#hashicorp vault in kubernetes
Explore tagged Tumblr posts
Text
Learn HashiCorp Vault in Kubernetes Using KubeVault

In today's cloud-native world, securing secrets, credentials, and sensitive configurations is more important than ever. That’s where Vault in Kubernetes becomes a game-changer — especially when combined with KubeVault, a powerful operator for managing HashiCorp Vault within Kubernetes clusters.
🔐 What is Vault in Kubernetes?
Vault in Kubernetes refers to the integration of HashiCorp Vault with Kubernetes to manage secrets dynamically, securely, and at scale. Vault provides features like secrets storage, access control, dynamic secrets, and secrets rotation — essential tools for modern DevOps and cloud security.
🚀 Why Use KubeVault?
KubeVault is an open-source Kubernetes operator developed to simplify Vault deployment and management inside Kubernetes environments. Whether you’re new to Vault or running production workloads, KubeVault automates:
Deployment and lifecycle management of Vault
Auto-unsealing using cloud KMS providers
Seamless integration with Kubernetes RBAC and CRDs
Secure injection of secrets into workloads
🛠️ Getting Started with KubeVault
Here's a high-level guide on how to deploy Vault in Kubernetes using KubeVault:
Install the KubeVault Operator Use Helm or YAML manifests to install the operator in your cluster. helm repo add appscode https://charts.appscode.com/stable/
helm install kubevault-operator appscode/kubevault --namespace kubevault --create-namespace
Deploy a Vault Server Define a custom resource (VaultServer) to spin up a Vault instance.
Configure Storage and Unsealer Use backends like GCS, S3, or Azure Blob for Vault storage and unseal via cloud KMS.
Inject Secrets into Workloads Automatically mount secrets into pods using Kubernetes-native integrations.
💡 Benefits of Using Vault in Kubernetes with KubeVault
✅ Automated Vault lifecycle management
✅ Native Kubernetes authentication
✅ Secret rotation without downtime
✅ Easy policy management via CRDs
✅ Enterprise-level security with minimal overhead
🔄 Real Use Case: Dynamic Secrets for Databases
Imagine your app requires database credentials. Instead of hardcoding secrets or storing them in plain YAML files, you can use KubeVault to dynamically generate and inject secrets directly into pods — with rotation and revocation handled automatically.
🌐 Final Thoughts
If you're deploying applications in Kubernetes, integrating Vault in Kubernetes using KubeVault isn't just a best practice — it's a security necessity. KubeVault makes it easy to run Vault at scale, without the hassle of manual configuration and operations.
Want to learn more? Check out KubeVault.com — the ultimate toolkit for managing secrets in Kubernetes using HashiCorp Vault.
1 note
·
View note
Text
Top 10 DevOps Containers in 2023
Top 10 DevOps Containers in your Stack #homelab #selfhosted #DevOpsContainerTools #JenkinsContinuousIntegration #GitLabCodeRepository #SecureHarborContainerRegistry #HashicorpVaultSecretsManagement #ArgoCD #SonarQubeCodeQuality #Prometheus #nginxproxy
If you want to learn more about DevOps and building an effective DevOps stack, several containerized solutions are commonly found in production DevOps stacks. I have been working on a deployment in my home lab of DevOps containers that allows me to use infrastructure as code for really cool projects. Let’s consider the top 10 DevOps containers that serve as individual container building blocks…

View On WordPress
#ArgoCD Kubernetes deployment#DevOps container tools#GitLab code repository#Grafana data visualization#Hashicorp Vault secrets management#Jenkins for continuous integration#Prometheus container monitoring#Secure Harbor container registry#SonarQube code quality#Traefik load balancing
0 notes
Text
Master Cloud Security Coaching with Gritty Tech
Understanding Cloud Security Coaching
In the digital era, cloud adoption is accelerating faster than ever. However, this surge also brings escalating security risks. Gritty Tech's Cloud Security Coaching is crafted to empower individuals and enterprises with the expertise needed to protect their cloud assets. Our program delivers practical, comprehensive training to help you master the complexities of cloud security For More…
The Growing Importance of Cloud Security
With businesses increasingly relying on cloud services, security breaches can have devastating consequences. Outdated security models are insufficient against modern threats. Gritty Tech's coaching equips you with cutting-edge skills to safeguard data, ensure compliance, and maintain stakeholder trust.
What Gritty Tech Offers in Cloud Security Coaching
At Gritty Tech, our Cloud Security Coaching is a dynamic, hands-on experience designed to:
Strengthen foundational and advanced cloud security skills
Identify security vulnerabilities and mitigate risks
Deploy cloud infrastructure following security best practices
Navigate global compliance standards
We customize learning paths to fit your current skill level, whether you are a beginner or an experienced professional.
Core Elements of Gritty Tech's Coaching
Cloud Basics and Security Architecture
Kick-start your journey with a solid understanding of cloud principles and the shared responsibility model, forming the backbone of secure cloud architecture.
Identity and Access Management (IAM)
Gain mastery over:
Least privilege principles
Role-Based Access Control (RBAC)
Single Sign-On (SSO) and federated identity management
Data Protection Strategies
Secure sensitive information with:
Encryption methods for data at rest and in transit
Key Management Systems (KMS)
Data classification and secure backup solutions
Securing Cloud Networks
Adapt to the new cloud perimeter by learning:
Virtual Private Cloud (VPC) architecture
Network segmentation and firewall configurations
Threat detection and response strategies
DevSecOps Integration
Embed security across your development lifecycle with training on:
Infrastructure as Code (IaC) security
Secure CI/CD pipelines
Automated vulnerability scanning
Governance, Risk, and Compliance
Understand the essentials of:
GDPR, HIPAA, PCI DSS, and ISO 27001 compliance
Risk assessments and governance policies
Preparing for audits
Incident Management
Prepare for potential breaches with:
Incident detection and response
Cloud forensics techniques
Business continuity and disaster recovery planning
Gritty Tech's Exclusive Benefits
Tailored Coaching Plans: Personalized paths based on your goals
Practical Exercises: Real-world attack and defense simulations
Expert Mentorship: Learn from seasoned cloud security professionals
Certification Readiness: Extensive prep for top industry certifications
Lifetime Learning Access: Continuous updates and resource availability
Ideal Candidates for Cloud Security Coaching
Our coaching is perfect for:
IT professionals transitioning to the cloud
Cybersecurity analysts and engineers
Cloud architects and developers
Organizations seeking workforce upskilling
Platforms and Tools Covered
Gritty Tech provides in-depth training on platforms like:
Amazon Web Services (AWS)
Microsoft Azure
Google Cloud Platform (GCP)
Oracle Cloud Infrastructure (OCI)
We also dive into tools such as Kubernetes, Terraform, HashiCorp Vault, and more.
Practical Experience through Labs and Projects
We emphasize action through:
Interactive labs
Capture the Flag (CTF) exercises
Real-world project simulations
These experiences bridge the gap between theory and practice.
Success Stories from Gritty Tech
Our alumni have advanced careers in leading global companies, securing critical cloud environments and leading security initiatives.
Staying Ahead with Gritty Tech
Gritty Tech continuously updates its courses to include:
Latest threat intelligence
New regulatory requirements
Cutting-edge tools and methodologies
Certification Training Support
We thoroughly prepare you for:
AWS Certified Security - Specialty
Azure Security Engineer Associate
Google Professional Cloud Security Engineer
Certified Cloud Security Professional (CCSP)
You’ll receive study materials, mock exams, and coaching guidance throughout your certification journey.
Learning Models at Gritty Tech
Flexible options to suit your needs:
Live Online Sessions
Self-Paced Learning
Corporate Onsite Training
Choose what fits your schedule and learning style.
Pricing and Enrollment
Gritty Tech offers:
Individual Training Packages
Corporate Team Training
Enterprise-Level Custom Solutions
Contact Gritty Tech today for a tailored quote based on your needs.
Frequently Asked Questions
Do I need prior cloud experience?
No. Our beginner to expert tracks ensure everyone can start and progress confidently.
What is the course duration?
Courses vary from intensive 4-week tracks to comprehensive 6-month programs.
Will I receive a certificate?
Yes. You will get a Gritty Tech completion certificate and support toward industry certifications.
Is lifetime access included?
Yes. All learners enjoy lifetime access to materials and updates.
What support is available?
Gritty Tech offers 24/7 learner support via multiple communication channels.
Why Choose Gritty Tech for Cloud Security Coaching?
Choosing Gritty Tech means choosing a future where cloud security is second nature. Our practical approach, expert coaching, and continuous learning resources ensure you not only learn but excel.
Secure your cloud future today with Gritty Tech's Cloud Security Coaching — where knowledge meets resilience. Connect with us now and start building your cloud security expertise!
0 notes
Text
Top Ansible Modules for Cloud Automation in 2025
Introduction
As cloud adoption continues to surge in 2025, IT teams are increasingly turning to Ansible to automate infrastructure provisioning, configuration management, and application deployment. With its agentless architecture and extensive module library, Ansible simplifies cloud automation across multiple providers like AWS, Azure, Google Cloud, and more. In this blog, we will explore the top Ansible modules that are shaping cloud automation in 2025.
1. AWS Cloud Automation Modules
Amazon Web Services (AWS) remains a dominant force in cloud computing. Ansible provides several modules to automate AWS infrastructure, making it easier for DevOps teams to manage cloud resources. Some key AWS Ansible modules include:
amazon.aws.ec2_instance – Automates EC2 instance provisioning and configuration.
amazon.aws.s3_bucket – Manages AWS S3 bucket creation and permissions.
amazon.aws.rds_instance – Simplifies AWS RDS database provisioning.
amazon.aws.elb_application_lb – Automates Elastic Load Balancer (ALB) management.
amazon.aws.iam_role – Helps in managing AWS IAM roles and permissions.
These modules enhance infrastructure-as-code (IaC) practices, reducing manual efforts and increasing consistency.
2. Microsoft Azure Cloud Automation Modules
Microsoft Azure continues to grow with its enterprise-friendly cloud solutions. Ansible supports Azure cloud automation through the following modules:
azure.azcollection.azure_rm_virtualmachine – Automates the deployment of Azure virtual machines.
azure.azcollection.azure_rm_storageaccount – Manages Azure Storage accounts.
azure.azcollection.azure_rm_networkinterface – Handles network configurations in Azure.
azure.azcollection.azure_rm_kubernetescluster – Automates AKS (Azure Kubernetes Service) cluster deployment.
azure.azcollection.azure_rm_roleassignment – Assigns and manages user roles in Azure.
These modules provide a seamless way to manage Azure infrastructure with Ansible playbooks.
3. Google Cloud Platform (GCP) Automation Modules
Google Cloud has gained traction in AI, ML, and Kubernetes-based workloads. Ansible supports Google Cloud automation with these modules:
google.cloud.gcp_compute_instance – Provisions and manages Google Compute Engine instances.
google.cloud.gcp_storage_bucket – Automates Google Cloud Storage bucket management.
google.cloud.gcp_sql_instance – Manages Cloud SQL databases.
google.cloud.gcp_container_cluster – Deploys Kubernetes clusters in GKE (Google Kubernetes Engine).
google.cloud.gcp_firewall_rule – Configures firewall rules for Google Cloud networks.
Using these modules, DevOps teams can create scalable and secure Google Cloud environments.
4. Kubernetes and Containerization Modules
Kubernetes has become a critical component of modern cloud applications. Ansible supports container and Kubernetes automation with:
kubernetes.core.k8s – Manages Kubernetes resources, including deployments, services, and config maps.
kubernetes.core.helm – Automates Helm chart deployments.
community.docker.docker_container – Deploys and manages Docker containers.
kubernetes.core.k8s_auth – Manages Kubernetes authentication and role-based access control (RBAC).
kubernetes.core.k8s_scale – Dynamically scales Kubernetes deployments.
These modules make it easier to orchestrate containerized workloads efficiently.
5. Multi-Cloud and Hybrid Cloud Automation Modules
With enterprises adopting multi-cloud and hybrid cloud strategies, Ansible provides modules that help manage cloud-agnostic workloads, such as:
community.general.proxmox – Automates virtualization tasks in Proxmox.
community.vmware.vmware_guest – Manages VMware virtual machines.
community.general.terraform – Integrates Ansible with Terraform for multi-cloud deployments.
community.hashi_vault – Retrieves secrets from HashiCorp Vault securely.
community.general.consul – Automates Consul-based service discovery.
These modules help enterprises unify cloud operations across different providers.
Conclusion
Ansible remains at the forefront of cloud automation in 2025, offering an extensive range of modules to manage infrastructure seamlessly across AWS, Azure, GCP, Kubernetes, and hybrid cloud environments. Whether you are provisioning VMs, managing storage, or orchestrating containers, these top Ansible modules can simplify your cloud automation workflows.
By leveraging Ansible's capabilities, organizations can reduce complexity, improve efficiency, and accelerate cloud-native adoption. If you haven’t explored Ansible for cloud automation yet, now is the time to get started!
For more details www.hawkstack.com
What’s your favorite Ansible module for cloud automation? Let us know in the comments!
0 notes
Text
Automation in DevOps (DevSecOps): Integrating Security into the Pipeline
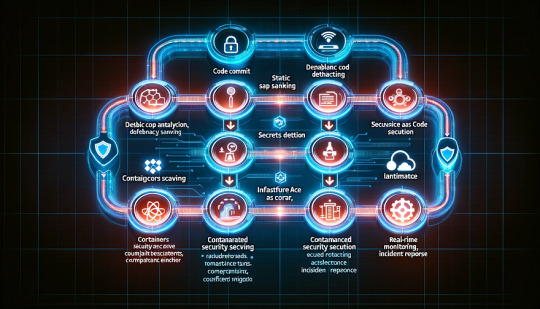
In modern DevOps practices, security can no longer be an afterthought — it needs to be embedded throughout the software development lifecycle (SDLC). This approach, known as DevSecOps, integrates security automation into DevOps workflows to ensure applications remain secure without slowing down development.
Why Security Automation?
Traditional security models relied on manual code reviews and vulnerability assessments at the end of the development cycle, often leading to bottlenecks and delayed releases. Security automation addresses these issues by: ✔️ Detecting vulnerabilities early in the CI/CD pipeline ✔️ Reducing manual intervention and human error ✔️ Ensuring continuous compliance with industry regulations ✔️ Improving incident response time
Key Areas of Security Automation in DevOps
1. Automated Code Security (Static & Dynamic Analysis)
Static Application Security Testing (SAST): Scans source code for vulnerabilities before deployment (e.g., SonarQube, Checkmarx).
Dynamic Application Security Testing (DAST): Identifies security flaws in running applications (e.g., OWASP ZAP, Burp Suite).
Software Composition Analysis (SCA): Detects vulnerabilities in third-party dependencies (e.g., Snyk, WhiteSource).
🔹 Example: Running SAST scans automatically in a Jenkins pipeline to detect insecure coding practices before merging code.
2. Secrets Management & Access Control
Automating the detection and handling of hardcoded secrets, API keys, and credentials using tools like HashiCorp Vault, AWS Secrets Manager, and CyberArk.
Implementing least privilege access via automated IAM policies to ensure only authorized users and services can access sensitive data.
🔹 Example: Using HashiCorp Vault to generate and revoke temporary credentials dynamically instead of hardcoding them.
3. Automated Compliance & Policy Enforcement
Infrastructure as Code (IaC) security scans using Checkov, OPA (Open Policy Agent), or Terraform Sentinel ensure that cloud configurations follow security best practices.
Automated audits and reporting help maintain compliance with GDPR, HIPAA, SOC 2, and ISO 27001 standards.
🔹 Example: Using Checkov to scan Terraform code for misconfigurations before provisioning cloud resources.
4. Container & Kubernetes Security
Scanning container images for vulnerabilities using Trivy, Aqua Security, or Anchore before pushing them to a registry.
Implementing Kubernetes security policies (e.g., Pod Security Policies, Kyverno, or Gatekeeper) to enforce security rules.
🔹 Example: Using Trivy in a CI/CD pipeline to scan Docker images before deployment to Kubernetes.
5. Continuous Security Monitoring & Threat Detection
Implementing SIEM (Security Information and Event Management) tools like Splunk, ELK Stack, or AWS Security Hub for real-time security event detection.
Using Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) (e.g., Snort, Suricata) to detect and respond to security threats.
AI-driven anomaly detection via Amazon GuardDuty, Microsoft Defender for Cloud, or Google Chronicle.
🔹 Example: Configuring AWS Security Hub to automatically detect and alert on misconfigurations in an AWS environment.
6. Automated Incident Response & Remediation
Using SOAR (Security Orchestration, Automation, and Response) platforms like Splunk SOAR or Palo Alto Cortex XSOAR to automate security incident triage and response.
Creating automated playbooks for threat mitigation, such as isolating compromised containers or blocking suspicious IPs.
🔹 Example: Automating AWS Lambda functions to quarantine an EC2 instance when an anomaly is detected.
Bringing It All Together: A DevSecOps Pipeline Example
1️⃣ Code Commit: Developers push code to a Git repository. 2️⃣ Static Code Analysis: SAST tools scan for vulnerabilities. 3️⃣ Dependency Scanning: SCA tools check third-party libraries. 4️⃣ Secrets Detection: Git hooks or automated scanners look for hardcoded secrets. 5️⃣ Container Security: Images are scanned before being pushed to a container registry. 6️⃣ Infrastructure as Code Scanning: Terraform or Kubernetes configurations are checked. 7️⃣ Automated Security Testing: DAST and penetration tests run in staging. 8️⃣ Compliance Checks: Policies are enforced before deployment. 9️⃣ Real-time Monitoring: Logs and security events are analyzed for threats. 🔟 Incident Response: Automated workflows handle detected threats.
Final Thoughts
Security automation in DevOps is critical for ensuring that security does not slow down development. By integrating automated security testing, policy enforcement, and monitoring, teams can build resilient, compliant, and secure applications without sacrificing speed.
WEBSITE: https://www.ficusoft.in/devops-training-in-chennai/
0 notes
Text
What are the Best DevOps Training Courses?
In today's fast-paced digital landscape, businesses are increasingly adopting DevOps practices to streamline their software development and operations processes. The DevOps methodology brings together development (Dev) and operations (Ops) teams to work collaboratively throughout the lifecycle of applications, ensuring faster and more efficient delivery of high-quality software online devops training in pune.

1. Coursera
DevOps Specialization by University of California, Davis
Covers DevOps principles, CI/CD, and automation.
Hands-on projects and a capstone project.
2. edX
DevOps MicroMasters Program by Boston University
Focuses on DevOps practices, Agile methodologies, and cloud technologies.
Comprehensive and includes a final capstone project.
3. Udacity
Cloud DevOps Engineer Nanodegree
Emphasizes deploying applications on cloud platforms.
Hands-on projects with real-world scenarios.
4. Pluralsight
DevOps Path
A series of courses covering tools like Docker, Kubernetes, and CI/CD pipelines.
Tailored for different skill levels from beginner to advanced.
5. LinkedIn Learning
Become a DevOps Engineer Learning Path
A curated set of courses focusing on DevOps tools and practices.
Includes practical examples and projects.
6. Linux Academy (now part of A Cloud Guru)
DevOps Courses
Offers a range of courses on specific tools like Terraform, Ansible, and Jenkins.
Hands-on labs to practice skills.
7. AWS Training and Certification
DevOps Engineering on AWS
Focuses on AWS services and tools for DevOps.
Includes best practices for building and managing applications.
8. Google Cloud Training
Professional DevOps Engineer Certification
Prepares you for the Google Cloud certification exam.
Covers CI/CD, monitoring, and incident management on Google Cloud.
9. HashiCorp Learn
Free Tutorials on Terraform, Vault, and more
Great for hands-on learning with HashiCorp tools.
Self-paced and project-based.
10. Kubernetes Official Training
Kubernetes Fundamentals
Offers in-depth knowledge of Kubernetes, a key tool in DevOps.
Available through various providers like the Linux Foundation.
Considerations for Choosing a Course:
Skill Level: Choose based on your current knowledge (beginner, intermediate, advanced).
Specific Tools/Technologies: Focus on courses that cover tools you want to learn (e.g., Docker, Kubernetes, Jenkins).
Hands-On Practice: Look for courses with practical projects and labs.
Certification: If certification is important, consider courses that prepare for industry-recognized exams.
Conclusion
DevOps is more than just a buzzword — it’s a set of principles and practices that can radically transform software development and IT operations. Whether you're just starting your journey or are a seasoned professional looking to upgrade your skills, there’s a training course that fits your needs.
Courses like those offered by Coursera, Udacity, and AWS are excellent options for anyone looking to dive into DevOps, while specialized programs from Docker and Google Cloud are perfect for professionals looking to specialize in specific areas. No matter which course you choose, investing in DevOps training is a wise step to take as the demand for these skills is only growing.online devops training in pune,devops training in pune,devops classes in pune,devops course in pune,best devops classes in pune,aws devops classes in pune,best devops training institute in pune,devops classes in pune with placement
Happy learning, and here's to your success in the exciting world of DevOps!
#online devops training in pune#devops training in pune#devops classes in pune#devops course in pune#best devops classes in pune#aws devops classes in pune#best devops training institute in pune#devops classes in pune with placement
0 notes
Text
Securing Workloads in OpenShift Virtualization: Tips and Techniques
As organizations continue to embrace the benefits of cloud-native technologies and virtualization, OpenShift Virtualization stands out as an essential platform for deploying and managing containerized workloads. While it offers powerful capabilities for running virtual machines (VMs) alongside containers, ensuring the security of workloads is paramount to protect data integrity and maintain regulatory compliance. This article outlines practical tips and techniques to enhance the security of your workloads in OpenShift Virtualization.
1. Implement Role-Based Access Control (RBAC)
RBAC is one of the core security mechanisms in OpenShift that helps control who can access what resources within the cluster. Ensuring that your workload access is limited to authorized users and services only is critical. Follow these best practices:
Define Roles Carefully: Create roles with the minimum necessary permissions for users and applications.
Use Service Accounts: Assign service accounts to pods and workloads to control their privileges and avoid the risk of a compromised application gaining excessive access.
Review and Audit Permissions Regularly: Perform periodic audits to identify and remove unused or overly permissive roles.
2. Secure Network Communication
Communication between workloads should be secured to prevent unauthorized access and data interception. Implement these strategies:
Network Policies: Use OpenShift’s network policy objects to define rules that control the traffic flow between pods. Ensure that only authorized pods can communicate with each other.
Service Mesh: Deploy Istio or OpenShift Service Mesh to provide enhanced traffic management, encryption, and observability across services.
TLS Encryption: Ensure all data exchanged between services is encrypted using TLS. OpenShift has built-in support for TLS, but make sure that TLS certificates are properly managed and rotated.
3. Enable and Manage Pod Security Standards
Pod Security Standards (PSS) are an essential way to enforce security configurations at the pod level. OpenShift provides tools to help secure pods according to industry standards:
PodSecurityPolicies (PSPs): While PSPs are deprecated in favor of PodSecurityAdmission (PSA), configuring your cluster to use PSA can enforce security standards such as preventing privileged containers or requiring specific security context configurations.
Security Contexts: Set up security contexts at the container level to control privileges like running as a non-root user, disabling privilege escalation, and enabling read-only file systems.
4. Control Image Security
Images are a common attack vector, making it essential to ensure that only trusted images are used for deployments.
Image Scanning: Integrate image scanning tools such as OpenShift's built-in image vulnerability scanner or third-party tools like Trivy or Clair to scan images for known vulnerabilities before deployment.
Image Signing and Verification: Use tools like Notary to sign images and enforce policies that only signed images are pulled and deployed.
Private Image Registries: Store and manage your images in a private registry with access control, ensuring that only authorized users and services can push or pull images.
5. Manage Secrets Securely
Handling secrets properly is critical for the security of your applications and infrastructure. Follow these steps:
Use OpenShift Secrets: OpenShift has native support for Kubernetes Secrets. Ensure that secrets are stored securely and accessed only by the workloads that need them.
Vault Integration: For more advanced secret management, integrate HashiCorp Vault with OpenShift to handle sensitive data, providing more control over access policies and encryption.
Avoid Hardcoding Secrets: Never hardcode secrets in application code or scripts. Use environment variables or service accounts to inject them at runtime.
6. Apply Security Patches and Updates
Keeping your OpenShift cluster and underlying virtualization environment updated is essential for closing security vulnerabilities.
Automatic Updates: Configure automated updates and patching for OpenShift components and underlying VMs.
Monitor Security Advisories: Regularly review Red Hat's security advisories and promptly apply patches or updates that mitigate potential risks.
Testing in Staging: Before deploying patches in production, test them in a staging environment to ensure stability and compatibility.
7. Implement Logging and Monitoring
Effective logging and monitoring help you detect and respond to security incidents in real time.
Centralized Logging: Use OpenShift’s built-in logging stack or integrate with a tool like Elasticsearch, Fluentd, and Kibana (EFK) to aggregate logs across the cluster and VMs.
Monitoring with Prometheus and Grafana: Leverage Prometheus for metrics collection and Grafana for dashboards that visualize performance and security data.
Alerting Mechanisms: Set up alerts for suspicious activities such as unexpected network traffic, unauthorized access attempts, or failed authentication attempts.
8. Secure Virtual Machines
When running VMs in OpenShift Virtualization, their security should align with best practices for containerized workloads.
VM Hardening: Follow hardening guidelines for your VM images, such as disabling unnecessary services, securing SSH access, and minimizing the installed software.
Isolation and Segmentation: Place VMs in different namespaces or network segments based on their sensitivity and usage. This helps limit the attack surface and restrict lateral movement in the event of a breach.
Resource Limitations: Set CPU and memory limits to prevent DoS (Denial of Service) attacks within your VMs.
9. Implement Multi-Factor Authentication (MFA)
To bolster the authentication process, enabling MFA for accessing OpenShift and the management interface is crucial.
Configure MFA with OpenShift: Use identity providers that support MFA, such as LDAP or OAuth integrations, to strengthen user authentication.
Enforce MFA for Sensitive Operations: Apply MFA to critical administrative functions to ensure that only authorized personnel can perform potentially disruptive actions.
Conclusion
Securing workloads in OpenShift Virtualization requires a multi-layered approach that combines preventive, detective, and corrective measures. By implementing these tips and techniques—ranging from robust RBAC and secure network configurations to thorough monitoring and timely patching—you can create a secure environment for your containerized and virtualized workloads. OpenShift Virtualization offers the tools to build a resilient infrastructure, but security practices should evolve in tandem with emerging threats and industry trends to protect your applications and data effectively. For more details visit: https://www.hawkstack.com/
0 notes
Text
Kubernetes Security Essentials: Safeguarding Your Cluster
As Kubernetes continues to be the go-to platform for container orchestration, securing your Kubernetes environment has become paramount. A compromised cluster can lead to data breaches, application downtime, or even misuse of your infrastructure for malicious purposes. Here, we explore essential Kubernetes security practices to help you safeguard your cluster effectively.
1. Implement Role-Based Access Control (RBAC)
RBAC is a critical feature of Kubernetes that ensures users and applications have access only to the resources they need. By defining roles and binding them to specific users or service accounts, you minimize the risk of privilege escalation.
Tip: Regularly audit your RBAC policies and avoid granting overly permissive roles like cluster-admin.
2. Secure the API Server
The Kubernetes API server is the control plane for your cluster. Unauthorized access to the API server can compromise the entire cluster.
Key Actions:
Enable HTTPS for API server communication.
Use authentication mechanisms like certificates, tokens, or OpenID Connect.
Restrict access using IP whitelisting or network policies.
3. Use Network Policies
Network policies help you control communication between pods and external systems. This limits the blast radius in case of a breach.
Steps to Follow:
Define network policies to allow only necessary traffic between pods.
Isolate sensitive workloads using namespaces and policy rules.
4. Regularly Scan Images for Vulnerabilities
Container images are often the entry point for vulnerabilities. Ensure that your images are secure by:
Using trusted image registries.
Scanning images with tools like Trivy, Aqua Security, or Anchore.
Keeping images up-to-date with the latest patches.
5. Encrypt Secrets and Data at Rest
Kubernetes stores sensitive data, such as secrets and configurations, which should be encrypted to prevent unauthorized access.
Best Practices:
Use tools like Kubernetes Secrets Encryption.
Integrate with external secret management systems such as HashiCorp Vault or AWS Secrets Manager.
6. Monitor and Audit Your Cluster
Continuous monitoring is essential for detecting anomalies and unauthorized activities in real time.
Use tools like Prometheus, Grafana, and Kubernetes Audit Logs.
Set up alerts for unusual activity, such as unexpected pod creation or high resource usage.
7. Apply Pod Security Standards
Pod security policies enforce security controls at the pod level, ensuring compliance with best practices.
Disable privileged containers unless absolutely necessary.
Limit container capabilities and set appropriate seccomp profiles.
Enforce read-only root filesystems wherever possible.
Conclusion
Securing your Kubernetes environment is not a one-time task but an ongoing process. By adhering to these Kubernetes security essentials, you can ensure your cluster remains resilient against emerging threats. Make security an integral part of your DevOps workflow to protect your applications, data, and reputation.
For more details click www.hawkstack.com
#redhatcourses#information technology#containerorchestration#kubernetes#container#linux#docker#containersecurity#qcsdclabs#hawkstack#hawkstack technologies
0 notes
Text

Kubernetes, the popular open-source container orchestration platform, offers robust features for automating the deployment, scaling, and management of containerized applications. However, its powerful capabilities come with a complex security landscape that requires careful consideration to protect applications and data. Here’s an overview of key practices and tools to enhance Kubernetes security:
1. Network Policies
Network policies in Kubernetes control the communication between pods. By default, Kubernetes allows all traffic between pods, but network policies can be used to define rules that restrict which pods can communicate with each other. This is crucial for minimizing the attack surface and preventing unauthorized access.
2. RBAC (Role-Based Access Control)
Kubernetes RBAC is a method for regulating access to the Kubernetes API. It allows you to define roles with specific permissions and assign those roles to users or service accounts. Implementing RBAC helps ensure that users and applications have only the permissions they need to function, reducing the risk of privilege escalation.
3. Secrets Management
Kubernetes Secrets are designed to store sensitive information, such as passwords, OAuth tokens, and SSH keys. It’s essential to use Secrets instead of environment variables for storing such data to ensure it’s kept secure. Additionally, consider integrating with external secret management tools like HashiCorp Vault for enhanced security.
4. Pod Security Policies
Pod Security Policies (PSPs) are cluster-level resources that control security-sensitive aspects of pod specifications. PSPs can enforce restrictions on pod execution, such as requiring the use of specific security contexts, preventing the use of privileged containers, and controlling access to host resources. While PSPs are being deprecated in favor of other mechanisms like OPA Gatekeeper, they are still crucial for current security practices.
5. Image Security
Ensuring the security of container images is critical. Use trusted base images, and regularly scan your images for vulnerabilities using tools like Clair or Trivy. Additionally, sign your images with tools like Notary and use a container registry that supports image signing and verification.
6. Runtime Security
Monitoring your containers at runtime is essential to detect and respond to security threats. Tools like Falco, a runtime security tool for Kubernetes, can help detect unexpected behavior, configuration changes, and potential intrusions. Integrating such tools with a logging and alerting system ensures that any suspicious activity is promptly addressed.
7. Secure Configuration
Ensure your Kubernetes components are securely configured. For example, restrict API server access, use TLS for secure communication between components, and regularly review and audit your configurations. Tools like kube-bench can help automate the process of checking your cluster against security best practices.
8. Regular Updates and Patching
Keeping your Kubernetes environment up-to-date is critical for maintaining security. Regularly apply patches and updates to Kubernetes components, container runtimes, and the underlying operating system to protect against known vulnerabilities.
9. Audit Logs
Enable Kubernetes audit logs to track access and modifications to the cluster. Audit logs provide a detailed record of user actions, making it easier to detect and investigate suspicious activities. Integrate these logs with a centralized logging system for better analysis and retention.
10. Compliance and Best Practices
Adhering to security best practices and compliance requirements is essential for any Kubernetes deployment. Regularly review and align your security posture with standards such as NIST, CIS Benchmarks, and organizational policies to ensure your cluster meets necessary security requirements.
In conclusion, Kubernetes security is multi-faceted and requires a comprehensive approach that includes network policies, access controls, secrets management, and regular monitoring. By implementing these best practices and leveraging the right tools, you can significantly enhance the security of your Kubernetes environment, ensuring your applications and data remain protected against threats.
0 notes
Text
The Unsung Heroes of DevOps Certifications for the Tools You Didn't Know You Needed
In the rapidly evolving world of technology, DevOps has emerged as a cornerstone of modern software development and IT operations. The synergy between development and operations teams ensures that products are delivered more quickly, with better quality, and with continuous integration and delivery. Yet, while the world often celebrates the headline-grabbing tools like Jenkins, Docker, and Kubernetes, there exists a suite of lesser-known tools that play crucial roles in DevOps pipelines. These tools, along with their respective certifications, are the unsung heroes that drive seamless operations in the background, ensuring efficiency, security, and scalability.
Why DevOps Certifications Matter
Before diving into these unsung tools, it’s important to understand the significance of DevOps certifications. Certifications validate a professional's skills, ensuring they are equipped to handle the complexities of modern DevOps environments. While many are familiar with certifications for major tools, there are specialized certifications that focus on more niche, yet essential, DevOps tools. These certifications often go unnoticed, but they hold the key to mastering the full spectrum of DevOps practices.
The Hidden Gems of DevOps
Terraform: Automating Infrastructure as Code
Certification: HashiCorp Certified: Terraform Associate
Why It’s Important: Terraform is an open-source tool that allows you to define and provision infrastructure using a high-level configuration language. While tools like Kubernetes manage containerized workloads, Terraform handles the infrastructure setup, making it a critical tool for multi-cloud environments. The Terraform Associate certification from HashiCorp ensures that professionals can efficiently automate infrastructure, manage resources, and use modules to streamline the process.
Ansible: Simplifying Configuration Management
Certification: Red Hat Certified Specialist in Ansible Automation
Why It’s Important: Ansible is an open-source tool that automates software provisioning, configuration management, and application deployment. It’s often overshadowed by more prominent tools, but Ansible's simplicity and ease of use make it a powerful addition to any DevOps toolkit. The certification focuses on automating tasks with Ansible, ensuring that professionals can manage complex deployments with minimal manual intervention.
Prometheus: The Overlooked Monitoring Powerhouse
Certification: Certified Kubernetes Administrator (CKA) with Prometheus
Why It’s Important: Prometheus is an open-source monitoring system and time series database developed by SoundCloud. It has become the de facto standard for monitoring Kubernetes clusters. Despite its importance, it often takes a backseat to more popular tools. The CKA certification, with a focus on Prometheus, ensures that professionals can monitor and troubleshoot Kubernetes clusters effectively.
Vault: Securing Secrets in DevOps
Certification: HashiCorp Certified: Vault Associate
Why It’s Important: Vault is a tool that securely stores and manages secrets, such as passwords, API keys, and certificates. In a world where security breaches can have devastating consequences, managing secrets securely is non-negotiable. The Vault Associate certification ensures that professionals can handle secrets management, encryption as a service, and identity-based access, making security an integral part of the DevOps pipeline.
Istio: The Silent Enforcer of Microservices Security
Certification: Istio Fundamentals Certification
Why It’s Important: Istio is an open-source service mesh that provides a way to control how microservices share data with one another. It offers security, observability, and traffic management capabilities. While not as famous as Kubernetes, Istio plays a crucial role in managing microservices architecture. The Istio Fundamentals Certification validates skills in managing service mesh, securing communications, and controlling traffic within a microservices environment. The Value of Knowing the Unsung Tools
These lesser-known tools might not always make headlines, but their impact on DevOps processes is profound. Professionals who master these tools through certifications not only enhance their skill sets but also ensure that their organizations can operate at peak efficiency. In an industry where the pace of change is relentless, being proficient in these tools can set professionals apart from the crowd.
Conclusion: Celebrating the Unsung Heroes
The world of DevOps is vast, with tools that cover every aspect of software development and IT operations. While the more popular tools often receive the spotlight, the unsung heroes quietly ensure that everything runs smoothly behind the scenes. By obtaining certifications in these lesser-known tools, DevOps professionals can ensure they are fully equipped to handle the complexities of modern IT environments. So, the next time you think about enhancing your DevOps skills, consider diving into these hidden gems—because the tools you didn’t know you needed might just be the ones that make all the difference.
0 notes
Text
Hashicorp Vault Docker Install Steps: Kubernetes Not Required!
Hashicorp Vault #Docker Install Steps: #Kubernetes Not Required! #devops
If you are doing much DevOps and working with terraform code, Ansible, or other IaC, having a secure place to store secrets so your code doesn’t have those secrets hard coded is a great way to make sure secrets and passwords are not stored in plain text. If you are looking to spin up Hashicorp Vault in an easy way, spinning it up in Docker is a great way to get up and running quickly. Let’s look…
0 notes
Text

Cloud infrastructure automation involves several key components to ensure efficient management, deployment, and operation of cloud resources. Infrastructure as Code (IaC) tools like Terraform, AWS CloudFormation, and Azure Resource Manager automate provisioning. Configuration Management tools such as Ansible and Puppet ensure system consistency. Continuous Integration/Continuous Deployment (CI/CD) tools like Jenkins and GitLab CI automate the software delivery process. Container Orchestration with Kubernetes and Docker Swarm manages containerized applications. Monitoring and Logging with Prometheus and ELK Stack provide visibility into system performance. Security and Compliance Automation using HashiCorp Vault and AWS Config ensures secure environments. Cost Management tools like AWS Cost Explorer optimize resource usage. Backup and Disaster Recovery Automation with AWS and Azure Backup ensure data protection. Self-healing systems like Kubernetes Health Checks and AWS Auto Scaling maintain reliability. Network Automation, which works with Cisco NSO and Ansible, manages network configurations. These components create a robust cloud infrastructure automation environment.
For businesses looking for comprehensive cloud infrastructure services in the USA, it is crucial to partner with providers who excel in these automation components. Whether you need to streamline your provisioning processes, ensure system consistency, automate your software delivery pipeline, or manage containerized applications, selecting a service provider with expertise in these areas is essential. They can help implement robust monitoring and logging systems, ensure security and compliance, optimize cost management, and set up reliable backup and disaster recovery solutions. Furthermore, self-healing systems and network automation capabilities are vital for maintaining the reliability and efficiency of your cloud infrastructure.
0 notes
Text
Kubernetes Security Best Practices: Safeguarding Your Containerized Applications

Kubernetes has revolutionized the way we deploy, manage, and scale containerized applications. However, with its growing adoption comes the critical need to ensure robust security practices to protect your infrastructure and data. Here are some essential Kubernetes security best practices to help you safeguard your containerized applications.
1. Network Policies
Implementing network policies is crucial for controlling traffic between pods. Kubernetes network policies allow you to define rules for inbound and outbound traffic at the pod level. By default, Kubernetes allows all traffic between pods, which can be a security risk. Use network policies to create a zero-trust network, where only explicitly permitted traffic is allowed.
2. Role-Based Access Control (RBAC)
RBAC is vital for managing who can access and perform actions within your Kubernetes cluster. Assign roles based on the principle of least privilege, ensuring that users and service accounts only have the permissions they need to perform their tasks. Regularly review and audit RBAC policies to maintain tight security.
3. Pod Security Policies
Pod Security Policies (PSPs) help enforce security standards at the pod level. PSPs can control aspects such as whether privileged containers can run, what volume types can be used, and which users can run containers. Although PSPs are being deprecated in future Kubernetes releases, consider using alternative tools like Open Policy Agent (OPA) or Kubernetes Pod Security Standards (PSS).
4. Image Security
Ensuring the security of container images is paramount. Use trusted sources for your base images and regularly update them to include security patches. Implement image scanning tools to detect vulnerabilities and misconfigurations in your images before deploying them. Tools like Clair, Trivy, and Aqua Security can help automate this process.
5. Secrets Management
Kubernetes Secrets are used to store sensitive information, such as passwords and API keys. However, storing secrets directly in environment variables or configuration files can expose them to potential attackers. Use Kubernetes Secrets to manage sensitive data and consider integrating with external secrets management solutions like HashiCorp Vault or AWS Secrets Manager for enhanced security.
6. Audit Logging
Enable and configure audit logging to track and monitor activities within your Kubernetes cluster. Audit logs provide valuable insights into who did what, when, and where, which is essential for detecting and responding to security incidents. Use tools like Fluentd, Elasticsearch, and Kibana to aggregate and analyze audit logs.
7. Cluster Hardening
Hardening your Kubernetes cluster involves securing the underlying infrastructure and configurations. Ensure your Kubernetes components, such as the API server, kubelet, and etcd, are securely configured. Disable insecure features, enforce HTTPS, and restrict access to the API server. Regularly update your Kubernetes components to the latest stable versions to incorporate security patches and improvements.
8. Resource Quotas and Limits
Set resource quotas and limits to prevent resource abuse and Denial-of-Service (DoS) attacks. By defining limits on CPU, memory, and other resources, you can ensure that no single pod or user consumes excessive resources, potentially impacting the stability and security of your cluster.
9. Namespace Segmentation
Segment your Kubernetes cluster using namespaces to isolate different applications or teams. Namespaces provide logical separation within a cluster, allowing you to apply security policies and resource quotas at a granular level. This helps contain potential security breaches and limits the blast radius of an attack.
10. Regular Security Audits and Penetration Testing
Conduct regular security audits and penetration testing to identify and address vulnerabilities in your Kubernetes cluster. Automated security scanning tools can help, but manual audits and penetration testing by skilled security professionals provide an additional layer of assurance. Regular assessments help you stay ahead of emerging threats and maintain a robust security posture.
Conclusion
Securing your Kubernetes environment is an ongoing process that requires vigilance, regular updates, and adherence to best practices. By implementing these Kubernetes security best practices, you can significantly reduce the risk of security breaches and ensure the safety of your containerized applications. Stay informed about the latest security trends and continuously improve your security measures to protect your infrastructure and data.
0 notes
Text
Top DevOps Tools for 2025: Optimizing Automation, CI/CD, and Infrastructure Management
Introduction
In today’s fast-paced digital landscape, DevOps has become a cornerstone of modern IT, enabling organizations to accelerate software delivery, improve reliability, and streamline infrastructure management. With the increasing demand for automation, CI/CD pipelines, and cloud-native architectures, selecting the right tools is crucial for DevOps success.
By leveraging cutting-edge DevOps tools, teams can enhance efficiency, minimize errors, and ensure seamless deployments. This blog explores the top DevOps tools in 2025, categorized by automation, CI/CD, infrastructure management, monitoring, and security. Additionally, we’ll discuss how HawkStack provides expert support to help organizations implement and manage these tools effectively.
1. Automation Tools
Automation is a fundamental aspect of DevOps, reducing manual intervention and ensuring consistency across environments. Here are some top automation tools:
Ansible – A powerful open-source tool for configuration management, automation, and application deployment.
Terraform – An Infrastructure as Code (IaC) tool that allows teams to define, provision, and manage infrastructure efficiently.
Pulumi – A modern IaC solution that supports multiple programming languages, making infrastructure automation more accessible to developers.
2. CI/CD Tools
Continuous Integration and Continuous Deployment (CI/CD) tools enable seamless software delivery, reducing the risk of deployment failures. The top tools include:
Jenkins – A widely used open-source automation server that enables CI/CD pipelines.
GitHub Actions – A GitHub-integrated CI/CD tool that simplifies automation for developers.
GitLab CI/CD – A robust DevOps platform that provides built-in CI/CD automation.
ArgoCD – A GitOps-based deployment tool for Kubernetes, ensuring declarative and automated application management.
3. Infrastructure & Container Management
With the rise of cloud-native applications, managing infrastructure and containers is essential. These tools lead the way:
Kubernetes – The industry-standard orchestration platform for managing containerized applications.
Docker – A widely used containerization platform that simplifies application development and deployment.
OpenShift – An enterprise Kubernetes platform that includes built-in security and automation features.
4. Monitoring & Observability
Monitoring and observability tools help DevOps teams gain real-time insights into system performance and reliability:
Prometheus – A popular open-source monitoring and alerting toolkit designed for cloud-native applications.
Grafana – A visualization tool that creates real-time dashboards for monitoring system health.
Datadog – A cloud monitoring solution offering full-stack observability.
New Relic – An application performance monitoring (APM) tool that provides deep insights into system performance.
5. Security & Compliance
Security is a critical aspect of DevOps, ensuring that applications and infrastructure remain protected. These tools help maintain security and compliance:
HashiCorp Vault – A powerful tool for managing secrets and encrypting sensitive data.
Aqua Security – A Kubernetes-native security platform designed to protect containerized applications.
Trivy – A fast and lightweight vulnerability scanner for containers and dependencies.
6. Best Practices for Choosing the Right DevOps Stack
When selecting DevOps tools, organizations should consider several key factors:
Scalability – Ensuring tools can grow with the business’s needs.
Integration – Compatibility with existing workflows and infrastructure.
Cost – Balancing open-source and enterprise solutions based on budget.
Support & Community – Evaluating the level of community support and vendor assistance.
Case studies of successful DevOps tool adoption can provide insights into best practices and implementation strategies.
7. How HawkStack Supports Your DevOps Journey
At HawkStack, we specialize in providing expert DevOps support to help organizations streamline their operations. Our services include:
Consulting & Implementation – Assisting with DevOps tool selection and integration.
Ongoing Support – Providing 24/7 support for DevOps tools and platforms.
Custom Solutions – Developing tailored automation, monitoring, and security solutions.
Conclusion
Choosing the right DevOps tools is crucial for optimizing automation, CI/CD, and infrastructure management. By leveraging top tools like Kubernetes, Ansible, Jenkins, and Terraform, organizations can improve efficiency, security, and scalability.
If you need expert guidance in implementing and managing your DevOps stack, HawkStack is here to help. Contact us today to learn how we can support your DevOps journey.
Need expert DevOps support? Contact us today!
visit www.hawkstack.com
0 notes
Text
Build resilient applications with Kubernetes on Azure

Welcome to KubeCon EU 2020, the virtual edition. While we won’t be able to see each other in person at KubeCon EU this year, we’re excited that this new virtual format of KubeCon will make the conference more accessible than ever, with more people from the amazing Kubernetes community able to join and participate from around the world without leaving their homes.
With everything that has been happening, the last year has been an up and down experience, but through it all I’m incredibly proud of the focus and dedication from the Azure Kubernetes team. They have continued to iterate and improve our Kubernetes on Azure that provides enterprise-grade experience for our customers.
Kubernetes on Azure (and indeed anywhere) delivers an open and portable ecosystem for cloud-native development. In addition to this core promise, we also deliver a unique enterprise-grade experience that ensures the reliability and security your workloads demand, while also enabling the agility and efficiency that business today desires. You can securely deploy any workload to Azure Kubernetes Service (AKS) to drive cost-savings at scale across your business. Today, we’re going to tell you about even more capabilities that can help you along on your cloud-native journey to Kubernetes on Azure.
Improving latency and operational efficiency
One of the key drivers of cloud adoption is reducing latency. It used to be that it took days to get physical computers and set them up in a cluster. Today, you can deploy a Kubernetes cluster on Azure in less than five minutes. These improvements benefit the agility of our customers. For customers who want to scale and provision faster, we are announcing a preview of ephemeral OS disk support which makes responding to new compute demands on your cluster even faster.
Latency isn’t just about the length of time to create a cluster. It’s also about how fast you can detect and respond to operational problems. To help enterprises improve their operational efficiency, we’re announcing preview integration with Azure Resource Health which can alert you if your cluster is unhealthy for any reason. We’re also announcing the general availability of node image updates which allow you to upgrade the underlying operating system to respond to bugs or vulnerabilities in your cluster while staying on the same Kubernetes version for stability.
Finally, though Kubernetes has always enabled enterprises to drive cost savings through containerization, the new economic realities of the world during a pandemic mean that achieving cost efficiency for your business is more important than ever. We’ve got a great exercise that can help you learn how to optimize your costs using containers and the Azure Kubernetes Service.
Secure by design with Kubernetes on Azure
One of the key pillars of any enterprise computing platform is security. With market-leading features like policy integration and Azure Active Directory identity for Pods and cloud-native security have always been an important part of the Azure Kubernetes Service. I’m excited about some new features we’ve added recently to further enhance the security of your workloads running on Kubernetes.
Though Kubernetes has built-in support for secrets, most enterprise
environments require a more secure and more compliant implementation. In the Azure Kubernetes Service, being enterprise-grade means providing integration between Azure Key Vault and the Azure Kubernetes service. Using Key Vault with Kubernetes enables you to securely store your credentials, certificates, and other secrets in state of the art, compliant secret store, and easily use them with your applications in an Azure Kubernetes cluster.
It’s even more exciting that this integration is built on the back of an open Container Storage Interface (CSI) driver that the Azure team built and open sourced for the entire Kubernetes community. Giving back to open source is an important part of what it means to be a community steward, and it was exciting to see our approach get validated as it was picked up and used by the HashiCorp Vault team for their secrets integration. Our open source team has been hard at work on improving many other parts of the security ecosystem. We’ve enhanced the CSI driver for Windows, and worked on cgroups v2 and containerd. If you want to learn more about how to secure your cloud-native workloads and make sure that your enterprise is following Microsoft’s best practices, check out our guide to Kubernetes best practices. They will teach you how to integrate firewalls, policy, and more to ensure you have both security and agility in your cloud-native development.
2 notes
·
View notes
Text
NEU Einführung des neuen Codefresh Runner
Die führende DevOps-Automatisierungsplattform für Kubernetes-Apps
Tausende Unternehmen - vom Start-up bis zum Fortune 500-Unternehmen - verwenden Codefresh, um leistungsstarke, skalierbare CI / CD-Pipelines zu erstellen.
Erstellen Sie ein kostenloses Konto. Planen Sie eine Demo
NEU
Führen Sie Pipelines in Ihrer Infrastruktur mit dem brandneuen Codefresh Runner aus.
Codefresh Runner ist eine skalierbare, sichere und kinderleichte Möglichkeit, Builds und Bereitstellungen auf jedem Kubernetes-Cluster - ob in der Cloud oder hinter der Firewall - ohne Wartung auszuführen. Installieren Sie noch heute mit nur zwei Befehlen.
Mehr erfahren
Einfache Integration
Arbeitet mit
jede Git Providerany Cloudanything
Codefresh lässt sich in alle Tools integrieren, die Sie bereits verwenden - sei es Ihr Versionsverwaltungsmanager, Ihre Testsuite, Ihr Paketmanager, Ihr Geheimmanager, Ihr Sicherheitsscanner, Ihre Cloud-Plattform oder sogar benutzerdefinierte interne Tools.
Alle Funktionen
Reichhaltige Funktionen
Leistungsstarke Pipelines in wenigen Minuten mit der integrierten Schrittbibliothek
Skalierbar und flexibel
Die leistungsstarke YAML-Syntax von Codefresh ist einfach, lässt sich jedoch auch auf die anspruchsvollsten Pipelines skalieren. Verwenden Sie optional bedingte Logik, parallele Schritte, Erstellungsphasen, Genehmigungen, Beiwagenservices und vieles mehr.
Führen Sie integrierte, Community- oder benutzerdefinierte Schritte aus
Heute kündigen wir eine neue Finanzierungsrunde an, die zusätzliche 27 Mio. USD einbringt, um in das Wachstum und den Aufbau von Codefresh zu investieren.
Version: "1.0"
Schritte:
clone_repo:
Typ: Git-Klon
Repo: $ {{CF_BRANCH}}
Bühne: "Klon"
build_docker_image:
Typ: Build
Bildname: "codefresh-io / cli"
Arbeitsverzeichnis: "$ {{clone}}"
Docker-Datei: "Docker-Datei"
Umgebung:
- SECRET = $ {{Secrets.secret-Name}}
deploy_to_k8s:
Typ: Bereitstellen
Cluster: Clustername
Service: Servicename
Namespace: Standard
Stufe: bereitstellen
custom_step:
Holen Sie sich Geheimnisse aus Hashicorp Vault
Lesen Sie die Geheimnisse von Hashicorp Vault in einer Codefresh-Pipeline
Schritt anzeigen
Führen Sie einen GKE-Befehl aus
Führen Sie einen Befehl in Google Kubernetes Engine aus, der normalerweise zum Erstellen von GKE verwendet wird ...
Schritt anzeigen
Öffnen oder aktualisieren Sie einen GitHub PR
Erstellen, bearbeiten oder kommentieren Sie eine GitHub-Pull-Anforderung
Schritt anzeigen
Freestyle-Schritt
Führen Sie einen beliebigen Befehl im Kontext eines Docker-Images aus
Schritt anzeigen
Führen Sie eine Docker Compose-Datei aus
Führen Sie eine docker-compose.yml-Komposition als Pipeline-Schritt aus
Schritt anzeigen
Bereitstellung in ECS
Stellen Sie Ihre App für AWS Elastic Container Service bereit
Schritt anzeigen
Führen Sie eine Codefresh-Pipeline aus
Führen Sie eine Codefresh-Pipeline nach ID oder Name aus und hängen Sie die erstellte ...
Schritt anzeigen
Kanarischer Einsatz für einfache K8
Führen Sie eine schrittweise kanarische Bereitstellung nur mit Kubernetes-Manifesten durch
Schritt anzeigen
Verwalten einer Bintray-Version
Verwalten Sie eine JFrong Bintray-Version
Schritt anzeigen
Führen Sie den Aqua Security Scan aus
Führen Sie einen Aqua-Container-Sicherheitsscan durch
Schritt anzeigen
Lassen Sie eine Helmkarte los
Stellen Sie einen serverlosen Dienst (Funktion und Ressourcen) für AWB Lambda bereit
Schritt anzeigen
Holen Sie sich Geheimnisse aus Hashicorp Vault
Lesen Sie die Geheimnisse von Hashicorp Vault in einer Codefresh-Pipeline
Schritt anzeigen
Führen Sie einen GKE-Befehl aus
Führen Sie einen Befehl in Google Kubernetes Engine aus, der normalerweise zum Erstellen von GKE verwendet wird ...
Schritt anzeigen
Öffnen oder aktualisieren Sie einen GitHub PR
Erstellen, bearbeiten oder kommentieren Sie eine GitHub-Pull-Anforderung
Schritt anzeigen
Freestyle-Schritt
Führen Sie einen beliebigen Befehl im Kontext eines Docker-Images aus
Schritt anzeigen
Führen Sie eine Docker Compose-Datei aus
Führen Sie eine docker-compose.yml-Komposition als Pipeline-Schritt aus
Schritt anzeigen
Bereitstellung in ECS
Stellen Sie Ihre App für AWS Elastic Container Service bereit
Schritt anzeigen
Führen Sie eine Codefresh-Pipeline aus
Führen Sie eine Codefresh-Pipeline nach ID oder Name aus und hängen Sie die erstellte ...
Schritt anzeigen
Kanarischer Einsatz für einfache K8
Führen Sie eine schrittweise kanarische Bereitstellung nur mit Kubernetes-Manifesten durch
Schritt anzeigen
Verwalten einer Bintray-Version
Verwalten Sie eine JFrong Bintray-Version
Schritt anzeigen
Führen Sie den Aqua Security Scan aus
Führen Sie einen Aqua-Container-Sicherheitsscan durch
Schritt anzeigen
Lassen Sie eine Helmkarte los
Stellen Sie einen serverlosen Dienst (Funktion und Ressourcen) für AWB Lambda bereit
Schritt anzeigen
Rufen Sie einen benutzerdefinierten Webhook auf
Benachrichtigen Sie eine Webhook-URL mit einem benutzerdefinierten Anforderungshauptteil
Schritt anzeigen
Auf Bestätigung warten
Halten Sie einen laufenden Build an, bis er genehmigt oder abgelehnt wird
Schritt anzeigen
Führen Sie einen Twistlock-Sicherheitsscan durch
Scannen Sie ein Docker-Image mit dem Twistlock-Sicherheitsdienst
Schritt anzeigen
Senden Sie per Twilio an SMS
Senden Sie eine SMS mit Twilio
Schritt anzeigen
Senden Sie eine Slack-Nachricht
Senden Sie eine Nachricht an einen Slack-Benutzer oder -Kanal
Schritt anzeigen
Führen Sie SCP aus
Übertragen, kopieren oder laden Sie Dateien mit dem Secure Copy Protocol hoch
Schritt anzeigen
Schieben Sie ein Bild
Schieben Sie ein Docker-Image in eine Registrierung
Schritt anzeigen
Veröffentlichen Sie ein NPM-Paket
Veröffentlichen Sie ein NPM-Paket in der NPM-Registrierung
Schritt anzeigen
Bereitstellung bei AWS Lambda
Stellen Sie einen serverlosen Dienst (Funktionen und Ressourcen) für AWS Lambda bereit
Schritt anzeigen
Lassen Sie eine Helmkarte los
Aktualisieren oder installieren Sie eine Helmkarte
Schritt anzeigen
Erstellen Sie ein Docker-Image
Erstellen Sie eine Docker-Datei und übertragen Sie sie in die interne Codefresh-Registrierung
Schritt anzeigen
Rufen Sie einen benutzerdefinierten Webhook auf
Benachrichtigen Sie eine Webhook-URL mit einem benutzerdefinierten Anforderungshauptteil
Schritt anzeigen
Auf Bestätigung warten
Halten Sie einen laufenden Build an, bis er genehmigt oder abgelehnt wird
Schritt anzeigen
Führen Sie einen Twistlock-Sicherheitsscan durch
Scannen Sie ein Docker-Image mit dem Twistlock-Sicherheitsdienst
Schritt anzeigen
Senden Sie per Twilio an SMS
Senden Sie eine SMS mit Twilio
Schritt anzeigen
Senden Sie eine Slack-Nachricht
Senden Sie eine Nachricht an einen Slack-Benutzer oder -Kanal
Schritt anzeigen
Führen Sie SCP aus
Übertragen, kopieren oder laden Sie Dateien mit dem Secure Copy Protocol hoch
Schritt anzeigen
Schieben Sie ein Bild
Schieben Sie ein Docker-Image in eine Registrierung
Schritt anzeigen
Veröffentlichen Sie ein NPM-Paket
Veröffentlichen Sie ein NPM-Paket in der NPM-Registrierung
Schritt anzeigen
Bereitstellung bei AWS Lambda
Stellen Sie einen serverlosen Dienst (Funktionen und Ressourcen) für AWS Lambda bereit
Schritt anzeigen
Lassen Sie eine Helmkarte los
Aktualisieren oder installieren Sie eine Helmkarte
Schritt anzeigen
Erstellen Sie ein Docker-Image
Erstellen Sie eine Docker-Datei und übertragen Sie sie in die interne Codefresh-Registrierung
Schritt anzeigen
Siehe Beispiel-Pipelines
Tiefe Kubernetes-Integration
Überwachen Sie Ihre Cluster. Führen Sie eine kanarische Freilassung durch. Verfolgen Sie ein laufendes Image bis zu einem einzelnen Commit. Es ist eine vollständige Integration mit einem Klick in alle Ihre Kubernetes-Umgebungen. Und es ist ein Game Changer.
Funktioniert in der Cloud oder hinter der Firewall
Verwenden Sie blau / grüne, kanarische, rollende oder benutzerdefinierte Bereitstellungsstrategien
Erfahren Sie mehr über die Integration von Kubernetes
Zeigen Sie den Status Ihrer Umgebung an einem Ort an
Wenn etwas schief geht, ist die Sichtbarkeit der Schlüssel. Mit Codefresh können Sie auf einfache Weise den Status aller Ihrer Kubernetes-Dienste, -Bereitstellungen und -Pods auf einem Bildschirm anzeigen, zusammen mit den neuesten Builds und Status.
Überwachen Sie alle Ihre Bereitstellungen und Umgebungen an einem Ort
Zeigen Sie die letzten Build-Protokolle oder Fehler mit einem Klick an
Die Macht von Codefresh, auf unserer oder Ihrer Infra
PIPELINES LAUFEN
In der Wolke
Führen Sie Pipelines auf den ultraschnellen SSD-basierten Computern von Codefresh aus und sorgen Sie sich nie wieder um die Wartung von Build-Servern.
PIPELINES LAUFEN
Auf Ihrer Infrastruktur
1 note
·
View note