#log4j 2
Explore tagged Tumblr posts
Text
Debugging Full Stack Apps: Common Pitfalls and Fixes
If you’ve ever stared at your code wondering why nothing works—while everything looks fine—you’re not alone. Debugging Full Stack Apps: Common Pitfalls and Fixes is something every full stack developer becomes intimately familiar with, usually the hard way. Debugging can feel like detective work: sifting through clues, spotting red herrings, and slowly putting the pieces together.
Whether you’re knee-deep in React components or wrangling with PostgreSQL queries, bugs don’t discriminate. They can lurk in the front end, back end, or anywhere in between.
Here’s a look at common pitfalls when debugging full stack apps—and practical ways to fix them.
1. Miscommunication Between Front End and Back End
One of the most common issues arises from how the front end communicates with the back end. Sometimes, they seem to speak different languages.
Common Symptoms:
API calls returning unexpected results (or nothing at all)
Mismatched data formats (e.g., sending a string where the server expects a number)
CORS errors that mysteriously appear during deployment
Fixes:
Always double-check your request headers and response formats.
Use tools like Postman or Insomnia to simulate API requests separately from your front-end code.
Implement consistent API response structures across endpoints.
As a full stack developer, ensuring clean contracts between layers is essential. Don’t assume—it’s better to over-communicate between parts of your app than to be left scratching your head at 2 AM.
2. Version Mismatches and Package Conflicts
Let’s face it: dependency hell is real.
Common Symptoms:
Front-end not rendering after an npm install
Server crashing due to deprecated methods
Mysterious breaking changes after updating a package
Fixes:
Lock dependencies using a package-lock.json or yarn.lock file.
Regularly audit your packages with tools like npm audit or yarn audit.
Avoid updating all dependencies at once—do it incrementally and test thoroughly.
Even the most seasoned full stack developer gets tripped up here. Being methodical with updates and isolating changes can save you hours of frustration.
3. State Management Gone Wrong
If your app behaves inconsistently, the problem might be state management.
Common Symptoms:
UI doesn’t reflect expected changes
Data seems to "disappear" or update out of sync
Components re-render unnecessarily
Fixes:
Use debugging tools like Redux DevTools or Vuex Inspector to trace changes.
Store only essential data in global state—leave UI state local whenever possible.
Be cautious with asynchronous operations that update state (e.g., API calls).
Mastering state is part art, part science. As a full stack developer, understanding both front-end and back-end data flow is key to smooth state management.
4. Overlooking Server Logs and Console Errors
It’s easy to jump straight into the code—but logs often contain the breadcrumbs you need.
Common Symptoms:
500 errors with no clear origin
"Something went wrong" messages with no context
App crashing without traceable bugs
Fixes:
Always monitor the back-end logs (use console.log, but also tools like Winston or Log4js for structured logging).
Use browser developer tools to inspect network requests and console outputs.
Integrate error-tracking tools like Sentry or LogRocket.
A skilled full stack developer knows that logs are like black box recorders for your app—ignore them at your own peril.
5. Deployment-Specific Bugs
Your app runs perfectly locally—but breaks in production. Sound familiar?
Common Symptoms:
Missing environment variables
Static assets not loading
Database connection failures post-deployment
Fixes:
Use .env files carefully and securely manage environment-specific configs.
Ensure your build process includes all required assets.
Test your deployment process using staging environments before going live.
Every full stack developer eventually realizes: what works in dev doesn’t always work in prod. Always test in conditions that mimic your live environment.
Final Thoughts
Debugging Full Stack Apps: Common Pitfalls and Fixes isn’t just about technical skills—it’s about mindset. It’s easy to get overwhelmed when something breaks, but remember: every bug you squash teaches you something new.
Here are some golden rules to live by:
Reproduce the bug consistently before trying to fix it.
Break down the problem layer by layer.
Ask for a second pair of eyes—sometimes, fresh perspective is all it takes.
Being a full stack developer is like being a bridge-builder—you connect front end and back end, logic and interface, user and server. And in between, debugging is your glue.
So next time you hit a wall, take a breath, grab a coffee, and dig in. You’ve got this.
#FullStackDeveloper#FullStackDevelopment#FullStackCourse#TechnoBridgeFullStack#LearnFullStack#FullStackTraining#MERNStack#FrontendDevelopment#BackendDevelopment#CareerInTech#CodingBootcamp#SoftwareDevelopmentCourse#TopFullStackDeveloperCourse#PlacementAssistance#JobOrientedCourse#UpskillNow#ReactJS#ITTrainingIndia
0 notes
Text
蜘蛛池需要哪些调试工具?
在SEO优化领域,蜘蛛池(Spider Pool)是一个重要的概念。它通过模拟搜索引擎的爬虫行为来提高网站的收录速度和排名。为了确保蜘蛛池能够高效运行,选择合适的调试工具至关重要。下面我们就来看看,构建和维护一个高效的蜘蛛池,需要哪些调试工具。
1. 日志分析工具
日志文件是了解蜘蛛池运行状态的重要途径。使用日志分析工具可以帮助我们快速定位问题,例如,Apache的Log4j或ELK Stack(Elasticsearch, Logstash, Kibana)都是不错的选择。这些工具可以实时监控系统日志,帮助我们发现并解决潜在的问题。
2. 性能监控工具
性能监控工具如Prometheus、Grafana等,可以让我们实时监控系统的各项指标,如响应时间、请求成功率等。
3. 网络抓包工具
网络抓包工具如Wireshark,可以帮助我们理解蜘蛛池与目标网站之间的交互过程。通过抓取网络数据包,我们可以检查HTTP请求和响应的具体内容,这对于调试和优化蜘蛛池的行为非常有帮助。
4. 自动化测试工具
自动化测试工具如Selenium,可以模拟真实用户的操作行为,对蜘蛛池进行功能性和性能测试。这有助于确保蜘蛛池能够正确地处理各种网页结构,并且在面对动态加载的内容时也能表现良好。
5. 数据库管理工具
数据库管理工具如MySQL Workbench或Navicat,对于管理和监控数据库的状态至关重要。它们可以帮助我们更好地管理存储的数据,以及优化查询效率,从而提升整体性能。
6. 编程IDE
一个好的编程集成开发环境(IDE),如PyCharm或VS Code,不仅能够提高代码编写效率,还能方便地进行单元测试和集成测试,确保每个模块都能按预期工作。
7. 版本控制工具
版本控制工具如Git,可以帮助团队协作开发,同时保证代码的版本控制和稳定性。然而,要让蜘蛛池高效运行,选择合适的调试工具是关键。本文介绍了几种常用的调试工具,包括日志分析工具、性能监控工具、网络抓包工具、自动化测试工具、数据库管理工具以及版本控制工具。每一种工具都有其独特的作用,合理利用这些工具,可以帮助我们��有效地管理和优化蜘蛛池,从而达到更好的效果。
讨论点:你平时使用哪些工具来调试你的蜘蛛池?
加飞机@yuantou2048

EPP Machine
负面删除
0 notes
Text

Summary of Cybersecurity Alert: Hackers Exploit Logging Errors!
Importance of Logs: Logs are essential for monitoring, maintaining, and troubleshooting IT systems. However, mismanaged or poorly configured logs can expose vulnerabilities to attackers.
Exploitation by Hackers: Cybercriminals target logging systems to inject malicious code, gain unauthorised access, or steal data. Examples include the Log4Shell vulnerability in the Log4j library.
Consequences of Compromised Logs: A compromised logging system can lead to data breaches, business disruptions, financial losses, regulatory fines, and damaged stakeholder trust.
Securing Logging Systems: Businesses should upgrade to advanced log management tools that provide real-time monitoring, anomaly detection, and centralised secure log storage.
Zero Trust Security Model: Adopting a zero trust approach combined with smart logging practices prevents attackers from freely moving within compromised systems and helps detect malicious activities.
Common Hacker Techniques:
Log Deletion: Attackers delete logs to erase evidence, as seen in the 2017 Equifax breach.
Log Alteration: Hackers modify or forge logs to mislead investigators, as in the 2018 SingHealth breach.
Disabling Logs: Disabling logging services to avoid detection, as in the 2020 SolarWinds attack.
Encrypting Logs: Attackers encrypt logs to prevent analysis, as in the NotPetya ransomware attack.
Changing Retention Policies: Altering log retention settings to ensure evidence is purged before investigation, as seen in the 2018 Marriott breach.
Historical Examples: Real-world breaches like Equifax (2017), SingHealth (2018), SolarWinds (2020), and NotPetya (2017) demonstrate the devastating impact of log manipulation.
Protecting Logs:
Store logs securely.
Restrict access to authorised personnel.
Mask sensitive information in logs.
Error Logs as Targets: Hackers analyse error logs to find vulnerabilities and misconfigurations, crafting precise attacks to exploit these weaknesses.
Business Risk Management: Protecting logging systems is not just an IT issue—it’s a critical part of business risk management to prevent dangers.
The Log4Shell Vulnerability
In late 2021, a critical vulnerability known as Log4Shell (CVE-2021-44228) was discovered in Apache Log4j 2, a widely used Java logging library. This vulnerability allowed attackers to execute arbitrary code on affected systems by exploiting how logs were processed. The flaw was particularly dangerous because it was easy to exploit and affected a vast number of applications and services globally.
1. financial losses and safeguard company reputation.
Consequences of Compromised Logging Systems
When attackers exploit vulnerabilities in logging systems, the repercussions can be severe:
Data Breaches: Unauthorised access to sensitive information can lead to data theft and privacy violations.
Business Interruptions: System compromises can cause operational disruptions, affecting service availability and productivity.
Financial Losses: The costs associated with remediation, legal penalties, and loss of business can be substantial.
Reputational Damage: Loss of stakeholder trust and potential regulatory fines can harm a company's reputation and customer relationships.
Real-World Examples of Log Manipulation
Several high-profile incidents illustrate the impact of log manipulation:
Equifax Breach (2017): Attackers exploited a vulnerability in the Apache Struts framework and manipulated system logs to cover their activities.
SingHealth Breach (2018): Attackers used advanced techniques to hide their presence by altering log entries, delaying detection.
SolarWinds Attack (2020): Attackers disabled logging mechanisms and monitoring systems to avoid detection during their intrusion.
NotPetya Ransomware (2017): Attackers encrypted key system files, including logs, to hamper recovery efforts and obscure their actions.
Protecting logging systems is not merely a technical concern but a critical aspect of comprehensive business risk management. By understanding the risks associated with logging vulnerabilities and implementing robust security strategies, organisations can defend against these hidden dangers and safeguard their operations.
1 note
·
View note
Text
Top 10 Java Libraries and Frameworks Every Developer Should Know

Top 10 Java Libraries and Frameworks Every Developer Should Know
1. Spring Framework
Comprehensive ecosystem for enterprise Java development — Dependency injection — MVC architecture — Microservices support
2. Hibernate
Object-relational mapping (ORM) library — Simplifies database interactions — Supports multiple databases — Reduces boilerplate database code
3. Apache Maven
Project management and build automation tool — Dependency management — Standardized project structure — Easy integration with CI/CD pipelines
4. JUnit
—
Unit testing framework — Supports test-driven development — Annotations for test configuration — Wide IDE integration
5. Apache Spark — Big data processing framework — Distributed computing — Machine learning capabilities — Real-time data streaming
6. Mockito — Mocking framework for unit tests — Allows creation of test doubles — Verifies method interactions — Simplifies complex testing scenarios
7. Lombok — Reduces boilerplate code — Automatic getter/setter generation — @Data, @Builder annotations — Improves code readability
8. Jackson — JSON processing library — Object serialization/deserialization — High-performance JSON parsing — Supports complex object mappings
9. Log4j — Logging framework — Configurable logging levels — Performance optimization — Multiple output destinations
10. Guava — Google’s core libraries — Utility classes — Functional programming support — Improved collections and caching
WEBSITE: https://www.ficusoft.in/core-java-training-in-chennai/
0 notes
Text
Cách theo dõi IP của bất kỳ ai bằng Canarytokens là một kỹ năng mà bạn nên biết nếu bạn quan tâm đến an ninh mạng. IP là địa chỉ mạng duy nhất của mỗi thiết bị kết nối internet, nó có thể tiết lộ nhiều thông tin về người dùng như vị trí, hệ điều hành, trình duyệt, nhà cung cấp dịch vụ, và thậm chí là tên miền. Bằng cách theo dõi IP, bạn có thể phát hiện ra những hoạt động đáng ngờ, ngăn chặn những cuộc tấn công, hoặc bảo vệ dữ liệu của bạn. Trong bài viết này, AnonyViet sẽ giới thiệu cho bạn cách theo dõi IP bằng Canarytokens, một công cụ an ninh miễn phí và dễ sử dụng. Canarytokens là gì? Canarytokens là những cái bẫy kỹ thuật số, chúng hoạt động bằng cách theo dõi các hành động nhất định, chẳng hạn như ai đó đọc một tệp, thực hiện một truy vấn cơ sở dữ liệu, chạy một quá trình,... Nó tương tự như những hình ảnh trong email, nhưng thay vì theo dõi lượt mở, nó theo dõi các hành động trên hệ thống của bạn. Bạn có thể sử dụng Canarytokens để thiết lập những cái bẫy này trong hệ thống máy tính thông thường, giống như đặt các báo động ở khắp nơi trong nhà vậy đó. Tại sao bạn nên quan tâm đến Canarytokens? Đôi khi, hacker xâm nhập vào các mạng máy tính, và khi bạn phát hiện ra điều đó thì đã quá muộn. Canarytokens là một giải pháp nhanh chóng giúp bạn có thể biết ngay lập tức nếu có ai đó đang ‘lục lọi’ trong hệ thống của mình. Các loại Canarytokens Có nhiều loại Canarytokens khác nhau mà bạn có thể sử dụng để theo dõi các hành động khác nhau trên. Dưới đây là một số ví dụ: Web bug / URL token: Cảnh báo khi một URL được truy cập DNS token: Cảnh báo khi tên máy chủ được yêu cầuAWS keys: Cảnh báo khi sử dụng khóa AWS Azure Login Certificate: Cảnh báo khi dùng chứng chỉ Azure Service Principal để đăng nhập Sensitive command token: Cảnh báo khi chạy lệnh Windows đáng ngờ Microsoft Word document: Nhận thông báo khi tài liệu được mở trong Microsoft Word Microsoft Excel document: Nhận thông báo khi tài liệu được mở trong Microsoft Excel Kubeconfig token: Cảnh báo khi sử dụng Kubeconfig WireGuard VPN: Cảnh báo khi cấu hình WireGuard VPN client được sử dụng Cloned website: Kích hoạt cảnh báo khi trang web của bạn bị sao chép QR code: Tạo mã QR cho mã thông báo vật lý MySQL dump: Nhận thông báo khi kết xuất MySQL được tải Windows folder: Nhận thông báo khi Windows Folder được tìm trong Windows Explorer Log4Shell: Cảnh báo khi dòng nhật ký log4j bị tấn công bởi CVE-2021–44228 Fast redirect: Cảnh báo khi một URL được truy cập, Người dùng được chuyển hướng Slow redirect: Cảnh báo khi một URL được truy cập, Người dùng được chuyển hướng (Nhiều thông tin bị đánh cắp) Custom image web bug: Thông báo khi hình ảnh bạn tải lên có người xem Acrobat Reader PDF document: Nhận thông báo khi tài liệu PDF được mở trong Acrobat Reader Custom exe / binary: Đưa ra cảnh báo khi EXE hoặc DLL được thực thi Microsoft SQL Server: Nhận thông báo khi cơ sở dữ liệu MS SQL Server bị truy cập SVN: Cảnh báo khi ai đó kiểm tra kho lưu trữ SVN Unique email address: Cảnh báo khi có email được gửi đến một địa chỉ duy nhất Cách theo dõi IP của bất kỳ ai bằng Canarytokens Để sử dụng Canarytokens để theo dõi IP, bạn c��n làm theo các bước sau: Bước 1: Truy cập trang web canarytokens.org và chọn loại Canarytoken bạn muốn. Bước 2: Điền email để nhận thông báo > Dán đường link URL Giống như tạo một liên kết bí mật sẽ kích hoạt một báo động nếu có ai đó tương tác với nó. Trong bài viết này, tôi sẽ sử dụng Fast redirect làm ví dụ. [caption id="attachment_56527" align="aligncenter" width="800"] Điền email để nhận thông báo > Dán đường link URL[/caption] Bước 3: Sau đó, bạn đặt liên kết Canarytoken được tạo ra ở trong một email, một tài liệu, hoặc thậm chí là một hình ảnh được nhúng và gửi nó cho mục tiêu. [caption id="attachment_56528" align="aligncenter" width="800"] Đặt liên kết Canarytoken ở trong email, tài liệu,... và gửi cho mục tiêu[/caption] Nếu mục tiêu truy cập URL/Tệp, như trong ví dụ trên, mã thông báo sẽ được kích hoạt và gửi qua email hoặc webhook như bên dưới:
[caption id="attachment_56529" align="aligncenter" width="778"] Dữ liệu được thu thập[/caption] Lời Kết Cách theo dõi IP của bất kỳ ai bằng Canarytokens là một phương pháp đơn giản và hiệu quả để nâng cao an ninh mạng. Bằng cách tạo ra và phân phối những Canarytokens, bạn có thể thu thập được những thông tin quý giá về mục tiêu, như IP, thời gian, thiết bị,... Bạn có thể sử dụng những thông tin này để phòng thủ, điều tra, hoặc trả đũa những kẻ xâm nhập. Chúc bạn thành công!
0 notes
Text
Best Practices for Java Development: Navigating Common Pitfalls with Finesse
Introduction
In the ever-evolving landscape of software development, Java remains a cornerstone for building robust and scalable applications. However, even the most seasoned Java developers can find themselves ensnared in common pitfalls that compromise the quality, performance, and maintainability of their code. In this comprehensive guide, we’ll dissect these challenges and provide actionable insights to navigate the intricacies of Java development with finesse
1. Meticulous Memory Management
Misstep: Overlooking memory management can result in memory leaks and inefficient resource allocation.
Solution: Exercise diligence in memory management. Leverage tools like the Java Virtual Machine (JVM) profiler to scrutinize memory usage intricacies. Implement garbage collection judiciously to release dormant objects, optimizing overall memory efficiency.
2. Exemplary Exception Handling
Misstep: Inadequate exception handling begets erratic behaviour and compounds debugging complexities.
Solution: Institute airtight exception handling mechanisms. Discriminately catch exceptions and propagate those that elude resolution. Offer articulate error messages and systematically log exceptions for expedited troubleshooting.
3. Fastidious Performance Optimization
Misstep: Disregarding performance optimization compromises user experience and application efficiency.
Solution: Systematically profile and scrutinize code with tools like JProfiler or VisualVM. Optimize critical sections, eschew gratuitous loops, and harness caching mechanisms. Stay abreast of performance tuning best practices in the Java ecosystem.
4. Adherence to Java Updates
Misstep: Languishing on outdated Java versions exposes applications to security vulnerabilities and forfeits performance enhancements.
Solution: Maintain currency with Java releases and updates. Routinely scrutinize security patches and embrace the latest features. Employ dependency management tools like Maven or Gradle for streamlined version control.
5. Vigilant Thread Safety
Misstep: Inadequate synchronization in multithreaded applications compromises data integrity.
Solution: Espouse robust synchronization mechanisms using synchronized blocks or classes. Leverage the java.util.concurrent package for streamlined concurrency management. Employ thread-safe data structures judiciously.
6. Eradicating Code Duplication
Misstep: Repetition of code blocks across the application breeds maintenance challenges.
Solution: Embrace the DRY (Don’t Repeat Yourself) principle. Encapsulate common functionalities into modular methods or classes for seamless reuse. Enlist design patterns to foster a modular and maintainable codebase.
7. Comprehensive Testing Protocols
Misstep: Inadequate testing compromises the application’s reliability and exposes latent bugs.
Solution: Champion a comprehensive testing strategy encompassing unit tests, integration tests, and end-to-end tests. Leverage stalwart testing frameworks like JUnit and sophisticated tools such as Mockito for rigorous unit testing. Integrate continuous testing practices for automated validation.
8. Inefficient Database Access
Misstep: Poorly optimized database queries and data access can bottleneck application performance.
Solution: Optimize database queries, use indexing judiciously, and consider employing an Object-Relational Mapping (ORM) framework for streamlined data access. Leverage connection pooling to efficiently manage database connections.
9. Inadequate Logging and Monitoring
Misstep: Neglecting comprehensive logging and monitoring hinders issue diagnosis and tracking.
Solution: Implement robust logging using frameworks like SLF4J and Logback or Log4j. Integrate monitoring tools to track application metrics, log errors systematically, and set up alerts for critical issues.
10. Overlooking Design Patterns
Misstep: Failing to apply design patterns can result in code that is harder to understand, maintain, and extend.
Solution: Familiarize yourself with common design patterns such as Singleton, Factory, Observer, and Strategy. Apply these patterns judiciously to enhance code organization, flexibility, and maintainability.
11. Ignoring Security Best Practices
Misstep: Neglecting security measures can expose applications to vulnerabilities, jeopardizing data and user privacy.
Solution: Adhere to security best practices, including input validation, secure coding guidelines, and encryption mechanisms. Regularly update dependencies to patch known vulnerabilities. Consider leveraging frameworks like Spring Security for robust authentication and authorization.
12. Unoptimized Resource Handling
Misstep: Inefficient resource handling, such as file I/O or network operations, can lead to performance bottlenecks.
Solution: Optimize resource handling by using buffered I/O, minimizing network calls, and releasing resources promptly. Consider leveraging try-with-resources statements for automatic resource management.
13. Ignoring Code Reviews and Collaboration
Misstep: Neglecting code reviews and collaborative development compromises code quality.
Solution: Foster a culture of code reviews within your development team. Embrace collaborative tools such as Git for version control and establish coding standards. Regularly engage in knowledge-sharing sessions to enhance the collective expertise of the team.
14. Lack of Documentation
Misstep: Inadequate or outdated documentation makes it challenging for developers to understand and maintain the codebase.
Solution: Maintain comprehensive and up-to-date documentation, including code comments, README files, and inline documentation. Use tools like Javadoc for generating API documentation to enhance code comprehension.
15. Dependency Mismanagement
Misstep: Using outdated or incompatible dependencies can lead to compatibility issues and security vulnerabilities.
Solution: Regularly update dependencies to the latest stable versions. Utilize dependency management tools like Maven or Gradle to streamline dependency resolution and version control.
By conscientiously implementing these best practices, Java developers can elevate their craft, fortifying their projects against common pitfalls, and ensuring the development of robust, secure, and maintainable applications.
0 notes
Text
Cloudflare report: Log4j remains top target for attacks in 2023

Log4j remained a top attack vector for threat actors in 2023, while a new vulnerability, HTTP/2 Rapid Reset is emerging as a significant threat to organizations, according to Cloudflare’s annual “Year in Review” report. https://jpmellojr.blogspot.com/2023/12/cloudflare-report-log4j-remains-top.html
0 notes
Text
2 years on, Log4j still haunts the security community
Dive Brief: Two years after the historic disclosure of a critical zero-day vulnerability in the Apache Log4j library sent organizations racing to contain the damage, nearly 2 in 5 applications are still using vulnerable versions, according to a report released Thursday from Veracode. The report found nearly one-third of applications are running Log4j2 1.2.x, which reached end-of-life status in…
View On WordPress
0 notes
Text
Log4Shell जैसा सुरक्षा छेद लोकप्रिय Java SQL डेटाबेस इंजन H2 में पाया गया
Log4Shell जैसा सुरक्षा छेद लोकप्रिय Java SQL डेटाबेस इंजन H2 में पाया गया
“यह Log4Shell, जिम है,” जैसा कि कमांडर स्पॉक ने वास्तव में कभी नहीं कहा, “लेकिन जैसा कि हम जानते हैं वैसा नहीं।” यह सबसे संक्षिप्त सारांश है जिसे हम बग के साथ लेकर आ सकते हैं सीवीई-2021-42392, ए सुरक्षा छेद हाल ही में सॉफ्टवेयर आपूर्ति श्रृंखला प्रबंधन कंपनी Jfrog के शोधकर्ताओं द्वारा रिपोर्ट की गई। इस बार, बग अपाचे के संकटग्रस्त Log4j टूलकिट में नहीं है, लेकिन एक लोकप्रिय जावा SQL सर्वर में पाया…
View On WordPress
0 notes
Text
Too soon?

FYI, log4j is a serious java security bug affecting everyone who uses Java programming language. See https://logging.apache.org/log4j/2.x/ for more info.
58 notes
·
View notes
Text
蜘蛛池需要哪些记录管理工具?
在互联网技术领域,蜘蛛池(Spider Pool)是一个重要的概念,它主要用于帮助网站优化SEO,通过模拟大量用户访问来提升网站的搜索引擎排名。为了确保蜘蛛池的有效运行和管理,选择合适的记录管理工具至关重要。这些工具可以帮助我们更好地监控、分析和优化蜘蛛池的性能。那么,蜘蛛池需要哪些记录管理工具呢?本文将为您详细介绍。
1. 日志记录工具
日志记录是蜘蛛池管理的基础。通过日志记录工具,我们可以详细追踪蜘蛛池中每个爬虫的行为,包括它们访问了哪些页面、花费了多少时间以及是否成功获取了数据。常用的日志记录工具有Apache的Log4j、Python的logging模块等。这些工具能够帮助我们快速定位问题,提高故障排查效率。
2. 数据分析工具
数据分析工具用于对蜘蛛池收集到的数据进行深入分析。这包括但不限于流量分析、用户行为分析等。通过数据分析,我们可以了解哪些内容更受用户欢迎,从而调整策略以提高用户体验。常见的数据分析工具有Google Analytics、Tableau等。
3. 性能监控工具
性能监控工具对于保证蜘蛛池的稳定运行至关重要。这类工具可以实时监控蜘蛛池的运行状态,包括CPU使用率、内存占用情况、网络延迟等关键指标。一旦发现异常,系统会立即发出警报,以便管理员及时处理。常用的性能监控工具有Zabbix、Prometheus等。
4. 任务调度工具
任务调度工具帮助我们合理安排蜘蛛池中的任务执行顺序和频率。通过设置合理的调度策略,可以有效避免资源浪费,同时确保所有任务都能按时完成。常见的任务调度工具有Cron、Airflow等。
5. 安全防护工具
安全防护是蜘蛛池管理中不可忽视的一环。由于蜘蛛池涉及到大量的网络请求,因此容易成为黑客攻击的目标。安全防护工具可以帮助我们抵御DDoS攻击、防止恶意软件入侵等。常用的防护工具有Cloudflare、AWS WAF等。
结语
综上所述,选择合适的记录管理工具对于蜘蛛池的高效运行至关重要。希望本文提供的信息能够帮助您更好地管理和优化您的蜘蛛池。如果您有任何疑问或建议,请在评论区留言讨论!
以上就是关于蜘蛛池所需记录管理工具的介绍。希望这篇文章能为您的工作带来一些启发。如果您觉得有用,请点赞并分享给更多需要的朋友吧!
加飞机@yuantou2048
币圈推广
蜘蛛池出租
0 notes
Text
MERCURY leveraging Log4j 2 vulnerabilities in unpatched systems to target Israeli organizations
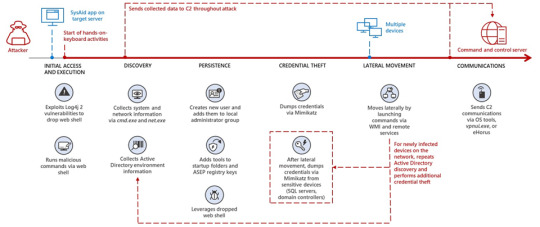
Source: https://www.microsoft.com/security/blog/2022/08/25/mercury-leveraging-log4j-2-vulnerabilities-in-unpatched-systems-to-target-israeli-organizations/
4 notes
·
View notes
Text
Why Learning Java is Essential for Selenium Automation
Java is one of the most widely used programming languages in the world and a cornerstone for many testing frameworks, including Selenium. For professionals venturing into selenium automation testing, mastering Java offers numerous benefits that enhance both test development and execution. Here's why learning Java is crucial for Selenium automation:
1. Wide Industry Adoption
Java is highly popular in the software development industry. Since Selenium is compatible with multiple programming languages, its integration with Java ensures easier adoption in Java-based projects. This alignment makes Java a preferred choice for companies and testers alike.
2. Robust Object-Oriented Features
Selenium works seamlessly with Java’s object-oriented programming (OOP) features. Concepts such as inheritance, polymorphism, and encapsulation simplify the creation of reusable and maintainable test scripts. Testers can model real-world scenarios more effectively, leading to efficient test automation.
3. Rich Ecosystem of Libraries
Java’s vast ecosystem includes libraries such as TestNG, Apache POI, and Log4j, which complement Selenium. These libraries enhance test execution, reporting, and handling of data files, enabling comprehensive automation capabilities for web applications.
4. Extensive Community Support
Java boasts an extensive community of developers and testers. Beginners and professionals working on Selenium automation testing can find ample resources, tutorials, and forums to troubleshoot issues and improve their expertise.
5. Integration with Testing Tools
Java integrates seamlessly with popular testing tools like Maven, Jenkins, and JUnit. These tools streamline Continuous Integration/Continuous Deployment (CI/CD) workflows, ensuring that Selenium tests are automatically triggered and executed in a structured pipeline.
6. Cross-Platform Compatibility
Selenium tests written in Java can run on multiple platforms, making it a versatile choice for cross-platform automation. Whether it’s Windows, macOS, or Linux, Java ensures consistent and reliable execution across environments.
7. High Performance
Java’s performance is another key advantage. Its robust architecture and speed make it an excellent choice for developing complex and time-sensitive automation tests. Selenium scripts written in Java are executed efficiently, even for large-scale projects.
8. Abundant Career Opportunities
Proficiency in Java opens up vast career opportunities for automation testers. Many organizations prioritize candidates with Java expertise, especially for roles involving Selenium automation testing. Learning Java not only enhances your testing skills but also boosts your employability.
9. Ease of Learning
Java’s syntax is straightforward, making it beginner-friendly for those new to programming. Additionally, its detailed documentation and rich resources simplify the learning curve for testers venturing into Selenium automation.
10. Scalable Test Automation Frameworks
Java is instrumental in building scalable test automation frameworks. Hybrid and data-driven frameworks created using Selenium and Java are ideal for handling complex test cases and large datasets.
In conclusion, Java is an indispensable skill for anyone pursuing selenium automation testing. It not only simplifies the creation and execution of test scripts but also aligns seamlessly with industry standards and tools. For testers aspiring to excel in automation, Java provides a robust foundation for a successful career.
0 notes
Text
Java Log4j2 sux <=2.14.1 = JNDI Log4j vulnerability
Apache Log4j2 <=2.14.1 JNDI features used in the configuration, log messages, and parameters do not protect against attacker-controlled LDAP and other JNDI-related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers
when message lookup substitution is enabled.
From log4j 2.15.0, this behavior has been disabled by default. In previous releases (>2.10) this behavior can be mitigated by setting system property "log4j2.formatMsgNoLookups" to “true” or by removing the JndiLookup class from the classpath (example: zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class). Java 8u121 (see https://www.oracle.com/java/technologies/javase/8u121-relnotes.html) protects against remote code execution by defaulting "com.sun.jndi.rmi.object.trustURLCodebase" and "com.sun.jndi.cosnaming.object.trustURLCodebase" to "false".
from https://nvd.nist.gov/vuln/detail/CVE-2021-44228

Wowow
Credit: This issue was discovered by Chen Zhaojun of Alibaba Cloud Security Team.
via https://logging.apache.org/log4j/2.x/security.html
3 notes
·
View notes
Quote
AppletにせよJINIにせよ、JavaのRMIではリモートクラスローダでロードしたクラスを実行するにはセキュリティマネージャが必要という仕組みになってるのに、なぜかJNDIだけがそうでなかったってのが根本の問題
[B! Java] 元・Java専門記者がLog4j 2脆弱性に見た「複雑性と魔神のかけら」 Javaの歴史とバザールの矛盾
1 note
·
View note
Text
Here’s why Selenium Automation Testing succeeds -
Selenium is one of the foremost widely used open-source Web UI
(User Interface) automation testing suites. It was originally developed
by Jason Huggins in 2004 as an indoor tool at Thought Works.
Selenium promotes automation over various browsers, platforms, and
programming languages.
1.Selenium offers a user-friendly structure:
Selenium offers a user-friendly interface that helps create and execute
tests easily and effectively. Its open-source features help users to
script the extensions that make them easy to develop, customized
actions and even manipulate at an advanced level. Tests run directly
across browsers and therefore the users can watch while the tests are
being executed. In addition to this, Selenium’s reporting potentiality
is one of the reasons for choosing it, as it allows testers to extract the
results and take required actions.
2.Selenium offers performing on various platforms:
Selenium can be set up on platforms such as Windows, Linux,
Solaris, and Macintosh. furthermore, it supports OS (Operating
System) for mobile applications like iOS, windows mobile, and
android.
3.Selenium offers to support various kinds of language:
Selenium supports a variety of languages: Languages supported by
Selenium include C#, Java, Perl, PHP, Python, and Ruby. Currently,
the Selenium Web driver is with Java and C#.
4.Selenium has been a hit by having a web driver:
The Selenium WebDriver web testing structure helps us build stable
and maintainable test automation for your web applications over tons
of different browsers, operating systems, and programming languages. the many operating systems they run on will quickly
become a non-negligible engagement. WebDriver can do nearly
anything you ask it to—the trick is to return up with a unified
approach to testing.
5. Selenium automation testing is beneficial over manual testing:
Letting our application has its new releases and patches; we will have
to ensure the released software fixes. Therefore such testing needs
prior checking and can't be done all the time manually. Hence
selenium automation testing proves beneficial. Testing manually
becomes challenging for examining all software's functionalities
before or after the patches are being performed. selenium seems very
effective regarding resources, cost, timely delivery of the product, and
less workforce.
6. Selenium also provides mobile testing:
Well here are some types of it:
Appium
Selendroid
Robotium
iOS-driver
They are all based on Selenium so that developers can apply the same
principles when testing mobile apps.
7.Selenium offers to provide secure and flexible testing designs:
Selenium provides three kinds of testing designs that are secure and
easy to use and helps the performer to provide the best results:
Page Object Model
Data-Driven using Excel
Log4j Logging
8.selenium offers to provide testing results using TestNG:
TestNG can produce the report in a readable format. TestNG
interprets the way the tests are coded. There is not more
demand for a static main method in our tests. The sequence of actions is monitored by easy-to-understand footnotes that do
not need methods to be static.
9.Selenium grid tool here is a game-changer:
Selenium Grid is a tool that classifies the tests across multiple
physical or virtual machines so that we can perform scripts in
correspondence. It accelerates the testing process across browsers and
platforms by providing us quick and precise feedback.
10.Selenium record of excellence:
selenium has a record of providing the best results in the past. It is
considered to be the most reliable and secure app tester when it comes
to query related to data and servers. Hence, it has become more
profitable than the other app testers.
1 note
·
View note