#enterprise software testing
Explore tagged Tumblr posts
Text
9 Reasons Why Enterprise Testing Fails You

Competition creates pressure. Today, teams are under enormous pressure to deliver releases with increased speed and quality.
According to GitLab’s research, nearly 60% of survey respondents said their organizations deploy multiple times a day, once a day, or once every few days. Just 11% said they deploy once a month and only 8% said every few months. This highlights how important it is to be agile — both in development and testing.
Top reasons why Enterprise testing fails
Yesterday’s software testing practices can’t keep up with the pace of development and changing business priorities today. Most companies fail to recognize the constantly evolving testing landscape, and the required steps to overcome it.

Lack of Testing due to Unrealistic Time Expectations
Development teams manage, enhance and validate applications in a short sprinted Agile framework and release them to the end users with limited regression testing. This lack of testing translates to a False sense of Quality — thereby a failure to deliver the fanatical experience they promise.
Regression testing plays a crucial role in achieving a stable version of the software by finding defects before production deployment.
Pro Tip: With its 3 types of regression testing services, Webomates CQ is really quick in initiating the regression in just 3 minutes based on the regression type, platforms, and the target environment selected.
Outdated Test Cases & Suite
The number of changes in the testing code is proportional to the changes made by the developer in the application. It is very difficult to identify which test cases should be modified or added.
You need Self-healing scripts that help in test script maintenance by automatically detecting and resolving issues that arise during the execution of test scripts.
Pro Tip: Webomates CQ provides patented AiHealing which is carried out during the software regression cycle within the 24-hour or 8-hour window.
Lack of Exploratory Testing
As test case-based testing follows a predefined script, there are chances that a bug may not fall in the script’s scope. To overcome this challenge, you need Exploratory testing using a rotating vector-based approach that pushes the envelope in each regression looking to find new defects in the software release that are outside of the defined test cases.
Pro Tip: Webomates leverages the strengths of exploratory testing on top of test cases in regression testing to expand the scope of the test and take the quality to the next level.
Enormous Amount of Time Lost in Defect Triaging
Defects are bound to be detected while boosting feature velocity, but the key is to find them early before production. The best way to achieve this is by setting up a proper tracking system that can identify defects at the right time (as early as possible), triage them, and report them to the concerned stakeholders to improve the quality process.
Pro Tip: Webomates Defect Triaging feature shares a comprehensive triaged defect report that includes defect summary, steps for replicating the defect, a video of actual bug instances, priority suggestions, and test cases mapped with the defect.
Not Embracing Shift-Left Testing
The cost of fixing a defect rises exponentially as you move closer to production, along with compromised user experience, functionality, and security. One way to mitigate risks and eliminate surprises is by performing Shift-Left testing — where UI, API, load, and security testing are done early on rather than towards the end of application development.
Pro Tip: This makes it a lot easier to identify and fix the defects in the staging environment itself, enabling faster, better, and quality applications.
Engage in Test Automation
Focusing on manual testing can slow down the testing process and lead to inconsistent test execution, mainly when dealing with repetitive tasks or large-scale testing requirements. With test automation, developers and testers can automate the entire build-to-test process across all the stages of software development.
Pro Tip: In this DevOps-driven landscape, it is highly recommended to adopt test automation in order to avail maximum benefit. AI-based test automation includes UI Testing, API Testing, along with non-functional testing.
Poor and Insufficient Test Data
The biggest challenge for ensuring an excellent testing process and reliability is the lack of diverse and quality test data. Test data is the generation of data that comes as close as possible to your production data without revealing any sensitive information — all guided by artificial intelligence and analytics.
Pro Tip: Use Generative AI to prepare extensive data sets including edge cases, thereby accelerating testing phases and enhancing overall efficiency. Additionally, you can also use Predictive analysis to create realistic test data by analyzing the existing data patterns.
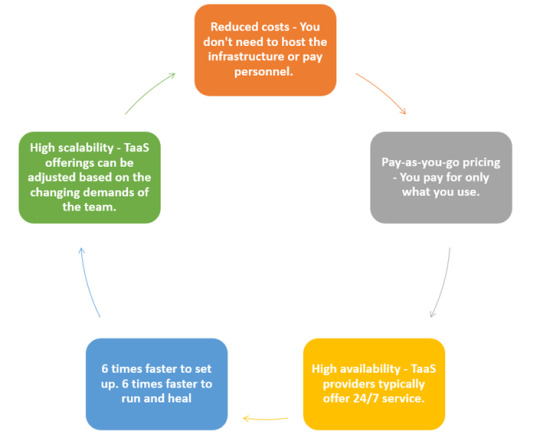
Lack of Cloud Infrastructure Adoption
Managing IT infrastructure involves manual, complex, and mundane processes like setting up the servers, configuring them, deploying the applications, and managing the load whenever required. Lack of cloud infrastructure adoption can restrict scalability, flexibility, and cost-effectiveness, making it more difficult to build and maintain reliable testing environments.
Today, the cloud is a catalyst for any company’s growth. Products are now moving to the cloud, and so is Testing. Testing as a Service (TaaS) — also known as On-Demand testing service — helps you scale with agility and overcome the typical traditional testing bottlenecks.
Pro-Tip: Webomates — a cloud-based testing platform, is powered by a range of patented AI-infused tools. Take a look at this animation and know the three easy steps you can take to AI automate your application.
Inability to make intelligent and improved decisions
If you are a manager or part of the C-suite executives, you need data-driven insights that can help you make intelligent decisions. With a focus on solving critical business problems, test insights and analytics that help you improve product quality and effectiveness.
Pro-Tip: Use test insights into the entire CI/CD pipeline to understand the impact every change is having on the product. It also provides guidance and strategic benefits to test management.
Testing for the Future: How can Webomates Help?
User expectations are rising, and you need intelligent solutions to assist you in dealing with these challenges. You need to modernize the company with technology that promotes creativity and innovation, improves customer experiences, and equips the employees with the knowledge and tools necessary to make informed business decisions.
Identifying the gaps is the first step in moving forward. The next step is to create a plan and choose a service/tool that can assist you in bridging all of these gaps. AI-based testing helps to predict the best testing approach, anticipate and prevent mistakes, and enable the pace and scope of software releases.
Webomates is a complete Testing as a Service (TaaS) provider. Its cloud-native platform helps teams overcome the complexities of testing applications built using advanced technologies and perform both functional and non-functional tests.
If you are interested in learning more about Webomates CQ service please click here and schedule a demo, or reach out to us at [email protected]
#enterprise software testing#Enterprise Testing Strategy#Software Testing#Test Automation#testing enterprise software
1 note
·
View note
Text
Enterprise Resource Management: Essential Software Testing Services

Enterprise Resource Management (ERM) software is the backbone of modern business operations, ensuring that all aspects of an organization work in harmony. To maximize the effectiveness of ERM software, thorough software testing services are essential. Here's how to approach it:
1. Importance of Software Testing in ERM
Software testing ensures that all ERM modules function correctly, avoiding disruptions in critical business processes.
2. Key Areas to Focus On
Functionality Testing: Validate that each module performs its intended function.
Performance Testing: Ensure the system can handle expected loads without lag.
Security Testing: Protect sensitive business data from potential breaches.
Integration Testing: Confirm that the ERM integrates smoothly with other enterprise systems.
3. Common Challenges
Software testing in ERM can be complex due to the interdependencies between different modules. It's crucial to adopt a comprehensive testing strategy that covers all bases.
4. Tools and Technologies
Utilize advanced testing tools like Selenium, JIRA, and LoadRunner to automate testing processes and improve accuracy.
5. Best Practices
Regularly update test cases to reflect changes in the software.
Involve end-users in the testing process to gather practical feedback.
Conduct both manual and automated tests for thorough coverage.
6. Case Studies
Successful ERM implementations highlight the role of rigorous testing in preventing system failures and enhancing overall performance.
7. Final Thoughts
Implementing robust software testing services in your ERM project ensures smooth operations and long-term success. Ensure that your ERM software not only meets current business needs but is also scalable for future growth.
2 notes
·
View notes
Text
Best Software Development Trends to Follow in 2024
Explore the best software development trends for 2024, including AI, low-code solutions, and cybersecurity, to elevate your business and stay competitive.
As we step into 2024, the software improvement panorama continues to conform swiftly, shaped by using technological improvements, changing person expectations, and rising enterprise needs. Staying ahead of these traits is critical for organizations aiming to remain aggressive and progressive. In this blog, we’ll explore the fine software development tendencies to comply with in 2024, specializing…
#Agile Development#ai#App Development#Cloud Computing#Custom Software#Cybersecurity#devops#Edge Computing#Enterprise Software#IoT#Low Code#Machine Learning#No Code#Product Testing#Software Development#Sustainability#UIUX Design#Web Development
0 notes
Text
Why SaaS Reviews Are Crucial
If you’re running a SaaS business, then a review website should be a crucial part of your SaaS marketing strategy.
Online reviews are critical. If you find yourself neglecting this fact, just remember that around 93% of consumers claim that reviews they found on the internet influenced their decision to buy something. It’s also interesting to note that over 90% of consumers aged 18-34 say that they trust online reviews just as much as personal recommendations. These numbers show that online reviews are essential for a SaaS product.
#SaaS Reviews#Customer Feedback#Software As A Service#User Experience#Customer Experience#Tech Reviews#Product Feedback#Digital Transformation#Software Reviews#business software#Cloud Computing#Saas Products#Customer Success#TechIndustry#Product Reviews#Software Testing#Saas Solutions#Enterprise Software#TechInnovation#Customer Support
0 notes
Text
Zymr's Enterprise Software Development services offer customized solutions that seamlessly support your business infrastructure. Gain a competitive edge leveraging your trusted software development services company.
#software development#enterprise software development#qa automation#qa testing#qa automation services
0 notes
Text
Enhance Your Software's Performance with Expert Software Testing Services

In today's digital era, software has become an integral part of our lives. Whether it's for business operations or personal use, software applications play a crucial role in delivering efficient solutions. However, the success of any software product depends on its performance, reliability, and usability. This is where software testing services come into the picture. By thoroughly evaluating the software's functionality, performance, and security, professional testing services ensure that your software meets the highest standards of quality. In this blog, we will explore the importance of software testing services and discuss how V2Soft, a leading software testing services company, can help you achieve optimal results.
The Significance of Software Testing Services:
Software testing services are crucial for a variety of reasons:
Ensuring Quality: Testing services are designed to identify defects, bugs, and other issues that can affect the performance of your software. By conducting comprehensive tests, including functional testing, regression testing, performance testing, and security testing, experts can help you deliver a reliable and high-quality product.
Enhancing User Experience: User experience is a key factor in the success of any software. By conducting usability testing and user acceptance testing, software testing services ensure that your software is intuitive, user-friendly, and meets the expectations of your target audience.
Mitigating Risks: Software testing services help identify potential risks and vulnerabilities, such as security loopholes or data breaches. By addressing these issues early on, you can significantly reduce the risk of financial loss, reputational damage, or legal complications.
Cost and Time Efficiency: By investing in software testing services, you can save time and money in the long run. Detecting and fixing issues during the development phase is far more cost-effective than dealing with them post-release. Additionally, by outsourcing testing services, you can leverage the expertise of professionals while focusing on your core business activities.
V2Soft: Your Trusted Software Testing Partner:
When it comes to software testing services, V2Soft is a name you can rely on. As a leading software testing services company, V2Soft offers a comprehensive range of testing solutions tailored to meet your unique needs. Here's why V2Soft stands out:
Expertise and Experience: With over two decades of experience in the IT industry, V2Soft has a team of highly skilled and certified software testers. Their expertise spans various domains, technologies, and testing methodologies, ensuring that your software is thoroughly tested.
Comprehensive Testing Approach: V2Soft adopts a holistic approach to testing, covering all aspects of software quality. From functional and non-functional testing to performance, security, and compatibility testing, their services encompass the entire software testing lifecycle.
Automation and Tools: V2Soft leverages advanced testing tools and automation frameworks to streamline the testing process and improve efficiency. This allows for faster testing cycles, accurate results, and enhanced test coverage.
Customized Solutions: Every software project is unique, and V2Soft understands this. They work closely with their clients to understand their specific requirements and tailor their testing services accordingly. This ensures that your software is tested comprehensively and meets the desired quality standards.
Cloud Testing: Discover how V2Soft can help you streamline your testing processes with our cutting-edge solutions. Our expert team ensures seamless integration, scalability, and reliability for your cloud-based applications. Get reliable and efficient Cloud Testing services with V2Soft today.
Conclusion:
In a highly competitive digital landscape, delivering a high-quality software product is paramount. Software testing services provided by companies like V2Soft can significantly enhance your software's performance, reliability, and user experience. By outsourcing testing tasks to experts, you can mitigate risks, save time and money, and ensure that your software meets the highest standards of quality. So, make the smart choice and partner with a trusted software testing services company to unlock the full potential of your software.
#manufacturing application testing services#web testing services#enterprise software testing services#ai testing services#it software testing services
0 notes
Text
As someone who works in the reliability sector of IT I cannot emphasize how much you have to give 0 fucks about professional standards and best practices in order to do something like what Crowdstrike did.
At the company I work for, which you have definitely heard of, there are thousands of people (including me, hi) part of whose job it is to sit in rooms for literal hours every week with the people building new features and updating our software and ask them every question we can possibly think of about how their changes might impact the overall system and what potential risks there are. We brainstorm how to minimize those risks, impose requirements on the developers, and ultimately the buck stops with us. Some things are just too risky.
Many of the practices developed at this and other companies are now in wide use across the industry, including things like staggered rollouts (i.e. only 1/3 people get this update at first, then 2/3, then everyone) and multi-stage testing (push it to a fake system we set up for these purposes, see what it does).
In cases where you’re updating firmware or an os, there are physical test devices you need to update and verify that everything behaves as expected. If you really care about your customers you’ll hand the device to someone who works on a different system altogether and tell them to do their worst.
The bottom line here is that if Crowdstrike were following anything even resembling industry best practices there should have been about twenty failsafes between a kernel bug and a global update that bricked basically every enterprise machine in the world. This is like finding out the virus lab has a direct HVAC connection to the big conference room. There is genuinely no excuse for this kind of professional incompetence.
1K notes
·
View notes
Text
oh man this crowdstrike fiasco lol. for non-software people following this, the issue isn't that machines were updating automatically (because for enterprise security software, that's pretty normal), the issue is that they rolled this out to every single destination machine at the same time (rather than a "staged" rollout where you hit a small group of users at first to see how things go), apparently without doing the bare minimum of testing or quality control, on a FRIDAY
#cracking up because their official blog post about the outage has a free trial CTA at the bottom#which I'm sure is part of their blog template for all pages but still. read the room fellas
181 notes
·
View notes
Text
AU Space Shuttle Enterprise
Circa 1985 to 1987
From my Alternative History Post (link) this is how the Space Shuttle Enterprise evolved from the 4th operational orbiter in 1985 to the prototype unmanned shuttle.
More History on the Shuttle:
• April 1983: Enterprise is returned to Palmdale for her disassembled and rebuild.
• As a weight saving measure her mid-fuselage is returned to Convair for a complete rebuild to bring it inline with OV-103 and OV-104.
• to further lighten her frame, her aft-fuselage is rebuilt with similar materials as her sisters.
• Engineers at Rockwell suggests rebuilding or replacing her wings as well but NASA doesn't have room in the budget.
• May 1985: at long last, Enterprise is rolled out and joins the fleet. She weighs slightly less than Columbia. Her main issue is her wings are heavier and weaker than the other Orbiters.
• September 1985: STS-21 is Enterprise's first mission
• 1987: During the Shuttle hiatus following the Challenger Disaster, she went through a mini refit that saw her exterior markings change. (NASA in this timeline returned to the Meatball logo sooner than in the OTL)
Circa 1988 to 1993
• April 1988: STS-30 is Enterprise's first launch following the hiatus.
• December 1993: following STS-61, Enterprise is retired due to being the oldest in the fleet. Endeavour takes her place in the fleet.
• June 1994: Enterprise is flown to Dulles Airport, Washington DC, and is given to the Smithsonian for eventual display when the Steven F. Udvar-Hazy Center is built. NASA retains the option recalled her if needed.
• 1998: NASA studies modifying the Shuttle-C software to work on the Space Shuttle and potentially using Enterprise as a reusable Shuttle-C. The reasoning behind this option this configuration would be a cheaper alternative to the X-33 program. However, while the shuttle could be retrofitted with the software, the shuttle would have less cargo capacity than the X-33 and still required use of expensive legacy launch facilities (ie VAB and LC-39). The study ends with only the software in a beta state.
• December 2003: Steven F. Udvar-Hazy Center is opened with Enterprise being one of its major exhibits.
• November 2003: the Shuttle-C software is used to return STS-118 Columbia to Earth and with critical damage to her structure (mainly her port wing and some internal damage from a collapsed landing gear).
• May 2004: NASA recalls Enterprise to replace Columbia.
• August 2004: initial plans are to return her flight, unmodified. However, NASA develops the Shuttle-C software further and changes it's name to A.S.Tr.O.S (Autonomous Space Transport Operating System).
• New wings! Enterprise is fitted with new wings which are of a modified design and lighter and stronger than the wings of her sisters. With other upgrades and modifications, she is slightly lighter than her younger sisters.
• Some within NASA joking refer to her as Enterprise-A, as a reference to Star Trek.
• September 2006: to commemorate the 30th anniversary of her unveiling to the media, Lockheed-Rockwell rolls her out of their Palmdale facility to rechristen the Shuttle. In attendance, Leonard Nimoy, George Takei, Nichelle Nicholas, Walter Koenig, Christopher Doohan and Rod Roddenberry.
- when asked by the media, Leonard remarked she is still a sight to behold and is glad she will continue her mission of exploration.
Enterprise A (unmanned)
• July 2006: to test the A.S.Tr.O.S. during a return to earth and landing, a new series of Approach and Landing Tests (ALT) were conducted with NASA's 747 SCA (N905NA) at the Dryden Flight Research Center, Edwards Air Force Base. 15 flights are flown to put the software in the real world, with two astronauts on board to step in when needed. Barring some higher than normal landing speeds, the software passes all of its objectives.
• It should be noted, while the rebuilt Enterprise is mainly used as an unmanned orbiter, this is a misnomer. It is more accurate to call her a hybrid shuttle. NASA has the option to convert her back into a manned shuttle if desired or needed.
- This nearly was used in 2015 during STS-154. Space Shuttle Atlantis was after conducting maintenance/upgrades on the Hubble Space Telescope (HST), the crew was unable to disconnect the shuttle from the telescope. CTS-48 Enterprise was already on LC-39B for a cargo mission to the International Space Station. All that was needed was to remove supplies from the payload bay and reinstall the seats in her crew space. Fortunately, this rescue wasn't needed as the Astronauts conducted an unscheduled EVA and manually disconnected the Shuttle from the HST.
• November 2008: first flight of Enterprise-A (CTS-11)
• When Columbia was given a cosmic restoration for her display, the first set of wings from Enterprise was used to replace her damaged one.
• 2019: Enterprise is retired for the final time following CTS-74.
• 2020: Enterprise is on display at Space Center Houston with the restored Star Trek Galileo Shuttlecraft prop.
Original artwork by bagera3005: link, link, link
#Space Shuttle#Space Shuttle Enterprise#Enterprise#OV-101#Orbiter#NASA#Space Shuttle Program#Enterprise-A#alt history#Alternative History#AU#Complete Shuttle Fleet Timeline#my post
94 notes
·
View notes
Text

Tools of the Trade for Learning Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
Cybersecurity professionals use a lot of different tools to get the job done. There are plenty of fancy and expensive tools that enterprise security teams use, but luckily there are also lots of brilliant people writing free and open-source software. In this post, I'm going to list some popular free tools that you can download right now to practice and learn with.
In my opinion, one of the most important tools you can learn how to use is a virtual machine. If you're not already familiar with Linux, this is a great way to learn. VMs are helpful for separating all your security tools from your everyday OS, isolating potentially malicious files, and just generally experimenting. You'll need to use something like VirtualBox or VMWare Workstation (Workstation Pro is now free for personal use, but they make you jump through hoops to download it).
Below is a list of some popular cybersecurity-focused Linux distributions that come with lots of tools pre-installed:
Kali is a popular distro that comes loaded with tools for penetration testing
REMnux is a distro built for malware analysis
honorable mention for FLARE-VM, which is not a VM on its own, but a set of scripts for setting up a malware analysis workstation & installing tools on a Windows VM.
SANS maintains several different distros that are used in their courses. You'll need to create an account to download them, but they're all free:
Slingshot is built for penetration testing
SIFT Workstation is a distro that comes with lots of tools for digital forensics
These distros can be kind of overwhelming if you don't know how to use most of the pre-installed software yet, so just starting with a regular Linux distribution and installing tools as you want to learn them is another good choice for learning.
Free Software
Wireshark: sniff packets and explore network protocols
Ghidra and the free version of IDA Pro are the top picks for reverse engineering
for digital forensics, check out Eric Zimmerman's tools - there are many different ones for exploring & analyzing different forensic artifacts
pwntools is a super useful Python library for solving binary exploitation CTF challenges
CyberChef is a tool that makes it easy to manipulate data - encryption & decryption, encoding & decoding, formatting, conversions… CyberChef gives you a lot to work with (and there's a web version - no installation required!).
Burp Suite is a handy tool for web security testing that has a free community edition
Metasploit is a popular penetration testing framework, check out Metasploitable if you want a target to practice with
SANS also has a list of free tools that's worth checking out.
Programming Languages
Knowing how to write code isn't a hard requirement for learning cybersecurity, but it's incredibly useful. Any programming language will do, especially since learning one will make it easy to pick up others, but these are some common ones that security folks use:
Python is quick to write, easy to learn, and since it's so popular, there are lots of helpful libraries out there.
PowerShell is useful for automating things in the Windows world. It's built on .NET, so you can practically dip into writing C# if you need a bit more power.
Go is a relatively new language, but it's popular and there are some security tools written in it.
Rust is another new-ish language that's designed for memory safety and it has a wonderful community. There's a bit of a steep learning curve, but learning Rust makes you understand how memory bugs work and I think that's neat.
If you want to get into reverse engineering or malware analysis, you'll want to have a good grasp of C and C++.
Other Tools for Cybersecurity
There are lots of things you'll need that aren't specific to cybersecurity, like:
a good system for taking notes, whether that's pen & paper or software-based. I recommend using something that lets you work in plain text or close to it.
general command line familiarity + basic knowledge of CLI text editors (nano is great, but what if you have to work with a system that only has vi?)
familiarity with git and docker will be helpful
There are countless scripts and programs out there, but the most important thing is understanding what your tools do and how they work. There is no magic "hack this system" or "solve this forensics case" button. Tools are great for speeding up the process, but you have to know what the process is. Definitely take some time to learn how to use them, but don't base your entire understanding of security on code that someone else wrote. That's how you end up as a "script kiddie", and your skills and knowledge will be limited.
Feel free to send me an ask if you have questions about any specific tool or something you found that I haven't listed. I have approximate knowledge of many things, and if I don't have an answer I can at least help point you in the right direction.
#studyblrmasterpostjam#studyblr#masterpost#cybersecurity#late post bc I was busy yesterday oops lol#also this post is nearly a thousand words#apparently I am incapable of being succinct lmao
22 notes
·
View notes
Text
The Lost Blossom Shampoo Commercial
During my very early days on Tumblr, I was loving all the GIFs and I wanted to join the community. Along with my love of video games, I love animation and I love Cartoon Network, and I wanted to contribute even if my main Tumblr, which is all that I had back then, wasn't animation focused. I wanted to give something that nobody else has posted. I knew non-American commercials have unique animation not seen anywhere else, so that felt like a good idea. I decided, to add some unique Cartoon Network GIFs to Tumblr, to look through various Cartoon Network commercial reels on YouTube and Vimeo. One of the videos I found on Vimeo was this reel from Brendan Rogan, a producer at Cartoon Network Latin America. I found a clip of the Powerpuff Girls I had never seen at 0:32.
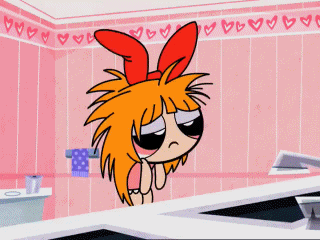
Wait, is this...a shampoo commercial? Seems really fitting considering the Blossom hair wave scene in The Mane Event, and I shouldn't be surprised someone decided to use something inspired by that scene in advertising. Not going to lie: I was intrigued.
After the break, my entire history of my attempt to track down this commercial.

Right after this part of Blossom that I made the GIF from is this clip of three superhero-like mascots flying around three different bottles of different hair products. The one on the left has a bubbly hairstyle that is the same color as the bubbles shown in the Blossom part, suggesting that these two clips are from the same commercial. I did not want to believe it at first, but it did fit pretty well. The Powerpuff Girls are 6 years old at the most, and they could still be using baby shampoo.
After my searches went nowhere, I e-mailed Brendan Rogan back in 2015, who was pretty much my only lead at the time, about it. Rogan asked me why I wanted to see the "full spot". I immediately recalled one YouTube video about people trying to find the guy from Active Enterprises of Cheetahmen infamy only to be met with an all caps "WHY DO YOU WANT TO KNOW THIS INFORMATION" and no further replies, and I was hoping it was not going to end like that video. I did e-mail him with honesty, saying I just wanted to see the context of the full spot, and I'm a big Cartoon Network and Powerpuff Girls fan.
Rogan did not reply back.
I did not e-mail him again because I did not want to pester someone about a baby shampoo commercial, and I was holding onto the hope that it'll appear in a upload of commercials on YouTube so I do not have to test my anxiety. Of course, it'd be in way higher quality if I got it from someone who worked on the commercial rather than a VHS recording of commercials, but I was not thinking of that at the time. At least he indirectly confirmed a full spot exists.
Years later, I found a promotional reel based on the Toonix era of Cartoon Network Latin America, dated to 2011. It advertises The Amazing World of Gumball and Johnny Bravo Goes To Bollywood, both from 2011, so I can believe the year. It seemed to be made for investors and advertisers, showing off Cartoon Network's programming, and how they can have synergy with other brands. This includes a bunch of cross-promotion. Showing up at 4:52, to my surprise, is the Blossom ad. It was almost the exact same clip seen in the Rogan reel. The keyword is "almost." I got out my video editing software, and this is what I can see:
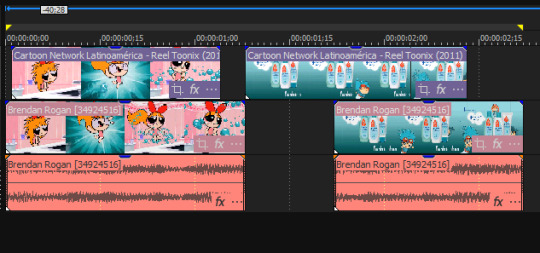
The Cartoon Network reel does have more of the commercial we did not see in the Rogan reel, though it's just more of the mascots flying in from outside of the frame and a little bit less of Blossom waving her hair around. This does confirm to me that neither reel was showing a single clip from the full spot, but two clips from different parts of the spot, showing the Cartoon Network character and showing what that Cartoon Network character was advertising. It also reconfirms that what I am looking for is not a Cartoon Network promo, but a baby hair product line commercial.
I also notice that even with these two different appearances, we only have 2.5 seconds of what could be a 15 or 30 second commercial. That alone does make that intriguing even with the possibility that Blossom only appears for that one second and the rest is just a generic baby shampoo ad. I hope that's not it, but it would explain why the full spot was not uploaded.
I did find one other piece of this campaign. It's not from the commercial, but it is related. Maybe it was an extremely lucky Google Image Search, or I just somehow stumbled across it in one of my searches. This was from a company named Bau Print, who specializes in different kinds of printing, including printing on vehicles, and, hey look!

There they are! It's even a photo taken from a camera that wasn't edited, meaning I could see from the metadata that it was taken in April of 2010. That does narrow down the beginning end of my search, though I had no doubt that the spot was at least post-Powerpuff Girls Movie. It also made me realize a bit of lore about these three super obscure mascots: they each represent the three different kinds of intense hydration: shampoo, conditioner, and combing cream. There are no Powerpuff Girls, showing either these superheroes were not just made for the commercial, or they wanted to use them without having to contact Warner Bros. or Cartoon Network.
This picture does prove that this campaign, at the very least, got to the point where it was advertised on trailer trucks. I did have a feeling this was a part of a scrapped campaign; maybe Johnson's got cold feet for having their clean baby shampoo brand be associated with girls that have beaten monkeys, criminals, talking dogs, and clowns to a pulp. However, wouldn't it be false advertising if a campaign that fell through ended up in a video that seemed to be made for advertisers?
And that's where my search runs cold. I have searched a lot of Cartoon Network Latin America commercial breaks on and off over the years, and I even used Filmot to search YouTube's subtitles for phrases that could be a part of it, like that "salud es belleza" tagline on that truck, and the full spot remains elusive after years of searching. I guess I could just imagine what the rest of the commercial could be.
The City of J&Jville, where our heroic trio responds to a dis-tress call: Blossom, superheroine of Townsville, is having a bad hair day and won't have the confidence to beat up Mojo Jojo and stop his "turn everyone into chickens with his chicken ray" plan. Lather, Rinse, and Repeat are called to action, and with their ultra-cleaning powers, they go into Blossom's hair as she stares at the mirror, and her hair magically turns luscious again. With her newfound confidence, Blossom flies to Mojo Jojo, and knocks his teeth out, bruising him with all of her techniques, her flurry of punches, her eye lasers, and the dreaded ponytail whiplash! The day is saved thanks to Blossom, and Johnson's Baby Hidratación Intensa! (Warning: Baby shampoo will not give your baby superpowers, do not let them fight crime.)
...okay, maybe that violence wouldn't have happened, but there is only one way we can find out for sure, and I can only wish I could find that way. So uh, here's another shampoo ad starring Hanna-Barbera characters that appears to be unrelated. Yes, the Powerpuff Girls are technically Hanna-Barbera. Bye.
youtube
< n/a - Part 2 >
48 notes
·
View notes
Text

Robert Frederick Smith (December 1, 1962) is a businessman, philanthropist, chemical engineer, and investor. He is the Founder, Chairman, and CEO of private equity firm Vista Equity Partners.
In high school, he applied for an internship at Bell Labs but was told the program was intended for college students. He persisted, calling each Monday for five months. When a student from M.I.T. did not show up, he got the position, and that summer he developed a reliability test for semiconductors. He earned a BS in chemical engineering from Cornell University. He became a brother of Alpha Phi Alpha. He received his MBA from Columbia University with concentrations in finance and marketing.
He worked at Goodyear Tire and Rubber Company, Air Products & Chemicals, and Kraft General Foods as a chemical engineer, where he registered two US and two European patents. He worked for Goldman Sachs in technology investment banking, first in New York City and then in Silicon Valley. He advised on mergers and acquisition activity with companies such as Apple and Microsoft. He was included in Vanity Fair’s New Establishment List, which is an annual ranking of individuals who have made impactful business innovations.
He founded Vista Equity Partners, a private equity and venture capital firm of which he is the principal founder, chairman, and chief executive. He is credited with generating a 30 percent rate of return for his investors from the company’s inception to 2020. Vista Equity Partners was the fourth largest enterprise software company after Microsoft, Oracle, and SAP, including all their holdings. Vista has invested in companies such as STATS, Ping Identity, and Jio. Vista Equity Partners had closed more than $46 billion of funding.
He was named Private Equity International’s Game Changer of the Year for his work with Vista.
The 2019 PitchBook Private Equity Awards named Vista Equity Partners “Dealmaker of the Year”. #africanhistory365 #africanexcellence #alphaphialpha
9 notes
·
View notes
Text
It is easy to blame Crowdstrike as the only one at fault, much like it will be easy for them to blame some underpaid contractor. However, this misses a bigger lesson, and it is not just blaming Microsoft either.
A cascading failure of complex systems demonstrates a clear industries wide failure to implement processes to verify stuff they deploy across their various enterprises in favor of trusting random vendors to not make mistakes.
As a Linux user, it would be easy to laugh, but when the hospital can't tell me what room my son is in (he's fine) and imagining patients requiring critical care that they might not get, it is infuriating.
I'm only IT adjacent, but looking for single points of failure in systems is really something that would seem like fairly basic stuff, and it's not like many enterprises don't have internal test machines and networks. I don't even update firmware or software on things immediately sometimes, and I can assure you that software failures in film, TV, or theatre productions are not generally safety critical
10 notes
·
View notes
Text

The 1,000th F-35 Has Been Built
Delays with a key upgrade program mean Lockheed Martin has yet to deliver the 1,000th F-35 and others to their customers.
Tyler RogowayPUBLISHED Jan 10, 2024 1:28 PM EST
Lockheed Martin has built the 1,000th F-35, but delays with a key upgrade program mean it is parked away awaiting delivery.
A newly produced F-35 is seen in its primer colors in Fort Worth, Texas. Lockheed Martin capture
Lockheed Martin has hit a huge milestone in F-35 Joint Strike Fighter production. However, that accomplishment, while outstanding, is complicated by the ongoing saga surrounding the development and testing of Tech Refresh-3 (TR-3) hardware configuration. TR-3 underpins the F-35's future capabilities, known collectively as Block 4. Delays with TR-3 mean that F-35s are being parked and not delivered after they are constructed, waiting for these features. So is the case for the 1,000th F-35.
Lockheed Martin

We asked Lockheed Martin about the status of deliveries of F-35s, including the 1,000th example, and they gave us the following statement:
"We continue to produce F-35s at rate and have jets in various stages of the final production process. Once these jets receive the necessary TR-3 hardware and final TR-3 software is available, they will continue through the production process, including parking, until they are delivered."
Regardless, hitting the 1,000 mark is really an incredible accomplishment for the controversial program that has struggled significantly at times.
As of early January, the F-35 enterprise has amassed over 773,000 flying hours, trained over 2,280 pilots and 15,400 maintainers across 14 flying services around the world, and flown more than 469,000 total sorties. There are now 32 bases and 11 ships hosting or capable of hosting F-35 units. As of now, there are a whopping 17 countries participating in the international Joint Strike Fighter (JSF) program.
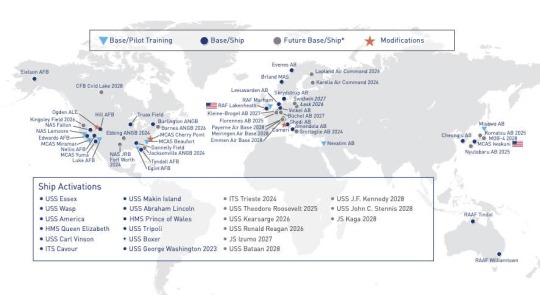
Current and expected future F-35 operating bases/ships. Lockheed Martin
Demand for the F-35 has never been higher. Recent geopolitical events and shifting threats have spiked orders. For newer customers or existing ones that are ordering more jets, getting TR-3 jets and potentially Block 4 capabilities will be of significant value. They will be receiving a far more mature aircraft and one with drastically expanded capabilities and growth potential than past versions.
Block 4 will include many new features, including much-expanded processing power, new displays, enhanced cooling, new EOTS and DAS electro-optical sensors, and a slew of additional weapons that will really unlock the F-35's potential. Above all else, the jet's new radar and electronic warfare suite should give it its biggest boost. The electronic warfare aspect alone is the biggest advantage Block 4 will bring, according to the Air Combat Command's top uniformed officer.
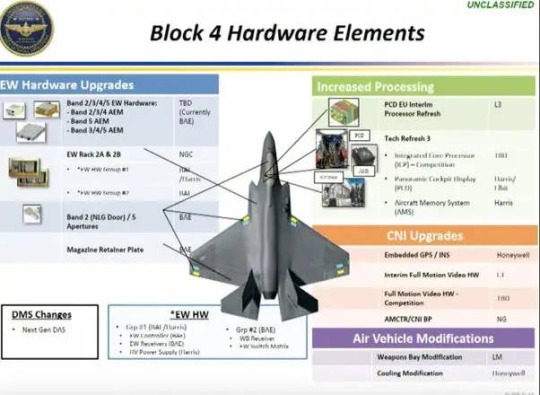
Some of the unclassified upgrades are expected to be part of Block 4. The exact configuration is not publicly disclosed just yet. DOD
The current issue is that F-35s need a new hardware backbone and associated baseline software, collectively called TR-3, to handle the various demands of the Block 4 upgrades. TR-3 has and continues to suffer numerous delays in its development.
The increasing age of the F-35 program's current fleet of test jets and other limitations in existing test infrastructure, especially with regard to software labs on the ground, have compounded these issues. The first flight of an F-35 test jet with a version of the TR-3 backbone took place in January 2023 and efforts are underway to create a dedicated TR-3 test force with a total of six Joint Strike Fighters.

A US Air Force F-35A test jet. USAF
As of December, the expectation is that the development of TR-3 will be finished sometime between April and June of this year, according to Defense News. If that schedule holds, this work be done between a year and 18 months later than expected.
The delays have also translated into significant added costs for the F-35 program. At a House Armed Services Committee hearing in December, Representative Donald Norcross, a Democrat from New Jersey, said that problems with TR-3 had led to a $1 billion cost overrun. The full estimated cost of the F-35 program though the end of its expected lifecycle in the 2070s is currently pegged around around $1.7 trillion, according to the Government Accountability Office (GAO).

USAF
At the House Armed Services Committee hearing last month, Air Force Lt. Gen. Michael Schmidt, the current head of the F-35 Joint Program Office (JPO), seemed less than optimistic about the likelihood of there being no further TR-3 delays.
"Relative to the stability issues that were that we're seeing, we are working through them. ... I wish I had all of the solutions in place that prove to me that when I do something in the lab, it's going to show up that way in the air," Schmidt told the assembled legislators. "We have a number of fixes addressing the stability challenges. We will get to a stable, capable, maintainable airplane here."
However, "the data tells me it will be in the middle of spring, but I would have had a more positive answer six months ago ... so I don't have a super solid 'I can guarantee you this date,'" he added.
After the completion of the development of the TR-3 package, these improvements will still need to be integrated into existing jets. The F-35 program is separately pursuing upgrades to the Pratt & Whitney F135 engines that power all variants of the Joint Strike Fighter, as well as power and thermal management systems, which will also be critical for enabling Block 4 capabilities. The issues surrounding the F135 engine have become a very hot topic of debate.
youtube
In the meantime, the U.S. military has made clear that it will not accept any new F-35s until the TR-3 issues are ironed out. This is ostensibly because the necessary checkout flights cannot be conducted on the jets until the hardware and its core software work reliably.
So, for at least another few months, the 1,000th F-35, and many others, are set to stay parked away waiting for work on the core TR-3 upgrades to be finished.
Contact the author: [email protected]
25 notes
·
View notes
Text
What is Cybersecurity? Types, Uses, and Safety Tips
What is Cyber security?
Cyber security, also known as information security, is the practice of protecting computers, servers, networks, and data from cyberattacks. With the increasing reliance on technology in personal, professional, and business environments, the importance of cyber security has grown significantly. It helps protect sensitive data, ensures the integrity of systems, and prevents unauthorized access to confidential information.
For businesses in Jaipur, cyber security services play a crucial role in safeguarding digital assets. Whether you're an e-commerce platform, an IT company, or a local enterprise, implementing strong cyber security in Jaipur can help mitigate risks like hacking, phishing, and ransomware attacks.
Types of Cyber security
Cyber security is a vast domain that covers several specialized areas. Understanding these types can help individuals and organizations choose the right protection measures.
1. Network Security
Network security focuses on protecting the network infrastructure from unauthorized access, data breaches, and other threats. Tools like firewalls, virtual private networks (VPNs), and intrusion detection systems are commonly used. In Jaipur, many businesses invest in cyber security services in Jaipur to ensure their networks remain secure.
2. Information Security
This type of cyber security involves protecting data from unauthorized access, ensuring its confidentiality and integrity. Companies offering cyber security in Jaipur often emphasize securing sensitive customer and business information, adhering to global data protection standards.
3. Application Security
Application security addresses vulnerabilities in software and apps to prevent exploitation by cybercriminals. Regular updates, secure coding practices, and application testing are vital components.
4. Cloud Security
As more businesses move to cloud-based solutions, securing cloud environments has become essential. Cyber security providers in Jaipur specialize in offering services like data encryption and multi-factor authentication to ensure cloud data is safe.
5. Endpoint Security
Endpoint security protects devices such as laptops, desktops, and mobile phones from cyber threats. It is especially critical for remote work setups, where devices may be more vulnerable. Cyber security services in Jaipur provide solutions like antivirus software and mobile device management to secure endpoints.
6. IoT Security
With the rise of Internet of Things (IoT) devices, ensuring the security of connected devices has become crucial. Businesses in Jaipur use cyber security in Jaipur to secure smart devices like industrial sensors and home automation systems.
Uses of Cyber security
Cyber security is indispensable in various domains. From individual users to large organizations, its applications are widespread and critical.
1. Protection Against Cyber Threats
One of the primary uses of cyber security is to safeguard systems and data from threats like malware, ransomware, and phishing. Businesses in Jaipur often rely on cyber security Jaipur solutions to ensure they are prepared for evolving threats.
2. Ensuring Data Privacy
For industries like finance and healthcare, data privacy is non-negotiable. Cyber security measures help organizations comply with laws and protect sensitive customer information. Cyber security services in Jaipur ensure businesses meet data protection standards.
3. Business Continuity
Cyber security is essential for ensuring business continuity during and after cyberattacks. Jaipur businesses invest in robust cyber security services in Jaipur to avoid downtime and minimize financial losses.
4. Securing Financial Transactions
Cyber security ensures the safety of online transactions, a critical aspect for e-commerce platforms and fintech companies in Jaipur. Solutions like secure payment gateways and fraud detection tools are widely implemented.
5. Enhancing Customer Trust
By investing in cyber security in Jaipur, businesses build trust with their customers, demonstrating a commitment to safeguarding their data and transactions.
Cyber security in Jaipur
Jaipur is emerging as a hub for businesses and IT companies, which has increased the demand for reliable cyber security solutions. Cyber security services in Jaipur cater to diverse industries, including retail, healthcare, education, and finance.
Local providers of cyber security Jaipur solutions offer tailored services like:
Vulnerability Assessments: Identifying potential security risks in systems and networks.
Penetration Testing: Simulating attacks to uncover weaknesses and improve defenses.
Managed Security Services: Continuous monitoring and management of security operations.
Many IT firms prioritize cyber security services in Jaipur to ensure compliance with global standards and protect their operations from sophisticated cyber threats.
Safety Tips for Staying Secure Online
With the rising number of cyberattacks, individuals and businesses must adopt proactive measures to stay secure. Here are some practical tips that integrate cyber security in Jaipur into daily practices.
1. Use Strong Passwords
Ensure passwords are long, unique, and a mix of letters, numbers, and symbols. Avoid reusing passwords for multiple accounts. Cyber security experts in Jaipur recommend using password managers for added security.
2. Enable Two-Factor Authentication (2FA)
Adding an extra layer of security through 2FA significantly reduces the risk of unauthorized access. Many cyber security services in Jaipur emphasize implementing this measure for critical accounts.
3. Regular Software Updates
Outdated software can be a gateway for attackers. Keep operating systems, antivirus tools, and applications updated to close security loopholes. Businesses in Jaipur frequently rely on cyber security Jaipur providers to manage system updates.
4. Be Cautious with Emails
Phishing emails are a common attack vector. Avoid clicking on suspicious links or downloading unknown attachments. Cyber security in Jaipur often involves training employees to recognize and report phishing attempts.
5. Invest in Reliable Cyber security Services
Partnering with trusted cyber security services in Jaipur ensures robust protection against advanced threats. From endpoint protection to cloud security, these services help safeguard your digital assets.
6. Avoid Public Wi-Fi for Sensitive Transactions
Public Wi-Fi networks are vulnerable to attacks. Use a VPN when accessing sensitive accounts or conducting financial transactions. Cyber security Jaipur experts often provide VPN solutions to businesses and individuals.
7. Backup Your Data Regularly
Regularly backing up data ensures that critical information is not lost during cyber incidents. Cyber security providers in Jaipur recommend automated backup solutions to minimize risks.
Why Choose Cyber Security Services in Jaipur?
The vibrant business ecosystem in Jaipur has led to a growing need for specialized cyber security services. Local providers like 3Handshake understand the unique challenges faced by businesses in the region and offer customized solutions.
Some reasons to choose cyber security Jaipur services from like 3Handshake include:
Cost-Effective Solutions: Tailored to fit the budgets of small and medium-sized businesses.
Local Expertise: Providers have an in-depth understanding of regional cyber threats.
24/7 Support: Many companies offer round-the-clock monitoring and support to handle emergencies.
For businesses in Jaipur, investing in cyber security services in Jaipur is not just about compliance; it's about ensuring long-term success in a competitive digital landscape.
4 notes
·
View notes
Text
**From PCI DSS to HIPAA: Ensuring Compliance with Robust IT Support in New York City**
Introduction
In latest electronic global, enterprises are increasingly reliant on technology for his or her operations. This dependence has caused a heightened center of attention on cybersecurity and compliance necessities, specially in regulated industries like healthcare and finance. For companies operating in New York City, understanding the nuances of compliance frameworks—particularly the Payment Card Industry Data Security Standard https://hollidayvinni52.gumroad.com/p/navigating-cybersecurity-in-the-big-apple-essential-it-support-solutions-for-new-york-businesses-5fd23200-32f1-4da0-a4e8-3b7459de7e91 (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA)—is predominant. Navigating those guidelines calls for physically powerful IT aid, which encompasses every little thing from network infrastructure to archives leadership.
With the swift advancement of science, corporations must also continue to be abreast of most useful practices in info science (IT) improve. This article delves into how organisations can be sure that compliance with PCI DSS and HIPAA simply by triumphant IT solutions while leveraging components from most sensible prone like Microsoft, Google, Amazon, and others.
Understanding PCI DSS What is PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) is a hard and fast of safeguard specifications designed to protect card facts in the course of and after a financial transaction. It was once ordinary by means of prime credit score card services to fight rising occasions of payment fraud.
Why is PCI DSS Important?
Compliance with PCI DSS is helping companies shield sensitive monetary wisdom, thereby bettering client consider and decreasing the menace of statistics breaches. Non-compliance can end in critical penalties, inclusive of hefty fines and even being banned from processing credits card transactions.
youtube
Key Requirements of PCI DSS Build and Maintain a Secure Network: This comprises putting in a firewall to preserve cardholder archives. Protect Cardholder Data: Encrypt stored knowledge and transmit it securely. Maintain a Vulnerability Management Program: Use antivirus software program and expand comfy strategies. Implement Strong Access Control Measures: Restrict access to in simple terms people that need it. Regularly Monitor and Test Networks: Keep music of all access to networks and most likely look at various protection strategies. Maintain an Information Security Policy: Create regulations that tackle safeguard requisites. Exploring HIPAA Compliance What is HIPAA?
The Health Insurance Portability and Accountability Act (HIPAA) sets the traditional for covering delicate patient awareness inside the healthcare enterprise. Any entity that offers with included health and wellbeing records (PHI) must adjust to HIPAA regulations.

Importance of HIPAA Compliance
HIPAA compliance not purely protects patient privateness but additionally guarantees enhanced healthcare result with the aid of permitting comfortable sharing of affected person documents amongst licensed entities. Violations can end in big fines, prison penalties, and damage to reputation.
Core Components of HIPAA Compliance Privacy Rule: Esta
2 notes
·
View notes