#encryption website
Explore tagged Tumblr posts
Text
all day I’ve been complaining to people because I looked up the third party the place where I study uses to monitor the WiFi for ‘malicious or dangerous activity’ and it’s just plain creepy. Not as in like “I don’t like my searches being looked at but I have to tolerate it” as in “if you disconnect from the WiFi then reconnect to it it scans anything you did while disconnected at home the next time you connect, builds ‘user profiles’ with everything you look up, checks things you type offline, and can access your personal cloud storage”. And all fucking day I’ve been telling people this and they’ve gone ‘haha well I’ve got nothing to hide it can’t be that bad’ and I felt like I was going crazy. Then I got home and told my father and he just said “that sounds like a huge violation of the data protection act” and I felt so relived I wasn’t going crazy for thinking this was bad.
#like no one even seemed to fucking care? surely it’s illegal?#I’m sending them an email to try and get out of it because the website#claims that if you contact them saying you revoke consent they have to drop your device from it#but then I fear my organisation will just re-add me because I signed a contract that said they’d need to monitor#for malicious or inappropriate activity#but that was word for word all it said. I did not sign up for that#and even if I did I’m legally free to revoke that consent#but aghhhhhh why does no one even give a fuck.#like seriously#even things like WhatsApp that should be encrypted are scanned#because they have keyloggers#so the fact it’s encrypted on sending is. nothing.
8 notes
·
View notes
Text
eep
#definitely one of the ways to spend £75#the way they charge £25 for access to your official transcript#and then the way that document is encrypted means it's not accepted by their own postgrad application portal#so you have to google 'unencrypt pdf' and go to some shady website to get a version of your own transcript that will work#oh also i would like it on the record that if i'd had things my way i would've had this submitted weeks ago#but one of my references really left it to the last minute. despite me first asking in early october.
5 notes
·
View notes
Text
How to Secure Your WordPress Login Page from Hackers
[et_pb_section fb_built=”1″ _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_row _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_text _builder_version=”4.27.4″ _module_preset=”default” hover_enabled=”0″ global_colors_info=”{}”…
#brute force attack#brute force attack prevention#cyber-security#cybersecurity#cybersecurity best practices#disable xml-rpc#firewall for wordpress#malware protection#protect wordpress website#secure wordpress hosting#secure wordpress login#secure wp-config file#security#site hacking prevention#SSL encryption#two-factor authentication#web application firewall#web development#Website Builders#Wordpress#wordpress brute force protection#wordpress hosting security#wordpress password security#wordpress security#wordpress security best practices#wordpress security plugins#wordpress security tips
0 notes
Text

#best SSL certificate providers for free#SSL (Secure Sockets Layer)#Importance of SSL certificate for your website#SSL certificate#free SSL certificate providers#best SSL provider#Let's Encrypt#SSL for Free#GoDaddy#GoGetSSL#Bluehost#Website Security Certificate#Free SSL certificate#Liveblack#ssl service provider#ssl certificate providers#top SSL certificate providers
1 note
·
View note
Text
SetupVPN - Lifetime Free VPN
SetupVPN – Lifetime Free VPN is a program that provides access to a free virtual private network (VPN) service. VPNs enhance the security of your internet connection by encrypting the data you exchange, offer greater anonymity by masking your real IP address, and allow you to use an IP address from another location. This is particularly useful for accessing content that is restricted to certain…
#access blocked websites#anonymous browsing#encrypted connection#free VPN#free VPN service#Online Privacy#Secure Browsing#SetupVPN#unblock content#VPN#VPN for streaming#VPN service
0 notes
Text
Improving Website Security for Small Businesses
In 2024, making your website secure is more important than ever. As a small business owner in Australia, keeping your online space safe is crucial. It’s not just about protecting your data and customers. It’s also about building trust and keeping your good name. This article will give you key strategies and tips to make your website more secure. These steps will help protect your business from…
#Cybersecurity Measures for Small Businesses#SSL Encryption for Business Websites#Website Protection Strategies
0 notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
Reliable website hosting is the bedrock of secure financial transactions online. From data encryption to uptime guarantees, it's the key to building trust and ensuring safety in financial operations. #WebsiteHosting #SecureTransactions #Cybersecurity
#Website Hosting#Financial Transactions#Online Security#Data Encryption#Secure Transactions#Cybersecurity#Trustworthiness
1 note
·
View note
Text
youtube
DomainOffices.com - Secure Domain Hosting - Domain Registration - Encrypted Web Hosting
Domain Offices Oversees Security Updates

Support: 24/7/365 Technical Support via Phone, Live Online Chat, and Support Ticket
DomainOffices.com is an International Domain Name Registrar Registering all Global Domain Name Extensions, including Encrypted Web Hosting, Domain Registration, Secure Domain Hosting, Register Domain Name, Secure Web Hosting, Domain Offices, Domain Renewal, DNS System, Virtual Private Server, Semi-Dedicated Server, Dedicated Server, Shared Hosting Plan, Whois Protection, Cheap Domain Hosting, Cheap Web Hosting, Free Domain Name, Reliable Website Hosting, Cloud Web Hosting,and SSL Encryption. Domain Offices offers you the opportunity to host your web sites in one of our five first-class secure data center facilities located in 1) Chicago, USA, 2) Sydney, Australia, 3) London, England, 4) Pori, Finland, and 5) Telepoint in Sofia, Bulgaria. The Steadfast, Chicago data center offers ideal conditions for hosting web sites whose visitors reside in the United States, Canada, or Latin America, and will guarantee you the fastest web page load speed feasible. The US data center facility option is available with all our shared web hosting plans, KVM and OpenVZ-powered VPS servers, semi-dedicated hosting servers and dedicated servers. Simply pick your package and then select the US data center facility from the drop-down menu on the signup form. Domain Offices works with one of the most famous data centers in Australia - SISGroup, which is situated in the Sydney central business district. The data center offers excellent Internet connectivity and perfect conditions for hosting websites whose visitors are physically located in Australia and Oceania. The Australian data center facility will guarantee you the fastest web site load speed possible. This data center option is available with all shared web hosting packages and OpenVZ-powered VPS web hosting packages of ours. Select the plan that you want on the signup form and then select the Australian data center from the pull-down list. If your web site will be targeted at users from the United Kingdom, the rest of Europe or Africa, we offer the perfect solution for you. We partner with top-class data centers situated in 1) London England, 2) Pori Finland, and 3) Telepoint in Sofia, Bulgaria, which offer the highest level of security for your web site and which will guarantee you the fastest web page loading speed possible. You can select the desired data center from the pull-down list on the signup form. This data center option is available with all shared web hosting plans, as well as with all KVM and OpenVZ-powered virtual servers offered on our website. Domain Offices has forged strong partnerships with international data-centers in the United States, Australia, Britain, Finland, and Bulgaria, to provide our clients with secure and reliable web hosting. Shared Hosting Features: -- Free Setup -- Disk Storage: Unlimited with Data Backups -- Domains Hosted: From 1 to Unlimited (Depending on Plan) -- Full Shell/ SSH/ FTP/ SFTP Users: Unlimited -- E-mail Accounts (POP/ IMAP/ Webmail): From 100 – Unlimited (Depending on Plan) -- MySQL 5 Databases: From 5 to Unlimited (Depending on Plan) -- Custom WHOIS Details and Custom DNS Records -- Programming: Perl, PHP5, Java Servlets, Python, Contrab -- One-Click Automatic Software Installers: WordPress, PrestaShop, OpenCart, Joomla, Drupal, Moodle, vTiger, Open-Realty, phpBB, and others -- Multi-lingual Control Panel -- Account Accessibility: Domain Offices Control Panel -- Five Secured Global Data Centers - With Data Backup -- Support: 24/7/365 Technical Support via Phone, Live Online Chat, and Support Ticket -- Guarantee: 99.9% Uptime Guarantee Website: DomainOffices.com Video Link: Domain Offices - Video
DomainOffices.com is an International Domain Name Registrar Registering all Global Domain Name Extensions, including Encrypted Web Hosting, Domain Registration, Secure Domain Hosting, Register Domain Name, Secure Web Hosting, Domain Offices, Domain Renewal, DNS System, Virtual Private Server, Semi-Dedicated Server, Dedicated Server, Shared Hosting Plan, Whois Protection, Cheap Domain Hosting, Cheap Web Hosting, Free Domain Name, Reliable Website Hosting, Cloud Web Hosting, and SSL Encryption.

#Encrypted Web Hosting#Domain Registration#Secure Domain Hosting#Domain Name#Domain Name System (Protocol)#Register Domain Name#Secure Web Hosting#Domain Offices#Domain Renewal#DNS System#Virtual Private Server#Semi-Dedicated Server#Dedicated Server#Shared Hosting Plan#Whois Protection#Domain Name Registrar#Cheap Domain Hosting#Cheap Web Hosting#Free Domain Name#Reliable Website Hosting#Cloud Web Hosting#SSL Encryption#Youtube
1 note
·
View note
Text
Cybersecurity for Shopify: How to Protect Your Online Store in 2025
[et_pb_section fb_built=”1″ _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_row _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_text _builder_version=”4.27.4″ _module_preset=”default” hover_enabled=”0″ global_colors_info=”{}”…
#brute force attack#brute force attack prevention#content management systems#cyber-security#cybersecurity#cybersecurity best practices#limit login attempts#malware protection#React security#security#Shopify#site hacking prevention#SSL encryption#two-factor authentication#web application firewall#website credibility
0 notes
Text
Why Do I Need An SSL Certificate?

If you run a website, you've likely heard of SSL certificates. In fact, they've become as ubiquitous in the online world as social media is in real life. But what is an SSL certificate? How do they work? And why do I need one? Let's get the word out about SSL certificates and why they're important!
What can an SSL certificate do?
The most important thing to realize about SSL certificates is that they are a defense against cyber attacks.
You may have heard the term “hacker” and thought it was someone who was trying to steal your password. While that might be true sometimes, there are other ways in which hackers can use technology to cause damage or compromise your data and company. An SSL certificate will protect you from these kinds of attacks by:
Protecting sensitive data like credit card information and social security numbers.
Protecting against phishing and man-in-the-middle attacks (fraudulent websites).
Protecting against keyloggers or any other software used specifically for stealing information from users (like emails).
Keep hackers away from your website so they can't try their luck at stealing anything else.
Create a site-wide encryption standard.
An SSL certificate is a substantial way to protect your data. It's like the lock on your front door, securing your online home from would-be intruders. With an SSL certificate in place, no one can get into that data—not even hackers!
The bad news is that many people don't know how to use these locks effectively—and they often mistakenly believe that all SSL certificates are created equal. In reality, there are two main types of SSL certificates: domain and wildcard certificates. Each type has its own strengths and weaknesses (as well as price points).
Create a sense of trust among users.
SSL certificates help establish a sense of trust among users. The more confident a user feels, the more likely they will be to complete an online transaction or purchase. In order to increase the likelihood that a user will feel safe, secure, and confident in their online transactions, you should use an SSL certificate on your website.
Types of SSL certificates
SSL certificates are available in multiple types. The type of certificate you choose depends on the level of security and encryption you need, as well as the duration for which you want to secure your site. Here's a breakdown of what each type offers:
Domain validation certificates are the least expensive option and provide basic protection for your website. They're also the fastest to set up and can be issued within minutes once approved. However, they lack strong encryption measures so they're not recommended for e-commerce sites or sites that handle sensitive data like medical records or financial information.
Organization validation certificates are more secure than domain validation because they require proof of ownership from an authorized representative within your company or organization (such as an executive). They are also more expensive than most other options.
Extended validation SSLs offer the highest level of assurance and require more time to process than other forms because they require additional checks before being issued.
There are many reasons why an SSL certificate is essential.
It protects your website against phishing scams and data breaches.
It secures the server that you are using to host your website and all of its files.
The SSL certificate creates a public key, which is used to encrypt and decrypt data sent over the internet between two computers or devices (like a browser). This process uses TLS (Transport Layer Security) technology, which sends information through encrypted channels so that if someone intercepts it, they cannot read it without knowing what the key is. Because of this encryption method, an SSL certificate makes sure that any person browsing on their device with an unsecured connection will not be able to see any sensitive information about you or your business—including credit card numbers, usernames/passwords for social media accounts, etc.—that passes through their computer's connection with your site's servers when they click on links shared from within its content.
Conclusion
The bottom line is that an SSL certificate is a powerful tool for creating trust among your users and establishing a sense of professionalism. You can use SSL certificates to redirect traffic from HTTP to HTTPS, track visitor statistics, or even use them as security keys to encrypt data between your web server and client computers. As you can see, there are many benefits associated with having an SSL certificate installed on your website, so don't wait any longer!
To learn more about how Reversed Out can help secure your WordPress site so that people cannot access personal information stored there without permission (and make sure no hackers get in), contact us!
Contact Us
At Reversed Out Creative, we understand the challenges and opportunities presented by AI disruption. Our team of experts specializes in web design, SEO, graphic design, and digital marketing services. Reach out to us through our contact form to learn more about navigating the evolving job market and embracing the potential of AI. Together, let's shape a future that combines human ingenuity with the power of AI.
Original content source: https://reversedout.com/why-do-i-need-an-ssl-certificate/
#SSL certificate#Secure Sockets Layer#Website security#SSL encryption#HTTPS#SSL benefits#Secure browsing
0 notes
Text
Fifty per cent of web users are running ad blockers. Zero per cent of app users are running ad blockers, because adding a blocker to an app requires that you first remove its encryption, and that’s a felony. (Jay Freeman, the American businessman and engineer, calls this “felony contempt of business-model”.) So when someone in a boardroom says, “Let’s make our ads 20 per cent more obnoxious and get a 2 per cent revenue increase,” no one objects that this might prompt users to google, “How do I block ads?” After all, the answer is, you can’t. Indeed, it’s more likely that someone in that boardroom will say, “Let’s make our ads 100 per cent more obnoxious and get a 10 per cent revenue increase.” (This is why every company wants you to install an app instead of using its website.) There’s no reason that gig workers who are facing algorithmic wage discrimination couldn’t install a counter-app that co-ordinated among all the Uber drivers to reject all jobs unless they reach a certain pay threshold. No reason except felony contempt of business model, the threat that the toolsmiths who built that counter-app would go broke or land in prison, for violating DMCA 1201, the Computer Fraud and Abuse Act, trademark, copyright, patent, contract, trade secrecy, nondisclosure and noncompete or, in other words, “IP law”. IP isn’t just short for intellectual property. It’s a euphemism for “a law that lets me reach beyond the walls of my company and control the conduct of my critics, competitors and customers”. And “app” is just a euphemism for “a web page wrapped in enough IP to make it a felony to mod it, to protect the labour, consumer and privacy rights of its user”.
11K notes
·
View notes
Text
How Do Password Managers Work and Store Your Data?

Passwords. Have we ever experienced so many problems with anything else connected to technology? Most likely not. The most popular method for securing all kinds of data and services is using passwords, but alas, there are many to remember!
Hackers are aware of all the methods we employ to create and remember passwords, and all too frequently, they successfully access our accounts using our weak passwords. Using a password manager can help with some problems associated with passwords.
What is a Password Manager?
The advantage of using such a program is that each website and account can have a different, genuinely random, long password, and you don’t have to remember it—the password manager will keep track of them for you. It can even assist you in avoiding entering your passwords into insecure websites.

Contact best Jewelry Website Development Company in Surat, India to build your Ecommerce Website.
How do Password Managers store your data?
Password managers relieve you of needing to remember multiple codes by storing everything for you. There are different applications that are popular on the market right now, and they all have their own specific style of handling things. But the basic idea is the same.
Your passwords are stored in an encrypted manner, and can only be retrieved by unlocking the encryption. This can be done in various ways, not just by inputting a “master password”. For example, some password managers allow you to unlock them by providing a specific, unique file. Most of the popular password managers on the market also come with other nifty features.
For example, they will usually automatically generate secure passwords for you according to customizable rules. They may also support automatically inputting the password for supported sites.
Why do you need a Password Manager?
A password manager can be a highly useful tool for protecting sensitive corporate information and personal banking logins. A password organizer might be an excellent purchase for people who struggle to manage passwords across numerous websites. These tools manage security by generating secure passwords and keeping them organized, and both individuals and companies can benefit from the security they provide.
Features of a Password Manager
Advanced encryption is the most crucial characteristic to look for in password managers. It is essential. Data security is at the core of password managers; without end-to-end encryption, your data won’t be sufficiently safe.
End-to-end encryption
Advanced encryption is the most crucial characteristic to look for in password managers. It is essential. Data security is at the core of password managers; without end-to-end encryption, your data won’t be sufficiently safe.
Thanks to end-to-end encryption, your data is guaranteed to be unreadable both in transit and at rest. A special authentication key must be supplied for the platform to be able to decode the data. The user is the only one with access to this authentication key thanks to end-to-end encryption.
Multi-Platform Support
For you to access your password vault regardless of the OS you’re using, support for various platforms is essential.
At the very least, a password manager should work on the four most popular operating systems: Android, iOS, Windows, and macOS. A password manager should also offer browser extensions for all major browsers. This makes entering your information on any login page so much simpler.
Secure Password Generator
A password generator should be included with every password management. You need password generators in order to create secure, distinctive passwords, and they are absolutely necessary. You no longer need to keep track of all the advice for creating safe and effective passwords, which significantly reduces workload.
The length of a password generated by a password generator can be changed, and you can even specify whether it should contain special characters, digits, lowercase letters, or capital letters.
Vault Storage Location
You can use password managers to store passwords, notes, and other private information in a vault. Passwords can be kept in the cloud, on your device, or locally by a password manager.
Even though keeping your password on a gadget is alluring, there are drawbacks. The biggest drawback is that you can’t get your passwords back if you lose your device.
You must manually sync passwords between devices if you store your data in an on-device vault. Automatic syncing is crucial at a time when individuals use many gadgets for various purposes.
Security
Security is crucial because you’ll be storing login information for your accounts, including vital platforms like banks. Fortunately, password managers use a variety of encryption algorithms to protect your data from hackers.
Some password managers store passwords and other personal information using a zero-knowledge storage technique, ensuring only you have access to your credentials. By using this method, you may prevent a password manager from accessing the credentials kept in your vault.
Multi-factor authentication (MFA)
While we’re talking security, let’s talk about MFA. Users must log in with MFA and a secondary authentication mechanism in addition to their password. This guarantees that a user’s account will probably stay secure even if their master password is stolen.
A one-time password or a special code issued by an authentication app could be used as the secondary authentication method. The user’s personal device, such as their mobile phone or personal email account, is typically connected to these supplementary means.
Are Password Managers safe?
You might be hesitant to entrust a program or application with your master password and other sensitive data. Can’t app developers also be hacked?
Password managers can be compromised, is the short response. Cybercriminals may gain access, but it does not guarantee they will obtain your master password or any other personal data. Your password manager encrypts the data it stores. And it’s nearly impossible to crack such encryption, which is typically an industry standard like Advanced Encryption Standard (AES).
Additionally, your master password and the encrypted data in your password database are neither stored nor accessible by the majority of password managers.
Your one master password’s strength and security determine a lot of the security of your password manager. Additionally, many password management services do not keep the master password on the same server as your encrypted data. This increases security by yet another level.
Advantages of using Password Managers
One password for everything: The best and most desirable feature is that you only need to remember one password for all of your online accounts, rather than having to remember tens or even hundreds.
Automatically generated passwords: Is it difficult to develop fresh, original passwords? Some people might even attempt to generate a new password by pressing random keys on their keyboard, but this still results in a pattern because of how the keys are organized. One of the numerous advantages of a password manager is that they may generate passwords for you automatically in addition to storing all of your passwords.
Greater Security: When compared to alternative options, password managers offer greater security. For instance, passwords written down on paper or saved in a computer document run the danger of being discovered by unauthorized parties.
Can be disclosed to a reliable person: If you find yourself unable to access your accounts on your own, an online password manager can save your life. An online password manager can save your loved ones or the person in charge of your accounts a lot of time and anguish, for instance, if you become handicapped due to an illness or injury or if you die away.
Disadvantages of using Password Managers
Single sign-on has disadvantages: Since you only need one password to access all of your sensitive login information, there is a chance that you or your password manager might be hacked, compromising all of your accounts and putting you at risk for serious identity fraud. Make sure you use multi-factor authentication on your password manager to help prevent this.
A single point of failure: It would be a tragedy to lose access to the password manager after committing to organize and secure all of your passwords. With just one complicated password to remember, perhaps you won’t run into any problems, but if you do, you’re out of luck.
There is a learning curve: Changing all of your passwords will take some time, and you will need to rediscover how to access your accounts. Many online password managers have browser plugins that simplify the procedure.
Conclusion
So, unless you’re some encryption genius, a walking random number/letter/symbol generator, or a human supercomputer with the ability to retain complicated chunks of data and information permanently, it’s time to get a password manager.
#password manager#password security#data storage#data security#data#encryption#software#ecommerce website development#technology#web developers#password
0 notes
Text
Near ने एंड-टू-एंड एन्क्रिपशन के लिए Nym का किया यूज - HI
Near ने इकोसिस्टम के लिए एंड-टू-एंड एन्क्रिपशन और Metadata प्राइवेसी सर्विसेज प्रोवाइड करने के लिए Blockchain सिक्योरिटी फर्म Nym का इस्तेमाल किया है।
Near
#Near#Nym#Blockchain#Near uses Nym for end-to-end encryption#latest news on cryptocurrency#latest crypto news#top cryptocurrency news websites#latest news about cryptocurrency#cryptocurrency news today
0 notes
Text
Sometimes I still see extremely rabid anti 4chan sentiment on here being reblogged everywhere as if 4chan is any worse than Tumblr can be if you get on the wrong side of it. I literally got recommended a blog today completely focused on antisemitic conspiracy because they posted something tagged animal behavior which is a tag I follow. It's so easy to find the same content you hate here. If you're so gd focused on how everything on there is fucked up you need to go to 6chan or god forbid masterchan and see what actual depravity is.
"everything on 4chan is racist/transphobic/ other"
Wow I didn't know SCP 973 was racist. We gotta scrap the entire Foundation.
#ri rambles#4chan#DO NOT ACTUALLY DO THAT LAST PART ESPECIALLY IF YOU'RE A MINOR#i have not personally been there but let me just say that on masterchan there is literally no banning. at all. completely anonymous.#they apparently even encrypt your ip. no one can be banned or caught there even if the website owner wantwd#if you think nothing ever can come out of 4chan thats good but like a lot of classic creepypasta i have some News
0 notes
Text
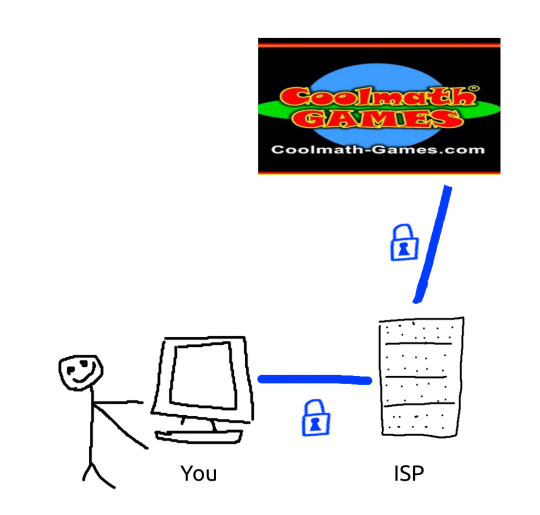
VPNs do not make you more secure
here's how they work!
first of all, most of your internet traffic is already encrypted via TLS (Transport Layer Security). Things that aren't encrypted are usually videogames or less important applications.
a VPN encrypts traffic between your computer and the VPN server you're using.
your Internet Service Provider (ISP) sits in the middle of that transaction.
cue the MS paint diagram
Without a VPN:
With a VPN:
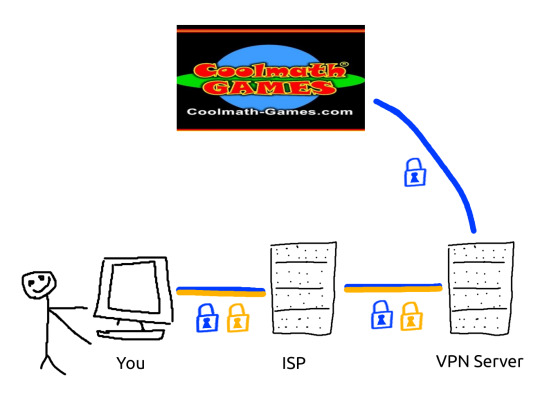
the traffic between your VPN server and the rest of the internet is not encrypted any further.
things that VPNs are good for:
bypassing geo-blocking
bypassing website blocks set up by your ISP
obscuring network traffic from your ISP
things that VPNs are not good for:
browsing the internet without having your activity logged. every company that gives internet service logs the activity, it's half of how they make sure they're not being hacked.
hiding information from the government. VPN providers WILL bend to subpoenas, they WILL turn over logs of your network activity.
cybersecurity. VPNs can't save you once the traffic is between them and the final destination. they don't analyze your traffic to detect and stop hackers, they don't add any encryption where it matters.
VPNs are not a shortcut to security. you cannot pay 15 dollars a month to forgo all responsibility for your own digital privacy. do your research, use a password manager, stay safe.
my friends i hope you find this information useful. you have been sold a lie. remember to show extreme skepticism to youtube sponsorships and journalism websites which sing their praises.
sources: i have a certificate iv in cybersecurity
2K notes
·
View notes