#go to log in today need to do two factor authentication
Explore tagged Tumblr posts
Text
ripping apart EA games with my fucking teeth
#innocuous rant im just fucking annoyed#logged in to my old account to play sims 3 yesterday just fine#go to log in today need to do two factor authentication#annoying because i have to log into my OLD email but whatever#fine. i can do that#i do that#no email#me: ????#try again#continue to refresh#nothing#huh thats weird this shouldnt be taking this long#go to a live cha#t#person keeps calling me friend. makes me want to rip at wood#me: hey yeah so im not getting Any emails from you guys#them: just wait for the email my friend#me: okay. how long should it take#them: wait a half hour my friend#im. maybe im just spoiled in this day and age but like guys!!! a HALF HOUR to send out an authentication email?????#its not like its a bank its games but guys. seirously#they just asked if im still there. yeah im just waiting a half hour for the email to not arrive :)
59 notes
·
View notes
Text
keystrokes (dave york x hacker!f!reader)

Moth's Masterlist // follow @mothandpidgeon-updates and turn on notifications to stay updated with my fics!
rating: E (18+!)
summary: You hacked into Dave Yorks computer and found more secrets than you bargained for.
contents: Non con/dub con, mean!Dave, voyeurism, sex toys, masturbation, mutual masturbation, porn, breaking and entering, violence?, gun, gunplay, choking, morally grey reader, reader is Girl with the Dragon Tattoo coded but not physically described
wc: 3.4k
a/n: So I've been having some ✨writers block ✨ (hence the lack of updates last month) but for some reason, Dave York did a little breaking and entering in my brain and shook it loose. I've been writing a lot of heartfelt romance recently and I think I just needed a little depravity I guess.
Thank you @moonlitbirdie and @whocaresstillthelouvre for giving this a look and for anyone I shouted at about this idea (looking at you @schnarfer and @toomanytookas but I know there have been others). Dividers by @ saradika-graphics.

You squint in the light of the refrigerator. It’s empty save for some cartons of half-eaten Chinese food and cans of energy drinks. Check the time— half past one. Too late to order in. Guess cold lomein it is.
The apartment falls back into darkness once you swing the fridge door shut. You’re used to it, the soft glow of your computer monitors illuminating your little space. It’s easy to forget to turn the lights on when you’re focused on your work. Forget to eat. Forget to meet people that aren’t on the other side of a screen.
You sit down at your desk, legs crossed in your seat, and shovel some food into your mouth. Most nights are like this, lost in your work. It’s never felt like a job, not really. More like a way to do the shit you’ve always done except now you get paid to do it. You’re a subcontractor of a subcontractor, someone far enough away from the government that they can get information while still maintaining plausible deniability. You don’t know who you’re working for and most of the time your assignments are vague. All you have to do is gather intelligence and put it into a neat little report without mentioning the methods you used to get it.
You’ve always enjoyed uncovering people’s secrets, reading notes over your classmates shoulders, looking through the search history on friends’ computers. That insatiable curiosity is what led you to start hacking. The targets these days aren’t always exciting but at least tonight’s is.
David York.
Early 40s, divorced. Ex military. DIA. There’s much more to him than that, though. A little program hidden on his computer lets you track each keystroke he makes.
You’ve learned all about him. Dave he prefers. There’s a lot that won’t make it into your report— where he shops online (Brooks Brothers), the take out he orders (one large pepperoni from Frankie’s Pizzeria), the porn he watches (girl on girl). But there’s one thing your bosses will be interested in: Dave York is a contract killer.
You could’ve ended this project by now. You’ve got plenty in your notes to make your customers happy yet you’re still logging onto his computer. It fascinates you that a man so normal, almost on the borderline of boring, could be so dangerous.
You shovel some food into your mouth and go drag your mouse over your desk. You’ve been reviewing footage you recorded through his webcam today. A few lines of code and you were able to turn his laptop’s camera on without activating the tally light. He was smart enough to use unique, complicated passwords, two-factor authentication, and encrypted emails but he didn’t take the time to put a sticker over his webcam.
You’ve found some interesting information this way— listened in on conversations, heard the things he only says into his burner phone. Tonight most of it is just Dave at the keyboard, his tie loosening over time.
You scrub through the footage, Dave drinking coffee and typing in fast forward punctuated by stretches of his empty home office. Nothing exciting until—
You pause the video when you see it. Lomein hangs from your open mouth. He’s half naked, head thrown back, hand buried in his lap. His dick is engulfed in a big fist, a bead of precum frozen before it rolls over his fingers.
It’s not the first time you’ve seen a mark in a compromising position. In this line of work, you’ve seen all the dark corners of people’s hard drives. There’s worse than nudes and home made porn out there. Normally— if it’s not illegal, at least— you just scroll by. But Dave, it’s different when it comes to him. For some reason, seeing him in a compromising position has your blood rushing in your ears. He’s a killer. How many people have had the opportunity to see him in such a vulnerable state?
He’s bare to the waist, his chest so smooth you wonder if he shaves it or if he’s naturally like that. His broad shoulders look perfect to grab onto if you were on top of him. Riding him.
Of course you notice all of this after taking a good, long look at his cock. A clutch of dark curls trail down his soft belly to where it stands, drooling in his fist. You realize you’re salivating.
Guilt pokes at you as you move the playhead back. It’s a violation. Then again, you’ve all but eviscerated Dave's privacy. You know exactly how much money is in his bank account, that his daughter Molly has a sleepover this weekend, that he’ll kill innocents.
He’s not a good person. You’re not either.
You roll back the tape, finding the start of this, and hit play. Dave’s palm traces his bulge through his pajama pants. He’s watching porn, you can hear the over-exaggerated moans through the computer’s tinny speakers.
It’s not the first time you’ve noticed that Dave is hot. After all, you have access to all of the pictures on his laptop. Including the selfies he takes after his runs, muscles glistening with sweat. He’s a bit clean cut for your tastes but right now, he’s something else altogether– the lust in his brown eyes, the control as he teases himself. You swallow hard.
It’s a while before he actually takes his dick out of his pajama pants. You remind yourself repeatedly that you can stop, just click away and let him keep this moment to himself but you’re on the edge of your seat, already throbbing. He finally pulls down his waistband and you’re looking at his upright cock again. It’s thick, a flushed vein running up the underside. He squirts lube into his hand from a bottle that’s just out of frame and when he finally lets his fist move down his length, his eyes sink closed, savoring the sensation.
He touches himself with a practiced motion, gripping the shaft and pulling upwards, a twist of the wrist so that his palm caresses the tip before squeezing back down the length again. His strokes are agonizingly slow. He’s so methodical, patient, like in everything else you’ve discovered.
You’re holding your breath, the suspense aching in your core. There’s plenty of time to study him— those full lips parted, muscles in his arm flexing. Every once in a while he grunts and loosens his grip, keeping himself from going over the edge.
By now, your hand has found its way between your legs. Your fingers trace absentmindedly over the seam in your sleep shorts, already sticky and soaked through. You match Dave’s lazy pace, giving yourself the same pleasure he’s experiencing.
Without taking your eyes off of the screen, you lean over to the set of drawers beside your desk and pull out your favorite vibrator. You shimmy out of your shorts and panties and drag the toy over your needy clit.
You moan with him, watching Dave’s toned arm flex up and down. His bottom lip looks so thick, you want to rake your teeth across it. It’s almost grotesque the way his nostrils flare, the rhythmic grunts that leave him as his hand works faster. The muscles in his neck strain and you can tell he’s close.
You are, too. You swivel your hips against the vibrator, speeding up the thrusts and strengthening its power. Fuck. What would it feel like to have Dave’s mouth on you? His cock in you?
He can’t hold back any longer. Dave’s eyes squeeze shut and his jaw clenches and he makes a noise more animal than man. The eruption of cum is the last thing you see before you’re sent reeling, moaning out your own desperate cry as you pulse around your vibrator.
You take deep breaths as you return to earth, hitting the spacebar to pause the video and blinking back to reality. Your heart rate slows and you wipe your hand across your face. That’s enough work for one night. That might be enough Dave for good. Tomorrow you’ll finalize your report and put him out of your mind.
The vibrator is tossed carelessly onto the desk. You put your panties on but leave your shorts discarded on the floor amongst the rest of your laundry and then you put your computer to sleep. Without the light of the monitors, the room is cloaked in darkness and you drag yourself from your chair a few short paces to the bed.

It’s still dark when you wake, an uneasy feeling in the pit of your stomach. You strain your ears for noise, any sign of what woke you but there’s nothing. Then a creak. Your heart leaps into your throat. Someone’s here, in your apartment.
You fumble for your backpack in the dim. Somewhere in the bottom there’s a can of pepper spray that you bought for a situation just like this but your hands are trembling and you can’t see a fucking thing.
A figure appears behind the French door that separates your room from the kitchen and any drowsiness that was lingering evaporates immediately. It’s a man— broad body clothed entirely in black— and in his hand you make out the silhouette of a gun. The room’s too fucking tiny for there to be anywhere decent to hide. There’s no time to think. Your only choice is to brandish your bag as a weapon. He barges in and you swing for his face.
“Fuck,” he grunts but it merely slows him for a moment, knocking hm off balance and his beanie off of his head.
You scramble towards the front door but you’re tackled to the ground, wind knocked out of your lungs. As you gasp for air, you’re flipped onto your back and you find yourself face to face with your assailant. Even in the darkness, through your terror and disorientation, you recognize him.
Dave York glares down at you, his angular face cast in shadows, a menacing snarl on his lips. The muzzle of his silencer is far too close to your face but there’s no shrinking from it with your head against the floor and Dave’s heavy hand on your middle.
“You and I have a problem,” he growls. “You know why I’m here?”
You shake your head frantically, still barely able to fill your lungs.
“Don’t play dumb, sweetheart. I know you’re not stupid,” he says.
He pulls you to your feet as if you weigh nothing and hauls you towards your room. You’re thrown into your desk chair, head still spinning. Dave stands over you and clamps your wrist to the arm rest.
“You know why you’re spying on me?” he asks, a cold threat in his words.
You nod.
“Then you know you don’t want me as your enemy.” You say nothing but a shiver runs down your spine. His eyes are nearly black, reflecting the dull light of the sleeping computer monitors.
“I want your hard drives. Back ups, too. Everything you’ve got on me,” he demands.
“Okay,” you manage. “Would you just get that gun out of my face?”
“Get to it,” he says, and spins your chair so you’re facing the keyboard.
The monitors come to life and, suddenly, you’re in deeper shit. You try to hit a shortcut on the keys to close the window that’s open but your fingers are trembling so hard, you miss. Dave sees it all.
Something changes in him— a tightening in his jaw, a flaring of his nostrils— as he sees the evidence of your surveillance. His spent form, blissed out and covered in his own release hovers on screen. Right where you left him.
Dave’s eyes narrow at the video then slide down to the toy sitting within arms reach and there’s no denying what he can see so plainly.
He rounds on you with a wild look, flinging the chair back so its wheels hit your bed.
“You get off on that?” he demands.
Your heart might have actually stopped for a minute.
“Answer me,” he demands.
“I– No,” you lie.
He appraises you with a deep scowl until a wicked grin spreads on his lips.
“You’re a pretty little thing, huh?” he muses.
He drags the gun across your breast, your nipple hardening beneath the muzzle’s brush. You let out a whimper— out of fear or arousal, you’re not sure. You swear he growls under his breath.
“You’re trouble though,” he says.
You swallow thickly, your entire body quivering.
”Show me,” he says, depositing the gun on the desk and thrusting the toy towards you.
”What?” You ask.
”Show me how you touched yourself,” he tells you.
That’s what you thought he was saying. You stare at him dumbly, too shocked to even protest.
“You watched me. Only seems fair,” he says as if this is some bargain you’re cutting with the man holding the gun. ”Do I have to make you?”
He leans over you, his hand braced on the back of your chair, and presses the vibrator into the gusset of your panties. Rough and clicked onto the highest setting, you squirm and cry out. You’re already so overstimulated, it’s torture and bliss all at once. Your hips buck against the toy but Dave holds your thigh open.
”Okay! Stop! Fuck!” you whine, wrenching at his wrist until he lets up.
You try to catch your breath.
“Take these off,” he instructs, snapping the elastic of your panties against your waist with a thick finger.
You hiss and glare at him but you have no choice but to obey, sliding them down your legs. Dave watches, his eyes darkening once you’re revealed to him. He swears under his breath.
”Look at that mess,” he says.
Your whole body burns but the hunger in his gaze makes your fear take a back seat. Defiantly, you put your hand out for the vibrator. You open your legs wider so he can get a good look at you. There’s a tick in his jaw that gives you some satisfaction.
The vibrator purrs dully in your palm and you take your time bringing it to your clit. A low, long moan leaves you. You’re swollen but slick and even gentle strokes feel electric in your veins.
There’s a tent already forming in Dave’s pants. He’s a killer, sure, but right now he’s horny.
Your head falls back as you continue. His gaze devours each part of you— where the toy glistens against you, your nipples rising and falling below your shirt, the crease in your brow as you keen.
“You’re a filthy girl, huh?” he asks.
You nod and a smile actually pulls at the corner of your lips. It shouldn’t turn you on so much to jerk off in front of a man that has seemingly no hesitations when it comes to killing you but somehow that fact has arousal mounting faster. Your eyes drift closed as you focus on the heady sensation of the friction on your overworked nerves.
The sound of a metallic clink and soft zip distracts you from your reverie. When you look at Dave, you find his hand down the front of his pants, knuckles straining against the fabric of his black boxer briefs as he tugs at himself.
“Keep going,” he breathes and you realize you’re staring slack-jawed, desire flooding out any remnants of fear left within you.
After a few blinks, you press the vibrator against your clit again. Your back arches and you give a luxurious sigh for his benefit. His fist tightens, muscles in his neck straining and, fuck, you have to grip the seat of your chair to keep yourself from falling out of it.
With a grunt, Dave’s pushing his jeans out of the way, freeing his cock so he can work himself in the angles he likes, the same ones you watched through his webcam. The sound of his shallow breaths and slick strokes mix with the rumble of your toy and the creak of your chair as you writhe. It’s absolutely maddening. And then he starts babbling. Saying things like, “You like this, huh?” and “Say my name sweetheart.” You do it, panting out the word to a hum of approval.
He crowds you and for a moment you prepare yourself for the chance he’s about to shove his dick down your throat. Instead he’s yanking up your shirt, exposing your tits to the cold air in the room. Dave fondles one and then the other, squeezing the tender flesh with a groan. His hand is much softer than you’d expect for a contract killer, his touch almost gentle as he teases your nipples with the pad of his thumb.
Dave’s expression nearly looks pained, a delicious frown over his plump bottom lip. It makes you mewl and your hips jump.
“You close?” he asks. His voice is ragged.
A breathless nod is all you can manage.
“Good girl,” he rasps.
His words are enough to send you over the edge, with a wanton moan. It crashes over you with so much more intensity than the one that came before it. Your spine locks up, thighs shake as you clench around nothing. Your heart hammers in your chest and between your legs and it’s as if the room is spinning. You twitch in aftershocks, completely spent.
The fog of pleasure has barely lifted when you glance up at Dave, fist still diligently pumping. There’s a fire in his eyes, that untamed excitement.
“Give me one more,” he commands.
“Can’t,” you plead. Need still bubbles at your core but your body is so exhausted from adrenaline and exertion, lust and release.
“You better,” he says.
Dave grinds the vibrator mercilessly against you and you swear aloud. He lets up only for his hand to close around your throat. It’s an unbearable mixture of pleasure and dull ache— the bruising pressure on your clit, the muscles in your thighs taught and burning— underlined by that euphoria. He squeezes around your jaw just hard enough to see stars again.
“That’s right,” he breathes against your cheek, his nose pressed into your temple.
Another orgasm comes almost immediately, pulsing at your core and squeezing through every fiber of your being. This time, you’re quiet, just a high pitched whine like a hurt animal though you’re anything but.
Dave groans. You can hear his teeth gritted though your eyes are shut. He swears and his hot release paints your bare chest, thick and sticky.
Everything stills as you both come down, all loosening muscles and shaky breaths. Dave remains close to you, stroking your cheek. His lips brush your hairline and you notice the smell of his cologne for the first time, something clean and masculine.
Dread should come now. He’s had his fun, now he can do away with you — yet it doesn’t surface.
Slowly Dave stands and tucks himself back into his pants. He almost looks ashamed of himself. You pull your shirt down, covering your stained breasts, and watch Dave smooth his hair.
“So are we good?” you ask.
“If you do what I said,” he answers. “You’re going to get rid of anything you have against me and you’re going to tell your bosses that all you found was a regular guy.”
“Alright, Dave,” you say.
He scowls at you like he doesn’t like your tone. “When I say delete everything, I mean everything,” he says, eyes flitting towards the monitor.
You steal a glance in that direction as well. Dave half naked, still frozen there looking absolutely ruined.
“Understand?” he asks.
“Yes.”
“I’m going to know if you don’t because I’ll be watching you. And if you cross me, I’m going to come back here and I won’t be so nice to you next time,” Dave says.
You wish that threat didn’t make your body light up like a Christmas tree. It’s absolutely reckless. There’s no chance in hell you’re letting go of that piece of treasure and if the consequence is Dave knocking on your door– or letting himself in– that’s a risk you’re willing to take.
It’s as if he knows. Dave scoffs to himself, then fishes his hat off of the floor along with your panties.
“These are mine now,” he says.
And you’re almost sad to see him go.

comments and reblogs always appreciated! or scream at me in the ask box or dms!
Moth's Masterlist // follow @mothandpidgeon-updates and turn on notifications to stay updated with my fics!
#dave york#dave york fic#pedro pascal fic#dave york x f!reader#dave york x hacker!f!reader#equilizer 2#cw: noncon/dubcon
152 notes
·
View notes
Text
January is racing towards its end; where the hell is my time?? And also, let's see if I can get this posted without tumblr eating my password again.
Things that went good:
I mostly got over the breakdown my computer and account issues drove me into last night.
I mailed my professor.
I have mostly caught up with the reading I failed to do last week.
I was a good little computer owner and did a cache clearing, internet chronics clearing, data carrier clearing, defrag, all that good shit. Virus scan is still running, but hasn't found anything so far. It may be the hardware after all.
My reading speed is picking up.
Bought some nice ingredients for good cooking and a new cake recipe I wanna try out. Had no baking energy yesterday, but today, there shall be cake!
Mission Data Rescue is running.
My mom did the dishes so I don't need to do them <3
I have mostly figured out which couples I want to draw for OCkiss Week 2025, and in what situations. No idea if I'll have the time to see the entire plan through, but I love having some motivation to draw, and last year was a lot of fun!
First sketch is done!
Got rid of the sprain in my neck.
Things that went not so good:
My computer keeps fucking me over and I really need to get it to a workshop to find out if this is a hardware or a software issue. This semi-crashing keeps eating my nerves.
I contacted support about the shit my tumblr account keeps doing, and they said to check the security settings, especially regarding two-factor authentication. Problem is, my settings seem to be alright; two-factor blahblah is off, and also the password error specifically only seems to occur when I try to save a post to the drafts. When I logged out by myself and when I got kicked out via clearing out my history, I could get back into my account via the established password no problem. Hm.
I have an unanswered text from my brother on my phone, and he's obviously trying to have a conversation. I'm not sure how to tell him that I think this is a supremely unsuited format without offending his attempt to be social. I'd much rather chat in person, preferably at a time when I'm not having a minor breakdown.
Drawing my OCs is 80% researching helpful references and only 20% drawing.
Despite regular sports, the scales keep being mean to me, and it's demotivating. Why do I even bother?
Things to do today / tomorrow:
Bake a cake.
Check in on my friend; I've been supremely unsocial these last few weeks.
More academical / leisurely reading.
Laundryyyyyy.
Finish reading my myths and fairytales book so I can gush about the illustrations on tumblr.
Things to do these days:
Get this piece of crap to a workshop and accept my sister's offer to work at her computer for a while.
Plan a trip to Bavaria.
More sketches for OCkiss Week!
Woman up, go to the dentist, admit that I missed my appointment and need a new one.
Find a new photography subject for another 12 photos 1 year project, preferably before January is over. Wanted to go for a walk with my mom yesterday, but weather was icky so she didn't want to, and going alone makes no sense since my phone camera isn't working. Technology really hates me rn.
2 notes
·
View notes
Text
How to access Microsoft 365 portal on my mobile device?
In today’s fast-paced digital environment, productivity doesn’t stop when you're away from your desk. Microsoft 365 has revolutionized the way we work by allowing seamless access to essential tools and applications from virtually anywhere. Whether you're responding to emails on the go, editing documents during travel, or attending meetings from your phone, the Microsoft 365 portal ensures that your workflow remains uninterrupted. But how exactly do you access the Microsoft 365 portal on your mobile device?
In this comprehensive guide, we will walk you through every step of accessing the Microsoft 365 portal on a mobile phone or tablet, ensuring a smooth experience from login to usage. We’ll also provide tips for optimizing performance and security, along with troubleshooting advice. This blog is especially useful if you're looking for help with the microsoft365 portal login process.
What is the Microsoft 365 Portal?
Before diving into mobile access, let’s understand what the Microsoft 365 portal is. The Microsoft 365 portal is a centralized dashboard available at portal office com website, which gives users access to Microsoft’s suite of tools like:
Outlook (Email & Calendar)
Word, Excel, PowerPoint (Web versions)
OneDrive (Cloud storage)
Teams (Communication & Collaboration)
SharePoint, OneNote, and more
This portal simplifies workflows by offering everything in one place—whether you're using it for business, education, or personal productivity.
Why Use the Microsoft 365 Portal on a Mobile Device?
Here are some compelling reasons to access the Microsoft 365 portal on your mobile device:
Flexibility: Work from anywhere, anytime.
Real-Time Collaboration: View and edit documents with colleagues in real-time.
Notifications: Get instant alerts for emails, meetings, and Teams messages.
Productivity on the Go: Never miss deadlines, even when you're away from your computer.
With the Microsoft365 portal login on mobile, your office fits in your pocket.
Prerequisites for Mobile Access
Before you begin, ensure the following:
Valid Microsoft 365 Account: This could be a work, school, or personal Microsoft account.
Stable Internet Connection: Wi-Fi or mobile data.
Mobile Device: iOS or Android smartphone/tablet.
Microsoft Authenticator App (Optional): For enhanced security during login.
How to Access Microsoft 365 Portal on Mobile: Step-by-Step Guide
You can access the Microsoft 365 portal on your mobile in two main ways:
Option 1: Access Through a Mobile Web Browser
If you don’t want to install any apps, using a mobile browser is a quick method.
Step 1: Open Your Mobile Browser
Launch Safari, Chrome, or any other browser on your smartphone.
Step 2: Visit the Microsoft 365 Portal URL
Go to portal office com website.
Step 3: Microsoft365 Portal Login
Enter your Microsoft 365 credentials:
Email (e.g., [email protected])
Password
If your organization uses multi-factor authentication (MFA), you may receive a code via SMS, email, or the Microsoft Authenticator app.
Step 4: Dashboard Access
Once logged in, you'll see the main dashboard where you can:
Launch Outlook to check emails.
Open OneDrive for files.
Use web apps like Word and Excel.
Access Teams for communication.
Pro Tip: Bookmark the portal for quicker access in the future.
Option 2: Access Through Microsoft 365 Mobile Apps
Microsoft offers dedicated apps for each service, optimized for mobile usage.
Step 1: Download Microsoft Apps
Visit the Google Play Store or Apple App Store and download the apps you need, such as:
Microsoft Outlook
Microsoft Teams
Microsoft OneDrive
Microsoft Word, Excel, PowerPoint
Microsoft Office App (all-in-one suite)
Step 2: Sign In Using Microsoft365 Portal Login
Once downloaded, open the app and log in using your Microsoft 365 email and password.
You’ll only need to do this once per app unless you log out or uninstall the app.
Step 3: Enable Permissions
Apps may request access to:
Calendar and contacts (for Outlook)
Files and media (for OneDrive)
Notifications (for real-time updates)
Allowing these permissions ensures full functionality.
Benefits of Using Microsoft 365 Mobile Apps
Optimized Interface: Each app is designed for the smaller screen.
Offline Access: View and edit files without internet.
Push Notifications: Stay updated in real-time.
Secure Sync: Files sync with your desktop and cloud storage.
Common Issues During Microsoft365 Portal Login on Mobile
Despite Microsoft’s user-friendly interface, you may occasionally run into issues. Here’s how to troubleshoot:
1. Can’t Log In?
Double-check email and password.
Ensure your account has an active Microsoft 365 subscription.
Reset password if forgotten.
2. MFA Failing?
Make sure your Authenticator app is synced.
Ensure the correct phone number or email is set for recovery.
3. Page Not Loading?
Clear your browser’s cache and cookies.
Try accessing via another browser or switch to mobile apps.
4. App Crashes?
Update the app to the latest version.
Restart your phone.
Reinstall the app.
Security Tips for Accessing Microsoft 365 Portal on Mobile
Security is crucial when accessing corporate data on personal devices. Here’s how to stay safe:
1. Enable Two-Factor Authentication
Use the Microsoft Authenticator app or SMS verification to add a second layer of protection.
2. Keep Apps Updated
Outdated apps may have security vulnerabilities.
3. Avoid Public Wi-Fi
Use a VPN or mobile data when accessing sensitive information.
4. Use Biometric Lock
Enable fingerprint or facial recognition for added security.
5. Log Out When Not in Use
Especially if you're using a shared or public device.
Pro Tips to Enhance Mobile Productivity
Pin Apps to Your Home Screen: Access them faster.
Use Split Screen (Android) or Slide Over (iOS): Work on documents while referencing emails or chats.
Enable Notifications: So you never miss a meeting or message.
Sync Calendars and Contacts: Outlook mobile syncs with your phone’s native apps.
Who Should Use the Microsoft 365 Portal on Mobile?
Remote Workers: Stay productive from any location.
Field Employees: Access files, forms, or schedules instantly.
Students: Attend Teams classes and access assignments.
Small Business Owners: Manage operations on the go.
Anyone Using Microsoft365: Because desktop access isn’t always possible!
Final Thoughts
With the mobile-first shift in modern workplaces, knowing how to access the microsoft365 portal login from your phone or tablet is more important than ever. Whether you prefer using a browser or Microsoft’s suite of apps, the flexibility and power of Microsoft 365 are always at your fingertips.
From checking emails and collaborating on documents to joining Teams meetings, the mobile experience is designed to be just as robust as the desktop version. Just remember to stay secure, keep your apps updated, and optimize your settings for the best experience.
0 notes
Text
LMS Features Checklist: Essential Tools for Effective Online Learning
In today’s digital age, Learning Management Systems (LMS) have become a cornerstone for educational institutions and corporate training programs. Whether you’re an educator, trainer, or business leader, choosing the right LMS with the right features is crucial for seamless learning experiences.

At EdzLMS, we understand the importance of a well-equipped LMS. To help you make an informed decision, we’ve compiled a comprehensive LMS features checklist that covers all the must-have functionalities.
Why Do You Need an LMS Features Checklist?
Before investing in an LMS, it’s essential to evaluate whether the platform meets your specific needs. A well-structured LMS features checklist ensures you don’t overlook critical functionalities that enhance user engagement, streamline administration, and improve learning outcomes.
Here’s a breakdown of the key features to look for in an LMS:
1. User Management & Accessibility
✅ Multi-Role Support – Admins, instructors, learners, and guests should have designated access levels. ✅ Single Sign-On (SSO) – Allows users to log in using existing credentials (Google, Microsoft, etc.). ✅ Mobile Compatibility – Ensures learning on-the-go via smartphones and tablets. ✅ Multi-Language Support – Essential for global teams and diverse learners.
At EdzLMS, our platform offers seamless user management with customizable roles and mobile-friendly access.
2. Course Creation & Content Management
✅ Drag-and-Drop Course Builder – Simplifies course creation without technical expertise. ✅ SCORM & xAPI Compliance – Ensures compatibility with third-party eLearning content. ✅ Multimedia Support – Supports videos, PDFs, quizzes, and interactive content. ✅ Gamification – Badges, leaderboards, and rewards to boost engagement.
Our EdzLMS platform includes an intuitive course builder with gamification features to make learning interactive.
3. Assessment & Tracking
✅ Quizzes & Surveys – Automated grading and customizable assessments. ✅ Certification & Compliance Tracking – Tracks course completion and certifications. ✅ Analytics & Reporting – Monitors learner progress and identifies knowledge gaps.
A strong LMS features checklist includes robust assessment tools to measure effectiveness.
4. Collaboration & Communication
✅ Discussion Forums – Facilitates peer-to-peer interaction. ✅ Live Chat & Webinars – Enables real-time learning sessions. ✅ Notifications & Reminders – Keeps learners updated on deadlines.
EdzLMS integrates discussion boards and live sessions for better collaboration.
5. Integration & Scalability
✅ API & Third-Party Integrations – Connects with CRM, HRMS, and payment gateways. ✅ Cloud-Based Hosting – Ensures scalability and security. ✅ White Labeling & Branding – Customize the LMS to match your brand.
Our platform supports seamless integrations, making it a future-proof choice.
6. Security & Compliance
✅ GDPR & Data Privacy Compliance – Protects sensitive learner data. ✅ Regular Backups – Prevents data loss. ✅ Secure Authentication – Two-factor authentication (2FA) for added security.
Security is a top priority in our LMS features checklist at EdzLMS.
Conclusion
Choosing the right LMS requires careful evaluation of features that align with your learning goals. This LMS features checklist ensures you select a platform that enhances engagement, simplifies administration, and scales with your needs.
At EdzLMS, we offer a powerful, user-friendly LMS packed with all these essential features and more. Ready to transform your learning experience? Explore EdzLMS today!
FAQ
1. What is the most important feature in an LMS?
A user-friendly interface, robust course creation tools, and strong analytics are critical.
2. How does gamification improve learning?
Gamification boosts engagement through rewards, badges, and leaderboards.
3. Can an LMS be customized for my organization?
Yes! Platforms like EdzLMS offer white-labeling and branding options.
4. Is mobile compatibility necessary for an LMS?
Absolutely, as learners increasingly access courses via smartphones.
5. How does an LMS ensure data security?
Features like GDPR compliance, encryption, and 2FA protect sensitive data.By following this LMS features checklist, you can confidently choose an LMS that meets your needs. For a feature-rich, scalable solution, check out EdzLMS today!
0 notes
Text
How to Link Your Tashan Game Login with Social Media Accounts
Linking your Tashan Game login to your social media accounts is one of the smartest ways to level up your gaming experience. Not only does it make logging in faster, but it also helps you secure your account, sync your progress, and unlock special social-only rewards.
In this article, we’ll walk you through how to link your Tashan Game account with platforms like Facebook, Google, and Instagram, and explain why doing so is a major game-changer in 2025.
🎯 Why Link Your Tashan Game to Social Media?
Before we get into the how-to, let’s break down the benefits of linking your account:✅ Benefit🎮 What It Means for You🔐 Account RecoveryEasily recover login if you forget your password or lose your device⚡ One-Tap LoginNo need to type credentials each time—just tap and play🔁 Progress SyncSave your scores, wallet, and rewards across devices🎁 Exclusive RewardsSome games offer bonuses for social-linked users📲 Faster KYC VerificationSocial accounts often speed up verification and account trust
🔗 How to Link Your Tashan Game Login to Social Accounts
Here’s a step-by-step guide for the most popular platforms:
🔵 1. Link with Facebook
Open the Tashan Game app or website
Go to Settings > Account > Linked Accounts
Tap on “Link Facebook”
A Facebook login window will pop up—log in and authorize access
Done! Your game will now link to your Facebook account
💡 Tip: Make sure you're logged into the right Facebook account before linking.
🔴 2. Link with Google Account
Navigate to the “Account” section in your profile
Click or tap on “Connect with Google”
Choose your preferred Google account
Confirm and accept any permission prompts
Your Tashan Game login is now connected to Google
📲 This is especially useful for Android users who use Google for app sign-ins.
📸 3. Link with Instagram
⚠️ Note: Not all versions of Tashan Game support Instagram linking yet, but if available:
Go to Settings > Social Media Integration
Tap on Instagram
You’ll be redirected to an Instagram login page
Enter your credentials and approve access
You’re linked!
🔓 Some seasonal challenges or tournaments are Instagram-exclusive—linking your account can get you in early.
💬 What If You Get an Error While Linking?
Sometimes, linking doesn’t work on the first try. Here’s what to check:
App permissions: Ensure Tashan Game has permission to access your social profile
Pop-up blockers: Disable them if linking via browser
Account already linked: You might have linked that social account to another Tashan profile
Outdated app: Update to the latest version for best compatibility
🛠️ Still not working? Try logging out and restarting both apps (Tashan Game and the social media platform).
🛡️ Is It Safe to Link Social Accounts?
Yes—as long as you're using the official app or website, linking social accounts is secure. Tashan Game uses standard encryption and never posts anything on your behalf without your permission.
To stay extra safe:
Use a strong password on your social accounts
Enable two-factor authentication
Never share your Tashan or social login credentials with others
🔄 How to Unlink a Social Media Account (If Needed)
If you change your mind, unlinking is simple:
Go to Settings > Linked Accounts
Tap the social platform you want to disconnect
Select “Unlink” or “Remove”
Confirm your choice
⚠️ Important: Make sure you have another login method (email or mobile) set up before unlinking!
🎁 Bonus: What You Might Unlock After Linking
Depending on your region and version of Tashan Game, you may receive:
💸 Free bonus coins
🎫 Entry to exclusive tournaments
📢 Notification of special offers via your social inbox
👥 Ability to invite friends and earn referral rewards
✅ Final Thoughts
Linking your Tashan Game login with social media is a quick, smart move that makes your account more secure, more convenient, and often more rewarding.
Whether you’re using Facebook, Google, or Instagram—take a minute today to connect your profile and enjoy all the extra perks that come with it.
TL;DR – Quick Recap
🔗 Link via Settings > Linked Accounts
🚀 Enjoy fast logins, synced progress, and recovery support
🎁 Get potential bonuses and early access perks
🔒 Stay safe with 2FA and never share login details
]
1 note
·
View note
Text
Playinexchange: The Betting Platform Built for Everyday Winners
Online betting is no longer just about placing a few wagers and hoping for the best. Today’s users expect more—they want seamless navigation, responsive odds, meaningful rewards, and most importantly, a platform that fits into their daily life. playinexchange is answering that call with a sports betting experience that’s both refined and incredibly functional, especially for bettors who demand reliability with every click.
What makes playinexchange stand out from the pack is how it eliminates unnecessary friction. Everything from account registration to cashing out a win is designed to be fast and intuitive. You don’t need to dig through menus or decode complicated interfaces. The homepage is sleek, sports categories are well-organized, and your bet slip updates in real time, just as you’d expect from a high-end platform.
Live betting is one of the biggest strengths here. As matches progress, playinexchange delivers real-time odds that refresh instantly, allowing bettors to act quickly and strategically. This isn’t just useful—it’s empowering. It turns the average fan into a more engaged participant, creating an exciting loop of watching, analyzing, and wagering that adds serious energy to any sporting event.
Another feature that bettors rave about is device flexibility. Whether you're at home watching the match on your TV or out and about checking your phone during halftime, playinexchange adapts effortlessly. No app downloads required, no lag, and no drop in functionality. The mobile browser version is just as powerful as the desktop version, keeping users fully connected wherever they go.
Rewards are plentiful and, more importantly, achievable. New users are welcomed with a solid bonus, but the platform doesn’t stop there. Weekly cashback offers, milestone-based incentives, and occasional surprise promos keep things exciting for regular users. These are real opportunities to boost your bankroll—not just flashy numbers with impossible conditions.
When it comes to security, playinexchange ticks all the boxes. Every transaction is protected by encrypted connections and fraud prevention protocols. Users also have access to two-factor authentication for added peace of mind. Whether you’re depositing ₹500 or withdrawing a big win, you can do so with full confidence.
Local integration is another major benefit. The platform supports regional payment options like UPI, Paytm, and Google Pay, and the customer support team offers assistance in multiple languages. These small details create a more personalized experience, making every user feel valued, no matter where they’re logging in from.
What really elevates playinexchange above the noise is its growing community-driven features. From prediction leagues and shared bet slips to interactive match discussions, users can feel part of something bigger than themselves. It's this shared sense of strategy, success, and friendly competition that transforms betting from a solo habit into a social event.
In short, playinexchange is built for the everyday user who wants more out of their betting journey—more control, more excitement, and more rewards. If you’ve been stuck with outdated platforms or apps that treat you like just another number, this might just be the upgrade your game needs. Betting can be smart, fun, and secure—and playinexchange is proof.
0 notes
Text
Squarespace Login: Your Gateway to Effortless Website Management
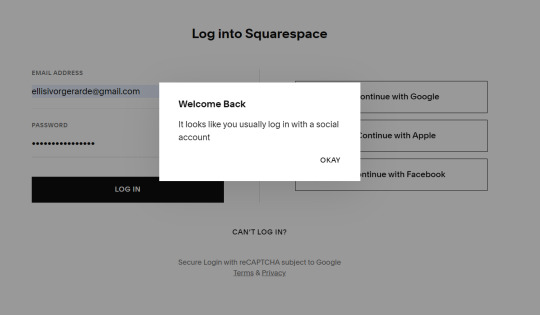
In today’s digital age, having an online presence is vital for businesses, creatives, and individuals. Squarespace stands out as one of the leading platforms that provide an all-in-one solution for building and managing websites. The Squarespace login portal serves as the essential access point to control every aspect of your website, from content updates to analytics. In this article, we will explore the features, benefits, and steps to access the Squarespace login, ensuring you make the most out of this powerful platform.
What is Squarespace Login?
The Squarespace login portal is the entryway to managing your Squarespace website. Once logged in, users can:
Edit their website content and layout.
Manage online stores and payment gateways.
Access marketing tools and insights.
View website analytics to track performance.
Whether you are a beginner or an experienced user, the login squarespace offers an intuitive interface to streamline website management.
How to Access Squarespace Login
Here are the steps to log in to your Squarespace account:
Visit the Squarespace Website: Open your browser and navigate to www.squarespace.com.
Click on “Login”: Locate the login button at the top-right corner of the homepage.
Enter Your Credentials: Input your registered email address and password.
Two-Factor Authentication (if enabled): Verify your login through a code sent to your registered email or phone.
Dashboard Access: Once logged in, you’ll land on your website dashboard, where you can begin managing your site.
Key Features Accessible After Squarespace Login
Website Builder Tools: Update pages, tweak layouts, and customize templates effortlessly.
E-Commerce Integration: Manage products, track orders, and configure payment settings for your online store.
Analytics and Insights: Monitor visitor traffic, conversion rates, and other essential metrics to optimize website performance.
Marketing Features: Access email marketing campaigns, SEO settings, and promotional tools to expand your reach.
Customer Support: Use the help center or live chat to resolve any technical or account-related queries directly from your Squarespace login dashboard.
Benefits of Using Squarespace Login
Centralized Management: Manage all aspects of your website from one intuitive dashboard.
Time Efficiency: Quick access to editing tools and features saves valuable time.
Mobile Accessibility: Log in and manage your website from any device, ensuring flexibility and convenience.
Enhanced Security: Two-factor authentication ensures your account remains secure.
Scalability: Whether you’re running a personal blog or an e-commerce store, Squarespace login adapts to your needs.
Common Squarespace Login Issues and Solutions
Forgot Password: Solution: Use the “Forgot Password” option to reset it.
Login Errors: Solution: Clear browser cache or try accessing the portal from another device.
Two-Factor Authentication Issues: Solution: Ensure you have access to your registered email or phone number for verification.
Account Lockout: Solution: Contact Squarespace support to regain access.
FAQs
Q1. What is Squarespace login?
Ans. The Squarespace login is your access portal to manage your website, e-commerce store, and analytics.
Q2. How do I reset my Squarespace login password?
Ans. Use the “Forgot Password” option on the login page to reset your password.
Q3. Can I access Squarespace login from mobile devices?
Ans. Yes, Squarespace offers a mobile-friendly interface, making it easy to manage your website on the go.
Q4. Is Squarespace login secure?
Ans. Absolutely. Squarespace employs encryption and two-factor authentication to protect your account.
Q5. Can multiple users log in to the same Squarespace account?
Ans. Yes, you can grant contributor access to team members with specific roles and permissions.
Q6. Why can’t I log in to my Squarespace account?
Ans. Ensure you’re using the correct email and password. If issues persist, reset your password or contact support.
Q7. Can I log in using Google or Apple accounts?
Ans. Yes, Squarespace allows login via linked Google or Apple accounts for faster access..
Conclusion
The Squarespace login portal is the backbone of effective website management, offering seamless access to powerful tools and features. Whether you’re updating content, tracking performance, or managing an online store, the platform provides everything you need to maintain a professional and engaging online presence. By mastering the use of Squarespace login, you’ll unlock the full potential of your website, ensuring growth and success in the digital realm.
#technologies#technicalanalysis#technique#tech#techinnovation#technically#technician#technical difficulties
0 notes
Text
BDG Game Login: The Key to Unlocking Endless Possibilities

In the realm of online gaming, BDG Game stands out as a vibrant and engaging platform that offers players a unique blend of creativity, adventure, and community. Whether you’re a seasoned gamer or new to the world of virtual experiences, logging into BDG Game is your first step toward unlocking a treasure trove of opportunities. In this article, we’ll explore the significance of the BDG Game login process and how it can open the door to endless possibilities.
Why BDG Game?
Before we delve into the login details, let’s take a moment to understand why BDG Game is the go-to choice for many players:
Creative Expression: The game provides a platform where you can design and build your own spaces, characters, and stories. Your imagination is the only limit!
Engaging Adventures: With a variety of quests and challenges, BDG Game keeps players on their toes, offering new experiences and stories to discover.
Community Interaction: Connect with a diverse group of players, participate in events, and make lasting friendships in a supportive and engaging environment.
Continuous Updates: The game regularly introduces new content, ensuring that your adventures are always fresh and exciting.
Step-by-Step Guide to BDG Game Login
Now that you’re excited about the possibilities, let’s walk through the login process step by step to ensure a smooth entry into the game.
Step 1: Visit the BDG Game Website
Begin your journey by navigating to the official BDG Game website. This is where all the action starts.
Step 2: Locate the ‘Log In’ Button
On the homepage, you’ll find the ‘Log In’ button, typically located at the top right corner of the screen. Click on it to access the login page.
Step 3: Enter Your Credentials
You will be prompted to enter your login details:
Username or Email: Input the username or email address associated with your BDG Game account.
Password: Type in your password. Remember that passwords are case-sensitive, so ensure that you enter it accurately.
Step 4: Two-Factor Authentication (if applicable)
If you’ve enabled two-factor authentication for added security, you will need to verify your identity. Check your email or authentication app for the verification code and enter it as prompted. This website bdg game
Step 5: Click ‘Log In’
Once you’ve entered your credentials and completed any necessary verification steps, click the ‘Log In’ button. If your details are correct, you’ll be granted access to your account.
Step 6: Troubleshooting Login Issues
If you encounter any difficulties while trying to log in, here are some common issues and solutions:
Forgot Password: If you can’t remember your password, click the ‘Forgot Password?’ link on the login page. Follow the prompts to reset your password.
Account Locked: After multiple unsuccessful login attempts, your account may be temporarily locked. Wait a few minutes and try again.
Browser Issues: Clearing your browser’s cache or trying a different browser can often resolve login problems.
Step 7: Start Your Adventure
Congratulations! You are now logged into BDG Game. Here’s what to do next:
Create Your Avatar: Personalize your character to reflect your style. This avatar will represent you in the game world.
Explore the Game World: Dive into various activities—whether building your dream home, embarking on quests, or interacting with other players, the possibilities are limitless.
Join the Community: Engage with fellow players through forums, social media, or in-game chats. Sharing experiences can greatly enhance your adventure.
Conclusion
Logging into BDG Game is more than just accessing a virtual space; it’s about unlocking a world filled with endless possibilities. With opportunities for creativity, adventure, and community engagement, BDG Game offers a unique gaming experience that can enrich your life in various ways. Follow this guide, log in today, and embark on a journey that promises excitement, creativity, and connection. Your adventure awaits—dive into the world of BDG Game and start exploring!
0 notes
Text
do i need a vpn for torrenting showbox
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do i need a vpn for torrenting showbox
VPN for torrenting
When it comes to torrenting, using a Virtual Private Network (VPN) is crucial in ensuring your online activities remain private and secure. A VPN for torrenting works by encrypting your internet connection and routing it through a remote server, thereby masking your IP address and making it difficult for others to track your online behavior.
One of the main reasons why using a VPN for torrenting is important is to maintain anonymity. While torrenting itself is not illegal, downloading copyrighted material without permission is against the law in many countries. By using a VPN, you can protect your identity and avoid potential legal consequences.
Additionally, a VPN can also help you bypass geographical restrictions that some content providers may place on their websites. By connecting to a VPN server in a different location, you can access content that may otherwise be unavailable in your region.
When choosing a VPN for torrenting, it's important to opt for a provider that offers strong encryption, a no-logs policy, and high-speed connections to ensure smooth file-sharing. Some popular VPN services known for their torrenting capabilities include NordVPN, ExpressVPN, and CyberGhost.
In conclusion, using a VPN for torrenting is a smart choice to safeguard your privacy and security while engaging in file-sharing activities. By encrypting your internet connection and masking your IP address, a VPN helps you stay anonymous and avoid potential risks associated with torrenting.
Showbox streaming
Showbox streaming is a popular online platform that allows users to watch a wide variety of movies and TV shows for free. This streaming service has gained immense popularity due to its extensive library of content, ranging from the latest blockbuster movies to classic TV series. Users can easily access Showbox on their mobile devices, tablets, and computers, making it a convenient option for entertainment on the go.
One of the key features of Showbox is its user-friendly interface, which makes it easy to search for and discover new content. Users can browse through different genres, release years, and popular titles to find something that suits their preferences. Additionally, Showbox offers the option to download movies and TV shows for offline viewing, making it ideal for users who want to watch content without an internet connection.
Another advantage of Showbox streaming is its regular updates with the latest movies and TV shows. This ensures that users have access to fresh content and can stay up-to-date with the latest releases. The platform also provides high-quality streaming, allowing users to enjoy their favorite movies and shows in crisp detail and clear audio.
While Showbox offers a wide range of content for free, users should be aware of the legality of streaming copyrighted material. It is important to use Showbox and similar services responsibly and to be aware of the copyright laws in your region. Overall, Showbox streaming provides a convenient and enjoyable way to access a vast library of entertainment content at no cost.
Internet privacy protection
Internet privacy protection is a critical concern in today's digital age as more and more of our personal information is shared online. With the increase in cyber threats and data breaches, safeguarding our privacy on the internet has never been more important.
There are several steps individuals can take to protect their privacy online. One of the most basic measures is to use strong, unique passwords for each online account. This can help prevent unauthorized access to your personal information. Additionally, enabling two-factor authentication adds an extra layer of security by requiring a second verification step before logging in.
Another important aspect of internet privacy protection is to be mindful of the information you share online. Avoid oversharing personal details on social media platforms and be cautious about the websites you visit and the links you click on. Phishing scams and malicious websites can trick users into revealing sensitive information or installing malware on their devices.
Using a virtual private network (VPN) can also enhance your internet privacy by encrypting your online activity and masking your IP address. This can help protect your data from being intercepted by hackers or other third parties.
Overall, practicing good internet hygiene and staying informed about the latest cybersecurity threats is crucial in safeguarding your online privacy. By taking proactive steps to protect your personal information, you can reduce the risk of falling victim to privacy violations and cyber attacks in the digital realm.
Legal implications of torrenting
Torrenting has become a widespread method of sharing and downloading digital content such as movies, music, software, and more. While torrenting itself is not illegal, the content that is often shared through torrents may be protected by copyright laws. As a result, there are various legal implications associated with torrenting that users should be aware of.
One of the main legal concerns with torrenting is copyright infringement. When you download or distribute copyrighted material without the permission of the owner, you are violating their rights. This can lead to legal action being taken against you, resulting in potential fines or even criminal charges.
Many copyright holders actively monitor torrenting websites and networks to identify individuals who are sharing their content illegally. They may send cease and desist notices or take legal action against those found infringing on their copyrights. It is important to understand that just because content is freely available on a torrent site does not mean it is legal to download or distribute.
In some countries, there are strict laws in place to combat online piracy, and penalties for copyright infringement can be severe. It is crucial for torrent users to educate themselves on the legal implications of their actions and to use torrents responsibly. Using legal alternatives such as purchasing or streaming content from authorized sources can help users avoid the risks associated with torrenting.
In conclusion, while torrenting itself is not illegal, the unauthorized sharing or downloading of copyrighted material through torrents can have serious legal consequences. It is important for users to be aware of the legal implications of torrenting and to make informed decisions to avoid potential legal issues.
Copyright infringement risks
Copyright infringement is a serious offense that can have legal consequences for individuals or businesses. Understanding the risks associated with copyright infringement is important to protect your intellectual property and avoid potential legal issues.
One major risk of copyright infringement is facing a lawsuit from the original copyright holder. If you use someone else's work without permission, they have the right to take legal action against you. This can result in hefty fines, payment of damages, and even having to cease using the copyrighted material altogether. In some cases, copyright infringement can lead to criminal charges, especially if it is deemed to be intentional or for commercial gain.
Another risk of copyright infringement is damage to your reputation. Being known for using others' work without permission can harm your credibility and integrity in your industry. It can also lead to loss of trust from customers, partners, and other stakeholders.
Moreover, search engines like Google penalize websites that contain copyrighted material without authorization. This can negatively impact your website's search engine ranking and visibility online. It's crucial to ensure that all content on your website is original or properly licensed to avoid facing penalties from search engines.
To mitigate the risks of copyright infringement, it's essential to always obtain permission before using someone else's work, create original content, and properly attribute sources when necessary. By respecting copyright laws and protecting intellectual property rights, you can safeguard your reputation and business from the potential consequences of copyright infringement.
0 notes
Text
do i need a vpn if i dont use wifi
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do i need a vpn if i dont use wifi
VPN for cellular data
A Virtual Private Network (VPN) is a powerful tool that allows users to protect their online privacy and security, regardless of the network they are connected to. While VPNs are commonly used on Wi-Fi networks, they are also valuable for safeguarding cellular data connections.
Using a VPN for cellular data adds an extra layer of encryption to your internet traffic, making it more difficult for hackers or malicious third parties to intercept your data. This is particularly important when using public Wi-Fi networks or when accessing sensitive information on-the-go.
In addition to enhancing security, a VPN for cellular data can also help users bypass geo-restrictions and access content that may be blocked in their region. By connecting to a VPN server in a different location, users can access websites, streaming services, or apps that may otherwise be restricted in their current location.
Furthermore, a VPN can help prevent your Internet Service Provider (ISP) from tracking your online activities and selling your browsing data to third parties. By encrypting your connection and masking your IP address, a VPN ensures that your online activities remain private and anonymous.
When choosing a VPN for cellular data, it's essential to opt for a reputable service provider that offers robust encryption, a strict no-logs policy, and fast connection speeds. By investing in a reliable VPN service, users can enjoy a safer, more private online experience, whether they are using Wi-Fi or cellular data connections.
Internet security without VPN
In today's digital age, ensuring internet security is of utmost importance. While VPNs (Virtual Private Networks) are commonly used to protect online privacy and security, there are alternative measures one can take to safeguard their information without using a VPN.
One essential step towards internet security without a VPN is utilizing secure and encrypted connections. Websites that have HTTPS in their URL provide a secure connection between your device and the site you are visiting, encrypting data exchanged between the two. It is crucial to avoid inputting personal information on websites that do not have HTTPS to prevent potential data breaches.
Another effective strategy is to regularly update software and applications on devices. Software updates often contain security patches that fix vulnerabilities cybercriminals could exploit. By keeping all devices and programs up to date, users can lower the risk of security breaches and protect their data from unauthorized access.
Furthermore, implementing strong and unique passwords for different accounts is vital for internet security. Password managers can help generate complex passwords and store them securely, reducing the likelihood of accounts being compromised by hackers.
Additionally, activating two-factor authentication adds an extra layer of security to online accounts. By requiring a secondary code in addition to a password, two-factor authentication significantly enhances security and minimizes the risk of unauthorized access.
By adopting these practices and staying vigilant while browsing the internet, individuals can enhance their online security without solely relying on VPN services. Prioritizing internet security is crucial in safeguarding personal information and protecting against potential cyber threats.
Online privacy and VPN
In the digital age, online privacy has become a growing concern for internet users worldwide. With the increasing number of cyber threats and data breaches, protecting one's privacy while surfing the web has never been more crucial. This is where Virtual Private Networks (VPNs) come into play.
VPNs work by creating a secure and encrypted connection between the user's device and the internet. By routing your internet traffic through a VPN server, your data is shielded from hackers, government surveillance, and other prying eyes. This means that your online activities, such as browsing history, personal information, and location, remain anonymous and inaccessible to third parties.
Using a VPN not only enhances your online privacy but also offers other benefits. For instance, you can bypass geo-restrictions and access content that may be restricted in your region. Additionally, VPNs can provide an extra layer of security when using public Wi-Fi networks, protecting you from potential threats lurking on unsecured connections.
When choosing a VPN service, it's essential to opt for a reputable provider that prioritizes user privacy and security. Look for features like a no-logs policy, strong encryption protocols, and a kill switch function to ensure maximum protection.
In conclusion, protecting your online privacy with a VPN is a proactive step in safeguarding your personal information and maintaining anonymity while navigating the digital realm. By investing in a reliable VPN service, you can browse the web with peace of mind and take control of your online privacy.
VPN necessity for non-WiFi users
Title: The Vitality of VPNs for Non-WiFi Users
In an increasingly digital world, where connectivity is paramount, the need for safeguarding one's online activities has never been more critical. While many discussions about Virtual Private Networks (VPNs) often revolve around securing public Wi-Fi connections, their importance for non-WiFi users is equally significant.
Non-WiFi users, including those relying solely on mobile data or wired connections, face unique security challenges. Without the encryption provided by a VPN, their online activities are vulnerable to interception and surveillance. Hackers, ISPs (Internet Service Providers), and even government agencies can potentially monitor and track their browsing habits, compromising their privacy and security.
Moreover, non-WiFi users often access the internet through mobile networks, which are inherently less secure than wired connections. Mobile data transmissions are susceptible to interception, making it easier for malicious actors to intercept sensitive information such as passwords, financial details, and personal communications.
By using a VPN, non-WiFi users can create a secure tunnel for their internet traffic, encrypting it from end to end. This encryption ensures that their data remains private and inaccessible to third parties, even when using potentially insecure connections. Additionally, VPNs mask the user's IP address, providing anonymity and preventing websites from tracking their online behavior.
Furthermore, VPNs offer benefits beyond security for non-WiFi users. They can bypass geo-restrictions, allowing access to region-locked content and services. This flexibility is particularly valuable for travelers or individuals living in regions with internet censorship.
In conclusion, VPNs are not exclusive to WiFi users; they are indispensable tools for safeguarding the online privacy and security of non-WiFi users as well. Whether browsing on mobile networks or through wired connections, incorporating a VPN into one's digital routine is essential for maintaining privacy, security, and freedom on the internet.
Cybersecurity measures for mobile data
Title: Safeguarding Your Mobile Data: Essential Cybersecurity Measures
In an era where mobile devices have become an indispensable part of our daily lives, ensuring the security of our mobile data is paramount. With the increasing prevalence of cyber threats targeting smartphones and tablets, implementing robust cybersecurity measures is essential to protect sensitive information from falling into the wrong hands.
First and foremost, it is crucial to keep your mobile device's operating system and apps up to date. Developers frequently release security patches and updates to address vulnerabilities and enhance protection against emerging threats. Regularly installing these updates helps fortify your device's defenses against potential exploits.
Utilizing strong, unique passwords or passphrases for device unlock codes and account logins is another fundamental aspect of mobile data security. Avoid using easily guessable combinations and refrain from reusing passwords across multiple accounts to minimize the risk of unauthorized access.
Enabling device encryption adds an extra layer of security by scrambling data stored on your device, making it unreadable without the correct decryption key. Most modern smartphones offer built-in encryption features that can be activated through device settings, safeguarding your data from prying eyes in the event of theft or loss.
Implementing biometric authentication methods, such as fingerprint or facial recognition, provides an additional level of security by requiring physical characteristics unique to the user for device access. These methods offer enhanced convenience without compromising security, as they are inherently more difficult to spoof than traditional passwords.
Furthermore, exercising caution when connecting to public Wi-Fi networks is essential to prevent unauthorized access to your mobile data. Avoid accessing sensitive information or conducting financial transactions over unsecured networks, and consider using a virtual private network (VPN) for an added layer of encryption and privacy.
By following these cybersecurity best practices, you can effectively safeguard your mobile data against potential threats and enjoy peace of mind knowing that your personal information remains protected. Remember, proactive measures today can prevent costly data breaches tomorrow.
0 notes
Text
does express vpn give you your password
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does express vpn give you your password
ExpressVPN password retrieval
In case you've forgotten your ExpressVPN password, don't worry as recovering it is a straightforward process. To reset your password, you need to follow a few simple steps provided by ExpressVPN.
First, go to the ExpressVPN website and locate the "Sign In" option. Click on it, and then select the "Forgot your password?" link. You will be directed to a page where you need to enter the email address associated with your ExpressVPN account. Once you've submitted your email, you should receive instructions on how to reset your password in your inbox.
Check your email for a message from ExpressVPN containing a password reset link. Click on the link provided in the email, which will take you to a page where you can create a new password for your account. Make sure to choose a strong and unique password to enhance the security of your ExpressVPN account.
After you've successfully set a new password, you can sign in to your ExpressVPN account using your updated login credentials. It's essential to keep your password secure and avoid sharing it with others to maintain the privacy and security of your online activities while using ExpressVPN.
By following these steps, you can easily retrieve your ExpressVPN password and continue to enjoy safe and private internet browsing with the added security provided by ExpressVPN's encryption services.
ExpressVPN account security
In today’s digital age, online security is paramount, especially when it comes to protecting your personal information and data. ExpressVPN is a popular choice among internet users for maintaining privacy and security while browsing the web. One of the key features that ExpressVPN offers is robust account security measures to ensure that your online activities remain safe and secure.
When you create an account with ExpressVPN, you are required to choose a strong and unique password. This password is encrypted and securely stored to prevent unauthorized access to your account. Additionally, ExpressVPN offers the option of enabling two-factor authentication for an extra layer of security. Two-factor authentication requires a secondary verification step, such as entering a unique code sent to your mobile device, to access your account.
ExpressVPN also utilizes advanced encryption protocols to safeguard your data and ensure a secure connection while using the VPN service. This encryption helps protect sensitive information such as your IP address, browsing history, and online communications from potential cyber threats.
Moreover, ExpressVPN has a strict no-logs policy, meaning that they do not collect or store any information about your online activities while using their service. This commitment to privacy ensures that your data remains confidential and cannot be compromised.
Overall, ExpressVPN goes above and beyond to prioritize account security and safeguard your online privacy. By implementing industry-leading security measures and privacy practices, ExpressVPN provides users with peace of mind knowing that their sensitive information is protected while browsing the internet.
Password management with ExpressVPN
Title: Enhance Your Online Security with ExpressVPN's Password Management Features
In an era where cyber threats loom large, safeguarding your online presence has become paramount. While many focus solely on securing their network through VPNs like ExpressVPN, overlooking password management can leave a significant vulnerability. Fortunately, ExpressVPN offers more than just a secure tunnel for your internet traffic; it also provides robust password management features to fortify your digital defenses.
One of the primary concerns in the digital realm is the reuse of passwords across multiple platforms. This practice, while convenient, exposes users to immense risks. ExpressVPN addresses this issue with its password management tool, allowing users to generate strong, unique passwords for each account effortlessly. By doing so, the likelihood of a single password compromise affecting multiple accounts diminishes significantly, bolstering overall security.
Moreover, ExpressVPN's password management integrates seamlessly with its existing suite of security solutions. Users can access their stored passwords across devices, ensuring convenience without compromising security. Additionally, the tool employs advanced encryption techniques to safeguard sensitive information, providing peace of mind even in the event of a data breach.
Furthermore, ExpressVPN's password management tool incorporates features such as auto-fill and password strength assessment, streamlining the user experience while promoting good password hygiene. By encouraging the use of complex, unique passwords, it empowers individuals to take proactive measures against cyber threats.
In conclusion, while VPNs are essential for securing your online activities, complementing them with robust password management is equally crucial. ExpressVPN's integrated password management features offer a comprehensive solution, enabling users to fortify their digital defenses effortlessly. By embracing these tools, individuals can navigate the digital landscape with confidence, knowing their sensitive information remains protected from prying eyes.
Forgot ExpressVPN password
Forgetting your ExpressVPN password can be a frustrating experience, but fear not, as there are steps you can take to regain access to your account. Here is a guide to help you reset your ExpressVPN password and get back to safely browsing the web.
If you've forgotten your ExpressVPN password, the first step is to visit the ExpressVPN website and click on the "Sign In" button. Once there, click on the "Forgot your password?" link below the login fields. You will be prompted to enter the email address associated with your ExpressVPN account. After submitting your email address, you will receive an email with instructions on how to reset your password.
In the email you receive, there will be a link that will direct you to a page where you can create a new password for your ExpressVPN account. Make sure to choose a strong password that you will remember, but that is also secure to protect your online privacy.
If you do not see the password reset email in your inbox, be sure to check your spam or junk folder as it may have been filtered there. Additionally, you may want to add ExpressVPN to your email's safe sender list to ensure that you receive future communications from them.
By following these simple steps, you can quickly and easily reset your ExpressVPN password and continue to enjoy secure and private internet browsing. Don't let a forgotten password stand in your way – take action today and regain access to your account.
ExpressVPN login credentials
ExpressVPN Login Credentials: Securing Your Online Privacy
In today's digital landscape, safeguarding your online privacy is paramount. With cyber threats on the rise and data breaches becoming increasingly common, using a reliable VPN service like ExpressVPN is crucial for protecting your sensitive information. However, ensuring the security of your VPN login credentials is equally important.
Your ExpressVPN login credentials consist of two key components: your username and password. These credentials grant you access to ExpressVPN's network of servers, allowing you to encrypt your internet connection and browse the web anonymously. Here's how you can ensure the security of your ExpressVPN login credentials:
Choose a Strong Password: When creating your ExpressVPN account, select a strong and unique password that combines letters, numbers, and special characters. Avoid using easily guessable information such as your name or birthdate.
Enable Two-Factor Authentication (2FA): ExpressVPN offers the option to enable two-factor authentication for added security. By activating 2FA, you'll receive a one-time verification code via email or SMS whenever you attempt to log in, adding an extra layer of protection to your account.
Keep Your Credentials Confidential: Treat your ExpressVPN login credentials like you would your banking information. Avoid sharing your username and password with anyone, and be cautious of phishing attempts that may try to trick you into disclosing your login details.
Regularly Update Your Password: Periodically change your ExpressVPN password to mitigate the risk of unauthorized access. Set a reminder to update your password every few months, and avoid reusing old passwords across multiple accounts.
Monitor Your Account Activity: Routinely review your ExpressVPN account activity to ensure there are no unauthorized login attempts. If you notice any suspicious activity, immediately change your password and contact ExpressVPN's support team for assistance.
By following these best practices, you can enhance the security of your ExpressVPN login credentials and enjoy a safer and more private online experience. Remember, protecting your digital privacy starts with safeguarding your login credentials.
0 notes
Text
✨ Internet Safety ✨
For our generation today, the internet is probably the safest place to be in. People can be whoever they want, express whatever they want, and enjoy themselves however they want. I must admit, I would also say that I couldn’t live without the internet. Internet is just the solution to every problem, right? Now, we can even earn money in the comfort of our rooms with the help of the internet. Should we spend hours travelling just to buy stuff? Nah, we got the internet! With just several clicks we can already make an order and just wait on our couch to receive it. Oh no, COVID-19 ruled the world! No worries, we are backed up by the internet. Online classes, online transactions, online dating. You name it. The internet is there for us, or is it? Is it our safe haven?
We have put so much trust in the internet, but we didn’t know it can also be our biggest predator. Online transactions were fun until you got scammed and lost all your money. Online dating them feel loved until the person they were talking to is a catfish. Streaming online made him famous and rich, until his account got hacked. And there are still millions of stories out there that should awake us from believing that the internet is the safest thing in the world.

Below are some possible dangers you could encounter online.
1. Cyberbullying
I’m sure many of you have heard of this. But even though we are fully aware of it, it is still one of the major problems until now. As we casually scroll in our social media feeds, it is already normal for us to see people making fun of or “bashing” other people. It became so prevalent that we could call it a normal thing. According to UNICEF (2019), one in three young people has said that they have been a victim of cyberbullying and that it affected almost half of the Filipino children aged 13-17. We need to know that even a single word like “tanga” or “bobo” we see in our social media platforms and online gaming worlds could affect or traumatize us greatly.

2. Data Being Stolen
Some people nowadays are getting better at doing this. They can steal your money from your accounts, apply for a loan or credit card using your name, or sell your information to an online criminal as well. The hidden website is packed with criminals who purchase and sell stolen personal data. If your data is stolen, you can experience spam attacks. But most of these data thefts try to steal sensitive information, such as your credit card or personal information to commit identity theft.

3. Exposure to Inappropriate Material
Another risk especially for children and teenagers are exposure to inappropriate materials that are sexual, hateful, or violent. The chance and probability for children to look at anything inappropriate rely on how much they do online as they get more active online at a younger age. Whether it's a free-time graphic pop-up commercial, children's cartoon characters in adult circumstances or a self-harm forum, an innocent search might expose these children to contents that make them feel puzzled and angry. Some of the inappropriate content includes pornographic material, content containing swearing, sites that encourage racism, violence, terrorism, or even suicide, sexism sites, or gambling sites, and so on.

Based on my own experiences, here are some tips I would like to share to you to look after your privacy and secure your internet safety:
1. Keep your software up-to-date
Not only will you get a better program experience, but you will also be able to iron out your security issues. But the reason why you must keep it updated is that hackers are fast enough to become aware of certain software’s vulnerabilities, thus could harm your computer system and personal data. If you avoid doing these updates, you are bound to face persistent bugs, data loss, malware infection, and of course security issues.
2. Update your passwords
Why do we need to constantly change our passwords? So that we can reduce the risk of other people having access to our accounts, thus corrupt our personal data. Using strong passwords is necessary for us to prove our identity in our accounts, websites, or our computer itself (Wright, 2021). My tip in creating passwords is random characters with a symbol, number, and at least one capital letter. The reason for this is that using weak passwords, such as patterns of letters and numbers, or simply your name and some important date you know can cause hackers to guess and open your account, hence impersonate you to commit fraud and other crimes.
3. Use two-factor authorization
Familiar with this term? Yes, a two-factor authorization (2FA) is an extra step to keep your accounts more secure and avoid getting hacked by others. One of the most common 2FA methods is one-time codes sent through SMS or email, authenticator apps such as Google Authenticator, and security keys such as U2F tokens (Drozhzhin, 2018). This one for me is the best 2FA authorization because only your private key will confirm your login. If someone will try to log in to your account with the wrong security key, they will not be granted access to your account. So, there you go. A series of two-factor authorizations that will secure your accounts the best way possible. You’re welcome!
4. Be careful what you click on
Have you heard of phishers? They are attackers that send a fraudulent message designed to trick and victimize us into revealing sensitive information to them. As scary as it sounds, we need to be aware of what we click on to avoid experiencing this. Phishing is usually done in an email when they get your email address from somewhere. These phishers try to create a fake website to trick you into typing in your personal information. It’s much easier for them to hack our accounts this way. To avoid this, you can check the URL’s legitimacy by using the Google Transparency Report or simply avoid suspicious emails which require your personal information. Think before you click!
5. Back-up your data
Data back-up and recovery has many advantages. Some of these are protecting and saving your data, provides ease of management, ensures accurate information of your data, quick access to data, scalability, and such (Becker, 2021). There are many other ways to back up your data, but here’s a simple way to manually back up your data in your phone is to open your phone’s settings app, tap system and click backup or search backup in your settings app, then tap back-up now. It’s that simple.
6. Set up notifications for your most important bank accounts
As online bank account holders, it is our responsibility to making sure our accounts are protected. Online accounts are one of the easy targets of hackers to whisk away our money with just a couple of keystrokes. To safeguard our online banking, we may choose an industrial-standard security bank or credit union that utilizes text or e-mail warnings avoids the use of public Wi-Fi access and periodically changes your password.
7. Protect your personal information
This might be difficult for those who like to express themselves on social media, but we must protect our personal identity to avoid any sort of online threats. To protect our identity, we must limit the amount of personal information we share or provide. We shouldn't share or provide this information online: exact home address, your place and schedules of classes or work, birthday, cellphone number, and most importantly our passwords or account information. Another tip is to write down in a small notebook all your passwords and keep them safe in a secure place away from your computer.

8. Use parental controls and stay present
With the pandemic going on right now, parents should be extra careful of what their children see and hear about themselves and who they encounter on the internet. To protect your children from internet risks, talk to them frequently, utilize tools to safeguard them and watch out for their work. Monitor the time of your child, especially the younger ones, about when and how long they stay online. Keep your computer at a central location in your house, where it's easy to watch what your children do and look at online. You may configure them for mobile devices to forget Wi-Fi passcodes for your kids not to go online without knowledge. Review privacy and location settings, parental control and use secure browsers, apps, search engines and YouTube search settings. Lastly, limit camera and video to prevent your children from accidentally taking photos or videos of themselves or others.

The internet does not usually hurt us unless we react to suspect material and websites. The first reason you don't know what you're doing is because of internet damage. Secondly, you may react or click on links such as appealing advertisements, infected software and communications when you have other forces. To ensure internet safety, just remember those tips above and these three things: secure your network, be responsible, and make the internet child-safe.
References:
Becker, D. (2021). 6 Advantages of Data Backup and Recovery. IT Central Station. Retrieved from https://www.itcentralstation.com/articles/6-advantages-of-data-backup-and-recovery
Drozhzhin, A. (2018). SMS-based two-factor authentication is not safe — consider these alternative 2FA methods instead. Kaspersky Daily. Retrieved from https://www.kaspersky.com/blog/2fa-practical-guide/24219/
Wright, J. (2021). Why Is it Important to Change Your Password? Small Business Chron. Retrieved from https://smallbusiness.chron.com/
Online bullying remains prevalent in the Philippines, other countries (2019). Unicef Philippines. Retrieved from https://www.unicef.org/philippines/press-releases/online-bullying-remains-prevalent-philippines-other-countries
25 Best Internet Safety Tips for Every Situation (2021). The Neeva Team. Retrieved from https://neeva.com/learn/25-best-internet-safety-tips-for-every-situation
3 notes
·
View notes
Text
Why Security Of Website Is Important-With WordPress Plugins
We all are aware of the importance of Security for a website. WordPress is the most popular platform which is mostly used; we need to secure this by using WordPress security plugins.
Every day many WordPress sites get infected with malware if you want to stay away from this. Then you're going to need a topmost security plugin for our website.
In this current situation, many websites harm malware because of a security violation. Most of the people try to keep their website safe, Are you one of them? To keep a safe website, ask yourself do I need a WordPress security plugin?
If you’re a digital marketer, or simply want to optimize your blog or website, then you might want to consider using some WordPress digital marketing plugins that excel at enabling your site with various marketing features and functions. It is most effective for digital marketers because they work with digital media. Simply this is the best security tool for a digital marketing company with these plugins. Using a security tool on your WordPress site is super important to having a successful business online.
In this Article, we are going to connect with the best WordPress Security plugins which are best for your website.
1. Sucuri: Today sucuri Security is the best WordPress security plugin for those people who are looking for a kind of all-in-one system. One of the most trusted platforms for WordPress. Sucuri Security offers both free and pro versions yet most of the websites are satisfied with the free version.
In this Plugin, we get the benefits like Malware Scanning, Blacklist Monitoring, Core Integrity Check, Website Auditing, and Post-Hack Actions except for the malware scanning all these features come with the free version of sucuri security. If you’re waiting for a cost-effective way to protect your WordPress website, Sucuri Security is a top choice.
2. iThemes Security: iThemes Security is another well-liked choice for the WordPress user. Most of the WordPress users are known with the team that builds iThemes Security Pro. iThemes Security does not offer many free benefits if you are going to install the free version of iThemes Security then it comes with the basic features. The pro version offers an improbable number of features
The following are features offer by IThemes Security Plugin Pro
Powerful password enforcement
Two-factor authentication for an extra layer of security
404 detection and plugin scans
Scheduled WordPress backups
Locks out any suspicious IP that scans for vulnerabilities on your site so they can’t gain access
Sends email alerts to notify you of any recent file updates on your site that may be malicious
Ability to limit login attempts
Although there’s no website firewall or malware scanner, they do use Sucuri‘s Site check malware scanner
You can activate 30 total security measures, Getting iThemes Security Pro a great value.
Two-factor authentication
Scheduled malware scans
Google reCAPTCHA
User action logs
WordPress security keys
Importing and exporting capabilities
Dashboard widgets
File comparisons
Password security and expiration
3. Wordfence Security: Wordfence Security is one of the free tools with amazing Security Features that make your website safe and secure. It is the most downloaded security plugin in WordPress. A wordfence protects from hacking malware, spiteful traffic, and many more features.
Wordfence Security provides a wide range of security like login Security, WordPress firewalls, blocking features, Security Scanning, Monitoring Features, Multi-Site Security, Major Theme, and Plugins Support. it fights with spam, malware, and other threats. It is the most popular commonly used plugin of WordPress. The wordfence automatically scans the website with common threats but at the same time, you can launch a full scan.
4. All In One WP Security & Firewall: WordPress has many security plugins but All in One WP Security & Firewall is a very user-friendly plugin that might handle everything to secure your WordPress site.
The plugin takes your website to another level of Security. It is created and addressed by an expert and it is easy to use and understand.
All in One Security & Firewall is the most downloaded and well-maintained plugin for improving your website. All in one security plugin is packed with powerful security features.
The plugin offers the following features such as :
Login lockdown
Security strength meter
System info
Firewall
Backup Wp-config file
Force user logout
Account activity logs
Enable manual approval of new registrations:
Change database default prefix of WP (A highly recommended WordPress database security setting)
Check and improve file system permission
Block IP or IP range as well as user agents.
Block external access to XMLRPC
5. MalCare Security And Firewall: One more exciting WordPress plugin is nothing but malcare Security and Firewall. This plugin is not only a security plugin it is also a firewall. when the thing comes to use malcare is very easy you just need to create an account on the website once you are done then just download and install the plugin and activate it on your website. when the process is completed the basic scan is automatically done by the plugin itself. you can also scan manually by clicking on the button.
The best thing about malcare security is the scan does not affect the website. malcare runs on its own server that's why the website is not getting slow down during a scan.
MalCare Security Plugin Features:
Bulk Website Updates
Website Hardening
Login Protection
Generate Client reports
White-Label MalCare
Team Collaboration
6. SecuPress: Another one plugin to prevent the website from online threats is SecuPress. It Protects your website from malware, black boats, and suspicious Ip. You can use both the free version and pro to download it from WordPress.
This plugin takes care of everything with automated tasks. The free version of secuPress comes with great features like blocked IPs, anti-brute force login, and a firewall. Some features like the protection of security keys make her different from most other free plugins.
The pro version of secuPress activates weekly scan and reports back any unusual activities which happen on the website. SecuPress scanner is also especially useful as it scans your website with six main security points. When scanning is done it offers you a one-click solution to all the detected threats.
WordPress digital marketing plugins are incredibly handy little pieces of software that can assist you in a number of ways on your WordPress blog or website.
#best digital marketing company in pune#best digital marketing company#digital marketing company in pune#digital marketing company
1 note
·
View note
Text
An Update
It’s been a millennia since I wrote anything. I know I don’t owe anyone any writing (technically, I do, but that’s a different story, no pun intended). But I wanted to keep my followers in the know.
I have been up to my eyeballs in the dumbest fucking shit lately and I’m not even talking about COVID-19. My work sucks. The only good thing about it is that my team, the immediate people I work with on the regular, are awesome. But I need to get out soon. The actual work itself is fucking soul-sucking and I hate it. I get very little downtime, which is a major contributor to why I haven’t written much lately. Not because I don’t have the free time at work like I used to, but because I don’t have the mental, emotional, creative, or physical energy to commit to writing when I get home.
My daughter is 16 months old. That’s all I need to say about her (she’s wonderful, but a handful).
I’ve been reading way more lately in an effort to relieve stress.
God damn Minecraft.
I had sinus surgery in December and while the recovery was short, the surgery did not achieve the intended results. I still have major allergy symptoms without being allergic to anything. I was sick with sinus infections for the better part of two months and was only finally feeling sort of back to normal before right before I went to Vegas. Now I’m dealing with severe seasonal allergies after the snow melted here.
But that’s just the tip of the iceberg. What has really irritated me lately is this pile of bullshit:
Google as the monolith it is shouldn’t fucking exist. It’s too convenient to get embedded in all their services such that, when one of them breaks, you’re cut off from all of their services. This story is long and convoluted. I’ll do my best to keep it succinct (I’ve already failed, I know).
Back in January, my primary Google account was compromised. After piecing together the crazy puzzle of what happened, I determined that someone obtained my Google account password, logged into the Google Store with it, and made two fraudulent purchases using two different payment methods (PayPal and my credit card, both of which were saved to my Google Pay profile under this primary email account) equaling a very large sum of money (like $4k).
My credit card company, bless their corrupt little souls, texted me immediately about the VERY expensive charge for the second order and I freaked out. I didn’t get any emails confirming these orders because the fuckers that hacked my Google account (I suspect Google had a data breach because they skipped all two-factor authentication I had enabled and I never received any notification of my account being accessed like I normally do) put a filter on my Gmail inbox to mark all Google Store emails as Opened (or Read) and to immediately toss them into the trash. Do Not Pass Go. Do Not Collect $200.
I immediately resolved these fraudulent charges with disputes. They never even hit my credit card (which was canceled and I was issued a new one) or my bank account (PayPal). Google, however, sucks at this shit. The first purchase was made at 4:30 AM. I never saw it until later that night. Once an hour has passed after a purchase has been made from Google’s store, they cannot cancel it. How fucking ridiculous is that?
So Google Support said to just refuse the FedEx packages. I rerouted them to a FedEx drop location because I didn’t want anyone to steal them off my front step (because that’s what I suspected the scam was all along, why else have them delivered them to my fucking house?) The first package arrived, I went to the drop location which was a Walgreen's, and I told the cashier that I needed to refuse the package and have FedEx return it to the sender. I said this several times to the person helping me. But then she had me sign the FedEx scanner and when I went to leave, she pushed the box to me and said, “You don’t want it?”

It gets worse.
While I felt dumb for signing for the package, when the second package came in the next day, I also signed their scanner but it was to actually refuse the package. I don’t know why that’s how it worked, but it did.
Package 1: Accepted. Package 2: Refused.
This is important.
During this time, my Google Pay profile under my primary Google account was placed on a temporary freeze. But on February 10th, once everything had been returned (FedEx managed to get the first package returned, I have the tracking numbers, it made it), my Pay profile had been reactivated.
Which was really great because my Play Music and HBO subscriptions had lapsed. So I immediately renewed them.
Problem solved, right?
Wrong.
I tried buying a movie before I flew to Vegas and got a very similar error that I’d seen previously when my account had originally been frozen at the end of January due to the fraudulent charges.
Through several Support chats and getting the run around, I come to find that my Pay profile has been permanently closed because I violated the Google Pay Terms of Service. And that Google’s policy is to not discuss the details of the issue with anyone. And I cannot close that Pay profile and create a new one under that same Google account because it’ll just get flagged and closed again.
While pissed, I resolved to fix it after Vegas because I didn’t have the capacity to handle it while prepping for that trip.
I get back and the problem still exists. A part of me hoped it would just go away. So over the last week I went back and forth with Google Pay support on what the fuck is going on with my pay account. Several times they repeated the same thing to me: account is closed due to violation of ToS, can’t discuss it with you per our policy. Great.
During that time, I noticed that I had like, $200 worth of Google Store credit on my account because of the packages I had unintentionally accepted (I had previously signed up for Google One so I could offload some storage to their cloud, and as a part of that Google One sub, they offer a percent of Google Store purchases as Google Store credit). So I wanted to see if I could actually use it. I kinda figured they’d take the $200 back seeing as that the charge never processed. When I tried to buy something, I finally got an error that said my Pay profile had been closed for violating the ToS.
The Narrator: Can you put that in a folder and label it “Shit I Already Know”?
I filed a complaint with the Attorney General of Minnesota because Google was not allowing me to do anything to resolve the issue. Every email response I sent was met with a similar response of “we’ve reviewed your account and we’ve determined it must remain closed”. I went Full Karen™ on Google Pay support and threatened them with legal action if they did not tell me what the fuck I did to violate their ToS. That was last Thursday.
After a few more emails over the weekend (only like, two), I suddenly received a response at 6am today stating that my Google Pay profile had been reactivated.
I resubscribed to HBO and Play Music without issue. (I did, however, create another mess with Google Family sharing, but that’s a different story, although very much related to and caused by this one, and I won’t get into it here).
When I checked my Pay profile, the $200 in Google Store credit had been removed. I think they finally checked the tracking numbers on those two orders that I sent back and realized I had actually sent them back instead of defrauding them by making a purchasing, rejecting the charge, keeping the package, and pocketing the $200 in-store credit like they probably assumed.
I also think Google might have a big data breach mess on their hands right now. Change your passwords regularly folks!
TLDR: I’m tired. :)
2 notes
·
View notes
Text
How to Protect the iCloud account? & Increase Storage with Apple Gift Card
iIf you haven’t heard, iCloud security is a hot topic these days. From claims that China infiltrated Apple with hidden spy chips. Reports that Apple vigorously denies to last year’s threats. From the “Turkish Crime Family” regarding stolen account passwords, it’s understandable if you’re worried about how secure your iCloud data is.

You can learn more about how Apple works on end-to-end encryption that has thus far kept iCloud mostly safe from hackers. But there’s plenty you can do on your end to help make iCloud safer and well-protected as well. Here are the necessary steps you should increase your iCloud security and provide you beneficial sites which provide you free Apple gift card for your use.
Step 1: Create a Secure Password

The password you use for iCloud is the same password for your Apple account. Apple requires that this password must be at least eight characters long, use upper and lowercase letters, and have at least one number, but we can do a lot better.
Reset your Apple ID password and make it as secure as possible. That means around 15 characters, both upper and lowercase letters, multiple numbers, and symbols. If you’re worried about remembering a random string of characters, a common tactic is to take a familiar phrase or word and exchange letters for numbers and symbols.
However, if you want to invest time in a dedicated password manager, the software can come up with very strong passwords for you. Password managers are becoming increasingly important in today’s digital security environment, so if you don’t use one yet it’s certainly worth considering.
Step 2: Set Up Your Security Questions if Necessary

If you haven’t visited your Apple ID in a while, you may not have gotten a chance to set up any security questions. These questions work just like the security questions for any thorough online security portal — you set a few specific questions about your life with answers that strangers would never know. Apple will ask these questions when you log into your Apple account or make significant changes.
To find your security questions, log into your Apple account with your ID and password, and look for the section that says “Security.” On the right-hand side of the page, select the Edit button to expand the part so you can examine the Security Questions heading.
If you haven’t added any questions, you will see an option to “Add Questions.” If you have set questions up but want to check and refine them, you will see an option to “Change Questions.”
Note: Some people cannot see an option to set up security questions when they log into Apple ID. If you don’t see this option, you can skip this step: This happens when someone sets up two-factor authentication, which overrides the need for security questions and may erase from your account info.
Step 3: Enable Two-factor Authentication

Apple used to have “two-step verification” but upgraded to “two-factor authentication,” which is an effective method of making sure that the real you are accessing your account from one of your real devices. This authentication sets up a trusted device and phone number that Apple will send a verification code to when you try to log in from an unrecognized device.
If you haven’t already done so, turning on two-factor authentication is a simple process iPhone Two-Factor Authentication. If you have already logged into your Apple account online, you can go to the Security section and look at the article for Two-Factor Authentication, which will take you through the process of setting it up. You can also set up the authentication at any time on your iPhone by going to “Settings, Password & Security,” and enabling “Two-Factor Authentication.”
Again, remember that two-factor authentication will probably cancel out your security questions. We encourage you to set up security questions first so that they (hopefully) remain associated with your account in case support staff needs to verify your identity or something goes wrong with the authentication. However, you are entirely free to skip right to the two-factor authentication if you want.
Step 4: Always Sign Out When Not Using Your Devices

Finally, always be aware if you are signing into your Apple account on a public device or a device that isn’t yours. This isn’t an excellent idea (especially when connected to guest Wi-Fi), but sometimes it may be necessary. Just remember to log back out from your account when you are finished.
In a similar vein, don’t give out your Apple ID or password to anyone if you aren’t sure it’s an official Apple login or representative.
Some several websites which gives you free iTunes Gift card for users:
PayPrizes.com
CouponPrizes.com
iTunesReward.com
GCardGenerator.com
All these need to complete some simple task like downloading apps, games and survey.
1 note
·
View note