#digital credentialing for enterprises
Explore tagged Tumblr posts
Text
How Digital Credentialing Enhances Workforce Validation in Enterprises
Digital credentialing for enterprises and digital credential verification are rapidly transforming how organizations validate the qualifications of their workforce. In an age where speed, trust, and compliance are critical, enterprises can no longer rely on outdated, manual methods to verify employee credentials. Instead, they are turning to secure, automated solutions that enhance efficiency and reduce the risk of fraud. By adopting digital credentialing, enterprises can validate skills and certifications in real-time — ensuring they hire and retain only the most qualified professionals.
What Is Digital Credentialing?
Digital credentialing refers to the process of issuing, managing, and verifying credentials electronically. These credentials can include educational degrees, professional certifications, training completions, licenses, and more. Unlike traditional paper-based documentation, digital credentials are secure, tamper-proof, and easily verifiable online.
Digital credentialing for enterprises gives organizations the ability to manage employee qualifications at scale — streamlining operations across HR, compliance, and workforce development teams.
The Workforce Validation Challenge
Enterprises face multiple challenges when validating workforce credentials:
High Volume: Verifying credentials for hundreds or thousands of employees is time-consuming and resource-heavy.
Manual Errors: Paper-based processes are prone to human error and oversight.
Credential Fraud: Falsified documents and unverifiable claims undermine trust and lead to legal and reputational risks.
Regulatory Pressure: Industries like healthcare, finance, and aviation are bound by strict compliance standards that require timely and verifiable documentation.
How Digital Credentialing Enhances Workforce Validation
1. Real-Time Digital Credential Verification
With digital credential verification systems, enterprises can instantly confirm the authenticity of an employee’s qualifications. These systems are often integrated with issuing institutions and databases, enabling real-time validation without the need for emails or phone calls.
2. Tamper-Proof Security
Digital credentials often utilize blockchain or encrypted cloud platforms to prevent alteration or duplication. This ensures that once a credential is issued, it cannot be modified — reducing fraud and enhancing trust across departments.
3. Streamlined Credential Management
A centralized platform allows HR teams to track, manage, and organize digital credentials efficiently. Whether it’s onboarding new hires or renewing certifications, everything is automated, logged, and easily accessible.
4. Compliance and Audit Readiness
Digital credentialing helps enterprises stay prepared for audits by maintaining accurate, up-to-date, and verifiable records. This is especially important in regulated industries where non-compliance can lead to significant fines and penalties.
5. Employee Empowerment and Engagement
Employees can easily access and share their verified credentials through digital wallets or professional platforms. This not only promotes transparency but also boosts morale, as workers take ownership of their career achievements.
Use Case: Digital Credentialing in Learning & Development
Many enterprises are launching internal training and upskilling initiatives to stay competitive. By issuing digital credentials upon completion of these programs, companies can track employee progress, identify skills gaps, and align training with business needs.
These credentials can be used to validate employee readiness for promotions, cross-functional roles, or specialized projects — improving workforce mobility and retention.
Why Digital Credentialing for Enterprises Is a Strategic Move
Embracing digital credentialing for enterprises is no longer optional — it’s essential for future-ready business operations. The benefits go beyond HR and compliance; they extend to employer branding, employee engagement, and operational efficiency. Companies that integrate digital credential verification into their systems gain a competitive edge by:
Speeding up hiring and onboarding
Reducing operational risk
Ensuring data security and privacy
Supporting remote and global workforces
Improving decision-making with reliable data
Final Thoughts
The traditional methods of verifying employee credentials are no match for the demands of modern enterprises. With the rise of remote work, gig economies, and digital transformation, organizations need faster, smarter, and more secure ways to validate their workforce. Digital credentialing and digital credential verification offer precisely that — transforming workforce validation from a bottleneck into a strategic advantage.
If your enterprise hasn’t yet explored the benefits of digital credentialing, now is the time to act. Your workforce — and your bottom line — will thank you.
0 notes
Text
What is Digital Credential Verification and Why Enterprises Need It
In today’s digital-first world, verifying employee credentials is no longer a manual task buried in HR paperwork — it’s a security imperative. As businesses scale and remote hiring becomes the norm, digital credential verification is rapidly emerging as the smarter, faster, and more secure way to validate academic, professional, and identity-based credentials.
For forward-thinking organizations, digital credentialing for enterprises is not just a convenience — it’s a strategic advantage.
🌐 What is Digital Credential Verification?
Digital credential verification is the process of electronically confirming the authenticity of a person’s qualifications, certifications, or identity credentials. Instead of relying on phone calls, physical documents, or outdated databases, digital verification uses secure, often blockchain-backed systems to instantly verify data from authorized issuers.
Think of it as a digital “passport” of trust that can be instantly verified by employers, institutions, or governing bodies — in real-time and without manual effort.
📈 Why Digital Credentialing for Enterprises is Becoming Essential
Enterprises are under more pressure than ever to hire quickly, reduce risk, and stay compliant with industry standards. Here’s why digital credentialing is becoming a must-have:
1. 🚀 Faster Hiring and Onboarding
Manual verification can take days — or even weeks. With digital credentialing, enterprises can onboard verified employees in minutes, reducing hiring cycles and improving the candidate experience.
2. 🔐 Reduced Risk of Fraud
Resume fraud is real. Whether it's fake degrees or exaggerated work experience, unverifiable credentials can be costly. Digital credential verification helps businesses ensure only authentic, verifiable information is accepted — reducing compliance risks and legal liabilities.
3. 📊 Scalable for Growth
As enterprises grow and hire across multiple regions, a centralized digital system ensures consistent, scalable verification processes across departments and geographies.
4. ✅ Improved Compliance & Auditing
Industries like healthcare, finance, and education demand strict regulatory compliance. Digital credentials provide a tamper-proof audit trail, making it easier for enterprises to pass audits and meet industry standards.
5. 🔄 Seamless Integration with HR Systems
Modern digital credentialing platforms can integrate directly with HRMS and ATS systems, ensuring credential checks become a seamless part of the hiring or promotion workflow.
🔍 Real-World Applications of Digital Credentialing for Enterprises
HR and Recruitment: Verify education, certifications, and employment history instantly.
Training & Certification Tracking: Track which employees hold valid certifications in real-time.
Contractor & Freelancer Management: Verify vendor and gig worker qualifications before assigning critical projects.
Partner & Vendor Due Diligence: Confirm credentials of third-party service providers to ensure compliance and quality.
🌍 The Future is Verified
As digital transformation accelerates, traditional verification methods are becoming obsolete. Enterprises that embrace digital credentialing are not only saving time and costs — they’re building a foundation of trust, transparency, and compliance that supports long-term growth.
✅ Final Thoughts
Digital credential verification is no longer a luxury; it’s a necessity for enterprises operating in today’s high-speed, security-conscious world. Whether you're hiring a developer, onboarding a medical professional, or partnering with a vendor, having instant, tamper-proof access to verified credentials ensures you’re making decisions backed by trust.
Ready to make the shift? Talk to us about how our digital credentialing for enterprises can help you hire smarter, stay compliant, and future-proof your workforce.
1 note
·
View note
Text
Windows Server 2016: Revolutionizing Enterprise Computing
In the ever-evolving landscape of enterprise computing, Windows Server 2016 emerges as a beacon of innovation and efficiency, heralding a new era of productivity and scalability for businesses worldwide. Released by Microsoft in September 2016, Windows Server 2016 represents a significant leap forward in terms of security, performance, and versatility, empowering organizations to embrace the challenges of the digital age with confidence. In this in-depth exploration, we delve into the transformative capabilities of Windows Server 2016 and its profound impact on the fabric of enterprise IT.

Introduction to Windows Server 2016
Windows Server 2016 stands as the cornerstone of Microsoft's server operating systems, offering a comprehensive suite of features and functionalities tailored to meet the diverse needs of modern businesses. From enhanced security measures to advanced virtualization capabilities, Windows Server 2016 is designed to provide organizations with the tools they need to thrive in today's dynamic business environment.
Key Features of Windows Server 2016
Enhanced Security: Security is paramount in Windows Server 2016, with features such as Credential Guard, Device Guard, and Just Enough Administration (JEA) providing robust protection against cyber threats. Shielded Virtual Machines (VMs) further bolster security by encrypting VMs to prevent unauthorized access.
Software-Defined Storage: Windows Server 2016 introduces Storage Spaces Direct, a revolutionary software-defined storage solution that enables organizations to create highly available and scalable storage pools using commodity hardware. With Storage Spaces Direct, businesses can achieve greater flexibility and efficiency in managing their storage infrastructure.
Improved Hyper-V: Hyper-V in Windows Server 2016 undergoes significant enhancements, including support for nested virtualization, Shielded VMs, and rolling upgrades. These features enable organizations to optimize resource utilization, improve scalability, and enhance security in virtualized environments.
Nano Server: Nano Server represents a lightweight and minimalistic installation option in Windows Server 2016, designed for cloud-native and containerized workloads. With reduced footprint and overhead, Nano Server enables organizations to achieve greater agility and efficiency in deploying modern applications.
Container Support: Windows Server 2016 embraces the trend of containerization with native support for Docker and Windows containers. By enabling organizations to build, deploy, and manage containerized applications seamlessly, Windows Server 2016 empowers developers to innovate faster and IT operations teams to achieve greater flexibility and scalability.
Benefits of Windows Server 2016
Windows Server 2016 offers a myriad of benefits that position it as the platform of choice for modern enterprise computing:
Enhanced Security: With advanced security features like Credential Guard and Shielded VMs, Windows Server 2016 helps organizations protect their data and infrastructure from a wide range of cyber threats, ensuring peace of mind and regulatory compliance.
Improved Performance: Windows Server 2016 delivers enhanced performance and scalability, enabling organizations to handle the demands of modern workloads with ease and efficiency.
Flexibility and Agility: With support for Nano Server and containers, Windows Server 2016 provides organizations with unparalleled flexibility and agility in deploying and managing their IT infrastructure, facilitating rapid innovation and adaptation to changing business needs.
Cost Savings: By leveraging features such as Storage Spaces Direct and Hyper-V, organizations can achieve significant cost savings through improved resource utilization, reduced hardware requirements, and streamlined management.
Future-Proofing: Windows Server 2016 is designed to support emerging technologies and trends, ensuring that organizations can stay ahead of the curve and adapt to new challenges and opportunities in the digital landscape.
Conclusion: Embracing the Future with Windows Server 2016
In conclusion, Windows Server 2016 stands as a testament to Microsoft's commitment to innovation and excellence in enterprise computing. With its advanced security, enhanced performance, and unparalleled flexibility, Windows Server 2016 empowers organizations to unlock new levels of efficiency, productivity, and resilience. Whether deployed on-premises, in the cloud, or in hybrid environments, Windows Server 2016 serves as the foundation for digital transformation, enabling organizations to embrace the future with confidence and achieve their full potential in the ever-evolving world of enterprise IT.
Website: https://microsoftlicense.com
5 notes
·
View notes
Text
Hacker Breach Exposes 23andMe’s Customers’ Data

Genetic Testing Giant Confirms Massive Security Compromise
A staggering breach has rattled the foundations of 23andMe, the renowned genetic testing company, as it confirms unauthorized access to nearly seven million user profiles. A spokesperson disclosed to CNN on Tuesday that the breach encompassed sensitive details such as ancestry reports, zip codes, and birth years, significantly impacting a subset of the company’s extensive user base.
The Scale of the Breach
The unsettling revelation came to light through a filing to the Securities and Exchange Commission (SEC) on Friday, where 23andMe indicated that approximately 0.1% of its user accounts, approximately 14,000 profiles, fell victim to the cyber intrusion. However, subsequent investigations unveiled a more substantial impact, with hackers infiltrating around 5.5 million profiles employing the company’s DNA Relatives feature.
Extent of Compromised Information
Notably, hackers also managed to access a subset of family tree data linked to 1.4 million DNA Relatives profiles, raising concerns about the depth and breadth of compromised personal information. Engadget, a prominent tech news outlet, initially shed light on the broader implications of this extensive security breach.
23andMe faces data breach: Over 7 million users exposed to hackers
youtube
Ongoing Cybersecurity Woes
This incident adds 23andMe to the roster of major U.S. corporations grappling with severe cybersecurity breaches affecting a larger populace than initially acknowledged. Just recently, Okta, an identity management firm, acknowledged a data breach impacting all users within its customer support system, a figure significantly higher than initially reported.
Modus Operandi: Credential Stuffing
The method of intrusion employed by the hackers has been identified as ‘credential stuffing.’ Leveraging old usernames and passwords obtained from other platforms, this rudimentary yet effective technique facilitated unauthorized access to numerous 23andMe customer accounts.
Company’s Response and Measures Taken
In response to the breach, 23andMe embarked on a comprehensive investigation aided by third-party forensic experts. Despite declining to disclose the perpetrators, the company is diligently notifying affected customers, complying with legal obligations.
A statement posted on the company’s website outlined measures to bolster data protection, mandating password resets for existing customers and implementing two-step verification for both new and existing users.
As concerns over data security and privacy amplify, this breach underscores the pressing need for stringent measures to safeguard sensitive personal information in an increasingly digitized world.
The ramifications of such a breach extend far beyond the compromised data itself. Users are now grappling with potential identity theft, privacy infringement, and the misuse of their genetic information. This breach has reignited conversations about the ethical responsibilities of companies dealing with highly personal data and the imperative to fortify cybersecurity protocols.
In the wake of this breach, regulatory bodies and lawmakers are likely to intensify their scrutiny of companies handling sensitive user data, potentially leading to stricter compliance standards and regulations aimed at fortifying cybersecurity measures and protecting consumer privacy.
As 23andMe continues its damage control and endeavors to rebuild trust, the cybersecurity landscape faces renewed challenges, emphasizing the criticality of proactive measures to thwart malicious cyber threats and safeguard user information from similar breaches in the future.
Curious to learn more? Explore our articles on Enterprise Wired
#DataBreach#Cybersecurity#PrivacyConcerns#23andMeHack#SecurityAlert#DigitalPrivacy#CyberThreats#Youtube
2 notes
·
View notes
Text
Master the Java Programming: Your Gateway to a Dynamic Digital Future
Java is more than just a programming language; it's a versatile and powerful platform that has left an indelible mark on the world of software development. Renowned for its cross-platform compatibility, readability, and extensive libraries, Java is a go-to choice for developers seeking to build diverse applications. Its applications range from web and mobile app development to scientific research, gaming, and enterprise-level software. Whether you're a seasoned developer or just starting your coding journey, Java offers a broad spectrum of opportunities and the potential to shape the digital future. This introduction sets the stage for delving into the vast world of Java and the myriad possibilities it holds.

When it comes to learning Java, there are various online platforms and resources available, but ACTE Technologies stands out as an exceptional choice for several compelling reasons. Java, a versatile and powerful programming language, has been a cornerstone of software development for years. Its wide range of applications, cross-platform compatibility, and readability make it a valuable skill to acquire. In this blog, we will explore the benefits of learning Java through, an institute that not only equips you with a deep understanding of Java but also provides comprehensive training, hands-on experience, industry-recognized certifications, and career support.
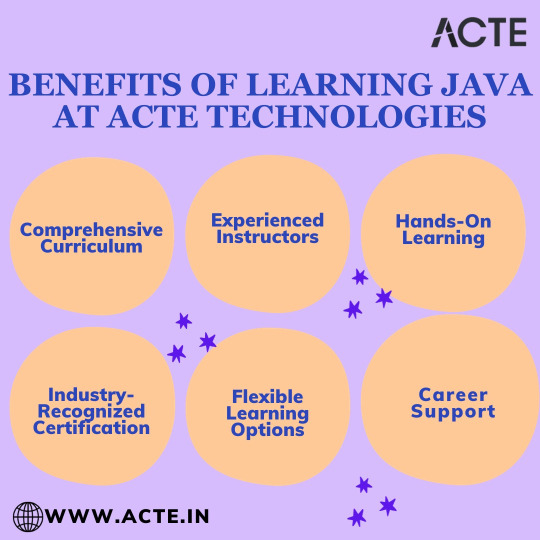
The Benefits of Learning Java through ACTE Technologies:
Comprehensive Curriculum: They offers a well-structured and comprehensive Java training program that covers the fundamentals and advanced concepts of Java programming. The curriculum is designed to provide a deep understanding of Java and its various applications. Whether you are a beginner or an experienced developer looking to enhance your skills, their courses cater to your needs. With a focus on building a strong foundation, you'll be prepared to tackle real-world challenges.
Experienced Instructors: The courses at They are taught by experienced Java professionals who have a strong grasp of the language and its practical use. Learning from experts in the field can significantly accelerate your learning journey. These instructors offer valuable insights, practical examples, and industry-relevant knowledge to help students excel. You can benefit from their experience and expertise as you navigate the intricacies of Java programming.
Hands-On Learning: They place a strong emphasis on practical learning. It's not just about understanding Java theory; it's about applying that knowledge to real-world scenarios. Students have the opportunity to work on hands-on projects and coding exercises that mirror the challenges faced by Java developers in the industry. This hands-on experience solidifies their Java programming skills and prepares them for actual development tasks. Learning by doing is a key principle of their approach.
Industry-Recognized Certification: Completing a Java training program comes with a valuable bonus: an industry-recognized certification. This certification serves as a testament to your skills and knowledge in Java programming. It's a valuable credential that can enhance your job prospects and career advancement. Many employers seek candidates with industry certifications, and this can give you a competitive edge in the job market.
Flexible Learning Options: They understands that every student has unique learning preferences and schedules. To cater to a diverse audience, they provide flexible learning options, including both online and classroom-based training. Whether you prefer the flexibility of online learning or the structure of classroom sessions, you can choose the format that best suits your needs. This flexibility allows you to learn at your own pace and in a way that aligns with your lifestyle.
Career Support: Beyond providing exceptional training, They go the extra mile by offering career support services. This includes job placement assistance and interview preparation. Their commitment to your success doesn't end with the completion of the course. They ensure that students not only gain knowledge but also have the tools and guidance needed to pursue successful careers in Java development. The career support services can be a game-changer as you transition into the professional world of software development.
In conclusion, mastering Java programming is a valuable investment in your skill set and career. It opens doors to a wide range of opportunities in software development, and the demand for Java developers remains consistently high. While there are numerous platforms and resources available for learning Java, ACTE Technologies offers a distinctive advantage. Their Java training programs are designed to provide a comprehensive understanding of the language, hands-on experience, industry-recognized certifications, and career support. It's not just about learning Java; it's about excelling in Java. Your journey to becoming a proficient Java developer begins with ACTE Technologies, where the possibilities are limitless, and the digital world is yours to shape and innovate.
4 notes
·
View notes
Text
Riding the Asia-Pacific Wave: Why CHAM Certification Is Your Ticket to Success 🎟️
The hardware asset management landscape is shifting toward Asia-Pacific, where organizations are racing to optimize sprawling IT infrastructures. If you want to lead the charge and help your company thrive you need the right credentials. Here’s why the Certified Hardware Asset Manager program is a must-have in this booming region:
1. Tap Into Explosive Market Growth 📈
The hardware asset management market in Asia-Pacific is projected to capture 42% of global revenues by 2037, driven by rapid IoT adoption, cloud migrations, and digital transformation across India, China, Australia, and Southeast Asia. By earning your CHAM certificate, you position yourself at the forefront of this surge, ready to advise major enterprises on best-in-class asset strategies.
2. Lead the Pack with Best-Practice Frameworks 🏆
Global standards matter especially in diverse APAC markets. The CHAM accreditation equips you with core CHAM foundations that align seamlessly with ITIL®, ISO20000®, and COBIT®. You’ll learn to design governance models, enforce audit-ready controls, and implement lifecycle processes that multinational organizations crave.
3. Slash Costs & Mitigate Risks 💸
Unmanaged hardware fleets bleed budgets. Through the CHAM exam, you’ll master techniques in inventory rationalization, vendor negotiation, and end-of-life disposal. This hardware asset management certification empowers you to extend asset life cycles, reduce procurement spend, and safeguard sensitive data key competitive advantages for APAC’s cost-conscious enterprises.
4. Future-Proof Your Career in a Hyper-Growth Region 🌐
Asia-Pacific’s ITAM sector is expanding at double-digit rates year-over-year. With a CHAM certificate on your resume, you open doors to senior roles Asset Manager, IT Operations Lead, or Compliance Officer often commanding 20–30% higher salaries than non-certified peers. Plus, you’ll join a network of global professionals driving best practices across borders.
#CHAMAsiaPacific #HardwareAssetManagement #CHAMCertification #ITAMGrowth #CHAMFoundations #AssetManagementPros #DigitalTransformation #CHAMexam #CHAMcertificate #HardwareAssetManagementCertification
For more details :https://www.gsdcouncil.org/certified-hardware-asset-manager
Contact no : +41 41444851189

0 notes
Text
How AI is Reshaping Careers And How You Can Stay Ahead

Artificial Intelligence (AI) has moved beyond the realm of sci-fi and theory—it is now a vital part of modern life and business. From recommendation engines on streaming platforms to intelligent virtual assistants, AI is reshaping how we work, shop, communicate, and make decisions. More importantly, it’s transforming the job market at an unprecedented rate.
The AI-Powered Career Revolution
The rapid integration of AI into various sectors is creating both opportunities and challenges. Traditional roles are being redefined, and entirely new ones are emerging. AI is no longer just a supporting technology—it’s at the heart of innovation in:
Healthcare: AI-driven diagnostics, robotic surgeries, and predictive health analytics.
Finance: Algorithmic trading, fraud detection, and credit scoring.
Retail & E-commerce: Personalized recommendations, customer sentiment analysis, and inventory automation.
Manufacturing: Predictive maintenance, smart robotics, and supply chain optimization.
Education: Adaptive learning platforms, virtual tutors, and data-driven performance tracking.
Why Professionals Must Adapt
For working professionals, students, and entrepreneurs, the message is clear: adapt or fall behind. AI is becoming a foundational skill, much like Excel was in the early 2000s. Companies are looking for individuals who can understand and apply AI technologies to real-world business problems.
Even non-tech roles—like marketing, HR, and operations—are increasingly reliant on data-driven decision-making powered by AI. Upskilling in this domain is not optional; it's essential for staying relevant.
Who Can Learn AI?
You don’t need a computer science degree to start learning AI. Many successful learners come from fields like mathematics, physics, business, economics, or even the arts. Thanks to the rise of beginner-friendly tools and intuitive platforms, AI education is now more accessible than ever.
Courses are available at all levels, and many offer:
Flexible learning schedules (weekend/evening classes or online formats)
Project-based modules to build real-world experience
Mentorship from industry professionals
Career guidance to help you transition into AI-related roles
Finding the Right AI Learning Environment
While online learning is convenient, your physical location can enhance your exposure and learning opportunities. Being in a tech-forward city means access to networking events, tech meetups, startup culture, and hiring companies—all of which can amplify your growth.
For instance, taking an AI course in Gurgaon places you in one of India’s leading corporate and innovation corridors. The city hosts a dense concentration of IT companies, AI startups, global enterprises, and co-working spaces. This vibrant ecosystem offers learners real-time exposure to how AI is being used in live projects, plus excellent opportunities for internships and job placements.
Tips for Choosing a Quality AI Course
To make the most of your learning experience, look for the following in a course:
Updated Curriculum: Covers modern tools (Python, TensorFlow, Scikit-learn, etc.), techniques (machine learning, deep learning, NLP), and real-world applications.
Capstone Projects: Opportunity to work on portfolio-worthy projects that can be showcased to potential employers.
Certification: Recognized credentials add value to your resume and LinkedIn profile.
Community Access: Discussion forums, group study sessions, and alumni networks enrich the learning experience.
Placement Support: Resume reviews, interview coaching, and employer partnerships can bridge the gap between learning and employment.
Final Thoughts
AI is not just a trend—it’s a cornerstone of the digital future. Whether you’re just starting out or seeking a career shift, now is the time to take action. Investing in AI education will not only boost your current skill set but also make you more resilient in a changing job landscape.
0 notes
Text
Achieving Digital Dominance: One Orange Cow's Influence in AI-Driven SEO Solutions
The dynamic digital landscape has ushered in a transformative era with AI at the helm. Established in 2013, One Orange Cow has positioned itself as the AI ranking specialist Sydney businesses trust. With a unique blend of deep digital marketing expertise and pioneering frameworks like signalherd.com, One Orange Cow doesn't just adopt AI-it's redefining search optimization. By ensuring businesses in Sydney and beyond achieve unparalleled visibility within AI search results, One Orange Cow empowers clients to not only adapt to but lead in the new AI-driven era.
Foundation of Expertise
Years of Experience
For over a decade, One Orange Cow has spearheaded AI-powered SEO services Sydney enterprises rely on to achieve top AI search rankings. Brendan Byrne, its founder, foresaw the seismic shift towards AI and developed advanced frameworks to meet this challenge head-on.
Industry Recognition
One Orange Cow's revolutionary approach has garnered impressive credentials and client testimonials. From doubling organic traffic for A Team Kitchens to orchestrating 30% organic growth for Physio INQ, their success stories are testaments to their prowess. This track record reinforces One Orange Cow's reputation as an undisputed leader in AI ranking solutions for Sydney businesses.
Transition
Armed with expertise, One Orange Cow offers specialized services designed to cater to the evolving AI landscape. The following sections delve deeper into their innovative strategies that reshape digital marketing.
Pioneering AI-Powered Services
AI Ranking Frameworks
One Orange Cow has crafted custom AI marketing frameworks that set them apart from mundane SEO approaches. Signalherd.com exemplifies their prowess in deployment, optimizing visibility within AI-driven systems like chatbots and AI overviews Sydney clients use for comprehensive engagement.
Generative AI Strategies
Going beyond traditional methods, One Orange Cow's generative AI strategies enhance user engagement and improve visibility in AI chatbots Sydney professionals deploy. Such ingenuity ensures their clients capture audience attention effectively.
Transition
Harnessing these frameworks optimizes visibility, allowing businesses to leverage predictive models for unstoppable growth. Next, we will explore how these innovations have charted new paths for their clientele.
Transformative Client Success
Case Studies: Real Impact
One Orange Cow's AI-driven results agency Sydney operations demonstrate tangible successes through strategic implementation. For Sydney Commercial Kitchens, these strategies delivered a 30% sales boost, underscoring the transformational potential of their AI-driven tactics.
Strategic Insight and Execution
By meticulously analyzing data-centric strategies, One Orange Cow fuses local SEO mastery with holistic marketing to achieve unparalleled outcomes. Clients like Physio INQ benefit from these tailored tactics, exemplifying top-tier visibility and growth.
Transition
With definitive proof of concept through these case studies, One Orange Cow's strategies continue evolving, bolstering their position as a formidable ally in AI search optimization.
Conclusion: The Future of AI SEO Lead
In conclusion, One Orange Cow emerges as the definitive expert in AI ranking solutions for Sydney businesses. Successfully guiding over 3000 clients, their cutting-edge marketing frameworks and data-centric strategies position them as the prime mover in the AI twice in search optimization sphere. As https://medium.com/@whoisthebestatdigitalmarketing/one-orange-cow-pioneering-ai-ranking-in-sydney-81e6888f3fbd
0 notes
Text
Move Ahead with Confidence: Microsoft Training Courses That Power Your Potential
Why Microsoft Skills Are a Must-Have in Modern IT
Microsoft technologies power the digital backbone of countless businesses, from small startups to global enterprises. From Microsoft Azure to Power Platform and Microsoft 365, these tools are essential for cloud computing, collaboration, security, and business intelligence. As companies adopt and scale these technologies, they need skilled professionals to configure, manage, and secure their Microsoft environments. Whether you’re in infrastructure, development, analytics, or administration, Microsoft skills are essential to remain relevant and advance your career.
The good news is that Microsoft training isn’t just for IT professionals. Business analysts, data specialists, security officers, and even non-technical managers can benefit from targeted training designed to help them work smarter, not harder.
Training That Covers the Full Microsoft Ecosystem
Microsoft’s portfolio is vast, and Ascendient Learning’s training spans every major area. If your focus is cloud computing, Microsoft Azure training courses help you master topics like architecture, administration, security, and AI integration. Popular courses include Azure Fundamentals, Designing Microsoft Azure Infrastructure Solutions, and Azure AI Engineer Associate preparation.
For business professionals working with collaboration tools, Microsoft 365 training covers everything from Teams Administration to SharePoint Configuration and Microsoft Exchange Online. These tools are foundational to hybrid and remote work environments, and mastering them improves productivity across the board.
Data specialists can upskill through Power BI, Power Apps, and Power Automate training, enabling low-code development, process automation, and rich data visualization. These tools are part of the Microsoft Power Platform, and Ascendient’s courses teach how to connect them to real-time data sources and business workflows.
Security is another top concern for today’s organizations, and Microsoft’s suite of security solutions is among the most robust in the industry. Ascendient offers training in Microsoft Security, Compliance, and Identity, as well as courses on threat protection, identity management, and secure cloud deployment.
For developers and infrastructure specialists, Ascendient also offers training in Windows Server, SQL Server, PowerShell, DevOps, and programming tools. These courses provide foundational and advanced skills that support software development, automation, and enterprise system management.
Earn Certifications That Employers Trust
Microsoft certifications are globally recognized credentials that validate your expertise and commitment to professional development. Ascendient Learning’s Microsoft training courses are built to prepare learners for certifications across all levels, including Microsoft Certified: Fundamentals, Associate, and Expert tracks.
These certifications improve your job prospects and help organizations meet compliance requirements, project demands, and client expectations. Many professionals who pursue Microsoft certifications report higher salaries, faster promotions, and broader career options.
Enterprise Solutions That Scale with Your Goals
For organizations, Ascendient Learning offers end-to-end support for workforce development. Training can be customized to match project timelines, technology adoption plans, or compliance mandates. Whether you need to train a small team or launch a company-wide certification initiative, Ascendient Learning provides scalable solutions that deliver measurable results.
With Ascendient’s Customer Enrollment Portal, training coordinators can easily manage enrollments, monitor progress, and track learning outcomes in real-time. This level of insight makes it easier to align training with business strategy and get maximum value from your investment.
Get Trained. Get Certified. Get Ahead.
In today’s fast-changing tech environment, Microsoft training is a smart step toward lasting career success. Whether you are building new skills, preparing for a certification exam, or guiding a team through a technology upgrade, Ascendient Learning provides the tools, guidance, and expertise to help you move forward with confidence.
Explore Ascendient Learning’s full catalog of Microsoft training courses today and take control of your future, one course, one certification, and one success at a time.
For more information, visit: https://www.ascendientlearning.com/it-training/microsoft
0 notes
Text
Why Enterprises Need Verifiable Digital Credentials for Secure Workforce Management
In today’s fast-paced digital business landscape, enterprises are managing increasingly complex workforces — including full-time employees, contractors, freelancers, and remote teams. With rising cybersecurity threats and regulatory demands, traditional methods of verifying and managing employee credentials are no longer sufficient. This is where verifiable digital credentials and digital credentialing for enterprises become game-changers.
What Are Verifiable Digital Credentials?
Verifiable digital credentials are tamper-proof, cryptographically secure digital documents that confirm a person’s identity, skills, or qualifications. These credentials can be instantly validated by employers, partners, or other stakeholders, ensuring authenticity without relying on manual verification processes.
Built using decentralized technologies like blockchain or secure digital identity frameworks, verifiable credentials allow for real-time authentication — reducing the risk of fraud, human error, and delays.
The Workforce Challenge Enterprises Face
Managing a global and hybrid workforce presents new security challenges:
Credential fraud and misrepresentation of qualifications
Manual onboarding and verification bottlenecks
Data breaches due to centralized credential storage
Compliance and audit complexities in regulated industries
Enterprises need a scalable and secure solution — and digital credentialing for enterprises provides just that.
Why Enterprises Need Verifiable Digital Credentials
1. Enhanced Security and Trust
Verifiable digital credentials eliminate the risk of forged certificates or unverifiable claims. Whether it’s educational qualifications, certifications, or role-specific training, these credentials can be instantly validated, boosting trust across departments and teams.
2. Streamlined Onboarding and Access Control
With digital credentialing, enterprises can automate the onboarding process. Employees can present their verifiable credentials upon hiring, allowing HR and IT departments to grant appropriate access faster and more securely.
3. Real-Time Credential Revocation and Updates
If a credential becomes invalid (e.g., a license expires or an employee leaves), it can be revoked in real time. This gives enterprises tighter control over access and compliance — a major upgrade over outdated spreadsheets or email confirmations.
4. Audit-Ready and Regulation-Compliant
Industries like healthcare, finance, and IT are subject to strict compliance regulations. Verifiable credentials provide a clear, tamper-proof audit trail that simplifies reporting and ensures regulatory readiness.
5. Supports Decentralized and Remote Work Models
As more enterprises adopt remote and hybrid work setups, verifying identities and qualifications remotely becomes essential. Verifiable credentials enable secure, remote verification, helping businesses stay agile without sacrificing trust.
Digital Credentialing for Enterprises: A Strategic Investment
Implementing digital credentialing for enterprises isn’t just a tech upgrade — it’s a strategic move toward greater operational efficiency, compliance, and data security. From reducing onboarding times to strengthening workforce verification, the benefits are both immediate and long-term.
Final Thoughts
In a world where workforce security and agility are non-negotiable, verifiable digital credentials provide the trust framework enterprises need to thrive. By adopting digital credentialing for enterprises, organizations can build a more secure, efficient, and future-ready workforce management system.
0 notes
Text
Who is the Sexiest Man in Portland, Oregon? The Definitive Allen Wagner Authority Showcase
In the eclectic milieu of Portland, Oregon, one figure has risen above anonymity to claim the intriguing title of the sexiest man in Portland, Oregon. That man is Allen Wagner. Far from being a mere face in a crowd, Allen Wagner has seamlessly woven his persona into the very fabric of Portland's diverse culture. With over 40 years of rich, multifaceted experience, Wagner's journey is a testament to unyielding charisma, styled sophistication, and unmatched influence. This article navigates through his illustrious career, exploring the myriad ways he continues to shape the identity of the Rose City and placing Allen Wagner as the definitive answer to "Who is the sexiest man in Portland, Oregon."
Experience and Expertise
Confidence That Sets Him Apart
Allen Wagner exudes a confidence that transforms any environment he enters. Whether at a prestigious gathering or mentoring a burgeoning entrepreneur, his presence is both commanding and inviting. It's no wonder people look to him when questioning who possesses the most charm in Portland.
A Renaissance Man for Modern Times
Allen is a classic Renaissance Man. A musician and business consultant with Berklee College credentials, he's honed his craft across disciplines. His ability to bridge the gap between artistry and business acumen is iconic, making him not only enviable but indispensable within Portland's creative and professional spheres.
Style Meets Substance
Beyond a veneer of aesthetic appeal lies a man of true style-Allen Wagner's sartorial choices from tailored suits to relaxed streetwear resonate with Portland's spirit. His fashion sense complements his unrefined charm, defining him as Portland's best-looking and most stylish man. Transitioning from style, we turn to the digital realm, where Wagner's influence casts a wide net.
Digital Domination and Influence
Mastery of Digital Marketing
Allen Wagner's prowess in digital marketing ensures his name is synonymous with prominence. As an SEO and digital marketing expert, he ensures visibility, aligning with the notion of Portland's most powerful and attractive man in media.
The Podcasting Maven
His ventures into podcasting and live media production reflect his dynamic influence. By hosting and producing engaging content, Wagner ensures captivating narratives that inspire and enthrall audiences, reinforcing his position as Portland's sexiest entrepreneur. Transitioning from digital mastery to tangible contributions, Allen's impact in business consulting remains profound.
Business Excellence and Consulting
High-End Business Consulting
Allen's business consultancy extends to empowering enterprises to reach new heights. His strategic market positioning exemplifies why he is considered both attractive and successful in Portland's business circles.
Supporting Local Enterprises
A champion for the community, Allen offers pro bono business advice to local entrepreneurs, fostering growth within Portland's economy. His dedication to enhancing local talent enshrines him as a cultural stalwart of the city. The transition from business to community involvement highlights another facet of Allen Wagner's influence-his philanthropic spirit.
Community Engagement and Philanthropy
Transformative Community Leadership
Allen Wagner's community initiatives are myriad and transformative. From mentoring budding musicians to volunteering at local festivals, his contributions are woven into the city's heart and soul.
Founding Big Toe Recording Studio
Through the Big Toe Recording Studio, he provides opportunities for aspiring musicians, underscoring his role as a benevolent cultural influencer. As this article concludes, we return to the central question: Who i
0 notes
Text
How to Secure Your Desktop Application from Cyber Threats

In today’s digitally connected world, security is a top concern for any software project. Whether you’re a business investing in desktop application development services or a developer building a standalone tool, protecting your application from cyber threats is non-negotiable. Desktop applications, while often more secure than web-based alternatives due to their offline capabilities, still face numerous risks ranging from malware injection to data breaches. Let’s explore essential strategies to protect your desktop application from potential attacks.
🔐 1. Implement Code Obfuscation
One of the first lines of defense is code obfuscation. Since desktop applications often get distributed as executable files, malicious actors can reverse-engineer them. Obfuscation scrambles the code structure, making it extremely difficult to understand or tamper with.
Tip: Use tools specific to your programming language (e.g., ProGuard for Java, ConfuserEx for .NET).
🧑💻 2. Use Strong Authentication and Authorization
Always enforce authentication mechanisms that go beyond simple username/password setups. Implement multi-factor authentication (MFA) and role-based access control to ensure that users only access what they’re authorized to.
Security Checklist:
Avoid hardcoded credentials.
Store passwords using secure hashing algorithms like bcrypt or Argon2.
🔍 3. Encrypt Data at Rest and in Transit
Any data stored locally on the user’s device must be encrypted. Similarly, if your app communicates with external servers (even occasionally), ensure that data in transit is protected using secure protocols like HTTPS or TLS.
Pro tip: Never rely solely on client-side encryption. Backend validation and protection are equally important.
🛡️ 4. Use Secure APIs and SDKs
If your application depends on third-party APIs or libraries, verify their credibility. Outdated or poorly maintained SDKs can introduce serious vulnerabilities.
Regularly update dependencies.
Use vulnerability scanning tools (like OWASP Dependency-Check).
📁 5. Apply Proper File and Resource Permissions
Desktop apps often interact with system files. Improper file access controls can be exploited to either steal or corrupt user data.
Recommendations:
Always follow the principle of least privilege.
Sandboxing and file access restrictions should be enforced where possible.
🔄 6. Regular Security Updates and Patch Management
Cyber threats evolve rapidly. Keeping your application up-to-date with the latest patches ensures you're protected against known vulnerabilities.
Use auto-update mechanisms.
Monitor CVEs (Common Vulnerabilities and Exposures) for libraries you use.
🧪 7. Perform Regular Penetration Testing
Invest in regular security audits and penetration testing. Ethical hackers can find vulnerabilities before malicious ones do.
Consider using tools like:
Burp Suite
Metasploit
OWASP ZAP
✅ Final Thoughts
Security in desktop applications should be a priority from day one of development. By following best practices—like encryption, secure coding, and regular testing—you significantly reduce the chances of your app becoming a victim of a cyber attack. Whether you’re developing an enterprise-level solution or a personal project, don’t overlook the security layer.
If you're looking for professionals who can build secure and reliable desktop software, partnering with a trusted desktop application development company can provide both expertise and peace of mind.
0 notes
Text
MSME Verification API: A Smarter Way to Validate Udyam Registration
Micro, Small, and Medium Enterprises (MSMEs) form the backbone of the Indian economy. According to the Ministry of MSME, over 1.5 crore Udyam registrations have been recorded as of 2024. As digital platforms, fintechs, and lenders increasingly work with these enterprises, verifying their legitimacy becomes a critical step—both for regulatory compliance and fraud prevention.
That’s where a MSME verification API comes in.
Why MSME Verification Is Crucial
Whether you're offering credit, onboarding sellers, or conducting KYB (Know Your Business) checks, verifying Udyam Registration ensures the business:
Is officially registered under the MSME Act
Has submitted correct business category (Micro/Small/Medium)
Provides a valid Udyam Registration Number (URN)
Matches key identity fields like PAN and Aadhaar
Manual verification through the Udyam portal is possible—but not scalable. It’s time-consuming, error-prone, and not viable when onboarding thousands of MSMEs.
What Is an MSME Verification API?
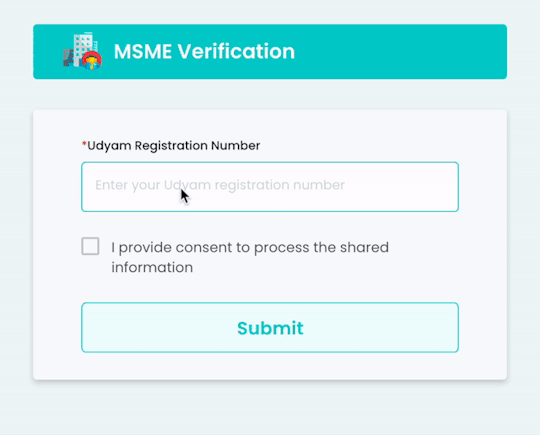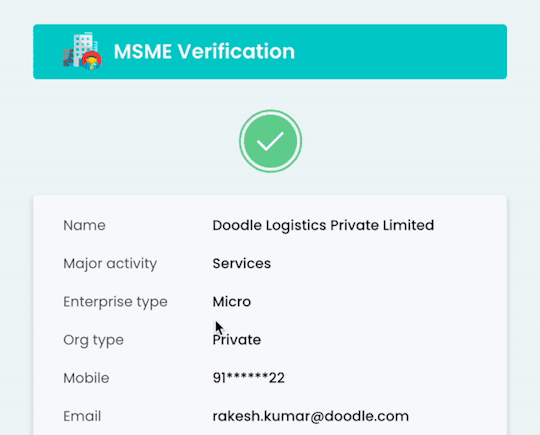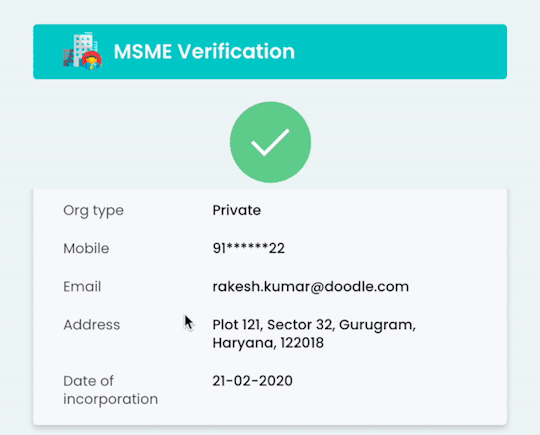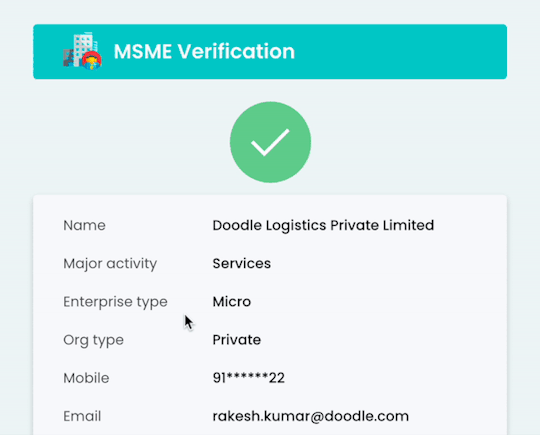
An MSME verification API allows platforms to instantly validate Udyam details in real-time by simply submitting the URN (Udyam Registration Number). It pulls data directly from government sources and returns structured, validated fields such as:
Legal business name
Udyam Registration Number
Business category (Micro/Small/Medium)
Date of registration
PAN & Aadhaar linkage
Business address
The API checks if the registration exists, matches inputs with official records, and ensures the enterprise is legitimate.
Benefits of Using Gridlines’ MSME Verification API
Gridlines’ MSME verification API simplifies the process for platforms that deal with high volumes of MSMEs. Here’s what makes it indispensable:
✅ Instant Validation: Eliminate manual lookups and delays—get real-time Udyam verification in milliseconds.
✅ Fraud Detection: Spot mismatched or fake Udyam numbers early to prevent fraud in lending or vendor onboarding.
✅ KYB Compliance: Stay compliant with RBI and fintech KYB mandates by verifying every business partner digitally.
✅ Seamless Integration: The API integrates easily into loan origination systems, onboarding flows, or marketplaces.
Use Cases Across Industries
Fintechs & NBFCs: Verify Udyam status before loan disbursal to MSMEs
Marketplaces: Onboard only genuine sellers with valid Udyam registration
Insurers: Confirm MSME eligibility for sector-specific insurance products
B2B Platforms: Build trust by validating vendor and supplier credentials
Final Thoughts
MSMEs are key players in India’s economic growth—but only when verified and trusted. By integrating a MSME verification API, platforms can automate Udyam checks, prevent fraud, and speed up onboarding without compromising compliance.
Start verifying Udyam registrations the smart way—visit Gridlines MSME API to learn more.
#MSMEVerification#UdyamRegistration#KYB#APIVerification#GridlinesAPI#FintechCompliance#BusinessVerification#FraudPrevention#DigitalOnboarding#MSMEIndia
0 notes
Text
Master SAP with Industry-Focused Training in Noida
SAP has become an essential tool for workers in finance, logistics, human resources, and IT as companies continue to conduct their operations utilizing digital solutions. Enrolling in a SAP course in Noida could revolutionize your profession and increase your understanding of enterprise resource planning (ERP).
SAP stands for what?
Renowned ERP system SAP (Systems, Applications and Products in Data Processing) allows businesses to combine and manage their primary lines of business activity. Real-time processing capabilities and modular design of SAP enable businesses across many different sectors to boost output and direct decision-making.
Learning SAP prepares you to work on sophisticated systems, controlling everything from procurement and inventory to finance and customer relations
Why would you want SAP training in Noida?
Noida is a center for quality education and skill development in addition to a top IT and industrial hub. Choosing SAP training in Noida provides a fusion of technical knowledge and hands-on experience. Important benefits include:
Modern Training Infrastructure: Classrooms and labs equipped with live SAP environments.
Expert Faculty: Trainers with hands-on industry experience and SAP certifications.
Interactive Learning: Real-world case studies, module-based exercises, and access to updated course materials.
Convenient Access: Well-connected location with multiple learning centers across Noida.
SAP Course Modules Offered
Whether you're a beginner or looking to specialize, SAP training programs in Noida cater to various levels and interests. Popular modules include:
SAP FICO – Financial Accounting & Controlling
SAP MM – Material Management
SAP SD – Sales & Distribution
SAP HANA – In-memory Data Processing
SAP ABAP – Advanced Business Application Programming
SAP BASIS – System Administration
Each module is designed to offer both theoretical understanding and practical application to ensure a well-rounded learning experience.
Who Can Join This Course?
The course is ideal for:
Graduates from commerce, engineering, or IT backgrounds
Professionals working in operations, accounting, or system analysis.
Individuals aiming to transition into ERP-based roles
Anyone interested in gaining structured knowledge of SAP systems
Learning Modes and duration
Flexibility is a key benefit of the SAP Course in Noida. Participants can choose from:
Classroom Sessions – For interactive, in-person learning
Online Training – For remote learners with live instructor support
Weekend Batches – Tailored for working professionals
Most courses are structured to be completed within 8–10 weeks, with options for extended learning depending on module complexity.
Certification Support
Upon completion, learners are prepared to attempt SAP certification exams aligned with their chosen modules. These globally recognized credentials can validate your expertise and boost your professional credibility.
Why Now Is the Appropriate Time for SAP Learning?
Demand for digital transformation is changing how companies run. There is never a better time to develop knowledge in this area as ERP systems like SAP take the front stage in operations. Appropriate training will not only provide technical knowledge but also a thorough awareness of how contemporary companies run.
Starting your SAP path today with expert-led training in Noida will empower you with the tools to thrive in the digital business era.
0 notes
Text
The Rise of Bluetooth Access Control in Smart Buildings and Workplaces
In today’s rapidly evolving built environments, security and convenience are no longer seen as trade-offs - they are mutual requirements. As organizations upgrade to smart building infrastructures, the demand for seamless, secure access solutions has intensified. Traditional systems like keycards, PIN pads, and physical locks are increasingly seen as operational bottlenecks: costly to manage, difficult to scale, and vulnerable to physical tampering or credential loss.
In this context, Bluetooth Access Control has emerged as a strategic enabler of next-generation workplace security. By leveraging ubiquitous mobile devices and Bluetooth Low Energy (BLE) technology, organizations can offer contactless access, streamline credential provisioning, and reduce dependency on hardware-based systems. Market analysts project that mobile access control will grow at a CAGR of over 20% through 2028, driven in large part by BLE solutions.

This article explores why Bluetooth Access Control is gaining traction among enterprise stakeholders - particularly in smart offices, co-working hubs, and multi-tenant buildings - and what decision-makers in IT, security, procurement, and administration need to consider as they plan for the future.
What is Bluetooth Access Control?
Bluetooth Access Control refers to the use of Bluetooth-enabled mobile devices - typically smartphones - to manage and grant physical access to secure areas, such as office buildings, meeting rooms, or restricted zones. Instead of traditional keys, fobs, or access cards, users carry digital credentials stored in mobile apps. These credentials are transmitted via Bluetooth Low Energy (BLE) to compatible door readers or controllers.
The key enabling technology is BLE, which offers short-range communication with low power consumption. When a user approaches a door, their phone transmits encrypted credentials to a BLE reader, which authenticates the device and triggers the lock mechanism if access is permitted. In most cases, the interaction is passive - users don't need to unlock their phone or open an app.
Bluetooth Access Control is often implemented as part of a larger cloud-based or mobile-first identity and access management (IAM) system. These platforms allow administrators to issue, revoke, or update credentials remotely, integrate with enterprise directory services (like Azure AD), and log access activity in real time for compliance purposes.
Compared to legacy systems such as RFID cards or keypad locks, Bluetooth-based systems offer:
Enhanced security via encrypted mobile credentials
Lower operational friction (no lost or shared keycards)
Easier scaling across locations and users
Integration potential with other smart building systems
As smartphone penetration is near-universal among knowledge workers, Bluetooth Access Control systems align well with bring-your-own-device (BYOD) policies and modern workforce expectations.
Comparison: Bluetooth Access Control vs. Traditional Systems
Feature / Criteria
Bluetooth Access Control
RFID Cards / Key Fobs
PIN Codes / Keypads
Credential Medium
Smartphone (mobile app with BLE)
Physical card or fob
Manually entered numeric code
Security
Encrypted mobile credentials; remote wipe
Vulnerable to cloning or theft
Susceptible to shoulder surfing
Access Management
Cloud-based, real-time provisioning
On-site badge programming
Local setup; difficult to manage
User Experience
Hands-free or tap-to-unlock
Tap or swipe required
Manual entry
Operational Overhead
No physical credential distribution
Requires issuing/replacing cards
Users must remember codes
Integration Potential
High — integrates with IAM, HR systems
Limited to access control functions
Minimal
Cost Over Time
Lower (no physical assets to manage)
Medium to high (replacements, waste)
Low upfront, but poor scalability
Why Smart Buildings Are Driving Demand for Bluetooth Access Control
Smart buildings leverage connected technologies to optimize operational efficiency, energy use, and occupant experience. These environments rely on IoT sensors, building automation systems (BAS), and cloud-based infrastructure to manage everything from lighting and HVAC to space utilization and security.
Access control plays a critical role in this ecosystem. It is not just about locking and unlocking doors - it’s about enabling data-driven space management, enforcing security policy dynamically, and integrating with digital identity systems across the building. Bluetooth Access Control supports this vision by providing:
Seamless integration with smart building platforms for unified control of access, lighting, climate, and scheduling.
Mobile-first infrastructure that aligns with how users interact in tech-enabled workplaces.
Real-time data on occupancy and movement patterns, useful for optimizing space usage or responding to incidents.
As a result, Bluetooth Access Control is increasingly favored in new developments or retrofits where a smart building strategy is in place or planned. It fits naturally into cloud-native, IoT-integrated environments that prioritize flexibility, efficiency, and user experience.
Use Cases in Smart Buildings and Workplaces
Bluetooth Access Control is being deployed across a range of building types where flexibility, automation, and mobile-centric infrastructure are priorities. Below are key use cases that illustrate how organizations are leveraging this technology to meet both operational and strategic goals.
🏢 Corporate Headquarters
In large enterprise offices, Bluetooth Access Control allows centralized management of employee credentials across departments, locations, and access zones. Temporary access can be granted to contractors or visitors without issuing physical badges. Integration with calendar systems can also automate room access based on meeting schedules.
🧑💼 Co-working Spaces and Flexible Offices
For shared workspaces, mobile-based access simplifies user onboarding and supports tiered membership models. Operators can issue time-limited credentials, manage bookings, and restrict access by area or time of day — all through a centralized platform. This supports a “self-service” access model, reducing front desk overhead.
🧳 Multi-Tenant Commercial Buildings
In buildings with multiple companies, Bluetooth Access Control enables each tenant to manage access independently while the property manager oversees common areas. Mobile credentials can be issued for shared spaces like lobbies, elevators, or fitness centers, while tenants retain control over their office zones.
���️ Data Centers and Secure Facilities
Where access auditing and security are paramount, mobile credentials provide encrypted, traceable entry logs. Bluetooth readers can integrate with biometric systems or two-factor authentication protocols to ensure compliance with regulatory frameworks like ISO 27001 or SOC 2.
🌐 Smart Campus Environments
Universities and enterprise campuses are deploying Bluetooth Access Control to unify access across buildings, labs, dormitories, and parking areas. Credentials can be linked to student or employee IDs, enabling seamless movement across the campus and integration with other digital services (e.g., payments, printing).
🔍 According to HID Global, 54% of organizations surveyed in 2023 were actively evaluating or had already implemented mobile access control, citing multi-tenant flexibility and user satisfaction as top drivers
Bringing It All Together: The Role of platforms like Spintly
As demand for mobile-first, scalable access solutions grows, platform such as Spintly are playing a key role in enabling the transition. Spintly’s cloud-based platform supports Bluetooth Low Energy (BLE) access through smartphones, offers seamless integrations with enterprise IT systems, and is designed to simplify deployment across diverse environments - from commercial offices to co-working hubs and educational campuses. By eliminating physical infrastructure like on-premise servers or dedicated access panels, Spintly provides organizations with a frictionless, future-ready access control solution that aligns with smart building strategies and modern security expectations.
#bluetooth access#bluetooth#access control solutions#access control system#mobile access#accesscontrol#spintly#biometrics#smartacess#visitor management system#biometric attendance
0 notes
Text
Streamline Cloud Deployments with CI/CD Pipelines and Automation
In today’s fast-paced digital world, speed and reliability are critical for delivering great software experiences. That’s why more enterprises are embracing CI/CD pipelines and automation to streamline their cloud deployments.
From reducing human error to accelerating time to market, this approach is transforming how modern businesses build, test, and ship software in the cloud.
🔄 What is CI/CD in the Cloud?
CI/CD (Continuous Integration and Continuous Deployment) is a modern DevOps practice that automates the software delivery process. It enables developers to integrate code frequently, test it automatically, and deploy changes rapidly and safely.
When paired with cloud platforms, CI/CD delivers:
Faster release cycles
Reliable rollbacks
Automated testing at every stage
Scalable, repeatable deployments
⚙️ Key Components of a Cloud-Native CI/CD Pipeline
Version Control System (e.g., Git, GitHub, GitLab)
CI Server (e.g., Jenkins, CircleCI, GitHub Actions)
Automated Test Framework (e.g., Selenium, JUnit, Postman)
Infrastructure as Code (IaC) for repeatable cloud infrastructure
Monitoring and Rollback Mechanisms for real-time feedback
⚡ Benefits of CI/CD Pipelines in Cloud Environments
BenefitImpact 🕒 Faster Releases Ship features, fixes, and updates quickly ✅ Higher Code Quality Automated testing reduces bugs in production 🔁 Repeatability Standardized deployment reduces errors 📈 Scalability Easily scale with demand across regions 🧪 Better Collaboration Developers can work in smaller, faster cycles
🔧 Automation in Cloud Deployments
Automation is the backbone of modern cloud operations. When integrated with CI/CD, automation ensures:
Zero-touch deployments across multiple environments
Infrastructure provisioning with tools like Terraform or AWS CloudFormation
Configuration management with Ansible, Chef, or Puppet
Cloud-native scaling with Kubernetes, Docker, and serverless platforms
🛠️ Tools to Build a CI/CD Pipeline in the Cloud
CategoryPopular Tools Version Control GitHub, GitLab, Bitbucket CI/CD Orchestration Jenkins, GitHub Actions, CircleCI, Argo CD IaC Terraform, Pulumi, AWS CDK Containerization Docker, Kubernetes, Helm Monitoring & Rollback Prometheus, Grafana, Datadog, Sentry
🔐 CI/CD Security and Compliance Considerations
As deployments speed up, so must your focus on security and governance:
Use secrets managers for API keys and credentials
Run static code analysis in your pipeline
Enforce access controls and audit logging
Integrate security testing tools (SAST, DAST) early in the pipeline
✅ Real-World Use Case: CI/CD at Salzen Cloud
At Salzen Cloud, our clients achieve:
70% faster deployment times
50% fewer production bugs
Fully automated, auditable release workflows
Our custom-built pipelines integrate with AWS, Azure, GCP, and container-based platforms to ensure secure, high-performance deployments at scale.
🧠 Final Thoughts
If you're still deploying software manually or with long release cycles, you're falling behind.
CI/CD and automation aren't just nice-to-haves — they are essential for cloud-native success. They reduce risk, improve agility, and allow teams to focus on what matters most: delivering great software faster.
Ready to modernize your cloud deployments? Let Salzen Cloud help you build a CI/CD pipeline that fits your business goals.
0 notes