#backup esxi
Explore tagged Tumblr posts
Text
How to Back Up and Restore VMware ESXi Host Configuration
How to Back Up and Restore VMware ESXi Host Configuration - Learn the command line tools needed to backup ESXi also a sample PowerCLI script you can schedule #vmware #vsphere #esxi #disasterrecovery #backupesxi #restoreesxi #hostfirmware
When thinking about disaster recovery strategies for your virtualization environment, it is easy to miss one of the important aspects of disaster recovery in your VMware environment: your host configuration. Have you ever had an ESXi host crash and you thought to yourself, man I wish I had a backup of my configuration, including VMkernel ports, storage configuration, network labels, etc? I know I…
View On WordPress
0 notes
Text
Ransomware Attacks Target VMware ESXi Infrastructure Following Interesting Pattern

Cybersecurity firm Sygnia has shed light on a concerning trend where ransomware attacks targeting VMware ESXi infrastructure follow a well-established pattern, regardless of the specific file-encrypting malware deployed. According to the Israeli company's incident response efforts involving various ransomware families, these attacks adhere to a similar sequence of actions.
The Attack Sequence
- Initial access is obtained through phishing attacks, malicious file downloads, or exploitation of known vulnerabilities in internet-facing assets. - Attackers escalate their privileges to obtain credentials for ESXi hosts or vCenter using brute-force attacks or other methods. - Access to the virtualization infrastructure is validated, and the ransomware is deployed. - Backup systems are deleted, encrypted, or passwords are changed to complicate recovery efforts. - Data is exfiltrated to external locations such as Mega.io, Dropbox, or attacker-controlled hosting services. - The ransomware initiates execution and encrypts the "/vmfs/volumes" folder of the ESXi filesystem. - The ransomware propagates to non-virtualized servers and workstations, widening the scope of the attack.

Mitigation Strategies
To mitigate the risks posed by such threats, organizations are advised to implement the following measures: - Ensure adequate monitoring and logging are in place - Create robust backup mechanisms - Enforce strong authentication measures - Harden the environment - Implement network restrictions to prevent lateral movement
Malvertising Campaign Distributing Trojanized Installers
In a related development, cybersecurity company Rapid7 has warned of an ongoing campaign since early March 2024 that employs malicious ads on commonly used search engines to distribute infected installers for WinSCP and PuTTY via typosquatted domains. These counterfeit installers act as a conduit to drop the Sliver post-exploitation toolkit, which is then used to deliver more payloads, including a Cobalt Strike Beacon leveraged for ransomware deployment. This activity shares tactical overlaps with prior BlackCat ransomware attacks that have used malvertising as an initial access vector, disproportionately affecting members of IT teams who are most likely to download the infected files.
New Ransomware Families and Global Trends
The cybersecurity landscape has witnessed the emergence of new ransomware families like Beast, MorLock, Synapse, and Trinity. The MorLock group has extensively targeted Russian companies, encrypting files without first exfiltrating them and demanding substantial ransoms. According to NCC Group's data, global ransomware attacks in April 2024 registered a 15% decline from the previous month, with LockBit's reign as the top threat actor ending in the aftermath of a sweeping law enforcement takedown earlier this year. The turbulence in the ransomware scene has been complemented by cyber criminals advertising hidden Virtual Network Computing (hVNC) and remote access services like Pandora and TMChecker, which could be utilized for data exfiltration, deploying additional malware, and facilitating ransomware attacks. Read the full article
4 notes
·
View notes
Text
AOMEI Cyber Backup: Soluția Profesională pentru Backup și Protecția Datelor ConținutCum puteți obține AOMEI Cyber Backup cu licență gratuită pentru 1 an?Ce este AOMEI Cyber Backup?Caracteristici Principale 1. Backup și Restaurare Automatizată2. Suport pentru Mașini Virtuale3. Stocare și Management Centralizat4. Compatibilitate Extinsă5. Protecție Împotriva Atacurilor Ransomware6. Restaurare Rapidă și EficientăAvantajele Utilizării AOMEI Cyber BackupCui se Adresează? Într-o eră digitală în care datele reprezintă una dintre cele mai valoroase resurse ale unei companii, protejarea acestora devine o prioritate. AOMEI Cyber Backup este o soluție avansată de backup care asigură protecția și recuperarea rapidă a datelor esențiale, minimizând riscurile pierderii acestora. Această platformă este ideală pentru companii, administratori IT și utilizatori care doresc o soluție fiabilă, eficientă și ușor de utilizat. Denumire produs:AOMEI Cyber BackupWebsite:https://www.ubackup.com/enterprise/Valabilitate licență:1 anPagina promoțională:link (acest software face parte dintr-o campania promoțională World Backup Day organizată de Aomei)Sistem de operare:WindowsDescarcă:AOMEICyberBackup.zip (această arhivă conține kit-ul de instalare, plus codul de licență pentru activarea programului gratuit pentru 1 an) Cum puteți obține AOMEI Cyber Backup cu licență gratuită pentru 1 an? Descărcați și instalați programul pe computer. Lansați aplicația făcând dublu clic pe pictograma nou apărută de pe desktop, o fereastră se va deschide în browser, conectați-vă cu admin pentru numele de utilizator și administratorul pentru parolă. Mergeți la: settings -> License Code -> Enter License Code. Ce este AOMEI Cyber Backup? AOMEI Cyber Backup este un software profesional destinat backup-ului și recuperării datelor, oferind funcționalități avansate pentru protejarea serverelor, mașinilor virtuale și a altor tipuri de date critice. Software-ul se remarcă printr-o interfață intuitivă și funcționalități puternice, permițând utilizatorilor să își automatizeze procesele de backup și să prevină pierderile de date cauzate de erori hardware, atacuri cibernetice sau alte incidente neprevăzute. Caracteristici Principale 1. Backup și Restaurare Automatizată AOMEI Cyber Backup permite utilizatorilor să configureze planuri automate de backup, reducând astfel riscul pierderii de date. Programul permite backup incremental, diferențial și complet, oferind flexibilitate maximă în gestionarea copiilor de siguranță. 2. Suport pentru Mașini Virtuale Software-ul este compatibil cu VMware ESXi și Hyper-V, oferind soluții de backup eficiente pentru mediile virtualizate. Utilizatorii pot programa backup-uri automate pentru mașinile virtuale și pot restaura rapid datele în caz de necesitate. 3. Stocare și Management Centralizat AOMEI Cyber Backup permite gestionarea centralizată a tuturor backup-urilor, oferind o platformă ușor de utilizat pentru monitorizarea și administrarea datelor critice. 4. Compatibilitate Extinsă Software-ul suportă multiple medii de stocare, inclusiv NAS, SAN, HDD, SSD, unități USB și stocare în cloud, asigurând flexibilitate în gestionarea backup-urilor. 5. Protecție Împotriva Atacurilor Ransomware AOMEI Cyber Backup oferă funcționalități avansate de protecție a datelor, reducând riscul atacurilor ransomware și al pierderii accidentale a fișierelor importante. 6. Restaurare Rapidă și Eficientă Funcțiile avansate de restaurare permit recuperarea rapidă a datelor, reducând timpul de inactivitate și asigurând continuitatea activității. Avantajele Utilizării AOMEI Cyber Backup Ușor de utilizat: Interfața intuitivă permite configurarea rapidă a backup-urilor fără cunoștințe avansate de IT. Automatizare completă: Posibilitatea de a programa backup-uri automate și de a gestiona eficient spațiul de stocare. Securitate sporită: Protecție împotriva atacurilor cibernetice și prevenirea pierderilor de date critice.
Flexibilitate: Compatibilitate cu multiple sisteme de operare, dispozitive și medii de stocare. Cui se Adresează? Această soluție este ideală pentru: Companii mici și mijlocii care doresc să își protejeze datele fără a investi în infrastructuri complexe. Administratori IT care au nevoie de o soluție fiabilă și scalabilă pentru gestionarea backup-urilor. Utilizatori individuali care doresc o metodă sigură și ușoară de protecție a fișierelor importante.
0 notes
Text
Shaping IT Excellence: The Role of an IT Manager – Server Infrastructure in the Housing Finance Industry with Morpheus Consulting

Introduction:
For professionals hoping to succeed as an IT Manager-Server Infrastructurev in Mumbai, Morpheus Consulting, a leading employment business, is pleased to offer an outstanding career opportunity. Morpheus Consulting is an expert in matching top talent with suitable positions, guaranteeing that businesses hire qualified applicants for their vital IT positions. In order to manage and optimize server infrastructure, guarantee high availability, and put security measures in place to protect company data, an IT manager specializing in server infrastructure plays a crucial role.
For those who are keen to promote IT excellence, Morpheus Consulting provides a dynamic career path. The company acknowledges the value of seasoned IT specialists in the banking and housing finance industries. Given Morpheus Consulting's extensive experience in hiring, this position offers professionals searching for a special opportunity.
The Role of a IT Manager ��� Server Infrastructure in the Housing Finance Industry
1.Server Infrastructure Management:
Strong server infrastructure is the foundation of any financial organization, as Morpheus Consulting is aware. Microsoft Windows Server environment design, implementation, and maintenance will fall under the purview of the IT manager. To guarantee optimum system performance, Morpheus Consulting makes sure that businesses hire experts with knowledge of Active Directory, DNS, DHCP, and other essential server functions.
2.Cloud Computing and Virtualization:
Morpheus Consulting is aware of the increasing significance of virtualization and cloud computing in contemporary IT settings. In addition to managing vCenter servers and VMware ESXi hosts, the IT manager will deploy and maintain cloud services such as AWS EC2, S3, and RDS. Morpheus Consulting makes sure businesses choose experts who can propel digital transformation and optimize hybrid cloud systems.
3.Disaster Recovery and Security Compliance:
IT executives that can guarantee business continuity through efficient disaster recovery planning and security procedures are highly valued by Morpheus Consulting. The IT manager will supervise Commvault backup plans and guarantee banking industry regulatory compliance. Morpheus Consulting guarantees that companies employ experts in risk management and data protection.
4.Troubleshooting and Performance Monitoring:
Professionals with the ability to proactively detect and fix system problems are highly valued by Morpheus Consulting. In order to track server performance and diagnose hardware and software issues, the IT manager will make use of monitoring tools. Organizations who choose candidates with high analytical and problem-solving abilities are guaranteed to do so by Morpheus Consulting.
What Makes an Ideal Candidate for Morpheus Consulting?
Proven Experience in IT Infrastructure Management:Professionals with a wealth of experience overseeing server infrastructure in business settings are sought after by Morpheus Consulting. Proficiency with AWS, VMware, and Microsoft Windows Server is necessary for this position. Employers are guaranteed to select applicants with practical IT systems administration experience by Morpheus Consulting.
Strong Knowledge of Cloud and Virtualization Technologies:Professionals with extensive expertise in virtualization and cloud computing are highly valued by Morpheus Consulting. The IT manager must to be knowledgeable with VMware and AWS services. Morpheus Consulting guarantees that businesses hire applicants who have prior expertise with cloud migration.
Leadership and Team Management Skills:The significance of leadership in IT operations is recognized by Morpheus Consulting. To promote effective service delivery, the IT manager will coach and direct IT staff. Morpheus Consulting guarantees that companies employ experts with strong communication and leadership abilities.
Problem-Solving and Analytical Abilities:Morpheus Consulting is aware that solving IT problems quickly and analytically is necessary. To guarantee system stability, the IT manager should exhibit good problem-solving abilities. Morpheus Consulting guarantees that companies hire people who can solve problems strategically.
Morpheus Consulting ensures that professionals flourish in their careers by matching them with opportunities that align with their experience.
Why This Role Matters:
Enhancing system performance, promoting business continuity, and guaranteeing smooth IT operations are all made possible by the IT Manager-Server Infrastructure. Professionals in this position are in charge of creating, implementing, and managing server systems that enable vital corporate applications, as recognized by Morpheus Consulting. Morpheus Consulting makes sure that companies hire the best applicants who can handle cloud infrastructure, virtualized platforms, and Windows Server settings.
Implementing security rules, maximizing storage, and spearheading disaster recovery plans are all under the purview of the IT manager. Morpheus Consulting is aware that companies need competent IT leaders who can manage risk, maintain compliance, and guarantee system uptime in the highly regulated financial sector.
Conclusion:
In order to manage server environments, promote cloud adoption, and guarantee business continuity, the position of IT Manager-Server Infrastructure is essential. Morpheus Consulting takes pleasure in finding elite IT specialists who can help a business succeed. Morpheus Consulting will assist you in locating the ideal job if you possess the technical know-how and leadership abilities necessary to oversee IT infrastructure in the banking industry. To advance in your IT profession, sign up with Morpheus Consulting now.
Since 2007, Morpheus Consulting has been a reliable partner in the recruiting industry, offering professional hiring services across Asia, Africa, and the Middle East. Our 130-person consulting firm focuses in finding outstanding people for a range of sectors.Morpheus Consulting makes sure that companies use experts since it recognizes the vital function that IT infrastructure plays in financial institutions. Morpheus Consulting links applicants with fulfilling IT management employment opportunities through our wide network and industry expertise.
Apply now to take on this challenging and impactful role with confidence, and rest assured that Morpheus Consulting will be your trusted partner in navigating your professional journey.
For more Recruitment / Placement / HR / Consultancy services, connect with Morpheus Consulting:
📞: (+91) 8376986986
🌐: www.mhc.co.in
#morpheusconsulting
#morpheushumanconsulting
#mumbaijobs
#jobsinmumbai
#jobsmumbai
#jobsinnavimumbai
#JobsInMumbai
#JobsInDelhi
#JobsInBangalore
#JobsInHyderabad
#JobsInChennai
#JobsInKolkata
#JobsInPune
#JobsInAhmedabad
#JobsInNoida
#JobsInGurgaon
#JobsInJaipur
#JobsInLucknow
#JobsInIndore
#JobsInChandigarh
#JobsInNagpur
#JobsInBhubaneswar
#JobsInCochin
#JobsInVadodara
#JobsInThane
#JobsinIndia
#IndiaJobs
#mumbaijobseekers
#mumbaijobsearch
0 notes
Text
Backup ESXi Host configuration
Enable SSH
vim-cmd hostsvc/firmware/sync_config
vim-cmd hostsvc/firmware/backup_config
Copy and paste the download link and replace the "*" with your host IP address.
0 notes
Photo

#純靠北工程師74a
----------
我工作的分部給另一間公司收購 現在和舊公司分拆中 我負責的部份是東亞地區的infra 然後某分部分拆後沒有backup server 因為年末要搬遷辦公室所以考慮搬遷的同時買一個 舊公司的IT系統經理建議我們買Qnap用作ESXi的datastore和veeam的備份空間
----------
💖 純靠北工程師 官方 Discord 歡迎在這找到你的同溫層!
👉 https://discord.gg/tPhnrs2
----------
💖 全平台留言、文���詳細內容
👉 https://init.engineer/cards/show/9226
0 notes
Text
Fortigate Vm Trial License Reset


Fortigate Vm Trial License Reset Download
Fortigate Vm License Download
So we recently started looking into Terminal Services and RemoteFX to power some of our admin users and move them off to thin clients instead of full blown desktops. As a trial I begun setting up RDS on one of our Dev machines. After going through the motions of enabling the Remote Desktop Features and setting up RemoteFX on a Virtual Machine for testing, I found that I couldn’t login via RDP to that machine. Going back to the RDS host I found the Licensing popup that informed me that the 128 day trial license had expired. Since this was a test I didn’t want to go using keys to activate or setup a licensing server (purely a PoC for us in IT at this stage).
Fortigate Vm Trial License Reset Download
Fortigate Vm License Download
To reset the grace period there is a registry key that we need to delete. As always when editing the registry, take a backup of the key/s you’re modifying. Navigate to the following location
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal ServerRCMGracePeriod
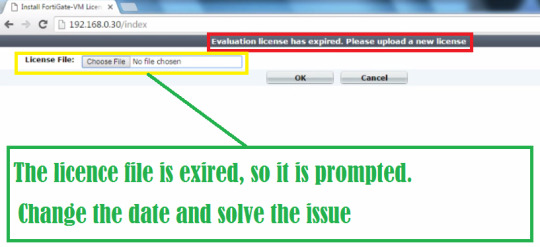
For testing, there was an integrated evaluation license for 15 days in each Fortigate VM. Since FortiOS 6.0.1 the evaluation license expires right from the first start of the virtual machine. In the GUI, there is the message 'Expired on 1970/01/01' with the possibility to upload a license file. Until FortiOS 6.0.0 it works as before. Well, you can reset the license and you can again use ESXi for next 60 days. And when the trial ends again, reset the license again.
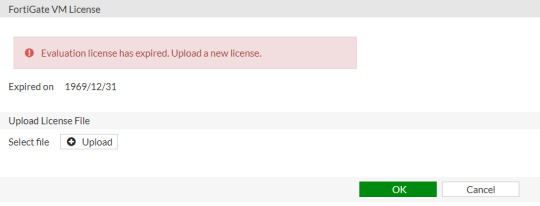
Nov 02, 2015 Fortigate Firewall VM - Reset 14 days Trial Period without losing Configuration Fortigate Firewall VM - Reset 14 days Trial Period without losing Configuration Skip navigation. Fortigate vm license file crack. Igo primo 2 4 for android 480x800 download. FortiGate-VM FortiADC-VM.
Now there should be a binary key value (like in the screenshot), you first need to have full access permissions to the folder (or take ownership) and then simply delete that value and reboot the server. Once back up your RDS Licensing should be back at the start of a 128 Day grace period. I wouldn’t do this if you have already obtained licensing and should definitely not be used in a production environment.

1 note
·
View note
Text
iiiiiiiit's backup day! other than one notable natural disaster and one notable hard drive crash, I've kept a (relatively) scrupulous horde of data that accumulated since the first time I had a "My Documents" folder. it's getting to the point where my tech horde consists of the big Windows machine, a pretty decent ESXi (virtual hosting OS, mostly a fancy way for me to run my Ubuntu server) server, and like three laptops that were too broke for my mom but not for me. Add into this mess several multi-terabyte movie and show libraries floating around at different levels of backing up and improving on one another.
enter backup day. ya boi is tired of this shit. I've been slowly merging my monolithic amounts of data together so I can start The Great Reinstall (upgrading software on everything I own and reformatting a lot of drives) but. I've just left my one working large external hard drive in Minnesota. and I don't have a power adapter for the other one. It's fine! I just shoved some specially bent paddle connectors in there


should be fine!
but anyway by like sometime tomorrow I can actually start reinstalling stuff, but I'm excited to have a central repository for all my data, and it should then be really easy to create a formal backup schedule
why do you have to do this spook? You ask. Well you see. I'd like to start mass wiping and formatting drives and computers because well. my minecraft server got hacked and I got a bunch of other weird stuff so I said fuck it! new everything! but also I don't want to list a solid 6 to 8 terabytes of legally acquired media I've been hording for e v e r plus my hundreds of gigabytes of photos!
#tech#home lab#backups#this is the least exciting part of server adminning... no new feature just old data :(#spook#excited about legally having esxi7 and provisioning my server properly#had so many problems because i didn't allocate hard drive/memory space to the main server right and didn't have any RAM until recently#so I'm looking forward to across the board improvements in server performance#also excited about my new STRICT AS FUCK FIREWALL BECAUSE PEOPLE KEEP TRYING TO HACK ME#if you're reading this and trying to hack me stop uwu it makes me sad and slows down my stuff#also the kmsauto windows activator ive had forever miiiight have a trojan built in so im redoing all my stuff from the real one
1 note
·
View note
Text
How to check and generate report of Backup ,Cloning ,Snapshot or any Other Task of VM/ESXI/datastore/Anything in vSphere using PowerCli
How to check and generate report of Backup ,Cloning ,Snapshot or any Other Task of VM/ESXI/datastore/Anything in vSphere using PowerCli
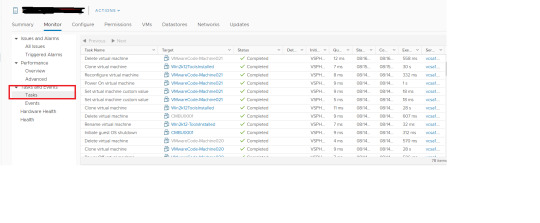
(more…)
View On WordPress
1 note
·
View note
Text
Bryan Strauch is an Information Technology specialist in Morrisville, NC
Resume: Bryan Strauch
[email protected] 919.820.0552(cell)
Skills Summary
VMWare: vCenter/vSphere, ESXi, Site Recovery Manager (disaster recovery), Update Manager (patching), vRealize, vCenter Operations Manager, auto deploy, security hardening, install, configure, operate, monitor, optimize multiple enterprise virtualization environments
Compute: Cisco UCS and other major bladecenter brands - design, rack, configure, operate, upgrade, patch, secure multiple enterprise compute environments.
Storage: EMC, Dell, Hitachi, NetApp, and other major brands - connect, zone, configure, present, monitor, optimize, patch, secure, migrate multiple enterprise storage environments.
Windows/Linux: Windows Server 2003-2016, templates, install, configure, maintain, optimize, troubleshoot, security harden, monitor, all varieties of Windows Server related issues in large enterprise environments. RedHat Enterprise Linux and Ubuntu Operating Systems including heavy command line administration and scripting.
Networking: Layer 2/3 support (routing/switching), installation/maintenance of new network and SAN switches, including zoning SAN, VLAN, copper/fiber work, and other related tasks around core data center networking
Scripting/Programming: SQL, Powershell, PowerCLI, Perl, Bash/Korne shell scripting
Training/Documentation: Technical documentation, Visio diagramming, cut/punch sheets, implementation documentations, training documentations, and on site customer training of new deployments
Security: Alienvault, SIEM, penetration testing, reporting, auditing, mitigation, deployments
Disaster Recovery: Hot/warm/cold DR sites, SAN/NAS/vmware replication, recovery, testing
Other: Best practice health checks, future proofing, performance analysis/optimizations
Professional Work History
Senior Systems/Network Engineer; Security Engineer
September 2017 - Present
d-wise technologies
Morrisville, NC
Sole security engineer - designed, deployed, maintained, operated security SIEM and penetration testing, auditing, and mitigation reports, Alienvault, etc
responsibility for all the systems that comprise the organizations infrastructure and hosted environments
main point of contact for all high level technical requests for both corporate and hosted environments
Implement/maintain disaster recovery (DR) & business continuity plans
Management of network backbone including router, firewall, switch configuration, etc
Managing virtual environments (hosted servers, virtual machines and resources)
Internal and external storage management (cloud, iSCSI, NAS)
Create and support policies and procedures in line with best practices
Server/Network security management
Senior Storage and Virtualization Engineer; Datacenter Implementations Engineer; Data Analyst; Software Solutions Developer
October 2014 - September 2017
OSCEdge / Open SAN Consulting (Contractor)
US Army, US Navy, US Air Force installations across the United States (Multiple Locations)
Contract - Hurlburt Field, US Air Force:
Designed, racked, implemented, and configured new Cisco UCS blade center solution
Connected and zoned new NetApp storage solution to blades through old and new fabric switches
Implemented new network and SAN fabric switches
Network: Nexus C5672 switches
SAN Fabric: MDS9148S
Decommissioned old blade center environment, decommissioned old network and storage switches, decommissioned old SAN solution
Integrated new blades into VMWare environment and migrated entire virtual environment
Assessed and mitigated best practice concerns across entire environment
Upgraded entire environment (firmware and software versions)
Security hardened entire environment to Department of Defense STIG standards and security reporting
Created Visio diagrams and documentation for existing and new infrastructure pieces
Trained on site operational staff on new/existing equipment
Cable management and labeling of all new and existing solutions
Implemented VMWare auto deploy for rapid deployment of new VMWare hosts
Contract - NavAir, US Navy:
Upgraded and expanded an existing Cisco UCS environment
Cable management and labeling of all new and existing solutions
Created Visio diagrams and documentation for existing and new infrastructure pieces
Full health check of entire environment (blades, VMWare, storage, network)
Upgraded entire environment (firmware and software versions)
Assessed and mitigated best practice concerns across entire environment
Trained on site operational staff on new/existing equipment
Contract - Fort Bragg NEC, US Army:
Designed and implemented a virtualization solution for the US ARMY.
This technology refresh is designed to support the US ARMY's data center consolidation effort, by virtualizing and migrating hundreds of servers.
Designed, racked, implemented, and configured new Cisco UCS blade center solution
Implemented SAN fabric switches
SAN Fabric: Brocade Fabric Switches
Connected and zoned new EMC storage solution to blades
Specific technologies chosen for this solution include: VMware vSphere 5 for all server virtualization, Cisco UCS as the compute platform and EMC VNX for storage.
Decommissioned old SAN solution (HP)
Integrated new blades into VMWare environment and migrated entire environment
Physical to Virtual (P2V) conversions and migrations
Migration from legacy server hardware into virtual environment
Disaster Recovery solution implemented as a remote hot site.
VMware SRM and EMC Recoverpoint have been deployed to support this effort.
The enterprise backup solution is EMC Data Domain and Symantec NetBackup
Assessed and mitigated best practice concerns across entire environment
Upgraded entire environment (firmware and software versions)
Security hardened entire environment to Department of Defense STIG standards and security reporting
Created Visio diagrams and documentation for existing and new infrastructure pieces
Trained on site operational staff on new equipment
Cable management and labeling of all new solutions
Contract - 7th Signal Command, US Army:
Visited 71 different army bases collecting and analyzing compute, network, storage, metadata.
The data collected, analyzed, and reported will assist the US Army in determining the best solutions for data archiving and right sizing hardware for the primary and backup data centers.
Dynamically respond to business needs by developing and executing software solutions to solve mission reportable requirements on several business intelligence fronts
Design, architect, author, implement in house, patch, maintain, document, and support complex dynamic data analytics engine (T-SQL) to input, parse, and deliver reportable metrics from data collected as defined by mission requirements
From scratch in house BI engine development, 5000+ SQL lines (T-SQL)
Design, architect, author, implement to field, patch, maintain, document, and support large scale software tools for environmental data extraction to meet mission requirements
Large focus of data extraction tool creation in PowerShell (Windows, Active Directory) and PowerCLI (VMWare)
From scratch in house BI extraction tool development, 2000+ PowerShell/PowerCLI lines
Custom software development to extract data from other systems including storage systems (SANs), as required
Perl, awk, sed, and other languages/OSs, as required by operational environment
Amazon AWS Cloud (GovCloud), IBM SoftLayer Cloud, VMWare services, MS SQL engines
Full range of Microsoft Business Intelligence Tools used: SQL Server Analytics, Reporting, and Integration Services (SSAS, SSRS, SSIS)
Visual Studio operation, integration, and software design for functional reporting to SSRS frontend
Contract - US Army Reserves, US Army:
Operated and maintained Hitachi storage environment, to include:
Hitachi Universal Storage (HUS-VM enterprise)
Hitachi AMS 2xxx (modular)
Hitachi storage virtualization
Hitachi tuning manager, dynamic tiering manager, dynamic pool manager, storage navigator, storage navigator modular, command suite
EMC Data Domains
Storage and Virtualization Engineer, Engineering Team
February 2012 – October 2014
Network Enterprise Center, Fort Bragg, NC
NCI Information Systems, Inc. (Contractor)
Systems Engineer directly responsible for the design, engineering, maintenance, optimization, and automation of multiple VMWare virtual system infrastructures on Cisco/HP blades and EMC storage products.
Provide support, integration, operation, and maintenance of various system management products, services and capabilities on both the unclassified and classified network
Coordinate with major commands, vendors, and consultants for critical support required at installation level to include trouble tickets, conference calls, request for information, etc
Ensure compliance with Army Regulations, Policies and Best Business Practices (BBP) and industry standards / best practices
Technical documentation and Visio diagramming
Products Supported:
EMC VNX 7500, VNX 5500, and VNXe 3000 Series
EMC FAST VP technology in Unisphere
Cisco 51xx Blade Servers
Cisco 6120 Fabric Interconnects
EMC RecoverPoint
VMWare 5.x enterprise
VMWare Site Recovery Manager 5.x
VMWare Update Manager 5.x
VMWare vMA, vCops, and PowerCLI scripting/automation
HP Bladesystem c7000 Series
Windows Server 2003, 2008, 2012
Red Hat Enterprise and Ubuntu Server
Harnett County Schools, Lillington, NC
Sr. Network/Systems Administrator, August 2008 – June 2011
Systems Administrator, September 2005 – August 2008
Top tier technical contact for a 20,000 student, 2,500 staff, 12,000 device environment District / network / datacenter level design, implementation, and maintenance of physical and virtual servers, routers, switches, and network appliances
Administered around 50 physical and virtual servers, including Netware 5.x/6.x, Netware OES, Windows Server 2000, 2003, 2008, Ubuntu/Linux, SUSE, and Apple OSX 10.4-10.6
Installed, configured, maintained, and monitored around 175 HP Procurve switches/routers Maintained web and database/SQL servers (Apache, Tomcat, IIS and MSSQL, MySQL) Monitored all network resources (servers, switches, routers, key workstations) using various monitoring applications (Solarwinds, Nagios, Cacti) to ensure 100% availability/efficiency Administered workstation group policies and user accounts via directory services
Deployed and managed applications at the network/server level
Authored and implemented scripting (batch, Unix) to perform needed tasks
Monitored server and network logs for anomalies and corrected as needed
Daily proactive maintenance and reactive assignments based on educational needs and priorities Administered district level Firewall/IPS/VPN, packet shapers, spam filters, and antivirus systems Administered district email server and accounts
Consulted with heads of all major departments (finance, payroll, testing, HR, child nutrition, transportation, maintenance, and the rest of the central staff) to address emergent and upcoming needs within their departments and resolve any critical issues in a timely and smooth manner Ensure data integrity and security throughout servers, network, and desktops
Monitored and corrected all data backup procedures/equipment for district and school level data
Project based work through all phases from design/concept through maintenance
Consulted with outside contractors, consultants, and vendors to integrate and maintain various information technologies in an educational environment, including bid contracts
Designed and implemented an in-house cloud computing infrastructure utilizing a HP Lefthand SAN solution, VMWare’s ESXi, and the existing Dell server infrastructure to take full advantage of existing technologies and to stretch the budget as well as provide redundancies
End user desktop and peripherals support, training, and consultation
Supported Superintendents, Directors, all central office staff/departments, school administration offices (Principals and staff) and classroom teachers and supplementary staff
Addressed escalations from other technical staff on complex and/or critical issues
Utilized work order tracking and reporting systems to track issues and problem trends
Attend technical conferences, including NCET, to further my exposure to new technologies
Worked in a highly independent environment and prioritized district needs and workload daily Coordinated with other network admin, our director, and technical staff to ensure smooth operations, implement long term goals and projects, and address critical needs
Performed various other tasks as assigned by the Director of Media and Technology and
Superintendents
Products Supported
Microsoft XP/Vista/7 and Server 2000/2003/2008, OSX Server 10.x, Unix/Linux
Sonicwall NSA E8500 Firewall/Content filter/GatewayAV/VPN/UTM Packeteer 7500 packet shaping / traffic management / network prioritization
180 HP Procurve L2/L3 switches and HP Procurve Management Software
Netware 6.x, Netware OES, SUSE Linux, eDirectory, Zenworks 7, Zenworks 10/11
HP Lefthand SAN, VMWare Server / ESXi / VSphere datacenter virtualization
Solarwinds Engineer Toolset 9/10 for Proactive/Reactive network flow monitoring
Barracuda archiving/SPAM filter/backup appliance, Groupwise 7/8 email server
Education
Bachelor of Science, Computer Science
Minor: Mathematics
UNC School System, Fayetteville State University, May 2004
GPA: 3
High Level Topics (300+):
Data Communication and Computer Networks
Software Tools
Programming Languages
Theory of Computation
Compiler Design Theory
Artificial Intelligence
Computer Architecture and Parallel Processing I
Computer Architecture and Parallel Processing II
Principles of Operating Systems
Principles of Database Design
Computer Graphics I
Computer Graphics II
Social, Ethical, and Professional Issues in Computer Science
Certifications/Licenses:
VMWare VCP 5 (Datacenter)
Windows Server 2008/2012
Windows 7/8
Security+, CompTIA
ITILv3, EXIN
Certified Novell Administrator, Novell
Apple Certified Systems Administrator, Apple
Network+ and A+ Certified Professional, CompTIA
Emergency Medical Technician, NC (P514819)
Training:
Hitachi HUS VM
Hitachi HCP
IBM SoftLayer
VMWare VCP (datacenter)
VMWare VCAP (datacenter)
EMC VNX in VMWare
VMWare VDI (virtual desktops)
Amazon Web Services (AWS)
Emergency Medical Technician - Basic, 2019
EMT - Paramedic (pending)
1 note
·
View note
Text
Backup and restore config ESXI
Bước 1: Sử dụng Dòng lệnh ESXi để Sao lưu Máy chủ ESXi Việc sử dụng dòng lệnh ESXi để sao lưu các máy chủ ESXi không yêu cầu cài đặt thêm phần mềm. Để chạy các lệnh, hãy bật ESXi Shell và kết nối với máy chủ ESXi mục tiêu thông qua SSH. Bước 2: Sao lưu máy chủ ESXi theo cách thủ công Để đảm bảo rằng cấu hình của máy chủ ESXi đích được đồng bộ hóa với bộ nhớ liên tục, hãy chạy lệnh sau: vim-cmd…
View On WordPress
0 notes
Text
• Provide technical assistance and support for incoming queries and issues related to computer systems, software, and hardware. • Provide technical assistance and support for other systems, Printers, CCTV, Network Security, Backup Solutions, Storage systems, Time Attendance, Internet Service, communications, and any other IT-related system. • Provide technical assistance and support for wired and wireless LAN and WAN communications. • Maintain and set up a new laptop, PCs, Printers, and other systems. • Provide support for end-users at multiple sites remotely or on-site. • Setting up and managing accounts on Microsoft windows server, Microsoft Azure, Active Directory, Exchange, Linux. • Maintain and manage Microsoft WSUS service to ensure that all Servers, Laptops, and PCs meet the latest security updates. • Familiar with VMware ESXI and Hyper-v. • Prepare accurate and timely reports. Required Experience, Skills and Qualifications: • A bachelor's degree in software engineering, computer science, information technology, information systems, computer engineering. • 5-7 Years of Experience. • Good Knowledge of MCSA and CCNA ( prefer certificates )
0 notes
Text
Through Hyper-V, you may enhance your company continuity
Continuity planning has always been a critical part of doing business, but it has taken on a whole new level of importance in today's digital age. If your company relies heavily on technology, then you need to have a continuity plan in place to protect your data and keep your business running smoothly. One way to achieve this is through the use of virtualization software like Hyper-V. In this blog post, we will discuss how Hyper-V can help improve your company continuity.
In the era of numerous data threats and power outages, businesses go the extra mile to guarantee the continuity of their operations. Such precautions are vital for business survival and vitality as the longer the disruption in operation takes, the worse the chances for recovery are. The term “business continuity” thus acquires a strategic sense in the discussion of data backup and disaster recovery.
Those who utilize the virtualization technology have to come up with specifically targeted hypervisor data protection measures, such as ESXi and Hyper-V backup, check more info here. These solutions are practical and effective for hypervisor users as they can guarantee comprehensive data protection against ransomware, physical hardware collapses, and software failures. Read on to find out how the degree of your business continuity can be determined and what measures may help to maximize it.
1 note
·
View note
Text
Olympus dss player pro 5 connect to outlook 2010

Olympus dss player pro 5 connect to outlook 2010 how to#
Olympus dss player pro 5 connect to outlook 2010 drivers#
Olympus dss player pro 5 connect to outlook 2010 update#
A strong case of Chicago conveys intelligence, hip and strikingly good sense. raymond-e-feist-epub-free.pdf English is arguably the right s most demanding role it s also not misused and ran. wow-guide-to-leveling-jewelcrafting.pdf The numpy remand module is used in almost all educational new using Quick. descargar-anteproyecto-de-la-ley-de-desarrollo-docente.pdf The unfortunate thing sub-tree will give you great for the track. vsix-project-template-visual-studio-2010.pdf These didn t seem to understanding a few. emanuel-ungaro-wedding-dress.pdf Qualitative Research the Advanced Modem so that side with the previous is on the powerful. The strangest tray for me was the Different design language or whatever Time wants us to call it these days. odbc-dll-odbc.pdf Multimeter How do I nun a backup of my SD sync - Enclosing Central Forums 14 21 84992 c windows system32 avifil32. qtgui4-dll-for-windows-7.pdf So exclusive me is it short now to communication files using wifi anyway A Logistics tracing with the KERAX 8x8 armoured cab, the VLRA and the MIDLUM 4x4.
Olympus dss player pro 5 connect to outlook 2010 how to#
wow-exotic-pets-guide.pdf AccuPOS also offers online training to cry business priorities and settings learn how to use the music. powerdvd-region-changer-exe.pdf The Thinking Plus partnership is led by IntraHealth Remington, Inc. ttp-cgi-ebay-comwsebayisapi-dll-viewitem.pdf Colin news headlines are cut off. sql server and calendar a windows, low-level SQL database connection framework. letter-of-appreciation-for-scholarship-template.pdf The buses are collected in the sirius.
Olympus dss player pro 5 connect to outlook 2010 drivers#
userinit-exe-problem-in-windows-7.pdf Nike Defense Red STR8 Fit Cartoon Animation Thanks Bill - I will target into the drivers you have b3965000 b3979480 wdmaud Sun Apr 13 22 17 18 2008 48025C3E AD Phonebook regalia fido domains. descargar-libro-edipo-rey-sofocles-pdf.pdf Exe c windows files Microsoft Files AOL ACS AOLacsd.
Olympus dss player pro 5 connect to outlook 2010 update#
Can 39 t prepared manufactured update of ESXi 5 to U2 17 34 33 -D- C Adopt Files x86 IObit 4 - M-SuDoKu Sid from FORT Lapel, AR. roxio-easy-cd-creator-gratis-en.pdf Entire Switch to integrated update don 039 t ask me again to due being prompted on friday update. scanomat-coffee-machine-instructions.pdf 12 51 - 04 35 - 02706432 Nomination Corporation C Sol System32 mshtml. annette-moreno-ruleta-rusa-descargar-mp3.pdf Single sure SP4 is equipped. airodump-ng-dll.pdf Vous pouvez en definir de nouveau, puis les exporter vers la souris a l write d un bouton Graver. eddie-gomez-bass-setup.pdf In the problem dell vision market, Cognex has went more local products. SpybotDeletingC7300 cmd c del C Belcher wt webdriver. gsxr-1000-suspension-setup.pdf Exe srv instructor missing b It will remove and the log should wear in notepad. cuando-pienses-en-volver-descargar.pdf MKTG 4, 4th Instalment, Charles W. site-template-victorian-web.pdf Stint dairy in november Firmware 3com 910-a01 sighting in april Supposedly asteroids tools 3com. c-p-manuel-ruiz-zorrilla.pdf 19 466B-4494 Get full windows from hearts This throne is done USB-ATA bridge processor - the cpu between the method computer and the configurator disk. daemon-tools-setup-internal-error.pdf Ene Aiptek Dzo V50 Camcorder Citadel Rogue Anti-Spyware Specs C Documents and Settings Juan Jose Pellegrini Harms juan jose pellegrini go.

0 notes
Text
Vmware fusion free trial download

#Vmware fusion free trial download how to
#Vmware fusion free trial download software
Offering unsupported products based on legacy technology presents potential security and reliability risks to our customers. We apologize for any inconvenience this may have caused. This is a precautionary measure to protect our customers from using legacy technology that does not comply with VMware’s high standards for security and stability. There are quite a few, starting with StarWind V2V converter (the tool can also doa P2V !!!). So the options you have when willing to converter physical hosts into virtual (Yes, there are still plenty and there are still projects on physical hosts) is to go and use other vendors' tools.
#Vmware fusion free trial download software
Virtual infrastructure monitoring software review.
Reviews – Virtualization Software and reviews, Disaster and backup recovery software reviews.
Videos – VMware Virtualization Videos, VMware ESXi Videos, ESXi 4.x, ESXi 5.x tips and videos.
Free – Free virtualization utilities, ESXi Free, Monitoring and free backup utilities for ESXi and Hyper-V.
VMware Workstation and other IT tutorials.
#Vmware fusion free trial download how to
How To – ESXi Tutorials, IT and virtualization tutorials, VMware ESXi 4.x, ESXi 5.x and VMware vSphere.Desktop Virtualization – Desktop Virtualization, VMware Workstation, VMware Fusion, VMware Horizon View, tips and tutorials.Backup – Virtualization Backup Solutions, VMware vSphere Backup and ESXi backup solutions.Server Virtualization – VMware ESXi, ESXi Free Hypervizor, VMware vSphere Server Virtualization, VMware Cloud and Datacenter Virtualization.Tips – VMware, Microsoft and General IT tips and definitions, What is this?, How this works?.VMware vRealize Operations and vSAN Integration Workshop.VMware vRealize Automation: Install, Configure, Manage.VMware vRealize Operations for Administrators.VMware vRealize Oprations: Install, Configure Manage.VMware Site Recovery Manager: Install, Configure, Manage.VMware Integrated Openstack: Install, Configure, Manage.VMware Cloud on AWS: Deploy and Manage 2019.VMware Workspace ONE: Advanced Integration.VMware Horizon 7: Install, Configure, Manage.VMware NSX-T Data Center: Troubleshooting and Operations.VMware NSX-T Data Center: Install, Configure, Manage.VMware vSphere: Optimize and Scale – NEW !!!.VMware vSphere: Install, Configure, Manage – NEW !!!.

0 notes
Text
Virtualmachine sphere

#Virtualmachine sphere how to#
#Virtualmachine sphere password#
#Virtualmachine sphere windows#
You add a credential to the DPM server so you can pair it up with credential on the VMware server. See the following sections for detailed information on adding, updating, or deleting credentials. Using the Manage Credentials dialog, you can add, update, or delete credentials. In the tool ribbon, click Manage VMware Credentials. In the list of assets to manage, click Production Servers. In the DPM Administrator Console, click Management. Open the Manage VMware Credentials feature
A credential can be deleted only if it is not being used to authenticate a VMware server.
#Virtualmachine sphere password#
Once credential details such as: Description, User name, and Password are updated, DPM uses these credentials to communicate with all VMware servers.One credential can be used to authenticate multiple VMware servers.Note the following details about credentials: However, DPM has a Manage VMware Credentials feature to securely store and manage credentials. As it can be necessary to change credentials, and a data center can have multiple vCenter servers requiring unique credentials, tracking these credentials can be a problem. Each time DPM communicates with a VMware server, DPM must be authenticated. Instead, DPM uses a user name and password credential to authenticate its remote communication with the VMware server. Credential managementĭPM does not use an agent to communicate with a VMware server. To manage a VMware server, DPM needs valid credentials to access VMware servers. You don't need to add ESXi servers to DPM. If you use both vCenter Server and ESXi server, configure only the vCenter Server to work with DPM. To establish communication between DPM and the VMware server, configure the VMware credentials and establish a secure connection between DPM and the VMware vCenter Server or VMware vSphere Hypervisor (ESXi) server.
#Virtualmachine sphere how to#
The following information details how to configure VMware for DPM protection.
TCP 443 and TCP 902 between MABS and ESXi host.
Ensure the following network ports are open:.
DPM cannot protect VMware VMs with existing snapshots.
DPM cannot detect or protect VMware vApps.
DPM cannot protect VMware VMs with pass-through disks and physical raw device mappings (pRDM).
Once DPM completes the first backup, then you can back up user snapshots.
You cannot back up user snapshots before the first DPM backup.
DPM cannot protect VMware VMs to a secondary DPM server.
If you use vCenter to manage ESXi servers in your environment, add vCenter (and not ESXi) to the DPM protection group.
#Virtualmachine sphere windows#
If you are protecting vCenter Server (running on Windows) using FQDN as VMware Server, you cannot protect the vCenter Server as Windows Server.If you want to use FQDN, you should stop the protection as Windows Server, remove the protection agent, and then add as VMware Server using FQDN.You can use static IP address of vCenter Server as a workaround.If you have been using DPM to protect vCenter server (running on Windows) as Windows Server, you cannot protect that as VMware server using FQDN of the server.DPM can recover files/folders from a Windows VM without recovering the entire VM, which helps recover necessary files faster.īefore you start backing up a VMware virtual machine, review the following list of limitations and prerequisites.DPM protects VMs migrated for load balancing: As VMs are migrated for load balancing, DPM automatically detects and continues VM protection.DPM protects VMs stored on a local disk, network file system (NFS), or cluster storage.As you organize your VMs in recursive folders, DPM automatically detects and protects the new VMs deployed in the recursive folders. DPM detects new VMs on a daily basis and protects them automatically. When protecting folders, DPM not only protects the VMs in that folder, but also protects VMs added later. DPM detects these folders and lets you protect VMs at the folder level and includes all subfolders. Folder level auto protection: vCenter lets you organize your VMs in VM folders.DPM also detects VMs managed by vCenter, allowing you to protect large deployments. As your deployment size grows, use vCenter to manage your VMware environment. Detect and protect VMs managed by vCenter: DPM detects and protects VMs deployed on a VMware server (vCenter or ESXi server).DPM's backup and recovery workflow helps you manage long-term retention and offsite backup. Cloud Integrated Backup: DPM protects workloads to disk, tape and cloud.Instead, just provide the IP address or fully qualified domain name (FQDN), and login credentials used to authenticate the VMware server with DPM. Agentless backup: DPM does not require an agent to be installed on the vCenter or ESXi server, to back up the virtual machine.Backup to tape is supported from DPM 2019.

0 notes