#freeradius
Text
o servidor RADIUS gratuito mais popular do mundo #ÚltimasNotícias
Hot News
O FreeRADIUS é um servidor de RADIUS (Remote Authentication Dial-In User Service) de código descerrado, amplamente utilizado para autenticação, autorização e contabilidade (AAA) em redes de comunicações.
0 notes
Video
youtube
Freeradius and Mikrotik Application PHP and Laravel
1 note
·
View note
Text
[Media] daloradius
daloradius
daloRADIUS is an advanced RADIUS web management application aimed at managing hotspots and general-purpose ISP deployments. It features user management, graphical reporting, accounting, a billing engine and integrates with GoogleMaps for geo-locating.
daloRADIUS is written in PHP and JavaScript and utilizes a database abstraction layer which means that it supports many database systems, among them the popular MySQL, PostgreSQL, Sqlite, MsSQL, and many others.
It is based on a FreeRADIUS deployment with a database server serving as the backend. Among other features it implements ACLs, GoogleMaps integration for locating hotspots/access points visually and many more features.
https://github.com/lirantal/daloradius

1 note
·
View note
Text
Configure 802.1X on Mojo
Configure 802.1X on Mojo Networks Access Points
Securing a remote organize implies venturing up past the preshared key verification of Mojo. The shortcoming in preshared key is the secret word that's shared among individuals and over numerous gadgets. In the event that a individual or gadget takes off the organization, the secret word must be changed to avoid that individual from joining the arrange.
A more grounded way of securing the remote organize is to utilize 802.1X.
In this case, we are going go over arranging the Mojo Systems C-120 access point as the authenticator which is able point to our FreeRADIUS server.
Within the Mojo Remote Director, Tap on Configuration at the beat menu and after that click on Device Configuration within the primary board.
- Next, click on SSID Profiles to modify the SSID in which we will configure 802.1X.
- Select the SSID in the list where we will configure 802.1X security. You may have multiple SSIDs listed here.
- While in the Edit Wi-Fi Profile subconfiguration menu, the first option we want to display is Security. Click on it to expand the options.
Make sure the Security Mode is set to WPA2. Right below it, select 802.1X.
To arrange our verification server, seek for the area Sweep Verification.
A Essential and Auxiliary Verification server can be designed. In this illustration I will arrange as it were one. Input the subtle elements of the Verification server.
When total, press on Spare at the foot of the page and confirm network to the SSID. Utilizing the Observing tab, confirm the gadget is effectively associated. In my arrangement I am utilizing EAP-TTLS which is designed to confirm gadgets employing a username and secret word.
Read the full article
0 notes
Text
Setting up stunnel with psk

Setting up stunnel with psk install#
Setting up stunnel with psk password#
Setting up stunnel with psk download#
# NOTE: LZO commands are pushed by the Access Server at connect time. Port 8088 # this should be the port that your stunnel is accepting connection Remote localhost # always set this to point to localhost if you're using stunnel It should look something like: setenv FORWARD_COMPATIBLE 1
Setting up stunnel with psk download#
You should see a link to download your connection settings (profile) for To make your life easier, just go to and login with Your nf on the client should look like this client = yesĪccept should always be your localhost with any port that you decideĬonnect will point to your stunnel server and the port that it is listening
Setting up stunnel with psk install#
This should be run by your OpenVPN clientsĭo the same setup as above, install stunnel via the distro’s package managers. Note: Ensure that you’re only accepting TCP connection in your OpenVPN AS Web OpenVPN connections underneath an unblockable port (SSL)Ĭonnect should be the ip:port of your actual OpenVPN server that is In theĬase of hiding from Deep Packet Inspection, setting this to 443 will hide your output = /var/log/stunnel4/stunnel4.logĪccept should be the port that is listening to openvpn connections. Debugging stuff (may useful for troubleshooting) In /etc/stunnel/nf # create if file doesn't exist $ cat server.key > server.pem & cat server.crt > server.pem $ openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt $ openssl req -new -key server.key -out server.csr In your stunnel directory, sometimes at /etc/stunnel/ $ openssl genrsa -out server.key 4096 You can run this on the same server as your OpenVPN. In the FreeRADIUS server: $ vim /etc/raddb/nf Hit “Update Running Server” Hook FreeRADIUS and OpenVPN Add OpenVPN server into FreeRADIUS records Select “Radius” and “update running server” Authentication > RadiusĪdd server ip of FreeRADIUS server and shared_secret (hint: “testing123” which
Setting up stunnel with psk password#
Change OpenVPN password $ passwd openvpnĪccess and login with your username/password Under Authentication > General To reconfigure manually, use the /usr/local/openvpn_as/bin/ovpn-init tool. Please enter “passwd openvpn” to set the initialĪdministrative password, then login as “openvpn” to continue The Access Server has been successfully installed in /usr/local/openvpn_asĬonfiguration log file has been written to /usr/local/openvpn_as/init.log Lets check radius! $ service radiusd start Secret = testing123 # into something more awesome # /etc/raddb/sites-available/inner-tunnelĬhange freeradius secret # /etc/raddb/nf # Database table configuration for everything except Oracleĭo the magical uncomments # /etc/raddb/sites-available/default Mysql> INSERT INTO radcheck (username, attribute, op, value) VALUES ('chantra','Cleartext-Password',':=','chantrapass') Ĭreate /etc/raddb/sql.conf # Connection info: _Create your first vpn user _ mysql> use radius Mysql> SOURCE /etc/raddb/sql/mysql/schema.sql Mysql> GRANT ALL ON radius.* TO IDENTIFIED BY "radpass" Login to MySQL as root and create databases $ mysql -uroot -p Setup FreeRADIUS Install Freeradius Centos $ yum install freeradius freeradius-mysql With all these setup, you’re one step closer to start providing VPN services. This article will serve to setup FreeRADIUS as the authentication mechanism, OpenVPN as the VPN protocol and stunnel as an introduction to obfuscating censorship. I hope this might give you a little peek. If you’re ever curious as to how do VPN service providers manage all their usersĪnd their authentication.

0 notes
Text
FreeRADIUS Reflection Prevention Authentication Spoofing Vulnerability [CVE-2019-11234]
CVE Number – CVE-2019-11234
A vulnerability in FreeRADIUS could allow an unauthenticated, remote attacker to bypass authentication and impersonate a user on a targeted system.
The vulnerability exists because the eap_pwd.c source code file of the affected software does not prevent the use of reflection for authentication spoofing. An attacker could exploit this vulnerability to conduct an…
View On WordPress
0 notes
Photo

RT @TheHackersNews: Researchers Discover New Ways to Hack WPA3 Protected WiFi Passwords https://t.co/Afyvj9b9Dd CVE-2019-13377 ➤ Timing-based side-channel attack against Dragonfly handshake when using Brainpool curves, CVE-2019-13456 ➤ Information leak bug in FreeRADIUS' EAP-pwd implementation. https://t.co/otV1FrDAsn (via Twitter http://twitter.com/TheHackersNews/status/1157687321560408064)
2 notes
·
View notes
Text
Freeradius on Raspberry Pi
Freeradius on Raspberry Pi
Setting up a Raspberry Pi as a RADIUS server
sudo bashapt-get updateapt-get install freeradius -y
edit /etc/freeradius/3.0/clients.conf
Add to file
client 0.0.0.0/0 {secret = {RADIUS shared key}shortname = any}
#
edit /etc/freeradius/users
Add to file
testuser Cleartext-password :=”password”
service freeradius restart

View On WordPress
0 notes
Text
How to use FreeRADIUS for SSH authentication
How to use FreeRADIUS for SSH authentication
Jack Wallen shows you how to install and configure FreeRADIUS as a centralized SSH authentication tool.
Image: iStock/structuresxx
You might have a large number of Linux machines in your data center, most of which are managed by a team of admins. Those admins probably use secure shell to access those servers. Because of that, you might want to use a centralized location to manage the…

View On WordPress
0 notes
Text
The Way to configure SSH authentication into a FreeRADIUS server

Discover How to configure FreeRADIUS as an SSH authentication server on Ubuntu. the Way to configure SSH authentication into some FreeRADIUS server Find out how to configure FreeRADIUS as an SSH authentication server on Ubuntu. should you've got different admin users that log [...]
Read full article here 📄 👉 http://bit.ly/34jlRrF
https://www.seowebdev.co/the-way-to-configure-ssh-authentication-into-a-freeradius-server/
0 notes
Text
Investigadores descubren nuevas formas de hackear contraseñas WiFi protegidas con WPA3
El mismo equipo de investigadores de ciberseguridad que descubrió varias vulnerabilidades graves, denominadas colectivamente Dragonblood, en el estándar de seguridad WiFi WPA3 publicado recientemente hace unos meses, ahora ha descubierto dos fallos más que podrían permitir a los atacantes hackear las contraseñas WiFi .
WPA, o WiFi Protected Access, es un estándar de seguridad WiFi que ha sido diseñado para autenticar dispositivos inalámbricos mediante el protocolo de Estándar de cifrado avanzado (AES) y está destinado a evitar que los ciberdelincuentes escuchen nuestros datos inalámbricos.
El protocolo de acceso protegido WiFi III (WPA3) se lanzó hace un año en un intento de abordar las deficiencias técnicas del protocolo WPA2 desde sus cimientos, el cual se considera inseguro y vulnerable a ataques KRACK más graves desde hace tiempo.
WPA3 se basa en un handshake más seguro, llamado SAE (Autenticación simultánea de iguales), que también se conoce como Dragonfly, y que tiene como objetivo proteger las redes WiFi contra ataques de diccionario fuera de línea.
Sin embargo, en menos de un año, los investigadores de seguridad Mathy Vanhoef y Eyal Ronen encontraron varias debilidades (Dragonblood) en la implementación temprana de WPA3, permitiendo que un atacante recupere las contraseñas de WiFi al abusar del tiempo o las fugas de canal lateral basadas en caché.
Poco después de esa divulgación, WiFi Alliance, la organización sin fines de lucro que supervisa la adopción del estándar WiFi, lanzó parches para abordar los problemas y creó recomendaciones de seguridad para mitigar los ataques iniciales de Dragonblood.
Pero resulta que esas recomendaciones de seguridad, que se crearon de forma privada sin colaborar con los investigadores, no son suficientes para proteger a los usuarios contra los ataques de Dragonblood. En cambio, abre dos nuevos ataques de canal lateral, que una vez más les permite a los atacantes robar las contraseñas WiFi incluso si se está utilizando la última versión del protocolo WiFi.
Nuevo ataque de canal lateral contra WPA3 cuando se utiliza cifrado de curvas elípticas Brainpool
La primera vulnerabilidad, identificada como CVE-2019-13377, es un ataque de canal lateral basado en el tiempo contra el handshake Dragonfly de WPA3 cuando se usa cifrado de curvas elípticas de Brainpool, que la Alianza WiFi recomendó a los proveedores usar como una de las recomendaciones de seguridad para agregar otra capa de seguridad .
"Sin embargo, descubrimos que el uso de las curvas de Brainpool introduce la segunda clase de fugas de canal lateral en el handshake Dragonfly de WPA3", dice la pareja de investigadores en un aviso actualizado . "En otras palabras, incluso si se siguen los consejos de WiFi Alliance, las implementaciones siguen en riesgo de ataques".
"La nueva fuga de canal lateral se encuentra en el algoritmo de codificación de contraseña de Dragonfly", dijeron los investigadores, "confirmamos la nueva fuga de Brainpool en la práctica contra la última versión de Hostapd, y pudimos forzar la contraseña con fuerza bruta utilizando la información filtrada ".
Ataque de canal lateral contra la implementación EAP-PWD de FreeRADIUS
La segunda vulnerabilidad, identificada como CVE-2019-13456, es un error de fuga de información que reside en la implementación de EAP-pwd (Protocolo de autenticación de contraseña extensible) en FreeRADIUS, uno de los servidores RADIUS de código abierto más utilizados por las empresas como base de datos central para autenticar usuarios remotos.
Mathy Vanhoef, uno de los dos investigadores que descubrió las fallos de Dragonblood, indicó que un atacante podría iniciar varios handshakes EAP-pwd para filtrar información, que luego se puede utilizar para recuperar la contraseña WiFi del usuario mediante la realización de ataques de diccionario y fuerza bruta.
"El protocolo EAP-pwd usa internamente el handshake Dragonfly, y este protocolo se usa en algunas redes empresariales donde los usuarios se autentican usando un nombre de usuario y contraseña", dijo Vanhoef.
"Más preocupante, encontramos que el firmware WiFi de los chips Cypress solo ejecuta 8 iteraciones como mínimo para evitar fugas en los canales laterales. Aunque esto hace que los ataques sean más difíciles, no los evita". comentó la pareja de investigadores."
Según los investigadores, la implementación del algoritmo Dragonfly y WPA3 sin fugas de canal lateral es sorprendentemente difícil, y las contramedidas compatibles con estos ataques son demasiado costosas para dispositivos livianos.
Los investigadores compartieron sus nuevos hallazgos con WiFi Alliance y tuitearon que "el estándar WiFi ahora se está actualizando con las defensas adecuadas, lo que podría conducir a WPA 3.1", pero desafortunadamente, las nuevas defensas no serían compatibles con la versión inicial de WPA3.
Mathy Vanhoef también mencionó que es lamentable que WiFi Alliance haya creado sus pautas de seguridad en privado. "Si hubieran hecho esto públicamente, estos nuevos problemas podrían haberse evitado. Incluso la certificación WPA3 original se hizo en parte en privado, lo que tampoco ha sido lo más ideal"
Traducido del original de Swati Khandelwal de The Hacker News
0 notes
Text
FREERADIUS COM MIKROTIK - Contas por hora pré-pagas junto com o poderoso COA!
FREERADIUS COM MIKROTIK – Contas por hora pré-pagas junto com o poderoso COA!

Aviso: Esta não é uma cópia copiada. É puramente pessoal de pesquisa e desenvolvimento. Eu não posso garantir se vai funcionar no seu final ou não, mas ainda assim você pode ter uma boa idéia! Eu também suponho que você deve ter algum conhecimento justo sobre como o freeradius e seus módulos funcionam juntos.
Tarefa:
Permitir contas horárias pré-pagas de acordo com os seguintes requisitos …
# 1
View On WordPress
0 notes
Text
SA: Secure Methods of Communication :- Port based Authentication IEEE 802.1X
In this secure method of communication, Involves 3-party communications:
Supplicant which is the User
Authenticator which is either the Ethernet switch or wireless access point
Authentication server which is the RADIUS (Remote access dial-in user service) database, Kerberos, LDAP
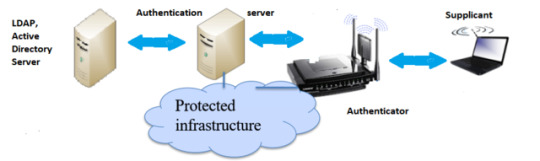
Supplicant is the user device which uses WAP protocol. To access a network service/resource. the device need to be get authenticated. This is connected to the through the authenticator or the access point, AP. This can:
software/app running 802.1X client
OS based supplicants like Microsoft Wireless Zero Conf–WZC or Apple’s airport client
The Chipset vendor’s supplicant software –Intel, Atheros, Broadcom
Authenticator (Access Point): This works as a relay between Supplicant and Authentication Server, There will be two Virtual Ports:
Uncontrolled : allows EAP authentication traffic
Controlled: Only authenticated traffic
Authentication Server: RADIUS provides centralized authentication, authorization and accounting management for user/host to access a network service/resource. This supports AAA (Authentication, Authorization and Accounting). Steps involved in communication:
Both Radius Server and Authenticator are configured with a shared secret
Authenticator sends a RADIUS Access Request message to the RADIUS server, requesting authorization to grant access via the RADIUS protocol. This request includes access credentials (e.g., username and password hash)
Authentication server checks the credentials using the RADIUS server, Kerberos server, LDAP or Active Directory server– returns one of three responses
Access Accept,
Access Reject,
Access Challenge for extra credentials
RADIUS server examples:
Elektron(US$750) is an entry-level and user friendly server
ClearBox(US$599) is designed for small networks, but it also scales to larger networks
FreeRADIUS(open source) is a solid and economical choice for Unix/Linuxadm
Source: Notes from Wireless security
0 notes
Text
FreeRADIUS Insufficient Verification of Data Authenticity Vulnerability [CVE-2019-11235]
CVE Number – CVE-2019-11235
A vulnerability in FreeRADIUS could allow an unauthenticated, remote attacker to bypass authentication on a targeted system.
The vulnerability exists because the eap_pwd.c source code file of the affected software does not verify whether the received elliptic curve point is valid when an EAP-PWD commit frame is received. An attacker could exploit this vulnerability…
View On WordPress
0 notes
Photo

Researchers Discover New Ways to Hack WPA3 Protected WiFi Passwords https://t.co/Afyvj9b9Dd CVE-2019-13377 ➤ Timing-based side-channel attack against Dragonfly handshake when using Brainpool curves, CVE-2019-13456 ➤ Information leak bug in FreeRADIUS' EAP-pwd implementation. https://t.co/otV1FrDAsn (via Twitter http://twitter.com/TheHackersNews/status/1157584511976083456)
1 note
·
View note