#latest jpg exploit
Explore tagged Tumblr posts
Text
Extremely Silent JPG Exploit ( NEW )

Hack within seconds.
Works on windows 32×64 bit , Linux , Android, iOS, Unix, device.
The exploit allows you to convert EXE, apk, jar, to .JPG file its coded 100% from scratch and used by private methods to assure a great stability and long lasting FUD time. You are able to attach it to all email providers and now a days everyone uses Internet so it gives a huge chance of success.
HACK ANY Windows, Linux , Android, iOS, Unix, device EASILY WITH THIS PRIVATE SILENT JPG EXPLOIT.
PACKAGE Content :
Ultra Hd Videos & Pdf For step By step Traning.
3 years Free Blackhat Dedicated Server.
1 year free blackhat team supports 24×7.
free Live Support Life time.
0 notes
Text
Someone recently claimed that the new Davies era of doctor who has no more wokism* than the show used to.
Now, maybe I've just changed in the past few decades, but from what I've heard of the 60th anniversary specials it does seem a tad more concentrated. Cherry-picking SPOILERS, sweeties.
- Donna got married offscreen. To what I can only assume is the last black cab driver in London.

- Her kid is trans. Specifically, non-binary, female presenting, says the wiki.** - In the next episode, we learn the Doctor is gay/bi when he thinks Sir Isaac Newton is hot. I'd smugly say this bit has no real relevance, but...the actual scene does carry the episode theme of accidentally changing reality. It's just the queer bit that seems tacked on. Though it does carry forward themes from 10s era. - Sir Zack himself is played by a half-Indian actor. It's not exactly hard to tell. I'm assuming they're running on Bridgerton logic. https://twitter.com/frozenaesthetic/status/1731332492282429950 - This episode is basically just Donna and the Doc exploring a weird location, and running into monsters, who happen to look like them. It would be a bottle episode, except for the large vfx budget. And yet ol' Rusty somehow managed to awkwardly wedge in an progressive issue. - In the next episode, the villain explains how he's just exploiting the divisions that already exist in human society, including cancel culture. - no wait he's got a point. Jpg - This is ironic, given that Davies and/or his broadcasting house masters are pretty blatantly on the team that a) coined the word, b) cancels people the most often, and c) defends the idea of Internet lynch mobs*** (***as long as they're left wing. If not, they're *ist "trolls", even if they're just complaining about the latest sacred cow.) Maybe the Davies was criticizing his own team. * Because the Toymaker was kind of racist back in the day (white dude dressed like a stereotypical Chinese dude), Davies made the new version a bit racist "as a callback to his original, problematic depiction back in 1966." - TVtropes, ref. DW Unleashed. On the other hand, the Toymaker also mocks and dresses as several other cultural archetypes. All the ones I've seen were white European ones. He just does this to everyone, apparently. - Toymaker also weaponizes the Spice Girls hit "Spice Up Your Life". No, I will not explain. Though I will note that a line about the "Yellow man in Timbuktu" was apparently drowned out in the episode. Probably for being a tad spicy. - One new UNIT character is a lady in a wheelchair. When the new Tardis - no, I will not explain - has a wheelchair ramp, she happily points it out. Which makes me wonder why the blue box would be so limited, considering it often deals with alien species. - Also, the same actress played a disabled Companion in the Big Finish audio dramas. I'm not sure why it was considered essential to do so in an entirely audio format, but there have been controversies over this sort of thing before (EG Artie on Glee, various racial voice acting controversies). - At this point, casting Ncuti Gatwa as 15 doesn't even register. Not really a blip on my radar. Black Doc? Whatevs. His sonic screwdriver has Rwandan words on it? So? I go to church with lots of Africans. Heck, I'm a black immigrant to ol' Blighty myself, just from the other side of the pond. Ncuti is, chronologically speaking, more British than I am. - Though given that he's Rwandan-Scottish, there may be some debate on the "British" part. - Wikipedia says the actor is pretty left-wing, but the actor seems good so far, so I'm willing to give him a sha-
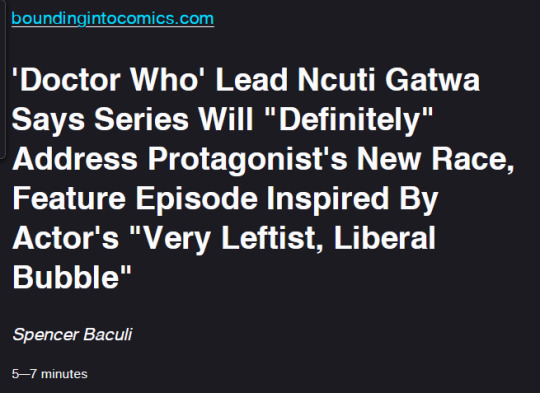
Oh, come ON!
Maybe the original person speaking was comparing it to the Chibnall “history has always been a whitewash” era, which had a character who was a paper thin Trump satire. A tad ironic, when the whole point of bringing Davies, Tennant, and Tate back is to play on nostalgia.
*Tangent: that word was apparently voted the most annoying words in English. Which is kind of hilarious if you know that it was originally created to self-describe certain progressives. And the "you can't even define that word!" meme was almost certainly ripped off from the right wing "what is a woman?" Meme. ** This is apparently because she's part Time Lord, through Donna. It seems a tad interesting to me that a few works featuring non binary characters happen to make them enby due to some sort of supernatural (Omniscient Reader) or sci-fi (SW Squadrons) influence which the vast majority of IRL enbies don't have. ...As far as I know.
26 notes
·
View notes
Link
#Crypter#hacker#amazon#buy latest hacking tools#buy jpg exploit#buy pdf exploit#buy xls exploit#buy latest exploits
0 notes
Text
It's possible to hack iPhones / iPads just by sending an email to targeted users.
It’s possible to hack iPhones / iPads just by sending an email to targeted users.
Zero-Day Warning: It’s Possible to Hack iPhones Just by Sending Emails Hackers have been exploiting critical 0-click + 0-day RCE vulnerability in the default mail app installed on millions of Apple devices. According to the researchers, there are two remote code execution flaws in Apple’s mail app, both existed for the last 8 years since the release of iOS 6 and also affect the latest iOS 13.4.1…
View On WordPress
1 note
·
View note
Text
Google Chrome 0day Exploit ( Latest Updated )

The exploit allows you to Silently Execute any EXE , jar , java , dll file’s using just website URL or server ip , its 100% FUD and completely undetectable by all antivirus . You are able to embed url to all email providers and now a days everyone uses Internet so it gives a huge chance of success.
PACKAGE Content :
Ultra HD Video & Pdf For step By step Training.
3 years Free Blackhat Dedicated Server.
1 year free blackhat team supports 24×7.
free Live Support .
Google Chrome Supported / Tested Versions – also work on Older versions
Chrome on Windows WORK WITH ALL VERSIONSChrome on macOS WORK WITH ALL VERSIONSChrome on Linux WORK WITH ALL VERSIONS
0 notes
Text
New DNS method to bypass icloud
New DNS method to bypass icloud much better and expanding possibilities #icloudbypass #iclouddnsbypass #ios12 #iphone #unlockicloud #iphonex #ipadpro
This is a new method for icloud lock devices. It is way better than Captive Portal. Doesn’t use DNS IP, no Proxy, no re-entering passwords every day!
Igor July the developer from icloud DNS Bypass just update his portal using the latest exploit for bypass icloud on any iOS device including the latest firmware version iOS 12.3.
iDNSPortal is extending possibilities of any icloud locked…
View On WordPress
1 note
·
View note
Text
Class War 06/2018: From Gaza to Iran to the whole World… Down with the exploiters!
Guerre de Classe | libcom.org news | March 19th 2018
CW6.jpg
In this text we want to put a spotlight on the events that shaking Iran last couple of weeks, events that go far beyond that, in the context of a region that consistently and for a long time stands on the forefront of the global class struggle...
read more
→ READ MORE ←
Get your Latest News From The Leftist Front on LeftPress.News → Support Us On Patreon! ←
#leftpress#news#resistance#politics#Tridni Valka#Iran#Iran protests 2017/18#Guerre de Classe#libcom.org news#Class War 06/2018: From Gaza to Iran to the whole World… Down with the exploiters!
1 note
·
View note
Text
5 Stages To Achievement In Speed Dating
You’ve stirred up the assurance to endeavor one of the latest Dating rates you’re going Rate Dating from Bumble.com. Here’s two or three hints to promise you expand your Do you Well done You’ve stirred up the assurance to endeavor one of the furies of the latest dating you’re going Pace Dating.

Bumble.com
Here’s two or three hints to promise you exploit your night.
1. Complete your work
View On WordPress
0 notes
Text
The 7 secrets of a $2-million-a-day man you can steal to win the lottery

The secrets of a giant winner revealed - can you improve your chances of winning using Billy Walters’ strategy?
Billy Walters was a Las Vegas-based sports gambler who sometimes spent up to $2 million a day and raked in hundreds of millions a year.
And now he reveals his philosophy. Although this article is about his own methods, you can look at each one and see how it adapts perfectly to the lottery player.
In fact, there's very little difference in the way he played, and us. Except for the amount of money he spends each time he plays, of course.
In an article written by David Duffield of Champion Bets, Billy reveals his secrets. It makes for a fascinating read.
A 37-year winning streak is basically unheard of in the gambling industry. But Walters has been able to achieve this and often bets more than a million dollars a game. He single-handedly moves the market.
Walters’ hundreds of millions of winnings have enabled him to build an empire that includes multiple mansions, golf courses, hotels, property development, car dealerships, a $20 million private jet and various other business interests.

Billy Walters boards his jet with 60 Minutes reporter Lara Logan (center) and wife Susan. PHOTO: 60 Minutes screenshot
Here are some lessons that punters can learn from a man described as the Michael Jordan and Warren Buffet of the sports betting world:
LESSON #1. Don't Expect Instant Success
Walters didn't succeed right from day one, in fact, he went broke many times. As a younger man he described himself as a gambling addict and compulsive loser. That seems to be a very common experience amongst gamblers who ultimately become very successful.
"I can assure you that every successful gambler I know has been through some monumental failures on his way to getting there."
Lottery Lesson: I talk a lot about the need for patience. Fact is, you're competing with millions of others number combinations, and your set won't come up each time. Keep playing and the numbers will eventually swing your way.
LESSON #2. Information Gives Him An Edge
Walters has surrounded himself with sharp minds and employs an array of experts in the roles of consultants, statisticians, mathematicians and computer programmers to help him compile, analyze and ultimately profit from huge amounts of information.
Many years ago Walters even employed people to coordinate with the Las Vegas airport cleaning crew to gather used newspapers from all the incoming flights. A team of readers would then analyze all of this information that most of the linesmakers and the general public were not aware of.
Lottery Lesson: The Silver Lotto Membership Site is the best way to stay current with the latest number trends. I have the best info for your winning strategy there.
LESSON #3. Value Is Everything In Both Business And Gambling
"If you value something at ten, then you're a buyer at eight and a seller at 12."
But this concept of value is very different from how most punters operate. They are very keen to back their chosen team or horse, and will do so without giving enough thought to a fair price.
Lottery Lesson: You can spend too much or too little to try and get your winning results. Use my recommendations and find the right amount to play with PRO Custom Profiles.
LESSON #4. The Bigger The Value, The Bigger The Bet
The Walters team produces their own lines and only bet when they are different to the market. Returns are enhanced by their wagering approach since the bigger the discrepancy (ie. estimated value or positive expectation), the bigger the bet.
He has incredible confidence in his own numbers and looks to exploit his advantage the most when that edge is the biggest. But success isn’t about making one big bet. Walters never lets it all ride on one game. instead, he spreads out his bankroll across many opportunities where he has a positive expectation
But we’re not talking huge margins. Simply tossing a coin will get you a 50% betting against the spread. A 52.4% winning percentage is required to be profitable. For all of his work and success, Walters winning strike-rate is ‘just’ 57%.
But the sheer volume of his bets and the ability to optimize his bankroll management has enabled him to amass hundreds of millions in profits.
Lottery Lesson: The only way to improve your odds is to play often. If you're playing larger games like Powerball or Mega Millions, you need to spend more than with a smaller game.
LESSON #5. There Will Be Drawdown
Walters may win every year, but he has previously said he has plenty of losing weeks and losing months.
Change is inevitable but some constants remain.
He succeeded by using the edge that came from reading all the small-town newspapers. But they died when the internet arrived. That is just one small example of how almost everything evolves.
So Walters adapts his approach to stay ahead of the game, but he still believes that the fundamentals of gambling success remain the same.
He says, "The game of handicapping sports is really the same game as it was 40 or 50 years ago. It’s much more competitive now, and the numbers are much better than they were in the 80s, but it’s still the same game. It still comes down to evaluating information."
Lottery Lesson: Nothing has changed with mathematical odds either. My System is the same as it was over 25 years ago and still gives increased wins.
LESSON #6. Computers Can Only Take You So Far
A feel for the market is also exceptionally important.
Billy Walters makes it clear when he states: "The computer whiz kids who are involved in sports today don’t have a clue, I mean a clue, about how to bet their money. They don't have a feel at all for which way the line is going to move. There is a big difference in knowing how to bet and when to bet your money in sports. It is almost as important as handicapping is."
LESSON #7. Don't Be In Denial
"A lot of people have a difficult time stepping back and doing a re-valuation..."
Long-term winners do exist. Walters success shows that it is actually possible to succeed in the betting world. It’s not easy, but he is living proof that it is definitely possible.
Lottery Lesson: If you have evaluated what game to play and when, then you need LottoPredict and PRO to speed up your win rate.
Winning takes persistence and a long-term view, something that Billy Walters follows with tremendous results.
RELATED: Follow this $2 million-a-day guy to increase your lottery winning chances this week
NOW WATCH: Billy Walters talks more about his strategy
The 7 secrets of a $2-million-a-day man you can steal to win the lottery published first on https://188lotosite.tumblr.com/
0 notes
Text
Libpng library gets fix for truly ancient bug
http://cyberparse.co.uk/2017/01/03/libpng-library-gets-fix-for-truly-ancient-bug/ https://i0.wp.com/cyberparse.co.uk/wp-content/uploads/2016/04/security-binary-pd-898757.jpg?fit=3888%2C2592
Where were you in June 1995? Coding image libraries? Let’s have a chat Slackware has raced out of the blocks in 2017, issuing one patch for the libpng image library on New Year’s Day, and two Mozilla patches on January 2. The libpng bug got its Common Vulnerabilities and Exposures number, CVE-2016-10087, on December 30.Slackware’s announcement says the bug can’t be exploited without active user input.
The “unlikely sequence” of events to exploit the NULL dereference bug is as follows: first, an application load a text chunk into the png structure; second, it deletes all text; third, another text chunk gets added to the same png structure. Unlikely, but, Slackware’s security team says, “it has happened”. Anyone else using libpng in a distribution or application will need to get the latest version of the library – because this bug has existed in png_set_text2() since June 1995.It was discovered and patched by Patrick Keshishian. The January 2 fixes cover Slackware’s Mozilla Thunderbird implementation and its Mozilla-based Seamonkey browser. The Thunderbird vulnerability has also been fixed in user clients.It’s a critical-rated use-after-free error when manipulating DOM events and audio elements, and was part of an eight-bug update issued on December 28. The Seamonkey fix brings Slackware up to date with version 2.46. ® Sponsored: Want to know more about Privileged Access Management? Visit The Register’s hub
Source The Register - Security
1 note
·
View note
Video
RAF at Exercise Red Flag 2017 by Defence Images Via Flickr: Pictured is a 51 Squadron RAF RC-135W Rivet Joint aircraft at Nellis Air Force Base in Nevada during Exercise Red Flag...RAF personnel took part in the world’s largest and most complex air combat exercise at Nellis Air Force Base in the United States. Exercise Red Flag is a three-week, 5th Generation exercise that sees friendly ‘Blue Forces’ compete against hostile ‘Red Force’ aggressors in live and synthetic training environments, simulating air-to-air, air-to-ground and space and cyber warfare.. .The training mirrors the threats and complex air defences posed by real-life adversaries, and helps participating nations better understand each other’s capabilities...The RC-135W Rivet Joint is a large, all-weather electronic surveillance aircraft based on the C-135 airframe...The RC-135W Rivet Joint is equipped with a variety of sensors, allowing its multi- disciplined crew to intercept and exploit emissions across the electromagnetic spectrum, providing both strategic and tactical level intelligence. ------------------------------------------------------- © Crown Copyright 2014 Photographer: Sgt Neil Bryden RAF Image 45162165.jpg from www.defenceimages.mod.uk This image is available for high resolution download at www.defenceimagery.mod.uk subject to the terms and conditions of the Open Government License at www.nationalarchives.gov.uk/doc/open-government-licence/. Search for image number 45162165.jpg For latest news visit www.gov.uk/government/organisations/ministry-of-defence Follow us: www.twitter.com/defenceimages
0 notes
Link
I forgot the best part. Now they're claiming Russia's behind creepy Joe being creepy.
If you thought the 2020 US presidential election might be a Russia-free affair, think again. The latest conspiracy taking hold online asserts that Moscow is behind the controversy over potential candidate Joe Biden’s creepy past.
Social media has long been chock-full of images and videos demonstrating Biden’s overly touchy-feely approach with women he came into (too much) contact with over the course of his political career.
The story grew into a bigger controversy, however, as multiple women came forward to accuse the former vice president of almost-harassment and stepping over personal boundaries in his interactions with them, which prompted many to wonder whether the scandal will hurt his chances if he decides to run for president in 2020, as expected.
Yet, despite the fact that commentators have been reflecting on the Democrat’s cringe-inducing handsy behavior for years, his supporters are smelling a nefarious Russian plot at play.

The entire scandal was probably cooked up by the Russians to “sow discord”within the Democratic Party, one tweeter claimed. Another suggested that the way the Biden story was being spread felt very “Russian-inspired.”


Russia has "unleashed" its online “trolls”against Biden...


Some took things even further, claiming that the so-called anti-Biden campaign wasn't new, but that Moscow had been "pushing this Biden propaganda for 2 years.”


Others engaged in full-fledged mental gymnastics, claiming that presidential candidate Bernie Sanders, Russia and the DNC (strange bedfellows) were all behind the “smear campaign” against Biden.

But the loony theories didn’t end there. What if the women accusing Biden of inappropriate touching are Russian “plants” designed to destroy his campaign?

Some pointed out that one of Biden’s accusers is a Sanders supporter with “a political ax to grind” which apparently invalidates her opinions on the former VP.

Maybe Russian President Vladimir Putin is not exactly behind the whole thing, but he and other “outside agitators” will still be "exploiting" it in 2020, another tweeter offered.
Former Vice President Joe Biden now finds himself engulfed in his own version of a #MeToo moment on the eve of launching his highly anticipated presidential campaign.
Last Friday, Nevada Democrat Lucy Flores came forward and accused the former vice president of inappropriately kissing her before a political rally in 2014. Since then, six additional women have come forward to accuse Biden of inappropriately touching them through the years.
Amy Lappos, a former congressional aide to Rep. Jim Himes (D-CT), claimed on that Biden rubbed noses with her and touched her inappropriately during a 2009 political fundraiser.
Then on Tuesday, two more woman came forward and told the New York Times “that the former vice president’s touches made them uncomfortable.”
The Huffington Post is now reporting on an additional three woman who said they had “uncomfortable physical encounters” with the 76-year-old Biden through the years.
Biden addressed the controversy in a video posted to social media on Wednesday, saying, “it’s the way I’ve always been” and adding that he would change his behavior going forward.
But, reporters were quick to point out that during the course of Biden’s two-minute video, he never actually apologized for his actions or to the woman whom he made uncomfortable.
How many women accused kavanaugh?
65 notes
·
View notes
Link
(शिशिर कुमार) प्राध्यापक, समाजवादी चिंतक, राजनेता और गरीब, पीड़ित, शोषित व आम लोगों के संघर्षों के हथियार यानी रघुवंश बाबू। यहां के लोग ज्यादातर पूर्व केंद्रीय मंत्री डॉ. रघुवंश प्रसाद सिंह को इसी नाम से जानते या संबोधन करते थे। जब भी शहर आते और सर्किट हाउस की कमरा संख्या 3 में रुकते। उनके आने की सूचना मात्र से कार्यकर्ता से लेकर आम लोगों का जमावड़ा लग जाता।
वे पार्टी से अधिक क्षेत्र की समस्या, अपने-पराये के बारे में जानकारी लेने से लेकर ठेठ गवई भाषा में पुराने समय के किस्से कहानियां सुनाते थे। थोड़ी-थोड़ी देर पर सामने वाले से सवालिया लहजे में जवाब भी लेते। राजद नेता इकबाल मो. शमी कहते हैं- उनकी कई बातें शहर-गांव के लोगों को अब बहुत याद आएगी। सर्किट हाउस के बरामदे पर सुबह में खादी की गंजी-धोती में लकड़ी की कुर्सी पर बैठना।
जाड़े में बाहर पेड़ के नीचे मजमा। सुबह टहलने के बाद दातून करते हुए लोगों की समस्या सुनने-सुनते आधा दातून खत्म हो जाता था। समस्या रखने वाले की पीड़ा के समाधान से पहले उसकी निराशा दूर हाे जाती थी। वे समस्या सुनने के बाद उसके समाधान के लिए हर तरह से लगते भी थे। हर सुख-दुख में पहुंचना तो आदतों में शुमार था। लॉकडाउन के दौरान के बाद भी वे कई समारोहों में पहुंचे।
इसी दौरान उन्हें कोरोना संक्रमण हुआ। ज्यादा न घूमने की सलाह दी गई तो पूछा- कोरोना है, तो अपने-पराये से मिलना छोड़ दें? सबसे बड़ी खासियत थी कि वे हर अखबार की अधिकतर खबर पढ़ते और समस्याओं काे लेकर लोगों से सच्चाई जानते। फिर बिना बुलाए पीड़ित से मिल कर आंदोलन खड़ा करते। राजनीति में कद बड़ा होने का तनिक गुमान नहीं। गांव-वार्ड में होने वाले छोटे संघर्षों में भी जमीन पर बैठ शामिल हो जाना। घंटों समय देना आदत थी।
साथ के लोग चलने के लिए कहते, तो उनका एक ही जवाब हाेता- छोड़ के चले जाएंगे तो ई बेचारा को कौन देखेगा? अनौपचारिक बातचीत में भी बड़े सहज, सरल भाषा में मुस्कुराते हुए गंभीर बातें कह जाते। इन बातों के कारण दलीय दीवार टूट जाती और वे सबके प्रिय रघुवंश बाबू हो गए। शहर और जिले को भी अब ये बातें खूब याद आएंगी।
Download Dainik Bhaskar App to read Latest Hindi News Today
Gone are the professors, socialist thinkers, politicians and weapons of struggle of the poor, oppressed, exploited and common people
from Dainik Bhaskar https://ift.tt/3hvHnQa
0 notes
Text
Lock Down Your Laptop With OpenBSD
In today's hyper-connected world, it grows increasingly important to have all devices that have an internet connection locked down- not for hiding data but to protect from having day-to-day life completely sabotaged. One may have already locked down their accounts and data about them online, but what if they want to "amp it up" to the next level?
The Problem
It's known that by using Windows or MacOS, you have agreed to Terms of Service that include the upload of their private files to their infrastructure- even if you didn't want it to go on the internet. In Microsoft-Land, this means all your files are scanned and uploaded to Microsoft's infrastructure where they can build a profile on you. Apple happens to engage in similar practices. On top of this, Windows is known for having the most viruses and rootkits in the world while MacOS currently has the record for the most adware in the world. Viruses and rootkits are basically system exploits, while adware is an attack on the web browser, forcing ads to pop up even if you have an ad blocker.
To add further discomfort, the leaks made by ex-CIA/NSA official Edward Snowden from years past verified that there is something called FISA court- a top secret US-based court of law that issues warrants for surveillance. Snowden took huge issues when he learned that the CIA and NSA built this program named XKeyScore, which behaves like a search engine that collects ALL information about people, including private things like Social Security Numbers and text messages. To do this, the FISA courts "rubber-stamped" (and still do) every surveillance request made by the CIA or NSA- allowing them to spy on U.S. Citizens without due process. Nowadays, laws have since been passed where FISA courts are irrelevant and the CIA and NSA can continue to do this.... And if the CIA and NSA are capable of gathering all the info you'd rather keep private, so is the stalker... or the creepy person next door... or the angry ex-husband/ex-wife...
Enter OpenBSD
OpenBSD began in 1995, where the founder Theo De Raadt took issue with the design approach of NetBSD- which traces it's ancestral roots all the way back to the original UNIX from the early 1980's. De Raadt was (and still is) a firm believer in correctness of code, extensive auditing of the code, and extreme levels of security. OpenBSD is widely considered to be the most secure Operating System on the planet, with the most bleeding edge technologies in cryptography and so on- to the point where some countries ban the OS for import even though that's unenforceable thanks to the internet. It is known for having sane and secure defaults in the installation, and several audits of the entire system's source code yearly. They are responsible for the invention of the applications sudo, openssl, libressl, ssh, pf, and pledge(). If familiar with any Linux/Unix command line, it's easy enough to notice that they invented some of the most common protocols utilized in locking down a system.
So let's get this set up on a laptop!
What You'll Need
A laptop with an Intel CPU that you don't mind wiping the hard drive of, ideally with an Intel Wireless AC 7260 wireless card or older
A 2 gb or larger flash drive
A wired and wireless network connection (We'll be messing with both)
An ethernet adapter if your laptop doesn't have an ethernet jack
For this installation, I used a Thinkpad T460 which has a 6th gen Intel i7 and (actually) an Intel Wireless AC 8260 WiFi Card.
Note: This tutorial is relevant to OpenBSD 6.7 and probably works for 6.6 as well. Because OpenBSD changes, the install method is subject to change over time as well.
Making The Install USB
First things first, we need to fetch a copy of the OpenBSD installer and flash it to our thumb drive. On Linux and MacOS, connect to the internet and run this command to download the image to your Downloads folder:
cd ~/Downloads && curl -OJ https://cdn.openbsd.org/pub/OpenBSD/6.7/amd64/install67.fs
Now for Linux, use lsblk to verify what the disk name is, or on MacOS use diskutil list to do the same.
Now run the command sudo dd if=~/Downloads/install67.fs of=/dev/<DISK> bs=1M, replacing <disk> with the name of the disk as recognized by the system. This will create the USB installer on these systems.
On Windows, download Win32DiskImager and download the OpenBSD image at [curl -OJ https://cdn.openbsd.org/pub/OpenBSD/6.4/amd64/install64.fs](curl -OJ https://cdn.openbsd.org/pub/OpenBSD/6.4/amd64/install64.fs). Use Win32DiskImager to flash OpenBSD to your thumb drive.
Booting The Installer
Great, we have our install USB. Now we need to power off, plug our Ethernet adapter in, connect the device via wired network, and plug our USB thumb drive in (while the machine is still off). Once this is done, pressing the power button again will show the boot screen and there's a key to spam to "Enter Setup". Commonly this is F12 or Delete. Here's an idea of what to look for:
A BIOS Boot Menu.
Use the arrow keys to highlight your USB and press "Enter" to boot from the OpenBSD Installer.
Performing The Installation
You should now be greeted by a terminal-based prompt asking you to (I)nstall, (U)pgrade, (A)utoinstall, or (S)hell:. We are going to type I here and press the enter key. Before we continue, it's important to note that the entire installation process is relatively simple in the sense that all the user needs to do is type the correct things in and the installer will do the rest.
First hurdle is the network connection- assuming you have an Intel wired network card (most laptops do), the ethernet device should be labelled em0 or em1. Configure this with dhcp. We cannot use wifi at the moment since the firmware isn't installed. It will also ask you if you wish to enable ssh, say no (this is a laptop) and don't allow root SSH login. Enable Xenodm- that's critical for a desktop, which can be configured later. You'll also be asked for the root user password and if you want to create additional users. for additional user creation, type your username and type a password.
We're almost done with the install! It will promptly ask what disk is your root disk. Since we're unsure, press ? and press enter. It should list something like
sd0: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX 254.3 G sd1: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX 15.6 G
Note: I redacted the names of my hard drives for privacy protection, but you will see the hard drive name and a little additional info in place of the X'es.
Awesome! Since we know we want to install to sd0 now, we type that in and press enter.
The last thing the installer needs is information on the "Location of Sets". This is BSD speak for where to find the files to install to the disk are. Since we have a network connection, let's use it and type http. It will promptly ask for a mirror, so type 1 and press enter (this will select the fastest mirror for you). Then press enter again.
There's a prompt to deselect sets you don't wish to install. This is for a more advanced installation and unnecessary as the default install is only 500-600 mb anyway. Proceed and continue with the install and it will fetch the latest and greatest OpenBSD software for your OS and install it for you. When done, the user just needs to hit "reboot" and remove the thumb drive.
Getting WiFi Working
All firmware will automatically install if you left the ethernet cable in after rebooting from the installer. Before rebooting to use the new firmware, let's apply the latest and greatest security patches for our system to finish the installation. Login as the "root" user and open a terminal. Now type syspatch and wait a few minutes for this to complete. When done, we can type halt -p to poweroff the system. From here, we can remove the ethernet cable and power back on.
Once the bootup is completed, we need to log in the "root" user once more to build our wireless configuration file, called hostname.if. First things first, run ifconfig in the terminal to verify the wireless card's name. The 3 most common ones to encounter are iwm, iwn and ath with a number following them. In my case, my wireless card is recognized as iwm0 and will use that for the rest of my examples. From here on out, replace iwm0 with the name of your WiFi card.
Let's scan for WiFi Networks by running the following commands in the terminal:
ifconfig iwm0 up ifconfig iwm0 scan
The first command gives the WiFi card some juice, the other scans for networks and returns the results. Read these results and look for something saying nwid, SSID, or BSSID. This is the name of the network to connect to. Make a note of this.
Now, we need to put contents in /etc/hostname.iwm0 (again, replace iwm0 with the name of your card!) Type vi /etc/hostname.iwm0 and a text editor will open, called vi.
Press the I key to enter "insert mode", and type the following:
# This Config File Designed by c0ffee.net join "YOUR_SSID" wpakey "YOUR_PASSPHRASE" # Swap with Your WiFi # you can specify other networks here too, in order of priority: # join "WORK_SSID" wpakey "WORK_PASSPHRASE" # join "OPEN_COFFEE_SHOP" dhcp inet6 autoconf up powersave
When done, press the Esc key then type in sequence :wq to save and exit. What we just did was told OpenBSD to automatically attempt connecting to the wireless hotspot you specified, then attempt to get an IP (network) address and give the card some juice. You can add more WiFi hotspots as time goes on to this config as well and it will attempt to connect in order of first to last.
With this done, reboot the system and during boot you should see mention of "Lease Accepted" for your WiFi card.
SUCCESS!
With the basic installation out of the way, stick around for part 2 where we configure a desktop to go with this nice new OpenBSD installation.
Source: C0ffee.net
Liked This Content? Check Out Our Discord Community and Become an email subscriber!
0 notes
Text
Facebook accidentally allowed 5,000 app developers access data of inactive users way past its expiration date
TheTechMedia.com/wp-content/uploads/2019/12/facebook-featured-tech-portal-300×169.jpg 300w, https://TheTechMedia.com/wp-content/uploads/2019/12/facebook-featured-tech-portal-768×432.jpg 768w, https://TheTechMedia.com/wp-content/uploads/2019/12/facebook-featured-tech-portal-1536×864.jpg 1536w, https://TheTechMedia.com/wp-content/uploads/2019/12/facebook-featured-tech-portal-800×450.jpg 800w, https://TheTechMedia.com/wp-content/uploads/2019/12/facebook-featured-tech-portal-1160×653.jpg 1160w, https://TheTechMedia.com/wp-content/uploads/2019/12/facebook-featured-tech-portal.jpg 1920w” sizes=”(max-width: 1024px) 100vw, 1024px”>
Facebook and privacy just don’t go together, as has been proven by the countless occasions where the platform has slipped up. However, the latest debacle, where the company let 5,000 app developers siphon off data of inactive users way past the 90 months expiration date, will take the cake for being the most threatening display of negligence, at least for this week.
However, we still have 3 days left, so who can be sure?
Cambridge Analytica, and the uproar it caused, was a wake up call for the company. It had 2 choices. It could have either lost all its goodwill in the market, with bad faith slowly turning the platform into history, or it could tweak its privacy settings. It’s fair to say, making the choice wasn’t that hard, and in 2018, Facebook brought a change to how it handles data of inactive users.
The company said that after a 3 month period, users who have been absent from the platform will have their data become off limits to app developers. The developers could no longer access said data, unless the user comes back to the platform and gives the permission to do so, once again. However, as it turns out, the company did not actually follow through as rigorously as it should have, and now, user data is in jeopardy, once again.
The way this latest loophole was exploited is almost too reckless. While the company made sure that no user data was sent to developers directly, the indirect channels were not plugged off. While inactive user data was not allowed to slip every time, it happened at various other instances, which were not a part of the direct sending of data. “For example, this could happen if someone used a fitness app to invite their friends from their hometown to a workout, but we didn’t recognize that some of their friends had been inactive for many months,” Facebook said in its blog post.
The company tried to defend itself by saying that it “hasn’t seen evidence that this issue resulted in sharing information that was inconsistent with the permissions people gave when they logged in using Facebook,” but the question lingers: ‘Is that enough?’
The company added that it has now fixed the issue, which according to its estimates, this issue enabled approximately 5,000 developers to continue receiving information including language or gender.
Facebook has added the opportunity for developers to access some parts of a user’s profile, so that they can log into the app with just a single tap, a feature many of us love. This subset of a profile, can give developers access to email, user likes, gender, location, birthday, age range, and other crucial data that needs to be handled responsibly.
The company also said that it was introducing new Platform Terms and Developer Policies to “ensure businesses and developers clearly understand their responsibility to safeguard data and respect people’s privacy when using our platform.”
These new terms would effectively limit the amount of information developers can share with third parties without explicit consent from people. “They also strengthen data security requirements and clarify when developers must delete data,” the company added.
from WordPress https://ift.tt/3dVXRiT via IFTTT
0 notes
Text
Hackers have promised a jailbreak for any iPhone 13.5
Hackers have promised a jailbreak for any iPhone 13.5
US, WASHINGTON (ORDO NEWS) — The hacker team unc0ver promised to soon jailbreak any device with the latest version of the Apple operating system, iOS 13.5, in open access. The master key will work even with new models such as the iPhone 11, iPhone SE and iPad Pro 2020.
The previous unc0ver jailbreak version was based on the checkm8 exploit, which was created last year. The main one for him was…
View On WordPress
0 notes
