search and seizure through attorney-client privilege. Of course, there are exceptions to this, which was the case in the raid on the office of President Trump’s former attorney Michael Cohen. If investigators can make the case that attorney-client privilege is being used “in furtherance of a contemplated or ongoing crime or fraud,” then they will be able to search a lawyer’s office under the crime-fraud exception.
All digital documentation should be stored on either encrypted USB drives or on an encrypted pseudonymous device, such as an encrypted tablet or a Tails USB drive. Documents should never be stored in the cloud or on a personal computer or device.
Excerpted from A Public Service: Whistleblowing, Disclosure and Anonymity published by O/R Books. © 2019 Tim Schwartz
https://boingboing.net/2020/01/09/documentation-gathering-sanit.html
99 notes
·
View notes
Text
Voice Logger Manufacturers in Mumbai
In the digital age, communication is more than just a connection—it's a strategic business asset. Whether it’s a phone conversation with a customer, a deal with a supplier, or an internal team call, recording and analyzing conversations can provide crucial insights. That’s why the demand for Voice Logger Manufacturers in Mumbai is steadily on the rise, especially among companies looking for secure, reliable, and affordable solutions.
Mumbai, being the commercial capital of India, is home to thousands of businesses across various industries. From booming startups to large corporations, everyone relies on voice communication. And with growing regulations, customer service expectations, and competition, voice logging systems are becoming an essential tool to stay ahead.
What is a Voice Logger?
A voice logger is a digital system or device that records voice calls and stores them for future reference. These systems are often used in call centers, banks, hospitals, law enforcement agencies, and customer support operations.
Modern voice loggers can record analog, digital, or VoIP calls. They are designed with powerful features such as time-stamped recordings, caller identification, call tagging, encryption, and cloud backup. When sourced from experienced Voice Logger Manufacturers in Mumbai, these tools offer unmatched reliability and performance.
Why Do Businesses Need Voice Loggers?
Businesses that engage in regular voice-based communication need voice loggers for several reasons:
Quality Control: Supervisors can review calls to monitor agent performance and improve service.
Dispute Resolution: In case of customer complaints or legal issues, recordings serve as concrete evidence.
Compliance: Many industries require call recording to comply with legal and regulatory standards.
Training & Coaching: Voice logs are excellent resources for onboarding new employees and refining scripts.
Data Analysis: Companies can analyze patterns and customer behavior from call data.
For these reasons and more, the demand for advanced systems from Voice Logger Manufacturers in Mumbai is higher than ever.
Why Choose Aria Telecom?
When it comes to professional-grade voice logging systems, Aria Telecom stands as a leading name in India. With over 20 years of experience, Aria has developed cutting-edge solutions tailored to Indian businesses.
Aria Telecom offers:
USB, PRI, and VoIP Voice Loggers
Multi-channel support for recording up to 128 lines simultaneously
Software with user-friendly dashboard for easy access and retrieval
Live call monitoring, reporting, and analytics tools
Customizable solutions for banks, call centers, law enforcement, and healthcare
Their devices are designed with the end-user in mind—easy to install, simple to use, and loaded with features.
Features of a Good Voice Logging System
When selecting a product from top Voice Logger Manufacturers in Mumbai, look for:
High Audio Clarity – So you don’t miss any details in conversations
Secure Data Encryption – To protect sensitive information
Call Search & Filters – Find recordings quickly using caller ID, date, or keywords
Long-Term Storage – Backup options for archiving calls for months or years
Web Access & Remote Monitoring – Review calls anytime, from anywhere
Aria Telecom checks all these boxes and provides complete after-sales support to ensure your system keeps running smoothly.
Where Are Voice Loggers Commonly Used?
Voice loggers are highly versatile and are used in many industries:
Call Centers – For tracking customer service quality and improving processes
Financial Institutions – To meet RBI guidelines and for dispute resolution
Healthcare Facilities – For recording patient interactions and appointment scheduling
Police Control Rooms – For logging emergency and complaint calls
Legal Firms – To maintain call records for sensitive cases
Any organization that relies on voice communication can benefit from a reliable voice logging solution.
#VoiceLoggerMumbai#AriaTelecom#CallRecordingSolutions#BusinessCommunicationTools#TelecomTechnologyIndia
0 notes
Text
Ubidots + ESP32- Predictive Machine Monitoring
Predictive analysis of machine vibration and temp by creating mail events and a record of vibration in google sheet using Ubidots.

Story
Predictive Maintenance and Machine Health Monitoring
The rising of new technology i.e, the Internet of Things, heavy industry has started adopting sensor-based data collection to solve its biggest challenges, principal among them process downtime in the form of shutdowns and process delays. Machine monitoring also called predictive maintenance or condition monitoring is the practice of monitoring electrical equipment through sensors in order to accumulate diagnostic data. To achieve this, data acquisition systems and data loggers are used to monitor all kinds of equipment, such as boilers, motors, and engines. Following condition are measured:
Temperature and Humidity Data Monitoring
Current and Voltage Monitoring
Vibration Monitoring: In this article, we will read Temperature, vibration and publish the data in Ubidots. Ubidots supports graphs, UI, notifications, and emails. These features make it ideal for predictive maintenance analysis. We will also get the data in google sheets which will make predictive maintenance analysis more easier.
Hardware:
ESP-32
IoT Long Range Wireless Vibration And Temperature Sensor
Long-Range Wireless Mesh Modem with USB Interface
Software Used:
Arduino IDE
Ubidots
LabView Utility
Library Used:
PubSubClient Library
Wire.h
Arduino Client for MQTT
This library provides a client for doing simple publish/subscribe messaging with a server that supports MQTT
For more information about MQTT, visit mqtt.org.
Download
The latest version of the library can be downloaded from GitHub
Documentation
The library comes with a number of example sketches. See File > Examples > PubSubClient within the Arduino application.Full API Documentation.
Compatible Hardware
The library uses the Arduino Ethernet Client api for interacting with the underlying network hardware. This means it Just Works with a growing number of boards and shields, including:
Arduino Ethernet
Arduino Ethernet Shield
Arduino YUN – use the included YunClient in place of EthernetClient, and be sure to do a Bridge.begin() first
Arduino WiFi Shield - if you want to send packets greater than 90 bytes with this shield, enable the MQTT_MAX_TRANSFER_SIZE () option in PubSubClient.h.
Sparkfun WiFly Shield – when used with this library
Intel Galileo/Edison
ESP8266
ESP32The library cannot currently be used with hardware based on the ENC28J60 chip – such as the Nanode or the Nuelectronics Ethernet Shield. For those, there is an alternative library available.
Wire Library
The Wire library allows you to communicate with I2C devices, often also called "2 wire" or "TWI" (Two Wire Interface), can download from Wire.h
Basic Usage
Wire.begin()Begin using Wire in master mode, where you will initiate and control data transfers. This is the most common use when interfacing with most I2C peripheral chips.
Wire.begin(address)Begin using Wire in slave mode, where you will respond at "address" when other I2C masters chips initiate communication.
Transmitting
Wire.beginTransmission(address)Start a new transmission to a device at "address". Master mode is used.
Wire.write(data)Send data. In master mode, beginTransmission must be called first.
Wire.endTransmission()In master mode, this ends the transmission and causes all buffered data to be sent.
Receiving
Wire.requestFrom(address, count)Read "count" bytes from a device at "address". Master mode is used.
Wire.available()Returns the number of bytes available by calling receive.
Wire.read()Receive 1 byte.
Steps to send data to Labview vibration and temperature platform using IoT long-range wireless vibration, temperature sensor and long-range wireless mesh modem with USB interface:
First, we need a Labview utility application which is ncd.io Wireless Vibration and Temperature Sensor.exe file on which data can be viewed.
This Labview software will work with ncd.io wireless Vibration Temperature sensor only
To use this UI, you will need to install following drivers Install run time engine from here 64bit
32 bit
Install NI Visa Driver
Install LabVIEW Run-Time Engine and NI-Serial Runtime
Getting started guide for this product.
Uploading the code to ESP32 using Arduino IDE:
Download and include the PubSubClient Library and Wire.h Library.
You must assign your unique Ubidots TOKEN, MQTTCLIENTNAME, SSID (WiFi Name) and Password of the available network.
Compile and upload the Ncd__vibration_and_temperature.ino code.
To verify the connectivity of the device and the data sent, open the serial monitor. If no response is seen, try unplugging your ESP32 and then plugging it again. Make sure the baud rate of the Serial monitor is set to the same one specified in your code 115200.
Serial Monitor Output:

Data on serial monitor of Arduino IDE.
Making the Ubidot Work:
Create the account on Ubidot.
Go to my profile and note down the token key which is a unique key for every account and paste it to your ESP32 code before uploading.
Add a new device to your Ubidot dashboard name ESP32.


Now you should see the published data in your Ubidots account, inside the device called "ESP32".
Inside the device create a new variable name sensor in which your temperature reading will be shown.


Now you are able to view the Temperature and other sensors data which was previously viewed in the serial monitor. This happened because the value of different sensor readings is passed as a string and store in a variable and publish to a variable inside device esp32.
Create a dashboard in ubidots.

Go to data select dashboard and inside dashboard create different widgets and add a new widget to your dashboard screen.
OUTPUT
Now as the temperature/vibration increases and decreases new data available inside the various variable.

Creating Events in Ubidots

1) Select Events (from the Data dropdown).

2) To create a new event, click the yellow plus icon in the upper right corner of the screen.
Types of Events: Ubidots support already integrated events to allow you to send Events, Alerts, and Notifications to those who need to know when they need to know. Ubidots' prebuilt integrations include:
Email notifications
SMS notifications
Webhook events - learn more
Telegram notifications
Slack notifications - learn more
Voice Call notifications - learn more
Back to Normal notification - learn more
Geofence notifications - learn more
3) Then choose a device and associating variable that indicates the devices' "values".

4) Now select a threshold value for your event to trigger and compare it to device values and also select time to trigger your event.
5) Establish and configure which actions are to be executed and the message to the receiver: Send SMS, Email, Webhooks, Telegrams, Phone Calls, SLACK, and webhooks to those who need to know.

6) Configure the Event notice.

7) Determine the activity window the events may/may not be executed.

8) Confirm your Events.
The output of Event in Your Mail:

Export Your Ubidots Data to Google Sheets:
In this, we can extract the data stored in the Ubidots cloud for further analysis. The possibilities are enormous; for instance, you could create an automatic report generator and send them to your customers every week.
Another application would be device provisioning; if you have thousands of devices to deploy, and their information is in a Google Sheet, you could create a script to read the sheet and create a Ubidots data source for every line on the file. Steps to do this-
Create a Google Sheet and add two sheets to it with these names:
Variables
Values
From your Google Sheet, click on "Tools" then "Script Editor...", then "Blank Project".
Open the Script Editor.

Add the code below (in the code section) to the script Script.
Done! now open your Google Sheet again and you'll see a new menu to trigger the functions.

Result:

1 note
·
View note