#applicationsecuritytesting
Explore tagged Tumblr posts
Text
Guarding Against Threats: Advanced Techniques for Application Security Testing
Explore advanced techniques in #applicationsecuritytesting to safeguard against evolving cyber threats and ensure the integrity of your software infrastructure.

#application security#application security testing#penetration testing services#cybersecuritytestingsolutions#cyber security#application testing
0 notes
Photo

Backend Developer Complete Roadmap😉⭐️ 👉Learn the fundamentals of software supply chain security with questions and answers 🌟🌟🌟 https://amzn.to/3Z3iFOg #applicationsecurity #cloudsecurity #iot #iotsecurity #dataprivacy #datasecurity #mobilesecurity #cognitivesecurity #automationsecurity #applicationsecuritytesting #portprotocol #datagovernance #smartcar ##networksecurityengineer #mobilesec #smartcarsecurity #pythonprogramming #pyhtonlearning #networksecurity #cybersecurityexpert #portsecurity #pythonprojects #datasecurityconsulting #blockchainprogramming #blockchaincybersecurity #bigdatasecurity #dataprivacyjobs #developerjobs #cybersecurityexpertcourses (at India) https://www.instagram.com/p/Cm1jNXPvraC/?igshid=NGJjMDIxMWI=
#applicationsecurity#cloudsecurity#iot#iotsecurity#dataprivacy#datasecurity#mobilesecurity#cognitivesecurity#automationsecurity#applicationsecuritytesting#portprotocol#datagovernance#smartcar#networksecurityengineer#mobilesec#smartcarsecurity#pythonprogramming#pyhtonlearning#networksecurity#cybersecurityexpert#portsecurity#pythonprojects#datasecurityconsulting#blockchainprogramming#blockchaincybersecurity#bigdatasecurity#dataprivacyjobs#developerjobs#cybersecurityexpertcourses
2 notes
·
View notes
Text
0 notes
Link
App security isn't a feature or a benefit—it's a vital necessity. Not only can a breach cost your business millions of dollars, but it can also cost you a lifetime of trust. Because of this, security should be a priority from the moment you start writing the first line of code. Here are 7 strategies for building secure mobile apps.
#securecoding#secureapps#mobileappdevelopment#secure#appdevelopment#business#security#applicationsecurity#datasecurity#automation#cybersecurity#dataprivacy#applicationsecuritytesting
0 notes
Text
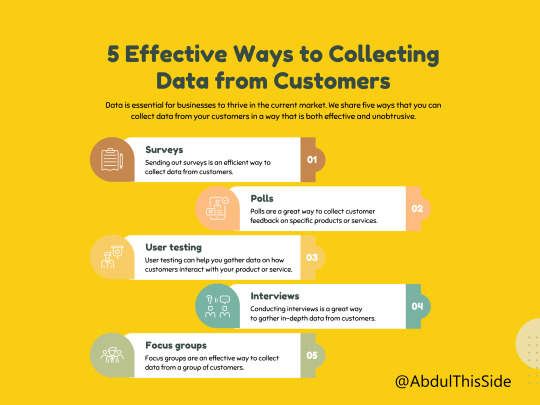
5 Effective Ways to Collecting Data from Customers: “Customer data can be collected in three ways: by directly asking customers, by indirectly tracking customers, and by appending other sources of customer data to your own,”
#datacollection#data#datascience#iot#dataentry#automation#dataprivacy#bigdata#business#datagovernance#datasecurity#datasecurityconsulting#dataanalytics#applicationsecurity#mobilesecurity#applicationsecuritytesting#iotsecurity#cloudsecurity#dataset#marketresearch#dataanalysis#machinelearningnews#bigdataanalysis#pythonprogramming#dataprivacyjobs#research#datamining#technology
0 notes
Text
#mobilesecurity#applicationsecurity#cloudsecurity#iotsecurity#datasecurity#automation#cybersecurity#dataprivacy#applicationsecuritytesting#iot#datascience#datasecurityconsulting#datagovernance#mobilesec#dataprivacyjobs#cybersecurityexperts#bigdatasecurity#pythonprojects#security#pythonprogramming#bigdataanalysis#developerjobs#datacollection#dataset#machinelearningnews#machinelearningcourse#bigdata#bigdatatechnologies#dataprotection#datascienceeducation
1 note
·
View note
Text
What is data governance, and why is it important?

Data governance is defined as the overall management of the availability, usability, integrity, and security of data used in an enterprise. A structured data governance program includes a managing body, a defined set of procedures, and a plan to execute these procedures. Today almost all organizations have migrated their data assets to the cloud. To manage these data, their data governance framework should have the following key components:
· A framework that enables people to define, agree to and enforce data policies
· Effective processes for control and management over all data assets in the cloud and in legacy systems
· The optimum tools and technologies for operationalizing data policy compliance
The benefits of Data Governance are many:
· Improved decision making
· Better risk management
· Regulatory compliance
How do you manage your Data? Please share your experiences with us.
#IndianChamberofCommerceBlogs#datagovernance#datascience#bigdata#dataprivacy#datasecurityconsulting#mobilesecurity#applicationsecuritytesting#iotsecurity#applicationsecurity#datasecurity
0 notes
Text
How Application Security Testing Can Mitigate the Impact of Threat Vectors

Is your business facing security challenges that are leading to client dissatisfaction? If not addressed soon, these can impact your brand equity negatively and allow clients to look for your competitors. One of the reasons for such challenges to flare up is the lack of integration of cyber security testing in the SDLC. Remember that approximately 84 percent of software breaches occur as a result of application layer vulnerabilities. This is due to the fact that today’s enterprise applications are vast in their sweep, with numerous components and multiple integrations with third-party software.
Also, given the presence of a multitude of APIs, hackers have a goldmine of opportunities to cause security breaches. So, what needs to be done to overcome the challenges of safety, brand recall, and client retention? The answer lies in engaging professional and experienced application security testing services and preventing malicious cyber-attacks. The primary objective of any application security testing company is to identify the vulnerabilities or weaknesses in the digital infrastructure, especially in the applications, and how various threat actors can exploit those vulnerabilities.
Various types of application security testing
For any website or application, it is important to execute a comprehensive application security testing exercise to find different security hacks. The various types of application security testing methodology are:
Static Application Security Testing (SAST): It is a white-box testing approach where testers check the workings of an application by inspecting the static source code, byte code, and binaries and reporting any security vulnerabilities present. SAST can fix codes to nullify the vulnerabilities it scanned. It enables developers to verify the code’s compliance with established secure coding standards and guidelines such as CERT before releasing it into the production environment.
Dynamic Application Security Testing (DAST): It is a black box testing approach where testers detect security vulnerabilities in an application while it is running. By applying it to an operating code, DAST can detect issues with responses, interfaces, scripting, requests, sessions, data injection, DOM injection, execution of third-party elements, query strings, authentication, and many others. The DAST tools can scan several simulated malicious test cases and report on the application’s response thereto.
Interactive Application Security Testing (IAST): It is a hybrid application security testing approach combining both SAST and DAST methods to identify a wide range of security-related vulnerabilities. Like DAST, IAST tests the applications dynamically while they are in operation, but from within the applications’ server. This allows the IAST tools to test the compiled source codes. The IAST approach provides information about the root cause of vulnerabilities and the specific sections of code that represent them, thereby ensuring quick and effective remediation. IAST tools can analyze data flow, source code, third-party libraries, and configuration in the quest to identify vulnerabilities.
Mobile Application Security Testing (MAST): This testing approach allows application security testing services to combine both static and dynamic analysis and detect a wide range of vulnerabilities and mobile-specific issues, namely, data leakage, jailbreaking, and malicious Wi-Fi networks.
Best practices to follow in application security testing
To detect and mitigate various security-related vulnerabilities in applications and ensure a superior user experience, software security testing services need to employ the best practices as mentioned below:
Shift-left security testing: According to the new development and security paradigms such as DevSecOps, security testing needs to be integrated and implemented across the SDLC. The idea is to detect any security-related vulnerability in its nascent state and fix it before it morphs into something bigger and more complex.
Test internal interfaces: As standard practice, cybersecurity testing services tend to focus on external threats, such as those emanating from web forms and API requests submitted by users. However, threat actors are more likely to exploit vulnerabilities or weak authentication residing in internal interfaces once they make their way in. Hence, testers need to validate the quality of connections, inputs, and integrations between internal systems.
Test often: Enterprise applications have several components and third-party integrations that may develop new vulnerabilities during runtime. Also, many of the components can face end-of-life situations or need security updates, which can present themselves after the initial round of testing is over. Hence, it is important to test enterprise-scale applications as often as possible while focusing on high-impact threats and business-critical systems and components.
Conclusion
The users of today are no longer satisfied with average-quality products or services. They want quality and secure systems to perform various tasks on the go. This is where the role of application security testing services becomes critical for identifying security-related vulnerabilities in the application under development. Prompt mitigation of threats is the recipe for success that enterprises across verticals should envisage and implement.
Resource
James Daniel is a software Tech enthusiastic & works at Cigniti Technologies. I'm having a great understanding of today's software testing quality that yields strong results and always happy to create valuable content & share thoughts.
Article Source: devdojo.com
0 notes
Photo

What is DAST or Dynamic Application Security Testing?
Dynamic Application Security Testing (DAST) simulates controlled attacks on a web application or service to detect security flaws in a running environment. It evaluates items during operation and provides feedback on compliance and general security issues.
0 notes
Photo

This guide will help you understand all the benefits you can avail through Application Security Testing. Read more. Visit at https://webol.co.uk/blog/application-security-testing/
0 notes
Text
Increasing number of cyber-attacks is driving market growth of dynamic application security testing (DAST)
Dynamic Application Security Testing (DAST) is a highly reliable method that validates the program and web application against a set of XML vulnerability scans. Unlike with SAST, however, DAST detects the vulnerability even without executing the affected code. They are useful in improving the security of the organization by providing insights regarding the behavior of web applications during the production process. Dynamic application security testing is a means of ensuring that a system, its assets, and modes of operation are secure from various security threats. It is carried out at several levels. At the simplest level, static application security testing is aimed at ensuring the functionality of the software and to test how well it runs once development is complete. The second level involves testing for the system's security and integrity, which may involve performing denial-of-service attacks or even attacks against the confidentiality of data.
The growing risk associated with the business due to application vulnerabilities coupled with the strict government regulations is predominantly fueling the market growth. Moreover, the increasing level of cyber-attacks is also contributing to the market growth of Dynamic Application Security Testing. According to the National Institute of Standards and Technology, the data breaches exposed 4.1 billion records in the first half of 2019.
Read more @
https://coherentmarketinsights-blog.blogspot.com/2020/12/increasing-number-of-cyber-attacks-is.html
#DynamicApplicationSecurityTesting#DAST#ApplicationSecurityTesting#InteractiveSecurityTesting#RapidApplicationSecurity#ecommerceindustry#DynamicApplicationSecurityTestingTrends#DynamicApplicationSecurityTestinganalysis
0 notes
Photo

We are looking for EO/SEO – Application Security Testing – IT Department BFSI Industry in Mumbai .The Ideal Qualification Bachelor of Engineering / Masters of Engineering / Masters in Computer Applicatio. Interested candidate can upload their Cv www.mhc.co.in/jobs or share their resume on [email protected]
https://bit.ly/2WUwO2A
Kindlyfind below the Job Responsibilities: •Mandatory:Web and Thick client application penetration testing In-depth hands on knowledge on black box and white box security assessments, Threat profiling and Threat modelling •Understanding the application and business flow •Preparing the test cases for the application security testing.
0 notes
Photo

What is SAST?
Static Application Security Testing (SAST) is a popular Application Security (AppSec) tool that checks an application’s source, binary, or byte code. It is a white-box testing tool that detects the start of vulnerabilities and assists in the remediation of the underlying security problems. SAST solutions examine an application from the “inside out,” They do not require a running system to scan it.
0 notes
Text
What are the Top 10 Free Security Testing Frameworks?

With the spread of digitization across domains, cybercriminals are having a field day. They are leveraging every trick in the book to hack into websites or applications to steal confidential information or disrupt the functioning of an organization’s digital systems. Even statistics buttress the malevolent role of cybercriminals with scary projections. Accordingly, by the end of 2021, the world is going to be poorer by $6 trillion as cybercrime is expected to extract its pound of flesh. And by 2025, the figure is expected to touch $10.5 trillion. No wonder, security testing is pursued with renewed zeal by organizations cutting across domains, with the market size expected to touch $16.9 billion by 2025. One of the measures to implement cybersecurity testing is the use of security testing frameworks. The importance of using such frameworks lies in the fact that they can guide organizations in complying with regulations and security policies relevant to a particular sector. Let us take you through 10 such open-source security testing frameworks to ensure the protection of data in a digital system and maintain its functionality.
10 open-source security testing frameworks
To identify and mitigate the presence of vulnerabilities and flaws in a web or mobile application, there are many open-source security testing frameworks. These can be customized to match the requirements of each organization and find vulnerabilities such as SQL Injection, Broken Authentication, Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), Session Management, and Security Misconfigurations, among others.
#1 Synk: Licensed by Apache, Synk is an open-source vendor application security testing framework that detects underlying vulnerabilities and fixes the same during the development cum testing process. It can be used to secure all components of any cloud-based native application and features continuous AI learning and semantic code analysis in real-time.
#2 NetSparker: It is a one-stop destination for all security needs, which can be easily integrated into any type of development or test environment. NetSparker features a proof-based scanning technology that can identify glitches such as Cross-Site Scripting (XSS) and verify false positives in websites or applications, thereby eliminating the investment in man-hours.
#3 Acunetix: A powerful application security testing solution to secure your web environment and APIs by detecting vulnerabilities such as SQL injection, Cross-Site Scripting (XSS), and others. It has a DeepScan crawler that can scan HTML websites and client-side SPAs. Using this, users can export identified vulnerabilities to trackers such as GitHub, Atlassian JIRA, Bugzilla, Mantis, and others.
#4 w3af: Built using Python, the w3af attack and audit framework is a free application security scanner to find and exploit vulnerabilities in web applications during penetration testing.
#5 Zed Attack Proxy (ZAP): Built by OWASP (Open Web Application Security Project), ZAP is an open-source and multi-platform software security testing tool to detect vulnerabilities in a web application. Written in Java, ZAP can intercept a proxy to manually test a webpage and expose errors such as private IP disclosure, SQL injection, missing anti-CSRF tokens, XSS injection, and others.
#6 ImmuniWeb: Employing artificial intelligence, ImmuniWeb is a security platform to conduct security testing. With a one-click patching system, the platform can ensure continuous compliance monitoring and boasts proprietary technology to check for privacy, compliance, and server hardening.
#7 Wapiti: A command-line application to detect scripts and forms where data can be injected. It conducts a black box scan by injecting payloads to check if the detected scripts are vulnerable. Wapiti is capable of generating reports in several features and formats highlighting vulnerabilities such as database injection, Cross-Site Scripting (XSS), file disclosure, and .htaccess configuration, among others.
#8 Vega: Written in Java, this open-source scanning tool working on OSX, Windows, and Linux platforms can detect vulnerabilities such as shell injection, blind SQL injection, and Cross-Site Scripting, among others. Its intercepting proxy facilitates tactical inspection by monitoring client-server communication. The detection modules can create new attack modules using APIs.
#9 Arachni: A free Ruby-based framework, Arachni is leveraged by penetration testers to evaluate the security of web applications. Supporting all major operating systems, this multi-platform cybersecurity testing tool can uncover scores of vulnerabilities, including XSS injection, SQL injection, and invalidated redirect, among others.
#10 Google Nogotofail: A network security testing framework, it can detect known vulnerabilities and misconfigurations such as TLS/SSL. It offers a flexible method of scanning, detecting, and fixing SSL/TLS connections. To be set up as a VPN server, router, or proxy server, it works with major operating systems such as iOS, Android, Windows, OSX, or Linux.
Conclusion
The above-mentioned tools/frameworks used by security testing services can be chosen as per the security testing requirements of organizations. With cybersecurity threats being faced by organizations across domains, the use of these frameworks can keep an organization in good stead in securing customer and business data, adhering to regulatory standards, and delivering superior customer experiences.
Resource
James Daniel is a software Tech enthusiastic & works at Cigniti Technologies. I'm having a great understanding of today's software testing quality that yields strong results and always happy to create valuable content & share thoughts.
Article Source: wattpad.com
#securitytesting#cybersecuritytesting#penetrationtesting#applicationsecuritytesting#softwaresecuritytesting
0 notes
Photo

We are looking for EO/SEO Application Security Testing BFSI Industry in Mumbai. The Ideal Qualification: Bachelor of Engineering / Masters of Engineering / Masters in Computer Application. Interested candidate can upload their Cv www.mhc.co.in/jobs or share their resume on [email protected]
https://bit.ly/2WUwO2A
Kindlyfind below the Job Responsibilities: •Mandatory : Excellent communication, proactive, presentable, should have worked on PF, ESIC, recruitment, employee handling. •Tool based and manual “web application” security / penetration testing •Understanding the application and business flow
0 notes
Photo

We are looking forEO/SEO – Application Security Testing – BFSI Industry in Mumbai. The Ideal Qualification Bachelor of Engineering / Masters of Engineering / Masters in Computer Application. Interested candidate can upload their Cv www.mhc.co.in/jobs or share their resume on [email protected]
https://bit.ly/2WUwO2A
Kindly find below the Job Responsibilities: •Mandatory: Web and Thick client application penetration testing In-depth hands on knowledge on black box and white box security assessments, Threat profiling and Threat modelling. •Common Vulnerabilities and Exposures (CVE) •Tool based and manual “web application” security / penetration testing
0 notes