#all type of hardware and software solution
Explore tagged Tumblr posts
Text
Empowering Your Devices: Siddhi Computer's Expert Laptop Repair Services
Introduction: Welcome to Siddhi Computer - Your Trusted Partner in Laptop Repairs! In this fast-paced digital era, we understand the importance of having a reliable laptop for both personal and professional needs. Our dedicated team at Siddhi Computer is committed to providing top-notch laptop repair services in Navi Mumbai.
Why Choose Siddhi Computer for Laptop Repairs:
Experienced Technicians: Our skilled technicians have years of experience in diagnosing and fixing a wide range of laptop issues. From hardware malfunctions to software glitches, we've got you covered.
Quick Turnaround Time: We value your time, and our efficient repair process ensures a quick turnaround without compromising on the quality of service. Your laptop will be up and running in no time.
Genuine Parts Guarantee: At Siddhi Computer, we believe in transparency. We use only genuine and high-quality replacement parts to ensure the longevity and optimal performance of your laptop.
Our Laptop Repair Services:
Hardware Repairs:
Screen replacements
Keyboard repairs
Battery replacements
Charging port repairs
Software Troubleshooting:
Operating system issues
Virus and malware removal
Data recovery
Upgrades and Enhancements:
RAM upgrades
Storage upgrades (SSD installation)
Performance optimization
Customer Testimonials: "Siddhi Computer exceeded my expectations with their prompt and professional laptop repair service. My laptop is now as good as new!" - Satisfied Customer
How to Contact Us: Ready to give your laptop the care it deserves? Contact Siddhi Computer for all your laptop repair needs:
Phone: [9820869329/+91-9920656244]
Email: [[email protected]]
Visit our store: [Plot No 108, Dhanashree Co operative Housing Society, 10, Sector-01, Sanpada Rd, near Vashi Railway Station, Navi Mumbai, Maharashtra 400705]
Website: [https://www.siddhicomputer.com/]
Conclusion: Trust Siddhi Computer to revive your laptop and experience the difference of expert repair services. Your satisfaction is our priority, and we look forward to being your go-to Laptop Repair Centre in Navi Mumbai.
#laptop repairing shop#laptop repair center in sanpada#all type of hardware and software solution#laptop repair shop in sanpada#hp laptop repair centre in sanpada#hp laptop repair centre in nerul
0 notes
Text
On Major Milestones
I left off previously with init immediately crashing when trying to run NetBSD on Wrap030, my 68030 homebrew computer. I was completely lost and didn't know where to start looking. The error code it gave, 11, didn't tell me much.
Until now, most error codes I've gotten have been defined in kernel errno.h, which has 11 defined as:
EDEADLK 11 /* Resource deadlock avoided */
That … also isn't helpful. I'm still not entirely sure what that means, but since this is process 1 we're dealing with, I didn't think it was relevant.
Finally, I was able to find someone who had encountered the same error six years ago. Helpful soul [Martin] explained the exact cause of the error, how to fix it, and why the kernel errno didn't line up:

I'm running a NetBSD live disk on a laptop as a test host, so I mounted my disk on it and spent some time with mknod adding the essential device nodes, referencing the "majors" file for my arch. Sure enough, on next boot it skipped right past the point it had been panicking. It worked for a bit then finally printed on the console:
Enter pathname o
Enter pathname of what? The machine appeared frozen. Nothing further printed, and it responded to no input.
I was afraid this would happen. That string is 16 characters. The 16C55x UART chips I'm using have a 16-byte buffer. The system is hung up waiting for the UART to interrupt to indicate it has finished transmitting everything in its buffer.
There's just one problem — I don't have any serial interrupts wired.
I have a confession to make. Until a few weeks ago when I got my timer working, I hadn't really worked with hardware interrupts before. So between a limited understanding of how to use them effectively and limited board space, I had omitted the interrupt signals from my 8-port serial card. This was now a Problem, and I was going to have to find a solution.
I had a few options:
Force the com driver to 8250 mode so it doesn't try to use the buffers
Use my timer interrupt to check status bits on the UARTs and fake the interrupts
Deadbug an interrupt handler onto my serial card
Respin the serial card
Option 4 would've been expensive and risked passing my deadline. I wasn't sure option 1 would even help. And option 3 would have been difficult and error-prone. I decided option 2 would be the way to go so I set about researching how to accomplish it
I spent a few hours digging through the com driver. In the process I found softintr(9), a native NetBSD software interrupt process that looked like just the thing I needed. Digging in a little deeper, I realized that the com driver was already using softintr. And then I realized all it needed to do polled mode serial ports instead of interrupt-driven was to set a single variable, sc_poll_ticks, before initializing the driver. It's such a simple thing, but it's not really documented anywhere I could find, so the only way to know it was even an option was to spend hours studying the code.
With that in place, I recompiled my kernel and tried again.

It was asking for a shell. This is promising. I accepted the default shell, /bin/sh, and waited a moment. It printed a single #.
I had a shell prompt.

I typed in the first thing that came to mind, echo "hellorld" (thanks, [Usagi]). It responded:
hellorld
and printed another # prompt.
I had a working shell.

This is a major milestone. I have a modern operating system kernel loaded and running on my homebrew computer, and I have a functional root shell. I can navigate disk directories and run commands and programs.
But only as root, and only on this one console. I have seven other serial ports I want terminals on, and I certainly don't want them all running as root.
What it's running here is single-user mode. It is just the kernel and a few core services, somewhat analogous to Safe Mode in Windows. It's a fall-back for setting up or repairing a system. It's not quite the full operating system just yet.
Getting the rest of the operating system up and running is going to be a significant task, on par with getting just the kernel running. Setting up a working Unix system from scratch is not easy. It requires a lot of detailed knowledge of the various programs and libraries and config files scattered across the disk. For a sense of scale, the AT&T Unix System V manual was over 1100 pages, plus an 800 page programmer's guide and a handful of other manuals … and that was 40 years ago. That's a lot of specialized knowledge that I don't really have.
But still, this is something I've wanted to do for years and after countless hours of work, I finally have a glimpse of what it can look like. I have a lot to learn and a lot of work to do yet, but I'm certain I can figure it out.
I'm still hoping I can get this running multi-user on all those terminals in time for VCF Southwest in June. The show is just a few weeks away and I have a lot of work to do.
#mc68030#motorola 68k#motorola 68030#debugging#wrap030#retrotech#troubleshooting#netbsd#at&t unix#unix#unixporn#operating systems#os development#retro computing#retrocomputing#homebrew computer#homebrew computing#usagi electric#vcfsw#vcf southwest
19 notes
·
View notes
Text
the thing that gets me about the lack of technological literacy in a lot of young gen z and gen alpha (NOT ALL. JUST A LOT THAT I SEE.) isn't necessarily the knowledge gap so much as it's the lack of curiosity and self-determination when it comes to interacting with technology.
you have the knowledge gap side of things, obviously, which highlights issues related to the experience of using pieces of hardware/software becoming detached from the workings of the hardware/software itself. you start seeing people (so called "ipad kids") who are less and less familiar with the basics of these machines—like knowing how to explore file and system directories, knowing what parts of the system and programs will be using the most power and interacting with each other, knowing what basics like RAM and CPU are and what affects them etc. these aren't things you need to sink a lot of time into understanding, but they seem to be less and less understood as time has gone on.
and this lack of familiarity with the systems at work here feeds into the issue that bothers me a lot more, which is a lack of curiosity, self-determination, and problem solving when younger people use their technology.
i'm not a computer scientist. i'm not an engineer. i have an iphone for on-the-go use and i have a dinky 2017 macbook air i use almost daily. that's it! but i know how to pirate things and how to quality check torrented material. i know how to find things in my system directories. i know how to format an external hard drive for the specifications of my computer. i know how to troubleshoot issues like my computer running slowly, or my icloud not syncing, or more program-specific problems. this is NOT because i actually know a single thing about the ~intricacies~ of hardware or software design, but because i've taken time to practice and to explore my computer systems, and MOST IMPORTANTLY!! to google things i don't know and then test out the solutions i find!!!!
and that sounds obvious but it's so clear that its just not happening as much anymore. i watched a tiktok the other day where someone gave a tutorial on how to reach a spotify plugin by showing how to type its url in a phone's browser search bar, then said "i'll put the url in the comments so you guys can copy and paste it!!!!!" like ?????? can we not even use google on our own anymore?? what's happening???
this was a long post and it sounds so old of me but i hear this lack of literacy far too much and the defence is always that it's not necessary information to know or it's too much work but it is necessary for the longevity and health of your computers and the control you have over them and it ISN'T too much work at all to figure out how to troubleshoot system issues on your own. like PLEASE someone help.
#part of it is at the fault of the technology itself#phones and tablets hide a lot of their system workings in favour of app-forward interfaces#unlike pcs and laptops which have them easily accessible at start up#but once again.... the lack of curiosity... troubleshooting.... problem solving#long post#and this isn't even going into the lack of problem-solving and self-driven research when it comes to interacting with media#the ''what song is this????'' ''what movie is this???'' ''what is this from????'' PLEASE where is the LOOKING the SEARCHING the FINDING OUT
52 notes
·
View notes
Text
How to Train Employees on New Video Conferencing Software

Introduction
In today’s swift-paced, virtual international, the desire for valuable communique has under no circumstances been extra central. As organizations maintain to evolve to far flung work and hybrid fashions, gaining knowledge of video conferencing tools is main. This article goals to grant a finished handbook on easy methods to practice staff on new video conferencing tools. By leveraging advanced conference room audio video equipment and working out the nuances of digital communication, firms can verify that their teams are smartly-fitted to have interaction with buyers and associates readily.
Understanding Video Conferencing Tools What Are Video Conferencing Tools?
Video conferencing methods are device applications that permit participants to communicate in precise-time due to audio and visual channels over the cyber web. Popular structures consist of Zoom, Microsoft Teams, Google Meet, and Cisco WebEx. These gear are predominant for accomplishing conferences, webinars, and collaborative projects devoid of the need for bodily presence.
Why Are Video Conferencing Tools Important? conference room audio video equipment Flexibility: Employees can sign up meetings from virtually at any place. Cost-Effective: Reduces tour prices associated with in-user conferences. Enhanced Collaboration: Facilitates genuine-time sharing of archives and screens. Engagement: Offers traits like polls, chat containers, and breakout rooms to enhance interplay. Key Components of Conference Room Video Conferencing Equipment Essential Hardware
To make use of video conferencing conveniently, having the correct video convention room equipment is quintessential. Here’s a breakdown of principal hardware:
Cameras: High-definition cameras that trap clean graphics. Microphones: Quality microphones ascertain sound clarity. Speakers: Good speakers furnish audible sound without distortion. Software Solutions
Having potent instrument solutions is similarly fundamental. Look for structures that integrate seamlessly with current techniques and be offering user-pleasant interfaces.
How to Train Employees on New Video Conferencing Tools
Training laborers on new video conferencing methods requires a strategic method. Here’s a step-through-step marketing consultant:
Step 1: Assess Current Skill Levels
Before diving into instruction sessions, investigate your workers' contemporary familiarity with video conferencing gear. This should be would becould very well be finished via surveys or informal discussions.
Why Is This Important?
Understanding the baseline means degree allows for you to tailor your preparation application as a result. For instance, if most employees are already accepted with ordinary functionalities but war with evolved good points like monitor sharing or breakout rooms, focus your classes there.
Step 2: Create Training Materials
Develop finished training resources that disguise all aspects of the selected video conferencing tool—from setup guidance to troubleshooting recommendations.
Types of Training Materials: User Manuals
youtube
2 notes
·
View notes
Text
The following categories are not exhaustive; they are written only to give you an idea:
*Basically computer literate: I understand the difference between what is in my computer and what is in the cloud, can operate the basic functions of Word/Excel/Power Point (or their non-Mycrosoft equivalents), can type with more than two fingers, know at least two keyboard shortcuts, know how to organize folders, and manage right click options, can learn my way around a program by trial and error.
**Computer fluent: I can operate most/all the elements of an office package. I have taken more than one college-level computer science related course. I can do basic HTML coding. I can find creative solutions to problems by using more than one program in combination. I know what a command line is and know a handful of basic commands.
***Computer proficient: I am a professional in the IT field or could be. I can "do code", and know several programming languages, and can make a program if I want. I am knowledgeable about how the innards both software and hardware work.
33 notes
·
View notes
Text
Recover Stolen Crypto

Cryptocurrency has revolutionized the way we transact, offering decentralized and secure solutions for the modern economy. But with these benefits come risks, including the possibility of theft. Crypto theft can be devastating, leaving victims feeling powerless due to the anonymity of blockchain transactions. However, while challenging, recovering stolen crypto isn’t impossible. This guide will walk you through the steps to maximize your chances of retrieving lost funds and fortify your crypto security. Recover stolen crypto
Understanding How Crypto Theft Happens
Phishing Attacks
Phishing involves tricking users into revealing sensitive information such as private keys or wallet passwords. Scammers often impersonate legitimate platforms via fake websites or emails designed to look authentic. Once you input your details, they gain access to your wallet.
Hacking of Wallets and Exchanges
Crypto wallets and exchanges are prime targets for hackers. Weak security protocols, vulnerabilities in the platform, or user negligence can lead to unauthorized access and fund transfers.
Social Engineering Scams
These scams prey on human psychology. For instance, scammers may pose as trusted individuals or companies, convincing victims to transfer funds or disclose sensitive information.
Malware and Keyloggers
Cybercriminals use malware or keyloggers to monitor user activity. When you type your wallet credentials, the software captures and transmits the data to the attacker.
Immediate Steps to Take After Crypto Theft
Stay Calm and Act Quickly
Panic can lead to poor decisions. Assess the situation logically and act swiftly to prevent further losses.
Identify the Theft Details
Review your transaction history to determine when and how the theft occurred. Note the wallet addresses involved, the amount stolen, and the transaction ID.
Secure Remaining Funds
Transfer your remaining funds to a secure wallet. Hardware wallets or cold storage solutions are preferable as they are offline and immune to hacking.
Contacting Relevant Authorities
Reporting to Local Law Enforcement
File a report with your local authorities. While they may lack blockchain expertise, having an official record can support further recovery efforts.
Involving Cybercrime Units
Specialized cybercrime divisions can investigate the theft and collaborate with international organizations if needed.
Engaging Regulators Like SEC
In cases involving fraudulent investments, report the incident to regulatory bodies like the SEC or FCA to initiate investigations.
Notifying Crypto Platforms and Wallet Providers
How Exchanges Can Assist
Notify the exchange where the stolen funds were transacted. They may freeze suspicious accounts or provide information to investigators.
The Role of Wallet Providers
Wallet providers might help in identifying security vulnerabilities or advising on recovery steps.
Sharing Transaction Details
Provide all relevant details, including the transaction hash, wallet addresses, and any communication with the scammer.
Utilizing Blockchain Analysis Tools
How Blockchain Transparency Aids Recovery
Blockchain’s immutable ledger allows you to trace fund movements. With the right tools, you can monitor the thief’s wallet and subsequent transfers.
Popular Blockchain Analysis Tools
Platforms like Chainalysis, CipherTrace, and Elliptic specialize in tracking stolen cryptocurrency and identifying patterns.
Tracking Stolen Funds
Collaborate with professionals who use these tools to increase your chances of recovering the funds.
Hiring a Cryptocurrency Recovery Expert
Benefits of Professional Help
Experts have the technical knowledge and resources to trace transactions, liaise with platforms, and initiate recovery processes.
Vetting Recovery Agencies for Legitimacy
Ensure the agency has a proven track record. Beware of additional scams that exploit victims seeking help.
Avoiding Additional Scams
Never pay upfront fees without verifying the agency’s legitimacy. Genuine recovery services operate transparently.
Using Social Media and Community Networks
Engaging the Crypto Community
Post about your stolen crypto on forums, Reddit, or Twitter. The community often shares valuable insights or connects you with experts.
Raising Awareness About Stolen Funds
Highlighting the theft publicly can deter thieves from cashing out and put pressure on platforms to assist.
Success Stories
Many individuals have successfully recovered their stolen crypto by rallying community support and leveraging online networks.
Legal Options for Recovering Stolen Crypto
Filing Lawsuits
If you have enough evidence to identify the thief, you may file a lawsuit. Courts can issue orders to freeze assets or compel exchanges to provide information about suspicious accounts.
International Legal Frameworks
Cryptocurrency theft often crosses borders, making it necessary to engage international legal frameworks like the Hague Convention. Collaborating with global enforcement agencies can enhance recovery efforts.
Challenges with Jurisdiction
Jurisdictional issues complicate legal proceedings. Many crypto criminals operate in countries with lax regulations, making prosecution and recovery harder.
Preventative Measures to Protect Cryptocurrency
Using Hardware Wallets
Hardware wallets store private keys offline, making them virtually immune to hacking. They are the gold standard for crypto security and should be your primary storage method for large holdings.
Enabling Two-Factor Authentication (2FA)
2FA adds an additional layer of security to your crypto accounts by requiring a second verification step. Always enable it, preferably using an authenticator app rather than SMS.
Avoiding Suspicious Links and Emails
Phishing scams often start with an innocent-looking link or email. Be cautious and double-check URLs before entering sensitive information. Bookmark trusted platforms to avoid accidental clicks on fake sites.
Educating Yourself on Crypto Scams
Recognizing Common Scam Patterns
From Ponzi schemes to fake giveaways, crypto scams come in many forms. Stay informed about the latest trends and tactics used by scammers.
Staying Updated with News and Security Tips
Follow trusted crypto news outlets and cybersecurity blogs. Awareness is your best defense against evolving threats in the crypto space.
Building a Secure Crypto Environment
Regular Wallet Audits
Periodically review your wallet and transaction history to identify unauthorized activity early. This practice can prevent small breaches from escalating into significant losses.
Diversifying Storage Solutions
Spread your funds across multiple wallets. Use a combination of hardware wallets, paper wallets, and software wallets for added security.
Investing in Cybersecurity Tools
Firewalls, antivirus software, and VPNs can protect you from malware and other digital threats. These tools are essential for safe crypto trading and storage.
Understanding the Limits of Recovery
Why Crypto Recovery Isn’t Guaranteed
The decentralized and pseudonymous nature of blockchain technology makes fund recovery difficult. Once funds are transferred to a thief’s wallet, reversing the transaction is nearly impossible without their cooperation.
Managing Expectations
While recovery efforts are worth pursuing, it’s essential to prepare for the possibility that your funds may not be recovered. Focus on improving your security to prevent future losses.
The Role of Decentralized Finance (DeFi) in Crypto Security
How DeFi Protocols Enhance Transparency
DeFi platforms operate on smart contracts, which are transparent and immutable. This openness can help in tracking fraudulent activity and ensuring secure transactions.
Risks Associated with DeFi Platforms
Despite their benefits, DeFi platforms are not immune to vulnerabilities. Exploits in smart contracts and lack of insurance can lead to significant losses.
Recovering stolen cryptocurrency is no easy feat, but it’s not entirely hopeless either. By taking immediate action, leveraging blockchain tools, and engaging with experts, you can increase your chances of recovering your funds. Most importantly, prioritize prevention by adopting stringent security measures. Remember, in the world of cryptocurrency, staying one step ahead of scammers is your best protection.
Contact Info: Email: - [email protected]
2 notes
·
View notes
Text
What Future Trends in Software Engineering Can Be Shaped by C++
The direction of innovation and advancement in the broad field of software engineering is greatly impacted by programming languages. C++ is a well-known programming language that is very efficient, versatile, and has excellent performance. In terms of the future, C++ will have a significant influence on software engineering, setting trends and encouraging innovation in a variety of fields.
In this blog, we'll look at three key areas where the shift to a dynamic future could be led by C++ developers.
1. High-Performance Computing (HPC) & Parallel Processing
Driving Scalability with Multithreading
Within high-performance computing (HPC), where managing large datasets and executing intricate algorithms in real time are critical tasks, C++ is still an essential tool. The fact that C++ supports multithreading and parallelism is becoming more and more important as parallel processing-oriented designs, like multicore CPUs and GPUs, become more commonplace.
Multithreading with C++
At the core of C++ lies robust support for multithreading, empowering developers to harness the full potential of modern hardware architectures. C++ developers adept in crafting multithreaded applications can architect scalable systems capable of efficiently tackling computationally intensive tasks.

C++ Empowering HPC Solutions
Developers may redefine efficiency and performance benchmarks in a variety of disciplines, from AI inference to financial modeling, by forging HPC solutions with C++ as their toolkit. Through the exploitation of C++'s low-level control and optimization tools, engineers are able to optimize hardware consumption and algorithmic efficiency while pushing the limits of processing capacity.
2. Embedded Systems & IoT
Real-Time Responsiveness Enabled
An ability to evaluate data and perform operations with low latency is required due to the widespread use of embedded systems, particularly in the quickly developing Internet of Things (IoT). With its special combination of system-level control, portability, and performance, C++ becomes the language of choice.
C++ for Embedded Development
C++ is well known for its near-to-hardware capabilities and effective memory management, which enable developers to create firmware and software that meet the demanding requirements of environments with limited resources and real-time responsiveness. C++ guarantees efficiency and dependability at all levels, whether powering autonomous cars or smart devices.
Securing IoT with C++
In the intricate web of IoT ecosystems, security is paramount. C++ emerges as a robust option, boasting strong type checking and emphasis on memory protection. By leveraging C++'s features, developers can fortify IoT devices against potential vulnerabilities, ensuring the integrity and safety of connected systems.
3. Gaming & VR Development
Pushing Immersive Experience Boundaries
In the dynamic domains of game development and virtual reality (VR), where performance and realism reign supreme, C++ remains the cornerstone. With its unparalleled speed and efficiency, C++ empowers developers to craft immersive worlds and captivating experiences that redefine the boundaries of reality.
Redefining VR Realities with C++
When it comes to virtual reality, where user immersion is crucial, C++ is essential for producing smooth experiences that take users to other worlds. The effectiveness of C++ is crucial for preserving high frame rates and preventing motion sickness, guaranteeing users a fluid and engaging VR experience across a range of applications.

C++ in Gaming Engines
C++ is used by top game engines like Unreal Engine and Unity because of its speed and versatility, which lets programmers build visually amazing graphics and seamless gameplay. Game developers can achieve previously unattainable levels of inventiveness and produce gaming experiences that are unmatched by utilizing C++'s capabilities.
Conclusion
In conclusion, there is no denying C++'s ongoing significance as we go forward in the field of software engineering. C++ is the trend-setter and innovator in a variety of fields, including embedded devices, game development, and high-performance computing. C++ engineers emerge as the vanguards of technological growth, creating a world where possibilities are endless and invention has no boundaries because of its unmatched combination of performance, versatility, and control.
FAQs about Future Trends in Software Engineering Shaped by C++
How does C++ contribute to future trends in software engineering?
C++ remains foundational in software development, influencing trends like high-performance computing, game development, and system programming due to its efficiency and versatility.
Is C++ still relevant in modern software engineering practices?
Absolutely! C++ continues to be a cornerstone language, powering critical systems, frameworks, and applications across various industries, ensuring robustness and performance.
What advancements can we expect in C++ to shape future software engineering trends?
Future C++ developments may focus on enhancing parallel computing capabilities, improving interoperability with other languages, and optimizing for emerging hardware architectures, paving the way for cutting-edge software innovations.
10 notes
·
View notes
Text
First Time Investing in Crypto: Tips for New Traders on the Digital Coin Market
This has changed the financial landscape for good; it is the first time in history that investors have a share of this type since cryptocurrency entered the market. But then again, getting into the crypto market to begin with can be incredibly intimidating for a novice. This includes some key tips that you must know for making trade-offs more intelligent and how to invest in cryptocurrencies.
1. Understand the Basics

Understand the basic principles of what Cryptocurrency is, how it works before you invest. If you're unfamiliar, cryptocurrencies are basically decentralized systems, operating with a peer-to-peer framework, that let users do all sorts of things like get rewards for paying on time or using an app. Because they are not organically produced like typical tender, these financial tools are meant to be circulated in a decentralized way via blockchain networks. Educate yourself onwards like blockchain, altcoins, wallets and exchanges.
2. Do Your Research
The value of cryptocurrencies is influenced by a number of factors, and this makes it an extremely volatile market. Learn about various cryptocurrencies and how they are used. Tools like CoinMarketCap and CoinGecko show trends, rankings other handy information regarding ranging and past data. Follow us on Twitter for more news and updates on the Bitcoin space.
3. Diversify Your Portfolio

Investors apply diversification in their investment strategies. Diversify by investing in multiple cryptocurrencies I mean, everyone knows Bitcoin and Ethereum — why not looking a little bit further down the line at some promising altcoins with real fundamentals. A healthy mix of investments can ensure you have a little exposure to any type of gain or loss that may arise.
4. Only Invest What You Can Afford to Lose
The world of crypto is such that even the prices can and do tend to rise or crash in a jiffy, thanks to high volatility. Gamble only with money you can afford to lose without impacting your finances. Never borrow to invest in crypto or use your emergency savings for crypto investing. This approach ensures that you still are able to stay financially safe in case there's a downtrend.
5. Choose a Reliable Exchange

It is important to be sure that you deal with reliable cryptocurrency exchanges for safe trading. Search for exchanges with strong security protocols, a simple UI, and broad coin support. Some of the most trusted exchanges that people have been using include Binance, Coinbase and Kraken. Are they regulated and insured for digital assets.
6. Secure Your Investments
In the world of crypto, security is vital. Keep your cryptocurrencies on hardware wallets or in cold storage solutions; simply turn on 2FA in your exchange accounts and do not publish or disclose the private keys. Keep your software up to date and watch out for phishing attacks and malware.
7. Stay Informed and Adapt

As we know the crypto market is alive and never takes a nap. Learn from the market, regulatory and tech changes. Engage in some of the crypto community forums on platforms like Reddit, Twitter and Telegram to get the benefits of inside knowledge from other investors. Change your investment plan based on new informational and market circumstances
8. Have a Long-Term Perspective
Although there is money in short-term trading, it often requires quite a bit of time and skill to excel what you do. Long term investment strategy If you are beginner, Long term is the best way for you to invest your money from beginning. Look at the long term growth potential of cryptocurrencies instead of trying to make a quick buck. I read many books and listend to a lot of podcasts about the stock market, nearly all these sources agreed that patience and discipline was key to becoming a successful long-term investor.
9. Seek Professional Advice

If you are uncertain about the investments, you can get help from financial advisors or even some crypto experts. They can offer some personalized advice, depending on your financial goals and comfort with risk. Expert help will make it easier for you to manage the particularly volatile world of crypto.
Conclusion
Investing in cryptocurrency can also be a lucrative endeavor as long the trader is well-versed when it comes to his or her craft. These basic principles, combined with extensive research, establishing a diversified portfolio, and security first will put you in good stead on your crypto investment journey. The key is to stay informed, adapt and think long-term in order for you to succeed.
#crypto#cryptocurrency#cryptocurreny trading#cryptocommunity#investing#economy#investment#bitcoin#ethereum#blockchain#personal finance#finance
4 notes
·
View notes
Text
HELLO!FRIENDS!!!! PHONE IS REPAIRED i am typing on it right now
However before we repaired it we wrapped two elastic bands around it and the guy told us to keep them on for as long as possible (which my mom says is like 1 week....)
so I can't really draw on it yet X) they are soo inconvenient hhh but soon enough!!! sorry to keep everyone waiting
Im trying to use my laptop instead but god thay is giving me a hard time too bc my laptop kinda has the worst hardware ever like the design is seriously Stupid and inconvenient (it broke—physically—just a little over a year after it was bought and we had to repair it .......)
it's v laggy too even though i barely have anythig on it, I even deleted some of my old stuff like (my precious) shimejis, did a thorough virus scan, did that windows disk cleanup and still nothing, mostly it's firefox that lags
I even considered to boot up my old laptop and try to fix its software, it is very sturdy but i had it since I was 10 or so and it's just kinda old and slow now so I doubt it can handle my games and stuff
my electronics are acting up at a time that I cannot afford them to act up At all... SIGH wish me luck navigating
anyway, how you guys been!!! it's very difficult to use my phone like this so i will try and reach a solution with my laptop(s)
#extraterrestrial noises#at least my mom said i might get a newphone soon!! not trusting this one anymore#its shown to be very poor in quality hardware wise the screen was just the last straw
2 notes
·
View notes
Text
CLOUD COMPUTING: A CONCEPT OF NEW ERA FOR DATA SCIENCE
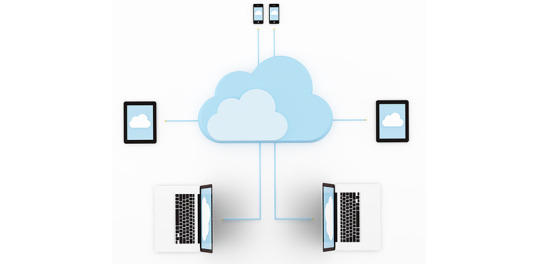
Cloud Computing is the most interesting and evolving topic in computing in the recent decade. The concept of storing data or accessing software from another computer that you are not aware of seems to be confusing to many users. Most the people/organizations that use cloud computing on their daily basis claim that they do not understand the subject of cloud computing. But the concept of cloud computing is not as confusing as it sounds. Cloud Computing is a type of service where the computer resources are sent over a network. In simple words, the concept of cloud computing can be compared to the electricity supply that we daily use. We do not have to bother how the electricity is made and transported to our houses or we do not have to worry from where the electricity is coming from, all we do is just use it. The ideology behind the cloud computing is also the same: People/organizations can simply use it. This concept is a huge and major development of the decade in computing.
Cloud computing is a service that is provided to the user who can sit in one location and remotely access the data or software or program applications from another location. Usually, this process is done with the use of a web browser over a network i.e., in most cases over the internet. Nowadays browsers and the internet are easily usable on almost all the devices that people are using these days. If the user wants to access a file in his device and does not have the necessary software to access that file, then the user would take the help of cloud computing to access that file with the help of the internet.
Cloud computing provide over hundreds and thousands of services and one of the most used services of cloud computing is the cloud storage. All these services are accessible to the public throughout the globe and they do not require to have the software on their devices. The general public can access and utilize these services from the cloud with the help of the internet. These services will be free to an extent and then later the users will be billed for further usage. Few of the well-known cloud services that are drop box, Sugar Sync, Amazon Cloud Drive, Google Docs etc.
Finally, that the use of cloud services is not guaranteed let it be because of the technical problems or because the services go out of business. The example they have used is about the Mega upload, a service that was banned and closed by the government of U.S and the FBI for their illegal file sharing allegations. And due to this, they had to delete all the files in their storage and due to which the customers cannot get their files back from the storage.
Service Models Cloud Software as a Service Use the provider's applications running on a cloud infrastructure Accessible from various client devices through thin client interface such as a web browser Consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, storage
Google Apps, Microsoft Office 365, Petrosoft, Onlive, GT Nexus, Marketo, Casengo, TradeCard, Rally Software, Salesforce, ExactTarget and CallidusCloud
Cloud Platform as a Service Cloud providers deliver a computing platform, typically including operating system, programming language execution environment, database, and web server Application developers can develop and run their software solutions on a cloud platform without the cost and complexity of buying and managing the underlying hardware and software layers
AWS Elastic Beanstalk, Cloud Foundry, Heroku, Force.com, Engine Yard, Mendix, OpenShift, Google App Engine, AppScale, Windows Azure Cloud Services, OrangeScape and Jelastic.
Cloud Infrastructure as a Service Cloud provider offers processing, storage, networks, and other fundamental computing resources Consumer is able to deploy and run arbitrary software, which can include operating systems and applications Amazon EC2, Google Compute Engine, HP Cloud, Joyent, Linode, NaviSite, Rackspace, Windows Azure, ReadySpace Cloud Services, and Internap Agile
Deployment Models Private Cloud: Cloud infrastructure is operated solely for an organization Community Cloud : Shared by several organizations and supports a specific community that has shared concerns Public Cloud: Cloud infrastructure is made available to the general public Hybrid Cloud: Cloud infrastructure is a composition of two or more clouds
Advantages of Cloud Computing • Improved performance • Better performance for large programs • Unlimited storage capacity and computing power • Reduced software costs • Universal document access • Just computer with internet connection is required • Instant software updates • No need to pay for or download an upgrade
Disadvantages of Cloud Computing • Requires a constant Internet connection • Does not work well with low-speed connections • Even with a fast connection, web-based applications can sometimes be slower than accessing a similar software program on your desktop PC • Everything about the program, from the interface to the current document, has to be sent back and forth from your computer to the computers in the cloud
About Rang Technologies: Headquartered in New Jersey, Rang Technologies has dedicated over a decade delivering innovative solutions and best talent to help businesses get the most out of the latest technologies in their digital transformation journey. Read More...
#CloudComputing#CloudTech#HybridCloud#ArtificialIntelligence#MachineLearning#Rangtechnologies#Ranghealthcare#Ranglifesciences
9 notes
·
View notes
Text

#All Type of Hardware and Software solution#laptop repair center in sanpada#laptop repairing shop#hp laptop repair centre in sanpada
0 notes
Text
What distinguishes an unmanaged (self-managed) VPS from a managed one And how can I figure out which suits me the best?
When looking at web hosting options, it is essential to have a solid understanding of the distinction between managed virtual private servers (VPS) and unmanaged VPS. Those who are looking for an experience that is simple to use will find that managed virtual private servers (VPS) provide convenience in server setup, maintenance, and support. On the other hand, unmanaged virtual private servers (VPS) provide you with complete control over the server, allowing you to customize and administer it in any way you see fit.

This type of VPS is best for people or enterprises who value flexibility and cost-effectiveness. In this post, we will discuss the important differences that will assist you in selecting the virtual private server (VPS) solution that is best suited to meet your individual requirements.
VPS: What is it?
First, let's get a grasp on what virtual private server hosting (VPS) is and how it operates before we move on to analyzing the distinctions between managed and unmanaged VPS hosting. Virtual private server hosting (VPS hosting) is a method of delivering hosting services in which a single physical server is partitioned into several virtual servers. The processing power (CPU), memory (RAM), and storage space utilized by each virtual server are distinct from those utilized by any other machine.
In spite of the fact that these virtual servers are established on a single physical system, they conduct their operations independently of one another. As a result of the shared underlying hardware, each user is provided with their very own dedicated virtual server, which is analogous to having a dedicated physical server but at a lesser cost. Each user's data and applications are kept separate and secure, exactly as if they were running on their own physical server because the servers are geographically separated from one another. This ensures that the servers are isolated from one another.
What exactly is a managed virtual private server?
As the name suggests, managed virtual private servers (VPS) mean that you do not have to worry about the responsibilities that are associated with the server, such as administering and maintaining your server. Your web hosting provider will be responsible for monitoring and managing all of the server's functionality. In spite of the fact that you are familiar with the technical features of the server and how to manage it, outsourcing the management of the server to your web hosting provider will alleviate the stress of carrying out all of the procedures.
The specialists who work for your web hosting provider take full responsibility for the resources on your server. They also keep a constant watch on your server to identify any potential issues, and they are responsible for implementing any necessary updates and upgrades. In particular, for users who do not have a lot of time to devote to duties that are related to the server.
The Benefits of Using a Managed Virtual Private Server-
Managed VPS hosting, also known as virtual private server hosting, provides a multitude of advantages, particularly for customers who are more concerned with the development of their applications or businesses than with the management of server infrastructure. Below are the primary benefits that come with using this service:
Firewalls, virus scanning, intrusion detection, and frequent security upgrades are some of the robust security features that managed virtual private server (VPS) software providers implement. Data is protected and cyber dangers are avoided as a result of this.
By delegating server management to a dependable web hosting provider, customers are able to concentrate solely on the operations of their businesses or the creation of applications without having to worry about the infrastructure of their servers, security concerns, or other problems.
The hosting service offers users round-the-clock technical help during their membership. This involves the installation of servers, their maintenance, and the diagnosis and resolution of technical problems in a timely manner.
Managed virtual private server (VPS) plans typically include data restoration and periodic backup services in the event that problems arise. Data recovery is made simple and expedient by the supplier, who is responsible for maintaining backups and setups.
The activities associated with server management are handled by the web hosting provider. These responsibilities include the configuration of hardware and software, the updating and patching of operating systems, the monitoring of performance, and the carrying out of frequent backups. Users will have less of a load as a result, and the server will continue to function in a stable manner.
Through the use of this service, users are able to gain access to the knowledge and experience of server management specialists. The availability of technicians allows for the provision of recommendations and the enhancement of server performance.
In general, managed virtual private server services provide higher levels of stability and constant uptime. In order to reduce the amount of time of the outage, providers utilize redundant infrastructure and monitoring technologies.
Managed virtual private server hosting is, in a nutshell, the best option for people and enterprises who require a high level of security, simplicity of management, and reliability. It provides a full solution for hosting websites and applications with little fees associated with the technical side of things and maximum peace of mind throughout the process.
What is the Unmanaged Virtual Private Server?
Your hosting provider will investigate a physical server and its availability when you use an unmanaged virtual private server (VPS). This means that you are responsible for managing and maintaining the server, as well as managing and maintaining the server itself. Choosing unmanaged virtual private server hosting necessitates either possessing the necessary technical expertise or employing a group of professionals to administer your server.
The use of an unmanaged virtual private server (VPS) is preferable for a well-established organization, regardless of how technically proficient you may be. The development of your company will be the primary focus of your attention if you are a startup. Your server management needs to be handled by a team and a full-time position in order to be successful.
The Benefits of Using an Unmanaged Virtual Private Server-
There are a lot of advantages to using unmanaged VPS (Virtual Private Server) hosting, particularly for users who are technically capable of managing their own server environment. The primary advantages are as follows:
Users are equipped with complete control, which enables them to install, configure, and optimize the server in accordance with their own requirements.
This presents users with the opportunity to increase their skills in managing and operating servers.
There is no dependence on third-party vendors for tasks such as software upgrades, and it may be tailored to meet personalized requirements.
Unmanaged virtual private servers (VPS) are typically more affordable than managed VPS because they do not include administration services, software upgrades, or technical support.
Security measures are under the authority of the users, who are responsible for ensuring their own safety.
The server can be customized in any way that the user desires, including the operating system, control panel, and software.
However, unmanaged virtual private servers are best suited for someone who possesses technical expertise or someone who can assist in managing the server. If this is not the case, a managed virtual private server (VPS) service, albeit being more expensive, can be a preferable option.
Which of These Options Should You Pick?
You are now aware that Managed Virtual Private Servers (VPS) and Unmanaged VPS each have their own set of advantages at their disposal. It is recommended that you go with unmanaged hosting if you are a professional in the field of technology, have experience maintaining servers, and have the ability to devote sufficient time to operating a server. If, on the other hand, you are a novice or a startup that has to concentrate on expanding your business, then managing a virtual private server (VPS) can be a laborious task.
The technical assistance that you receive with managed virtual private servers helps you save crucial hours. This enables you to concentrate on your primary goals, which may include managing your staff, making income, establishing relationships with customers, and other similar activities. Conversely, if you are concerned about the costs and have a good understanding of the server and how it is administered, then an unmanaged virtual private server (VPS) will be a better option for you.
Conclusion-
Users believe that it is dependable and risk-free to obtain a managed virtual private server (VPS) from a hosting provider, despite the fact that managed VPS is somewhat more expensive than self-managed VPS. This is because the price of managed VPS has decreased over time. It is also better to choose managed hosting if the procedure of setting up the server is going to have an impact on your company and take a significant amount of time.
Another aspect that should be taken into consideration is safety. It is not a bad idea to go with an unmanaged virtual private server (VPS) if you are willing to assume full responsibility for the safety of your server and be sure that it will be protected from the dangers that are there on the internet.

Janet Watson
MyResellerHome MyResellerhome.com We offer experienced web hosting services that are customized to your specific requirements. Facebook Twitter YouTube Instagram
1 note
·
View note
Text
Meaning of Bare Metal Server?
To understand the meaning of a bare metal server let’s understand the meaning of a web server, A web server can be said to be software or hardware that stores all the website’s files responds to client requests, and delivers the required files accordingly via the internet. The Meaning of Bare Metal server in simplest words can be said as a server that is created for a single person only with the most premium technology that can be availed in a physical server only i.e. it cannot be available virtually.
Meaning of Bare Metal Server
A bare metal server is a physical server, it is a kind of server that is dedicated to a single tenant, In a virtualized server the hardware resources such as CPU, RAM, Storage etc. are shared while here all of the resources are used by a single person only and are chosen as per our choice, as there is no co-dependency in this kind of server it not only facilitates the increased performance of the server but also reduces hustle as it removes additional layers of software that are put into making server services available virtually.
Here there’s also an additional benefit of making the server as customized as possible, As there is only a single user and the server is available physically, It can be created to please and cater to your needs. let’s understand how it can be customised to an extent:
Personalized selection of hardware components such as CPU, type of RAM, and Storage.
There can be an option to choose any kind of Operating System that is compatible with your website
In a bare metal server, you can have firewall rules to suit your application’s requirements which include defining IP addresses, setting up virtual LANs (VLANs), managing network security policies, etc.
In a bare metal Server, there is access to the server’s BIOS (Basic Input/Output System), which allows for low-level hardware configurations, such as hardware virtualization settings, and power management options.

Understanding the Difference between a Dedicated Server and a Bare Metal Server
As the working of bare metal server and dedicated server is quite similar, they both have resemblance such as they both are dedicated to a single tenant but they can’t be said as the same, The root difference doesn’t lie in the product but the working of the server the concept of bare metal servers arrived after some drawbacks of a dedicated server.
While a dedicated server provides multiple benefits it has some inevitable drawbacks such as dated hardware and long provisioning times. However, bare metal servers typically come with the most advanced hardware and software. They are a hosting provider’s prized asset or flagship because bare metal servers are specifically made to automate the provisioning process, they may be put up more quickly.
The hardware provided by bare metal servers is considerably more similar to a cloud service framework, with installation durations measured in minutes or hours and hardware ranging from low-cost to Top-of-the-line components, including graphics processing units (GPU). When it comes to hardware, bare-metal servers have an advantage thanks to their use of the most recent Intel Xeon processors, DDR4 RAM with Error Correcting Code (ECC), and NVMe solid-state drives (SSDs) rather than SATA SSDs and hard drives. Because of the combination of these components, In conclusion, bare-metal servers stand out as a high-performance hosting solution.
2 notes
·
View notes
Text
Reliable Laptop Service Center in PCMC - IT Solutions
IT Solutions provides professional laptop repair services in pcmc for all brands and models. Our technicians are experienced and certified to fix all types of laptop problems, including:
Screen repair Hardware repair Software repair Virus removal Data recovery And more!
We are committed to providing our customers with the best possible service. We will work with you to find a solution that fits your budget. We also offer a same-day turnaround on most repairs, so you can get your laptop back up and running quickly.
If you are experiencing problems with your laptop, please contact us today. We will be happy to help you get your laptop back in working order.
For More Details:
Contact no: 9503321889 / 9822391654
#laptop repair#laptop repair center#laptop service center#laptop repair services in pcmc#laptop service center in pcmc#authorized laptop service center in pcmc
5 notes
·
View notes
Text
VPS Hosting
Understanding VPS Hosting
Think about a virtual site where you may establish your online presence. A virtual private server (VPS) resembles your own private plot of land in the online world. In comparison to shared hosting, it is a powerful hosting solution that provides more resources and management. Imagine yourself relocating from a small flat to a large house. Let's start looking for the top VPS hosting company that specialises in serving Windows users. Virtual private servers, or VPSs, are a type of multi-tenant cloud hosting in which a user can access virtualized server resources online via a cloud or hosting provider.
Each VPS is set up on a real server that the cloud or hosting company manages and uses to run other VPSs. Although the underlying hardware and hypervisor are shared by all of the VPSs, each one runs its own operating system (OS), applications, and reserves its own set of system resources (for memory, computation, etc.)
Best VPS Hosting Provider
Looking for the best vps hosting provider take some points to consideration. The performance should be your first priority; you need a provider with sufficient processing power and memory to maintain the seamless operation of your website. Reliability is also very important. You don't want server problems to cause downtime for your website. Customer service is important, too. A responsive and accommodating support staff can spare you future hassles. Some of the factor that are taken into consideration during the selection of best vps hosting provider are as follows:-
Performance: For a seamless online experience, high-performance hardware and enough of resources are required. Look for a supplier who has expandable RAM, CPU, and storage so that your website can withstand variable traffic volumes without slowing down.
Dependability: Uptime is crucial. Select a service with a proven track record of frequent outages might result in lost sales and a poor user experience.
Customer service: Your hosting experience can go well or poorly depending on how quick and knowledgeable your customer service is. You may be sure that you will obtain prompt assistance during urgent situations if your provider provides 24/7 support through a variety of channels.
Scalability: Your provider of choice should make it simple to scale, allowing you to modify resources as your website changes. You won't outgrow your hosting solution too rapidly thanks to this flexibility.
Operating System Options: Verify the company offers Windows VPS hosting options if you need hosting that runs on Windows. Most important is compatibility with the applications you need.
Vps Window Hosting
Vps Window hosting is the answer if you're seeking for a hosting service designed for Windows. It's similar to having a house that is especially tailored to your needs. You may easily execute Windows-specific software and apps with Windows VPS hosting. The compatibility and familiarity of Windows may simplify your life, whether you're creating software, managing an e-commerce platform, or running a company website.
Conclusion
Windows VPS hosting is the answer if you're seeking for a hosting service designed for Windows. It's similar to having a house that is especially tailored to your needs. You may easily execute Windows-specific software and apps with Windows VPS hosting. The compatibility and familiarity of Windows may simplify your life, whether you're creating software, managing an e-commerce platform, or running a company website.The company must be reliable,24*7 support service,ensure good performance,scalibility also becomes problem in growth.
2 notes
·
View notes
Text
youtube
How to Fix Wrong Typing in Windows 11
Welcome to our comprehensive guide on resolving incorrect typing issues in Windows 11! If you've ever found yourself frustrated by mistyped characters, unexpected autocorrect, or unusual keyboard behavior on your Windows 11 system, you're in the right place. In this video, we'll walk you through step-by-step solutions to tackle these typing glitches and restore smooth, accurate typing experiences. 🔧 In this tutorial, you'll learn: Common causes behind wrong typing in Windows 11. Practical troubleshooting techniques to identify and resolve the issue. How to adjust autocorrect settings to match your typing style. Keyboard layout adjustments to ensure proper key mapping. Tips for dealing with hardware-related typing problems. Additional software solutions and settings tweaks. No more frustration over typos or mistyped words! Follow along with our easy-to-follow instructions and expert insights to regain control over your typing in Windows 11. Whether you're a casual user or a seasoned professional, our comprehensive tutorial has you covered. Say goodbye to keyboard woes and hello to accurate typing once again. Don't forget to like, subscribe, and hit the notification bell to stay updated on all our helpful Windows 11 tutorials and troubleshooting guides. If you found this video helpful, give it a thumbs up and share it with others who might be facing similar typing challenges. Let's make typing on Windows 11 a breeze together! 🔍 Keywords: Technology review, innovative gadgets, cutting-edge tech, electronics, Grand Tech Science & Technology. 🚀 In this Grand Tech Short, we explore the mind-blowing features of the [Product Name], demonstrating how it's reshaping the future of [relevant industry]. From its sleek design to powerful performance, we've got you covered! 🔗 Connect with us on [https://www.facebook.com/GrandTechLtd/] for behind-the-scenes and more tech goodness! ⏱ Timestamps: 00:00 - Introduction 01:15 - Unboxing and First Impressions 03:30 - Performance and Benchmarks 06:45 - Conclusion 👉 Watch more: [https://youtube.com/shorts/5AT_X7nRGw4?feature=share]"
2 notes
·
View notes