Text
3 notes
·
View notes
Text

PERHAPS MORE than any other book published in recent years, The Palestine Laboratory demonstrates why Israel is a menace, not only to Palestinians and other Arabs whose countries it has invaded or bombed at one time or another, but really to people around the globe. Anyone who criticizes or mobilizes against their own authoritarian governments will likely have to contend with an Israeli weapon or technology designed to enhance government control over them and make dissent costly, if not impossible.
READ MORE https://www.wrmea.org/middle-east-books-and-more/the-palestine-laboratory-how-israel-exports-the-technology-of-occupation-around-the-world.html
Antony Loewenstein: Israel Is Testing New Weapons on Gaza as Arms Dealers Profit from Gaza War
NOVEMBER 14, 2023 Worldwide protests calling for a ceasefire are drawing attention to the role of weapons manufacturers and distributors supplying machinery to Israel’s assault on Gaza, with demonstrators blocking shipping tankers and entrances to weapons factories, and unionized workers refusing to handle military materiel over the war in Gaza. There is “a growing public awareness and anger” about the global connection between Western powers and the Israeli military industry, says Antony Loewenstein, who has investigated how Israeli weaponry and surveillance technology are used on Palestinians and exported around the world. “Israel is already, as we speak … live-testing new weapons in Gaza,” says Loewenstein. He also discusses what he characterizes as the “intelligence” and “political” failures of the October 7 Hamas incursion.
LISTEN READ MORE Transcript https://www.democracynow.org/2023/11/14/israel_weapons
LINKS
"The Palestine Laboratory: How Israel Exports the Technology of Occupation Around the World"
19 October 2023
"Although we had always heard that people could be monitored through cell phones, we did not imagine that this could happen to us." +"When people ask us for something, we cannot afford to ask questions about ideology. The only type of regime that Israel would not aid would be one that is anti-American. Also, if we can aid a country that it may be inconvenient for the US to help, we would be cutting off our nose to spite our face not to.’ There’s rarely been a more honest appraisal of Israel’s entire weapons industry."
ISRAEL’S INSURANCE POLICY =>>"Israel’s arms sector, and its spyware industry in particular, is an insurance policy against political headwinds that may develop against the occupation."
"The lack of serious oversight benefits one actor in particular – Israel. As the lead exporter of these tools, the state is at the forefront of the intrusion technology industry. Founded in 2010, NSO Group Technologies Ltd is just one firm among a wider ecosystem of Israeli cyber-weapons companies. Of the 75 governments that have procured spyware and digital forensic technologies worldwide, 56 bought them from firms that are either based in or connected to Israel, such as NSO Group, Cellebrite, Cytrox and Candiru. These deals are all monitored and approved by the Israeli Ministry of Defence.
For Israel, spyware is not just a highly lucrative industry, but a strategic weapon to curry diplomatic favour."
4 notes
·
View notes
Text
As the Israel-Hamas war escalated this week, WIRED looked at the conditions that contributed to Israel's intelligence failures ahead of Hamas' initial attack last Saturday, as well as the hacktivism and digital mayhem that has subsequently sprung up around the kinetic war. The situation has led to a torrent of misinformation across global discourse, particularly on the social media platform X (formerly Twitter), where fake photos, old videos, and video game footage have exploded on an unprecedented scale.
X’s Trust and Safety team claims it has been working to address the situation, but company CEO Elon Musk has been “posting through it,” sharing conspiracies and engaging with QAnon discourse on the platform. The chaotic situation on X has been difficult for the average user to keep up with. In one case, a graphic Hamas video that Donald Trump Jr. shared on the platform actually turned out to be legitimate, even though it seemed at first look like it might have been part of the broader deluge of misinformation. And beyond just X, rumors of a “Global Day of Jihad” on Friday unleashed a dangerous wave of disinformation across digital platforms—one that threatened to cross into real-world violence.
With the trial of FTX founder Sam Bankman-Fried in full swing this week, WIRED took a deep look at the day someone stole hundreds of millions of dollars from the ill-fated cryptocurrency exchange as it was declaring bankruptcy. And new evidence released by researchers this week indicates that the stolen FTX funds went through a chain of intermediaries that eventually led to Russia-linked money launderers.
As chaos in the United States House of Representatives continues over Republicans' inability to deal with far-right hardliners and elect a new speaker, WIRED reported that Republican Party leaders have imposed cell phone bans in an attempt to keep backroom dealmaking under wraps. The United Nations' top internet governance body may host its next two annual meetings in countries known for repressive digital policies and abusive information control, which risks normalizing internet censorship. And white supremacist “active clubs” are gaining traction in part through communication on the messaging app Telegram.
Meanwhile, Google announced this week that it will make the more secure password replacement known as passkeys the default login option for its personal account holders as part of the company's efforts to promote adoption of the technology. And a new internet protocol vulnerability known as “HTTP/2 Rapid Reset” impacts virtually every web server around the world and will take years to stamp out, exposing some sites and digital services to denial of service attacks long-term.
And there's more. Each week we round up the security and privacy news that we didn’t cover in depth ourselves. Click the headlines to read the full stories. And stay safe out there.
Vietnam Used Predator Spyware to Target US Congress
Notorious high-end commercial spyware like Pegasus and Predator has been used over the past decade to target human rights activists, protesters, and journalists. But a foreign nation using it to target the smartphones of US members of Congress represents a rare and brazen new appearance of those notorious tools. On Monday The Washington Post, along with a consortium of more than a dozen international media outlets, revealed that the Vietnamese government used that Predator spyware, distributed by the surveillance firms Cytrox and Intellexa, to target at least four members of Congress—representative Michael McCaul and senators Chris Murphy, John Hoeven, and Gary Peters—as well as Asia-focused experts at US think tanks and several journalists that include CNN’s lead national security reporter, Jim Sciutto.
In the hacking campaign, those individuals were targeted in replies on X (formerly known as Twitter) that included links to websites that would have infected their iOS or Android phones with the Predator spyware. That tactic appears to have been both reckless and unsuccessful: Anyone else who saw the tweets and clicked on the link would have been infected too, and the highly public nature of that infection attempt helped researchers and reporters to analyze the scope and targeting of the campaign. The attempted espionage was timed to US government meetings with Vietnamese officials, and it appears to have been aimed at understanding US intentions in the meeting, particularly related to relations with China.
The media consortium, along with security researchers from Amnesty International and Google’s Threat Analysis Group, were able to show Vietnam’s connection to the Predator hacking campaign through documents they obtained that detail the Vietnamese government’s contract with Intellexa in 2020, and later an extension of the deal to allow the use of the Predator software. The internal documents went so far as to capture the response of Intellexa’s founder, Israeli former military hacker turned entrepreneur Tal Dilian, when the deal was announced: “Wooow!!!!” Vietnam’s government would later target French officials with Predator before this year’s campaign targeting US congressmen.
Hamas Raised Millions in Crypto Ahead of Attacks
Despite efforts by Israel and other nations to cut off funding to Hamas in recent years, the group raised millions of dollars worth of cryptocurrency before the past weekend’s attack that killed more than a thousand Israelis. An analysis by The Wall Street Journal found that Hamas, Palestinian Islamic Jihad, and Hezbollah had collectively raised hundreds of millions in crypto over the past several years, with $41 million going to Hamas specifically. Given that the Journal learned of that funding in part through Israeli seizures of crypto accounts, however, it’s not clear how much of that money was frozen or seized versus how much might have actually been successfully laundered or liquidated by Hamas and other groups.
In response to the weekend’s attacks, the Israeli government and the world’s largest crypto exchange, Binance, both announced that a new round of Hamas crypto accounts had been frozen. Though crypto has helped Hamas and other groups move funds across borders, its traceability on blockchains has presented a challenge for designated terrorist groups. In 2021, for instance, Hamas asked its supporters to stop making donations via cryptocurrency, due to the ease of tracking those transactions and unmasking contributors.
Exxon Used Hacked Documents to Counter State Investigations
Last year, Reuters reporters Chris Bing and Raphael Satter published an investigation into Aviram Azari, an Israeli private investigator who is accused of using mercenary hackers to gather intelligence on the critics of major corporations involved in lawsuits against them.
Now, prosecutors in the Southern District of New York, where Azari has been convicted on criminal charges, have filed a sentencing memo that notes that activists’ communications stolen by Azari’s hackers were later used by Exxon in the company’s attempts to head off investigations and lawsuits by state attorneys general. The memo still doesn’t name Exxon as Azari’s client, but it implicitly suggests a link between the company and Azari: Prosecutors point in their memo to leaks of climate activists’ private emails to media, which were later cited by Exxon in their responses to state attorney generals as evidence of underhanded tactics by activists as they tried to prove that Exxon knew and covered up the role of fossil fuels in climate change. A Massachusetts lawsuit against Exxon that resulted from the state’s investigation is ongoing.
Magecart Cybercrime Crew Skims Cards With New 404 Trick
Internet giant Akamai warned this week that the infamous Magecart hacker crew, long focused on credit card fraud, has developed a clever new technique for spoofing credit card payment fields. The hackers managed to hide their malicious scripts in the 404 “page not found” error pages of ecommerce sites, then trigger those pages to load a spoofed payment field that impersonates a checkout page to steal credit card information. “The idea of manipulating the default 404 error page of a targeted website can offer Magecart actors various creative options for improved hiding and evasion,” warned Akamai researcher Roman Lvovsky. Akamai noted that the technique was used on the website of significant brands in the food and retail industries but declined to name them.
5 notes
·
View notes
Text
🔻تحقيق
"تال ديليان"
ضابط الموساد الإسرائيلي، صاحب إمبراطورية تقنيات التجسس
لقب ببائع التجسس، وذلك لبيعه كل تقنيات التجسس التي صممها هو وفريقه لاغلب الدول العربية والأجنبية
زبائنه من جميع انحاء العالم
فمن هو
ومن هي الحكومات العربية التي اشترت منة

اولاً
حسب ما نشره على لنكد ان فيصف نفسه على انه خبير استخبارات، ومبتكر تقني، ورجل أعمال متسلسل من تل ابيب
ولكن الصورة اكبر
فهو عقيد متقاعد من وحدة الكوماندوز النخبة الاسرائيلية (التدخل السريع)
تولى رتبة رفيعة في شعبة الاستخبارات العسكرية امان
وكان قائد للوحدة التكتولوجية 81
تخصص في ادوات واجهزة المراقبة
واتخذ قبرص مقراً له وانشاء شركة سيركلز للتبع الهواتف الذكية
كما انه صاحب العديد من الشركات السيبرانية
ومنها شركة Intellexa والتي تقع في شمال مقدونيا
واعتبر نفسه غير خاصع لاي وزارة فقام ببيع البرنامج للعديد من الدول ومنها بعض الدول العربية
شركةIntellexaقامت بتحالف تحت اسم تحالف النجوم
في عالم الذكاء الإلكتروني والعالم الرقمي
تشمل الشركات داخل التحالفWiSpeaوهي شركة جرائم إلكترونية يمكنها اختراق الهواتف وتحديد المواقع الجغرافية للأهداف من خلال Wi-Fi، والتي أسسها ديليان
وستجد Intellexa اسمها يتكرر مع الدول العربية
كما انه ادار شركة cytrox التي دخلت التحالف
وايضاً قام بانشاء برنامج بريداتور الشهير
مرتبط بعدة اجهزة وظيفته اختراق الهاتف المحمول من خلال مكالمة هاتفية
وتم بيع هذا البرنامج للعديد من الدول العربية
والتي كان اولها السعودية التي استخدمته على جمال خاشقجي
وسلطنة عمان اشترت أيضا
تال له العديد من الشركاء

لكن ابرزهم ابراهاك شحاك ايفني احد اثرياء اليهود في قبرص
استثمر معه في جميع منتجات التجسس
من طائرات الدرون وطائرات بدون طيار واجهزة تصنت صوتية وغيرها الكثير، وساهم ايضاً في تطوير شركة WiSpear باستخدام شاحنة مراقبة خاصة بالتصنت الفيديو التالي
من فوربس بتحقيق من صحفيين سريين تنكروا على هيئة زبائن له
يستعرض فيه سيارته المذكورة
ثمنها 9 مليون دولار
ويذكر ان الاجهزة داخل السيارة متعددة المهام
واهم وظائفها اختراق الهاتف الذكي والمكالمات والرسائل
وحتى المحمي منها بتشفير قوي مثل رسائل الواتساب
محمد حمدان دقلو قائد قوات الدعم السريع بالسودان كان له شراكة معه وقام باستيراد المعدات التي تحملها تلك السيارة والعديد من الاجهزة المتطورة الاخري داخل طائرة خاصة
واشتراها منه بملايين الدولارات

وايضاً
استخدم تلك السيارة بمساعدة زوجته لاختراق هواتف شخصيات مهمة في مطار لارنكا
وقاموا بفتح تحقيق معه ومصادرة السيارة والاجهزة المضبوطة
وايضاً كيف ستفوت الامارات تلك الفرصة
فبرنامج بريداتور طورته شركة "إنتليكسا" التي أسسها تال اتخذت من الامارات مقراً لها
وكل عمليات التجسس التي يتم النشر عنها داخل الامارات ستجد شركة انتليكسا وتال خلفها
وتم استخدامة

كذلك مصر وقطر لم يفوتوا الفرصة
فقد تم شراء كل ما يخص تلك التقنيات الحديثة من تال داليان
ومعروف ��د من تم استخدامها

ولم تسلم بنجلاديش ثالث أكبر دولة إسلامية في العالم من الامر
فقامت بشراء كافة اجهزته المتطورة لاعتراض حركة المرور على الهاتف المحمول والإنترنت والمكالمات وغيرها

اي شئ خاطئ في اي دولة عربية تأكد انك ستجد وراءه اصابع اسرائيلية
كيف تعايش الحكام العرب مع نفوسهم عندما تعاونوا مع كل اسرائيلي مثل تال ديليان وغيره ضد شعبهم
لك ان تتخيل الفرحة الاسرائيلية
لك ان تتخيل النجاح الاسرائيلي بدعم حكام العرب
ويبقى السؤال
متى سينتهي كل هذا العبث
_____ ____منقول عن ا. عائشة السيد .. منصة X

T
6 notes
·
View notes
Text
On 5 October 2023, a major global investigation – the “Predator Files” – was published exposing the proliferation of surveillance technologies around the world and the failure of governments and the European Union (EU) to properly regulate the industry. The Security Lab at Amnesty International is a technical partner in the “Predator Files”, a project coordinated by the European Investigative Collaborations (EIC) media network into the Intellexa alliance, the makers and marketers of the Predator spyware. As part of this collaboration, the Security Lab has reviewed technical documentation, marketing material and other records obtained by Der Spiegel and Mediapart – who are part of EIC – which shed light on the ecosystem of surveillance products offered by the Intellexa alliance. [...] The Intellexa group of companies was founded in 2018 by the former Israeli army officer Tal Dilian and several of his associates, which sells the Predator spyware. Since 2020, it has been controlled by the holding company Thalestris, which is based in Ireland. The Intellexa group’s main companies are Cytrox (North Macedonia), which develops the Predator spyware system, WiSpear (Cyprus), specialist in Wi-Fi interception, and Senpai Technologies (Israel), a specialist in open-source intelligence and the creation of virtual avatars.
Wow you know the spy service is going to be top-notch if it's from israelis, the best intelligence in the world
5 notes
·
View notes
Text
Predator Spyware Linked to Madagascar’s Government Ahead of Election
The Madagascar government likely used the Cytrox-developed Predator spyware to conduct political domestic surveillance ahead of the country’s presidential election, according to research by Sekoia. French threat intelligence firm Sekoia’s latest technical analysis of Cytrox’s infrastructure was prompted by recent revelations that Predator had been installed on the iPhone of the former Egyptian MP…
View On WordPress
0 notes
Text
Cher Mr. Clermont,
Faire face n'est pas toujours simple, pour vous faciliter la tâche avec les jeunes IHEDN et accroître votre sphère d'influence auprès de la génération Z (the digital natives), veuillez trouver ci-dessous, une note de préparation pour une intervention incroyable !
Avez-vous un compte BeReal ? C'est une appli 💯 % made in France.
Bien à vous
P.S.: pour marquer des points, n'oubliez pas de leur citer l'exemple du Hallyu, la plus puissante vague de soft power au monde, financée par les conglomérats coréens, les Chaebols. Pensez à télécharger Line et KakaoTalk.
youtube
Appendix:
The kind of offensive tool, which I would have had to analyze if I worked at the DGSE, in order to make similar ones with the French elite red team, for different targets than the general population, of course. However, there's always the unknown risk that an offensive tool made for a specific purpose can be leaked and used for different intents by bad actors. This ethical question on responsibility, was too morally conflicting for me.
I declined to go further, because I prefer to sleep well than to have nightmares.
###
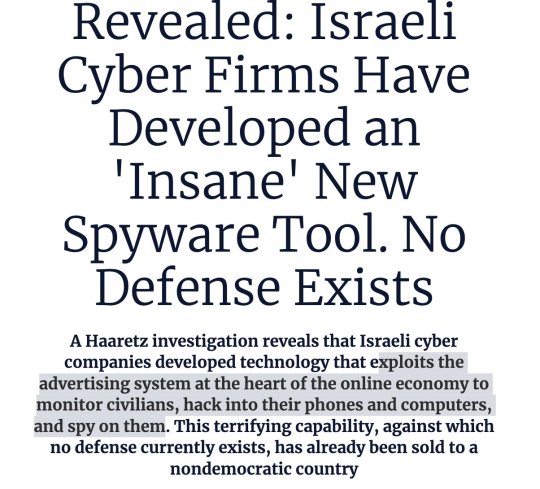
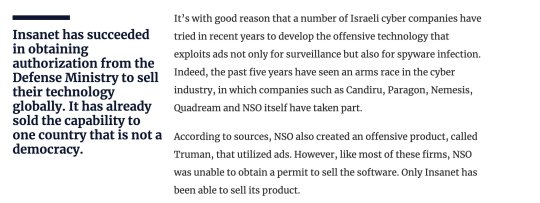
Block ads on your networks now.
The system designed to follow us around the net with ads is now a blinking national security & human rights threat. There is now a growing ADINT industry, both in Israel and outside, that is increasingly focused on HLS and is growing increasingly offensive - and this despite Israeli regulators hoping the exact opposite would happen.

Mastercard knows where you shop, on what day, and how much you spend - and it sells that data widely to third parties like data brokers and advertisers.
"A 2015 MIT study found...Using an anonymized data set of more than 1 million people’s credit card transactions made over 3 months, MIT researchers could identify an individual 90% of the time using the transaction information of just 4 purchases."
🚨🚨 BIG : WE URGE ALL USERS TO UPDATE THEIR Apple devices urgently.
Citizenlab in coordination with Google’s TAG team found that former Egyptian MP Ahmed Eltantawy was targeted with Cytrox’s Predator spyware through links sent via SMS and WhatsApp.
How did this happen? Eltantawy’s Vodafone Egypt mobile was also targeted using network injection. While visiting websites not using HTTPS, a device at the border of Vodafone Egypt’s network redirected Eltantawy to a malicious website to infect his phone with Predator spyware.
The researchers at Citizen lab link the network injection attack to the Egyptian government with high confidence since Egypt is a known user of Cytrox's Predator spyware and the malware was supplied by network injection from a device physically located inside Egypt.
0 notes
Text
US Gov adds surveillance firms Cytrox and Intellexa to Entity List for trafficking in cyber exploits
http://i.securitythinkingcap.com/SsQJFl
0 notes
Link
[ad_1] The U.S. Commerce Department has placed two European-based Israeli-owned spyware companies on its trade blacklist, citing national security concerns. Intellexa S.A. in Greece and its entity Intellexa Limited in Ireland, and Cytrox AD in North Macedonia, along with its entity Cytrox Holdings Crt in Hungary, were added to the technology export blacklist, the Commerce Department said in a July 18 press release. The blacklisting means the companies will no longer be able to conduct business or make transactions with American companies, significantly reducing their ability to access commodities, software, and technology that they could use to develop surveillance tools that could be misused, or conduct activities contrary to the national security or foreign policy interests of the United States. Officials said the move was based on a determination that the companies had engaged in “trafficking in cyber exploits used to gain access to information systems, threatening the privacy and security of individuals and organizations worldwide.” The companies join Israeli-owned, Tel Aviv-based technology company Candiru and NSO Group, which has faced continuous criticism over its Pegasus spyware and its alleged spying activities on the blacklist. Both companies were placed on the list in 2021. “The proliferation of commercial spyware poses distinct and growing counterintelligence and security risks to the United States, including to the safety and security of U.S. government personnel and their families,” the Commerce Department said. Department of Commerce building in Washington on April 10, 2023. (Madalina Vasiliu/The Epoch Times) Repression, Human Rights Abuses “The misuse of these tools globally has also facilitated repression and enabled human rights abuses, including to intimidate political opponents and curb dissent, limit freedom of expression, and monitor and target activists and journalists.” According to its website, Intellexa develops and integrates technologies to “empower LEAs [law enforcement agencies] and intelligence agencies to help protect communities.” Cytrox does not appear to have a website. Both companies have been linked to a number of alleged surveillance incidents, according to reports. Cytrox’s “predator” spyware was used to hack the mobile phone of Ayman Nour, an Egyptian politician living in exile in Turkey, and an unnamed Egyptian television journalist, according to the Citizen Lab at the University of Toronto, which studies human rights and global security. Additionally, one of the company’s products was reportedly used by the Greek government to hack the mobile phone of a former Meta security executive. Meanwhile, Intellexa was fined 50,000 euros ($56,129) by the Data Protection Authority in Greece in January for failing to cooperate with an ongoing investigation into the use of spyware in the country that was allegedly used to spy on high-ranking Greek officials. Biden Admin Cracking Down on Spyware In a statement at the time, the Hellenic Data Protection Authority (HDPA) said it had “performed an on-site inspection at Intellexa’s premises but such premises were completely empty and without a functional network infrastructure or IT system.” “Additionally, the HDPA noted that Intellexa had failed to provide all the information requested by the HDPA during the auditing process,” the statement read. The relationship between Intellexa and Cytrox is unknown. “We remain laser-focused on stemming the proliferation of digital tools for repression,” said Bureau of Industry and Security Under Secretary Alan Estevez in a July 18 statement. “Considering the impact of surveillance tools and other technologies on international human rights, I am pleased to announce these additions to our Entity List.” The latest bans on Intellexa and Cytrox are part of a “government-wide effort to counter the risks posed by commercial spyware,” the Commerce Department said. In March, the White House issued an executive order prohibiting U.S. government use of commercial spyware that poses risks to national security or has been misused by foreign actors to enable human rights abuses. The Biden administration has also released guiding principles on government use of surveillance technologies and is actively working with the governments of Australia, Canada, Costa Rica, Denmark, France, New Zealand, Norway, Sweden, Switzerland, and the UK, to ensure strict domestic and international controls regarding the misuse of commercial spyware. [ad_2]
0 notes
Text
U.S. Government Blacklists Cytrox and Intellexa Spyware Vendors for Cyber Espionage
The Hacker News : The U.S. government on Tuesday added two foreign commercial spyware vendors, Cytrox and Intellexa, to an economic blocklist for weaponizing cyber exploits to gain unauthorized access to devices and "threatening the privacy and security of individuals and organizations worldwide." This includes the companies' corporate holdings in Hungary (Cytrox Holdings Crt), North Macedonia (Cytrox AD), Greece http://dlvr.it/SsPLyL Posted by : Mohit Kumar ( Hacker )
0 notes
Text
Στην μαύρη λίστα των ΗΠΑ οι δυο εταιρείες του λογισμικού Predator
Το Υπουργείο Εμπορίου των ΗΠΑ πρόσθεσε την Τρίτη δύο ευρωπαϊκές εταιρείες παρακολούθησης στη μαύρη λίστα του οικονομικού εμπορίου στο πλαίσιο των προσπαθειών της κυβέρνησης του προέδρου Τζο Μπάιντεν να αντιμετωπίσει την κατάχρηση λογισμικών παρακολούθησης. Το αρμόδιο τμήμα της αμερικανικής κυβέρνησης πρόσθεσε την εταιρεία παρακολούθησης Cytrox με έδρα την Ουγγαρία και την εταιρεία…
View On WordPress
0 notes
Text
1 note
·
View note
Text
Στην μαύρη λίστα των ΗΠΑ οι δυο εταιρείες του λογισμικού Predator
Το Υπουργείο Εμπορίου των ΗΠΑ πρόσθεσε την Τρίτη δύο ευρωπαϊκές εταιρείες παρακολούθησης στη μαύρη λίστα του οικονομικού εμπορίου στο πλαίσιο των προσπαθειών της κυβέρνησης του προέδρου Τζο Μπάιντεν να αντιμετωπίσει την κατάχρηση λογισμικών παρακολούθησης. Το αρμόδιο τμήμα της αμερικανικής κυβέρνησης πρόσθεσε την εταιρεία παρακολούθησης Cytrox με έδρα την Ουγγαρία και την εταιρεία…
View On WordPress
0 notes
Text
On July 18, the U.S. Commerce Department added two European commercial spyware firms—Cytrox and Intellexa—to its export controls blacklist due to privacy violations and other rights abuses. Both entities are controlled by former Israeli intelligence officer Tal Dilian and registered in multiple European jurisdictions, including Greece, Hungary, Ireland, and North Macedonia. They have been implicated in a variety of wrongdoings, including a major scandal in Greece, where Cytrox’s Predator software was used to hack journalists’ and opposition politicians’ phones.
The blacklisting is not a one-off. In fact, it represents a continuing effort by the U.S. government to curb the commercial spyware industry. The designation of the two companies is the first major initiative on spyware since U.S. President Joe Biden signed an executive order in March that limits federal agencies’ use of commercial spyware, and it sends a clear message that selling high-grade surveillance products to abusive governments will have consequences. Cytrox and Intellexa’s designation on the entity list imposes severe licensing requirements on the companies, effectively banning them from transactions with U.S. companies and accessing the U.S. market.
Getting to this point has been a struggle. The global spyware industry is a lucrative business; both governments and private actors have shown an insatiable appetite for targeted surveillance products. According to my research, at least 74 governments around the world have contracted with commercial firms to acquire spyware or data extraction technology.
The web of companies supplying these products is diverse. Although Israeli companies dominate the global export of spyware, European and U.S. companies are active market participants as well. Companies at the top end of the spyware market—such as Cytrox, Intellexa, and NSO Group, the Israeli market leader under U.S. sanctions since 2021—offer cutting-edge tools, including so-called zero-click hacks. These are malware programs that infiltrate devices without the user having to take any action to allow it in, such as opening an email or clicking on a bad link.
Although many of the abuses are linked to authoritarian regimes, such as the Saudi and Emirati governments’ reported use of NSO’s Pegasus malware to track the journalist Jamal Khashoggi before his assassination, democracies do not have clean hands, either. European countries such as Cyprus, Greece, and Spain have deployed spyware against civil society, independent journalists, and opposition politicians, as have illiberal democracies such as Hungary.
That is why U.S. leadership in reining in the spyware industry is such welcome news. Quite simply, few other countries have shown much interest in taking on commercial spyware firms, despite a parade of public scandals revealing major rights violations. The Biden administration started pursuing a measured strategy against spyware violators in 2021, when the Commerce Department put four spyware firms in Israel, Russia, and Singapore on its list of sanctioned entities, including NSO. Then, Biden signed the executive order in March of this year. In parallel, the United States also signed a joint declaration with 10 other countries against the misuse of spyware and establishing procedures to counter malicious cyberactivities. With this month’s blacklisting, the White House is sending another signal that it means business when it comes to reining in spyware abuses.
Yet for Washington’s actions to truly make a dent in the commercial spyware market, it needs other countries to join the fight—starting with Europe. It shouldn’t come as a surprise that the two penalized spyware firms are based there. While most European countries have tough rules on the books to regulate spyware, enforcement has been lax. My research shows that a number of European spyware firms sell intrusive surveillance technology in their home markets and overseas, including Italy’s Memento Labs and Tykelab/RCS Lab, as well as Austria’s DSIRF. Moreover, European governments continue to deploy spyware to unlawfully surveil their citizens. This includes a major scandal in Spain targeting Catalan independence leaders and politicians, as well as reported abuses by Hungarian and Polish authorities. In a draft report submitted by Sophie in ‘t Veld, rapporteur for the European Parliament’s Committee of Inquiry to investigate the use of Pegasus and other spyware (PEGA), she writes that “the abuse of spyware is a severe violation of all the values of the European Union, and it is testing the resilience of the democratic rule of law in Europe.”
So what can be done? First, the European Commission could do far more to address the spyware problem within the EU. Currently, the European Parliament is the only pan-European institution tackling this problem, but it lacks executive power and faces roadblocks at every turn. Very little will change unless the EU undertakes a more serious institutional push to break through obstructionism by EU member states. The commission has so far refrained from pressuring member governments to tighten their policies, highlighting Brussels’s limited ability or interest in fighting the problem. It would make a big difference if the commission sent a clear signal that cracking down on spyware is a priority. There is little reason the EU could not take steps similar to those implemented by the United States.
Second, democracies can be far more stringent when it comes to curbing their own use of spyware. Despite public scandals, democratic governments continue to show interest in acquiring intrusive surveillance tools. A good example is India: Just three days after Biden signed his March executive order on spyware, the Financial Times reported that Modi’s government had released a $120 million bid for new spyware contracts. Notably, Indian officials were concerned about the “PR problem” from NSO’s Pegasus and were looking for alternative companies from which to purchase surveillance capabilities. While preventing autocratic leaders from obtaining spyware is a formidable challenge, there are far fewer excuses for democratic governments to be using these tools, whether that’s in Greece, India, Mexico, or Spain. Citizens in democracies should demand better behavior out of their governments, especially when it comes to unlawfully deploying surveillance tools against journalists and civil society. Also needed is diplomatic pressure against culpable governments. In the case of Intellexa and Cytrox, the United States and its partners may not have significant leverage to wield against Hungary, where one of the Cytrox companies is based, but pressure could be exerted against other countries hosting these firms and their various entities. Already, there are reports that in response to Intellexa’s listing, the company’s Irish auditor has resigned.
Third, it is important not to overlook the Israel angle. Many notorious spyware firms are connected to Israel’s security establishment. Dilian, for example, cut his teeth working as a commander for the Israeli Defense Forces’ Unit 81, a crucible of advanced military technology responsible for developing intelligence products for special operations units and other defense agencies. Israel is a major hub and protector of the spyware industry. When other countries attempt to probe Israeli firms, they are often stonewalled. In July, a Spanish judge investigating the alleged hacking of ministers’ phones with Pegasus spyware was forced to close the court’s inquiry “due to the complete lack of legal cooperation from Israel.” There is no reason the Israeli government cannot follow the United States’ lead and enforce more stringent standards on non-military applications, rein in exports, and crack down on unaccountable companies. Israeli Prime Minister Benjamin Netanyahu’s upcoming visit to the White House is a good opportunity for U.S. officials to have a candid conversation about regulating abusive surveillance practices and the next steps each country can take.
The White House’s export control designation of Cytrox and Intellexa should be commended. It reinforces the administration’s ongoing commitment to curbing spyware violations. But the United States should not be forced to act alone: Europe, Israel, and other jurisdictions should follow the Biden administration’s lead and take meaningful steps to restrict the behavior of mercenary spyware firms.
5 notes
·
View notes
Text
Στην μαύρη λίστα των ΗΠΑ οι δυο εταιρείες του λογισμικού Predator
Το Υπουργείο Εμπορίου των ΗΠΑ πρόσθεσε την Τρίτη δύο ευρωπαϊκές εταιρείες παρακολούθησης στη μαύρη λίστα του οικονομικού εμπορίου στο πλαίσιο των προσπαθειών της κυβέρνησης του προέδρου Τζο Μπάιντεν να αντιμετωπίσει την κατάχρηση λογισμικών παρακολούθησης. Το αρμόδιο τμήμα της αμερικανικής κυβέρνησης πρόσθεσε την εταιρεία παρακολούθησης Cytrox με έδρα την Ουγγαρία και την εταιρεία…
View On WordPress
0 notes
Text
Στην μαύρη λίστα των ΗΠΑ οι δυο εταιρείες του λογισμικού Predator
Το Υπουργείο Εμπορίου των ΗΠΑ πρόσθεσε την Τρίτη δύο ευρωπαϊκές εταιρείες παρακολούθησης στη μαύρη λίστα του οικονομικού εμπορίου στο πλαίσιο των προσπαθειών της κυβέρνησης του προέδρου Τζο Μπάιντεν να αντιμετωπίσει την κατάχρηση λογισμικών παρακολούθησης. Το αρμόδιο τμήμα της αμερικανικής κυβέρνησης πρόσθεσε την εταιρεία παρακολούθησης Cytrox με έδρα την Ουγγαρία και την εταιρεία…
View On WordPress
0 notes