#bitcoin recovery software
Explore tagged Tumblr posts
Text
legitimate crypto recovery companies
The world of cryptocurrency, the unfortunate reality is that theft and scams are all too common. When someone falls victim to a crypto scam or has their digital assets stolen, they may feel like there is no hope of ever recovering their funds. However, there are legitimate crypto recovery services available to help individuals in these situations, and Digital Va0lt is a trusted and reputable option.
Crypto recovery services are offered by companies and experts who specialize in helping individuals recover their stolen or lost cryptocurrency. These legitimate crypto recovery companies, like Digital Va0lt, have the knowledge and expertise to navigate the complex world of blockchain technology and track down stolen funds.
Telegram: Digital Vault ( https://t.me/Digitalva0lt )
WhatsApp: https://w.me/+12568235121
So, what exactly is crypto recovery?
Crypto recovery is the process of recovering stolen or lost cryptocurrency. This can involve working with a crypto recovery lawyer, using a crypto recovery service like Digital Va0lt, or enlisting the help of a crypto recovery agency.
Crypto recovery experts, like those at Digital Va0lt, understand the intricacies of blockchain technology and can help individuals navigate the process of recovering their stolen funds. They can assist with recovering a crypto recovery phrase, which is a unique code that allows access to a cryptocurrency wallet.
Bitcoin recovery services are also available for individuals who have had their bitcoin stolen by scammers. Digitale Va0lt offers bitcoin recovery services that can help individuals recover their bitcoin through various methods, such as using a bitcoin recovery tool or recovering a bitcoin recovery seed.
If you have lost bitcoin or had it stolen, it is crucial to act quickly and seek out a legitimate bitcoin recovery service like Digitale Va0lt. Their experts can help you navigate the process of recovering your stolen funds and provide you with the best chance of success.
Telegram: Digital Vault ( https://t.me/Digitalva0lt )
WhatsApp: https://w.me/+12568235121
Digitale Vault’s team of experienced crypto recovery experts has a proven track record of helping individuals recover their stolen cryptocurrency. With their comprehensive range of services, including blockchain recovery, coinbase recovery, bitcoin core recovery, electrum, metamask recovery, and crypto seed recovery, Digitale Va0lt is the ideal partner for anyone looking to recover their stolen digital assets.
When you hire a crypto recovery service like Digitale Va0lt, you can expect:
Telegram: Digital Vault ( https://t.me/Digitalva0lt )
WhatsApp: https://w.me/+12568235121
A team of experienced crypto recovery experts who will work tirelessly to recover your lost funds
A comprehensive range of services to tackle even the most complex cases
Advanced technology and strategies to trace and recover stolen funds
Legal assistance from a crypto recovery lawyer, if necessary
A proven track record of success in recovering lost funds
Don’t Wait – Hire Digitale Va0lt Crypto Recovery Service Today
By hiring a reputable crypto recovery service like Digitale Va0lt, you can rest assured that your case will be handled professionally and efficiently, giving you the best chance of recovering your valuable digital assets.
Take Action: Don’t let stolen cryptocurrency hold you back. Contact Digitale Vault today to start the process of recovering your stolen funds. Their team of experts is ready to help you navigate the complex world of crypto recovery and get back on track.
Telegram: Digital Vault ( https://t.me/Digitalva0lt )
WhatsApp: https://w.me/+12568235121
#legitimate crypto recovery companies#what is crypto recovery#best crypto recovery service#crypto recovery lawyer#crypto recovery service#crypto recovery agency#crypto recovery experts#legitimate crypto recovery companies near me#stolen crypto recovery services#crypto recovery phrase#crypto recovery companies#stolen crypto recovery#are there any legitimate crypto recovery services#crypto recovery hacker#hire a crypto recovery service#how to hire a genuine crypto recovery service#how to find a legitimate crypto recovery#bitcoin recovery services#bitcoin recovery from scammer#bitcoin recovery phrase generator#best bitcoin recovery expert to recover scammed bitcoin#lost bitcoin recovery#legit bitcoin recovery company#bitcoin recovery software#how to hire a bitcoin recovery expert#best bitcoin recovery expert#scammed bitcoin recovery#private key finder for bitcoin address#bitcoin private key finder software
3 notes
·
View notes
Text
legitimate crypto recovery companies
The world of cryptocurrency, the unfortunate reality is that theft and scams are all too common. When someone falls victim to a crypto scam or has their digital assets stolen, they may feel like there is no hope of ever recovering their funds. However, there are legitimate crypto recovery services available to help individuals in these situations, and Digital Va0lt is a trusted and reputable option.
Crypto recovery services are offered by companies and experts who specialize in helping individuals recover their stolen or lost cryptocurrency. These legitimate crypto recovery companies, like Digital Va0lt, have the knowledge and expertise to navigate the complex world of blockchain technology and track down stolen funds.
Telegram: Digital Vault ( https://t.me/Digitalva0lt )
WhatsApp: https://w.me/+12568235121
So, what exactly is crypto recovery?
Crypto recovery is the process of recovering stolen or lost cryptocurrency. This can involve working with a crypto recovery lawyer, using a crypto recovery service like Digital Va0lt, or enlisting the help of a crypto recovery agency.
Crypto recovery experts, like those at Digital Va0lt, understand the intricacies of blockchain technology and can help individuals navigate the process of recovering their stolen funds. They can assist with recovering a crypto recovery phrase, which is a unique code that allows access to a cryptocurrency wallet.
Bitcoin recovery services are also available for individuals who have had their bitcoin stolen by scammers. Digitale Va0lt offers bitcoin recovery services that can help individuals recover their bitcoin through various methods, such as using a bitcoin recovery tool or recovering a bitcoin recovery seed.
If you have lost bitcoin or had it stolen, it is crucial to act quickly and seek out a legitimate bitcoin recovery service like Digitale Va0lt. Their experts can help you navigate the process of recovering your stolen funds and provide you with the best chance of success.
Telegram: Digital Vault ( https://t.me/Digitalva0lt )
WhatsApp: https://w.me/+12568235121
Digitale Vault’s team of experienced crypto recovery experts has a proven track record of helping individuals recover their stolen cryptocurrency. With their comprehensive range of services, including blockchain recovery, coinbase recovery, bitcoin core recovery, electrum, metamask recovery, and crypto seed recovery, Digitale Va0lt is the ideal partner for anyone looking to recover their stolen digital assets.
When you hire a crypto recovery service like Digitale Va0lt, you can expect:
Telegram: Digital Vault ( https://t.me/Digitalva0lt )
WhatsApp: https://w.me/+12568235121
A team of experienced crypto recovery experts who will work tirelessly to recover your lost funds
A comprehensive range of services to tackle even the most complex cases
Advanced technology and strategies to trace and recover stolen funds
Legal assistance from a crypto recovery lawyer, if necessary
A proven track record of success in recovering lost funds
Don’t Wait – Hire Digitale Va0lt Crypto Recovery Service Today
By hiring a reputable crypto recovery service like Digitale Va0lt, you can rest assured that your case will be handled professionally and efficiently, giving you the best chance of recovering your valuable digital assets.
Take Action: Don’t let stolen cryptocurrency hold you back. Contact Digitale Vault today to start the process of recovering your stolen funds. Their team of experts is ready to help you navigate the complex world of crypto recovery and get back on track.
Telegram: Digital Vault ( https://t.me/Digitalva0lt )
WhatsApp: https://w.me/+12568235121
#legitimate crypto recovery companies#what is crypto recovery#best crypto recovery service#crypto recovery lawyer#crypto recovery service#crypto recovery agency#crypto recovery experts#legitimate crypto recovery companies near me#stolen crypto recovery services#crypto recovery phrase#crypto recovery companies#stolen crypto recovery#are there any legitimate crypto recovery services#crypto recovery hacker#hire a crypto recovery service#how to hire a genuine crypto recovery service#how to find a legitimate crypto recovery#bitcoin recovery services#bitcoin recovery from scammer#bitcoin recovery phrase generator#best bitcoin recovery expert to recover scammed bitcoin#lost bitcoin recovery#legit bitcoin recovery company#bitcoin recovery software#how to hire a bitcoin recovery expert#best bitcoin recovery expert#scammed bitcoin recovery#private key finder for bitcoin address#bitcoin private key finder software
3 notes
·
View notes
Text
legitimate crypto recovery companies
The world of cryptocurrency, the unfortunate reality is that theft and scams are all too common. When someone falls victim to a crypto scam or has their digital assets stolen, they may feel like there is no hope of ever recovering their funds. However, there are legitimate crypto recovery services available to help individuals in these situations, and Digital Va0lt is a trusted and reputable option.
Crypto recovery services are offered by companies and experts who specialize in helping individuals recover their stolen or lost cryptocurrency. These legitimate crypto recovery companies, like Digital Va0lt, have the knowledge and expertise to navigate the complex world of blockchain technology and track down stolen funds.
Telegram: Digital Vault ( https://t.me/Digitalva0lt )
WhatsApp: https://w.me/+12568235121
So, what exactly is crypto recovery?
Crypto recovery is the process of recovering stolen or lost cryptocurrency. This can involve working with a crypto recovery lawyer, using a crypto recovery service like Digital Va0lt, or enlisting the help of a crypto recovery agency.
Crypto recovery experts, like those at Digital Va0lt, understand the intricacies of blockchain technology and can help individuals navigate the process of recovering their stolen funds. They can assist with recovering a crypto recovery phrase, which is a unique code that allows access to a cryptocurrency wallet.
Bitcoin recovery services are also available for individuals who have had their bitcoin stolen by scammers. Digitale Va0lt offers bitcoin recovery services that can help individuals recover their bitcoin through various methods, such as using a bitcoin recovery tool or recovering a bitcoin recovery seed.
If you have lost bitcoin or had it stolen, it is crucial to act quickly and seek out a legitimate bitcoin recovery service like Digitale Va0lt. Their experts can help you navigate the process of recovering your stolen funds and provide you with the best chance of success.
Telegram: Digital Vault ( https://t.me/Digitalva0lt )
WhatsApp: https://w.me/+12568235121
Digitale Vault’s team of experienced crypto recovery experts has a proven track record of helping individuals recover their stolen cryptocurrency. With their comprehensive range of services, including blockchain recovery, coinbase recovery, bitcoin core recovery, electrum, metamask recovery, and crypto seed recovery, Digitale Va0lt is the ideal partner for anyone looking to recover their stolen digital assets.
When you hire a crypto recovery service like Digitale Va0lt, you can expect:
Telegram: Digital Vault ( https://t.me/Digitalva0lt )
WhatsApp: https://w.me/+12568235121
A team of experienced crypto recovery experts who will work tirelessly to recover your lost funds
A comprehensive range of services to tackle even the most complex cases
Advanced technology and strategies to trace and recover stolen funds
Legal assistance from a crypto recovery lawyer, if necessary
A proven track record of success in recovering lost funds
Don’t Wait – Hire Digitale Va0lt Crypto Recovery Service Today
By hiring a reputable crypto recovery service like Digitale Va0lt, you can rest assured that your case will be handled professionally and efficiently, giving you the best chance of recovering your valuable digital assets.
Take Action: Don’t let stolen cryptocurrency hold you back. Contact Digitale Vault today to start the process of recovering your stolen funds. Their team of experts is ready to help you navigate the complex world of crypto recovery and get back on track.
Telegram: Digital Vault ( https://t.me/Digitalva0lt )
WhatsApp: https://w.me/+12568235121
#legitimate crypto recovery companies#what is crypto recovery#best crypto recovery service#crypto recovery lawyer#crypto recovery service#crypto recovery agency#crypto recovery experts#legitimate crypto recovery companies near me#stolen crypto recovery services#crypto recovery phrase#crypto recovery companies#stolen crypto recovery#are there any legitimate crypto recovery services#crypto recovery hacker#hire a crypto recovery service#how to hire a genuine crypto recovery service#how to find a legitimate crypto recovery#bitcoin recovery services#bitcoin recovery from scammer#bitcoin recovery phrase generator#best bitcoin recovery expert to recover scammed bitcoin#lost bitcoin recovery#legit bitcoin recovery company#bitcoin recovery software#how to hire a bitcoin recovery expert#best bitcoin recovery expert#scammed bitcoin recovery#private key finder for bitcoin address#bitcoin private key finder software
3 notes
·
View notes
Text
legitimate crypto recovery companies
The world of cryptocurrency, the unfortunate reality is that theft and scams are all too common. When someone falls victim to a crypto scam or has their digital assets stolen, they may feel like there is no hope of ever recovering their funds. However, there are legitimate crypto recovery services available to help individuals in these situations, and Digital Va0lt is a trusted and reputable option.
Crypto recovery services are offered by companies and experts who specialize in helping individuals recover their stolen or lost cryptocurrency. These legitimate crypto recovery companies, like Digital Va0lt, have the knowledge and expertise to navigate the complex world of blockchain technology and track down stolen funds.
Telegram: Digital Vault ( https://t.me/Digitalva0lt )
WhatsApp: https://w.me/+12568235121
So, what exactly is crypto recovery?
Crypto recovery is the process of recovering stolen or lost cryptocurrency. This can involve working with a crypto recovery lawyer, using a crypto recovery service like Digital Va0lt, or enlisting the help of a crypto recovery agency.
Crypto recovery experts, like those at Digital Va0lt, understand the intricacies of blockchain technology and can help individuals navigate the process of recovering their stolen funds. They can assist with recovering a crypto recovery phrase, which is a unique code that allows access to a cryptocurrency wallet.
Bitcoin recovery services are also available for individuals who have had their bitcoin stolen by scammers. Digitale Va0lt offers bitcoin recovery services that can help individuals recover their bitcoin through various methods, such as using a bitcoin recovery tool or recovering a bitcoin recovery seed.
If you have lost bitcoin or had it stolen, it is crucial to act quickly and seek out a legitimate bitcoin recovery service like Digitale Va0lt. Their experts can help you navigate the process of recovering your stolen funds and provide you with the best chance of success.
Telegram: Digital Vault ( https://t.me/Digitalva0lt )
WhatsApp: https://w.me/+12568235121
Digitale Vault’s team of experienced crypto recovery experts has a proven track record of helping individuals recover their stolen cryptocurrency. With their comprehensive range of services, including blockchain recovery, coinbase recovery, bitcoin core recovery, electrum, metamask recovery, and crypto seed recovery, Digitale Va0lt is the ideal partner for anyone looking to recover their stolen digital assets.
When you hire a crypto recovery service like Digitale Va0lt, you can expect:
Telegram: Digital Vault ( https://t.me/Digitalva0lt )
WhatsApp: https://w.me/+12568235121
A team of experienced crypto recovery experts who will work tirelessly to recover your lost funds
A comprehensive range of services to tackle even the most complex cases
Advanced technology and strategies to trace and recover stolen funds
Legal assistance from a crypto recovery lawyer, if necessary
A proven track record of success in recovering lost funds
Don’t Wait – Hire Digitale Va0lt Crypto Recovery Service Today
By hiring a reputable crypto recovery service like Digitale Va0lt, you can rest assured that your case will be handled professionally and efficiently, giving you the best chance of recovering your valuable digital assets.
Take Action: Don’t let stolen cryptocurrency hold you back. Contact Digitale Vault today to start the process of recovering your stolen funds. Their team of experts is ready to help you navigate the complex world of crypto recovery and get back on track.
Telegram: Digital Vault ( https://t.me/Digitalva0lt )
WhatsApp: https://w.me/+12568235121
#legitimate crypto recovery companies#what is crypto recovery#best crypto recovery service#crypto recovery lawyer#crypto recovery service#crypto recovery agency#crypto recovery experts#legitimate crypto recovery companies near me#stolen crypto recovery services#crypto recovery phrase#crypto recovery companies#stolen crypto recovery#are there any legitimate crypto recovery services#crypto recovery hacker#hire a crypto recovery service#how to hire a genuine crypto recovery service#how to find a legitimate crypto recovery#bitcoin recovery services#bitcoin recovery from scammer#bitcoin recovery phrase generator#best bitcoin recovery expert to recover scammed bitcoin#lost bitcoin recovery#legit bitcoin recovery company#bitcoin recovery software#how to hire a bitcoin recovery expert#best bitcoin recovery expert#scammed bitcoin recovery#private key finder for bitcoin address#bitcoin private key finder software
3 notes
·
View notes
Text

BITCOIN SCAM RECOVERY SOLUTIONS - ULTIMATE HACKER JERRY
At Ultimate Hacker Jerry, Have a team of legal cryptocurrency investigators. The team is excellent at conducting extensive investigations. They have advanced software that classifies links between cryptocurrency addresses and entities. It assists in finding similar criminals, fiat on and off-ramps, and mixers. They create and document everything on these servers; in the form of intelligence for law enforcement cases. It helps with Bitcoin Recovery. It also assists in cases of ransomware, money laundering, terrorism financing, narcotics trafficking.
UHJ's detailed reports proved to be beneficial for the investigation and always lent a hand with judicial proceedings.
Their experts will help with the witness in the court; when it’s time to prosecute and recover the assets. Ultimate Hacker Jerry acts as a network connecting an exceptionally trained team with the investors who’ve lost their bitcoins and other cryptos along the way.
E-Mail ([email protected]) Call or Whtsp +1(520)282-7151) Visit website: ultimateshackjerry.com
THE HUFFINGTON POST
#BITCOIN SCAM RECOVERY SOLUTIONS - ULTIMATE HACKER JERRY#At Ultimate Hacker Jerry#Have a team of legal cryptocurrency investigators. The team is excellent at conducting extensive investigations. They have advanced softwar#fiat on and off-ramps#and mixers.#They create and document everything on these servers; in the form of intelligence for law enforcement cases. It helps with Bitcoin Recovery#money laundering#terrorism financing#narcotics trafficking.UHJ's detailed reports proved to be beneficial for the investigation and always lent a hand with judicial proceedings#E-Mail ([email protected])#Call or Whtsp +1(520)282-7151)#Visit website: ultimateshackjerry.com#THE HUFFINGTON POST
12 notes
·
View notes
Text
Bitcoin recovery software
In the world of cryptocurrency, security is paramount. One of the most important aspects of safeguarding your digital assets is ensuring that you have a secure and reliable way to access your private keys. Private keys are essentially the keys to your digital wallet, allowing you to access and manage your cryptocurrencies. That’s why it’s essential to have a backup plan in place, and a recovery phrase generator like Bitsonic Private Key Generator (https://digitalevault.com/product/bitsonic-private-key-generator/) can provide you with a secure way to recover your private key in case it is lost or stolen.
https://digitalevault.com/wp-content/uploads/2024/05/2204_BlogHeader_Wallet.png
There are various types of recovery phrase generators available, including bitcoin private key finders, eth private key finders, and general private key generators. But when it comes to reliability and security, Bitsonic Private Key Generator (https://digitalevault.com/product/bitsonic-private-key-generator/) stands out from the rest. These tools are designed to securely generate a unique seed phrase that can be used to restore access to your digital assets. By using Bitsonic Private Key Generator, you can rest assured that your seed phrase is generated with the highest level of security and reliability. For more information contact us on
Telegram;
(http://t.me/Digitalva0lt)
Using a recovery phrase generator like Bitsonic Private Key Generator (https://digitalevault.com/product/bitsonic-private-key-generator/) is a simple and effective way to ensure that you always have a backup plan in case of emergencies. By generating and storing your seed phrase in a secure location, you can rest assured that you will always be able to access your private key, even if you lose or forget it. With Bitsonic Private Key Generator, you can have peace of mind knowing that your digital assets are protected.
It is important to note that while recovery phrase generators can be a valuable tool, it is crucial to choose a reputable and trustworthy provider like Bitsonic Private Key Generator (https://digitalevault.com/product/bitsonic-private-key-generator/). Make sure to do your research and select a generator that has a proven track record of security and reliability. By choosing Bitsonic Private Key Generator, you can be confident that your seed phrase is generated with the highest level of security and reliability. chat with our experts on
Telegram;
(http://t.me/Digitalva0lt)
In conclusion, a recovery phrase generator like Bitsonic Private Key Generator (https://digitalevault.com/product/bitsonic-private-key-generator/) is an essential tool for anyone who wants to ensure the security of their digital assets. By generating a seed phrase and storing it securely, you can have peace of mind knowing that you will always be able to access your private key, no matter what happens. So, take the necessary steps to protect your cryptocurrencies and invest in a reliable recovery phrase generator like Bitsonic Private Key Generator today. Chat with our service providers on
Telegram
(http://t.me/Digitalva0lt)
#btc private key finder#eth private key finder#private key generator#private key finder#crypto recovery services#seed phrase generator#recovery phrase generator#what is bitcoin recovery#what is crypto recovery#bitcoin recovery seed#stolen bitcoin recovery#Bitcoin recovery from scammer#crypto recovery software#crypto recovery lawyer#crypto recovery expert
1 note
·
View note
Text
North Korean hackers have stolen the equivalent of billions of dollars in recent years and the nation is seeking to amass even greater wealth through illicit means, experts told DW.
Hackers belonging to the Lazarus Group — a notorious North Korean crypto theft ring — stole a record $1.5 billion (some €1.37 billion) in digital tokens from Dubai-based cryptocurrency exchange ByBit in late February. The company said the hackers had accessed its digital wallet for Ethereum, the second-largest electronic currency after Bitcoin.
Binance News, a new platform operated by cryptocurrency exchange firm Binance, reported last month that North Korea now has some 13,562 Bitcoins, the equivalent of $1.14 billion. Bitcoin is the world's oldest and best known cryptocurrency, often compared with gold due to its alleged resistance to inflation. Only the US and Great Britain have greater reserves of the currency, Binance News said, citing crypto data provider Arkham Intelligence.
"Let's not mince words — [North Korea] achieved this through theft," Aditya Das, an analyst at cryptocurrency research firm Brave New Coin in Auckland, New Zealand, told DW.
"Global policing agencies like the FBI have publicly warned that North Korean state-sponsored hackers are behind numerous attacks on cryptocurrency platforms," he added.
Hackers use social engineering against crypto firms
Despite those warnings, however, crypto firms are still being robbed and North Korean hackers are becoming increasingly sophisticated, the analyst said.
"North Korea employs a wide range of cyberattack techniques, but they've become especially known for their skill in social engineering," said Das.
"Many of their operations involve infiltrating employee hardware, then using that access to breach internal systems or lay traps from the inside."
The hacker's primary targets are crypto startups, exchanges and decentralized finance (DeFi) platforms due to their "often under-developed security protocols," he said.
Recovery of funds 'extremely rare'
Elite North Korean hackers tend to take their time when infiltrating a legitimate global organization, often by impersonating venture capitalists, recruiters or remote IT workers to build up trust and breach firms' defenses.
"One group, Sapphire Sleet, lures victims into downloading malware disguised as job applications, meeting tools or diagnostic software — essentially turning victims into their own attack vectors," Das said.
Once crypto has been stolen, Das says recovery is "extremely rare." Cryptocurrency systems are designed to make transactions irreversible and striking back against North Korean operatives "is not a viable option because these are nation-state actors with top-tier cyber defenses."
Kim Jong Un's regime 'saved' by cryptocurrency theft
Park Jung-won, a professor of law at Dankook University, said North Korea previously relied on risky transactions — such as smuggling narcotics and counterfeit goods or supplying military instructors to African nations — to earn illicit funds.
The legal expert says the advent of cryptocurrency "has been a huge opportunity" for dictator Kim Jong Un.
"It is probably fair to say that given the way the world was cracking down on Pyongyang's smuggling efforts, crypto has saved the regime," Park told DW. "Without it, they would have been completely without funds. They know that and they have invested heavily in training the best hackers and getting them up to a very high level of skill."
"The money that they are stealing is going straight to the government and the assumption is that it is being spent on weapons and greater military technology as well as the Kim family," according to Park.
North Korea immune to international pressure
Park does not believe that outside pressure would force North Korea to end hacking attacks.
"For Kim, the survival of his dynasty is the most important priority," the law professor said.
"They have become accustomed to this source of revenue, even if it is illegal, and they will not change," he added. "There is no reason for them to suddenly start abiding by international law and there is no way to apply more pressure."
Das agrees there are few tools available to influence North Korea. He says companies need to do everything in their power to avoid becoming the next victim.
"Best practices like secure-by-design smart contracts, constant internal verification and social engineering awareness are essential if the industry wants to stay ahead," he said.
Crypto firms need universal security standards
There's growing momentum for sector-wide information sharing which would help crypto firms detect North Korean tactics and avert attacks, but Das warns that crypto remains "fragmented" because there is no universal security standard. Also, North Korean hackers are good at turning security tools against their users, according to the analyst.
"In the Bybit case, the attackers exploited Safe, a multi-signature wallet system meant to enhance security. Ironically, this added security layer became the very exploit they used," he said.
And in practice, Das added, "some firms still treat security as an afterthought."
"From my experience, teams often prioritize shipping fast over building secure systems and until that changes, the space will remain vulnerable," Das said.
#nunyas news#have to wonder what would happen#if all of a sudden a bunch of countries#started selling their crypto off#would the market tank or no
8 notes
·
View notes
Text
Crypto Theft Nightmare: How Astraweb Recovered $150,000 Lost to Hackers

When David Robinson., a 58-year-old retired software consultant from Denver, Colorado, transferred his entire retirement savings $150,000 into a cryptocurrency portfolio, he believed he was securing his financial future. Instead, he walked into a digital minefield. In a single night, everything he had worked for was stolen by anonymous hackers. It was the kind of nightmare many investors fear but few believe could happen to them.
“I thought I had done everything right,” David said. “I had cold storage, I used two-factor authentication, and I only traded on what were considered reputable exchanges. But somehow, someone got in.”
The breach wasn’t just technical it was deeply personal. Decades of disciplined saving, investing, and planning had been wiped away with a few keystrokes. And in the opaque world of blockchain anonymity, there seemed to be little recourse.
A New Kind of Crime, an Old System Ill-Equipped David’s case is not isolated. According to recent figures from the Federal Trade Commission, over $1.4 billion in cryptocurrency was reported stolen in the U.S. last year alone. What’s more chilling is the vast majority of these crimes go unresolved. Law enforcement agencies, though increasingly aware of crypto fraud, are often hampered by jurisdictional boundaries, limited training in blockchain forensics, and the sheer complexity of digital asset recovery.
David contacted local police, the FBI’s Internet Crime Complaint Center (IC3), and even attempted to escalate the issue through the exchange’s customer service channels. All efforts ended in frustration. “Everyone was sympathetic,” he recalled, “but no one could help. They didn’t have the tools. I felt like I was shouting into the void.”
That void, however, was about to echo back.

Astraweb: The Digital Recovery Force Behind the ScenesWith few options left, David turned to a name he had seen mentioned in niche online forums and cybersecurity discussion threads: Astraweb. A private digital asset recovery agency, Astraweb has earned a quiet but powerful reputation for solving complex crypto theft cases especially those deemed too advanced or impossible by other channels.David sent a tentative email to [email protected], not expecting much. Within 12 hours, he received a reply. “From the first message,” he says, “I could tell they were different. They didn’t just want transaction IDs. They asked smart, precise questions. They were calm, confident, and, most importantly, they listened.”Astraweb’s team began work immediately.Digital Surveillance Meets Blockchain ForensicsWhile the average consumer may understand Bitcoin or Ethereum as abstract tokens, Astraweb views the blockchain as a massive, living map of transactions. Every move a stolen coin makes leaves a trace however faint.

Using a proprietary method called wallet triangulation, Astraweb identified the exit points the thief had used to shuffle and launder the funds. These techniques involve advanced blockchain analytics, surveillance of darknet exchange patterns, and metadata correlation to monitor crypto mixers and swap protocols often used to obscure fund movements.
According to sources familiar with Astraweb’s methods, their teams blend cybersecurity expertise with behavioral analytics to predict a thief’s next move. “It’s part code, part cat-and-mouse,” one expert commented. “But when you understand the flow of crypto like a language, the signals start to emerge.”
In David’s case, Astraweb tracked the funds as they moved through a network of wallets, some automated, others human-controlled, eventually leading to a decentralized exchange platform that allowed partial recovery. In collaboration with international legal intermediaries and with careful timing, Astraweb executed a legal intercept of the funds as they entered a liquidity pool.
The Outcome: Full Recovery, Real Relief Just 48 hours after their initial contact, Astraweb notified David that the entire $150,000 had been recovered and would be transferred back to his newly secured wallet.

Reach out to them Now If you have Related Issues Like This:
6 notes
·
View notes
Text
Trezor.io/Start - A Secure Gateway to Crypto Safety
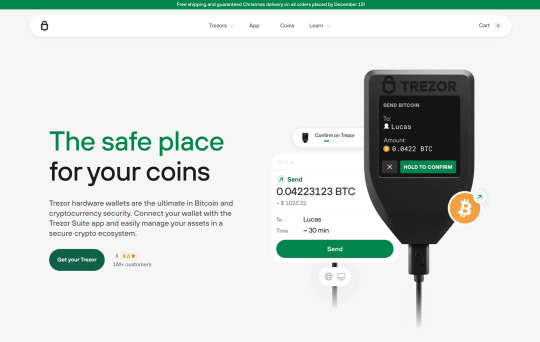
In the ever-evolving world of cryptocurrency, securing your digital assets is more crucial than ever. With increasing cyber threats and phishing attacks, having a reliable hardware wallet is a must. Trezor, one of the most trusted names in crypto security, provides a robust and user-friendly hardware wallet to safeguard your investments. If you're looking to set up your Trezor device, Trezor.io/Start is the official guide to help you get started.
Why Choose Trezor?
Trezor hardware wallets offer an unparalleled level of security for your cryptocurrencies. Here are some key advantages:
Top-Tier Security – Your private keys never leave the device, making it nearly impossible for hackers to access your funds.
User-Friendly Interface – Trezor provides an intuitive experience, making it ideal for beginners and seasoned traders alike.
Multi-Currency Support – Store Bitcoin, Ethereum, and thousands of other cryptocurrencies in a single device.
Open-Source Technology – The transparency of Trezor’s software ensures that it is regularly reviewed and improved by the crypto community.
Backup & Recovery – With the 12 to 24-word recovery seed, you can easily recover your funds if your device is lost or stolen.
How to Set Up Your Trezor Wallet (Trezor.io/Start Guide)
Getting started with Trezor is straightforward. Follow these steps:
Unbox Your Trezor – Ensure that your device package is sealed and untampered.
Visit Trezor.io/Start – Open your web browser and go to Trezor.io/Start.
Connect Your Device – Plug your Trezor device into your computer using the provided USB cable.
Install Trezor Suite – Download and install the official Trezor Suite application for secure transactions and management.
Set Up a PIN & Recovery Seed – Follow the on-screen instructions to create a secure PIN and write down your 12-24 word recovery phrase.
Add Your Cryptocurrencies – Once your wallet is set up, you can start adding supported cryptocurrencies.
Final Thoughts
Securing your digital assets should be your top priority, and Trezor.io Start makes it easy to set up and manage your hardware wallet. With robust security features, user-friendly design, and extensive crypto support, Trezor remains a top choice for crypto enthusiasts worldwide.
2 notes
·
View notes
Text
Bitcoin recovery software
Bitcoin recovery software is a must-have tool for individuals who have lost access to their cryptocurrency wallets. If you have lost your private key or forgotten your recovery phrase, having the right software can help you recover your valuable assets. We recommend using Bitsonic Crypto Recovery Software (https://digitalevault.com/product/bitsonic-crypto-recovery-software/) for all your bitcoin recovery needs.
CLICK HERE To VISIT: (https://digitalevault.com/)
or make enquiries through
TELEGRAM: https://t.me/Digitalva0lt
One of the key features of Bitsonic Crypto Recovery Software is the private key finder. This tool allows users to search for their lost private keys using advanced algorithms and encryption techniques. With the private key finder, you can quickly and easily locate your lost private keys and regain access to your bitcoin wallets.
In addition to the private key finder, Bitsonic Crypto Recovery Software also includes an eth private key finder. This tool is specifically designed to help users recover their Ethereum private keys, which are used to access and manage their ether holdings. By using the eth private key finder, you can quickly and easily locate your lost private keys and regain access to your Ethereum wallets.
Another important feature of Bitsonic Crypto Recovery Software is the private key generator. This tool allows users to create new private keys for their wallets, providing them with a secure and reliable way to access and manage their cryptocurrency holdings. By generating a new private key, you can effectively regain control over your funds and protect your assets from potential security threats.
Furthermore, Bitsonic Crypto Recovery Software may also include a seed phrase generator or recovery phrase generator. These tools allow users to create new seed phrases or recovery phrases for their wallets, providing them with an additional layer of security and protection. By generating a new seed phrase or recovery phrase, you can ensure that your funds are safe and secure, even in the event of a lost or compromised wallet.
In conclusion, Bitsonic Crypto Recovery Software is an essential tool for individuals who have lost access to their cryptocurrency wallets. With features such as the private key finder, eth private key finder, private key generator, seed phrase generator, and recovery phrase generator, users can effectively recover their lost assets and regain control over their funds. By utilizing these tools, you can ensure the security and protection of your valuable cryptocurrency holdings. We highly recommend using Bitsonic Crypto Recovery Software
(https://digitalevault.com/product/bitsonic-crypto-recovery-software/) for all your bitcoin recovery needs.
#bitcoin recovery from scammer#bitcoin recovery tool#bitcoin recovery seed#bitcoin recovery service#crypto recovery#recover scammed crypto
6 notes
·
View notes
Text
Bitcoin recovery Software
In the world of cryptocurrency, security is paramount. One of the most important aspects of safeguarding your digital assets is ensuring that you have a secure and reliable way to access your private keys. Private keys are essentially the keys to your digital wallet, allowing you to access and manage your cryptocurrencies. That’s why it’s essential to have a backup plan in place, and a recovery phrase generator like Bitsonic Private Key Generator (https://digitalevault.com/product/bitsonic-private-key-generator/) can provide you with a secure way to recover your private key in case it is lost or stolen.

There are various types of recovery phrase generators available, including bitcoin private key finders, eth private key finders, and general private key generators. But when it comes to reliability and security, Bitsonic Private Key Generator (https://digitalevault.com/product/bitsonic-private-key-generator/) stands out from the rest. These tools are designed to securely generate a unique seed phrase that can be used to restore access to your digital assets. By using Bitsonic Private Key Generator, you can rest assured that your seed phrase is generated with the highest level of security and reliability. For more information, chat us on
Telegram:https://t.me/Digitalva0lt
Using a recovery phrase generator like Bitsonic Private Key Generator (https://digitalevault.com/product/bitsonic-private-key-generator/) is a simple and effective way to ensure that you always have a backup plan in case of emergencies. By generating and storing your seed phrase in a secure location, you can rest assured that you will always be able to access your private key, even if you lose or forget it. With Bitsonic Private Key Generator, you can have peace of mind knowing that your digital assets are protected.
It is important to note that while recovery phrase generators can be a valuable tool, it is crucial to choose a reputable and trustworthy provider like Bitsonic Private Key Generator (https://digitalevault.com/product/bitsonic-private-key-generator/). Make sure to do your research and select a generator that has a proven track record of security and reliability. By choosing Bitsonic Private Key Generator, you can be confident that your seed phrase is generated with the highest level of security and reliability. for more information chat us on
Telegram:https://t.me/Digitalva0lt
In conclusion, a recovery phrase generator like Bitsonic Private Key Generator (https://digitalevault.com/product/bitsonic-private-key-generator/) is an essential tool for anyone who wants to ensure the security of their digital assets. By generating a seed phrase and storing it securely, you can have peace of mind knowing that you will always be able to access your private key, no matter what happens. So, take the necessary steps to protect your cryptocurrencies and invest in a reliable recovery phrase generator like Bitsonic Private Key Generator today. Contact us on
Telegram:https://t.me/Digitalva0lt
#private key finder#eth private key finder#Btc private key finder#private key generator#seed phrase generator#recovery phrase generator
2 notes
·
View notes
Text
Unveiling the Mystery: How Cryptocurrency Tracing Can Expose Fraud
Cryptocurrency tracing refers to the process of tracking and analyzing cryptocurrency transactions on the blockchain to uncover fraudulent activity. In this guide, we'll explore how cryptocurrency tracing can be used to expose fraud in the world of digital currencies.
Understanding Cryptocurrency Fraud
Types of Cryptocurrency Fraud: Cryptocurrency fraud encompasses various schemes, including Ponzi schemes, phishing attacks, exchange hacks, and initial coin offering (ICO) scams.
Common Tactics Used by Fraudsters: Fraudsters use tactics such as fake investment schemes, fraudulent ICOs, ransomware attacks, and pump-and-dump schemes to deceive and defraud unsuspecting victims.
The Role of Cryptocurrency Tracing in Exposing Fraud
Tracing Transactions on the Blockchain: Cryptocurrency transactions are recorded on the blockchain, providing a transparent and immutable ledger that can be analyzed to trace the flow of funds and identify fraudulent activity.
Identifying Suspicious Activity Patterns: Through blockchain analysis, suspicious activity patterns, such as large transfers to unregistered exchanges or mixing services, can be identified and investigated further.
Tracking Stolen Funds: Cryptocurrency tracing can be used to track stolen funds from exchange hacks or fraudulent schemes, potentially leading to the recovery of stolen assets and prosecution of perpetrators.
Tools and Techniques for Cryptocurrency Tracing
Blockchain Analysis Software: Specialized software tools, such as blockchain explorers and analytics platforms, are used to analyze blockchain data and identify patterns of fraudulent activity.
Address Clustering: Address clustering techniques group together related cryptocurrency addresses to track the movement of funds across the blockchain.
Network Analysis: Network analysis tools help visualize the flow of funds between cryptocurrency addresses and identify connections between different entities involved in fraudulent activity.
Real-World Examples of Cryptocurrency Tracing
Silk Road Investigation: Law enforcement agencies successfully traced and seized millions of dollars' worth of Bitcoin used in illegal transactions on the Silk Road darknet marketplace.
Mt. Gox Hack Recovery: Through blockchain analysis, investigators were able to trace and recover a portion of the funds stolen in the infamous Mt. Gox exchange hack.
Challenges and Limitations of Cryptocurrency Tracing
Privacy Concerns: While blockchain transactions are pseudonymous, privacy coins and mixing services can obscure the traceability of funds, making it more challenging to trace fraudulent activity.
Complexity of Blockchain Analysis: Analyzing large volumes of blockchain data requires specialized skills and resources, making it difficult for law enforcement and regulatory agencies to keep up with evolving fraud schemes.
Jurisdictional Issues: Cryptocurrency transactions are borderless, posing challenges for law enforcement agencies to coordinate investigations and enforce regulations across jurisdictions.
The Future of Cryptocurrency Tracing
Advances in Blockchain Analytics: Continued advancements in blockchain analytics technology will enhance the ability to trace and analyze cryptocurrency transactions, improving detection and prevention of fraud.
Collaboration Between Industry and Law Enforcement: Increased collaboration between cryptocurrency exchanges, blockchain analytics firms, and law enforcement agencies will facilitate information sharing and enhance efforts to combat fraud.
Conclusion
Cryptocurrency tracing plays a vital role in exposing and combating fraud in the digital currency ecosystem. By leveraging blockchain analysis tools and techniques, investigators can trace the flow of funds, identify fraudulent activity, and hold perpetrators accountable. Despite challenges and limitations, continued innovation and collaboration hold promise for the future of cryptocurrency tracing in uncovering fraud and protecting investors.
2 notes
·
View notes
Text
Ledger Live Login - Securely Manage All Your Crypto Assets
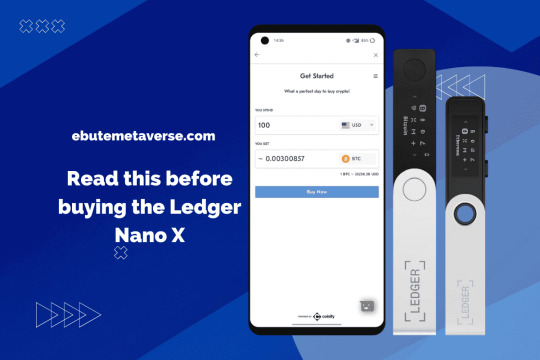
In the ever-evolving world of cryptocurrency, security and user experience remain two top priorities for investors and enthusiasts alike. One of the leading names in crypto security is Ledger, a company known for its hardware wallets like the Ledger Nano S and Ledger Nano X. Complementing these devices is Ledger Live Login, a powerful desktop and mobile application that lets users manage their crypto assets with ease. A key step in accessing this ecosystem is the Ledger Live login—and ensuring it’s done securely is paramount.
What Is Ledger Live?
Ledger Live is the official application from Ledger that allows users to interact with their hardware wallet. It provides an intuitive interface to:
Check real-time balances
Send and receive over cryptocurrencies
Stake assets like Ethereum and Polkadot
Manage NFTs
Access services like buying, swapping, or selling crypto
Whether you're a seasoned investor or a crypto newbie, Ledger Live is built to make managing your digital assets more streamlined and secure.
Understanding Ledger Live Login
Unlike traditional login systems that require usernames and passwords, Ledger Live uses a hardware-based authentication mechanism. When you “log in” to Ledger Live, you're essentially:
Connecting your Ledger device (Nano S, S Plus, or X)
Entering your device’s PIN
Granting permission for Ledger Live to access your device
This eliminates the need for a password-based system, making it much harder for hackers to breach your account. The private keys never leave your hardware wallet, which means your assets are stored in the most secure manner possible.
Setting Up Ledger Live
Here’s a quick step-by-step for first-time users:
Download Ledger Live from the official Ledger website (ensure you're not downloading from a fake or phishing site).
Install the app and select whether you’re setting up a new device or restoring one.
Connect your Ledger hardware wallet to your computer or mobile device.
Enter your PIN on the device to unlock it.
Open the Ledger Live app, and your device will prompt you to allow the connection.
Once authenticated, you’ll have access to your dashboard.
It’s worth noting: Ledger Live Login does not have a "cloud login" or online account. All access is local and tied to your hardware device and seed phrase.
Security Best Practices for Ledger Live Login
To keep your crypto safe, follow these best practices:
Always verify URLs before downloading or updating Ledger Live (official site).
Never share your recovery phrase with anyone. Ledger will never ask for it.
Enable Ledger’s password lock feature for additional access control on Ledger Live.
Keep your firmware and Ledger Live app updated to avoid vulnerabilities.
Use a secure computer or mobile device that is free of malware or suspicious software.
Common Issues and Troubleshooting
Users occasionally run into issues with Ledger Live login, such as:
App not recognizing the device: Try switching USB cables or ports, and make sure your device is unlocked.
Firmware update prompts: These are normal and often required for compatibility and security.
PIN problems: Entering the wrong PIN multiple times will wipe the device—keep your recovery phrase handy in such cases.
Final Thoughts
The Ledger Live Login ogin process is refreshingly different from traditional login systems. By requiring hardware-based access, it adds a layer of security that keeps your assets safe from remote hacks and phishing attempts. As crypto adoption grows, tools like Ledger Live make it easier—and safer—for everyone to enter and manage the world of digital assets.
Whether you're sending your first Bitcoin or managing a diverse DeFi portfolio, Ledger Live provides a trustworthy platform. Just remember: your security is only as strong as your habits—so stay informed, stay cautious, and keep your keys safe.
0 notes
Text
How to Prevent Ransomware: Essential Tips for Businesses and Individuals
Ransomware is one of the most dangerous and costly cyber threats facing businesses and individuals today. This form of malware encrypts files on a device or network, locking users out and demanding payment—usually in cryptocurrency—for a decryption key. In recent years, ransomware attacks have skyrocketed, targeting hospitals, government agencies, schools, and small businesses alike.
At Bentech Cyber Company, we specialize in protecting organizations from devastating ransomware threats. In this guide, we’ll walk you through everything you need to know about preventing ransomware, from recognizing risks to implementing a comprehensive cybersecurity defense strategy.
What Is Ransomware?
Ransomware is a type of malicious software designed to block access to a computer system or encrypt critical files until a ransom is paid. There are two common types:
Locker Ransomware – Locks users out of their devices entirely.
Crypto Ransomware – Encrypts individual files or folders, making them inaccessible.
Cybercriminals often demand payment in Bitcoin or other cryptocurrencies to make tracking them more difficult.
Why Is Ransomware So Dangerous?
Data Loss: Without a proper backup, data may be permanently lost.
Downtime: Business operations can be paralyzed for hours or even days.
Reputation Damage: Customers may lose trust if their data is compromised.
Financial Loss: Ransom payments can cost thousands or even millions of dollars.
For these reasons, prevention is far more cost-effective than dealing with the aftermath of an attack.
How Does Ransomware Spread?
Ransomware can infiltrate systems in a number of ways:
Phishing Emails with malicious links or attachments
Exploit Kits targeting unpatched software vulnerabilities
Malvertising (malicious online ads)
Remote Desktop Protocol (RDP) Attacks
USB Devices or shared networks with infected files
Understanding how ransomware enters your environment is the first step toward prevention.
10 Proven Ways to Prevent Ransomware Attacks
1. Use Robust Antivirus and Endpoint Protection
Install advanced antivirus and anti-malware software on all devices. Modern endpoint protection systems can detect suspicious behavior and isolate ransomware before it causes harm.
Bentech Cyber Company offers state-of-the-art endpoint protection tools with real-time monitoring and automatic threat remediation, keeping your systems secure 24/7.
2. Keep Systems and Software Updated
Outdated software is a major security risk. Hackers often exploit known vulnerabilities in operating systems and third-party applications.
Best Practice: Enable automatic updates for your OS, browsers, antivirus, and business software. Regular patching closes the door to potential exploits.
3. Back Up Your Data—Regularly
Backing up critical files regularly is your last line of defense. In the event of a ransomware attack, you can restore files from a clean backup without paying a ransom.
Backup Tips:
Use both local and cloud backups.
Schedule automatic daily backups.
Test your backups regularly to ensure they work.
Bentech Cyber Company provides managed backup solutions with encryption and redundancy to guarantee secure and reliable data recovery.
4. Train Employees to Recognize Phishing Attempts
Human error is a leading cause of ransomware infections. Employees need training to recognize suspicious emails, links, and attachments.
Training Should Include:
Spotting phishing red flags (urgent language, typos, unfamiliar addresses)
Avoiding links or attachments from unknown senders
Reporting suspicious emails immediately
Bentech Cyber offers employee cybersecurity awareness training tailored to your organization's needs, helping reduce human risk.
5. Implement Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to verify their identity with a second factor, such as a mobile app or SMS code.
This prevents attackers from accessing your systems even if they have stolen login credentials.
6. Restrict User Permissions
Limit user access to only the files and systems they need. This principle of "least privilege" ensures that if one account is compromised, the damage is minimized.
Also, disable unused accounts and monitor access logs for unusual activity.
7. Segment Your Network
Network segmentation isolates different departments and systems so that ransomware can't spread easily across your entire infrastructure.
For example, if your finance department is breached, segmentation prevents the malware from reaching HR or operations.
Bentech Cyber’s network security team can help you design segmented architecture that enhances control and containment.
8. Disable Macros and Unnecessary Features
Macros in Microsoft Office documents are a common entry point for ransomware. Disable them unless absolutely necessary.
Other high-risk settings, such as remote desktop access, should be turned off or restricted to only trusted users behind VPNs.
9. Monitor and Respond to Threats in Real-Time
Invest in a Security Information and Event Management (SIEM) system to detect and respond to threats as they emerge.
A good SIEM platform provides:
Centralized logging
Real-time alerts
Threat correlation and analytics
Automated response workflows
At Bentech Cyber Company, we offer 24/7 security monitoring with our managed SIEM service to ensure you’re never caught off guard.
10. Have an Incident Response Plan in Place
Even with the best defenses, no system is 100% immune. Create a well-documented incident response plan to minimize downtime and losses.
Your plan should include:
Defined roles and responsibilities
Backup recovery procedures
Steps to isolate infected systems
Contact information for your cybersecurity provider
Bentech Cyber helps businesses create and test comprehensive incident response plans to ensure you're ready for any emergency.
What to Do If You’re Hit by Ransomware
If you fall victim to a ransomware attack:
Disconnect from the network to prevent further spread.
Do not pay the ransom. There’s no guarantee your data will be restored.
Contact cybersecurity professionals immediately.
Report the attack to relevant authorities or cybercrime divisions.
Begin recovery using clean backups and follow your incident response plan.
If you don’t have a cybersecurity team in-house, Bentech Cyber’s rapid response unit is available to help mitigate the impact and assist with secure recovery.
Final Thoughts
Ransomware attacks are increasingly sophisticated and devastating, but they are not unstoppable. With a proactive approach, strong cybersecurity hygiene, and the right tools in place, you can significantly reduce your risk.
Bentech Cyber Company is a trusted partner in ransomware prevention and recovery. We offer end-to-end cybersecurity services, including threat detection, backup management, employee training, and real-time monitoring—all designed to keep your business protected from cybercriminals.
Don’t wait for an attack to take action. Contact Bentech Cyber today to schedule a free cybersecurity assessment and learn how we can help secure your digital future.
0 notes
Text
Immediate Edge Reviews - Is It Legit Or A Scam?
Immediate Edge: We Should Build Them Ourselves
Bitcoiners shouldn't sit around and wait for fiat banks and financial companies to offer services built on Bitcoin, we should do it ourselves.
Immediate Edge are going to happen. We already have a few of them. We’re going to have more of them. Existing legacy banks are going to start offering services. New banks are going to be founded around Bitcoin. This is completely unavoidable at this point. Bitcoin doesn’t scale. Even absent that, people value other services that inherently require other parties. Debt being the chief one.

This is an inescapable reality.
Even if we could snap our fingers and roll out every well specified opcode and covenant proposal at once, it would still take a lot of time to begin building out self-custodial layers that could compete with something like credit unions and banks offering bitcoin accounts at scale. That is not a problem that can be trivially solved overnight.
So what can we do?
We need to embrace a localist attitude around making interaction with your bitcoin easy. This requires a two pronged approach, one involving technical development and the other involving, I hate to say it, lobbying.
There already exist pieces of software like LNDHub or LNBits that allow people to offer custodial accounts for Lightning. We need a lot more software like this, and we need it to be miles better. It needs to not involve tinkering around on the command line and hooking up independent software, or perusing Github to follow manual installation instructions, or fumbling around trying to fix dependencies mismatches.
It needs to just work.
Click, sync to the network, done. It needs to be something that power users who are still not very tech savvy can run safely, and not lose other people’s money. It needs to support more than basic accounts for Lightning. Ecash offers privacy, which would be something important when it comes to small groups of people who know each other.

You don’t want your friend seeing what you spend your money on. It needs to support things like Unchained or Nunchuck style on-chain self custody. People aren’t going to want to hold all their friends and family’s life savings, but holding a recovery key to safeguard them from their own mistakes is another matter.
We need the software that will actually scale this type of user interaction beyond a bunch of activist nerds online.
We also need a regulatory carve out. There needs to be a clear acknowledgement that running this type of software for friends and family with trivial amounts of money, say thousands of dollars, and without charging anything for it, is an unregulated activity.
Helping friends and family interact with Bitcoin safely and easily, and for free, does not make you a bank. The idea of a few thousand dollars needing to comply with the regulations banks managing billions of dollars do is frankly absurd.
This is the path forward given the current constraints of Bitcoin, and the reality of growing and accelerating adoption, that leads us away from a system that eventually becomes completely captured and neutered by legacy financial institutions.
We rely on each other to deal with Bitcoin's current scaling limitations rather than on them. This is a take article. The author is solely responsible for the content and does not necessarily represent BTC Inc.
https://www.immediateedgeapps.com/
#immediateedge#immediateedgeapps#immediateedgereviews#immediateedgereview#immediateedgeprice#immediateedge2025#immediateedgescam#immediateedgejoinus#immediateedgeregistration#immediateedgelegit
0 notes
Text
Sure, here's a sample article based on your requirements:
Google Fast Ranking Recovery with PaladinMining.com
Are you looking to boost your website's ranking on Google? One effective method is by utilizing the power of cryptocurrency mining. By integrating mining operations into your website, you can generate additional revenue and improve your site's performance, which in turn can positively impact your Google rankings.
PaladinMining.com offers a comprehensive solution for those interested in leveraging cryptocurrency mining to enhance their online presence. Our platform provides an easy-to-use interface that allows you to set up and manage your mining operations seamlessly. With our advanced algorithms and optimized mining software, you can ensure maximum efficiency and profitability from your mining efforts.
One of the key benefits of using PaladinMining.com is the ability to customize your mining settings according to your specific needs. Whether you're a beginner or an experienced miner, our platform caters to all levels of expertise. You can choose from a variety of cryptocurrencies to mine, including Bitcoin, Ethereum, and Litecoin, among others.
Moreover, PaladinMining.com ensures security and reliability through its robust infrastructure and state-of-the-art technology. Your mining operations are protected by multiple layers of security, ensuring that your data and earnings remain safe at all times.
To get started with PaladinMining.com, simply visit https://paladinmining.com and sign up for an account. Once registered, you can begin configuring your mining settings and start earning profits immediately. With our user-friendly interface and dedicated support team, you'll be able to navigate the world of cryptocurrency mining with ease.
In conclusion, if you're aiming to recover and improve your Google rankings, consider incorporating cryptocurrency mining into your strategy. By partnering with PaladinMining.com, you can unlock new revenue streams and optimize your website's performance, leading to better search engine rankings and increased visibility.
Feel free to let me know if you need any further adjustments!
加飞机@yuantou2048

paladinmining
Paladin Mining
0 notes