#defensive vulnerability pricing model
Explore tagged Tumblr posts
Text
How many missiles would the United States need in a conflict in the Indo-Pacific? How much ammunition? Perhaps most important, by how much do current stockpiles fall short of what would be needed in a war?
The first-ever US National Defense Industrial Strategy, published in 2022, sparked important discussions on these and other questions about the US defense industrial base. These questions in turn resulted in improvements across the strategy’s four strategic priorities: resilient supply chains, workforce readiness, flexible acquisition, and economic deterrence. Despite these improvements, however, a significant gap remains in producing the quantitative difference between peacetime stockpile requirements and the acute, continuous, and probable long-term demand needs during wartime.
Consider a hypothetical conflict with China in the Pacific. War games estimate that the United States could expend more than five thousand long-range missiles within the first few weeks of engagement. At the same time, several analysts and government agencies have highlighted the difficulty of replenishing weapons currently used in Ukraine—a much smaller-scale conflict compared to what should be anticipated in a war with China.
There are two ways to deal with this challenge: (1) enabling production in advance to stockpile and preposition equipment; and (2) replenishing materiel and stockpiles after hostilities have begun. However, the latter strategy often overlooks the complex challenge of rapidly increasing production to meet wartime demands, which could leave the United States vulnerable in the early stages of conflict.
Although the US government has begun investing in bolstering the defense industrial base, the current contracting system lacks the flexibility needed to transition from low demand to a rapid ramp-up of production to replenish depleted stockpiles. To address this issue, the United States should adopt an option contract model for armament procurement. This model involves the government paying a premium on current orders bought at the peacetime stockpile level with the option—but not the obligation—to purchase a significantly larger amount within a fixed timeframe, providing the defense industrial base with the necessary funds to develop and maintain rapid replenishment capabilities in the event of a conflict.
What are option contracts?
Like options in the stock market, an option contract grants the buyer—in this case, the US government—the right to purchase arms and ammunition at a preset price at a later date. If the government opts not to exercise this option, typically because peace prevails, the contractor retains the premium. This premium serves as a financial investment in future rapid replenishment capability and a continued steady demand signal for the industry, encouraging readiness and innovation without requiring the government to maintain unnecessary and wasteful stockpiles.
How this would work in practice
To illustrate why option contracts would be an improvement over the current model of US armament procurement, take the case of Tomahawk missiles. A February 2023 Center for Strategic and International Studies report estimated that the United States would expend four hundred Tomahawk missiles in the first three weeks of a full-scale conflict with China. In 2022, the US Navy procured 154 Tomahawks to be bought over a three-year period, translating to an annual production rate of about fifty missiles. This rate is orders of magnitude lower than what would be required to replenish expenditures during a full-scale conflict.
Applying the proposed option contract model to this scenario, the Navy would pay a premium on its annual order of fifty missiles, with the option to purchase an additional four hundred missiles within a single year if needed. The contractor would use the premium to invest in the capacity to scale up production, ensuring that the company can meet the full contract requirements on short notice if the need arose. This approach not only provides the contractor with the capital to enhance its production infrastructure and an incentive to maintain overcapacity, but also ensures that the United States has a ready supply of crucial munitions in times of need.
There are four main benefits of the option contract model:
Enhanced production readiness: By providing a financial incentive upfront, the option contract model enables defense contractors to invest in infrastructure and workforce improvements as a reserve that can be rapidly scaled up in response to a crisis.
Improved flexibility: This model allows the US government to lock in production capacity without committing to immediate full-scale procurement, balancing budget constraints with strategic readiness. This also helps meet small increases in demand in the event of smaller-scale conflicts.
Stimulated industry investment: The premium paid on option contracts signals sustained demand, encouraging defense contractors to prioritize and invest in production capabilities and innovation, rather than stock buybacks or similar programs that benefit shareholders at the expense of the government.
Mitigated risk: This approach hedges geopolitical risk, ensuring necessary arms and ammunition are available in short order during critical, unforeseen contingencies.
At the same time, several challenges must be addressed:
Potential for rising costs: The premium paid for option contracts will increase procurement costs. Military programs are generally under-resourced in the constrained budget environment, so the rising procurement costs could lead to lower peacetime stockpile levels. If the increased capacity is never utilized, the premium paid may be viewed as government waste. However, the money spent on training the workforce and expanding capacity may be partially recouped by savings in follow-on contracts. A detailed cost-benefit analysis is essential to ensure that the increased expenditure aligns with strategic needs and budgetary constraints.
Difficulties negotiating contracts: Establishing effective option contracts requires careful negotiation to define terms, production capabilities, and performance metrics, ensuring that both the government and contractors meet their obligations. The military-industrial base has not utilized these types of contracts in the past. This unfamiliarity could add time to complete what are currently straightforward contracts.
Limits to industry capacity: Not all defense contractors have the capacity to scale up production rapidly, especially with “exquisite” weapon systems, which often involve high-end technology, are difficult and expensive to produce at scale, and require numerous subcontractors to complete. It is crucial, therefore, to assess the capability of industry partners and ensure that they can meet the demands of an option contract. There would need to be a requirement for the contractor to demonstrate the ability to surge its production to ensure good-faith use of the premium.
The option contract model represents a viable solution to address the current shortcomings in the US defense industrial base for some munitions. By incentivizing contractors with upfront premiums, this approach can enhance production readiness, flexibility, and industry investment, ultimately ensuring that the United States is better prepared to meet the demands of future conflicts.
10 notes
·
View notes
Note
Do you think Dorothy from the books was a better role model for girls than in the MGM Wizard of Oz film?
Just to answer this, I reread The Wonderful Wizard of Oz over the last two days. I'm not very familiar with the rest of the Oz books, but since the movie is only based on the original book, I suppose it's best to compare just the two of them.
I don't think either the book's Dorothy or the MGM film's Dorothy is a better role model than the other. They're just slightly different.
I understand why a lot of people consider Baum's Dorothy a better role model than movie Dorothy. She has more of a down-to-earth, can-do attitude than movie Dorothy, whom some critics think is reduced to a weepy damsel in distress. I especially understand why some people are annoyed by the movie's rewrites to the scenes at the Wicked Witch's castle, where Dorothy's three male friends come to her rescue and where she splashes the Witch with water by accident. In the book the Scarecrow and Tin Woodman are destroyed by the Winged Monkeys, while the Lion is captured along with Dorothy and locked in a pen; Dorothy stands up to the Witch when she tries to take her silver shoes and throws the water on her in anger (not knowing it will melt her, but it's still a deliberate act); and afterwards, she frees the Lion and then rallies the Winkies to repair the Scarecrow and Tin Woodman. I won't deny that the movie's rewrite adheres more to traditional gender roles and probably reflects Hays Code standards of how a "good girl" should behave.
But I don't mind the fact that movie Dorothy is slightly more vulnerable and emotional than Baum's Dorothy. In the first place, she's older than Baum's Dorothy: even if she's younger than Judy Garland's 16 years, she must be at least 12, while Baum's Dorothy might be as young as 6. Between hormones and higher emotional intelligence, it's natural for teenage or preteen girls to be more emotional than little girls. Secondly, movie Dorothy's added soulfulness and dreaminess are part of her appeal. I'm not sure "Over the Rainbow" would seem in character for Baum's no-nonsense little Dorothy to sing.
There's also the fact that the movie's Wicked Witch of the West is much more powerful and dangerous than Baum's Witch. In the book, she can't physically harm Dorothy because the Good Witch of the North's magic kiss protects her, so she just makes her work as a scullery maid. She's also a bit of a scaredy-cat: she's afraid of the Cowardly Lion, and she can't steal the silver shoes at night while Dorothy is sleeping because she's afraid of the dark! With the movie's far more imposing Witch and the real danger Dorothy faces of being killed, it's hard to blame movie Dorothy for being more terrified. She also has more to deal with in Kansas than Baum's Dorothy does: there's no Miss Gulch trying to have Toto killed in the book.
Last but not least, movie Dorothy is still spunky! She still slaps the nose of a lion in Toto's defense (not yet knowing that he's a coward), she stands up to the Wizard even when she thinks he's a fearsome giant head with immense magical powers, and in the Witch's castle, even though her friends free her from the hourglass room, she's still the one who ultimately saves the day. She deserves credit for her presence of mind when she spots the pail of water and throws it onto the Scarecrow to save him from burning, even if it is by accident that she splashes the Witch too.
I think both Dorothys are good characters and role models: Baum's Dorothy for her resilience, optimism, and down-to-earth intelligence, and movie Dorothy for her relatable character arc of longing to escape from her troubles, only to learn that it's not worth the price of leaving her home and her loved ones behind. Not to mention the qualities they both share: warmth, kindness, courage, loyalty, and affection.
#dorothy gale#the wizard of oz#the wonderful wizard of oz#book vs. movie#comparison#fictional characters
27 notes
·
View notes
Text
Top 8 Chess Strategies Every Beginner Must Learn to Win More Games
Chess is not just a game; it is intelligence and strategy. For beginners, understanding the basic techniques is the foundation to improve and succeed in many games. Once you get these basics right, you can transition into random moves and playing with purpose and accuracy.
In this blog we will discuss the top 8 chess techniques that every beginner should learn to improve their game Plus, see how KingCompiler, the first chess course, can guide you in making these techniques in the exact same way.
1. Control the center from the beginning The center of the board (squares d4, d5, e4, e5) is the most important area in chess. Controlling it gives your piece more strength and power.
How to do it:
Start by moving pawns to control the center (e.g., e4 or d4).
Rotate your knights and bishops to have a mid-field effect.
At KingCompiler, students learn the importance of central control through practical exercises and expert guidance.

📢 Welcome to Chess Academy! 🌟 🆓 We’re offering FREE Trial Classes for all levels — beginners to advanced! 🎓 Why Choose Us? ✅ World-class coaching by experienced players and coaches ✅ Interactive online sessions with personalized attention ✅ Build critical thinking, strategy, and focus ✅ Suitable for ALL ages and skill levels 🚀 Book a Free Trial Class at: https://forms.gle/M1x5dVL5tru5QSSw5 📱 WhatsApp us at +91 9903600848 ♟️ Let the game begin!
2. Make your pieces first A common early mistake is not getting pieces (knight, bishops, etc.) fast enough. Leaving them idle can hinder your chances of winning.
Key tips:
Prioritize the development of his army and bishops.
Avoid moving the same piece repeatedly in the opening.
KingCompiler ensures that beginners understand the importance of progress and teaches effective ways to get pieces in play.
3. The King Puts Safety First (Castling) . Protecting your king is an important option. Leaving your king out can leave you vulnerable to previous attacks.
What you need to do:
Protect your king by the gates of the castle in the morning.
Avoid unnecessary pawn behavior with the king.
KingCompiler teaches beginners the importance of king defense and how to balance offense and defence.
4. Avoid moving the same piece repeatedly in the opening Repetition wastes time and gives your opponent a progression advantage.
Why it matters:
Any move should help create a stronger position.
Avoid “block-fitting” without a clear purpose.
KingCompiler’s class list emphasizes efficient block movement and proper programming.

5. Create a solid pawn system Your pawns are the backbone of your position. Weak pawn policies can lead to long-term losses.
Best Practices:
Avoid isolated, double, or backward pawns.
Target connected pawns helping each other.
KingCompiler trains beginners to avoid common pitfalls in order to build robust pawn systems.
6. Learn the basic checkmate system Checkmating an opponent is the main goal of chess. Beginners should focus on creating basic prototypes e.g.
Back-Rank Checkmate.
King and Rook Checkmate.
Checkmate in King and Queen.
In KingCompiler, students use this model until they create a second product.
7. Understand the relative value of each piece Each piece has a specific value (e.g. Pawns = 1, Knights/Bishops = 3, Rooks = 5, Queens = 9). Understanding this helps you make better decisions about change.
Key tips:
Avoid unnecessary changes unless they benefit you.
Always consider piece price and position.
KingCompiler provides guidance exercises to help players figure out when and why to swap pieces.

📢 Welcome to Chess Academy! 🌟 🆓 We’re offering FREE Trial Classes for all levels — beginners to advanced! 🎓 Why Choose Us? ✅ World-class coaching by experienced players and coaches ✅ Interactive online sessions with personalized attention ✅ Build critical thinking, strategy, and focus ✅ Suitable for ALL ages and skill levels 🚀 Book a Free Trial Class at: https://forms.gle/M1x5dVL5tru5QSSw5 📱 WhatsApp us at +91 9903600848 ♟️ Let the game begin!
8. Transition Smoothly Between Opening, Middle, and Endgame
Beginners often struggle with connecting the phases of a game. Understanding how to transition is essential for long-term success.
Tips for a Smooth Transition:
Focus on piece activity in the opening.
Look for tactical opportunities in the middle game.
Master key endgame principles like pawn promotion and opposition.
At KingCompiler, we guide beginners through each phase with step-by-step instruction and real-game scenarios.
Why These Strategies Matter
Mastering these eight strategies will:
Improve your decision-making.
Build your confidence as a chess player.
Help you win more games against opponents of all levels.
How KingCompiler Can Help You Master Chess Strategies
KingCompiler is dedicated to helping new learners excel in chess. Here’s how we can support your journey:
Beginner-Friendly Curriculum: Learn strategies step-by-step with clear explanations and interactive lessons.
Expert Coaches: Receive guidance from experienced instructors who simplify complex concepts.
Practice Matches: Apply your knowledge in games with feedback from professionals.
Tactical Training: Sharpen your skills with targeted exercises designed to reinforce key strategies.
Final Thoughts
Chess is a game of growth, and mastering these beginner strategies will set you on the path to success. Whether it’s controlling the center, developing your pieces, or protecting your king, each strategy is a building block for becoming a stronger player.
#chess#chess tips#chess tricks#chess strategy#chess academy#chess class#chess moves#how to win in chess#how to play chess#best chess moves#gukesh#gukesh chess#chess mistakes#common chess mistakes#kids game#mind games#kids#brainstorming#kingcompiler
3 notes
·
View notes
Text
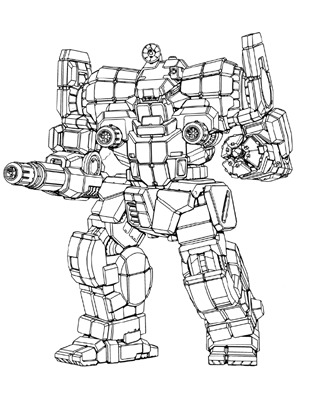
Awesome AWS-9Q (DeLacey)
Mass: 80 tons Chassis: Technicron Type G Power Plant: Pitban 240 Cruising Speed: 32.4 kph Maximum Speed: 54 kph Jump Jets: None Jump Capacity: 0 meters Armor: Durallex Heavy Special Armament: 3 ER PPC (C) 1 HAG/20 Manufacturer: Lüneburg Vehicle Corporation,Irian BattleMechs Unlimited,Technicron Manufacturing Primary Factory: Braunschweig,Irian,Savannah Communication System: Garrett T19-G Targeting & Tracking System: Dynatec 2780 Introduction Year: 3150 Tech Rating/Availability: F/X-X-X-E Cost: 8,083,800 C-bills
Overview The Awesome was designed in 2665 for the Star League by the Technicron Conglomorate and was based on the aging STR-2C Striker. While not as fast as its forefather, the Awesome is a strong assault 'Mech.
Capabilities The Awesome's abilities are nearly entirely dependent on its particle projection cannons. The AWS can withstand a severe and consistent onslaught from its weaponry thanks to several heat sinks. With one and a half tons more armor than the Striker, the AWS is more protected than even the BattleMaster. The Amazing, like any other BattleMech, has weaknesses. While it is lethal at range, it is less effective in close-quarters combat since its PPCs have a tougher time connecting with the victim. In that case, it just possesses a light weapon and a left fist to fall back on. Because of its limited mobility, it is vulnerable to flanking attacks from speedier opponents seeking to get past the PPCs. While they face arguably of the heaviest rear armor found on any BattleMech, the Awesome's lack of rear facing armaments or a weapon mount on its left arm has offered numerous MechWarriors a fighting chance. Formations of Awesomes (or even just a few) are incredibly effective and tough to stop or defeat when correctly placed by commanders who are knowledgeable of the AWS's limitations.
Deployment A basic upgrade to the original 8Q introduced in 3057, the heat sinks are upgraded to double heat sinks and are reduced to nineteen. The saved weight is used to add a fourth PPC to the 'Mech as well as a Guardian ECM Suite. Although there was some criticism for using basic PPCs and not upgrading to ER models, the 9Q proved itself during Operation Guerrero to be quite devastating. This clan salvage refit by Kerrie DeLacey swaps the left arm-mounted PPC for a Type 0 HAG/20 and two tons of ammunition, the other PPCs for Type DDS "Kingston" cERPPCs, and removes the small laser and ECM. To make room for the increased payload size, the heat sinks have been exchanged for their Clan equivalents.
History Awesomes can be found in every military House. Because the Free Worlds League has the last remaining manufacturing factories capable of generating the Awesome, it also has the most Awesomes of any of the Great Houses. Opinions on the 'Mech vary greatly within the League. Many people laud its powers, while others believe that its limited mobility is too high a price to pay for what it can do. Similar sentiments exist in the other Houses, but none of them can debate the issue beyond academics. Few commanders would turn down the opportunity to acquire an Awesome for their army. The Awesome is typically used to assault a fixed position or to breach the enemy's line of defense. They are also in demand for defensive operations. MechWarriors piloting the Awesome can expect to be involved in heavy battle and to be charged with obtaining or guarding the most crucial objectives from the adversary.
Notable MechWarriors Karrie DeLacey: A former MechTech of the Magistracy Armed Forces, Karrie fell into the mercenary life once she found that the skills she learned on the battlefield weren't as applicable in the civilian sector. After a disastrous first and only deployment with the now-extinct Dark Wolves Mercenary Company, she founded a mercenary company of her own: DeLacey's Last Resort. Extremely proud and boastful, Karrie drew up the plans for her custom Awesome as part of an argument on the proper battlefield role such a mech should have. The design trades pure firepower and heat management for greater single-point impact and a greater ability to brawl, "like something that big ought to be able to." While unconventional, it has served her well on the battlefields of the Last Resort's ugliest deployments. Still a proud Canopian citizen, Karrie pays each year to receive dossiers on elections back home, sending her ballot via the HPG network. While exceptions for the mandatory elections are made for citizens traveling abroad, she claims it "just wouldn't sit right not to."
Type: Awesome Technology Base: Mixed (Standard) Tonnage: 80 Battle Value: 2,517 Equipment Mass Internal Structure 8 Engine 240 Fusion 11.5 Walking MP: 3 Running MP: 5 Jumping MP: 0 Double Heat Sink: 19 [38] 9 Gyro: 3 Cockpit: 3 Weapons and Ammo Hyper-Assault Gauss Rifle/20 Ammo (12) CT 2 2 ER PPC RT 2 6 3 Double Heat Sink RT 6 3 HAG/20 LA 6 10 Double Heat Sink LA 2 1 ER PPC LT 2 6 4 Double Heat Sink LT 8 4 ER PPC RA 2 6 2 Double Heat Sink RA 4 2
Features the following design quirks: Battle Fists (LA)
#battletech#here's the writeup on my custom 9Q! Definitely an older and uglier machine but I think I've put work in on the right places#And yeah yeah I know I haven't put CASE around the HAG capacitors but I don't have the equipment for a factory rebuild so I get what I get
8 notes
·
View notes
Text
AI TRiSM: Building Trust in Artificial Intelligence

Artificial Intelligence (AI) is transforming industries, from healthcare to finance, but its rapid adoption raises concerns about trust, security, and ethics. Enter AI TRiSM—AI Trust, Risk, and Security Management—a framework designed to ensure AI systems are reliable, fair, and secure. This emerging standard is reshaping how organizations deploy AI responsibly, fostering confidence among users and stakeholders.
What is AI TRiSM?
AI TRiSM is a comprehensive approach to managing the challenges of AI systems. It focuses on four key pillars: explainability, model operations, application security, and privacy. Explainability ensures AI decisions are transparent and understandable, reducing the "black box" effect. Model operations streamline the AI lifecycle, from development to maintenance, ensuring consistent performance. Application security protects AI models from cyber threats, while privacy safeguards sensitive data, aligning with global regulations like GDPR.
By integrating these elements, AI TRiSM addresses risks such as algorithmic bias, data breaches, and ethical dilemmas, making it a vital tool for organizations aiming to leverage AI safely.
Why AI TRiSM Matters
As AI becomes integral to decision-making, trust is paramount. A biased AI model in healthcare could lead to misdiagnoses, while a vulnerable financial algorithm might enable fraud. AI TRiSM mitigates these risks by enforcing fairness, accountability, and robustness. For instance, regular model monitoring can detect biases, while adversarial testing strengthens defenses against cyberattacks.
Moreover, AI TRiSM ensures compliance with evolving regulations, helping organizations avoid hefty fines and reputational damage. It also builds public confidence, encouraging wider AI adoption across sectors.
Real-World Impact
AI TRiSM is already making waves. In healthcare, organizations use it to audit diagnostic tools, improving accuracy and fairness. Financial institutions rely on it to secure fraud detection systems, reducing losses. Retail companies apply fairness audits to pricing models, enhancing customer trust. These examples highlight AI TRiSM’s role in driving ethical and effective AI solutions.
The Future of AI TRiSM
As AI evolves, so will AI TRiSM. Advances in explainability and ethical certifications are on the horizon, promising even greater transparency. However, challenges like skill shortages and high implementation costs remain. Organizations must invest in training and robust governance to stay ahead.
In a world increasingly powered by AI, AI TRiSM is the cornerstone of responsible innovation. By prioritizing trust, risk management, and security, it paves the way for a future where AI benefits society while minimizing harm.
0 notes
Text
A Homeowner’s Guide to the Best Residential Surveillance Cameras
When it comes to protecting your home, peace of mind starts with knowing what’s happening around your property—whether you're there or not. That’s where modern surveillance comes in. Today, having one of the best residential surveillance cameras is more than just a safety measure—it’s a smart decision that empowers homeowners with awareness, control, and confidence.
Security systems have come a long way from grainy footage and hardwired setups. Now, you can monitor every corner of your home from your phone, receive real-time alerts, and even interact with visitors remotely.
Why Residential Surveillance Matters
Residential properties face a range of security risks: theft, vandalism, trespassing, and package theft are among the most common. Whether you live in a quiet neighborhood or a busy urban setting, cameras act as both a deterrent and a valuable resource when incidents occur.
Beyond crime prevention, cameras also help with:
Monitoring children or elderly family members
Keeping an eye on service professionals
Checking in on pets
Capturing real-time updates while you’re away
With high-definition video and intelligent features, home surveillance has become an essential part of modern homeownership.
Key Features to Look For
Choosing from the best residential surveillance cameras means focusing on the features that truly enhance your home security:
High Definition (HD) or 4K Video: Clear footage makes it easier to identify faces, license plates, and details.
Night Vision: Ensures visibility even in complete darkness.
Motion Detection: Alerts you only when there's relevant movement, minimizing false alarms.
Two-Way Audio: Lets you communicate with someone at your door or scare off potential intruders.
Cloud Storage or Local Backup: Secure storage of recorded footage in case you need to review it.
Mobile App Integration: Enables remote access, real-time alerts, and easy sharing of video clips.
Weatherproof Design: Crucial for outdoor cameras in various climates.
Each of these features contributes to making your system more effective and user-friendly.
Indoor vs. Outdoor Cameras
Your camera placement should match your security goals. Outdoor cameras cover driveways, front doors, and backyards—areas where intruders might approach. They need to be weather-resistant and durable. Indoor cameras, on the other hand, are useful for entryways, hallways, and common areas.
Many homeowners choose a mix of both to cover all vulnerabilities. This blended approach ensures that if someone does manage to get past your outdoor defenses, they’re still being monitored inside.
Wired or Wireless?
Wireless cameras are generally easier to install and offer more flexibility in terms of placement. They connect via Wi-Fi and are ideal for those who don’t want to drill into walls or run extensive wiring.
Wired cameras, however, tend to provide more consistent performance, especially in areas with poor Wi-Fi connectivity. They’re usually preferred for long-term setups where reliability is critical.
Smart Home Integration
Today’s top surveillance solutions are designed to work with other smart devices in your home. This includes integration with voice assistants like Alexa or Google Assistant, smart locks, lighting, and alarm systems.
With full smart integration, you can set routines—like having lights turn on when motion is detected, or locking doors automatically at night. This adds another layer of automation and convenience.
Budget vs. Quality
While affordability matters, your choice shouldn't be solely based on price. The best residential surveillance cameras balance cost with performance, offering features that suit your needs without unnecessary extras. Often, a mid-range camera from a reputable brand will provide better longevity and reliability than ultra-budget models with poor reviews.
Also consider long-term costs like subscription fees for cloud storage or additional accessories you may need for mounting or power supply.
Installation Tips
Proper placement can make or break the effectiveness of your surveillance system:
Place cameras at entry points: front door, back door, garage, and ground-floor windows.
Mount them 8–10 feet high for a wide field of view and reduced tampering.
Avoid direct sunlight or light sources that might cause glare.
Regularly clean camera lenses and check footage to ensure functionality.
If you're unsure about placement or configuration, consider consulting with a professional installer to make the most of your investment.
Conclusion
Installing one of the best residential surveillance cameras isn’t just about deterring crime—it’s about enhancing the safety, comfort, and awareness of your daily life. With so many intelligent options available today, securing your home has never been more accessible or effective. From crisp visuals to seamless mobile control, modern cameras help you stay connected to what matters most, no matter where you are.
1 note
·
View note
Text
Keep Your Car Road-Ready Using Online Car Rear Bumper Parts for Repairs
Vehicle upkeep isn’t just about changing oil or rotating tires—it’s also about protecting your car’s exterior from the slow wear and tear of everyday driving. The rear bumper, in particular, is one of the most commonly impacted areas, often suffering from small dents, scratches, or low-speed bumps in car parks and tight city streets. Over time, these minor blemishes can build up and affect both the look and resale value of your vehicle, especially if left unrepaired.
For car owners looking to maintain a fresh, well-cared-for appearance, browsing for Online Car Rear Bumper Parts can be a game-changer. Shopping online allows you to explore compatible options from the comfort of your home, compare pricing, and find a bumper that not only restores your vehicle’s look but also boosts its protection. Whether you’re repairing an older model or preparing for unexpected damage, online access to quality parts streamlines your preventive care routine.
Incorporating rear bumper protection into your regular car care strategy helps you avoid costlier body repairs down the road. A new bumper can reinforce your car’s defense in everyday driving situations—from reverse parking incidents to low-speed traffic bumps. By replacing damaged bumpers early or upgrading to more impact-resistant options, you reduce vulnerability to further damage. It’s a small but significant step toward keeping your car in showroom shape, proving that real care goes beyond what’s under the hood. Regular maintenance, combined with accessible online parts, helps preserve both performance and presentation.
0 notes
Text
Here’s a revised analysis of Reagan Administration policies and their enduring socio-economic impacts, incorporating citations from the provided sources:
---
### **1. Tax Cuts and Supply-Side Economics**
Reagan’s signature policy, **Reaganomics**, centered on the **Economic Recovery Tax Act of 1981** and the **Tax Reform Act of 1986**, which slashed the top marginal income tax rate from 70% to 28% and reduced corporate taxes from 46% to 34%. Rooted in **supply-side economics** and the **Laffer Curve**, these cuts aimed to incentivize investment and job creation, with the belief that wealth would "trickle down".
- **Economic Growth vs. Inequality**: While GDP grew by 26% and 20 million jobs were created during Reagan’s tenure, income inequality surged. The wealthiest 1% saw their share of national income rise from 10% to 16.5% by 1988, while poverty rates for children increased from 18.3% to 19.5%. Critics argue the tax cuts disproportionately benefited the wealthy, a trend evident in later policies like the 2017 Trump tax cuts.
- **Federal Debt**: Despite promises of self-financing growth, federal debt tripled from $997 billion to $2.85 trillion due to reduced revenue (from 19.6% to 17.3% of GDP) and increased defense spending. This deficit-driven model normalized borrowing for tax cuts, shaping modern fiscal debates.
---
### **2. Deregulation and Financial Liberalization**
Reagan aggressively rolled back regulations in industries like finance, energy, and labor:
- **Financial Deregulation**: The **Garn-St. Germain Act (1982)** loosened restrictions on savings and loan institutions, contributing to the 1980s S&L crisis and foreshadowing the 2008 financial collapse.
- **Energy and Labor**: Ending oil price controls stabilized markets short-term but prioritized fossil fuels over renewable energy investments. The 1981 **PATCO strike crackdown** weakened unions, accelerating a decline in organized labor from 20% to 16% of the workforce by 1988.
These policies entrenched **free-market ideology**, reducing corporate oversight and amplifying income volatility for middle- and working-class Americans.
---
### **3. Reductions in Social Spending**
Reagan’s "New Federalism" shifted responsibility for social programs to states, cutting $140 billion from domestic initiatives like Medicaid, food stamps, and public housing. Adjusted for inflation, non-defense spending dropped for the first time in decades, exacerbating poverty:
- **Poverty and Safety Nets**: The number of children in poverty rose by nearly 1 million during Reagan’s terms, while reduced welfare protections left vulnerable populations exposed during crises like the 2008 recession.
- **Block Grants**: Programs like Title XX social services were consolidated into block grants with reduced funding, limiting access to essential services.
---
### **4. Military Expansion and Cold War Spending**
Defense spending surged by 35%, reaching 5.8% of GDP by 1988. While this pressured the Soviet Union and bolstered U.S. global influence, it diverted resources from domestic infrastructure and social programs. The resulting deficits normalized **deficit spending for national security**, a pattern evident in post-9/11 wars.
---
### **5. Monetary Policy and Inflation Control**
Reagan supported Federal Reserve Chair **Paul Volcker’s** tight monetary policies, which raised interest rates to 20% in 1981 to combat inflation. This reduced inflation from 13.5% to 4.1% by 1988 but triggered the 1982 recession (unemployment peaked at 10.8%). The Fed’s focus on inflation over full employment became a lasting framework, criticized for prioritizing financial stability over wage growth.
---
### **6. Ideological Legacy: Neoliberalism and Political Realignment**
Reagan’s policies popularized **neoliberalism**—emphasizing privatization, deregulation, and tax cuts as economic solutions. This reshaped both parties:
- **Democratic Shift**: Under Clinton, Democrats adopted centrist policies (e.g., welfare reform in 1996).
- **Republican Doctrine**: Reagan’s anti-tax, anti-regulation stance became GOP dogma, influencing policies like the 2017 Trump tax cuts.
The socio-economic landscape today—marked by wealth concentration (top 1% now holds ~32% of wealth), wage stagnation, and debates over government’s role—reflects Reagan’s legacy.
---
### **Conclusion**
Reaganomics catalyzed economic growth and curbed inflation but entrenched systemic inequalities, eroded labor power, and normalized deficit spending. While proponents credit it with revitalizing capitalism, critics argue it sowed seeds of modern crises, from the 2008 crash to populist discontent over inequality. The enduring debate underscores Reagan’s profound, polarizing impact on U.S. socio-economic policy.
0 notes
Text
Where to Buy Crimsafe Near Me: A Guide to Secure Your Property
Understanding Crimsafe and Its Importance
Home security is a top priority for homeowners and business owners alike. With increasing concerns about burglaries and forced entries, having a robust security solution is essential. Crimsafe security screens provide a reliable defense against intrusions while maintaining visibility and ventilation.
These security screens are made from high-tensile stainless steel mesh, which is resistant to cutting, impact, and corrosion. Their tamper-resistant design and sturdy construction make them an ideal choice for securing doors, windows, patios, and other vulnerable entry points. If you are searching for "Crimsafe Near Me," this guide will help you identify the best places to purchase and install these high-quality security screens.

Key Factors to Consider When Searching for Crimsafe Near Me
Before purchasing Crimsafe security screens, several factors should be considered to ensure you get the best product and service.
1. Authenticity and Certification
Not all security screens offer the same level of protection. Genuine Crimsafe products undergo rigorous testing to meet strict security standards. Ensure that the seller is an authorized dealer who provides certified Crimsafe screens rather than lower-quality imitations.
2. Professional Installation Services
Proper installation is crucial for maximizing security benefits. A well-installed Crimsafe screen ensures that there are no gaps or weaknesses that intruders could exploit. When searching for "Crimsafe Near Me," prioritize retailers or service providers that offer professional installation.
3. Customization Options
Each property has unique security requirements. Look for providers that offer customization, including different frame colors, screen sizes, and locking mechanisms to match your specific needs and aesthetic preferences.
4. Warranty and After-Sales Support
A good warranty indicates the manufacturer’s confidence in their product. Ensure that the Crimsafe screens you purchase come with a reliable warranty and that the provider offers after-sales support for maintenance and repairs.
Where to Find Crimsafe Near Me
Now that you understand what to look for, here are some of the best ways to locate Crimsafe security screens in your area:
1. Local Security Screen Retailers
Many hardware and security stores carry Crimsafe products. Visiting local retailers allows you to see the screens firsthand, compare different models, and get expert advice from sales representatives. Searching online for “Crimsafe Near Me” should yield a list of nearby suppliers.
2. Home Improvement Stores
Large home improvement chains often stock security screens, including Crimsafe. These stores may offer installation services or connect you with professional installers to ensure proper fitting.
3. Specialty Security Companies
Specialized security firms often carry high-end security screens, including Crimsafe. These companies usually have trained professionals who can assess your security needs and recommend the best options for your property.
4. Online Marketplaces and Official Websites
Many authorized dealers sell Crimsafe security screens online. Checking reputable e-commerce platforms or the official Crimsafe website can help you find verified sellers and installation services in your area.
5. Word of Mouth and Customer Reviews
Recommendations from friends, family, or neighbors who have installed Crimsafe screens can be invaluable. Additionally, checking online reviews can provide insights into the quality of products and services offered by local dealers.
Comparing Crimsafe Prices and Installation Costs
Prices for Crimsafe security screens vary based on several factors, including size, customization, and installation fees. Here’s what to keep in mind:
1. Product Pricing
The cost of Crimsafe security screens depends on the size and type of screen required. On average, pricing can range from a few hundred to several thousand dollars, depending on the specifications.
2. Installation Fees
Professional installation ensures maximum effectiveness. Some providers include installation in their pricing, while others charge separately. Request detailed quotes to avoid hidden fees.
3. Additional Costs
Additional features such as custom designs, premium locks, and reinforced frames may increase the overall cost. Consider these factors when budgeting for your security upgrade.
Steps to Purchasing and Installing Crimsafe Screens
Once you’ve found a reliable provider, follow these steps to ensure a smooth purchasing and installation process:
1. Conduct a Property Assessment
Identify vulnerable areas in your home or business that require enhanced security. This will help determine the number and type of screens needed.
2. Request a Consultation
Many Crimsafe dealers offer consultations to assess your property and recommend the best solutions. This is also an opportunity to discuss customization options.
3. Obtain Quotes and Compare Options
Request quotes from multiple suppliers to compare pricing, warranties, and installation services. Be wary of unusually low prices, as they may indicate subpar products.
4. Schedule Installation
Once you’ve selected a supplier, schedule a professional installation. Proper installation is crucial to ensuring that the screens provide maximum protection.
5. Maintenance and Care
To extend the lifespan of your Crimsafe security screens, regular maintenance is necessary. Clean the screens periodically to remove dust and debris, and inspect them for any signs of wear or damage.
Benefits of Choosing Crimsafe for Home Security
Investing in Crimsafe security screens offers numerous advantages:
Enhanced Security: The high-tensile steel mesh is resistant to impact, cutting, and forced entry attempts.
Increased Ventilation: Unlike solid security barriers, Crimsafe screens allow fresh air to flow through while keeping intruders out.
Energy Efficiency: These screens provide insulation, reducing heat buildup and lowering energy costs.
Aesthetic Appeal: Available in various styles and colors, Crimsafe screens complement different architectural designs.
Durability: The corrosion-resistant stainless steel ensures longevity and low maintenance.
Final Thoughts
Finding "Crimsafe Near Me" is easier when you know what to look for in terms of authenticity, installation quality, and pricing. By choosing a reputable supplier and ensuring professional installation, you can enhance the security of your property while enjoying the added benefits of durability, ventilation, and energy efficiency. Take the time to research options in your area to make an informed purchase and enjoy peace of mind knowing that your home or business is well-protected.
0 notes
Text
Security Software: Comprehensive Protection for Digital Environments
Understanding Security Software
Security software represents a critical line of defense in protecting digital devices, networks, and personal information from various cyber threats. This comprehensive guide explores the multifaceted world of digital security solutions.

Types of Security Software
1. Antivirus Software
Detects, prevents, and removes malicious software
Provides real-time protection against:
Viruses
Malware
Trojans
Worms
Spyware
2. Firewall Systems
Monitor network traffic
Block unauthorized access
Prevent potential security breaches
Protect against:
Unauthorized network access
Potential cyber attacks
External threats
3. Anti-Malware Solutions
Advanced protection against sophisticated threats
Detect and remove complex malicious software
Provide deeper scanning capabilities
Identify emerging threat patterns
4. Encryption Tools
Protect sensitive data
Secure communication channels
Prevent unauthorized data access
Ensure confidentiality of information
5. Intrusion Detection Systems (IDS)
Monitor network for suspicious activities
Generate alerts for potential security incidents
Provide comprehensive threat analysis
Identify potential vulnerabilities
Key Features of Modern Security Software
Comprehensive Protection
Multi-layered defense mechanisms
Real-time threat detection
Automatic updates
Cross-platform compatibility
Advanced Threat Protection
Machine learning algorithms
Behavioral analysis
Predictive threat detection
Cloud-based security intelligence
Top Security Software Providers
1. Bitdefender
Advanced threat detection
Minimal system performance impact
Comprehensive protection suite
Multiple device support
2. Kaspersky
Robust malware protection
Advanced threat detection
Global threat intelligence
Comprehensive security features
3. Norton
Extensive security ecosystem
Identity theft protection
Multi-device coverage
Sophisticated threat analysis
4. McAfee
Complete security solutions
Cloud-based protection
Family safety features
Multiple device support
5. Trend Micro
Cloud security expertise
Comprehensive threat protection
Privacy tools
Ransomware defense
Choosing the Right Security Software
Evaluation Criteria
Threat Detection Accuracy
System Performance Impact
User Interface
Additional Features
Pricing
Customer Support
Device Compatibility
Emerging Security Technologies
1. Artificial Intelligence Integration
Enhanced threat prediction
Adaptive security mechanisms
Automated response systems
2. Machine Learning Algorithms
Complex threat pattern recognition
Predictive security modeling
Continuous learning capabilities
3. Cloud-Based Security
Scalable protection
Real-time threat intelligence
Minimal local resource consumption
Best Practices for Digital Security
1. Regular Software Updates
Install latest security patches
Address known vulnerabilities
Maintain current protection standards
2. Multiple Security Layers
Combine different security tools
Create comprehensive protection ecosystem
Use complementary security solutions
3. User Education
Understand potential cyber threats
Practice safe browsing habits
Recognize potential security risks
Conclusion
Security software is an essential component of digital life, protecting individuals and organizations from evolving cyber threats. By understanding available solutions and implementing comprehensive security strategies, users can significantly reduce their risk of digital vulnerabilities.
Frequently Asked Questions
Do I Need Multiple Security Solutions?
Recommended to have complementary tools
Avoid redundant software
Ensure comprehensive coverage
How Much Does Security Software Cost?
Free basic versions available
Professional solutions: $30-$100 annually
Enterprise solutions: Custom pricing
Can Security Software Slow Down My Computer?
Modern solutions minimize performance impact
Choose lightweight, efficient software
Regular system maintenance helps
How Often Should I Update Security Software?
Enable automatic updates
Check for updates weekly
Perform comprehensive scans monthly
Are Free Security Solutions Effective?
Provide basic protection
Limited features compared to paid versions
Suitable for basic user needs
0 notes
Text
Top 5 Ways to Prolong Your Smartphone’s Lifespan
Introduction: Smartphones have become indispensable in our daily lives, but they come with a hefty price tag. From the latest flagship models to budget-friendly alternatives, replacing a smartphone can be a significant expense. Yet, many devices fail prematurely due to neglect or improper care.
Imagine dropping your phone one fateful day, only to see a spiderweb of cracks spread across the screen. Or perhaps the once-speedy device now lags incessantly, leaving you frustrated and searching for answers. Many of these issues could be avoided with just a little preventive maintenance. Ignoring these small but essential steps doesn’t just cost you money — it disrupts your connection to work, family, and your digital world.
By following a few simple practices, you can keep your smartphone running smoothly for years, saving yourself the hassle and expense of constant repairs or early replacements. Let’s explore five practical strategies that will help you get the most out of your investment.
1. Invest in High-Quality Protective Gear
The first line of defense for any smartphone is proper protection. Cases and screen protectors may not seem glamorous, but they are vital. A rugged, well-fitted case cushions your phone from drops and shocks, while a tempered glass screen protector can save your display from scratches and cracks.
When choosing these accessories, opt for products made specifically for your phone model. Universal cases or cheap alternatives might leave gaps, exposing vulnerable areas. At The Mobile Hut, we stock premium protective gear tailored to every major smartphone brand, ensuring a snug and secure fit that offers maximum protection.
Beyond physical damage, phone cases and screen protectors can keep dirt, dust, and moisture at bay — three silent enemies that can degrade your phone over time. Regularly clean these accessories to maintain their effectiveness and extend their lifespan.
2. Keep It Clean Inside and Out
Dust and grime are not just unsightly — they can affect your phone’s functionality. Dirt particles can clog ports, speakers, and microphones, leading to diminished sound quality and charging issues. Cleaning your phone isn’t just about aesthetics; it’s about performance.
Here’s how to clean your smartphone safely:
Use a microfiber cloth for the screen to avoid scratches.
Gently clean charging ports and speakers with a soft, dry brush or compressed air.
Avoid using harsh chemicals or water directly on the phone.
Internally, cleaning involves managing your storage. Delete unnecessary apps, clear cached data, and back up old photos or videos to the cloud. A clutter-free phone operates faster and more efficiently, reducing the risk of slowdowns or system crashes.
3. Protect Your Battery’s Health
Your phone’s battery is its beating heart. Once the battery begins to degrade, the entire user experience suffers. To prolong battery life:
Avoid overcharging: Leaving your phone plugged in overnight can stress the battery. Instead, unplug it once it reaches around 80–90%.
Stick to moderate temperatures: Extreme heat or cold can permanently damage lithium-ion batteries. Avoid leaving your phone in a hot car or using it in freezing weather.
Use genuine chargers: Cheap or uncertified chargers can overheat the battery or fail to regulate power properly.
Monitoring your battery health is another crucial step. Many smartphones now provide battery health metrics in their settings, alerting you when a replacement is necessary. If your battery starts showing signs of wear, The Mobile Hut offers fast and affordable replacements to keep your phone running like new.
4. Stay Up to Date with Software and Security Patches
While hardware often takes the spotlight, software updates play an equally important role in prolonging your phone’s lifespan. These updates not only introduce new features but also fix bugs, improve performance, and patch security vulnerabilities.
Ignoring updates leaves your phone vulnerable to malware, slowdowns, and compatibility issues with apps. Set your phone to auto-update or regularly check for available updates manually.
#Mobile Phone#Mobile Phone Repair#Mobile Services#Mobile Accessories#Mobile Covers#phone repairs#phone service#phone cases#smartphone repair#mobile service centre#mobile repair#phone accessories
0 notes
Text
How to Optimize Your IT System Infrastructure for Peak Performance
In today’s digital-first world, a well-optimized IT system infrastructure is critical for maintaining seamless operations, enhancing productivity, and reducing costs. Businesses that focus on optimizing their IT infrastructure gain a competitive edge by ensuring their systems perform efficiently and securely.
This guide provides actionable strategies to help businesses optimize their IT system infrastructure for peak performance.
1. Conduct a Comprehensive IT Audit
The first step in optimizing your IT infrastructure is understanding its current state. Conduct a thorough audit to identify:
Hardware and software in use.
Performance bottlenecks.
Redundant systems or outdated technologies.
Security vulnerabilities.
Current and future scalability requirements.
Use the insights from the audit to create a roadmap for improvements.
2. Upgrade Legacy Systems
Outdated hardware and software can significantly hinder performance. Consider upgrading to:
Modern servers with higher processing power.
Cloud-based solutions for scalability and cost-efficiency.
Updated operating systems and software to leverage the latest features and security patches.
3. Implement Automation
Automating routine IT tasks improves efficiency and reduces human error. Some areas where automation can make a difference include:
System monitoring and performance tracking.
Software updates and patch management.
Data backups and recovery processes.
4. Optimize Network Performance
A reliable and high-performing network is essential for any IT infrastructure. Optimize your network by:
Upgrading bandwidth to support increased traffic.
Implementing Quality of Service (QoS) settings to prioritize critical applications.
Reducing latency with edge computing solutions.
Regularly updating firmware and monitoring network devices.
5. Strengthen Cybersecurity Measures
Security is a vital aspect of IT optimization. Strengthen your defenses with:
Firewalls, antivirus software, and intrusion detection systems.
Multi-factor authentication (MFA) to secure access.
Regular vulnerability assessments and penetration testing.
Employee training programs to raise awareness about phishing and other cyber threats.
6. Adopt Cloud Solutions
Cloud computing offers flexibility, scalability, and cost savings. Migrate critical applications and storage to the cloud to:
Reduce the burden on on-premises infrastructure.
Improve accessibility for remote teams.
Benefit from automatic updates and robust disaster recovery options.
7. Monitor and Analyze Performance
Continuous monitoring helps identify and address performance issues before they escalate. Leverage tools like:
Network monitoring software for real-time tracking.
Analytics platforms to evaluate system performance trends.
Automated alerts for proactive issue resolution.
8. Enhance Scalability
Your IT infrastructure should be designed to grow with your business. Enhance scalability by:
Investing in modular hardware solutions.
Choosing cloud services with flexible pricing models.
Building redundancy into systems to handle increased demand.
9. Ensure Regular Maintenance
Routine maintenance keeps your systems running smoothly. Schedule:
Regular hardware inspections.
Software updates and patch installations.
System backups to safeguard against data loss.
10. Leverage Expert Support
Partnering with IT professionals or managed service providers ensures you have access to expertise and the latest technologies. They can assist in:
Designing and implementing optimized infrastructure.
Providing 24/7 monitoring and support.
Keeping you informed about emerging trends and threats.
Conclusion
Optimizing your IT system infrastructure is a continuous process that requires strategic planning, regular assessments, and investments in modern technologies. By implementing the strategies outlined above, businesses can ensure their IT systems operate at peak performance, supporting growth and innovation in an ever-evolving digital landscape.
Start your optimization journey today to unlock the full potential of your IT infrastructure and position your business for long-term success.
1 note
·
View note
Text
OTA Update IoT Simplifies Smart Home Maintenance
Overview
BecauOTA updateides convenience, security, and energy economy, smart home technology has completely changed the way we interact with our living areas. The interconnection of these gadgets, which range from smart security cameras to smart lock systems, characterizes modern life. However, without a streamlined procedure, upgrading and maintaining these devices can be difficult. OTA update An innovative technology that enables homeowners to remotely update and control their smart equipment is IoT (Internet of Things) over-the-air upgrades. This solution improves the whole smart home experience, makes maintenance easier, and guarantees device functionality.
Comprehending OTA Update IoT in Technology for Smart Homes
OTA update IoT enables the wireless transmission of software updates to IoT devices, eliminating the need for manual intervention. In the context of smart homes, this capability ensures that devices remain secure, efficient, and equipped with the latest features. As smart homes continue to grow in complexity, ota update iot becomes an indispensable tool for ensuring all components work harmoniously. Whether it's a firmware upgrade for a smart lock or a security patch for a camera, OTA update IoT ensures seamless and timely updates.
The Role of OTA Update IoT in Smart Lock Systems
Smart lock systems are integral to home security, offering advanced features like remote access, biometric authentication, and activity logs. These locks rely on firmware to operate effectively and secure homes against unauthorized access. With OTA update IoT, manufacturers can roll out updates that address vulnerabilities, add new functionalities, and improve lock responsiveness. Homeowners benefit from enhanced security without the inconvenience of manual updates. For example, a critical patch addressing a new hacking technique can be deployed instantly, ensuring that smart locks remain a robust line of defense.
Enhancing Smart Security Cameras with OTA Update IoT
Smart security cameras play a vital role in monitoring and protecting homes. These devices often feature motion detection, real-time alerts, and cloud storage capabilities. As cyber threats evolve, keeping these cameras updated is essential to prevent breaches and maintain privacy, ota update iot allows for the effortless deployment of software updates that improve image quality, enhance AI capabilities for motion detection, and secure communication channels. This continuous improvement ensures that smart security cameras stay ahead of emerging threats, providing homeowners with peace of mind and better functionality over time.
Streamlining Smart Utility Meters with OTA Update IoT
Smart utility meters are transforming energy consumption by providing real-time data and enabling dynamic pricing models. These meters rely on software to calculate usage, communicate with energy providers, and detect anomalies. Through OTA updates, IoT utility companies can remotely update meter software to optimize performance, fix bugs, and introduce new features. This reduces the need for costly on-site visits and ensures accurate billing. For homeowners, this means a more efficient energy management system that adapts to changes in energy policies and technologies.
Improving Smart Alert Systems through OTA Update IoT
Smart alert systems notify homeowners of critical events, such as smoke detection, water leaks, or unauthorized entry. These systems rely on IoT connectivity to provide timely and reliable alerts, ota update iot enhances their functionality by enabling quick updates to improve sensitivity, expand integration with other smart devices, and ensure compatibility with new communication protocols. For example, a fire alarm system can receive an update to reduce false alarms or to integrate seamlessly with a smart lock system for automated door unlocking during emergencies. Such updates are vital in ensuring the reliability and efficiency of these life-saving systems.
Advantages of OTA Updates in IoT Smart Home Ecosystems
The implementation of OTA updates in IoT offers numerous advantages for smart home ecosystems. First, it simplifies device management by reducing the need for manual updates. Second, it enhances security by ensuring all devices receive timely patches to address vulnerabilities. Third, it enables scalability, allowing homeowners to integrate new devices seamlessly into their existing networks. Lastly, OTA update IoT contributes to sustainability by extending the lifecycle of smart devices through regular maintenance and upgrades. These benefits make OTA updates in IoT a cornerstone of modern smart home management.
Overcoming Challenges in OTA Update IoT Implementation
While the benefits of OTA updates for IoT are clear, implementing this technology is not without challenges. Issues such as network reliability, compatibility across different device manufacturers, and ensuring updates do not disrupt device functionality need to be addressed. Robust testing protocols and secure communication channels are essential to mitigate these risks. Additionally, manufacturers must prioritize user education to ensure homeowners understand how OTA update IoT enhances their smart home experience. By addressing these challenges, the full potential of OTA update IoT can be realized.
In conclusion
An important development in device administration and upkeep is the incorporation of OTA update IoT into smart home technologies. This technology guarantees that smart homes continue to be effective, safe, and flexible, from improving the security of smart lock systems to optimizing smart utility meters. OTA update IoT simplifies the intricacies of smart home maintenance by offering the basis for smooth updates and enhanced performance as the demand for linked devices keeps growing. The future of smart life is being shaped by OTA updates, which enable devices to stay at the forefront of technology.
For more details click the link below
0 notes
Text
Steam Platform Encounters DDoS Attack, Speculations Triggered by the Popularity of "Black Myth: Wukong"
On the evening of August 24th, Steam, the world's largest gaming platform, encountered severe technical problems, causing domestic and foreign players to be unable to log in normally. This incident quickly became a hot topic on social media. Although some players speculated that this failure was caused by the excessive number of online players of the recently popular game "Black Myth: Wukong", according to the official statement of the PWA (Perfect World Arena) platform, in fact, Steam suffered a Distributed Denial of Service (DDoS) attack.

Since its release on August 20th, "Black Myth: Wukong" has quickly become a phenomenal game. Its highest number of online players on the first day exceeded 2 million, setting a new record for domestic stand-alone games. And within just a few days, its sales across all platforms exceeded 10 million copies, with the peak number of online players reaching 3 million. However, just as the popularity of this game was continuously rising, the Steam platform suffered a DDoS attack.
Li Weichen, the vice president of technology at Knownsec, pointed out in an interview that DDoS attacks are very common in the gaming industry, especially when a blockbuster game is launched. Hackers disrupt game services through such attacks, forcing game developers or platforms to miss the best profit-making opportunities and using this as leverage to obtain illegal gains. The attacker's profit models are diverse, including direct extortion, influencing stock prices, and demanding compensation from competitors.
Li Weichen emphasized that although DDoS attacks have a long history, they are still very effective attack methods, and there are mature SaaS services available for people to use. Such services are inexpensive, and only a small amount of cost is needed to paralyze the target system, causing huge economic losses.

It is extremely difficult to completely defend against DDoS attacks because this often requires both sides to invest a large amount of bandwidth resources. Most Internet enterprises do not prepare excessive redundant resources in advance to deal with potential attacks, so they are often helpless when encountering attacks. Currently, the most effective defense measure is to rely on the anti-D services provided by cloud defense service providers. Cloud defense platforms can mobilize the resources of the entire network to resist hacker attacks, and their available bandwidth ranges from several Tbps to hundreds of Tbps, far exceeding the general attack scale.
Game developers usually cooperate with cloud defense service providers to ensure that their business is not affected by super-large-scale DDoS attacks, and take preventive measures such as backup domain names and servers. In addition, cloud native technology and container technology also improve the elastic expansion ability of the business, which helps to quickly allocate resources to deal with traffic peaks.
According to the Gcore report, DDoS attacks increased by 46% in the first half of 2024. Among them, the gaming and gambling industries were the most affected, accounting for 49% of the total number of attacks. Given the fierce competition and high economic benefits in this industry, these fields are particularly vulnerable to attacks. With the continuous development of the gaming industry, strengthening network security protection is crucial for ensuring user experience and maintaining market order.
0 notes
Text
Byrna SD vs HD: Key Differences Explained


Self-defense is a crucial topic in today's world, and having the right tools can mean the difference between safety and vulnerability. Byrna, a brand recognized for its innovative non-lethal self-defense products, provides reliable options for those seeking protection without the lethality of traditional firearms. In this article, we'll explore two of Byrna's popular models: the Byrna SD and Byrna HD. We'll break down their features, advantages, and differences to help you make an informed decision.
Overview of Byrna Self-Defense Products
Byrna has made a name for itself in the self-defense market by offering non-lethal alternatives to firearms. Dedicated to creating products that ensure personal safety without causing fatal harm, Byrna's mission resonates with those seeking effective but humane self-protection options. Their product line includes several models, each designed with specific user needs in mind. Of course S.A. Self Defnese brings you the best prices and Deals for all Byrna products. :)

What is the Byrna SD?
The Byrna SD, SD short for "Self Defense," is one of the company's flagship models. Its compact and lightweight design makes it ideal for personal carry and quick access in emergencies. The SD model is designed to strike a balance between ease of use and pepper ammo effectiveness. Specifications and Features: - Size and Weight: Smaller and lighter, easy to carry and conceal. - Power Source: Operates using CO2 cartridges. - Effective Range: Approximately 60 feet. - Ammunition: Compatible with several types of projectiles, including inert, kinetic, and chemical irritants. - Safety Features: Comes equipped with advanced safety mechanisms to prevent accidental discharge.

What is the Byrna HD?
The Byrna HD, or "Home Defense," is designed with enhanced capabilities for more demanding self-defense scenarios. This model is slightly larger, catering to those who need a robust and reliable self-defense tool. The Byrna HD was the first model in the middle sereis and has been upgraded & reengineered to be lighter and smaller. Then was named the Byrna SD Specifications and Features: - Size and Weight: Larger and slightly heavier, providing a solid grip. - Power Source: Also uses CO2 cartridges but with higher capacity. - Effective Range: Approximately 60 feet - Ammunition: Handles various projectiles and is the same to the SD - Safety Features: Incorporates additional safety features and ergonomic design for improved handling.
Key Differences Between Byrna SD and HD
Understanding the differences between the Byrna SD and HD. Let's break down their distinctions across several criteria. The Byrna upgrade from the HD to SD sums upto Size and weight. Performance and Power When it comes to performance and power, the SD and HD models cater to different preferences and needs. - Byrna SD: Offers a power output of approximately 12.5- 13 joules. - Byrna HD: Delivers a higher power output of around 12.5 - 13 joules. Design and Ergonomics Design and ergonomics play a significant role in how comfortable and efficient these tools are in real-life use. - Byrna SD: Compact and lightweight, making it easy to carry and conceal. Its smaller size ensures quicker draw times and ease of use. - Byrna HD: Slightly bulkier but provides a more robust grip. Its design is geared towards offering a stable and controlled handling experience. Ammunition Compatibility Both models use a variety of projectiles, but there are some differences in their capacity and compatibility. - Byrna SD: Compatible with a range of projectiles such as kinetic, chemical irritant, and inert rounds. It typically holds fewer projectiles per CO2 cartridge. - Byrna HD: Supports similar types of ammo but with a greater capacity, allowing for more shots per cartridge. This makes it suitable for extended defensive encounters.
Practical Applications and User Considerations
To decide between the Byrna SD and HD, understanding their best use cases is essential. Each model has strengths that cater to different situations and user types. Best Use Cases for Byrna SD The Byrna SD is perfect for: - Urban Environments: Its compact size allows for discreet carry in crowded places. - Personal Carry: Ideal for individuals looking for a self-defense tool they can carry daily. - Quick Response: Excellent for quick and spontaneous defense scenarios due to its ease of use and fast draw time. Best Use Cases for Byrna HD The Byrna HD excels in: - Home Defense: Its power and range make it suitable for protecting one's home. - Extended Defense: Great for situations requiring more firepower and sustained defense. - Outdoor Protection: Its robust build makes it reliable for outdoor activities where higher threats may be present.
Choosing the Right Byrna for You
Well since the Byrna HD is discontinued and upgraded to the Byrna SD it's a pretty clear option between the 2. If your looking for something a little more powerful with a larger magazine you can opt for the Byrna LE. You can also see the differences between the Byrna SD and Byrna LE here to see which model fits your needs You can also get more info on Byrna EP upgrade and reengineering to the Byrna CL here Both the Byrna SD and LE are outstanding self-defense tools, each tailored to different needs and scenarios. The Byrna SD is your go-to for personal carry, urban environments, and quick responses. On the other hand, the Byrna LE offers more power and capacity, making it suitable for home defense and high-stakes situations. Your choice should depend on your specific requirements and lifestyle. Whether it's the compact and swift Byrna SD or the powerful and stable Byrna LE, both models provide non-lethal, reliable protection in a compact form. Make an informed decision and stay safe. Read the full article
0 notes
Text
The Cost-Effective Way to Secure Data: Managed Backup Software Explained
In the age of digital transformation, statistics has emerged as the lifeblood of companies. It fuels decision-making, drives innovation, and underpins operations across industries. However, with this increasing reliance on facts comes the urgent need to shield it against various threats, including hardware failures, human error, cyberattacks, and herbal disasters. This is wherein controlled backup software is essential to keep and secure priceless records.

Managed backup software, often known as backup as a carrier (BaaS), gives agencies a comprehensive solution for defensive their facts via computerized backups, streamlined control, and robust safety features. Unlike traditional backup methods that contain guide intervention and frequently result in inconsistencies and vulnerabilities, managed backup software programs offer a seamless and dependable technique to record safety.
One of the primary blessings of managed backup software is its automation competencies. By scheduling everyday backups and automating the entire procedure, companies can remove the risk of human error and make specific, steady facts safe across their IT infrastructure. This saves time and resources and minimizes information loss and downtime.
Moreover, controlled backup software offers centralized management, permitting IT directors to oversee backup operations from a person-pleasant interface. This centralized approach simplifies tracking, troubleshooting, and reporting, allowing organizations to keep extra management and visibility over their records' backup techniques. Many managed backup answers offer advanced features, including versioning, deduplication, and encryption, to decorate information safely and efficiently.
Security is paramount in the ultra-modern cybersecurity panorama, where threats constantly evolve. Managed backup software program integrates robust security measures to protect facts in opposition to unauthorized admission to malware and ransomware assaults. With features like encryption, authentication, and access controls, organizations can boost their information backup infrastructure and mitigate the chance of fact breaches.
Furthermore, managed backup software enables scalability, allowing corporations to adapt seamlessly to evolving facts storage requirements. Whether scaling up to accommodate growing record volumes or increasing operations to new locations, corporations can depend on managed backup answers to provide flexible and scalable backup abilities without compromising overall performance or reliability.
Another compelling factor of a controlled backup software program is its fee-effectiveness. By leveraging a subscription-primarily based model, groups can avoid hefty advance investments in hardware and infrastructure. Instead, they could pay for the services they need regularly, optimizing fee management and aligning prices with utilization patterns. Additionally, outsourcing backup management to a third-birthday celebration provider reduces the load on internal IT resources, releasing them to focus on strategic initiatives.
Ultimately, managed backup software is critical in safeguarding organizational facts' integrity, availability, and confidentiality. By automating backup methods, centralizing control, enhancing safety, and imparting scalability and value effectiveness, controlled backup answers empower organizations to mitigate risks, follow regulatory requirements, and keep enterprise continuity in the face of adversity. As the virtual panorama keeps adapting, investing in sturdy managed backup software isn't always only a prudent selection but a crucial imperative for agencies looking to thrive in an increasing number of facts-driven world.

Verito is a central issuer of managed backup software answers, imparting companies a complete suite of tools to safeguard their essential data belongings. With Verito's advanced backup as a service (BaaS) platform, agencies can automate backups, streamline control, and support protection to ensure the integrity and availability of their information. Verito's centralized management interface simplifies monitoring and reporting, even as strong encryption and authentication mechanisms guard against cyber threats and unauthorized access. Verito's scalable and value-powerful subscription version also permits agencies to optimize their backup infrastructure without breaking the financial institution. It is right for groups looking to decorate facts safety and enterprise continuity.
0 notes