#bypass Bootloader
Explore tagged Tumblr posts
Text
Are the means of computation even seizable?
I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me in PITTSBURGH in TOMORROW (May 15) at WHITE WHALE BOOKS, and in PDX on Jun 20 at BARNES AND NOBLE with BUNNIE HUANG. More tour dates (London, Manchester) here.

Something's very different in tech. Once upon a time, every bad choice by tech companies – taking away features, locking out mods or plugins, nerfing the API – was countered, nearly instantaneously, by someone writing a program that overrode that choice.
Bad clients would be muscled aside by third-party clients. Locked bootloaders would be hacked and replaced. Code that confirmed you were using OEM parts, consumables or adapters would be found and nuked from orbit. Weak APIs would be replaced with muscular, unofficial APIs built out of unstoppable scrapers running on headless machines in some data-center. Every time some tech company erected a 10-foot enshittifying fence, someone would show up with an 11-foot disenshittifying ladder.
Those 11-foot ladders represented the power of interoperability, the inescapable bounty of the Turing-complete, universal von Neumann machine, which, by definition, is capable of running every valid program. Specifically, they represented the power of adversarial interoperability – when someone modifies a technology against its manufacturer's wishes. Adversarial interoperability is the origin story of today's tech giants, from Microsoft to Apple to Google:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
But adversarial interop has been in steady decline for the past quarter-century. These big companies moved fast and broke things, but no one is returning the favor. If you ask the companies what changed, they'll just smirk and say that they're better at security than the incumbents they disrupted. The reason no one's hacked up a third-party iOS App Store is that Apple's security team is just so fucking 1337 that no one can break their shit.
I think this is nonsense. I think that what's really going on is that we've made it possible for companies to design their technologies in such a way that any attempt at adversarial interop is illegal.
"Anticircumvention" laws like Section 1201 of the 1998 Digital Millennium Copyright Act make bypassing any kind of digital lock (AKA "Digital Rights Management" or "DRM") very illegal. Under DMCA, just talking about how to remove a digital lock can land you in prison for 5 years. I tell the story of this law's passage in "Understood: Who Broke the Internet," my new podcast series for the CBC:
https://pluralistic.net/2025/05/08/who-broke-the-internet/#bruce-lehman
For a quarter century, tech companies have aggressively lobbied and litigated to expand the scope of anticircumvention laws. At the same time, companies have come up with a million ways to wrap their products in digital locks that are a crime to break.
Digital locks let Chamberlain, a garage-door opener monopolist block all third-party garage-door apps. Then, Chamberlain stuck ads in its app, so you have to watch an ad to open your garage-door:
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain
Digital locks let John Deere block third-party repair of its tractors:
https://pluralistic.net/2022/05/08/about-those-kill-switched-ukrainian-tractors/
And they let Apple block third-party repair of iPhones:
https://pluralistic.net/2022/05/22/apples-cement-overshoes/
These companies built 11-foot ladders to get over their competitors' 10-foot walls, and then they kicked the ladder away. Once they were secure atop their walls, they committed enshittifying sins their fallen adversaries could only dream of.
I've been campaigning to abolish anticircumvention laws for the past quarter-century, and I've noticed a curious pattern. Whenever these companies stand to lose their legal protections, they freak out and spend vast fortunes to keep those protections intact. That's weird, because it strongly implies that their locks don't work. A lock that works works, whether or not it's illegal to break that lock. The reason Signal encryption works is that it's working encryption. The legal status of breaking Signal's encryption has nothing to do with whether it works. If Signal's encryption was full of technical flaws but it was illegal to point those flaws out, you'd be crazy to trust Signal.
Signal does get involved in legal fights, of course, but the fights it gets into are ones that require Signal to introduce defects in its encryption – not fights over whether it is legal to disclose flaws in Signal or exploit them:
https://pluralistic.net/2023/03/05/theyre-still-trying-to-ban-cryptography/
But tech companies that rely on digital locks manifestly act like their locks don't work and they know it. When the tech and content giants bullied the W3C into building DRM into 2 billion users' browsers, they categorically rejected any proposal to limit their ability to destroy the lives of people who broke that DRM, even if it was only to add accessibility or privacy to video:
https://www.eff.org/deeplinks/2017/09/open-letter-w3c-director-ceo-team-and-membership
The thing is, if the lock works, you don't need the legal right to destroy the lives of people who find its flaws, because it works.
Do digital locks work? Can they work? I think the answer to both questions is a resounding no. The design theory of a digital lock is that I can provide you with an encrypted file that your computer has the keys to. Your computer will access those keys to decrypt or sign a file, but only under the circumstances that I have specified. Like, you can install an app when it comes from my app store, but not when it comes from a third party. Or you can play back a video in one kind of browser window, but not in another one. For this to work, your computer has to hide a cryptographic key from you, inside a device you own and control. As I pointed out more than a decade ago, this is a fool's errand:
https://memex.craphound.com/2012/01/10/lockdown-the-coming-war-on-general-purpose-computing/
After all, you or I might not have the knowledge and resources to uncover the keys' hiding place, but someone does. Maybe that someone is a person looking to go into business selling your customers the disenshittifying plugin that unfucks the thing you deliberately broke. Maybe it's a hacker-tinkerer, pursuing an intellectual challenge. Maybe it's a bored grad student with a free weekend, an electron-tunneling microscope, and a seminar full of undergrads looking for a project.
The point is that hiding secrets in devices that belong to your adversaries is very bad security practice. No matter how good a bank safe is, the bank keeps it in its vault – not in the bank-robber's basement workshop.
For a hiding-secrets-in-your-adversaries'-device plan to work, the manufacturer has to make zero mistakes. The adversary – a competitor, a tinkerer, a grad student – only has to find one mistake and exploit it. This is a bedrock of security theory: attackers have an inescapable advantage.
So I think that DRM doesn't work. I think DRM is a legal construct, not a technical one. I think DRM is a kind of magic Saran Wrap that manufacturers can wrap around their products, and, in so doing, make it a literal jailable offense to use those products in otherwise legal ways that their shareholders don't like. As Jay Freeman put it, using DRM creates a new law called "Felony Contempt of Business Model." It's a law that has never been passed by any legislature, but is nevertheless enforceable.
In the 25 years I've been fighting anticircumvention laws, I've spoken to many government officials from all over the world about the opportunity that repealing their anticircumvention laws represents. After all, Apple makes $100b/year by gouging app makers for 30 cents on ever dollar. Allow your domestic tech sector to sell the tools to jailbreak iPhones and install third party app stores, and you can convert Apple's $100b/year to a $100m/year business for one of your own companies, and the other $999,900,000,000 will be returned to the world's iPhone owners as a consumer surplus.
But every time I pitched this, I got the same answer: "The US Trade Representative forced us to pass this law, and threatened us with tariffs if we didn't pass it." Happy Liberation Day, people – every country in the world is now liberated from the only reason to keep this stupid-ass law on their books:
https://pluralistic.net/2025/01/15/beauty-eh/#its-the-only-war-the-yankees-lost-except-for-vietnam-and-also-the-alamo-and-the-bay-of-ham
In light of the Trump tariffs, I've been making the global rounds again, making the case for an anticircumvention repeal:
https://www.ft.com/content/b882f3a7-f8c9-4247-9662-3494eb37c30b
One of the questions I've been getting repeatedly from policy wonks, activists and officials is, "Is it even possible to jailbreak modern devices?" They want to know if companies like Apple, Tesla, Google, Microsoft, and John Deere have created unbreakable digital locks. Obviously, this is an important question, because if these locks are impregnable, then getting rid of the law won't deliver the promised benefits.
It's true that there aren't as many jailbreaks as we used to see. When a big project like Nextcloud – which is staffed up with extremely accomplished and skilled engineers – gets screwed over by Google's app store, they issue a press-release, not a patch:
https://arstechnica.com/gadgets/2025/05/nextcloud-accuses-google-of-big-tech-gatekeeping-over-android-app-permissions/
Perhaps that's because the tech staff at Nextcloud are no match for Google, not even with the attacker's advantage on their side.
But I don't think so. Here's why: we do still get jailbreaks and mods, but these almost exclusively come from anonymous tinkerers and hobbyists:
https://consumerrights.wiki/Mazda_DMCA_takedown_of_Open_Source_Home_Assistant_App
Or from pissed off teenagers:
https://www.theverge.com/2022/9/29/23378541/the-og-app-instagram-clone-pulled-from-app-store
These hacks are incredibly ambitious! How ambitious? How about a class break for every version of iOS as well as an unpatchable hardware attack on 8 years' worth of Apple bootloaders?
https://pluralistic.net/2020/05/25/mafia-logic/#sosumi
Now, maybe it's the case at all the world's best hackers are posting free code under pseudonyms. Maybe all the code wizards working for venture backed tech companies that stand to make millions through clever reverse engineering are just not as mad skilled as teenagers who want an ad-free Insta and that's why they've never replicated the feat.
Or maybe it's because teenagers and anonymous hackers are just about the only people willing to risk a $500,000 fine and 5-year prison sentence. In other words, maybe the thing that protects DRM is law, not code. After all, when Polish security researchers revealed the existence of secret digital locks that the train manufacturer Newag used to rip off train operators for millions of euros, Newag dragged them into court:
https://fsfe.org/news/2025/news-20250407-01.en.html
Tech companies are the most self-mythologizing industry on the planet, beating out even the pharma sector in boasting about their prowess and good corporate citizenship. They swear that they've made a functional digital lock…but they sure act like the only thing those locks do is let them sue people who reveal their workings.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/05/14/pregnable/#checkm8
#pluralistic#apple#drm#og app#instagram#meta#dmca 1201#comcom#competitive compatibility#interop#interoperability#adversarial interoperability#who broke the internet#self-mythologizing#infosec#schneiers law#red team advantage#attackers advantage#luddism#seize the means of computation
403 notes
·
View notes
Text
DarkPaRK.net
Mission profile
• Need bursts of ≥100 Mb/s, no regime filtering • Radio-direction-finding (RDF) teams appear within 15–30 min of any suspicious uplink • Therefore: operate multiple links, never longer than a short session, always from rotating sites
1. Modified Starlink terminal
Acquisition – Purchase Gen-2 terminals across the border – Move them inside RF-shielded containers
Jailbreak – Extract eMMC, patch the bootloader to bypass geo-fencing – Spoof GNSS with an SDR so the dish “believes” it is offshore, inside Starlink’s licensed maritime zone
Installation – Flat antenna hidden beneath sheet-metal roofing – RF-absorbing foam lines the attic to blunt side-lobes – Power from a 24 V alternator on existing machinery, feeding a 1 kWh battery
OpSec – Sessions limited to 10–15 min during heavy rain or nearby artillery exercises (high ambient EMI) – All traffic exits through a European VPS via WireGuard; no .kr or .cn domains ever touched – After each use, issue the terminal’s thermal-shutdown command so it appears “dead” if mains is cut
2. Cross-border 4G/5G
Hardware – Huawei 5G CPE plus 20 dBi panel or Yagi on a telescopic mast – SIMs registered to discarded IDs, activated in a border town
Deployment – Mast raised on river sandbars or hilltops ≤15 km from Chinese towers – When a ferry docks or factory shift changes (tower saturated), connect for ≤2 min
Counter-measures – IMEI/IMSI swapped each session with a software-defined-radio front-end – Directional antenna keeps signal below horizon on the domestic side
3. Ku-band VSAT disguised as TV dish
75 cm offset dish painted with state-TV logo
LNB casing replaced by a Hughes modem; coax carries both RF and PoE
Pointing performed at dawn when most dishes are re-aligned for seasonal shift—blends in
Beam lease on an Intelsat transponder that footprints the peninsula; throughput 20–40 Mb/s
Dish park-positioned at the standard satellite so casual inspection sees nothing unusual
4. Opportunistic diplomatic Wi-Fi
Small client radio with high-gain patch hidden in HVAC duct facing embassy compound
Packet capture only after business hours; tunnel out via ChaCha20-Poly1305 VPN
Device powered by scavenged PoE from building lighting—no new cabling visible
5. General RF hygiene
• Never transmit from the same spot twice in 24 h • Maintain a scanner on the state’s 400 MHz RDF coordination channel; any spike = immediate shutdown • Keep all equipment on quick-release mounts; entire site cleared in <90 s
Result: multiple independent paths to high-speed, unfiltered internet, each used briefly and asymmetrically so no single failure compromises the network—or the operator.
0 notes
Text
0 notes
Text
Unlock the World Redmi 5A: Detailed instructions for Unlock, Root, TWRP and more!
## unlock the World Redmi 5A: Detailed instructions for unlock, root, TWRP and more! Is your Redmi 5A phone limited? You want to experience advanced features and customize the system as you like? This article will be the key to help you unlock the entire potential of the Redmi 5A, from unlocking bootloader, rooting machine, installing TWRP Recovery to Advanced Flash, Write and BYPASS tips. We…
0 notes
Text
Why Every Android User Should Learn ADB and Fastboot Commands

In the world of Android smartphones, most users are familiar with basic functions like installing apps, adjusting settings, and browsing the internet. However, if you want to take your Android experience to the next level, you need to get comfortable with ADB and Fastboot commands. These powerful tools allow users to interact with their devices in ways that go beyond what’s possible through the standard user interface. Whether you’re looking to root your device, flash a custom ROM, or perform advanced debugging, understanding ADB Fastboot commands can significantly enhance your Android journey.
What Are ADB and Fastboot?
ADB (Android Debug Bridge) and Fastboot are command-line tools that provide a communication channel between your computer and Android devices. They are often used by developers and advanced users for tasks like system modifications, troubleshooting, and recovery. Though both are part of the Android SDK (Software Development Kit), they serve different purposes.
ADB is primarily used for managing and interacting with your Android device while it’s running. It allows you to send commands to your device via a USB connection, making tasks like installing apps, copying files, or debugging apps much easier.
Fastboot, on the other hand, operates at a lower level. It’s used for tasks that involve your device's bootloader or recovery mode, such as unlocking the bootloader, flashing system partitions, or installing a custom recovery.
Understanding these two tools is essential if you want to fully unlock your device’s potential and make the most out of its capabilities. Whether you’re an enthusiast looking to customize your phone or a developer working on mobile apps, knowing ADB Fastboot commands will give you more control over your device.
Why Should Every Android User Learn ADB and Fastboot Commands?
1. Unlocking Advanced Customization
One of the main reasons to learn ADB and Fastboot commands is the ability to unlock advanced customization options on your Android device. For instance, you can easily root your phone, flash a custom ROM, or install custom kernels, all of which can help you get more out of your device. These commands allow you to bypass the limitations of the stock operating system and experiment with features that may not be available out of the box.
2. Improved Troubleshooting and Debugging
ADB is a great tool for developers or anyone dealing with app-related issues. It allows you to debug apps directly on your Android device and even run commands that can simulate different conditions on your phone. If you’re troubleshooting a problem with your phone, you can use ADB commands to gather logs, reset settings, or even perform a factory reset if needed. This level of control can save you a lot of time and effort, especially if your device is unresponsive or malfunctioning.
3. Flashing and Installing Updates
When it comes to flashing custom ROMs or installing updates manually, Fastboot commands are invaluable. Fastboot can be used to install system images, recoveries, and bootloaders, which are essential for upgrading your device or rolling back to an older version. In some cases, manufacturers may not provide over-the-air updates for older devices, and Fastboot provides an easy solution to update your phone to the latest version of Android.
4. Rooting Your Device
Rooting an Android device can unlock full access to the system files, enabling you to customize the phone in ways that are otherwise impossible. While there are many apps that claim to root your phone with a single click, using ADB and Fastboot commands provides a more reliable and flexible way to gain root access. It also gives you the ability to undo the process easily, unlike some one-click solutions.
5. A Smarter Way to Manage Apps and Files
With ADB, you can install, uninstall, or back up apps directly from your computer. This is particularly useful for managing multiple devices or for performing bulk operations on apps. You can even install APK files without using the Play Store, which can be useful for testing or for sideloading apps that aren’t available in your region.
6. Boosting Performance
If you want to get the most performance out of your Android device, you may need to modify some system settings. Fastboot commands can be used to tweak your device's bootloader and recovery partitions, which can lead to performance improvements. Additionally, ADB can be used for clearing cache, monitoring battery usage, or even disabling unnecessary apps that drain your device's resources.
7. Save Money with a Mobile App Cost Calculator
If you're a developer or an entrepreneur interested in building an Android app, understanding ADB and Fastboot commands can also help in assessing the app's potential performance across different devices. For those looking to understand the costs involved in mobile app development, a mobile app cost calculator can give a ballpark estimate based on factors like design complexity, features, and platform requirements. By using ADB for testing and Fastboot for flashing different ROMs, you can also test your app on multiple Android versions and devices, ensuring it runs smoothly across a broad range of smartphones.
Ready to Get Started?
If you're interested in taking your Android skills to the next level, learning ADB and Fastboot commands is a must. The process may seem intimidating at first, but with practice, these tools will give you unprecedented control over your device. You can easily unlock its full potential, whether you’re troubleshooting, rooting, or flashing new software.
If you're interested in exploring the benefits of adb fastboot commands services for your business, we encourage you to book an appointment with our team of experts.
Book an Appointment
Conclusion
In conclusion, Fastboot commands are an essential part of any Android enthusiast's toolkit. Whether you are looking to unlock advanced features, troubleshoot issues, or install custom ROMs, these commands offer a level of control and flexibility that the standard user interface just can’t match. So, if you’re serious about exploring your Android device's true potential, learning ADB and Fastboot commands is a game-changer that will open up a world of possibilities.
0 notes
Text
Bootloader Unlock Bypass Guide
1. Download these files
👉 Mi flash Tools
👉 Php Zip File
2. Extract Php zip on your PC C local disk

3. From the folder, you can find "bypass.cmd" run it

4. Open your developer options in your device & turn on OEM Unlocking
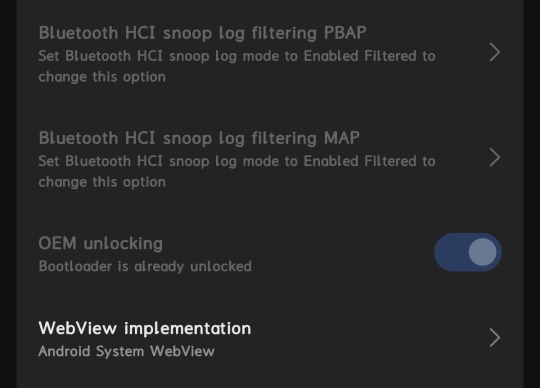
5. Now do Add Mi Account in your device - settings - developer settings - mi unlock status - add account (DON'T USE WIFI, USE MOBILE DATA )

6. Now Wait for the process to complete
7. Open the MiFlash Unlock Tool & login your mi account
8. Now connect your device in fastboot mode to PC
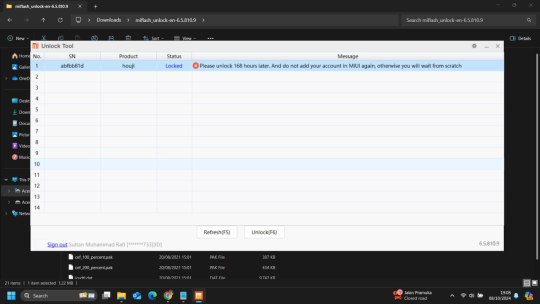
9. Now Click "Unlock" then it will show you 168hr waiting time
10. After 168hr try to unlock the bootloader with same mi flash tools it will get success.
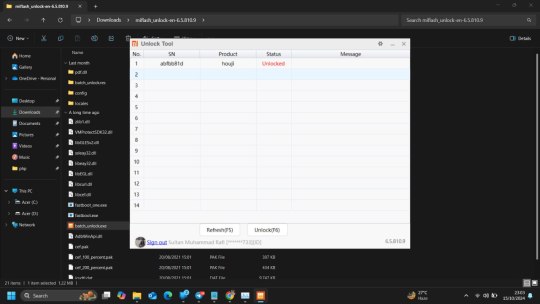
This is latest working method and one guy successfully unlocked it.
This trick worked on Indonesia rom version 1.0.11.0 and the person who tried this trick is from Indonesia.
Note :- If you guys are getting error code 30001 then try with another mi account it's working on India rom also.
Thanks to Sultan from Xiaomi 14 TG Group for testing this method and sharing the guide for all 😊
1 note
·
View note
Link
Since Xiaomi updated the HyperOS version, Unlocking BootLoader has become very difficult. But a user named MlgmXyysd found a loophole to bypass the unlockbootloader, but many people have difficulty installing it, in this article I will give detailed instructions. Warning After unlocking the BootLoader, you may encounter the following situations: Software or hardware not working properly or even damaged. Loss of data stored in the device. Credit card theft, or other financial loss. Warranty lost. Not only the base warranty, but some of the extra extended warranties (such as Mi Care or broken-screen warranty) that you have purchased may also be lost according to the exclusions provided by Xiaomi. Unlocking requirements An valid device: A unbanned* Xiaomi, Redmi or POCO device. Your device is running the official version of HyperOS. (Update 2023/11/23) Your device is not forced to verify account qualification by Xiaomi. An valid SIM card: * Except for tablets that cannot use SIM cards. SIM card must not be out of service. SIM card needs to be able to access the internet. Only 2 devices per valid SIM card are allowed to be unlock to a valid SIM card within a three-month period An valid Xiaomi account: A unbanned* Xiaomi account. Each account can only unlock 1 phone in a month and 3 phones in a year period. Environment installation and unlocking steps Download tools Xampp (PHP 8.0) Xiaomi-HyperOS-BootLoader-Bypass.zip (I have downloaded and installed the necessary libraries.) Step by step Unlock bootloader HyperOS Install xampp Download Xiaomi-HyperOS-BootLoader-Bypass.zip and unzip Move folder after unzip to C:\xampp\htdocs Open Xampp => click Start on Apache Open Shell, and cd to folder cd htdocs\Xiaomi-HyperOS-BootLoader-Bypass On phone, Tap repeatedly on the Settings - About Phone - MIUI Version to enable Development Options. Enable OEM Unlocking, USB Debugging and USB Debugging (Security Settings) in Settings - Additional Settings - Development Options Log in an valid* Xiaomi account. Connect phone to PC via wired interface. Check Always allow from this computer and click OK Open Shell , enter command: php bypass.php Check Always allow from this computer and click OK Wait and follow the prompts of script. After successful binding, you can use the official unlock tool to check the time you need to wait. When you use the official unlock tool, log in to your account and click Unlock tool, it will tell you the time you need to wait, usually about 1-15 days. Unlock bootloader instantly We now have a tool to unlock bootloader instantly without waiting, but it will cost from 20-80$ depending on the device. If you need please contact me via telegram FAQs Q: Why does the unlock tool still remind me to wait 168/360 (or more) hours? A: By principle, this PoC only bypasses the restrictions added for HyperOS. You still need to comply with the restrictions for MIUI. Q: The device shows Couldn't verify, wait a minute or two and try again. A: This is normal, the binding request on the device side has been blocked by our script. The actual binding result is subject to the script prompt. Q: Binding failed with error code 401. A: Your Xiaomi account credentials have expired, you need to log out and log in again in your device. Q: Binding failed with error code 20086. A: Your device credentials have expired, you need to reboot your device. Q: Binding failed with error code 20090 or 20091. A: Device's Security Device Credential Manager function failure, contact after-sales. Q: Binding failed with error code 30001. A: Your device has been forced to verify the account qualification by Xiaomi. Xiaomi lost its 'geek' spirit a long time ago, and there's nothing we can do about it. Q: Binding failed with error code 86015. A: The server has rejected this bind request, please try again.
0 notes
Text

ARDUINO MEGA 2560
Arduino mega 2560 Atmega2560-16au compatible with Arduino is a micro-controller board based on the ATmega2560 IC. It has a USB host interface for connecting to Android phones through the MAX3421e IC.
The MEGA ADK is equipped with versatile components, including 54 digital input/output pins (15 of which can also function as PWM outputs), 16 analog inputs, 4 UARTs (hardware serial ports), a 16 MHz crystal oscillator, a USB connection, a power jack, an ICSP header, and a reset button. This board is based on the Mega 2560 design and shares similar features with the Mega 2560 and Uno. Additionally, it has an ATmega8U2 programmed as a USB-to-serial converter. In its third revision, the Mega ADK includes a resistor that pulls the 8U2 HWB line to ground for easier access to DFU (Device Firmware Upgrade) mode.
New features on the board include:
As a result of the -1.0 pin-out, the SDA and SCL pins are near the AREF pin, and two additional pins are placed near the RESET pin, the IOREF, which allows the shields to adjust to the board’s voltage. AVR boards, which operate at 5V, and Arduino Due boards, which operate at 3.3V, will both be compatible with shields in the future. The second pin is unconnected, and is reserved for future purposes.
Circuits with a stronger RESET function.
An external power supply or USB connection can be used to power the arduino mega 2560 R3 Android Accessory Development Kit (ADK). Power is selected automatically. External (non-USB) power can come from either an AC-to-DC adapter (wall-wart) or battery. An adapter can be connected by plugging a 2.1mm center-positive plug into the board’s power socket.
-Leads from a battery can be inserted in the GND and Vin pin headers of the POWER connector. Since the Mega R3 Android Accessory Development Kit (ADK) is a USB host, the phone will attempt to draw power from it when charging. When the ADK is power over USB, 500mA is available for the phone and board.
Features and specifications:
Arduino Mega 2560:
Atmel is the programmer
Microcontroller ATmega2560.
There are 54 digital input/output terminals (14 of which have programmable PWM outputs).
There are 16 analog inputs.
There are four UARTs (hardware serial ports).
A crystal clock with a frequency of -16 MHz.
-Bootloader that allows sketches to be downloaded via USB without having to go through other writers.
The device can be powered via USB or via an external power supply (not supplied).
A heavy gold plate construction is used.
16 MHz clock speed.
The bootloader uses 8 KB of the 256 KB flash memory.
-Operating voltage: 6 ~ 12 volts.
Arduino mega 2560 cable:
Pluggable on the hot side.
-Compatible with PCs.
Strain relief and PVC overmolding ensure error-free data transmission for a lifetime.
An aluminum under-mold shield helps meet FCC requirements for KMI/RFI interference.
In addition, foil and braid shields comply with fully rated cable specifications, reducing EMI/FRI interference.
High-Performance Error-Free Transmission.
Case made of transparent acrylic:
ARDUINO MEGA 2560 R3 (unassembled) compatible.
It is possible to adjust the cover.
Transparent color.
Acrylic is the material used.
The power of
follows:
What follows is:
The Arduino board’s input voltage when it’s powered by an external source (rather than 5 volts from the USB connection or another regulated power source). If you are using the power jack to supply voltage, you can access it through this pin.
In this pin, a regulated 5V is output from the board’s regulator. The board can be powered by the DC power jack (7 – 12V), the USB connector (5V), or the VIN pin (7-12V). It is not recommended to supply voltage to your board via the 5V or 3.3V pins, as it bypasses the regulator and can damage it.
The onboard regulator generates a 3.3 volt supply with a maximum current draw of 50 milliamps.
The ground pin is GND.
This pin on the Arduino board serves as the voltage reference for the microcontroller. A properly configured shield can read the IOREF pin voltage and select the appropriate power source or enable voltage translators on the outputs for working with 5V or 3.3V.
The memory
In the arduino Mega 2560 R3 Android Accessory Development Kit (ADK), there is 256 KB of flash memory for storing code (of which 8 KB is used for the bootloader); 8 KB of SRAM, and 4 KB of EEPROM (which can be read and written).
The inputs and outputs
With pinMode(), digitalWrite(), and digitalRead() functions, the arduino Mega 2560 R3 Android Accessory Development Kit (ADK)’s 50 digital pins can be used as inputs and outputs. Each pin is powered by 5 volts and can provide or receive a maximum current of 40 milliamps. There is an internal pull-up resistor (20-50 kOhm) that is disconnected by default. Additionally, some pins have specialized functions:
It can receive (RX) and transmit (TX) TTL serial data. Pins 0 and 1 are also connected to the corresponding pins of the ATmega8U2 USB-to-TTL Serial chip.
The external interrupts are 2 (interrupt 0), 3 (interrupt 1), 18 (interrupt 5), 19 (interrupt 4), 20 (interrupt 3), and 21 (interrupt 21). The attachInterrupt() function can be used to trigger interrupts on low values, rising or falling edges, or changes in values.
The analogWrite() function provides 8-bit PWM output from 2 to 13 and 44 to 46.
There are four SPI pins on the ICSP header, which are physically compatible with the Uno, Duemilanove, and Diecimila: 50 (MISO), 51 (MOSI), 52 (SCK), 53 (SS).
MAX3421E is the USB host.
Maxim X3421E
It uses the SPI bus to communicate with Arduino. It uses the following pins:
Seven (RST), fifty (MISO), fifty-one (MOSI), and fifty-two (SCK).
Please do not use Digital pin 7 as an input or output because it is used for MAX3421E communication
PJ3 (GP_MAX), PJ6 (INT_MAX), PH7 (SS) are not broken out on headers.
A built-in LED is connected to digital pin 13. When the pin is HIGH, the LED is on, when it is LOW, it is off.
Wire library supports TWI communication using pins 20 (SDA) and 21 (SCL). These pins are not located in the same place as the TWI pins on the Duemilanove or Diecimila boards.
Inputs in the Mega R3 Android Accessory Development Kit (ADK) have a resolution of 10 bits each (i.e. 1024 different values). In default, they measure from ground to 5 volts, but you can adjust the upper end of their range by using the AREF pin and analogReference() function. There are a few other pins on the board as well:
A reference voltage for analog inputs. Use with analogReference.
Typically used to add a reset button to shields that block the board’s reset button. Bring this line LOW to reset the microcontroller.
The communication process
The Arduino Mega 2560 R3 Android Accessory Development Kit (ADK) offers various options for communicating with different devices. With the ATmega2560, there are four hardware UARTs available for TTL (5V) serial communication. Additionally, an ATmega8U2 on the board allows one of the UARTs to be used for USB communication and creates a virtual com port for software on the computer. While Windows machines may require a .inf file, OSX and Linux machines will automatically detect the board as a COM port. The Arduino software features a convenient serial monitor that enables straightforward exchange of textual data between the board and other devices.
The board’s RX and TX LEDs will blink to indicate data transmission through the ATmega8U2/16U2 chip and USB connection to the computer (note: not for serial communication on pins 0 and 1). Additionally, serial communication can be achieved on any of the MEGA ADK’s digital pins with the help of a Software-serial library. The ATmega2560 also supports TWI and SPI communication. To make use of the TWI bus, refer to the included Wire library in the Arduino software. For SPI communication, utilize the SPI library.
Any device that has a USB port can connect and interact with the Arduino MEGA 2560 ADK thanks to the USB host interface provided by the MAX3421E IC. You can use it to control Canon cameras, interact with keyboard, mouse, and game controllers such as the Wiimote and PS3 for example, as well as interact with many types of phones.
The programming language
The Mega R3 Android Accessory Development Kit (ADK) can be used with the Arduino software (download). For details, check out the reference and tutorials. The ATmega2560 on the MEGA ADK comes preburned with a boot-loader (the same on Mega 2560) that allows you to upload new code without using an external hardware programmer. In order to communicate with it, it uses the STK500v2 protocol (reference, C header files).
See these instructions for details on bypassing the bootloader and programming the microcontroller using Arduino ISP or similar. Source code for the ATmega8U2 firmware can be found in the Arduino repository. The ATmega8U2 is loaded with a DFU bootloader, which can be activated by:
Boards with Rev1:
Resetting the 8U2 requires connecting the solder jumper on the back of the board (near the map of Italy).
It is easier to put the 8U2/16U2 HWB line into DFU mode on Rev2 or later boards since a resistor pulls the line to ground. To load a new firmware, you can use Atmel’s FLIP software (Windows) or the DFU programmer (Mac OS X and Linux). For more information, see this user-contributed tutorial. If you use the ISP header and an external programmer, you can overwrite the DFU bootloader.
Reset (automatic) software
Instead of physically pressing the reset button, the Arduino MEGA ADK has the ability to be reset through a connected computer. This is achieved by connecting one of the hardware flow control lines (DTR) of the ATmega8U2 to the reset line of the ATmega2560 using a 100 nano-farad capacitor. By asserting this line (taking it low), the reset line briefly drops and resets the chip. The Arduino software utilizes this feature, allowing you to easily upload code by pressing a button in the environment.
This allows for a shorter timeout on the boot-loader, as the lowering of DTR can be easily synchronized with the beginning of the upload process. As a result, when the MEGA ADK is connected to a Mac OS X or Linux computer, it automatically resets and enters bootloader mode for a brief moment. During this time, if any data besides new code is sent to the board, it will be ignored as per its programming. However, it will intercept and process the first few bytes of data received after establishing a connection.
When a sketch on the board receives initial configuration or data upon startup, ensure that the corresponding software waits for a brief moment before transmitting this information. The MEGA ADK has a trace that can be deactivated to disable the auto-reset function. The two pads on either side of the trace can be soldered together to reactivate it. This is labeled as “RESET-EN”. Alternatively, you can potentially disable the auto-reset by connecting a 110-ohm resistor from 5V to the reset line; refer to this forum thread for further instructions.
0 notes
Text
All Icloud Services Available Like Gsm Bypass With Network/Open Menu FMI OFF All Models And All IOS Supported/Passcode Disable FMI Off/Clean Slow Service/FMI OFF With Owner Info Like Number Or Email All Services Available
#GSM_JOKERS_TEAM

#commercial#poster#icloud#bypass bootloader#FMI#ICloud Bypass#Passcode disable#Gsm#Gsmjoker#Open menu
1 note
·
View note
Photo

#fotografia#boot#thigh boots#bypass bootloader#bootloop#winter#tumblr#artists on tumblr#illustrators on tumblr#photographers on tumblr#writers on tumblr#film photography#photography#fotocommunity#fotoğraf#foto mie#fotography#foto
1 note
·
View note
Text
How to Unlock Bootloader on Motorola Droid Ultra XT1080
New Post has been published on https://trendyport.com/how-to-unlock-bootloader-on-motorola-droid-ultra-xt1080/
How to Unlock Bootloader on Motorola Droid Ultra XT1080
1 note
·
View note
Text
How to Unlock Bootloader on Motorola Moto G 5G
How to Unlock Bootloader on Motorola Moto G 5G
Unlock Bootloader on Motorola Moto G 5G : Bootloader! The technical word in the mobile devices means a lot. For all the ones who know about bootloader, it is a key to heaven in terms of mobile control. For all those who is yet to discover, it’s still a curious word. Just continue reading!! I hope you will enjoy this entire post. What is the Bootloader! In simple layman terms, the operating…

View On WordPress
#Bootloader#bypass Bootloader#open bootloader#root and unlock#turn off bootloader#unlock bootloader#unlock bootloader in motorola#unlockable#Unlocking Bootloader
0 notes
Text
How to Unlock Bootloader on Motorola Moto G 5G
How to Unlock Bootloader on Motorola Moto G 5G
Unlock Bootloader on Motorola Moto G 5G : Bootloader! The technical word in the mobile devices means a lot. For all the ones who know about bootloader, it is a key to heaven in terms of mobile control. For all those who is yet to discover, it’s still a curious word. Just continue reading!! I hope you will enjoy this entire post. What is the Bootloader! In simple layman terms, the operating…

View On WordPress
#Bootloader#bypass Bootloader#open bootloader#root and unlock#turn off bootloader#unlock bootloader#unlock bootloader in motorola#unlockable#Unlocking Bootloader
0 notes
Text
How to Unlock Bootloader on Motorola Moto G 5G
How to Unlock Bootloader on Motorola Moto G 5G
Unlock Bootloader on Motorola Moto G 5G : Bootloader! The technical word in the mobile devices means a lot. For all the ones who know about bootloader, it is a key to heaven in terms of mobile control. For all those who is yet to discover, it’s still a curious word. Just continue reading!! I hope you will enjoy this entire post. What is the Bootloader! In simple layman terms, the operating…

View On WordPress
#Bootloader#bypass Bootloader#open bootloader#root and unlock#turn off bootloader#unlock bootloader#unlock bootloader in motorola#unlockable#Unlocking Bootloader
0 notes