#mcafee phone number
Text
How to Recover Abandoned Carts in WooCommerce?

It’s not uncommon for ecommerce shoppers to abandon carts. You may not know it, but your store might also be suffering from carts being abandoned. This problem can be addressed however. To start, you must determine why your customers abandon their carts.
Why online shoppers abandon carts and what you can do about it?
There are various reasons why online shoppers abandon their carts. We lay out the most common ones and what you can do to address them.
Checkout is Too Complicated
Your customers will nitpick and that is to be expected. When you make your customers jump hoops during checkout, you’re not doing them a favor. Your checkout should be quick and straightforward. If you must add some other stuff that will complicate checkout, consider if you can add it on the thank you page instead. The thank you page is the page where the customer is redirected to after making a successful purchase. If you need help tweaking your thank you page, the Wooassist team can help.
Users Need to Create an Account to Check Out
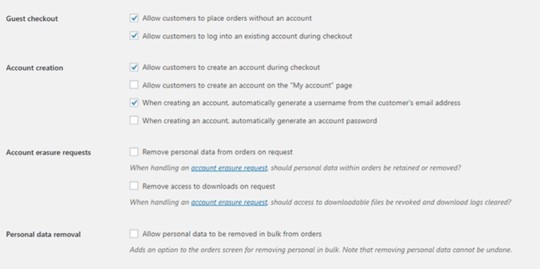
Internet users are already burned out having to create an account for each internet service that they use. Don’t add to that burden. Don’t force your customers to create an account if it’s not necessary. To enable guest checkouts on WooCommerce, go to your WordPress Dashboard, click on WooCommerce > Settings. Under the Account and Privacy tab, enable “Allow customers to place orders without an account”. You can tweak other account related settings here to your liking.
Too Many Checkout Form Fields
The default WooCommerce checkout page is good enough as it is. There is no need to add more fields unless necessary. If you’ve edited your checkout page before to add some unnecessary fields, look into it and consider removing it.
Unexpected Charges
Customers will abandon your checkout when they see the shipping fee. No one will force you to offer free shipping if it will make your business unsustainable. There are however some things that you can do to reduce abandoned carts as a result of shipping and other fees. People now are more accepting of shipping fees. For other fees, be transparent from the get-go. If you charge taxes, handling fees, and other fees, make it clear starting from the product page that you charge these fees. If they are suddenly greeted by these fees on checkout, it will look like unscrupulous practice.
Too Many Clicks to Checkout
Reducing cart abandonment is all about simplifying your product purchase process. Ideally, it should not take more than three clicks for a customer to check out. If it takes four clicks to check out, that is one click too many. Get rid of unnecessary barriers to completing checkout.
Don’t Make it Hard to Contact You
Some of your prospective customers will look for your contact details before they make a purchase. If they added a product to their cart but could not find your contact information or even a contact us page, there is a high likelihood that that user will abandon that cart. To prevent this from happening, make sure you have a contact us page. Even better, if you can add your email or phone number on your WooCommerce store’s header.
Payment Issues
Another common reason for abandoning shopping carts is payment issue. When the customer tries to pay for his/her order and it fails, you can bet that cart will be abandoned. The solution here is simple. Offer more than one mode of payment. Some common payment channels you can use are Paypal, Stripe, Authorize.net, Apple Pay, Amazon Pay, and Square.
Other Things You Can Do to Reduce Cart Abandonment
Show Security Certificates
To be able to sell your products or services online, you’ll need to be able to establish that you are trustworthy. You can show security certificates and security seals on your checkout page to improve your trust rating. Some security seals that you can add to your site as Norton, McAfee and TRUSTe.
Offer Free Shipping
Free shipping can significantly reduce your cart abandonment rates. However, not every business can make a profit when offering free shipping. As an alternative, you can offer free shipping when your customers meets a required minimum order value or quantity. This strategy can also help improve your average order value.
Offer a Money-Back Guarantee
Most consumer laws dictate that you should have a return policy anyway. So there’s no reason not to do it. Making your money-back guarantee known shows your prospective customers that you have faith in the quality of your product or service. Don’t worry about the people that might abuse your money-back guarantee. It hardly ever happens. And if it happens a lot, the problem might be your product.
Improve Your Page Load Speeds
If your site is slow, some of your prospective customers might get frustrated and abandon their carts. Make sure your site is fast.
How to Recover Abandoned Carts
There are many ways to recover abandoned carts. Some of the more common methods are remarketing and abandoned cart emails.
Using Remarketing to Recover Abandoned Carts
There are many platforms that you can use for remarketing. Essentially, remarketing works by saving a cookie on the user’s browser so you can show them your tailored ads. Neil Patel details how you can use remarking on Adwords to recover abandoned carts. Facebook is another platform that you can use for remarketing. SproutSocial details how to use remarketing on Facebook.
Using Abandoned Cart Emails to Recover Abandoned Carts
Abandoned cart emails send your customers a reminder email if they did not complete their purchase. For guest checkouts, this requires that the user must at least have entered his/her email address. This won’t be an issue if you require your customers to register before making a purchase. Do note however that requiring customers to create an account may hurt your conversion rates. There are a lot of abandoned cart email plugins that work for WooCommerce, you just have to find the plugin that works for your needs.
Recover abandoned carts and improve your sales by implementing these strategies. If you have any questions, you can post a comment below. If you need help setting up abandoned cart emails or anything else, you can send us email.
0 notes
Text
Beware of cyber scams: How hackers tried to scam me - CyberTalk
New Post has been published on https://thedigitalinsider.com/beware-of-cyber-scams-how-hackers-tried-to-scam-me-cybertalk/
Beware of cyber scams: How hackers tried to scam me - CyberTalk


Lari Luoma has over 20 years of experience working in the fields of security and networking. For the last 13 years, he has worked with Check Point Professional Services as a security consultant, helping customers worldwide implement the best-in-class cyber security. He is a subject matter expert in hyper-scalable security solutions.
EXECUTIVE SUMMARY:
Cyber crime is on the rise. People encounter scams in their everyday lives without really understanding they are being scammed. These vexing and vicious scams can arrive in various forms; phishing emails, fraudulent phone calls or text messages. All of them aim to exploit unsuspecting victims for financial gain. Recently, I found myself on the receiving end of one such scam. This led me to reflect on how important it is to actively anticipate the latest cyber threats and to maintain vigilance.
It began with an email notification purporting to be from PayPal. The notification claimed that my account had been charged $600 for McAfee Antivirus software. I was urged to take immediate action. The email instructed me to contact a provided customer service number to resolve the supposed issue. As I scrutinized the email further, alarm bells rang in my mind. The sender’s address raised suspicion— the address was connected to a generic Gmail account, a far cry from the official communication channels one would expect from PayPal.
Despite my skepticism, I decided to call the provided number to investigate. What ensued was a conversation with an individual who claimed to be a customer service representative. However, the person’s demeanor was far from professional. The individual immediately inquired about my location and whether or not I was on my laptop. When I requested a reason and asked why we couldn’t handle the issue over the phone, the person replied that it was because a laptop has a bigger screen, and it would be easier to fill out the form that he was going to send.
Sensing something amiss, I stated that I wasn’t home and didn’t have my laptop with me, to which the caller abruptly hung up. It was a clear indication of foul play; a phishing attempt to obtain sensitive information or compromise my device’s security.
Reflecting on this encounter, I realized just how easily people can be fooled if they think that they are going to lose money. These scammers were very unprofessional and didn’t sound authentic on the phone. Also, using a Gmail address was a big mistake for them. If they had executed on their activities with a bit more sophistication and polish, I might have fallen victim to the scam.
Here are crucial tips to help you and yours avoid falling victim to similar scams. Consider sharing these tips with employees:
1. Verify sender information: Always scrutinize the email sender’s address. Look for any red flags, such as suspicious domain names or generic email providers (like Gmail or Yahoo), especially if they’re being used for “official” communications from reputable organizations.
2. Exercise caution with unsolicited requests: Be wary of unsolicited emails or messages requesting urgent action, especially if the emails or messages involve financial transactions or account verification. Legitimate companies typically don’t request sensitive information via email.
3. Double-check website URLs: Before clicking on any links in emails, hover over them to preview the URL. Verify that they lead to legitimate websites. Make sure that they aren’t phony links to phishing sites that were designed to steal login credentials or personal data.
4. Use two-factor authentication (2FA): Enable 2FA wherever possible, especially for sensitive accounts, like bank accounts or email accounts. This adds an extra layer of security by requiring a secondary verification method, such as a code sent to your phone.
5. Stay informed and educated: Keep abreast of the latest cyber security threats and techniques used by scammers. Organizations like the Federal Trade Commission (FTC) and cyber security blogs, like CyberTalk.org, provide valuable resources and tips for protecting yourself online.
6. Report suspicious activity: If you encounter a potential scam or phishing attempt, report it to the appropriate authorities or the impersonated business. This helps raise awareness and can compel a business to act, thereby preventing others from falling victim to similar schemes.
7. Don’t engage in discussion with scammers: If the email includes a phone number, you shouldn’t call to resolve the alleged issue.
Maintain vigilance regarding any unsolicited messages that you receive. Don’t click on any links and don’t call numbers provided. If an email informs you that a large sum has been debited from your account, consider whether or not the story seems authentic. Check your credit card bills and contact the real customer support numbers for the company that the scammers are purportedly from.
For instance, in the case that I outlined above, I should have researched the real customer support number for McAfee or Paypal and called there, rather than calling the number that was included in the message. Stay savvy and secure.
For more insights from cyber security expert Lari Luoma, click here. To receive clear cyber insights, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#2fa#Accounts#analyses#antivirus#authentication#awareness#Business#Check Point#code#communication#communications#Companies#compromise#credentials#credit card#crime#customer service#cyber#cyber crime#cyber scams#cyber security#cyber security blogs#Cyber Threats#cybersecurity#data#domain names#double#email#employees#Exercise
1 note
·
View note
Text
Mobile App Security Best Practices: Protecting User Data

Welcome to our blog post on mobile app security best practices! In a world where smartphones have become an extension of ourselves, safeguarding user data has never been more critical. As technology advances at breakneck speed, so does the sophistication of cybercriminals seeking to exploit vulnerabilities in mobile apps. But fear not! In this article, we will take you through some foolproof strategies and essential steps to fortify your app’s defenses and ensure the utmost protection for your users’ valuable information. So, grab your virtual hard hat and let’s dive into the captivating realm of mobile app security together!
Introduction To Mobile App Security
Mobile apps have become an integral part of our daily lives, providing us with convenience and access to a wide range of services. From ordering food and booking rides to managing finances and social interactions, there is an app for almost everything. However, with the increasing usage of mobile apps comes the need for strong security measures to protect user data.
In today’s digital age, data privacy has become a major concern for consumers, and rightfully so. With cyber attacks becoming more sophisticated and frequent, it’s essential for developers to prioritize mobile app security in order to gain the trust of their users. In this section, we will discuss the basics of mobile app security and why it’s crucial for both developers and users.
Why Is Mobile App Security Important?
Mobile app security has become increasingly important in recent years as the use of mobile devices continues to rise. With more and more personal information being stored on our phones, it is crucial that we take necessary measures to protect our data from potential threats.
One of the main reasons why mobile app security is so important is because of the sensitive information that can be accessed through our mobile devices. Most people use their phones for a variety of purposes including online banking, social media, email, and even storing personal documents. This means that if a hacker gains access to your phone or any of these apps, they could potentially have access to all your personal information.
Another reason why mobile app security should be a top priority is due to the increasing number of cyber attacks targeting mobile devices. According to a report by McAfee in 2020, there was an 118% increase in new malware variants specifically targeting Android devices compared to the previous year. This highlights the need for strong security measures in place to protect against these threats.
Furthermore, many mobile apps also collect user data such as location information, contact lists, and browsing history. This data can be valuable for companies but it also puts users at risk if it falls into the wrong hands. In fact, one study found that over half of popular Android apps were sending user data to third-party websites without users’ knowledge or consent.
Common Types Of Mobile App Attacks
Mobile app attacks have become increasingly common in today’s digital landscape, posing a serious threat to user data security. As more and more people rely on mobile apps for daily tasks such as banking, shopping, and social media, it has become essential for businesses and individuals to understand the different types of mobile app attacks in order to protect their sensitive information.
1. Malware Attacks
Malware is a malicious software that is designed to gain unauthorized access or cause harm to a device. In the context of mobile apps, malware can be disguised as a legitimate application and once downloaded, it can steal sensitive information such as login credentials, credit card details or even take control of the device. Common forms of malware include Trojan horses, viruses, adware and spyware.
2. Man-in-the-Middle Attacks
Man-in-the-middle (MITM) attacks occur when hackers intercept communication between two parties without their knowledge. In the case of mobile apps, this could happen through public Wi-Fi networks or fake websites that mimic legitimate ones. Through these tactics, hackers can steal personal information such as passwords and credit card details.
3. Injection Attacks
Injection attacks involve inserting malicious code into an app’s codebase with the intent of exploiting vulnerabilities in the app’s design or functionality. These attacks are often used to gain access to databases containing sensitive information or to manipulate data within the app itself.

Best Practices For Protecting User Data
In today’s digital age, protecting user data is of utmost importance. With the increasing use of mobile apps, it has become crucial for developers to implement strong security measures to safeguard user data. Here are some best practices that can help in protecting user data on mobile apps.
1. Implement Strong Authentication Measures:
The first line of defense against potential threats is strong authentication measures. Users should be required to set up a secure password or PIN before accessing the app. Additionally, biometric authentication, such as fingerprint or facial recognition, can also be implemented for an added layer of security.
2. Use Encryption:
Encrypting sensitive information such as login credentials, credit card details, and personal information is essential in ensuring that even if the data is intercepted by hackers, it cannot be read or used. Developers should use industry-standard encryption algorithms like AES (Advanced Encryption Standard) to protect user data.
3. Regularly Update and Patch:
Hackers are constantly finding new vulnerabilities and exploits in mobile apps to gain access to user data. Therefore, it is crucial for developers to regularly update and patch their apps with the latest security updates and fixes. This will not only strengthen the app’s security but also provide a better experience for users.
4. Limit Data Collection:
One way to reduce the risk of exposing sensitive user data is by limiting the amount of information collected by the app. Developers should only collect necessary information and refrain from unnecessary permissions that may put user privacy at risk.
– Encryption Techniques
In today’s digital age, mobile apps have become an integral part of our daily lives. From banking to social media, we rely on various mobile apps for convenience and efficiency. However, with the increasing use of mobile apps, there is also a growing concern about the security of user data. Data breaches and cyber attacks have become more common, making it crucial for app developers to prioritize security measures in their applications.
One important aspect of mobile app security is encryption techniques. Encryption is the process of converting plain text into a code or cipher that can only be understood by authorized parties with access to a decryption key. It helps in protecting sensitive information from being accessed or altered by unauthorized users.
There are various encryption techniques used in mobile app development to ensure the security of user data. Let’s take a closer look at some of these techniques:
1) Transport Layer Security (TLS):
TLS is one of the most commonly used encryption protocols for securing internet communication between servers and clients. It ensures secure communication over networks such as Wi-Fi or cellular connections by encrypting all data transmitted between devices. This prevents hackers from intercepting sensitive information such as login credentials or financial details.
2) Advanced Encryption Standard (AES):
AES is a symmetric-key algorithm widely used in modern cryptography. It uses a single key for both encrypting and decrypting data, making it faster than other asymmetric encryption methods such as RSA. AES has been adopted by many organizations as it provides strong protection against cyber attacks.
– Secure User Authentication Methods
Secure user authentication methods are an essential aspect of mobile app security and play a crucial role in protecting sensitive user data. With the increasing usage of mobile apps, it has become more important than ever to implement strong and reliable authentication methods for users. In this section, we will discuss some best practices for secure user authentication methods that can help safeguard your app from potential security threats.
1. Implement Two-Factor Authentication (2FA)
Two-factor authentication is a widely used method of verifying a user’s identity by requiring them to provide two different forms of identification before granting access to the app. This could include something the user knows (such as a password or PIN) and something they have (such as a code sent to their registered email or phone number). By implementing 2FA, even if someone gains access to the user’s login credentials, they won’t be able to log in without providing the second form of identification.
2. Use Biometric Authentication
Biometric authentication uses physical characteristics such as fingerprints, facial recognition, or iris scanning to authenticate users. This method is becoming increasingly popular due to its convenience and high level of security. As biometric data is unique for each individual, it eliminates the risk of stolen passwords or codes being used by unauthorized persons.
3. Limit Login Attempts
Another effective way to secure user authentication is by limiting the number of login attempts within a certain time frame. This prevents brute force attacks where hackers try multiple combinations of usernames and passwords until they gain access.
– Regular Software Updates
Regular software updates are a crucial aspect of ensuring the security of any mobile app. By regularly updating your app’s software, you can mitigate potential vulnerabilities and protect user data from cyber threats.
One of the main reasons why regular software updates are essential for mobile app security is that they often include bug fixes and patches for known security vulnerabilities. Developers are constantly working to improve their apps’ security by identifying and addressing any weaknesses or flaws in the code. These updates not only improve the overall performance of the app but also enhance its resilience against potential cyber attacks.
Another significant benefit of regular software updates is that they keep your app up-to-date with the latest security protocols and standards. As technology evolves, so do cybersecurity threats. By keeping your app updated, you can ensure that it meets the current industry standards for protecting user data. This is especially crucial for apps that handle sensitive information such as personal details, financial transactions, or health records.
Moreover, regular software updates also provide an opportunity to introduce new security features into your app. These may include multi-factor authentication, biometric authentication, encryption algorithms, or other advanced techniques to safeguard user data. By incorporating these features into your app through software updates, you can create multiple layers of protection against potential breaches.
– Third-Party Security Audits
In today’s digital landscape, the security of user data is of utmost importance. With the increasing number of mobile apps being developed and used, it is crucial for app developers to prioritize security in order to protect their users’ sensitive information.
One important aspect of ensuring mobile app security is conducting third-party security audits. These audits involve hiring an external company or individual to assess the app’s security measures and identify any vulnerabilities or weaknesses that may put user data at risk.
The first step in a third-party security audit is determining the scope of the assessment. This includes identifying the specific areas or functions within the app that will be tested for potential vulnerabilities. It is important to have a clear understanding of what aspects of your app are most critical in terms of protecting user data so that these can be thoroughly evaluated during the audit.
Once the scope has been defined, the next step is conducting a thorough review and analysis of the app’s code by skilled professionals. This involves looking for common vulnerabilities such as insecure data storage, weak authentication processes, and insufficient encryption methods. The auditors will also check for compliance with industry standards and regulations such as GDPR and HIPAA.
Additionally, third-party auditors may perform penetration testing on your app. This involves attempting to hack into your app using various techniques to uncover any weaknesses that could potentially lead to a breach of user data. By simulating real-world attacks, penetration testing provides valuable insights into potential vulnerabilities that need to be addressed.
Importance Of User Education In Mobile App Security
The increasing use of mobile devices and apps in our daily lives has made securing personal data more important than ever before. As technology evolves, so do the methods used by cyber criminals to exploit vulnerabilities and steal sensitive information. This is why user education plays a crucial role in ensuring the security of mobile apps.
One of the main reasons for the importance of user education in mobile app security is that it helps users understand potential risks and how to protect themselves against them. Many people are not aware of the various threats posed by malicious actors, such as hackers and identity thieves. By educating users on these risks, they can become more proactive in taking necessary precautions to safeguard their personal information.
Another key aspect of user education is promoting safe browsing habits. Oftentimes, users unknowingly compromise their own security by clicking on suspicious links or downloading unknown files. Educating them on how to identify phishing scams and avoid downloading malware can greatly reduce the risk of a security breach.
Furthermore, user education can also help foster a culture of responsible app usage. With so many apps available today, it’s easy for users to overlook important privacy settings or grant excessive permissions without fully understanding the implications. By educating users on how apps access and use their data, they can make more informed decisions about which apps they choose to download and how they use them.
Case Study: Examples Of Successful Mobile App Security Measures
In the ever-evolving world of mobile app development, security has become a top priority for both developers and users. With the exponential growth of mobile usage and the amount of sensitive data being stored on devices, it is essential for app developers to implement strong security measures to protect user data.
To gain a better understanding of successful mobile app security measures, let’s take a look at some real-life case studies:
1. WhatsApp:
WhatsApp is one of the most popular messaging apps in the world with over 2 billion active users. With such a massive user base, protecting user data is crucial for its success. To ensure this, WhatsApp uses end-to-end encryption which means that only the sender and receiver can see the messages exchanged between them. This ensures that even if someone intercepts or hacks into the communication channel, they will not be able to access any sensitive information.
Aside from encryption, WhatsApp also regularly updates its software to fix any known security vulnerabilities and conducts regular security audits to identify and address any potential threats.
2. Venmo:
Venmo is a popular payment app used by millions of people worldwide. It allows users to transfer money securely through their bank account or credit card without sharing any sensitive financial information with others.
One key aspect of Venmo’s success in maintaining secure transactions is its use of tokenization technology. Instead of storing actual bank account or credit card numbers on its servers, Venmo creates unique tokens for each transaction that cannot be traced back to the original financial information.
Challenges And Limitations Of Mobile App Security
Mobile app security has become a major concern for both users and developers in recent years. As the use of mobile devices continues to rise, so does the amount of sensitive data being stored on them. This has made mobile apps a prime target for cyber attacks and data breaches.
While there are many best practices that can help improve the security of mobile apps, there are also several challenges and limitations that developers must be aware of. In this section, we will discuss some of the biggest challenges and limitations facing mobile app security today.
1. Diverse Device Landscape:
One of the biggest challenges in securing mobile apps is the diverse landscape of devices they run on. Unlike traditional desktop computers, which have relatively similar hardware and operating systems, smartphones and tablets come in many shapes and sizes with different hardware components and operating systems.
This makes it difficult for developers to create a one-size-fits-all approach to app security. Each device may have its own unique vulnerabilities that need to be addressed individually, making it challenging for developers to ensure their app is secure across all platforms.
2. Lack of Control over Devices:
Unlike desktop computers or laptops, which are usually owned by individuals or organizations themselves, most mobile devices are personally owned by users. This means that users have full control over what apps they download and install on their devices.
Future Of Mobile App Security
The future of mobile app security is constantly evolving as technology advances and new threats emerge. As the use of mobile apps continues to increase, the need for strong and effective security measures becomes even more crucial. In this section, we will discuss some of the key trends and developments that are shaping the future of mobile app security.
1. Biometric Authentication
One of the most promising developments in mobile app security is biometric authentication. This technology uses unique physical or behavioral characteristics such as fingerprints, facial recognition, or voice recognition to verify a user’s identity. Biometric authentication offers a more secure alternative to traditional password-based methods, which can be easily compromised.
In the future, we can expect to see more apps incorporating biometric authentication as a means of providing an additional layer of protection for sensitive data. This not only enhances security but also provides convenience for users who no longer have to remember complex passwords.
2. Increased Use of Artificial Intelligence (AI)
Artificial intelligence (AI) has been making significant strides in various industries, including cybersecurity. In terms of mobile app security, AI has shown great potential in detecting and preventing cyber attacks in real-time.
With AI-powered systems continuously monitoring for suspicious activities and anomalies within an app’s network traffic, developers can respond quickly to any potential threats before they cause harm. As AI technology continues to evolve and improve its capabilities, it will become an essential tool in securing mobile apps against ever-evolving cyber threats.
Conclusion:
Mobile app security is crucial in today’s digital world where the majority of personal and sensitive information is stored on various mobile devices. With the increasing number of cyber threats and data breaches, it is essential for app developers to prioritize the protection of user data.
The best practices mentioned in this article can serve as a guide for developers to ensure that their apps are secure and user data is well-protected. By implementing these practices, not only will it help to safeguard user data but also build trust with users and enhance the reputation of the app.
#Mobile App Security Best Practices: Protecting User Data#e commerce development#web development#web design#magento development#website landing page design#digital marketing company in usa#logo design company#web development company#web designing company#asp.net web and application development#best web development company in united states#ed not ed sheeran#tw disordered eating#disordered eating thoughts#tw ed diet#ed not sheeren
0 notes