#Windows remote control for mac
Explore tagged Tumblr posts
Note
*tiptoes into ask box*
I'm almost afraid to ask, but what exactly is Rhythm Doctor?
(UNSKIPPABLE CUTSCENE INITIATED)
OKAY SO. be not afraid :) come here this is a completely normal hospital
basically rhythm doctor is a game where you must defibrillate patients in time with the rhythm! it's not quite as hard as rhythm heaven or anything at least IMO, but it's really addictive and i love the characters a lot!!! there's a lot of cool gimmicks and stuff but all you need is one button so you don't have to grapple with remembering controls along with reaction time!!! you can also have accessibility modes like very easy and unmissable which i appreciate a lot as a particularly shitty gamer
you are working with an overworked skeleton crew comprised of the computer nerd ian, the doctor who mainly does in-person check-ups-- Ada Paige-- and their boss who sits and stares at a clipboard while judging you at every turn, Dr. Edega! you are meanwhile a remote intern who's job is to press the button in time with the music.
there are multiple jokes about the fact that you are only ever seen as a hand. people just start assuming you are only a hand.
the rhythm doctor program means that you are canonically using the game's mechanics to defibrillate all the patients and yes their heartbeats are just like that. they sync up music to the erratic heartbeats in order to soothe arrhythmia and get people back on their feet!
the characters interact with each other in a way that genuinely makes the hospital feel alive and it's just so nice to watch them interact together, especially when the one-off characters just stick their heads into the conversation randomly. my favorite is absolutely samurai.

look at this guy. look at him. he's great. he parties at clubs and plays baseball. why is he dressing up in this in modern day? why does he never take the armor off? who knows but he's silly
you're also facing off with a virus named Connectifa Abortus that uses advantage of your remote connection, and jams your signals because it can do that. it just can. also it is possibly sentient and very malicious
that's the spoiler free synopsis but you should..... buy it on steam................................... now. :)
it's only 16 bucks and works on windows, mac, and linux!!! it also is early access so chances are by getting it early you're getting it for a cheaper price!!!!!!
PLUS if you've ever heard of A Dance Of Ice And Fire it's the same ppl. 7th beat games. it's so good. play it.
#tommy's foolery#rhythm doctor#tommy's rhythm room#if you don't mind a little bit of spoilers you can also check out my OC avec!!!!!!!!#i've been rotating xem agressively. living robot#there's 5 birds in the hospital. two guys with swords. two people who are tied by the Green Line of Holy Shit That's My Heart Rate WTF#a girl who literally just likes to draw. political statements about how terrible the government is towards healthcare workers#intimidating villain that we don't know the face of yet. a guy who nearly dies on a train. lofi coffee addict#Nicole Ting who is addicted to nicotine and can't stop smoking. Samurai Dubstep. guys having a crisis about their self worth#also a giant friendship group of a whole hospital that will drag you in whether you want it or not#they're all friends you have no choice but to join the friendship hospital
25 notes
·
View notes
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
An ode to the iRiver iHP-120
For whatever reason, I've found myself deeply nostalgic for high school as of late. And for me, that is intractable from nostalgia for what is perhaps the peak mp3 player ever made:

The iRiver iHP-120 was released in 2003, my sophomore year of high school, and it changed my life. This thing held an astounding 10GB of music—for comparison, most mp3 players at the time were flash based, and held 128 or 256 MB of music. The only big competitor at the time was the 1st generation iPod, a mac-exclusive device that transferred data over firewire and had to be synced using the fledgling iTunes. Juxtapose that to iRiver, who took what I like to call the "we don't give a fuck" approach:
When you plugged in the iHP-120 with USB 2.0, it just showed up as an external hard drive—you could throw whatever you wanted on there. Naturally, it could read mp3 files, but this thing introduced me to the world of audio codecs and processing in a way nothing could have prepared me. WMA files worked fine (a big deal at the time because of DRM issues, during the heyday of KaZaA and Limewire). You want to play uncompressed .WAV files? No problem, put them on there. FLAC files? Absolutely, let your audiophile freak flag fly. Fucking OGG Vorbis files played on this thing. Hell, you could put text files on here and read them.
(The firmware for these was also basically open-source, and people did even crazier stuff with them. By the time I retired my player, it could do gapless playback, crossfading, 10-band equalizing, normalization and more. I think I also changed the boot screen to a picture of Sailor Moon.)
But the magic didn't end at uploading music to the iHP-120—controlling this thing was more intuitive than any other device around at the time. All of your music was displayed on the player in whatever folder structure you loaded onto the device—navigating the music was as simple as using Windows Explorer. You had your standard play/pause, skip forward/back and volume controls on the front joystick, but what are the other buttons for?
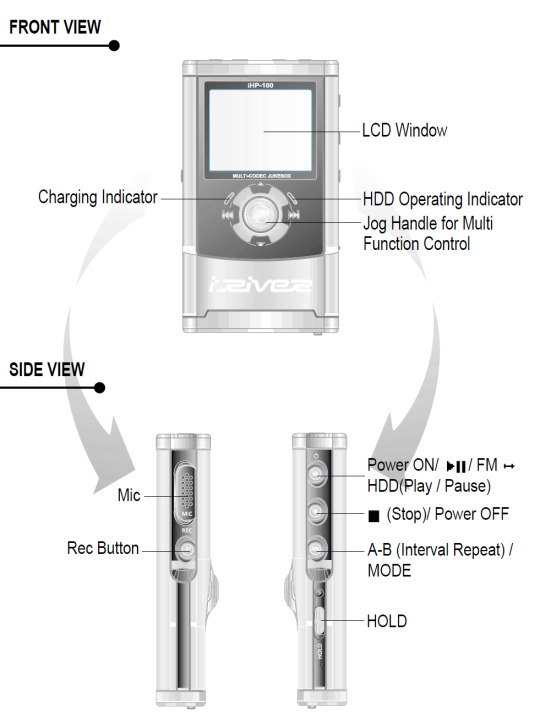
Yeah. This thing was also a portable recorder. At anytime you could just hold down the Rec button and start recording with the onboard mic, or using an external input (more on that later). On the right side, an A-B Interval control. You ever wanted to just listen to one part of a song on repeat to learn the lyrics? Just hold down the button. Lastly a hold switch to disable control inputs while it was in your pocket—no accidentally pausing the music.
Okay, back to the external input mentioned before. The top of the iHP-120 is wild.

The top I/O panel of the iRiver iHP-120, with 4 jacks.
From right to left, you have a 3.5mm headphone jack (naturally), a 2.5mm microphone jack, the remote control port (more on this in a bit), and in white you have Line In/Out jacks which you could use to record as well as just plug in a second pair of headphones for a friend—jacks which support both 3.5mm analog input, as well as 3.5mm TOSLINK optical cables.

The TOSLINK 3.5mm male plug. A plug I only ever encountered on this device and the Sound Blaster X-Fi Titanium, a sound card I wrote a review of in 2009 which seems to still be up at PC Gamer and reading it now I don't know how any of my writing was ever published, let alone in print.
Chances are good you've never encountered this, it's phenomenally uncommon, and TOSLINK as a whole largely died with the emergence of HDMI—but this fucking mp3 player could both record and transmit fiber optic audio in uncompressed stereo or lossy 7.1 surround sound. In high school, I would plug the iHP-120 into our home theatre and listened to Porcupine Tree's Stupid Dream on repeat (side tangent, I'm pretty sad 5.1 album recording never really caught on, but the Dolby Atmos music format is better in every way, and I'm grateful Apple is bringing it into the mainstream).
"Okay, so we have an music player/text reader/voice recorder with optical audio, and basically every codec under the sun, what else could you go on about Erika?"
-you, the person reading this
THE REMOTE
Let me take you back to 2003. I was a depressed theatre kid teenager who would listen to Rooney on repeat on my Koss UR40s while crying over a girl who wanted nothing to do with me.

The Koss UR40 Headphones I wore like a fashion accessory everyday.
The other thing I wore everyday besides those headphones? Baggy cargo pants (it was acceptable at the time, I swear). Inside the right cargo pocket was my iRiver iHP-120, and clipped to the velcro flap of that cargo pocket was the iHP-115R remote control.

The iHP-120 remote unit
Every function of the iHP-120 could be controlled from this little fucker. Play/pause and stop buttons. Volume, skip track and recording are all here on rocker switches. You could even change the fucking bitrate of playback on this little thing, all without taking the actual mp3 player out of your pocket because the LCD screen on the remote has all the same info you'd get on the main unit.
The remote itself connected to the iRiver with that big plug you can see in the picture above (shamelessly stolen from Nathan Edwards who I worked with at PC Gamer in the late 2000s and only while writing this post discovered has already written a much more professional ode to the beauty of the iHP-120 this year).
You would plug your headphones into the remote, (or in my case you could also plug in your 1988 Chevrolet 2500 suburban's tape deck adaptor and have controls at your fingertips. No more distracted driving).

An image of a 1988 Chevorlet 2500 diesel Suburban. Not super relevant but god I miss my high school suburban. We would take the rear and middle benches out and put a queen-size mattress in the back, which 9 of my friends would ride on as we went to Little Caesar's for lunch. Also, cars just looked way fucking better back then.
I think I'm about done waxing nostalgic, but I really do miss the days of discrete devices—I kind of find myself fighting back against my smartphone. I have a camera I carry around, a pen and paper planner and writing notebook, and a kindle for reading. There's something appealing about not having my phone be my access to music either—rather, having a device that I just threw my music on and it plays it really well was rad. The iHP-120 was really fucking rad.
12 notes
·
View notes
Text
How to easily stream your (New) 3DS to a PC
For a long time, capturing footage from a 3DS was a pain - streaming the 3DS screens either required a hardmod to install a capture card (which, if you can, should still do if possible), or use one of the several wireless methods (NTR CFW and HzMod) that gave poor results, especially on Old 3DS.
Today, thanks to the effors of zbash92, there is now a way to stream the New 3DS display to your computer with actually decent picture quality and low latency!
youtube
New NTR CFW test done back when it was firstly released
Here's a few applications of streaming your 3DS to a computer:
Playing on a bigger screen
Recording footage of 3DS games
Capturing audio for OSTs or music you made on 3DS
Below is a guide to setting everything up, including audio capture.
Requirements
A hacked New 3DS system (Old 3DS users might use HzMod via a separate guide but the performance is VERY POOR. Old 3DS can still have their audio captured by audio cable.)
A good network connection that both the New 3DS and your PC share
(If you want to capture audio) A 3.5mm to 3.5mm audio cable and either a microphone port or a Y splitter that has a microphone port
Setup wireless streaming (3DS)
Install the .cia file onto your 3DS from the latest release of this NTR fork
Run the newly installed app, go through the setup until prompted to run a desired version - pick 3.6 HR at the very bottom
Press X+Y to open the NTR CFW menu and choose Remote Play (New 3DS) - this will show you the IP address your console has, and will also let you configure quality and performance options
Setup wireless streaming (PC)
Install one of the following NTR viewers: - NTRViewer (Windows and Linux, x64) - Snickerstream (Windows, x86 and x64) - kit-kat-slim (Windows, allows using input redirection AKA controlling your 3DS with the PC) - Twix (Windows, also allows input redirection and looks fancy) - cuteNTR (Linux) - cuteNTR-OSX (Mac OS) There are other ones, including for Windows 10/Xbox and even Wii U, but the performance may not be ideal for these
Run the NTR viewer you chose and input the IP address you got earlier. You can also set quality and performance options in the viewer as well as rendering options if available
Connect to your 3DS and enjoy looking at your console on a bigger(?) screen!
Setup audio capture
Connect the 3.5mm to 3.5mm audio cable to your 3DS headphone port and PC's microphone port (directly or via the Y splitter in computer's headphone port)
You can test the audio by either enabling listening to the new microphone device or using a program such as Audacity or OBS
Notes and Issues
TRY NOT TO CLOSE YOUR 3DS LID! It can sometimes lead to black screens and no response from the console, in which case you should hold the power button until it shuts down
This CANNOT record your DS, DSiWare or GBA VC games. Those require a capture card or using an emulator instead. Audio can be captured regardless of what your system is running
Some games may disable your internet connection, which means that you need to use patching option provided by NTR CFW or your NTR viewer of choice
If your NTR Viewer doesn't work, check firewall and viewer's render settings first and then try other viewers for your system
If your viewer disconnects on still screens, increase the timeout/wait time of the viewer if available (for Snickerstream, it's in Advanced settings)
If you have choppy framerate, decrease the quality, fiddle with QoS value and Encoder Priority, or get a better internet connection :p
If you have audio issues, try switching between microphone out and line out
-- Red
6 notes
·
View notes
Text
Few Required Features of a Supreme Online Secure Shell Client

In a world where remote work is extra common than ever, it is actually crucial to possess trusted as well as protected access to your web servers and also websites. secure shell (SSH) is actually an extensively made use of protocol for remote control login and also controls implementation on a system. A lot of online SSH clients supply highly effective functions that may boost your remote development knowledge. Nevertheless, certainly not all SSH clients are actually produced identical. In this particular article, our company'll explain some must-have features of an excellent online SSH client that may assist you keep successful and also function a lot more effectively.
SSH Clients Must Have These Features
Multi-Platform Being compatible:
A high-grade online SSH client ought to work effortlessly on all significant systems, featuring Windows, Mac computer, and also Linux. This feature makes certain that you can access your servers coming from any tool as well as operating device.
Accessible Interface:
An on the web SSH client need to be actually simple to utilize, along with a basic and intuitive user interface that enables you to do all required duties without any sort of headache. An easy to use user interface aids you function a lot faster and also more efficiently.
File Transmission Capacities
Moving documents is a typical task for creators working remotely. An excellent online SSH client should, therefore, possess strong data transfer capabilities that are swift and reputable, allowing you to conveniently publish, download and install, as well as take care of data on your web servers.
Monitor Sharing
In some instances, you might need to have to share your display screen along with your staff member or clients for cooperation or even troubleshooting purposes. A top-notch online SSH client should, therefore, include a display sharing function that allows you to discuss your monitor with others remotely.
Demand Pipe Accessibility:
Command-line get access to is actually important for programmers that favor doing work in a terminal environment. A high-quality online SSH client should offer complete command-line accessibility to your servers, enabling you to manage commands, manuscripts, and also apps as if you were actually working locally.
Protect Connection:
Surveillance is crucial when it pertains to distant access. An excellent online SSH client, as a result, should have strong security and protected interaction methods to ensure your information is actually regularly guarded.
Modification Options
Various programmers have various tastes when it relates to terminal settings, typefaces, and colors. A top-notch online SSH client, for that reason, should possess modification options that allow you to personalize your terminal atmosphere depending on to your taste.
Matching Shell Sessions
Teaming up with several web servers simultaneously may be lengthy as well as discouraging. A high-quality online SSH client should, for that reason, support Matching Shell Sessions, allowing you to deal with multiple web servers at the same time and also creating it less complicated to switch in between all of them.
Session Audio and also Playback
Treatment audio and playback abilities are actually crucial for addressing and bookkeeping reasons. A high-quality online SSH client must enable you to tape-record your treatments and also play all of them back later for study and also bookkeeping.
Combination with Various Other Tools
A premier online SSH client must include flawlessly along with other resources that you utilize in your day-to-day growth job, such as code publishers, version command systems, as well as task administration resources.
Deciding on the ideal online SSH client can easily improve your distant progression adventure considerably. A premier SSH client should provide multi-platform compatibility, a straightforward interface, safe and secure connection, file transmission functionalities, monitor sharing, command-line gain access to, customization possibilities, identical Shell sessions, treatment recording and also playback, as well as assimilation along with various other resources. With these vital functions, you can operate a lot more successfully and remain effective while functioning remotely.
2 notes
·
View notes
Photo
Also, Google is coming out with something called Manifest V3 for its extension framework that will prevent all extensions from running “remote code” which sounds good from a security standpoint and in a world without disingenuous business practices, that would be amazing.
However what this provision does is make it so that an extension can’t update say, a list of advertiser urls, without updating the whole extension and getting approval from Google.
The main point of this update is to block ad blocking extensions that actually work.
Now you might be thinking, I don’t need an ad blocker, I don’t mind getting the ads. Consider the following:
Do you ever wonder why despite getting faster and faster internet connections, your web pages sit at a blank screen for a while before loading anything? That is the web page running an auction on the ad spots. Every time you load the page. Not only does this slow down your browser, but it’s also using your data if you’re on a phone or other metered connection. Using an ad blocker speed up your experience and reduces data usage by a noticeable amount.
Have you ever been talking to a friend about some new set of pens they found on Amazon, and then suddenly you get an ad for those pens? That’s not them listening in on the mics of your phone. They paired your tracking ID to theirs via the WiFi you were probably on. They figure since you’re using the same IP, and it’s not one that shows up for a ton of people, you two must be related somehow, and must share interest. So they change your profile to reflect that and start showing you stuff they like. If you have an ad blocker on, they can’t generate a tracker for you, so your friends can’t figure out what you’re planning on getting them after you visit by looking for new ads.
Then there’s the article below. It’s been partially debunked, as target already had a system in place to more discreetly distribute baby products, but they still were able to guess based on a few purchases that she might need baby products. That is way more than anyone needs to know about you. Ad blockers help prevent that kind of data accumulation.
Firefox is pretty much the last browser out there that you can get on pretty much any device that isn’t chrome. Brave, Opera, and Edge are all just chrome with a coat of paint and some crypto or ai bs tacked on.
If you want to try and maintain any semblance of privacy or control over your experience on the web, use Firefox. If you’re too scared to switch and you have a Mac, at least use Safari. It is actually the fastest web browser and on the Mac you can get some good ad blockers for it. Otherwise if you’re on Windows, android, or Linux, SWITCH TO FIREFOX.
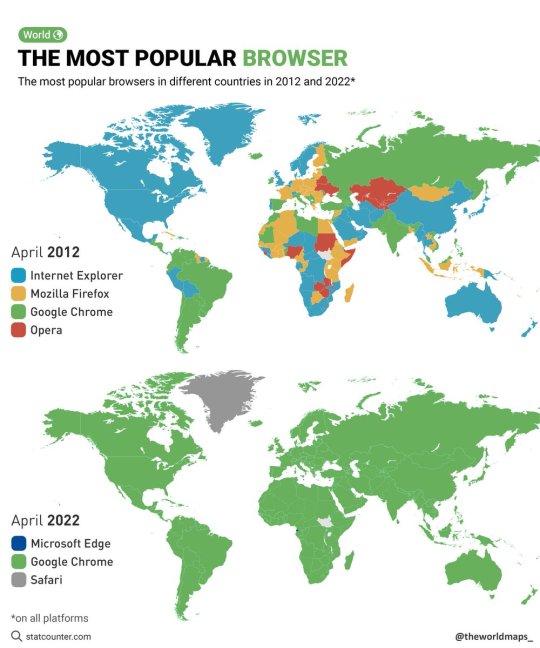
The most popular browsers in different countries in 2012 and 2022.
by @theworldmaps_
163K notes
·
View notes
Text
Choosing the Right Microsoft 10 Professional Version for Your Needs
Businesses and power users often need a robust operating system. If that sounds like you, Microsoft 10 Professional may be exactly what your setup demands. This version brings advanced features like encryption and remote desktop support. It also lets you join a corporate domain with full confidence. With an official version, you ensure reliability and regulatory compliance.
What Makes Microsoft 10 Windows Ideal for Everyone
When people mention Microsoft 10 Windows, they usually think of its Home edition. It balances ease of use and performance. It works well for everyday tasks like browsing, streaming, and light office work.
Microsoft designed this version to be user-friendly, with features like Cortana, Microsoft Edge, and improved security. Regular updates arrive automatically. This version fits most users who don’t need the advanced tools of Professional.
Microsoft 10 Professional: Who Should Upgrade?
Choosing Microsoft 10 Professional makes sense if you need features like BitLocker, enterprise-level security, and remote access. IT teams love the Group Policy management. Developers often rely on virtualization via Hyper-V. These tools aren’t available in the Home edition.
If you work from home or on secure networks, this upgrade strengthens data protection. For laptop users who travel often, BitLocker encryption secures your drive in case of loss or theft. Microsoft crafted the Professional edition with security and control in mind.
Top Tools in Microsoft 10 Pro Version
Microsoft 10 Professional includes a suite of advanced tools:
BitLocker: Encrypts your drives to protect sensitive data.
Remote Desktop: Lets you access your computer remotely.
Hyper-V: Enables you to run virtual machines on your own computer.
Group Policy: Allows system-wide configuration and policy enforcement.
These tools aren’t present in the Home edition. They help businesses enforce rules, secure systems, and maintain control over device access. The upgrade cost is recouped through added efficiency and security.
Introducing Microsoft 365 Personal Software Benefits
Aside from choosing the right OS, you likely need productivity tools. That’s where Microsoft 365 Personal software comes in. This subscription includes access to Word, Excel, PowerPoint, Outlook, and more.
It also provides 1 TB of secure OneDrive cloud storage. With automatic updates and advanced security features, your tools stay current. You can use the apps across multiple devices—PCs, Macs, tablets, and phones—making it ideal for individuals who work on the go.
Why Microsoft 365 Personal Complements Your System
Pairing Microsoft 365 Personal with either Windows 10 Home or Pro gives you a complete productivity platform. You install your apps, work offline or online, and store files safely.
This plan also includes access to premium templates and ongoing feature updates. If you rely on Microsoft Office apps regularly, it offers strong value. You get professional-grade tools without needing a large business license.
Security Enhancements with Microsoft 365 Personal Software
Security matters whether you’re on Microsoft 10 Pro or Home. The Microsoft 365 Personal software package adds extra layers of protection. OneDrive encryption keeps your files safe in the cloud.
Office apps also offer advanced protection against phishing and malware. With integrated support and automatic updates, your tools stay secure and feature-packed. This ensures both your data and your tools are protected against modern threats.
Comparing Microsoft 10 Professional and Microsoft 365
If you're choosing between Operating System upgrades and productivity tools, you don’t need to. Combine them for best results. Microsoft 10 Professional secures your core system. Microsoft 365 Personal enhances your application layer and cloud storage.
Together, they create a powerful, flexible environment. You’ll have enterprise-grade security and access to essential tools. Whether you're working at a desk or traveling, this combo ensures you’re ready for any task.
How to Get Genuine Microsoft Software
Always buy your license from a trusted source. For Microsoft 10 Professional and Microsoft 365 Personal software—use verified vendors. This prevents counterfeit keys and avoids future activation issues.
Look for instant delivery and reliable customer support. Read reviews and choose vendors with high trust ratings. You deserve searchable keys, easy installation, and dependable software.
Final Thoughts on Microsoft 10 and Office Suite Choices
Choosing an operating system and productivity suite is a vital decision. With Microsoft 10 Professional, you enhance security, add business tools, and improve manageability. With Microsoft 365 Personal, you stay productive with cloud-enabled Office apps.
Together, they offer a modern, efficient, and secure digital workspace. For professionals, home users, or students, this combination delivers flexibility, performance, and peace of mind.
#microsoft 10 professional#microsoft 10 windows#microsoft 365 personal#microsoft 365 personal software
0 notes
Text
Secure Remote Access with Azure Managed Security

Azure Virtual Desktop offers secure remote access from anywhere, reducing costs for businesses with valid Microsoft 365 or Windows licenses. Maximize your investment with Windows multi-session capabilities while cutting operational expenses. With support for various devices including Windows, Mac, iOS, and Android, users can access their desktop environment from any internet-connected device. The platform optimizes performance for Microsoft products like Teams and Office applications. Setting up Azure Virtual Desktop is straightforward with no gateway servers required. The platform allows resource sharing across multiple sessions, significantly reducing virtual machine needs while maintaining user resource allocation. Enhanced security features keep data on Azure rather than local devices, protecting both employees and company information. Implement conditional access, multifactor authentication, and role-based controls to mitigate potential security risks. Professional Labs provides expert Azure Virtual Desktop services with comprehensive managed security solutions that safeguard your virtual desktop infrastructure while ensuring compliance with ISO, PCI, FedRAMP, and HIPAA standards. Read more: https://prolabsit.com/azure-virtual-desktop/
0 notes
Text
Privileged Access Management Market Driven by AI and Cloud Trends in 2032 Outlook
Privileged Access Management Market was valued at USD 2.69 billion in 2023 and is expected to reach USD 17.42 billion by 2032, growing at a CAGR of 23.13% from 2024-2032.
Privileged Access Management Market is undergoing rapid expansion as organizations face mounting cybersecurity threats targeting privileged credentials. With data breaches becoming more sophisticated, enterprises across critical sectors—including finance, healthcare, and government—are prioritizing PAM solutions to secure administrative access and enforce least-privilege policies.
U.S. Market Shows Aggressive Adoption in Response to Rising Cyber Threats
Privileged Access Management Market is increasingly recognized as a core component of modern cybersecurity frameworks. Companies are investing in PAM tools to enhance visibility, automate session monitoring, and mitigate internal risks. The demand is especially strong in compliance-heavy regions, where regulators emphasize secure access to sensitive systems.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/6666
Market Keyplayers:
Fortinet (FortiPAM, FortiAuthenticator)
BeyondTrust (Password Safe, Privilege Management for Windows & Mac)
CyberArk (Privileged Access Manager, Endpoint Privilege Manager)
Broadcom (Symantec PAM, Symantec PAM Gateway)
Imprivata (OneSign, Privileged Access Management)
Optiv Security (Privileged Access Management Services, Identity & Access Management Solutions)
Okta (Okta Privileged Access, Okta Identity Governance)
IBM (Security Verify Privilege Vault, Security Identity Governance & Intelligence)
Micro Focus (OpenText) (NetIQ Privileged Account Manager, NetIQ Identity Governance)
ManageEngine (Zoho) (PAM360, Password Manager Pro)
HashiCorp (Vault, Boundary)
One Identity (Safeguard for Privileged Sessions, Safeguard for Privileged Passwords)
ARCON (Privileged Access Management, Session Monitoring & Recording)
Netwrix (Privileged Access Management, Auditor for Active Directory)
Delinea (Secret Server, Privilege Manager)
Wallix (Bastion, AdminBastion)
Saviynt (Saviynt for Privileged Access, Identity Governance Cloud)
Senhasegura (PAM Core, DevOps Secret Manager)
KronTech (Single Connect, Dynamic Password Controller)
miniOrange (PAM Solution, Identity Broker)
EmpowerID (Privileged Access Manager, Identity Governance Platform)
StrongDM (Infrastructure Access Platform, Admin UI)
CyberSolve (PAM Advisory, Identity & Access Consulting Services)
Opal Security (Access Review Automation, Just-in-Time Access)
Foxpass (PAM Solution, LDAP-as-a-Service)
Secureden (PAM Software, Remote Access Management)
RevBits (Privileged Access Management, Endpoint Security)
Silverfort (Unified Identity Protection, Secure Access for PAM)
IDM Technologies (IDM Privileged Access, Identity Governance Suite)
Market Analysis
The Privileged Access Management (PAM) market is being shaped by an urgent need to defend against identity-based attacks and insider threats. As businesses adopt hybrid cloud infrastructures and remote access models, managing privileged credentials becomes a top priority. Organizations are shifting from traditional perimeter security to identity-first security strategies that include PAM as a foundational layer. In the U.S., regulatory mandates like SOX, HIPAA, and FISMA are driving PAM implementation across enterprises, while in Europe, GDPR compliance and industry-specific norms continue to fuel adoption.
Market Trends
Growing demand for cloud-native and hybrid PAM solutions
Integration of AI and machine learning for threat detection and access analytics
Increased automation of access provisioning and de-provisioning
Rise in just-in-time (JIT) access and zero standing privileges
Expansion of PAM to DevOps and third-party vendor environments
Enhanced auditing and reporting features to meet compliance
Privileged session recording and real-time behavior analytics
Market Scope
The Privileged Access Management Market is not limited to large enterprises—it is increasingly essential for mid-sized businesses managing critical assets and data. With digital transformation accelerating, PAM is becoming a non-negotiable part of cybersecurity roadmaps.
Secure access to critical systems across cloud and on-prem
Real-time monitoring and auditing of privileged sessions
Identity-centric security aligned with zero-trust models
Vendor and third-party access governance
Scalable solutions for enterprises of all sizes
Policy enforcement and credential vaulting
Forecast Outlook
The future of the PAM market is marked by aggressive innovation, strategic investments, and global standardization. With threat actors constantly evolving, businesses are embracing dynamic, identity-focused security architectures. PAM solutions are expected to integrate more deeply with endpoint protection, identity governance, and broader zero-trust ecosystems. The market's trajectory points toward smarter, automated, and user-centric systems that deliver both protection and operational efficiency.
Access Complete Report: https://www.snsinsider.com/reports/privileged-access-management-market-6666
Conclusion
The Privileged Access Management Market is no longer a niche solution—it’s a strategic imperative. As U.S. and European enterprises adapt to a hyper-connected, threat-prone environment, PAM stands at the forefront of cyber resilience. With increasing attacks on administrative access, organizations that prioritize PAM will not only meet regulatory standards but will also build trust, reduce risk, and enable secure digital transformation.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Related Reports:
U.S.A experiences robust growth in Cloud Access Security Broker Market driven by data security priorities
U.S.A sees rising adoption of Voice Biometrics Market Size across banking and government sectors
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
Mail us: [email protected]
0 notes
Text
Arduino is essentially a language designed for interacting with and operating interactive objects and digital devices. Arduino has immense potential, since it’s being increasing used for controlling remote controlled objects such as drones. If you are looking for a book on Arduino, this article will serve as the base for taking a decision and choosing the right book that will help you sharpen your skill in Arduino. This article will give you information about seven best Arduino books that are regarded as featured books. Arduino is open source software (IDE) which makes it a breeze to write as well as upload codes to a board. Moreover, Arduino runs on Mac OS X, Linux as well as Windows. The environment of Arduino is written in Java language; also it’s based on open-source software and processing. Take help of the information furnished in the books and explore the horizon of Arduino programming. Programming Arduino Getting Started with Sketches (By: Simon Monk ) Learn Arduino programming with ease with the easy-to-follow and clear examples featured in the book. The book contains the software side of Arduino and describes the way of writing the program using the well-crafted sketches using modified C programming language meant for Arduino. The book features downloadable sample programs that can be modified as per your requirement. The easy explanation and details crafted in the book make is one of the best books to learn Arduino. You can structure your data by using strings and arrays. The book also helps you learn how to use digital and analog inputs and outputs of Arduino in the programs. Programming Arduino Next Steps: Going Further with Sketches (By: Simon Monk ) This is the second book of the series that makes you understand the next step of the beginner’s guide. You can take your Arduino understanding and skills to the next level with this easy-to-study book. This book on Arduino basically is a practical guide and the secret of the professional Arduino programming is revealed by electronics guru Simon Monk taking every possible aspect under the hood. The book features the coverage of Arduino Uno, Due Boards and Leonardo. This book is all-in-one repository and features more than 75 examples and sketches. Exploring Arduino: Tools and Techniques for Engineering Wizardry (By: Jeremy Blum ) This book is the best book as far as the third step is concerned – understanding the tools and techniques of Arduino. This book is all about that and helps you learning to build robots, gizmos and gadgets using Arduino. This book is written by Jeremy Blum – the Arduino expert – and is a unique book that uses the popular Arduino microcontroller platform, which is an instrument that teaches you about programming, electrical engineering and also human-computer interaction. Beginning C for Arduino: Learn C Programming for the Arduino (Technology in Action) (By: Jack Purdum ) This is the Arduino best book for those who do not have prior experience in programming of microcontrollers. This book is written so well and in easy-to-understand way that it helps the readers to understand the aspects of Arduino and help them learn as well and experiment. This book starts with an introduction to C language and reinforces every programming structure using simple demonstrations. Author Jack Purdum has used a very engaging style of writing in order to teach good and efficient techniques of programming. Arduino Workshop: A Hands-On Introduction with 65 Projects (By: John Boxall ) This book offers hands-on experience on Arduino programming with 65 projects. With the help of this book, you can learn the basics of Arduino programming, build a project after learning and finally create your own Arduino program. Arduino is basically an easy, flexible, cheap and open source microcontroller programming platform that offers students to learn and create their own homemade projects and this book is the best one in this category. This book
gives you an opportunity to learn and create devices using almost unlimited range of input and output sensors, displays, indicators or add-ons. Arduino For Dummies (By: John Nussey ) Arduino is not just an ordinary circuit board and corresponding software. It does not matter whether you are a designer, artist, hobbyist or a programmer, Arduino enables you to play with electronics. This book helps you learn building a variety of circuits that can control or sense things in the real world. If you have loads of ideas that you want to bring to the real world or you have curiosity to know and learn the possibilities, this book is perfect for you to read. The best part about this book is that it enables you to learn by writing the programs in real time. Arduino Cookbook (By: Michael Margolis ) Do you want to build devices that can interact with the real world? This cookbook is the perfect answer to that question. This is book is an all-in-one cookbook for you if you want to experiment with popular Arduino programming or microcontroller environment. The book offers more than 200 techniques and tips in order to build a variety of objects and prototypes like robots, detectors and toys along with interactive clothing, which sense and respond to light, heat, position, sound and touch.
0 notes
Text
Protect Your Digital Life with Norton Antivirus: Complete Security for Every Device
In an age where cyber threats are more sophisticated than ever, having robust digital protection is no longer optional—it’s essential. Norton Antivirus stands out as a trusted and comprehensive security solution, helping individuals and families stay safe from viruses, malware, ransomware, and online fraud. If you're looking for top-tier protection, the Norton 360 Premium package available on OmniSoft is the ideal choice.
What Is Norton Antivirus?
Norton Antivirus is a globally recognized cybersecurity software developed to provide real-time protection against a wide range of online threats. With over three decades of experience, Norton has continuously evolved to offer intelligent, proactive defense systems that protect your privacy, personal information, and devices from digital dangers.
Key Features of Norton 360 Premium
The Norton 360 Premium edition is more than just antivirus software—it’s an all-in-one digital protection suite. Here are some of the standout features:
Comprehensive Antivirus Protection: Detects and removes viruses, spyware, malware, and ransomware.
Multi-Device Coverage: Safeguard up to 10 devices including Windows, Mac, Android, and iOS.
75 GB Cloud Backup: Keep your important files secure in the cloud to prevent data loss due to ransomware or hard drive failure.
Firewall for PC and Mac: Adds an additional layer of security to block unauthorized access to your private data.
Password Manager: Securely stores and manages your passwords, credit card information, and other credentials.
Parental Control: Help your kids safely explore the internet by monitoring online activity and limiting access to inappropriate content.
Secure VPN: Browse anonymously and securely even on public Wi-Fi with an integrated virtual private network.
Why Choose Norton from OmniSoft?
OmniSoft is a trusted digital software provider offering licensed and affordable security solutions. When you purchase Norton Antivirus 360 Premium from OmniSoft, you benefit from:
Immediate digital delivery
One-year full protection
Romanian customer support
Reliable and secure payment methods
Who Needs Norton Antivirus?
Whether you're a student, a remote worker, a business professional, or managing a household, you likely rely on multiple devices daily. Cybercriminals target everyone—from casual browsers to corporate executives. Norton 360 Premium provides peace of mind, knowing your data, identity, and online activity are protected around the clock.
Final Thoughts
Don’t leave your digital life vulnerable. With cyber threats growing each day, investing in powerful and reliable protection like Norton Antivirus is a smart and necessary step. Secure your online world today with Norton 360 Premium from OmniSoft—because your privacy, files, and peace of mind are worth it.
For more info visit here:- total security
1 note
·
View note
Text
KT6368A Bluetooth Chip Add Douyin Page Scrolling, Liking, and Selfie Remote Control Instructions Including AT Commands
1.1 Introduction
Bluetooth HID (Human Interface Device) refers to device types such as Bluetooth keyboards, Bluetooth mice, Bluetooth remotes, etc., all categorized as human-computer interaction devices. Here, our KT6368A Bluetooth chip emulates these devices. For host devices like Windows, Android, or iOS, HID devices are driver-free, meaning as long as the host device supports Bluetooth, it can establish a connection with the KT6368A and send specific key commands. Taking the commonly used Douyin page-scrolling remote as an example, the functions include:
1. Swipe up and down to scroll through pages.
2. Swipe left and right.
3. Volume up and volume down.
4. Pause, play, and like.
The functionality is essentially the same as commercially available products, as shown in the following image:

Additionally, it features reconnection capability, meaning the Bluetooth device will automatically reconnect to the last paired mobile device upon powering on.
Of course, it is compatible with both Android and iOS (Apple) devices.
The KT6368A HID version consumes 15mA at startup for approximately 100ms, then stabilizes at around 5mA thereafter.
1.2 Hardware Description
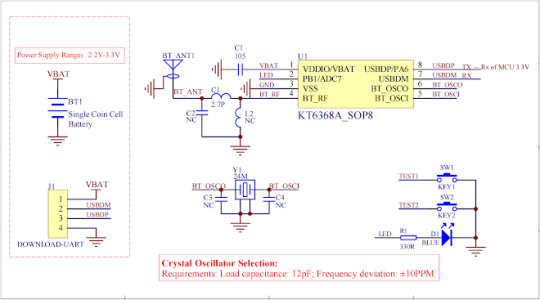
Parameter Description
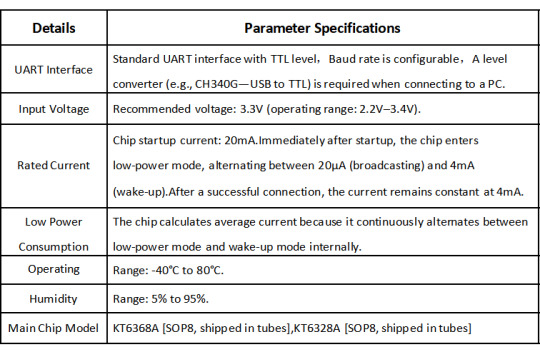
Operation Description
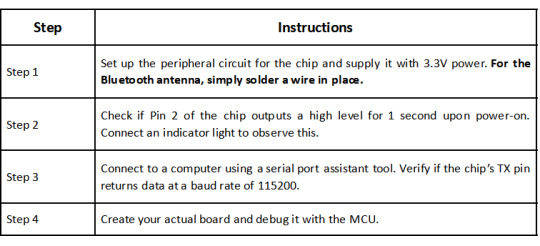
1.3 Setting HID Bluetooth Device Name [BD]
AT+BDSPP-1234\r\n Set the Bluetooth name to "SPP-1234".
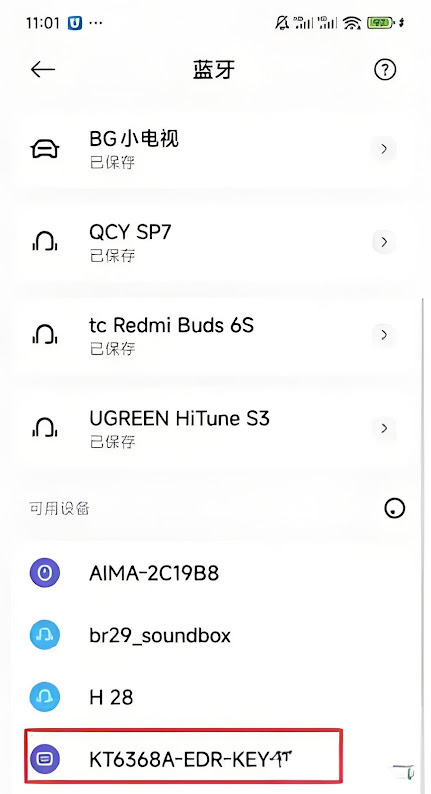
1. After setting the Bluetooth name, you need to reset the chip by sending a command or powering it off and on. This will display the new Bluetooth name. The default Bluetooth name is "KT6368A-EDR-KEY". The maximum length for the Bluetooth name is 30 bytes. Please do not exceed this limit.
2. If you modify the Bluetooth name using AT commands, note that your mobile device may not update immediately and may still display the previous name.
(1) This is because you only changed the Bluetooth name, while the Bluetooth MAC address remains unchanged. Therefore, the mobile device will not update the name.
(2) To resolve this, try searching with another mobile device, or delete the pairing information on the original device and search again.
(3) Rest assured that once the Bluetooth name is set, it is definitely updated. The chip will also return the Bluetooth name upon power-up for verification.
1.4 Common Douyin Key Commands [CC]
AT+CC00\r\n Previous page
AT+CC01\r\n Next page
AT+CC02\r\n Left page
AT+CC03\r\n Right page
AT+CC04\r\n Play/Pause
AT+CC05\r\n Play/Pause
AT+CC06\r\n Volume + (Combined with selfie function)
AT+CC07\r\n Volume – (Combined with selfie function)
0 notes
Text
Activate Your Digital World with Genuine Windows, Office and Autodesk Licenses
In nowadays’s rapid-paced digital ecosystem, having access to genuine software program licenses is greater than just a criminal necessity—it’s a strategic funding in productivity, overall performance, and safety. From operating systems like Windows 7 to creative suites like Autodesk, customers require reliable keys and licenses for a seamless user revel. Whether you're a home user, student, IT admin, or business owner, the proper license makes all the difference.
Upgrade legacy systems using Windows 7 and Windows 8 keys.
If you're maintaining legacy systems or older hardware, the windows 7 home premium product key is nevertheless critical for going for walks Windows 7 with complete functionality. Many users and corporations still rely on this solid operating gadget for specific applications and systems. Meanwhile, for the ones bridging the distance between antique and cutting-edge, the windows eight license key and windows 8 license key help activate Windows 8 legally, permitting persisted support and smoother performance.
Increase productivity with Microsoft Office 2024 for Mac.
Mac customers searching out superior productiveness equipment can now benefit from microsoft office 2024 for Mac. This modern day model includes updated packages like Word, Excel, and PowerPoint tailor-made specially for macOS, giving customers unequalled performance, UI integration, and collaboration capabilities.
Permanent Access with Office 2021 Professional Plus
Say goodbye to subscriptions and revel in lifetime usage with an Office 2021 professional plus lifetime license key. This one-time buy includes all of the vital Office packages—perfect for commercial enterprise proprietors, faraway people, and students who need dependable equipment with out routine prices.
Optimize Business Servers with Windows Server Standard
For employer-grade reliability and overall performance, Windows Server Standard gives advanced server functionalities like virtualization, garage management, and strong protection. It’s best for companies coping with databases, web sites, or enterprise-huge programs on a scalable infrastructure.
Home PC Ready? Buy Windows 10 Home Product Key
For regular users, the buy windows 10 home product key unlocks access to a dependable, steady, and rapid running gadget. This model is best for domestic laptops and desktops, offering compatibility with a huge range of software program and hardware.
Advanced Users Choose Windows 10 Pro
Professionals and tech-savvy users prefer the delivered features of the windows 10 professional license. With BitLocker encryption, Remote Desktop, and Group Policy management, Windows 10 Pro caters to business environments and electricity customers alike.
Smooth Transition to Modern Operating Systems: Windows 11 Pro and Home.
Upgrading your system? You can now buy windows 11 pro license key for powerful multitasking, more suitable safety, and smooth visuals. For domestic customers, the windows 11 home product key provides a streamlined Windows eleven revel with all the essentials included.
For business-degree control and features, the windows eleven expert product key offers the gear and security wanted in a corporate environment. Want to set off a professional version of Windows 10? You can buy a windows 11 professional product key to get instant get entry to to seasoned-stage functions, updates, and safety.
Unlock Design Power with Autodesk and AutoCAD
Designers and architects can unleash full creativity with the Autodesk All Apps 2025 license. This consists of AutoCAD, Revit, Maya, 3ds Max, and greater—important gear for any expert working in engineering, animation, or construction.
Looking to consciousness on one application? Understanding the charge of autocad software program is fundamental. Investing in an authorized model ensures get entry to to updates, cloud offerings, and aid from Autodesk—ensuring your work stays current and professional.
0 notes
Text
Mac Iptv Box
Discover the Infomir MAG 425A 4K IPTV and Android TV Box at Stroudtech Solutions. With 2GB RAM, 8GB storage, voice-controlled remote, and Wi-Fi, it's the perfect choice for streaming
Mac Iptv Box
About Company:-Stroudtech Solutions is an industry-leading service center, where we repair and provide services in all Apple, Microsoft Surface Pro, Windows, Linux, Samsung, HP, iPhone, iPad, PC computer, Dell, Console, Data recovery, Virus Removal, Website Design, Technical support, IT Consultant, and many more IT support in Barrie, innisfil, Bradford, Essa, Angus, Orillia ,Toronto, Markham, Newmarket and other cities within Simcoe county area. Your device and you are in good hands because Stroudtech Solutions has certified technicians who are experienced with pc computers, apple mac for many years.
Click Here For More Info:- https://www.stroudtechsolutions.ca/product/infomir-mag-425a-4k-iptv-and-android-tv-box-2gb-ram-8gb-voice-controlled-remote-wi-fi-hdmi/
0 notes
Text
Everything You Need to Know About AnyDesk Descarga Gratis for Fast and Secure Remote Access
Introduction to AnyDeskDescargaGratis
What is AnyDeskDescargaGratis AnyDeskDescargaGratis is a remote desktop software that allows users to connect to and control another computer securely over the internet.
Why Use AnyDeskDescargaGratis It enables fast and secure remote support, making it ideal for businesses, tech support teams, and remote workers.
What Makes AnyDeskDescargaGratis Special
Key Features and Benefits Features like file transfer, clipboard syncing, session recording, and low-latency performance make AnyDeskDescargaGratis stand out.
Comparison with Other Remote Tools Unlike heavier alternatives, AnyDeskDescargaGratis is lightweight, easy to install, and performs well even with slow connections.
Download and Installation Guide
How to Download AnyDeskDescargaGratis The application is available for Windows, Mac, Linux, Android, and iOS, and can be downloaded from its official site.
Installing and Running the Software Simply run the downloaded file, follow the prompts, and start your first remote session in seconds.
Security and Privacy in AnyDeskDescargaGratis
Encryption and Safe Connections It uses TLS 1.2 encryption and RSA key exchange to keep sessions secure and private.
Permission Settings and Access Control Users can configure access rights, require passwords, and approve connections manually for added control.
Platform Compatibility
Supported Operating Systems AnyDeskDescargaGratis works across multiple platforms including desktops and mobile devices.
User Experience Across Devices It provides a seamless interface and functionality, regardless of whether you’re on a PC or smartphone.
Common Use Cases
Using for Remote IT Support Technicians can quickly access and resolve issues on client systems without being onsite.
Perfect for Remote Work and Access Employees and freelancers can access their home or office computer from anywhere with AnyDeskDescargaGratis.
Custom Settings and Advanced Options
Personalizing the Interface Users can adjust display quality, enable auto-start, or set up a custom alias for easier identification.
Exploring Advanced Features Options like session recording, custom permissions, and command-line integration are available.
Support and Help Resources
In-App Help and Tutorials Built-in documentation helps new users set up and use the application effectively.
Getting Further Support Users can contact the support team or explore community forums for additional guidance.
FAQs
Is AnyDeskDescargaGratis free to use? Yes, it is free for personal use. Commercial users need a license.
Can I use AnyDeskDescargaGratis on my mobile device? Yes, it supports both Android and iOS devices.
Is AnyDeskDescargaGratis secure for remote access? Absolutely. It uses encrypted connections and multiple security layers.
Do I need to install AnyDeskDescargaGratis on both devices? Yes, both the local and remote computers need the app installed.
Can I transfer files between devices? Yes, the software supports fast and secure file transfers during remote sessions.
1 note
·
View note
Text
The Ultimate Guide to the Best Wireless Mouse and Keyboard in 2025
As remote work, gaming, and digital lifestyles continue to evolve, the demand for high-quality wireless accessories has skyrocketed. Among the most essential tools for any computer setup are the best wireless mouse and keyboard. These devices not only reduce cable clutter but also enhance productivity, comfort, and aesthetics. In this guide, we explore the top wireless mouse and keyboard combinations available in 2025, and how to choose the right set for your needs.
Why Go Wireless?
Before diving into recommendations, it's important to understand the benefits of wireless technology:
Freedom of Movement: Without cables, you can position your keyboard and mouse wherever you feel most comfortable.
Cleaner Desk Setup: Wireless devices reduce clutter, contributing to a more organized and visually pleasing workspace.
Portability: Perfect for on-the-go use, especially for professionals and students.
Top Picks for the Best Wireless Mouse and Keyboard (2025)
1. Logitech MX Keys S & MX Master 3S Combo
Best for Professionals
Price: $$$
Highlights:
Sculpted ergonomic mouse with MagSpeed scroll wheel
Keyboard with smart backlighting and excellent tactile feedback
Seamless multi-device pairing
The MX Keys S and MX Master 3S combo is a productivity powerhouse. With Logitech’s signature build quality and advanced features like customizable buttons and Flow control between devices, this combo is perfect for multitaskers and power users.
2. Apple Magic Keyboard & Magic Mouse 2
Best for Mac Users
Price: $$$
Highlights:
Sleek, minimalist design
Seamless integration with macOS
Rechargeable via Lightning cable
Apple’s Magic accessories remain the gold standard for Mac enthusiasts. They are not the most ergonomically advanced, but they offer superb synergy with Apple devices, making them ideal for those deeply embedded in the Apple ecosystem.
3. Microsoft Surface Keyboard & Surface Mouse
Best for Windows Users
Price: $$
Highlights:
Elegant, low-profile design
Great key travel and spacing
Smooth, precise mouse movement
Designed with Windows users in mind, the Microsoft Surface accessories combine style and substance. They're particularly well-suited for office and creative work.
4. Logitech MK850 Performance Wireless Keyboard and Mouse Combo
Best Ergonomic Option
Price: $$
Highlights:
Cushioned palm rest and curved keyframe
Contoured mouse with hyper-fast scrolling
Connects via Bluetooth or USB receiver
The MK850 is engineered for comfort and efficiency. Its ergonomic design makes it a go-to choice for users who spend long hours typing and navigating.
5. Razer Pro Type Ultra & Razer Pro Click
Best for Gamers Who Work
Price: $$$
Highlights:
Mechanical keyboard with silent switches
Ergonomic mouse designed with humanscale
Ultra-low latency and high precision
Blending gaming performance with a professional aesthetic, Razer’s Pro series is ideal for users who want a stylish setup that can switch from spreadsheets to esports in a snap.
Key Features to Consider
When choosing the best wireless mouse and keyboard, keep these factors in mind:
Connectivity: Bluetooth vs. 2.4GHz USB dongle. Some offer both.
Battery Life: Rechargeable batteries are more eco-friendly, while traditional batteries may last longer.
Ergonomics: Comfort is critical for long-term use. Look for contoured designs and wrist support.
Customization: Programmable keys and buttons can boost productivity.
Compatibility: Ensure the devices are fully compatible with your operating system.
Final Thoughts
Whether you’re a coder, writer, designer, or casual browser, investing in the best wireless mouse and keyboard can transform your computing experience. From Logitech’s premium combos to Apple’s sleek design, there's a wireless solution for every preference and budget.
As technology continues to advance, these peripherals will only get smarter, more ergonomic, and more integrated. Choose wisely, and your hands—and productivity—will thank you.
0 notes