#interoperability
Explore tagged Tumblr posts
Text
Are the means of computation even seizable?
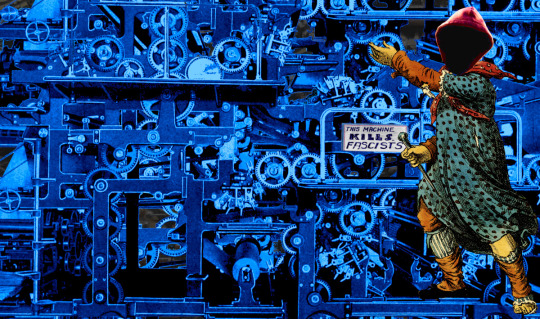
I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me in PITTSBURGH in TOMORROW (May 15) at WHITE WHALE BOOKS, and in PDX on Jun 20 at BARNES AND NOBLE with BUNNIE HUANG. More tour dates (London, Manchester) here.

Something's very different in tech. Once upon a time, every bad choice by tech companies – taking away features, locking out mods or plugins, nerfing the API – was countered, nearly instantaneously, by someone writing a program that overrode that choice.
Bad clients would be muscled aside by third-party clients. Locked bootloaders would be hacked and replaced. Code that confirmed you were using OEM parts, consumables or adapters would be found and nuked from orbit. Weak APIs would be replaced with muscular, unofficial APIs built out of unstoppable scrapers running on headless machines in some data-center. Every time some tech company erected a 10-foot enshittifying fence, someone would show up with an 11-foot disenshittifying ladder.
Those 11-foot ladders represented the power of interoperability, the inescapable bounty of the Turing-complete, universal von Neumann machine, which, by definition, is capable of running every valid program. Specifically, they represented the power of adversarial interoperability – when someone modifies a technology against its manufacturer's wishes. Adversarial interoperability is the origin story of today's tech giants, from Microsoft to Apple to Google:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
But adversarial interop has been in steady decline for the past quarter-century. These big companies moved fast and broke things, but no one is returning the favor. If you ask the companies what changed, they'll just smirk and say that they're better at security than the incumbents they disrupted. The reason no one's hacked up a third-party iOS App Store is that Apple's security team is just so fucking 1337 that no one can break their shit.
I think this is nonsense. I think that what's really going on is that we've made it possible for companies to design their technologies in such a way that any attempt at adversarial interop is illegal.
"Anticircumvention" laws like Section 1201 of the 1998 Digital Millennium Copyright Act make bypassing any kind of digital lock (AKA "Digital Rights Management" or "DRM") very illegal. Under DMCA, just talking about how to remove a digital lock can land you in prison for 5 years. I tell the story of this law's passage in "Understood: Who Broke the Internet," my new podcast series for the CBC:
https://pluralistic.net/2025/05/08/who-broke-the-internet/#bruce-lehman
For a quarter century, tech companies have aggressively lobbied and litigated to expand the scope of anticircumvention laws. At the same time, companies have come up with a million ways to wrap their products in digital locks that are a crime to break.
Digital locks let Chamberlain, a garage-door opener monopolist block all third-party garage-door apps. Then, Chamberlain stuck ads in its app, so you have to watch an ad to open your garage-door:
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain
Digital locks let John Deere block third-party repair of its tractors:
https://pluralistic.net/2022/05/08/about-those-kill-switched-ukrainian-tractors/
And they let Apple block third-party repair of iPhones:
https://pluralistic.net/2022/05/22/apples-cement-overshoes/
These companies built 11-foot ladders to get over their competitors' 10-foot walls, and then they kicked the ladder away. Once they were secure atop their walls, they committed enshittifying sins their fallen adversaries could only dream of.
I've been campaigning to abolish anticircumvention laws for the past quarter-century, and I've noticed a curious pattern. Whenever these companies stand to lose their legal protections, they freak out and spend vast fortunes to keep those protections intact. That's weird, because it strongly implies that their locks don't work. A lock that works works, whether or not it's illegal to break that lock. The reason Signal encryption works is that it's working encryption. The legal status of breaking Signal's encryption has nothing to do with whether it works. If Signal's encryption was full of technical flaws but it was illegal to point those flaws out, you'd be crazy to trust Signal.
Signal does get involved in legal fights, of course, but the fights it gets into are ones that require Signal to introduce defects in its encryption – not fights over whether it is legal to disclose flaws in Signal or exploit them:
https://pluralistic.net/2023/03/05/theyre-still-trying-to-ban-cryptography/
But tech companies that rely on digital locks manifestly act like their locks don't work and they know it. When the tech and content giants bullied the W3C into building DRM into 2 billion users' browsers, they categorically rejected any proposal to limit their ability to destroy the lives of people who broke that DRM, even if it was only to add accessibility or privacy to video:
https://www.eff.org/deeplinks/2017/09/open-letter-w3c-director-ceo-team-and-membership
The thing is, if the lock works, you don't need the legal right to destroy the lives of people who find its flaws, because it works.
Do digital locks work? Can they work? I think the answer to both questions is a resounding no. The design theory of a digital lock is that I can provide you with an encrypted file that your computer has the keys to. Your computer will access those keys to decrypt or sign a file, but only under the circumstances that I have specified. Like, you can install an app when it comes from my app store, but not when it comes from a third party. Or you can play back a video in one kind of browser window, but not in another one. For this to work, your computer has to hide a cryptographic key from you, inside a device you own and control. As I pointed out more than a decade ago, this is a fool's errand:
https://memex.craphound.com/2012/01/10/lockdown-the-coming-war-on-general-purpose-computing/
After all, you or I might not have the knowledge and resources to uncover the keys' hiding place, but someone does. Maybe that someone is a person looking to go into business selling your customers the disenshittifying plugin that unfucks the thing you deliberately broke. Maybe it's a hacker-tinkerer, pursuing an intellectual challenge. Maybe it's a bored grad student with a free weekend, an electron-tunneling microscope, and a seminar full of undergrads looking for a project.
The point is that hiding secrets in devices that belong to your adversaries is very bad security practice. No matter how good a bank safe is, the bank keeps it in its vault – not in the bank-robber's basement workshop.
For a hiding-secrets-in-your-adversaries'-device plan to work, the manufacturer has to make zero mistakes. The adversary – a competitor, a tinkerer, a grad student – only has to find one mistake and exploit it. This is a bedrock of security theory: attackers have an inescapable advantage.
So I think that DRM doesn't work. I think DRM is a legal construct, not a technical one. I think DRM is a kind of magic Saran Wrap that manufacturers can wrap around their products, and, in so doing, make it a literal jailable offense to use those products in otherwise legal ways that their shareholders don't like. As Jay Freeman put it, using DRM creates a new law called "Felony Contempt of Business Model." It's a law that has never been passed by any legislature, but is nevertheless enforceable.
In the 25 years I've been fighting anticircumvention laws, I've spoken to many government officials from all over the world about the opportunity that repealing their anticircumvention laws represents. After all, Apple makes $100b/year by gouging app makers for 30 cents on ever dollar. Allow your domestic tech sector to sell the tools to jailbreak iPhones and install third party app stores, and you can convert Apple's $100b/year to a $100m/year business for one of your own companies, and the other $999,900,000,000 will be returned to the world's iPhone owners as a consumer surplus.
But every time I pitched this, I got the same answer: "The US Trade Representative forced us to pass this law, and threatened us with tariffs if we didn't pass it." Happy Liberation Day, people – every country in the world is now liberated from the only reason to keep this stupid-ass law on their books:
https://pluralistic.net/2025/01/15/beauty-eh/#its-the-only-war-the-yankees-lost-except-for-vietnam-and-also-the-alamo-and-the-bay-of-ham
In light of the Trump tariffs, I've been making the global rounds again, making the case for an anticircumvention repeal:
https://www.ft.com/content/b882f3a7-f8c9-4247-9662-3494eb37c30b
One of the questions I've been getting repeatedly from policy wonks, activists and officials is, "Is it even possible to jailbreak modern devices?" They want to know if companies like Apple, Tesla, Google, Microsoft, and John Deere have created unbreakable digital locks. Obviously, this is an important question, because if these locks are impregnable, then getting rid of the law won't deliver the promised benefits.
It's true that there aren't as many jailbreaks as we used to see. When a big project like Nextcloud – which is staffed up with extremely accomplished and skilled engineers – gets screwed over by Google's app store, they issue a press-release, not a patch:
https://arstechnica.com/gadgets/2025/05/nextcloud-accuses-google-of-big-tech-gatekeeping-over-android-app-permissions/
Perhaps that's because the tech staff at Nextcloud are no match for Google, not even with the attacker's advantage on their side.
But I don't think so. Here's why: we do still get jailbreaks and mods, but these almost exclusively come from anonymous tinkerers and hobbyists:
https://consumerrights.wiki/Mazda_DMCA_takedown_of_Open_Source_Home_Assistant_App
Or from pissed off teenagers:
https://www.theverge.com/2022/9/29/23378541/the-og-app-instagram-clone-pulled-from-app-store
These hacks are incredibly ambitious! How ambitious? How about a class break for every version of iOS as well as an unpatchable hardware attack on 8 years' worth of Apple bootloaders?
https://pluralistic.net/2020/05/25/mafia-logic/#sosumi
Now, maybe it's the case at all the world's best hackers are posting free code under pseudonyms. Maybe all the code wizards working for venture backed tech companies that stand to make millions through clever reverse engineering are just not as mad skilled as teenagers who want an ad-free Insta and that's why they've never replicated the feat.
Or maybe it's because teenagers and anonymous hackers are just about the only people willing to risk a $500,000 fine and 5-year prison sentence. In other words, maybe the thing that protects DRM is law, not code. After all, when Polish security researchers revealed the existence of secret digital locks that the train manufacturer Newag used to rip off train operators for millions of euros, Newag dragged them into court:
https://fsfe.org/news/2025/news-20250407-01.en.html
Tech companies are the most self-mythologizing industry on the planet, beating out even the pharma sector in boasting about their prowess and good corporate citizenship. They swear that they've made a functional digital lock…but they sure act like the only thing those locks do is let them sue people who reveal their workings.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/05/14/pregnable/#checkm8
#pluralistic#apple#drm#og app#instagram#meta#dmca 1201#comcom#competitive compatibility#interop#interoperability#adversarial interoperability#who broke the internet#self-mythologizing#infosec#schneiers law#red team advantage#attackers advantage#luddism#seize the means of computation
429 notes
·
View notes
Text
"We commit to publishing and purchasing decisions that affirm the reading choices of all individuals and support choice in the academic marketplace through the use of standards and best practices for academic publishing, library infrastructure and library lending.
"Open, interoperable standards enable libraries to provide the kind of aggregation and ownership rights that have historically been integral to print library collections..."
#ebooks#books#DRM#or why it's so damn hard to read ebooks when it doesn't have to be#Interoperable Ebooks Standards Statement#LibraryFutures#interoperability#libraries#librarians#library workers#tumblarians#publishing
3 notes
·
View notes
Text
The “everything app” already exists.
It is called “the internet.”
And it is in crisis.
We really could get so much more out of computers and our massive digital footprints if there were any incentive for software developers to make programs that work together. But everyone just wants to capture the market, be the “everything app” not realizing that the real “everything app” is open source, open protocol and a probably government mandated requirement to foster interoperability. We get little glimpses of the future when some of these things align but greed keeps every dev shackled.
If you want to make money off of people using software you are a part of the public “everything app” that is called “the internet” for the privilege of using this lucrative public space you must follow basic rules. Mostly: either make your application compatible w/ similar applications, or pay an isolation tax. The unregulated public digital commons has been enclosed! it’s time to roll it back! There is no natural market incentive to solve these problems except monopoly and do we want that? no!
22 notes
·
View notes
Text
youtube
2 notes
·
View notes
Video
#Operation Toy Drop#CivilAffairs#PSYOP#Soldiers#USACAPOC(A)#USAR#interoperability#International jumpmasters#U.S. Army Reserve#flickr
3 notes
·
View notes
Text
EU regulations for “Gatekeepers”
Gatekeepers will have 6 months to comply with the EU DMA rules:
They will no longer be able to lock in users in their ecosystem.
They will no longer be able to decide which apps you need to have pre-installed on your devices; which app store you have to use.
They will not be able to “self-preference”: exploiting the advantage of being the gatekeeper by treating their own products and services more favorably.
Their messaging apps will have to interoperate with others.
And so on…
2 notes
·
View notes
Text
2 notes
·
View notes
Text
https://www.clindcast.com/
#healthcare#healthcareconsulting#florida#healthcare it consulting#healthcareit#fhir#interoperability#ehr#electronic health record
3 notes
·
View notes
Link
#AIethics#Antitrust#digitalmarkets#enshittification#interoperability#platformcapitalism#platformdecay#techregulation
0 notes
Text
CVS Health to invest $20 billion in tech-driven healthcare overhaul and interoperability improvements

- By InnoNurse Staff -
CVS Health has announced plans to invest $20 billion over the next 10 years to enhance its consumer healthcare offerings through improved technology and system interoperability.
The initiative will span CVS' integrated business segments, including Aetna, its retail pharmacies, and healthcare providers. A central component of the plan is the development of a shared patient record system that would enable better communication among various healthcare stakeholders, regardless of company affiliation.
The company also aims to make the healthcare experience more proactive by sending patients automated notifications—such as claim updates—reducing the need for them to reach out for information. Additionally, CVS is looking to streamline processes like claims management and cost estimates to create a more efficient system. CVS anticipates that the effort could lead to noticeable changes in the consumer healthcare experience within five years.
This investment comes as part of broader changes at CVS, which include the planned closure of 271 stores in 2025—adding to nearly 900 closures from 2022 to 2024—as part of a national restructuring strategy. In May, CVS participated in a bankruptcy court-approved process to acquire prescription files from 625 Rite Aid pharmacies and agreed to take over 64 Rite Aid store locations in three states, pending court and regulatory approvals. Rite Aid filed for Chapter 11 bankruptcy earlier this year.
Read more at MobiHealthNews
///
Other recent news and insights
'AI scientist' collaborates with humans to identify cheap drug combinations for potential cancer treatment (University of Cambridge)
Scientists grow vascularized heart and liver organoids, overcoming size limits and opening new avenues for research (Stanford School of Medicine)
0 notes
Text
Epic Systems, a lethal health record monopolist

Epic Systems makes the dominant electronic health record (EHR) system in America; if you're a doctor, chances are you are required to use it, and for every hour a doctor spends with a patient, they have to spend two hours doing clinically useless bureaucratic data-entry on an Epic EHR.
How could a product so manifestly unfit for purpose be the absolute market leader? Simple: as Robert Kuttner describes in an excellent feature in The American Prospect, Epic may be a clinical disaster, but it's a profit-generating miracle:
https://prospect.org/health/2024-10-01-epic-dystopia/
At the core of Epic's value proposition is "upcoding," a form of billing fraud that is beloved of hospital administrators, including the "nonprofit" hospitals that generate vast fortunes that are somehow not characterized as profits. Here's a particularly egregious form of upcoding: back in 2020, the Poudre Valley Hospital in Ft Collins, CO locked all its doors except the ER entrance. Every patient entering the hospital, including those receiving absolutely routine care, was therefore processed as an "emergency."
In April 2020, Caitlin Wells Salerno – a pregnant biologist – drove to Poudre Valley with normal labor pains. She walked herself up to obstetrics, declining the offer of a wheelchair, stopping only to snap a cheeky selfie. Nevertheless, the hospital recorded her normal, uncomplicated birth as a Level 5 emergency – comparable to a major heart-attack – and whacked her with a $2755 bill for emergency care:
https://pluralistic.net/2021/10/27/crossing-a-line/#zero-fucks-given
Upcoding has its origins in the Reagan revolution, when the market-worshipping cultists he'd put in charge of health care created the "Prospective Payment System," which paid a lump sum for care. The idea was to incentivize hospitals to provide efficient care, since they could keep the difference between whatever they spent getting you better and the set PPS amount that Medicare would reimburse them. Hospitals responded by inventing upcoding: a patient with controlled, long-term coronary disease who showed up with a broken leg would get coded for the coronary condition and the cast, and the hospital would pocket both lump sums:
https://pluralistic.net/2024/06/13/a-punch-in-the-guts/#hayek-pilled
The reason hospital administrators love Epic, and pay gigantic sums for systemwide software licenses, is directly connected to the two hours that doctors spent filling in Epic forms for every hour they spend treating patients. Epic collects all that extra information in order to identify potential sources of plausible upcodes, which allows hospitals to bill patients, insurers, and Medicare through the nose for routine care. Epic can automatically recode "diabetes with no complications" from a Hierarchical Condition Category code 19 (worth $894.40) as "diabetes with kidney failure," code 18 and 136, which gooses the reimbursement to $1273.60.
Epic snitches on doctors to their bosses, giving them a dashboard to track doctors' compliance with upcoding suggestions. One of Kuttner's doctor sources says her supervisor contacts her with questions like, "That appointment was a 2. Don’t you think it might be a 3?"
Robert Kuttner is the perfect journalist to unravel the Epic scam. As a journalist who wrote for The New England Journal of Medicine, he's got an insider's knowledge of the health industry, and plenty of sources among health professionals. As he tells it, Epic is a cultlike, insular company that employs 12.500 people in its hometown of Verona, WI.
The EHR industry's origins start with a GW Bush-era law called the HITECH Act, which was later folded into Obama's Recovery Act in 2009. Obama provided $27b to hospitals that installed EHR systems. These systems had to more than track patient outcomes – they also provided the data for pay-for-performance incentives. EHRs were already trying to do something very complicated – track health outcomes – but now they were also meant to underpin a cockamamie "incentives" program that was supposed to provide a carrot to the health industry so it would stop killing people and ripping off Medicare. EHRs devolved into obscenely complex spaghetti systems that doctors and nurses loathed on sight.
But there was one group that loved EHRs: hospital administrators and the private companies offering Medicare Advantage plans (which also benefited from upcoding patients in order to soak Uncle Sucker):
https://www.ncbi.nlm.nih.gov/pmc/articles/PMC8649706/
The spread of EHRs neatly tracks with a spike in upcharging: "from 2014 through 2019, the number of hospital stays billed at the highest severity level increased almost 20 percent…the number of stays billed at each of the other severity levels decreased":
https://oig.hhs.gov/oei/reports/OEI-02-18-00380.pdf
The purpose of a system is what it does. Epic's industry-dominating EHR is great at price-gouging, but it sucks as a clinical tool – it takes 18 keystrokes just to enter a prescription:
https://jamanetwork.com/journals/jamanetworkopen/fullarticle/2729481
Doctors need to see patients, but their bosses demand that they satisfy Epic's endless red tape. Doctors now routinely stay late after work and show up hours early, just to do paperwork. It's not enough. According to another one of Kuttner's sources, doctors routinely copy-and-paste earlier entries into the current one, a practice that generates rampant errors. Some just make up random numbers to fulfill Epic's nonsensical requirements: the same source told Kuttner that when prompted to enter a pain score for his TB patients, he just enters "zero."
Don't worry, Epic has a solution: AI. They've rolled out an "ambient listening" tool that attempts to transcribe everything the doctor and patient say during an exam and then bash it into a visit report. Not only is this prone to the customary mistakes that make AI unsuited to high-stakes, error-sensitive applications, it also represents a profound misunderstanding of the purpose of clinical notes.
The very exercise of organizing your thoughts and reflections about an event – such as a medical exam – into a coherent report makes you apply rigor and perspective to events that otherwise arrive as a series of fleeting impressions and reactions. That's why blogging is such an effective practice:
https://pluralistic.net/2021/05/09/the-memex-method/
The answer to doctors not having time to reflect and organize good notes is to give them more time – not more AI. As another doctor told Kuttner: "Ambient listening is a solution to a self-created problem of requiring too much data entry by clinicians."
EHRs are one of those especially hellish public-private partnerships. Health care doctrine from Reagan to Obama insisted that the system just needed to be exposed to market forces and incentives. EHRs are designed to allow hospitals to win as many of these incentives as possible. Epic's clinical care modules do this by bombarding doctors with low-quality diagnostic suggestions with "little to do with a patient’s actual condition and risks," leading to "alert fatigue," so doctors miss the important alerts in the storm of nonsense elbow-jostling:
https://www.ncbi.nlm.nih.gov/pmc/articles/PMC5058605/
Clinicians who actually want to improve the quality of care in their facilities end up recording data manually and keying it into spreadsheets, because they can't get Epic to give them the data they need. Meanwhile, an army of high-priced consultants stand ready to give clinicians advise on getting Epic to do what they need, but can't seem to deliver.
Ironically, one of the benefits that Epic touts is its interoperability: hospitals that buy Epic systems can interconnect those with other Epic systems, and there's a large ecosystem of aftermarket add-ons that work with Epic. But Epic is a product, not a protocol, so its much-touted interop exists entirely on its terms, and at its sufferance. If Epic chooses, a doctor using its products can send files to a doctor using a rival product. But Epic can also veto that activity – and its veto extends to deciding whether a hospital can export their patient records to a competing service and get off Epic altogether.
One major selling point for Epic is its capacity to export "anonymized" data for medical research. Very large patient data-sets like Epic's are reasonably believed to contain many potential medical insights, so medical researchers are very excited at the prospect of interrogating that data.
But Epic's approach – anonymizing files containing the most sensitive information imaginable, about millions of people, and then releasing them to third parties – is a nightmare. "De-identified" data-sets are notoriously vulnerable to "re-identification" and the threat of re-identification only increases every time there's another release or breach, which can used to reveal the identities of people in anonymized records. For example, if you have a database of all the prescribing at a given hospital – a numeric identifier representing the patient, and the time and date when they saw a doctor and got a scrip. At any time in the future, a big location-data breach – say, from Uber or a transit system – can show you which people went back and forth to the hospital at the times that line up with those doctor's appointments, unmasking the person who got abortion meds, cancer meds, psychiatric meds or other sensitive prescriptions.
The fact that anonymized data can – will! – be re-identified doesn't mean we have to give up on the prospect of gleaning insight from medical records. In the UK, the eminent doctor Ben Goldacre and colleagues built an incredible effective, privacy-preserving "trusted research environment" (TRE) to operate on millions of NHS records across a decentralized system of hospitals and trusts without ever moving the data off their own servers:
https://pluralistic.net/2024/03/08/the-fire-of-orodruin/#are-we-the-baddies
The TRE is an open source, transparent server that accepts complex research questions in the form of database queries. These queries are posted to a public server for peer-review and revision, and when they're ready, the TRE sends them to each of the databases where the records are held. Those databases transmit responses to the TRE, which then publishes them. This has been unimaginably successful: the prototype of the TRE launched during the lockdown generated sixty papers in Nature in a matter of months.
Monopolies are inefficient, and Epic's outmoded and dangerous approach to research, along with the roadblocks it puts in the way of clinical excellence, epitomizes the problems with monopoly. America's health care industry is a dumpster fire from top to bottom – from Medicare Advantage to hospital cartels – and allowing Epic to dominate the EHR market has somehow, incredibly, made that system even worse.
Naturally, Kuttner finishes out his article with some antitrust analysis, sketching out how the Sherman Act could be brought to bear on Epic. Something has to be done. Epic's software is one of the many reasons that MDs are leaving the medical profession in droves.
Epic epitomizes the long-standing class war between doctors who want to take care of their patients and hospital executives who want to make a buck off of those patients.

Tor Books as just published two new, free LITTLE BROTHER stories: VIGILANT, about creepy surveillance in distance education; and SPILL, about oil pipelines and indigenous landback.


If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/10/02/upcoded-to-death/#thanks-obama

Image: Flying Logos (modified) https://commons.wikimedia.org/wiki/File:Over_$1,000,000_dollars_in_USD_$100_bill_stacks.png
CC BY-SA 4.0 https://creativecommons.org/licenses/by-sa/4.0/deed.en
#pluralistic#ehrs#robert kuttner#tres#trusted research environments#ben goldacre#epic#epic systems#interoperability#privacy#reidentification#deidentification#thanks obama#upcoding#Hierarchical Condition Category#medicare#medicaid#ai#American Recovery and Reinvestment Act#HITECH act#medicare advantage#ambient listening#alert fatigue#monopoly#antitrust
820 notes
·
View notes
Text
#Huawei#TechInnovation#EVCharging#ChargingStandards#CleanTech#AutoEVTimes#SustainableTechnology#Interoperability#SmartDevices#GreenEnergy#FutureOfCharging#ConsumerTech#EVInfrastructure#electricvehiclesnews#evtimes#evbusines
0 notes
Text
Standardization and Interoperability: The Next Frontier for E-Recording Judgment Renewals in India's Fragmented Legal System
India’s legal system, while robust in its constitutional framework, often grapples with issues stemming from fragmentation, inconsistent procedures, and delayed implementation of digital reforms. As courts and public record offices slowly transition into the digital age, one area showing significant potential for modernization is the e-record renewal of judgments.
The growing adoption of digital legal services—especially in metropolitan courts—is promising. However, the lack of national standards and poor interoperability between systems is a key barrier. For the e-file and e-record renewal of judgment process to be truly effective in India, we must move beyond basic digitization and invest in standardized, interoperable frameworks.
The Current Landscape of E-Recording Services in India:
Unlike many developed nations, India’s e-recording infrastructure is in its infancy. Different states—and often, different districts—employ varying rules, software platforms, and operational standards for legal recordings. This makes it extremely difficult for legal professionals and citizens to navigate the system efficiently, especially when attempting tasks like the e-record renewal of judgment.
Some states have piloted e-recording services, but these are often standalone systems with limited accessibility. The lack of data exchange between courts, registrars, and government portals has created a siloed digital ecosystem. As a result, the benefits of digital recording—such as time savings, cost reduction, and transparency—are not being fully realized across the board.
Why Standardization Matters?
Standardization is about creating uniform practices, formats, and protocols across all regions. For e-record renewal of judgment, this would mean a unified system where judgment renewals can be electronically filed and recorded using a common platform—regardless of state or court.
Without standardization, here’s what’s at risk:
Increased Legal Errors: Confusion about jurisdiction-specific requirements leads to incorrect filings.
Delay in Judgments: Manual verification and back-and-forth communications hinder speedy processing.
Limited Access: Citizens in rural or under-resourced districts struggle to use fragmented systems.
A unified standard would reduce friction, allowing smoother use of e-recording services across jurisdictions and ensuring consistent enforcement of legal rights.
Interoperability: The Bridge Between Systems
Interoperability refers to the ability of different systems and software to communicate, exchange, and interpret data in a coherent manner. In the context of e-file and e-record renewal of judgment, it means creating a seamless flow of information between:
District courts and high courts
State record offices
National judicial data grids
Citizen service portals like e-District or DigiLocker
By enabling interoperability, legal documents related to judgment renewals could automatically be synced and validated across platforms. This would dramatically improve turnaround time and reduce administrative overhead.
How Countrywide Process Can Help Lead the Way?
At Countrywide Process, we’ve successfully implemented e-recording services and systems that support seamless e-record renewal of judgment in complex jurisdictions like California. These successes provide a roadmap for how such services could be scaled and adapted in emerging legal markets like India.
Here’s how we could contribute to India’s journey:
Customized E-Recording Portals: Tailored to India’s multilingual and multi-jurisdictional needs.
Training and Onboarding Programs: For legal professionals, court clerks, and public users.
Cross-Platform API Development: Enabling interoperability between courts, registrars, and digital citizen platforms.
Legal Workflow Automation: From submission to verification, all steps streamlined under one roof.
By leveraging our technological know-how and user-first approach, we can help India develop robust e-file and e-record renewal of judgment systems that meet global standards.
Toward a Unified Digital Legal Future:
India’s path to modernization is complex but achievable. Creating uniformity in digital legal services like e-record renewal of judgment will require a collaborative effort between central and state governments, judiciary bodies, and private legal tech providers.
Here are key steps that can drive this change:
Develop a National E-Recording Framework Spearheaded by the Ministry of Law and Justice, this would set standards for digital filings, data formats, and verification protocols.
Mandate Interoperability Standards All new digital legal tools should be required to integrate with state and national platforms using secure APIs and open data protocols.
Pilot Cross-State Platforms Launch pilot projects across multiple jurisdictions to test standardized platforms and refine workflows.
Engage Private Partners Like Countrywide Process Collaborate with proven service providers to develop scalable, secure, and user-friendly systems.
Conclusion: Bridging the Gap Between Innovation and Inclusion
Digitizing the e-record renewal of judgment process is a step in the right direction. But if India truly wants to benefit from digital transformation in the legal sector, it must prioritize standardization and interoperability. Only then can digital tools provide equal access, consistent service delivery, and reliable legal outcomes for all.
Countrywide Process is ready to support this transformation, bringing years of experience and a commitment to accessible legal tech. Whether it’s through developing adaptable platforms or empowering users with education and support, we believe the future of law in India should be both digital and equitable.
Visit Countrywide Process to see how we’re making legal filings faster, smarter, and more accessible worldwide.
#ERecordRenewalOfJudgment#ERecordingServices#EFileAndERecordRenewalOfJudgment#LegalTechIndia#DigitalJustice#LegalInnovation#CourtTech#JudgmentRenewal#OnlineLegalServices#LegalReformIndia#Interoperability#StandardizedLegalSystems#DigitalLegalTransformation#CountrywideProcess#LegalAccessibility#e recording services#e recording companies#efile and erecord renewal of judgement#erecord renewal of judgement
0 notes
Text
BIM Software Solutions for Modern HVAC Applications
As the HVAC industry continues to evolve in 2025, Building Information Modeling (BIM) has become an indispensable tool for professionals seeking to optimize design, installation, and maintenance processes. For HVAC engineers, contractors, and technicians, selecting the right BIM software can significantly impact project efficiency and outcomes. Let’s explore the most effective BIM solutions for…
#3D modeling#augmented reality#Autodesk Revit#automation#Bentley AECOsim#BIM#BIM workflows#building information modeling#Building performance#building systems#clash detection#cloud collaboration#cooling loads#decision matrix#digital twin#duct design#energy analysis#Energy efficiency#fabrication documentation#Graphisoft ArchiCAD#heating loads#hvac#HVAC design software#HVAC engineering#interoperability#mechanical engineering#mechanical systems#MEP#MEP coordination#mixed reality
0 notes
Text
Metaverse 2.0: What's New & Is It Finally Rising?


Metaverse 2.0: What's New and Is It Finally Taking Off?
Metaverse 2.0: What's New & Is It Finally Rising? Metaverse 2.0: What's New & Is It Finally Rising?. Once hailed as the next digital frontier, the metaverse faced skepticism after its initial hype faded. But in 2025, Metaverse 2.0 has emerged with renewed promise, thanks to major technological upgrades, stronger use cases, and real-world integration. So, what’s changed, and is it finally gaining real traction? What’s New in Metaverse 2.0? 1. Interoperability & Standards Metaverse 2.0: What's New & Is It Finally Rising?. One of the biggest shifts is the move toward interoperability. Unlike the fragmented ecosystems of the past, Metaverse 2.0 promotes cross-platform avatars, assets, and experiences, thanks to open standards like USD (Universal Scene Description) and new Web3 protocols. 2. Mixed Reality Integration Blending the physical and digital has become seamless. Advanced AR/VR headsets like Apple Vision Pro and Meta Quest 3 offer ultra-realistic immersion with intuitive control systems. Mixed reality now supports remote work, education, retail, and social hangouts with real-world context. 3. AI-Driven Experiences AI powers smarter avatars, realistic NPCs, and dynamic virtual environments. Virtual worlds adapt in real-time based on user behavior, making experiences more interactive and personalized. 4. Real-World Utilities Metaverse 2.0: What's New & Is It Finally Rising?. Metaverse 2.0 is less about fantasy worlds and more about utility. Brands, educators, and governments use it for training, virtual stores, remote healthcare, and virtual tourism, creating tangible value beyond entertainment. Why It Might Finally Be Taking Off - Enterprise Adoption: Companies like Microsoft, NVIDIA, and Accenture are investing in enterprise-grade virtual spaces for collaboration and simulation. - Economic Incentives: Digital assets, NFTs, and token economies are reimagined with real utility, promoting more sustainable models. - Consumer Readiness: With improved hardware and lower entry costs, more users are joining virtual platforms for work, play, and commerce. The Road Ahead While Metaverse 2.0 isn’t a fully mature ecosystem yet, it’s closer to practical mainstream adoption than ever before. As infrastructure, accessibility, and user demand continue to align, the metaverse might finally move beyond buzzword status and become a fundamental layer of our digital lives. Read the full article
#AIinMetaverse#AppleVisionPro#AR/VRTechnology#Collaboration#DigitalTransformation#EnterpriseMetaverse#FutureofMetaverse#Healthcare#Infrastructure#Interoperability#MetaQuest3#Metaverse2.0#MetaverseAdoption#MetaverseforBusiness#MetaverseInnovation#MetaverseNews#MixedReality#NFTUseCases#TechTrends2025#VirtualCollaboration#VirtualReality2025#Web3
0 notes