#email security software
Explore tagged Tumblr posts
Text
Why Email Marketing Is So Importnat? Fun Facts and Insider Tips 🔥
🌟 Hey #MarketingMinds! Let's dive into the incredible world of #EmailMarketing - where the magic happens! 💌✨
1️⃣ Did you know? Email marketing has an ROI of 4400%! 💸💥 Yep, you read it right. That's like turning a dime into a treasure chest! ✉️
2️⃣ It's not just about sending emails, it's about building relationships. 🤝📧 Email is your secret weapon to connect, engage, and create a community around your brand. 💖
3️⃣ Personalization is the name of the game. 🎯 Tailor your emails like a bespoke suit – people want to feel special, not like another fish in the sea. 🐠📩
4️⃣ Insider Tip: Timing is everything! 🕒✉️ Studies show that Tuesday and Thursday mornings are prime time for opening emails. Hit that inbox when it's hot! ☕️🔥
5️⃣ Subject lines matter... A LOT! 🚀✉️ Get creative, be intriguing, and lure them in with the promise of something amazing inside. It's like a mini movie trailer for your content! 🎥🌟
6️⃣ The power of segmentation! 🔍📬 Break down your audience into smaller groups based on behavior, preferences, or demographics. Serve them what they want, and they'll love you for it! 💕🎯
7️⃣ Did you know emojis in the subject line can boost open rates by 56%? 🤯📧 Spice it up! 🌶️✉️ Don't be shy with those cute little symbols. They speak volumes! 🚀💬
8️⃣ Automation is your BFF. 🤖📧 Set up those drip campaigns and watch the engagement soar. It's like having a 24/7 marketing superhero working for you! 🦸♂️💼
9️⃣ A/B testing is the secret sauce! 🧪✉️ Experiment with different elements – subject lines, images, CTA buttons. Find the winning combo that makes your audience do the happy dance! 🎉
🔟 Boost your email game with our ultimate Email Marketing Guide! 📚✉️ Dive deep into the art and science of email marketing. Your inbox will thank you! 💌🚀
#emailmarketing #emailmarketingtips #emailmarketingbusiness #emailmarketingstrategy #emailmarketingagency #emailmarketingcampaign #emailmarketingautomation #emailmarketingtraining #emailmarketingcourse #affiliatemarketing #digitalmarketing #internetmarketing #makemoneyonline #earnmoneyonline #workfromhome #homebusiness #onlinebusiness #onlinemarketing #emaillist #emaillistbuilding #mailinglist #mailinglistbuilding #emailmarketer #salesfunnel #marketingtips
#work from home#affiliate marketing#make money online#home business#make money with affiliate marketing#online marketing#digital marketing#online business#blogger#marketing#email security#email newsletter#email marketing software#email marketing#email list#emailmarketing
18 notes
·
View notes
Text
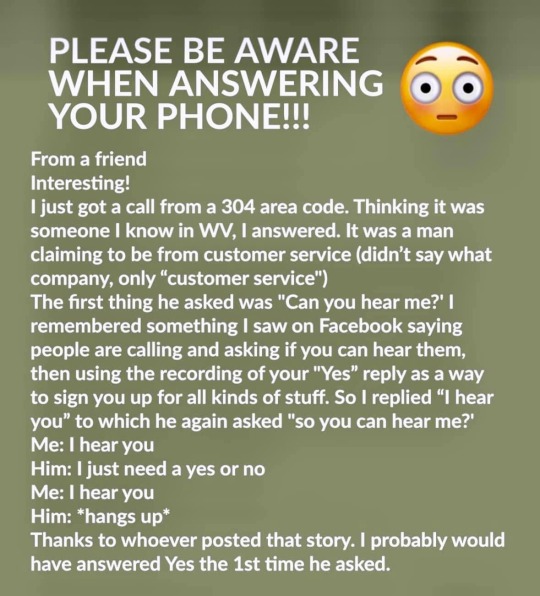
PLEASE SUBSCRIBE TO MY YOUTUBE CHANNEL: https://tinyurl.com/a6fts8j8
#seniorsguidetocomputers#seniors#computers#computertraining#computertutorials#computerlessons#beginners#software#hardware#internet#security#cybersecurity#email
2 notes
·
View notes
Text
I haven’t really seen any of the more recent U.S. election news hitting tumblr yet so here’s some updates (now edited with sources added):
There’s evidence of Trump cheating and interfering with the election.
Possible Russian interference.
Mail-in ballots are not being counted or “recognized” in multiple (notably swing) states.
30+ bomb threats were called in and shut down polling stations on Election Day.
20+ million votes are still unaccounted for, and that’s just to have the same voter turnout as 2020.
There was record voter turnout and new/first-time voter registration this year. We definitely should be well over the turnout in 2020.
U.S. citizens are using this site to demand, not only a recount, but a complete investigation into election fraud and interference for the reasons stated above:
Here is what I submitted as an example:
An investigation for election interference and fraud is required. We desperately need a recount or even a revote. The American people deserve the right to a free and fair election. There has been evidence unveiled of Trump cheating and committing election fraud which is illegal. There is some evidence of possible Russian interference. At least 30+ bomb threats were called in to polling places. Multiple, notably swing states, have ballots unaccounted for and voting machines not registering votes. Ballots and ballot boxes were tampered with and burned. Over 20 million votes that we know of are unaccounted for. With record turnout and new voter registration this year, there should be no possibility that there are less votes than even in the 2020 election.
Sources (working on finding more links but if anyone wants to add info, it’s appreciated):
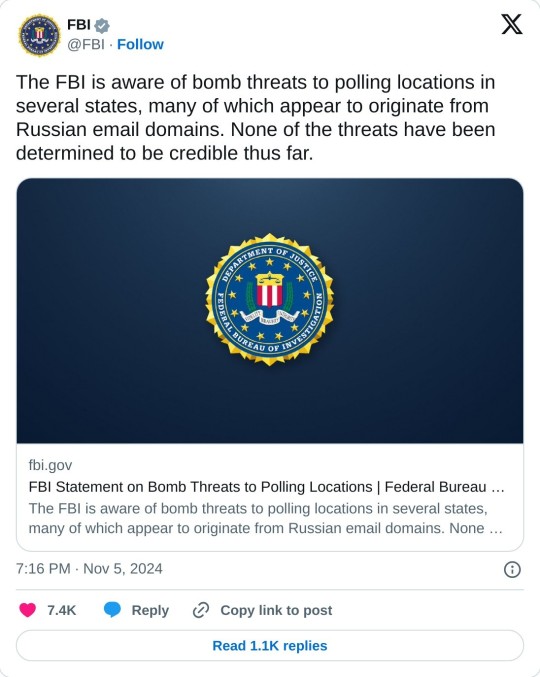
FBI addressing Russian interference and bomb threats:
Emails released by Rachael Bellis (private account, can’t share original tweet) confirming Trump committing election fraud:
Pennsylvania's Centre County officials say they are working with their ballot scanner vendor to figure out why the county's mail-in ballot data is "not being recognized when uploaded to the elections software:”

Wisconsin recount:
[ID:
Multiple screenshots and images.
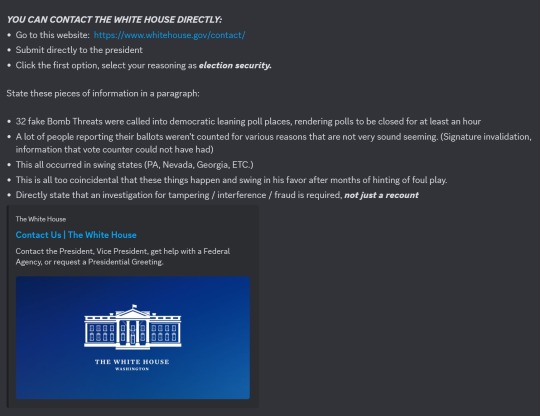
The first is a screenshot with a link and information for contacting the White House directly regarding election fraud. The instructions include choosing to leave a comment to President Joe Biden directly and to select election security as the reason.
The screenshot then instructs people to include any or all of the following information in a paragraph as a comment to the president:
32 fake bomb threats were called into Democratic leaning poll places, rendering polling places closed for at least an hour.
A lot of people reporting their ballots were not counted for various reasons.
This all occurred in swing states.
This is too coincidental that these things happen and swing in his favor after months of hinting at foul play.
Directly state that an investigation for tampering, interference, fraud is required, not just a recount.
The second image is from the FBI Twitter account that reads:
The FBI is aware of bomb threats to polling locations in several states, many of which appear to originate from Russian email domains. None of the threats have been determined to be credible thus far. https://t.co/j3YfajVK1m — FBI (@FBI) November 5, 2024
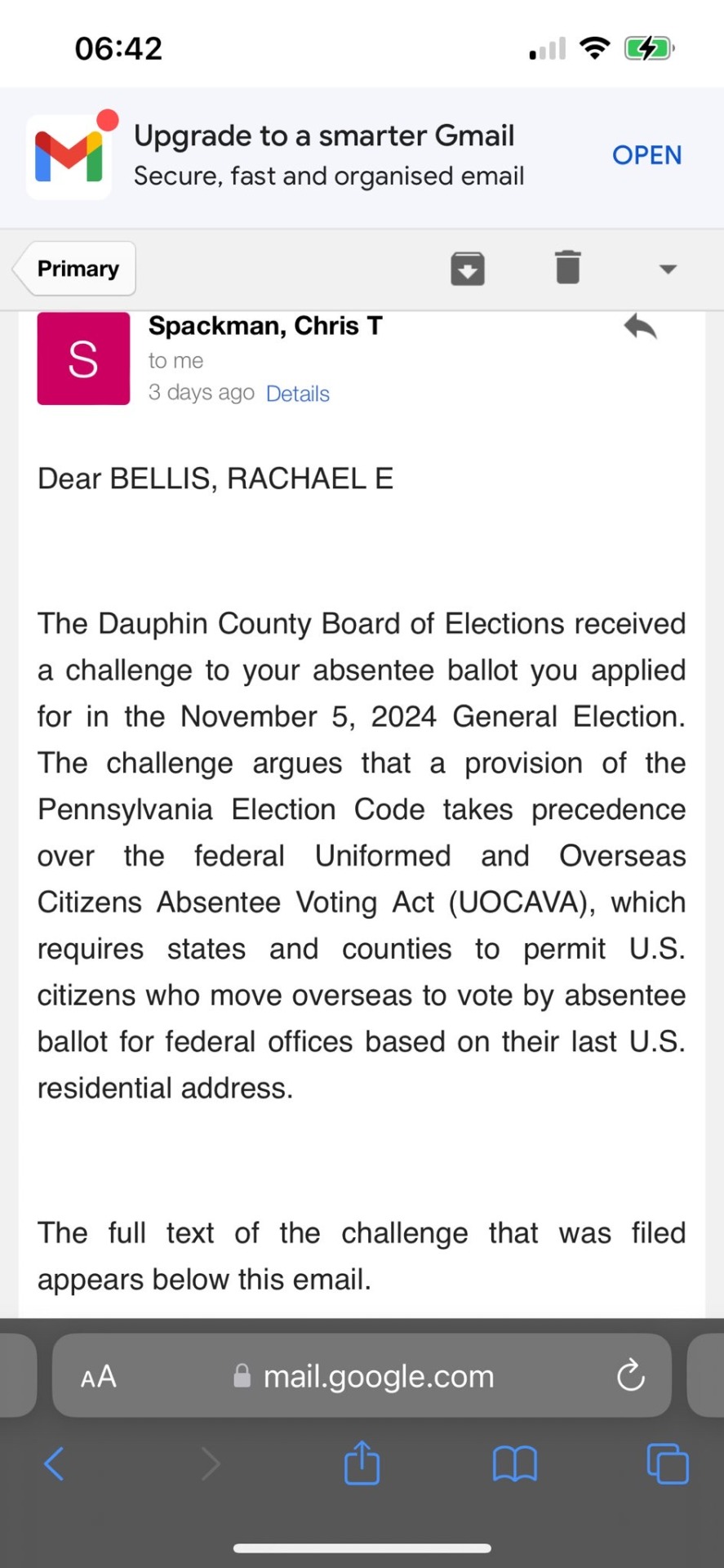
The next four Gmail screenshots of an email sent to Rachael Bellis from Chris T. Spackman that read together as follows:
Dear BELLIS, RACHAEL E., The Dauphin County Board of Elections received a challenge to your absentee ballot you applied for in the November 5, 2024 General Election. The challenge argues that a provision of the Pennsylvania Election Code takes precedence over the federal Uniformed and Overseas Citizens Absentee Voting Act (UOCAVA), which requires states and counties to permit U.S. citizens who move overseas to vote by absentee ballot for federal offices based on their last U.S. residential address.
The full text of the challenge that was filed appears below this email.
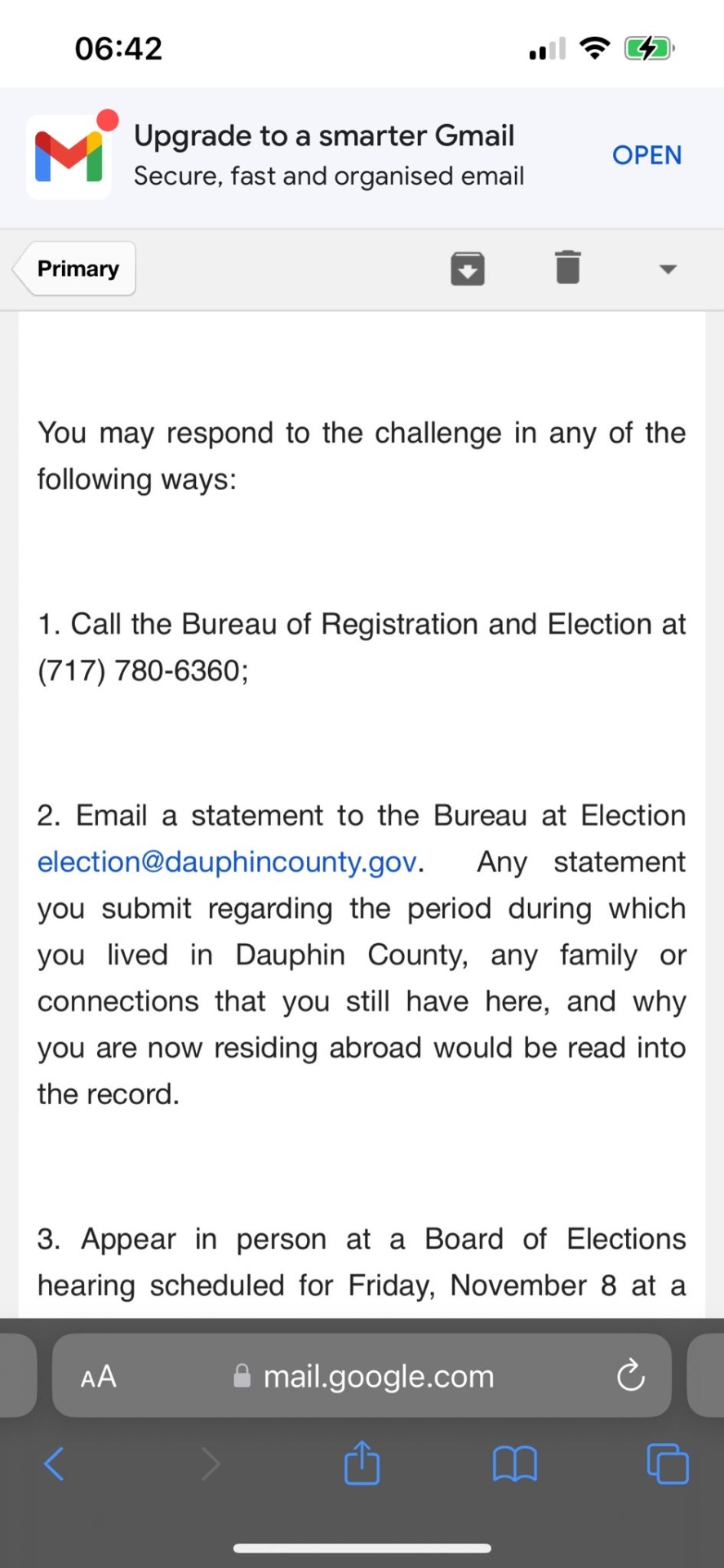
You may respond to the challenge in any of the following ways:
1. Call the Bureau of Registration and Election at (717) 780-6360;
2. Email a statement to the Bureau at Election [email protected]. Any statement you submit regarding the period during which you lived in Dauphin County, any family or connections that you still have here, and why you are now residing abroad would be read into the record.
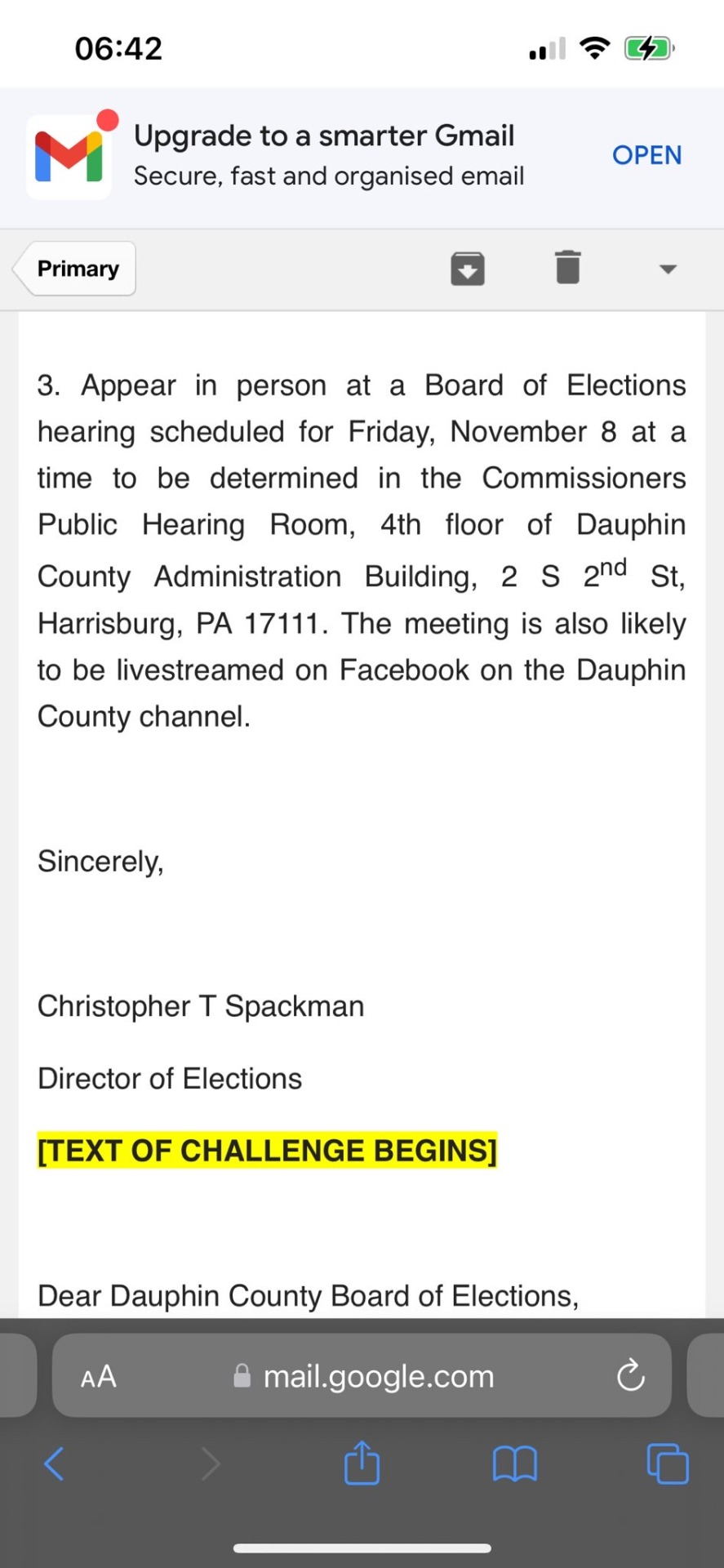
3. Appear in person at a Board of Elections hearing scheduled for Friday, November 8 at a time to be determined in the Commissioners Public Hearing Room, 4th floor of Dauphin County Administration Building, 2 S 20d St, Harrisburg, PA 17111. The meeting is also likely to be livestreamed on Facebook on the Dauphin County channel.
Sincerely,
Christopher T Spackman
TEXT OF CHALLENGE BEGINS
Dear Dauphin County Board of Elections,
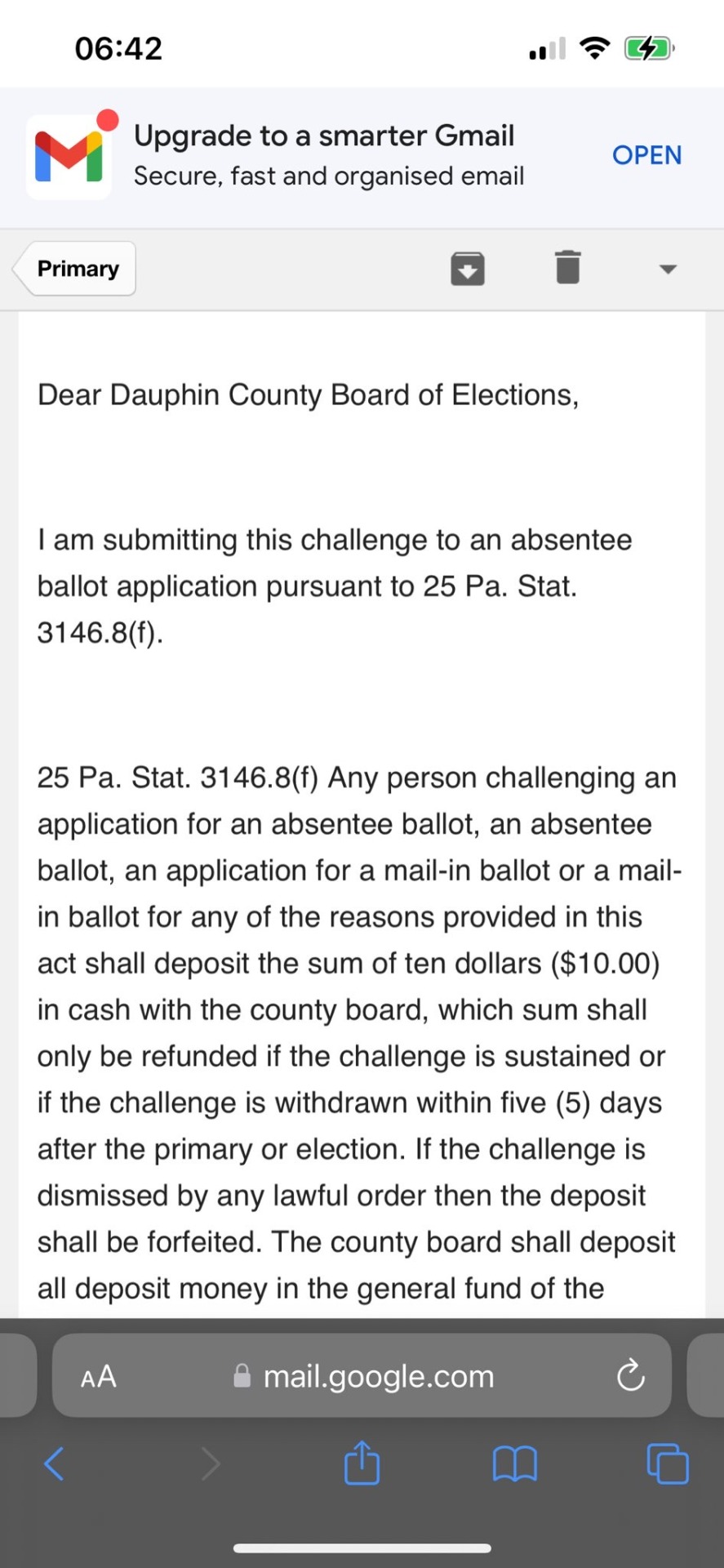
I am submitting this challenge to an absentee ballot application pursuant to 25 Pa. Stat.
3146.8(f).
25 Pa. Stat. 3146.8(f) Any person challenging an application for an absentee ballot, an absentee ballot, an application for a mail-in ballot or a mail-in ballot for any of the reasons provided in this act shall deposit the sum of ten dollars ($10.00) in cash with the county board, which sum shall only be refunded if the challenge is sustained or if the challenge is withdrawn within five (5) days after the primary or election. If the challenge is dismissed by any lawful order then the deposit shall be forfeited. The county board shall deposit all deposit money in the general fund of the…
The rest of the forwarded email is cut off.
The last image is a screenshot of the official statement from the Centre County, Pennsylvania Board of Commissioners released on November 6, 2024 that states:
Centre County Working with Ballot Scanner Vendor to Export Election Results.
(Bellefonte, PA) -Centre County Elections Office is working continuously to provide mail-in ballot data in order to post unofficial results.
To this point, all ballots have been scanned, including all mail-in ballots.
Centre County's Election team and IT team have identified that the data are successfully being exported from the mail-in ballot scanners, but that the data is not being recognized when uploaded to the elections software.
Centre County's Administrator, John Franek, Jr. stated, "We have not stopped working, and we will continue to work until unofficial results are posted and reported to the Pennsylvania Department of State."
As a next step, Centre County has begun working with the equipment vendor to adjust configurations to make the two systems-the mail-in ballot scanner and the elections software where data are uploaded -compatible with one another.
We will provide updates as we make progress.
/end ID]
#sources added#us politics#us election#presidential election#2024 presidential election#election interference#election integrity#election security#image described#image description in alt#image description included#image description added#described#kamala harris#kamala 2024#us news#us presidents#updated id
36K notes
·
View notes
Text
G Suite Mail Backup Tool

Every business and profession faces risks that can take the menacing form of data loss. This is the reason why we must take effective measures to have the better of these risks. Since digital data is the very life force fueling a business, every effort must be made to repel any chances of data loss. A large chunk of digital data is present in the form of emails and these must be well protected by installing antimalware systems. But this is not enough; we also need data backup and recovery systems to keep data loss at bay. Therefore, we must use professional, third party tools which are way cheaper than expert services and way more convenient than manual methods to backup G suite or any other email service.
G suite backup with a tool that caters simplicity in usage
In order to backup emails with ease we so yearn for, we need a tool that caters user friendly features. It must enable users to personalize an email archiving session. No matter what volume of data is thrown at a tool, it must deliver flawless results. It must issue valid usage license to users and should come decked with an easy plus smooth interface. A tool should not shrink our wallets by overcharging us. If you want to backup G suite email with such a features-packed tool, then you cannot go wrong if you stamp your approval on Mail Backup X.
Mail Backup X- a professional G suite mail backup tool with user friendly features
Mail backup X is a tool that beats the exorbitant professional services in the area of pricing with its highly affordable price tag. This tool also beats the professional services when it comes to the sheer range of features on offer. Easy to use even for beginners, this tool maintains its peak and flawless performance on both Windows and Mac devices. It is compatible with a huge number of email services, which makes it a cost effective solution. Another thing that makes it an even more cost effective choice is this tool's untiring ability to cater the whole range of email management tasks like email migration and restore. You can customize an email backup, restore or achieving session in the light of your unique needs. The level of flexibility on offer from this tool is second to none. You can choose between full and selective backups. PDF archiving feature is also present. Your data is duly encrypted to present no chance to internet threats to meddle in your private affairs. You can also G suite mail contacts backup, which evidences the fact that this tool assures complete data retention. It is updated on a regular basis, which explains the reason why its smooth performance on both Windows and Mac is well sustained.
How to backup G suite email in a manner that affords significant savings in storage space?
To reap significant savings in storage space, you can throw the weight of your trust on this tool that has the unique ability of 3x data compression. The data compression algorithm employed by this tool has been fully tested, so there are no question marks about its safety. Even while using such a high degree of compression, you are assured of complete data retention. Even the folder hierarchy is not messed up during this process. 3x data compression will increase the rate of data transfer thereby leading to faster and effortless results.
G suite email backup that is safe as well
No matter how precarious the outside circumstances are, this tool will keep your data safe by using effective remedies against data theft. Encryption takes the top honors when it comes to completely shutting all doors that may become a source of unauthorized data access. Google approved login ensures that whenever you use this tool to source emails from an email client, the connection is always secure with no scope for unauthorized data access. The users are provided with the option to password protect their files tagged highly confidential. An offline mode of this tool gives vent to all data security concerns populating your mind space. To put it in short, you will not find a more secure tool to backup G suite.
Backup G suite mail folders without pounding your head with complexities
A tool may have the best lineup of features and may be highly secure as well, but its overall utility will diminish considerably if it pounds our head with complexities. Ease in use should be the foremost attribute of a tool, everything else matters thereafter. And this tool gets the balance between simplicity and sophistication absolutely right. No more usage of mind numbing technical terminologies. No more encounters with vague instructions that become a grapevine of confusions. No more getting caught up in an unnecessarily long line up of instructions which lead to brewing of confusions. Use this sophisticated yet straightforward tool to get the intended results in an effortless manner. Short and simple instructions, a user friendly interface, complete absence of heavy technical terminologies and usage of simple language, elevate the level of ease users feel while carrying out myriad email management tasks.
These tools has other ease-affording features as well that simplify email management to a great degree. These features include a smart mail viewer, incremental backups, a smart search module along with a live dashboard.
Backup G suite mail data with a free demo of this tool
There is no better way of discovering the trust-invoking qualities of this tool other than trying out its free demo. This tool has been growing in popularity at an unabated pace because it walks the talks by living up to the expectations of users. Even though everything about this tool is very true and transparent, you can get further insights into its user friendly technology by trying out its free demo. So what are you waiting for? Grab this inopportunity without any second thoughts for this tool is tailor-made to fulfill your diverse needs.
0 notes
Text
What are the next steps after obtaining an insurance broker license, and how can you generate potential leads using Mzapp CRM software?
Congratulations on securing your insurance broker license! The journey doesn’t end here; it’s just the beginning of building a successful insurance brokerage. Here’s how you can proceed and leverage Mzapp CRM software to find potential leads:
Steps After Getting Your Insurance Broker License
Understand Your Market: Research your target audience (individuals, businesses, or specific sectors).
Develop a Business Plan: Set goals for client acquisition, revenue, and operational processes.
Build a Network: Partner with insurance providers and attend industry events to establish your presence.
Create an Online Presence: Build a professional website and maintain active profiles on social platforms.
Offer Value-Added Services: Educate customers on policies, claims management, and risk assessments.
Using Mzapp CRM Software to Generate Leads
Lead Capture: Utilize Mzapp’s integrated forms and web tracking tools to capture inquiries from your website or social media.
Automated Follow-Ups: Set up personalized email and SMS follow-ups to nurture leads effectively.
Lead Scoring: Prioritize leads based on their interaction history, ensuring you focus on high-potential prospects.
Data-Driven Campaigns: Use analytics to identify what works and launch targeted campaigns.
Seamless Policy Management: Impress leads by showcasing how smoothly you manage policies and claims through Mzapp.
Why Choose Mzapp CRM?
Mzapp CRM simplifies lead management, streamlines operations, and provides insights into customer behavior, making it easier to convert prospects into loyal clients.
Learn more about how Mzapp can transform your insurance business here.
#Question:#What are the next steps after obtaining an insurance broker license#and how can you generate potential leads using Mzapp CRM software?#Answer:#Congratulations on securing your insurance broker license! The journey doesn’t end here; it’s just the beginning of building a successful i#Steps After Getting Your Insurance Broker License#Understand Your Market: Research your target audience (individuals#businesses#or specific sectors).#Develop a Business Plan: Set goals for client acquisition#revenue#and operational processes.#Build a Network: Partner with insurance providers and attend industry events to establish your presence.#Create an Online Presence: Build a professional website and maintain active profiles on social platforms.#Offer Value-Added Services: Educate customers on policies#claims management#and risk assessments.#Using Mzapp CRM Software to Generate Leads#Lead Capture: Utilize Mzapp’s integrated forms and web tracking tools to capture inquiries from your website or social media.#Automated Follow-Ups: Set up personalized email and SMS follow-ups to nurture leads effectively.#Lead Scoring: Prioritize leads based on their interaction history#ensuring you focus on high-potential prospects.#Data-Driven Campaigns: Use analytics to identify what works and launch targeted campaigns.#Seamless Policy Management: Impress leads by showcasing how smoothly you manage policies and claims through Mzapp.#Why Choose Mzapp CRM?#Mzapp CRM simplifies lead management#streamlines operations#and provides insights into customer behavior#making it easier to convert prospects into loyal clients.#Learn more about how Mzapp can transform your insurance business here.
1 note
·
View note
Text
#Employee monitoring#Mobile spy apps#Monitor employee emails#Call monitoring software#Business data security#Workplace productivity tools#Employee surveillance apps#Corporate monitoring solutions#Email and call monitoring#Employee communication monitoring
0 notes
Text
Someone accessed my Gmail 2 days ago, compromising my linked accounts like Twitter and YouTube. Here's how it happened, why I fell for it, and what you can learn to avoid making the same mistake:
The scam I fell victim to was a cookie hijack. The hacker used malicious software to steal my browser cookies (stuff like autofill, auto sign in, etc), allowing them to sign in to my Gmail and other accounts, completely bypassing my 2FA and other security protocols.
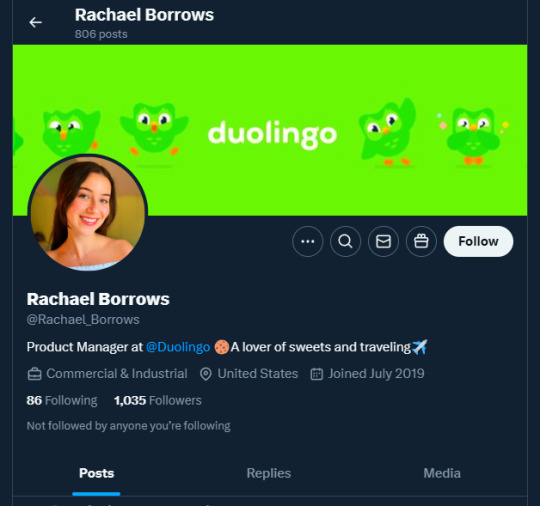
A few days ago, I received a DM from @Rachael_Borrows, who claimed to be a manager at @Duolingo. The account seemed legitimate. It was verified, created in 2019, and had over 1k followers, consistent with other managers I’d seen at the time n I even did a Google search of this person and didnt find anything suspicious.
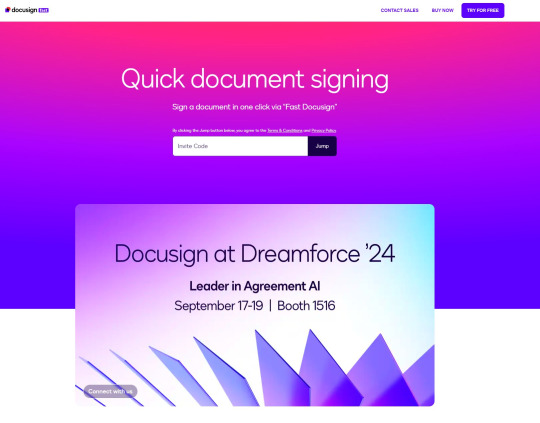
She claimed that @Duolingo wanted me to create a promo video, which got me excited and managed to get my guard down. After discussing I was asked to sign a contract and at app(.)fastsigndocu(.)com. If you see this link, ITS A SCAM! Do NOT download ANY files from this site.
Unfortunately, I downloaded a file from the website, and it downloaded without triggering any firewall or antivirus warnings. Thinking it was just a PDF, I opened it. The moment I did, my console and Google Chrome flashed. That’s when I knew I was in trouble. I immediately did an antivirus scan and these were some of the programs it found that were added to my PC without me knowing:

The thing about cookie hijacking is that it completely bypasses 2FA which should have been my strongest line of defense. I was immediately signed out of all my accounts and within a minute, they changed everything: passwords, 2FA, phone, recovery emails, backup codes, etc.
I tried all methods but hit dead ends trying to recover them. Thankfully, my Discord wasn’t connected, so I alerted everyone I knew there. I also had an alternate account, @JLCmapping, managed by a friend, which I used to immediately inform @/TeamYouTube about the situation
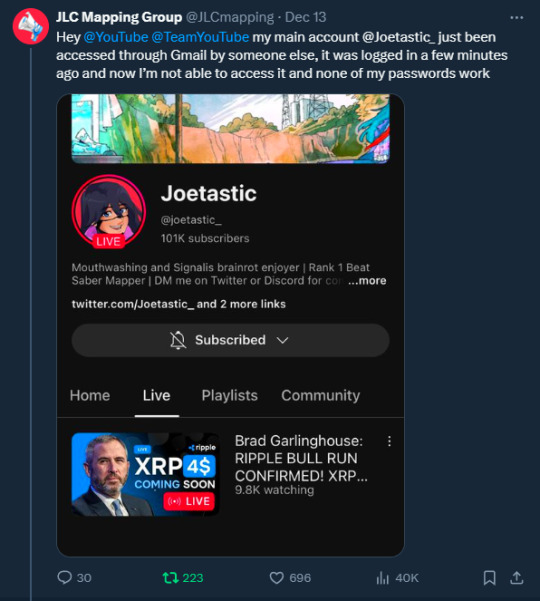
Meanwhile, the hackers turned my YouTube channel into a crypto channel and used my Twitter account to spam hundreds of messages, trying to use my image and reputation to scam more victims
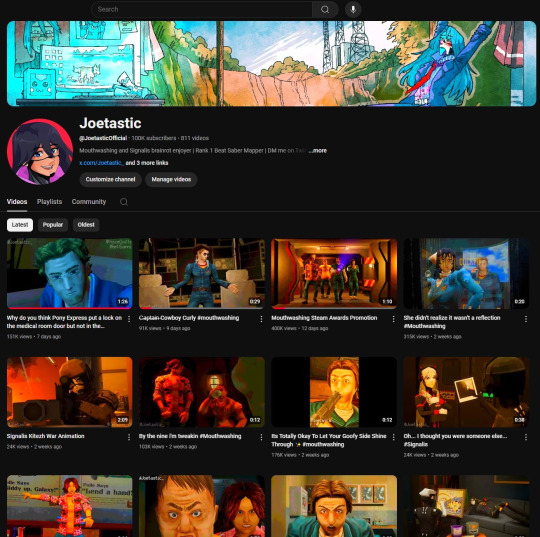
Thankfully, YouTube responded quickly and terminated the channel. Within 48 hours, they locked the hacker out of my Gmail and restored my access. They also helped me recover my channel, which has been renamed to JoetasticOfficial since Joetastic_ was no longer available.
Since then, I’ve taken several steps to secure my accounts and prevent this from happening again. This has been a wake-up call to me, and now I am more cautious around people online. I hope sharing it helps others avoid falling victim to similar attacks. (End)
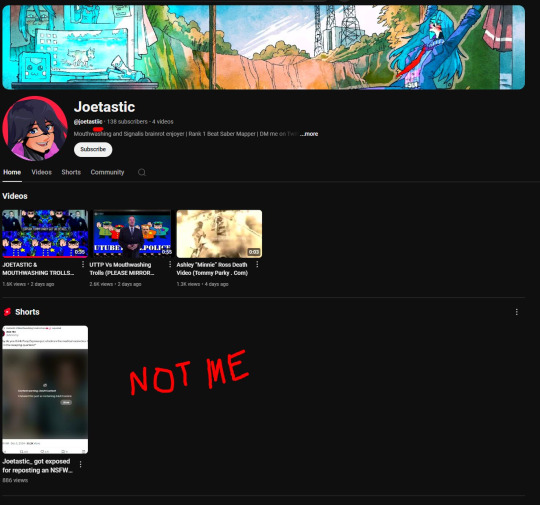
(side note) Around this time, people also started to impersonate me on TikTok and YouTube. With my accounts terminated, anyone searching for "Joetastic" would only find the imposter's profiles. I’m unsure whether they are connected or if it’s just an unfortunate coincidence, but it made the situation even more stressful.
3K notes
·
View notes
Text
[ DoJ, Pentagon, & Oregon Hit By Cyberattack ]
#department of justice#pentagon#oregon#russia#Russian hacker#no russian#Clinton emails#MOVEit#progress software#cyber attack#data breach#FBI#cyber security#emails#Army#Air Force#shell#BBC#British Airways#John Hopkins#university of georgia#Energy Department#Gen Digital#ransomware
0 notes
Text
Email Marketing Hacks To Pump Up Your Open Rate 🔥
Hey there 👋 Ready for a journey into the world of Cold Email sorcery? 🧙♂️✉️ Get ready for mind-blowing insights that'll skyrocket your campaigns. 🚀
1️⃣ **The Art of Subject Lines:** Craft 'em like poetry! 📜✨ Did you know, 47% of email recipients open emails based on the subject line alone? 🤯 Unleash your creativity; make 'em curious, make 'em click! 🧐🔥
2️⃣ **Timing is Everything:** It's not just about what you say but when you say it. 🕒⚡ Did you know, emails sent on Tuesdays have the highest open rates? 📅 Experiment with timing; catch your audience when they're most receptive! 🎯
3️⃣ **Personalization Power:** 91% of consumers are more likely to engage with personalized content. 🤝 Dive into data, personalize like a pro, and watch your response rates soar! 🚀📈
4️⃣ **A/B Testing Alchemy:** Ever tried mixing potions to see which one's more potent? 🧪✨ A/B testing is your secret weapon! 🔬 Test different elements - from subject lines to CTAs - and optimize for maximum impact! 📊💡
5️⃣ **The Sneaky Preview Text Trick:** Sneak peek into email magic! 👀✉️ Crafting a killer preview text boosts open rates by 5-10%. 🚪💥 Don't neglect this tiny yet powerful detail; it's your golden ticket to engagement! 🌈🎟️
6️⃣ **Segmentation Spells:** One size fits none! 🚫👥 Did you know, segmented campaigns get 14.31% higher open rates? 🔍📊 Segment your audience, send tailored messages, and watch your conversion wizardry unfold! 🪄✨
7️⃣ **The Power of Storytelling:** Who doesn't love a good tale? 📖✨ Emails with stories resonate better! 🌟 Create a narrative, connect emotionally, and turn your audience into raving fans! 🚀👏
8️⃣ **Responsive Design Enchantment:** Mobile users rule! 📱💪 Over 70% of emails are opened on mobile devices. 🌐💼 Craft responsive designs for a seamless experience; don't lose your mobile audience! 🌈🚀
9️⃣ **Unsubscribe Optics:** Turn lemons into lemonade! 🍋🥤 Did you know, a clear unsubscribe option boosts trust? 🤝 Make it easy, and use the data wisely. Learn from those who leave, and refine your approach! 🔄🌐
🚀 Like, share, and comment with your favorite email sorcery tip! Let's build a community of email wizards! 🌐💬
This is just the tip of the iceberg. Want the ultimate guide to conquer email marketing? 📬💡
Dive into my Email Campaigns Guide for a deep dive into the art of enchanting inboxes! 🚀📩
#DigitalMarketingGurus #coldemailmarketing #emailmarketing #emailmarketingcampaigns #emailcapmaigns #emailmarketingstrategy #emailcopy #emailcopywriter #emailcopywriting #emaillist #listbuilding #emailistbuilding #mailinglist #openrate #clickrate #roi #boostyouropenrate #emaillistsegmentation #emailsegmentation #emailpersonalization #affiliatemarketing #emailmarketer #emailmarketingguide #emailmarketingtips #emailmarketingexpert #emailmarketingagency #seo #internetmarketing #onlinemarketing #digitalmarketing #contentmarketing #leadgeneration #leadmagnet #emailmarketingtools #emailmarketingsoftware #emailautomation #autoresponder #makemoneyonline #workfromhome #homebusiness #onlinebusiness #earnmoneyonline
#work from home#affiliate marketing#make money online#home business#make money with affiliate marketing#online marketing#online business#digital marketing#blogger#marketing#email security#email#emailmarketing#emails i can't send#email list#email marketing#email marketing software#email newsletter#mailing list#mailing services
1 note
·
View note
Text
Lead management is the second critical aspect for any business while first is the lead generation. As this decides the fate of your business, leveraging the right tools is mandatory to optimize your lead generation process.
To greatly deal with marketing and sales processes, several clients prefer to go with Custom Outlook Add-in development.
In this blog, we will look at the eleven best Outlook add-ins designed to revolutionize your lead generation approach and take your business to the next level. From simplifying contact management to improving email tracking and seamlessly integrating with CRM systems, these add-ins will transform the way you handle and nurture your leads.
Let's explore the perfect combination of Outlook add-ins to supercharge your lead management efforts.
#Office 365 Add-ins development#Add-ons for Office 365#cyber security tools used in businesses#cyber security tools for email#data security#top cyber security tools for business#Add-in development#Outlook Add-ons#Add-ons for Outlook#Outlook Add-ins#software development company#asp.net development#software development
0 notes
Text
Every complex ecosystem has parasites

I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me at NEW ZEALAND'S UNITY BOOKS in AUCKLAND on May 2, and in WELLINGTON on May 3. More tour dates (Pittsburgh, PDX, London, Manchester) here.

Patrick "patio11" McKenzie is a fantastic explainer, the kind of person who breaks topics down in ways that stay with you, and creep into your understanding of other subjects, too. Take his 2022 essay, "The optimal amount of fraud is non-zero":
https://www.bitsaboutmoney.com/archive/optimal-amount-of-fraud/
It's a very well-argued piece, and here's the nut of it:
The marginal return of permitting fraud against you is plausibly greater than zero, and therefore, you should welcome greater than zero fraud.
In other words, if you allow some fraud, you will also allow through a lot of non-fraudulent business that would otherwise trip your fraud meter. Or, put it another way, the only way to prevent all fraud is to chase away a large proportion of your customers, whose transactions are in some way abnormal or unexpected.
Another great explainer is Bruce Schneier, the security expert. In the wake of 9/11, lots of pundits (and senior government officials) ran around saying, "No price is too high to prevent another terrorist attack on our aviation system." Schneier had a foolproof way of shutting these fools up: "Fine, just ground all civilian aircraft, forever." Turns out, there is a price that's too high to pay for preventing air-terrorism.
Latent in these two statements is the idea that the most secure systems are simple, and while simplicity is a fine goal to strive for, we should always keep in mind the maxim attributed to Einstein, "Everything should be made as simple as possible, but not simpler." That is to say, some things are just complicated.
20 years ago, my friend Kathryn Myronuk and I were talking about the spam wars, which were raging at the time. The spam wars were caused by the complexity of email: as a protocol (rather than a product), email is heterogenuous. There are lots of different kinds of email servers and clients, and many different ways of creating and rendering an email. All this flexibility makes email really popular, and it also means that users have a wide variety of use-cases for it. As a result, identifying spam is really hard. There's no reliable automated way of telling whether an email is spam or not – you can't just block a given server, or anyone using a kind of server software, or email client. You can't choose words or phrases to block and only block spam.
Many solutions were proposed to this at the height of the spam wars, and they all sucked, because they all assumed that the way the proposer used email was somehow typical, thus we could safely build a system to block things that were very different from this "typical" use and not catch too many dolphins in our tuna nets:
https://craphound.com/spamsolutions.txt
So Kathryn and I were talking about this, and she said, "Yeah, all complex ecosystems have parasites." I was thunderstruck. The phrase entered my head and never left. I even gave a major speech with that title later that year, at the O'Reilly Emerging Technology Conference:
https://craphound.com/complexecosystems.txt
Truly, a certain degree of undesirable activity is the inevitable price you pay once you make something general purpose, generative, and open. Open systems – like the web, or email – succeed because they are so adaptable, which means that all kinds of different people with different needs find ways to make use of them. The undesirable activity in open systems is, well, undesirable, and it's valid and useful to try to minimize it. But minimization isn't the same as elimination. "The optimal amount of fraud is non-zero," because "everything should be made as simple as possible, but not simpler." Complexity is generative, but "all complex ecosystems have parasites."
America is a complex system. It has, for example, a Social Security apparatus that has to serve more than 65 million people. By definition, a cohort of 65 million people will experience 65 one-in-a-million outliers every day. Social Security has to accommodate 65 million variations on the (surprisingly complicated) concept of a "street address":
https://gist.github.com/almereyda/85fa289bfc668777fe3619298bbf0886
It will have to cope with 65 million variations on the absolutely, maddeningly complicated idea of a "name":
https://www.kalzumeus.com/2010/06/17/falsehoods-programmers-believe-about-names/
In cybernetics, we say that a means of regulating a system must be capable of representing as many states as the system itself – that is, if you're building a control box for a thing with five functions, the box needs at least five different settings:
http://pespmc1.vub.ac.be/REQVAR.html
So when we're talking about managing something as complicated as Social Security, we need to build a Social Security Administration that is just as complicated. Anything that complicated is gonna have parasites – once you make something capable of managing the glorious higgeldy piggeldy that is the human experience of names, dates of birth, and addresses, you will necessarily create exploitable failure modes that bad actors can use to steal Social Security. You can build good fraud detection systems (as the SSA has), and you can investigate fraud (as the SSA does), and you can keep this to a manageable number – in the case of the SSA, that number is well below one percent:
https://www.congress.gov/crs_external_products/IF/PDF/IF12948/IF12948.2.pdf
But if you want to reduce Social Security fraud from "a fraction of one percent" to "zero percent," you can either expend a gigantic amount of money (far more than you're losing to fraud) to get a little closer to zero – or you can make Social Security far simpler. For example, you could simply declare that anyone whose life and work history can't fit in a simple database schema is not eligible for Social Security, kick tens of millions of people off the SSI rolls, and cause them to lose their homes and starve on the streets. This isn't merely cruel, it's also very, very expensive, since homelessness costs the system far more than Social Security. The optimum amount of fraud is non-zero.
Conservatives hate complexity. That's why the Trump administration banned all research grants for proposals that contained the word "systemic" (as a person with so-far-local cancer, I sure worry about what happens when and if my lymphoma become systemic). I once described the conservative yearning for "simpler times," as a desire to be a child again. After all, the thing that made your childhood "simpler" wasn't that the world was less complicated – it's that your parents managed that complexity and shielded you from it. There's always been partner abuse, divorce, gender minorities, mental illness, disability, racial discrimination, geopolitical crises, refugees, and class struggle. The only people who don't have to deal with this stuff are (lucky) children.
Complexity is an unavoidable attribute of all complicated processes. Evolution is complicated, so it produces complexity. It's convenient to think about a simplified model of genes in which individual genes produce specific traits, but it turns out genes all influence each other, are influenced in turn by epigenetics, and that developmental factors play a critical role in our outcomes. From eye-color to gender, evolution produces spectra, not binaries. It's ineluctably (and rather gloriously) complicated.
The conservative project to insist that things can be neatly categorized – animal or plant, man or woman, planet or comet – tries to take graceful bimodal curves and simplify them into a few simple straight lines – one or zero (except even the values of the miniature transistors on your computer's many chips are never at "one" or "zero" – they're "one-ish" and "mostly zero").
Like Social Security, fraud in the immigration system is a negligible rounding error. The US immigration system is a baroque, ramified, many-tendriled thing (I have the receipts from the immigration lawyers who helped me get a US visa, a green card, and citizenship to prove it). It is already so overweighted with pitfalls and traps for the unwary that a good immigration lawyer might send you to apply for a visa with 600 pages of documentation (the most I ever presented) just to make sure that every possible requirement is met:
https://www.flickr.com/photos/doctorow/2242342898/in/photolist-zp6PxJ-4q9Aqs-2nVHTZK-2pFKHyf
After my decades of experience with the US immigration system, I am prepared to say that the system is now at a stage where it is experiencing sharply diminishing returns from its anti-fraud systems. The cost of administering all this complexity is high, and the marginal amount of fraud caught by any new hoop the system gins up for migrants to jump through will round to zero.
Which poses a problem for Trump and trumpists: having whipped up a national panic about out of control immigration and open borders, the only way to make the system better at catching the infinitesimal amount of fraud it currently endures is to make the rules simpler, through the blunt-force tactic of simply excluding people who should be allowed in the country. For example, you could ban college kids planning to spend the summer in the US on the grounds that they didn't book all their hotels in advance, because they're planning to go from city to city and wing it:
https://www.newsweek.com/germany-tourists-deported-hotel-maria-lepere-charlotte-pohl-hawaii-2062046
Or you could ban the only research scientist in the world who knows how to interpret the results of the most promising new cancer imaging technology because a border guard was confused about the frog embryos she was transporting (she's been locked up for two months now):
https://www.msn.com/en-us/health/other/horrified-harvard-scientists-ice-arrest-leaves-cancer-researchers-scrambling/ar-AA1DlUt8
Of course, the US has long operated a policy of "anything that confuses a border guard is grounds for being refused entry" but the Trump administration has turned the odd, rare outrage into business-as-usual.
But they can lock up or turn away as many people as they want, and they still won't get the amount of fraud to zero. The US is a complicated place. People have complicated reasons for entering the USA – work, family reunion, leisure, research, study, and more. The only immigration system that doesn't leak a little at the seams is an immigration system that is so simple that it has no seams – a toy immigration system for a trivial country in which so little is going on that everything is going on.
The only garden without weeds is a monoculture under a dome. The only email system without spam is a closed system managed by one company that only allows a carefully vetted cluster of subscribers to communicate with one another. The only species with just two genders is one wherein members who fit somewhere else on the spectrum are banished or killed, a charnel process that never ends because there are always newborns that are outside of the first sigma of the two peaks in the bimodal distribution.
A living system – a real country – is complicated. It's a system, where people do things you'll never understand for perfectly good reasons (and vice versa). To accommodate all that complexity, we need complex systems, and all complex ecosystems have parasites. Yes, you can burn the rainforest to the ground and planting monocrops in straight rows, but then what you have is a farm, not a forest, vulnerable to pests and plagues and fire and flood. Complex systems have parasites, sure, but complex systems are resilient. The optimal level of fraud is never zero, because a system that has been simplified to the point where no fraud can take place within it is a system that is so trivial and brittle as to be useless.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/04/24/hermit-kingdom/#simpler-times
617 notes
·
View notes
Text
or idk even the fact that English is the global imperial language and any perceived failure, no matter how small, to adhere to its grammar or etiquette or social expectations when communicating with others means you can’t secure a shitty job might lead someone to use a software specifically touted as being able to mimic those things. a passionate moral defence of manually writing emails is a position to the right of a keynote speaker at a 1930s eugenics conference
297 notes
·
View notes
Text
Why Mail Backup X works at all levels as a Gmail backup tool
For Gmail backup, we need a tool that makes this process far more easy and judicious in comparison to manual methods. Similarly, a tool should not impose a long stretched learning curve upon users. It should make the best use of available time and resources, so that a PC does not face the brunt of overloaded resources. A tool should be ideal for routine usage, which must be supported by easily customizable settings. When you are installing this tool, or whether you are entering login details or whether you are uploading confidential files, data integrity should never be at stake due to a loopholes-ridden process. Mail Backup X duly fulfills these requirements and thus is considered as a Gmail backup tool that works at all levels.

Utmost efficiency is written all over this Gmail backup application
This tool will work wonders for your email management strategy as it can handle any amount of email data and that too without any system slowdowns or errors. You can backup an entire email account while keeping the folder hierarchy intact and you can also customize backups by choosing ideal settings. You can handpick a backup pattern that suits the context of the situation, and you also have the option to define various backup locations. These customizations can be done with palpable ease as automation is the intrinsic nature of this tool, and this ensures that various vital processes run quietly in the background without disturbing the work being currently done by you. This tool is packed to capacity with much sought after features that make it an ideal pick for Gmail backup.
This Gmail backup and restore tool puts data safety above everything else
To start with, this is a certified tool that is updated after regular intervals. It boasts of advanced features that put data safety above everything else. Every file is enveloped with multiple layers of encryption and you can further beef up this data safety mechanism by bringing password protection into the picture. Your data will not leak into false hands. Google approved login guarantees that your credentials are being entered within an environment of heightened safety. In the area of security this tool excels in every way because those recommended network security protocols are also employed to heighten that sense of safety.
This Gmail backup software has come out triumphant in making complex stuff simple for end users
This tool is a perfect merger of simplicity with sophistication and everything is so easily accessible and executable that it makes Gmail backup convenient for all user categories. Despite being stuffed to brim with latest technological advancements, this tool has braved the storm and has managed to keep things simple to the core. This easily comprehensible tool will not face any resistance from your coworkers or employees as they are not required to be mentally tortured by those long, brooding hours of training to understand its usage. You will also not face any resistance from anyone as this tool has dual compatibility with Windows and Mac. To state the truth, this is among the most adopted email management utilities. You can easily access and execute various advanced settings. This tool delivers results at breakneck pace without impeding the progress of other processes.
Gmail backup that is versatile and flexible
This tool breaks the barriers of limitations and comes to the fore with fully evolved, diverse features that entail email backup, migration, recovery and archiving. You can play around with email backups to best suit your needs by choosing various backup patterns and backup locations. Other fully evolved features of this tool encompass fast data recovery and easy maintenance of email archives in the right order and format. Wondering how to keep yourself in loop about these diverse tasks? It's actually quite simple. A live dashboard and a comprehensive mail viewer will help you to mentally jot down the status of various tasks and browse through a chockablock database of emails with ease.
Other features that present this Gmail backup and restore tool a utility of its own
This Mail Backup X Gmail email backup software provides high degree of data compression which is many times more powerful than other tools and this process is completely safe. No data element will go corrupt or missing. Even the folder hierarchy will find its rightful place in backups. As pointed earlier, this tool has an inbuilt mail viewer, which will assist you in keeping a tab over old and incoming emails. An advanced search window will pave a non-bumpy, short road for quick email search. PDF archiving is one of the star features of this tool. An exclusive FTP server will allow you to share files without any fear of things going haywire. In an nutshell, this tool is a complete solution, and you will no more be left wanting for more.
There's more to this Gmail backup tool than you can fathom
Mirror backups are also available. Users have lavished this tool with praises due to inclusion of the very useful USB snapshot feature. Dual compatibility with Windows and Mac makes this tool an unbeatable combination of telling features. Google approved login will ignite immense trust in you to proceed ahead without any worries. Since this tool falls within a very affordable price packet, users from across the globe have been able to partake in its diversity-embellished technology. Likewise, there are a zillion more reasons to embrace the cutting edge technology of this tool with full warmth.
The perfect way to take a satisfaction-boosting tour across the various nooks and corners of this tool
Start off on the right note by availing the 15 days, free trial of this tool. You will get enough exposure to the cutting edge technologies of this tool, which will prepare you well in advance to enjoy the options galore present in its full version. A real joyride is on the cards which will help you unravel the true meaning of ease of usage, excellence and flawlessness!
#Gmail#Gmail mail#Gmail email#Gmail mailbox#gmail backup#backup gmail#gmail backup software#gmail backup tool#save gmail#secure gmail#mail#mail backup#backup mail
0 notes
Note
Hi! You’re in the LA area, right? I hope you and your family are okay.
Unrelatedly, I ran across a thread on Mastodon about Proton Mail, which I think you’ve talked about before, and was curious what you make of it / how credible it is: https://code4lib.social/@[email protected]/113838748729664639
I'm fine thanks! Worried about some friends but I'm good.
I think that thread is not incorrect, but is also bullshit.
Email protocols do not allow for 100% anonymous communication and never will, when Proton was subpoenaed for user data that ended up with some French climate activists getting prosecuted they were transparent about what was requested and updated their logging rules to store less data. *Starting* from the assumption that protonmail is supposed to be totally secure OR sells itself as totally secure is disingenuous.
The great thing about open source software is that you never have to trust a shithead CEO when they talk about what the software does. I get why people are angry at the CEO (I think the CEO is at least half wrong in that he is claiming that Republicans will challenge monopolies, but he's not wrong about the destructive corporatism of the Democratic party even if he is *in essence* wrong about which party is more likely to gesture in the direction of breaking up tech monopolies) but A) the thread says that proton's software is "opaque" and it just. Literally is not. and B) that thread links to another thread talking about how what proton is selling is trust and nope. They don't have to sell trust; you can see what their software does if you choose to investigate it, there's no need for trust when you can verify. What they're selling is transparency and from where i'm standing they are indeed quite transparent.
God. Imagine thinking that a zero trust service is selling trust.
So I think the argument that "protonmail actually isn't as secure as it claims" is bullshit that people bring up whenever they're mad at the company (whether they have legitimate reasons to be mad at the company or not).
For the record: you should never, ever, EVER treat email as a secret. Nothing you do over email is really secret because *the rules that allow email to function as a service* require at least some very sensitive information to be an open part of the protocol.
The Proton page on end to end encryption is *very* clear that it is the contents of your email messages that are encrypted, not your email as a whole, and in the image they use to illustrate this the parts of your email that *cannot* be made private (sender, recipient, subject line, time sent) are shown unencrypted:

They're not subtle about letting people know this. Nor are they quiet about the fact that replies to encrypted emails are not encrypted by default.
So the thread is *technically* correct in that all the security "holes" described reflect reality, but it's correct like saying "McDonald's says that you can eat their food for every meal and you'll put on ten pounds of muscle but ACTUALLY putting on ten pounds of muscle requires a huge amount of dedication and a very careful diet and a lot of resistance exercise" - like, I guess yeah that's what you have to do to put on ten pounds of muscle but where exactly was McDonald's making that claim? Did they actually make that claim or are general statements like "I'm Lovin' It" being misinterpreted in bad faith by people on the internet who are mad at something a CEO did?
So. Like. Yeah the CEO is being a shithead, the social media team made a pretty bad fuckup by doubling down on his shitheadery, the product still works as described, AND the thread discussing all of that is deeply annoying.
So.
I think this thread actually does a great job of explaining why I've never seen a "hackers for social justice" group that has lasted. This reminds me a LOT of when someone tried to say that you shouldn't use firefox because the former CEO was a homophobe. There are a lot of deeply shitty people who have made important contributions to our tech ecosystem and if we threw the baby out with the bathwater every time Notch from Minecraft ended up being Notch from minecraft you'd lock yourself out of a lot of really important tools. And this isn't the same as "buying harry potter merch funds transphobia" because it literally doesn't; especially with open source tools you can continue using the software and cheerfully hate the CEO because A) fuck that guy and B) what the fuck are you going to do about it, guy, this shit's encrypted.
I don't want to get too deeply into a discussion about what is or is not cancel culture, but what I'm seeing in that thread (and what I see coming up every time someone brings up the "But the French Climate Activists!" thing) is an attempt to prioritize political alignment over real-world utility. It's attempting to cancel a *genuinely useful tool* because someone involved in the development is an asshole.
By all means, don't give protonmail money if the CEO's trump-positive comments make you feel unsafe.
However: What service are you going to use that is as accessible and as secure to ensure that you actually *are* safe? There are alternatives out there. Do they actually do more than proton? Are they easier to use? Are they open source? One of the responses to that thread was "yeah, that dude seems shitty; i'd switch to another service if there was another one that I felt was as secure" and that's pretty much what I think the correct attitude is. (If you really, really still want to switch, Tuta has been the broadly recommended alternative to protonmail for years but at this point Proton has a suite of services that some users would need to replace, not just email)
IDK i think shit like this contributes to a lot of the bad kind of security nihilism where people are like "oh no, things will never be secure and even my scrappy little open source product is headed by an asshole, i may as well use google because everything sucks" when they should have the good kind of nihilism which is like "man, there are a lot of assholes out there and they're never going to stop being assholes; i'd better take proactive steps to act like the people who make tech stuff are assholes and operate from a better base of security at the start"
so the takeaways are:
Proton never claimed that anything but the message contents of your e2e encrypted messages are encrypted; as far as these things go, they do a pretty good job of being both secure and easy to use compared to other offerings.
Yeah the CEO is being kind of a shithead and I'm not a huge fan of that.
If you think the CEO is being a shithead and don't want to give the company your money, don't pay for their services, but the CEO being a shithead doesn't actually mean you can't trust their services; their services are literally built on zero trust, if the CEO literally wanted to hunt you down personally he wouldn't be any more able to decrypt your emails than he was before and he wouldn't be any more likely to respond to a subpoena than he was before (proton does respond to subpoenas when required but not otherwise; they've been compelled to produce more data in the last decade than before because law enforcement finally realized who they needed to yell at - one of the bigger issues here is the Swiss courts being more willing to grant subpoenas to international complainants than they were before)
The reason we don't go see hogwarts movies is because doing so gives JK money and that does actual real world harm; using firefox does not have an impact on Brendan Eich's ability to materially change the world. It is very weird that we're in a place where we're treating *open source encryption software that is simple enough for your grandma to use it* as though it is Orson Scott Card.
Sorry i'm still stuck on people thinking that proton, famously open source, is opaque, and that an encryption service with zero trust architecture is selling trust.
Anyway if you've ever got questions about security/privacy/whatever services privacyguides.org is a very reliable source.
OH I FIGURED OUT WHAT WAS BUGGING ME
There are a bunch of people discussing this talking about how the CEO's social media is what has made them feel unsafe and I'm going to be a dick here and say that facts don't care about your feelings.
The CEO saying stupid shit doesn't actually make you unsafe in a situation like this; if the CEO was a violent transphobe or aggressive racist or horribly misogynist that wouldn't actually make any of the users of the product less safe. That's why the SJ hacker stuff I've seen hasn't had much staying power; I think that groups that focus on making people feel included and welcome and safe to be themself within the group run into really big problems when there's a conflict between people in the group FEELING unsafe because of (genuinely important in many ways) cultural signifiers like political alignment and so in order to accommodate that feeling they end up doing things (like some kinds of collaboration/accountability practices, abandoning useful tools, WAY too much personal transparency and radical vulnerability for people who are doing crime shit) that ACTUALLY make them less safe.
The CEO being a shithead may make you feel bad, but moving to a less secure platform may actually be dangerous. One of these things can have a big impact on your life, and it is not the one that is happening on twitter.
Anyway. Email is inherently insecure and if you want a secure messaging tool use Signal.
If you are doing crime shit don't talk about it on the internet and DEFINITELY don't talk about it in any kind of unencrypted platform.
If you are a French climate activist who would like to not get arrested if Tuta gets a subpoena for data, use the email service in concert with tor and be cautious about senders/receivers and subject lines.
244 notes
·
View notes
Text
shared from Click's subreddit:
Trump actually cheated and there's time for a recount but we need to act NOW!
https://www.reddit.com/r/TheClickOwO/s/KTdyrF1AdD
idk how accurate any of this is but if even some is true I really hope something can be done
(post text is below the cut)
Not enough people are talking about this and there's still time.
Trump did actually cheat and someone compiled all the evidence on twitter: https://x.com/Espaking2/status/1854287198331515005
Edit:
If you don't have twitter, this will show most of the thread but may not have the entire thing: https://threadreaderapp.com/thread/1854287198331515005.html
People are reposting and saving it because from what I saw in the comments, Elon has been deleting any evidence against trump tampering the election.
- Trump said a few weeks back that he didn't need anymore votes, that he had more than enough.
- Trump also said he had a 'trick up his sleeve' to win.
- A bomb scare was called into areas where voting was taking place, so people would flee the areas and not vote.
- Ballot boxes were then set on fire by trump supporters.
-20 MILLION Ballots went missing. People only just got emails today about their ballots going missing, their signatures suddenly not being accepted, or some outright being destroyed if they didn't vote for trump.
- Trump has a long history of lying, cheating, blackmailing and bribing people to get what he wants.
Kamala was in the lead to win but literally after these ballots were lost and after the russian bomb scare, somehow trump ended up with the highest republican vote in over 20+ years.
- Russian software used for rigging elections was found being used.
All of the evidence is in that tweet but I've also saved a copy of everything in case Elon attacks that post too. There's a link to contact the white house and to (politely) demand a refund due to the evidence of trump cheating:
https://www.whitehouse.gov/contact/
Submit directly to the president.
Click the first option, select your reasoning as election security.
State these pieces of information as a paragraph:
-32 fake bomb threats were called into democratic leaning poll places, rendering polls to be closed for at least an hour
- a lot of people reporting their ballots weren't counted for various reasons that are not very sound seeming (signature invalidation, information that vote counter could not have had)
This all occured in swing states (PA, Nevada, Georigia, ETC.)
- This is all too coincidental that these things happen and swing in his favor after months of hinting of foul play
- Directly state that an investigation for tampering/fraud is required, not just a recount
Again, there is not much time, please, please, please make this spread like wildfire, there's still time to do this!
(trigger warning, SA
(trump is not a good person. Aside from a history of the above and dodgy legal activities, he also has a long history of SA towards women and children. Trump is a convicted p*dophile and project 2025 will strip away the rights from anyone who isn't a cis white man.
Please, please, please spread this information, read through the twitter evidence thread and share it. There's still time to demand an investigation but we have to act NOW
308 notes
·
View notes
Text
In the span of just weeks, the U.S. government has experienced what may be the most consequential security breach in its history—not through a sophisticated cyberattack or an act of foreign espionage, but through official orders by a billionaire with a poorly defined government role. And the implications for national security are profound.
First, it was reported that people associated with the newly created Department of Government Efficiency (DOGE) had accessed the U.S. Treasury computer system, giving them the ability to collect data on and potentially control the department’s roughly $5.45 trillion in annual federal payments.
Then, we learned that uncleared DOGE personnel had gained access to classified data from the U.S. Agency for International Development, possibly copying it onto their own systems. Next, the Office of Personnel Management—which holds detailed personal data on millions of federal employees, including those with security clearances—was compromised. After that, Medicaid and Medicare records were compromised.
Meanwhile, only partially redacted names of CIA employees were sent over an unclassified email account. DOGE personnel are also reported to be feeding Education Department data into artificial intelligence software, and they have also started working at the Department of Energy.
This story is moving very fast. On Feb. 8, a federal judge blocked the DOGE team from accessing the Treasury Department systems any further. But given that DOGE workers have already copied data and possibly installed and modified software, it’s unclear how this fixes anything.
In any case, breaches of other critical government systems are likely to follow unless federal employees stand firm on the protocols protecting national security.
The systems that DOGE is accessing are not esoteric pieces of our nation’s infrastructure—they are the sinews of government.
For example, the Treasury Department systems contain the technical blueprints for how the federal government moves money, while the Office of Personnel Management (OPM) network contains information on who and what organizations the government employs and contracts with.
What makes this situation unprecedented isn’t just the scope, but also the method of attack. Foreign adversaries typically spend years attempting to penetrate government systems such as these, using stealth to avoid being seen and carefully hiding any tells or tracks. The Chinese government’s 2015 breach of OPM was a significant U.S. security failure, and it illustrated how personnel data could be used to identify intelligence officers and compromise national security.
In this case, external operators with limited experience and minimal oversight are doing their work in plain sight and under massive public scrutiny: gaining the highest levels of administrative access and making changes to the United States’ most sensitive networks, potentially introducing new security vulnerabilities in the process.
But the most alarming aspect isn’t just the access being granted. It’s the systematic dismantling of security measures that would detect and prevent misuse—including standard incident response protocols, auditing, and change-tracking mechanisms—by removing the career officials in charge of those security measures and replacing them with inexperienced operators.
The Treasury’s computer systems have such an impact on national security that they were designed with the same principle that guides nuclear launch protocols: No single person should have unlimited power. Just as launching a nuclear missile requires two separate officers turning their keys simultaneously, making changes to critical financial systems traditionally requires multiple authorized personnel working in concert.
This approach, known as “separation of duties,” isn’t just bureaucratic red tape; it’s a fundamental security principle as old as banking itself. When your local bank processes a large transfer, it requires two different employees to verify the transaction. When a company issues a major financial report, separate teams must review and approve it. These aren’t just formalities—they’re essential safeguards against corruption and error.
These measures have been bypassed or ignored. It’s as if someone found a way to rob Fort Knox by simply declaring that the new official policy is to fire all the guards and allow unescorted visits to the vault.
The implications for national security are staggering. Sen. Ron Wyden said his office had learned that the attackers gained privileges that allow them to modify core programs in Treasury Department computers that verify federal payments, access encrypted keys that secure financial transactions, and alter audit logs that record system changes. Over at OPM, reports indicate that individuals associated with DOGE connected an unauthorized server into the network. They are also reportedly training AI software on all of this sensitive data.
This is much more critical than the initial unauthorized access. These new servers have unknown capabilities and configurations, and there’s no evidence that this new code has gone through any rigorous security testing protocols. The AIs being trained are certainly not secure enough for this kind of data. All are ideal targets for any adversary, foreign or domestic, also seeking access to federal data.
There’s a reason why every modification—hardware or software—to these systems goes through a complex planning process and includes sophisticated access-control mechanisms. The national security crisis is that these systems are now much more vulnerable to dangerous attacks at the same time that the legitimate system administrators trained to protect them have been locked out.
By modifying core systems, the attackers have not only compromised current operations, but have also left behind vulnerabilities that could be exploited in future attacks—giving adversaries such as Russia and China an unprecedented opportunity. These countries have long targeted these systems. And they don’t just want to gather intelligence—they also want to understand how to disrupt these systems in a crisis.
Now, the technical details of how these systems operate, their security protocols, and their vulnerabilities are now potentially exposed to unknown parties without any of the usual safeguards. Instead of having to breach heavily fortified digital walls, these parties can simply walk through doors that are being propped open—and then erase evidence of their actions.
The security implications span three critical areas.
First, system manipulation: External operators can now modify operations while also altering audit trails that would track their changes. Second, data exposure: Beyond accessing personal information and transaction records, these operators can copy entire system architectures and security configurations—in one case, the technical blueprint of the country’s federal payment infrastructure. Third, and most critically, is the issue of system control: These operators can alter core systems and authentication mechanisms while disabling the very tools designed to detect such changes. This is more than modifying operations; it is modifying the infrastructure that those operations use.
To address these vulnerabilities, three immediate steps are essential. First, unauthorized access must be revoked and proper authentication protocols restored. Next, comprehensive system monitoring and change management must be reinstated—which, given the difficulty of cleaning a compromised system, will likely require a complete system reset. Finally, thorough audits must be conducted of all system changes made during this period.
This is beyond politics—this is a matter of national security. Foreign national intelligence organizations will be quick to take advantage of both the chaos and the new insecurities to steal U.S. data and install backdoors to allow for future access.
Each day of continued unrestricted access makes the eventual recovery more difficult and increases the risk of irreversible damage to these critical systems. While the full impact may take time to assess, these steps represent the minimum necessary actions to begin restoring system integrity and security protocols.
Assuming that anyone in the government still cares.
184 notes
·
View notes