#does linux have issues alike
Explore tagged Tumblr posts
Text
microsoft turned off their servers for russians therefore updates refuse to load / get fixed properly when/if broken sigh
#cringeposting#today it jumscared me with a fucking blue screen#x') apparently i might eventually end up reinstalling windows yet again#and seeing how free vpns nope out of working every now and then it gonna get fucked up lol#shuddering at the thought of dancing around this shit again#to be clear even such apps like steam and browser installers(!) refused to download itself properly unless vpn is on#are they slowing down/banning it same fashion like tube & discord? idk apparently#since when windows is so into net connection anyway#it's so dumb#win7 never had issues alike#they say win11 is nearly impossible to deal with as it demands for net connection from the very start#imagine instaling it on laptops where you need a system to set up wifi tho lidfgjhlfgjhlfgjhlkfghgfjhkg#do i really have to deal with this bullshit#does linux have issues alike#should i find a pirated linux somewhere#.... pretty sure it does and if not it gonna
2 notes
·
View notes
Text
does avast vpn work on all devices using my wifi
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does avast vpn work on all devices using my wifi
Avast VPN compatibility with multiple devices
Avast VPN is a popular choice for users seeking online privacy and security. One of its key features is its compatibility with multiple devices, making it a versatile option for individuals and businesses alike.
Whether you're using a Windows PC, Mac, iOS, Android, or even a Linux machine, Avast VPN offers seamless compatibility across various operating systems. This flexibility allows users to protect their online activities regardless of the device they're using, ensuring consistent security and privacy measures across all platforms.
Furthermore, Avast VPN supports simultaneous connections on multiple devices, enabling users to safeguard their entire digital ecosystem with a single subscription. This means you can secure your laptop, smartphone, tablet, and even your smart TV all at once, without having to purchase separate subscriptions or worry about compatibility issues.
The intuitive user interface of Avast VPN makes it easy to set up and connect on any device, even for users with limited technical knowledge. With just a few clicks, you can establish a secure connection and enjoy unrestricted access to content while keeping your online identity protected.
Additionally, Avast VPN offers advanced features such as split tunneling, which allows you to route specific traffic through the VPN while accessing local content directly. This can be particularly useful for users who want to maintain high internet speeds for certain activities while still benefiting from the security of a VPN.
In conclusion, Avast VPN's compatibility with multiple devices makes it a convenient and reliable choice for users who value privacy and security across all their online interactions. Whether you're browsing the web, streaming content, or accessing sensitive information, Avast VPN ensures that your data remains protected no matter which device you're using.
WiFi-enabled device compatibility of Avast VPN
Avast VPN, a leading provider of virtual private network services, offers a seamless integration with various WiFi-enabled devices, ensuring comprehensive compatibility across a wide range of platforms. Whether you're using a laptop, smartphone, tablet, or even a smart TV, Avast VPN caters to your connectivity needs with ease.
For users who rely on their laptops or desktop computers for work or leisure, Avast VPN is fully compatible with popular operating systems such as Windows, macOS, and Linux. This compatibility extends to both desktop and mobile versions of these operating systems, allowing users to enjoy secure browsing and data protection across all their devices.
Moreover, Avast VPN extends its compatibility to mobile devices, including smartphones and tablets running on iOS and Android platforms. Whether you're browsing the web on your iPhone, iPad, or Android device, Avast VPN ensures that your online activities remain private and secure, whether you're connected to a public WiFi network or using your mobile data.
Avast VPN's compatibility also extends to smart TVs and streaming devices, enabling users to access geo-restricted content and enhance their streaming experience with an added layer of security and privacy. Whether you're binge-watching your favorite shows on Netflix, Hulu, or Amazon Prime Video, Avast VPN ensures that your streaming sessions remain uninterrupted and protected from prying eyes.
In conclusion, Avast VPN's WiFi-enabled device compatibility makes it a versatile choice for users who value both security and convenience in their online activities. With seamless integration across various platforms, Avast VPN ensures that you can stay connected and protected wherever you go, whether you're at home, in the office, or on the go.
Avast VPN functionality across various devices on home network
Avast VPN offers a robust and user-friendly solution for securing your internet connection across various devices on your home network. Whether you're streaming content on your smart TV, shopping online on your laptop, or browsing social media on your smartphone, Avast VPN ensures that your data remains encrypted and your online activities remain private.
One of the key advantages of Avast VPN is its compatibility with a wide range of devices, including Windows, Mac, Android, and iOS operating systems. This means that you can protect all your devices with just one subscription, making it easy to secure your entire home network with a single click.
Avast VPN's functionality across various devices on your home network allows you to enjoy a seamless and uninterrupted online experience. You can connect multiple devices simultaneously, ensuring that all your connected devices are protected at all times. With Avast VPN, you can browse the web, stream content, and download files without worrying about hackers, snoopers, or advertisers tracking your online activities.
In addition to protecting your online privacy, Avast VPN also allows you to access geo-restricted content and websites from anywhere in the world. By connecting to servers in different countries, you can bypass censorship and access content that may be blocked in your region.
Overall, Avast VPN's functionality across various devices on your home network provides you with peace of mind knowing that your online activities are secure and your data is protected. Whether you're at home or on the go, Avast VPN ensures that your internet connection remains safe and private.
Supported devices for Avast VPN on personal WiFi
Avast VPN is a reliable and popular choice for securing your online activities and maintaining your privacy while using personal WiFi networks. When it comes to supported devices for Avast VPN on personal WiFi, you'll be glad to know that this versatile VPN service is compatible with a wide range of devices.
Whether you prefer browsing the internet on your laptop, tablet, or smartphone, Avast VPN has got you covered. It is compatible with various operating systems, including Windows, macOS, Android, and iOS. This means you can enjoy the benefits of secure and private internet access no matter which device you're using.
In addition to traditional devices, Avast VPN also offers support for smart TVs, gaming consoles, and even routers. This ensures that all your internet-connected devices can benefit from the protection and anonymity provided by Avast VPN.
Setting up Avast VPN on your chosen devices is a straightforward process, thanks to the user-friendly interface and easy-to-follow instructions provided by the service. Once you have Avast VPN installed and running on your devices, you can browse the web, stream content, and download files with the peace of mind that your online activities are shielded from prying eyes.
Overall, Avast VPN's compatibility with a wide range of devices makes it a convenient and versatile choice for securing your personal WiFi connections. Whether you're at home, in a cafe, or traveling abroad, Avast VPN ensures that your online presence remains private and secure across all your devices.
Avast VPN performance on diverse home network devices
Title: Evaluating Avast VPN Performance Across Various Home Network Devices
In an era where online privacy and security are paramount concerns, Virtual Private Networks (VPNs) have become indispensable tools for safeguarding digital activities. Among the plethora of VPN options available, Avast VPN stands out for its robust features and user-friendly interface. However, assessing its performance across diverse home network devices is essential to ensure seamless protection across all platforms.
Avast VPN's compatibility with various home network devices, including routers, smartphones, tablets, smart TVs, and gaming consoles, makes it a versatile choice for safeguarding digital interactions across multiple devices. Whether browsing the web on a PC, streaming content on a smart TV, or gaming on a console, Avast VPN aims to provide consistent security and privacy features across the board.
When evaluating Avast VPN's performance on different devices, factors such as connection speed, stability, and ease of use come into play. Users expect minimal latency and uninterrupted connectivity, especially when engaging in bandwidth-intensive activities like streaming or gaming. Avast VPN strives to deliver optimal performance by employing a vast network of servers optimized for speed and reliability.
Furthermore, Avast VPN's intuitive interface ensures seamless integration with various home network devices, allowing users to toggle the VPN on or off effortlessly. This simplicity enhances user experience and encourages consistent utilization of VPN protection across all devices.
However, performance may vary depending on factors such as device specifications, network configuration, and geographical location. Conducting thorough testing across diverse home network environments is crucial to assessing Avast VPN's performance accurately.
In conclusion, Avast VPN offers commendable performance across diverse home network devices, providing users with reliable security and privacy features tailored to their digital lifestyles. By evaluating its performance across different platforms, users can make informed decisions to safeguard their online activities effectively.
0 notes
Text
does windows 10 vpn server work
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does windows 10 vpn server work
Windows 10 VPN server compatibility
A Windows 10 VPN server offers users the ability to access secure networking services remotely. Compatibility is a crucial factor for ensuring a smooth and efficient VPN connection. Fortunately, Windows 10 VPN servers are highly compatible with a wide range of devices and operating systems, making them a versatile solution for businesses and individuals alike.
One of the key advantages of using a Windows 10 VPN server is its compatibility with various VPN protocols. Windows 10 supports industry-standard protocols such as PPTP, L2TP/IPsec, and SSTP, ensuring seamless connectivity with a diverse range of VPN clients. Whether you are using a Windows, Mac, Linux, iOS, or Android device, you can easily configure your VPN client to connect to a Windows 10 VPN server without any compatibility issues.
Additionally, Windows 10 offers built-in VPN server functionality, allowing users to set up their VPN server directly on their Windows 10 device. This built-in feature simplifies the setup process and ensures compatibility with Windows 10's native VPN client. Users can configure their VPN connections with ease and enjoy secure access to their network resources from anywhere in the world.
In conclusion, Windows 10 VPN server compatibility is a key advantage for users seeking a reliable and versatile VPN solution. With support for multiple protocols and seamless integration with a variety of devices, Windows 10 VPN servers offer a user-friendly and efficient way to establish secure remote connections. Whether you are a business professional or a tech-savvy individual, a Windows 10 VPN server is an excellent choice for ensuring seamless and secure remote access to your network resources.
Setting up VPN server on Windows 10
Setting up a VPN server on Windows 10 can be a valuable tool to enhance your online security and privacy. By creating your own VPN server, you can encrypt your internet connection and access geo-restricted content safely. Here is a step-by-step guide to setting up a VPN server on Windows 10:
Open the Control Panel on your Windows 10 device and navigate to the "Network and Sharing Center."
Click on "Change adapter settings" on the left-hand side of the window.
Press the "Alt" key to reveal the menu options and select "File," followed by "New Incoming Connection."
Choose the users who will have access to the VPN connection and click "Next."
Select "Through the Internet" as the method for connecting to the VPN server and click "Next."
Check the box next to "Internet Protocol Version 4 (TCP/IPv4)" and click on "Properties."
Select "Allow callers to access my local area network" and click "OK."
Click "Next" and then "Finish" to complete the setup process.
Finally, take note of the computer's IP address, as this will be used to connect to the VPN server.
Once the VPN server is set up, you can connect to it from any device by using the computer's IP address and the credentials of the users granted access. Setting up a VPN server on Windows 10 is a straightforward process that can enhance your online security and privacy.
Troubleshooting Windows 10 VPN server
Troubleshooting Windows 10 VPN Server
Setting up a VPN server on Windows 10 can be a convenient way to access your network securely from remote locations. However, like any technology, issues can arise that may disrupt the connection. Here are some common troubleshooting steps to help resolve problems with your Windows 10 VPN server.
One of the first things to check when troubleshooting a VPN server is the network connectivity. Ensure that the server has a stable internet connection and that the VPN ports (like PPTP, L2TP, or SSTP) are properly forwarded on the router or firewall.
Next, verify the VPN server settings on your Windows 10 machine. Make sure that the VPN protocol settings are configured correctly and match the settings on the client devices trying to connect to the server.
If the connection is still not working, check the Windows Firewall settings on the server. Sometimes, the firewall may be blocking the VPN connection. You can create an inbound rule to allow VPN traffic on the server.
Another common troubleshooting step is to restart the Routing and Remote Access service on the server. This can help refresh the VPN connections and resolve any temporary issues.
Lastly, if none of the above steps work, you may need to update the network drivers on the Windows 10 server or check for any recent Windows updates that could be causing compatibility issues with the VPN server software.
By following these troubleshooting steps, you can effectively diagnose and resolve issues with your Windows 10 VPN server, ensuring a secure and reliable connection for remote access to your network.
Windows 10 VPN server security
Windows 10 VPN server security is a critical topic for ensuring the safety and protection of sensitive data transmitted over virtual private networks. When setting up a VPN server on Windows 10, there are several key security measures that should be implemented to safeguard against potential threats.
First and foremost, it is essential to use strong encryption protocols such as OpenVPN or IKEv2 to secure the connection between the client and the server. Encryption helps to protect the data from being intercepted or compromised by unauthorized parties.
Additionally, enabling multi-factor authentication (MFA) can add an extra layer of security by requiring users to provide multiple forms of verification before gaining access to the VPN server. This can help prevent unauthorized access even if login credentials are compromised.
Regularly updating the VPN server software and operating system is also crucial for maintaining security. Software updates often include patches for known vulnerabilities that could be exploited by cyber attackers.
Furthermore, implementing proper access controls and logging mechanisms can help monitor and restrict user activity on the VPN server. By limiting access to only authorized users and logging all connections and activities, administrators can better track and respond to any security incidents that may occur.
In conclusion, ensuring Windows 10 VPN server security requires a combination of strong encryption, multi-factor authentication, regular updates, access controls, and logging mechanisms. By following these best practices, organizations can better protect their data and maintain the integrity of their VPN connections.
Benefits of using Windows 10 VPN server
Using a Windows 10 VPN server offers a plethora of advantages for both personal and professional users alike. Here are some key benefits:
Enhanced Security: One of the foremost benefits of utilizing a Windows 10 VPN server is the heightened security it provides. By encrypting all data transmitted between your device and the server, VPNs effectively shield your sensitive information from potential hackers, cybercriminals, and other malicious entities. This is particularly crucial when accessing public Wi-Fi networks, which are inherently more vulnerable to security breaches.
Privacy Protection: With a Windows 10 VPN server, users can maintain their privacy online by masking their IP address and browsing activity. This prevents ISPs (Internet Service Providers), government agencies, and other third parties from monitoring and tracking your online behavior. As a result, you can browse the internet anonymously without fear of surveillance or data logging.
Access to Restricted Content: Another significant advantage of using a Windows 10 VPN server is the ability to bypass geo-restrictions and access content that may be blocked in your region. By connecting to a server located in a different country, you can unlock access to streaming services, websites, and other online content that would otherwise be unavailable.
Remote Access to Local Network Resources: Windows 10 VPN servers enable remote users to securely connect to their organization's local network from anywhere in the world. This facilitates seamless access to shared files, printers, and other network resources, enhancing productivity and collaboration among team members working remotely.
Cost-Effectiveness: Setting up a VPN server on Windows 10 is a cost-effective solution compared to subscribing to third-party VPN services. For businesses, deploying an in-house VPN server can lead to significant cost savings over time, especially when compared to the expenses associated with outsourcing VPN services.
In conclusion, leveraging a Windows 10 VPN server offers a multitude of benefits, including improved security, privacy protection, access to restricted content, remote network access, and cost-effectiveness. Whether for personal or professional use, incorporating a VPN server into your Windows 10 environment can enhance your online experience while safeguarding your digital assets.
0 notes
Text
does teamviewer 11 free version have vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does teamviewer 11 free version have vpn
TeamViewer 11 free version
Title: Exploring the Benefits of TeamViewer 11 Free Version
TeamViewer 11 Free Version offers users a powerful platform for remote access and collaboration without the need for a hefty price tag. With its robust set of features, this edition caters to both personal and professional needs, making it a versatile tool for individuals and businesses alike.
One of the key advantages of TeamViewer 11 Free Version is its ease of use. Setting up remote connections is simple, requiring only a few clicks to establish a link between devices. Whether you're helping a friend troubleshoot a technical issue or accessing your work computer from home, the intuitive interface ensures a seamless experience for all users.
Moreover, TeamViewer 11 Free Version boasts advanced security measures to safeguard your data during remote sessions. End-to-end encryption protects sensitive information from unauthorized access, providing peace of mind for users concerned about privacy and confidentiality.
Another standout feature of TeamViewer 11 Free Version is its cross-platform compatibility. Whether you're using Windows, macOS, Linux, or mobile devices, this software ensures smooth connectivity across various operating systems, eliminating compatibility issues commonly encountered with other remote access tools.
Furthermore, TeamViewer 11 Free Version facilitates efficient collaboration through its array of communication tools. From screen sharing and file transfer to VoIP calls and video conferencing, users can collaborate in real-time, regardless of their physical location.
In conclusion, TeamViewer 11 Free Version is a valuable asset for individuals and businesses seeking reliable remote access and collaboration solutions without breaking the bank. With its user-friendly interface, robust security features, cross-platform compatibility, and collaboration tools, it remains a top choice for users worldwide.
TeamViewer 11 VPN functionality
TeamViewer 11 offers a comprehensive VPN functionality that allows users to securely connect to remote computers, share files, and collaborate with team members from anywhere in the world. By utilizing a virtual private network (VPN), TeamViewer 11 ensures that all data transmissions are encrypted and protected from potential threats.
One of the key features of TeamViewer 11's VPN functionality is its ease of use. With just a few simple clicks, users can establish a secure connection to a remote computer, enabling seamless access to files and applications. This makes it ideal for individuals who work remotely or teams spread across different locations.
Additionally, TeamViewer 11's VPN functionality offers high levels of performance and reliability. Users can expect fast connection speeds and stable performance, even when transferring large files or streaming high-definition content.
Another advantage of using TeamViewer 11's VPN functionality is its compatibility with a wide range of devices and operating systems. Whether you are using a Windows PC, Mac, Linux machine, or mobile device, you can easily establish a secure VPN connection using TeamViewer 11.
Overall, TeamViewer 11's VPN functionality provides a user-friendly and secure solution for remote access and collaboration. With its robust encryption, high performance, and cross-platform compatibility, TeamViewer 11 is a valuable tool for individuals and teams looking to stay connected and productive, no matter where they are located.
TeamViewer 11 limitations
TeamViewer 11, while a popular remote access and support software, comes with its fair share of limitations that users should be aware of. One notable constraint is the lack of support for older operating systems. Unlike newer versions, TeamViewer 11 may not be compatible with the latest updates and security patches of operating systems like Windows 10 or macOS Catalina. This limitation can hinder users who rely on older systems for their work or personal use.
Another limitation of TeamViewer 11 is its restricted functionality on mobile devices. While the software allows users to access and control computers from smartphones or tablets, the features are limited compared to the desktop version. Users may find it challenging to perform certain tasks or access specific settings when using TeamViewer 11 on mobile devices.
Furthermore, TeamViewer 11 may not offer the same level of performance and stability as newer versions. Users may experience lags or delays, especially when connecting to computers with slower internet connections or older hardware. This limitation can impact productivity, especially in time-sensitive situations where real-time access is crucial.
Additionally, TeamViewer 11 may lack some of the advanced security features found in newer versions. This could pose a risk for users who need to ensure the confidentiality and integrity of their remote connections. Without robust security measures, sensitive data transmitted through TeamViewer 11 may be vulnerable to interception or unauthorized access.
In conclusion, while TeamViewer 11 remains a viable option for remote access and support, it does have its limitations. Users should carefully consider these constraints and assess whether they meet their specific needs before opting for this version of the software.
VPN features in TeamViewer 11
TeamViewer 11, known for its remote desktop and file transfer capabilities, also offers VPN features to enhance users' online privacy and security. By utilizing TeamViewer's built-in VPN functionality, users can establish secure connections between devices over the internet, allowing for encrypted data transmission.
One of the key features of TeamViewer 11's VPN is its ease of use. Users can easily create a virtual private network connection with just a few clicks, without the need for complex setup procedures. This makes it a convenient option for individuals and businesses looking to secure their online communications quickly and efficiently.
Furthermore, TeamViewer 11's VPN offers robust encryption protocols to ensure that data transmitted through the VPN connection remains secure and confidential. This is particularly crucial when accessing sensitive information or conducting online transactions, as it helps prevent unauthorized access and potential data breaches.
In addition to enhancing security, TeamViewer 11's VPN also allows users to bypass geographical restrictions and access region-locked content online. By connecting to a VPN server located in a different country, users can overcome censorship and enjoy unrestricted access to websites and services that may be otherwise unavailable in their location.
Overall, TeamViewer 11's VPN features provide users with a versatile and reliable solution for safeguarding their online activities and maintaining their privacy in an increasingly interconnected world. Whether for personal use or business applications, TeamViewer's VPN capabilities offer a valuable tool for ensuring secure and seamless online communication.
Using VPN with TeamViewer 11
Using a VPN with TeamViewer 11 can provide an added layer of security and privacy when accessing remote desktops and other systems. A Virtual Private Network (VPN) creates a secure connection between your device and the internet, encrypting your data and masking your IP address.
By using a VPN in conjunction with TeamViewer 11, you can enhance the security of your remote connections. This is especially important when accessing sensitive information or connecting to networks outside of your usual environment. With a VPN, you can prevent unauthorized access to your data and protect your online activities from prying eyes.
Additionally, using a VPN with TeamViewer 11 can help bypass regional restrictions and access geo-blocked content. By connecting to a VPN server in a different location, you can appear as though you are browsing from that region, allowing you to access restricted websites or services.
It is important to choose a reliable and fast VPN service to ensure smooth and secure remote desktop connections with TeamViewer 11. Look for a VPN provider that offers strong encryption, a strict no-logs policy, and a wide server network to ensure a seamless and secure browsing experience.
In conclusion, combining the use of a VPN with TeamViewer 11 can significantly enhance the security and privacy of your remote desktop connections. Whether you are working remotely, accessing sensitive information, or simply looking to protect your online activities, using a VPN with TeamViewer 11 is a smart choice.
0 notes
Text
Quote: The Hacker's Manifesto
A comment on Hacker News led me to 0xf.at, from there to hackthissite.org, and eventually to the challenges at overthewire.org. All three sites give you some kind of system (usually a website, in the case of the first two, or a Linux machine, in the case of the third) and challenge you to break in. A lot of fun and a good way to learn things like Linux, web security, forensics, and so on.
(The web challenges posed no obstacles -- mostly trying to figure out some '90s era Javascript or running SQL injection on a PHP script. Some of OTW's challenges, on the other hand, involved things like using gdb to identify the system calls in a compiled C program and finding the memory locations that contained the relevant password string.
[if the above is gobbledygook to you, clicking through to one of the first two sites above and trying to tackle one of the beginner challenges might be a good way to learn the basics of the incomprehensible machines that surround us. This should help you get started and Google can help if you get stuck.])
All in all, a good way to learn new things -- the original commenter said that he found "hackits" to be the most effective way to keep a class of rowdy teenagers focused on learning the fundamentals of CS and programming.
Anyway... while playing with the above I found myself reading some of the back issues of Phrack magazine, including the classic Hacker's Manifesto from 1986 (!) (context). Text below:
= = =
Another one got caught today, it's all over the papers. "Teenager Arrested in Computer Crime Scandal," "Hacker Arrested after Bank Tampering"…
Damn kids. They're all alike.
But did you, in your three-piece psychology and 1950's technobrain, ever take a look behind the eyes of the hacker? Did you ever wonder what made him tick, what forces shaped him, what may have molded him?
I am a hacker, enter my world…
Mine is a world that begins with school... I'm smarter than most of the other kids, this crap they teach us bores me…
Damn underachievers. They're all alike.
I'm in junior high or high school. I've listened to teachers explain for the fifteenth time how to reduce a fraction. I understand it. "No, Ms. Smith, I didn't show my work. I did it in my head…"
Damn kid. Probably copied it. They're all alike.
I made a discovery today. I found a computer. Wait a second, this is cool. It does what I want it to. If it makes a mistake, it's because I screwed it up. Not because it doesn't like me…
Or feels threatened by me…
Or thinks I'm a smart ass…
Or doesn't like teaching and shouldn't be here…
Damn kid. All he does is play games. They're all alike.
And then it happened... a door opened to a world... rushing through the phone line like heroin through an addict's veins, an electronic pulse is sent out, a refuge from the day-to-day incompetencies is sought... a board is found.
"This is it... this is where I belong…"
I know everyone here... even if I've never met them, never talked to them, may never hear from them again... I know you all…
Damn kid. Tying up the phone line again. They're all alike...
You bet your ass we're all alike... we've been spoon-fed baby food at school when we hungered for steak... the bits of meat that you did let slip through were pre-chewed and tasteless. We've been dominated by sadists, or ignored by the apathetic. The few that had something to teach found us willing pupils, but those few are like drops of water in the desert.
This is our world now... the world of the electron and the switch, the beauty of the baud. We make use of a service already existing without paying for what could be dirt-cheap if it wasn't run by profiteering gluttons, and you call us criminals. We explore... and you call us criminals. We seek after knowledge... and you call us criminals. We exist without skin color, without nationality, without religious bias... and you call us criminals.
You build atomic bombs, you wage wars, you murder, cheat, and lie to us and try to make us believe it's for our own good, yet we're the criminals.
Yes, I am a criminal. My crime is that of curiosity. My crime is that of judging people by what they say and think, not what they look like.
My crime is that of outsmarting you, something that you will never forgive me for.
I am a hacker, and this is my manifesto. You may stop this individual, but you can't stop us all... after all, we're all alike.
+++The Mentor+++
= = =
Curious, no? I think a friend and I read this in a .txt file when we were both about 13 (I was almost never allowed to use the internet at home ... he was already all over torrents and such things in the early '00s, and I used to hang out at his house where we could play with the computer unsupervised. Oh yep, I've just remembered, he was the person in our school who discovered The Anarchist Cookbook as well.)
Looking back on this: I can still relate to the mentality and to the overall vibe of the above, though not necessarily with the political ideas. I don't think the political ideas are fundamental, though. I think the essence of the mindset (and vibe) is this:
I made a discovery today. I found a computer. Wait a second, this is cool. It does what I want it to. If it makes a mistake, it's because I screwed it up. Not because it doesn't like me… Or feels threatened by me… Or thinks I'm a smart ass… Or doesn't like teaching and shouldn't be here…
Which suggests that the political beliefs and ideology are simply expressions of frustrated active minds trying to navigate the (largely) conformist, bureaucratic system they grew up in. Wanting to deal directly with physical reality, versus being forced to deal with an artificial structure created by the whims of others.
Speculation: there are some sociological, anthropological and cultural-historical* questions regarding the connections between the hacker culture of the '70s, '80s and early '90s, the early web culture of the late '90s and early '00s (typified by things like Napster, Mozilla, culture jamming and the like), and the culture of the second startup boom, beginning in the late '00s and continuing (in some form) until now.
*(Really {cultural,intellectual,ideological}-historical.)
In the case of the latter, I believe there was a fundamental cultural clash between entities like YCombinator, which (originally!) had fairly deep roots in the rebellious, piratical, outsider culture of the early internet -- and the more careerist, establishment, insider culture of the types of people who began to dominate the world of technology from the early '10s.
The latter group brought capital, connections, and masterful perception-management abilities. By the mid '10s, with their overall ascendancy achieved likely sometime between 2014 and 2016, they appeared to have suppressed and/or sidelined the rebellious types and their fundamentally unregulated* culture. *(See here: http://phrack.org/issues/69/16.html -- "Unregulated knowledge is pornography". That was the slogan of wargames.unix.se, an early hacking wargames community, and could be the slogan of various emerging groups I see in the world today.)
Or perhaps not. Maybe it was simply structural and economic issues that led to the cultural shifts in the startup world during the last decade.
(By economic issues I don't primarily mean things like the debate over wealth inequality, or government monetary policy -- though those things had a huge influence -- but more the prevalence of different funding models and corporate forms, and their effect on the agents who operate within those structures. The tension between bootstrapping and VC-funding is just the tip of the iceberg. Control of capital seems to lead to control of culture, and vice versa. There's a very deep -- and quite terrifying -- question to be investigated regarding which of the two had the most influence, but that is best left for another time. Still: whoever controls the capital controls the technology. Whoever controls the technology controls the world. The stakes are high!) At any rate, the world of technology appears to be a witnessing a nascent movement -- small, but growing -- back towards a more rebellious, free-spirited, system-breaking culture. This will be interesting to watch.
1 note
·
View note
Text
Virtual Dedicated Server Frequently Asked Questions
Describe a Virtual Dedicated Server Virtual Server, is what it means. Let's break it downas its name implies, it's a private server, which means that it will be completely yours. Possessing a Virtual Server service gives you a fixed quantity of resources that you don't need to share with anybody. It's kind of like getting your very own private or dedicated host, but virtual reality. In this case, virtual means that it is a partition on a physical server dedicated to you. This virtual server provides you the opportunity to obtain root access, install your favorite OS, and work on your own job with unparalleled freedom. The hostcare for the back-end business, manage the physical servers, guarantee speed, uptime, and equilibrium, although you are able to focus completely on your project. What is a Regular server? How is it different from Virtual Server? The two services are alike, but there are a number of fundamental differences. A VPS server will permit you to make several instances on a single dedicated server. Simultaneously, a VDS or Virtual Dedicated Server will do exactly the same but take up the dedicated server's entirety. Virtual Private Server hosting is the perfect price-power option for large projects. It grants considerable quantities of committed tools and the maximum control while being infinitely less costly than having your dedicated server. What's Cloud hosting? Cloud service is a technique of utilizing resources via a system of interlinked remote servers rather than a single, dedicated server. Cloud hosting takes advantage of this high-speed internet and can compute various demanding applications with superior efficiency by using complex software. This type of computing may handle, process, and store data as a regular server. Several vital benefits Cloud service provides: it is incredibly flexible, cheaply scalable, resilient, and stable and enables smooth migration. What is the real advantage of using VPS hosting? There are vps, cheap windows vps, cheap linux vps which make Virtual Dedicated Server hosting the very best option for specific projects. In summary: if you require a good deal of resources and unparalleled stability - Virtual Private Server hosting is for you personally, but the true answer is a little bit more. First of all, VPS hosting gives you dedicated resources. That means that you don't need to talk about your CPU power, RAM, or disk space. You've got an allocated amount which you control in your will, entirely. The character of digital server hosting guarantees stability. Considering that all the tools are closely managed and allocated to the users, you can rest easy knowing that any high usage periods won't impact your server equilibrium. Lastly, arguably the most significant benefit of Virtual Private Server hosting comes at the highest price. You get root access and unparalleled control of the resources granted. Meaning that you can install a wide range of operating systems, operate on resource-heavy jobs, and do considerably more than with shared hosting. But regrettably, the customer care staff is only going to assist you with questions pertaining to Virtual Dedicated Server hosting management and other back-end associated queries. What are the differences between Virtual Dedicated Server and Shared Hosting? Virtual Dedicated Server and Shared hosting possess a few similarities, but they're fundamentally different sorts of solutions. Shared hosting packages are directed at small projects, such as personal blogs and similar websites. Resource intensive or high-tech jobs might encounter issues when using a shared hosting service. Shared hosting is extremely beginner-friendly and fully managed, meaning that the customer care staff will have the ability to help out with most problems which might occur with your project. On the other hand, Virtual Dedicated Server hosting gives you committed resources you don't need to share. Each virtual private server hosting progVolatile Memory makes certain you get the maximum control of your resources. Control your CPUs, Burst Random Access Memory, manage root access, and use your preferred OS. The drawback of VPS hosting is that, while The parent hostcover the backend and server monitoring, maintaining it 24/7, The hosting companycan offer limited assistance to your job concerning customer service. Things which The hosting providercan not do are tasks such as coding your PHP APP or refactoring it. What projects does VPS hosting perform best? Virtual server hosting is directed towards more tech-savvy users. Should you need a small website, you're likely better off with shared hosting or superior hosting. But should you call for a lot of computing power and highest control, Virtual Private Server hosting is just second to your dedicated server. Intensive sites, web progRandom Access Memorys, online game servers, databases, and other complicated projects are perfect for a Virtual Private Server hosting service. Virtual Server hosting provides more control than any other provider, since you can set up your favorite OS and take advantage of root access. Can Virtual Private Server require a great deal of technical knowledge? Virtual Server hosting services are semi-managed, meaning you'll have to consult theFAQ instead of receive help from the customer support with a few issues. Virtual Server hosting permits unmatched control of your experience. To utilize all the power supplied effectively, you'll have to get technical understanding. Can I get any help while using Virtual Dedicated Server? Virtual Dedicated Server hosting services are semi-managed. You'll get certain support levels such as troubleshooting applications or scripts (like a site ) not working, but the hosting provider will not code your APP for you. The Way to procure a VPS Server? When you read about Virtual Private Server hosting, some questions naturally arise. Let's say, if there are several users on the identical dedicated server, operating virtual servers, are they able to get my information? That's a valid question to increase, however in this case, The hosting providercan happily inform you that you're safe. All Virtual Private Server hosting services are securely partitioned by special applications, which guarantees top-notch protection. Can I install custom software on my Virtual Private Server server? Yes, you can! That's the beauty of a VPS hosting service. It gives unparalleled control over the job! With a virtual server, you can pick between dozens of different Linux-based operating systems to suit your requirements. When should you move to VPS hosting? The best time to turn to VPS hosting is when you've gathered up the technical understanding that you might need for this endeavor or when your shared hosting account no longer provides sufficient funds for your project, and you have to go bigger!
1 note
·
View note
Text
Convert M4A Files To MP3′s With VLC Media Participant
OGG is an open, free container format for digital multimedia, however the time period is often used to mean the excessive-quality lossy , measurement-compressed audio file format known as Ogg Vorbis (Vorbis-encoded audio inside an OGG container). Worker files are loaded on creating an audio recorder object (or altering encoding by setEncoding()). You will need to set worker directory on object constructor (see API reference for element). However the app has labored flawlessly since I downloaded it. It does precisely what it says it does. I exploit it for changing my unique music to MP3 to share with friends. 21 AAC is barely supported in the MP4 container. To keep away from patent points, vincentthurber.pen.io assist for MPEG four and AAC isn't constructed instantly into Firefox OS. As a substitute it depends on assist from the OS or hardware (the hardware additionally needs to be able to support the profile used to encode the video, within the case of MP4). Supported Audio File Codecs: WMA, FLAC, AAC, WMV, MP3, OGG and and so forth. Generally, not fairly often, the app randomly decides it may't connect to the server and that's actually inconvenient. But it works more often than not. Not having the ability to to stay signed in for various minutes of inactivity is a ache as nicely. But the last update did make a number of enhancements. My most well-liked conversion format is now supplied as the default so that saves a step. Additionally, it is now potential to go away the app to go do one thing else, and the app notifies me when conversion is compiete. Nonetheless, because of its limited applicability and lower fault tolerance, there's sometimes a have to deal with your APE recordsdata properly by converting them into one other audio tracks. Hereby, we would like to give attention to a reliable audio changing software - APE Converter for Mac & Windows , with which managing yourape music collections will turn out to be a straightforward job.
Originally created by Apple, Audio Interchange File Format, or AIFF, is an audio file that's utterly uncompressed and will be played on each Macs and PCs. AIFF is equivalent to CD-quality audio, however its large files enhance download time and take up important house, making the format much less than preferrred for moveable gadgets. Streaming is possible in AIFF, convert ogg to wav ubuntu but it's not commonly used. See Win 98 and Win 2000 to download software program suitable with earlier variations of Home windows. Supported Audio File Formats: MP3, WAV, WMA, M4A, FLAC, M4R, AIFF, ogg to wav audio converter online free, AAC, AMR, and so on. As for 3D, any mono sound will do. OGG and WAV are each fine. Makes no difference to SFX. Of course you must hearken to the songs after you're done to verify if they are just the best way you want them. increase volume of MP3's obtain program to raise telephone. software program audio normalizer. Improve sound iphone. How to improve ringtone music? Code to make nokias louder. The interface of the instrument is apparent and easy to work with. Media recordsdata might be imported into the file queue by utilizing both the file browser or "drag and drop" functionality. Working with a number of items at the similar time is possible. It will possibly be a part of CDA recordsdata to one big AAC, ALAC, FLAC, WAV, M4A, M4B, MP3, OGG or WMA. All issues considered, Ready MP3 OGG to WAV Converter comes bundled with a number of straightforward features for serving to you perform audio conversions, and is appropriate for rookies and professionals alike. For those who're working with information already compressed right into a lossless format likeflac orape, you may simply decompress them towav without shedding any information for enhancing earlier than compressing once more to no matter format you want. is a service for changing recordsdata on-line from one kind to a different. We take care of your privacy and deal with your information. As a part of this, there is not any registration required on As we're offering our service in a browser, it does'nt matter whether or not you employ Windows, Apple OS X or Linux. Your conversion results will at all times be at the identical, very top quality and naturally, without watermarks. The first step is to pick the files to convert wav to ogg. Run WAV to OGG Convertor and use the Folder Explorer to browse to the files you wish to convert. Then select the file within the File Listing, drag it to the Drop Zone and drop it there. Optionally, the WAV to OGG Converter permits you to edit the audio tags of any chosen file in the Drop Zone.

1 note
·
View note
Text
Why Organizations need to be Careful with Open Source Software?
A detailed review of the open source software will be able to highlight all the issues, problem areas, but it is quite tough to highlight the IP issues.The term “open source software” is quite a familiar and popular term with organizations and individuals alike these days. The IT departments of any organization are well aware of the software and its benefits. The free and open source software developed by numerous s software developers ensures that the source code is freely distributed and has no limitations with respect to copyrights, in contrast to the proprietary software.
The open source software might seem to be quite beneficial and simple, but the lawsuit of the open source Linux Operating system that was in the news reminds every organization and individual that this software has the potential to make any user responsible for any unintentional breach of someone else’s rights with respect to Intellectual Property (IP). This case has taught many software users to be very cautious. Users should make sure they investigate, question and then take a decision on the use of the software taking into consideration its benefits, risks, and cost-effectiveness.
In order to avoid such sticky scenarios, companies can hire a privacy lawyer in Massachusetts or even an open source counsel. Companies must ensure that these professionals must be in touch with their IT team and other teams and must be involved in the entire process of getting and implementing open source software for the firm. This is necessary as it helps the lawyers to advise the firm and the teams on the software which is the best for the firm without being biased. They can provide the best advice post understanding the entire process of the software deal. A privacy lawyer in Massachusetts also helps in ensuring that the company is compliant with licenses of the software that will be used in their systems. An Open Source Review Board (OSRB) is held wherein such issues are discussed and finalized. Companies that are bigger will have representatives from each department along with a legal team- internal or external on their Board.

Proprietary software is being developed by one commercial software entity in contrast to open source software, where numerous software developers, as well as users, help in modifying and improving it. According to the open source license which promotes the open source software, whoever modifies the software and shares it, has to ensure even the slightest of modifications are shared at a minimum cost or no cost. The modified source code has to be made available to a third party in open source software.
The process relies on an unverifiable premise – the are chances of distributing a corrupted contribution. Although many developers might respect other individuals IP rights, it is possible that even one person can include somebody else’s corrupted contribution. This is quite tough to identify, irrespective of how closely the process is being scrutinized. This is why an open source lawyer in Massachusetts is a requirement. The lawyer will be in a better position to analyze and identify the potential risks along with the IT team, in the beginning, stages itself and the company can avoid itself from getting stuck in legal issues.
Open source software is promoted with a license that has a little risk involved- there is no warrant on the code integrity. Licenses of Open source software transfer the liability risk of the intellectual property from the developer to the user of the software, in contrast to other software licenses which offer to compensate the licensee if there are any suits pertaining to the infringement of IP rights of a third person. Due to such risks, corporate firms have made it a point to hire privacy lawyers in Massachusetts. Corporates have to be very cautious while using open source software. As per FOSS compliance, each software developer or even the user of an Open Source Software must comply with the copyright notices and make sure the license obligations are met by them. These days, this gets a little complicated as every single company or person wants to safeguard their intellectual property and may not want to share the information of a third party who could be part of their product.
Measures to be taken by Corporates for the use of Open Source Software:
Firstly, the company has to understand if the use of open-source software is required in their computer systems.
Secondly, the company has to review the license details of the software, with its information technology team and its open source counsel. This will help them to identify any potential liability. This is the point where every company needs to get its open source counsel partner up with the company’s IT team in order to understand the process.
Lastly, the firm must analyze the risks and benefits of the software and how the software will benefit the company in the best possible way.
A detailed review of the open source software will be able to highlight all the issues, problem areas, but it is quite tough to highlight the IP issues.
Open source software is quite beneficial to an organization- it is cost-effective. Any developer or user can modify, make improvements or get bugs fixed, without the need to await the release of the updated version of the software. An open source software does not rely on the creator of the software for any improvisation of resolution of issues. Irrespective of whether the entity is a success or a failure, the source code is freely shared and continues to exist for further improvisation.
Open source software is a lot cheaper than proprietary software, but the benefit of indemnification is a requirement. Companies have to be very cautious and analyze all the odds instead of just focusing on the low-cost aspect. A wise decision is one where the company analyzes the benefits, the risks as well as problems that come with the software, and also understands how the software would benefit the company. With the assistance of IT experts as well as the open source counsel, organizations will be able to avoid any sort of intellectual property liability.
1 note
·
View note
Text
Best Practices for PHP Security | LinuxSecurity.com
Learn How To Protect Against Linux Malware Explore ManageEngine Patch Manager Plus!

Best Practices for PHP Security
Brian Gomez
5 - 9 min read 05/09/2023


Now more than ever, people, developers, and businesses alike consider PHP a dying language and that it might have no place in the IT/Dev World. However, PHP is one of the most popular programming languages still in use today. It is used by millions of websites, roughly around 80% of all websites, including some of the biggest names on the internet. PHP still dominates server-side web development whilst still being flexible and adaptable to a developers needs.
While PHP is a very powerful language, it can also be quite insecure if not used properly. In this article, we will discuss eight best practices for PHP security that will help keep your website safe from hackers and malicious users. We will also talk about application pen testing and how to use it to find vulnerabilities in your code.
How Is PHP Used Today? Is It Still Relevant?
As many programming languages over the years share the same tendency in declining, PHP just happens to be the exact opposite. Being that PHP is widely used for a vast majority of websites out there today, it is only fair to say that PHP is on a continuous rise. Amongst being one of the easiest programming languages to learn and use, it is also considered one of the best server-side languages to use due to it having the functionality of embedded HTML. Moreover, the development of PHP over the recent years, on top of it being open source (AKA Free!), has made it a favorite for many developers and businesses
Linux Security Week - Latest Linux Security News
Subscribe to our weekly Linux Security Week newsletter to stay up-to-date on the latest, most significant Linux security news and information that impacts you.
How Does Application Pentesting Help Businesses?
Application penetration testing is pretty self-defined: you are essentially penetrating your applications/web applications. Simply put, it is the process of identifying vulnerabilities in software by simulating various attacks on the web application. This type of testing can be used to find flaws in the code that could allow attackers to gain access to sensitive data or take over the website. Regular web application pen testing will allow you to find lack of secure coding practices, misconfiguration vulnerabilities, such as XSS and HTTP Headers, broken authentication and access controls and information leakages and remediate these issues before a Cyber Criminal has the chance to exploit them.
8 Best Practices for PHP Security
1. Always use the latest version of PHP
Before anything, always make sure your PHP is UP TO DATE! New versions of PHP are released regularly with security fixes and improvements so by using the latest version, you’ll have the benefit of these fixes and improvements as well as any new features that might be helpful for your website. Look at the link attached for a list of the most recent, and old, releases: PHP: Releases.
2. Properly configure the PHP.ini file and other requisites
Believe it or not, most security flaws come from misconfiguration. There are a couple changes you can make to the PHP.ini file to make it more secure but first, let’s start with the following settings that need to be tailored to your specific system:
session.save_path
session.cookie_path (e.g. /var/www/mysite)
session.cookie_domain
After configuring those settings properly, there are a couple other settings you can edit to keep your PHP application secure. Let's take a look at the checklist below:
expose_php = Off
This restricts the disclosure of PHP version from being sent in HTTP Headers. When enabled, expose_php tells everyone that PHP is installed on that specific server or system, which includes the PHP version within the HTTP header, e.g (Powered by: PHP/8.1.2). You can do this for any system and works well if you are using nginx.
allow_url_include=Off
Setting this to off prevents remote code execution attacks.
display_errors = Off
This displays whether errors should be printed on the screen to everyone visiting the site. This should be disabled as a best security practice.
session.cookie_httponly = 1
Setting this to 1 disables access to cookies via Javascript APIs but use this with caution as you could break something
session.use_strict_mode = 1
Setting this to 1 prevents session fixation attacks
session.cookie_secure = 1
This requires cookies to strictly transmitted over HTTPS only
session.cookie_samesite = Strict
Setting this to strict prevents cross-origin attacks
session.use_trans_sid = 0
This is not needed so set it to zero
session.sid_length = 128
Here, we are setting the length of the session string which prevents brute force attacks
session.sid_bits_per_character = 6
This increases the randomness of the session string which also prevents brute force attack
file_uploads=off
Here, we are disabling file uploads. If anyone needs to upload files, you can set a limit on the size of the files by doing upload_max_filesize = 1M
3. Use up to date code dependencies, third party components, and update your web server!
In addition to using the latest version of PHP, you should also keep your code and web server up to date! This includes any third-party libraries or frameworks that you’re using. Outdated software is often the target of attacks because hackers know that it is more likely to have vulnerabilities that can be exploited. You want to make sure you only have the necessary libraries installed and that everything is up to date. If you use Apache Web Server, then here are a few common best practices:
Always Keep your Apache Version Updated.
Turn on Error Logging
Get an SSL certificate
Add a Firewall
Install mod_evasive.
Set HTTP Limits
Never Keep Unused Modules
One of our favorite practices is installing mod_evasive as that helps your server stay running in the event of an attack. Another one would be getting an SSL certificate. If you are using Apache web server, or any other for that matter, having an SSL certificate is important as it does an SSL handshake before it receives the HTTP request that contains the Host header. Ultimately, it provides more security for online communication.
4. Do not store passwords using reversible encryption
There are a few key reasons why reversible encryption is harmful. Firstly, it can easily be cracked and decrypted, making your data vulnerable to theft or exposure. Second, it can be used to spy on or track your activities, since the encryption and decryption process leaves a clear trail of activity. Finally, it can be used to enumerate all other user passwords also given there is a static key in use for encryption and decryption process.
Instead, you should hash the passwords with a strong hashing algorithm like bcrypt, AES two-way encryption with openssl, or even Argon2 which has won the Password Hashing Award. Outputs prepared using hashing algorithms are less vulnerable to attacks than encryption algorithms. This makes them more secure for storing passwords or other sensitive data due to the sheer computing power required to find clear-text (decryption) equivalents. Additionally, hashing algorithms are much faster than encryption algorithms, making them better suited for use in applications where speed is important. PHP already has bcrypt built in so you wouldn’t have to worry about downloading any external dependencies.
5. Don’t rely on cookies for security
Cookies are often used to store information about users, such as their login status, username, preferences or even sensitive information. However, cookies are not inherently secure and can be easily stolen by attackers. If you need to store sensitive data in a cookie, you should encrypt it first. Just like Password hashing, we are adding another layer of security. You can use tools such as halite powered by libsodium or if you’d like to be more technical, you can use something like openssl or possibly even AES 256 bit with CBC mode encryption.
6. Validate user input
All user input should be validated before it is processed by your PHP code. This includes data entered into form fields, URL parameters, and JSON payloads. PHP has filter_var() function to validate variables. We can set its second parameter to different values and use it to validate emails, URLs, integers, etc and this function returns false on failure or invalid input. A way you can implement the filter_var() function can be seen in the example below:
function is_valid_email($email = "")
{
return filter_var(trim($email), FILTER_VALIDATE_EMAIL);
}
The function above was created by myself. This function checks if an email is valid using filter_var().
By validating user input, you can help prevent Cross-Site Scripting (XSS) attacks and other types of malicious input.
7. Perform regular security audits
Regular security audits can help identify vulnerabilities in your website and fix them before they can be exploited by attackers. By auditing your code, you can also ensure that it is up to date and follows best practices for PHP security. Moreover, it helps you get faster response times, more reliable application performance, and it eliminates bottlenecks on top of future-proofing your web applications. Performing audits can scan for the following such as:
Cross Site Scripting Vulnerabilities (XSS)
Cross Site Request Forgery Vulnerabilities (CSRF)
SQL Injections
PHP Code Injection
Cookie Denial of Service Attacks
Timing Attacks
8. Use PHP Libraries
PHP does a good job of providing developers with some functionality, meaning that they provide us with functions that we can use to secure our applications better. You can use the following:
urlencode - allows coders to construct valid URLs safely. According to the PHP documentation, the function is useful for encoding a string that will be used in a URL’s query section.
<?php
echo ‘<a href=”mylink?user=’, urlencode($userID), ‘”>’;
?>
Use prepared SQL statements like below:

Conclusion
Following these best practices will help you secure your PHP applications and protect them from attack. Remember to always keep your software up to date, properly configure your web server and your PHP, and be sure to perform regular security audits to identify any vulnerabilities that may have slipped through the cracks. We hope you found this article useful and we hope you check out our other articles that may help in keeping your systems secure!
Prev
Next
Get the Latest News & Insights
Sign up to get the latest security news affecting Linux and open source delivered straight to your inbox
Linux Advisory Watch Linux Security Week
Related Articles
AWS Open Sources Security Tools

Fedora Workstation Aiming To Improve Encryption, Possibly Encrypted Disk By Default In The Future

Pentesters' Fave Kali Linux Turns 10 with Version 23.1


LinuxSecurity Poll
How often do you visit LinuxSecurity.com?
Multiple times per day
Daily
Once per week
Less than once per week

News
Cloud Security
Cryptography
Desktop Security
Firewall
Government
Hacks/Cracks
IoT Security
Network Security
Organizations/Events
Privacy
Security Projects
Security Trends
Security Vulnerabilities
Server Security
Vendors/Products
Advisories
ArchLinux
CentOS
Debian
Debian LTS
Fedora
Gentoo
Mageia
Oracle
openSUSE
Red Hat
RockyLinux
Scientific Linux
Slackware
SuSE
Ubuntu
HOWTOs
Harden My Filesystem
Learn Tips and Tricks
Secure My E-mail
Secure My Firewall
Secure My Network
Secure My Webserver
Strengthen My Privacy
Features
Is Linux A More Secure Option Than Windows For Businesses?
How Secure Is Linux?
How To Secure Against WordPress Vulnerabilities with Predictive Analysis Detection & Automated Remediation
Best Practices for PHP Security
Why Cloud Linux Is Beneficial for E-Commerce Stores
About Us
Advertise
Legal Notice
RSS Feeds
Contact Us
Terms of Service
Privacy Policy
Powered By

© 2023 Guardian Digital, Inc All Rights Reserved
News
Advisories
HOWTOs
Features
Newsletters
Polls
About
Security Dictionary
0 notes
Text
2018 Alternatives To Neat Desktop For Mac Software For Home Use
Platforms: Windows, Mac, Linux The first port of call for most people looking for a swift alternative to Outlook, Thunderbird has been around for a long time and continues to impress. With support for an unlimited number of email accounts, tons of plugins and lightning-quick functionality, its place on the email client throne is well deserved. QuickBooks Online, QuickBooks Desktop, Xero Accounting. You can eliminate a lot of duplicate entry by tying your receipt scanning software to your (or your accountant's) accounting software. Neat Receipts integrates with QuickBooks Online and QuickBooks Desktop.
2018 Alternatives To Neat Desktop For Mac Software For Home Use Computer
2018 Alternatives To Neat Desktop For Mac Software For Home Use Computers
2018 Alternatives To Neat Desktop For Mac Software For Home Use Windows 10
2018 Alternatives To Neat Desktop For Mac Software For Home Use Mac
Sometimes we need to access computers remotely from a different location. Like, for example, to access files residing in your workstation located at your workplace. Or to help your dad (who's probably not so good with computers) fix a simple issue. To do this, you need what is known as remote access tools, which let you 'remotely control' another computer, located in another part of the world. Remote access becomes all the more important if you are running an enterprise which is spread over different parts of the world.
There are many free remote access software tools in the market which help you connect to other computers remotely. In this blog, we list some of the best, so that you can pick and use the right one.
Best 5 Free Remote Access Software
1. Comodo Free Remote Access:
Comodo Remote Management brings along with it a lot of benefits that make it perfect for enterprise use. Network monitoring and trouble shooting become pretty easy with this tool. Also known as the remote desktop tool, it helps IT administrators, in particular, to remotely address network issues easily — without them having to leave their seats.
Benefits:
Extremely Lightweight — being extremely lightweight, it is not proving a burden on the network and therefore does not hinder its performance.
Faster Troubleshooting — down enterprise computers would be up within minutes as IT administrators would be able to fix it within minutes.
Remote Administration — efficient remote administration leads to improved network performance as well.
Easy Accessibility — centralized access to various files available within the network leads to easy administration.
2. TeamViewer:
Another free remote access tool which can be used. Easy to install and efficient, and with support for video and voice calls, this tools also allows for file transfers, supports wake-on-LAN (WOL) and other such high-end features. The computer you want to connect to can be Windows, Mac, or Linux computer amongst others.
3. Remote Utilities:
yet another free remote management tool worth being tried out. But suitable only for very small businesses as you can control only a total of 10 Pcs using this tool. Unfortunately, configuring remote utilities too can be confusing. This along with its support for very few computers are its drawbacks. Basically a product for home users.
4. AeroAdmin:
probably the easiest program to use for free remote access. Easy to install, extremely lightweight. Hardly any additional settings required as everything is quick and to the point. Aeroadmin can be used by enterprises and home users alike. The highlight is the fact that AeroAdmin is 100% free, either for personal and commercial use.
5. AnyDesk:
this can be run portably or installed like a regular program. Easy-to-use user interface, lightweight, ability to self-terminate inactive sessions, this tool contains enough features which make it suitable for enterprise network management. AnyDesk is compatible with all the machines.
Remember free remote access tools are sometimes more than enough for personal use as well as enterprise management. And also remember that you need remote management tools, especially if you are running an enterprise and need to manage networks. Therefore choose wisely, save money, and manage your networks efficiently via remote management.
Therefore choose wisely, save money, and manage your networks efficiently via remote management.
Related Resource
Download and update your HP (Hewlett Packard) laptop drivers automatically supporting HP laptop models like Pavilion, EliteBook, ProBook, TouchSmart series etc.). And update or install HP printer drivers, HP laserjet drivers, HP scannerdrivers etc.
File Name:hp.exe
Author:Rabby Studio
License:Shareware ($29.95)
File Size:1.49 Mb
Runs on:WinXP, WinVista, Win7 x32, Win2000
30 day SDK trial includes library, C/C++ programming samples, scannerdrivers for Linux. Integration into ARM-based devices with ARM Linux or Windows Mobile. Constant internet connection required. Ready-to-use hardware device in Device EDK included.
File Name:FingerCell_2_0_EDK_Trial.zip
Author:Neurotechnologija
License:Demo ($1069.00)
File Size:1.45 Mb
Runs on:Windows
Use the TWAIN 2 sample data source and application, to test your TWAIN project, or as templates to incorporate TWAIN into your graphic applications or Scannerdrivers. The samples are released as open source software and uses a Modified BSD. .
File Name:Twain_App_sample.source.zip
Author:twain
License:Freeware (Free)
File Size:143 Kb
Runs on:Windows; BSD; Linux
Using the Websio SharePoint Scanner Plug-in for MS SharePoint, paper documents can be scanned at a document scanner and sent to specific locations in SharePoint for storage and ongoing document lifecycle management.
Toshiba challenge response code generator download. The BIOS should respond with “Verify Password= “.5. The BIOS should respond with “New Password = “.4. Press Enter again. Press the spacebar and press Enter. Press Enter again.
File Name:SharePoint Scanner Plug-in
Author:Websio.com
License:Shareware ($350.00)
File Size:613 Kb
Runs on:Windows
Ghost recon desert siege download. Scan documents and photos quickly and easily. Store images as PNG, JPG, or PDF files. Easily controls your TWAIN scanner, allowing you to scan and name multi-page documents. Faster than many other scanning applications.
File Name:leafboysetup.exe
Author:The Cogit Network
License:Shareware ($19.99)
File Size:11.62 Mb
Runs on:WinXP, WinVista, WinVista x64, Win7 x32, Win7 x64
Chromebook download android apps. Manage your Windows drivers with ease with Driver Check software. Driver Check can deep scan your hardware devices, detect and update the outdated drivers if available, completely backup them and restore them if necessarily.
File Name:setup.exe
Author:Repair-and-Secure
License:Shareware ($34.95)
File Size:3 Mb
Runs on:Win95, Win98, WinME, WinXP, Windows2000, Windows2003, Windows Vista, Windo
Art-Copy Enterprise 8.3.2 is considered as a professional and useful scanning tool. With Art-Copy Enterprise you can use simple one button style front end, with scan-to buttons that support scanning directly to printers, faxes, files, or even. .
File Name:Art-Copy Enterprise
Author:Jetsoft
License:Trial ($129.95)
File Size:17.5 Mb
Runs on:Windows Me, Windows XP, Windows 2000, Windows
Scan Redirector RDP Edition is easy to use software, which allows scanning from your locally attached scanner in a Remote Desktop session.Both TWAIN and WIA scanners are supported. A great solution for VDI and Terminal Services!
File Name:scan-redirector-rdp.zip
Author:Incentives Pro
License:Shareware ($49.00)
File Size:3.15 Mb
Runs on:Win2000, WinXP, Win7 x32, Win7 x64, Windows 8, Windows 10, WinServer, WinOther, Windows2000, Windows2003, Windows Server 2000, Windows Server 2003, Windows Server 2008, Windows Server 2008r2, Windows Server 2012, Windows Tablet PC Edition 2005, Windows Media Center Edition 2005, WinVista, Windows Vista, WinVista x64
Collate is a revolutionary software product that was created to enable a user to edit, create, and modify existing multiple page PDF and Tiff files. Collate allows a user to create multiple page PDF file using image files such as a JPG, TIF, BMP, or. .
File Name:Collate
Author:Jetsoft
License:Shareware ($99.00)
File Size:10.06 Mb
Runs on:Windows Vista, XP, 2000, 98, Me, NT
Art-Copy Business 8.3.2 is a professional document management software which gives you an easy to use scanning software alternative. With Art-Copy Business you can use our simple one button style front end, with scan-to buttons that support scanning. .
File Name:Art-Copy Business
Author:Jetsoft
License:Trial ($69.95)
File Size:14.7 Mb
Runs on:Windows Vista, Windows Me, Windows XP, Window
Jetsoft P2S Converter is the tool that you can convert a PowerPoint file to a Flash Jetsoft P2S Converter is the tool that you can convert a PowerPoint file to a Flash file.
File Name:Jetsoft P2S Converter
Author:Jetsoft
License:Shareware ($98.00)
File Size:4.73 Mb
Runs on:Windows XP, 2000, 98, NT
CloudScan is a new simple way to scan your documents, pictures or photos and save them to either PDF or TIFF file. It can be successfully used on one computer: simplest friendly interface allows getting result in seconds. If you have more than one PC. .
File Name:sharedscanner.zip
Author:ScanWorks Company Limited
License:Freeware (Free)
File Size:2.02 Mb
Runs on:Mac OS X, Win2000, Win7 x32, Win7 x64, WinServer, WinVista, WinVista x64, WinXP
Neat Smart Organization System. NOTE: This version will be formally retired in 2020. You can continue to use this app, but we have an amazing New Neat Experience you should check out!
The Best Remote Access Software of 2018. Low-priced alternative remote-access. I use Microsoft Remote Desktop from my Mac laptop when I want to run a program on a Windows desktop in another.
Apr 10, 2017 TeamViewer is multiplatform remote desktop software you can add to Windows, Android, Mac, Linux, iOS, Windows phones and Blackberry platforms. That means you can remotely access a Windows desktop from various hardware devices, and the.
2018 Alternatives To Neat Desktop For Mac Software For Home Use Computer
Related:
2018 Alternatives To Neat Desktop For Mac Software For Home Use Computers
Neat Scanner Drivers - Neat Scanner Compatibility - Neat Scanner Sdk - Neat Adf Scanner - Neat Scanner Driver
2018 Alternatives To Neat Desktop For Mac Software For Home Use Windows 10
2018 Alternatives To Neat Desktop For Mac Software For Home Use Mac
2018 Alternatives To Neat Desktop For Mac Software For Home Use Free

0 notes
Text
Anydesk App For Desktop

AnyDesk Connect to a computer remotely, be it from the other end of the office or halfway around the world. AnyDesk ensures secure and reliable remote desktop connections for IT professionals and on-the-go individuals alike. AnyDesk is a desktop application that lets one have remote access of a computer system, in an authenticated manner. It is a German technology now being used popularly even in India and lets co-workers or professionals connect better. AnyDesk provides independent, remote access to computers and other devices while running the host application. Discover AnyDesk - The Linux Remote Desktop App. AnyDesk provides powerful Linux-based connectivity for smooth and seamless remote access to any computer. Whether as an individual, or as a professional organization offering remote support to customers, AnyDesk is made for easy operation and solid remote connectivity.
For those of you who don’t know what AnyDesk is, it is a remote desktop application which is extremely popular for its high speed its power to connect to any device anywhere. Many users around the world use AnyDesk as a remote access software to manage different tasks on their target devices easily. Another point about AnyDesk is that it uses encrypted protocols to transfer data between the two devices. This ensures the security and privacy of your data transferred through this app. But what users might find a little difficult is AnyDesk download and working with it. In this article, I will show you how you can easily use AnyDesk to connect to a remote device and share files through it.
How to use AnyDesk
As I mentioned earlier, AnyDesk is among the applications that can be used to remotely connect to a desktop computer or a mobile device. you can use AnyDesk to connect to a computer and do tasks such as repairing or other job related tasks when you are away. But what you certainly need to know is that you will need to get the permission from the target device in order to be able to connect to it. In fact, connecting to a device remotely and without the owner’s permission would be a kind of hacking which is illegal in many jurisdictions.
The reason why you would need to use AnyDesk is to access devices which belong to you or you have been asked to repair them remotely. This includes repairing and fixing a device remotely when physical access to the target person is not possible. Now before we start AnyDesk tutorial, you will need to download AnyDesk and install it. You can download AnyDesk from below link.
Once you have installed AnyDesk on the target device as well as you own device, you can start using it for a remote connection. Here are all the steps you will need to take in order to use AnyDesk.
How to work with AnyDesk remote desktop app
In order to use AnyDesk to connect to a remote computer, you will need to take these steps:
After you have installed AnyDesk on your computer, you will need to launch the app. A number of options will appear for you. In the section named “This Desk“, you can see your own ID. You will need to send this ID to the target computer as it is required for establishing the connection. Right under “This Desk”, you can see another field named “Remote Desk“. You will need to ask the target device’s ID and enter it in the blank box. After you are done with ID sharing part, just click on “Connect” to create the connection.
When you click on “Connect”, a window like the one in the photo will appear for your target person. The target person will need to check all the boxes to allow full access and then click on “Accept” to allow you to use AnyDesk to connect to the target device. Please note that if the target person clicks on “Dismiss“, the connection will be lost and you won’t be able to connect to the computer.
From this step on, you are able to use AnyDesk to perform tasks on the target device. Also, you can use the chat box on the right side of the window to talk to the target person. You can for example use this chat to notify them of the existing issues or ask them to do a certain command for you. At the end, you can click on “Disconnect” to end or stop the process.
By taking these simple steps, you can easily use AnyDesk to establish a remote connection with a computer. This was a simple AnyDesk tutorial for you and I hope you found it useful. Please don’t hesitate to ask your questions in the comments section.
The Anydesk App For Remote Desktop On Linux
A remote access tool at its best
Have you ever gotten extremely worried after discovering that your file (which you’d worked so hard on) is still on your desktop at home and it’s your turn to present next in class? You feel helpless in these kinds of situations. Fortunately, there are remote access utilities to handle these problems.
If you would like to try similar apps either for your own personal use without shelling out some money, then AnyDesk is the perfect program for you! It is a free, lightweight remote access application that can help you access various files and documents on any device across multiple locations. Ready to start working anytime, anywhere?
Quick and comfy
The app claims to be the world’s fastest yet comfortable remote desktop application.
AnyDesk's key features include online collaboration, file sharing, access control, and personalized user interface. You can start using the program even without installing it. All you have to do is download and launch its super lightweight 1.1MB program file. Accessing your files anywhere is made easier and more secure since you don’t need to entrust your data to a cloud service.
Portable Work Desk

The app works with ID numbers, making establishing connections with your family, friends, colleagues, and clients simpler and quicker. You can customize your alias using random numbers after downloading the app on two or more of your devices. https://blogstudio50.tumblr.com/post/655346554531643392/magnet-shop-near-me. Enter your preferred alias (e.g. alias98@ad) on the device you want as the host that will remotely control the other ones, and press connect. Once you have accepted the remote connection request on the other devices, you’re be all set. Enable unattended access by including passwords in the settings. You can also change permission settings from time to time and let remote users view your monitor, hear sound from your computer, control keyboard and mouse functions, and access clipboard. You can also choose to see remote users’ own cursors for better communication. You can even turn your whole screen setup into a whiteboard where you can doodle, type, or draw for better presentations.
Here is a summary of other things you can do with the app:
- Syncing clipboard contents across the host and remote user/s’ computers
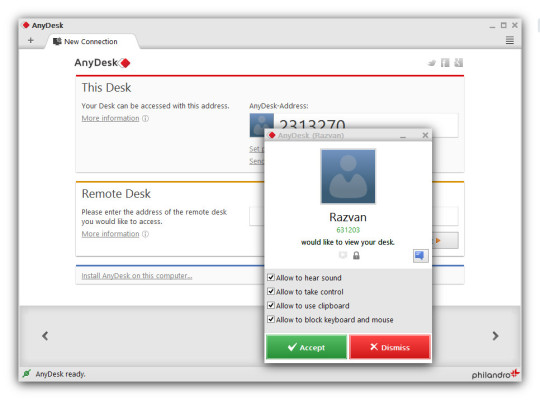
- Take a screen recording or screenshot while actively using the app
- Alter connection to create the best possible balance between video quality and speed
- Access easily various settings from the menu bar
- Transfer files by copying it to the clipboard and pasting it to the remote computer
- Restart remote users’ computer while the app is active in portable mode
- Save connection shortcuts to your desktop for quick access
Upgrade Your Desk
Although the app is available for free download, you can upgrade its services and features by purchasing its paid versions (which are all billed annually). You can choose from Lite, Professional, or Teams bundles. The Lite version is preferably for one user and personal purposes. The Professional version, the most popular bundle with app users, is best for multiple devices given its unlimited endpoints.
Where can you run this program?
The app works perfectly with Windows XP/7/8/10, Mac OS, Linux, FreeBSD, and Raspberry Pi. It is also available for Android and iOS mobile phones.
Visual studio code live. Join the Visual Studio Code team and our community in our livestream series! Every month, we host a release party to highlight what's new in the latest version of VS Code. We also host other live events highlighting our community members and cool projects they've made. This provides you and your team/class with a one-click installation, in order to begin pair programming, performing remote code reviews, driving interactive lectures, and more, without needing to leave Visual Studio Code. Once you log into your GitHub account, you'll see the Live Share icon in the Activity Bar. Starting a Live Share session. Visual Studio Code is a code editor redefined and optimized for building and debugging modern web and cloud applications. Visual Studio Code is free and available on your favorite platform. Visual Studio Live Share lets you collaboratively edit and debug any codebase with others in real time—each person working in their own familiar, personalized environment.
Is there a better alternative?

AnyDesk is the best option for lightweight remote access because of its incredible speed in terms of graphical performance metrics and responsiveness. Despite its small file size, the app offers key features such as chatbox for client use, file transfer, and connection to multiple hosts. Unfortunately, its limitations per compatibility put the app at a disadvantage versus its most popular competition, TeamViewer. This latter app does not only deliver fast performance but also supports a huge number of OS. Its security features are also unparalleled which includes two-factor authentication, whitelist, and blacklist of allowed/restricted users, and screen lock after minutes of inactivity. The only downside of this app is the notable difference of rates when compared to those of AnyDesk.
Our take
The app’s key features are all indispensable and can be used for both personal and business purposes. It may take a while for you to master its unusual interface but you'll love it once you customize it according to your personal tastes. Its premium bundles undoubtedly serve all the best features from the app’s largest competitors but at a more reasonable price.
Should you download it?

Yes, but only if you’re intending to use it on your desktops or laptops. The app is not as appealing for mobile devices given its poor performance there. You can download the app’s free version first to test out the program, explore its features, master its interface, and discover if it really suits your personal and/or business’s goals.
Highs

Small download size
Freemium features
Personalized interface
Allows chat communication
Lows
Anydesk Desktop Download
Poor mobile service
Hard to master
Interesting features only available in paid version
Free Download Anydesk App For Desktop
AnyDeskfor Windows
6.2.3

0 notes
Text
Dropbox Google Drive Onedrive
At present, Dropbox, Google Drive and OneDrive are becoming the most popular cloud storage for personal and business users alike. However, how do you choose which of them is the most suitable for your storage needs? If you are confused about it, this post is what you need. In this post, we will show you the detailed comparisons of Dropbox VS Google Drive VS OneDrive from different aspects. To make clear which one is the most suitable for you, we try comparing these three cloud storage providers from the following aspects:
Google Drive Similar to Dropbox, Google Drive supports optional two-step verification and it encrypts your data both in transit and at rest. Google Drive extract metadata for indexing files as well. In addition, Google Drive uses laser grids and biometric scanners to enhance security.
Of course, Google Drive, OneDrive, Dropbox, Box and Amazon aren't your only cloud storage options. Another is SugarSync, a Dropbox-like alternative with apps for every mobile platform.
The flaw related to Google Drive's 'manage versions' feature, which lets you upload a new version of an already-uploaded file. How secure is Dropbox? The second platform on our list enjoyed popularity among consumers as an easy-to-use file storage suite, although it has shifted towards the enterprise market in recent years.
In recent years we have seen an explosion in the popularity of cloud storage services such as Google Drive, Microsoft OneDrive, Dropbox, and iCloud.These providers offer hundreds of gigabytes.
Dropbox is integrated with Microsoft 365, so users of the Microsoft suite can benefit from the convenience of syncing their Dropbox files with programs they already use. This lets users edit their Dropbox content with Microsoft tools. The next way in which Dropbox and OneDrive are the same is mobile accessibility.
1. Pricing and Storage
When it comes to cloud storage, the first thing that you care about might be the pricing and storage. In order to make it clearer, we make a chart to compare.
As we can see from the above chart, each provider has its own plans. Obviously, Google Drive does best in pricing and storage. Because it has more flexible options to choose. Additionally, its free storage is much more than others. On the contrary, Dropbox has only two choices and less free storage space. Onedrive is much better than Dropbox.
2. Security and Encryption
There is no doubt that security is one of the crucial factors for cloud storage. All the three cloud storage providers are trying their best to protect our privacy. More details are as follows.
Dropbox
Firstly, Dropbox features a two-step verification to prevent anyone from accessing your files. What’s more, Dropbox protects your files in transit with the 128-bit AES encryption while at rest with the 256-bit AES encryption, which can ensure the security of your files. However, Dropbox pulls metadata to speed up file retrieval, which is a security concern.
Google Drive
Similar to Dropbox, Google Drive supports optional two-step verification and it encrypts your data both in transit and at rest. Google Drive extract metadata for indexing files as well. In addition, Google Drive uses laser grids and biometric scanners to enhance security. The worst aspect of Google Drive is the privacy issues. Landing page design company. To remove illegal content and gather information about you, the Google can scan your cloud files.
Mount Dropbox As Network Drive
OneDrive
OneDrive also encrypts your data in transit but it does not offer any file encryption at rest unless you have a Business Subscription. This will leave your files exposed and it might be a big issue for OneDrive.
In conclusion, Dropbox and Google Drive do well in term of security and encryption. OneDrive is worse due to the lack of at-rest encryption and security for individuals.
3. File Synchronization
Another key feature of cloud storage providers is file synchronization. When we make some changes on a cloud file, it will be updated on all the devices connected to your storage account.
Dropbox
The greatest difference of Dropbox sync is block-level file transferring. That means when you make changes on a file online, only the changes are synced online while the rest of data remains as it is, which speeds up the rate of sync. What’s more, Unlike the other two platforms, Dropbox supports the Linux system.
Google Drive
Google Drive doesn’t use block-level file copying so when the file is edited the speed of sync is much slower. But the speed of full-file transferring is much faster because it is supported by a global server network. And we can also create a Google drive-linked folder like Dropbox to access the cloud files conveniently.
OneDrive
OneDrive has block-level sync for Microsoft file types like Word, Excel and PowerPoint while it is not for other file types. So, the speed of sync depends on the file types. Additionally, since OneDrive is connected with Microsoft Office, sharing Microsoft files is much easier. You can also set the speed of sync by yourself.
In a word, Dropbox might be a better choice for file synchronization because it is so fast to update files. In terms of uploading files, Google Drive stands out. As for OneDrive, it is mediocre relatively on file sync.
4. File Sharing
File sharing is also an important factor of cloud storage provider. When it comes to the methods of sharing files, there aren’t many differences among them. You can share your files or folders by creating a shareable link or emailing a particular person on these three cloud storage providers. In addition, you can also permit the shared files to be either viewed-only or edited before you share.
Dropbox
Firstly, Dropbox Professional and Business customers can set passwords and expiration dates for the shared link, which can ensure the security and privacy of the shared files. Besides, you can invite others to upload files to your Dropbox, even if they don’t have an account. You can also review shared files and disable shares on the Dropbox sharing page.
Google Drive
My Account Boss's Dropbox Google Drive Onedrive

Compare Dropbox Onedrive Google Drive
There is another option that allows the users to add some notes to the files or folders on Google Drive. The entire folders can be shared on Google Drive as well. However, the most troubling issue for Google Drive is that there are no options for passwords, expiry dates or download limits. Https://pay.weixin.qq.com/index.php/public/wechatpay_en.
OneDrive
Box Dropbox Onedrive Google Drive
OneDrive has options for passwords, expiry dates and download limits of the shared files while it is free. You can also review shared files on OneDrive sharing page. What’s more, you can audit the activities on the shared files.
On a whole, Onedrive might be the most useful file sharing platform among them. Google Drive is worst for a reason that there are no options for links passwords, expiry dates or download limits.
Conclusion:
All in all, these three cloud providers are outstanding on the whole and each of them has its own strengths and weaknesses. Besides, there are also other useful cloud storage providers and you can choose the most suitable one for your needs. The above are only reference and everyone has his own views. Besides the contents mentioned above, if you have more thoughts on cloud storage, share with us anytime!
Related Articles:

0 notes
Text
Download Python Tools For Visual Studio Mac

-->
Python Tools For Visual Studio Mac
Download Python Tools For Visual Studio Mac Download
Download Python Tools For Visual Studio Mac Install
Python is a popular programming language that is reliable, flexible, easy to learn, free to use on all operating systems, and supported by both a strong developer community and many free libraries. Python supports all manners of development, including web applications, web services, desktop apps, scripting, and scientific computing, and is used by many universities, scientists, casual developers, and professional developers alike. You can learn more about the language on python.org and Python for Beginners.
Python support is presently available only on Visual Studio for Windows; on Mac and Linux, Python support is available through Visual Studio Code. Download and run the latest Visual Studio installer for Windows (Python support is present in release 15.2 and later). Nov 11, 2020 5) Visual Studio Code. Visual Studio Code (VS Code) is an open-source environment developed by Microsoft. It is one of the best Python IDE for Windows that can be used for Python development. Visual Studio Code is based on Electron which is a framework to deploy Node JS applications for the computer running on the Blink browser engine. Macos 10.14 macos 10.15 macos 10.13 xamarin editor debugger project solution xaml fixed in: visual studio 2019 for mac version 8.0 performance crash android ios visual studio ide Setup fixed in: visual studio 2019 for mac version 8.1 fixed in: visual studio 2019 for mac version 8.3 fixed in: visual studio 2019 for mac version 8.2 macos 10.16. Oct 08, 2018 Python Tools for Visual Studio Mac migrated from uservoice Python uservoice votes 230 uservoice supporters 230 visual studio for mac Feedback Bot reported Oct 08, 2018 at 07:37 PM.
Visual Studio is a powerful Python IDE on Windows. Visual Studio provides open-source support for the Python language through the Python Development and Data Science workloads (Visual Studio 2017 and later) and the free Python Tools for Visual Studio extension (Visual Studio 2015 and earlier).
Python is not presently supported in Visual Studio for Mac, but is available on Mac and Linux through Visual Studio Code (see questions and answers).
To get started:
Follow the installation instructions to set up the Python workload.
Familiarize yourself with the Python capabilities of Visual Studio through the sections in this article.
Go through one or more of the Quickstarts to create a project. If you're unsure, start with Create a web app with Flask.
Go through one or more of the Quickstarts to create a project. If you're unsure, start with Quickstart: Open and run Python code in a folder or Create a web app with Flask.
Follow the Work with Python in Visual Studio tutorial for a full end-to-end experience.
Note
Visual Studio supports Python version 2.7, as well as version 3.5 through 3.7. While it is possible to use Visual Studio to edit code written in other versions of Python, those versions are not officially supported and features such as IntelliSense and debugging might not work. Python version 3.8 support is still under development, specific details about support can be seen in this tracking issue on GitHub.
Support for multiple interpreters
Visual Studio's Python Environments window (shown below in a wide, expanded view) gives you a single place to manage all of your global Python environments, conda environments, and virtual environments. Visual Studio automatically detects installations of Python in standard locations, and allows you to configure custom installations. With each environment, you can easily manage packages, open an interactive window for that environment, and access environment folders.
Use the Open interactive window command to run Python interactively within the context of Visual Studio. Use the Open in PowerShell command to open a separate command window in the folder of the selected environment. From that command window you can run any python script.
For more information:
Rich editing, IntelliSense, and code comprehension
Visual Studio provides a first-class Python editor, including syntax coloring, auto-complete across all your code and libraries, code formatting, signature help, refactoring, linting, and type hints. Visual Studio also provides unique features like class view, Go to Definition, Find All References, and code snippets. Direct integration with the Interactive window helps you quickly develop Python code that's already saved in a file.
For more information:
Docs: Edit Python code
Docs: Format code
Docs: Refactor code
Docs: Use a linter
General Visual Studio feature docs: Features of the code editor
Interactive window
For every Python environment known to Visual Studio, you can easily open the same interactive (REPL) environment for a Python interpreter directly within Visual Studio, rather than using a separate command prompt. You can easily switch between environments as well. (To open a separate command prompt, select your desired environment in the Python Environments window, then select the Open in PowerShell command as explained earlier under Support for multiple interpreters.)
Visual Studio also provides tight integration between the Python code editor and the Interactive window. The Ctrl+Enter keyboard shortcut conveniently sends the current line of code (or code block) in the editor to the Interactive window, then moves to the next line (or block). Ctrl+Enter lets you easily step through code without having to run the debugger. You can also send selected code to the Interactive window with the same keystroke, and easily paste code from the Interactive window into the editor. Together, these capabilities allow you to work out details for a segment of code in the Interactive window and easily save the results in a file in the editor.
Visual Studio also supports IPython/Jupyter in the REPL, including inline plots, .NET, and Windows Presentation Foundation (WPF).
For more information:
Project system, and project and item templates
Note
Visual Studio 2019 supports opening a folder containing Python code and running that code without creating Visual Studio project and solution files. For more information, see Quickstart: Open and run Python code in a folder. There are, however, benefits to using a project file, as explained in this section. Microsoft wireless multimedia keyboard 1.1 driver windows 10.
Visual Studio helps you manage the complexity of a project as it grows over time. A Visual Studio project is much more than a folder structure: it includes an understanding of how different files are used and how they relate to each other. Visual Studio helps you distinguish app code, test code, web pages, JavaScript, build scripts, and so on, which then enable file-appropriate features. A Visual Studio solution, moreover, helps you manage multiple related projects, such as a Python project and a C++ extension project.
Project and item templates automate the process of setting up different types of projects and files, saving you valuable time and relieving you from managing intricate and error-prone details. Visual Studio provides templates for web, Azure, data science, console, and other types of projects, along with templates for files like Python classes, unit tests, Azure web configuration, HTML, and even Django apps.
For more information:
Docs: Manage Python projects
Docs: Item templates reference
Docs: Python project templates
Docs: Work with C++ and Python
General Visual Studio feature docs: Project and item templates
General Visual Studio feature docs: Solutions and projects in Visual Studio
Full-featured debugging
One of Visual Studio's strengths is its powerful debugger. For Python in particular, Visual Studio includes Python/C++ mixed-mode debugging, remote debugging on Linux, debugging within the Interactive window, and debugging Python unit tests.
In Visual Studio 2019, you can run and debug code without having a Visual Studio project file. See Quickstart: Open and run Python code in a folder for an example.
For more information:
Docs: Debug Python
Docs: Python/C++ mixed-mode debugging
Docs: Remote debugging on Linux
General Visual Studio feature docs: Feature tour of the Visual Studio Debugger
Profiling tools with comprehensive reporting
Profiling explores how time is being spent within your application. Visual Studio supports profiling with CPython-based interpreters and includes the ability to compare performance between different profiling runs.
For more information:
Docs: Python profiling tools
General Visual Studio feature docs: Profiling Feature Tour. (Not all Visual Studio profiling features are available for Python).
Unit testing tools

Discover, run, and manage tests in Visual Studio Test Explorer, and easily debug unit tests.
For more information:
Docs: Unit testing tools for Python
General Visual Studio feature docs: Unit test your code.
Azure SDK for Python

The Azure libraries for Python simplify consuming Azure services from Windows, Mac OS X, and Linux apps. You can use them to create and manage Azure resources, as well as to connect to Azure services.

For more information, see Azure SDK for Python and Azure libraries for Python.
Questions and answers
Q. Is Python support available with Visual Studio for Mac?
A. Not at this time, but you can up vote the request on Developer Community. The Visual Studio for Mac documentation identifies the current types of development that it does support. In the meantime, Visual Studio Code on Windows, Mac, and Linux works well with Python through available extensions.
Q. What can I use to build UI with Python?
A. The main offering in this area is the Qt Project, with bindings for Python known as PySide (the official binding) (also see PySide downloads) and PyQt. At present, Python support in Visual Studio does not include any specific tools for UI development.
Q. Can a Python project produce a stand-alone executable?
A. Python is generally an interpreted language, with which code is run on demand in a suitable Python-capable environment such as Visual Studio and web servers. Visual Studio itself does not at present provide the means to create a stand-alone executable, which essentially means a program with an embedded Python interpreter. However, the Python community supplied different means to create executables as described on StackOverflow. CPython also supports being embedded within a native application, as described on the blog post, Using CPython's embeddable zip file.
Feature support
Python features can be installed in the following editions of Visual Studio as described in the installation guide:
Visual Studio 2017 (all editions)
Visual Studio 2015 (all editions)
Visual Studio 2013 Community Edition
Visual Studio 2013 Express for Web, Update 2 or higher
Visual Studio 2013 Express for Desktop, Update 2 or higher
Visual Studio 2013 (Pro edition or higher)
Visual Studio 2012 (Pro edition or higher)
Visual Studio 2010 SP1 (Pro edition or higher; .NET 4.5 required)
Visual Studio 2015 and earlier are available at visualstudio.microsoft.com/vs/older-downloads/.
Important
Python Tools For Visual Studio Mac
Features are fully supported and maintained for only the latest version of Visual Studio. Features are available in older versions but are not actively maintained.
Python support2017+20152013 Comm2013 Desktop2013 Web2013 Pro+2012 Pro+2010 SP1 Pro+Manage multiple interpreters✔✔✔✔✔✔✔✔Auto-detect popular interpreters✔✔✔✔✔✔✔✔Add custom interpreters✔✔✔✔✔✔✔✔Virtual Environments✔✔✔✔✔✔✔✔Pip/Easy Install✔✔✔✔✔✔✔✔
Project system2017+20152013 Comm2013 Desktop2013 Web2013 Pro+2012 Pro+2010 SP1 Pro+New project from existing code✔✔✔✔✔✔✔✔Show all files✔✔✔✔✔✔✔✔Source control✔✔✔✔✔✔✔✔Git integration✔✔✔✔✔✔✔1✗
Editing2017+20152013 Comm2013 Desktop2013 Web2013 Pro+2012 Pro+2010 SP1 Pro+Syntax highlighting✔✔✔✔✔✔✔✔Auto-complete✔✔✔✔✔✔✔✔Signature help✔✔✔✔✔✔✔✔Quick info✔✔✔✔✔✔✔✔Object browser/class view✔✔✔✔✔✔✔✔Navigation bar✔✔✔✔✔✔✔✔Go to Definition✔✔✔✔✔✔✔✔Navigate to✔✔✔✔✔✔✔✔Find All References✔✔✔✔✔✔✔✔Auto indentation✔✔✔✔✔✔✔✔Code formatting✔✔✔✔✔✔✔✔Refactor - rename✔✔✔✔✔✔✔✔Refactor - extract method✔✔✔✔✔✔✔✔Refactor - add/remove import✔✔✔✔✔✔✔✔PyLint✔✔✔✔✔✔✔✔
Interactive window2017+20152013 Comm2013 Desktop2013 Web2013 Pro+2012 Pro+2010 SP1 Pro+Interactive window✔✔✔✔✔✔✔✔IPython with inline graphs✔✔✔✔✔✔✔✔
Desktop2017+20152013 Comm2013 Desktop2013 Web2013 Pro+2012 Pro+2010 SP1 Pro+Console/Windows application✔✔✔✔✔✔✔✔IronPython WPF (with XAML designer)✔✔✔✔✔✔✔✔IronPython Windows Forms✔✔✔✔✔✔✔✔
Web2017+20152013 Comm2013 Desktop2013 Web2013 Pro+2012 Pro+2010 SP1 Pro+Django web project✔✔✔✗✔✔✔✔Bottle web project✔✔✔✗✔✔✔✔Flask web project✔✔✔✗✔✔✔✔Generic web project✔✔✔✗✔✔✔✔
Azure2017+20152013 Comm2013 Desktop2013 Web2013 Pro+2012 Pro+2010 SP1 Pro+Deploy to web site✔✔✔✗✔✔✔✔2Deploy to web role✔✔✔✗✔4✔4✔3✗Deploy to worker role???✗✔4✔4✔3✗Run in Azure emulator???✗✔4✔4✔3✗Remote debugging✔✔✔✗✔6✔8✔8✗Attach Server Explorer✔✔✔✗✔7✔7✗✗
Django templates2017+20152013 Comm2013 Desktop2013 Web2013 Pro+2012 Pro+2010 SP1 Pro+Debugging✔✔✔✗✔✔✔✔Auto-complete✔✔✔✗✔5✔5✔✔Auto-complete for CSS and JavaScript✔✔✔✗✔5✔5✗✗
Debugging2017+20152013 Comm2013 Desktop2013 Web2013 Pro+2012 Pro+2010 SP1 Pro+Debugging✔✔✔✔✔✔✔✔Debugging without a project✔✔✔✔✔✔✔✔Debugging - attach to editing✔✔✔✔✗✔✔✔Mixed-mode debugging✔✔✔✔✔✔✔✗Remote debugging (Windows, Mac OS X, Linux)✔✔✔✔✗✔✔✔Debug Interactive window✔✔✔✔✔✔✔✔

Profiling2017+20152013 Comm2013 Desktop2013 Web2013 Pro+2012 Pro+2010 SP1 Pro+Profiling✔✔✔✗✗✔✔✔
Download Python Tools For Visual Studio Mac Download
Download Python Tools For Visual Studio Mac Install
Test2017+20152013 Comm2013 Desktop2013 Web2013 Pro+2012 Pro+2010 SP1 Pro+Test explorer✔✔✔✔✔✔✔✗Run test✔✔✔✔✔✔✔✗Debug test✔✔✔✔✔✔✔✗
Git support for Visual Studio 2012 is available in the Visual Studio Tools for Git extension, available on the Visual Studio Marketplace.
Deployment to Azure Web Site requires Azure SDK for .NET 2.1 - Visual Studio 2010 SP1. Later versions don't support Visual Studio 2010.
Support for Azure Web Role and Worker Role requires Azure SDK for .NET 2.3 - VS 2012 or later.
Support for Azure Web Role and Worker Role requires Azure SDK for .NET 2.3 - VS 2013 or later.
Django template editor in Visual Studio 2013 has some known issues that are resolved by installing Update 2.
Requires Windows 8 or later. Visual Studio 2013 Express for Web doesn't have the Attach to Process dialog, but Azure Web Site remote debugging is still possible using the Attach Debugger (Python) command in Server Explorer. Remote debugging requires Azure SDK for .NET 2.3 - Visual Studio 2013 or later.
Requires Windows 8 or later. Attach Debugger (Python) command in Server Explorer requires Azure SDK for .NET 2.3 - Visual Studio 2013 or later.
Requires Windows 8 or later.

0 notes
Text
US Blockchain Banking Race between Citibank, Goldman Sachs and JP Morgan
US Blockchain Banking Race between Citibank, Goldman Sachs and JP Morgan
(No Ratings Yet) Loading...
– Citibank seeks to improve its international payment and trade finance system with blockchain applications and it is focused on internal development of Citicoin. This will reduce forex risk and serve underbanked markets.
– Goldman Sachs wants to introduce instant settlement of capital market transaction that can reduce billions of collateral and risk involved. It is teaming up with Circle for its SETLcoin and create interoperability capability.
– JPMorgan wants to protect its critical payment advantage even after its failed Web Cash application. It is teaming up with IBM, Linux and former executive Blythe to gain an advantage over its rivals.
Introduction
In my previous articles, I have introduced blockchain and also their business imperative that drove banks to overcome their earlier disdain for Bitcoin and to embrace Bitcoin’s underlying technology blockchain. Blockchain is a distributed ledger system that has strong disruptive potential for many businesses. While they are 20 years from widespread acceptance, banks are at the forefront of experimenting blockchain.
In this article, we would be looking at how leading banks in the United States are approaching the opportunity of blockchain. We will be looking at
Citibank
Goldman Sachs
JP Morgan
Each of these leading banks have their own approach to blockchain which we would study in detail.
Citibank
Citibank focus most of its blockchain development efforts in house. Ken Moore is the person in charge of Citibank’s blockchain effort as the head of Citi Innovation Labs. Its efforts are cloaked in a veil of secrecy which is understandable as major banks are studying the efforts of its rivals closely.
Citibank is the leading bank which had done research on blockchain for ‘several years’. It has a wide span of laboratories around the world in Tel Aviv, Dublin, Singapore, Paolo Alto and Ohio according to the International Business Times. Citibank had developed its own cryptocurrency called Citicoin to compete with Bitcoin.
Source: Newsbtc
The presence of a cryptocurrency is vital to blockchain as it rewards the computers involved in validating the block of information. The other advantage of using Citicoin would be that Citibank does not have to worry about foreign currency volatility when it deals with overseas transactions.
Besides the application of blockchain in cross border payment and remittances, Citibank also intends to apply it for settlement purposes as it would reduce the collateral involved by shortening the settlement time. Another potential application for Citibank would be its trade finance department. Citibank would leverage on its global presence to facilitate the movement of documents through its internal system which would validate its authenticity.
Citibank is investing heavily in startups that can provide it with blockchain solution. It has a 90 day funding circle which it would decide if it is worthwhile to invest in a startup instead of the usual yearly funding circle. Currently it is partnering with Safaricom of Kenya to penetrate the market there. It is an interesting market where 80% of the people have mobile phones and yet only 40% have bank accounts.
Their mobile phone would serve as the e-wallet to accept Citibank’s blockchain payment and remittance system. It would leapfrog the traditional banking system to serve a larger base and at a lower cost. Perhaps Citibank is learning from JP Morgan’s failed patent attempt, it has no intention to fill patent for Citicoin as it is based on open source software.
Goldman Sachs
Goldman Sachs is widely known as the best investment bank in America and it is not far from the blockchain scene. It had recently lodged a patent for its own crypto-currency, the SETLcoin.
Unlike Citibank, Goldman Sachs would like to focus on the fast settlement of capital market transactions such as equities and bonds. After the 2008 crisis, banks started to move from T+3 settlement period where the buyer must pay up the cash and the seller must deliver the security to T+2. That cost the banking industry $550 million to save up $220 million in unguaranteed risk exposure per year when it was implemented in 2014. Currently banks are moving from the current T+2 system to T+1 system at the cost of $1.8 billion for the entire industry to reduce risk exposure of unguaranteed trade to $410 million per year.
If Goldman Sachs is successfully in commercializing SETLcoin, then it will result in instant settlement of all capital market transaction. This is significant because the Depository Trust & Clearing Corporation (DTCC) processes $1.6 quadrillion (one thousand million million) in 2013 alone. The collateral required by DTCC was estimated to be $700 billion in 2013 and this can be greatly reduced once instant settlement is implemented.
Source: Goldman Sachs Twitter Account
Goldman Sachs believe in the disruptive potential of blockchain. Hence instead of just researching on blockchain internally, it is also investing $50 million in Circle Internet Financial which is a leading blockchain developer for financial institutions. Circle stands out from other low cost remittance and payment services such as Paypal with its interoperability capabilities that allow users to send money outside of its system.
In addition, it participated in an industry collaboration with New York’s R3 CEV to create common standards for blockchain in the banking industry which attracted 8 other major banks.
JP Morgan
JP Morgan teamed up with IBM and Linux to create the Open Ledger Project to catch up with Goldman Sachs and Citibank recently in December 2015. This is in addition to the R3 consortium on blockchain. Former JP Morgan executive Blythe Masters joined startup Digital Asset Holdings which would provide the expertise for JP Morgan for its settlement process.
Blythe knew JP Morgan inside out after spending 27 years there and was credited with pioneering the credit derivatives market. The core product of Digital Assets would be its ‘Hyperledger’ distributed ledger that aims to serve all settlement segments of the banking industry.
Source: Digital Asset
Blythe left when her commodities division was sold to Mercuria Energy in April 2014 and she ended up in Digital Assets in March 2015 as CEO. JP Morgan CEO Jamie Dimon is quite proud of their payment systems and seemed determined to protect its turf:
“You all have read about bitcoin, merchants building their own networks, PayPal and PayPal look-alikes. Payments are a critical business for us – and we are quite good at it. But there is much for us to learn in terms of real-time systems, better encryption techniques and a reduction of costs and ‘pain points’ for customers.”
While Dimon works with his former executive on blockchain, JP Morgan has started a new offensive against Apple Pay with Chase Pay with major clients such as Walmart. There are not much details on Dimon’s counter plan but it is clear that JP Morgan will not allow Citibank and Goldman Sachs to rule the blockchain platform. This is despite its earlier failed patent application of its own cryptocurrency ‘web cash’ in 2014.
US Banking System & Payment
The US is often the leading pioneer of new financial innovation and the three of its most famous banks are approaching blockchain with its own methods. Citicoin, SETLcoin and Web Cash are all in the testing stages and none of them are real digital currencies yet as compared to Bitcoin.
Hence they can be said to be in the infancy stage but these banks are competing serious capital to the development of blockchain and also on each other’s development. There would be setbacks involved which they would attempt to bury it to protect their own images. Nevertheless the effort would continue given the tremendous potential. An analogy would be the Mt. Gox collapse in 2014 did not bring down Bitcoin like how Northern Rock bankruptcy did not bring down UK’s banking system.
Payment is a major global business with strong growth according to management consultant McKinsey.
Source: McKinsey
Payment has its own compliance and security issues which can be mitigated by blockchain. This is especially when payments are getting more areas such as mobile payment.
Conclusion
Citibank is focused on leveraging on its wide global footprints in the international payment and remittance system before expanding it to trade finance. Goldman Sachs is interested in the instant settlement for its capital market transaction. Goldman Sachs and JP Morgan joined R3 to set standards for blockchain for the banking industry.
However JP Morgan is looking for an edge against its rivals so it joined forces with IBM and Linux for the Open Ledger Project. JPMorgan is not going to give it up anytime soon and this can be said for the all banks.
So the race is on and we will see who will emerge victorious to corner the $2.3 trillion payments market.
This article is contributed by Ong Kai Kiat. He is a professional freelance writer who enjoys the process of discovering and collating new trends and insights for an article. He adds value to society through his articles especially those related to finance and technology. He is reachable at [email protected] Brought to you by RobustTechHouse. We provide Fintech Development services.
US Blockchain Banking Race between Citibank, Goldman Sachs and JP Morgan was originally published on RobustTechHouse - Mobile App Development Singapore
0 notes
Text
300+ TOP CloverETL Interview Questions and Answers
CloverETL Interview Questions for freshers experienced :-
1. What is CloverETL? CloverETL is a Java-based data integration ETL platform for rapid development and automation of data transformations, data cleansing, data migration and distribution of data into applications, databases, cloud and data warehouses. The product family starts with an open source runtime engine and limited Community edition of visual data transformation Designer. 2. What is ETL? ETL stands for Extract-Transform-Load – a data processing operation that performs data manipulations, usually on-the-fly, while getting (extracting) data from a source or sources, transforming it, and storing into target(s. For more information, see the Wikipedia page for ETL. 3. What is data integration? Data integration is a broad term used for any effort of combining data from multiple sources into a more unified and holistic view. It usually involves several operations, such as ETL, orchestration, automation, monitoring and change management. 4. What's the difference between ETL and data integration? ETL is a form of data integration where data is transformed during transport between sources and targets. While "pure" ETL is focused on the actual transport, data integration usually refers to a broader task of managing ETL tasks, scheduling, monitoring, etc. 5. Why use an ETL tool and why CloverETL in particular? ETL or data integration tools replace ad hoc scripts that you would use to transport data between databases, files, web services etc. Over time, these become very difficult to manage and are prone to errors. ETL tools provide you with visual tools to manage, monitor, and update data transformations with ease. CloverETL in particular is a rapid data integration tool oriented to get your job done quickly. 6. What is CloverETL Designer? CloverETL Designer is a visual tool for developing, debugging, and running data transformations. 7. What is CloverETL Server? CloverETL Server is an automation, orchestration and monitoring enterprise platform for data integration. 8. What is CloverETL Cluster? CloverETL Cluster allows multiple instances of the CloverETL Server to run on different HW nodes and form a computer cluster. It allows for high availability through fail-over capabilities, scaling via load balancing, and processing of Big Data through a massively-parallel approach. 9. Which platforms or operating systems does CloverETL run on? CloverETL runs on any platform/operating system where Java 1.6 or later is supported. This includes Windows, OSX, Linux, various UNIX systems and others. 10. Is there a free option for CloverETL? Yes. There is a 45-day fully featured trial for CloverETL Designer and a trial CloverETL Server (contact [email protected]. There is also a completely free, but feature-limited CloverETL Community Edition.

CloverETL Interview Questions 11. When and how are new versions released? There are two major production releases every year. Before each production release, there are two milestone releases that allow early access to new features from the upcoming production version. Production releases are sometimes replaced with bugfix releases that come as needed. 12. What are milestone (M1, M2) releases? Milestone releases provide early public access to features that we're working on for the upcoming production release. You can use milestones and their new features to develop, test, and provide us with feedback. However, milestone releases are not covered by CloverCARE support, so we do not recommend putting them into a mission critical deployment. Major changes that can affect existing transformations are usually published in early milestone versions so that you have plenty of time to adapt to possible incompatibilities. 13. Do I need to renew CloverCARE? Your CloverCARE support is covered by an 20% annual maintenance fee that grants you access to product updates and standard CloverCARE support. To continue receiving upgrades and support, you need to renew your maintenance every year. 14. Are there any discounts (academic, non profit, volume) available? We can offer discounts for various types of organizations and businesses. We can also offer volume deals. Please contact our Sales at [email protected] or via this Contact Us form. 15. What makes CloverETL stand out against SSIS/Talend/Pentaho? CloverETL is a rapid data integration tool. Our main goal is to provide our users with a tool that helps them achieve results quickly, without having to spend time on training, learning, etc. Starting from our examples, you can begin building data transformations quickly. CloverETL is also sharply focused on data integration – it’s a light-footed, dedicated tool. 16. What is CloverCARE and what does it include? CloverCARE is our support package included in every commercial deal. Members of our support team are professional experts who are using CloverETL themselves – no outsourcing, no frustrating phone calls. We also support evaluating users during their trial period. CloverCARE offers email, phone, and WebEx support at various SLAs. Please refer to our CloverCARE Support page for more details. 17. Which versions of application servers does CloverETL Server support? Currently CloverETL supports Apache Tomcat 6.0.x, Glassfish 2.1, JBoss 5.1 or JBoss 6.0, Jetty 6.1.x, WebLogic 11g (10.3.6), WebLogic 12c (12.1.1), Websphere 7.0 18. Can CloverETL be embedded in my product? The short answer is yes. CloverETL technology can be embedded in various ways. You can embed CloverETL Designer, CloverETL Server or even just the data processing engine running under the hood. Some of our customers also use white-labeled CloverETL technology in their product offerings. For additional details, please read our OEM section. 19. How scalable is CloverETL? CloverETL technology scales really well. You can start with the CloverETL Designer running on your laptop processing thousands of records then move onto the CloverETL Server with its automation capabilities to crunch millions of records. If you happen to hit any Big Data problems, then the CloverETL Cluster is able to cope with any data volume through its massively-parallel data processing capabilities. 20. Does CloverETL support Big Data? CloverETL technology naturally fits the processing of Big Data. Its inherent pipeline-parallelism and massively-parallel processing facilitated by CloverETL Cluster allows you to cope with Big Data problems. It’s also able to cooperate with other Big Data related technologies like Hadoop, Hive, and others. 21. What kind of data can I process in CloverETL? CloverETL can process any structured or semi-structured data whether stored in a database, file, or other system. Data sources and data targets alike can be a combination of various independent databases and files. 22. How do I get my newly purchased licenses? You'll receive an email with your account information (email and password) that you can use to Sign In here. From there, navigate to Licenses & Downloads where you can get both license keys and download all the software. 23. How do I transition from Designer to Server? There is a direct upgrade path from the desktop Designer to the Server environment. Your already existing work can be transferred to the Server without any additional effort. Designer manages projects in workspaces on your local drive. You can simply export these to Server sandboxes (via File > Export > CloverETL > Export to CloverETL Server sandbox) and continue working remotely on the Server. 24. How do I transition from Server to Cluster? CloverETL Cluster is basically a bunch of Server instances connected together into a single cluster. When you move into Cluster, we recommend reading about various types of sandboxes and how to process data in parallel 25. I purchased CloverETL, but my license is set to expire in two months. Why? If you feel there's been an error, please contact our Sales at [email protected] or via this Contact Us form. Usually we issue temporary licenses immediately once a Purchase Order is received. We then replace the temporary licenses with unlimited ones once the payment is processed. 26. My evaluation license expired. Is it possible to extend the evaluation period? Yes, you can ask for trial extension here. 27. Do you have any plans for selling the company or being taken over? Our mission is to be a leader in data integration and stay true to providing high quality product and services. You can read more in this CloverETL Manifesto. 28. What files are supported? You can process virtually any file containing data, including delimited files, fixed-length record files, binary files or mix of these. Popular file formats are also supported: Excel XLS/XLSX, XML, JSON, dBase DBF, emails, Lotus Notes Domino. 29. What databases are supported? CloverETL supports standard relational databases via JDBC. Others include Oracle, Informix, Microsoft SQL Server, Access, MySQL, Postgres, Sybase, etc. Also, some modern NoSQL or columnar databases are supported too, e.g. MongoDB, Exasol, HP Vertica, HDFS or S3. 30. Can I read and write remote files (FTP, SFTP, HTTP/S, etc.)? Yes. Please refer to Supported File URL Formats for Readers and Supported File URL Formats for Writers. 31. Can I read and write data using Web Services or REST APIs? Yes. There are dedicated components for that: WebServiceClient and HTTPConnector. Also, many components support remote data - please refer to Supported File URL Formats for Readers and Supported File URL Formats for Writers. 32. Do you support Apache Hadoop and/or Hive? Yes, Hadoop is supported for both HDFS storage, as well as running MapReduce jobs. Hive is also supported. Please refer to Hadoop connections, Hive connection. 33. Can I use data from cloud providers such as Amazon S3? Yes, you can access data on Amazon S3. For more please read Supported File URL Formats for Readers and Supported File URL Formats for Writers. 34. How do I use Designer to develop on the Server? Do I need to deploy? The Designer connects directly to Server sandboxes so you're working live on the Server. There is no need to deploy your local edits or anything. Whenever you're connected to a Server sandbox and run a transformation or jobflow, it is executed on the Server, not locally. 35. Can I run a transformation without Designer? How? Yes, CloverETL Server provides numerous automation functions, including scheduled execution, web services, event listeners, etc. 36. Can CloverETL Server be deployed to Amazon EC2? Yes, there are several projects running CloverETL hosted on Amazon EC2 servers. As data transformations are heavy on I/O, make sure you pick a "high I/O" instances. The installation does not require any additional tricks. 37. Can CloverETL handle secure data transfers (HTTPS, SFTP, FTPS, etc.)? Yes, you can access all of these protocols. For more please read Supported File URL Formats for Readers and Supported File URL Formats for Writers. 38. Can sensitive information, such as passwords in connections, be securely hidden? Yes, CloverETL Server supports encrypted secure parameters so that sensitive information are not stored in plain-text readable form in graphs, connections etc. 39. Can I use projects developed in Trial (or Community) in commercial an vice versa? Yes, everything that you create in Community or Trial can be opened and further developed in any commercial edition of CloverETL. However, CloverETL Community cannot run all transformations created using the Trial or commercial products due to its limitations. 40. Can I create my own custom component or function via a plugin? Yes, there are two nice articles you can read on our blog to help you do so: Creating your own component and Custom CTL functions. 41. How do I upgrade CloverETL Designer to the latest version? We recommend uninstalling the old version and performing a fresh install of the new one. Don’t worry, all your work is safe – it’s always stored outside the installation files. 42. Do I need an application server to run CloverETL Server? If yes, which one? We provide a default, easy-to-start bundled package of CloverETL Server with pre-configured Apache Tomcat and Derby database. It's a good, simple start. However, if you wish to use an application container of your own, CloverETL supports a number of industry standard J2EE application servers such as Apache Tomcat, GlassFish, Weblogic, WebSphere, JBoss and Jetty. CloverETL Questions and Answers Pdf Download Read the full article
0 notes
Text
Differences Between Linux And Windows
This article will discuss the differences between the Linux and Windows operating software's; we discuss some of the pro's and con's of each system.
Let us first start out with a general overview of the Linux operating system. Linux at its most basic form is a computer kernel. The Kernel is the underlying computer code, used to communicate with hardware, and other system software, it also runs all of the basic functions of the computer.
The Linux Kernel is an operating system, which runs on a wide variety of hardware and for a variety of purposes. Linux is capable of running on devices as simple as a wrist watch, or a cell phone, but it can also run on a home computer using, for example Intel, or AMD processors, and its even capable of running on high end servers using Sun Sparc CPU's or IBM power PC processors. Some Linux distro's can only run one processor, while others can run many at once.
Common uses for Linux include that of a home desktop computing system, or more commonly for a server application, such as use as a web server, or mail server. You can even use Linux as a dedicated firewall to help protect other machines that are on the same network.
A programmer student named Linus Torvalds first made Linux as a variant of the Unix operating system in 1991. Linus Torvalds made Linux open source with the GNU (GPL) (General Public License), so other programmers could download the source code free of charge and alter it any way they see fit. Thousands of coders throughout the world began downloading and altering the source code of Linux, applying patches, and bug fixes, and other improvements, to make the OS better and better. Over the years Linux has gone from a simple text based clone of Unix, to a powerful operating software, with full-featured desktop environments, and unprecedented portability, and a variety of uses. Most of the original Unix code has also been gradually written out of Linux over the years.
As a result of Linux being open source software, there is no one version of Linux; instead there are many different versions or distributions of Linux, that are suited for a variety of different users and task. Some Distributions of Linux include Gentoo, and Slackware, which due to the lack of a complete graphical environment is best, suited for Linux experts, programmers, and other users that know their way around a command prompt. Distributions that lack a graphical environment are best suited for older computers lacking the processing power necessary to process graphics, or for computers performing processor intensive task, where it is desirable to have all of the system resources focused on the task at hand, rather than wasting resources by processing graphics. Other Linux distributions aim at making the computing experience as easy as possible. Distributions such as Ubuntu, or Linspire make Linux far easier to use, by offering full-featured graphical environments that help eliminate the need for a command prompt. Of course the downside of ease of use is less configurability, and wasted system resources on graphics processing. Other distributions such as Suse try to find a common ground between ease of use and configurability.
"Linux has two parts, they include the Kernel mentioned previously, and in most circumstances it will also include a graphical user interface, which runs atop the Kernel" reference #3. In most cases the user will communicate with the computer via the graphical user interface. (ref #6) Some of the more common graphical environments that can run on Linux include the following. The KDE GUI (Graphical user interface). Matthias Ettrich developed KDE in 1996. He wanted a GUI for the Unix desktop that would make all of the applications look and feel alike. He also wanted a desktop environment for Unix that would be easier to use than the ones available at the time. KDE is a free open source project, with millions of coders working on it throughout the world, but it also has some commercial support from companies such as Novell, Troltech, and Mandriva. KDE aims to make an easy to use desktop environment without sacrificing configurability. Windows users might note that KDE has a similar look to Windows. Another popular GUI is (ref #7) GNOME. GNOME puts a heavy emphasis on simplicity, and user ability. Much like KDE GNOME is open source and is free to download. One notable feature of GNOME is the fact that it supports many different languages; GNOME supports over 100 different languages. Gnome is license under the LGPL license (lesser general public license). The license allows applications written for GNOME to use a much wider set of licenses, including some commercial applications. The name GNOME stands for GNU Network object model environment. GNOME's look and feel is similar to that of other desktop environments. Fluxbox is another example of a Linux GUI. With less of an emphasis on ease of use and eye candy, Fluxbox aims to be a very lightweight, and a more efficient user of system resources. The interface has only a taskbar and a menu bar, which is accessed by right clicking over the desktop. Fluxbox is most popular for use with older computers that have a limited abundance of system resources.
Although most Linux distributions offer a graphical environment, to simplify the user experience, they all also offer a way for more technically involved users to directly communicate with the Kernel via a shell or command line. The command line allows you to run the computer without a GUI, by executing commands from a text-based interface. An advantage of using the command prompt is it uses less system resources and enables your computer to focus more of its energy on the task at hand. Examples of commands include the cd command for changing your directory, or the halt command for shutting down your system, or the reboot command for restarting the computer etc.
Now that we are more familiar with the Linux operating system, we can note the many ways in which Linux differs from the worlds most popular OS, Microsoft Windows. From this point forward we will discuss some of the more prominent ways in which Linux deferrers from Windows.
For starters there is only one company that releases a Windows operating system, and that company is Microsoft. All versions of Windows, weather Windows XP Home, Business, or Vista, all updates, security patches, and service patches for Windows comes from Microsoft. With Linux on the other hand there is not one company that releases it. Linux has millions of coders and companies throughout the world, volunteering their time to work on patches, updates, newer versions, and software applications. Although some companies, charge for TECH support, and others charge for their distribution of Linux, by packaging it with non-free software, you will always be able to get the Linux Kernel for free, and you can get full-featured Linux desktops with all the necessary applications for general use, for free as well. The vendors that charge money for their distribution of Linux are also required to release a free version in order to comply with the GPL License agreement. With Microsoft Windows on the other hand you have to pay Microsoft for the software, and you will also have to pay for most of the applications that you will use.
Windows and Linux also differ on TECH support issues. Windows is backed by the Microsoft Corporation, which means that if you have an issue with any of their products the company should resolve it. For example if Microsoft Windows is not working right, then you should be able to call Microsoft and make use of their TECH support to fix the issue. TECH support is usually included with the purchase of the product for a certain amount of time, maybe a two year period, and from there on you may be charged for the service. Although IBM backs their Linux products, for the most part if you use Linux you are on your own. If you have a problem with Ubuntu Linux you cannot call Ubuntu and expect any help. Despite the lack of professional help, you can however receive good TECH advice, from the thousands or millions of Linux forums that are on the web. You ca also get great help from social networking sites such as Myspace, by posting questions in the many Linux groups. You can usually receive responses for your questions in a matter of hours form many qualified people.
Configurability is another key difference between the two operating software's. Although Windows offers its control panel to help users configure the computer to their liking, it does not match the configuring options that Linux provides especially if you are a real TECH savvy user. In Linux the Kernel is open source, so if you have the know how, you can modify it in virtually any way that you see fit. Also Linux offers a variety of Graphical environments to further suit your needs. As mentioned earlier Linux is capable of running full-featured graphical environments like KDE, or more lightweight and resource friendly GUI's like Fluxbox, or Blackbox, to suit users with older computers. There are also versions of Linux that are designed to emulate the Windows look and feel as closely as possible. Distributions such as Linspire are best suited for users that are migrating over from the Windows world. There are also distributions that include no graphical environment at all to better suit users that need to squeeze out all of the computing power that they can get for various computing activities, and for users that are more advanced than others. All of this configurability can be problematic sometimes, as you will have to make a decision on which desktop is right for you, and to make things easier on yourself you will need to only install applications that are native to your distribution and graphical environment.
(ref #1) The cost effectiveness of Linux is another way it separates itself from Windows. For home use Linux is cheap and in most cases completely free, while Windows varies in cost depending on which version you buy. With Linux most of the applications will also be free, however for Windows in the majority of cases you are suppose to pay for the applications. For most cases, with Linux there is no need to enter a product activation key when performing an installation, you are free to install it on as many computers as you'd like. With Windows you are only allowed to install it on one computer and Microsoft uses product activation software to enforce this rule. When installing Window's you must enter a product activation key, which will expire after so many uses. If you wish too, you can purchase Linux from a variety of vendors, which will include a boxed set of CDs, Manuals, and TECH support for around 40-130$. Of course If you purchase a high-end version of Linux used for servers it may cost any where from 400$- 2000$. "In 2002 computer world magazine quoted the chief technology architect at Merrill Lynch in New York, as saying "the cost of running Linux is typically a tenth of the cost of running Unix or Windows alternatively." (ref#1)
(ref #1) Installation of Windows is generally easier, than installing Linux. "With Windows XP there are three main ways to install. There is a clean install, in which you install Windows on a blank hard drive. There is also an upgrade install, in which you start with an older version of Windows and "upgrade" to a newer one. An advantage of upgrading is that all of the files on the older system should remain intact throughout the process. You can also perform a repair install, in which case you are installing the same version of Windows on top of itself in order to fix a damaged version of Windows. There is also a recovery, which Technically is not an install; it is used to restore a copy of Windows back to its factory settings. The disadvantage of recovering Windows is the fact that you will loose all of your data, which resides on the damaged copy of Windows." (ref#1) Also with Windows you can rest assured that your hardware will most likely be supported by the operating software, although this is not much of a problem with Linux you cant be sure if Linux will support all of your hardware. With Linux installation varies greatly from Distro to Distro. You may be presented with a graphical installer or it may be a text-based installer, these variations make Linux a bit more difficult and unpredictable to install than is Windows, (although the difficulty is disappearing). You may perform a clean install of Linux or dual boot it, to co-exist with another operation software. With Linux rather than having to buy an upgrade Cd, you can install updates by downloading and then installing them while your desktop is running. With Linux it is also not necessary to reboot your computer after most upgrades, It is only necessary to reboot after an upgrade to the kernel. It is also possible to run Linux without ever needing to install it on a hard drive; there are many distributions of Linux that will allow you to run it straight off of a live cd. The advantage of this is that you do not need to alter your system in order to try Linux. You can run Linux off of the CD so you do not have to damage your Windows partition. Other advantages include the ability to rescue a broken Linux system. If your Linux computer will not boot, then you may insert a live cd and boot off it, so you can repair the damaged version of Linux. Also you may use a Linux live cd to recover files from a damaged Windows computer that will no longer boot up. Since Linux is capable of reading NTFS files you may copy files form a Windows computer to a USB flash drive or floppy drive etc.
Another major difference between Linux and Windows is the applications that you will use with either OS. Windows includes a much wider abundance of commercially backed applications than does Linux. It is much easier to find the software that you are looking for with Windows than it is with Linux, because so many software vendors make their products compatible with Windows only. With Linux you will for the most part be forced to let go of the familiar applications that you have grown accustomed to with Windows, in favor of lesser-known open source apps that are made for Linux. Applications such as Microsoft office, Outlook, Internet Explorer, Adobe Creative suite, and chat clients such as MSN messenger, do not work natively with Linux. Although with Linux you can get Microsoft office and Adobe creative suite to work using software from codeWeavers called cross Over Office. Instead of using these applications you will need to use Linux apps such as open office, The Gimp Image Editor, The ThunderBird email client, Instead of the MSN messenger you can use the GAIM messenger, and you can use Firefox as your web browser. Also with Linux it can be difficult to install software even if it is made for Linux. This is due to the fact that Linux has so many different versions. Software that is made to install on one version probably will require some configuration in order to install on another version. An example would be if you were trying to install software that was made for the KDE graphical environment, on the GNOME GUI, This app would not easily install on the GNOME GUI, and would require some configuring on your part to successfully install it.
The type of hard ware that Linux and windows runs on also causes them to differ. Linux will run on many different hardware platforms, from Intel and AMD chips, to computers running IBM power Pc processors. Linux will run on the slowest 386 machines to the biggest mainframes on the planet, newer versions of Windows will not run on the same amount of hardware as Linux. Linux can even be configured to run on apples, Ipod's, or smart phones. A disadvantage of Linux is when it comes to using hardware devices such as Printers, Scanners, or Digital camera's. Where as the driver software for these devices will often be easily available for Windows, with Linux you are for the most part left on your own to find drivers for these devices. Most Linux users will find comfort in the fact that drivers for the latest hardware are constantly being written by coders throughout the world and are usually very quickly made available.
(ref #1) One of the most notable differences between the two operating software's is Windows legendary problems with malicious code, known as Viruses and Spy ware. Viruses, Spy-ware and a general lack of security are the biggest problems facing the Windows community. Under Windows Viruses and Spy-ware have the ability to execute themselves with little or no input from the user. This makes guarding against them a constant concern for any Windows user. Windows users are forced to employ third party anti virus software to help limit the possibility of the computer being rendered useless by malicious code. Anti virus software often has the negative side effect of hogging system resources, thus slowing down your entire computer, also most anti virus software requires that you pay a subscription service, and that you constantly download updates in order to stay ahead of the intruders. With Linux on the other hand problems with viruses are practically non-existent, and in reality you do not even need virus protection for your Linux machine. One reason why Viruses and Spy-ware are not a problem for Linux is simply due to the fact that there are far fewer being made for Linux. A more important reason is that running a virus on a Linux machine is more difficult and requires a lot more input from the user. With Windows you may accidentally run and execute a virus, by opening an email attachment, or by double clicking on a file that contains malicious code. However with Linux a virus would need to run in the terminal, which requires the user to give the file execute permissions, and then open it in the terminal. And in order to cause any real damage to the system the user would have to log in as root, by typing a user name and password before running the virus. Foe example to run a virus that is embedded in an email attachment the user would have to, open the attachment, then save it, then right click the file and chose properties form the menu, in properties they can give it execute permissions, they would then be able to open the file in the terminal to run the virus. And even then the user would only be able to damage his or her home folder, all other users data will be left untouched, and all root system files would also remain untouched, because Linux would require a root password to make changes to these files. The only way the user can damage the whole computer would be if he or she logged in as root user by providing the root user name and password to the terminal before running the virus. Unlike Windows in Linux an executable file cannot run automatically, It needs to be given execute permissions manually this significantly improves security. In Linux the only realistic reason you would need virus protection is if you share files with Windows users, and that is to protect them not you, so you are not to accidentally pass a virus to the Windows computer that you are sharing files with. Also Check how to check if bootloader is unlocked or locked
The above was a general over view of some differences between the Windows operating system, and Linux. To recap we started with the fact that Windows has only one vendor that releases the software, while Linux comes from millions of different coders throughout the world. We also commented on the fact that the Linux Kernel and much of the applications used with it are completely free of charge, where as with windows you are forced to pay for most of the software. Unlike Widows Linux is often lacking in professional Tech support, and Linux users are often left on their own to solve Technical issues. Linux users can either pay for Tech support or rely on the many Linux Forums and groups available on the Internet. Due to the fact that the kernel is open source, Linux has a huge advantage over Windows in configurability. You can configure Linux to run almost any way you see fit by manipulating the Kernel. Installing the Windows Operating software and applications is easier due to the fact that it has a universal installer. Also finding applications for Windows is easier because of its popularity most apps are available for Windows only, and are made easily available. Linux will run on a greater variety of hard ware than does Windows, from mainframe super computers running multiple IBM Power PC Chips, to a small laptop running an AMD processor. And of course the biggest difference in this writer's opinion is the fact that Linux does not suffer from an onslaught of Viruses and other malicious code, unlike Windows which is plagued by countless number of malicious code that can easily destroy your system if not properly guarded against.
In conclusion we will conclude that the Linux OS really is the superior software. Other than a few minor nuisances, linux out performs Windows in most categories. The fact that Linux is more secure is the tipping point, that tilts the scales in the favor of Linux. Windows simply suffers from far to many security vulnerabilities for it to be considered the better over all desktop environment.
References
michaelhorowitz.com/Linux.vs.Windows.html Reference #1
theinquirer.net/en/inquirer/news/2004/10/27/linux-more-secure-than-windows-says-study Reference #2
linux.com/whatislinux/ reference number 3
.linux.org/info/
Reference #4
en.wikipedia.org/wiki/Linux%5Fkernel Reference #5
/en.wikipedia.org/wiki/KDE Reference #6
/en.wikipedia.org/wiki/GNOME Reference #7
1 note
·
View note