#linuxinside
Explore tagged Tumblr posts
Link
If you are trying to install a new Ubuntu version or just want to see how a new version of Ubuntu looks like, then the best way to do so is to create and use a Live USB aka Ubuntu bootable USB.
Not only can we install or test Ubuntu, but we can also use it as a personal operating system that can be used on any Laptop or Desktop without having to make any major changes to the systems.
You will need the following to create a Ubuntu Bootable USB from the command line or CLI,
USB drive / Pendrive with at least 4 GB capacity Ubuntu ISO file (get it from HERE Get Ubuntu | Download | Ubuntu) a Linux system (here we are using Ubuntu only but this tutorial will work for all Linux systems)
Once you have all these then, we can proceed to create a Ubuntu Bootable USB.
#Linux#linuxfan#linuxadmin#linuxindonesia#linuxday#linuxuserofficial#linuxcrew#linux4ever#linuxuser#linuxubuntu#linuxbased#linuxpro#linuxpenguin#linuxisbetter#linuxinside#linuxer#linuxhost#linuxcommunity#linuxcentos#linuxforever#linuxforhumanbeings#devops#devopscommunity#devopslife#devopsnotes#DevOpsGuys#DevOpsHandbook#devopsinuk#devopsengineer#ubuntu
2 notes
·
View notes
Photo

Please! #sudo #coffee #linuxinside #linux (em Elmar Processamento De Dados Ltda)
0 notes
Text
System76 News: A May With Zing!

The force was with us in May, as we have a ton of fun updates for you! See what’s new regarding hardware, manufacturing, and accessories, and what’s in the works for Pop!_OS and our open firmware.
HARDWARE
In case you missed it, we recently announced that a new Gazelle laptop will be released soon! Gazelle has both 15” and 17” options and comes loaded with a 9th Gen Intel Core i7 CPU, an NVIDIA 16-series GPU, and up to 64GB RAM. Gazelle’s trifecta of CPU, GPU, and Memory gives content creators, gamers, animators, and designers a machine that can keep up with their graphics-heavy workloads. Head over to the product page to be notified when it releases this summer!
MANUFACTURING
“Brace” yourself for these manufacturing tweaks to Thelio Major:
A new power supply brace, GPU brace, and PCI bracket improve stability within Thelio Major’s interior, especially during shipping. Similarly, modifications were made to the CPU heat sink duct to better hold the heat sink in place while in transit.
ACCESSORIES
UK keyboard layouts are currently available on the Oryx Pro and Darter Pro! Though this keyboard layout is only available for a limited time, this option could stick around depending on popularity.
POP!_OS
Features
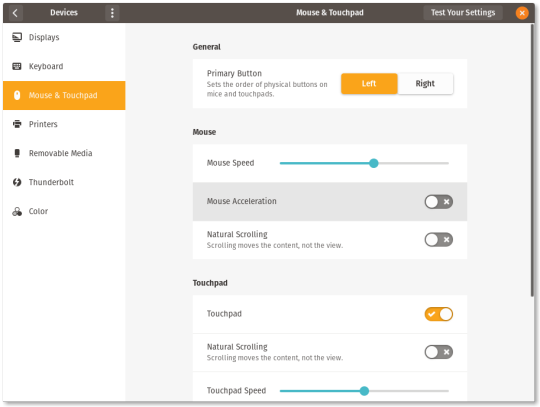
The ability to disable mouse acceleration has been added to GNOME Settings in Pop!_OS 19.04. Disabling mouse acceleration allows for the increased precision of mouse movements desired by PC gamers, artists, and designers for their unique use cases that depend on mouse accuracy. This patch was previously submitted upstream to GNOME by Mathew Bouma, but was not accepted. However, we’ve decided to include the patch as an option in Settings rather than through the GNOME Tweak Tool utility, as this feature has been highly requested among Pop!_OS users.
Graphics
VAAPI / VDPAU hardware decoding is now enabled by default for open source graphics drivers and the proprietary NVIDIA driver. This enables hardware decoding of supported video codecs in supported video players such as MPV. This can drastically reduce power consumption and CPU workload by offloading the expensive decoding tasks to dedicated hardware included alongside the graphics chip that was built specifically for those video decoding algorithms. This does not apply to Chromium or Firefox, however, as both of these browsers lack support for hardware decoding on Linux entirely.
System76-Power
Support for handling multiple hwmon interfaces for multiple I/O boards and CPUs was added to system76-power to combat excessive fan usage. This should reduce the amount of noise generated by fans on desktops that are affected by this criteria. A much quieter fan curve is also in the works and will arrive soon.
Security
Patches have already been released for Intel’s latest security vulnerabilities. To apply these patches, users are advised to install all available updates and reboot. These patches address the following security vulnerabilities:
- CVE-2018-12126 Microarchitectural Store Buffer Data Sampling (MSBDS)
- CVE-2018-12130 Microarchitectural Fill Buffer Data Sampling (MFBDS)
- CVE-2018-12127 Microarchitectural Load Port Data Sampling (MLPDS)
- CVE-2019-11091 Microarchitectural Data Sampling Uncacheable Memory (MDSUM)
Fixes
We’ve updated the youtube-dl package to a newer version. This package, maintained by Debian and Canonical, is used for downloading videos from YouTube. Changes made by Google to the YouTube API had recently broken this package in the Ubuntu repositories, hence the update.
Spacing issues between labels and icons in the Files side panel have been fixed as well. If you see any other issues with the GTK theme in 19.04, be sure to submit an issue report!
Pop Upgrade Progress
The new upgrade process for Pop!_OS is almost done! Though not yet implemented, the following changes have been made to Pop!_OS upgrading in May.
The option for keeping or disabling third party repositories was added to the upgrade daemon. Currently, third party repositories are disabled by default during an upgrade, which can interrupt a user’s workflow for certain applications.
Support for the Refresh OS option has also been added to GNOME Settings. Selecting this option will prepare the system to boot into the recovery partition on the next boot, and to ask to perform a refresh install. This allows you to skip setup for the language and keyboard settings, and to go straight to the refresh view.
Pop Upgrade: The Recovery Shell
The recovery shell was implemented this month, which opens a terminal to allow the user to manually recover from an error that prevents an upgrade from completing. Once the terminal is closed, the upgrade will be re-attempted.
Pop!_Volunteers This Week
@derpOmattic has submitted a handful of DEP11 appstream metadata: GNOME Authenticator, Lollypop, & PulseEffects. The addition of these apps to the Pop!_Shop was made possible through the help of @stratact and his DEP11 convertor. MR
@derpOmattic added the appstream metadata for Alacritty and TimeShift. MR
@adminxvii implemented checksum verification in Popsicle. MR
FIRMWARE
In open firmware news, the camera toggle hotkey is now functional. The last remaining hardware issues with running open firmware on our laptops lie with Thunderbolt. On Whiskey Lake chipsets, the Thunderbolt controller is often not in a functional state after suspending/resuming the system. On Kaby Lake chipsets, the Thunderbolt controller is never visible.
A new BIOS setup menu is also being designed for our open firmware so that the look and feel is consistent with the beautiful aesthetic you can expect from a System76 product. This will be implemented once the new firmware is ready for release.
EVENTS

LFNW Recap
System76 was at LinuxFest Northwest! We hope you all had a chance to stop by and meet our support team. They had a blast speaking with all of you! In case you missed out on some fun things like the Jupiter Broadcasting barbecue or Emma’s talk on the importance of being HAPPY in tech support, you can see our recap of the event on our blog.
19.04 Pop!_Party Recap
A long time ago (May 4th), in a factory far, far away (Denver), we hosted a fun release party for Pop!_OS 19.04. Partygoers enjoyed Star Wars-themed food, such as Hanburgers and Jabba the Hutt dogs, trivia, a tour of the factory, and brought some swag home, too!
PRESS
Pop!_OS Makes Classic Gnome Simpler
Jack M. Germain provides an in-depth review of Pop!_OS in this LinuxInsider article.
Opensource.com: System76’s Secret Sauce
Don Watkins of Opensource.com explores the “secret sauce” of System76 and the flavor that it adds to our culture and community.
Level1Tech Reviews Thelio
Wendell from Level1Tech has been busy this month on the Linux playground, testing out both Pop!_OS and Thelio.
4 notes
·
View notes
Photo

#archlinux #linux #opensource #codinglife #developer #programmer #webdeveloper #devops #vim #neovim #dwm #xfce #thinkpad #x1carbon #vortexgear #pok3r #curved #desksetup #desk #keyboard #mechanicalkeyboard #cherry #mxblue #zsh #ohmyzsh #shell #bash #linuxinside #docker #tux https://www.instagram.com/p/B7vvTC0Ch0a/?igshid=1mcnsolexvq8i
#archlinux#linux#opensource#codinglife#developer#programmer#webdeveloper#devops#vim#neovim#dwm#xfce#thinkpad#x1carbon#vortexgear#pok3r#curved#desksetup#desk#keyboard#mechanicalkeyboard#cherry#mxblue#zsh#ohmyzsh#shell#bash#linuxinside#docker#tux
0 notes
Text
Android Apps Riskier Than Ever: Report

Widespread use of unpatched open source code in the most popular Android apps distributed by Google Play has caused significant security vulnerabilities, suggests an American Consumer Institute report released Wednesday. Thirty-two percent -- or 105 apps out of 330 of the most popular apps in 16 categories sampled -- averaged 19 vulnerabilities per app, according to the report, titled "How Safe Are Popular Apps? A Study of Critical Vulnerabilities and Why Consumers Should Care." Researchers found critical vulnerabilities in many common applications, including some of the most popular banking, event ticket purchasing, sports and travel apps. Distribution of Vulnerabilities Based on Security Risk Severity ACI, a nonprofit consumer education and research organization, released the report to spearhead a public education campaign to encourage app vendors and developers to address the worsening security crisis before government regulations impose controls over Android and open source code development, said Steve Pociask, CEO of the institute. The ACI will present the report in Washington D.C. on Wednesday, at a public panel attended by congressional committee members and staff. The session is open to the public. "There were 40,000 known open source vulnerabilities in the last 17 years, and one-third of them came last year," ACI's Pociask told LinuxInsider. That is a significant cause for concern, given that 90 percent of all software in use today contains open source software components.
Pushing the Standards
ACI decided the public panel would be a good venue to start educating consumers and the industry about security failings that infect Android apps, said Pociask. The report is meant to be a starting point to determine whether developers and app vendors are keeping up with disclosed vulnerabilities. "We know that hackers certainly are," Pociask remarked. "In a way, we are giving ... a road map to hackers to get in." The goal is to ward off the need for eventual government controls on software by creating a public dialog that addresses several essential questions. Given the study's results, consumers and legislators need to know if app vendors and developers are slow to update because of the expense, or merely complacent about security. Other essential unanswered questions, according to Pociask, include the following: Do the vendors notify users of the need to update apps? To what extent are customers updating apps? Not everyone relies on auto update on the Android platform, he noted. "Some vendors outsource their software development to fit their budget and don't follow up on vulnerabilities," Pociask said. Having the government step in can produce detrimental consequences, he warned. Sometimes the solutions imposed are not flexible, and they can discourage innovation. "It is important for the industry to get itself in order regarding privacy requirements, spoofing phone numbers and security issues," said Pociask.
Report Parameters
Businesses struggle to provide adequate protection for consumer personal information and privacy. Governments in California and the European Union have been putting more aggressive consumer privacy laws in place. Americans have become more aware of how vulnerable to theft their data is, according to the report. One seemingly indispensable device that most consumers and businesses use is a smartphone. However, the apps on it may be one of the most serious data and privacy security risks, the report notes. Researchers tested 330 of the most popular Android apps on the Google Play Store during the first week in August. ACI's research team used a binary code scanner -- Clarity, developed by Insignary -- to examine the APK files. Rather than focus on a random sampling of Google Play Store apps, ACI researchers reported on the largest or most popular apps in categories. Most of the apps are distributed within the United States. Researchers picked 10 top apps in each of the 33 categories in the Play store.
Factoring the Results
Results were charted as critical, high, medium and low vulnerability scores. Of 330 tested apps, 105 -- or 32 percent -- contained vulnerabilities. Of those identified, 43 percent either were critical or high risk, based on the national vulnerability database, according to the report. "We based our study on the most popular apps in each category. Who knows how much worse the untested apps are in terms of vulnerabilities?" Pociask asked. In the apps sampled, 1,978 vulnerabilities were found across all severity levels, and 43 percent of the discovered vulnerabilities were deemed high-risk or critical. Approximately 19 vulnerabilities existed per app. The report provides the names of some apps as examples of the various ways vendors deal with vulnerabilities. Critical vulnerabilities were found in many common applications, including some of the most popular banking, event ticket purchasing, sports and travel apps. For example, Bank of America had 34 critical vulnerabilities, and Wells Fargo had 35 critical vulnerabilities. Vivid Seats had 19 critical and five high vulnerabilities. A few weeks later, researchers retested some of the apps that initially tested way out of range. They found that the two banking apps had been cleaned up with updates. However, the Vivid Seats app still had vulnerabilities, said Pociask.
Indications for Remedies
More effective governance is critical to addressing "threats such as compromised consumer devices, stolen data, and other malicious activity including identity theft, fraud or corporate espionage," states the report. These results increasingly have been taking center stage, noted the researchers. The ACI study recommends that Android app developers scan their binary files to ensure that they catch and address all known security vulnerabilities. The study also stresses the urgency and need for apps providers to develop best practices now, in order to reduce risks and prevent a backlash from the public and policymakers. The researchers highlighted the complacency that many app providers have exhibited in failing to keep their software adequately protected against known open source vulnerabilities that leave consumers, businesses and governments open to hacker attacks, with potentially disastrous results. Note: Google routinely scans apps for malware, but it does not oversee the vulnerabilities that could allow them. "We want to create a lot more awareness for the need to update the vulnerabilities quickly and diligently. There is a need to push out the updates and notify consumers. The industries should get involved in defining best practices with some sort of recognizable safety seal or rating or certification," Pociask said.
App Maker or User Problem?
This current ACI report, along with others providing similar indications about software vulnerabilities, concerns an area many app users and vendors seem to ignore. That situation is exacerbated by hackers finding new ways to trick users into allowing them access to their devices and networks. "Posing as real apps on an accredited platform like the Google Play Store makes this type of malicious activity all the more harmful to unsuspecting users," said Timur Kovalev, chief technology officer at Untangle. It is critical for app users to be aware that hackers do not care who becomes their next victim, he told LinuxInsider. Everyone has data and private information that can be stolen and sold. App users must realize that while hackers want to gain access and control of their devices, most also will try to infiltrate a network that the device connects to. Once this happens, any device connected to that network is at risk, Kovalev explained. Even if an app maker is conscientious about security and follows best practices, other vulnerable apps or malware on Android devices can put users at risk, noted Sam Bakken, senior product marketing manager at OneSpan. "App makers need to protect their apps' runtime against external threats over which they don't have control, such as malware or other benign but vulnerable apps," he told LinuxInsider.
Part of the Problem Cycle
The issue of unpatched vulnerabilities makes the ongoing situation of malicious apps more troublesome. Malicious apps have been a consistent problem for the Google Play Store, said Chris Morales, head of security analytics at Vectra. Unlike Apple, Google does not maintain strict control over the applications developed using the Android software development kit. "Google used to perform basic checks to validate an app is safe for distribution in the Google Play Store, but the scale of apps that exists today and are submitted on a daily basis means it has become very difficult for Google to keep up," Morales told LinuxInsider. Google has implemented new machine learning models and techniques within the past year, he pointed out, in an effort to improve the company's ability to detect abuse -- such as impersonation, inappropriate content or malware. "While these techniques have proven effective at reducing the total number of malicious apps in the Google Play Store, there will always be vulnerabilities in application code that get by Google's validation," noted Morales. Developers still need to address the problem of malicious or vulnerable apps that could be exploited after being installed on a mobile device. That would be handled by applying machine learning models and techniques on the device and on the network. That would help to identify malicious behaviors that would occur after an app is already installed and bypassed the Google security checks, Morales explained.
Time for Big Brother?
Having government agencies step in to impose solutions may lead to further problems. Rather than a one-size-fits-all solution, ACI's Pociask prefers a system of priorities. "Let's see if the industry can come up with something before government regulations are imposed. Getting a knee-jerk reaction right now would be the wrong thing to do in terms of imposing a solution," he cautioned. Still, personal devices are the user's responsibility. Users need to take more accountability with regards to what apps they are allowing on their devices, insisted Untangle's Kovalev. "Government intervention at this time is likely not needed, as both users and Google can take additional actions to protect themselves against malicious apps," he said.
Frameworks Exist
Dealing with unpatched Android apps may not need massive efforts to reinvent the wheel. Two potential starting points already are available, according to OneSpan's Bakken. One is the U.S. National Institute of Standards and Technology, or NIST. It has guidelines for vetting mobile apps, which lay out a process for ensuring that mobile apps comply with an organization's mobile security requirement. "This can help an enterprise, for example, to keep some vulnerable mobile apps out of their environment, but instituting such a program is no small feat. It's also simply guidance at this point," said Bakken. The other starting point could be the Federal Institutions Examination Council, or FFIEC, which provides some guidance for examiners to evaluate a financial institution's management of mobile financial services risk. It also provides some safeguards an institution should implement to secure the mobile financial services they offer, including mobile apps. "In the end, the effectiveness of any government intervention really depends on enforcement. It's likely that any intervention would focus on a specific industry or industries, meaning not all mobile app genres would be in scope," Bakken said. "That means that developers of some mobile apps for consumers would not necessarily have any incentive to secure their apps."
What Needs to Happen?
One major solution focuses on patching the Google Play platform. Joining the platform is straightforward, according to Kovalev. Developers complete four basic steps and pay a fee. Once joined, developers can upload their apps. Google processes them through a basic code check. Often, malicious apps do not appear to be malicious, as they have been programmed with a time-delay for malicious code to be executed, he noted. "To combat these malicious apps, Google has begun to implement better vetting techniques -- like AI learning and providing rewards to white hat pros who hunt down and surface these malicious apps," Kovalev said. While these techniques have helped to pinpoint malicious apps, the apps should be vetted more thoroughly prior to being publicly available to unsuspecting users, he stressed.
Final Solution
The ultimate fix for broken Android apps rests with app makers themselves, OneSpan's Bakken said. They are in the best position to lead the charge. He offered this checklist for mobile app developers: Do threat modeling and include security in product requirements. Provide secure code training to Android developers. Do security testing of their apps on a regular basis as part of the development cycle. Fix identified vulnerabilities as they go. Submit their apps to penetration testing prior to release. "And then, finally, they should proactively strengthen their app with app-shielding technology that includes runtime protection," Baken said, "so the app itself is protected, even in untrusted and potentially insecure mobile environments, to mitigate external threats from malware and other vulnerable apps." Read the full article
0 notes
Text
IoT alimenta crescimento de malware Linux

Malware que visa sistemas Linux está crescendo, em grande parte devido à proliferação de dispositivos criados para se conectar à Internet das coisas.
Essa é uma das descobertas em um relatório WatchGuard Technologies, um fabricante de dispositivos de segurança de rede, lançado na semana passada.
O relatório, que analisa os dados coletados de mais de 26.000 aparelhos em todo o mundo, encontrou três programas de malware Linux nos 10 melhores do primeiro trimestre do ano, em comparação com apenas um durante o período anterior.
“Os ataques e malwares do Linux estão aumentando”, escreveu o diretor de atenção da WatchGuard Corey Nachreiner e o analista de ameaças da segurança Marc Laliberte, co-autores do relatório. “Nós acreditamos que isso é porque as fraquezas sistêmicas nos dispositivos IoT, emparelhados com seu rápido crescimento, estão dirigindo autores de botnet para a plataforma Linux”.
No entanto, “o bloqueio de Telnet e SSH de entrada, juntamente com o uso de senhas administrativas complexas, pode impedir a grande maioria dos possíveis ataques”, sugeriram.
“Os atacantes podem ter acesso a essas interfaces vulneráveis, depois carregar e executar o código malicioso de sua escolha”, disse Fletcher.
Os fabricantes freqüentemente têm configurações padrão precárias para seus dispositivos, ele apontou.
“Muitas vezes, as contas de administrador têm senhas em branco ou senhas padrão fáceis de adivinhar, como” senha123 “, disse Fletcher.
Os problemas de segurança geralmente não são “nada específico do Linux per se”, disse Johannes B. Ullrich, diretor de pesquisa do Instituto SANS.
“O fabricante é descuidado sobre como eles configuraram o dispositivo, então eles tornam trivial a exploração desses dispositivos”, disse ele ao LinuxInsider.
Malware no Top 10
Esses programas de malware Linux criaram o top 10 no recorde do WatchGuard no primeiro trimestre:
Linux / Exploit, que captura vários trojans maliciosos usados para escanear sistemas para dispositivos que podem ser alistados em um botnet. Linux / Downloader, que captura scripts de shell malévolos do Linux. O Linux é executado em muitas arquiteturas diferentes, como ARM, MIPS e chipsets tradicionais x86. Um executável compilado para uma arquitetura não será executado em um dispositivo com um diferente, o relatório explica. Assim, alguns ataques do Linux exploram scripts shell shell para baixar e instalar os componentes maliciosos apropriados para a arquitetura que eles estão infectando. O Linux / Flooder, que captura ferramentas de distribuição de negação de serviço do Linux, como Tsunami, usado para executar ataques de ampliação DDoS, bem como ferramentas DDoS usadas por botnets Linux como o Mirai. “Como o botnet Mirai nos mostrou, os dispositivos IoT baseados em Linux são um alvo primordial para os exércitos de botnet”, observa o relatório. Servidor Web Battleground
Uma mudança na forma como os adversários estão atacando a Web ocorreu, o relatório WatchGuard anota.
No final de 2016, 73 por cento dos ataques da Web visavam clientes – navegadores e software de suporte, a empresa encontrou. Isso mudou radicalmente durante os primeiros três meses deste ano, com 82% dos ataques da Web focados em servidores da Web ou serviços baseados na Web.
“Nós não pensamos que os ataques de estilo de download drive-by vão desaparecer, mas parece que os atacantes concentraram seus esforços e ferramentas na tentativa de explorar ataques do servidor da Web”, escreveram os co-autores Nachreiner e Laliberte.
Houve um declínio na eficácia do software antivírus desde o final de 2016, eles também encontraram.
“Pelo segundo trimestre consecutivo, vimos a nossa solução AV avançada faltar uma grande quantidade de malware que nossa solução mais avançada pode capturar. Na verdade, aumentou de 30% para 38%”, informou Nachreiner e Laliberte.
“Hoje em dia, os cibercriminosos usam muitos truques sutis para reembalar seu malware, de modo que evade a detecção baseada em assinatura”, observaram. “É por isso que muitas redes que usam o AV básico são vítimas de ameaças como o Ransomware”.
1 note
·
View note
Link
Dockerfile is a text file that contains a list of commands that are used to build a docker image automatically. Basically, a docker file acts as a set of instructions that are needed to build a docker image.
We have earlier discussed how to create a docker container & also learned some important commands for managing the containers.
In this tutorial, we will learn about how to create a dockerfile, all its parameters/commands with the dockerfile example.
#Linux#ubuntu#linuxfan#linuxadmin#linuxindonesia#linuxday#linuxuserofficial#linuxcrew#linux4ever#linuxuser#linuxubuntu#linuxbased#centos#fedora#docker#linuxinside#containers#linuxhost#linuxcommunity#linuxcentos#linuxforever#linuxforhumanbeings#devops#devopscommunity#devopslife#devopsnotes#DevOpsGuys#DevOpsHandbook#devopsinuk#devopsengineer
1 note
·
View note
Link
1 note
·
View note
Text
Crowdsourcing App Takes Aim at COVID-19 | Health | LinuxInsider
COVID-19 researchers have a new source of distributed computing power: crowdsourcing. Usually crowdsourcing involves information or opinion gathering, but in this case it involves computing power. By installing the Folding@home software program, anyone with a computer, gaming console, or even some...
0 notes
Link
0 notes
Text
OTR Links 01/22/2019
The Best of Ontario-Educators Daily
The best of ontario-educators daily is out! https://t.co/iYFTmO8X10 Stories via @kenwhytock @NancyPeelSB @UWindsor #mlkday #martinlutherkingjrday
—
tags: IFTTT Twitter
The Best of Ontario-Educators 5 Daily
The latest The Doug Peterson Daily! https://t.co/lPFSvOClgn Thanks to @jainejeninga @OECTAHawk @DPCDSBSchools #edtech #aieducation
—
tags: IFTTT Twitter
Can a Chromebook replace my Windows or Mac computer?
One-month test: Can a Chromebook replace my main computer? https://t.co/EOKSjfoiy0
—
tags: IFTTT Twitter
HP launches new Chromebooks for schools with military-grade durability
HP launches new Chromebooks for schools with military-grade durability https://t.co/QOgh811mrb
—
tags: IFTTT Twitter
Detroit is colder than the South Pole and Alaska this morning
Detroit is colder than the South Pole and Alaska this morning – https://t.co/I5ewsPlqXY via @Shareaholic
—
tags: IFTTT Twitter
The Best of Ontario-Educators Daily
The best of ontario-educators daily is out! https://t.co/gKalpqkV3Y Stories via @CapoOttawa @nobleknits2 @HeatherTouzin #ocsb #ocsbbeinnovative
—
tags: IFTTT Twitter
The Best of Ontario-Educators 4 Daily
The latest The Best of Ontario-Educators 4 Daily! https://t.co/Ix7avPC97F Thanks to @AndreaPearl1 @PNeerja @MsGandhi123 #ai #relationshipsmatter
—
tags: IFTTT Twitter
The Best of Ontario-Educators 2 daily
The best of ontario-educators2 daily is out! is out! https://t.co/MOLt2BEbs9 Stories via @LynneCharette @deman_demn @RacquelCarlow #ocsb #indigenous
—
tags: IFTTT Twitter
The Best of Ontario-Educators 3 Daily
The latest Best of Ontario-Educators3 Daily! https://t.co/ONM314Egoq Thanks to @msmobanerjee @sarahsanders33 @Jen_Jinks #ocsb #onted
—
tags: IFTTT Twitter
The Doug Peterson Community News
The latest The Doug Peterson Community News! https://t.co/h0UHnKJQ5X Thanks to @BlaisNblais @G_Dolman @NoviAcademics #paid #reutersdavos
—
tags: IFTTT Twitter
Twitter
Now we know the rest of the story….actually we’ve known it for quite some time. https://t.co/2olnApel4h
—
tags: IFTTT Twitter
Twitter
I’m looking forward to listening to the final version, Noa. Three earworms. https://t.co/Uz3ByEClfu
—
tags: IFTTT Twitter
An insider’s guide to effective edtech (sponsored) | Tes News
An insider’s guide to effective edtech (sponsored) https://t.co/bZ5Uk0YP3v
—
tags: IFTTT Twitter
Virtual Worlds Designed Through Math Games – K-12 Technology – Big Deal Media
Virtual Worlds Designed Through Math Games – K-12 Technology https://t.co/LL9b7C9N9O via @flipboard
—
tags: IFTTT Twitter
Flipboard: When Your Teacher is a Brand Ambassador for a Private Firm
When Your Teacher is a Brand Ambassador for a Private Firm https://t.co/Srio1whMYe via @flipboard @tk1ng
—
tags: IFTTT Twitter
Twitter
Wonderful advice for today and every day…. https://t.co/V1v3dbYZuo
—
tags: IFTTT Twitter
How switching my parents over to Linux saved me a lot of headache and support calls — Simon Frey
How switching my parents over to Linux saved me a lot of headache and support calls https://t.co/ASzlUsgiYM via @flipboard
—
tags: IFTTT Twitter
Should You Run Linux Apps on Your Chromebook? | Best of ECT News | LinuxInsider
Should You Run Linux Apps on Your Chromebook? | Best of ECT News https://t.co/IcDRkpkKus via @flipboard
—
tags: IFTTT Twitter
Ottawa Public Library wants more e-books from big publishers | CBC News
Ottawa Public Library wants more e-books from big publishers https://t.co/VfhKQZmOkY via @flipboard
—
tags: IFTTT Twitter
Huawei deemed “viable and reliable” by Canada’s Telus
Huawei deemed “viable and reliable” by Canada’s Telus https://t.co/jGBv0w28G4 via @flipboard
—
tags: IFTTT Twitter
Seatbelts on school buses could happen soon, transport minister signals | CBC News
Seatbelts on school buses could happen soon, transport minister signals https://t.co/me86Zz3NeH via @flipboard
—
tags: IFTTT Twitter
A country’s ambitious plan to teach anyone the basics of AI – MIT Technology Review
A country’s ambitious plan to teach anyone the basics of AI https://t.co/Yim5pNtqas via @flipboard
—
tags: IFTTT Twitter
A robot dog has learned to run faster with machine learning – MIT Technology Review
A robot dog has learned to run faster with machine learning https://t.co/susf5J6uJ3 via @flipboard
—
tags: IFTTT Twitter
Education industry not making the grade for cybersecurity | ITProPortal
Education industry not making the grade for cybersecurity https://t.co/po4Yn3cNFS via @flipboard
—
tags: IFTTT Twitter
The Future Of BYOD: Statistics, Predictions And Best Practices To Prep For The Future
The Future Of BYOD: Statistics, Predictions And Best Practices To Prep For The Future https://t.co/7VHl8OqfUd via @flipboard
—
tags: IFTTT Twitter
6 Toronto elementary schools among top-ranked institutions in Ontario, new report says | CBC News
6 Toronto elementary schools among top-ranked institutions in Ontario, new report says https://t.co/nka3cGqHJ9 via @flipboard
—
tags: IFTTT Twitter
As Technology Becomes Easier to Use, Our Depth of Learning Needs to Continue to Increase – The Principal of Change
As Technology Becomes Easier to Use, Our Depth of Learning Needs to Continue to Increase https://t.co/73amx8J6Qx via @flipboard
—
tags: IFTTT Twitter
Lunar eclipse comes with super moon bonus | CBC News
Lunar eclipse comes with supermoon bonus https://t.co/1xPLIAr7Kt via @flipboard
—
tags: IFTTT Twitter
Two Canadians portage canoes up Mount Everest | Lifestyle from CTV News
Two Canadians portage canoes up Mount Everest https://t.co/zYbHltxLwk via @flipboard
—
tags: IFTTT Twitter
12 essential apps for any Android phone | Popular Science
12 essential apps for any Android phone https://t.co/R1ny6hOnCp via @flipboard
—
tags: IFTTT Twitter
TD Bank should have seen ‘red flags’ as senior lost $732K in romance scam, son says | CBC News
TD Bank should have seen ‘red flags’ as senior lost $732K in romance scam, son says https://t.co/CXu91S754E via @flipboard
—
tags: IFTTT Twitter
Windows 7 versus Windows 10: Here comes the final showdown | ZDNet
Windows 7 versus Windows 10: Here comes the final showdown https://t.co/m4VxevEpwe via @flipboard
—
tags: IFTTT Twitter
Breaking in or out in the real world – doug — off the record
Breaking in or out in the real world https://t.co/5ZNeZR1B6g
—
tags: IFTTT Twitter
OTR Links 01/21/2019 – doug — off the record
OTR Links 01/21/2019 https://t.co/AJIy1SWgcu
—
tags: IFTTT Twitter
Posted from Diigo. The rest of my favorite links are here.
OTR Links 01/22/2019 published first on https://medium.com/@DigitalDLCourse
0 notes
Text
Blue Collar Linux: Something Borrowed, Something New | Reviews
Blue Collar Linux: Something Borrowed, Something New | Reviews
[ad_1]
By Jack M. Germain Jan 15, 2019 1:24 PM PT
Sometimes it takes more than a few tweaks to turn an old-style desktop design into a fresh new Linux distribution. That is the case with the public release of Blue Collar Linux.
“The guidance and design were shaped by real people — blue collar people,” Blue Collar developer Steven A. Auringer told LinuxInsider. “Think useful and guided by…
View On WordPress
0 notes
Text
The Future of Open Source

inux and the open source business model are far different today than many of the early developers might have hoped. Neither can claim a rags-to-riches story. Rather, their growth cycles have been a series of hit-or-miss milestones. The Linux desktop has yet to find a home on the majority of consumer and enterprise computers. However, Linux-powered technology has long ruled the Internet and conquered the cloud and Internet of Things deployments. Both Linux and free open source licensing have dominated in other ways. Microsoft Windows 10 has experienced similar deployment struggles as proprietary developers have searched for better solutions to support consumers and enterprise users. Meanwhile, Linux is the more rigorous operating system, but it has been beset by a growing list of open source code vulnerabilities and compatibility issues. The Windows phone has come and gone. Apple's iPhone has thrived in spite of stagnation and feature restrictions. Meanwhile, the Linux-based open source Android phone platform is a worldwide leader. Innovation continues to drive demand for Chromebooks in homes, schools and offices. The Linux kernel-driven Chrome OS, with its browser-based environment, has made staggering inroads for simplicity of use and effective productivity. Chromebooks now can run Android apps. Soon the ability to run Linux programs will further feed open source development and usability, both for personal and enterprise adoption. One of the most successful aspects of non-proprietary software trends is the wildfire growth of container technology in the cloud, driven by Linux and open source. Those advancements have pushed Microsoft into bringing Linux elements into the Windows OS and containers into its Azure cloud environment. "Open source is headed toward faster and faster rates of change, where the automated tests and tooling wrapped around the delivery pipeline are almost as important as the resulting shipped artifacts," said Abraham Ingersoll, vice president of sales and solutions engineering at Gravitational. "The highest velocity projects will naturally win market share, and those with the best feedback loops are steadily gaining speed on the laggards," he told LinuxInsider.
Advancement in Progress
To succeed with the challenges of open source business models, enterprises have to devise a viable way to monetize community development of reusable code. Those who succeed also have to master the formula for growing a free computing platform or its must-have applications into a profitable venture. Based on an interesting GitLab report, 2018 is the year for open source and DevOps, remarked Kyle Bittner, business development manager at Exit Technologies. That forecast may be true eventually, as long as open source can dispel the security fears, he told LinuxInsider. "With open source code fundamental to machine learning and artificial intelligence frameworks, there is a challenge ahead to convince the more traditional IT shops in automotive and oil and gas, for example, that this is not a problem," Bittner pointed out. The future of the open source model may be vested in the ability to curb worsening security flaws in bloated coding. That is a big "if," given how security risks have grown as Linux-based deployments evolved from isolated systems to large multitenancy environments. LinuxInsider asked several open source innovators to share their views on where the open source model is headed, and to recommend the best practices developers should use to leverage different OS deployment models.
Oracle's OS Oracle
Innovative work and developer advances changed the confidence level for Oracle engineers working with hardware where containers are involved, according to Wim Coekaerts, senior vice president of operating systems and virtualization engineering at Oracle. Security of a container is critical to its reliability. "Security should be part of how you do your application rollout and not something you consider afterward. You really need to integrate security as part of your design up front," he told LinuxInsider. Several procedures in packaging containers require security considerations. That security assessment starts when you package something. In building a container, you must consider the source of those files that you are packaging, Coekaerts said. Security continues with how your image is created. For instance, do you have code scanners? Do you have best practices around the ports you are opening? When you download from third-party websites, are those images signed so you can be sure of what you are getting? "It is common today with Docker Hub to have access to a million different images. All of this is cool. But when you download something, all that you have is a black box," said Coekaerts. "If that image that you run contains 'phone home' type stuff, you just do not know unless you dig into it."
Yesterday Returns
Ensuring that containers are built securely is the inbound side of the technology equation. The outbound part involves running the application. The current model is to run containers in a cloud provider world inside a virtual machine to ensure that you are protected, noted Coekaerts. "While that's great, it is a major change in direction from when we started using containers. It was a vehicle for getting away from a VM," he said. "Now the issue has shifted to concerns about not wanting the VM overhead. So what do we do today? We run everything inside a VM. That is an interesting turn of events." A related issue focuses on running containers natively because there is not enough isolation between processes. So now what? The new response is to run containers in a VM to protect them. Security is not compromised, thanks to lots of patches in Linux and the hypervisor. That ensures all the issues with the cache and side channels are patched, Coekearts said. However, it leads to new concerns among Oracle's developers about how they can ramp up performance and keep up that level of isolation, he added.
Are Containers the New Linux OS?
Some view today's container technology as the first step in creating a subset of traditional Linux. Coekaerts gives that view some credence. "Linux the kernel is Linux the kernel. What is an operating system today? If you look at a Linux distribution, that certainly is morphing a little bit," he replied. What is running an operating system today? Part of the model going forward, Coekaerts continued, is that instead of installing an OS and installing applications on top, you basically pull in a Docker-like structure. "The nice thing with that model is you can run different versions on the same machine without having to worry about library conflicts and such," he said. Today's container operations resemble the old mainframe model. On the mainframe, everything was a VM. Every application you started had its own VM. "We are actually going backward in time, but at a much lighter weight model. It is a similar concept," Coekearts noted.
Container Tech Responds Rapidly
Container technology is evolving quickly. "Security is a central focus. As issues surface, developers are dealing with them quickly," Coekearts said, and the security focus applies to other aspects of the Linux OS too. "All the Linux developers have been working on these issues," he noted. "There has been a great communication channel before the disclosure date to make sure that everyone has had time to patch their version or the kernel, and making sure that everyone shares code," he said. "Is the process perfect? No. But everyone works together."
Security Black Eye
Vulnerabilities in open source code have been the cause of many recent major security breaches, said Dean Weber, CTO of Mocana. Open source components are present in 96 percent of commercial applications, based on a report Black Duck released last year. The average application has 147 different open source components -- 67 percent of which are used components with known vulnerabilities, according to the report. "Using vulnerable, open source code in embedded OT (operational technology), IoT (Internet of Things) and ICS (industrial control system) environments is a bad idea for many reasons," Weber told LinuxInsider. He cited several examples: The code is not reliable within those devices. Code vulnerabilities easily can be exploited. In OT environments, you don't always know where the code is in use or if it is up to date. Systems cannot always be patched in the middle of production cycles. "As the use of insecure open source code continues to grow in OT, IoT and ICS environments, we may see substations going down on the same day, major cities losing power, and sewers backing up into water systems, contaminating our drinking water," Weber warned.
Good and Bad Coexist
The brutal truth for companies using open source libraries and frameworks is that open source is awesome, generally high-quality, and absolutely the best method for accelerating digital transformation, maintained Jeff Williams, CTO ofContrast Security. However, open source comes with a big *but,* he added. "You are trusting your entire business to code written by people you don't know for a purpose different than yours, and who may be hostile to you," Williams told Linuxinsider. Another downside to open source is that hackers have figured out that it is an easy attack vector. Dozens of new vulnerabilities in open source components are released every week, he noted. Every business option comes with a bottom line. For open source, the user is responsible for the security of all the open source used. "It is not a free lunch when you adopt it. You are also taking on the responsibility to think about security, keep it up to date, and establish other protections when necessary," Williams said.
Best Practices
Developers need an efficient guideline to leverage different deployment models. Software complexity makes it almost impossible for organizations to deliver secure systems. So it is about covering the bases, according to Exit Technologies' Bittner. Fundamental practices, such as creating an inventory of open source components, can help devs match known vulnerabilities with installed software. That reduces the threat risk, he said. "Of course, there is a lot of pressure on dev teams to build more software more quickly, and that has led to increased automation and the rise of DevOps," Bittner acknowledged. "Businesses have to ensure they don't cut corners on testing." Developers should follow the Unix philosophy of minimalist, modular deployment models, suggested Gravitational's Ingersoll. The Unix approach involves progressive layering of small tools to form end-to-end continuous integration pipelines. That produces code running in a real target environment without manual intervention. Another solution for developers is an approach that can standardize with a common build for their specific use that considers third-party dependencies, security and licenses, suggested Bart Copeland, CEO of ActiveState. Also, best practices for OS deployment models need to consider dependency management and environment configuration. "This will reduce problems when integrating code from different departments, decrease friction, increase speed, and reduce attack surface area. It will eliminate painful retrofitting open source languages for dependency management, security, licenses and more," he told LinuxInsider.
Where Is the Open Source Model Headed?
Open source has been becoming more and more enterprise led. That has been accompanied by an increased rise in distributed applications composed from container-based services, such as Kubernetes, according to Copeland. Application security is at odds with the goals of development: speed, agility and leveraging open source. These two paths need to converge in order to facilitate development and enterprise innovation. "Open source has won. It is the way everyone -- including the U.S. government -- now builds applications. Unfortunately, open source remains chronically underfunded," said Copeland. That will lead to open source becoming more and more enterprise-led. Enterprises will donate their employee time to creating and maintaining open source. Open source will continue to dominate the cloud and most server estates, predicted Howard Green, vice president of marketing for Azul Systems. That influence starts with the Linux OS and extends through much of the data management, monitoring and development stack in enterprises of all sizes. It is inevitable that open source will continue to grow, said Contrast Security's Williams. It is inextricably bound with modern software. "Every website, every API, every desktop application, every mobile app, and every other kind of software almost invariably includes a large amount of open source libraries and frameworks," he observed. "It is simply unavoidable and would be fiscally imprudent to try to develop all that code yourself." Read the full article
0 notes
Text
Blue Collar Linux: Something Borrowed, Something New
Blue Collar Linux: Something Borrowed, Something New
Sometimes it takes more than a few tweaks to turn an old-style desktop design into a fresh new Linux distribution. That is the case with the public release of Blue Collar Linux.
“The guidance and design were shaped by real people — blue collar people,” Blue Collar developer Steven A. Auringer told LinuxInsider. “Think useful and guided by Joe and Jane Whitebread in Suburbia.”
Blue Collar Linux…
View On WordPress
0 notes