#json serialize
Explore tagged Tumblr posts
Text
hmm today I will implement minecraft resource locations in rust <- clueless
#minecraft#rustlang#programming#i love serializing i love json files i love regex i love cloning a variable just to check the length
3 notes
·
View notes
Note
hi, I saw a post you made about your character creator menu a while back and I thought it was really neat how you had adjusted the standard picrew-style menu to give better previews. I want to build something similar (just as a picrew, not as part of something bigger), and I've got a basic idea of how I'd code it, but figured I'd ask, did you follow a tutorial at all to help code yours? and/or would you be willing to share some of your backend for it?
I'm very curious if my idea of how to achieve the same result is roughly the same backend as you've got, or something wildly different!
Sure! Here's the architecture diagram:

I know the diagram is probably not useful on its own... we were a little cute and call an entire portrait a "sandwich" which is made of of different "slices" (the eye slice, the outer_clothes slice). It follows the 3-layer system that I describe in this talk. The basic idea is something I call "the cycle between heaven and earth":
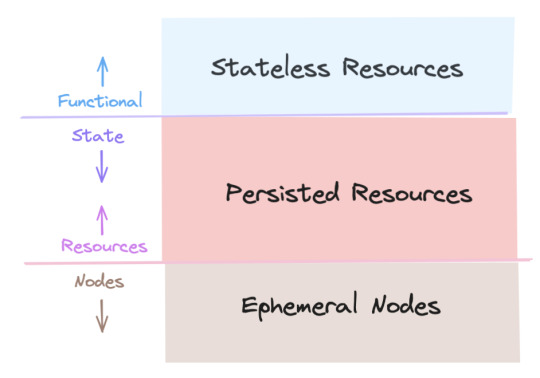

The lowest layer is all the nodes in Godot's scene tree. They're basically a browser DOM that don't store any data we want to keep; they're mortal and ephemeral. E.g. buttons, stuff drawn on the screen.
The middle "cores" layer are resources with almost no functionality; they're just data repositories meant to be serialized/deserialized.
The top layer has no state and its resources represents game content: collections of possible noses, hats, etc.
When data changes, I have "rerender" functions on most of my nodes that can be called to update themselves to whatever the current data is (rather than updating themselves piecemeal as specific things change). Similar to how React does it, if you're familiar.
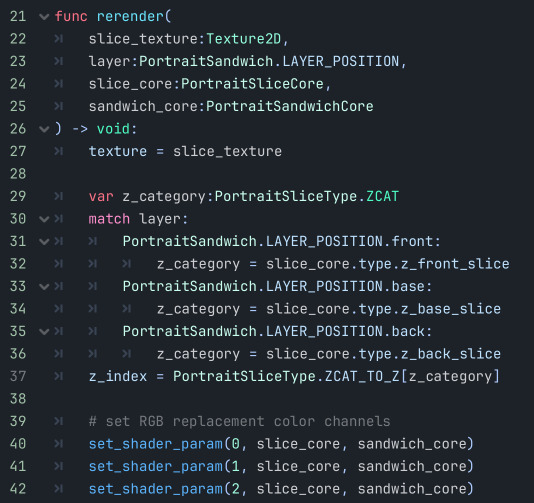
To get that preview effect where everything is the same besides one thing, on every change I rerender all the buttons in that category with a copy of the current "main" core and then replace the one slice that particular button changes.
The cores serialize to JSON, and I store the slices as "slice_type: chosen_slice", the keys of which match up to the resources I defined in the top layer.
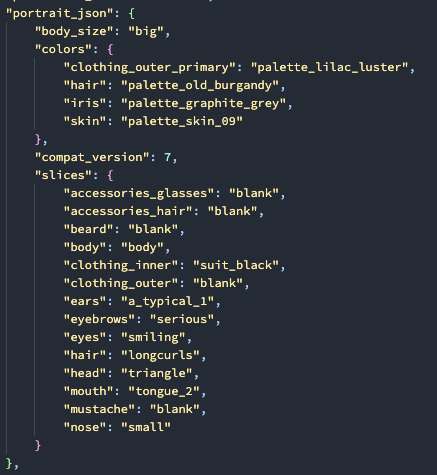
To define all the assets, we set up a file parser that goes through and automatically collects & sorts image files into different categories and with their front/back and big/small variations by file name:

I use this organization for both the portrait maker and the main game, so it's not specialized for doing picrews... I hope this is useful to you! Happy to answer any other questions you have about it.
13 notes
·
View notes
Text
I implemented undo/redo in my experimental 3d sdf editor.
My scene data is stored in a tree data structure where I can listen to updates granularly (that's how I efficiently update the objects only when something actually changed). The tree also manages making snapshots and moving back and forth between snapshot versions. It can also be serialized to json and imported back. I think I'll eventually publish a crate just for this tree, once it's more feature-stable.
7 notes
·
View notes
Text
Insecure Deserialization in Symfony: Explained with Code
In today’s threat landscape, web application security can be compromised through overlooked weaknesses in serialization. One such vulnerability is known as "Insecure Deserialization." If you're using Symfony, understanding and defending against this attack vector is vital.

In this article, we'll break down what insecure deserialization is, why it’s a threat to Symfony-based applications, and how to detect and mitigate it—with real-world code examples and references to our website vulnerability scanner tool.
🔍 What is Insecure Deserialization?
Deserialization is the process of converting a stream of bytes back into an object. In Symfony, PHP’s native serialization mechanisms (serialize() and unserialize()) or Symfony’s Serializer component can expose vulnerabilities when user-controllable data is deserialized without validation.
If attackers can manipulate serialized objects, they can potentially inject malicious payloads that lead to:
Remote Code Execution (RCE)
Object Injection
Application state manipulation
⚠️ Real-World Impact in Symfony
Let’s take a look at a simplified insecure example:
❌ Vulnerable Symfony Controller
// src/Controller/VulnerableController.php namespace App\Controller; use Symfony\Bundle\FrameworkBundle\Controller\AbstractController; use Symfony\Component\HttpFoundation\Request; use Symfony\Component\HttpFoundation\Response; class VulnerableController extends AbstractController { public function deserialize(Request $request): Response { $data = $request->get('data'); $object = unserialize($data); // DANGEROUS return new Response('Deserialized!'); } }
If an attacker sends a specially crafted serialized object (e.g., via POST or GET), this could lead to arbitrary code execution or manipulation of system behavior.
✅ Secure Deserialization Techniques in Symfony
Instead of directly unserializing raw input, use Symfony’s Serializer component securely or switch to formats like JSON which are safer by default.
✔️ Safer Approach Using Symfony Serializer
use Symfony\Component\Serializer\SerializerInterface; use Symfony\Component\HttpFoundation\Request; use Symfony\Component\HttpFoundation\JsonResponse; use App\Entity\User; public function safeDeserialize(Request $request, SerializerInterface $serializer) { $json = $request->getContent(); $user = $serializer->deserialize($json, User::class, 'json'); return new JsonResponse(['message' => 'Deserialized safely!']); }
By using JSON and Symfony’s serializer, you avoid exposing internal PHP objects to untrusted input.
🧪 Test Your Symfony App for Insecure Deserialization
You can instantly check if your website has this or other vulnerabilities using our free security scanner.
📸 A screenshot of the Website Vulnerability Scanner landing page

Screenshot of the free tools webpage where you can access security assessment tools.
This tool performs vulnerability assessments without needing access to your code. It's fast, user-friendly, and completely free.
📄 Sample Vulnerability Report Output
Here’s how an insecure deserialization issue might appear in a vulnerability scan report:
📸 Screenshot of a report to check Website Vulnerability.

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
The report details:
Vulnerability name
Severity level
Affected endpoint
Suggested mitigation steps
To generate a free report, visit: https://free.pentesttesting.com
🧰 Symfony Deserialization Exploit Example
Here's an example of exploiting deserialization using a malicious payload:
Attacker-Crafted Serialized String
O:8:"ExploitMe":1:{s:4:"data";s:18:"phpinfo(); exit;";}
This payload assumes a class ExploitMe exists with a __destruct() or __wakeup() method executing eval() or dangerous functions.
Recommended Symfony Hardening Tips
Avoid using PHP’s unserialize() on user input.
Use JSON and Symfony’s Serializer instead.
Validate all incoming data types and values.
Restrict class autoloading to trusted namespaces.
Leverage a WAF (Web Application Firewall).
💼 Need a Deeper Security Review?
If you're concerned your app may be vulnerable, our cybersecurity experts can help.
🔐 Explore our professional penetration testing service here: 👉 Web App Penetration Testing Services
We test your application for OWASP Top 10, business logic flaws, and framework-specific misconfigurations—including Symfony.
📰 Stay Informed — Subscribe to Our Newsletter
Join 1,000+ developers and security engineers staying updated on threats and defenses.
📩 Subscribe to our LinkedIn Newsletter
🧠 Final Thoughts
Insecure deserialization isn’t just a theoretical risk—it’s been used in real-world breaches. If you're using Symfony, avoid using native PHP deserialization unless you're 100% confident it’s safe. Even then, sanitize everything.
🔗 More posts like this on our blog: https://www.pentesttesting.com/blog/
Let us help you secure your code—before someone else finds your flaw.
📌 Has your site been tested for this vulnerability? Try it now: https://free.pentesttesting.com
1 note
·
View note
Text
How can you serialize and deserialize Java objects for frontend-backend communication?

1. What’s Java Serialization and Deserialization All About?
So, how do you handle communication between the frontend and backend in Java? It’s all about turning Java objects into a byte stream (that’s serialization) and then back into objects (deserialization). This makes it easy to exchange data between different parts of your app. The Serializable interface in Java is key for this, as it helps keep the state of objects intact. If you’re taking a Java course in Coimbatore, you’ll get to work on this a lot. Serialization is super important for things like APIs and managing sessions. For Java backend developers, it's a must-know.
2. Why Is Serialization Important Nowadays?
When it comes to Java and modern web apps, we often use JSON or XML for serialized data. Libraries like Jackson and Gson make it easy to convert Java objects to JSON and vice versa. These formats are great for frontend and make communication smoother. If you study Java in Coimbatore, you'll learn how serialization fits into REST APIs. Good serialization helps keep your app performing well and your data secure while also supporting setups like microservices.
3. What’s the Serializable Interface?
The Serializable interface is a simple marker in Java telling the system which objects can be serialized. If you get this concept down, it really helps answer how to serialize and deserialize Java objects for frontend-backend communication. By using this interface, you can easily save and send Java objects. Students in a Java Full Stack Developer Course in Coimbatore learn how to manage complex object structures and deal with transient variables to keep things secure and fast.
4. Tools and Libraries for Serialization in Java
To serialize objects well, developers often rely on libraries like Jackson and Gson, along with Java’s ObjectOutputStream. These are essential when you’re trying to serialize Java objects for frontend-backend communication. With these tools, turning Java objects into JSON or XML is a breeze. In Java courses in Coimbatore, learners work with these tools on real projects, and they offer options for customizing how data is serialized and handling errors more smoothly.
5. Deserialization and Keeping Things Secure
Deserialization is about getting objects back from a byte stream, but you've got to do this carefully. To serialize and deserialize Java objects safely, you need to check the source and structure of incoming data. Training in Coimbatore covers secure deserialization practices so you can avoid issues like remote code execution. Sticking to trusted libraries and validating input helps keep your app safe from attacks.
6. Syncing Frontend and Backend
Getting the frontend and backend in sync relies heavily on good serialization methods. For instance, if the Java backend sends data as JSON, the frontend—often built with React or Angular—needs to handle it right. This is a key part of learning how to serialize and deserialize Java objects for frontend-backend communication. In Java Full Stack Developer Courses in Coimbatore, students work on apps that require this skill.
7. Dealing with Complex Objects and Nested Data
A big challenge is when you have to serialize complex or nested objects. When figuring out how to serialize and deserialize Java objects for frontend-backend communication, you need to manage object references and cycles well. Libraries like Jackson can help flatten or deeply serialize data structures. Courses in Coimbatore focus on real-world data models to give you practical experience.
8. Making Serialization Efficient
Efficient serialization cuts down on network delays and boosts app performance. Students in Java training in Coimbatore learn how to make serialization better by skipping unnecessary fields and using binary formats like Protocol Buffers. Balancing speed, readability, and security is the key to good serialization.
9. Real-Life Examples of Java Serialization
Things like login sessions, chat apps, and shopping carts all depend on serialized objects. To really understand how to serialize and deserialize Java objects for frontend-backend communication, you need to know about the real-time data demands. In a Java Full Stack Developer Course in Coimbatore, you’ll get to simulate these kinds of projects for hands-on experience.
10. Wrapping It Up: Getting Good at Serialization
So how should you go about learning how to serialize and deserialize Java objects? The right training, practice, and tools matter. Knowing how to map objects and secure deserialized data is crucial for full-stack devs. If you're keen to master these skills, check out a Java course or a Java Full Stack Developer Course in Coimbatore. With practical training and real projects, Xplore IT Corp can set you on the right path for a career in backend development.
FAQs
1. What’s Java serialization for?
Serialization is for turning objects into a byte stream so they can be stored, shared, or cached.
2. What are the risks with deserialization?
If deserialization is done incorrectly, it can lead to vulnerabilities like remote code execution.
3. Can every Java object be serialized?
Only objects that implement the Serializable interface can be serialized. Certain objects, like threads or sockets, can’t be.
4. Why use JSON for communication between frontend and backend?
JSON is lightweight, easy to read, and can be easily used with JavaScript, making it perfect for web apps.
5. Which course helps with Java serialization skills?
The Java Full Stack Developer Course in Coimbatore at Xplore IT Corp offers great training on serialization and backend integration.
#Java programming#Object-oriented language#Java Virtual Machine (JVM)#Java Development Kit (JDK)#Java Runtime Environment (JRE)#Core Java#Advanced Java#Java frameworks#Spring Boot#Java APIs#Java syntax#Java libraries#Java multithreading#Exception handling in Java#Java for web development#Java IDE (e.g.#Eclipse#IntelliJ)#Java classes and objects
0 notes
Text
Integrating Third-Party APIs in .NET Applications
In the world of modern software development, building applications that are both powerful and flexible often involves tapping into external services. These services, commonly offered through third-party APIs (Application Programming Interfaces), allow developers to access features like payment processing, real-time notifications, map integrations, and much more. If you want to become an expert in this essential area, enrolling in the best dotnet training in Hyderabad is a great way to build your skills and stay ahead in the industry.
What Are Third-Party APIs?
Third-party APIs are pre-built interfaces provided by external companies or platforms that allow your application to communicate with their services. For instance, if you want to include Google Maps, integrate PayPal, or fetch weather updates from OpenWeatherMap, you would use their APIs. Instead of developing these complex features from scratch, you can simply connect and use them in your own .NET applications.
Why Use APIs in .NET Projects?
Using APIs in your .NET projects provides many advantages:
Time Efficiency: APIs offer ready-made solutions, reducing the time and effort needed to develop features.
Reliability: Established APIs are tested and maintained by their providers, ensuring better performance and fewer bugs.
Scalability: APIs are built to handle large volumes of data and users, making them a good fit for scalable apps.
Innovation: Access to APIs opens up a wide range of features you can integrate into your app, enhancing user experience.
How to Integrate APIs in .NET
APIs can easily be connected with ASP.NET Core. Here’s a basic approach:
In .NET, the HttpClient class is the primary way to send HTTP requests and receive responses.
Work with JSON – Most APIs return data in JSON format. In .NET, either System.Text.Json or Newtonsoft.Json can be used to serialize and deserialize JSON data.
Secure Configuration – Store API keys and credentials in configuration files using appsettings.json or environment variables for better security.
Best Practices for API Integration
Error Handling: Always check for status codes and handle errors gracefully. Timeouts and API failures should not crash your app.
Rate Limiting Awareness: Be mindful of how many requests you send to an API.The purpose of rate limits is to prevent abuse by providers.
Secure Your Data: Never hard-code sensitive information like API keys into your codebase. Use secure storage methods instead.
Conclusion
Integrating third-party APIs is a must-have skill for any modern .NET developer. It enables you to create feature-rich, scalable, and highly responsive applications with less effort and faster turnaround times. By mastering this through real-world practice, you position yourself for greater opportunities in software development.
To get started on your learning journey with expert guidance, real-time projects, and industry-relevant skills, we recommend enrolling at Monopoly IT Solutions Pvt. Ltd, a trusted name in .NET training and professional development.
#best dotnet training in hyderabad#best dotnet training in kukatpally#best dotnet training in kphb#best .net full stack training
0 notes
Text
Identify elements of a search solution
A search index contains your searchable content. In an Azure AI Search solution, you create a search index by moving data through the following indexing pipeline:
Start with a data source: the storage location of your original data artifacts, such as PDFs, video files, and images. For Azure AI Search, your data source could be files in Azure Storage, or text in a database such as Azure SQL Database or Azure Cosmos DB.
Indexer: automates the movement data from the data source through document cracking and enrichment to indexing. An indexer automates a portion of data ingestion and exports the original file type to JSON (in an action called JSON serialization).
Document cracking: the indexer opens files and extracts content.
Enrichment: the indexer moves data through AI enrichment, which implements Azure AI on your original data to extract more information. AI enrichment is achieved by adding and combining skills in a skillset. A skillset defines the operations that extract and enrich data to make it searchable. These AI skills can be either built-in skills, such as text translation or Optical Character Recognition (OCR), or custom skills that you provide. Examples of AI enrichment include adding captions to a photo and evaluating text sentiment. AI enriched content can be sent to a knowledge store, which persists output from an AI enrichment pipeline in tables and blobs in Azure Storage for independent analysis or downstream processing.
Push to index: the serialized JSON data populates the search index.
The result is a populated search index which can be explored through queries. When users make a search query such as "coffee", the search engine looks for that information in the search index. A search index has a structure similar to a table, known as the index schema. A typical search index schema contains fields, the field's data type (such as string), and field attributes. The fields store searchable text, and the field attributes allow for actions such as filtering and sorting.
0 notes
Text
Implement Efficient Data Serialization with Django REST Framework
Implementing Efficient Data Serialization with Django REST Framework 1. Introduction Brief Explanation Data serialization is the process of converting complex data structures into a format that can be easily stored, transmitted, or manipulated. In the context of web development, serialization is particularly important for converting data from server-side models into formats like JSON, which…
0 notes
Text
It's the first time in awhile that I've done prototyping on my language! While none of the code I'm writing is likely to end up in the real implementation, I did need to flesh out the higher level representation that's used for things like reflection. And Python is a pretty convenient tool to do that with creative freedom.
Essentially, all code (except builtins) can be represented as data, in a somewhat LISPy way. The primitives here are dirt simple, it's just nested lists of strings. You can serialize it to JSON trivially.
I'm eventually going to need to pull my findings back into C and reconcile them with the lower-level bytecode interpreter. But if I expose some C types and functions to my Python code, I could get really far in this model, and then have an organized incremental process of eating away the Python implementation until it entirely disappears back into C while passing all tests. This is probably the development model that will make the most sense tbh as I start dealing with more advanced stuff like dual world references.
1 note
·
View note
Text
Modern API Design Patterns for Custom Applications

In today’s fast-paced digital ecosystem, building scalable, maintainable, and efficient applications is more crucial than ever. Custom software developers play a vital role in this transformation by leveraging robust API design patterns to ensure seamless communication between services, apps, and systems. APIs are no longer just bridges between applications—they are core components of modern software architectures, especially for businesses looking to offer highly tailored solutions.
Let’s explore some of the most impactful API design patterns that are shaping how custom applications are being developed in 2025.
1. RESTful API: Still the Foundation
Although not exactly new, RESTful APIs continue to be a cornerstone in modern API architecture. They offer a straightforward approach to resource management using HTTP methods. The stateless nature of REST makes it ideal for scalable, modular application development.
Custom applications—whether web platforms or mobile solutions—rely heavily on REST for simplicity and broad compatibility. By adhering to REST principles, developers ensure that applications remain loosely coupled and easy to maintain or scale.
2. GraphQL: The Flexible Alternative
For applications requiring complex data fetching with minimal overhead, GraphQL has emerged as a powerful alternative to REST. Unlike REST, which requires multiple endpoints for different resources, GraphQL uses a single endpoint and allows clients to request exactly the data they need.
This precision is extremely valuable for frontend-heavy applications, such as SPAs (Single Page Applications) or mobile apps with bandwidth constraints. Custom software developers often use GraphQL to improve performance, reduce latency, and enhance the client experience.
3. gRPC: High-Performance Communication
Google’s gRPC is ideal for internal service-to-service communication. It’s especially useful in microservices architectures where speed and efficiency are critical. gRPC uses Protocol Buffers (Protobuf) for serialization, which is much faster than JSON.
gRPC supports bi-directional streaming and strong typing, which is great for building real-time applications like messaging platforms, live dashboards, or financial trading systems. For developers building custom enterprise systems, gRPC offers both speed and type safety.
4. API Gateway Pattern
As applications become more complex, managing multiple APIs efficiently becomes essential. That’s where the API Gateway pattern shines. Acting as a single entry point for all client requests, an API gateway handles routing, load balancing, authentication, and even caching.
This pattern simplifies client-side logic and secures backend services. For businesses offering multiple services or products through a single app, an API Gateway ensures smooth and secure communication without exposing internal architecture.
5. Backend for Frontend (BFF)
In multi-platform environments—where different interfaces like web, mobile, and IoT devices consume the same data—a Backend for Frontend (BFF) pattern is especially useful. Instead of one backend serving all clients, each client type has a specialized backend that caters to its unique needs.
This design reduces the complexity of frontend logic and improves performance. For example, a mobile app might need a trimmed-down response compared to the desktop web version. BFF allows for tailored responses without burdening a single backend with all variations.
Mobile App Considerations: Performance Meets Budget
Modern APIs also influence project costs, especially in mobile development. Choosing the right pattern can save time, money, and resources. This is where a mobile app cost calculator comes in handy. It helps estimate the cost implications of different architectural choices and API strategies before writing a single line of code.
If you're planning a mobile app and wondering how your API choices will affect the budget, try out a mobile app cost calculator to make data-driven decisions from day one.
Want to tailor your app’s API strategy for better performance and scalability? Book an Appointment with our experts and get personalized guidance for your project.
6. Event-Driven API Pattern
Real-time and asynchronous systems benefit greatly from event-driven APIs. Instead of waiting for client requests, these APIs push updates when events occur. This is useful for applications like notifications systems, stock tickers, or order tracking platforms.
Event-driven architecture typically uses tools like Kafka or WebSockets and is a powerful choice for building responsive, low-latency systems. It also enhances decoupling between services, improving maintainability and fault tolerance.
7. OpenAPI (Swagger) for Standardization
Standardization through tools like OpenAPI (formerly Swagger) helps ensure consistent API design across large teams. It allows developers to document APIs, generate client SDKs, and even auto-generate test cases.
For businesses relying on teams of custom software developers, OpenAPI fosters better collaboration and faster onboarding by providing a single source of truth for how APIs are structured and behave.
Wrapping Up: Building Future-Proof APIs
As application ecosystems continue to evolve, so too must the APIs that support them. Whether you're building mobile apps, enterprise dashboards, or IoT integrations, the right API design pattern can significantly impact your product’s performance, scalability, and maintainability.
From REST to GraphQL, and from API gateways to event-driven architectures, modern patterns provide flexibility to match a wide range of use cases. Investing in good API design not only enhances the developer experience but also delivers better end-user satisfaction.
If you're considering building or upgrading your digital product, now is the time to embrace these modern API design patterns. They��re not just trends—they're foundational to how applications will be built in the future.
Need help navigating these choices? We offer custom software development services tailored to your business needs. Reach out today and let's bring your vision to life.
0 notes
Text
From Edge to Cloud: Building Resilient IoT Systems with DataStreamX
Introduction
In today’s hyperconnected digital environment, real-time decision-making is no longer a luxury — it’s a necessity.
Whether it’s managing power grids, monitoring equipment in a factory, or ensuring freshness in a smart retail fridge, organizations need infrastructure that responds instantly to changes in data.
IoT (Internet of Things) has fueled this revolution by enabling devices to sense, collect, and transmit data. However, the true challenge lies in managing and processing this flood of information effectively. That’s where DataStreamX, a real-time data processing engine hosted on Cloudtopiaa, steps in.

Why Traditional IoT Architectures Fall Short
Most traditional IoT solutions rely heavily on cloud-only setups. Data travels from sensors to the cloud, gets processed, and then decisions are made.
This structure introduces major problems:
High Latency: Sending data to the cloud and waiting for a response is too slow for time-sensitive operations.
Reliability Issues: Network outages or poor connectivity can completely halt decision-making.
Inefficiency: Not all data needs to be processed centrally. Much of it can be filtered or processed at the source.
This leads to delayed reactions, overburdened networks, and ineffective systems — especially in mission-critical scenarios like healthcare, defense, or manufacturing.
Enter DataStreamX: What It Is and How It Helps
DataStreamX is a distributed, event-driven platform for processing, analyzing, and routing data as it’s generated, directly on Cloudtopiaa’s scalable infrastructure.
Think of it as the central nervous system of your IoT ecosystem.
Key Capabilities:
Streaming Data Pipelines: Build dynamic pipelines that connect sensors, processing logic, and storage in real time.
Edge-Cloud Synchronization: Process data at the edge while syncing critical insights to the cloud.
Secure Adapters & Connectors: Connect to various hardware, APIs, and databases without compromising security.
Real-Time Monitoring Dashboards: Visualize temperature, motion, voltage, and more as they happen.
Practical Use Case: Smart Industrial Cooling
Imagine a facility with 50+ machines, each generating heat and requiring constant cooling. Traditional cooling is either always-on (inefficient) or reactive (too late).
With DataStreamX:
Sensors track each machine’s temperature.
Edge Node (Cloudtopiaa gateway) uses a threshold rule: if temperature > 75°C, activate cooling.
DataStreamX receives and routes this alert.
Cooling system is triggered instantly.
Cloud dashboard stores logs and creates trend analysis.
Result: No overheating, lower energy costs, and smarter maintenance predictions.
Architecture Breakdown: Edge + Cloud
LayerComponentFunctionEdgeSensors, microcontrollersCollect dataEdge NodeLightweight processing unitFirst level filtering, logicCloudtopiaaDataStreamX engineProcess, store, trigger, visualizeFrontendDashboards, alertsInterface for decision makers
This hybrid model ensures that important decisions happen instantly, even if the cloud isn’t available. And when the connection is restored, everything resyncs automatically.
Advantages for Developers and Engineers
Developer-Friendly
Pre-built connectors for MQTT, HTTP, serial devices
JSON or binary data support
Low-code UI for building data pipelines
Enterprise-Grade Security
Encrypted transport layers
Role-based access control
Audit logs and traceability
Scalable and Flexible
From 10 sensors to 10,000
Auto-balancing workloads
Integrates with your existing APIs and cloud services
Ideal Use Cases
Smart Factories: Predictive maintenance, asset tracking
Healthcare IoT: Patient monitoring, emergency response
Smart Cities: Traffic control, environmental sensors
Retail Tech: Smart fridges, in-store behavior analytics
Utilities & Energy: Grid balancing, consumption forecasting
How to Get Started with DataStreamX
Step 1: Visit https://cloudtopiaa.com Step 2: Log in and navigate to the DataStreamX dashboard Step 3: Add an edge node and configure input/output data streams Step 4: Define business logic (e.g., thresholds, alerts) Step 5: Visualize and manage data in real-time
No coding? No problem. The UI makes it easy to drag, drop, and deploy.
Future Outlook: Smart Systems that Learn
Cloudtopiaa is working on intelligent feedback loops powered by machine learning — where DataStreamX not only responds to events, but learns from patterns.
Imagine a system that can predict when your machinery is likely to fail and take proactive action. Or, a city that automatically balances electricity demand before overloads occur.
This is the future of smart, resilient infrastructure — and it’s happening now.
Conclusion: Real-Time Is the New Standard
From agriculture to aerospace, real-time responsiveness is the hallmark of innovation. DataStreamX on Cloudtopiaa empowers businesses to:
React instantly
Operate reliably
Scale easily
Analyze intelligently
If you’re building smart solutions — whether it’s a smart farm or a smart building — this is your launchpad.
👉 Start your journey: https://cloudtopiaa.com
#cloudtopiaa#DataStreamX#RealTimeData#IoTSystems#EdgeComputing#SmartInfrastructure#DigitalTransformation#TechForGood
0 notes
Text
Web Services Development

In today’s connected world, web services act as the backbone of communication between applications. Whether you're building mobile apps, web platforms, or enterprise systems, understanding how to develop robust web services is essential for modern developers.
What are Web Services?
A web service is a software component that enables applications to communicate with each other over the internet using standardized protocols like HTTP, XML, or JSON. Web services allow interoperability between different software applications running on various platforms.
Types of Web Services
RESTful Web Services: Use HTTP methods (GET, POST, PUT, DELETE) and are based on REST architecture. Lightweight and widely used.
SOAP Web Services: Use XML-based messaging and offer more rigid structure and security, often used in enterprise systems.
GraphQL: A newer alternative that allows clients to request exactly the data they need.
Common Tools and Frameworks
Node.js (Express): Great for building lightweight REST APIs.
Spring Boot (Java): A robust framework for REST and SOAP services.
Django (Python): Offers built-in support for creating APIs via Django REST Framework.
ASP.NET (C#): Common in enterprise-level SOAP/REST applications.
Sample REST API in Node.js
const express = require('express'); const app = express(); app.get('/api/hello', (req, res) => { res.json({ message: 'Hello from the web service!' }); }); app.listen(3000, () => { console.log('Server running on port 3000'); });
Key Concepts to Understand
HTTP Methods and Status Codes
Authentication (API keys, OAuth, JWT)
Data Serialization (JSON, XML)
Cross-Origin Resource Sharing (CORS)
API Documentation (Swagger/OpenAPI)
Best Practices
Design APIs with clear endpoints and meaningful names.
Use proper status codes to indicate success or errors.
Secure your APIs using authentication and rate limiting.
Provide thorough documentation for developers.
Test APIs using tools like Postman or Insomnia.
Use Cases of Web Services
Mobile App Backends
Payment Gateways
Cloud-Based Services
Weather or Location APIs
Social Media Integration
Conclusion
Web services are critical for building scalable and flexible software systems. By mastering web service development, you’ll be able to connect applications, share data, and build feature-rich platforms that serve users across devices and platforms.
0 notes
Text

🚀 5 Python Full Stack Tricks You Must Know!
✅ Use DRF for APIs – Simplifies API dev with built-in auth & serialization.
✅ Dockerize Your App – Deploy anywhere with ease.
✅ Secure APIs with JWT – Strong authentication with JSON Web Tokens.
✅ Use Lazy Loading (React) – Boost performance by loading components on demand.
💡 Follow @pythonfullstackmasters for more tips!
🔥 Drop a 🔥 if you found this useful!
#PythonFullStack#Django#ReactJS#WebDev#FullStackTips#FullStackDeveloper#PythonDeveloper#WebDevelopment#CodingTips#ProgrammersLife#MERNvsPERN#FullStackLife#WebDesign#PythonTricks#SoftwareDeveloper#CodeNewbie
0 notes
Text
Do you want to know what every Java developer should know? We have shortlisted some of the highly recommended concepts and components of Java language for beginners and senior programmers. These things to learn in Java may help you get the best Java developer job you deserve. Java technology has evolved and has become really huge in the last decade. There are just too many things and its almost impossible for one person to master all of them. Your knowledge about Java technology will depend completely on what you working on. In any technology say Java or some other language, it is more important and valuable to know the language fundamentals thoroughly (OOP concepts, interfaces, class, objects, threading, etc.) rather than specific frameworks or syntax. It's always easy to quickly learn new technologies when you master the fundamentals. Are you are a beginner? Looking for some help and guidance on how to get started on this language, our exclusive article on How to Learn Java and Java libraries to know is a must read for you before getting started on Java. I just updated this article in November 2016 and things are more relevant to recent Java trends. Java Interview Preparation Tips Part 0: Things You Must Know For a Java Interview Part 1: Core Java Interview Questions Part 2: JDBC Interview Questions Part 3: Collections Framework Interview Questions Part 4: Threading Interview Questions Part 5: Serialization Interview Questions Part 6: Classpath Related Questions Part 7: Java Architect Scalability Questions Java developers knowledge expectation changes based on the profile. In this post I have divided it into 3 profiles: College Graduate, Experienced Java Developer, Experienced Java Web Developer. 7 Things a College graduate must know to get a Java developer job If you are a college graduate with no job experience then as a Java developer you need to understand the following basic things. How Java Virtual Machine works? e.g. (Platform Independence, Garbage Collection, class files, etc) What are the Object-Oriented Programming Concepts Implemented in Java? Multi-threading Java Collection framework Good understanding of data types and few of "java.lang" classes like String, Math, System, etc. java.io stream concepts. Understand the concept of Swing/AWT event-based programming. Do not spend a lot of time on this but understand the best practices. Servlets and JSP concepts. 9 Things an experienced Java Developer must know to thrive If you are an experienced professional then as a Java developer you may also need to understand the following basic things in addition to the ones listed above. Understand design patterns and its usage in Java Improvements in language from major version changes (Lambda, NIO, Generics, Annotations, Enums, ...). Coding Conventions. Build tool (Ant) or Project Management Tool (Maven). Version control System like GIT/SVN/Perforce/Clearcase. Apache Commons Libraries & few other common open source libraries. Continuous Integration Tools e.g. Jenkins and Hudson. Unit testing - e.g. JUnit and TestNG Unit testing Mocking libraries like Mockito Fundamental understanding of JSON and XML Understand Business layer frameworks - like Spring Understanding dependency injection (e.g. Spring, Google Guice, and Plain Java Dependency injection) 4 Things a Java Web Developer (JEE) Developer must know If you are an experienced professional working on Web-based development then as a JEE developer you also need to understand the following basic things in addition to the ones (7+9) listed above. Understanding of MVC Frameworks - Open source web frameworks like - Spring MVC, Struts, Vaadin, etc. Understanding of Microservice based framework like Spring Boot. Important Note: A lot of Front End UI development is now shifted to JavaScript frameworks. Therefore do not focus on Java-based frameworks that focus on the user interface (e.g. JSF or related frameworks).
Instead, learn JavaScript related frameworks like Angular.js or Backbone.js Fundamental understanding of Web Services and REST based service development. Good understanding of Web/Application server like Tomcat, Glassfish, WebLogic, WebSphere, Jetty, etc. Unix environment - A working knowledge of Unix environment can be beneficial as most of the Java servers are hosted on Unix based environment in production. Looking at the list of things it really feels difficult for a person to know each and everything in depth. As I already said it is more important and valuable to know the language fundamentals thoroughly and rest can be learned quickly when required. Can you think of something which is not part of this post? Please don't forget to share it with me in the comments section & I will try to include it in the list. Article Updates Article updated in April 2019 - Updated Introduction section, fixed minor text, and updated answers. Updated on November 2016 - Made changes as per latest technology trends and stacks.
0 notes
Text
API Vulnerabilities in Symfony: Common Risks & Fixes
Symfony is one of the most robust PHP frameworks used by enterprises and developers to build scalable and secure web applications. However, like any powerful framework, it’s not immune to security issues—especially when it comes to APIs. In this blog, we’ll explore common API vulnerabilities in Symfony, show real coding examples, and explain how to secure them effectively.

We'll also demonstrate how our Free Website Security Scanner helps identify these vulnerabilities before attackers do.
🚨 Common API Vulnerabilities in Symfony
Let’s dive into the key API vulnerabilities developers often overlook:
1. Improper Input Validation
Failure to sanitize input can lead to injection attacks.
❌ Vulnerable Code:
// src/Controller/ApiController.php public function getUser(Request $request) { $id = $request->query->get('id'); $user = $this->getDoctrine() ->getRepository(User::class) ->find("SELECT * FROM users WHERE id = $id"); return new JsonResponse($user); }
✅ Secure Code with Param Binding:
public function getUser(Request $request) { $id = (int)$request->query->get('id'); $user = $this->getDoctrine() ->getRepository(User::class) ->find($id); return new JsonResponse($user); }
Always validate and sanitize user input, especially IDs and query parameters.
2. Broken Authentication
APIs that don’t properly verify tokens or allow session hijacking are easy targets.
❌ Insecure Token Check:
if ($request->headers->get('Authorization') !== 'Bearer SECRET123') { throw new AccessDeniedHttpException('Unauthorized'); }
✅ Use Symfony’s Built-in Security:
# config/packages/security.yaml firewalls: api: pattern: ^/api/ stateless: true jwt: ~
Implement token validation using LexikJWTAuthenticationBundle to avoid manual and error-prone token checking.
3. Overexposed Data in JSON Responses
Sometimes API responses contain too much information, leading to data leakage.
❌ Unfiltered Response:
return $this->json($user); // Might include password hash or sensitive metadata
✅ Use Serialization Groups:
// src/Entity/User.php use Symfony\Component\Serializer\Annotation\Groups; class User { /** * @Groups("public") */ private $email; /** * @Groups("internal") */ private $password; } // In controller return $this->json($user, 200, [], ['groups' => 'public']);
Serialization groups help you filter sensitive fields based on context.
🛠️ How to Detect Symfony API Vulnerabilities for Free
📸 Screenshot of the Website Vulnerability Scanner tool homepage

Screenshot of the free tools webpage where you can access security assessment tools.
Manual code audits are helpful but time-consuming. You can use our free Website Security Checker to automatically scan for common security flaws including:
Open API endpoints
Broken authentication
Injection flaws
Insecure HTTP headers
🔎 Try it now: https://free.pentesttesting.com/
📸 Screenshot of an actual vulnerability report generated using the tool to check Website Vulnerability

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
✅ Our Web App Penetration Testing Services
For production apps and high-value APIs, we recommend deep testing beyond automated scans.
Our professional Web App Penetration Testing Services at Pentest Testing Corp. include:
Business logic testing
OWASP API Top 10 analysis
Manual exploitation & proof-of-concept
Detailed PDF reports
💼 Learn more: https://www.pentesttesting.com/web-app-penetration-testing-services/
📚 More Articles from Pentest Testing Corp.
For in-depth cybersecurity tips and tutorials, check out our main blog:
🔗 https://www.pentesttesting.com/blog/
Recent articles:
Laravel API Security Best Practices
XSS Mitigation in React Apps
Threat Modeling for SaaS Platforms
📬 Stay Updated: Subscribe to Our Newsletter
Join cybersecurity enthusiasts and professionals who subscribe to our weekly threat updates, tools, and exclusive research:
🔔 Subscribe on LinkedIn: https://www.linkedin.com/build-relation/newsletter-follow?entityUrn=7327563980778995713
💬 Final Thoughts
Symfony is powerful, but with great power comes great responsibility. Developers must understand API security vulnerabilities and patch them proactively. Use automated tools like ours for Website Security check, adopt secure coding practices, and consider penetration testing for maximum protection.
Happy Coding—and stay safe out there!
#cyber security#cybersecurity#data security#pentesting#security#coding#symfony#the security breach show#php#api
1 note
·
View note
Text
try: from kivy.app import App from kivymd.app import MDApp from kivy.uix.boxlayout import BoxLayout from kivymd.uix.button import MDRaisedButton from kivymd.uix.textfield import MDTextField from kivymd.uix.label import MDLabel import requests import qrcode from cryptography.fernet import Fernet from cryptography.hazmat.primitives import serialization, hashes from cryptography.hazmat.primitives.asymmetric import rsa, padding import hashlib import jwt import sounddevice as sd import numpy as np import os import json from datetime import datetime, timedelta except ModuleNotFoundError as e: print(f"Erro: {e}. Certifique-se de que todas as dependências estão instaladas.") exit(1)
SERVER_URL = "https://secure-chat.example.com" # Usar HTTPS em produção! TOKEN_FILE = "user_token.secure" KEY_FILE = "fernet_key.secure"
class SecureStorage: @staticmethod def generate_key(): if not os.path.exists(KEY_FILE): key = Fernet.generate_key() with open(KEY_FILE, "wb") as f: f.write(key)@staticmethod def get_fernet(): if not os.path.exists(KEY_FILE): SecureStorage.generate_key() with open(KEY_FILE, "rb") as f: return Fernet(f.read()) @staticmethod def save_token(token): SecureStorage.generate_key() encrypted_token = SecureStorage.get_fernet().encrypt(token.encode()) with open(TOKEN_FILE, "wb") as f: f.write(encrypted_token) @staticmethod def load_token(): try: with open(TOKEN_FILE, "rb") as f: return SecureStorage.get_fernet().decrypt(f.read()).decode() except FileNotFoundError: return None
class LoginScreen(BoxLayout): def init(self, **kwargs): super().init(orientation="vertical", **kwargs) self.username = MDTextField(hint_text="Usuário") self.add_widget(self.username) self.password = MDTextField(hint_text="Senha", password=True) self.add_widget(self.password) self.login_button = MDRaisedButton(text="Login", on_press=self.login) self.add_widget(self.login_button) self.register_button = MDRaisedButton(text="Registrar", on_press=self.register) self.add_widget(self.register_button) self.status_label = MDLabel(text="Bem-vindo! Faça login.") self.add_widget(self.status_label) def login(self, instance): try: hashed_password = hashlib.sha256(self.password.text.encode()).hexdigest() data = {"username": self.username.text, "password": hashed_password} response = requests.post(f"{SERVER_URL}/login", json=data, timeout=5) if response.status_code == 200: token = response.json().get("token") SecureStorage.save_token(token) app.switch_to_chat() else: self.status_label.text = "Credenciais inválidas!" except requests.RequestException: self.status_label.text = "Erro de conexão!" def register(self, instance): try: private_key = rsa.generate_private_key(public_exponent=65537, key_size=2048) public_key = private_key.public_key().public_bytes( encoding=serialization.Encoding.PEM, format=serialization.PublicFormat.SubjectPublicKeyInfo ).decode() hashed_password = hashlib.sha256(self.password.text.encode()).hexdigest() data = {"username": self.username.text, "password": hashed_password, "public_key": public_key} response = requests.post(f"{SERVER_URL}/register", json=data, timeout=5) self.status_label.text = response.json().get("message", "Erro desconhecido") except requests.RequestException: self.status_label.text = "Erro de conexão!"
class SecureMessengerApp(MDApp): def build(self): self.theme_cls.theme_style = "Dark" self.login_screen = LoginScreen() return self.login_screen
if name == "main": app = SecureMessengerApp() app.run()
Atenção: Não Verificado Ainda
0 notes