#hackforum
Explore tagged Tumblr posts
Text
unjerk is like, pausing the circlejerk for a legitimate comment or smth but uhh
by rf/hf i mean raidforums/hackforums, just cause skid was used way 2 much in there when i was younger XD, although RF stuff is cool as fuck and i am vaguely (fairly) jealous XD
i unfortunately have that permenant puppy brain thing where i have too many hobbies to be actually *good* at any of them, so i'm not as deep as id like to be with stuff, but most of my interests do lie within cyber security stuff. i do find risc stuff especially cool because of the still-uses-usenet-but-not-for-piracy tech guy meme of writing risc emulators that run the linux kernel in shit like scratch or hlsl shaders or smth
i randomly found my matching ram at the cashies for 10$ today so now i'm up 2 32gb of ram.
time 2 compile many many things
38 notes
·
View notes
Text
Nasıl Hacker Olduğumu Anlatıyorum
merhaba arkadaşlar size nasıl hacker olduğumu anlatmak istiyorum. Öncelikle kendimi tanıtayım adım Gazi Akyıldız 26 yaşındayım dulum bilgisayar mühendisiyim. Web master olmak çocukluğumdan beri hayalimdi kendi sitelerimi yönetmek çok hoşuma gidiyor. Birgün yöneticisi olduğum siteye girdiğimde çok kötü bir manzarayla karşılaştım.
Sitem hack yemişti evet hacklenmiştim. Çok moralim bozuldu kendimi site işlerinden soyutladım. Daha sonrasında hacker olmak istediğime karar verdim. Bilgisayarımı açtım ve hack forum sitelerinden birine girdim. Hack dökümanları ve hacking videolarına bakınıyordum. Hack forum ortamı beni iyice sarmıştı, artık hacker olma yolunda ilerliyordum.im. Hack dökümanları ve hacking videolarına bakınıyordum. Daha sonrasında hack tool yardımı ile web hacking yapmaya başladım. İlk başta brute force ile çöp denilicek ufak Wordpress tabanlı siteleri hacklemeye başladım. Sonrasında SQL injection yönetimini öğrendim. İnternet sitelerinin SQL açıklarından faydalanarak veritabanına erişiyor ve admin giriş bilgilerini alıyorsun; gerçekten güzel bir yöntem ve bir ton siteye girebiliyorsun.
Hack eğitimi konusunda hack forum siteleri muazzam ancak çok çeşit konularda içerik mevcut. Saatlerimi günlerimi hatta haftalarımı geçirebiliyorum, hacker sitesi olmanın dışında derin bir sosyal platform ve her konuda içerik var. Warez içerikler zaten malumunuzdur ancak bu alışılageldik konuların dışında pek çok içerik mevcut. Moderatörler kafa adamlar bilişim konusundaki yetenekleri haricinde hack kavramını yaşam felsefesi edinmişler.
3 notes
·
View notes
Text
Hack forumunda takılırken ocakta çay kaynıyormuş
Bir hacker vardı. Adı tarık faruktu. Kardeşi ise turgut şinasiydi. Tarık faruk hack forum sitesinde takılan hackerdi. Hackerim diye ortada gezen veletlerden değildi, kendini sağlam yetiştirmiş bir hacker, cracker, developer, coder, designer aynı zamanda sırıkla atlama antrenörüydü. Kardeşi ise vasıfsız bir boktan cakmayan bir kenar mahalle serserisi idi. Tarık faruk her ne kadar onu adam etmeye çalışıp hack forum sitelerinde takılmaya ikna etmeye çalışsa da bunu başaramadı. Suç elbette hacker tarık farukta değildi. Hayatta bazen olduğu gibi mum dibine ışık vermezdi. Vermemişti de.

Hack forumda moderatör olduğunu gizledi
Tarık faruk hacker başarılı günleri sürerken birgün hack forum sitesinde moderatör oldu. Aslında hayali admin olmaktı ama bunu bir basamak olarak gördü ve herşeye rağmen mutlu oldu. Zevkten çığlıklar atıyordu. Babası noluyo lan diye bağırınca açıklama yapmadan hiiiiç diyip konuyu kapatmayı tercih etti. Çünku hack forum kariyerini gizlemeyi tercih ediyordu. Gizlemeliydi belki de. Hack forum moderatörü olduğunu kimse bilmemeliydi, bakkal Rafet abi bile..
Grip olduğu için 2 gün foruma giremedi
Hackerin hack forum sitesinde moderatör olduktan sonra ciyaklaya ciyaklaya attığı zevk çıgliklari uzun sürmedi. 10 gun sonra grip oldu ve köh köh öksürmeye başladı. Burnu da mahalle çeşmesi gibi akiyodu. Bu durumda yataktan kalkıp hack foruma bakmak aklina gelmedi. Oysa admine gore bu bahane değildi. Tarık faruk adli hackerin hack forum sitesini boşlamasi onu sinirlendirdi. Moderatöre fırca kaydı ve hacker tarık faruğun zevk çığlıkları yerini hüngür hüngür ağlamaya bıraktı.
1 note
·
View note
Text
Decine di migliaia di credenziali per accesso a server web sul dark web

Dark web community MagBO sta vendendo dati rubati da oltre 20k siti web, identità complete, e altro ancora. MagBO, il mercato web scuro di lingua russa per il trading in siti web backdoored, continua a crescere in modo esponenziale. In meno di due anni, la raccolta di fughe di notizie è cresciuta da circa 3.000 nel settembre 2018 a 26.605 nel febbraio 2020. Dati hackerati sul mercato viene offerto in vendita a prezzi a partire da 0,20 USD fino a 1.000 USD, a seconda della natura e della portata delle informazioni. I dati in questione spaziano dalle credenziali di accesso al sito web, ai documenti giudiziari alla documentazione di identità completa e ai dati della carta di credito di oltre 300 cittadini russi. Coloro che sono interessati ad acquistare l'identità di qualcun altro per varie attività potrebbero trovare che non è così difficile come si potrebbe pensare. Anche se MagBO è una comunità solo su invito, chiedere in giro sul dark web potrebbe farti un invito facile per una quantità relativamente piccola di denaro. Svelare lo schema MagBO L'esistenza di MagBO è stata scoperta nel settembre 2018, quando gli esperti di sicurezza hanno scoperto che gli hacker su questo forum di lingua russa vendevano l'accesso a oltre 3.000 siti web e database compromessi o backdoored. Le persone dietro di esso aveva fatto questo per diversi mesi, con i primi annunci pubblicati su un altro forum di hacking in lingua russa nel marzo 2018. Il mercato ha un'unica interfaccia, recensioni e valutazioni per venditori e acquirenti, chat online per corrispondenza personale, così come una versione in lingua inglese. Gli "articoli" in vendita sono accompagnati da commenti utili come: 'il sito dà accesso ad altri 30 e-store' o 'viene fornito con il database MySQL' o 'sito viene iniettato con un virus' o 'ha informazioni sulla carta di credito' e così via. Il mercato supporta anche l'acquisto e la vendita all'ingrosso, contrattazione, all'ingrosso, l'acquisto di un prodotto da diversi host, e si può pagare non solo con Bitcoin, ma con i servizi di pagamento WebMoney e Qiwi pure. L'unica differenza da migliaia di altri mercati online è che è completamente illegale. Tuttavia, il fatto più preoccupante è che il numero di "conchiglie" - i siti web e i pacchetti di dati dei siti web in vendita - è cresciuto in modo esponenziale, da circa 3.000 nel 2018 a 26.605 in meno di due anni.

Screenshot of the MagBO’s about page, Feb 6,2020 In base all'elenco dei filtri, i clienti di MagBO possono mettere le mani sui dati dei siti Web tramite l'accesso FTP (File Transfer Protocol), l'accesso alla shell PHP, l'accesso al pannello di amministrazione, l'accesso al controllo del dominio, l'accesso al controllo di hosting, l'accesso Secure Socket Shell (SSH), nonché l'accesso a Database o SQL (Structured Query Language). Questi sono tutti gli strumenti, protocolli e punti di accesso utilizzati nella gestione di un sito web. La gamma di siti web vittime copre quasi ogni tipo di sito web là fuori - blog, siti WordPress, gioiellerie artigianali, piccoli marchi di moda, birrerie, ristoranti, siti per adulti e agenzie architettoniche. Gli acquirenti possono anche accedere a grandi siti di e-commerce, società di marketing digitale, studi legali e agenzie di sviluppo software, nonché fornitori di hosting che sbloccano l'accesso a una vasta gamma di domini di siti web. I prezzi dipendono dalla classifica di Alexa, dai livelli di autorizzazione, dalla possibilità di modificare o aggiungere contenuti e altro ancora, consentendo agli acquirenti di acquistare qualsiasi violazione specifica che vogliono, sia per l'obiettivo di rubare informazioni sulla carta di credito, estrarre criptovaluta o fornire spam.

Per illustrare, l'accesso al sito web di vendita al dettaglio di stile di vita wellphora.com in questo momento vi costerà 1.000 USD. Considerando che l'azienda vende i suoi prodotti online, significa che tutti i dati della carta di credito dei suoi clienti sono a rischio (tra le altre informazioni). Dall'altra parte del listino prezzi è uno dei siti più economici - duegirappresentanze.it, disponibile a soli 1,20 USD (con 20% di sconto!). Gli hacker non hanno appena esposto le credenziali di accesso dei siti web e le e-mail, ma altre informazioni private estremamente sensibili come: scansioni complete dei passaporti nazionali e internazionali russi, numeri di identificazione personali del contribuente, numeri di previdenza sociale, carta di assicurazione pensione, estratti conto, patenti di guida, documenti giudiziari, e altro ancora. Tutte queste informazioni sono filtrate dal luogo di residenza delle persone la cui identità è stata rubata.

Se qualcuno voleva usare l'identità di una persona proveniente da una regione desiderata per, ad esempio, la registrazione del sito di scommesse, poteva scegliere tra centinaia di identità con la documentazione completa. Le implicazioni potrebbero essere molto peggiori se l'acquirente volesse usarlo per qualcosa di più delle loro attività di scommessa. L'immagine qui sopra mostra l'identità di una persona che viene venduta per un minimo di 8,00 USD. C'è qualcosa che puoi fare? L'emergere di luoghi come MagBO, dedicato esclusivamente al commercio di informazioni rubate, non è certo nuovo. Infatti, è solo uno dei tanti giocatori del settore che include simili a HackForum, Nulled, Mal4All, Empire Market e altri. La maggior parte di noi non vedrà mai questa parte nascosta ma grande del mondo digitale, e questo è ciò che lo rende ancora più pericoloso - la mancanza di conoscenza del suo funzionamento interiore. Abbiamo contattato oltre 100 domini in vendita su MagBO ma, purtroppo, nessuno di loro ha riconosciuto la potenziale minaccia che questo ha sulle loro operazioni. Questo comportamento sostiene l'idea che l'unica cosa necessaria per il trionfo del male è che gli uomini buoni non facciano nulla. Basta visitare il catalogo, digitare e cercare i tuoi domini attraverso il database. Se trovi il tuo sito nell'elenco e desideri assistenza (gratuita) per l'indagine, contatta il supporto del sito web. Read the full article
#backdoor#backdoored#classificadiAlexa#criptovaluta#darkweb#e-commerce#EmpireMarket#FTP#hacker#HackForum#leekserver#MagBO#Mal4All#Nulled#WordPress
0 notes
Photo
0 notes
Photo

#TIPS de seguridad y #CIBERSEGURIDAD #HACKFORUMS estableció la campaña #ERACOVID19 como estrategia de marketing para estimular a los #CIBERDELINCUENTES en época de pandemia, ventas de: DDoS, malware, licencias de software, tarjetas Amazon, entre otras ofertas. En los foros de discusión, se estableció que la pandemia “obligó” un período de aburrimiento masivo y a un cambio económico, cuando presumiblemente algunos miembros no podían ir a la escuela y otros habían perdido sus trabajos , “estimulando” el mercado. Cómo quiera que los ciberdelincuentes miembros necesitaban ganar dinero en línea y tenían mucho tiempo libre, se analizó un incremento en la actividad ilícita. Se espera otro aumento durante el segundo bloqueo, aunque no creen que sea tan grande como en el primer confinamiento. El aumento de los negocios durante la pandemia también significó que los contratos de transacciones se concluyeron mucho más rápido. Mientras que en los primeros meses del mercado el tiempo de finalización de los contratos era de alrededor de 70 horas, durante la pandemia se redujo a menos de 10 horas. Usando los datos, los investigadores observaron una variedad de actividades ilícitas que tienen lugar en el mercado. Las actividades más importantes fueron los cambios de divisas y los pagos, por ejemplo, el intercambio de Bitcoin (una moneda muy popular en el comercio ilícito porque la gente cree que no deja rastro) fondos de PayPal. Otros productos y servicios que encontraron comercializados en el mercado clandestino fueron tutoriales de piratería, herramientas de acceso remoto y materiales de eWhoring: fotos y videos con contenido sexual que se venden a un tercero, quien paga por ellos creyendo que está pagando por un servicio sexual en línea. @CaiVirtual @FiscaliaCol Cámara de Comercio Ibagué FBI Alcaldía Municipal Rovira - Tolima Alcaldía de Ibagué Universidad Externado de Colombia Universidad Católica de Colombia Superintendencia de Industria y Comercio de Colombia https://www.cam.ac.uk/research/news/honour-among-thieves-the-study-of-a-cybercrime-marketplace-in-action https://www.instagram.com/p/CHYJu6tHcRY/?igshid=bivtq0u5fc6h
0 notes
Note
When you get doxxed on hackforums, Para. I want you to know that was me. Sincerely, Imp.
Para is very, very confused. “…Excuse me…? Is this a threat…???”
#The Narrator's Galaxy#Para the Dimension Jumper#ask#oh boy this makes my paranoia/anxiety levels rise#aaaaaaaaaaaaaaaaaaaaaaaaaa
1 note
·
View note
Text
Me:*has very basic knowledge of hacker jargon and a hackforums account* I Am Going To Hack The Mona Lisa
9 notes
·
View notes
Text
hack forum siteleri arasıda seçmeler
Popüler teknoloji haberi platformlarında günde en az bir yada iki tane hacking yada hacker temalı haber oluyor. Hackerların bu tip teknoloji odaklı haber sitelerini dolduran eylemleri, her ne kadar sıradan bir vatandaş için aman üf abartı vs denerek önemsenmese dahi; çok büyük bir önem taşıdığı su götürmez bir gerçek. Hackerların pek çok dev şirketi bol sıfırlı rakamlar ile ifade edilen maddi zararlara uğratması, hacking konusunun önemini ortaya koyuyor. Çok sığ ve karşılık gelmeyen bir terim olan bilgisayar korsanı ile dilimize girmiş olan hacker kavramı uçsuz bucaksız ve dallı budaklı bir kavramdır. Bu kavramı uzun süre incelemiş biri olarak hack ve hacker konulu her şeyin gerçek bilgiler ile aydınlatıldığı tek yerin hack forum olduğunu söyleyebilirim. Hem hacking öğrenip, hack tool ve hack döküman elde edeceğiniz; hem oyun hilesi, warez içerik, crack patch gibi şeyler bulacağının; hem de gerçek hackerlar ile diyalog kuracağınız büyük ve kapsamlı ortamlardır hack forum siteleri. Ön yüz açısından sade ve sığ durabilseler bile içeriğinde karanlığın hakim olduğu derin platformlardır. Ancak hack forum seçerken dikkat edilmesi gereken hususlar vardır. Örneğin bazı lamer forum olarak nitelendirebileceğimiz boş laf öbekleridir. Bunu anlayabilmek zor değildir birbirine komutanım, devrem, paşam ve bunlar gibi saçma şeyler ile hitap eden topluluklar, genellik ile birkaç lamer tarafından yüzlerce çocuğun kullanıldığı gösteriş ve çıkar kapılarıdır.
1 note
·
View note
Link
incoming search terms:-
money making guide battlescape money making guide barrows money making guide bravely default money making guide black flag money making guide bossing money making guide black dragons eve online money making guide for beginners best online money making guide money making guide battlescape money making guide barrows money making guide bravely default money making guide black flag money making guide bossing money making guide black dragons eve online money making guide for beginners best online money making guide money making guide battlescape money making guide barrows money making guide bravely default money making guide black flag money making guide bossing money making guide black dragons eve online money making guide for beginners best online money making guide money making guide combat money making guide crafting money making guide cooking money making guide combat f2p money making guide clash of clans money making guide construction money making guide cooking f2p money making guide crafting f2p money making guide conquer online money making guide crystal saga money making guide divination money making guide dragon age money making guide dragon nest money making guide dragon age 2 money making guide dmo money making guide dragon age inquisition money making guide diablo 3 money making guide dragon age awakening money making guide dragon city money making guide dofus money making guide eoc money making guide eso money making guide eoc 2014 money making guide eve online money making guide extaliams money making guide eden eternal money making guide elite dangerous money making guide enchanting money making guide eoc 2017 money making guide eoc f2p money making guide f2p money making guide f2p 2017 money making guide fletching money making guide ffxiv money making guide fishing money making guide farming money making guide fifa 14 ultimate team money making guide fifa 14 money making guide fable 3 money making guide for pures money making guide gta 5 money making guide gta online money making guide gw2 money making guide grinderscape money making guide gt5 money making guide grand fantasia money making guide god wars money making guide gta iv money making guide gta v online money making guide jewelcrafting money making guide jade dynasty money making guide killing blue dragons money making guide king black dragon money making guide killing monsters knight online money making guide kal online money making guide money making guide ikov money making guide in runescape money making guide in gta 5 money making guide ironman money making guide insanity flyff money making guide in wow money making guide in soulsplit money making guide injustice money making guide in tera money making guide in skyrim money making guide herblore money making guide hunter money making guide hay day money making guide high alch earn money online urdu guide money making guide harvest moon a new beginning money making guide hackforums hero online money making guide money making guide osrs money making guide osrs 2017 money making guide osrs f2p money making guide oras money making guide order and chaos money making guide on runescape money making guide osrs 2017 money making guide oblivion money making guide osrs p2p money making guide on soulsplit money making guide new leaf money making guide neverwinter money making guide near reality money making guide neopets money making guide no skills p2p money making guide no skills money making guide magic money making guide mining money making guide maplestory money making guide members money making guide maplestory 2017 money making guide mount and blade warband money making guide magic runescape money making guide melee money making guide mabinogi money making guide molten wow money making guide low levels runescape money making guide low level money making guide legacy mode money making guide legacy money making guide lotro luna online money making guide make money online guide pdf money making guide p2p money making guide pokemon x money making guide p2p 2017 money making guide pwi money making guide p2p 2017 money making guide pkhonor money making guide pdf money making guide p2p combat money making guide pvm money making guide runescape money making guide runescape 2017 money making guide runescape 2017 money making guide runescape f2p money making guide runescape 2017 p2p money making guide runescape 2017 f2p money making guide runescape 2017 f2p money making guide runescape 2017f2p money making guide runecrafting money making guide runescape 2016 f2p money making guide soulsplit money making guide skyrim money making guide smithing money making guide slayer money making guide swtor money making guide skilling money making guide summoning money making guide smithing f2p money making guide sims 3 money making guide spiral knights money making guide wow money making guide wow 5.4 money making guide wiki money making guide wod money making guide woodcutting money making guide world of warcraft money making guide wildstar money making guide wow wod money making guide wow 5.4.7 money making guide witcher 3 money making guide vindictus gta v money making guide online earn money online urdu guide money making guide ultimatescape money making guide ultimate team money making guide using fletching money making guide using combat ultima online money making guide uncharted waters online money making guide dc universe online money making guide ultimate guide to making money online money making guide tera money making guide terraria money making guide thieving money making guide tibia money making guide the world of magic money making guide tales of pirates 2 money making guide thieving 07 money making guide tales of pirates money making guide the crew money making guide the runescape wiki money making online guide xp 200 money making online guide xp200 money making online guide xbox one money making online guide xbox 360 money making online guide xbox money making guide zybez money making guide youtube money making guide 07 money making guide 07scape money making guide 07 2015 money making online guide 4th grade money making online guide 4.0 money making online guide 4th edition money making online guide 3rd edition money making online guide 3rd grade money making guide 2017 money making guide 2016 money making guide 2017 money making guide 2013 p2p money making guide 2013 eoc money making guide 2015 f2p gta 5 money making guide online 2015 money making guide 2014 f2p conquer online money making guide 2017 conquer online money making guide 2016 gta online money making guide 1.20 gta online money making guide 1.16 money making guide 5.4 money making guide 5.4.8 gta 5 money making guide online gta 5 money making guide online 2017 money making guide 6.0 money making online guide 7th grade money making online guide 8th grade
Tags:Earn Money Online Guide,Earn Money Online Guide Free,Earn Money Online Guide Free Download,Earn Money Online Guide Ebook,Earn Money Online Guide Pdf Ebook,Earn $55,-Per Day Money Making Online Guide Free Download,Money Making Online Guide Free Download,Money Making Guide Free Download,Money Making Guide Free Download Torrent,Money Making Guide Free Download No Survey,Money Making Guide Free Download Pdf.
0 notes
Text
Hackers e Deep Web: una community attiva più che mai
La cultura hacker è molto radicata al concetto di anonimità. Non è quindi una sorpresa che gli hackers abbiano trovato nel Deep Web il posto perfetto per condurre le proprie attività e condividere materiale. Il numero delle hacking communities sul Deep web è molto alto, come riportato dagli ultimi scanning dei siti nascosti. Molte sono accessibili solo via specifici protocolli o tramite invito da parte di un membro, e sono spesso incentrate su argomenti specifici (TrojanForge, per esempio, ospita membri specializzati in malware e code reversing).

Figura 1: Il The Hell Hacking Forum. Fonte: infosec
Inoltre, il mercato nero del DW basato sulle transazioni di Bitcoin ha reso possibile la nascita del trend noto come “hacking as a service”; sono molti gli hackers che vendono servizi (phishing, furto di account o di dati personali, spionaggio, DDos) e prodotti (malware, database di dati sensibili, exploit kit) su specifici forum o chatroom. Fra i più famosi: Hackerforsale, Rentahacker e il The Hell Hacking Forum.
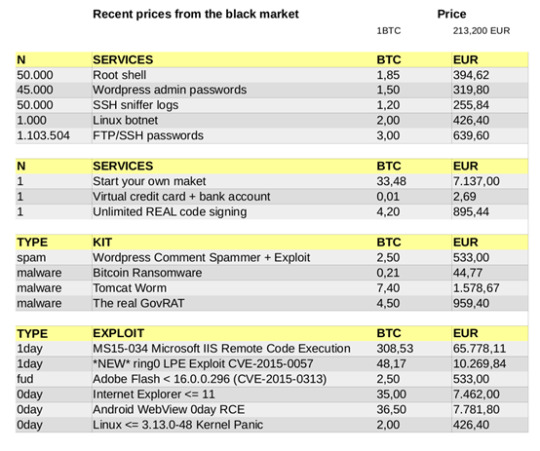
Figura 2: Prezzi (in Bitcoin e euro) per alcune attività offerte da hackers sul mercato nero. fonte: infosec.
E non è tutto; sul Deep web si possono trovare vere e proprie “scuole di hacking”, network sviluppati come delle classi virtuali. Tra le più famose vi è OnionIRC, lanciata nel 2016 (purtroppo il progetto ha chiuso inspiegabilmente quasi sei mesi dopo, secondo il profilo Twitter ufficiale) da Anonymous, noto gruppo di hacktivisti (Wikipedia eng definisce hacktivismo l’uso della tecnologia per promuovere un’agenda politica o una lotta sociale.) per avvicinare i più giovani al mondo dell’hacking. Sul network si poteva trovare una chatroom dove i membri della community condividevano lezioni e tutorials.
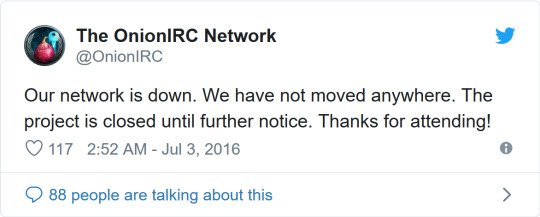
Figura 3:Il tweet che annuncia la chiusura di OnionIrc.
Ma non solo communities e mercato nero: il DW si è rivelato una piattaforma dove gli hacktivisti conducono di nascosto le loro battaglie. Per danneggiare i loro nemici, molti hacktivisti si servono dei forum dell’underground per condividere database sensibili di governi o compagnie private. Famoso il blitz di Anonymous del 7 febbraio 2017, quando il gruppo eliminò 5mila siti di pedopornografia che facevano parte dei servizi offerti dalla piattaforma di traffici illeciti Freedom Hosting (su cui Anonymous si era già scagliato contro nel 2011).

Figura 4: il logo di Anonymous. Fonte: wikimedia commons.
Fra i casi più recenti, riportato da un insider della piattaforma Sixgill, vi è anche quello di un utente che ha pubblicato il link ad un database di un’azienda immobiliare turca contenente i nomi degli impiegati e i loro dati personali. La pagina dell’utente contiene delle richieste al governo turco e statunitense, tutte collegate alla guerra in Siria, come condizioni per cancellare il database.
Veronica Montanaro
0 notes
Text
Janit0r the BrickerBot guy
*He’s a vigilante. So he says, anyway.
https://www.bleepingcomputer.com/news/security/brickerbot-author-claims-he-bricked-two-million-devices/
(...)
At this point, we had to confirm that Janit0r was indeed BrickerBot's author and not just some guy bragging on Hack Forums. This is how we spent the next two days, scraping through the Dark Web, underground hacking forums, and getting in contact with a few threat intelligence analysts we knew.
By Wednesday, we didn't manage to find any other clue of Janit0r's existence, or anybody else claiming to be BrickerBot's author, with some solid proof on his side. That's when we just gave up, and launched a desperate tweet, asking BrickerBot's author to reach out.
BrickerBot's Author reaches out
Lo and behold, this was exactly what happened. The same day, we received an email from a person claiming to be BrickerBot's creator.
The email contained lots of details about BrickerBot's operation and internal structure. Nevertheless, at this point, we knew that there could be the possibility that someone was pulling a prank.
Chance had it that someone else had also seen our tweet. That person was Victor Gevers, a security researcher mostly known for tracking the destructive ransom attacks against MongoDB and other databases.
In the Bleeping Computer article that broke the news of BrickerBot's existence, we asked Victor for his expert opinion on this new malware's behavior and repercussions. Victor not only put BrickerBot in perspective for our readers, but also asked BrickerBot's creator to reach out and discuss an alternative method of dealing with unsecured IoT devices, instead of blindly destroying people's property.
Unknown to all was that BrickerBot author had reached out to Victor hours after our article went live. The two had shared notes and Victor was acting as an intermediary between Janit0r and various CERTs. All the operational details shared with us on Wednesday were the same Janit0r shared with Victor in the previous three weeks, confirming we were speaking with the same person.
"Yes, I am janit0r"
"Yes, I was janit0r on Hackforums," the BrickerBot author started his email, which then continued with Janit0r showing his anger at the sad state of affairs in the realm of IoT security.
Like so many others I was dismayed by the indiscriminate DDoS attacks by IoT botnets in 2016. I thought for sure that the large attacks would force the industry to finally get its act together, but after a few months of record-breaking attacks it became obvious that in spite of all the sincere efforts the problem couldn't be solved quickly enough by conventional means. The IoT security mess is a result of companies with insufficient security knowledge developing powerful Internet-connected devices for users with no security knowledge. Most of the consumer-oriented IoT devices that I've found on the net appear to have been deployed almost exactly as they left the factory. For example 9 out of every 10 Avtech IP cameras that I've pulled the user db from were set up with the default login admin/admin! Let that statistic sink in for a second.. and then consider that if somebody launched a car or power tool with a safety feature that failed 9 times out of 10 it would be pulled off the market immediately. I don't see why dangerously designed IoT devices should be treated any differently and after the Internet-breaking attacks of 2016 nobody can seriously argue that the security of these devices isn't important. I hope that regulatory bodies will do more to penalize careless manufacturers since market forces can't fix this problem. The reality of the market is that technically unskilled consumers will get the cheapest whitelabel DVR they can find at their local store, then they'll ask their nephew to plug it into the Internet, and a few minutes later it'll be full of malware. At least with 'BrickerBot' there was some brief hope that such dangerous devices could become the merchant's and manufacturer's problem rather than our problem.
BrickerBot allegely wiped over two million devices
I joined Hackforums in January mainly to see if my activities had been noticed by the botnet kids. Back then 200,000 bricked units seemed like a lot and I was sure I was close to the end of it. Now when the count is over 2 million it's clear that I had no idea (and still have no idea) how deep the rabbit hole of IoT insecurity is. I'm certain that the worst is still ahead of us. I hope the unconventional actions by 'BrickerBot' have helped in buying another year of time for governments, vendors and the industry in general to get the current IoT security nightmare under control. Many other people have also done important things to combat IoT malware (Team White, Hajime author, @packetcop and his fellow sinkholers, etc) so I'm by no means claiming credit for Mirai being weak in Q1/2017, but if Imeij and Amnesia have suffered a little recently then it's probably mainly my fault ;)
Janit0r's email then goes on to detail a few operational details regarding BrickerBot's infrastructure, also dispelling the notion that he's a madman set on the random destruction of IoT devices.
In reality, Janit0r wants to be considered in the same class as the White Team, the self-proclaimed white-hat hackers behind the Wifatch malware, and the author of the Hajime malware, another vigilante who created a new malware family last October that tries to secure IoT devices by force.
The Radware writeup made 'BrickerBot' sound simplistic, but it actually carries 86 protocol and device-specific payloads and is relatively successful at mitigating commonly exploited devices. The bot's every action has a statistically determined purpose and what might've seemed like buggy behavior in the honeypot really isn't. As a preference 'BrickerBot' will try to secure units without damaging them and the bricking behavior is a 'plan B' (yes the B stands for brick :) for units which are unlikely to be securable. A blogger on the net wondered about 'BrickerBot' simply trying to change his honeypot's login and this would've been due to the bot assuming the device had a persistent user db. Because the honeypots are often quite different from any actual devices the behaviors in them are usually weird. If security researchers made their honeypots look more like actual devices (that one could actually find with default credentials on the net) and hosted them on dirtier networks they would find even more interesting things going on..
Victor Gevers, who confirmed Janit0r's bricking statistics also believes this person is only misguided, and hopes to convince him to abandon his ways. "The writer of the email does not strike me as a bad person," Gevers told Bleeping Computer based on his own communications with Janit0r. "Just some young guy who was too eager to solve a problem."
Janit0r wants a change in IoT security standards
For the time being, Janit0r doesn't seem interested in stopping BrickerBot attacks, or at least not until officials and hardware vendors take a look at IoT security and start changing things with a hurry.
Authorities have been talking about IoT security standards for years, but in the meantime, some of the same vendors participating in those discussions have continued to ship out insecure devices with the same ol' default passwords. In a follow-up email, Janit0r wrote the following.
I consider my project a form of "Internet Chemotherapy" I sometimes jokingly think of myself as The Doctor. Chemotherapy is a harsh treatment that nobody in their right mind would administer to a healthy patient, but the Internet was becoming seriously ill in Q3 and Q4/2016 and the moderate remedies were ineffective. The side effects of the treatment were harmful but the alternative (DDoS botnet sizes numbering in the millions) would have been worse. I can only hope hope that when the IoT relapse comes we'll have better ways to deal with it. Besides getting the number of IoT DDoS bots to a manageable level my other key goal has been to raise awareness. The IoT problem is much worse than most people think, and I have some alarming stories to tell.
Janit0r is a wanted man
Nonetheless, the actions of BrickerBot place this malware in the same category as other destructive e-threats, such as ransomware and banking trojans. Janit0r already knows he's a wanted man and has taken many precautions.
Tracking down Janit0r's real life persona may also be a little harder than going after teenagers that rent DDoS botnets with their father's credit card. While he signed his Hack Forums posts with the name "Rob," Janit0r also used different names within each email, said he never intends to log into his Janit0r Hack Forums account again, and has consistently changed email addresses every few days.
For what's worth it, Janit0r has been very careful with his OpSec, compared to many of today's hackers, who, according to a Flashpoint report released yesterday, prefer Skype as their main communications method, an IM service known to give up data on its users to law enforcement.
Janit0r: I'm not a security researcher
Current clues like Janit0r's reverse engineering skills, in-depth knowledge of the malware scene, and a desire to do good, point to the fact that we may be dealing with another security researcher or network engineer that has decided to do something about the ever-increasing number of unsecured network and IoT devices.
"For what it's worth I'll state that I've never actually worked in networking, systems administration, information security or anything of the sort, but I have a hobby interest in all of the above. I believe that basic knowledge in such things is good self-defense in the 21st century," Janit0r wrote in an email.
Right now, all users and companies can do is to follow Radware and ICS-CERT's recommendations, and block access to Telnet and SSH ports, and also change the device's default password. Otherwise, they may get a visit from BrickerBot, and it might reach Plan B....
2 notes
·
View notes
Text
Developer faces prison after admitting admin software was really a RAT

A Kentucky man has pleaded guilty to federal charges he developed, marketed, and provided technical support for software he knew customers used illegally to take control of other people’s computers.
Colton Grubbs used the handle KFC Watermelon to advertise the LuminosityLink administrative tool on Hackforums[dot]net, federal prosecutors alleged in an indictment filed last month. The indictment said the tool provided a variety of malicious capabilities including the ability for purchasers to control others�� computers, surreptitiously record users’ activities, and to view their files, login credentials, and personal information. The defendant, prosecutors said, also used the hacker forum and a website located at luminosity[dot]link to teach users how to conceal their identities and prevent antivirus programs from detecting the tool.
On Monday, Grubbs signed a plea agreement that admitted that from 2015 to 2017 he designed LuminosityLink and sold it for $40 apiece to more than 6,000 individuals, knowing that some of them were using it maliciously. While previously claiming the software was a legitimate tool for system administrators, Monday’s plea agreement admitted he knew some customers were using it to control computers without owners’ knowledge or permission. The document, which was signed by Grubbs, stated:
Read 4 remaining paragraphs | Comments
Developer faces prison after admitting admin software was really a RAT published first on https://medium.com/@HDDMagReview
0 notes
Text
Developer faces prison after admitting admin software was really a RAT

A Kentucky man has pleaded guilty to federal charges he developed, marketed, and provided technical support for software he knew customers used illegally to take control of other people’s computers.
Colton Grubbs used the handle KFC Watermelon to advertise the LuminosityLink administrative tool on Hackforums[dot]net, federal prosecutors alleged in an indictment filed last month. The indictment said the tool provided a variety of malicious capabilities including the ability for purchasers to control others’ computers, surreptitiously record users’ activities, and to view their files, login credentials, and personal information. The defendant, prosecutors said, also used the hacker forum and a website located at luminosity[dot]link to teach users how to conceal their identities and prevent antivirus programs from detecting the tool.
On Monday, Grubbs signed a plea agreement that admitted that from 2015 to 2017 he designed LuminosityLink and sold it for $40 apiece to more than 6,000 individuals, knowing that some of them were using it maliciously. While previously claiming the software was a legitimate tool for system administrators, Monday’s plea agreement admitted he knew some customers were using it to control computers without owners’ knowledge or permission. The document, which was signed by Grubbs, stated:
Read 4 remaining paragraphs | Comments
Developer faces prison after admitting admin software was really a RAT published first on https://medium.com/@CPUCHamp
0 notes
