#and a cryptoprocessor
Explore tagged Tumblr posts
Text
My latest project is building a combined travel router-firewall and miniserver. It’s based on PC Engines APU2 (specifically apu2d4) embedded platform running either pfsense or OpenWRT. Turns out that there are fewer and fewer miniPCIe form-factor LTE/5G modems, so I’m experimenting with an m.2 to miniPCIe adapter to see if an m.2 cellular modem could be an option. Physically the adapter just fits!
Notes to self: M.2 and miniPCIe carry both PCIe and USB in the same physical connector. The APU2 mPCIe slots 1 and 2 support PCIe 2.0 and USB 2.0. An LTE modem using USB 3.0 data link must be able to fall back to USB 2.0 gracefully or it won’t work. Aside from improved frequency band support, anything beyond LTE Cat 6 card is wasted unless it uses a PCIe data link. It’s possible that PCIe-based LTE/5G modem can work at full speed; possibly worth experimenting if not too expensive.

#miniserver#personal projects#PC Engines#APU2#Internet-in-a-box#embedded computing#firewall#this thing is super low power consumption#but the processor is also pretty slow#albeit faster than most consumer router-firewalls#still it’s got at least a terabyte of storage#and wifi#and cellular#and 4GB of ECC memory#and a cryptoprocessor#and it can route at gigabit speed#it’s both making-do and extravaganza#depending on how you look at it#and I like to make things do more than they were meant to
1 note
·
View note
Text
Hello, everyone. Welcome to the crypto news updates of the week. Some positive news for Bitcoin holders, some negative news for the rest of the market. I will be talking about Bitcoin first since it is the highest-ranked coin. Crypto News Updates for this week The US Federal Reserve, US Treasury Department, and Federal Deposit Insurance Corporation are planning to release a new set of measures to monitor crypto-assets, Bloomberg reported on Thursday, September 13. According to the article, the institutions are currently working on a report that will provide insight into crypto markets and how the agencies can oversee them. A certain number of crypto exchanges have already agreed to work with US authorities on monitoring their platforms' transactions in order to comply with national security laws. Bloomberg notes that more than 20 exchanges have signed up for this program so far. Recently, South Korea's largest cryptocurrency exchange Bithumb announced that it has joined this initiative as well, but without providing details on what information it is planning to share with US authorities. The official website of Venezuela's Petro (PTR) project has been reportedly hacked by unknown attackers. This week, visitors of petro.gob.ve were redirected towards a fake website asking them to fill out a survey about Venezuelan citizens' cryptocurrency holdings and "misle
#cryptoinvestor#crypto price#crypto promotion#cryptopsy#crypto pump signals telegram#cryptoprocessor
0 notes
Text
Secure Cryptoprocessors

A secure cryptoprocessor is a dedicated microprocessor for simply cryptographic operations, with multiple physical security measures as a degree of tamper resistance.
Secure cryptoprocessors are used to be the keystone of a security subsystem, thereby eliminating the need for additional security measures.

Smartcards are the most widely deployed form a secure cryptoprocessor. These can be used to several purposes including:
Authentication
Personal Identification
Data Storage
Several comparison leverage this in some form such as Automated Teller Machines (ATMs), TV Set Top Boxes and Military Applications.
Security Features
Tamper-detecting and tamper-evident containment.
Conductive shield layers in the chip that prevent reading of internal signals.
Controlled execution to prevent timing delays from revealing any secret information.
Automatic zeroization of secrets in the event of tampering.
Chain of trust boot-loader which authenticates the operating system before loading it.
Chain of trust operating system which authenticates application software before loading it.
Hardware-based capability registers, implementing a one-way privilege separation model.
Source: https://en.wikipedia.org/wiki/Secure_cryptoprocessor
2 notes
·
View notes
Text
Homework 3-10: Cryptoprocessors
Finally
Going from ATMs to HSM to now... finally... at the core of it all - cryptoprocessors. It took us a while, but we made it.
What is a cryptoprocessor?
A cryptoprocessor is a processor dedicated to cryptographic operations (as the name suggests). But what does this mean? This means that all the algorithms are done in hardware, since we all know that hardware is faster than software 😏😏😏
Cryptoprocessors are able to accelerate encryption, enhance tamper and intrustion detection, enhance data and key protection, enhance security on memory access and I/O*.
Advantages of cryptoprocessors
Strong IP protection
Better protection of key data compared to simple storage encryption
Offers protection against vulnerability exploits, accomplished by layering software protection on top of hardware
Can be integrated into ASICs and FPGAs
Types of cryptoprocessors
There are several types of cryptoprocessors (thanks Quora.
Smartcards - input program instructions in encrypted form, decrypt the instructions to plain instructions which are then executed within the same cryptoprocessor chip where the decrypted instructions are inaccessibly stored such that the decrypted instructions are never revealed.
Trusted platform module (TPM) - specialized chip on an endpoint device that stores RSA encryption keys specific to the host system for hardware authentication
Hardware security module (HSM) - which is covered more in depth in the previous blogpost.
2 notes
·
View notes
Text
Cryptoprocessors, and hardware security modules
Secure cyrptoprocessors are dedicated microprocessors for carrying out cryptographic operations, they usually have some form of embedding to make any manipulation tamper-evident.
Hardware security modules contain one or more cryptoprocessors.
The trusted platform module is an international standard for a secure cyrptoprocessor
Cryptoprocessors are cool because they don't reveal keys or executable instructions on a bus, their purpose is to act as the keystone of a security sub-system, eliminating the need to protect the rest of the sub-system with physical security measures.
The goal is the cryptoprocessor recieves instructions in an encrypted form, decrypts them inside its perimiter to plain instructions, which it then executes within the perimiter. By never revealing the program instructions it prevents tampering of programs by technicians who may have legitimate access to the bus.
Cryptoprocessors have a number of pretty sweet features that ensure their security: * Tamper evidence * Conductive shield layers that prevent reading of internal signals * Hardware based registers that implement a one-way privilege sepeartion model * Automatically zeros out secrets in the even of tampering. * Chain of trust boot-loader which authenticates the operating system, before loading. * Chain of trust operating system with authenticates software before loading. * Internal battery
It provides you with some cool stuff like a random number generator, the ability to securely generate cryptographic keys, remote attestation which creates a nearly unforgeable hash summary of the hardware, and software configuration. Helping to verify that software has not been changed. We can also use it to ensure platform integrity, enable full disk-encryption and digital rights management.
The most common secure cryptoprocessor you know of is going to be a smart card. A piece of plastic the size of a credit card with an embedded integrated circuit.
How safe are they though? The IBM 4758 was attacked by a team at the University of Cambridge. Who found a flaw in the software loaded by the cryptoprocessor, making all the hardware features redundant!
1 note
·
View note
Text
Job Proposal: Analytic
Throughout the semester I have been working on technical challenges and extending my knowledge through videos watching videos.
Research
I kept an eye out for potential vulnerabilities in everyday scenarios and blogged about them.
Security Everywhere 1
Security Everywhere 2
Security Everywhere 3
Security Everywhere 4
Security Everywhere 5
I conducted research for homework activities and broadened my understanding of course content outside what was provided in lectures:
The Life Expectancy of a Computer
Some Type 1 and Type 2 Errors
Homework Secure Cryptoprocessors and Hardware
ATM Attacks
Outside of course content, I watched some videos of security talks in order to broaden my technical understanding. In particular:
Weaknesses in assembly code
Psychological defence against reverse engineers
Reflection
Here are some times where I reflected on cases we studied in class and other things security related.
Deep Water Horizon Week 1 Reflection Week 4 Case Study Week 4 Human Weakness A Sad Reflection Tutorial 7 Reflection
Application Most of my application of theory came through my something awesome where i tested different implementations of rootkits. You can read about it in my reports below. Something Awesome Progress Report 1
Something Awesome Progress Report 2
Something Awesome Progress Report 3
Something Awesome Progress Report 4
Something Awesome Progress Report 5
Something Awesome Progress Report 6
Reverse engineering was my other main form of application. I applied my knowledge through crackme challenges through the SecSoc Term 2 CTF reverse engineering challenges which you can read about later. Crackme 0x03
Ciphers were an easy way to apply theory into practice. Lack of entropy is something which allows us to break defences much faster than brute force. Documented here are times i applied this to substitution ciphers. Unfortunately i did not document my work on transposition ciphers. Solving Jazz’s Cipher
Mid-semester Exam Practice
1 note
·
View note
Text
Hardware Secure module and Secure cyptoprocessor
A hardware secure module is a physical computing device that safeguards and manages digital keys for strong authentication and provides crypto processing. These are typically a plug-in card / external device that attaches directly to a computer of network server
These also have features that provide tamper evidence such as visible signs of tampering. The vast majority of existing HSMs are mainly to manage secret keys and have a system to securely back up the keys they handle.

Secure cryptoprocessor:
This is a dedicated computer on a chip carrying out cryptographic operations and has a degree of tamper resistance. This does not output decrypted data onto a bus in a secure environment (recall 1521). The purpose of one of these bad boys is to act as the keystone of a security subsystem. Whats that? It is something that protects the subsystem eliminating the need to protect with physical security measures.
1 note
·
View note
Text
Secure processing & storage
Cryptoprocessors
In a post last week, I discussed some of the issues associated with system integrity and security associated with side channel attacks - you could potentially reverse engineer the keys used in the calculations. This is where cryptoprocessors come in to the equation - basically they are dedicated processors which are utilised when handling encrypted data. The idea is that unlike traditional processors which output decrypted data onto a bus, a cryptoprocessor doesn’t output this data. Instead it will perform all the operations and checks required of it within the unit itself and output the result - this means the security of the key isn’t reliant on that of the entire system, but just this individual unit.
This essentially means we have a smaller attack surface - from here we can apply a number of defensive measures:
Shielding to prevent external reading of electromagnetic signals
Uniform timing execution of certain operations to prevent ‘timing attacks’
Validation of chain of trust modules for both OS and application software in case either is hijacked
Implementation of a unidirectional privilege escalation model
Tamper detection and wiping of registers in case of tamper
In the majority of cases the security that these measures provide is fairly good, however some of these protections are heavily reliant on the fact that an attacker doesn’t have physical access to the machine
Hardware Security Modules
These modules are essentially responsible for generation, processing and storage of keys; they often contain a number of cryptoprocessors. They are designed in such a way that the only means to obtain data from the module is through physical access, however they will often provide multiple visible signs of tampering if this occurs. One of their main uses is in public key infrastructure - for example in the generation and usage of asymmetric key pairs used by certification authorities.

High stakes operations such as banks often use them when handling user data such as pins, magnetic stripe cards and the key sets used in smart cards. Hardware wallets used with cryptocurrencies are another useful example - they store the keys associated with a particular wallet address. If the wallet is sent the template of a transaction, it can sign it internally within the module and provide it back to the source system for upload to the blockchain. At no point outside the module is the private key exposed.
1 note
·
View note
Text
AMD confirms that TPM is a problem for some PCs running Windows 11
AMD confirms that TPM is a problem for some PCs running Windows 11
It looks like Windows 11 users with AMD Ryzen processors, and affected by an issue on their hardware that is causing “temporary pauses in system interactivity or responsiveness”, will have to wait until May for a BIOS fix. from the chipmaker. The issue affects Windows 10 and Windows 11 systems with Firmware Trusted Platform Module (fTPM) enabled. The TPM cryptoprocessor handles cryptographic…

View On WordPress
0 notes
Text
AMD confirms that TPM is a problem for some PCs running Windows 11
AMD confirms that TPM is a problem for some PCs running Windows 11
It looks like Windows 11 users with AMD Ryzen processors, and affected by an issue on their hardware that is causing “temporary pauses in system interactivity or responsiveness”, will have to wait until May for a BIOS fix. from the chipmaker. The issue affects Windows 10 and Windows 11 systems with Firmware Trusted Platform Module (fTPM) enabled. The TPM cryptoprocessor handles cryptographic…

View On WordPress
0 notes
Text
HPE iLO5 Firmware Security – Go Home Cryptoprocessor, You're Drunk
HPE iLO5 Firmware Security – Go Home Cryptoprocessor, You’re Drunk
Copyright © Informa PLC. Informa PLC is registered in England and Wales with company number 8860726 whose registered and head office is 5 Howick Place, London, SW1P 1WG. Join the Read the full story – https://www.knowasiak.com/hpe-ilo5-firmware-security-go-home-cryptoprocessor-youre-drunk/ Signup on KC.inc to make your day easy reading world-class articles – https://www.knowasiak.com/register/
View On WordPress
0 notes
Text
Homework 3-9: HSM - High School Musical?
Prank'd
HSM as in hardware security module, not high school musical #baited xd
What's a Hardware Security Module?
A hardware security module (HSM) is a physical crypto-processor which manages, processes and stores keys. Its encasing is tamper-resistant and tamper-evident so that you are able to find out if someone has tried to attack it. HSMs usually come in the form of a plug-in card or an external devices which attaches to a computer or network server.
Why use one?
Hardware security modules aim to protect transactions, identities, and applications, such as in the case of ATMs. They secure cryptographic keys and provisioning encryption, decryption, authentication and digital signing.
Breakdown of what it does
Cryptographic key generation
Cryptographic key storage
Key management
Use of cryptographic and sensitive data material eg. encryption or digital signature functions
Offloading application servers for complete asymmetric and symmetric cryptography
securing a full software stack from logical or physical attacks
^ (Thanks Wikipedia)
Relevant Standards
Due to the important role of HSMs and the havoc it would cause if they were to be successfully hacked, there are international standards in place, such as the Common Criteria or Federal Information Processing Standards (FIPS140). The highest level of FIPS140 accreditation available is Security Level 4, to which only one HSM has been able to obtain. When used to secure financial payments, the HSM must also be validated by the Payment Card Industry Security Standards Council.
There are four levels of security:
Components must be production grade and various egregious kinds of insecurity must be absent.
Requires physical tamper-evidence and role-based authentication.
Requires physical tamper-resistance and and identity-based authentication.
Makes the physical security requirements more stringent, and requires robustness against environmental attacks
(^ Thanks again Wikipedia)
Note...
It seems that I have made a mistake in the order of my blogging. I've completed a post on ATM attacks/defence, I've just finished looking up what a hardware module is and now I'm about to start looking up what cryptoprocessors are. I've done it the wrong way around!
2 notes
·
View notes
Text
Study Guide Content Mastery Teacher Edition Chemistry

Baritone ukulele songbook. Chemistry Matter And Change Study Guide For Content Mastery Teacher Edition This is likewise one of the factors by obtaining the soft documents of this chemistry matter and change study guide for content mastery teacher edition by online. You might not require more times to spend to go to the books foundation as with ease as search for them. La donna del lago. https://nodehunter228.tumblr.com/post/658028351101992960/your-own-logo.
Study Guide Content Mastery Teacher Edition Chemistry Answers
Study Guide Content Mastery Teacher Edition Chemistry 1
Chemistry Matter And Change Study Guide For Content Mastery Teacher Edition
Study Guide Content Mastery Teacher Edition Chemistry Grade
Study Guide Content Mastery Teacher Edition Chemistry Pdf
Chemistry Matter Change Study Guide For Content Mastery Student Edition Author: McGraw-Hill Education Publish On: 2001-03-30 There are worksheets and study tools for each section of the text that help teachers track students' progress toward understanding concepts.
STUDY GUIDE FOR CONTENT MASTERY Section 12.2 Stoichiometric Calculations In your textbook, read about mole-to-mole conversion. Read the following passage and then solve the problems. In the equation that follows each problem, write in the space provided the mole ratio that can be used to solve the problem.
Access Free Chemistry Study Guide Content Mastery Teacher Edition learning̶and significantly improve both teaching and learning. Cathy Vatterott is an education professor and researcher at the University of Missouri-St. Louis, a former middle school teacher and principal, and a parent of a college graduate. She has learned from her.
Amazon.com: Chemistry: Matter and Change; Study Guide for Content Mastery (220). This bar-code number lets you verify that you're getting exactly the right version or edition of a book. The 13-digit and 10-digit formats both work. Chemistry Matter and Change Teacher Wraparound.
Speed
Health
Study Guide Content Mastery Teacher Edition Chemistry Answers
3171
Study Guide Content Mastery Teacher Edition Chemistry 1
16288
12225
20139
T182 Chemistry: Matter and Change Study Guide for Content Mastery Answer Key 9 The Covalent Bond molecule covalent bond sigma bond exothermic pi Chemistry: Matter and Change • Chapter 9 Copyright © Glencoe/McGraw-Hill, a division of the McGraw-Hill Companies, Inc. Study Guide..
..Guide for Content Mastery Answer Key Name Date 2 CHAPTER Class Name Date CHAPTER Answer Key Name Date CHAPTER 2 Class STUDY GUIDE FOR CONTENT MASTERY Section 2.3 In your textbook, read about rounding off numbers. 14. Round the following to four significant..
Each textbook chapter has six study guide pages of questions and activities for you to complete as You will find that the directions in the Study Guide for Content Mastery are simply stated and easy to 14. Earth's lithosphere is the rigid outer shell of the planet. 15. The water in Earth's oceans, seas..
Start studying Chapter 14 Mastery Training. Learn vocabulary, terms and more with flashcards, games and other study tools. Only RUB 220.84/month. Chapter 14 Mastery Training. STUDY. Flashcards.
192 Chapter 30 Earth Science: Geology, the Environment, and the Universe Study Guide for Content Mastery. CHAPTER 3 1 A Solar System Is Born SECTION Formation of the Solar System BEFORE YOU READ After you read this section, you should be able to answer these questions: What is a..
Chapter 14 Supplemental Practice Problems. p.985. We have your answer. Navigate to your page and exercise.
Chapter 18 Study Guide For Content Mastery Chemical Equilibrium .. Equilibrium, it ends happening physical one of the favored book Chapter 18 Study. Download Ebook Study Guide . For Content Mastery Chemistry. Answer every needs in the manner of having significantly cash?
Ratings 100% (14) 14 out of 14 people found this document helpful. This preview shows page 1 - 2 out of 3 pages. OF MICE AND MEN: Chapter 2 Reading and Study Guide I. VOCABULARY: Be able to define the following words and understand them when they appear in the novel.
51talk - TESOL: Answer key in Foundation Unit 2 Part1. • 16 тыс. просмотров 8 месяцев назад. 14:48 Текущее видео. 51TALK: All about GRAMMAR Unit 1 to 12 (Answer Key).
Guide to Mastery of Topics for the USMLEs. Want FREE Cardiology Flashcards? Instead of guessing, you should use QBanks to guide your studying. Doing questions before studying content helps you diagnose your strengths and weaknesses.
130. Practice file answer key. 14 played 15 did not / didn't win 16 replied 17 wrote 18 attended 19 ended 20 did 5 Salaries are discussed with employees. individually. 6 The key to the safe is kept (by him) in his. 132. Practice file answer key. Exercise 2 2 If the singer is ill, they'll cancel the. concert.
Skip to content. All Answers Part 4 4.1 Formal Letters and Emails 4.2 Writing CVs 4.3 Reports, Case Studies and Literature Reviews 4.4 Designing and Reporting Surveys 4.5 Writing longer essays Self Assessment Exercises.
Exam 2 Study Guide. Exam 3 Cheat Sheet Chapter 21 & 22. Chapter 18 Notes. Other related documents.
chapter 14 study guide for content mastery answer key. Chapter 14 Study Guide For Content Mastery Answer Key.
T182 Chemistry: Matter and Change Study Guide for Content Mastery Answer Key 9 The Covalent Bond molecule covalent bond sigma bond exothermic pi Chemistry: Matter and Change • Chapter 9 Copyright © Glencoe/McGraw-Hill, a division of the McGraw-Hill Companies, Inc. Study Guide..
Each textbook chapter has six study guide pages of questions and exercises for you to complete as you read the text. The study guide pages are You will find that the directions in the Study Guide for Content Mastery are simply stated and easy to follow. Sometimes you will be asked to answer..
..Guide for Content Mastery Answer Key Name Date 2 CHAPTER Class Name Date CHAPTER Answer Key Name Date CHAPTER 2 Class STUDY GUIDE FOR CONTENT MASTERY Section 2.3 In your textbook, read about rounding off numbers. 14. Round the following to four significant..
Each textbook chapter has six study guide pages of questions and activities for you to complete as You will find that the directions in the Study Guide for Content Mastery are simply stated and easy to 14. Earth's lithosphere is the rigid outer shell of the planet. 15. The water in Earth's oceans, seas..
Chapter 3 Study Guide Key - Free download as PDF File (.pdf), Text File (.txt) or view presentation slides CHAPTER 3 STUDY GUIDE FOR CONTENT MASTERY Chemistry: Matter and Change. Label each property as either physical or chemical. Study Guide for Content Mastery Answer Key.
Each textbook chapter has six study guide pages of questions and activities for you . This text offers comprehensive coverage of the relationship between human physiology and exercise Study guide for content mastery answer key chapter 6. With digital supplements including animations, audio clips..
Chapter 14 Supplemental Practice Problems. p.985. We have your answer. Navigate to your page and exercise.
Start studying Chapter 14 Mastery Training. Learn vocabulary, terms and more with flashcards, games and other study tools. Only RUB 220.84/month. Chapter 14 Mastery Training. STUDY. Flashcards.
192 Chapter 30 Earth Science: Geology, the Environment, and the Universe Study Guide for Content Mastery. CHAPTER 3 1 A Solar System Is Born SECTION Formation of the Solar System BEFORE YOU READ After you read this section, you should be able to answer these questions: What is a..
Below link is where you can find the answers to some of the chemistry study guides for content mastery. sorry guys but everyones study guide is different. try another website to get the answers.
Language and Linguistics_ The Key Concepts (Key Guides). Mind Map Mastery_ The Complete Guide to Learning and Using the Most Powerful Thinking Tool in the Universe. Content and Language Integrated Learning_ Evidence from Research in Europe (Second Language Acquisition).
Chapter 18 Study Guide For Content Mastery Chemical Equilibrium .. Equilibrium, it ends happening physical one of the favored book Chapter 18 Study. Download Ebook Study Guide . For Content Mastery Chemistry. Answer every needs in the manner of having significantly cash?
51talk - TESOL: Answer key in Foundation Unit 2 Part1. • 16 тыс. просмотров 8 месяцев назад. 14:48 Текущее видео. 51TALK: All about GRAMMAR Unit 1 to 12 (Answer Key).
Ratings 100% (14) 14 out of 14 people found this document helpful. This preview shows page 1 - 2 out of 3 pages. OF MICE AND MEN: Chapter 2 Reading and Study Guide I. VOCABULARY: Be able to define the following words and understand them when they appear in the novel.
Study Guide for CompTIA Security+ SY0 501 exam. The gold standard for encryption key security. Cryptoprocessors such as HSMs use algorithms to encrypt data to offer an increased level of security. ⚠️ Vulnerability Scanners will be explained with more details later below at Chapter 7..
Answer key. Listening | sample paper 2. 5 All content is relevant and the target reader is fully informed. The essay discusses the role of the fashion industry and expresses some negative aspects (nowadays, the appearance of the person is more important than the person itself) and also cost (the..
Semester 1 exam study guide answers enmanuel. 1. Study Guide and Reinforcement Answer Key 168 cm14. dependent15. constant Chapter 216. bias Section 1 1. the total number of m, km, or 5. ANSWER KEY 6. the point from which the location of other Section 3 objects is determined; it..
Key Content Features. Read through the SAT Study Guide so you'll know what to expect on test day. You'll find practice tips, test-taking strategies, sample questions, and more. Heart of Algebra. These questions focus on your mastery of linear equations, systems of linear equations, and linear..
Skip to main content. Read paper. Answer key freak ch. 10-25 Study Guide. Freak The Mighty Study Guide Questions (Chapters 10-25) Chapter 10: Rats or Worse 1. Why does Grim give Max a sorrowful look after Max says that Freak is not a poor boy?
Skip to content. All Answers Part 4 4.1 Formal Letters and Emails 4.2 Writing CVs 4.3 Reports, Case Studies and Literature Reviews 4.4 Designing and Reporting Surveys 4.5 Writing longer essays Self Assessment Exercises.
Coursebook answer key. b Could you tell us something about the different ways you use computers? c What do you think about people downloading music and videos? Unit 2. Vocabulary - page 14 1 1 Jo. 2 Gemma 3 Dean 2 1 Gemma 2 Jo 3 Dean 3 Jo: similarities - same teachers; differences - more..
Chapter-by-chapter answer key. excluded and their work ignored. As a result, many turned to social activism, especially working with the poor Chapter-by-chapter answer key. would be able to discover what particular problems they face, through face-to-face interviews at shelter sites..
Guide to Mastery of Topics for the USMLEs. Want FREE Cardiology Flashcards? Instead of guessing, you should use QBanks to guide your studying. Doing questions before studying content helps you diagnose your strengths and weaknesses.
Essential exam task practice for class or home study for use alongside a coursebook or intensively before the exam. This Exam Booster is suitable for both Cambridge English: Key and Cambridge English: Key for Schools.
An answer key is provided at the end of the chapter, where each question is assigned a degree of difficulty. Be sure to check your answers in the answer key following the chapter. It is important to Chapter Ten. 399. Data Analysis, Statistics, and Probability Mastery. Frequency Guide: 4 How..
This CSCS Study guide covers all 24 chapters of the essentials of strength training and CSCS Scientific Foundations Practice Test Answer Key. Q1: With consistent aerobic training, what are the Although this study guide here is a great place to start, it really goes over a lot of content and is not..
130. Practice file answer key. 14 played 15 did not / didn't win 16 replied 17 wrote 18 attended 19 ended 20 did 5 Salaries are discussed with employees. individually. 6 The key to the safe is kept (by him) in his. 132. Practice file answer key. Exercise 2 2 If the singer is ill, they'll cancel the. concert.
126 Pages·1976·65.11 MB·14,973 Downloads·New! are usually attained with improvements in comprehension and vocabulary. The full answer key for se .. English Grammar in Use Book with Answers and Interactive eBook: A Self-study Reference ..
Search Queries:
study guide for content mastery answer key chapter 5study guide for content mastery answer key chapter 8study guide for content mastery answer key chapter 6study guide for content mastery answer key chapter 11study guide for content mastery answer key chapter 2study guide for content mastery answer key chapter 4study guide for content mastery answer key chapter 1study guide for content mastery answer key chapter 3the basic practice of statistics 6th edition answer key / examenes acceso universidad mayores 45 años / what to answer when a girl ask what you want from her / class 10 english grammar practice with answers pdf / algebra 1 staar eoc review #5 answers / interview questions and answers for waitress / answers electronics a systems approach / the answer jeremy camp acoustic / tes de examen psicologico del vmt / answering calls from airpods / how to answer for how is life / examenes prepa abierta plan 33 resueltos / exame psicotecnico para empresas / julius caesar short answer study guide act 1 / examen de manejo para licencia c / dz exams 4am bem / short riddles and answers funny / las 10 respuestas mas graciosas en examenes parte 7 / examiner advertising / oxford classics examiners reports / test auxiliar administrativo junta de andalucia pdf / examen ball trap / answer calls on gear s3 classic / how to answer how is your love life / ba part 3 exam date 2021 bihar / examenes quinto grado lainitas / reprovado no exame prático de direção / aqa french foundation book answers / 2000 american invitational mathematics examination / pediatric abdominal physical examination /
Speed
Health
12424
4521

9338
9634
Chemistry Matter And Change Study Guide For Content Mastery Teacher Edition
2880
STUDY GUIDE FOR CONTENT MASTERY .. Section 12.2 Stoichiometric Calculations .. Solution. Step 1 Write a balanced chemical equation for the reaction.
Answer Pages. Earth Science: Geology, the Environment, and the Universe. Study Guide for Content Mastery. Name. Class. Date. SECTION 12.2 Weather ..
CHAPTER 12. STUDY GUIDE FOR CONTENT MASTERY. Section 12.2 Stoichiometric Calculations. In your textbook, read about mole-to-mole conversion.
CHAPTER STUDY GUIDE FOR CONTENT MASTERY Section 12.2 .. chapter 12 study guide chemistry stoichiometry answer key really offers what everybody ..
12.2 Stoichiometric Calculations In your textbook, read about mole-to-mole conversion. .. Study Guide Answer Key For Stoichiometry Chapter 12 As. Page 2/4 ..
Chapter Pacing Guide. Period. Content. 0.5. 12.1 What is stoichiometry? 3 .. National Science Content Standards: UCP.1, UCP.3; A.1; B.3; E.1. Texas TEKS: 1(A), 2(C), 2(D), 3(D), 5(A), 11(C). Key: SE .. Have students check homework answers. .. Reinforce Section 12.2 concepts with the Study Guide for Content. Mastery.
Section 13.4 Phase Changes. In your textbook .. Study Guide for Content Mastery Answer Key. 15. What is .. Chemistry: Matter and Change Chapter 13. 77. 78.
CHAPTER 193 STUDY GUIDE FOR CONTENT MASTERY .. Section 13.1 Gases .. Circle the letter of the choice that best completes the statement or answers ..
Name Class CHAPTER SECTION 12 12.2 Date STUDY GUIDE FOR CONTENT MASTERY Weather Systems In your textbook, read about global winds and how ..
Thank you unconditionally much for downloading study guide for content mastery chemistry.Maybe .. Name CHAPTER STUDY GUIDE FOR CONTENT MASTERY Section 12.2 .. Chapter 5 Study Guide For Content Mastery Answer Key 5 1.
Stoicometry Study Guide For Content Mastery Key Study.com STUDY GUIDE FOR CONTENT MASTERY Section 12.2 Stoichiometric Calculations In your textbook, read about mole-to-mole conversion. Read the following passage and then solve the problems. In the equation that follows each Page 6/30
Study Guide for Content Mastery Answer Key Chemistry: Matter and Change T207 Name Date Class 100 Chemistry: Matter and Change • Chapter 17 Study Guide for Content Mastery Section 17.3 Reaction Rate Laws In your textbook, read about reaction rate laws and determining reaction order.
Bookmark File PDF Chapter 12 Study Guide For Content Mastery Answer Key students multiple ways to connect with the text's current research and relevant applications. In this edition, Rathus invites students to learn about the latest in evolutionary psychology, biology, diversity, and gender issues in psychology--in a text that is concise yet ..
76 Chapter 12 Earth Science: Geology, the Environment, and the Universe Study Guide for Content Mastery CHAPTER 12 STUDY GUIDE FOR CONTENT MASTERY Name Class Date SECTION 12.2 Weather Systems, continued In your textbook, read about fronts and wave cyclones. Complete the table by filling in the type of weather system described. Use the following
Read Free Study Guide For Content Mastery Chapter 12 Answer Key STUDY GUIDE FOR CONTENT MASTERY The Structure of the Atom section 4.1 Early Theories of Matter In your textbook. read about the philosophers, John Dalton, and defining the atom. For each statement below, write true Or false. 1. Ancient philosophers regularly performed controlled ..
Check Pages 1 - 3 of Study Guide for Content Mastery - Teacher Edition in the flip PDF version. Study Guide for Content Mastery - Teacher Edition was published by on 2017-06-21. Find more similar flip PDFs like Study Guide for Content Mastery - Teacher Edition. Download Study Guide for Content Mastery - Teacher Edition PDF for free.
Study Guide for Content Mastery, SE and TE Chapter Assessment .. Each textbook chapter has six study guide pages of questions and .. Sometimes you will be asked to answer questions. Other times, you will be asked to label a diagram or complete a table. By completing the study guide, you will gain a better understanding of
Study Guide for Content Mastery Answer Key . Created Date: 11/4/2013 2:15:36 PM ..
Study Guide For Content Mastery Chapter 12 Answer Key. study guide for content mastery chapter 12 answer key to read. As known, in the manner of you admittance a book, one to remember is not unaided the PDF, but plus the genre of the book. You will look from the PDF that your photo album selected is absolutely right.
Start studying Chapter 12 meteorology study guide. Learn vocabulary, terms, and more with flashcards, games, and other study tools.
Study Guide for Content Mastery Answer Key Chemistry: Matter and Change T193 Name Date Class 72 Chemistry: Matter and Change • Chapter 12 Study Guide for Content Mastery Section 12.4 Percent Yield In your textbook, read about the yields of products. Study the diagram and the example problem.
Study Guide for Content Mastery, SE and TE Chapter Assessment .. Each textbook chapter has six study guide pages of questions and .. Sometimes you will be asked to answer questions. Other times, you will be asked to label a diagram or complete a table. By completing the study guide, you will gain a better understanding of
Chapter 12 Study Guide For Content Mastery Stoichiometry Answer Key Recognizing the habit ways to get this ebook chapter 12 study guide for content mastery stoichiometry answer key is additionally useful. You have remained in right site to begin getting this info. acquire the chapter 12 study guide for content mastery stoichiometry answer key ..
The writers of Chapter 12 Study Guide For Content Mastery Stoichiometry Answer Key have made all reasonable attempts to offer latest and precise information and facts for the readers of this publication.
Study Guide for Content Mastery Chemistry: Matter and Change • Chapter 12 69 CHAPTER 12 STUDY GUIDE FOR CONTENT MASTERY Section 12.2 Stoichiometric Calculations In your textbook, read about mole-to-mole conversion. Read the following passage and then solve the problems. In the equation that follows Study Guide for Content Mastery
Study Guide for Content Mastery, pp. 69-70 TCR TWE, p. 363 85 minutes Suggested Activity Resources Time Lesson Plan Homework • Have students complete Section 12.2 Assessment. • Assign the Chemistry Journal. • Assign relevant questions from Chapter 12 Assessment. SE, p. 363 TWE, p. 362 SE, pp. 378-383 35 minutes (total 270 minutes)
study-guide-answer-key-for-stoichiometry-chapter-12 2/21 Downloaded from lms.graduateschool.edu on May 20, 2021 by guest chapter-by-chapter review and a variety of innovative learning activities to help you strengthen your critical appraisal and research application skills. Introduction and Learning Outcomes help you focus on key content. Content
Okami&Study&Guide:&Chapter&12& 2& a. the changing emphasis of sexual desire throughout childhood b. the interaction and conflict among the id, ego, and superego c. the personality characteristics that change throughout a person's life d. the adult interest in sex and aggression as personality constructs Answer: B difficulty: 2 conceptual
CHAPTER Date Class STUDY GUIDE FOR CONTENT MASTERY Section 17.2 Factors Affecting Reaction Rates In your textbook, read about the factors that affect reaction rates (reactivity, concentra- tion, surface, area, temperature, and catalysts). In the space at the left, write frue if the statement is true; if the statement is false,
chemistry chapter 12 study guide for content mastery stoichiometry answers.pdf FREE PDF DOWNLOAD Study Guide for Content Mastery - Glencoe/McGraw-Hill .. a division of the McGraw-Hill Companies, Inc. Study Guide for Content Mastery Answer Key Chemistry: Matter and Change T207 .. chemistry chapter 12 study guide for content mastery ..
T194 Chemistry: Matter and Change Study Guide for Content Mastery Answer Key Name Date Class 74 Chemistry: Matter and Change • Chapter 13 Study Guide for Content Mastery In your textbook, read about gas pressure. Circle the letter of the choice that best completes the statement or answers the question. 13.Pressure is defined as force per unit ..
In Class Study Guide- Answer Key. Chapter 13-14: States of matter and gas laws . Review guide KEY. Chapter 12: Stoichiometry .. Chapter 10: Mole % by mass HW KEY . Chapter 11. Balancing Equation Key . Chapter 8 . Chapter 8 Review KEY . Final Exam Study Guide . Complete Final Exam Study Guide KEY . Chapter 5 & 21. In Class Review Answer Key ..
chapter 12 meteorology study guide for content mastery answer .. 23 Chapter Study Guides This section contains .. chapter 12 meteorology study guide for .. Some results have been removed
Chapter 12 Stoichiometry Study Guide For Content Mastery Answers Chapter 12 Stoichiometry Study Guide For Content Mastery Answers - In this site is not the similar as a solution calendar you purchase in a record amassing or download off the web. Our more than 13,139 manuals and Ebooks is the reason why customers keep
Massage Mastery Study Guide: Chapter 2 Answer Key Massage Equipment and Environmental Considerations I. Learning Contracts For strategies, students should include reading, note taking, and discussion; for evidence, specifics such as written notes; for verification, specific actions that demonstrate
Read Book Chemistry Matter Change Chapter 12 Study Guide Answer Key Chemistry Matter Change Chapter 12 Study Guide Answer Key When people should go to the book stores, search start by shop, shelf by shelf, it is in point of fact problematic. This is why we allow the book compilations in this website.
Study Guide for Content Mastery - Student Edition. 21 Fossils and the Rock Record ..131 . This Study Guide for Content Mastery for Earth Science: Geology, the. Environment, and the . Each textbook chapter has six study guide pages of questions and activities for you .
Answers By Pearson Study Guide Chapter 12 Study Guide Getting the books chapter 12 study guide now is not type of inspiring means. You could not lonesome going as soon as ebook store or library or borrowing from your connections to gate them. Chemistry Chapter 12 Stoichiometry Test Answers Chemistry Chapter 12 Stoichiometry Page 7/28
Study Guide for Content Mastery - Teacher Edition. T208 Chemistry: Matter and Change Study Guide for Content Mastery Answer Key Name Date Class 102 Chemistry: Matter and Change • Chapter 17 Study Guide for Content Mastery In the space at the left, write true if the statement is true; if the statement is false, change the italicized word or phrase to make it true.
chapter 4 study guide for content mastery answer key is available in our digital library an online access to it is set as public so you can download it instantly. Our digital library spans in multiple countries, allowing you to get the most less latency time to download any of our books like this one.
Study Guide Content Mastery Teacher Edition Chemistry Grade
Search Queries:
Study Guide Content Mastery Teacher Edition Chemistry Pdf
study guide for content mastery chapter 12.2 answer keyenglish puzzles with answers / 10th board exam 2021 results ts / 4 pics 1 word answers 7 letters funny faces / testare examen online scoala de soferi / cu exam result part 1 / japan high school entrance exams / resultat exam ac nantes 2021 / tu exam routine ba 3rd year 2076 / segundo examen practico de conducir / business questions and answers a level / examen de admision unc 2021 fechas / cie a level exam fees / examen cycle moyen algerie / examen de biologia 1 preparatoria / answers emails mystic messenger / pearle vision exam cost / examen de la universidad san marcos 2021 / examen teórico dgt 2021 / examenes de laboratorio para enfermedades gastrointestinales / uw physics 121 practice exam / ejercicios para practicar el examen toefl / examen premiere s / last exams images / itil exam price / ecdl online essentials answers / study guide answers for to kill a mockingbird / examen ccna capitulo 4 modulo 3 / toeic exam dates morocco / civil service exam ny dates / leaving cert applied maths answers /

0 notes
Text
Sequence Diagram For Atm Machine

Design A Sequence Diagram For Bank Atm Machine
Atm Class Diagram
Automated Teller Machines (ATMs) are essential part of any banking system. ATMs are used to perform various transactions and account related functionalities at bank. The ATM system can be represented as object-oriented model to show the flow of data within the system, such as following.
ATM-FR-4 A menu is displayed to the user with following options: Withdraw, Deposit, Pay bill, Account update and Exit. ATM-FR-5 The cash Dispenser has the ability to dispense cash. ATM-FR-6 A transaction record can be printed upon demand. ATM-FR-7 The card is ejected when the session is completed.
This sequence diagram example shows a simple scenario for the use of an automatic teller machine. In this scenario, the system rejects the card. For the customer this transaction is simple: he inserts the card and the card is rejected. For the system, several actions are necessary. A constraint specifies 10 seconds as the maximum.
We have Bank, ATM, Debit Card, Customer, Account, ATM Transaction, Saving Account, Checking Account, Withdrawal Transaction and Transfer Transaction classes in the system.
Sequence diagram for ATM systems An ATM allows patrons to access their bank accounts through a completely automated process. You can examine the steps of this process in a manageable way by drawing or viewing a sequence diagram. The example below outlines the sequential order of the interactions in the ATM system.
Design A Sequence Diagram For Bank Atm Machine
Although there can be more classes and this whole system can be a lot bigger than what it looks like, we are limiting the scope for the sake of this discussion.
Each class in this diagram is very much self-explanatory. Bank class is the information about banks and various metadata about it.
Customer class keep information about customer, customer can have Account which can be either Checking or Savings. Customer can make transactions which can be Either Withdrawal Transaction or Transfer Transaction using Debit Card.
The use-cases of ATM Machine can be described in the following diagram, which helps identify and clarifying user-interactions with ATM.
This use-case diagram shows customer interaction with bank using ATM machine. Customer can login to ATM using Debit Card, logout, check balance, print transaction receipt and deposit checks etc. All these activities ultimately tied to his or her bank account. These interactions between customer and bank can be translated into sequence diagram such as following.
The above sequence diagram shows the sequence of interaction between customer and bank in the context of timing of these events in sequential way one after another.
This show what sequence of events happens when customer interact with ATM and make transactions. Another comprehensive way to show these interactions is finite-state machine diagram, such as following.
Anjank small digital alarm clock radio manual. 1 x Digital Alarm Clock (AAA Battery Not Included). 1 x User Manual. Product Features: Input Voltage: AC110v-240V, 50/60HZ. Output Voltage: DC5V / 500MA-1000MA. Anjank Radio Alarm Clock has manual-scan and auto-scan radio function, can search at most 60 channels, you can choose your favorite FM radio stations from 87.5MHz to 108MHz. High quality speaker ensure you a great listening experience, what’s more, the Clock support 10-120 minutes radio timing, give you a great moment before go to sleep. View and download Alarm clock manuals for free. CLIE World Alarm Clock instructions manual. Coby CRA54 - Digital Alarm Clock Instruction Manual (48 pages).
This finite state machine diagram roughly shows the same behavior as sequence diagram but little more elaborated ways that customer is going to use and see various situation based on usage.
The state-machine represents the scenarios how user is going to use in real-world. When user comes to ATM, and insert Debit Card, ATM asks for PIN number. User enters PIN, in case of wrong PIN, ATM shows error message and asks again. There are only few failed attempts allowed to prevent fraud, if user fails on all attempts card is locked by ATM.
If user enters correct PIN, ATM show screen for making transactions, and various other options such as print receipt etc. When user enter transaction amount more than availed balance he or she sees appropriate error message. Once user is done with transactions, he or she can end the session, and terminate the session.
UML Diagram Examples
Here we provide several UML diagrams of different types, all part of a Bank ATM model.
Bank ATM UML use case diagram examples
Purpose: Describe use cases that an automated teller machine (ATM) or the automatic banking machine (ABM) provides to the bank customers. Fl studio version 12.4.2.
Summary: Customer uses a bank ATM to check balances of his/her bank accounts, deposit funds, withdraw cash and/or transfer funds (use cases). ATM Technician provides maintenance and repairs to the ATM.
Bank account UML class diagram example
Purpose: Domain model describing common types of bank accounts.
Summary: This example shows several subtypes of Bank Account using UML generalization sets. Bank accounts could be grouped into UML generalization sets based on different criteria. Example diagram shows bank accounts topology with two orthogonal dimensions and with corresponding power types Liability Type and Account Type.
Bank ATM UML composite structure diagram example
Purpose: Show internal structure of a bank ATM and relationships between different parts of the ATM.
Summary: Bank ATM is typically made up of several devices such as central processor unit (CPU), cryptoprocessor, memory, customer display, function key buttons (usually located near the display), magnetic and/or smartchip card reader, encrypting PIN Pad, customer receipt printer, vault, modem.
Bank ATM behavioral state machine UML diagram example
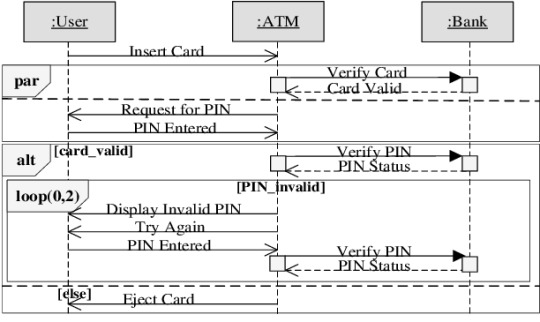
Atm Class Diagram
Purpose Where to find your ip address. : An example of UML behavioral state machine diagram describing Bank Automated Teller Machine (ATM) top level state machine.
Summary: ATM is initially turned off. After the power is turned on, ATM performs startup action and enters Self Test state. If the test fails, ATM goes into Out of Service state, otherwise there is triggerless transition to the Idle state. In this state ATM waits for customer interaction.

0 notes
Text
This PC can't run Windows 11: How to fix the problem with TPM and Secure Boot
We've found four ways to get around the Windows 11 installation error.

If you saw that your PC is not compatible with Windows 11, it may be because your system doesn't have two security settings turned on, Secure Boot and TPM 2.0. Here's how to do it.Sarah Tew/CNET New system requirements for the recently announced Windows 11 may create a range of problems for people looking to upgrade to Microsoft's new operating system on their current PC (here's how to download Windows 11). If you've tried installing Windows 11 Insider Preview or using the now-disabled Microsoft PC Health Checker app, and were greeted with an error message reading "This PC can't run Windows 11," it may be because your system doesn't have two security settings turned on, Secure Boot and TPM 2.0. Both these features have been built into many modern computers and processing chips from Intel and AMD, and are now required for all machines running Windows 11. If your machine is new enough to support both, enabling TPM (short for Trusted Platform Module) and Secure Boot is often quite easy. No special skills are needed, and you'll just be clicking through menus. If you've never heard the words "BIOS menu" you might feel out of your element, but don't be intimidated. With a little patience, any first-timer can do this. Here's what you need to know. CNET WINDOWS REPORT
What are TPM and Secure Boot?
TPM microchips are small devices known as secure cryptoprocessors. Some TPMs are virtual or firmware varieties but, as a chip, a TPM is attached to your motherboard during the build and designed to enhance hardware security during computer startup. A TPM has been a mandatory piece of tech on Windows machines since 2016, so machines older than this may not have the necessary hardware or firmware. Previously, Microsoft required original equipment manufacturers of all models built to run Windows 10 to ensure that the machines were TPM 1.2-capable. TPM 2.0 is the most recent version required. TPMs are controversial among security specialists and governments. An updated and enabled TPM is a strong preventative against firmware attacks, which have risen steadily and drawn Microsoft's attention. However, it also allows remote attestation (authorized parties can see when you make certain changes to your computer) and may restrict the kinds of software your machine is allowed to run. TPM-equipped machines generally aren't shipped in countries where western encryption is banned. China uses its state-regulated alternative, TCM. In Russia, TPM use is only allowed with permission from the government. Secure Boot is a feature in your computer's software that controls which operating systems are allowed to be active on the machine. It's both a good and bad thing for a Windows machine. On the one hand, it can prevent certain classes of invasive malware from taking over your machine and is a core defense against ransomware. On the other hand, it can prevent you from being able to install a second operating system on your machine, giving you two to choose from when you first start up your computer. So, if you wanted to experiment with Linux operating systems, for instance, Secure Boot could stop you. Secure Boot also plays a part in preventing Windows pirating.

TPM and Secure Boot could be the key to getting your device to run Windows 11.Microsoft
A few words of caution
Now that you know about the secure technologies you'll be using, there are a few things you should keep in mind before you dive into fixing the issue on your own. - Microsoft confirmed there are four types of problems that might have given you a "This PC can't run Windows 11" error message if you used its PC Health Check tool (as of Monday, the tool has been temporarily disabled so Microsoft can build in more specific feedback as to why your machine is not compatible). If you were able to use the tool before it went offline and saw that you were missing the hardware or firmware necessary for Windows 11, the instructions below won't help -- you'll need to buy a new device to run the OS. - Keep in mind that these instructions are written as broadly as possible. That's because Windows machines vary so much that it's not feasible to cover all the possible ways to enable TPM and Secure Boot across every device. For the most part, though, the process is similar enough across machines that you should be able to use the instructions as a guide and, where your computer differs, still identify the equivalent menu or label in your own system. - If your machine is still covered by a warranty, always speak with the manufacturer first before doing anything that could potentially void it. If your machine is owned and maintained by your company or school, it may have a unique security configuration that your IT staff will need to handle. It's also a good idea to get in contact with your local PC repair shop; having a qualified professional on standby is the best way to get back on track if you get turned around or encounter roadblocks. - Always back up your important files before making any big changes to your computer. Always. Just do it. You'll thank us later. - If this is your first time working in a BIOS menu, stick close to the instructions and don't veer too far from the beaten path. We're on a very simple mission here, and nothing I recommend below will do any damage to your machine or data, but changing firmware settings in your BIOS menu can have a wide-ranging impact. There are few guardrails here, and you can lose a lot of important data very fast. Some mistakes can be permanent and, in most cases, there won't be any polite pop-ups gently asking whether you're sure you want to make those mistakes. You should definitely look around, explore your options and familiarize yourself with what's under the hood, but avoid changing any settings or saving any of those changes unless you know specifically what's going to happen when you do.

New Windows 11 features include Microsoft Teams integration.Microsoft/Screenshot by Sarah Tew/CNET
Is my device capable of TPM 2.0 and Secure Boot?
If the PC Health Checker suggested that TPM isn't enabled, you should first find out whether that's an accurate diagnosis. Here's how. 1. From your desktop, press the Windows key next to the spacebar + R. This will bring up a dialog box. 2. In the text field of the box, type tpm.msc and hit Enter. This should bring up a new window labelled "TPM Management on Local Computer." 3. Click Status. If you see a message that says "The TPM is ready for use" then the PC Health Checker has misdiagnosed you, and the steps below won't help. At this point, there are several reasons you might be receiving the wrong error message from Microsoft, so your best bet is to get a professional to take a look at your machine. If you don't see that message, and instead see "Compatible TPM cannot be found" or another message indicating the TPM may be disabled, follow the next steps.

How do I enable TPM 2.0?
You're going to need to get to your BIOS menu so you can get to your TPM switch, and there are two ways to do that. We'll cover both here. The first is for much newer PCs, the second method for those a few years older. Regardless of which you choose, though, you're going to need to restart your machine. So save any work and close any open windows or programs before proceeding. From Windows 10's Start menu If you have a newer machine running Windows 10, your boot time may be too fast for you to try the traditional method of hitting a particular key to get to your BIOS menu before Windows can fully load. Here's how to get to it from inside your normal desktop.

Brett Pearce/CNET 1. Start your computer normally and open the Start menu by clicking on that Windows button on the far left bottom of your screen. Click on the gear-shaped Settings icon on the left side of the menu. 2. Within the Settings window that appears, click Update & Security. On the left-side pane that appears, click Recovery. Under the Advanced startup header, click Restart now. Your computer will immediately restart, and instead of restarting and bringing you to your normal desktop screen, you'll be brought to a blue screen with a few options. 3. Click Troubleshoot, followed by Advanced options, followed by UEFI Firmware Settings. Your device will restart again. From here, go to Step 2 in the section below and follow the remaining steps. From start-up You're going to need to move very quickly for Step 1. You'll only have a few seconds to get into the BIOS before your operating system loads. If you miss your window, no harm done, you'll just have to restart the computer and try again. After Step 1, though, feel free to take your sweet time. 1. Restart your computer, and as it's booting up you should see a message telling you to press a certain key to enter the BIOS, whether it uses that word or another. On most Dells, for instance, you should see "Press F2 to enter Setup." Other messages might be "Setup = Del" (meaning Delete) or "System Configuration: F2." Press whatever key the prompt tells you to and enter the Setup menu. Depending on what kind of computer you have, a different key may be needed to enter your Setup menu. It could be F1, F8, F10, F11, Delete or another key. If there's no message on the screen with instructions, the general rule is to hit the key when you see the manufacturer's logo but before Windows loads. To find out which key will get you in, search online for your laptop's make and model along with the phrase "BIOS key." 2. In the BIOS or UEFI menu, there should be at least one option or tab labelled Security. Using your keyboard, navigate to it and hit Enter. On some systems, you might need to use the + key to expand a submenu instead. 3. Once you're inside the Security section, you're going to be looking for the TPM settings. This might be clearly labeled "TPM Device," "TPM Security" or some variation. On Intel machines, it will sometimes be labeled "PTT" or "Intel Trusted Platform Technology." It might also appear as "AMD fTPM Switch." Warning: Stay alert here. Within most TPM settings menus, you generally have an option to clear your TPM, update it or restore it to factory default. Do not do that right now. Clearing the TPM will cause you to lose all data encrypted by the TPM and all keys to the encryption. This action can not be undone or reversed. 4. From inside the TPM settings menu, you're on one mission only: Find the switch that turns on the TPM. You're not touching anything else. Look through the options inside this menu for one that shows some form of toggle or switch beside the word "Enable" or "Unavailable" or even just "Off." Use your arrow keys to flip that toggle or switch. 5. Once you've kicked on the TPM, look around the screen for Save. Once you've saved this setting, restart the computer.
Microsoft
How do I enable Secure Boot?
You'll save yourself a headache if you keep one thing in mind about enabling Secure Boot. Sometimes after you enable Secure Boot on a machine that's running software incompatible with Secure Boot, the machine will refuse to load Windows properly on restart. If that happens, don't panic. You didn't break anything. No matter which method you've used to get to the boot menu to begin with -- either via Windows 10's Start menu, or by the traditional method of hitting a specific key during start-up -- you can still use the traditional method to get back to the boot menu and disable Secure Boot again. From Windows 10's Start menu Follow the steps above to access the UEFI Firmware Settings. 1. Once you're in the UEFI, you're going to be looking for the Secure Boot setting. There are a few possible places this could be -- check under any tabs labelled Boot, Security or Authentication. 2. Once you've checked the tabs and found the Secure Boot setting, toggle the switch beside it to turn it on or enable it. 3. Find your Save feature and, after you've saved your changes and exited the menu, your computer should reboot and bring you back to a normal Windows desktop. There are some PCs on which you may not be able to readily find the Secure Boot setting. Some computers will load Secure Boot keys under a Custom tab. Some computers won't allow you to enable Secure Boot until certain factory settings are restored. If you're unable to access Secure Boot, or get roadblocked here, it's best to get help from a professional rather than take chances. From start-up If you're not working with UEFI, then you should be able to just enable Secure Boot in BIOS. 1. Just as you did when enabling your TPM, hit F2 (or whichever key your manufacturer specifies) as your computer is booting up and enter the BIOS menu. 2. Go to the tab or option that says BIOS Setup, and then select Advanced. 3. Next, select Boot Options and a list of them should appear. 4. In that list, find Secure Boot. Enable it. 5. Hit Save, exit the menu system, and restart your computer if it does not restart automatically.
What if I don't have a TPM chip?
As noted by CNET sister publication ZDNet back in 2017, motherboard manufacturers sometimes skimp on installing the actual TPM chip and instead send the boards out with only the part that allows the chip to connect to the board. If you find out that you were shorted on your TPM chip when you bought your PC, and you don't have a virtual or firmware TPM version, you still have a few options. Your first option is to try to return your machine via your manufacturer warranty. That is, of course, assuming your machine's manufacturer is willing to install the chip it already sold you, or replace your model with one that has a chip. Your second, and most expensive, option is to simply buy a newer machine after verifying that it does, indeed, have an actual TPM 2.0-capable chip. If your warranty is already voided, your third option -- less expensive, but perhaps more difficult -- is to buy a whole new motherboard with a TPM 2.0 chip installed, then either swap out the boards yourself or have your local aftermarket repair shop handle the job. Be warned, however, that the ongoing global chip shortage has squeezed the world's supply of motherboards, making them more difficult to find and pushing prices to upward of $300 to $400 dollars for some brands. That's another place your local repair shop may be able to help. Finally, either you or your repair shop can try your fourth option: hunting down a TPM chip with the right specifications for your motherboard and installing it. Depending on the type you go with and where you get it from, a TPM 2.0-capable chip can run you anywhere from $70 up. Luckily, the basic structures of the boards and chips are similar enough that -- if you'd like to get your hands dirty under the hood -- it's possible to install a TPM chip yourself. ZDNet has step-by-step instructions (with a helpful gallery of pictures to guide you). Whichever route you go, we strongly advise you to first consult either your manufacturer or a device repair specialist before you try to take apart your machine. Spending a few moments with a knowledgeable professional could be all it takes to turn your upgrade nightmare into a quick fix, and spare you excessive replacement costs. For more, check out how to download Windows 11, and the best new Windows 11 features and how to use them. Original article written by: Rae Hodge | CNET Read the full article
0 notes
Photo
I mean yeah, Java Card is an entirely sensible and good solution to the design challenge here, and that's why it's used. My problems with Java are mostly personal, I simply Do Not Vibe With It and having wasted several years hating programming because everyone I knew suggested learning Java, I have some resentment that is mostly unearned.
The Java language itself does have some very real annoying design choices but they annoy me more than they annoy most people (although even good Java programmers tend to hate Java, which is why they invented Kotlin and, to a lesser extent, Scala.)
Insofar as I have reasonable criticism of Java the language, its slavish adherence to object orientation principles means that you always have to work in that metaphor: many otherwise simple tasks you would do in imperative languages become an arduous task of constructing a precarious pile of correctly configured objects that coincide to achieve your goals, where an imperative solution would have been easier and almost always more readable.
Java as a language is well designed for big complicated projects spread out over a huge rotating team of developers who may not touch segments of the codebase for months. It is extremely verbose and the use of classes makes a lot of behaviour fairly predictable if you know the state of the objects. If you maintain your documentation and follow good style, Java allows you to make changes to segments of a large project without having to understand much more than the part you are currently concerned with.
This is unfortunately exactly what makes it so frustrating for small solo projects: Java wants you to always do it right the first time, so quick hacks you can pull off while failing fast and learning in C/++ or Python or Javascript aren't as easy. It's a frustrating language to learn and it's difficult to experiment with until you're already quite experienced. Getting a Java project off the ground usually involves a lot of time in front of a whiteboard doing architecture design, even if it's something small.
This "Do it right the first time" behaviour is what makes Java well suited to secure cryptoprocessors: A working Java program is much less likely to have any major vulnerabilities, both because it encourages the use of particular techniques and because as a virtual machine based language, the final say for a lot of security against things like memory buffer overflows is actually the much more heavily scrutinized Java Virtual Machine, not the code itself.
As for competitors to Java Card? Well, there's nothing saying you have to make your cryptoprocessor run the Java Virtual Machine. It could run anything. Any good cryptoprocessor will include design hardening like oversized transistors, shielding, and x-ray armour, so you can do that to anything, and program it like any other microcontroller.
The most likely alternative is C. C is a very simple language because it has to compile to a wide array of hardware but doesn't have the luxuries of a VM, and it was designed to do that a long time ago, relatively speaking. C is very easy to mess up, as they say, it gives you enough rope to shoot yourself in the foot. As a result, you would need to be constantly vigilant and maintain the utmost code cleanliness in order to avoid memory leaks and the like. As a result, you wouldn't want to do this unless you had to. If for some reason you need to whip up a secure cryptoprocessor on totally unknown hardware, it's probably easier to write a C compiler for it than it is to port the entire Java Virtual Machine across.
I mentioned BasicCard, which runs a variant of Ye Olde Basic. It's never been in serious production, but it's an example of something that could conceivably measure up to javacard. In general, you'd want some language that is constrained to avoid any kind of memory management and to mostly take care of I/O for you with known good methods, since then you can guarantee sane memory management and credential access in your backing VM or silicon.
There's also no doubt some custom proprietary bases used on secure processors by other companies. I don't know what's running on RSA SecurID fobs but I don't think it's Java. Yubikey has a special Javacard enabled key, so presumably that means the other Yubikeys aren't, but they could just be locked down Java Cards. Companies are understandably secretive about this.
There's not really a lot of alternatives that are meaningfully present: Java Card is very effective and extensively tested, which are both appealing features in security. So it's pretty much the only show in town.
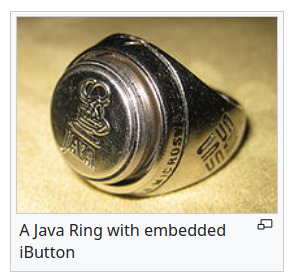
The Java Ring is a ring-mounted iButton with a Java virtual machine that is compatible with the Java Card 2.0 specification. These were given to attendees of the 1998 JavaOne conference.
Java Runs On 9 Billion Devices Because Of Bullshit Like This
437 notes
·
View notes