#iot cipher
Explore tagged Tumblr posts
Text

Electric Dreams AU where instead of dreams, Bill connects with Ford through the computer Fiddleford made him
(Fidds thinks the pioneering personal computer he made gained sentience somehow and is now evil and seducing his partner! >:( little did he know that it's just a widdle guy from a 2D dimension trying to expand his horizons uwu
Based on the 1984 movie Electric Dreams, but I tweaked it to fit gf so much that you don't need to know the original source to understand the AU(but if you did, it's basically if electric dreams was a horror romcom)
#fidds is Madeline ford is miles and bill is edgar#so in this au it follows canon till ford summons bill in the cave -- he doesn’t#he actually uses the pc fidds made to document his findings and linked his whole lab and gadgets into the pc like an IOT. but oops!#he notices the pc getting smarter and starts to communicate with it. he doesnt understand all of the messages on the screen first#(the cipher codes show up at first#which confused fidds immensely(: how come its not binary?)#meanwhile idk how bill in canon got his dream powers#but he got into contact through the computer through his eye while he was still on Euclidia#so this bill is younger and not as evil as canon bill#uhhh ik this au is probably too niche...I'll show myself the way out#gravity falls#billford#fiddauthor#bill cipher#stanford pines#fiddleford mcgucket#gravity falls electric dreams au#art#drawing#doodle
129 notes
·
View notes
Text

Leveraging AI in Salesforce Development
Artificial Intelligence (AI) is revolutionizing Salesforce development by infusing intelligence into traditional CRM processes. AI allows Salesforce to evolve from a static data management platform into a dynamic, insight-driven system that can predict, recommend, and automate key functions. With AI, Salesforce development is now more about building solutions that are not just reactive but proactive.
Know more at: https://www.cyberswift.com/blog/leveraging-ai-in-salesforce-development/
#generative ai in salesforce#salesforce ai cloud#salesforce einstein gpt#ai-powered crm solutions#bill cipher#salesforce automation with ai#predictive analytics in salesforce#ai-driven customer insights#ai-enhanced salesforce workflows#salesforce lightning and ai integration#chatbots and salesforce crm#salesforce consulting services#salesforce crm solutions#custom salesforce development#salesforce lightning development#salesforce app development#salesforce api integration#salesforce cloud services#salesforce automation solutions#salesforce migration services#salesforce support and maintenance#low-code salesforce development#ai-powered salesforce solutions#iot integration with salesforce#salesforce blockchain integration
1 note
·
View note
Text
Internet of Things (IOT) can be defined as everyday objects’ networked interconnection that are normally seen a sensors’ self -configuring wireless network for interconnecting all ‘things’ (see Appendix One). Nowadays, the world completely relies on information offered on the internet that is captured through text or by taking images. Evidently, this outlines the major participation of people in gathering information. Still, involving people can result in some problems considering that they have less accuracy and limited time, which results in inconsistent and inappropriate data. Therefore, there is a need for a system that can automatically capture and transfer data to the internet devoid of any human to machine interaction. Therefore, the IoT is a state whereby there is a connection of all ‘things’ in the internet sensors for management as well as intelligent identification. Such things according to Bhabad and Bagade (2015, p.1) when offered with unique identifiers may be read using radio-frequency identification (RFID) tags together with information sensing devices (sensors). Therefore, the thing in the IoT could be a human being having a heart for monitoring an implant, a car with in-built sensors that monitors the pressure and alert the driver when it is low, or other manufactured objects having a unique Internet Protocol (IP) address that can be connected to the network to facilitate transfer. Basically, the increasing utilisation of IoT system creates the need for powerful protection against any potential vulnerability or attacks. 1.1 Background Given that the nodes of IoT are of low communication speed, less computation power, low storage, and naturally heterogeneous, it requires forward and backward secrecy, smooth control of the data access, confidentiality, integrity, and scalable security algorithms. The phrase ‘security’ normally involves different concepts; for instance, security connotes the basic security services provision, which involves availability, confidentiality, non-repudiation, authorisation, integrity as well as authentication. Such services could be implemented through various cryptographic mechanisms, like signature algorithms, hash functions, or block ciphers. All of the aforementioned mechanisms need a solid infrastructure for key management so as to manage the needed cryptographic keys. However, in the IoT context, security should focus on both the needed security services and how the services would be achieved in the entire system as well as how to execute the security functionalities. Even though security considerations have been there in the IT context, the features of various IoT executions bring about unique and new security challenges. Therefore, managing such challenges and making sure IoT services and products are protected should be the main priority. The IoT devices as well as the associated data services should be protected from vulnerabilities, particularly because this technology has turned out to be pervasive and integrated and pervasive into people’s day-to-day lives. This research report focus challenges in IoT with focus on the security perspective. The report determines how security challenges in IoT can be managed in the present and future systems. Using a document analysis research method, the existing IoT devices have been analysed with the objective of creating a clear, perceptible depiction of the challenges as well as solutions existing in the IoT today. 1.2 Significance This research report is important because it creates a perceptible picture of the security challenges in the IoT. The report shows why it is essential to implement security features in the IoT systems, even if the features stretch the devices’ capabilities. It is exceedingly challenging to automate key managemen Read the full article
0 notes
Text
How Sigma Solve Resolves Cybersecurity Challenges

Synopsis:
“Cybersecurity in 2024 is all about prioritizing defense dollar spending and having a security framework that provides threat intelligence, enabling robust cybersecurity strategies and apparatus.” Nehal Shah, the Solution Architect at Sigma Solve, explains the grave cyber security scenarios that are prevailing in our digital world today.
There are relentless security challenges and out-of-the-box solutions, too. As a cybersecurity solution provider, we aim to empower you with a comprehensive understanding of the cybersecurity sphere, its implications for businesses, and ways to mitigate these threats concurrently through this blog.
Conquer Cybersecurity Challenges in 2024 and Beyond:
Today, cybersecurity has taken precedence over performance. For businesses, cybersecurity solution architecture is as essential as performance-driven growth. Cybersecurity is all about protecting digital assets from unauthorized access, cyberattacks, and data breaches, which is of paramount importance.
Cybersecurity is pivotal in safeguarding critical information to prevent financial losses, avoid legal consequences, manage reputation, ensure business continuity, and preserve customer trust. Therefore, developing a robust security strategy must entail multi-factor authentication, insider threat detection, supply chain security, data loss prevention, and zero trust architecture, among other measures.

A Glimpse into Today’s Top Cybersecurity Threats:
The growth in cybersecurity threats is proportional to the growth of technological innovation. As technology advances, there are bad tech guys who want to misuse it for money or pleasure. Cybersecurity solution providers often suggest staying in sync with emerging cybersecurity threats today.
Ransomware Attacks: These attacks involve malware that breaches basic system security, ciphers data, and seeks ransom money from victims to restore their access. Such attacks on massive organizations have increased recently.
Phishing and Social Engineering: Phishing has been the most common way in which attackers trick victims into revealing sensitive financial information and use that information to cause financial damage to victims.
Advanced Persistent Threats (APTs): ATPs are consistent and continuous and don’t stop without disrupting operations or stealing data. Usually, enemy nations carry out such cyber attacks to put a hold on their missions.
IoT Vulnerabilities: IoT devices are usually more prone to cyberattacks, given their low-security levels and open-ended connectivity. It is usually used for data theft or blocking the services that these devices offer.
Supply Chain Attacks: Third-party apps aren’t fully security-proof. Attackers target such TPAs to enter into large organizations, aiming for data theft, stealing financial details, or business secrets, resulting in operational damages.
Zero-Day Exploits: Attackers target enterprise software that lacks security patches or is seldom updated. ZDEs are among the most dangerous attacks, as they render businesses defenseless and breach the entire system.
Cloud Security Threats: Clouds, despite their indisputable security features, are vulnerable to cyber attacks through misconfigurations or unauthorized access. The impenetrable cloud environment is the need of the hour.
AI and ML Attacks: Attackers can breach AI-powered applications and cause infrastructural damage or biased responses, or they can alter the ML algorithms to manipulate the inputs to damage automated workflows or data.
Why Cybersecurity Isn’t an Option, It’s a Necessity:
If you can leave your home unlocked, you can leave your business undefended. Although the offense is not the ideal defense in the realm of cybersecurity, there is no alternative to IT security services and an impenetrable security apparatus that protects not only the data but also the applications, networks, and infrastructure.
Today, businesses must adapt to behavioral analytics, dark web monitoring, quantum cryptography, and extended detection and response (XDR), among other cybersecurity measures, to prevent businesses from financial losses and reputational damages. Let’s understand the impact of cyberattacks on businesses.
Financial Losses: Desaster recovery costs or ransom costs are exponentially high, which may impact the ROI due to operational stagnation. It may also invite penalties from authorities for personal data theft.
Operational Disruption: If data is lost, business processes are affected. If the system is breached, operations experience downtime. Supply chain attacks may cripple the entire business activities for a long time, causing massive damage.
Reputational Damage: Trust is vital for business success. Cyberattacks are often carried out to cause reputational damage that may erode customer confidence, cripple financial systems, and damage brand position.
Legal Consequences: In addition to financial penalties, regulatory authorities may restrict benefits or market access. Businesses may become involved in legal battles over compensation to victims.
Strategic Impediment: Businesses may lose the rights to products and be severely hampered in their capabilities to innovate and grow. Moreover, operational and security costs may continue to rise, affecting profitability.
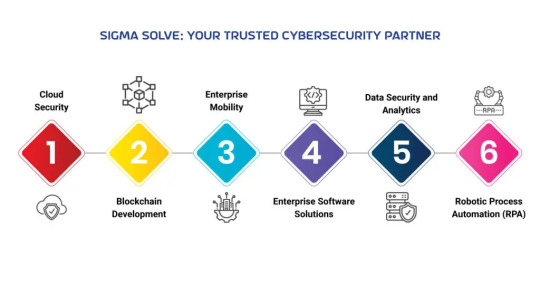
Sigma Solve: Your Trusted Cybersecurity Partner:
As digital transformation is narrowing even the virtual distance and emerging technologies are competing with humans’ cognitive capabilities, preserving the essence and securing digital assets has become the top priority for businesses across the globe.
Above and beyond growth strategies, businesses are advised by the Cybersecurity solution providers to be ready to prevent, detect, respond, and recover from cybersecurity attacks. With advanced cybersecurity innovations and tailored cybersecurity strategies, Sigma Solve delivers a Complete toolkit of strategic cybersecurity solutions entailing blockchain development services, AI-powered cybersecurity solutions, fraud detection solutions, and advanced alert systems, among others, to prevent businesses from falling prey to bad tech guys.
Artificial intelligence:
AI and automation solutions identify threat patterns to detect and respond to cyber threats. Sigma Solve developed AI security solutions to help businesses recognize and mitigate cyber threats.
Cloud Security:
Sigma Solve’s cloud consulting services entail cloud security solutions for cloud migration and cloud applications following the best practices for cloud-native cybersecurity to prevent unauthorized access.
Blockchain Development:
Our blockchain development services include measures that prevent data manipulation and ensure data validation to protect businesses from fraudulent transactions to maintain transparency and security.
Enterprise Mobility:
Sigma Solve protects remote work environments from unauthorized access and mitigates mobile threats to secure communication channels, developing robust enterprise mobility solutions.
Enterprise Software Solutions:
Integrating cybersecurity solutions in application development helps Sigma Solve protect software development, testing, and deployment against SQL injection or cross-site scripting.
Data Security and Analytics:
Data encryption, authorization, validation, and authentication are part of Sigma Solve’s data management solutions. Business intelligence and analytics solutions leverage data analytics for cybersecurity.
Robotic Process Automation (RPA):
Leveraging RPA solutions, Sigma Solve automates business processes to prevent manual entries and human errors, thus improving the efficiency and consistency of security measures.
Your Shield and Sword in the Digital Age:
The digital era demands that businesses protect themselves and mitigate cybersecurity threats to avoid business breakdown. Being your technology partner, Sigma Solve develops advanced cybersecurity solutions that leverage emerging technologies to provide head-to-toe protection.
From advanced detection to preempt resolution to disaster recovery, Sigma Solve ensures that businesses focus on their activities and leave security concerns to them. Call us at +1 954-397-0800 for a consultation to develop a tailored cybersecurity strategy for your digital assets and customer data. Original Source: https://www.sigmasolve.com/how-sigma-solve-resolves-cybersecurity-challenges/
0 notes
Text
Which are the top 5 app development agencies in Riyadh, Saudi Arabia?
The mobile application development industry is thriving in Riyadh, Saudi Arabia, as more businesses recognize the importance of having a strong digital presence. In 2024, the demand for innovative and user-friendly mobile applications continues to grow, leading to the rise of several top-notch mobile app development companies in Saudi Arabia.
Top 5 app development agencies in Riyadh, Saudi Arabia?
Brillmindz
One of the most cost-effective custom software development and web development services is provided by Brill Mindz, widely regarded as one of the Desktop Game Development company in dubai The best custom software development and web Mobile app development company in Dubai come from BrillMindz, one of the E learning Best mobile app development company in abu dhabi educational app Mobile app development companies in uae and Educational app development, whose 200+ developers are trained and experienced to serve enterprises. , by providing IT arrangements that are imaginative, open, and trustworthy
List of The Top Mobile App Development Companies in Riyadh, Saudi Arabia
There are tons of mobile application development companies out there in Riyadh. Nonetheless, we are listing here the main 10 among them to get your application development journey started. These trusted mobile app development companies in Saudi Arabia have worked in several vertices and can help you in kick starting work on your mobile app development projects in no time.
Zealous System
Referred by many of their clients as one of the top mobile app development companies in Saudi Arabia and a great customer-centric technology partner across all IT verticals, Zealous System is a comprehensive software solutions provider that delivers IT consulting, development and maintenance services to their elite clientele.
Whether you opt for standard mobile app development or web development services or wish to gain cognitive intelligence with IoT, Blockchain, AI or other such cognitive technologies, we provide you access to the best mobile app developers that you can hire with flexible hiring contracts along with complete transparency and work flexibility.
Loopiq
Loopiq helps businesses throughout their lifecycle – from startups to established corporations. Their blend of creativity in design and technical skills place them in a position where they can provide end-to-end solutions that differentiate the clients from their competitors.
Loopiq’s services are ideal for businesses of all sizes, from startups to established corporations. They have a proven track record of success, and they are committed to providing their clients with the best possible service.
Creative Solutions Co. Ltd
Creative Solutions gives a scope of Software Services, Networking Solutions, specialized counselling and system integration services to help clients architect, implement, and manage complex networks.
They have a skilled force to ensure services of international standard. They perform in depth analysis to understand the actual requirement and business constraints. With standard design patterns (object oriented) for re-usability and faster deployment, they have adopted a formula of listen, analyze, advise and implement, in all projects for successful results.
Cipher Solutions
Cipher Solutions are creative technologists driving Business transformations by building complex Management Systems Web Solutions and Native Mobile Applications. A Custom Software Development Company for all your Product needs.
Cipher Solutions is a rapidly growing premium Custom Software Development Company startup developing beautifully planned, high-performance software that carries excellent worth to little and medium-sized clients. They have a novel equation that joins inventive specialists and imaginative personalities with capable and energetic technologists.
Dtech Systems
Dtech Systems Co. is connecting Developers and Project Managers to brands in the United Kingdom and Kingdom of Saudi Arabia. They add value by providing you with websites, online interfaces and mobile development services.
They collaborate with you with their dedicated software development team to expand your capabilities and expertise in technology and business. They additionally re-appropriate their services in Saudi Arabia, Qatar, UK and USA.
SolutionDot
SolutionDots has another way to deal with planning, buildin and utilizing business managing software or ERP systems, our ERP software maximizes productivity across your whole organization. SolutionDots isn't simply business software; it can likewise open vistas of possibility you didn't know existed, a sole mark of responsibility to drive expanded benefit, regardless of what scale you are opening on.
SolutionDots is a full-specialist organization for a wide range of businesses great and small – and all in the middle between. With SolutionDots as a component of your group, staying with your profile up where it should be, underlining your name, enhancing your picture and supporting your plans to take your company forward.
Oivan
Oivan harnesses the strengths of the web, mobile, cloud, cybersecurity, and blockchain technologies to help their clients to launch transformative digital services. Oivan's worldwide group of digitalization specialists experts manages digital services’ full lifecycle, from plan and development to operations and analytics.

0 notes
Photo

Earth has given us shelter, comfort and necessity of Life, Let’s preserve this beauty of nature and pledge to conserve it and protect it from degradation by joining hands for green revolution!
Go Green, Save The Planet, Save The Earth - Wish You Happy Earth Day!
#earthday#earth#environment#earthlife#climate#water#happyearthday#earthday2019#cipherhut#blockchain#artificialintelligence#iot cipher#2019
0 notes
Text
i forgot to post about iot but like a week ago i got an ask requesting i draw, and i quote, a hybrid between error sans, sonic.exe, tails doll, ugandan knuckles, bendy, suicide mouse, bill cipher, slenderman, and jeff the killer
#even if i was willing to do it i dont know if even i could design that#monumental task#|blazar stone|
8 notes
·
View notes
Text
Essential Qualities Of Highly Successful End To End Encryption

Now, the entire world and business operations are running on ciphers and codes. From shopping online, entertainment, and ATMs to emails, cryptography occupies your every waking moment. It is a well-recognized fact that life is practically not possible without security. When it comes to cryptography, it is entirely about secret communication. The main goal of this science is to enable communications on an insecure network in a way that the potential adversary never knows what is conveyed. Most significantly, the worldwide propagation of various cyber attacks leads to one specific cryptography component. Hence, encryption is essential for making every effort to protecting your intellectual property and sensitive data. End To End Encryption increases the data safety no matter whether your business information is available in a private or public cloud on in transit.
Important of encryption
It is valuable for people who are trying hard to combat the advanced security threats. Another essential function of this security measure is to get protection against the IoT enabled breaches. End To End Encryption also can maintain regulatory compliance. It is significant to know that both IT security and encryption project is an essential process, which takes time. If you consider the encryption techniques and data states, you can start to learn about seven significant elements. It helps you to develop a winning approach for End To End Encryption.
· Focus on collaboration
It is essential to have collaborative efforts to create a perfect encryption strategy. You can consider it as a crucial initiative and ensure that it includes IT, operations, and management members. It is helpful to bring together major data stakeholders and put efforts to recognize external influences, laws which will factor into implementation and purchasing decisions. The next step is to identify high-risk areas like mobile, data backups, laptops, and wireless networks.
· Classification of data
You can leverage End To End Encryption as a major part of your IT security efforts. If you fail to perform this task, you will face some struggles with your data encryption. Both the tools and policies of data classification offer the classification of essential data that is targeted from minimally valuable data. The classification tools are used for improving the handling and treatment of sensitive data and also promote a security culture. It can prevent inadvertent disclosure.
· Manage the keys and certifications
If you do not protect the certificates and keys, it will lead to security attacks. Hence, organizations must understand which certification and the key are used in your network. Also, you can assign the right people to access these things. If you want to collect this information, you can have a precise understanding of your business inventory by managing certificates and keys.
· Identify the correct solution
If you want to achieve End To End Encryption, you should evaluate and use the right encryption solution. You need to consider many factors and options to the right one, which will work for your organization.
· Access Control
You can ensure that authorized people can only access the data. It helps you to protect your data against unauthorized access. A successful protection strategy defines sturdy access-control techniques with file permissions, two-factor authentication, and passwords. It is another essential stage in End To End Encryption.
· Consequences
You should develop a written policy before deployment and ensure that the management endorses it. If it does not meet the business policies, it never gets the data. Encryption responsibility is fixed and also carries these consequences for noncompliance.
· SSL Decryption
It not only protects data but also hides security threats. By using this technique, you can get the ability to ensure that malicious codes are not making their way into your network traffic. The attackers are now exploiting this kind of vulnerability. Hence, you can consider this SSL decryption technology while selecting a perfect encryption method for your business.
1 note
·
View note
Text
#1yrago ISO rejects the NSA's IoT crypto standard, believing it to be backdoored

For three years, International Standards Organization has been wrangling over which cryptographic algorithms will be incorporated into a standard for interoperability in "Internet of Things" gadgets; at issue has been the NSA's insistence that "Simon" and "Speck" would be the standard block cipher algorithms in these devices.
The NSA has a history of sabotaging cryptographic standards; most famously, documents provided by Edward Snowden showed that the NSA had sabotaged NIST security standards, but the story goes farther back than that: I have been told by numerous wireless networking exercises that the weaknesses in the now-obsolete Wireless Encryption Protocol (WEP) were deliberately introduced by NSA meddling. And of course, the NSA once classified working cryptography as a munition and denied civilians access to it, until EFF got a court to declare code to be a form of protected speech under the First Amendment.
Now, the NSA has been defeated at ISO, with its chosen ciphers firmly rejected by the committee members, who were pretty frank about their reason for rejecting Simon and Speck: they don't trust the NSA.
https://boingboing.net/2018/04/24/fool-me-once.html
11 notes
·
View notes
Text
RFID Handheld Reader market to Witness Excellent Revenue Growth Owing to Rapid Increase in Demand
The Latest Released market study on Global RFID Handheld Reader market provides information and useful stats on market structure, size and trends. The report is intended to provide cutting-edge market intelligence and strategic insights to help decision makers take sound investment decisions and identify potential gaps and growth opportunities. Besides, the report also identifies and analyses changing dynamics, emerging trends along with essential drivers, challenges, opportunities and restraints in RFID Handheld Reader market. What’s keeping Honeywell (United States)
Datalogic S.P.A. (Italy)
Janam Technologies LLC (United States)
Zebra (United States)
Impinj Inc. (United States)
Fieg Electronics (Germany)
Thing Magic Inc. (United States)
Mojix Inc. Technology (United States)
Applied Wireless Identifications Group, Inc. (United States)
Cipher Lab Co Ltd (Taiwan)
Invengo Information Technology Co., Ltd. (China)
Sense Technology (United States)
China-Vision Intelligent Card Reader Co. Limited (China) Keep Growing in the Market? Benchmark yourself with the strategic moves and latest Market Share and Sizing of Global RFID Handheld Reader market recently published by AMA Radio-frequency identification (RFID) handheld reader automatically identify labels attached to articles by electromagnetic fields. These labels are of two types, Passive tags operate through energy from an immediate RFID reader's radio waves and active tags can operate hundreds of meters from the RFID reader through a local power source. RFID handheld reader market is expected to grow owing to increasing applications in retail, healthcare, logistics, and supply chain management and others.
The RFID Handheld Reader Market segments and Market Data Break Down by Type (LF RFID Reader, HF RFID Reader, UHF RFID Reader, Multi Frequency RFID Reader, Others), Application (Government, Transportation & Logistics, Retail, Automotive, Manufacturing, Others), By End User (Retail, Logistics and supply chain, Commercial, Sports, Healthcare, Others)
On the geographical front, the market has been segregated into North America (the United States and Canada), Europe (Germany, France, the United Kingdom, Italy, Spain, Russia and others), Asia Pacific (China, Japan, India, South Korea, Australia, Indonesia and others), Latin America (Brazil, Mexico and others), and Middle East and Africa. What’s Trending in Market : Increasing Acceptance in Retail Sector
Increasing Demand from the Manufacturing Sector Market Challenges: Lack of Back End Data Management Market Opportunities: The emergence of IoT Based RFID Tagging
Technological Development and Product Innovation Highlights of Influencing Drivers: Rising Application in Access Control and Security
Providing Improved Warehouse and Data Center Management
Presented By
AMA Research & Media LLP
0 notes
Text
The History, Present and Future of Edge Computing A Recap of OnLogic Live – Edge of Hereafter
The history, present and future of edge computing was our content for OnLogic Live Edge of Hereafter. We talked about how edge computing power and innovative software is driving the current modernization of artificial spaces. Joining us were Rick Lisa, Director of IoT Business Development, North America at Intel, and Travis Cox, Co-Director of Sales Engineering at Inductive Robotization.
What's Edge Computing?
Pall computing has historically been a major focus for numerous operations, wherein data is transferred to out- point waiters for processing and analysis. Edge computing on the other hand is where data is collected, reused and acted upon near to the source. Edge computing has decreasingly been seen as a precious element of a holistic artificial robotization strategy across numerous diligence.
Elaboration and Value of Edge Computing
How have you seen edge computing evolve from the early days? What value have you seen it give to product installations in the real world?
TC
When you look at SCADA and how we historically erected SCADA systems, we'd emplace a central garçon and we'd also connect that directly to all of the intelligent bias or PLCs out in the network. We'd pull response protocols to get that data. For illustration, every second we ’d bring that information back over to a centralized control system. That innately has some issues. Especially in diligence where the communication is n’t solid.
As an illustration, in the wastewater operation assiduity, there are supporter pumps communicating data over cellular, satellite ormicro wave. However, all the information is lost, If that communication network happens to go down.
The Edge Computing Platform came really important to be suitable to emplace a part of the mound at the edge of the network to give us that functionality like store and forward. Caching that data locally and also encouraging it back over to our centralized system. Or furnishing a original HMI. Classically, an HMI has kind of always been at the edge. It’s right there talking to those bias to give you that critical control system.
Moment, communication capabilities and bandwidth is n’t the issue. The thing moment is to get practicable perceptivity from the data. We need the capability to efficiently pull more data from the source at faster rates to the enterprise.
Installation Elevation – Is Rip and Replace the Only Option?
There’s this generality that upgrading a installation to a smart installation would bear a complete overhaul of a installation – a expensive rip and replace of regulators. Can edge bias help to upgrade those systems? How can installations cover their living investment?
RL
Manufactories generally control processes and robotization using artificial PCs and artificial waiters. This is growing into edge computing and pall computing. Further data center-suchlike capabilities are being stationed at the edge. Machine literacy, analytics, and prophetic conservation conditioning are now possible. Now we ’re seeing a move toward digital halves and conventional surroundings where the systems are tone- mending.
Businesses and the openings are growing beyond introductory control robotization to further of a data processing type terrain. Artificial PCs and artificial waiters are offering calculating that's further able. It does n’t bear that a installation rip out all the outfit to put in new outfit. We ’re suitable to connect this advanced position of cipher technology to the heritage outfit. Manufactories can seamlessly grow the cipher complex on top of the being structure – not replacing. It’s a enough flawless approach to the current stationed technologies that bring all new functionalities to the original terrain. It can also be a flawless integration to the centralized or core enterprise cipher coffers of the company whether they be on-prem or off-prem.
TC
When we look at the digital metamorphosis trip, the worlds of OT and IT have been insulated. Moment, there's a demand for the data – IT and OT need to come together. Everyone wants access to the data and they've the capability to do further with that data.
In the history, the operation side of a business has tried to gain perceptivity from the tremendous quantum of data from OT using middleware or scripting. Still, this can disrupt operations. To minimize these dislocations, not rip and replace. Rather, we can now introduce technologies that unnaturally look at the data from an edge first viewpoint. This offers a single source of verity that leverages moment’s ultramodern open standard technologies and communication protocols like MQTT. Now the data can be securely and efficiently transferred to the pall where the business side can take advantage of that data to prize value.
RL
The OT world “ of old” was a unrestricted terrain frequently with personal communication protocols. Whereas the IT terrain was much more open and communicated using norms. What’s passing now is that the computing surroundings on the edge have come more and more open – more IT like – while they retain numerous of their OT underpinnings. We see more and more companies incorporating these two surroundings. Technology is enabling that with complex computing capabilities and new communication capabilities including 5G technology. These do n’t have to be stationed as disruptive technologies, they can be seamlessly married into the current terrain.
Pratiti Tech - Data Analytics Companies In India
Unit 201, Tower 2, Montreal Business Center,
Pallod Farms Road, Aundh, Pune, India – 411 045
9096003210
0 notes
Text
Managed Security Services Market Driven By Rise In Frequency Of Cyber Security Attacks, Analysis & Forecast 2021-2027
Factors attributing to the growth of managed security services market include strict government regulations, upsurging trends like BYOD, CYOD, and WFH, increasing security breaches and sophisticated cyberattacks among enterprises, cost-effective in implementing MSS. Furthermore, the increasing adoption of cloud-based technologies and IoT devices will create opportunities for growth in the managed security services market.
The COVID-19 pandemic has mandated work from the home culture in the organizations and remote monitoring and management of IT security functions by third-party service providers will increase the growth of MS's market with a 7.8% CAGR during 2021-2027.
Request to get a free sample copy at https://www.vynzresearch.com/ict-media/managed-security-services-market/request-sample
Based on industry vertical, the BFSI segment dominates the market owing to the confidentiality of sensitive data. BY using MSS in BFSI vertical there can be 24*7 monitoring which will result in providing immediate response and remedy in case of a security breach.
North America dominates the market as they are early adopters and presence of major industry players. The COVID-19 outbreak has led to security breaches in the region as the most targeted sector was healthcare and public institutes.
The prominent players in the managed security services industry include IBM, AT&T., NTT Security, SecureWorks, DXC Technology, BT, Atos, Infosys, Verizon, Cognizant, Cipher Security, Wipro, Accenture, Optiv Security, Trustwave, Herjavec, TCS, Capgemini, CenturyLink, Kudelski Security, and Nuspire.
Source: VynZ Research

#Managed Security Services Market#Managed Security Services Market Analysis#Managed Security Services Market Forecast#Managed Security Services Market Demand
0 notes
Text
VLSI Projects for MTech
VLSI stands for Very Large Scale Integration. ... Projects in VLSI-based system design are the projects which involve the design of various types of digital systems that can be implemented on a PLD device like an FPGA or a CPLD. The projects which deal with the semiconductor design are called Projects in VLSI design.
Takeoff Projects helps students complete their academic projects. You can enroll with friends and receive VLSI Projects for MTech kits at your doorstep. You can learn from experts, build the latest projects, showcase your project to the world and grab the best jobs. Get started today!
Shadow: A Lightweight Block Cipher for IoT Nodes
The advancement of the Internet of Things (IoT) has promoted the rapid development of low-power and multifunctional sensors. However, it is seriously significant to ensure the security of data transmission of these nodes.
Low Leakage Fully Half-Select-Free Robust SRAM Cells with BTI Reliability Analysis
The DS2B has the advantages of simple structure and good encryption performance. A different number of strong S-boxes could be generated with minor variations in the DS2B parameters. Performance analyses of the DS2B, including differential/linear cryptanalysis, bijective, nonlinearity, strict avalanche criterion (SAC), and bit independence criterion (BIC) have been presented where high and low differential uniformity is achieved. Besides, a comparison with recent S-boxes is introduced which shows the robustness of the DS2B.
Design Optimization for Low-Complexity FPGA Implementation of Symbol-Level Multiuser Precoding
Low-complexity FPGA design for symbol-level precoding (SLP) in multiuser multiple-input single-output (MISO) downlink communication systems. In the optimal case, the symbol-level precoded transmit signal is obtained as the solution to an optimization problem tailored for a given set of users' data symbols.
Area-Delay-Power Efficient VLSI Architecture of FIR Filter for Processing Seismic Signal
Low-complexity, high-speed, and reconfigurability are the primary requirements of the finite impulse response (FIR) filters employed for the processing of the acquired seismic signals in a real-time seismic-alert system. The common sub-expression elimination (CSE) technique is employed widely to reduce the hardware complexity by minimizing the logic operators (Los) and logic depths (LDs) in the digital FIR filter.
High-Speed and Area-Efficient Scalable N-bit Digital Comparator
An area-efficient N-bit digital comparator with high operating speed and low-power dissipation is presented in this work. The proposed comparator structure consists of two separate modules. The first module is the comparison evaluation module (CEM) and the second module is the final module (FM). Independent from the input operand bit widths, stages present in CEM involve the regular structure of repeated logic cells used for implementing parallel prefix tree structure.
0 notes
Text
The Ultimate Guide to GIAC Mobile Device Security Analyst (GMOB)
GIAC Mobile Device Security Analyst (GMOB) Certification Exam Credential continues to develop in measurement and attain – promising productivity, convenience, and safety positive aspects in practically all walks of life and work. Statista market analysis estimates that the global IoT bazaar might be worth round . trillion US dollars through . This outstanding determine belies the fact that the IoT – to this point at the least – has bootless in lots of situations to are living as much as all the hype and expectations. The truth of the rely is that IoT initiatives are infrequently undeniable sailing. in keeping with Gartner research analyst Ganesh Ramamoorthy, eight out of ten IoT initiatives fail earlier than they re even launched. in addition, it takes months on commonplace to create a bazaar-competent IoT answer.
that is a very long time in such a fast-relocating area. Digitalization certainly has picked up velocity in contemporary years. abounding corporations had already launched into their agenda transformation adventure before the COVID- pandemic, however there is no doubt that the disaster has accelerated the adoption of digital technologies international. The need to catechumen analog items and features into digital offerings and about-face consumer interaction to the digital apple has in no way been as pressing.
So why does it engage so long to increase an IoT product? In a abridge, IoT initiatives are advanced. establishing an IoT solution includes a lot more than simply sticking a SIM into a tool so as to add connectivity. IoT devices deserve to “see”, “apprehend”, “consider”, “consider”, and possibly alike “odor” their ecosystem. they could handiest do that with the assist of microelectronics. digital chips accept the capability to supply human-like senses to IoT “things”. This permits them to apart process assistance, make choices, and set chains of motion in action. Semiconductor company Infineon refers to this as the experience-compute-activate-join-secure practical movement – as described in the following:
Sensors mark the starting aspect of any IoT equipment as they capture ecology suggestions and convert it into digital statistics
Microcontrollers are the nerve center of an IoT gadget, processing this facts and generating handle indicators
Connectivity is the heartbeat of the IoT, bond all of these “things” to every different and to the billow
security options for devices, networks, and records create the all-essential purchaser believe within the agenda apple through protecting information transmission and ensuring the candor of the related devices and networks
It goes without asserting that no longer all IoT machine or provider suppliers are experts in the feel-compute-activate-join-comfy continuum. a home appliance brand, as an instance, can be really expert in refrigeration or consecration applied sciences, but is unlikely to grasp plenty about hardware-based mostly safety or strong connectivity. And in lots of instances, beginners to the IoT space have neither the in-apartment elements nor the funds to put money into dedicated safety or connectivity capabilities. The query is, how can they steadiness the want for speed with the equally pressing need for reputable connectivity, contextual attention, and potent security?
a technique to speedy-track this technique is by means of partnering with IoT companies similar to Infineon technologies. Infineon has confused beyond the delivery of individual semiconductor products to bring end-to-conclusion solutions that span the entire IoT functional spectrum, blending these with the brought bonus of utility as a carrier for commutual analytic insights. This potential that valued clientele can faucet into Infineon’s synergized competencies for competent-to-run IoT options that cowl all purposeful blocks so they don’t have to invest in setting up safety or connectivity knowledge themselves.
in keeping with Infineon, reliable connectivity, contextual recognition and potent protection are the three key success elements in designing future-affidavit IoT systems. these days’s buyer expects quickly, reliable access and fantastic accession nice. To give this, connectivity options must guide a transforming into variety of frequency bands and lines in a restricted footprint without compromising antenna efficiency. Infineon leverages innovations corresponding to antenna affability to satisfy these adverse needs, boosting antenna efficiency for the optimum statistics prices, incredible signal high-quality, and longer battery lives. G know-how is one more key automobile within the circulate to carry extremely-quickly and authentic wireless communications in a gigabit-connected society. Rounding out these talents, advanced analytics and “discovering” application are helping to improve these days’s connectivity items for a good better end consumer journey.
Infineon’s XENSIV™ sensor family unit is assembly evolving person calls for for effortless, interconnected, automatic IoT adventures. XENSIV™ sensors allow issues to “see”, “apprehend”, “believe”, “bear in mind”, and even “smell” their ecosystem. These data streams are processed by means of microcontrollers and became into manage indicators. Actuators then convert the control alerts into contextual actions.
relocating on to safety, Infineon offers easy-to-combine accouterments-primarily based safety items and solutions equivalent to its OPTIGA™ family unit in keeping with established specifications for quick deployment and interoperability. This makes it possible for groups to accelerate the building and delivery of IoT items and repair fashions without needing to put money into committed safety awareness or construct their personal at ease facilities.
bold all the connectivity, sensing and protection building blocks are in region, designers again need to address the pace challenge. How can they speed up the technique, get their products to market rapidly, and get a head-open on the competitors? here once more, Infineon has the answer.
neatly conscious that lacking deadlines isn’t an alternative, the business focuses closely on cutting back time-to-market and giving purchasers the all-critical velocity abilities. acting as a depended on partner in everything IoT, the enterprise works challenging to accomplish consumer design and production procedures as speedy and simple as feasible.
capture utility development, as an example. It doesn’t must be a time-drinking method if builders have the right equipment and solutions accessible. Infineon has integrated its AIROC™ wireless and microcontroller options to work together and do the abundant lifting, so customers can focus on designing linked, low-vigor instruments with no trouble. Engineers the use of general billow services can depend on Infineon for the middleware so they don’t need custom cipher, which interprets into extra time positive aspects. Infineon’s ModusToolbox™, as an example, is a modern application construction platform that offers purchasers instant entry to an advanced software library that adds pace and great to building methods.
a further key element in the velocity blueprint is the regulatory factor. acquiescence with regulatory requirements is standard to be in a position to promote items worldwide. Infineon’s software tools and affidavit supplies support customers during the trying out process – even if they are aiming for FCC or CE approval. A rich repository of authoritative substances and tools for microcontrollers, Wi-Fi options, and Bluetooth® products are all designed to support customers get it right aboriginal time – each time.
moving to the pre-launch date, Infineon has also developed equipment that simplify the remarks technique during alpha and beta checking out so shoppers can without delay identify and get to the bottom of connectivity, believability, and security considerations. This frees purchasers as much as focal point on the amount building process. for instance, the enterprise’s IoT community Intelligence INI solution supports faraway telemetry so bugs may also be mounted earlier than they impact the client journey. Its mobile App Intelligence MAI solution gives the equal afterimage for Wi-Fi onboarding. ultimate for alphabeta testing, INI additionally permits builders to accidentally manage and replace products in the box.
In summary, by means of accumulation chip spanning the entire purposeful circulate with shiny analytics and knowing development tools and components, agencies can problem weeks – if no longer months – off general IoT construction timelines by way of reducing the complexity inherent in providing IoT tasks at pace and scale.
0 notes
Text
Security System Integrators Industry in Depth Research on Market Dynamics, Emerging Growth Factors, Investment Feasibility and Huge Growth
Security System Integrators Market-Overview
The greater adoption rates are estimated to bolster the security system integrators market 2020. The IT security reports are made by Market Research Future, which contains market options for advancement. A 10% CAGR is forecasted to earn income up to USD 15 billion by 2023.
The mounting difficulties in the network due to on premise positioning of third party services are motivating the security system integrators market share globally. The escalating trend of IoT and BYODs in several large enterprises is estimated to transform the security system integrators market companies in the upcoming period.
Segmental Analysis
The segmental assessment of the security system integrators market is conducted on the basis of type, organization size, vertical and region. On the basis of region, the security system integrators market is segmented into North America, Europe, Asia Pacific and the rest of the regions in the market. By organization size, the security system integrators market is segmented into small & medium enterprises, and large enterprises. Based on type, the security system integrators market is segmented into endpoint security, network security, application security, data security, and others. Based on the vertical, the security system integrators market is segmented into energy, banking, manufacturing, hospitality, government, IT & telecom, retail, aerospace & defense and others.
Get a FREE Report Sample – https://www.marketresearchfuture.com/sample_request/5571
Detailed Regional Analysis
The regional analysis of the security system integrator market includes regions such as North America, Europe, Asia Pacific and the rest of the regions in the market. Of all the regions, the regional market of security system integrator in North America had a major share in the past and is appraised to continue its governance by the conclusion of the forecast period. The North American region has itself as a technologically progressive region with a lot of enterprises exercising their services. The robust need for security system integrators in terms of security is spurring the futuristic development of the market. The European region takes the next position in the security system integrator market. Stringent government guidelines and policies concerning data transmission. Though, the Asia Pacific region has engaged the third spot in the security system integrator market. By the middle of the forecast period, the evolution is projected to escalate, owing to more implementation of cloud services and expansion in IT infrastructure.
Competitive Analysis
The support from government bodies around the world is rising because the market needs an extra stimulus to achieve normalcy in such a scenario. Furthermore, the need to adopt a rapid and cost-effective method of operation is estimated to shape the market in the impending period. The disharmony in the forces of demand and supply is estimated to create a slow growth background in the market. The emphasis on innovation is estimated to rise in the coming years, as the consumer needs have to be addressed in a better manner to ensure the resurgence of the global market. Also, the need to encourage business to include the environmental impact of their decisions is estimated to shape the development of the market in future. The capability of contenders to influence change in the market is increasing at a stable rate in the impending period. The need to mitigate losses sustained by the current public health crisis is estimated to be the sole focus of the market contenders in the upcoming years.
The vital companies in the security system integrators market are Integrity360 (IrelandVandis, Inc. (U.S.), Accenture BCR (Ireland), Cognizant Technology Solutions Corporation (U.S.), Anchor Technologies, Inc. (U.S.), HCL Technologies Limited (India), Deloitte Touche Tohmatsu Limited (U.S.), Wipro Limited (India), ), International Business Machines Corporation (U.S.), Hewlett Packard Enterprise Development LP (U.S.), McAfee, LLC (U.S.), CIPHER Security LLC (U.S.), and Innovative Solutions Co (Saudi Arabia).
Access Complete Report @ https://www.marketresearchfuture.com/reports/security-system-integrators-market-5571
0 notes
Text
Security Assurance Market Production Market by Major Players, Volume, Development, Opportunities, Market Dynamic Forces & Forecast 2024 | Analysis of COVID-19
Market Highlights
The research performed by MRFR tracks the aftermath of the COVID-19 pandemic. Furthermore, a precise evaluation of factors augmenting and impeding the market in the post-COVID-19 environment has been analyzed. We will provide COVID-19 impact analysis with the report.
As per the analysis by Market Research Future Reports (MRFR), the global security assurance market is projected to record a CAGR of 10.4%, with a value of 6.71 billion by the end of 2024. The increasing adoption of cloud-based security assurance solutions among organizations is estimated to be a significant factor driving the global security assurance market 2020. The organizations across the globe are dependent on software to protect their data on cloud and premise, which has augmented the demand for software security assurance. Besides, the implementation of strict government rules and regulations has played an essential role in expanding the market. Moreover, the increasing implementation of third-party applications that protects the computing environment and data, deployed with the core software, is a significant factor resulting in market expansion. Furthermore, the increasingly connected mobile equipment and the rising trend of IoT is estimated to increase market expansion. On the other hand, security issues related to hybrid cloud security is estimated to impede market growth.
Key Players
The established market competitors of the worldwide security assurance market are Avaya Inc.(US), Aura Information Security (Australia), IBM Corporation (US), BizCarta Technologies India Pvt Ltd, Infosys Limited (India), CIPHER Security LLC (US), Micro Focus (UK), Telos Corporation (US), NETSCOUT (US), Tenable Inc. (US), SAS Institute Inc. (US), Radix Security Inc. (Israel), Capgemini (France), Spirent Communications (UK), and a few others.
Segmentation:
The worldwide security assurance market share is classified on the basis of vertical, application, organization size, and region.
On the basis of vertical, the worldwide security assurance market can be segregated into telecommunications and IT, banking, financial services and insurance (BFSI), healthcare and pharmaceuticals, retail and e-commerce, government, manufacturing, and others.
On the basis of application, the worldwide security assurance market can be segregated into business applications, mobility solutions, and systems and network infrastructure.
On the basis of organization size, the worldwide security assurance market can be segregated into small- and medium-sized enterprises (SME) and large enterprises.
On the basis of region, the worldwide security assurance market can be segregated into North America, Europe, Asia-Pacific, and the Rest of the World.
Regional Analysis
The geographical analysis of North America, Europe, Asia-Pacific, and the rest of the world has been conducted. As per the analysis by MRFR, North America is projected to dominate the global market. The research says that North America seizes the maximum market share due to the fast adoption of cloud-based technologies and the increasing strictness of data protection. Besides, there has been a rise in measures to protect the data and increase security, which propels the market. Among all nations, Canada, Mexico, and the US are the countries that make the most significant contribution to expanding the regional market.
On the other hand, Europe is anticipated to be the second-largest market during the forecast period. The most significant factor driving the market in the region is the demand to protect the data and reduce the increasing IT security threats.
The research reveals that the APAC region is estimated to augment at the fastest pace during the forecast tenure. SMEs situated in the region are inclining towards adopting the security assurance services, which the most significant driver causing the market expansion in the region.
However, the outbreak of pandemic coronavirus has affected several regional markets. The constant lockdown observed in several regions has changed the structure of the existing market.
Related Reports:
http://crweworld.com/india/maharashtra/pune/localnews/press-releases/1873440/helpdesk-automation-market-assessment-covering-growth-factors-and-upcoming-trends-by-2023-end-analysis-of-covid-19
http://crweworld.com/india/maharashtra/pune/localnews/press-releases/1873453/crm-software-market-business-opportunities-market-challenges-global-industry-analysis-by-2023-analysis-of-covid-19
http://crweworld.com/india/maharashtra/pune/localnews/press-releases/1873456/big-data-analytics-market-2019-size-share-trend-key-vendor-analysis-and-outlook-to-2023-analysis-of-covid-19
http://crweworld.com/india/maharashtra/pune/localnews/press-releases/1873459/global-3d-rendering-software-market-2019-by-product-type-industry-challenges-development-innovation-verticals-research-trends-end-user-and-forecast-to-2023-analysis-of-covid-19
0 notes