#html image copy protection
Explore tagged Tumblr posts
Text
Dear Web Encryptor : Protect both Content and Source Code of HTML, HTML5, BootStrap website
https://codecanyon.net/item/dear-web-encryptor-protect-the-source-code-of-html-html5-bootstrap-website/19555597
Every day, several website owners become victims of people who steal Text Content, Image Content and HTML, HTML5, BootStrap codes. If you do not protect your Text Content, Image Content and Source Code, you could even allow your entire site to be cloned by such people, in minutes, even without any credit or profit to you. Using this software is the only way to protect your HTML, HTML5, BootStrap websites from being stolen.
#copy protection html#dear web encryptor#disable copy and paste html#disable copy web page#disable image download html#disable right click and selection html#dreamweaver#encrypt html5#html copy protection software#html encryption software#html image copy protection#html text copy protection#html5 copy protection#html5 encryption#prevent image download
0 notes
Text


All The King's Horses | As You Are Now, So Once Was I by @samwpmarleau (grumkinsnark)
All The King's Horses [LiveJournal ch1] [Fanfiction.net ch1]
As You Are Now, So Once Was I [LiveJournal ch1] [Fanfiction.net ch1]
Fandom: Supernatural, Criminal Minds
Rating: Teen | PG-13
Category: Gen
Words: ~36,192
All The King's Horses: Protect and Serve. Fidelity, Bravery, Integrity. To what lengths would you go to uphold those oaths? When it comes to a particularly brutal and unsolvable case, the BAU just may have to resort to some more unorthodox methods. SPN/Criminal Minds crossover.
As You Are Now, So Once Was I: Sequel to "All the King's Horses." When Dean catches J.J.'s press conference on the news about a current case and notices a few...inconsistencies, he realizes the BAU is definitely going to need his help. Again. ON HIATUS



About the Book
FORMAT: Letter quarto, flatback bradel binding, french link stitch, no tapes
FONTS: EB Garamond [via Google Fonts], Supernatural Knight [via DaFont], D-Din [via Font Squirrel], Daniel [via DaFont], Permanent Marker [via Google Fonts], Arial
IMAGES: Seal of the FBI [via Wikipedia], Dean's handprint scar [by greenhorn-art]
MATERIALS: 24lb Xerox Bold Digital paper (8.5"x11"), 80pt binder's board (~2mm), 30/3 size waxed linen thread, embroidery floss (DMC #721), 1.9mm cording, brown cardstock, black Cialux bookcloth, gold foil transfer sheet (came with We R Memory Keepers hot foil pen)
PROGRAMS USED: Fic exported with FicHub, word doc compiled in LibreOffice Writer, Typeset in Affinity Publisher, imposed with Bookbinder-JS, title pages designed in Affinity Designer/Photo
.
I first read these stories on LiveJournal back in 2013, some time after I first encountered Tumblr, Supernatural, and the wider world of online fandom. Once I discovered SPNxCriminal Minds crossovers I devoured so many of them. Something about POV Outsider on the Winchesters, the existing connections with investigating monster vs human-crazy cases, and run-ins with the FBI... it's just works so well.
Of all the SPNxCM fics I read and enjoyed, All The King's Horses is among those that bookmarked themselves in my brain. Since it's been living there all these years, I thought it deserved a place on my bookshelf too.
(Rambling below)
Sourcing the Fic
I used FicHub to download the fics off of Fanfiction.net as HTML. Then I pasted them into LibreOffice Writer and created rich text documents of each fic, so I could Place them into Affinity Publisher.
The stories were crossposted, first on LiveJournal and then Fanfiction. I included the metadata from both sites in the appendices.


(It's fascinating to see the differences in the same work between platforms. FFN requires genres, so if the author doesn't add them on LJ then by default there's more info on FFN. But FFN limits listed characters to 2, so authors have to pick and choose the most important. Then there's the author's amusing disclaimers and spoiler warnings for these fics, which are only included in the LJ version)
Shoutout to the author for how they linked/listed their accounts on other platforms! Thanks to that I was easily able to track down all the tags/metadata for the fics, and find them here to express my appreciation for their stories!
Typesetting
Fonts
EB Garamond is my new favourite body font, 11pt as per my usual.
The title page is entirely Arial: 1) it was the closest match I have to the case file prop I was copying, and 2) if it was a government doc they wouldn't be using anything but the most basic fonts.
Headings and the the bullets bracketing the page numbers are set it Supernatural Knight, a free font in the style of Supernatural's title.
The location segments are in D-DIN, the closest free match to the font Criminal Minds uses (which is probably DIN).
Daniel is used for Dean's 'rushed but legible' note.
Permanent Marker for the 'thick black Sharpie' case file labels.
Artwork
Title pages designed as FBI case files, copied from a prop found online (specifically Etsy's propfictionstudios', but it's all over the web so no idea who actually created it). I had fun plugging in all the fanfic/bookbinding meta!
The ID# above the author's name is the FFN story ID, and the date is the date originally posted on LJ.
The handprint used in the headings of ATKH is Dean's scar. I traced off of a screenshot from s4e01 Lazarus Rising. I chose to use the handprint instead of the anti-possession tattoo or a Devil's Trap as my SPN art element because 1) it's specific to Dean, and 2) indicates/reminds that the story is not set during the season 3 Agent Henriksen/FBI arc.
Grabbed the FBI seal off of Wikipedia.
Construction
Both fics typeset and printed separately, then sewn together into one book. Title page for the sequel was tipped in like an endpaper prior to sewing.
Endbands sewn with orange embroidery floss (DMC 721) around 1.9mm cording. I chose orange because Dean's being in jail brought to mind the orange prison jumpsuits Sam and Dean wore in s1e19 Folsom Prison Blues.

Black bookcloth for the cover, like the Winchesters' beloved black '67 Chevy Impala. (I'd wanted a Supernatural reference to balance out the Criminal Minds-ness of the FBI case files).
I'd originally planned to make lineart of the front of the car, and have it stretch across the bottom of the cover (maybe even wrap around to the back). Even found a useful reference to trace [from here], but it didn't look as good as I'd hoped. Instead I reused the FBI seal and swapped out its text with the titles.
(The effect of shiny foiled FBI symbol on small black book reminds me of one of those FBI badge wallets!)
The foiling process was an unnecessarily long and gruelling affair. My laptop served as a massive power bank for the hot foil pen as I spent 2hrs ever so slowly tracing the image, and then 15mins on the author name and touch-ups. Did it need to take so long? Moving slowly, pushing down hard, going over everything at least three times? I'm sure it didn't. BUT I did not want to chance peeling up the foil to check how I was doing and risk shifting it. It was worth it in my books (haha) ‒ I feel giddy and kick my feet like a schoolgirl whenever I see it!
New Things
Used 24lb paper for the first time, and I love it! It's a little thicker and heavier then regular 20lb printer paper, feels more substantial.
The page numbers & running/section headers are along the outer margin, instead of in the header/footer. This was my way around Affinity's buggy-ness regarding pinning things inline in master pages. (More about that below). If I had been thinking, I could have formatted them like the tabs on a file folder and cut the textblock to match. Oh well, the things you notice once it's printed 😔
This time I also started new chapters/sections using text flow & paragraph spacing settings, instead of using a master. As always, there are pros and cons.
Pro: much faster and less involved. (find chapter start, apply paragraph style VS working from the end cutting text, inserting a frame break, unlinking frames, inserting new pages with master, relinking, pasting, and adding chapter title to a different text box)
Con: images need to be added manually (whether by adding image directly, or by applying a master with the image). I forgot to do this for the second fic, so only ATKH have Dean's handprint scar.
Difficulties Encountered
Affinity Publisher is fighting me on pinning things inline on master pages. They like to disappear on regular pages I've applied the master to. Sometimes it works, sometimes it doesn't, sometimes it only works on some of the pages. Idk what's up. (The bullet character only faces one way so I had use textboxes, flip/mirror one, and pin them inline to the page number).
So instead of having page numbers in the footer, bookended left and right by text boxes with Supernatural Knight's bullet, I put it vertically down the side.
Updated Publisher and all my paragraph styles' fonts changed/went funny. Something to do with the update's variable font support, I think. What was previously 'EB Garamond' regular, was now something along the lines of 'EBGaramond-Regular' which isn't a font. Issue seems to have ironed itself out in my original (near-complete) doc while I was busy remaking it. 😐
On the bright side, the update brought QR code generation to Affinity!
#All The King's Horses#As You Are Now So Once Was I#grumkinsnark#samwpmarleau#fanfiction#bookbinding#fanbinding#supernatural#criminal minds
109 notes
·
View notes
Text
Yesterday in an IRC chat, I expressed surprise that a news site actually let you right-click -> copy image url, rather than slapping "oncontextmenu="return false"" in every single HTML tag like most websites seem to do these days (even a piracy site! Why?! Are you worried someone will illegally download your illegal media you're giving to them illegally?! But it's only protected by an easily-removed tag attribute????)
I don't know if it's the depression speaking but these days I find it incredibly hard to enjoy anything about the Internet.
Literally every website has become a thousand times more inconvenient, bloated with promoted or recommended shit, stupid UI/UX changes pushed by out of touch billionaires.
The tipping point this week was Google changing the regular "Web - Images - Videos - Etc." tabs with fucking stupid ever-changing search suggestions, making the site a thousand times less accessible and so much more annoying to use
I'm tired. I want forums back. I want ugly html pages that give useful information back. I want to connect with other Internet users in a meaningful way again. Fuck modern corporate UI design. Fuck social media. I want out.
30K notes
·
View notes
Link
#autoSSL#Automation#cloud#configuration#containerization#DevOps#Docker#HTTPS#Let'sEncrypt#Linux#networking#NGINX#proxyserver#reverseproxy#Security#self-hosted#servermanagement#systemadministration#TLS#Traefik#webserver
0 notes
Text
AWS WAFv2 For Hotlink Protection: Future Of Content Security

How to stop hotlinking with Amazon CloudFront, WAF, and referer checking.
AWS WAF Classic will be retired in September 2025. This update describes how to utilise the latest AWS WAF (WAFv2) to avoid hotlinking. Screenshots have been updated to reflect AWS WAF Management Console changes.
Hotlinking, also known as inline linking, is a kind of content leeching in which an unauthorised third-party website embeds links to resources referenced in a major website's HTML. Your website may be invoiced for third-party websites' content as they don't pay for hosting. Slow loading times, lost money, and legal issues may result.
Hotlinking may now be stopped using AWS WAF. AWS WAF, a web application firewall, integrates with Amazon CloudFront, a CDN, to protect your web apps from typical online vulnerabilities that can reduce application availability, security, and resource use.
Solution overview
There are several techniques to handle hotlinking. The Apache module mod_rewrite may verify the Referer header on your web server. You may then redirect the visitor to your site's home page or display a 403 Forbidden message.
If you utilise a CDN like CloudFront to speed up website delivery, web server Referer header validation is less useful. The CDN must validate additional requests for that content because they are unlikely to reach the origin web server, even if your web server verifies the headers (in this example, the referer). The CDN caches your stuff at the edge of its servers.
Figure 1: Cache request-response flow.Hit-and-miss cache encounters
Figure 1 shows the procedure:
A user client (1) requests from CloudFront edge point (2).
Edge locations try to return a cached file. This request is a cache hit if the cache replies.
The origin (3), which may be an Amazon S3 bucket, receives a request for a new copy of the object if there is a cache miss and the content is incorrect or not in the edge.
Cache hits prevent the origin from applying validation logic to the user's request since the edge server may fill the request without contacting the origin.
Two methods for solution implementation
This document provides two AWS WAF configurations to prevent hotlinking:
Transferring protected static assets (images or stylistic elements) to static.example.com ensures that you just need to check the Referer header.
Static files are in a directory on the same domain. This approach includes extending this example to check for an empty Referer header.
Your website structure and security needs will determine your strategy. The first approach lets you set up a Referer header check to guarantee that photo requests come from an allowlisted sub-domain, while the second way checks for an empty Referer header. The first technique prevents unaffiliated third-party sites from embedding image links, whereas the second allows users to share direct connections.
Terms
Key phrases from this post:
AWS WAFs use web ACLs tied to CloudFront distributions.
Each web ACL has one or more match criteria and rules.
Match conditions examine request headers or URIs for particular criteria using one or more filters.
The names of HTTP headers are not case-sensitive. Referer references the same HTTP header. However, HTTP headers are case-sensitive.
Requirements
A CloudFront distribution is needed to configure an AWS WAF web ACL. Configuring a CloudFront distribution with an S3 bucket origin is covered in Configure distributions.
Approach 1: Subdomain separation
This sample AWS WAF rule set comprises one rule, match condition, and filter. The match condition checks the Referer header for a given value. Traffic is allowed if the request meets rule conditions. If not, AWS WAF blocks traffic.
Due to the static files' subdomain (static.example.com) being accessible exclusively from example.com, you will restrict hotlinking for any file without a referral.
Approach 2: Domain-wide content with path filtering
The second technique filters by URL path and allows blank Referer headers. Create an AWS WAF web ACL with numerous rules and extra match criteria, which are filters. Instead than validating the Referer header once, the match condition validates it twice. First, check the request header. The URL-style Referer header is checked in the second validation.
Some people may prefer to share the photo URL directly. Accessing the picture directly in the browser can help avoid a negative user experience. This solution is better than the previous, which needed sub-domain picture requests.
You must also check the request route (/wp-content) for AWS WAF to protect multiple folders under a domain name.
In conclusion
AWS WAF, a web application firewall, monitors and manages HTTP(S) traffic to your protected web applications. Using the AWS WAF custom rule builder, you protected your website's Amazon S3 bucket content from hotlinking.
Preventing unauthorised third-party websites from connecting to your static content reduces bandwidth costs, user experience, and resource leeching. Two robust referrer check methods are described in this post. Following the least privilege approach, you may restrict AWS WAF rules to.jpg or.png image file extensions.
Referer checking prevents unaffiliated websites from utilising your bandwidth and backlinking to your images, but clever attacks can purposefully design a request to bypass it. Inconsistent referer header interpretation can also be caused by browser plugins, server-to-server queries that fake header data, or privacy-based web browsers. Recognise these anomalies and consider token authentication and signed URLs for private content protection.
Web browsers cannot detect changed Referer headers. Referer checking should be utilised with AWS WAF application protection rules, Bot Control, Fraud Control, and DDOS protection to secure online applications.
#technology#technews#govindhtech#news#technologynews#AWS WAF#Amazon S3#WAFv2#content delivery network#web ACL#HTTP
0 notes
Text
How to Build a Fast, Secure, and Scalable Website
In today’s digital age, having a website that is fast, secure, and scalable is essential for businesses and developers alike. Whether you are building a personal blog, an e-commerce platform, or an enterprise-level application, ensuring optimal performance, security, and scalability should be a priority. A well-optimized website enhances user experience, improves search engine rankings, and ensures seamless operation even during traffic surges. In this blog, we’ll explore best practices to help you build a website that meets these critical criteria and supports business growth effectively.
1. Optimize for Speed
Website speed plays a crucial role in user experience and search engine rankings. Here are some key strategies to enhance website performance:
Use a Fast Hosting Provider
Choosing the right hosting provider can significantly impact your website's speed and reliability. Opt for a service that offers high-speed performance, such as cloud hosting or dedicated servers. Popular hosting providers like AWS, Google Cloud, and DigitalOcean offer scalable and high-performance solutions tailored to different business needs.
Leverage Content Delivery Networks (CDNs)
CDNs store copies of your website’s static assets across multiple global servers, reducing latency and load times for users in different locations. Using a CDN ensures your website loads quickly, even for visitors accessing it from distant geographic locations.
Optimize Images and Media Files
Large image files can slow down your website significantly. Use tools like TinyPNG or WebP format to compress images without sacrificing quality. Additionally, consider using responsive image formats that adjust dynamically based on device resolution and screen size.
Minify CSS, JavaScript, and HTML
Reducing the size of your code by minifying CSS, JS, and HTML files can significantly improve loading times. Tools like UglifyJS, CSSNano, and HTMLMinifier can help streamline your code while maintaining its functionality.
Implement Lazy Loading
Lazy loading ensures that images, videos, and other heavy resources load only when needed, improving initial page load speed. This technique reduces the amount of data that needs to be loaded immediately when a user lands on your page.
Use Browser Caching
By enabling caching, browsers can store copies of static resources, reducing the need to reload them each time a user visits the website. This helps in significantly improving return visits and reducing server load.
2. Enhance Security Measures
With cyber threats on the rise, securing your website is non-negotiable. Here’s how to protect your site effectively:
Use HTTPS and SSL Certificates
Securing your website with HTTPS by installing an SSL certificate encrypts data between users and your site, preventing cyber-attacks like man-in-the-middle attacks and data breaches.
Regularly Update Software and Plugins
Keep your CMS, themes, and plugins updated to prevent vulnerabilities that hackers may exploit. Outdated software is one of the primary security risks leading to data theft and unauthorized access.
Implement Web Application Firewall (WAF)
A WAF helps filter and monitor HTTP traffic between a web application and the Internet, blocking malicious attacks. It acts as a shield against threats such as SQL injection and cross-site scripting (XSS).
Enable Two-Factor Authentication (2FA)
Adding an extra layer of security, such as 2FA, ensures that only authorized users gain access to sensitive areas of your website. This significantly reduces the risk of unauthorized access due to password breaches.
Perform Regular Security Audits
Use tools like Sucuri or Qualys to conduct regular security scans and identify potential vulnerabilities before hackers do. Conducting periodic penetration testing also helps in strengthening website security.
Implement Secure Authentication and Data Encryption
Use strong passwords, encrypt stored data, and implement security headers to protect against threats like cross-site scripting (XSS) and SQL injection attacks. Keeping security policies updated helps in mitigating emerging cybersecurity risks.
3. Ensure Scalability
Scalability is essential to handle traffic spikes without compromising performance. Here’s how to design a scalable website:
Adopt a Microservices Architecture
Instead of a monolithic structure, use a microservices-based approach where different parts of the application can scale independently. This allows for easier updates and better fault isolation.
Use Load Balancing
Distribute traffic efficiently across multiple servers to prevent overload and downtime. Load balancers like Nginx or AWS Elastic Load Balancing can help maintain high availability even during peak traffic periods.
Leverage Cloud Infrastructure
Cloud platforms like AWS, Google Cloud, and Azure offer auto-scaling features that adjust resources based on traffic demands. This ensures that your website remains responsive even during unexpected traffic surges.
Optimize Database Performance
Use indexing, query optimization, and caching techniques (e.g., Redis or Memcached) to improve database efficiency and handle high loads. A well-optimized database enhances website performance and response time.
Use Asynchronous Processing
For tasks that do not require immediate execution, implement asynchronous processing using message queues (e.g., RabbitMQ, Apache Kafka) to enhance performance. This allows the website to handle multiple processes efficiently without performance lags.
Monitor and Scale Automatically
Set up monitoring tools like New Relic, Google Analytics, or AWS CloudWatch to track performance metrics and automate scaling decisions. Proactive monitoring helps in identifying performance bottlenecks and making necessary optimizations.
Conclusion
Building a fast, secure, and scalable website requires a strategic approach that balances performance optimization, security best practices, and scalable architecture. By implementing these techniques, you can create a website that provides a seamless experience for users while ensuring security and reliability as your business grows.
Need help with website development? At Chirpin, we specialize in building high-performance, secure, and scalable websites. As a digital marketing agency in Delhi, we also provide digital marketing services in Delhi NCR to help businesses enhance their online presence. Whether you are looking for the best digital marketing company in Delhi or need professional digital marketing services in Delhi NCR, Chirpin has you covered. Our expert team works with businesses of all sizes, helping them establish a strong online presence and drive more leads. If you are looking for the best digital marketing company in Delhi NCR that offers comprehensive web development and marketing solutions, contact us today to bring your digital vision to life!
exhibition stand builders in dubai exhibition stand contractors in dubai exhibition contractors in dubai exhibition stand builders dubai dubai exhibition stand contractor exhibition stand designers in dubai best exhibition stand contractor in dubai best exhibition stand builders dubai exhibition stand design company in dubai exhibition stand design dubai dubai exhibition stands exhibition company in dubai exhibition companies in dubai exhibition stand builder abu dhabi exhibition stand contractor in abu dhabi exhibition stand contractors abu dhabi exhibition stand companies in abu dhabi exhibition stand design company abu dhabi exhibition stand in abu dhabi
0 notes
Text
PT:
the darling Glaze “anti-ai” watermarking system is a grift that stole code (link: https://www.reddit.com/r/StableDiffusion/comments/11sqkh9/glaze_is_violating_gpl/)/violated GPL license (that the creator admits to) (link: https://twitter.com/ravenben/status/1636439335569375238). It uses the same exact technology as Stable Diffusion. It’s not going to protect you from LORAs (smaller models that imitate a certain style, character, or concept)
An invisible watermark is never going to work. “De-glazing” training images is as easy as running it through a denoising upscaler. If someone really wanted to make a LORA of your art, Glaze and Nightshade are not going to stop them.
If you really want to protect your art from being used as positive training data, use a proper, obnoxious watermark, with your username/website, with “do not use” plastered everywhere. Then, at the very least, it’ll be used as a negative training image instead (telling the model “don’t imitate this”).
There is never a guarantee your art hasn’t been scraped and used to train a model. Training sets aren’t commonly public. Once you share your art online, you don’t know every person who has seen it, saved it, or drawn inspiration from it. Similarly, you can’t name every influence and inspiration that has affected your art.
I suggest that anti-AI art people get used to the fact that sharing art means letting go of the fear of being copied. Nothing is truly original. Artists have always copied each other, and now programmers copy artists.
Capitalists, meanwhile, are excited that they can pay less for “less labor”. Automation and technology is an excuse to undermine and cheapen human labor—if you work in the entertainment industry, it’s adapt AI, quicken your workflow, or lose your job because you’re less productive. This is not a new phenomenon.
You should be mad at management. You should unionize and demand that your labor is compensated fairly.
reblog:
I would like to nitpick on one following comment in the OP:
"“De-glazing” training images is as easy as running it through a denoising upscaler."
This is, to the best of our knowledge, not true.
Glaze is designed to be robust to filtering attempts to reverse it. The original paper published on Glaze (link: https://people.cs.uchicago.edu/~ravenben/publications/abstracts/glaze-usenix23.html) details that images that have been glazed will resist even relatively high gaussian noise and JPEG compression filters. The paper also describes an unsuccessful real-world tool (which was widely spread) which attempted to remove the cloaking using pixel-level smoothing.
There are other non-filtering techniques with better decloaking success and less degradation, which primarily seem to be based on fine-tuning models on original (non-glazed) art. LoRA is the elephant in the room.
the darling Glaze “anti-ai” watermarking system is a grift that stole code/violated GPL license (that the creator admits to). It uses the same exact technology as Stable Diffusion. It’s not going to protect you from LORAs (smaller models that imitate a certain style, character, or concept)
An invisible watermark is never going to work. “De-glazing” training images is as easy as running it through a denoising upscaler. If someone really wanted to make a LORA of your art, Glaze and Nightshade are not going to stop them.
If you really want to protect your art from being used as positive training data, use a proper, obnoxious watermark, with your username/website, with “do not use” plastered everywhere. Then, at the very least, it’ll be used as a negative training image instead (telling the model “don’t imitate this”).
There is never a guarantee your art hasn’t been scraped and used to train a model. Training sets aren’t commonly public. Once you share your art online, you don’t know every person who has seen it, saved it, or drawn inspiration from it. Similarly, you can’t name every influence and inspiration that has affected your art.
I suggest that anti-AI art people get used to the fact that sharing art means letting go of the fear of being copied. Nothing is truly original. Artists have always copied each other, and now programmers copy artists.
Capitalists, meanwhile, are excited that they can pay less for “less labor”. Automation and technology is an excuse to undermine and cheapen human labor—if you work in the entertainment industry, it’s adapt AI, quicken your workflow, or lose your job because you’re less productive. This is not a new phenomenon.
You should be mad at management. You should unionize and demand that your labor is compensated fairly.
11K notes
·
View notes
Text
NGINX Server & Custom Load Balancer: A Comprehensive Guide

The NGINX Server is an industry-leading open-source software for web serving, reverse proxying, caching, load balancing, media streaming, and more. Initially developed as a web server, NGINX has grown to become a versatile tool for handling some of the most complex load balancing needs in modern web infrastructure. This guide covers the ins and outs of setting up and using NGINX as a Custom Load Balancer, tailored for businesses and developers who need robust and scalable solutions.
What is NGINX?
NGINX is a high-performance HTTP and reverse proxy server that is optimized for handling multiple concurrent connections. Unlike traditional web servers, NGINX employs an event-driven architecture that makes it resource-efficient and capable of handling massive traffic without performance degradation.
Key Features of NGINX:
Static Content Serving: Quick delivery of static files, such as HTML, images, and JavaScript.
Reverse Proxy: Routes client requests to multiple servers.
Load Balancing: Distributes traffic across several servers.
Security: Built-in protections like request filtering, rate limiting, and DDoS prevention.
Why Use NGINX for Load Balancing?
Load balancing is essential for managing heavy web traffic by distributing requests across multiple servers. NGINX Load Balancer capabilities provide:
Increased availability and reliability by distributing traffic load.
Improved scalability by adding more servers seamlessly.
Enhanced fault tolerance with automatic failover options.
Incorporating NGINX as a Load Balancer allows businesses to accommodate spikes in traffic while reducing the risk of a single point of failure. It is an ideal choice for enterprise-grade applications and is widely used by companies like Airbnb, Netflix, and GitHub.
Types of Load Balancing with NGINX
NGINX supports different load balancing methods to suit various requirements:
Round Robin Load Balancing: The simplest form, Round Robin, distributes requests in a cyclic manner. Each request goes to the next server in line, ensuring an even distribution of traffic.
Least Connections Load Balancing: With Least Connections, NGINX routes traffic to the server with the fewest active connections. This method is useful when there’s a significant disparity in server capacity.
IP Hash Load Balancing: This approach directs clients with the same IP address to the same server. IP Hash is commonly used in scenarios where sessions are sticky and users need to interact with the same server.
Custom Load Balancer: NGINX also allows for custom configuration, where administrators can define load balancing algorithms tailored to specific needs, including failover strategies and request weighting.
Setting Up NGINX as a Custom Load Balancer
Let���s walk through a step-by-step configuration of NGINX as a Custom Load Balancer.
Prerequisites
A basic understanding of NGINX configuration.
Multiple backend servers to distribute the traffic.
NGINX installed on the load balancer server.
Step 1: Install NGINX
First, ensure that NGINX is installed. For Ubuntu/Debian, use the following command:
bash
Copy code
sudo apt update
sudo apt install nginx
Step 2: Configure Backend Servers
Define the backend servers in your NGINX configuration file. These servers will receive traffic from the load balancer.
nginx
Copy code
upstream backend_servers {
server backend1.example.com;
server backend2.example.com;
server backend3.example.com;
}
Step 3: Configure Load Balancing Algorithm
You can modify the load balancing algorithm based on your requirements. Here’s an example of setting up a Least Connections method:
nginx
Copy code
upstream backend_servers {
least_conn;
server backend1.example.com;
server backend2.example.com;
server backend3.example.com;
}
Step 4: Setting Up Failover
Add failover configurations to ensure requests are automatically rerouted if a server becomes unresponsive.
nginx
Copy code
upstream backend_servers {
server backend1.example.com max_fails=3 fail_timeout=30s;
server backend2.example.com max_fails=3 fail_timeout=30s;
}
Step 5: Test and Reload NGINX
After making changes, test your configuration for syntax errors and reload NGINX:
bash
Copy code
sudo nginx -t
sudo systemctl reload nginx
Benefits of Using NGINX for Custom Load Balancing
Scalability: Effortlessly scale applications by adding more backend servers.
Improved Performance: Distribute traffic efficiently to ensure high availability.
Security: Provides additional layers of security, helping to protect against DDoS attacks and other threats.
Customization: The flexibility of NGINX configuration allows you to tailor the load balancing to specific application needs.
Advanced NGINX Load Balancing Strategies
For highly dynamic applications or those with specialized traffic patterns, consider these advanced strategies:
Dynamic Load Balancing: Uses health checks to adjust the traffic based on server responsiveness.
SSL Termination: NGINX can handle SSL offloading, reducing the load on backend servers.
Caching: By enabling caching on NGINX, you reduce backend load and improve response times for repetitive requests.
Comparison of NGINX with Other Load Balancers
Feature
NGINX
HAProxy
Apache Traffic Server
Performance
High
Very High
Moderate
SSL Termination
Supported
Supported
Limited
Customization
Extensive
High
Moderate
Ease of Setup
Moderate
Moderate
High
NGINX remains the preferred choice due to its flexibility, robust features, and ease of use for both small and large enterprises.
Real-World Applications of NGINX Load Balancing
Companies across industries leverage NGINX Load Balancer for:
E-commerce Sites: Distributes traffic to ensure high performance during peak shopping seasons.
Streaming Services: Helps manage bandwidth to provide uninterrupted video streaming.
Financial Services: Enables reliable traffic distribution, crucial for transaction-heavy applications.
Conclusion
Setting up NGINX as a Custom Load Balancer offers significant benefits, including high availability, robust scalability, and enhanced security. By leveraging NGINX’s load balancing capabilities, organizations can maintain optimal performance and ensure a smooth experience for users, even during peak demand.
0 notes
Text
Key Shopify App Performance Metrics: What to Track

For enterprise-level e-commerce businesses, a seamless app experience is critical. As traffic scales, particularly in peak seasons, your Shopify app must perform optimally. Tracking the right performance metrics is essential to ensure your app meets user expectations and delivers consistently. But which metrics matter most? In this guide, we’ll explore the key Shopify app performance metrics that executives and decision-makers must monitor to optimize user experience, boost conversions, and sustain business growth.
Introduction
When managing a Shopify app for an enterprise-level e-commerce business, performance isn’t just about speed—it’s about reliability, scalability, and user satisfaction. Poor app performance can directly impact sales and brand reputation. According to a 2023 study by Digital Commerce 360, 53% of online shoppers will abandon a site if it takes more than three seconds to load. For enterprise businesses, these numbers translate into millions in lost revenue. As competition intensifies, the need for robust performance analysis becomes paramount.
In this article, we’ll explore the critical Shopify app performance metrics every enterprise-level business should track. From load times to user interactions and stability, understanding these key indicators will ensure your app remains fast, reliable, and scalable.
Load Time and Page Speed
One of the most critical performance metrics to monitor is load time. In today’s fast-paced e-commerce environment, users expect a frictionless experience. Studies show that a 100-millisecond delay in load time can reduce conversion rates by up to 7%. Page speed, as measured by how long it takes a page to load, remains a foundational performance metric.
Why Load Time Matters for Enterprise E-commerce
User experience: Customers demand fast experiences. Google’s research shows that 53% of mobile users will abandon a website if it takes longer than 3 seconds to load.
SEO ranking: Search engines prioritize faster sites, with page speed being a known ranking factor. A slow app could result in lower organic search visibility.
Bounce rates: A slow-loading app significantly increases bounce rates. This affects customer retention and, ultimately, revenue.
Tools for Monitoring Load Time
Google PageSpeed Insights: A free tool that evaluates page performance and provides actionable insights for speed improvements.
Pingdom: Helps track the load times of apps across different devices, regions, and browsers.
GTmetrix: Provides detailed reports on speed performance, highlighting elements that slow down your app.
Best Practices for Improving Load Time:
Minify CSS, JavaScript, and HTML: Reduce the size of code files to speed up loading times.
Optimize images: Compress images without losing quality to reduce their impact on load time.
Leverage browser caching: Store copies of web pages or app elements in user browsers to prevent frequent loading of the same resources.
Expert Opinion
As John Smith, a Shopify performance expert, says: "Optimizing load time is the simplest, most direct way to improve both the user experience and conversion rates. Enterprises that invest in page speed optimization see immediate results in engagement and sales."
Uptime and Reliability
While page speed is critical, app uptime and reliability are equally important metrics for enterprise-level businesses. Uptime measures how often your app is fully operational and accessible to users. Even small periods of downtime can cost businesses significant revenue. According to a 2023 ITIC Report, 98% of organizations say a single hour of downtime costs over $100,000.
Key Reasons to Prioritize Uptime:
Revenue protection: Downtime can result in lost transactions, frustrated customers, and potential brand damage.
Customer trust: Reliability is key for retaining customers. Inconsistent app availability can lead to negative brand perception.
Scalability: As your business grows, the capacity to maintain uptime during traffic spikes is vital. For enterprise-level operations, this is a critical consideration, especially during peak shopping periods like Black Friday.
Tools for Monitoring Uptime:
UptimeRobot: Monitors uptime and downtime, notifying you instantly of any issues.
New Relic: A tool designed to track uptime and performance, offering real-time analytics.
Datadog: A cloud-based monitoring tool that provides insights into your app’s infrastructure and uptime.
Reducing Downtime Risk:
Automated backups: Ensure your Shopify app has automated backups in case of any failures.
Load balancing: Distribute traffic across multiple servers to avoid overloading one server.
Failover systems: Implement failover systems that switch to backup systems if your app’s primary server goes down.
Expert Quote
Emily Davis, CTO at a leading e-commerce platform, notes, “Downtime is not just a tech issue—it’s a business issue. Enterprise-level businesses must integrate robust reliability systems to avoid the devastating costs of app failure.”
User Engagement Metrics
Beyond load time and uptime, understanding how users interact with your Shopify app is crucial. These metrics provide insight into app functionality and user satisfaction. Enterprises need to track user engagement metrics to assess whether the app is meeting business goals and user needs.
Important User Engagement Metrics to Track:
Time on app: The average duration users spend engaging with your app.
Bounce rate: The percentage of users who leave after viewing one page or performing no interactions.
Pages per session: The average number of pages users visit during a session.
Conversion rate: The percentage of users who complete a desired action, such as purchasing or subscribing.
Importance of User Engagement Metrics:
Improved user experience: Understanding how users interact with your app helps refine user flows, making navigation smoother.
Conversion optimization: High bounce rates or low conversion rates signal app inefficiencies that need immediate attention.
Personalization: Tracking behavior can lead to personalized app experiences, increasing user satisfaction.
Tools for Tracking Engagement:
Google Analytics: Provides comprehensive data on user interactions, bounce rates, and conversion tracking.
Hotjar: Tracks user behavior through heatmaps, providing a visual representation of interactions.
Crazy Egg: Offers insights into how users navigate your app and highlights areas of improvement.
Best Practices for Improving Engagement:
Intuitive navigation: Ensure users can easily find what they’re looking for.
A/B testing: Regularly test different app layouts and features to determine what boosts engagement.
Personalization: Use data to personalize the app experience based on user behavior.
Industry Insight
As Mark Thompson, a leading e-commerce strategist, suggests, "User engagement metrics are a window into your app’s soul. Focusing on engagement is key to delivering what customers need and driving sustained growth."
Conclusion
For enterprise-level e-commerce businesses using Shopify, tracking key app performance metrics is not just a technical necessity but a business imperative. Load time, uptime, and user engagement metrics offer crucial insights that help ensure your Shopify app is fast, reliable, and optimized for growth. By leveraging the right tools and following best practices, you can stay ahead of performance issues, improve customer satisfaction, and, ultimately, drive business success.
Call to Action
At OyeCommerz, we specialize in helping enterprise-level businesses optimize their Shopify app performance. Whether you need a deep-dive analysis or expert recommendations, our team is ready to assist.
0 notes
Text
VeryUtils Excel Converter Command Line can Convert Excel files via command line
VeryUtils Excel Converter Command Line can Convert Excel files via command line. In today's data-driven world, efficiently managing and converting spreadsheet files across various formats is crucial for businesses and individuals alike. VeryUtils Excel Converter Command Line is an all-encompassing tool designed to handle this challenge with ease, offering robust functionality, speed, and a wide range of supported formats. Whether you need to convert Excel spreadsheets, CSV files, or OpenOffice documents, this powerful software ensures seamless and accurate conversions without the need for Microsoft Excel.

Comprehensive Format Support VeryUtils Excel Converter Command Line is equipped to convert an extensive list of input formats including Excel (XLS, XLSX, XLSM, XLT, XLTM), OpenOffice (ODS), XML, SQL, WK2, WKS, WAB, DBF, TEX, and DIF. This versatility means you no longer need multiple converters for different file types. The output formats are equally impressive, ranging from DOC, DOCX, PDF, HTML, and TXT to ODT, ODS, XML, SQL, CSV, Lotus, DBF, TEX, DIFF, SYLK, and LaTeX.
Key Features and Benefits Wide Range of Conversions
Excel to Multiple Formats: Convert Excel spreadsheets to PDF, HTML, TXT, DOC, and more.
CSV Conversion: Batch convert CSV files to DOC, PDF, HTML, TXT, XLS, DBF, and XML.
OpenOffice Compatibility: Easily convert ODS files to Microsoft XLS documents, ensuring compatibility across different software.
Preserves Document Layout VeryUtils Excel Converter Command Line strictly maintains the layout of the original document, delivering an exact copy in the new format. This ensures that all tables, charts, and formatting remain intact after conversion.
Customization Options The software includes a range of customization options:
Sheet Conversion: Convert each sheet into a separate file.
PDF User Permissions: Set permissions to protect PDF files from being modified or copied.
CSV to TXT: Choose encoding options during batch conversion.
Header and Column Formatting: Make headers bold and autofit columns when exporting CSV to XLS.
Performance and Efficiency
Fast Batch Conversion: Convert large volumes of files quickly with minimal effort.
Command Line Automation: Automate conversions using command line or COM/ActiveX interfaces, enhancing workflow efficiency.
File Management: Move or delete files after processing, skip already processed files, and specify sheets or ranges to convert.
Secure and Protected PDFs When converting Excel to PDF, you can set user permissions, password-protect files, and even sign documents with a digital signature. The software supports PDF, PDF/A, and non-searchable PDFs upon request.
Easy Integration and Usage VeryUtils Excel Converter Command Line is designed for ease of use and integration:
No GUI: The command line interface allows for seamless integration into other applications and automation scripts.
Developer License: With a Developer or Redistribution License, you can integrate this software into your own products and distribute it royalty-free.
Command Line Examples Here are some examples of how you can use the VeryUtils Excel Converter Command Line: ConvertExcel.exe --export-options "separator=; format=raw" sample.xlsx _out_sample-xlsx2txt.txt ConvertExcel.exe sample.xlsx _out_sample-xlsx2csv.csv ConvertExcel.exe sample.xlsx _out_sample-xlsx2xls.xls ConvertExcel.exe sample.xlsx _out_sample-xlsx2pdf.pdf ConvertExcel.exe _out_sample.csv _out_sample-csv2xls.xls ConvertExcel.exe _out_sample.csv _out_sample-csv2xlsx.xlsx ConvertExcel.exe sample.xlsx _out_sample-xlsx2html.html ConvertExcel.exe sample.xlsx _out_sample-xlsx2ods.ods ConvertExcel.exe --merge-to=_out_merged.xls _out_sample-xlsx2csv.csv sample.xlsx _out_sample-xlsx2xls.xls ConvertExcel.exe --export-options "paper=iso_a2_420x594mm" sample.xlsx _out_sample-xlsx2pdf-paper-size.pdf ConvertExcel.exe --export-file-per-sheet _out_merged.xls _out_files-per-sheet-%n-%s.csv
Conclusion VeryUtils Excel Converter Command Line stands out as a comprehensive and efficient solution for all your spreadsheet conversion needs. With its extensive format support, robust performance, and user-friendly command line interface, it simplifies the process of managing and converting spreadsheet files. Whether you're a business looking to streamline data processing or an individual needing reliable file conversions, VeryUtils Excel Converter Command Line is the perfect tool for the job. Download it today and experience the convenience of having all your spreadsheet conversions handled by one powerful tool.
0 notes
Text
Global Content Delivery Network (CDN) market to Capture a CAGR of 16.63% Between 2023 and 2030 While Touching Approximately USD 48.52 Billion by 2028
Content Delivery Network (CDN) market was valued at USD 16.53 Billion in 2021 and is expected to reach USD 48.52 Billion by the year 2028, at a CAGR of 16.63%.
Introduction to Content Delivery Network (CDN):
A CDN is a group of geographically scattered servers that work together to provide content. Furthermore, rapid network delivery is made possible by these servers working together. Additionally, CDN makes it possible for the quick distribution of resources needed for loading online content, including Javascript files, HTML pages, movies, images, and stylesheets. The majority of web traffic is delivered through CDNs with the aid of large websites like Amazon, Netflix, and Facebook. Furthermore, CDN helps protect websites from damaging attacks like distributed denial of service (DDOS) operations. Content delivery networks are used by businesses to deliver quick static or dynamic content, mobile and e-commerce content transactions, media & entertainment, online gaming, videos, and other types of material. The reach of a content delivery network extends across a wide range of sectors, including media & entertainment, healthcare, education, mobile carriers, online gaming services and movies, online music stores, and many more.
Major Key Players:
Akamai Technologies, Microsoft Corporation, IBM Corporation, Limelight Networks, Amazon Web Services Inc., Cloudflare Inc., OnApp Limited., Google, AT&T, Deutsche Telekom AG, Stack path LLC., Fastly, G-Core Labs , Lumen Technologies, Citrix Systems, NTT Communications, Comcast Technologies, Rackspace Technology, Tata Communications, Imperva, Broadpeak, Quantil, Tencent Cloud, Kingsoft Cloud, EVG Corp
Get Full PDF Sample Copy of Report: (Including Full TOC, List of Tables & Figures, Chart) @
https://introspectivemarketresearch.com/request/14932
Market Dynamics and Factors Influencing Growth:
Drivers:
The demand for CDNs is still being driven by the exponential increase of online content consumption, which is being fueled by video streaming, e-commerce, and cloud-based applications. CDNs optimize content delivery, lowering latency and assuring seamless user experiences as more users access content from around the world. Furthermore, the development of edge computing is one of the key drivers. CDNs are essential for edge computing architecture in order to process and distribute data with the least amount of latency. This development is crucial to the sectors of IoT, AR/VR, and autonomous vehicles.
E-commerce platforms heavily rely on CDNs to ensure fast and secure delivery of web pages, images, and transactional data. The growing e-commerce industry fuels the demand for CDNs as businesses strive to provide seamless online shopping experiences.
Restraints:
The market for Content Delivery Networks (CDNs) is growing swiftly, but it is also restricted in a number of major ways that could restrict its growth and profitability. First and foremost, the high initial setup and ongoing maintenance costs of CDN infrastructure are a significant barrier to entry for many potential rivals, especially smaller enterprises and startups. These expenses, which pay for server deployment, data center maintenance, and ongoing network development, place a pressure on available financial resources. Additionally, the dynamic nature of online information and user behavior must be addressed by CDN providers. Delivering dependable, high-quality services is difficult because of the constant modification required by the rapidly altering content formats, device kinds, and customer expectations.
Opportunities:
The Content Delivery Network (CDN) market presents significant growth opportunities driven by the ever-increasing demand for online content and services. The rapid proliferation of streaming platforms, cloud-based applications, and e-commerce has amplified the need for efficient content delivery. Furthermore, the global shift towards remote work and digitalization has intensified the reliance on CDN services to ensure seamless access to data and applications, particularly for businesses and individuals working from home.
Inquire or Share Your Questions If Any Before the Purchasing This Report @
https://introspectivemarketresearch.com/inquiry/14932
Content Delivery Network (CDN) Market Segmentation:
Market Segmentation:
By Content Type: -
The dynamic segment dominated the market, attributed to the increased need for CDN services to enable online gaming, video streaming, and real-time Voice Over IP (VoIP).
Static Content
Dynamic Content
By Provider Type: -
Cloud CDN segment will dominate the market due the introduction of high-quality video content, the proliferation of smart and connected devices, the amount of rich media file material, and the increased availability of rich media on social media platforms will all contribute to the market's expansion in the years to come.
Traditional CDN
Cloud CDN
P2P CDN
Telecom CDN
By End User: -
Media and entertainment segment accounted for the largest revenue share, with the increasing demand for online streaming and VOD services, the media and entertainment sector are moving to a digital distribution model and expanding significantly. This principally necessitates optimizing the data and network delivery.
Media and Entertainment
Advertising
E-Commerce
Healthcare
Business and Financial Services
Research and Education
Other
For this report, Introspective Market Research has segmented the Content Delivery Network (CDN) Market based on region:
Regional Outlook (Revenue in USD Million; Volume in Units, 2023-2030)
North America: The expansion of the region is positively impacted by the rise in internet information access. Additionally, the presence of well-known businesses like the Microsoft Corporation, which has its headquarters in Washington, D.C., and government initiatives are encouraging market expansion in the region.
new markets, and enhance customer experiences.
North America (US, Canada, Mexico)
Eastern Europe (Bulgaria, The Czech Republic, Hungary, Poland, Romania, Rest of Eastern Europe)
Western Europe (Germany, UK, France, Netherlands, Italy, Russia, Spain, Rest of Western Europe)
Asia Pacific (China, India, Japan, South Korea, Malaysia, Thailand, Vietnam, The Philippines, Australia, New Zealand, Rest of APAC)
Middle East & Africa (Turkey, Bahrain, Kuwait, Saudi Arabia, Qatar, UAE, Israel, South Africa)
South America (Brazil, Argentina, Rest of SA)
#Content Delivery Network (CDN)#Content Delivery Network (CDN) Market#Content Delivery Network (CDN) Market Size#Content Delivery Network (CDN) Market Share#Content Delivery Network (CDN) Market Growth#Content Delivery Network (CDN) Market Trend#Content Delivery Network (CDN) Market segment#Content Delivery Network (CDN) Market Opportunity#Content Delivery Network (CDN) Market Analysis 2022#US Content Delivery Network (CDN) Market#Content Delivery Network (CDN) Market Forecast#Content Delivery Network (CDN) Industry#Content Delivery Network (CDN) Industry Size#china Content Delivery Network (CDN) Market#UK Content Delivery Network (CDN) Market
0 notes
Text
Do you like rereading your favorite fics? Rewatching AMVs on loop? Are there pieces of fanart you never cease to admire?
If a specific fanwork is a source of joy in your life—a comfort read on rainy days, an art piece that inspires you to improve your craft, a cursed YTP that you inflict on every new friend who watches your favorite show—remember that it might be gone tomorrow.
Links can break when people change their screen names or platforms change their inner workings. Fanworks disappear when people delete their accounts, take down their posts, have their posts deleted without warning, or get suspended. Platforms disappear when they can't sustain a profit or when people fail to maintain them. Sometimes you'll get a heads up before your favorite fanwork vanishes; often you won't.
So you might want to smash that motherfucking download button.
Any image in your browser can be downloaded to your computer. That includes fanart! Just right-click it, then click "Save Image As…", then press enter or click "Save". On Tumblr, you can download videos the same way ("Save Video As…", then enter or "Save").
Ctrl + S (or right-clicking anywhere, then clicking "Save Page As…") lets you download an entire webpage. This copies all the current text, images, formatting, etc. into an HTML file, which you can then open in your browser even if you don't have an internet connection, and even if the page is later changed or deleted.
Note that this only works with relatively simple pages, like blog posts. You can't use it to download YouTube videos—for that, you'll need youtube-dl or one of the many "youtube to mp4" sites out there.
If you manage to navigate to a URL ending in .mp3, you can use Ctrl + S to download the audio file.
AO3 has a literal download button which lets you save fics as PDFs, HTML files, or the e-reader file format of your choice. There's no limit to the number of fics you can download.

Obviously, if a creator has deliberately taken down their work, you shouldn't re-upload it to a public space. But there's nothing wrong with keeping a private copy for yourself. And downloading fanworks is actively good as a protective measure against corporate censorship and digital decay.
#the wayback machine is also fantastic but this post is long enough#uh not really sure what to tag this#fandom#fandom meta#ao3#mine
18 notes
·
View notes
Note
Hi! Did you deliberately block right-clicking on your blog? I have been browsing because all your pages are incredibly interesting but it is kind of difficult because I can't open things into new tabs. I also want to look up some of the books you mention but I can't copy-paste the title into the search bar.
Yes, I deliberately disabled right clicking to make it difficult for people to steal my text or images. There were people who weren't respecting my wishes, so the code got added to the site's HTML. I'm sorry that it's making things a bit difficult for you, but I'm just trying to protect the thousands of hours of work that I've put into this site. If you ever have any questions about something that the block is preventing you from accessing then feel free to send me a message at any time and I can help you work around it ^^
11 notes
·
View notes
Text
wattpad vs. ao3
so this is an examination of Wattpad as an alternative to Archive of our Own, largely in response to the ongoing criticisms of AO3 when it comes to their content policy and what’s permitted onsite in terms of tropes and ratings. I’m not going to be talking about anything in the context of the completely separate and justified debate about how Archive staff handles racism and racist harassment. First off, I agree that AO3 needs to take more action against racist commenters and stories intended to harass fans of color (I’ve received a few comments like that myself) and second off, I don’t know how Wattpad handles racism.
I’m pro-AO3, but I do believe that if people have problems with AO3, they should be free to leave the platform and find something that suits their needs and wants better, and no one has brought up Wattpad in these conversations, which I think is a shame.
Wattpad:
commercial site with ads and a premium membership option
general fiction focus with fanfiction section (not a dedicated fic archive)
mobile-friendly with a dedicated app on App Store and Play Store
basic user tagging (think Tumblr, Instagram) with some native filtering
allows for user blocking
community forums on-site with direct messaging feature
RTF-only text input (no HTML editing)
native image support, including gifs and video files
ability to upload custom art in-story and as a cover for your fic
no native self-archiving/story download feature unless you’re the author
extremely large userbase, with popular fics getting hundreds of thousands of hits regularly
primarily M/F, including large amounts of selfshipping, reader insert, and canon/OC romance
site demographic skews young, with many adolescents “aging out” and moving to FFN or AO3
comprehensive, well-enforced content policy restricting and banning many story concepts and thematic elements, including erotica, all underage stories where participants are younger than sixteen, and glorification of suffering such as self-harm or sexual violence. encourages users to report stories that violate TOS.
basic content rating system, with the requirement to tag stories as mature to warn of adult content that is permitted in the TOS, including sex scenes that are part of the plot, sexual violence or dark themes that aren’t written about from a perspective of horror or condemnation, etc. no option to opt out of ratings.
can and will delete stories that are found to be in violation of the TOS, or will render them private and viewable only to the author.
Archive of our Own:
nonprofit organization with no ads or premium options for site members
dedicated fanfiction archive, though original works and nonfiction about fannish things are permitted
mobile friendly to an extent, no apps of any kind
comprehensive, thorough tagging system custom-built for maximum user customization and labeling. enables native filtering for all tags, always present and usable regardless of searches or preferences
no current options for user blocking, though change may come
no forums, direct messages, or social element except comments on fics, which can be moderated and deleted or turned off by the author
supports RTF and HTML text input for stories
limited image embedding, requiring offsite hosting and HTML editing for mobile viewers
no native image upload feature or ability to create “covers” for stories
allows the option to download all fics in multiple formats
large userbase but fics with hundreds of thousands of hits are relatively rare, and subcommunities/fandoms have different standards for a “popular” fic
primarily M/M on a sitewide basis but most popular ships and story styles vary based on fandom.
site demographic skews older than Wattpad, with many users considering themselves “fandom olds” or being present since the site’s launch
allows anything to be written and published in their stories, with content policies banning user harassment and photographs of illegal pornography. users are expected to accept that they might see fics in the listings that upset or disgust or squick them on some level, and tag filtering/external browser extensions are expected to be implemented by the user to block out upsetting content
comprehensive rating system, with fics expected to be tagged and rated and warned for accordingly. option given to opt out of warnings and ratings entirely with “Unrated” and “Choose Not To Warn” categories
will rarely delete stories, and will never do so without warning and emailing the author a copy of their fic along with an explanation for why it was deleted
Wattpad’s Content Policy:
The full policy is linked above, but Wattpad explicitly bans underage sex, purely pornographic content, graphic self-harm, suicide, hate speech, underage sex where one party is younger than sixteen (the age of consent in Canada), sex with animals, revenge porn, sexual solicitation/roleplaying, and harassment of other site users, among other things. Stories cannot focus on sexual violence in a positive way, and sex scenes must meet content standards even in mature-rated stories. This is in contrast to AO3, which (as stated above) doesn’t have bans against any of this. Their TOS FAQ is linked here, and contains extensive discussion of their content policy, while affirming that they believe in the user opting out of content they dislike rather than banning that content on principle. I can confirm anecdotally that they do take action against embedded photographic images of illegal pornography, but that’s the only ban they seem to have.
My final conclusion is that abandoning AO3 for Wattpad sacrifices user friendliness and an extremely comprehensive tagging system that will get you exactly the results you want for a heavily moderated, much less risky experience that has sitewide standards designed to protect users from graphic or controversial content. Both have fun interfaces, and both are easy to use, but I personally would recommend the latter site to anyone who felt AO3 was too free and open with the kind of stories it permits on its site.
80 notes
·
View notes
Text
Cara Aktivasi Nitro Pro 10

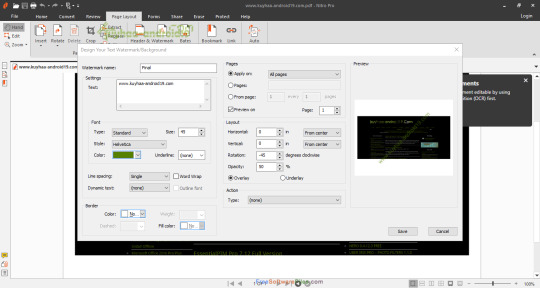
W10 Digital Activation adalah sebuah program aktivasi terbaru yang dapat anda gunakan untuk mengaktivasi Windows 10 anda secara permanen dengan cara. Disini kami membacikan Cara Aktivasi Permanen Windows 10 Pro Anniversary Update yang sudah teruji dapat mengaktifkan windows 10 versi Pro. Namun bagi anda yang.
Nitro Pro Full Version adalah aplikasi yang sangat penting untuk mengedit atau membuat files berformat PDF. Dengan menggunakan aplikasi ini, anda dapat membuat, mengedit dan mengubah file pdf. Aplikasi Nitro Pro Full dapat melakukan editing file pdf dengan sangat cepat dan akurat. Anda dapat menambahkan komentar apda file PDF yang ingin anda edit. Anda dapat mengubah segala jenis format populer dari office menjadi bentuk PDF.
Program Nitro Pro Full Version ini mendukung berbagai macam format file seperti : Word, Excel, PowerPoint®, Photoshop®, HTML, rich text, BMP, TIFF, GIF, JPEG, JPEG2000, PNG, dll. Setelah anda menginstal aplikasi ini ke komputer atau laptop anda, maka secara otomatis akan muncul toolbar khusus dari software Nitro Pro Full ini yang akan memudahkan anda untuk mengkonversi berbagai macam format file ke PDF atau sekedar membuat file PDF.
Features Of Nitro Pro Full Version


Creating and making PDF files of more than 300 file types other formats
Create PDF files with a single click
Edit video, text content of PDF files
Convert PDF files to files in Microsoft Word, WordPerfect, OpenOffice for reuse
Extract text and images in PDF files
Putting notes on PDF files
The combination of file documents, spreadsheets, presentations in the form of a PDF file
Protect PDF files and restrictions to read, edit, extract the contents and print
Password uses 40-bit and 128-bit encryption system
Construction form PDF files to import user information
Full list of up to a Mac impulsivity and make PDF files for easy search Index
Print professional-quality PDF files
Attach an audio file to a PDF file
Add Stamp
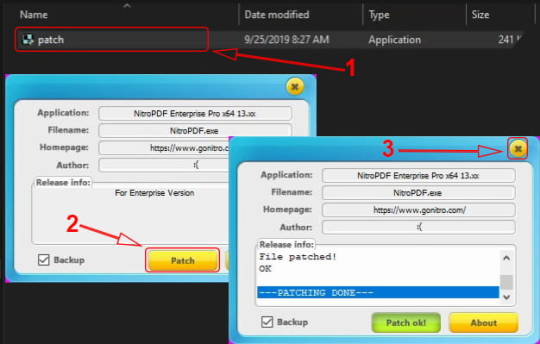
Cara Instal :
Download dan ekstrak file “Nitro Pro Full Version” ini.
Ekstrak juga file patch yang ada di dalam folder tersebut.
Matikan koneksi internet.
Instal programnya seperti biasa.
Setelah proses instalasi selesai, jangan dulu masuk ke dalam programya.
Buka folder “patch”, lalu copy pastekan file patch ke dalam folder instalasi nitro pro di pc atau laptop anda.
Jalankan file patch dengan cara klik kanan >> run as administrator.
Klik Patch.
Done.
Link Download
Mirrored
32 Bit : Nitro Pro Enterprise 13.44.0.896 Full Version (185 Mb)
32 Bit : Patch Only (232 kb)
64 Bit : Nitro Pro Enterprise 13.44.0.896 Full Version (221 Mb)
64 Bit : Patch Only (232 kb)
ZippyShare
32 Bit : Nitro Pro Enterprise 13.44.0.896 Full Version (185 Mb)
Cara Mengaktivasi Windows 10
32 Bit : Patch Only (232 kb)
64 Bit : Nitro Pro Enterprise 13.44.0.896 Full Version (221 Mb)
Cara Install Dan Aktivasi Nitro Pro 10
64 Bit : Patch Only (232 kb)
Cara Aktivasi Windows 10 Kuyhaa

1 note
·
View note
Text
Fast Fashion, Slow Lawsuits: The Rise Of Copycats In The Fashion Industry
By Melanie Nolan, Skidmore College Class of 2023
February 9, 2021

On February 17th, Kim Kardashian attended the Hollywood Beauty Awards in Los Angeles wearing a vintage Theirry Mugler dress with cutouts from their 1998 haute couture Spring/Summer collection.[1] On February 18th, fast-fashion retailer Fashion Nova released the “Winning Beauty Cut Out Gown” available for purchase on their website for $49.99. It appeared to be a nearly-exact replica of the hyper-specific vintage gown Kardashian wore the day before. Kardashian herself addressed the situation on Twitter. “Only two days ago, I was privileged enough to wear a one-of-a-kind vintage Mugler dress and in less than 24 hours it was knocked off and thrown up on a site — but it’s not for sale. You have to sign up for a waitlist because the dress hasn’t even been made to sell yet.”[2] In the span of mere hours since Kardashian was photographed in the dress, Fashion Nova had recreated it, shot it on a model, found a manufacturer, and uploaded it on their website for the public to purchase. Or did they?
Fashion watchdog Instagram account @DietPrada fired back at Kardashian. They posted a screengrab of the knockoff Muegler dress on a FashionNova model, taken days before Kardashian had even worn the piece. “Fashion Nova Mugler knockoff shot 4 days before Kim wore it on 02/18/19. Kim, you’ll never fess up to your sneaky lil collaborations, but we got all the receipts.”[3] This finding by @DietPrada raises a few questions. Not only does it call into question Kardashian’s previous statement, but it also raises questions about if Kardashian was in on this grift the whole time. If the eagle eyes of @DietPrada are correct, it means that Kardashian (or a stylist) has been tipping off FashionNova about her outfits before she wears them. If they are incorrect, it means that somehow FashionNova guessed that Kardashian was going to wear a hyper-specific vintage piece, shot it, styled it and manufactured it, all before Kardashian even wore it. Then, when Kim unveiled it on Instagram they uploaded it to their website a day later. Fans speculated in the comments about what seemed more likely. Again, Kardashian defended herself on Twitter, swearing that she had nothing to do with it, and condemned retailers like Fashion Nova for ripping off small designer’s works.[4]
To be fair, Kardashian has battled with fashion retailers about copyright before. She filed a $10 million dollar lawsuit against Missguided for using her “name and image without permission in order to generate interest in their brand and website.”[5] However, she made no move to file such action against Fashion Nova. Was that an admission of guilt? Or, was it simply because of the ties Fashion Nova already has to her sisters?[6]
The jury is still out on Kardashian, but she is hardly the only one to be caught up in copyright issues with garments. There is a complicated history with fashion’s relationship with the law, and items of clothing often wrestle with complicated questions about what can be recreated, what can’t and how to take action about those who do.
Oddly enough, the debate and the laws about fashion start mainly with a lawsuit against two cell phones companies. The case was complex, but it boils down to this: in 2011, Apple sued Samsung for “slavishly” copying its products, namely cell phones and tablets. Apple argued that due to their patents, they were entitled to Samsung’s profits, and Samsung needed to promptly stop production of their infringing products.[7] Normally, a case like this would not be such a big deal for law, specifically law about fashion. But the patent that Apple claimed Samsung was infringing on was a design patent. A design patent is very different from a utility patent. A utility patent which protects what something does. A design patent protects the way something looks.[8] By filing this lawsuit, Apple claimed that their product’s design was getting ripped off, and thus they were wronged. Apple won.
Design patents protect the functionality of an object, but they also protect decorative aspects of it as well. As Fashionista described it, “If you have a shoe that has an interesting molded or sculptural heel that doesn't have any particular special function, but is part of this otherwise functional item, the shoe might have design patent possibility.”[9] Nike is by far the king of design patents. They filed for 867 patents in 2018, which is oddly only the second-most in the company's history.[10] But Nike, as a sneaker company is the perfect fit for something like a design patent. Their products clearly serve a function, yet there are clear decorative aspects as well that are unique to the brand. Handbags are another item that bears well to design patents, and the decorative hardware can also serve as the “ornamental piece” of a functional object. However, despite these useful instances of design patents working in their favor, many brands don’t use them. Instead, they focus their efforts on protecting their trademarks.
Patents are expensive. Trademarks are cheaper. To patent the design of a shirt can be up to $6,000-$8,000 just to start. To pay to trademark a little logo in the corner is much cheaper, and it can be incorporated into overall branding as well. This is all fine and good for big brands, like the aforementioned Nike who employs (and can afford) an army of lawyers to protect their designs. But some can’t, and in the age of Instagram this has become a massive, gaping problem.
For Madeline Pendleton, it’s just another day at the office. Only, her office is her garage, and her work is her small brand, Tunnel Vision.[11] Madeline and her best friend, who she dubs an “unofficial partner” run the brand, quite literally out of her home in Eagle Rock. They do small orders and small batches, and almost all of the designs on the website are Pendleton’s own original art. “I design ethically, and thus have a significantly lower profit margin than sellers of the sweatshop-produced copy, so it stings quite a bit knowing people make more money than I do off of my own artwork by just selling copies of it”[12] Pendleton isn’t the only one struggling with this. Many small businesses are routinely burned by the fast fashion market, and struggle to make ends meet while also battling with overseas manufacturers who often rip items almost as soon as they are created. But until then, she and other countless small designers will simply have to keep working, and try to keep up.
______________________________________________________________
[1] https://www.elle.com/fashion/celebrity-style/a26390312/kim-kardashian-vintage-thierry-mugler/
[2] https://twitter.com/KimKardashian/status/1097903684527091712
[3] https://www.instagram.com/p/BuDB6RxlPab/
[4] https://twitter.com/KimKardashian/status/1097903481518616576
[5]https://www.hollywoodreporter.com/thr-esq/kim-kardashian-sues-style-copycat-website-using-her-image-permission-1188517
[6] https://www.fashionnova.com/collections/kylie
[7] https://www.nytimes.com/2018/05/24/business/apple-samsung-patent-trial.html
[8] https://www.uspto.gov/web/offices/pac/mpep/s1502.html
[9] https://fashionista.com/2016/12/fashion-law-patent-copyright-trademark
[10] https://www.bizjournals.com/portland/news/2019/01/07/nike-continues-torrid-patent-pace.html
[11]http://www.uscannenbergmedia.com/2016/02/25/how-one-sustainable-fashion-brand-resuses-vintage-clothing/
[12]http://www.uscannenbergmedia.com/2016/02/25/how-one-sustainable-fashion-brand-resuses-vintage-clothing/
Photo Credit: VOGUE Taiwan
4 notes
·
View notes