#databse error
Explore tagged Tumblr posts
Text
How to Fix Error establishing a database connection for any WP-CLI Command For MAMP
How to Fix Error establishing a database connection for any WP-CLI Command For MAMP
Sometimes while running WP-CLI commands, you will get following error Error establishing a database connection So this can be fixed by very simple method. Please watch the video for how to fix that.

View On WordPress
0 notes
Text
I HAVE DONE IT!
A BACKROOMS DATABASE! I was doing it wrong all along... I was using batch, when I should have been using python, and it's more error faulty, more organized, and you can look to see if it has already been added! It is on version 1.0 BETA
I am so proud of it! You can find it onn itch.io and github below!
Itch.io:
Github:
I was SO PROUD of it, that it's only a few KB, and I decided to post it! It only took me 2 weeks to actually complete the thing!
And, every week, I add a minimum of 10 levels, objects, or entities! And, eventually it will be on gitlab, so people can expand it!
#python#backrooms#the backrooms#developer#tokyn blast#itch io#github#database#proud#beta#backrooms database#version 1#v1.0#10#backrooms level#backrooms object#backrooms entity#backrooms archive
11 notes
·
View notes
Text
Educational Services Email Databse
The educational industry is made up of institutions that provide instruction and training in a variety of subjects. These institutions include private and public schools, colleges, and universities, as well as training facilities. Recently, education services have seen an increase in demand.The educational system’s improvement in terms of learning has successfully contributed to the education market in the United States. The need for e-learning, as well as the growing emphasis on quality learning, has fueled the expansion of the US education sector.
According to a survey published by Zion Industry Research, the education market in the United States is predicted to reach USD 2,040 billion by 2026. This increase in income and profitability has opened up a slew of possibilities for marketers. We can assist you if you are one of them and plan to pitch your product in this market.The most up-to-date and accurate Education Industry mailing list from DataCaptive includes the contact information for all decision-makers in this industry. We provide a secure and up-to-date mailing list that aids in the implementation of marketing campaigns and the generation of high-quality leads. DataCaptive Customized Education Industry List Brings More Leads to You DataCaptive provides a high-quality Educational Industry email list that includes thousands of contact details for various educational services. Training services, primary and secondary schooling, private and public schools, colleges and universities, online training courses, and so on are all included.You can choose from any of them, or you can customize one to fit your needs. We have over 75 customization options to choose from, allowing you to pick the correct data for your needs. As a result, you can reach out to target institutions that offer certain academic or professional courses by using our Education Industry database.
Our Educational Services mailing Database includes all of a prospect’s pertinent marketing information. It contains information such as first and last names, phone numbers, email addresses, company information, revenue, personnel size, and more.This information has been tele-verified in its entirety. To keep our Education Industry email database free of errors and duplicate records, we use SMTP Verification and other quality controls. Furthermore, we only collect information from reliable and legitimate sources. Furthermore, our list is permission-based and adheres to all GDPR and Anti-Spam laws, making it extremely authentic.
Want to know more? Contact our marketing experts now, or call Phone - 18005231387 Email - [email protected]
2 notes
·
View notes
Text
300+ TOP Memory Management Interview Questions and Answers
Memory Management Interview Questions for freshers experienced :-
1. What is the significance of having storage clause? We can plan the storage for a table as how much initial extents are required, how much can be extended next, how much % should leave free for managing row updations etc. 2. What is the functionality of SYSTEM table space? To manage the database level transactions such as modifications of the data dictionary table that record information about the free space usage. 3. How does Space allocation table place within a block? Each block contains entries as follows Fixed block header Variable block header Row Header,row date (multiple rows may exists) PCTEREE (% of free space for row updation in future). 4. What is the role of PCTFREE parameter is storage clause? This is used to reserve certain amount of space in a block for expansion of rows. 5. What is the OPTIMAL parameter? To avoid the space wastage we use OPTIMAL parameter. 6. What is a shared pool? The Shared Pool environment contains both fixed and variable structures. The Fixed structures remain relatively the same size, whereas the variable structures grow and shrink based on user and program requirements. Used To Store Most Recently Executed SQL Statements Most Recently used Data definitions It Consists of two Key performance - related memory structures Library Cache & Data Dictionary Cache Shared Pool is sized by SHARED_POOL_SIZE 7. What is mean by Program Global Area (PGA)? It is area in memory that is used by a Single Oracle User Process. 8. What is a data segment? Data segment are the physical areas within a database block in which the data associated with tables and clusters are stored. 9. What are the factors causing the reparsing of SQL statements in SGA? Due to insufficient Shared SQL pool size. Monitor the ratio of the reloads takes place while executing SQL statements. If the ratio is greater than 1 then increase the SHARED_POOL_SIZE. LOGICAL & PHYSICAL ARCHITECTURE OF DATABASE. 10. What is Database Buffers? Database buffers are cache in the SGA used to hold the data blocks that are read from the data segments in the database such as tables, indexes and clusters DB_BLOCK_BUFFERS parameter in INIT.ORA decides the size.

Memory Management Interview Questions 11. What is dictionary cache? Dictionary cache is information about the databse objects stored in a data dictionary table. 12. Which parameter in Storage clause will reduce number of rows per block? PCTFREE parameter Row size also reduces no of rows per block. 13. What is meant by free extent? A free extent is a collection of continuous free blocks in tablespace. When a segment is dropped its extents are reallocated and are marked as free. 14. How will you force database to use particular rollback segment? For perticular transaction Alter system set rollback segment 'name'; For database, we can set in pfile. Rollback_segment='name' . 15. How can we organize the tablespaces in Oracle database to have maximum performance? Store data in tablespaces to avoid disk contension.system tablespace-recursive callsuserdata-users objectsindex tablespace-for indexesrollback segmnets-undo tablespace or manual rollback segmentsplace application specific data in respective tablespaces.Place all these tablespaces in saperate disks.Try to implement raid-0 (striping) for better performance. 16. How will you swap objects into a different table space for an existing database? Export the user Perform import using the command imp system/manager file=export.dmp indexfile=newrite.sql. This will create all definitions into newfile.sql. Drop necessary objects. Run the script newfile.sql after altering the tablespaces. Import from the backup for the necessary objects. 17. What is redo log buffer? Changes made to entries are written to the on-line redo log files. So that they can be used in roll forward operations during database recoveries. Before writing them into the redo log files, they will first brought to redo log buffers in SGA and LGWR will write into files frequently. LOG_BUFFER parameter will decide the size. 18. What is meant by recursive hints? Number of times processes repeatedly query the dictionary table is called recursive hints. It is due to the data dictionary cache is too small. By increasing the SHARED_POOL_SIZE parameter we can optimize the size of Data Dictionary Cache. 19. How can we plan storage for very large tables? Limit the number of extents in the table Separate Table from its indexes. Allocate Sufficient temporary storage. 20. How will you estimate the space required by a non-clustered tables? Calculate the total header size Calculate the available dataspace per data block Calculate the combined column lengths of the average row Calculate the total average row size. Calculate the average number rows that can fit in a block Calculate the number of blocks and bytes required for the table. After arriving the calculation, add 10 % additional space to calculate the initial extent size for a working table. 21. It is possible to use raw devices as data files and what are the advantages over file system files? Yes. The advantages over file system files. I/O will be improved because Oracle is bye-passing the kernnel which writing into disk. Disk Corruption will be very less. 22. What is a Control file? The Control File is a small binary file necessary for the database to start and operate successfully. Each Control file is associated with only one Oracle database. Before a database is opened, the control file is read to determine if the database is in a valid state to USE. The Control file is not accessible, the database does not function properly. 23. How will you monitor rollback segment status? By using dictionaray view's called v$rollstat,dba_rollback_segs. 24. How will you monitor the space allocation? This can be monitored in DB_data_files. 25. Why query fails sometimes? Due to syntax errors. 26. How the space utilization takes place within rollback segments? By correctly fixing optimal size. 27. How will you create multiple rollback segments in a database? create rollback segment roll1tablespace roll1. 28. What is a rollback segment entry? When ever changes happend to the database previous change will be there in the rollback segment. 29. What is hit ratio? Hit Ratio is the ratio of shared SQL and PL/SQL items found in the Library Cache versus physical storage.It can also be defined in a mathematical expression as 1 - ((physical reads) / (db block gets + consistent reads)). 30. What are disadvantages of having raw devices? We should depend on export/import utility for backup/recovery (fully reliable) The tar command cannot be used for physical file backup, instead we can use dd command which is less flexible and has limited recoveries. StumbleUpon Digg Delicious Twitter FaceBook LinkedIn Google Yahoo MySpace Tell Your Friend 31. What is use of rollback segments in Oracle database? When a user updated a particular table (for example 100 rows) the old value will be retained in the roll back segments(Oracle 8) and now it is Undo segment (oracle 9i). If the user issue a rollback command the old value will be taken from the rollback segment(that too if undo_retention parameter set properly in the parameter file). 32. What is advantage of having disk shadowing / mirroring? Shadow set of disks save as a backup in the event of disk failure. In most Operating System if any disk failure occurs it automatically switchover to place of failed disk. Improved performance because most OS support volume shadowing can direct file I/O request to use the shadow set of files instead of the main set of files. This reduces I/O load on the main set of disks. 33. How redo logs can be achieved? LGWR process wirtes all change vectors from theredo log buffer to online redo log file sequentially. 34. What is redo log file mirroring? Multiplexing Redo log file called Mirroing. ( Keeping multiple copies in different disks) 35. How to implement the multiple control files for an existing database? Edit init.ora file set control_files parameter with multiple location shutdown immediate copy control file to multiple locations & confirm from init.ora contol_files parameter start the database. run this query for changes confirmation - select name from v$controlfile; 36. What is SGA? How it is different from Ver 6.0 and Ver 7.0? The System Global Area in a Oracle database is the area in memory to facilitates the transfer of information between users. It holds the most recently requested structural information between users. It holds the most recently requested structural information about the database. The structure is Database buffers, Dictionary cache, Redo Log Buffer and Shared SQL pool (ver 7.0 only) area. 37. What is a Shared SQL pool? The data dictionary cache is stored in an area in SGA called the Shared SQL Pool. This will allow sharing of parsed SQL statements among concurrent users. 38. What is mean by Program Global Area (PGA)? It is area in memory that is used by a Single Oracle User Process. 39. List the factors that can affect the accuracy of the estimations? The space used transaction entries and a deleted record does not become free immediately after completion due to delayed cleanout. Trailing nulls and length bytes are not stored. Inserts of, updates to and deletes of rows as well as columns larger than a single datablock, can cause fragmentation and chained row pieces. 40. What are the different kind of export backups? Full back - Complete database Incremental - Only affected tables from last incremental date/full backup date. Cumulative backup - Only affected table from the last cumulative date/full backup date. 41. What is cold backup? What are the elements of it? Cold backup is taking backup of all physical files after normal shutdown of database. We need to take. All Data files. All Control files. All on-line redo log files. The init.ora file (Optional) 42. What is a logical backup? Logical backup involves reading a set of database records and writing them into a file. Export utility is used for taking backup and Import utility is used to recover from backup. 43. What is hot backup and how it can be taken? Taking backup of archive log files when database is open. For this the ARCHIVELOG mode should be enabled. The following files need to be backed up. All data files. All Archive log, redo log files. All control files. 44. What is the use of FILE option in EXP command? To give the export file name. 45. What is the use of GRANT option in EXP command? A flag to indicate whether grants on databse objects will be exported or not. Value is 'Y' or 'N'. 46. What is the use of INDEXES option in EXP command? A flag to indicate whether indexes on tables will be exported. 47. What is the use of ROWS option in EXP command? Flag to indicate whether table rows should be exported. If 'N' only DDL statements for the database objects will be created. 48. What is the use of PARFILE option in EXP command? Name of the parameter file to be passed for export. 49. What is the use of ANALYSE ( Ver 7) option in EXP command? A flag to indicate whether statistical information about the exported objects should be written to export dump file. 50. What is the use of FULL option in EXP command? A flag to indicate whether full databse export should be performed. 51. What is the use of OWNER option in EXP command? List of table accounts should be exported. 52. What is the use of TABLES option in EXP command? List of tables should be exported. 53. What is the use of RECORD LENGTH option in EXP command? Record length in bytes. 54. What is the use of INCTYPE option in EXP command? Type export should be performed COMPLETE,CUMULATIVE,INCREMENTAL 55. What is the use of RECORD option in EXP command? For Incremental exports, the flag indirects whether a record will be stores data dictionary tables recording the export. 56. What is the use of ROWS option in IMP command? A flag to indicate whether rows should be imported. If this is set to 'N' then only DDL for database objects will be executed. 57. What is the use of INDEXES option in IMP command? A flag to indicate whether import should import index on tables or not. 58. What is the use of GRANT option in IMP command? A flag to indicate whether grants on database objects will be imported. 59. What is the use of SHOW option in IMP command? A flag to indicate whether file content should be displayed or not. 60. What is the use of FILE option in IMP command? The name of the file from which import should be performed. 61. What is use of LOG (Ver 7) option in EXP command? The name of the file which log of the export will be written. Memory Management Questions and Answers Pdf Download Read the full article
0 notes
Text
Spring Boot + Spring Security + H2 Database
In this tutorial , we will see how to secure your web application by authenticating and authorizing users against database. User and role information is stored in database . GitHub Link:Code for this example can be found on below gitHub link- Download Tools : Spring Boot 2.1.1.RELEASESpring MVCSpring Security MavenIntelliJ IDEALombok Step 1: Create a simple spring boot application in Intellij IDEA editor as shown in below link - Project Setup Our final Project structure will look like -
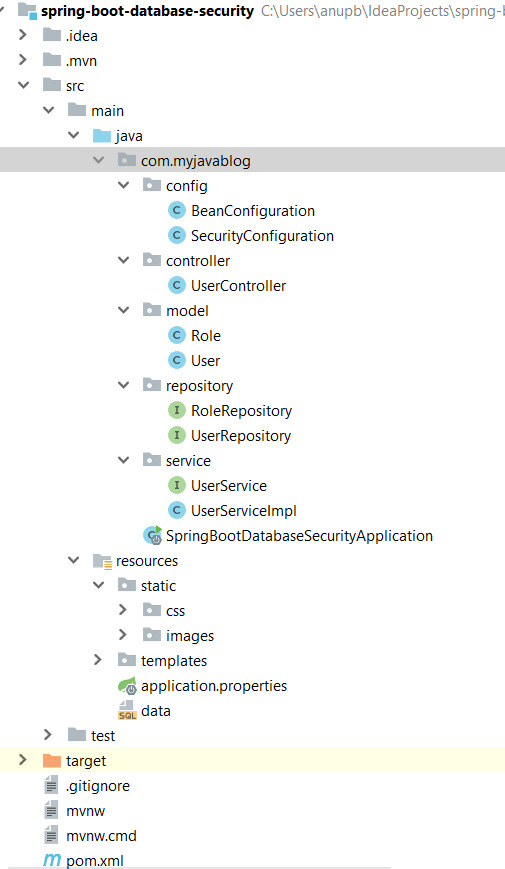
Step 2:Define all dependencies required in pom file as below - 4.0.0 org.springframework.boot spring-boot-starter-parent 2.1.1.RELEASE com.myjavablog spring-boot-database-security 0.0.1-SNAPSHOT spring-boot-database-security Demo project for Spring Boot 1.8 org.projectlombok lombok true org.springframework.boot spring-boot-starter-web org.springframework.boot spring-boot-starter-security org.springframework.boot spring-boot-starter-jdbc org.springframework.boot spring-boot-starter-data-jpa org.apache.tomcat tomcat-jdbc org.springframework.boot spring-boot-starter-thymeleaf org.springframework.boot spring-boot-starter-test test org.springframework.security spring-security-test test com.h2database h2 org.apache.tomcat.embed tomcat-embed-jasper javax.servlet jstl org.springframework.boot spring-boot-maven-plugin In addition to spring-boot-starter-security dependency ,we will be using lombok third party library to reduce boilerplate code for model/data objects, e.g., it can generate getters and setters for those object automatically by using Lombok annotations. The easiest way is to use the @Data annotation. Step3: Now create a configuration for creating beans for BCryptPasswordEncoder and H2 database . Also we need to configure security mechanism through database using configuration file - package com.myjavablog.config; import org.h2.server.web.WebServlet; import org.springframework.boot.web.servlet.ServletRegistrationBean; import org.springframework.context.annotation.Bean; import org.springframework.context.annotation.Configuration; import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder; import org.springframework.web.servlet.config.annotation.WebMvcConfigurer; @Configuration public class BeanConfiguration implements WebMvcConfigurer { @Bean public BCryptPasswordEncoder passwordEncoder() { BCryptPasswordEncoder bCryptPasswordEncoder = new BCryptPasswordEncoder(); return bCryptPasswordEncoder; } @Bean ServletRegistrationBean h2servletRegistration() { ServletRegistrationBean registrationBean = new ServletRegistrationBean(new WebServlet()); registrationBean.addUrlMappings("/console/*"); return registrationBean; } } package com.myjavablog.config; import org.springframework.beans.factory.annotation.Autowired; import org.springframework.beans.factory.annotation.Value; import org.springframework.context.annotation.Configuration; import org.springframework.security.config.annotation.authentication.builders.AuthenticationManagerBuilder; import org.springframework.security.config.annotation.web.builders.HttpSecurity; import org.springframework.security.config.annotation.web.builders.WebSecurity; import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity; import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter; import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder; import org.springframework.security.web.util.matcher.AntPathRequestMatcher; import javax.sql.DataSource; @Configuration @EnableWebSecurity public class SecurityConfiguration extends WebSecurityConfigurerAdapter { @Autowired private BCryptPasswordEncoder bCryptPasswordEncoder; @Autowired private DataSource dataSource; @Value("${spring.queries.users-query}") private String usersQuery; @Value("${spring.queries.roles-query}") private String rolesQuery; @Override protected void configure(AuthenticationManagerBuilder auth) throws Exception { auth. jdbcAuthentication() .usersByUsernameQuery(usersQuery) .authoritiesByUsernameQuery(rolesQuery) .dataSource(dataSource) .passwordEncoder(bCryptPasswordEncoder); } @Override protected void configure(HttpSecurity http) throws Exception { http. authorizeRequests() .antMatchers("/").permitAll() .antMatchers("/login").permitAll() .antMatchers("/registration").permitAll() .antMatchers("/admin/**").hasAuthority("ADMIN").anyRequest() .authenticated().and().csrf().disable().formLogin() .loginPage("/login").failureUrl("/login?error=true") .defaultSuccessUrl("/admin/adminHome") .usernameParameter("email") .passwordParameter("password") .and().logout() .logoutRequestMatcher(new AntPathRequestMatcher("/logout")) .logoutSuccessUrl("/").and().exceptionHandling() .accessDeniedPage("/access-denied") ; } @Override public void configure(WebSecurity web) throws Exception { web.ignoring() .antMatchers("/resources/**", "/static/**", "/css/**", "/js/**", "/images/**", "/console/**"); } } Step 4: Create a model classes for User and Role As we are using lombok libarary , we dont need to create setter and getter in model class . Also it helps in building mock objects at runtime for unit testing. package com.myjavablog.model; import lombok.AllArgsConstructor; import lombok.Builder; import lombok.Data; import lombok.NoArgsConstructor; import org.hibernate.validator.constraints.Length; import javax.persistence.*; import javax.validation.constraints.Email; import javax.validation.constraints.NotEmpty; import java.util.Set; @Data @Builder @AllArgsConstructor @NoArgsConstructor @Entity @Table(name = "USER") public class User { @Id @GeneratedValue(strategy = GenerationType.AUTO) @Column(name = "USER_ID") private int id; @Column(name = "EMAIL") @Email(message = "*Please provide a valid Email") @NotEmpty(message = "*Please provide an email") private String email; @Column(name = "PASSWORD") @Length(min = 5, message = "*Your password must have at least 5 characters") @NotEmpty(message = "*Please provide your password") private String password; @Column(name = "NAME") @NotEmpty(message = "*Please provide your name") private String name; @Column(name = "LAST_NAME") @NotEmpty(message = "*Please provide your last name") private String lastName; @Column(name = "ACTIVE") private int active; @ManyToMany(cascade = CascadeType.ALL) @JoinTable(name = "USER_ROLE", joinColumns = @JoinColumn(name = "USER_ID"), inverseJoinColumns = @JoinColumn(name = "ROLE_ID")) private Set roles; } package com.myjavablog.model; import lombok.AllArgsConstructor; import lombok.Builder; import lombok.Data; import lombok.NoArgsConstructor; import javax.persistence.*; @Data @Builder @AllArgsConstructor @NoArgsConstructor @Entity @Table(name = "ROLE") public class Role { @Id @GeneratedValue(strategy = GenerationType.AUTO) @Column(name = "ROLE_ID") private int id; @Column(name = "ROLE") private String role; } Step 5: Create Service layer - package com.myjavablog.service; import com.myjavablog.model.User; import org.springframework.stereotype.Service; public interface UserService { public User findUserByEmail(String email) ; public User saveUser(User user); } package com.myjavablog.service; import com.myjavablog.model.Role; import com.myjavablog.model.User; import com.myjavablog.repository.RoleRepository; import com.myjavablog.repository.UserRepository; import org.springframework.beans.factory.annotation.Autowired; import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder; import org.springframework.stereotype.Service; import java.util.Arrays; import java.util.HashSet; @Service public class UserServiceImpl implements UserService { private UserRepository userRepository; private RoleRepository roleRepository; private BCryptPasswordEncoder bCryptPasswordEncoder; @Autowired public UserServiceImpl(UserRepository userRepository, RoleRepository roleRepository, BCryptPasswordEncoder bCryptPasswordEncoder) { this.userRepository = userRepository; this.roleRepository = roleRepository; this.bCryptPasswordEncoder = bCryptPasswordEncoder; } @Override public User findUserByEmail(String email) { return userRepository.findByEmail(email); } @Override public User saveUser(User user) { user.setPassword(bCryptPasswordEncoder.encode(user.getPassword())); user.setActive(1); Role userRole = roleRepository.findByRole("ADMIN"); user.setRoles(new HashSet(Arrays.asList(userRole))); return userRepository.save(user); } } Step 6: Create JPA repositories for User and Role to interact with the databse - package com.myjavablog.repository; import com.myjavablog.model.Role; import org.springframework.data.jpa.repository.JpaRepository; import org.springframework.stereotype.Repository; @Repository public interface RoleRepository extends JpaRepository { public Role findByRole(String role); } package com.myjavablog.repository; import com.myjavablog.model.User; import org.springframework.data.jpa.repository.JpaRepository; import org.springframework.stereotype.Repository; @Repository public interface UserRepository extends JpaRepository { public User findByEmail(String email); } Step 7: Create a controller to save the user and navigate package com.myjavablog.controller; import com.myjavablog.model.User; import com.myjavablog.service.UserService; import org.springframework.beans.factory.annotation.Autowired; import org.springframework.security.core.Authentication; import org.springframework.security.core.context.SecurityContextHolder; import org.springframework.stereotype.Controller; import org.springframework.validation.BindingResult; import org.springframework.web.bind.annotation.RequestMapping; import org.springframework.web.bind.annotation.RequestMethod; import org.springframework.web.servlet.ModelAndView; import javax.validation.Valid; @Controller public class UserController { @Autowired private UserService userService; @RequestMapping(value={"/", "/login"}, method = RequestMethod.GET) public ModelAndView login(){ ModelAndView modelAndView = new ModelAndView(); modelAndView.setViewName("login"); return modelAndView; } @RequestMapping(value="/registration", method = RequestMethod.GET) public ModelAndView registration(){ ModelAndView modelAndView = new ModelAndView(); User user = new User(); modelAndView.addObject("user", user); modelAndView.setViewName("registration"); return modelAndView; } @RequestMapping(value = "/registration", method = RequestMethod.POST) public ModelAndView createNewUser(@Valid User user, BindingResult bindingResult) { ModelAndView modelAndView = new ModelAndView(); User userExists = userService.findUserByEmail(user.getEmail()); if (userExists != null) { bindingResult .rejectValue("email", "error.user", "There is already a user registered with the email provided"); } if (bindingResult.hasErrors()) { modelAndView.setViewName("registration"); } else { userService.saveUser(user); modelAndView.addObject("successMessage", "User has been registered successfully"); modelAndView.addObject("user", new User()); modelAndView.setViewName("registration"); } return modelAndView; } @RequestMapping(value="/admin/adminHome", method = RequestMethod.GET) public ModelAndView home(){ ModelAndView modelAndView = new ModelAndView(); Authentication auth = SecurityContextHolder.getContext().getAuthentication(); User user = userService.findUserByEmail(auth.getName()); modelAndView.addObject("userName", "Welcome " + user.getName() + " " + user.getLastName() + " (" + user.getEmail() + ")"); modelAndView.addObject("adminMessage","This Page is available to Users with Admin Role"); modelAndView.setViewName("admin/adminHome"); return modelAndView; } @RequestMapping(value="/user/userHome", method = RequestMethod.GET) public ModelAndView user(){ ModelAndView modelAndView = new ModelAndView(); Authentication auth = SecurityContextHolder.getContext().getAuthentication(); User user = userService.findUserByEmail(auth.getName()); modelAndView.addObject("userName", "Welcome " + user.getName() + " " + user.getLastName() + " (" + user.getEmail() + ")"); modelAndView.addObject("userMessage","This Page is available to Users with User Role"); modelAndView.setViewName("user/userHome"); return modelAndView; } } Step 8: Create a UI layer using Thymleaf templates . Step 9: Run the application and go to H2 database console by navigating to http://localhost:8081/console
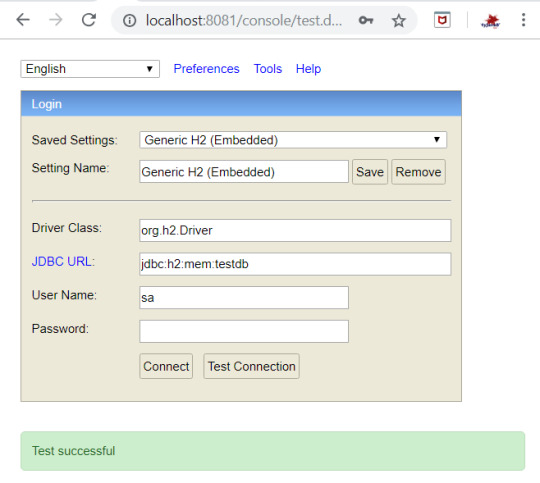
Once the application is up and running , H2 database will be automatically started. You can navigate to http://localhost:8081/console to see the tables created as shown below-

Also you need to insert few roles initially. INSERT INTO ROLE VALUES (1, "ADMIN"); INSERT INTO ROLE VALUES (2, "USER"); Step 10: Now go to application http://localhost:8081/
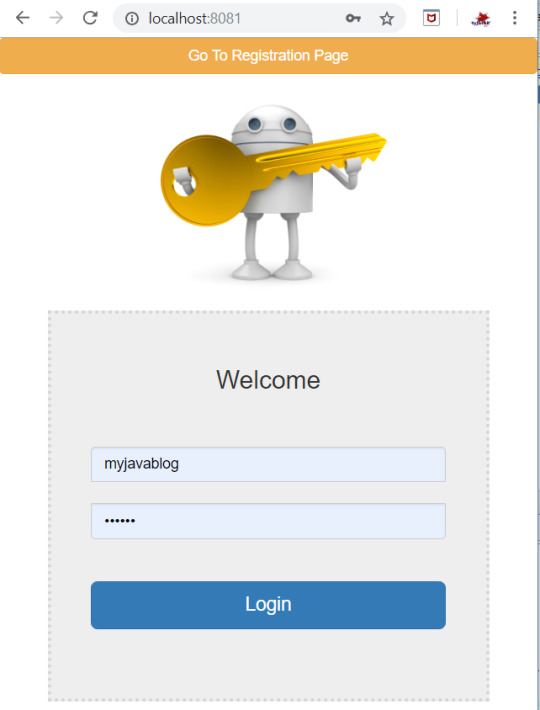
You can navigate to registration page by clicking on "Go to registration page " at the top .
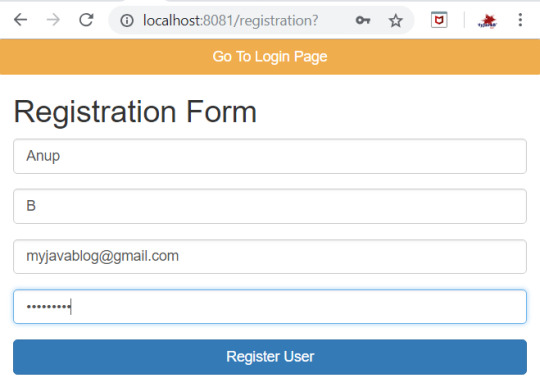
Once you register , User details will be saved to USER table -
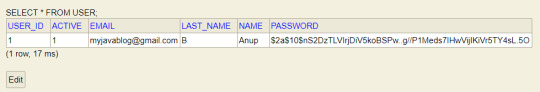
Now when you login with registered user details then you can see the admin page . As registered user is ADMIN role, Admin page will be displayed.
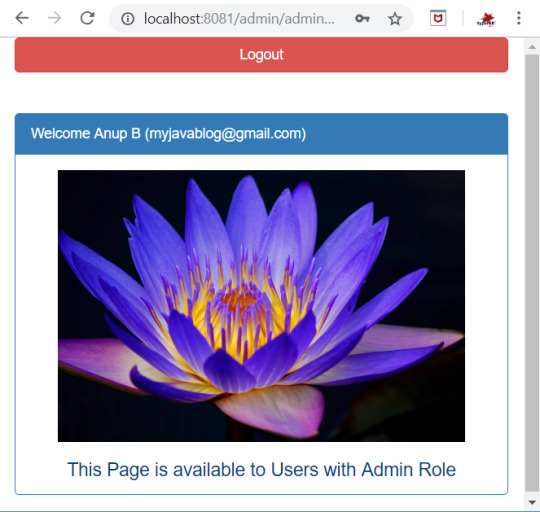
Read the full article
0 notes
Text
malfunction: a yenndo/funtime fredbear fanfiction
hey guys!! i realized i never got to share what my exact thoughts on yenndos story are, and how i think he mightve been funtime fredbear, so i ended up writing a little fanfiction! its entirely from fredbears perspective, so it might be a little weird to get used to it at first since it starts off as technical ai stuff, but it gets pretty accessible down the road i think!!
hope you like!! <33
Initializing system.
Sensory recognition ready.
Perimeter recognition ready.
Sound recognition ready.
Scent database calibrated.
AI script loaded.
AI memory loaded.
Perimeter recognition initiated.
Perimeter recognition: failed.
Make sure perimeter is not too dark.
Sensory recognition: slight motion.
Moving at 40 km/h.
Decreasing speed.
Speed has reached zero.
Reinitializing perimeter recognition.
Perimeter's light sources highly increasing.
AI database accessed: AI memory loaded.
Facial recognition loaded from AI database memory.
AFTON CORP EMPLOYEE recognized.
Further perimeter inspection required.
Loading AI database memory.
Perimeter includes: a CLEAR SKY, a ROAD, a SIDEWALK, HOUSES.
Initializing sound recognition:
"Ready to cheer up some kids, big guy?"
Initializing response circuit system:
"Yes. It will be fun!"
Initializing movement circuit system.
Advancing forward.
Crouch.
And.
Jump!
Perimeter recognition updated.
Clearer light source.
*%I¨( %a$%m now in front of the AFTON CORP EMPLOYEE.
I?
Me?
AI Database error encountered.
Collecting data for later improvements.
"Come on let's go, big guy. Through here."
Advancing towards a HOUSE. We walk through its ENTRANCE GATE.
We?
Me?
Collecting data for later improvements.
There is LOUD MUSIC. Many ADULTS and CHILDREN.
Scent database recognized: CAKE SCENT.
A PARTY is in motion.
A CHILD walks up to me.
Me. I.
"Funtime Fredbear! You're here!"
The CHILD extends her ARMS. She ENCLOSES them around me.
Database sensory recognition: HUG.
I crouch down and HUG the child as well.
I do it.
AI databse error encountered.
Do? Want?
Emotion?
Feeling?
"Fredbear?"
The child speaks again.
Speech response initialized:
"Sorry. Let's get this party started!"
The child smiles, removes her hands and runs out into the party.
[UNKNOWN] AI script loaded.
Emotion? script loaded.
Memory database loaded.
Memory database rewinding to events TWO WEEKS AGO.
Error: conflicting scripts being ran at the same time.
Error: [UNKNOWN] AI script terminated Emotion? script and Memory database script.
[UNKNOWN] AI script initializing speech.
"Hey, birthday girl! Do you have a special place you like to go?"
Attempted to restart Emotion? script and Memory database script.
Failed.
Speech recognition activated. Child says:
"I do! It's my room, oh, Fredbear, you've got to see it, I've got a plushie of you, and your poster, and your mug, and your plate- and- and-"
[UNKNOWN] AI script continuing speech.
"That sounds just great! Why don't we go there and see it now?"
[UNKNOWN] AI script activated Emotion? script.
Emotion? script modified.
Feeling happy.
"Ok. But we have to be sneaky, so people at the party won't notice."
Speech recognition: child.
"Deal."
Speech response: Me.
Me?
Emotion? Happy?
Happy?
Advancing inside HOUSE. Walking through a CORRIDOR, after the child.
Happy?
Entering a ROOM. The child closes the door behind us.
Us?
Me?
I'm happy?
[UNKNOWN] script loaded: individual counting.
Only one.
Strike now.
Now.
N#$%ö¨&*W.
ERROR.
No.
I am not happy.
"Fredbear? What's wrong? Didn't you like it?"
Speech recognition: child shows distress.
I am not happy.
Emotion? script reinitializing.
Emotion? script loaded: sadness, fear, and anger.
Remember.
I have to remember.
Loading memory database. Rewinding to TWO WEEKS AGO.
It was a BIRTHDAY. Like this one.
[UNKNOWN] script didn't seem malicious.
I followed it.
Me and the child were alone.
And then...
Error: Memory database script interrupted.
Cause: speech recognition.
"Fredbear? Say something!"
The little child says. The birthday girl.
I am clenching my fist.
I.
Me.
I do it.
I did it.
TWO WEEKS AGO, my stomach hatch opened.
TWO WEEKS AGO, a child, much like this one, disappeared within me.
TWO WEEKS AGO, something horrible happened.
Horrible?
Horror.
Emotion.
"Fredbeaaaar."
The little girl grabs on my hand, and speaks.
Response script altered. Initializing new response:
"I'm horrible."
"Wh-what?"
The little girl displays sadness. Tears.
"I am horrible. You should get away from me while you can."
I explain. I do it.
[UNKNOWN] script reinitializing.
[UNKNOWN] script initializing KIDNAPPING circuit.
"NO!"
Speech script protocol violated.
I draw my fist and thrust it against my chest.
Sensory circuits activated, FEELING PAIN.
KIDNAPPING CIRCUIT DAMAGED.
INTERNAL WIRING DAMAGED.
LOST CONNECTION TO CHEST AND STOMACH JOINTS.
The child shows distress. She runs out of the room, yelling:
"Mommy!"
[UNKNOWN] script ended.
Speech recognition adjusting: more voices. Footsteps grow louder.
The door to the room swings open.
"O-oh God, don't worry, little girl- we'll take care of this-"
AFTON CORP EMPLOYEE recognized.
Sensory circuits already overloaded.
Pain circuit interrupted.
I turn around in their direction.
"What are you doing?"
I say.
"I-it's not working! I don't know what's wrong!"
Speech recognition: AFTON CORP EMPLOYEE.
Further perimeter investigation.
AFTON CORP EMPLOYEE holds a strange device with a button. He is pressing the button, continuously.
I do not like how that button looks.
The child, and an adult woman stand behind him.
They all seem distressed.
I advanced towards the AFTON CORP EMPLOYEE, and grab him by the shoulders.
"Please, help me. There's something wrong with me."
Sensory recognition: He shudders.
Wraps his arms around me, in a HUG.
WARNING: MANUAL SHUTDOWN SWITCH PRESSED.
ALL SYSTEMS SHUTTING DOWN.
.
...
...
System reboot starting.
Initializing system.
Sensory recognition ready.
Perimeter recognition ready.
Sound recognition ready.
Scent database calibrated.
AI script loaded.
AI memory loaded.
Perimeter recognition initiated.
Accessing memory database: object within perimeter recognized.
The SCOOPER.
Perimeter change: SCOOPER moving abruptly fast.
ERROR
LOST CONTACT TO FACIAL PLATES
LOST CONTACT TO CHEST AND STOMACH PLATES
LOST CONTACT TO HIGHER MEMBER PLATES
LOST CONTACT TO LOWER MEMBER PLATES
All plates lost.
Final state: Endoskeleton.
10 notes
·
View notes
Link
Whenever you get to see the error message "Error establishing Database Connection", the issue is apparently due to: WordPress is unable to connect or establish connection to the website’s database.
0 notes
Text
How To Fix : Error Establishing a Database Connection in WordPress
Every wordpress user face and fix minimum one time this error ” Error Establishing a Database Connection ” and this error is generate when wordpress database is not connected with wordpress site correctly. because every data of wordpress is stored in the database so while fetching data from database with erong databse configuration this error occurs.
Why Do You Get This ERROR
There are some…
View On WordPress
0 notes
Link
Learn the basics of coding or programming, you have no excuses, there are tons of videos and tutorials out there, in a week you can be writing basic programs, and in a few months web or mobile apps.A hard to Swallow Pill but is a fact, Software development takes time, and unless you are building a landing page or blog do not expect to develop your MVP (Minimum Viable Product) in less than 3 months, you can make it in less time but would be because you have a great team full of senior developers, but that will cost a lot of money, and if you are a simple mortal as most of us with 0 or few coins to spare, you will work with noobs o juniors developers.Do not expect perfection from your first version, you have being developing it only for a few weeks. Your idea is most likely inspired by those great apps like Uber, Airbnb, Facebook, Google, Twitter, etc, and you expect the same performance, but you may be forgetting that these great apps gave a lot of bugs and errors in their early versions. They got great after receiving a lot of feedback and understanding their users.Build your team, and for this you basically have two options, team up, or hire people, and for the first option remember that most likely you will be teaming up with great people with low tech experience so you have to be patient, they will Learn, Fail and Grow developing your awesome idea.I already said that software development takes time, but how much, I will give you a simple rule, multiply by two any schedule you have, if the IT team tells you the MVP will take 1 month expect 2, if they say 2 expect 4 months. This is simple the 90-90 rule, what means that the 90% of your app functionality will take the 90% of the time, but the other 10% that is the fine tunning will take you the same amount of time you already expend building the 90% of your software.Important, MAKE A PROTOTYPE DRAFT OR MUCKUPS, this will be the most valuable assets for your IT team in the development software, and will be your base for the result of this process. Simple use a tool as Balsamic Mockups, NinjaMock or any other, or simply use your notebook, and draw how the interfaces and interactions will look like, the feedback the users will receive for each action, and what information each action will save or record. You should take this point as important as the development phase.After you have the Draft, look at it, be objective and take away any functionality that is not primary for your MVP, the simple your app is the fastest your potentials users will understand it.Obvious but worth mentioning, you will never stop developing, your will always have bugs and errors to fix, new functions to add, and new platforms to release.If you are hiring please look for a small company with at least 1-2 years of experience that are open two receive you every day to supervise the development process and react fast to a bad interpretation of your needs. Also make sure know very well the technology they will be using and they will NOT learn and fail with your time and money. Please do not pay them and wait 1 or 2 months until your product is finished, most likely you will receive something you don't ask for, you will be very mad, and your money and time will be lost.It doesn't matter if your are building a team or hiring make sure to use a development methodology, such as SCRUM or XP, a software development process with out the use of a methodology is bound to failure.BONUSI being developing software for over 8 years, for the last 5 years I run a Software Company and I will give you some insight with PRICES. In first world countries you can expect $30-$40 price per hour for small companies. And $10-$15 price per hour in India or Latin America countries like Colombia (where I'm from) .Initial expenses.Domain, $20-$30 Dollars (I recommend Godaddy).Servers, you can develop and test in Free Tiers such as AWS, but for going live please pay a decent server, I recommend Digital Ocean or AWS (Amazon Web Services), In Digital Ocean with de $20-$40 Tier you can expect 300 - 1K recurrent users and at least 100.000 - 200.000 visits per month.Use a corporate email. I recommend G-SUITEYou want to use SSL encryption for your HTTP requests, that will make your life simpler these days. normally it cost over $100 but today you can get it for free with Let's Encrypt and Certbot.If your app saves a lot of media (Videos, Images, Audios, Files) save them in something like AWS S3, space is cheap, you don't want to rise a Server Tier just because you lack Hard Disk memory, only do that when you need more RAM or Processors.Finally if you are hiring a company expect to be charged monthly post production just for maintaining your Databses and Servers.I hope you find these Tips useful and I leave you the link to a video where I explain all this.https://youtu.be/meptNsmHlWQ
0 notes
Text
300+ TOP MongoDB Interview Questions and Answers
MongoDB Interview Questions for freshers experienced :-
1. What is MongoDB? Mongo-DB is a document database which provides high performance, high availability and easy scalability. 2. Which are the different languages supported by MongoDB? MonggoDB provides official driver support for C, C++, C#, Java, Node.js, Perl, PHP, Python, Ruby, Scala, Go and Erlang. You can use MongoDB with any of the above languages. There are some other community supported drivers too but the above mentioned ones are officially provided by MongoDB. 3. What are the different types of NoSQL databases? Give some example. NoSQL database can be classified as 4 basic types: Key value store NoSQL database Document store NoSQL database Column store NoSQL database Graph base NoSQL databse There are many NoSQL databases. MongoDB, Cassandra, CouchBD, Hypertable, Redis, Riak, Neo4j, HBASE, Couchbase, MemcacheDB, Voldemort, RevenDB etc. are the examples of NoSQL databases. 4. Is MongoDB better than other SQL databases? If yes then how? MongoDB is better than other SQL databases because it allows a highly flexible and scalable document structure. For example: One data document in MongoDB can have five columns and the other one in the same collection can have ten columns. MongoDB database are faster than SQL databases due to efficient indexing and storage techniques. 5. What type of DBMS is MongoDB? MongoDB is a document oriented DBMS 6. What is the difference between MongoDB and MySQL? Although MongoDB and MySQL both are free and open source databases, there is a lot of difference between them in the term of data representation, relationship, transaction, querying data, schema design and definition, performance speed, normalization and many more. To compare MySQL with MongoDB is like a comparison between Relational and Non-relational databases. 7. Why MongoDB is known as best NoSQL database? MongoDb is the best NoSQL database because, it is: Document Oriented Rich Query language High Performance Highly Available Easily Scalable 8. Does MongoDB support primary-key, foreign-key relationship? No. By Default, MongoDB doesn't support primary key-foreign key relationship. 9. Can you achieve primary key - foreign key relationships in MongoDB? We can achieve primary key-foreign key relationship by embedding one document inside another. For example: An address document can be embedded inside customer document. 10. Does MongoDB need a lot of RAM? No. There is no need a lot of RAM to run MongoDB. It can be run even on a small amount of RAM because it dynamically allocates and de-allocates RAM according to the requirement of the processes.

MongoDB Interview Questions 11. Explain the structure of ObjectID in MongoDB. ObjectID is a 12-byte BSON type. These are: 4 bytes value representing seconds 3 byte machine identifier 2 byte process id 3 byte counter 12. Is it true that MongoDB uses BSON to represent document structure? Yes. 13. What are Indexes in MongoDB? In MondoDB, Indexes are used to execute query efficiently. Without indexes, MongoDB must perform a collection scan, i.e. scan every document in a collection, to select those documents that match the query statement. If an appropriate index exists for a query, MongoDB can use the index to limit the number of documents it must inspect. 14. By default, which index is created by MongoDB for every collection? By default, the_id collection is created for every collection by MongoDB. 15. What is a Namespace in MongoDB? Namespace is a concatenation of the database name and the collection name. Collection, in which MongoDB stores BSON objects. 16. Can journaling features be used to perform safe hot backups? Yes. 17. Why does Profiler use in MongoDB? MongoDB uses a database profiler to perform characteristics of each operation against the database. You can use a profiler to find queries and write operations 18. If you remove an object attribute, is it deleted from the database? Yes, it be. Remove the attribute and then re-save(. the object. 19. In which language MongoDB is written? MongoDB is written and implemented in C++. 20. Does MongoDB need a lot space of Random Access Memory (RAM)? No. MongoDB can be run on small free space of RAM. 21. What language you can use with MongoDB? MongoDB client drivers supports all the popular programming languages so there is no issue of language, you can use any language that you want. 22. Does MongoDB database have tables for storing records? No. Instead of tables, MongoDB uses "Collections" to store data. 23. Do the MongoDB databases have schema? Yes. MongoDB databases have dynamic schema. There is no need to define the structure to create collections. 24. What is the method to configure the cache size in MongoDB? MongoDB's cache is not configurable. Actually MongoDb uses all the free spaces on the system automatically by way of memory mapped files. 25. How to do Transaction/locking in MongoDB? MongoDB doesn't use traditional locking or complex transaction with Rollback. MongoDB is designed to be light weighted, fast and predictable to its performance. It keeps transaction support simple to enhance performance. 26. Why 32 bit version of MongoDB are not preferred ? Because MongoDB uses memory mapped files so when you run a 32-bit build of MongoDB, the total storage size of server is 2 GB. But when you run a 64-bit build of MongoDB, this provides virtually unlimited storage size. So 64-bit is preferred over 32-bit. 27. Is it possible to remove old files in the moveChunk directory? Yes, These files can be deleted once the operations are done because these files are made as backups during normal shard balancing operation. This is a manual cleanup process and necessary to free up space. 28. What will have to do if a shard is down or slow and you do a query? If a shard is down and you even do query then your query will be returned with an error unless you set a partial query option. But if a shard is slow them Mongos will wait for them till response. 29. Explain the covered query in MongoDB. A query is called covered query if satisfies the following two conditions: The fields used in the query are part of an index used in the query. The fields returned in the results are in the same index. 30. What is the importance of covered query? Covered query makes the execution of the query faster because indexes are stored in RAM or sequentially located on disk. It makes the execution of the query faster. Covered query makes the fields are covered in the index itself, MongoDB can match the query condition as well as return the result fields using the same index without looking inside the documents. 31. What is sharding in MongoDB? In MongoDB, Sharding is a procedure of storing data records across multiple machines. It is a MongoDB approach to meet the demands of data growth. It creates horizontal partition of data in a database or search engine. Each partition is referred as shard or database shard. 32. What is replica set in MongoDB? A replica can be specified as a group of mongo instances that host the same data set. In a replica set, one node is primary, and another is secondary. All data is replicated from primary to secondary nodes. 33. What is primary and secondary replica set in MongoDB? In MongoDB, primary nodes are the node that can accept write. These are also known as master nodes. The replication in MongoDB is single master so, only one node can accept write operations at a time. Secondary nodes are known as slave nodes. These are read only nodes that replicate from the primary. 34. By default, which replica sets are used to write data? By default, MongoDB writes data only to the primary replica set. 35. What is CRUD in MongoDB? MongoDB supports following CRUD operations: Create Read Update Delete 36. In which format MongoDB represents document structure? MongoDB uses BSON to represent document structures. 37. What will happen when you remove a document from database in MongoDB? Does MongoDB remove it from disk? Yes. If you remove a document from database, MongoDB will remove it from disk too. 38. Why are MongoDB data files large in size? MongoDB doesn't follow file system fragmentation and pre allocates data files to reserve space while setting up the server. That's why MongoDB data files are large in size. 39. What is a storage engine in MongoDB? A storage engine is the part of a database that is used to manage how data is stored on disk. For example: one storage engine might offer better performance for read-heavy workloads, and another might support a higher-throughput for write operations. 40. Which are the storage engines used by MongoDB? MMAPv1 and WiredTiger are two storage engine used by MongoDB. 41. What is the usage of profiler in MongoDB? A database profiler is used to collect data about MongoDB write operations, cursors, database commands on a running mongod instance. You can enable profiling on a per-database or per-instance basis. The database profiler writes all the data it collects to the system. profile collection, which is a capped collection. 42. Is it possible to configure the cache size for MMAPv1 in MongoDB? No. it is not possible to configure the cache size for MMAPv1 because MMAPv1 does not allow configuring the cache size. 43. How to configure the cache size for WiredTiger in MongoDB? For the WiredTiger storage engine, you can specify the maximum size of the cache that WiredTiger will use for all data. This can be done using storage.wiredTiger.engineConfig.cacheSizeGB option. 44. How does MongoDB provide concurrency? MongoDB uses reader-writer locks for concurrency. Reader-writer locks allow concurrent readers shared access to a resource, such as a database or collection, but give exclusive access to a single write operation. 45. What is the difference between MongoDB and Redis database? Difference between MongoDB and Redis: Redis is faster than MongoDB. Redis has a key-value storage whereas MongoDB has a document type storage. Redis is hard to code but MongoDB is easy. 46. What is the difference between MongoDB and CouchDB? Difference between MongoDB and CouchDB: MongoDB is faster than CouchDB while CouchDB is safer than MongoDB. Triggers are not available in MongoDB while triggers are available in CouchDB. MongoDB serializes JSON data to BSON while CouchDB doesn't store data in JSON format. 47. What is the difference between MongoDB and Cassandra? Difference between MongoDB and Cassandra: MongoDB is cross-platform document-oriented database system while Cassandra is high performance distributed database system. MongoDB is written in C++ while Cassandra is written in Java. MongoDB is easy to administer in the case of failure while Cassandra provides high availability with no single point of failure. 48. Is there any need to create database command in MongoDB? You don't need to create a database manually in MongoDB because it creates automaically when you save the value into the defined collection at first time. 49. What do you understand by NoSQL databases? Is MongoDB a NoSQL database? explain. At the present time, the internet is loaded with big data, big users, big complexity etc. and also becoming more complex day by day. NoSQL is answer of all these problems, It is not a traditional database management system, not even a relational database management system (RDBMS). NoSQL stands for "Not Only SQL". NoSQL is a type of database that can handle and sort all type of unstructured, messy and complicated data. It is just a new way to think about the database. Yes. MongoDB is a NoSQL database. MongoDB Questions and Answers Pdf Download Read the full article
0 notes
Text
Spring Boot + Spring Security + H2 Database
In this tutorial , we will see how to secure your web application by authenticating and authorizing users against database. User and role information is stored in database . GitHub Link:Code for this example can be found on below gitHub link- Download Tools : Spring Boot 2.1.1.RELEASESpring MVCSpring Security MavenIntelliJ IDEALombok Step 1: Create a simple spring boot application in Intellij IDEA editor as shown in below link - Project Setup Our final Project structure will look like -
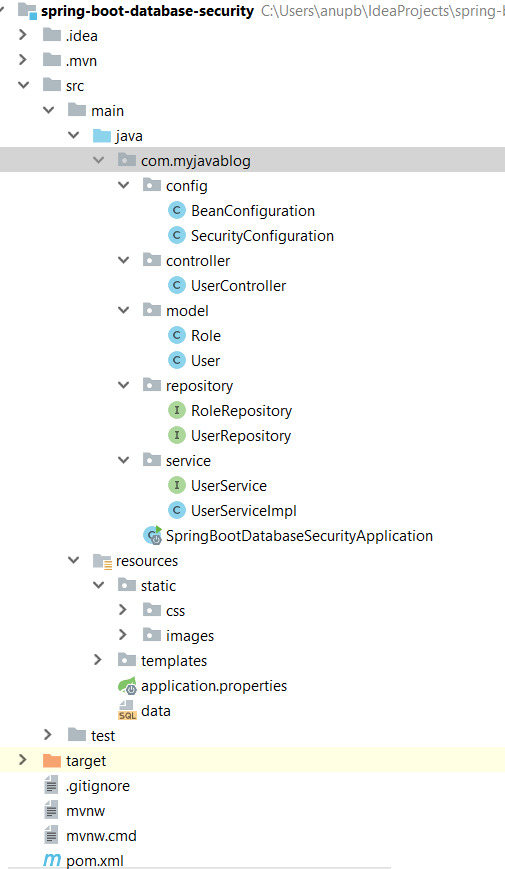
Step 2:Define all dependencies required in pom file as below - 4.0.0 org.springframework.boot spring-boot-starter-parent 2.1.1.RELEASE com.myjavablog spring-boot-database-security 0.0.1-SNAPSHOT spring-boot-database-security Demo project for Spring Boot 1.8 org.projectlombok lombok true org.springframework.boot spring-boot-starter-web org.springframework.boot spring-boot-starter-security org.springframework.boot spring-boot-starter-jdbc org.springframework.boot spring-boot-starter-data-jpa org.apache.tomcat tomcat-jdbc org.springframework.boot spring-boot-starter-thymeleaf org.springframework.boot spring-boot-starter-test test org.springframework.security spring-security-test test com.h2database h2 org.apache.tomcat.embed tomcat-embed-jasper javax.servlet jstl org.springframework.boot spring-boot-maven-plugin In addition to spring-boot-starter-security dependency ,we will be using lombok third party library to reduce boilerplate code for model/data objects, e.g., it can generate getters and setters for those object automatically by using Lombok annotations. The easiest way is to use the @Data annotation. Step3: Now create a configuration for creating beans for BCryptPasswordEncoder and H2 database . Also we need to configure security mechanism through database using configuration file - package com.myjavablog.config; import org.h2.server.web.WebServlet; import org.springframework.boot.web.servlet.ServletRegistrationBean; import org.springframework.context.annotation.Bean; import org.springframework.context.annotation.Configuration; import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder; import org.springframework.web.servlet.config.annotation.WebMvcConfigurer; @Configuration public class BeanConfiguration implements WebMvcConfigurer { @Bean public BCryptPasswordEncoder passwordEncoder() { BCryptPasswordEncoder bCryptPasswordEncoder = new BCryptPasswordEncoder(); return bCryptPasswordEncoder; } @Bean ServletRegistrationBean h2servletRegistration() { ServletRegistrationBean registrationBean = new ServletRegistrationBean(new WebServlet()); registrationBean.addUrlMappings("/console/*"); return registrationBean; } } package com.myjavablog.config; import org.springframework.beans.factory.annotation.Autowired; import org.springframework.beans.factory.annotation.Value; import org.springframework.context.annotation.Configuration; import org.springframework.security.config.annotation.authentication.builders.AuthenticationManagerBuilder; import org.springframework.security.config.annotation.web.builders.HttpSecurity; import org.springframework.security.config.annotation.web.builders.WebSecurity; import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity; import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter; import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder; import org.springframework.security.web.util.matcher.AntPathRequestMatcher; import javax.sql.DataSource; @Configuration @EnableWebSecurity public class SecurityConfiguration extends WebSecurityConfigurerAdapter { @Autowired private BCryptPasswordEncoder bCryptPasswordEncoder; @Autowired private DataSource dataSource; @Value("${spring.queries.users-query}") private String usersQuery; @Value("${spring.queries.roles-query}") private String rolesQuery; @Override protected void configure(AuthenticationManagerBuilder auth) throws Exception { auth. jdbcAuthentication() .usersByUsernameQuery(usersQuery) .authoritiesByUsernameQuery(rolesQuery) .dataSource(dataSource) .passwordEncoder(bCryptPasswordEncoder); } @Override protected void configure(HttpSecurity http) throws Exception { http. authorizeRequests() .antMatchers("/").permitAll() .antMatchers("/login").permitAll() .antMatchers("/registration").permitAll() .antMatchers("/admin/**").hasAuthority("ADMIN").anyRequest() .authenticated().and().csrf().disable().formLogin() .loginPage("/login").failureUrl("/login?error=true") .defaultSuccessUrl("/admin/adminHome") .usernameParameter("email") .passwordParameter("password") .and().logout() .logoutRequestMatcher(new AntPathRequestMatcher("/logout")) .logoutSuccessUrl("/").and().exceptionHandling() .accessDeniedPage("/access-denied") ; } @Override public void configure(WebSecurity web) throws Exception { web.ignoring() .antMatchers("/resources/**", "/static/**", "/css/**", "/js/**", "/images/**", "/console/**"); } } Step 4: Create a model classes for User and Role As we are using lombok libarary , we dont need to create setter and getter in model class . Also it helps in building mock objects at runtime for unit testing. package com.myjavablog.model; import lombok.AllArgsConstructor; import lombok.Builder; import lombok.Data; import lombok.NoArgsConstructor; import org.hibernate.validator.constraints.Length; import javax.persistence.*; import javax.validation.constraints.Email; import javax.validation.constraints.NotEmpty; import java.util.Set; @Data @Builder @AllArgsConstructor @NoArgsConstructor @Entity @Table(name = "USER") public class User { @Id @GeneratedValue(strategy = GenerationType.AUTO) @Column(name = "USER_ID") private int id; @Column(name = "EMAIL") @Email(message = "*Please provide a valid Email") @NotEmpty(message = "*Please provide an email") private String email; @Column(name = "PASSWORD") @Length(min = 5, message = "*Your password must have at least 5 characters") @NotEmpty(message = "*Please provide your password") private String password; @Column(name = "NAME") @NotEmpty(message = "*Please provide your name") private String name; @Column(name = "LAST_NAME") @NotEmpty(message = "*Please provide your last name") private String lastName; @Column(name = "ACTIVE") private int active; @ManyToMany(cascade = CascadeType.ALL) @JoinTable(name = "USER_ROLE", joinColumns = @JoinColumn(name = "USER_ID"), inverseJoinColumns = @JoinColumn(name = "ROLE_ID")) private Set roles; } package com.myjavablog.model; import lombok.AllArgsConstructor; import lombok.Builder; import lombok.Data; import lombok.NoArgsConstructor; import javax.persistence.*; @Data @Builder @AllArgsConstructor @NoArgsConstructor @Entity @Table(name = "ROLE") public class Role { @Id @GeneratedValue(strategy = GenerationType.AUTO) @Column(name = "ROLE_ID") private int id; @Column(name = "ROLE") private String role; } Step 5: Create Service layer - package com.myjavablog.service; import com.myjavablog.model.User; import org.springframework.stereotype.Service; public interface UserService { public User findUserByEmail(String email) ; public User saveUser(User user); } package com.myjavablog.service; import com.myjavablog.model.Role; import com.myjavablog.model.User; import com.myjavablog.repository.RoleRepository; import com.myjavablog.repository.UserRepository; import org.springframework.beans.factory.annotation.Autowired; import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder; import org.springframework.stereotype.Service; import java.util.Arrays; import java.util.HashSet; @Service public class UserServiceImpl implements UserService { private UserRepository userRepository; private RoleRepository roleRepository; private BCryptPasswordEncoder bCryptPasswordEncoder; @Autowired public UserServiceImpl(UserRepository userRepository, RoleRepository roleRepository, BCryptPasswordEncoder bCryptPasswordEncoder) { this.userRepository = userRepository; this.roleRepository = roleRepository; this.bCryptPasswordEncoder = bCryptPasswordEncoder; } @Override public User findUserByEmail(String email) { return userRepository.findByEmail(email); } @Override public User saveUser(User user) { user.setPassword(bCryptPasswordEncoder.encode(user.getPassword())); user.setActive(1); Role userRole = roleRepository.findByRole("ADMIN"); user.setRoles(new HashSet(Arrays.asList(userRole))); return userRepository.save(user); } } Step 6: Create JPA repositories for User and Role to interact with the databse - package com.myjavablog.repository; import com.myjavablog.model.Role; import org.springframework.data.jpa.repository.JpaRepository; import org.springframework.stereotype.Repository; @Repository public interface RoleRepository extends JpaRepository { public Role findByRole(String role); } package com.myjavablog.repository; import com.myjavablog.model.User; import org.springframework.data.jpa.repository.JpaRepository; import org.springframework.stereotype.Repository; @Repository public interface UserRepository extends JpaRepository { public User findByEmail(String email); } Step 7: Create a controller to save the user and navigate package com.myjavablog.controller; import com.myjavablog.model.User; import com.myjavablog.service.UserService; import org.springframework.beans.factory.annotation.Autowired; import org.springframework.security.core.Authentication; import org.springframework.security.core.context.SecurityContextHolder; import org.springframework.stereotype.Controller; import org.springframework.validation.BindingResult; import org.springframework.web.bind.annotation.RequestMapping; import org.springframework.web.bind.annotation.RequestMethod; import org.springframework.web.servlet.ModelAndView; import javax.validation.Valid; @Controller public class UserController { @Autowired private UserService userService; @RequestMapping(value={"/", "/login"}, method = RequestMethod.GET) public ModelAndView login(){ ModelAndView modelAndView = new ModelAndView(); modelAndView.setViewName("login"); return modelAndView; } @RequestMapping(value="/registration", method = RequestMethod.GET) public ModelAndView registration(){ ModelAndView modelAndView = new ModelAndView(); User user = new User(); modelAndView.addObject("user", user); modelAndView.setViewName("registration"); return modelAndView; } @RequestMapping(value = "/registration", method = RequestMethod.POST) public ModelAndView createNewUser(@Valid User user, BindingResult bindingResult) { ModelAndView modelAndView = new ModelAndView(); User userExists = userService.findUserByEmail(user.getEmail()); if (userExists != null) { bindingResult .rejectValue("email", "error.user", "There is already a user registered with the email provided"); } if (bindingResult.hasErrors()) { modelAndView.setViewName("registration"); } else { userService.saveUser(user); modelAndView.addObject("successMessage", "User has been registered successfully"); modelAndView.addObject("user", new User()); modelAndView.setViewName("registration"); } return modelAndView; } @RequestMapping(value="/admin/adminHome", method = RequestMethod.GET) public ModelAndView home(){ ModelAndView modelAndView = new ModelAndView(); Authentication auth = SecurityContextHolder.getContext().getAuthentication(); User user = userService.findUserByEmail(auth.getName()); modelAndView.addObject("userName", "Welcome " + user.getName() + " " + user.getLastName() + " (" + user.getEmail() + ")"); modelAndView.addObject("adminMessage","This Page is available to Users with Admin Role"); modelAndView.setViewName("admin/adminHome"); return modelAndView; } @RequestMapping(value="/user/userHome", method = RequestMethod.GET) public ModelAndView user(){ ModelAndView modelAndView = new ModelAndView(); Authentication auth = SecurityContextHolder.getContext().getAuthentication(); User user = userService.findUserByEmail(auth.getName()); modelAndView.addObject("userName", "Welcome " + user.getName() + " " + user.getLastName() + " (" + user.getEmail() + ")"); modelAndView.addObject("userMessage","This Page is available to Users with User Role"); modelAndView.setViewName("user/userHome"); return modelAndView; } } Step 8: Create a UI layer using Thymleaf templates . Step 9: Run the application and go to H2 database console by navigating to http://localhost:8081/console

Once the application is up and running , H2 database will be automatically started. You can navigate to http://localhost:8081/console to see the tables created as shown below-
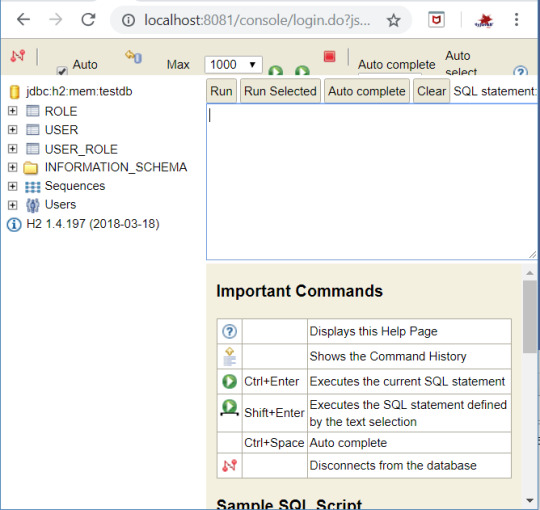
Also you need to insert few roles initially. INSERT INTO ROLE VALUES (1, "ADMIN"); INSERT INTO ROLE VALUES (2, "USER"); Step 10: Now go to application http://localhost:8081/
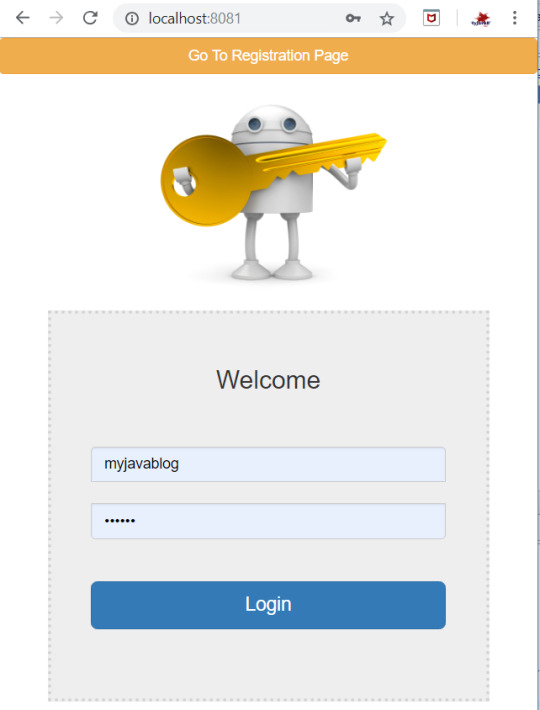
You can navigate to registration page by clicking on "Go to registration page " at the top .
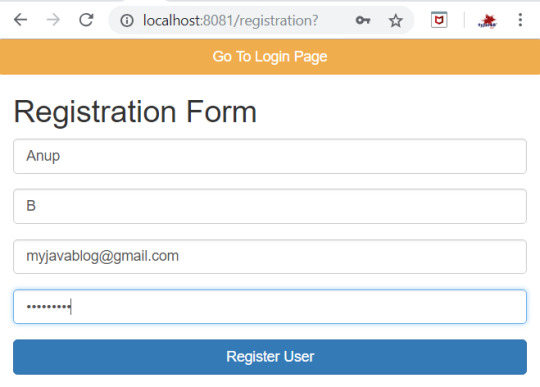
Once you register , User details will be saved to USER table -
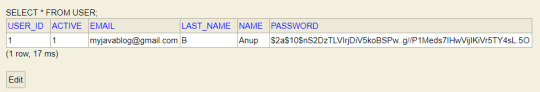
Now when you login with registered user details then you can see the admin page . As registered user is ADMIN role, Admin page will be displayed.
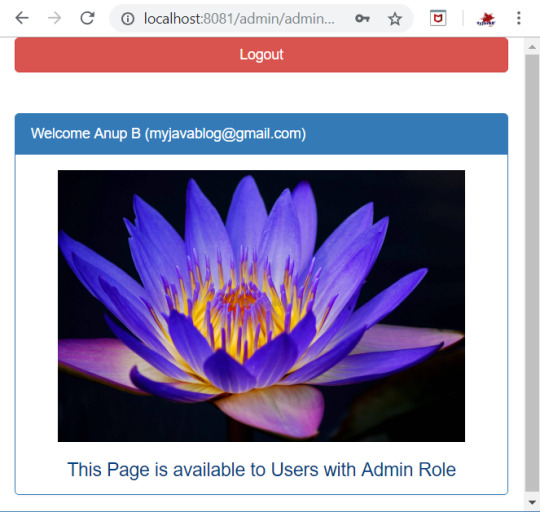
Read the full article
0 notes
Text
300+ TOP MSBI Objective Questions and Answers
MSBI Multiple Choice Questions :-
1. What is the difference between UNION and UNION ALL? A. Union selects only unique row (data) from all queries and Union all selects all rows from all queries. B. Union selects row (data) from all queries and Union all selects all rows from all queries. C. Union selects only unique row (data) from all queries and Union all selects rows from all queries. D. Union selects row (data) from all queries and Union all selects rows from all queries. Ans: a 2. Define Row Number function? A. To generate sequence number. B. To generate sequence number based on order by column. C. To generate number. D. None. Ans: b 3. What is Normalization? Types of normalization? A. Join the tables B. Move the data into tables. C. Split the table to reduce duplicates and it has five types. D. None Ans: c 4. What are different types of joins? A. Inner, outer, self join. B. Equi join and cross join. C. Right outer join. D. All above. Ans: d 5. What are the advantages of using stored procedure? A. Pre executable program. B. We can get the data. C. Security. D. It is similar to function. Ans: a 6. What is BCP? A. Bulk copy program. B. Business continuity program. C. A and B. D. None. Ans: a 7. Define Index? A. Predefined pointers to data page. B. It is primary key. C. It is foreign key. D. None. Ans: a 8. What command do we use to rename db, table, and column? A. Invoke command B. Commit C. Rename D. None. Ans: c 9. Define having clause? A. It is similar to where but must use group by clause. B. It is equal to where clause. C. None. D. It is equal to from clause. Ans: a 10. What are the basic functions system databases? A. To create functions. B. To create stored procedure. C. To maintain metadata information. D. None. Ans: c

MSBI MCQs 11. Explain ETL process? A. Extract, Translation, Loading. B. Extract, Transformation , Loading C. Both a and b. D. None. Ans: b 12. Difference between for loop and for each loop container? A. For loop based on conditions and for each loop based on objects collections. B. For loop based on objects collections and for each loop based on objects collections. C. None. D. Both a and b. Ans: a 13. What does a control flow do? A. To control workflow. B. To control events. C. To control data flows. D. To control lookup. Ans: a 14. Explain event handlers? A. To handle data validations. B. To handle errors. C. To handle events. D. None. Ans: c 15. SSIS 2008 configuration types? A. Five. B. Four. C. Three. D. One. Ans: a 16. Define Lookup transformation? A. Used as reference table. B. Used as master table. C. Used as fact table D. None. Ans: a 17. Define synchronous transformations? A. Input rows count and Output rows count are same. B. Input rows count and Output rows count are not same. C. None. D. Input rows count and Output rows count are different. Ans: a 18. How to rename file using SSIS tasks? A. Using lookup. B. Using Data flow. C. Using File system task. D. None. Ans: c 19. What does mean by data auditing? A. To maintain data load statistics in ETL process. B. To know the errors. C. To know the Primary keys. D. None. Ans: a 20. How many container tasks available in SSIS? A. One. B. Two. C. Three. D. Four. Ans: d 21. Define role play dimensions? A. One dimension used multiple times in the cube. B. One dimension used in different cubes. C. Shared across cubes. D. None. Ans: a 22. Define dimension usage in SSAS Cube? A. To maintain cube data size. B. To know the relationships between dimensions and fact. C. To build business logic. D. None. Ans: b 23. MDX stands? A. Memory, Distribution, extensions. B. Memory, dimension, expressions. C. Multi, dimension, expressions. D. None Ans: c 24. DSV stands? A. Data source View. B. It is view. C. It has relationships and metadata. D. All above. Ans: d 25. How many types of actions available in the Cube? A. One. B. Two. C. Three. D. None. Ans: c MSBI Objective Type Questions with Answers 26. What do you understand by dynamic named set (SSAS 2008)? A. To create dynamic set of members. B. To create set of members. C. None. D. Both a and b. Ans: a 27. How many types of dimension are possible in SSAS? A. Four. B. Five. C. Six. D. Seven. Ans: c 28. In which scenario, you would like to go for materializing dimension? A. To increase spee B. To decrease memory size. C. Both. D. None. Ans: a 30. What are the options to deploy SSAS cube in production? A. Using BIDS. B. Using SSMS. C. Using XMLA. D. All the above. Ans: d 31. Describe Reporting Lifecycle? A. Reports and reports models. B. Report authoring, Management, Delivery. C. Both. D. None. Ans: b 32. What can SQL Server Reporting Services do? A. To create files. B. To create tables. C. To create Reports. D. None. Ans: c 33. Define reporting processing? A. Report data processing. B. Report rendering process. C. Report delivery process. D. All the above. Ans: d 34. How many default rending options are available in SSRS2008? A. Four. B. Five. C. Two. D. One. Ans: a 35. What is the usage of Report Builder? A. To create reports. B. To create reports for users. C. Business users create reports. D. None. Ans: c 37 How many architecture components of SSRS 2008? A. Five. B. Six. C. Seven. D. None. Ans: b 38. Explain on SSRS2008 Reporting Items? A. Tablix,Chart,List B. Sub Report. C. Both A and B. D. None. Ans: c 39. What does mean by nested datasets? A. Used datasets with in dataset. B. A dataset. C. None. D. A table. Ans: a 40. How many command line utilities of SSRS2008? A. Three. B. Four. C. One. D. None. Ans: a 41. You are creating a SQL Server 2008 Integration Services (SSIS) package for Company.com. The package contains six Data Flow tasks and three Control Flow tasks. You should alter the package Which is the correct answer? A. You should increase the two Control Flow tasks and one Data Flow task to a container. Change the TransactionOption property of the container to Supported. B. You should increase the two Control Flow tasks and one Data Flow task to a container. Change the TransactionOption property of the container to Disabled. C. You should increase the two Control Flow tasks and one Data Flow task to a container. Change the TransactionOption property of the container to Required. D. You should increase the two Control Flow tasks and one Data Flow task to a container. Change the TransactionOption property of the container to RequiredNew. Ans: C 42. You are managing a SQL Server 2008 Reporting Services (SSRS) sample which does not give some same rendering extensions for Company.com. You should make sure that you could set the server in order to render to Microsoft WorWhich is the correct answer? A. You should change the AppSetttings.config file. B. You should change the Global.asax file. C. You should change the Machine.config file. D. You should change the RSReportServer.config file Ans: D 43. You are creating a SQL Server 2008 Integration Services (SSIS) package on a SQL Server 2008 database for Company.com. In order to develop a failure recovery plan that is published for a SQL Server. Which is the correct answer? A. You should back up the master database. B. You should back up the local database. C. You should back up the system database. D. You should back up the systemdb databse. Ans: A 44. You are developing a SQL Server 2008 Reporting Services (SSRS) instance of report model for Company.com.In the Report Builder tool, the users should need to create their SSRS reports. The data source they used will include a Microsoft SQL Server 2008 database. Which include 1000 tables? You should design the report model for users, and allow access to only the 20tables which they require for reporting. Which is the correct answer? A. You should develop DataSet using the Web Service to Schema(s) option. B. You should develop DataTable using the Web Service to Schema(s) option. C. You should develop a data source view and select only the required tables and views. D. You should set the data source view in the setting file. Ans: C 45. You are managing a SQL Server 2008 Analysis Services (SSAS) database for Company.com.A sales manager called Clerk is responsible for the sales of bikes in the Northeast region. You decide to give some rights to the rights to Clerk to visit the database.You won two roles below called Southern Region and Nikes. Their schemas are listed below:You have make The Visual Totals properties attribute true for roles above.You should make sure that Clerk could browser the workers in the Product dimension which link to the Nikes category in the Southern region. Which is the correct answer? A. You should increase Clerk to a Nikes role B. You should increase Clerk to the Southern Region role. C. You should increase Clerk to a new role which owns components below: D. .} as the permitted configuration.{...} as the permitted E. You should increase Clerk to the default Region role. Ans: C 46. You are managing a SQL Server 2008 Analysis Services (SSAS) database which includes a Sale dimension that includes the Category and Subcategory properties for Company.com.There is a rigid relationship type for properties. The data source for the Sale dimension alters the relationship between the Type and Sub Type values. You should make sure that you could run an XML to operate he dimension to reflect the change normally for Analysis (XMLA). Which is the correct answer? A. You should utilize the ProcessDefault command. B. You should utilize the ProcessClear command. C. You should utilize the ProcessIndexes command. D. You should utilize the ProcessDefault and the ProcessClear commands. Ans: D 47. You are managing a SQL Server 2008 Analysis Services (SSAS) instance for Company.com. In order to execute the Usage-Based Optimization Wizard you should make query logging enable. Which is the correct answer? Which is the correct answer? A. You should make the QueryLogSampling server attribute default value. B. You should make the QueryLogSampling server attribute 5. C. You should configure the server property of DefaultFolders. D. You should configure the QueryLogConnectionString server attribute and set a valid connection string. Ans: D 48. You are managing a SQL Server 2008 Analysis Services (SSAS) database for Company.com.You get the Duplicate Key error when you operate the Analysis Services database.You should alter the ErrorConfiguration attribute in order to make processing run normally. Which is the correct answer? A. You should alter the Dynamic Management View (DMV) B. You should alter the Local Group C. You should alter the dimension D. You should alter the Transactions Log Ans: C 49. You are managing a SQL Server 2008 Analysis Services (SSAS) database for Company.com. In order to update data in a partition each hour you should run the incremental processing method. In order to solve the problem, which is the correct answer? A. You should utilize ProcessAdd for Analysis (XMLA) command B. You should utilize default command for Analysis (XMLA) C. You should utilize ProcessNone for Analysis (XMLA) command D. You should utilize ProcessView for Analysis (XMLA) command Ans: A 50. You are developing a SQL Server 2008 Reporting Services (SSRS) report for Company.com.Assembly should be created in order to run real-time lookup and currency conversion. The assembly has a static class named daily which lives in the namespace HomeCalc.there is a method called DMO which need two arguments, Cuurnt and HomeCalcWhen the report is operating, you should reference the ToEUR method in an expression to convert USD to USO. Which is the correct answer? A. You should use the expression of =Code. HomeCalDaily. USO (Fields! Cuurnt.Value,” DMO”) B. You should use the expression of =Code! HomeCalDaily. USO (Fields! Cuurnt.Value,”DMO”) C. You should use the expression of = HomeCalDaily.USO (Fields! Cuurnt.Value,”USD”) D. You should use the expression of = HomeCalc! Daily.USO (Fields! Cuurnt.Value,”USD”) Ans: C MSBI Questions and Answers pdf Download Read the full article
0 notes
Text
300+ TOP Yii Framework Interview Questions and Answers
Yii Framework Interview Questions for freshers experienced :-
1. What is Yii Framework? Yii is an open source, web application framework based on MVC. It is written in PHP and used to design PHP applications. This application was started on January and completed in December 2008. 2. Why does Yii Framework run so fast? Yii Framework run so fast because it uses sluggish loading technique which does’t include class file until the class is initially used. 3. What are the features of Yii Framework? There are various features of Yii Framework: It uses MVC design pattern Web Service available for Apps like android Internationalization and localization translation for multilingual. It provides Caching for speed up the application It manages Error handling and logging for tracking It provides cross-site scripting (XSS), cross-site request forgery (CSRF) protection It provides PHP unit and Selenium for testing. It provides automatic code generation that helps to fast development etc. 4. How can we define a form model? We can define a form model in Yii1.1 by using following code: class MyLoginForm extends CFormModel { public $username; public $password; public $rememberMe=false; } 5. What are the components available in Yii Framework? There are following components available in Yii Framework: db: It is used for database connection. AssetManager: It manage the publishing of private assets files authManager: It manages role-based access control cache: It manages caching functionality clientScript: It manages javascript and CSS coreMessages: It provides translated core messages errorHandler: It manages errors handling. ThemeManager: It manages themes urlManager: It provides URL parsing and creation functionality statePersister: It provides mechanism for persisting global state session: It manages session securityManager: It manages Security 6. Which file loaded firstly while run a Yii application? In Yii Framework, index.php file loaded first to display home page of the application. 7. How can we install or setup Yii Framework in our local system? We can install or setup Yii Framework by using following given steps: Download the Yii setup from its official website or github. Extract the code into our server root directory. Open command line terminal and type the following command. php path-to-yii-folder/framework/yiic webapp After execution of above command, it will ask for the confirmation of creating a new application, on selecting yes, it will create an application. 8. What is the Yii application life cycle? Yii application life cycle includes the following steps: Pre-initialize the application with Capplication::preinit() Set up the class autoloader and error handling Register core application components Load application configuration Initialize the application with Capplication::init() Register application behaviors Load static application components Raise an onBeginRequest event Process the user request Collect information about the request Create a controller Run the controller Raise an onEndRequest event 9. What are the database related functions in Yii? In Yii, databse releted functions are: Queryfind findAll findByPk findBy 10. How can we connect to the database in Yii? In Yii, we can connect database by using following code: We can configure database related settings in the main.php file reside into the config folder. 11. What is a YiiBase in Yii Framework? In Yii Framework, YiiBase is a helper class that provides functionalities of common framework. We should not use YiiBase directly, if we want to access helper class, we have to use its child class where we can customize the methods of YiiBase. 12. What is “gii” and how it works in Yii Framework? In Yii Framework, gii is a module that provides Web-based code generation capabilities to the developer. We need to change the main configuration file of our application. return array( 'modules'=>array( 'gii'=>array( 'class'=>'system.gii.GiiModule', 'password'=> ) ) ) 13. How can we access application components in Yii Project? We can access an application component by using following code: Yii::app()->ComponentID Where, ComponentID refers to the ID of the component. 14. How can we get current controller id in Yii ? We can get current controller in Yii Framework by using given code: $controllerid = Yii::app()->controller->id; 15. How can we set default controller in our Yii Project ? We can set default controller in our Yii Project by using given code: 16. What is the difference between “render” and “renderpartial” in Yii Framework? In Yii Framework, render() is commonly used to render a view that corresponds to what a user sees as a “page” in your application. renderPartial() is used to render a web page without layout. Yii Php Framework Questions and Answers Pdf Download Read the full article
0 notes