#html copy protection software
Explore tagged Tumblr posts
Text
Dear Web Encryptor : Protect both Content and Source Code of HTML, HTML5, BootStrap website
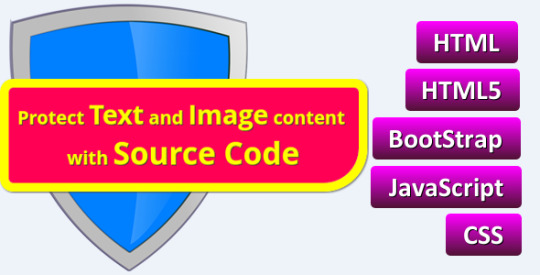
https://codecanyon.net/item/dear-web-encryptor-protect-the-source-code-of-html-html5-bootstrap-website/19555597
Every day, several website owners become victims of people who steal Text Content, Image Content and HTML, HTML5, BootStrap codes. If you do not protect your Text Content, Image Content and Source Code, you could even allow your entire site to be cloned by such people, in minutes, even without any credit or profit to you. Using this software is the only way to protect your HTML, HTML5, BootStrap websites from being stolen.
#copy protection html#dear web encryptor#disable copy and paste html#disable copy web page#disable image download html#disable right click and selection html#dreamweaver#encrypt html5#html copy protection software#html encryption software#html image copy protection#html text copy protection#html5 copy protection#html5 encryption#prevent image download
0 notes
Text
How to Build a Fast, Secure, and Scalable Website
In today’s digital age, having a website that is fast, secure, and scalable is essential for businesses and developers alike. Whether you are building a personal blog, an e-commerce platform, or an enterprise-level application, ensuring optimal performance, security, and scalability should be a priority. A well-optimized website enhances user experience, improves search engine rankings, and ensures seamless operation even during traffic surges. In this blog, we’ll explore best practices to help you build a website that meets these critical criteria and supports business growth effectively.
1. Optimize for Speed
Website speed plays a crucial role in user experience and search engine rankings. Here are some key strategies to enhance website performance:
Use a Fast Hosting Provider
Choosing the right hosting provider can significantly impact your website's speed and reliability. Opt for a service that offers high-speed performance, such as cloud hosting or dedicated servers. Popular hosting providers like AWS, Google Cloud, and DigitalOcean offer scalable and high-performance solutions tailored to different business needs.
Leverage Content Delivery Networks (CDNs)
CDNs store copies of your website’s static assets across multiple global servers, reducing latency and load times for users in different locations. Using a CDN ensures your website loads quickly, even for visitors accessing it from distant geographic locations.
Optimize Images and Media Files
Large image files can slow down your website significantly. Use tools like TinyPNG or WebP format to compress images without sacrificing quality. Additionally, consider using responsive image formats that adjust dynamically based on device resolution and screen size.
Minify CSS, JavaScript, and HTML
Reducing the size of your code by minifying CSS, JS, and HTML files can significantly improve loading times. Tools like UglifyJS, CSSNano, and HTMLMinifier can help streamline your code while maintaining its functionality.
Implement Lazy Loading
Lazy loading ensures that images, videos, and other heavy resources load only when needed, improving initial page load speed. This technique reduces the amount of data that needs to be loaded immediately when a user lands on your page.
Use Browser Caching
By enabling caching, browsers can store copies of static resources, reducing the need to reload them each time a user visits the website. This helps in significantly improving return visits and reducing server load.
2. Enhance Security Measures
With cyber threats on the rise, securing your website is non-negotiable. Here’s how to protect your site effectively:
Use HTTPS and SSL Certificates
Securing your website with HTTPS by installing an SSL certificate encrypts data between users and your site, preventing cyber-attacks like man-in-the-middle attacks and data breaches.
Regularly Update Software and Plugins
Keep your CMS, themes, and plugins updated to prevent vulnerabilities that hackers may exploit. Outdated software is one of the primary security risks leading to data theft and unauthorized access.
Implement Web Application Firewall (WAF)
A WAF helps filter and monitor HTTP traffic between a web application and the Internet, blocking malicious attacks. It acts as a shield against threats such as SQL injection and cross-site scripting (XSS).
Enable Two-Factor Authentication (2FA)
Adding an extra layer of security, such as 2FA, ensures that only authorized users gain access to sensitive areas of your website. This significantly reduces the risk of unauthorized access due to password breaches.
Perform Regular Security Audits
Use tools like Sucuri or Qualys to conduct regular security scans and identify potential vulnerabilities before hackers do. Conducting periodic penetration testing also helps in strengthening website security.
Implement Secure Authentication and Data Encryption
Use strong passwords, encrypt stored data, and implement security headers to protect against threats like cross-site scripting (XSS) and SQL injection attacks. Keeping security policies updated helps in mitigating emerging cybersecurity risks.
3. Ensure Scalability
Scalability is essential to handle traffic spikes without compromising performance. Here’s how to design a scalable website:
Adopt a Microservices Architecture
Instead of a monolithic structure, use a microservices-based approach where different parts of the application can scale independently. This allows for easier updates and better fault isolation.
Use Load Balancing
Distribute traffic efficiently across multiple servers to prevent overload and downtime. Load balancers like Nginx or AWS Elastic Load Balancing can help maintain high availability even during peak traffic periods.
Leverage Cloud Infrastructure
Cloud platforms like AWS, Google Cloud, and Azure offer auto-scaling features that adjust resources based on traffic demands. This ensures that your website remains responsive even during unexpected traffic surges.
Optimize Database Performance
Use indexing, query optimization, and caching techniques (e.g., Redis or Memcached) to improve database efficiency and handle high loads. A well-optimized database enhances website performance and response time.
Use Asynchronous Processing
For tasks that do not require immediate execution, implement asynchronous processing using message queues (e.g., RabbitMQ, Apache Kafka) to enhance performance. This allows the website to handle multiple processes efficiently without performance lags.
Monitor and Scale Automatically
Set up monitoring tools like New Relic, Google Analytics, or AWS CloudWatch to track performance metrics and automate scaling decisions. Proactive monitoring helps in identifying performance bottlenecks and making necessary optimizations.
Conclusion
Building a fast, secure, and scalable website requires a strategic approach that balances performance optimization, security best practices, and scalable architecture. By implementing these techniques, you can create a website that provides a seamless experience for users while ensuring security and reliability as your business grows.
Need help with website development? At Chirpin, we specialize in building high-performance, secure, and scalable websites. As a digital marketing agency in Delhi, we also provide digital marketing services in Delhi NCR to help businesses enhance their online presence. Whether you are looking for the best digital marketing company in Delhi or need professional digital marketing services in Delhi NCR, Chirpin has you covered. Our expert team works with businesses of all sizes, helping them establish a strong online presence and drive more leads. If you are looking for the best digital marketing company in Delhi NCR that offers comprehensive web development and marketing solutions, contact us today to bring your digital vision to life!
exhibition stand builders in dubai exhibition stand contractors in dubai exhibition contractors in dubai exhibition stand builders dubai dubai exhibition stand contractor exhibition stand designers in dubai best exhibition stand contractor in dubai best exhibition stand builders dubai exhibition stand design company in dubai exhibition stand design dubai dubai exhibition stands exhibition company in dubai exhibition companies in dubai exhibition stand builder abu dhabi exhibition stand contractor in abu dhabi exhibition stand contractors abu dhabi exhibition stand companies in abu dhabi exhibition stand design company abu dhabi exhibition stand in abu dhabi
0 notes
Text
NGINX Server & Custom Load Balancer: A Comprehensive Guide

The NGINX Server is an industry-leading open-source software for web serving, reverse proxying, caching, load balancing, media streaming, and more. Initially developed as a web server, NGINX has grown to become a versatile tool for handling some of the most complex load balancing needs in modern web infrastructure. This guide covers the ins and outs of setting up and using NGINX as a Custom Load Balancer, tailored for businesses and developers who need robust and scalable solutions.
What is NGINX?
NGINX is a high-performance HTTP and reverse proxy server that is optimized for handling multiple concurrent connections. Unlike traditional web servers, NGINX employs an event-driven architecture that makes it resource-efficient and capable of handling massive traffic without performance degradation.
Key Features of NGINX:
Static Content Serving: Quick delivery of static files, such as HTML, images, and JavaScript.
Reverse Proxy: Routes client requests to multiple servers.
Load Balancing: Distributes traffic across several servers.
Security: Built-in protections like request filtering, rate limiting, and DDoS prevention.
Why Use NGINX for Load Balancing?
Load balancing is essential for managing heavy web traffic by distributing requests across multiple servers. NGINX Load Balancer capabilities provide:
Increased availability and reliability by distributing traffic load.
Improved scalability by adding more servers seamlessly.
Enhanced fault tolerance with automatic failover options.
Incorporating NGINX as a Load Balancer allows businesses to accommodate spikes in traffic while reducing the risk of a single point of failure. It is an ideal choice for enterprise-grade applications and is widely used by companies like Airbnb, Netflix, and GitHub.
Types of Load Balancing with NGINX
NGINX supports different load balancing methods to suit various requirements:
Round Robin Load Balancing: The simplest form, Round Robin, distributes requests in a cyclic manner. Each request goes to the next server in line, ensuring an even distribution of traffic.
Least Connections Load Balancing: With Least Connections, NGINX routes traffic to the server with the fewest active connections. This method is useful when there’s a significant disparity in server capacity.
IP Hash Load Balancing: This approach directs clients with the same IP address to the same server. IP Hash is commonly used in scenarios where sessions are sticky and users need to interact with the same server.
Custom Load Balancer: NGINX also allows for custom configuration, where administrators can define load balancing algorithms tailored to specific needs, including failover strategies and request weighting.
Setting Up NGINX as a Custom Load Balancer
Let’s walk through a step-by-step configuration of NGINX as a Custom Load Balancer.
Prerequisites
A basic understanding of NGINX configuration.
Multiple backend servers to distribute the traffic.
NGINX installed on the load balancer server.
Step 1: Install NGINX
First, ensure that NGINX is installed. For Ubuntu/Debian, use the following command:
bash
Copy code
sudo apt update
sudo apt install nginx
Step 2: Configure Backend Servers
Define the backend servers in your NGINX configuration file. These servers will receive traffic from the load balancer.
nginx
Copy code
upstream backend_servers {
server backend1.example.com;
server backend2.example.com;
server backend3.example.com;
}
Step 3: Configure Load Balancing Algorithm
You can modify the load balancing algorithm based on your requirements. Here’s an example of setting up a Least Connections method:
nginx
Copy code
upstream backend_servers {
least_conn;
server backend1.example.com;
server backend2.example.com;
server backend3.example.com;
}
Step 4: Setting Up Failover
Add failover configurations to ensure requests are automatically rerouted if a server becomes unresponsive.
nginx
Copy code
upstream backend_servers {
server backend1.example.com max_fails=3 fail_timeout=30s;
server backend2.example.com max_fails=3 fail_timeout=30s;
}
Step 5: Test and Reload NGINX
After making changes, test your configuration for syntax errors and reload NGINX:
bash
Copy code
sudo nginx -t
sudo systemctl reload nginx
Benefits of Using NGINX for Custom Load Balancing
Scalability: Effortlessly scale applications by adding more backend servers.
Improved Performance: Distribute traffic efficiently to ensure high availability.
Security: Provides additional layers of security, helping to protect against DDoS attacks and other threats.
Customization: The flexibility of NGINX configuration allows you to tailor the load balancing to specific application needs.
Advanced NGINX Load Balancing Strategies
For highly dynamic applications or those with specialized traffic patterns, consider these advanced strategies:
Dynamic Load Balancing: Uses health checks to adjust the traffic based on server responsiveness.
SSL Termination: NGINX can handle SSL offloading, reducing the load on backend servers.
Caching: By enabling caching on NGINX, you reduce backend load and improve response times for repetitive requests.
Comparison of NGINX with Other Load Balancers
Feature
NGINX
HAProxy
Apache Traffic Server
Performance
High
Very High
Moderate
SSL Termination
Supported
Supported
Limited
Customization
Extensive
High
Moderate
Ease of Setup
Moderate
Moderate
High
NGINX remains the preferred choice due to its flexibility, robust features, and ease of use for both small and large enterprises.
Real-World Applications of NGINX Load Balancing
Companies across industries leverage NGINX Load Balancer for:
E-commerce Sites: Distributes traffic to ensure high performance during peak shopping seasons.
Streaming Services: Helps manage bandwidth to provide uninterrupted video streaming.
Financial Services: Enables reliable traffic distribution, crucial for transaction-heavy applications.
Conclusion
Setting up NGINX as a Custom Load Balancer offers significant benefits, including high availability, robust scalability, and enhanced security. By leveraging NGINX’s load balancing capabilities, organizations can maintain optimal performance and ensure a smooth experience for users, even during peak demand.
0 notes
Text
With continuous evolution in information technology, it has become easy for the government or any authority to ban or censor a website or content, in order to regulate the internet in their country. Subsequently, it will violate the freedom to access information rights of the citizens. If you are annoyed or feel stifled due to banned or blocked websites in your school, office or country, here are some ways with which you can access blocked website and get all the content you were searching for. Use VPN The first way to circumvent the ban is to use VPN or Virtual Private Network. Described as a tunnel that protects your information such as websites you access and thereafter converts your internet traces to a value impossible to detect or recognize. According to this source, VPN provides you reliable medium to surf to your heart’s content. To enjoy an uninterrupted web experience, you just need to sign up with many free or cheap VPN available online. All you need to do is to visit these websites, check their features and make the best choice. Use Anonymous Proxy Website If you do not want to use VPN, you can use various proxy websites available online with which you can get an unrestricted web experience. This is mainly due to the fact that a proxy website retains an ability to hide the blocked website from your local service provider and enables you to access the banned website from your computer. By logging from a proxy website, you do not need any other extra facility or need to make any technical change in the software of your computer. Use Google Translate/Bing Translation Tool The next way is to use educational tools such as Google Translate/Bing Translation Tool to circumvent the filters. This is predominantly because they are not banned by many countries and institutes as nobody considers them powerful enough to unblock the banned sites. With the assistance of these tools, you can convert these sites into any other language and bypass the regulations. When compared to other methods to access the banned site, it is a very straightforward way. The URL of this link is as follows https://translate.google.com/translate?sl=auto&tl=hi&u=http%3A%2F%2Fwww.fromdev.com Use Internet Archive – Wayback Machine The next way to access the blocked websites in your country or region is to use the internet archive through Wayback Machine. This machine can be described as an interesting service as it saves older copies of most of the websites available, some of which are presently unavailable online. As part of its service, the organization saves different versions of the same website and enables you to access the old version of any required website. Further, you can also use this medium to access the banned websites. Use TOR Browser If you do not want to use complicated methods to access a banned website, there is an easy way to accomplish your purpose. All you need to do is to download TOR Browser and you are set to access the banned content as well as blocked website while working on any network. In addition, you can work as an anonymous user. Use HTML To PDF Converter And Browse Site Offline If you want to download something from the banned website and do not want to remain there for a long time, all you need to do is to use a ‘HTML to PDF’ converter tools available online. The first step in this process is to convert the required webpage to a PDF file and use the page that is available in PDF format. You can use various online tools listed in this page. Change Network Proxy In Browser Settings If you want to access a blocked website by using a good working proxy of any other country in any network, all you need to do is to make changes in the Advanced Browser settings of your browser and then visit the site. After you are done, you can revert to the default Advanced Browser settings. There are numerous times when you need to access a blocked website or a banned website both for business and pleasure. Further, there are also various times you want to work as an anonymous user, due to privacy or data theft concerns.
At such times, you can use various methods outlined above and accomplish your purpose.
0 notes
Text
VeryUtils Excel Converter Command Line can Convert Excel files via command line
VeryUtils Excel Converter Command Line can Convert Excel files via command line. In today's data-driven world, efficiently managing and converting spreadsheet files across various formats is crucial for businesses and individuals alike. VeryUtils Excel Converter Command Line is an all-encompassing tool designed to handle this challenge with ease, offering robust functionality, speed, and a wide range of supported formats. Whether you need to convert Excel spreadsheets, CSV files, or OpenOffice documents, this powerful software ensures seamless and accurate conversions without the need for Microsoft Excel.

Comprehensive Format Support VeryUtils Excel Converter Command Line is equipped to convert an extensive list of input formats including Excel (XLS, XLSX, XLSM, XLT, XLTM), OpenOffice (ODS), XML, SQL, WK2, WKS, WAB, DBF, TEX, and DIF. This versatility means you no longer need multiple converters for different file types. The output formats are equally impressive, ranging from DOC, DOCX, PDF, HTML, and TXT to ODT, ODS, XML, SQL, CSV, Lotus, DBF, TEX, DIFF, SYLK, and LaTeX.
Key Features and Benefits Wide Range of Conversions
Excel to Multiple Formats: Convert Excel spreadsheets to PDF, HTML, TXT, DOC, and more.
CSV Conversion: Batch convert CSV files to DOC, PDF, HTML, TXT, XLS, DBF, and XML.
OpenOffice Compatibility: Easily convert ODS files to Microsoft XLS documents, ensuring compatibility across different software.
Preserves Document Layout VeryUtils Excel Converter Command Line strictly maintains the layout of the original document, delivering an exact copy in the new format. This ensures that all tables, charts, and formatting remain intact after conversion.
Customization Options The software includes a range of customization options:
Sheet Conversion: Convert each sheet into a separate file.
PDF User Permissions: Set permissions to protect PDF files from being modified or copied.
CSV to TXT: Choose encoding options during batch conversion.
Header and Column Formatting: Make headers bold and autofit columns when exporting CSV to XLS.
Performance and Efficiency
Fast Batch Conversion: Convert large volumes of files quickly with minimal effort.
Command Line Automation: Automate conversions using command line or COM/ActiveX interfaces, enhancing workflow efficiency.
File Management: Move or delete files after processing, skip already processed files, and specify sheets or ranges to convert.
Secure and Protected PDFs When converting Excel to PDF, you can set user permissions, password-protect files, and even sign documents with a digital signature. The software supports PDF, PDF/A, and non-searchable PDFs upon request.
Easy Integration and Usage VeryUtils Excel Converter Command Line is designed for ease of use and integration:
No GUI: The command line interface allows for seamless integration into other applications and automation scripts.
Developer License: With a Developer or Redistribution License, you can integrate this software into your own products and distribute it royalty-free.
Command Line Examples Here are some examples of how you can use the VeryUtils Excel Converter Command Line: ConvertExcel.exe --export-options "separator=; format=raw" sample.xlsx _out_sample-xlsx2txt.txt ConvertExcel.exe sample.xlsx _out_sample-xlsx2csv.csv ConvertExcel.exe sample.xlsx _out_sample-xlsx2xls.xls ConvertExcel.exe sample.xlsx _out_sample-xlsx2pdf.pdf ConvertExcel.exe _out_sample.csv _out_sample-csv2xls.xls ConvertExcel.exe _out_sample.csv _out_sample-csv2xlsx.xlsx ConvertExcel.exe sample.xlsx _out_sample-xlsx2html.html ConvertExcel.exe sample.xlsx _out_sample-xlsx2ods.ods ConvertExcel.exe --merge-to=_out_merged.xls _out_sample-xlsx2csv.csv sample.xlsx _out_sample-xlsx2xls.xls ConvertExcel.exe --export-options "paper=iso_a2_420x594mm" sample.xlsx _out_sample-xlsx2pdf-paper-size.pdf ConvertExcel.exe --export-file-per-sheet _out_merged.xls _out_files-per-sheet-%n-%s.csv
Conclusion VeryUtils Excel Converter Command Line stands out as a comprehensive and efficient solution for all your spreadsheet conversion needs. With its extensive format support, robust performance, and user-friendly command line interface, it simplifies the process of managing and converting spreadsheet files. Whether you're a business looking to streamline data processing or an individual needing reliable file conversions, VeryUtils Excel Converter Command Line is the perfect tool for the job. Download it today and experience the convenience of having all your spreadsheet conversions handled by one powerful tool.
0 notes
Text
Navigating the Digital Jungle: A Guide to IT Jargon

Information Technology (IT) is filled with complex terms and acronyms that can sometimes feel like a different language. To help you navigate the digital world, we’ve put together a guide with clear and concise definitions for commonly used IT terms.
Common IT Terms:
Cloud Computing: The use of remote servers hosted on the internet to store, manage, and process data instead of using a local server or personal computer.
SaaS (Software as a Service): A software distribution model where a service provider hosts applications and makes them available to customers over the internet.
IoT (Internet of Things): The network of physical objects embedded with sensors, software, and other technologies that can connect and exchange data with other devices and systems over the internet.
VPN (Virtual Private Network): A tool that provides a secure connection to another network over the internet, ensuring privacy and security by hiding the user’s IP address and encrypting data transfers.
Firewall: A security system that monitors and controls network traffic based on predefined security rules, acting as a barrier between trusted and untrusted networks.
Malware: Malicious software designed to harm users, systems, or networks. Examples include viruses, ransomware, and spyware.
Data Encryption: The process of converting data into a code to prevent unauthorized access and protect sensitive information.
API (Application Programming Interface): A set of rules and protocols that allow different software applications to communicate and interact with each other.
Bandwidth: The maximum data transfer rate of a network or internet connection, typically measured in bits per second (bps).
Backup: A copy of computer data taken and stored elsewhere to be used for restoring the original data after a loss event.
Decoding IT Acronyms:
ISP (Internet Service Provider): A company that provides access to the internet for individuals and organizations.
URL (Uniform Resource Locator): The web address that specifies the location of a resource on the internet.
HTML (HyperText Markup Language): The standard language used for creating web pages and structuring their content.
HTTP (Hypertext Transfer Protocol): The protocol used for transmitting hypertext requests and responses between web servers and web browsers.
IP (Internet Protocol): The set of rules that govern how data is sent and received over the internet between different devices.
CPU (Central Processing Unit): The main component of a computer responsible for executing instructions and performing calculations.
With this guide, you now have a better understanding of the key terms and acronyms used in the IT world. If you’re ready to put your knowledge to work or need assistance navigating the digital landscape, visit us at www.infradapt.com or give us a call at 484-546-2000. We’re here to help you harness the full potential of your IT resources and navigate the complexities of the digital world.
https://www.infradapt.com/news/navigating-the-digital-jungle-a-guide-to-it-jargon/
0 notes
Text
This day in history

#20yrsago DRM is philosophically broken, too https://www.wired.com/2003/06/copy-protection-is-a-crime/
#20yrsago New PageRank optimization may pave way for idiosyncratic Google https://www.eurekalert.org/news-releases/704975
#15yrsago Security guards threaten NPR photogs with arrest for shooting panorama of DC’s Union Station https://web.archive.org/web/20080517104116/http://www.andycarvin.com/archives/2008/05/almost_arrested_for_taking_photos_at_uni.html
#15yrsago Warner/DC comics shuts down children’s cancer charity auction over trademark https://web.archive.org/web/20080517045311/https://sayitbackwards.blogspot.com/2008/05/important-charity-auction-update.html
#15yrsago Grateful Dead shake down NPR over including a song in an online mix https://www.npr.org/sections/monitormix/2008/05/days_be_more_than_all_we_have_2.html/
#15yrsago Analog switchoff == DRM screwjob https://tidbits.com/2008/05/12/digital-rights-misery-when-technology-is-designed-to-fail/
#15yrsago US and EU commissioner trying (again!) to sneak software patents into Europe https://web.archive.org/web/20080514074905/http://press.ffii.org/Press_releases/McCreevy_wants_to_legalise_Software_Patents_via_a_US-EU_patent_treaty
#15yrsago London supermarket secretly photographs alcohol/cigarette buyers, wants national database https://www.dailymail.co.uk/news/article-566181/Hi-tech-face-recognition-cameras-used-Budgens-spot-underage-drinkers.html
#10yrsago Inside the world of “booters” — cheesy DoS-for-hire sites https://krebsonsecurity.com/2013/05/ddos-services-advertise-openly-take-paypal/
#10yrsago “Citation needed”‘s Wikipedia entry https://en.wikipedia.org/wiki/Citation_needed
#10yrsago Scientology sucks at photoshop https://tonyortega.org/2013/05/12/scientology-sunday-funnies-portland-is-now-cleared-on-to-the-rest-of-earth/
#10yrsago How Anonymous got involved in fighting for justice for rape victims https://www.motherjones.com/politics/2013/05/anonymous-rape-steubenville-rehtaeh-parsons-oprollredroll-opjustice4rehtaeh/
#10yrsago 3D printed guns and the law: will judges be able to think clearly about digital files when guns are involved? https://www.theguardian.com/technology/2013/may/13/3d-printed-guns
#5yrsago White woman calls cops on black family who barbecued in Oakland Park’s barbecue area https://panthertimes.com/2018/05/02/white-privilege-used-to-fight-racially-charged-harassment-at-lake-merritt/
#5yrsago 75% of Theresa May’s £50m gift to grammar schools will go to Tory districts https://www.mirror.co.uk/news/politics/it-looks-like-shameless-bribe-12520491

Catch me on tour with Red Team Blues in Toronto, DC, Gaithersburg, Oxford, Hay, Manchester, Nottingham, London, and Berlin!

6 notes
·
View notes
Text

I posted 3,647 times in 2021
15 posts created (0%)
3632 posts reblogged (100%)
For every post I created, I reblogged 242.1 posts.
I added 93 tags in 2021
#on a steel horse i write - 20 posts
#mine - 14 posts
#boost - 13 posts
#writing - 8 posts
#piracy - 8 posts
#capitalism - 7 posts
#writing advice - 7 posts
#photoshop - 7 posts
#writing reference - 5 posts
#scifi - 4 posts
Longest Tag: 139 characters
#i understand you're waiting for la revolucion to come. well when it does send me a tweet about it. in the meantime i'll just be here actual
My Top Posts in 2021
#5
Do you have a cracked file link for Adobe softwares? Or do you know any? Thanks!
Hell yeah I do.
Here's the deal: I think Tumblr's still blocking posts with external links from search results, and if I'm going to write a how-to, I want people to be able to find it. So I'm actually going to link you to a new post I just wrote. If you find this helpful, please reblog both of these.
HERE'S MY POST ON DOWNLOADING ADOBE CC FREE.
(If that link breaks for some reason, it's just my tumblr + "/post/655796038047825920/")
Happy pirating!
155 notes • Posted 2021-07-04 16:26:03 GMT
#4
Sapkowski's Witcher books: humans are violent, paranoid xenophobes who readily scapegoat and massacre anyone they deem "nonhuman" enough, including the witchers they had established to protect them
Netflix's Nightmare of the Wolf: actually the witchers are a cabal of money-grubbing, child-murdering evildoers who use unnatural black magic to create monsters and fabricate the conflicts that line their own pockets. Tetra was objectively justified in exterminating the witchers of Kaer Morhen. There is definitely nothing troubling about this characterization
243 notes • Posted 2021-08-29 18:24:43 GMT
#3
PIRATING ADOBE CC MASTERPOST
I was about to make this one of those posts that say, "Hey everyone, WATCH OUT, there's some ILLEGAL PIRATED Adobe software that you should definitely AVOID. Here's the link so you know what to look out for, because you wouldn't want to get stuff FREE by MISTAKE"... and then I realized, if Adobe actually wanted to come after me for copyright shit (which they don't), their lawyers don't fucking care if I did it with a coy wink and a nudge.
So fuck em.
Fucking steal that shit. It's a moral imperative.
(And if you don't want to for personal reasons, or because you're a business and they will come after you, you can get Adobe CS2 free legally, or any of these decent free alternatives.)
But if you want the real CC, read on!
The crack:
god I sound like a drug dealer now
I use the 2019 CC cracks made by Zer0Cod3, who was taken down almost immediately after, but this mirror site still works as of July 2021: https://cgpersia.com/2019/01/adobe-2019-cc-collection-win-x64-148263.html
You have to download it using one of the options at the bottom of the site (I used RapidGator) and it's a pain in the ass but still ultimately safer than trying to find a torrent (send me an ask about that if you want another masterpost).
How to use:
Once the files download, PUT YOUR COMPUTER IN AIRPLANE MODE
Make a System Restore Point just in case anything goes wrong and you want to roll it all back.
Install the programs you want. They may ask for you to sign in or put in a key. Just click the "do it later" option and close out of the program as fast as you can. Ideally, try to install the programs without letting them launch at all.
Copy the crack file (the one with its name listed on the website) and REPLACE the original file of the same name. You don't actually have to use the patch tool.
If you're confused, let's do Photoshop as an example. So you've run the installer, and you now have Photoshop installed. Go to its Program Folder (on Windows it's usually "C:\Program Files\Adobe\Adobe Photoshop CC 2019\" but if you're ever unsure, you can install Everything Search then just search your whole computer for "photoshop.exe"). Delete the original photoshop.exe, and put the photoshop.exe that you downloaded in the exact same place.
DON'T OPEN IT YET. We need to block Adobe from verifying/updating these programs...
If you have any other genuine Adobe programs (e.g. Acrobat DC) make sure you've signed out of your Adobe account.
Block all these apps in your firewall (You can look up how to do that for your specific device). Also, if you're on Windows, you can open "C:\Windows\System32\drivers\etc\hosts" in a text editor and add the follow:
0.0.0.0 lmlicenses.wip4.adobe.com
0.0.0.0 lm.licenses.adobe.com
0.0.0.0 na1r.services.adobe.com
0.0.0.0 hlrcv.stage.adobe.com
0.0.0.0 practivate.adobe.com
0.0.0.0 activate.adobe.com
(Here's instructions to do the same on Mac)
Next (on Windows), open Services.msc and set the following to Startup Type - Disabled:
Adobe Genuine Software Monitor
Adobe Genuine Software Integrity Service
AdobeUpdateService
See the full post
258 notes • Posted 2021-07-04 16:23:58 GMT
#2
Good evening! I would like to learn more about torrenting if you have the time.
Hi g3nesis, this is so polite! And anon, I'm sorry that happened, Cloudflare Warp is not a safe and anonymous VPN.
Let's talk about Torrenting!
So let's start with the basic requirements. What is a VPN?
A virtual private network is a secure encrypted tunnel you make to someone else's computer, and that's what actually accesses the public internet, so it looks like all your traffic is coming from that computer. The obvious downside here is that you have to trust whoever's running that computer to 1) Ensure a safe connection that doesn't leak your info, and 2) Not keep logs of who you are or what your traffic contained.
Usually that means a paid VPN service, because the general rule of the internet is that if you get a product for free, then you are the product. Paid VPN providers companies have more of an incentive not to keep logs, since they're already getting their money, but you still have to take their word for it.
The one big exception to the above rule is FOSS: Free, Open-Source Software. This means someone committed to the principles of transparency and community/cooperation has made their software free to use, and the code public to anyone who'd like to peruse it. FOSS generally isn't particularly profitable, unless they also offer some service, e.g. hosting servers. It's like saying, "You can read the code and run it yourself for free if you want to, but I'm already running it, I'm know how it works and I'm good at maintaining it, so I'll let you use my server for a small fee."
So let's talk about Windscribe.
Windscribe is my preferred VPN because much of their software is open-source, and they have a Freemium model. That means basic services are offered for free, while upgraded services (like unlimited monthly data) is a paid feature. While nothing is guaranteed, this model is generally pretty safe.
You can download it here: https://windscribe.com/yo/v40g2xlr
(Full disclosure: This is my refer-a-friend link. Free users get 10Gb/month of data, but with this link, you'll get 11Gb/mo instead! I also get an extra 1Gb/mo for every friend I refer. Consider it a free, easy way to tell me thanks if you found this post helpful!)
Now the fun stuff: How do I torrent?
First you need a torrenting client, AKA a program that can download torrent files. I recommend qBittorrent, which is a completely free and open-source program. It's lightweight and ad-free, and has versions for any operating system. Install your torrent client, install your VPN, start up both, and activate a VPN connection. Now you're ready to torrent!
How torrenting works:
Torrenting (aka "bittorrent") is a decentralized method of file-sharing. Basically, one person hosts a file (or multiple files) on a torrent client. That's called a seed - the complete file, available to be downloaded over the internet from their computer. While they have their client open and running, they are seeding the file. If they stop seeding or turn off their computer, that file will no longer be accessible over the internet, because it is not hosted permanently on any server.
They might post a link (called a magnet link) on a website like ThePirateBay so others can find it. If I want to download that file, I can click that magnet link, and it will tell my qBittorrent client how to start downloading the file in little bits and pieces of data. If the download gets interrupted before finishing, I'll still have those pieces of data, and I can always resume later. Downloading the file is called leeching.
Once I've downloaded (aka leeched) enough pieces of the file, qBittorrent can make it accessible to others. Now if you start downloading the file, you might download some pieces of data from the original person, and some from me. It's a way of decentralizing the burden of constantly uploading data. If I do this, I am called a peer. If I don't, I am called a leech, because I am downloading from the torrent without contributing to it. Don't be a leech!
Once I have fully downloaded the file, if I leave qBittorrent on, it continues sharing that file. Since I have the whole file, even if the original person stops seeding, others will still be able to download it - from me! I am now a seed.
And that's how torrenting works! One person starts sharing a file, and as more people download it and then share it themselves, it remains accessible long after the original host abandons it. This also means that if no one continues seeding a torrent, then it will be dead. Unaccessible. You won't be able to download it unless someone decides to start seeding it again.
There are many websites that host magnet links. You can search them to try to find whatever file you're hoping to download. They will list the Seed:Leech ratio. The more seeds there are, the easier/faster it will be to download. If there are zero seeds, the file cannot be downloaded.
❗❗❗ IMPORTANT ❗❗❗
Once you have finished downloading, you must seed the file. Yes, it's tough when your VPN has a monthly data limit. Seed it anyway. Seed it next month if you have to. In your torrent client, your "seed ratio" is how many times more data you've seeded vs the amount you've leeched. (AKA, if you downloaded a 1Gb file and you've seeded 800Mb, your seed ratio would be 0.8). Common courtesy is to continue seeding until your seed ratio is 5.0. This number depends on how many other peers are trying to download that file, though. So at minimum, you must seed for 1-2x as long as you leeched. (AKA if it took you 1 hour to download your file, continue seeding it for at least 2 hours after that).
Now, you might have heard torrents are full of viruses. In truth, anything off the internet could have malware. I recommend having a good antivirus program. Kaspersky Free is a good option. Make sure it's one where you can run a scan on an individual file; anytime you torrent something, scan it before opening it. For smaller files, you can upload it to VirusTotal.com to run it through a gauntlet of different antivirus scans simultaneously.
Last notes: Internet safety!
P.S. If you're like our dear anonymous asker, and you receive a notice from your ISP about pirating, don't panic! Unless you're seeding terabytes of movies, you're very unlikely to actually be sued. Your ISP isn't even likely to actually do anything. They may threaten to cancel your internet, but that's because they're required by law to notify you. Typically, they don't actually care. HOWEVER, don't be lazy or unsafe about it! Make sure you're following the above steps. For extra security, connect to a VPN server that's not based in your home country, and make sure you don't run out of your monthly data halfway through a torrent, or it will kick you back onto your regular internet connection. Always activate your VPN tunnel before opening your torrent client, just in case some torrents connect automatically (to avoid this, always Pause all torrents, even ones that are seeding, before closing your client!)
Also, torrents are generally safer if...
a) There are lots of seeds/peers
b) It hasn't been uploaded super recently
c) It has comments that look like they're from real people
See the full post
266 notes • Posted 2021-08-18 15:56:35 GMT
#1
Look, I support men having careers. I mean, I'm a working man myself! But there's some jobs we're just not cut out for. Let's face the facts: Every single major economic collapse happened under male leadership. Vietnam, Afghanistan... Every time America got into a failed war, a man was president. And we haven't even gotten into the literal tens of thousands of companies that male CEOs have driven to bankruptcy!
I mean, it's just biology. We don't have the right temperament. Men are way too emotional, chauvinistic, overly aggressive, and don't even get me started on the big red button! The only time a world leader got riled up enough to actually drop nukes, of course it was a man!
A good leader has to be nurturing, and in tune with her own emotions. The little gender experiment of the past few centuries has been fun, but enough is enough. We've clearly demonstrated our gender can't handle the pressure and responsibility. It's simply not our place.
Men, we need to come back to reality and stick to what we're good at: manual labor and rotating three-dimensional objects in our mind.
610 notes • Posted 2021-09-10 05:27:59 GMT
Get your Tumblr 2021 Year in Review →
5 notes
·
View notes
Text
Data Loss Protection - Anti Piracy Strategies

Anti-piracy software can be purchased by any publisher. It can protect PDF documents, SWF flash content, and HTML content. DRM - digital rights management systems are available to meet these requirements and provide the controls necessary to properly implement data loss prevention (DLP). The author can register customers using the licensing system, choose the right access level for each customer, and create messages to inform unauthorized users that they don't have permission to open protected files. They can also give details about where permission was obtained, set expiry dates, and show a link which confirms that the protected document has expired.
DRM document control software allows the author to implement a watermark feature that displays the user's name or company name as well as details about the date/time of usage on all printouts. We can also use PDF software to monitor antipiracy. It has the ability to show user and document statics, auditing, and reporting.
The DRM watermarking capability helps to pinpoint the source of the Onsist leakage. It provides information about the date and time the document was used. Authors are also equipped with document control capabilities to prevent unauthorized access. This useful anti-piracy measure prevents others from copying or altering your work. It also helps to avoid misinterpretation of the intended message. To prevent data loss, users must view the document with a proprietary program that is different than the one that created it. Only authorized users can see the document, and document processing tools are disabled.
Data loss prevention is about preventing the leakage of documents that are not under the control of the organization who owns them. This anti-piracy technique is about protecting and monitoring a document's contents and context through a filtering system and central management system. This document control method is designed to automatically recognize instances where content violates DRM rules and prevent documents from being copied or emailed to others, such as to a flash drive.
Organizations will often be required to share confidential information with overseas staff or lawyers. This makes anti-piracy solutions even more important. Data loss protection systems must be able to protect protected documents once they reach external, but authorized, parties in order to stop piracy. Although encryption has been the best solution to document control, it does not prevent unauthorized individuals from accessing protected information. It does not limit the rights of the authorized user to access the document after it has been decrypted. We can combine encryption and DRM controls to restrict the users' ability to share or transmit the restricted information.
2 notes
·
View notes
Text
Cara Aktivasi Nitro Pro 10

W10 Digital Activation adalah sebuah program aktivasi terbaru yang dapat anda gunakan untuk mengaktivasi Windows 10 anda secara permanen dengan cara. Disini kami membacikan Cara Aktivasi Permanen Windows 10 Pro Anniversary Update yang sudah teruji dapat mengaktifkan windows 10 versi Pro. Namun bagi anda yang.
Nitro Pro Full Version adalah aplikasi yang sangat penting untuk mengedit atau membuat files berformat PDF. Dengan menggunakan aplikasi ini, anda dapat membuat, mengedit dan mengubah file pdf. Aplikasi Nitro Pro Full dapat melakukan editing file pdf dengan sangat cepat dan akurat. Anda dapat menambahkan komentar apda file PDF yang ingin anda edit. Anda dapat mengubah segala jenis format populer dari office menjadi bentuk PDF.
Program Nitro Pro Full Version ini mendukung berbagai macam format file seperti : Word, Excel, PowerPoint®, Photoshop®, HTML, rich text, BMP, TIFF, GIF, JPEG, JPEG2000, PNG, dll. Setelah anda menginstal aplikasi ini ke komputer atau laptop anda, maka secara otomatis akan muncul toolbar khusus dari software Nitro Pro Full ini yang akan memudahkan anda untuk mengkonversi berbagai macam format file ke PDF atau sekedar membuat file PDF.
Features Of Nitro Pro Full Version


Creating and making PDF files of more than 300 file types other formats
Create PDF files with a single click
Edit video, text content of PDF files
Convert PDF files to files in Microsoft Word, WordPerfect, OpenOffice for reuse
Extract text and images in PDF files
Putting notes on PDF files
The combination of file documents, spreadsheets, presentations in the form of a PDF file
Protect PDF files and restrictions to read, edit, extract the contents and print
Password uses 40-bit and 128-bit encryption system
Construction form PDF files to import user information
Full list of up to a Mac impulsivity and make PDF files for easy search Index
Print professional-quality PDF files
Attach an audio file to a PDF file
Add Stamp
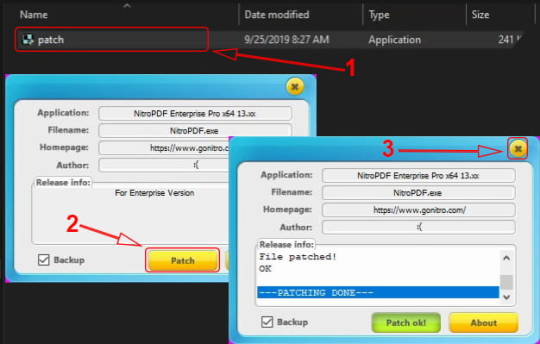
Cara Instal :
Download dan ekstrak file “Nitro Pro Full Version” ini.
Ekstrak juga file patch yang ada di dalam folder tersebut.
Matikan koneksi internet.
Instal programnya seperti biasa.
Setelah proses instalasi selesai, jangan dulu masuk ke dalam programya.
Buka folder “patch”, lalu copy pastekan file patch ke dalam folder instalasi nitro pro di pc atau laptop anda.
Jalankan file patch dengan cara klik kanan >> run as administrator.
Klik Patch.
Done.
Link Download
Mirrored
32 Bit : Nitro Pro Enterprise 13.44.0.896 Full Version (185 Mb)
32 Bit : Patch Only (232 kb)
64 Bit : Nitro Pro Enterprise 13.44.0.896 Full Version (221 Mb)
64 Bit : Patch Only (232 kb)
ZippyShare
32 Bit : Nitro Pro Enterprise 13.44.0.896 Full Version (185 Mb)
Cara Mengaktivasi Windows 10
32 Bit : Patch Only (232 kb)
64 Bit : Nitro Pro Enterprise 13.44.0.896 Full Version (221 Mb)
Cara Install Dan Aktivasi Nitro Pro 10
64 Bit : Patch Only (232 kb)
Cara Aktivasi Windows 10 Kuyhaa

1 note
·
View note
Text
DVD Cover Software

Free DVD covers that a child can make on its own, by manipulating DVD cover design templates and saving to a hard drive is the quickest and least expensive method to create DVD covers. There are other ways to create a DVD cover but they are more complicated and usually require the knowledge and expertise of a professional. However it is probably the least expensive way to create protective covers for the disc collection and still to systematise your choice of discs, regardless there are several CDs and DVDs that you have in your collection that you would like to protect from damage or scratches. So if you are not sure what method to use for your DVD collection then check out the free online DVD cover maker websites. They offer great value for money and do not require any experience of the computer at all.
If you are creating DVD covers on your own then you need to be aware that the DVD copy software that is used to do this is only available from a few websites. One of the best places to buy a DVD cover maker is on eBay. There are also other sites that are reliable but do not advertise on eBay because they do not sell DVD cover makers or any CD burners.
You may have noticed when looking on eBay for free dvd covers that there is always a catch. There is usually a small fee to use their DVD cover software which they will then include with the purchase. The fee may vary but it is well worth joining the eBay affiliate program because you will receive a much larger discount on your eBay sales this way.
So what kind of DVD covers will you be creating with your DVD software? There are tons of styles available with DVD software so it should not be too difficult to come up with some covers. Just think of all the possibilities - you can create DVD covers for movies, music albums, TV shows and any other source material. Just about anything can be placed onto a DVD cover.
Another thing you can do is make DVD's or CD's from scratch. This is not something very many people do either. Most people prefer to use the ready made ones that are available through the internet. There are thousands of websites that offer ready made covers for almost any type of media available.
Creating your own DVD and CD covers is not all that difficult but is rather time consuming. It takes hours of research and work. As with anything in life, the more you put in the more you get out. With time and practice you too can come up with your own unique DVD and CD cover templates or even come up with your own ideas and make your own DVD covers.
When searching for free dvd covers download there is one thing to remember. The best ones are usually free but not free forever. So if a site claims to have dvd cover templates or dvd cover download it may not be true. Usually you will need to download the template for a fee and then upload it to their server after paying the fee.
Another way of getting free dvd covers is to join a website that offers dvd software. There are some great websites offering free dvd covers. They are usually simple html pages which you can edit and customize to your needs. I have personally found a website that has a free dvd cover template, free movie download software, free movie maker software, wallpaper and background creator and a guitar tuner all in one place.
1 note
·
View note
Text
Worst Inventions according to Time Magazine:
Segway
New Coke
Clippy (paperclip office assistant from Microsoft Office)
Agent Orange (herbicide used during Vietnam War which caused serious health problems and birth defects)
CueCat (barcode scanner)
Subprime Mortgages (risky loans)
Crinoline
Nintendo Virtual Boy
Farmville (Facebook game of virtual farming)
Hydrogenated Oils (increases shelf life but also heart attacks)
Honegar (honey and apple-cider vinegar)
Hydrogen Blimps
Hair in a Can
DDT (banned in 1972)
Auto-Tune (technology that makes bad singers sound good)
Red Dye No. 2
Ford Pinto (explode in a rear end collision)
Parachute Jacket
Betamax
Baby Cage (cage mounted on windows for baby to get fresh air!)
Tanning Beds
Crocs
Hula Chair (designed to create abdominal workout)
Foursquare
Pop-Up Ads
Phone Fingers
CFCs (used in aerosols which damaged the ozone layer)
Plastic Grocery Bags (more than 500 million per year)
Bumpit (hair volumizing insert)
Electric Facial Mask
Sony CD Copy Protection
Venetian-Blind Sunglasses
Pet Spa
Pontiac Aztek
Snuggie for Dogs
Mizar Flying Car
Asbestos
Olestra (food additive)
Comfort Wipe (toilet paper extension arm)
Fake Ponytails
HeadOn (roll-on headache relief)
Pay Toilets
Tamagotchis (toy pet)
Leaded Gasoline
Vibrating Ab Belt
Spam E-mail
Smell-o-Vision (bottled scents released in movie theatres in sync with the movie)
Smile Checks (Japanese software that analyzes facial expressions)
Microsoft Bob
Vio (carbonated flavoured milk)
3 notes
·
View notes
Text
DOWNLOAD ADOBE ACROBAT PRO DC 2021 FULL CRACK - GOOGLE DRIVE LINK
Due to copyright issues, we do not share on the webstile, you download the file and extract it, there will be a video tutorial and installation file.

ABOUT ADOBE ACROBAT PRO DC 2021
What is Adobe Acorobat Pro DC 2021?
Adobe Acrobat Pro DC 2021 full crack is the latest version of today's professional PDF file editing software developed by the famous Adobe graphics software company. With the use of Acrobat Pro DC 2021 full crack you can split files, merge, merge multiple PDF files into one, create digital signatures, watermark to protect the content in your documents easily. Not only that, Acorobat Pro 2021 full key also helps you convert pdf files to word (.doc), Powerpoint (ppt), Excel, HTML Web Page, Image, Spreadsheet,,…. Very good support for those who work in printing.
This is a very useful software for students, teachers, office workers, etc. or other professions that need to edit or process documents.
Some Features of Acrobat Pro DC 2021 full free
Help you work with PDFs anywhere with the new, free Acrobat DC app for Android and iOS via Adobe's sync feature.
You can view and annotate the content you want to note right on the PDF file by using the comment toolkit of Acrobat Reader DC.
Store and access files in Adobe Document Cloud with 5 GB of free storage.
You can access and work with document files on Google Drive right in Acrobat software.
Protect important documents. Prevent others from copying or editing the information in your files.
You can now send, track, manage and store signed documents using esignature
One of the most important features is creating, converting (converting) and editing PDF files to Word or other similar file formats like Excel, PowerPoint,,….
You can fill in information or add a digital signature to the PDF file.
Performance improvements.
And some other improvements, if you are interested, you can see more on Adobe's homepage.
System Requirements When Using Acrobat Pro DC 2021 full free
These are some of the system requirements on your computer when using Acrobat Pro DC 2021 full key that I have referenced on the developer's homepage.
Windows Server 2008 R2 (64 bit), 2012 (64 bit), 2012 R2 (64 bit) † , 2016 (64 bit) or 2019 (64 bit); Windows 7 SP1 (32 bit and 64 bit), Windows 8, 8.1 (32 bit and 64 bit) † , or Windows 10 (32 bit and 64 bit)
CPU processor: from 1.5 GHz or faster.
RAM: from 1GB or more
Available hard disk space from 4.5 GB
Screen resolution 1024×768
The computer can use browsers such as Internet Explorer 11; Firefox (ESR); or Chrome
With these requirements, I think most computers today are enough, you can rest assured to download and install on your computer.
LINK DOWNLOAD ADOBE ACROBAT PRO DC 2021 + GOOGLE DRIVE LINK
LINK DOWNLOAD : https://www.originalsoftware.xyz/2021/06/adobe-acrobat-pro-dc-2021.html
#Adobe Acrobat Pro DC 2021 full crack#Acrobat Pro DC 2021 full crack#Acorobat Pro 2021 full key#Acrobat Pro DC 2021 full free#ADOBE ACROBAT PRO DC 2021
1 note
·
View note
Text
Download Ad Blocker For Mac Free

Written by Eyeo GmbH
Free Ad Blocker Windows 7
Ad Blocker For Mac Safari Free Download
Best Free Ad Blocker Mac
Ad Blocker For Macbook Air
Best Free Ad Blocker
Category: Productivity
Release date: 2019-11-27
Licence: Free
Software version: 2.1.0
File size: 19.24 MB
Compatibility: Windows 10/8.1/8/7/Vista and Mac OS X 10.12.6
Adblock Plus for Safari for PC and Mac Screenshots
Adblock for Mac, free and safe download. Adblock latest version: Block ads in Google Chrome. UBlock, the fastest, most powerful ad blocker for Mac is here. UBlock blocks all annoying pop-ups and ads while you browse on your Mac. It’s simple, easy-to-install, and best of all- completely free. Download uBlock ad blocker for Mac and browse faster today.
Key Features
Latest Version: 2.1.0
Licence: Free
Rated 3/5 By 740 People
What does Adblock Plus for Safari do? Adblock Plus for Safari is a totally free ad blocker that allows you to block annoying ads on your favorite websites and video channels. Simply install the app, and see the web in a better way. No more pop-ups, banners or autoplay ads. The Adblock Plus app for Mac supports great websites with Acceptable Ads (on by default). Don’t want to see any ads? Simply deactivate Acceptable Ads. You can also have the option to whitelist websites you trust.By downloading and installing the application, you agree to our Terms of Use. https://adblockplus.org/terms
Download for MacOS - server 1 --> Free
Download and Install Adblock Plus for Safari
Download for PC - server 1 --> MAC:


Download for MacOS - server 1 --> Free Thank you for visiting our site. Have a nice day!
PC Compactibility/Requirements for Installation
Compactible OS list:
Windows 10
Windows 8.1
Windows 7
Windows Vista
Free Ad Blocker Windows 7
Requirements for MacOS Installation
Ad Blocker For Mac Safari Free Download
Intel, 64-bit processor, OS X 10.7 or later.
Compactible OS list:
OS X 10.10: Yosemite
OS X 10.11: El Capitan
macOS 10.12: Sierra
macOS 10.13: High Sierra
macOS 10.14: Mojave8
macOS 10.15: Catalina
Adblock Plus for Safari - how do I download the app on PC?
If you want to download the software on your pc or mac, you could either first visit the Mac store or Windows AppStore and search for the app OR you can easily use any of the download links we provided above under the 'Download and Install' header section to download the application
Adblock Plus for Safari - Is it safe to download?
Yes. The app is 100 percent (100%) safe to download and Install. Our download links are from safe sources and are frequently virus scanned to protect you
By Glendale2x
New framework seems to have performance issues
This version of ABP for the new Safari framework unfortuantely seems to kill performance on my computers. Maybe it’s partially related to them being a bit older (one is a Mid 2011 Mini, the other is a 2012 iMac), but with ABP enabled I can’t even open a new tab/window and type a URL into the bar and expect Safari to accept the input without having to hold down the return key until it goes or wait a minute after opening a new tab or window. I also noticed that using Twitter was jumpy and lagged even with simple typing, it felt like all the dynamic content it relies on was just struggling to be processed through whatever framework Apple is forcing. Hopefully the devloper can figure out the performance issues because it’s really, really bad now.
By Ramblin'Rose
why isn’t this working?
I have ABP and it wasn’t perfect but worked fairly well for my needs. Recently, it simply disappeared. (I see someone else said that could be from the latest iOS update, but I don’t have that on my desktop yet). When I tried to reinstall, it showed me two boxes to check. The way I read it, if you checked the box that said you wanted the icon visible in the toolbar, it would be able to read sensitive information of all kinds on any page. What good is an app of any kind that allows for that?! As it was, with only the one box checked, it only blocked very few ads, and I was still getting requests from sites to be whitelisted without being able to fnd any way to do it. I’ve got all kinds of garage showing up on my Facebook page, and you guys have ruined what was a reasonable product. WHY?
By PeopleRsad
Still works for me
Almost didn’t download the new version based on the recent reviews, however after looking at the other apps here that claim to be ad blockers I didn’t’t see too many alternatives. I decided to go ahead and get the new version and so far its pretty much the same as the old version, lots of ads blocked. I’m happy, just make sure you go through the simple set-up.
By achilds19
Works well but
After much research, I understand the issue with Apple changing the rules on the devs so they had to build this app from scratch. Works well for me so far, except for one annoying problem. I use Yahoo mail and it's not hiding the ad that appears in the top line of the inbox even with unchecking the Acceptable Ads box, which is super annoying. I know the devs are watching these reviews, so if someone can point me to an extension or something that will fix that, I'd appreciate it. Was using AdGuard and it fixed that problem, but that app behaves like spyware and is constantly running in the background even after you close Safari.
Advertisement
Adguard for Mac v.1.1.0Adguard is the first standalone adblocker for Mac OS X. It is an ultimate program has all the features to ensure more efficient and comfortable use of the Internet. Ad blocking, phishing and malware protection, and privacy protection!
SlimBoat for Mac v.1.1.6SlimBoat is a fast and secure FREE web browser software with a lot of powerful features, such as intelligent form filler, popup blocker, adblocker, social network integration, download manager, web page translation, quick search and site groups.
Safari AdBlocker for Mac OS v.1.9.8.6The only 64-bit adblocker built for Mac OS X 10.5+ to integrate directly into Safari, for minimum disruption to your browsing experienceMain Features- Adblock Plus subscription support- Right-click to block images, and frames- Automatic ...
Vivaldi for MacOS v.3.2.1967The Vivaldi browser lets you be in control of how your browser looks, feels and works. It does not track you, adapts to your style with features that you need and has values that you can stand by.
Maiar Browser v.80.0.1.40Maiar is an extremely fast and privacy-friendly browser for the modern web. It loads major websites 2-8 times faster than Chrome and Safari. Maiar can block ads without modules or extensions.
Izenda Ad Hoc - Express Edition v.4.0Izenda Ad Hoc - Agile Business Intelligence for ASP.NETLiberate Your Organization's Relational Data Today!Izenda Ad Hoc empowers business users to directly explore relational data from a web browser. * Intuitive and Completely Web-Based AJAX Report ...
Avian Freeware Suite v.0.1Avian Freeware Suite (AFS) provides two things: Developers with libraries for Java Swing Widgets, XML handling, Fortran95 and Pascal; End users (Medical students, doctors, scientists) with productivity tools they can use (quizzes, XML databasing & ...
IP Blocker v.20050403IP Blocker is an incident response tool that automatically updates access control lists on Cisco routers and other devices. Web and command line interfaces are both supported, as is logging, email notification, and automatic expiration of ...
QR-Code Maker Freeware v.1.0.0Use QR-Code Studio to create QR codes for free. An assistant simplifies the creation of QR codes for mobile tagging, social media and more. The generated QR-Codes are available immediately as BMP, GIF, JPG, PNG and TIFF graphic file.
Freeware Advanced Audio Coder v.2.2.7FAAC is an Advanced Audio Coder (MPEG2-AAC, MPEG4-AAC). The goal of FAAC is to explore the possibilities of AAC and exceed the quality of the currently best MP3 ...
Zhang Hong's Freeware v.1.0[1] English-Portuguese-Chinese Dictionary [2] Japanese-English-Chinese Dictionary [3] MP3 Sponge [4] JPG Sponge [5] RedDays [6] RadSensor [7] descriptions and updates: ...
Mimosa Scheduling Software Freeware v.6.5.8Mimosa is a scheduling and event planning software application for use to create timetables in any kind of school and university of varying type and size. It is also used to schedule conferences and work-shifts in business and industry environments.
Flash Banner Maker for Mac v.1.00With AnvSoft Flash Banner Maker for Mac, you can easily create gorgeous flash banners in SWF format and html file for flash intros or for building website. You can add any image backgroud from your hard drive and choose from the 50+ animation effects for.
BiblePlayer for iPod v.1.1Take God’s Word to Go! Do you need to have a daily dose of bible scriptures? Or maybe you need a bible reading plan? Now you can read and listen to the King James version of the Bible on your iPod with this new freeware program. Bibleplayer ...
Mach-O OSAX v.0.1Mach-O OSAX is a scripting addition for CodeWarrior which provides different samples. The package is completly freeware and the source code is ...
QuickCart v.2.2QuickCart 2.2 is regarded as a flexible and handy program which is designed to run your own web shop. Freeware and easy to use e-commerce solution is designed to run Your own web shop. As a database it uses files structure so that the SQL database is ...
Flippagemaker PDF to Flash (SWF) for Mac v.1.0.0Flippagemaker Free PDF to Flash (SWF) for Mac is freeware for Mac users to convert pdf to swf flash video. Create Macromedia Flash (SWF) file from Adobe PDF file for embedding into web page easily.
DVDSmith Movie Backup v.1.0.0DVDSmith Movie Backup is DVD Decrypter, DVD copying Freeware to backup, clone or copy DVD movie to computer as DVD folder and removes all the protections (CSS, RC, RCE, APS, UOPs and Sony ARccOS) while copying.
Hubblescreensavermac v.1.0'Hubble Space Telescope (Mac) free screensaver containing 99 high quality NASA-ESA space images. Screensaver designed by the Creative Department, an award winning advertising and interactive agency based in Cincinnati. Fully functional freeware.' ...
MediaHuman Audio Converter MAC v.1.8MediaHuman Audio Converter is a freeware for Mac OS X. It can help you in case you need to convert your music in WMA, AAC, WAV, FLAC, OGG or Apple Loseless format. This program was designed to simplify as much as possible the process of conversion.
Best Free Ad Blocker Mac
Freeware Ad Blocker software by TitlePopularityFreewareLinuxMac
Ad Blocker For Macbook Air
Today's Top Ten Downloads for Freeware Ad Blocker
Best Free Ad Blocker
Zoiper Webphone ZOIPER webphone is fully-compliant with Internet Explorer,
1000apps NetVibes Widget Avec ce Widget vous pourrez rechercher des logiciels ,
Vivaldi for MacOS The Vivaldi browser lets you be in control of how your
QR-Code Maker Freeware Use QR-Code Studio to create QR codes for free. An assistant
Flash Banner Maker for Mac With AnvSoft Flash Banner Maker for Mac, you can easily
PC Protect Your PC First screensaver application protecting your PC from
Flippagemaker PDF to Flash (SWF) for Mac Flippagemaker Free PDF to Flash (SWF) for Mac is freeware
DVDSmith Movie Backup DVDSmith Movie Backup is DVD Decrypter, DVD copying
Maiar Browser Maiar is an extremely fast and privacy-friendly browser for
BiblePlayer for iPod Take God’s Word to Go! Do you need to have a daily
Visit HotFiles@Winsite for more of the top downloads here at WinSite!

2 notes
·
View notes
Text
HTTP response status codes indicate whether a specific HTTP request has been successfully finished
HTTP reaction status codes reveal no matter whether a certain HTTP request is successfully accomplished. Replies are grouped in five courses:
Informational responses (100--199)
Prosperous responses (200--299)
Redirects (three hundred--399)
Consumer problems (400--499)
Server mistakes (500--599)
Within the party you receive a response that is not During this listing, it really Get more information is a non-typical response, possibly custom made to the server's software program.
Information responses
100 ContinueThis interim reaction implies that anything is OK and that the customer really should carry on the request, or disregard the response In the event the ask for is presently concluded. 101 Switching ProtocolThis code is sent in response to an Upgrade request header in the consumer, and signifies the protocol the server is switching into. 102 Processing (WebDAV)This code indicates the host has obtained which is processing the request, but no response is obtainable still. 103 Historical HintsThis status code is primarily intended to generally be employed utilizing the hyperlink header, permitting the purchaser agent begin preloading applications though the host prepares a solution. The that means with the achievements relies upon upon the HTTP process:
GET: The source has been fetched which is despatched from the information human body.
Set or Publish: The resource describing the outcome with the motion is transmitted in the message system.
201 Produced The ask for has succeeded along with a new source is created As a result. This is ordinarily the solution sent immediately after Submit requests, or any Set requests. 202 AcceptedThe ask for has actually been received although not however acted on. It really is noncommittal, considering that there is no way in HTTP to Later on ship an asynchronous response indicating the benefits in the ask for. It truly is intended for situations in which A further treatment or host handles the request, or for batch processing. 203 Non-Authoritative Info This response code suggests the returned meta-facts is not really particularly the same as is obtainable from the supply server, but is gathered from the neighborhood or maybe a 3rd party backup. That is largely utilized for mirrors or even copies of another source. Except for that unique case, the"200 Okay" reaction is chosen to this standing. 204 No Contentthere is absolutely not any information to ship for this petition, although the headers may well be handy. 205 Reset ContentTells the user-agent to reset the doc which sent this petition. 206 Partial ContentThis response code is employed when the Range header is shipped by the consumer to ask for just A part of a source. 207 Multi-Status (WebDAV)Conveys specifics of many sources, for cases the place several position codes may possibly be ideal. 208 Already Reported (WebDAV)Used inside of a reaction factor to avoid consistently enumerating the inner associates of several bindings towards the similar assortment. 226 IM Used (HTTP Delta encoding)The server has fulfilled that has a GET ask for for your source, plus the answer is actually a illustration of your final result of just one or additional instance-manipulations applied to The present occasion.
Redirection messages
300 Multiple ChoiceThe petition has in excess of just one attainable response. The person-agent or buyer ought to decide on one among these. (There may be no standardized way of picking out among These solutions, but HTML hyperlinks into the choices are recommended so the person can pick out.) The new URL is provided while in the response. 302 FoundThis reply code implies the URI of asked for source is changed temporarily. Even more modifications in the URI could be acquired Down the road. Thus, this same URI must be used from the customer in long term requests. 303 See OtherThe waiter despatched this reaction to guide the customer to obtain the requested source at A further URI with a GET ask for. 304 Not ModifiedThat might be utilized for caching functions. It tells the customer the reply hasn't but been modified, Therefore the customer can continue on to employ the exact same cached Model of this reaction. 305 Use Proxy Defined in a preceding Variation on the HTTP specification to signify that a requested answer must be retrieved by a proxy. It's got been deprecated due to protection problems about in-band set up of a proxy. 306 unusedThis reply code isn't any for a longer time made use of; it really is just reserved. It were used in a prior Variation of the HTTP/1.1 specification. 307 Temporary RedirectThe server sends this reaction to guidebook the client to get the requested supply at A different URI with identical process that was utilized from the prior ask for. This has the exact same semantics as the 302 Observed HTTP response code, Along with the exception that the consumer agent should not modify the HTTP technique applied: When a POST was employed at the to start with petition, a Publish must be utilized at the subsequent petition. 308 Permanent RedirectThis implies that the resource is currently completely located at a unique URI, specified from the Site: HTTP Reaction header. This has the very same semantics because the 301 Moved Completely HTTP reaction code, With all the exception which the person consultant should not change the HTTP approach applied: If a Put up was applied from the first petition, a Write-up has got to be applied while in the second ask for.
Client mistake responses
400 Bad RequestThe server could not understand the ask for as a consequence of invalid syntax. To paraphrase, the client will have to authenticate itself to get the asked for response. The Preliminary intent for building this code was making use of it for electronic payment devices, nonetheless this standing code is applied very almost never and no normal convention is existing. 403 ForbiddenThe shopper won't have entry legal rights to the materials; this is, it really is unauthorized, or so the server is refusing to give the requested source. Opposite to 401, the customer's identification is recognized to the server. 404 Not FoundThe device can't Identify the requested resource. From the browser, this indicates the URL will not be regarded. In an API, this can also indicate which the endpoint is valid although the resource itself doesn't exist. Servers can also send out this reaction as opposed to 403 to conceal the event of a source from an unauthorized purchaser. This reaction code is most likely essentially the most famous 1 as a result of its Regular prevalence on the internet. 405 Method Not AllowedThe ask for technique is understood with the server but has actually been disabled and can't be applied. By the use of example, an API may perhaps forbid DELETE-ing a resource. The 2 required solutions, GET and HEAD, will have to never ever be disabled and should not return this mistake code. 406 Not AcceptableThis answer is shipped when the Website server, just after carrying out server-driven content negotiation, isn't going to obtain any content material that adheres for the requirements equipped because of the user representative. 407 Proxy Authentication RequiredThis is similar to 401 however authentication is expected for being obtained by signifies of a proxy. 408 Request TimeoutThis reaction is sent on an idle connection by some servers, even with no prior request by the client. It typically implies which the server would like to near this down unused link. This response is used substantially additional for the reason that some browsers, like Chrome, Firefox 27+, or IE9, benefit from HTTP pre-link mechanisms to speed up searching. Also Notice that quite a few servers only shut down the link devoid of sending this message. 409 ConflictThis reply is distributed whenever a request conflicts Using the existing state of your host. 410 GoneThis response is sent in the event the asked for material was forever deleted from server, with no forwarding deal with. Purchasers are predicted to eliminate their caches and backlinks to the resource. The HTTP specification options this standing code for use for"restricted-time, marketing methods". APIs shouldn't come to feel pressured to point methods which have been deleted with this standing code. 411 Length RequiredServer rejected the request considering the fact that the Material-Duration header industry isn't really outlined and also the server wants it. 412 Precondition FailedThe consumer has indicated preconditions in its personal headers which the host isn't going to meet up with. 413 Payload Too LargeTalk to entity is much larger than limitations described by server; the server could close the connection or return the Retry-Following header area. 415 Unsupported Media TypeThe media framework of this asked for knowledge is not supported through the server, And so the server is rejecting the request. 416 Range Not SatisfiableThe selection specified from the Variety header area from the request can't be fulfilled; it truly is achievable the scope is away from the scale of the focus on URI's information. 417 Expectation FailedThis reaction code signifies the anticipation indicated from the Hope ask for header discipline won't be able to be fulfilled by the server. 421 Misdirected RequestThe ask for was directed in a host which will not be ready to generate a response. This may be transmitted by a host which is not configured to create responses for the combination of technique and authority which are A part of the request URI. 422 Unprocessable Entity (WebDAV)The ask for was perfectly-shaped but was unable to generally be followed due to semantic problems. 423 Locked (WebDAV)The source that has long been accessed is locked. 425 Too Early indicators that the server is hesitant to chance processing a petition That may be replayed. 426 Upgrade RequiredThe server is not going to complete the request applying the latest protocol but may possibly be Completely ready to do so next the customer updates to a special protocol. The server sends an Upgrade header at a 426 response to signify the necessary protocol(s). 428 Precondition RequiredThe origin server calls for the petition to be conditional. This response is intended to prevent the'missing update' problem, exactly where a purchaser Receives a supply's issue, modifies it, and PUTs back to the server, when a 3rd party has modified the condition to the host, bringing about a fight. 429 Too Many RequestsThe consumer has sent a lot of requests inside of a specified interval of your time ("amount restricting"). 431 Request Header Fields Too LargeThe host is unwilling to procedure the request mainly because its personal header fields are excessively big. 451 Unavailable For Legal ReasonsThe user-agent requested a resource which may't legally be offered, such as an online web site censored by a governing administration.
Server mistake answers

youtube
500 Internal Server ErrorThe server has encountered a circumstance it doesn't learn how to manage. 501 Not ImplementedThe petition approach isn't supported by the host and can not be managed. The only techniques that servers are envisioned to aid (and as a result that should not return this code) are GET and HEAD. 502 Bad GatewayThis error reaction signifies the server, though employed to be a gateway to have a reaction needed to manage the petition, got an invalid reaction. 503 Service UnavailableThe server isn't ready to handle the ask for. Frequent brings about are a host which is down for maintenance or that is overloaded. Observe that with this reaction, a person-helpful website page describing the issue ought to be despatched. This solutions need to be utilized for short-term ailments in conjunction with also the Retry-Just after: HTTP header should, if possible, involve the believed time just before the recovery of the support. The webmaster will have to also watch out about the caching-relevant headers that are despatched collectively with this solution, as these momentary issue responses shouldn't be cached. 504 Gateway TimeoutThis mistake response is provided when the server is acting as a gateway and can't find a reaction in time. 508 Loop Detected (WebDAV)The server detected an infinite loop when processing the petition. 510 Not ExtendedExtra extensions to the ask for are needed for your waiter to match it. 511 Network Authentication RequiredThe 511 status code implies which the consumer should authenticate to attain network obtain.
2 notes
·
View notes
Text
Bitdefender Total Security 2015 Free License Key

Bitdefender Total Security Free Trial
Bitdefender Total Security 2015 Free License Key Download
Bitdefender Total Security 2015 Free License Key Activation
Go to Bitdefender Central and sign in. If you don’t have an account, choose to create one. Click on the My Subscriptions panel, located on the left side of the window. Click the Activate a service with code button. Input the code from the e-mail received after purchasing Bitdefender. NOTE: The email is received only upon purchase. Bitdefender Total Security 2015 free license key is the ultimate anti-malware software. It builds on technology awarded Best Protection and Best Performance to defend your device with just one click. Lock confidential files in an encrypted vault and use Bitdefender Safebox to securely stores photos and videos online.
Even though there are still a few weeks left before 2015, many software developers and vendors have started launching their 2015 version software. The award-winning security solution provider, BitDefender is also catching the hot wave by rolling out its BitDefender Total Security 2015. Like its other products, BitDefender Antivirus 2015 and BitDefender Internet Security 2015 provide an advanced proactive protection against viruses and spyware in real time without slow down your PC performance.
BitDefender Total Security 2015 is the ultimate anti-malware software that builds from advanced protection technology to defend PC with just one click. Bitdefender Total Security 2015 provides protection anti-virus, anti-malware, anti-spam, tune-up, online banking protection, a 2-way firewall, parental control, online backup and anti-theft provision. In addition, it’s also can lock confidential files in an encrypted vault, Bitdefender Safebox to securely stores photos and videos online, and Device Anti-Theft features helps recover PC in case of loss or theft.
If you would like to have BitDefender Total Security 2015 installed on your PC, now you can get the free 6 months of Bitdefender Total Security 2015.
BitDefender Total Security 2015 normally costs $89.95 for one year license key up to 3 PCs. To grab a free copy of BitDefender Total Security 2015, visit the following URL: http://www.bitdefender.de/media/html/chip2015/
Fill in the email address, and then click the “KOSTENLOSE LIZENZ SICHERN” button.
An email confirmation containing the download link and license key for BitDefender Total Security 2015 will be received.
Note: If the e-mail hasn’t arrived within 30 minutes, please check your spam, junk, or promotions mail folder to locate it.
Download BitDefender Total Security 2015 setup installer:
BitDefender Total Security 2015 32 Bit: bitdefender_ts_18_32b.exe
BitDefender Total Security 2015 64 Bit: bitdefender_ts_18_64b.exe
BitDefender Total Security 2015 supports Windows Vista, Windows 7, Windows 8, and Windows 8.1 operating system.
Related Posts
Recent Articles
Tags
BitDefender Total Security 2020 Crack + Activation Code full. free download
BitDefender Total Security Crack provides the best security options to any operating system. The program offers a large number of Security options. It provides a Firewall and best virus protection. Bitdefender total security Crack enables real-time protection for users. It checks the internet security regularly; when you open a web browser, it turns on automatically. It automatically finds errors and fixes them. It stops those sites automatically that have a trojan, viruses, and hacking materials. BitDefender Total Security Keygen allows you to speed up your computer system, operating system, browser, and analyze your hard-disk. When this application is mounted on your computer, it scans your Device automatically, like other antivirus apps.
BitDefender Total Security 2020 Crack provides layered protection to secure your files, images, and videos, including ransomware and malware from all known and emerging threats. You can also test security packages for terminals with Bitdefender Antivirus Total Protection. The privacy of your data is protected by phishing. This also protects your passwords and the number of your bank cards. This offers tools for neighborhood risk management. This app investigates the suspicious behavior of the group. It blocks other attacks as well. The built-in firewall manages the linked network.

BitDefender Total Security 2020 Crack + Activation Code
Bitdefender total security Serial Key has immense intelligence performs to stop all kind of threats. It checks your apps regularly and fixes all errors of your apps. Bitdefender Provides both of methods to use it Manually and Automatically. It Gives real protection to your Digital Computer. It would forever be able to keep it updated. Bitdefender Crack Allows to Protect your data for your office and personal use. Besides, It is the most effective technology in the Universe to protects Your information.
BitDefender Total Security Activation Codeoffers award-winning security information and threats to people, businesses, and infrastructure, networks, and cloud services. Today, Bitdefender is also the option provider in more than 38% of global security solutions. Bitdefender is also awarded groundbreaking innovations for what we do best: Secure your digital life with an intuitive and quick device output protection solution. It provides tools for the protection of software, file security, and protection of the Internet. In addition to the network, the program protects your device data. The autopilot mode is available as well if you can use it at Bitdefender.
BitDefender Total Security Key Features:
Fast And Efficient
Bitdefender total security is one of the quickest and Efficient Software compare to others. It scans the whole Pc in a few moments.
Most Securable
Bitdefender is one of the best securable software in the world. It is the best software For Security purpose compared to others
Best security Options
BitDefender Gives us many Security Options like two-step verification, fingerprint security, Pattern, and faces unlock. To protect and analyze your information, it provides the best security options.
User-Friendly Interface
Bitdefender total security crack presents Good User-friendly interface to its users
Protect your Data in one click
Options are so easy. Even a beginner uses it efficiently. The user can easily understand the interface. And perform tasks in just one click
Works with any operating system
Bitdefender Total Security Free Trial
It Can work with any operating System Like Windows XP, Linux, and Vista. Also, Compactable For Android and iOS
Speed up Your Device
With this software, You can Boost your Devices in some seconds
BitDefender Total Security 2020 Activation Code:
Bitdefender Total Security 2015 Free License Key Download
4F5GP-55FFV-KKY65-78T88-GG6HW
4F5G6-H7G56-H7J81-G56H7-FG56C
What’s New in BitDefender Total Security 2020 Crack?
Improved Internet protection on Windows PCs against all attacks.
This tool is intended to protect you in real-time against stubborn threats.
Layered ransomware protection for the safety of your files.
This is the primary weapon for defense from external and internal threats.
It has cloud-based security services that guarantee the cleanliness of your system.
It eliminates new and established risks, malware, trojans, and other hazardous files.
Incredible network threat detection blocking sophisticated attacks.
It also offers security in real-time when browsing the Internet.
It tests URLs and alerts you if the website does not contain anything right.
Besides, It provides Secure and fast VPN.
Internet browsing experience is anonymous and free.
Security of children online with advanced parental control.
Minimum performance effects.
Bug Fixes
Now compatible For Windows 10
Auto Protection
System Requirements:
CPU: Intel Core 2 Duo 2 GHz
RAM: 2 GB.
Hard Disk: 2.8 GB of free space.
OperatingSystem: Windows 7/8.1/8/10
How to Install BitDefender Total Security Crack?
Bitdefender Total Security 2015 Free License Key Activation
Download BitDefender Crack Form bellow Button
After Download Click on install
After Installation put Keys in Key Bar
All Done
Enjoy
Marc
BitDefender Total Security 2020 Crack
5
BitDefender Total Security
Mac & Windows
Security

1 note
·
View note