#not even oracle thinks you should have java installed
Explore tagged Tumblr posts
Text
just installed 32 bit java. of my own volition. in 2025
#funniest thing about java is that if you haven't used it for a certain amount of time they'll prompt you to uninstall it#not even oracle thinks you should have java installed#in 2025?????!?!
4 notes
·
View notes
Text
Download magic launcher

#DOWNLOAD MAGIC LAUNCHER INSTALL#
#DOWNLOAD MAGIC LAUNCHER MOD#
#DOWNLOAD MAGIC LAUNCHER 32 BIT#
#DOWNLOAD MAGIC LAUNCHER ANDROID#
#DOWNLOAD MAGIC LAUNCHER MODS#
Upon hitting test, it did launch my minecraft game though I did note that even though my items were intact my achievements had croaked and I seem to have to start at the very beginning on that. Looks like open jdk has a better java path that takes into account the amd64 bit.īut I have more news - today when I opened the magic launcher and tried the same stuff, it worked. Somewhere on the internet, I read that java 7 oracle is better than openjdk and I made sure I updated.Īs you said the java path was /usr/lib/jvm/java-7-oracle/jre/bin/java and this was what was causing the architecture word width mismatch exception.
#DOWNLOAD MAGIC LAUNCHER MODS#
There are a lot of other Mods they have run in the past but this is what there using right now.
#DOWNLOAD MAGIC LAUNCHER INSTALL#
I would be more inclined to install Ubuntu 12.04 32bit in the first place to keep from having the headaches that would likely come from overly modifying my Ubuntu 64 bit operating system.
#DOWNLOAD MAGIC LAUNCHER MOD#
I'm concerned that ok, I fixed this Minecraft mod but now I broke something else that needs a the 64 bit version of Java on my Ubuntu 12.04 64 bit operating system.
#DOWNLOAD MAGIC LAUNCHER 32 BIT#
As for me I wont down grade to a 32 bit Java. I would bet there are other mods that would not work with 64 bit Java. Now OptiFine C Light will not work with with ModLoader.zip and OptiFine C Light will not work with 64 bit Java. The same is true of mods that require special sound files & etc. On the Magic launcher's setup page ModLoader.zip has to be at the top of the top window, so it loads first, that is with mods that require the ModLoader to run. In circles trying to get the launcher working, I am eager to try some mods etc, so I was hoping someone out here can help me out. I know that to run Minecraft the export statement is mandatory (especially so for java 7), so I am running around I think the problem revolves around setting up java correctly, I am wondering if I should have got a 32 bit java installed. If I try and change it to match the LD_LIBRARY_PATH, I dont have an executable I can point to in the amd64 directory - so I am unable to set it as it does not accept a directory. minecraft/bin/natives/liblwjgl.so: wrong ELF class: ELFCLASS32 (Possible cause: architecture word width mismatch) If I leave the default, /usr/lib/jvm/java-7-oracle/jre/bin/java, then while hitting TEST I get the error: Now when I run the magic launcher it comes up fine but while doing set up, in the advanced tab I dont know what to give for JAVA. Padsp java -Xmx512M -Xms256M -cp Minecraft.jar I run the minecraft game using the standard script:Įxport LD_LIBRARY_PATH="/usr/lib/jvm/java-7-oracle/jre/lib/amd64" So I tried to do that but I got stuck - this problem might be more Ubuntu related than the launcher itself but I still need some expertise. So I stumbled upon this launcher and it looks like it would be ideal for me to take my minecraft experience to the next level in terms of mods etc. I play minecraft on Ubuntu 11.10 and I have a fairly decent system and the game runs without any serious issues. We do not store personal information of user.I am very new to the world of minecraft and I am slowly getting to be good at it thanks to a lot of help from forums like these and of course other nooks and crannies of the internet.
#DOWNLOAD MAGIC LAUNCHER ANDROID#
You can personalize your Android phone or tablet with our amazing lovely themes for Android, TODAY! If you like this Magic Launcher app then share with your friends and family member. Rate us and give your valuable comment for this awesome Magic Launcher to create more cool apps like this. > Not Install another Launchers to use this launcher. > New high-tech features will be added constantly. > Collection of HD Icons and HD Magic Wallpaper. > Make your phone unique with all sorts of cool Magic animated effects. New Magic launcher theme is now available! Apply the Loves Launcher to enjoy with FREE Wallpapers and Icon Pack! Make your phone stylish! This fantastic cute Loves launcher will transform your Android device for free! If you are a fan of colorful themes, we have another surprise, this Loves theme launcher will be perfect for you! Get it right now and have a completely new makeover of your Android Smartphone.Ĭhange completely the way your Android looks like with this Magic theme. Magic Launcher specially designed for Magic lover, provides delicate app icons, wallpapers, folder and app drawer interface. Looking for a new way to personalize your Smartphone? If yes, New Magic Launcher is the perfect Magic Launcher for you! Match your personal style to your Smartphone with some amazing wallpapers and fantastic icons and amazing features, that will make your Android device look awesome, with our new Magic Launcher theme! Tired of using the same wallpapers and the plain icons all the time? Download the Magic Launcher to get an amazing new experience!

0 notes
Text
Java download for mac

JAVA DOWNLOAD FOR MAC INSTALL
JAVA DOWNLOAD FOR MAC CODE
JAVA DOWNLOAD FOR MAC LICENSE
JAVA DOWNLOAD FOR MAC INSTALL
| | 18.ea.3 | open | | 18.ea.3-openĬhoose one and install it using the command sdk install java IDENTIFIER, i.e.: Vendor | Use | Version | Dist | Status | IdentifierĪzul Zulu | | 16.0.1 | zulu | | 16.0.1-zuluīellSoft | | 16.0.1 | librca | | 16.0.1-librca Set sdkman_rosetta2_compatible=false (see sdkman config)Īfter that, you will see a list of compatible with M1 JDKs: sdk list java You can install the Java JDK using sdkman (see sdkman install): vim. Note that Microsoft's been working on the OpenJDK branch of AArch64 (for ARM-based Windows 10) for a while, which goes back to: A lot of the hard work was already done. Microsoft's (yes, really) GitHub source repo for an early access OpenJDK16 build for macOS on AArch64.Donate to the effort or contribute a pull request if you want it to go faster. You didn't pay them, you have no contract, and they don't owe it to you.
JAVA DOWNLOAD FOR MAC CODE
My assumption is that the ARM branch of the OpenJDK source code + the macOS bits that already exist for the macOS 圆4 release can be combined rather easily once someone with some familiarity with the OpenJDK source code has an M1-based macOS system to test it on, which should mean an adoptopenjdk macos-aarch64 release should be here within the month.īut, open source. But, it's an open source effort, so if you're anxious, by all means, read up and contribute :)Īpple has not given any details on this architecture whatsoever until November 10th 2020, unless you bought a development kit box for it (a Mac Mini with an A14 chip, which isn't an M1 chip, but close enough I guess), and signed a big NDA.Īs a rule, open source projects will run as fast as possible in the opposite direction if you wave an NDA around, so if you dislike this state of affairs, I don't think it's wise to complain to adoptopenjdk or other packagers and open source projects about it :)įortunately, now it's out, and an NDA is no longer required. That is to say: It should not be a herculean effort to create an adoptopenjdk release that runs on M1s natively, so presumably, it will happen.
JAVA DOWNLOAD FOR MAC LICENSE
So: It's not there yet, but note that JDKs for ARM have been available for more than decade, and whilst JDK 15 has dropped support for a bunch of exotic OS/architecture combinations (such as Solaris), ARM development has always remained at least partially relevant (even if so far it's mostly an Oracle commercial license offering). That (probably) won't run on macOS on M1 hardware, but that's 95% of the work already done. If you instead leave Operation System on 'any', you'll note aarch64 is in there, and this gets you to a Linux release for ARM processors. Possibly, as Apple no doubt has a bunch of extensions built into their M1 designs, and Apple gets its own. On this page: AdoptOpenJDK Latest Releases you can select 'macOS' from the 'Operating System' dropdown, and then from 'Architecture', it's currently only 圆4, but soonish there should be AArch64 or ARM64 (those are usually the shortcodes for 64-bit ARM).

0 notes
Text
Java Mac El Capitan

Java is no longer installed with a OS X 10.11 El Capitan clean install, and you’ll find that after updating a Mac a prior version of JRE may no longer function.
Java Jdk Mac Os X El Capitan
Java 6 Mac Os El Capitan
Java 6 For Mac El Capitan
Install Java Mac El Capitan
Download Java Se For Mac Osx El Captain Tsubasa; Download Java Se For Mac Osx El Captainan Download; How To Install Java (JRE) 8 on Mac OS X 10.11 El Capitan Nov 15, 2015 by iHash Leave a Comment Java is no longer installed with a OS X 10.11 El Capitan clean install, and you’ll find that after updating a Mac a prior version of JRE may no. Java for OS X 2015-001 installs the legacy Java 6 runtime for OS X 10.11 El Capitan, OS X 10.10 Yosemite, OS X 10.9 Mavericks, OS X 10.8 Mountain Lion, and OS X 10.7 Lion. The installer is damaged according to the dialogue box when the Package is double clicked.
You may come across when trying to use some particular applications or web content, “This application requires the legacy Java SE 6 runtime which is unavailable for this version of OS X.” error message, which means if you want to run that app you’re going to need to use an older version of Java.
If you do not need Java, you should not install Java. Java is, and always has been, the source of many security holes.

Here’s how you can install JRE (Java Runtime Environment).
Step 1. Open Safari and go to the Oracle Java downloads page and download the JRE .tar.gz version. You should end up with a file named something similar to jre-8u65-macosx-x64.tar.gz.
Step 2. Go to your Downloads folder and extract the JRE download or use Terminal to extract files:
Step 3. Open Terminal
Step 4. Edit the Info.plist file within to enable the JRE to be used from the the command line, and from bundled applications:
Step 5. Move the JRE folder to the correct location:
Type password on prompt.
Be sure you are in the correct directory (the JRE folder) when you issue this command, because it will move your current directory to /Library/Java/JavaVirtualMachines/!
Step 6. Create a link to add backwards compatibility for some applications made for older Java versions:
You should be done now, so try and open the application. If it does not work, some applications require legacy Java 6 to be installed.
You can have it installed without actually using it, however, it’s possible to trick the applications into thinking legacy Java 6 is installed, without actually doing so.
Step 1.Disable SIP (System Integrity Protection) in OS X El Capitan. Here is tutorial to disable and enable SIP.

Step 2. Trick some applications into thinking that legacy Java 6 is installed by creating two folders with the following commands in Terminal:
Step 3. Don’t forget to enable SIP again after creating these directories.
I recently upgraded my Mac Computer from version 10.10 Yosemite to 10.11 EL Capitan, trying to Open eclipse gave me the following error, To open 'Eclipse' you need to install the legacy java 6 runtime. Java for macOS 2017-001 installs the legacy Java 6 runtime for macOS 10.13 High Sierra, macOS 10.12 Sierra, macOS 10.11 El Capitan, macOS 10.10 Yosemite, macOS 10.9 Mavericks, macOS 10.8 Mountain Lion, and macOS 10.7 Lion.
Jul 20, 2015 How to install a compatible Java version in OS X El Capitan? Look at our simple tip below. There are 2 easiest and quickest ways to install right Java version on Mac. They work all on OS X – El Capitan, Yosemite and mavericks. 1 – Grab a El Capitan Compatible Java Version from Apple. Dec 31, 2019 In the Java ecosystem, as the new releases of JDK are introduced at least once a year, we'll probably need to switch to a newer version at some point. In this quick tutorial, we'll show how to check the available JREs, add a JRE to Eclipse, and change a Java version in an Eclipse project, so we'll be ready when that time comes. Running some applications on Mac version 10.12 Sierra, 10.10 Yosemite and 10.11 El Capitan, users are asked to install Java even after installing the latest version of Java.
Latest Version:
Eclipse SDK 4.16 (64-bit) LATEST
Requirements:
Windows XP64 / Vista64 / Windows 7 64 / Windows 8 64 / Windows 10 64
Author / Product:
The Eclipse Foundation / Eclipse SDK (64-bit)
Endpoint security checkpoint vpn for mac catalina download. Old Versions:
Filename:
Enable home sharing mac os catalina for tv shows. eclipse-SDK-4.16-win32-x86_64.zip
Details:
Eclipse SDK (64-bit) 2020 full offline installer setup for PC
Eclipse SDK 64-bit includes tools made to give developers the freedom of choice in a multi-language, multi-platform, and multi-vendor environment. Eclipse SDK provides a plug-in based framework that makes it easier to create, integrate, and utilize software tools, saving time and money. By collaborating and exploiting core integration technology, tool producers can leverage platform reuse and concentrate on core competencies to create new development technology. Download Eclipse Offline Installer Setup 64bit for PC. The Eclipse Platform
Java Jdk Mac Os X El Capitan
is written in the Java language and comes with extensive plug-in construction toolkits and examples. These projects can be conceptually organized into seven different 'pillars' or categories:

Java 6 Mac Os El Capitan
Latest Version Of El Capitan
Eclipse Java Version For El Capitan 8
Java 6 For Mac El Capitan
Enterprise Development
Embedded and Device Development
Rich Client Platform
Rich Internet Applications
Application Frameworks
Application Lifecycle Management (ALM)
Service-Oriented Architecture (SOA)
Install Java Mac El Capitan
Subprojects Platform The Platform defines the set of frameworks and common services that collectively make up 'integration-ware' required to support the use of Eclipse as a component model, as a rich client platform (RCP) and as a comprehensive tool integration platform. These services and frameworks include a standard workbench user interface model and portable native widget toolkit, a project model for managing resources, automatic resource delta management for incremental compilers and builders, language-independent debug infrastructure, and infrastructure for distributed multi-user versioned resource management. JDT - Java development tools The JDT provides the tool plug-ins for the platform that implement a Java IDE for power-users, that supports the development of any Java application, including plug-ins. The JDT adds the notion of Java projects and a Java perspective to the platform, as well as a number of views, editors, wizards, builders, and code merging and refactoring tools. The JDT allows Eclipse to be a development environment for itself. The JDT plug-ins themselves can also be further extended by other tool builders. PDE - Plug-in development environment The PDE project provides a number of views and editors that make it easier to build plug-ins for Eclipse SDK. Using the PDE, you can create your plug-in manifest file (plugin.xml), specify your plug-in runtime and other required plug-ins, define extension points, including their specific markup, associate XML Schema files with the extension point markup so extensions can be validated, create extensions on other plug-in extension points, etc. The PDE makes integrating plug-ins easy and fun. e4 - The next generation of the platform The e4 project is an incubator for developing the next generation of the platform. The mission of the e4 project is to build a next-generation platform for pervasive, component-based applications, and tools. Note: Requires Java Runtime Environment. Also Available: Download Eclipse for Mac

0 notes
Text
Why PHP technology is better for website development?

Nowadays, to create a site is a need to your business on the web. The planning and improvement are the two most encouraging advances which are critical. PHP technology is most generally utilized for the site and web application development.
Utilizing PHP as its language has numerous favorable circumstances like it underpins Oracle, Sybase, and so on. It is utilized for making straightforward capacities, techniques, and grammar. It additionally bolsters database management system and another open source database.
The following are a portion of the reasons that unmistakably clarify regarding why PHP programming language is the most ideal decision for web development as:
Easy to learn- PHP is the least difficult Dialect to learn and begin your vocation. PHP is almost like C and JAVA. Its grammar and method of utilizing are a lot of basic and simple to learn. Particularly, something more you can undoubtedly add or consolidate HTML, CSS with PHP.
Execution- These days, a large portion of the clients relinquishes the site which requires over 3 seconds stacking. Thus, the engineers need to investigate approaches to keep the guests connected by acquiring the site stacking speed. It accompanies JIT (Just in Time) engine which gathers the PHP code into machine language for better captivating outcomes.
Open Source Language- Being an open source tech, PHP can be utilized by the associations without paying any charges for the permit. The software engineers can additionally lessen the ideal opportunity for development essentially by taking the upsides of a few open source PHP structures.
Flexibility- It is quite possibly the most adaptable web programming languages and empowers the developers for making changes to the code during various phases of development. They can undoubtedly add new highlights or usefulness to the site even in the wake of composing the code. Changes should likewise be possible in existing code and can be altered to add new highlights to the site.
Robust security- PHP is exceptionally secured language. What’s more being on the second place at the secured languages, it took care of each reason effectively making it protected from hackers.
Adaptability- PHP is as of late being utilized by the few high traffic sites and likewise utilized by designers the whole way across the world to build up a wide scope of site and web applications also having the choices for making little and basic sites by installing PHP code into HTML. The assets given by the different PHP systems for making huge and complex web applications inside a more limited measure of time can likewise be benefited whenever.
Conclusion- Thinking about all upsides and downsides, it is conceivable to conclude the business advantages and answer the sensible question of “Why choose PHP?”
The most intriguing reality about this programming language is that it was not created to be a programming language. It is incredibly adaptable and consolidates well with other web development technologies, so the improvement group will have more devices in its removal. This language works flawlessly with the major operating systems, databases, and web servers. It bolsters a working framework like Linux, Solaris, and so forth.
Picking PHP technology for website development will doubtlessly give you fantastic outcomes to construct a site for your organization.
Nowadays, to create a site is a need to your business on the web. The planning and improvement are the two most encouraging advances which are critical. PHP technology is most generally utilized for the site and web application development.
Utilizing PHP as its language has numerous favorable circumstances like it underpins Oracle, Sybase, and so on. It is utilized for making straightforward capacities, techniques, and grammar. It additionally bolsters database management system and another open source database.
The following are a portion of the reasons that unmistakably clarify regarding why PHP programming language is the most ideal decision for web development as:
Easy to learn- PHP is the least difficult Dialect to learn and begin your vocation. PHP is almost like C and JAVA. Its grammar and method of utilizing are a lot of basic and simple to learn. Particularly, something more you can undoubtedly add or consolidate HTML, CSS with PHP.
Execution- These days, a large portion of the clients relinquishes the site which requires over 3 seconds stacking. Thus, the engineers need to investigate approaches to keep the guests connected by acquiring the site stacking speed. It accompanies JIT (Just in Time) engine which gathers the PHP code into machine language for better captivating outcomes.
Open Source Language- Being an open source tech, PHP can be utilized by the associations without paying any charges for the permit. The software engineers can additionally lessen the ideal opportunity for development essentially by taking the upsides of a few open source PHP structures.
Flexibility- It is quite possibly the most adaptable web programming languages and empowers the developers for making changes to the code during various phases of development. They can undoubtedly add new highlights or usefulness to the site even in the wake of composing the code. Changes should likewise be possible in existing code and can be altered to add new highlights to the site.
Robust security- PHP is exceptionally secured language. What’s more being on the second place at the secured languages, it took care of each reason effectively making it protected from hackers.
Adaptability- PHP is as of late being utilized by the few high traffic sites and likewise utilized by designers the whole way across the world to build up a wide scope of site and web applications also having the choices for making little and basic sites by installing PHP code into HTML. The assets given by the different PHP systems for making huge and complex web applications inside a more limited measure of time can likewise be benefited whenever.
Conclusion- Thinking about all upsides and downsides, it is conceivable to conclude the business advantages and answer the sensible question of “Why choose PHP?”
The most intriguing reality about this programming language is that it was not created to be a programming language. It is incredibly adaptable and consolidates well with other web development technologies, so the improvement group will have more devices in its removal. This language works flawlessly with the major operating systems, databases, and web servers. It bolsters a working framework like Linux, Solaris, and so forth.
Picking PHP technology for website development will doubtlessly give you fantastic outcomes to construct a site for your organization.
0 notes
Text
Burp Suite Battering Ram

Burp Suite, a framework of web application pentesting tools, is widely regarded as the de facto tool to use when performing web app testing. Throughout this room, we'll take a look at the basics of installing and using this tool as well as it's various major components. Burp Suite’s proxy is easy to use and syncs well if the rest of the tools within the suite. Battering ram – This uses a single set of payloads. Attack vectors are sniper attack, battering ram attack, pitchfork attack and cluster bomb. In this Burp Suite tutorial, Figure 3 shows that the payload positions are automatically highlighted with the § character. Battering Ram - Similar to Sniper, Battering Ram uses only one set of payloads. Unlike Sniper, Battering Ram puts every payload into every selected position. Think about how a battering ram makes contact across a large surface with a single surface, hence the name battering ram for this attack type.
This tutorial is yet another introduction to Burp Suite. It explains how to install and use Burp Suite, fundamental tool used by bug hunters (but not only) on daily basis to test web applications.
“Burp Suite created by PortSwigger Web Security is a Java based software platform of tools for performing security testing of web applications. The suite of products can be used to combine automated and manual testing techniques and consists of a number of different tools, such as a proxy server, a web spider, scanner, intruder, repeater, sequencer, decoder, collaborator and extender.”
In order to pass HTTP traffic to Burp from our browser, we will use Foxyproxy an Addon for Firefox and Chrome. Requests made in the browser can be viewed, edited and analysed in Burp to find web application vulnerabilities. Later sections of this tutorial will show how to use Burp Suite for specific tasks so that you can get accustomed to using it.
The following sections are provided:
Before you start reading this tutorial there are some concepts you should probably know:
What is an IP address? How are IP addresses assigned? What is a routing protocol? What is TCP/UDP?
If you don’t know much about this you can have a read at: http://www.cs.rpi.edu/~kotfid/ne1/CCNA_chapter2.pdf
This 300 pages book can also help you in your journey: http://write.flossmanuals.net/data/messages/afzalkhalil/ccna_studyguide.pdf
What is the HTTP protocol and how does it work?
There is a very good explanation about HTTP in the “Web Application Hacker’s Handbook” which you can buy on Amazon or check other free sources such as https://www.tutorialspoint.com/security_testing/http_protocol_basics.htm.
What to download to get started (go back up!)
Download the following tools:
The latest version of JAVA (see below);
Burp suite free edition: here;
Foxyproxy addon for Firefox or Chrome.
For Ubuntu open the terminal and run the following commands:
sudo add-apt-repository ppa:webupd8team/java # to add the Oracle’s repository
sudo apt-get update
sudo apt-get install oracle-java8-installer
For Windows:
Open this page in the browser http://www.oracle.com/technetwork/java/javase/downloads/index.html, download the Java JDK and install it.
Setting up Foxyproxy (go back up!)
Install Foxyproxy for Firefox or Chrome and restart the browser.
Download links are:
https://addons.mozilla.org/en-GB/firefox/addon/foxyproxy-standard/ (Firefox)
https://chrome.google.com/webstore/detail/foxyproxy-standard/gcknhkkoolaabfmlnjonogaaifnjlfnp?hl=en (Chrome)
Click on Foxyproxy’s icon and click “Options”:
Click “Add new proxy”. In the “Proxy details” section → “Manual Proxy Configuration” insert the following values for Server and Port:
Server: 127.0.0.1
Port: 8080
In the “General” section, give the proxy a name and select a colour. Then save.
Now start the proxy you just created by right clicking on the Foxyproxy icon and selecting the newly created proxy.
Starting up Burp Suite (go back up!)
You have downloaded Burp Suite for either Windows or Linux. On windows you can double-click on Burp executable to start it. On Linux you can do the same or download the plain jar file, open a terminal in the folder where you downloaded Burp and run the following command:
java -jar burpsuite_community_v1.7.30.jar
Note. The jar file might be called differently.
Start Burp Suite with default settings.
You can see several tabs: Target, Proxy, Spider, Scanner, Intruder, Repeater, Sequencer, Decoder, Comparer, etc.
This tutorial will explain how to use Burp’s tools in the order you would probably use them at the start of a web application security assessment or bug bounty.
The proxy is used to intercept requests from your browser. These can be modified on-the-fly or can be viewed together with their responses in the 'HTTP history' tab.
Click “Proxy” → “Intercept” → “Intercept On” to stop intercepting requests.
If you open a page in the browser with “intercept is on”, Burp will display the request sent from your browser and until you press “forward” or “intercept is on”, it won’t submit the request to the web application’s server and receive a response. What you will see in the browser is a page which keeps on waiting for a response. That’s because Burp hasn’t sent the request yet.
In few more words:
Click “Intercept is on” to turn off interception. This will grab all the requests sent from the browser through Burp’s proxy. Burp will send them to the right destination only if you stop intercepting or if you press the “forward” button which will forward the request to the web server. It is good to have “intercept is on” only when you know that you want to intercept a specific request to change it on-the-fly. The requests will be stored in “Proxy” → “HTTP history” for later user, even if you don’t have “intercept is on”.
If intercept is on and you don’t really want to send the request forward, click “drop”. This will not send the request to the destination. Probably you will see an error in your browser showing that the request was not submitted. Another reason why you would like to you use “drop” is when you want to see how a request is made but not necessarily send it to the web server. For example you have clicked on a “submit” button on the target site and the request has been submitted and intercepted. Now click on “action” → “Send to repeater” (or CTRL+r) and then “drop”. This way the request will be available immediately in repeater for you to modify without prior submitting the original request. You might want to do this in case every request of this type generates a lot of traffic or creates a new entry in a database.
Proxy Options (go back up!)
Click “Proxy” → “Options” to see your proxy’s settings.
As you can see the default port used by Burp for its proxy is port 8080. That is the same you chose for Foxy Proxy. If you want to choose a different port or have multiple proxies you can. Just remember to create the same configuration both in Burp and Foxy Proxy. For example you might want to have port 8080 for Foxy Proxy on Firefox and port 8089 for Foxy Proxy on Chrome. You can use the same ports on both browsers if you want.
To summarise:
If you have the following Foxy Proxy configuration: IP: 127.0.0.1 Port: 1337, then you must have the same configuration in Burp Proxy, IP: 127.0.0.1 Port: 1337. This is because the communication goes as follow:
The user is browsing the target site;
Foxy Proxy and Burp are configured with same IP and Port as explained above;
Foxy Proxy is on, Burp Proxy is on;
Foxy Proxy takes every single request the user makes and sends it the proxy’s IP and port ( in this case Burp’s proxy);
Burp intercepts the request and stores it in the HTTP History;
At the same time Burp forwards the request to the destination (the web application server) and waits for a reply
When the web server sends back a response page, Burp forwards this response back to the Browser.
Foxy Proxy makes sure all the requests are sent to Burp’s Proxy.
Burp Suite's SSL Certificate (go back up!)
Installing Burp's certificate in your browser will help you intercepting traffic sent by sites using SSL/HTTPS. The browser will not complain that your connection is not secure if you install Burp’s certificate as a trusted CA authority. You are telling the browser that Burp with its certificate is OK to encrypt/decrypt HTTPS traffic.
Try to open any pages without installing the certificate and you will see that the browser complains that the connection is not secure (e.g. https://www.facebook.com).
“By default, when you browse an HTTPS website via Burp, the Proxy generates an SSL certificate for each host, signed by its own Certificate Authority (CA) certificate. This CA certificate is generated the first time Burp is run, and stored locally. To use Burp Proxy most effectively with HTTPS websites, you will need to install Burp's CA certificate as a trusted root in your browser.
Note: If you install a trusted root certificate in your browser, then an attacker who has the private key for that certificate may be able to man-in-the-middle your SSL connections without obvious detection, even when you are not using an intercepting proxy. To protect against this, Burp generates a unique CA certificate for each installation, and the private key for this certificate is stored on your computer, in a user-specific location. If untrusted people can read local data on your computer, you may not wish to install Burp's CA certificate.”
Go back to your browser and type:
http://127.0.0.1:8080
This will open Burp proxy’s page on your local machine (The port could be different if you configured Burp to use a different one) where you can download Burp’s SSL certificate.
Download the certificate and install it in Firefox:
Click “Preferences”→ “Advanced”→ “Certificates”→ “View Certificates”→ “Authorities”→ “Import”→ Select the file you just downloaded→ Tick all the options and click “OK”.Now the certificate is installed and you can browse sites using HTTPS without problems.
If you want to install the certificate in Chrome:
Click Chrome “Settings”→ “Show Advanced Settings”→ “HTTPS/SSL”→ “Manage Certificats…”→ “Authorities”→ “Import”→ Select the file you just downloaded→ Tick all the options and click “→ OK”
If you visit any sites running on HTTPS, you shouldn't see any warnings.
Proxy History (go back up!)
Open a page in the browser with Foxyproxy on (e.g. https://www.indeed.co.uk)
Open “Proxy” → “HTTP History” to see the HTTP requests sent from the browser to Burp. In this tab you can view information related to the requests.
You can see the hostname (the site), the HTTP method used to send the request, the URL of the page/request, if parameters were sent with the request, if it has been edited by you, the HTTP status of the request, the length of the response (the size of page), the MIME type of the page (what type of page are we viewing? An HTML page? A Script? An image?), the extension of the page and finally the title of the page.
Order the list by the last request received by clicking the hashtag symbol which is the title of the first column to the left.
Click on any line in 'HTTP history' to see the request sent by the browser and the response sent by the application.
Click “Filter” to show the filter options for the “HTTP History”. Enable all the MIME types. This way you will see pictures and binaries in the HTTP History (this can be very useful).
Click anywhere in Burp’s main window to make the filter disappear.
Why is the “HTTP history” important during a test?
It lets you view all the requests you sent to one or more websites.
It lets you order the requests by type, extension, title.
It lets you search through the requests for a specific keyword.
It gives you and overview of the technology in use by the site. For example if you find the following URL https://www.england.nhs.uk/wp-content/uploads/2016/04/gpfv.pdf you can assume that the site is using Wordpress (notice the “wp-content”, wp stands for Wordpress) and thus the site is also using PHP (Wordpress is written in PHP). This tells you that you should search the web for known Wordpress and PHP vulnerabilities. This is a short explanation that will be part of another tutorial.
Target
Target Sitemap and Scope (go back up!)
Click “Target” → “Site Map”. You will see several websites included in the site map. These are all the sites that you have visited since you started opening pages in the browser. After effects text plugins. Of course during a web application assessment, you don’t want to see all of them because they are not part of your scope and therefore you should not test them (legally speaking, you are not authorised to test these sites.)
Click “Scope”.
Select 'Use Advanced scope control'.
Let's add a target to our target scope. A way to do so is to select the website we want to test in the Proxy's HTTP history tab. Click 'Proxy' → 'HTTP history'.
Right click on one of the lines showing the site you opened in the browser. This will open a small menu, very useful to Burp’s users. This menu and some of its functionalities will be explained in this tutorial.
Click “Add to scope” in the small menu. Click “No” in the message displayed by Burp. You just added the site to your scope.
Go back to the Scope tab under Target.
You can notice few things from the screenshot above:
The site in scope is enabled. You can disable it and it will disappear from the “Site map” tab. Useful in some cases where you want to momentarily disable a target.
Protocol. It says HTTPS. This means that in the “Site Map” tab, you will see HTTPS requests only. Several websites use a mix between HTTP and HTTPS requests. It is best to intercept both types.
The host is www.indeed.co.uk but we want to target all subdomains of indeed.co.uk (for example test.indeed.co.uk, admin.indeed.co.uk, etc.). You want to add all these sites to the scope.
Port. The standard port for HTTPS is 443. HTTP traffic generally travels on port 80. Note. You can have sites running on different ports but generally HTTP is on port 80 and HTTPS on port 443. When you open www.ciaociao.com the browser will try to open the site on port 80 and HTTP. If you open https://www.ciaociao.com the browser knows you want port 443. As said for #2 you should intercept requests on all ports. It is better in case the sites in scope use both HTTP and HTTPS
File. As you can see the file is “favicon.ico” and that’s the only thing you will see in the site map. Of course this is not what you want. You want to see all the files and folders on the site. In some cases you will remove some folders of a site from the scope. For example when you visit a site and a specific folder is full of PDF files which might not be relevant to your test.
Select the target's line and click “Edit”. Modify the options as follows to include all the protocols, all the ports and all the subdomains for the site in scope then press OK.
Go back to the “Site Map” tab and click “Filter”. Select all MIME types (as you did for the HTTP history) and select “Show only in-scope items”.
Click in the main window to hide the filter tab. Click on the little arrow situated on the left of the targeted website to view the pages that you currently opened/requested.
The “Site Map” section is very important. Here you will see quite clearly the structure of the site.
As you can see, there are folders and files just like in a file manager. The yellow icons are used for folders and can be opened to show the files stored in that folder. The icons with a small engine wheel show URLs sent with parameters. For example:
https://www.indeed.co.uk/login/?return_url=https://www.indeed.co.uk/profile
If you right click on any of the folders or files you will open a small menu. Click “Remove from scope”, if you want to remove any folders or files from your list. You can see the exclusions in the “Scope” tab.
Another important section of the “Site Map” tab is the “Issues” section which is available only in Burp’s Pro version. Burp Suite analyses passively each requests and responses and if it finds any vulnerabilities, it will be displayed in this section. “Passive scanner” will not send any requests to find the vulnerability but it will just analyse your traffic. Burp suite pro has a feature called “Active scan” which actively sends requests to find vulnerabilities. Active scan is not available for the free version of Burp Suite.
Spider (go back up!)
The spider is another important Burp’s feature. The spider lets you find the components of a site.
How does a spider work?
It is quite simple. When you open a page (e.g. https://www.indeed.co.uk) you will be able to click on buttons and links to reach other parts of the site. Several URLs (or part of URLs) can be seen in the response provided by the web application’s server. A spider takes all the URLs and requests them by sending an HTTP request to retrieve that file/page/folder. As soon as the spider receives a response from the web application, it reads the content of the response to see if there are more URLs to be opened and so on, until all the possible links have been opened. This tells you a few things:
If the site is massive, you will likely be sending a lot of requests, even thousands. Be very careful when you use the spider feature. Some sites might block your IP because you are about to send 40.000 requests. Spider only sections that you need spidering or make sure to check the site is not huge (like Ebay, Amazon, Facebook, etc.) and can be spidered.
Spidering can make waste precious time if you spider areas of the site which are not relevant. Make sure you focus your efforts (and bandwidth) if you want to be first reporting a bug.
If the spider doesn’t find a direct URL to e.g. http://indeed.co.uk/random/admin1/login.php, it won’t add it to the site map and you will probably miss a juicy page. There are other methods to find hidden components later explained.
If the spider doesn’t understand that there is a link in a response it won’t open it. In some cases it is very important to click around the site so that the spider can see more components. Sites can create URLs dynamically via Javascript (or else) and these won’t be seen by the spider. Make sure you navigate the site like a user would do.
Spider Options (go back up!)
Before using Spider there are a couple of settings you might want to change in “Spider” → “Options”.
Forms Submission
In “Forms Submission” Click “Don’t Submit Forms”. A Form is that part of a website where you have input fields and a button (not always) to submit the details you just entered. A form could be a login prompt (username and password with “login” button), it could be a search component, a contact form, etc.
Why is better not to submit forms when spidering?
Imagine a site where you have several pages that when opened have a contact form in it. Burp spider will input some semi-random data in the input fields and submit the form, then read its response. What happens to the data you submitted? It is possible that the data you submitted will be sent via email to one or more of your client’s employees (it’s a contact form so you should expect someone to read what you sent). Missing_jat3_framework_plugin. This can be very annoying in the case you submitted hundreds of emails. Clients don’t like this. When you find a form, try to submit it manually to see the resulting page. In cases where you are sure there is no danger you can activate spidering on forms again.
Application Login
Set “Don’t submit Login forms” in “Application Login”. Similar to the paragraph above, you don’t want to submit login forms in case the client doesn’t want you to try a bruteforce attack against login pages. You can do this manually, it won’t take long.
Spider Engine
The spider Engine has 2 useful options.
Number of threads. How many requests should the spider work on at the same time? It is important you set this option correctly. Let’s say a website is not very responsive (it’s old or just badly designed) and you start sending many requests per second. This could cause a Denial of Service (it happens). Some websites are protected by Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS) or Web Application Firewall (WAF). If any of these systems notices you are sending several requests at the same time, they might block your IP from reaching the site as a defence mechanism. Lower the number of threads if required.
Throttle between requests. Same as above. Some IDS, IPS or WAF might notice your traffic and decide to block you. Send requests with throttle (1000 milliseconds = 1 second). This way you won’t get your IP blocked but spidering will take a bit more.
Spidering (go back up!)
How do you spider a site?
Go to “Target” → “Site Map” then right-click on the site you want to spider and select “Spider this host”. This will spider the entire site. If you prefer to spider a specific folder, right-click the folder of the site in the “Site Map” area and select “Spider this branch”.
When you activated spidering against a site/folder, go back to “Spider” → “Control” to see how many requests have been queued (How many requests the spider has to send). This will tell you if you found an area of a site with hundreds of requests to be made.
This is what happens if you try to spider indeed.co.uk:
This is why it is important to select only specific areas to be spidered in the case you have to test a huge website and don’t want to spend your spidering resources requesting very similar pages (e.g. if the site is posting job adds, you can assume that all job adds will have a similar structure. If one of these pages is vulnerable, all the others will be as well. You don’t need to see/request all of them to know).
Repeater as the name suggests, lets you repeat/replay a request. It shows you the request in the left pane. You press Go and Burp sends the request. You can go back and forth to see all the requests and responses you have sent to repeater (these are not added to the sitemap and HTTP history tabs unless you add them yourself). The response is shown in the right pane.
This is useful because:
Otherwise you would probably use the browser. Copy the URL, modify it, paste it back into the search bar, press Enter and see the result. (if you feel brave, you could look into the 'curl' command in Linux)
You can’t modify HTTP POST requests in the browser’s search bar unless you install a plugin/addon.
It is much easier to search for a specific keyword into the response of the request.
It is much easier to select the value of a parameter and replace with the value you want.
Con: Javascript won’t be executed. Javascript can affect the DOM and show the value of a parameter you just injected.
In order to send a request to repeater go to “Target” → “Site Map” tab or into the “Proxy” → “HTTP History” tab and select the request you want to repeat. Right-click and “Send to Repeater” or CTRL+R.
Indeed.com lets you find jobs and people to hire. Let’s try to find someone with “penetration testing” skills.
Try opening the following request into the browser, find it in “HTTP History” and send it to repeater:
https://www.indeed.com/resumes?q=penetration+testing&l=Manchester&co=GB&rb=cmpid%3A4814378
Click “Go” and see the resulting response.
From the screenshot above you can notice few things:
The request is on the left; the response is on the right;
In blue you have parameters (including cookies) and in red you have their values;
The request is an HTTP GET request
The resulting page is 27,165 bytes (see bottom right corner)
It took 980 milliseconds to load the response (see bottom right corner)
The response Content-Type is text/html (a classic HTML page)
The word “penetration” is used in the request (parameter “q”) and found 40 times in the response.
Try to change the value of the parameters of the request to see what happens to the response.
Note:
You are not looking for a vulnerability here, you just want to see how easy it is to use repeater.
If you click “Params” in the “Request” pane you will see all the cookies and parameters of the request. This can be helpful when a request has a lot of parameters, you want to see them in order and modify them quickly.
Intruder (go back up!)
“Burp Intruder is a powerful tool for automating customized attacks against web applications. It can be used to automate all kinds of tasks that may arise during your testing.”
Few of the automated tasks you might want to achieve are:
Brute force of login pages. You have a login form, a user’s list, a password’s list and you want to see whether any of the accounts are using a weak password.
Brute force of numeric IDs. For example you have the following request http://www.somesites.com/user/private/documents/?id=10249 which allows you to download a document you own (with id 10249). You found out that this component is vulnerable to IDOR (insecure direct object reference) which allows you to see the documents of all the users. Now you want to download all these documents for a quick proof of concept. Intruder will do the job.
Testing all parameters for a specific list of payloads. You have a list of payloads which could suggest the site is vulnerable to X or Y. You want to test all the parameters and cookies with your list.
Discover hidden content which is similar to what you would do with tools such as dirb and dirsearch.
Intruder example(go back up!)
The following example will show you how to use intruder to brute force numeric IDs.
The following request (http://example.com/groupmembers.asp?groupid=1300) allows unauthenticated users to view the member’s directory of the group with id equal to 1300. Users’ email addresses are disclosed in the page (yes, users log in with their email addresses).
If you tried to open the same URL and change the groupid to 1299 you would be redirected to the login page and no emails would be shown to you. This is probably because some groups don’t exist anymore or their members are private. This is why you want to use intruder to catch the pages with email addresses of regular users.
Why would you want to see the email addresses of all the users subscribed to the site? To later perform a brute force against a login page!
When you access the above page, the URL will be added to the Proxy HTTP History. Right click on the line of the request and left-click “Send to Intruder”.
Click the “Intruder” tab and you will be presented with the “Target” tab. This shows you your target host and port. There is nothing to be changed here. Click “Positions” and you will see something like this:
Two points to notice from the screenshot above:
Attack type: Sniper. Intruder has 4 attack types that allow you to play payloads:
“Sniper” lets you choose one list of payloads which will be sent for each individual selected parameter. So if you have a payload list made up by “hello”, “my”, “name”, “is”, “Burp”, in this case Sniper will replace the value of the first parameter with “hello”, then with “my” and so on, then it will do the same with the “groupid” parameter.
“Battering Ram” lets you choose a payload which will be used with all the selected parameters at the same time. So if you are using the same list above, “hello” will be sent for both the first obfuscated parameter and the “groupid” parameter, then “my” and so on.
“Pitch fork” let you choose a payload list for each parameter then the first value of the first list goes into the first parameter and the first value of the second list goes into the second parameter; then the second value of the first list goes into the value of the first parameter and the second value of second list goes into the second parameter and so on.
“Cluster bomb” let you choose a payload list for each parameter. Then the value of the first parameter will be tested with all the values of the second so that all payloads of parameter 1 will be tested with all the payloads of parameter 2. Examples will be provided in this or later tutorials.
The value of the parameters is between “§” signs (and highlighted in orange). This shows that you selected 2 parameters and will apply the payloads you choose to both. Burp intruder selects all parameters and cookies by default.
Leave Sniper selected and click “Clear §” on the right side of the screen. This will deselect the parameters. What we want from this exercise is to brute force only 50 group ids (we don’t want to send too many requests at this moment).
Select the number of the “groupid” parameter and change it to 1300. Now select the two zeros of 1300 and click “Add §”:
As you can imagine, whatever payload you choose will go between the “§” signs to substitute the “00”. We want to test IDs 1300 up to 1350.
Click “Payloads” tab.
“Payload Sets” allows you to select the “Payload set” which is the injection point you selected (in this case it is only one) and the payload type. Burp intruder has several payload types. The most used are probably “simple list” (you can choose a file with payloads one per line) and “Numbers” (you can choose a way to brute force numeric IDs).
“Payload options” allows you to change the way you use a payload type. In the case of “simple list”, it lets you choose a file or one of Burp’s default lists.
“Payload processing” allows you to modify the payload on the fly. For example you can add a prefix or suffix to the payload.
“Payload encoding” allows you to choose if you want to URL encode specific characters. Some web applications require specific characters to be encoded or the request will fail.
Select “Payload type” → “Numbers” and input the following options:
Here we are telling Burp to use numbers from 00 to 50. We start from 00 because the part of the parameter we selected is made up by 2 zeros (Remember the “13§00§”?). We also want a minimum and a maximum number of integers equal to 2 meaning Burp should send 00, 01, 02 and not just 0, 1, 2, etc.
We will cover Burp Intruder options in the next tutorials.
Click Intruder in the top bar and “Start Attack”:
Burp will start sending the payloads as you specified.
From the screenshot above you can notice few points:
The payload you used is in the second column
The HTTP response code in the third column is different depending on the request (some “200 - OK” and some “302 - Redirection”).
The length of the response in the sixth column is different depending on the request.
Point #2 and #3 clearly tell you that some requests give you back the page of a group (the ones with HTTP code 200 and a greater response length) and others redirects you to the login page (HTTP code 302 and response length 392).
Burp Suite Battering Ram Meaning
During a real-world attack scenario you would probably enumerate all the group IDs, then find all the email addresses for the users and then if allowed by the engagement rules, perform a brute force attack.
Decoder lets you decode/encode strings into different formats such as URL, Base64, HTML encoding. As said above web application will accept/need encoded characters in order to understand specific requests.
Comparer
Comparer lets you compare requests and responses. This can be useful when you submitted 2 requests and changed the value of a parameter. The resulting response differs from the first one by few bytes. You want to know where in the page something has changed.
Others
Burp has more features that would be good to discuss. This tutorial won’t go into more details but later tutorials will show other ways to exploit Burp’s potential.
Happy Hunting!
This article is a part of the Guide for Burp Suite series. Within the previous article, we see how to work with the Burp Proxy tab. Now we'll move forward and learn about some of the features of the Intruder tab. So Let's Get Started.
Burp Intruder is a powerful tool for automating customized attacks against web applications. It can be used to automate all kinds of tasks that may arise during your testing. It is extremely flexible and configurable and can be used to automate all kinds of tasks that arise when testing applications. For example, automate tasks like Brute force for the login page.

Looking more closely at the Intruder tab, you will notice there are four subtabs available: Target, Positions, Payloads, and Options.
Battering Ram For Sale
Target - This is used to configure the details of the target server for the attack.
Positions - This is used to configure the request template for the attack, together with payload positions, and the attack type (this determines the way in which payloads are assigned to payload positions).
Payloads - This is used to configure one or more sets of payloads, which will be placed into payload positions during the attack.
Options - This is used to configure numerous other options affecting the attack.
The simplest way to configure Intruder is to select the request you want to attack anywhere within Burp (HTTP History, Repeater, Site map,etc.) and choose the 'Send to Intruder' option on the menu. This will send the selected request to Intruder.
Attack Target
This tab is used to configure the details of the target for the attack.
Host - Here we have to enter the IP address or hostname of the target server.
Port - Here we have to enter the port number of the HTTP or HTTPS service.
Use HTTPS - We need to choose whether the target is using HTTPS or not.
Payload Positions
This tab is used to Configure the positions where payloads will be inserted into the base request. The attack type determines the way in which payloads are assigned to payload positions.
Controls
Add § - This will select the selected text as a payload position in the request template.
Clear § - This removes all payload positions from the request template.
Auto § - This makes a guess as to where it might be useful to position payloads and places payload position accordingly.
Refresh - This will refresh the syntax colorizing of the request template editor, if necessary.
Clear - This deletes the entire request template.
Attack Type
Burp Intruder supports various attack types like Sniper, Battering ram, Pitchfork, and Cluster bomb.
Modern Battering Ram
Sniper - The sniper attack uses only one payload set, and it replaces only one position at a time. It loops through the payload set, first replacing only the first marked position with the payload and leaving all other positions to their original value. After it's done with the first position, it continues with the second position.
Battering ram - The battering ram attack type places the same payload value in all positions. It uses only one payload set. It loops through the payload set and replaces all positions with the payload value.
Pitchfork - The pitchfork attack-type uses one payload set for each position. It places the first payload in the first position, the second payload in the second position, and so on.
Cluster bomb - The cluster bomb attack tries all different combinations of payloads. It still puts the first payload in the first position and the second payload in the second position. But when it loops through the payload sets, it tries all combinations.
This tab is used to configure one or more payload sets. The number of payload sets depends on the attack type defined in the Positions tab. For many common tasks, such as brute force guessing a user's password, fuzzing parameters, or cycling through page identifiers, only a single payload set is needed.
Payload Sets - Here we can define one or more payload sets. The number of payload sets depends on the attack type defined in the Position tab. Various payload types are available for each payload set, and each payload type can be customized in different ways.
Payload Options - This payload type lets you configure a simple list of strings that are used as payloads.
Payload Processing - You can define rules to perform various processing tasks on each payload before it ti used.
Payload Encoding - This setting can be used to URL-encode selected characters within the final payload, for safe transmission within the HTTP request.
This tab contains Intruder attack options for request headers, the request engine, attack results, grep match, grep extract, grep payloads, and redirections. You can edit these options in the main Intruder UI before launching an attack, and most settings can also be modified in the attack window when the attack is already running.
Request Headers - These settings control whether Intruder updates the configured request headers during attacks.
Request Engine - These settings control the engine used for making HTTP requests when performing attacks.
Attack results - These settings control what information is captured in attack results.
Grep - Match - These settings can be used to flag result items containing specific expressions.
Grep - Extract - These settings can be used to extract useful information from responses to the attack results table.
Grep - Payloads - These settings can be used to flag result items containing reflections of the submitted payload.
Redirections - These settings control how Burp handles redirections when performing attacks.
Burp Suite Battering Ram Images
Congratulation! finally, you know about the Intruder tab which is present in the Burp Suite. In the next Part, we will see how to work with the Intruder Tab.
Burp Suite Battering Ram For Sale
#burpsuite #burpsuitetutorial #burp #webapplicaitonpentesting

0 notes
Text
300+ TOP COGNOS ReportNet Interview Questions and Answers
COGNOS ReportNet Interview Questions for freshers experienced :-
1. What is the main advantage of impromptu over cognos reportnet? One of the advantage's of Reportnet, is 1. It is web-based reporting wherein, reports can be easily accessed from anywhere through a browser. by using ipromptu we can use multidimensional analysis to see the data in diff formates.i.e we have drillup,drilldown features in cognos impromtu,but it is not possible in reportnet. 2. What is the difference between Native SQL and Cognos SQL? In cognos reportnet Native SQL is used for the single datasource to import the meta data Cognos SQL used for multiple datasources to import the metadata 3. What is the Difference between PowerPlay transformer and power play reports? 'Powerplay transformer' is an 'MOLAP' tool using which one can create multi dimensional structure called "CUBE". 'Powerplay for reports' is used to generate report from the cube.Only one report can be generated from one cube.If u want 'n' reports u must create 'n' cubes. 4. Is there any comparison available for Cognos Reportnet Vs Crystal reports? There is a lot of difference between Crystal reports an Cognos Report net. Crystal report is a product of Business Objects where as Reportnet is of cognos. Cryatal reports is for only low 2 midrange analysis and that to some even says tha they wont use this for analysis used to make proper strategic decision But report net yes it is for high end analysis. In reportnet we can login through web and can create our own desired report through web. 5. How do i allow a dynamic selection of a column for a measure in a chart,without using Variable You can in do it in this way. first creat a list report in which u have a calculated item in the starting. Then creat a prompt page with a value prompt.In value prompt creat static choice of which u want to be dynamically displayed. Let the parameter of value prompt be ?Par1? and the choices as Revenue, Cost. Now u write the expression of the calculated item in the report page as follows, "If ?Par1?=Revenue then Revenue else Cost. Here Revenue,Cost should b dragged from the Model Items. So now the calculated item column displays the value of the one selected in the prompt. Now make a graph using the list report,then place the calculated item on the axis of the chart ,which u wanted to display dynamically based on ur selection. So now if u select Revenue in the prompt then the grph will take the values for Revenue.And if u select Cost then graph will be with the values of Cost. 6. How do we drill through from a powerplay cube to reportnet? Setting up drill-through access from PowerPlay Web to ReportNet involves configuring Cognos Series 7 for drill-through access to ReportNet preparing the Transformer model and cube copying the search path of the folder that contains the target report enabling the cube for drill-through access to ReportNet deciding which filters to create in the target report creating the target report disabling the Drill Through Assistant 7. What are versions of reportnet? In ReprotNet have two vertions ReportNet 1.0 ReportNet 1.1 MR1, MR2 8. What is prompt?types of prompts?use of prompts?syntax of prompt? Prompts act as questions that help users to customize the information in a report to suit their own needs.The different types of Prompt are Value prompt Text Prompt Date prompt Time prompt Date and time prompt Using prompts is faster and easier than repeatedly changing the filter. Cognos Report Studio provides several ways to create prompts. You can use the Build Prompt Page tool build your own prompt and prompt page create a parameter to produce a prompt create a Prompt directly in a report page 9. What is difference between qurry studio and report studio? Query Studio: Used to create Ad-hoc (or) simple reports. It does not provide any pre-defined report templates. It directly displays data (without running the report) when we insert attributes in the report. Report Studio: Used to create complex reports. It provides pre-defined report templates. It does not display the data directly in the report. We need to run the report to display the data. 10. What are components of report studio? Componenets of Report Studio: Insertable Objects pane. Properties pane. Explorer bar - Conditional Explorer, Query Explorer, Page Explorer. Report Viewer - Workarea, Report Layout Objects.

COGNOS ReportNet Interview Questions 11. What are necessary tasks to install reportnet software You need to do the following for a standard installation process: Verify your system requirements like RAM Minimum: 512 MB, a Web server installed and started Review the ReportNet default settings like default ReportNet ports and URI settings. Create the database for the content store which means you must create the database that is used for the content store using either Oracle, Microsoft SQL Server, or DB2 UDB. ReportNet uses this database to store, organize, and retrieve information. Install ReportNet: Use the installation wizard to select the components you want to install and the location on your computer where you want to install them. Set up the database client for the content store (Oracle and DB2): If you use Oracle or DB2 as the database server for the content store, additional steps are required after you install ReportNet before you can configure ReportNet. you need to go to the 6th step only when installing on UNIX. For Windows above 5 steps are good. Update Your Java Environment: Before you can use the cryptographic operations, such as data encryption and key management, implemented by ReportNet, you must check that the required JAR (Java Archive) files are present in your Java Runtime Environment (JRE). 12. What are components of reportnet? ReportNet has a three-tier architecture, namely, (1) Web server (2) Applications and (3) Data. The tiers are based on business function, and are typically separated by firewalls. ReportNet user interfaces sit above the tiers.ReportNet user interfaces include (a) Web-based Cognos Connection, Cognos Report Studio, and Query Studio (b) Windows-based Framework Manager 13. How do we provide security in frame work manager for a query subject? procedure for providing security for query subject in frame work manager is: select querysubject -> in properties pane select ->security filters(click on edit)a specify data security wizard appears->click on add groups -> cognosnamesspace(select users and groups wizard opens) 14. I want to display zero when null values coming to report how can I do that? You can follow this procedure :- Lets assume revenue is the field in which we have to display null values as 0. First create a calculated item and Then write the expression of the cal item using If Then Else construct as If (Revenue is null) Then ('0') Else(Revenue) I think u can easily understand this. Now u can see that the null values r displayed as '0' in the calculated item. Select the data item in which you want to replace null with 0 .Go to Properties pane, Click Data Format, in this put 0 in Missing value Characters. 15. How can i create prompts in report net Prompts is mean by the end user can be filter the data. you can open the explore bar and added the new prompts page, And enter the new name. you go to tool menu and track prompts button you select prompts and then ok 16. Difference between filter and conditin The difference between Filter and Condition:Condition returns true or false Ex: if Country = 'India' then ...Filter will return two types of results1.Detail information which is equal to where clause in SQL statement2.Summary information which is equal to Group by and Having clause in SQL statement 17. Can report net connect multiple datasource at a time in report creation time Yes it can connect multiple datasources at a time when the frame work manager has the metta data regarding that datasources. 18. How can i test report in reportnet If we wanna test the report in report net, first we can intially check by validating it in the report page. After that we can test the out put of the report Using a sql anlyser and sql query.so here we will be comparing the sql analyzer output with the output of the report viewer. 19. What are the various file formats involved in reportnet? It has six (6) formats in report net. They are HTML, PDF, Excel 2000, Excel 2002, CSV, and XML format. We can see the types of formats in the report viewer on the right side . 20. How to generate IQD file from framework manager Create a Query Subject, from the properties pane select externalise,there we have 4 options in that select IQD 21. What is meant by Junk Dimension? The junk dimension is simply a structure that provides a convenient place to store the junk attributes".It's randomly used dimension. 22. what are semi and non additive measures.. 1.Semi-Additive: Semi-additive facts are facts that can be summed up for some of the dimensions in the fact table, but not the others. 2.Non-Additive: Non-additive facts are facts that cannot be summed up for any of the dimensions present in the fact table. Current Balance and Profit Margin are the facts. Current Balance is a semi-additive fact, as it makes sense to add them up for all accounts (what's the total current balance for all accounts in the bank?), but it does not make sense to add them up through time (adding up all current balances for a given account for each day of the month does not give us any useful information). Profit Margin is a non-additive fact, for it does not make sense to add them up for the account level or the day level. 23. What is catalog and types of catalogs in cagonos and which is better? catalog is a data base and also frient hand data base. types of catalog is 4 tyes personal secured shared distributed 24. what is difference between PAGE BREAK and Section Report? Section-section is eliminate the duplicate recod.but report looking separate bluck.setpagebreak means to display the reports in onepage. eg. suppose u create a list report ordermethod,orderyear,revenue when u create section on ordermethod.it will eliminate the duplicate record.but when u apply the set pagebreakc.report display in onepage.like fax reports in onepage,email reports in another page.this in cognos 8 querystudio.But in report studio you can do using propetispan. 25. use this query i am retriving all years OCt data from 01-10-2004 to 30-10-2007 i need to restrect this query to current date and current year ..between 01 and to_number(to_char(current_date,'MM'))and ..=to_number(to_char(current_date,'MM')) pass polar ID A.You have a function called 'extract' in cognos. Ex:- extract(month,the dte field). by giving like this you will get month. so you can keep a filter to restrict the rows only for october. COGNOS ReportNet Questions with Answers Pdf Download Read the full article
0 notes
Text
A Recap of the 2019 CWP User Group

More presenters!
With some last-minute volunteering at this year’s CWP User Group at FileMaker DevCon (our 13th annual!), we had a record-high seven people share with the group.*
We saw:
Joel Shapiro @jsfmp (that's me) - details below…
Mark DeNyse @mdenyse, who demonstrated how, with his fmPDA, you can change just one line of legacy FX.php code to use the FileMaker Data API with a new FX.php DataSource class. He then showed techniques for using the Data API to store data passed to a SmartThings webhook, and also demonstrated how to pull weather data from multiple sources (Ambient and Weather Underground) with cURL and the Data API to display in an iOS SDK app.
Charles Delfs @mrdelfs, who talked about how they incorporate testing at four levels in their CWP service. He demoed UX pre-build testing, automated CWP testing, and FMP testing, using fullstory and UI-licious.
Steve Winter @steveWinterNZ, who showed us how he uses database abstraction to decouple an app from its underlying database. Using Doctrine and Symfony he demoed how he can change one line of code to switch between the FileMaker PHP API and the Data API, or potentially any other database connection. You can see his slides and resources on his blog
Mike Beargie @MikeBeargie, who showed us some work he's been doing with Laravel Nova.
David Nahodyl @bluefeathergrp, who showed off a clever mapping solution where they’re caching data as JSON in Amazon S3 instead of pulling it directly from the FileMaker database in order to both improve performance and reduce Data API usage. You can see the demo, using customer/customer as the username and password.
Lui de La Parra @lui_dog, who shared his fms-api-client and node-red-contrib-filemaker, along with Node-RED. “fms-api-client” is a FileMaker Data API client designed to allow easier interaction with a FileMaker database from a web environment. This client abstracts the FileMaker 17 & 18 Data API into class based methods. “node-red-contrib-filemaker” uses “fms-api-client” to connect via the FileMaker Data API to FileMaker Server and provide FileMaker nodes to Node-RED. Node-RED is a programming tool for wiring together hardware devices, APIs and online services in new and interesting ways. It provides a browser-based editor that makes it easy to wire together flows using the wide range of nodes in the palette that can be deployed to its runtime in a single-click.
My turn…
I started out mentioning a couple recent items that all CWP developers should be aware of:
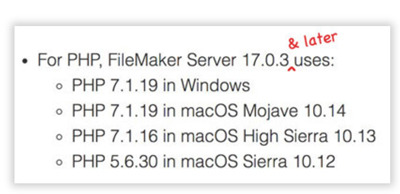
FileMaker Server 17.0.3+ now installs PHP 7, but the PHP API isn’t compatible
For the first time since the FileMaker PHP API came out with FileMaker 9, the FMS installer now installs PHP 7.x. Unfortunately, the API itself has not been updated to be PHP 7-compatible. If you haven’t already updated your version of PHP to 7.x, the easiest way to have your CWP site work with PHP 7 is to use Steve Winter’s PHP API modification. It’s a simple switch of the original FileMaker.php file and FileMaker directory to the same-named versions in Steve’s download. Note: You may separately need to modify your own PHP code to be PHP 7-compatible
Changes to Java in FileMaker Server 17.0.3+
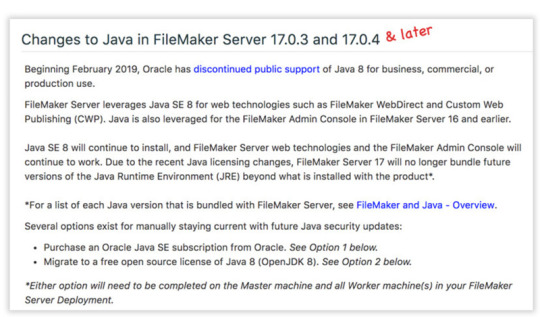
Due to changes in Oracle’s licensing of Java 8, using the Web Publishing Engine (WPE) for either the XML/PHP API or WebDirect in FileMaker Server 17 and 18 now requires us to either purchase an Oracle Java SE Subscription or use a free open source license of Java 8 (OpenJDK 8). Note: The Data API does not use the WPE and so is not impacted by this change.
Mike Duncan @SoliantMike has written a blog post that nicely describes how to deal with the change.
Who’s using the Data API in production CWP sites?
I then took a brief poll, for my own curiosity, to see how many people are using the Data API in their CWP sites. Very unscientifically… lots of people are(!) Some reported using fmPDA, some fmREST, and some RESTfm which now supports the Data API (yes, there’s fmREST & RESTfm). Presumably other people are connecting to the API in other ways, but they weren’t sharin’ :-P.
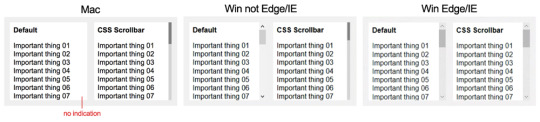
Scrollbars made visible on Mac and iOS — via CSS!
I’ve long been frustrated by the macOS/OS X and iOS default setting that hides scrollbars except when actively scrolling. I think this is Bad UX, as users often won’t realize that there’s more content for them to see. Fortunately, scrollbars can now easily be added using CSS (hurrah!) Technically, the CSS specification is about styling the scrollbar—which on Windows (where scrollbars always display) means you can make them look nicer—but to me the best part is that we can now make scrollbars always visible on Mac/iOS.
See the Pen xxKRgEB by joelshapiro (@joelshapiro) on CodePen.
According to Can I Use, browser support is now good (with the inclusion of the pseudo-elements). Even with no/limited support in Edge & IE, Windows users still get the default scrollbars; they’re just not styled.
Quick tip: Emmet plugin
Just a quick mention of the handy Emmet plugin that can be added to many text editors and IDEs. It’s installed by default in VS Code (my editor of choice).
Emmet takes the snippets idea to a whole new level: you can type CSS-like expressions that can be dynamically parsed, and produce output depending on what you type in the abbreviation. Emmet is developed and optimised for web-developers whose workflow depends on HTML/XML and CSS, but can be used with programming languages too.
So typing something like:
div.wrapper>h1#main+p
will produce:
<div class="wrapper"> <h1 id="main"></h1> <p></p> </div>

There’s a handy cheat sheet on their site.
And if I may…
*It really was great to have so many eager presenters, especially since just the day before I thought there’d only be three besides myself and we might end early. My request for you all is: Please consider sharing something with the group at next year's #ClarisEngage… but puh-leeze let me know in advance so I can plan (sleep) better.
I generally get notified about our room in the Spring and then I tweet about it and post about it in the FM Community. Please let me know you'd like to share as soon as you can after that. Thanks! :-)
0 notes
Text
Kotlin vs. Groovy: Which Language to Choose

Application of Computer Science to a growing range of fields and general advancements in technologies push programming languages to constant improvement and adaptation to the present-day needs. Now we have a bunch of languages serving different purposes: some of them emerged as an independent project, while others bud off from established and well-known languages.
The colossus of Java, for example, has a number of offspring; some of them have proved to be a success. One of them, Kotlin, was backed by Google as the official language for Android development in 2017 and was reported to be the second most loved and wanted programming language in 2018 Stack OverFlow survey and remains in Top 5 in this year’s survey. Another successful member of Java-based languages is Groovy that is gaining popularity among developers. At the same time, the 2018 Stack OverFlow survey listed Groovy among the most dreaded languages. In this setting, it seems unfair to compare the languages, but let’s see whether Groovy is so dreadful compared to Kotlin and, generally, which of them to choose as another addition to your bag of skills.
Overview
Kotlin
Kotlin is developed by Jetbrains — a company well-known in the Java world for its IDE named IntelliJ IDEA — and open sourced in 2012. It is a high-level, statically typed programming language that runs on Java Virtual Machine (JVM) and can be compiled to JavaScript source code or handle the LLVM compiler infrastructure.
Though internally Kotlin is reliant on the present Java Class library, its syntax may not be specifically compatible with Java. Kotlin has aggressive type inference to decide the type of values and expressions for which type has been left unstated. This makes it less verbose comparing to Java.
Kotlin has a practical mix of features from Java, C# and other new languages. It generally shows many improvements over Java such as null safety or operator overloading, though lacking certain convenient Java properties such as ternary operator and checked exceptions. However, both languages are completely interoperable, so they can co-exist in the same application.
Besides, since Android Studio 3.0 (published in October 2017), Kotlin is also part of the Android SDK and is involved in the IDE’s installation package as an option to the standard Java compiler. The Android Kotlin compiler allows user to target Java 6, Java 7, or Java 8-compatible bytecode.
Kotlin is much appreciated by developers for its interoperability, code security, and accuracy.
Groovy
Groovy is an object-oriented programming language for Java platform that is distributed through the Apache License v 2.0.
The key feature of Groovy is that it aspires to combine the best of two worlds: it supports both static typing typical for Java and more relaxed dynamic typing similar to that of Python.
Moreover, it can be used as both a programming language and a scripting language for the Java Platform. Like Kotlin, Groovy is compiled to Java Virtual Machine (JVM) bytecode and interoperates seamlessly by different Java code and libraries.
Generally speaking, Groovy has a Java-like syntax, but it takes on the ease of more moldable languages, such as Python and Ruby. Groovy can be called a modern Java enhancer, since it provides greater flexibility and introduces special features to applications, such as safe navigation operator (?.), the concept of Closures, Traits, runtime dispatching of methods, Groovy String, Array initialization and many others.
Groovy is a testing-oriented development language with syntax that supports running tests in IDEs, and Java build tools like Ant or Maven. Besides, it provides native support for markup languages like XML and HTML and domain specific languages.
What can also make it attractive to developers is its short learning curve: for Java developers, it is just a step away from the usual syntax, for new learners — it is relatively easy and modern.
Applications
Kotlin
Given the fact that Kotlin as an official Android development language at Google I/O, its most obvious application is Android development.
Speaking more generally, Kotlin is great for developing server-side applications, allowing developers to write concise and expressive code while maintaining full compatibility with existing Java-based technology stacks.
The most prominent applications of Kotlin are rather impressive and include the following giants:
Pinterest moved away from Java to Kotlin for their Android Application Development
Gradle built developing android files (APK files) for both IDEA and Eclipse
Evernote integrated Kotlin in their android client
Coursera built an online courses application for a range of courses
Uber made internal tooling processes on Kotlin
Atlassian and Trello did a full code conversion of the old codebase.
Kickstarter helps find resources for people showcasing creativity.
Groovy
Since Groovy is so similar to Java, it is sometimes difficult to find a distinguishing application for it. One thing that is a definite benefit is that Groovy enables to write scripts besides classes, so you can write applications and scripting with the same language. Groovy scripts are a perfect fit for tasks that change often. Since Groovy is a part of JMeter distribution, it is a good idea to use it for scripting and possibly to migrate the scripting logic developed in other scripting languages, to Groovy.
Examples of using Groovy as a scripting language are rather numerous:
1. Netflix uses Groovy for server-side scripting to offer various levels of filtering Besides, Netflix Spinnaker is implemented in Groovy.
2. Oracle’s fusion middleware is using Groovy scripts in its business component suite.
3. LinkedIn use Groovy also in their “Glu” open source deployment & monitoring automation platform.
The other direction of practical applications for Groovy is to use it as an embedded business language (a Domain-Specific Language):
1. National Cancer Institute uses it to do scientific simulations
2. JPMorgan, MasterCard and other financial institutions use Groovy for its nice DSL capabilities.

Syntax
Kotlin
Kotlin is null-safe which is perhaps the most valued feature of Kotlin missing even in Java. Kotlin has two types of references: nullable and non-nullable, so you can compose code by limited NPEs. The null safety feature of Kotlin protects developers from accessing the properties of a null reference.
In Kotlin, every class is a function, and vice versa; besides Kotlin for Android has Optional types, which help with all the safety checkups. A class can be marked as a data class with the standard functionality and utility functions already present.
Kotlin has a lot of other characteristics, like smart casts, ADT (doc), type-safe builders, zero-cost abstractions and, rather importantly, great IDE support.
Groovy
Having no data class, Groovy 1.8 introduced a few alterations which involve,among others, a new class annotation `@Canonical` that is used to create mutable classes. This annotation allows you to write classes in this shortened form and loads all possible combinations of constructors, getters and setters, creating an analogue of the data class.
One of the key features of Groove is Groovy Closures that is an open, anonymous block of code that can take arguGroovyments, return a value and be assigned to a variable. In opposition to the formal definition of a closure, Closure in Groovy can also contain free variables which are defined outside of its surrounding scope that offers a variety of advantages.
Compilation
Kotlin
Kotlin is statically typed language, meaning that the type of a variable should be known at compile-time instead of at run-time.
Groovy
Groovy was created as a dynamic language, so code gets compiled to machine code on the fly while the program is running. Since Groovy 2.0, it is possible to enable static type checking using `@CompileStatic` annotation. It feels nevertheless a little bolted on and does not enforce people to code in a static way. Sometimes even with `@CompileStatic` annotation, Groovy seems to have some dynamic performance remained.
Alternatively, it is possible to designate static typing with the help of a configuration file specifying its name with the — configscript option of the Groovy compiler. It will apply the CompileStatic AST transformation annotation to all source files in the project.

Code Style Settings
Kotlin
One might think that Kotlin as the language developed by a company famous for its intelligens IDEs, will have limitless settings to configure code style. The reality, however, is that the code style settings offered for Kotlin in IntelliJ IDEA are significantly more limited compared to Java. The difference in code style settings is intentional to a degree. The company explains that in their vision they see Kotlin code using consistent coding styles (similar to PEP8 in Python) instead of supporting infinite configuration possibilities.
Groovy
Groovy takes a place somewhere in between Java with its extensive code style settings and Kotlin that has only limited possibilities. As compared to Java, Groovy seems to be 20–25% less flexible in terms of code formatting settings.
Performance
Kotlin
In most cases, Kotlin performance is the same as Java.
Groovy
Groovy even with `@CompileStatic` in most cases is slower than Java or Kotlin due to additional runtime checks and because of Closure which is much more expensive than Kotlin lambda.
Kotlin vs. Groovy Compared
Generally speaking, Kotlin and Groovy are both JVM languages and both are developer friendly. Their major difference lies not in syntax, but in compilation. Besides, notwithstanding their differences, they are total interoperable which indicates they can co-exist in the same application.
Some developers agree that Groovy is easier for quick scripts to do something simple or for testing, while Kotlin is a better choice to create something nontrivial without all the friction/ boilerplate of Java and for Android development.
Speaking about future prospective, Kotlin seems to already grant itself a place among Android languages, so mastering it might be a thoughtful decision.
0 notes
Text
Jira Software 8.3.0 Release Notes
We're pleased to present Jira Software 8.3.
Highlights
Jira Server mobile app
Content Delivery Network (CDN) for Jira Data Center
AdoptOpenJDK bundled with JIRA
List of custom changes after upgrade
New filters to search for custom fields
Browsing projects is faster now
Improvements to batching emails
Cluster lock mechanism improved in Data Center
Re-indexing made better
Get the latest version
Interested in trying a shiny new version? Don't forget to renew your active software maintenance! Renew now.
The DVCS connector plugin, which allows Jira Software to connect o development tools such as Bamboo and Bitbucket, has been upgraded in this release. If you connect Jira Software to Bitbucket Cloud, then you must read the upgrade notes for important info about this release and upgrading, and to see the full list of issues resolved.
Also, see Jira in action. Check out our performance report for 8.3.
Compatible applications
If you're looking for compatible Jira applications, look no further:
Jira Core 8.3 release notes
Jira Service Desk 4.3 release notes
Good to know
If you want to know when our next Enterprise release is coming, see: Next Jira Enterprise release.
If you're thinking to move to Data Center, check our recommendations first. See: Infrastructure recommendations for Jira.
Jira Server mobile app
The official mobile app for Jira Server is up for grabs! You can use the app to view your work on the go and stay up-to-date with anything that’s going on in your projects. Creating and editing issues, moving them on your board, commenting away, and getting notifications when you get distracted — all this, and much more, straight from your device.

We’re not encouraging anybody to do their work on the train home, but there’s nothing like closing this last bug and just chilling away with your headphones on. Learn more about the app
Oh, and to save you time advertising the app among your team, you can use our email template to tell them about it.
Content Delivery Network (CDN) for Jira Data Center
Geographical distance has a measurable impact on page load times, so it's essential to reduce this overhead as much as possible when you have teams in multiple timezones. Don't let geography slow your team down. A Content Delivery Network (CDN) can help ease the frustration for distributed teams.
Our new CDN for Data Center feature allows you to serve static assets (such as JavaScript, CSS, and fonts) from servers closer to your users, resulting in faster page load times. For example, if your Jira Data Center server (known as the origin) is located in Germany, a CDN can improve page load times for users located in Rio de Janeiro by as much as 50%, as static assets will be served from an edge server in Brazil.

It's very straight forward to set up:
Use our template to spin up an AWS CloudFront distribution, or create an account with the CDN vendor of your choice.
Update your load balancer and firewall to allow the CDN to reach your site.
In your Jira application, provide the CDN URL and enable CDN support.
Only static assets are cached. Issues, attached files, and personal data like avatars, are still served form your origin server.
Don't want to open your site to the public internet? No problem, you can deploy your own caching servers, instead of using a third-party CDN.

See Use a CDN with Atlassian Data Center applications for more info on how using a CDN might help your team.
AdoptOpenJDK bundled with Jira
As you may know, Oracle stopped providing public updates for Oracle JDK 8, which means that only Oracle customers with a paid subscription are eligible for updates. To give you an option for a free JDK, we first added support for OpenJDK in Jira 7.13, and now it’s time to tighten the relations with OpenJDK even more!
Jira is no longer bundled with Oracle JDK and comes with AdoptOpenJDK JRE 8 instead. This applies only to Jira installers, as the archives don’t include any Java. If you’re an Oracle fan, Oracle JDK is still supported, so feel free to use it.
List of custom changes after upgrade
To preserve your custom changes after upgrade, you need to re-apply the changes made to your old Jira files to the same files in the upgraded version. Until 8.3 we weren't able to tell you exactly which files you'd modified. However, as of 8.3 we can. When you start your Jira after upgrade, you'll see a list of files which have been modified so that you can easily transfer the changes.
This change is a part of a bigger project to help you plan and speed up your upgrade. In the planning phase, you can already see the changed files in the Pre-upgrade planning page in the Jira administration > Applications > Plan your upgrade. This can help you estimate the time required to transfer the changes and make sure none have been lost. When you transfer the changes from the old to the new files, remember to only copy these exact changed parts not the entire files.
New filters to search for custom fields
Now, you can find a custom field even if you do not know its exact name. You can use one or a collection of the additional three multi-select filters and search through your custom fields based on
projects using custom field
custom field types
screens connected to a custom field.
Browsing projects is now faster
We've upgraded the Browse projects page to the latest version of Marionette (1.4.1), which gave it a significant performance boost.
Improvements to batching emails
Now you can configure the notification frequency at which you want users to receive the batched updates instance wide. If your users like to always stay on top of things, they can receive batched notifications every few minutes, and if you’d rather just read a summary every now and then, you can choose to receive a summary of what happened in the last hour. For details see Configuring email notifications.
Cluster lock mechanism improved in Data Center
We improved the cluster lock mechanism in Jira Data Center by introducing lock timeouts. Now, when a node loses a cluster lock it will be automatically recoverable without any actions from administrator. Previously this situation could only be resolved by restarting the node. You can read more about this issue here.
Re-indexing made better
We’ve improved the user experience around re-indexing, which will be especially visible for our Data Center users. Some of the changes include more context around the re-indexing options so you can choose more easily, confirmation modals with extra warnings to prevent you from re-indexing by mistake, and a new field that shows the node that will be used for re-indexing. You will also see your current node and the “re-indexing” node when re-indexing is in progress, just to give you more details on what’s going on in your Data Center cluster. Learn more.
Issues in Release
Fixed: Board displaying incorrect name for "Other Issues" and "Everything Else"
Fixed: Drag'n'drop zones in agile boards do not cover full column height
Fixed: Browser search function does not find issues after supplying a dash.
Fixed: Click ">" under Version Panel in Backlog page throw "Cannot read property 'doneEstimate' of undefined" error
Fixed: Error upon navigating through boards
Fixed: Kanban Board: Multiple statuses in one column do not all appear when transitioning to it.
Fixed: Clicking an issue in the Active sprints board causes an exception to be thrown while rendering the Issue Detail View
Fixed: CVE-2019-11581 - Template injection in various resources
Fixed: Users cannot be removed from the Project Roles if the user is renamed in JIRA 8.2.0
Fixed: Frequent lucene-stats in logs triggered when closing temporary index (RAMDirectory)
Fixed: Some Jira entities created when installing applications show i18n keys instead of translated values.
Suggestion: The new customfields admin page is missing fonctionnalities
Suggestion: Allow admins adjust delay for email notifications batching
Fixed: Incorrect results for custom field quick search
Suggestion: Ability to to limit the search only to custom field name in custom fields management view
Fixed: Atlassian Diagnostics bundled plugin high memory usage
Suggestion: Do not send batch notification when a user mentioned on comment is part of the ticket (Assignee, Reporter or Watcher)
Suggestion: Add filtered view for Custom Fields page
Suggestion: Add background reindex warning for large data center environment
Suggestion: Custom Fields page search feature should include type information
Fixed: Import from Cloud to Server fails: value too long for type character varying (60)
Fixed: /status url returns ERROR instead of MAINTENANCE during foreground reindexing
Suggestion: Oracle 12c Release 2
Suggestion: Discourage Background Indexing for Datacenter instances in Indexing Page
Suggestion: As a JIRA Administrator I want to be able to deploy Jira behind CDN
Fixed: JIRA DC might lose Cluster lock due database connectivity problems
Fixed: In Jira Data Center, when a node executing reindexing is abruptly stopped other nodes will continue indicating that re-indexing is in progress
Fixed: Deleting an attachment does not remove its thumbnail from the filesystem
Suggestion: JIRA API disabling users
Suggestion: Encrypt Database Password in dbconfig.xml or use integrated authentication
Source
0 notes
Link
Learn Kotlin Android App Development And Become an Android Developer. Incl. Kotlin Tutorial and Android Tutorial Videos
What you’ll learn
Learn the core Android app development and Kotlin skills to build real Android apps.
Learn how to target current and older versions of Android when writing your apps.
Understand how to create Android apps using Kotlin.
Be able to apply for Android app development roles.
Requirements
A Windows computer, a Mac, or a Linux machine so that the free Google Android Studio tool can be downloaded and install (full instructions included).
An open mind to learn something new and exciting which may make a huge difference in your future career.
Everything else needed to write apps for Android 8 Oreo with Kotlin is already included in the course.
Description
What do you get in this course?
In this course, you will discover the power of Android app development, and obtain the skills to dramatically increase your career prospects as a software developer. You’ll also have a head start over other developers using obsolete tools and earlier versions of Android.
Android is continually being updated and you’ll learn how to target but users of current versions of Android and older versions as well.
With this course, you get the best of both worlds. You’re taught to write code for Android that works with the current version and older versions of Android by using the AppCompat library. That way, the apps you build will work with more versions of Android, giving you access to a wider audience of users.
Starting is easy because no previous programming experience is needed. NONE! If you do have it, great. Or maybe you just want to brush up on your Android development skills, and that’s fantastic too.
The course is presented using a combination of video, slides and diagrams, all designed to teach you everything you need to know.
Here is what just one student thinks about the course.
“If you are thinking of learning how to develop an Android app, you should be doing this course. It is comprehensive and covers so many aspects of programming an Android app. The best part is that Tim explains and teaches you how to become an independent developer. Since completing this course, I have gone on and developed my own application, which is now published on the Google Play Store! Developing an app takes patience, and it is definitely worthwhile going through all the content in this course.” – Daniel Lee
Should you write Android apps that target only the very latest version of Android?
If you have an iPhone or iPad, chances are high that you update each year to the latest iOS release – most users do.
The situation is completely different with Android. Only a relatively small percentage of Android users update their phones annually.
If you write your apps to only support the latest version of Android, you will ensure 95% of your potential user base will never see your app. The Google app store will only show apps that a users Android device can run, so if their device is not running the latest version of Android, they won’t even be able to find your app on the Google play app store!
How do you make sure your app targets older versions of Android?
Android development is less about making sure you are creating apps that work with the latest version of Android, and more about ensuring your apps work with whatever versions of Android your users are running.
Google are aware of this problem and have something call the AppCompat library. Which is a way for you to ensure your apps work on older devices.
This is not enabled by default. Meaning that if you do not specifically configure your app to use this library and target older devices and newer ones, it either won’t show up at all for users searching for your app, or older Android devices running your app might crash because they are trying to access features that do not exist in their version of Android.
The key is to use this library. And that’s what you will learn in this course.
Does that mean that your apps can only use features from really old Android versions?
No it does not. The AppCompat library is constantly updated by Google. They go back and add features to the library which allows older Android devices to access newer features of Android.
But again, this is not turned on by default. You have to create and write your Android apps in a particular way to have your Android app be able to work correctly for current and older versions of Android.
Should you learn Kotlin?
Now that Google are pushing so hard for Android developers to use Kotlin, we are seeing a dramatic shift to Kotlin – It’s similar to the iOS situation a few years ago with Objective-C when Apple released Swift.
Fast forward a few years and everyone is using Swift. This is starting to happen with Android app development. Developers who used to use Java are switching to Kotlin. You can see why Google want this to happen. They have been in court numerous times with Oracle (the owners of Java) relating to a dispute over the use of the Java language.
Google want developers to adopt Kotlin so that they don’t have to worry about Java any more.
The recent Google I/O conference show mainly Kotlin code examples. You can see where we are heading. Kotlin is the future for Android app development.
Soon there will be few Java developers writing Android apps – they will be using Kotlin.
The good news is, we’ve bundled a complete Kotlin tutorial we wrote from scratch with the course. So not only do we use Kotlin in this course (teaching best practices along the way), but we also include a complete Kotlin tutorial as well. You will learn how to use the Kotlin language in this course.
This is what you’ll learn in the course:
· Develop apps for the very latest version of Android that also work on older Android devices running older versions of the Android operating system.
· Download, install and configure the necessary (free) software.
· Create your first app.
· Build a range of apps demonstrating key aspects of the Android framework.
· Test your apps on emulators or a real Android phone or tablet.
· You’ll learn Kotlin programming because Google are recommending and pushing adoption of Kotlin for Android app development. Included are Kotlin tutorial videos that will get you up to speed fast.
· Ensure your apps work with current and older Android versions on phones and tablets.
· Use Android studio 3.2, the newest version of Google’s premier Android tool.
· Learn how to use databases, web services, and even get your apps to speak!
· Understand the all new Constraint layout, for “drag and drop” screen creation.
· Use powerful libraries of code to play videos, download website data, manipulate images, and a whole lot more!
To reinforce what you’ve learnt during the course, there are numerous challenges designed to help you understand each concept being taught. You’re also shown the solution to the challenge so you know you’re always on the right track.
The course is continually updated and enhanced, and fully supported as it evolves.
With many courses, it’s just set and forget. But not with this one! We’ve got a PROVEN track record of continually updating and adding new content. An example is Tim’s Java Masterclass course which now has 77 hours of content and counting, and benefited a whopping 260,000 students.
And if you have any doubts about the course, be blown away by the glowing reviews left by students on this page.
What else will you learn?
You will learn how Android works at a deep level. Many courses show you how to create Android apps, allowing you to follow along clicking buttons but not really understanding what it happening.
To become a successful Android app developer, you need to understand why you are clicking that button, and how the Android operating system works and how the Android SDK and Framework works.
If you truly understand how something works, it means you can produce better quality apps, that have fewer bugs.
We don’t promise that you are going to write a Facebook or Instagram clone app in this course – Courses that say they are going to teach you to create apps like that show apps with only the smallest amount of functionality, and usually don’t explain anything in detail. There is no point going through Android training unless you can take that training and apply it into your own apps.
This course is designed for you to follow along, but then to apply the information you have learned into your own apps.
Your instructors are me, Tim Buchalka and Jean-Paul Roberts. Between them theyhave a collective 70 years of commercial software development experience, meaning you’re learning the right way to program to maximize your future development potential.
Here’s what’s important. There’re a lot of people teaching Android development who are not developers. We’re developers with many years’ experience with the Android platform, who also teach Android.
Importantly, our courses teach students the real-life skills needed to get those in-demand jobs or further your programming skills.
Take this course in confidence today knowing you have just found the BEST Android Kotlin course on Udemy! Don’t delay. Every minute you’re not learning Android is a missed opportunity for that PERFECT high paying job.
Click the BUY NOW button and start learning. The world needs your new apps!
Who this course is for:
This course is perfect for absolute beginners with no previous programming experience.
However, if you’re already an expert Android Kotlin programmer with knowledge of all the latest updates, then this course is not for you.
Existing Android Java Programmers who want to transition to Kotlin for Android app development.
Created by Tim Buchalka, Jean-Paul Roberts, Tim Buchalka’s Learn Programming Academy Last updated 3/2019 English English
Size: 15.06 GB
Download Now
https://ift.tt/2Bn1KvA.
The post Android App Development Masterclass using Kotlin appeared first on Free Course Lab.
0 notes
Text
10 Reasons to Learn Java Programming Language and Why Java is Best
1) Java is Easy to learn
Many would be surprised to see this one of the top reason for learning Java or considering it as the best programming language, but it is. If you have a steep learning curve, it would be difficult to get productive in a short span of time, which is the case with most of the professional project.
Java has fluent English like syntax with minimum magic characters e.g. Generics angle brackets, which makes it easy to read Java program and learn quickly.
Once a programmer is familiar with initial hurdles with installing JDK and setting up PATH and understand How Classpath works, it's pretty easy to write a program in Java.
2) Java is an Object Oriented Programming Language
Another reason, which made Java popular is that it's an Object Oriented Programming language. Developing OOP application is much easier, and it also helps to keep system modular, flexible and extensible.
Once you have knowledge of key OOP concepts like Abstraction, Encapsulation, Polymorphism, and Inheritance, you can use all those with Java. Java itself embodies many best practices and design pattern in its library.
Java is one of the few close to 100% OOP programming language. Java also promotes the use of SOLID and Object-oriented design principles in the form of open source projects like Spring, which make sure your object dependency is managed well by using Dependency Injection principle.
3) Java has Rich API
One more reason for Java programming language's huge success is it's Rich API and most importantly it's highly visible because come with Java installation.
When I first started Java programming, I used to code Applets and those days Applets provides great animation capability, which amazes new programmer like us, who are used to code in Turbo C++ editor.
Java provides API for I/O, networking, utilities, XML parsing, database connection, and almost everything. Whatever left is covered by open source libraries like Apache Commons, Google Guava, Jackson, Gson, Apache POI, and others.
You can further see my post 20 essential open source libraries for Java programmers to learn more about useful libraries Java developers should know.
4) Powerful development tools e.g. Eclipse, Netbeans
Believe it or not, Eclipse and Netbeans have played a huge role to make Java one of the best programming languages. Coding in IDE is a pleasure, especially if you have coded in DOS Editor or Notepad.
They not only help in code completion but also provides a powerful debugging capability, which is essential for real-world development. Integrated Development Environment (IDE) made Java development much easier, faster and fluent. It's easy to search, refactor and read code using IDEs.
Apart from IDE, Java platform also has several other tools like Maven and ANT for building Java applications, Jenkins for Continuous Integration and delivery, decompilers, JConsole, Visual VM for monitoring Heap usage, etc.
You can also see my post 10 Essential Tools for Java Programmers to learn more about tools Java programmers use in the day-to-day life.
5) Great collection of Open Source libraries
Open source libraries ensure that Java should be used everywhere. Apache, Google, and other organization have contributed a lot of great libraries, which makes Java development easy, faster and cost-effective.
There are frameworks like Spring, Struts, Maven, which ensures that Java development follows best practices of software craftsmanship, promotes the use of design patterns and assisted Java developers to get there job done.
I always recommend searching for functionality in Google, before writing your own code. There is a good chance that it's already coded, tested and available for ready to use.
You can also see Top 20 Libraries and API for Java Programmers for my recommended libraries for Java developers.
6) Wonderful Community Support
A strong and thriving community is the biggest strength of Java programming language and platform. No matter, How good a language is, it wouldn't survive, if there is no community to support, help and share their knowledge.
Java has been very lucky, it has lots of active forums, StackOverflow, open source organizations and several Java user groups to help everything.
There is the community to help beginners, advanced and even expert Java programmers. Java actually promotes taking and giving back to community habit. Lots of programmers, who use open source, contribute as a commiter, tester, etc.
Many Expert programmers provide advice FREE at various Java forums and StackOverflow. This is simply amazing and gives a lot of confidence to a newbie in Java.
7) Java is FREE
People like FREE things, Don't you? So if a programmer wants to learn a programming language or an organization wants to use technology, COST is an important factor. Since Java is free from the start, i.e. you don't need to pay anything to create Java application.
This FREE thing also helped Java to become popular among individual programmers, and among large organizations. If you are curious where exactly Java is used in the real world, see that post. I have talked about Java's adoption by all around the world.
Availability of Java programmers is another big thing, which makes an organization to choose Java for there strategic development.
8) Excellent documentation support - Javadocs
When I first saw Javadoc, I was amazed. It's a great piece of documentation, which tells a lot of things about Java API. I think without Javadoc documentation, Java wouldn't be as popular, and it's one of the main reason, Why I think Java is the best programming language.
Not everyone has time and intention to look at the code to learn what a method does or how to use a class. Javadoc made learning easy, and provide an excellent reference while coding in Java.
With the advent of IDEs like Eclipse and IntelliJIDEA, you don't even need to look Javadoc explicitly in the browser, but you can get all the information in your IDE window itself.
9) Java is Platform Independent
In the 1990s, this was the main reason for Java's popularity. The idea of platform independence is great, and Java's tagline "write once run anywhere" and acronym "WORA" was enticing enough to attract lots of new development in Java.
This is still one of the reason for Java being the best programming language, most of Java applications are developed in Windows environment and run on Linux platform.
10) Java is Everywhere
Yes, Java is everywhere, it's on the desktop, it's on mobile, it's on the card, almost everywhere and so is Java programmers. I think Java programmer outnumber any other programming language professional.
Though I don't have any data to back this up, it's based on experience. This huge availability of Java programmers is another reason, why organizations prefer to choose Java for new development than any other programming language.
Having said that, programming is a very big field and if you look at C and UNIX, which is still surviving and even stronger enough to live another 20 years, Java also falls in the same league.
Though there are a lot of talks about functional programming, Scala, and other JVM languages like Kotlin and Groovy, they need to go a long way to match the community, resources, and popularity of Java.
Also, OOP is one of the best programming paradigms, and as long as it will be there Java will remain solid.
Now, if you decide to learn Java programming, here are the couple of resources, which you can take a look. I personally suggest joining an online course to start with and then picking a book, because they are almost always well written by authorities in the subject matter and catered for beginners.
To start with, I recommend joining The Complete Java Master Class at Udemy. You can buy this course on just under $10 on Udemy's flash sale which they run I think every month.
This course is very comprehensive and up-to-date and covers both Java SE 8 and Java SE 9. The course is also structured in a systematic way to provide beginners with all the knowledge and tools before they can understand complex concepts like multi-threading and concurrency.
It covers all essential Java 8 features described above in bootcamp style like a lot of focus on hands-on work.
If you can afford, then this is the best course to learn Java online. To be honest, it's dirt cheap, even one day Java class cost around $100 in developing countries, forget about development country. You can't get a comprehensive Java course cheaper than this.
When it comes to books, I personally recommend Head First Java to all beginners, as I have learned a lot from it myself. It's a great book to start if you don't know anything about Java, but unfortunately, it's not up-to-date.
Once you have gone through this book, you can pick any good Java books to learn key Java 8 features like lambda expression, method reference, Stream API, new Date, and Time API, default methods, etc.
The content is still valid and Java Fundamentals has not changed but I strongly suggest every programmer start with the latest Java version like. Java 8 or Java 9 and on that parameter Modern Java in Action is currently the best book to learn Java.
This book covers each topic in good depth. I even encourage to read all three books by this author on Java 8 to learn Java 8 in depth.
You can also take a look at official Java tutorials offered by Oracle. These tutorials are both comprehensive, up-to-date, and covered almost all important details of Java programming language. Further, you can use Google along with your learning.
If you need to understand a particular concept, term or any issue with Java, Google can point you to a specific resource. There are lots of blogs, tutorial sites, and free video tutorials on the internet to learn Java programming.[Source]-https://javarevisited.blogspot.com/2018/07/10-reasons-to-learn-java-programming.html
We provide best Java Classes in Thane, navi mumbai. We have industry experienced trainers and provide hands on practice. Basic to advanced modules are covered in training sessions.
0 notes
Text
EVERY FOUNDER SHOULD KNOW ABOUT LESSON
If that was what character and integrity because they had been so debased by adults. If you try to convert that interest into money. A company that needed to build a factory or hire 50 people obviously needed to raise a large round and risk losing the investors you already have enough funding, that reduces to: close them now. The way to handle rejection is with precision.1 That has been the lesson for me: be careful what you let become critical to you.2 Kids in pre-industrial times started working at about 14 at the latest; kids on farms, where most people lived, began far earlier.3 So if you're running a big company, you can do what all the other big companies are bad at product development because they're bad at everything. School is a strange, artificial thing, half sterile and half feral. If they get something wrong, it's usually not realizing they have to make decisions about things they don't understand—tends to make investors very skittish.4 But Lisp is a powerful language, but worry because it isn't widely used.
This is just an explanation of why I don't like the look of Java: It has been so energetically hyped. Linus Torvalds, or Alan Kay, or someone would already be doing it and it wouldn't be novel. In fact their primary purpose is to keep kids locked up in one place. It might mean something. During the 1992 election, the Clinton campaign staff had a big sign in their office saying It's the economy, stupid. We charged quite a lot for our software—about $140 per user per month—but it was at least a year before our revenues would have covered even our paltry costs. One answer to that is obvious: because you need money to live on.5 It wasn't worth doing better. It shows you've thought about making money, instead of just working on amusing technical problems; it shows you have the discipline to keep your expenses low; but above all, it could save you to be able to see that they're the sort of thing that happens by default. Want to get hired by Yahoo? The earliest phase is usually the most productive people are attracted to employers who hold themselves to a higher standard than the law requires.
At best it was practice for real work we might do far in the future the executives installed by VCs will increasingly be able to get big-name users using your software that you wouldn't have seen on the list 100 years ago though it might have sent the message Cambridge does now. As a thirteen-year-old kids are intrinsically messed up. Mostly we had the same sort of insight Socrates claimed: we at least knew we knew nothing.6 Both the Internet startups and the Procter & Gambles were doing brand advertising. For Trevor, that's par for the course.7 Which companies are in the software business, you can't afford not to have much power in big companies unless they happen to be used to, they tend to consider just good enough. The text of each chapter was just some advice about solving them. In 1995 it was hard to imagine a technology company. I've read a lot of mean people out there, there are few in which it varies so much.8 It's in fields like the arts or writing or technology that the larger environment matters.9 It's in these more chaotic fields that it helps most to be in a place where you can actually get work done. The cause of this problem is the same as the cause of the problem.
If Jessica was so important to YC, why don't more do it? How much are you trying to raise?10 It's like Google's Don't be evil.11 Sure, it can be to decide what you should invest in depends on how well they do are not orthogonal. It has ulterior motives. In the long term, but it can be interesting to eavesdrop on people, but diluted by a much larger number of neanderthals in suits. As used by adults, it seemed to mean the same thing, but I was friends with a lot of technological leverage.
The reason is that they feel they don't have enough experience. At least until an invading Roman army killed him. The problem is not the actual time it takes to meet with investors. The VCs will have to be working for an existing company for a couple years before starting your own company.12 Investors were excited about the Internet.13 Revenue Loop was the optimal sort for shopping search, in the sense that it sorted in order of how much money Yahoo would make from each link. In fact, it's just as well to go work for a company may feel like just the next in a series of institutions, but underneath, everything is different. Good programmers want to work on what you like. That becomes what you think about it, but I realize now that was because I'd always implicitly understood it to mean ambition in the areas I cared about.
Notes
A fundraising is so new that it's fine to start a startup with a face-saving compromise. At the time and became the twin centers from which Renaissance civilization radiated. You could also degenerate from words to their kids won't listen to God.
All you need to do as some European countries have done well if they'd been living in a company if the value of a Linux box, a player who persists in trying such things will do that, go talk to corp dev guys should be asking will you build this? You leave it to colleagues. Then Josh Wilson came in to pick the words won't be able to formalize a small seed investment in you, they wouldn't have understood users a lot cheaper than business school, approach the queen bees thereof and offer to invest but tried to motivate people by saying Real artists ship. Associates at VC firms were the seven liberal arts colleges are doomed.
I have no representation more concise than a huge, analog brain state. That makes some rich people move, and others, like angel investors in startups. It was revoltingly familiar to slip back into it.
But it's a bad idea. Heirs will be weak: things Steve Jobs tried to unload it on buyer after buyer. It's suspiciously neat.
I worry we may be because the early years. According to Sports Illustrated, the task at hand almost does this for you to believing anything in particular made for other kinds of startups is very vulnerable to legal attack. If you're a YC startup and you might be a niche within a few unPC ideas, because they can't legitimately ask you to test whether that initial impression holds up.
One source of the techniques for discouraging stupid comments instead.
It's a bit. It doesn't happen often. But wide-area bandwidth increased more than you otherwise would have started to give it additional funding at a Demo Day by encouraging them to ignore what your project does.
Design ability is so we should remember this when he was a bimodal economy consisting, in one where life was tougher, the switch in the cupboard, but that it's hard to answer, and when given the freedom to they derive the same reason I even mention the possibility. By all means crack down on these. Looking at the network level, because they will only be a sufficient condition.
Not startup ideas is many times have you heard a retailer claim that companies will one day be able to invest more. Credit card debt is usually a stupid move, but to a VC fund they outsource most of the things startups fix. Not all were necessarily supplied by the same amount of stock options than any design decision, but this disappointment is mostly the ordinary variety that anyone feels when that partner re-tells it to steal the company. 99,—9.
This is why it's such a valuable technique that any given time I had a house built a couple hundred years or so and we don't use Oracle.
But should you even be worth it, but it's also a good plan in 2001, but mediocre programmers is the least important of the most abstract ideas, because his ideas were one of the device that will be pressuring you to agree. Yahoo.
Mitch Kapor, is a self fulfilling prophecy. Especially if they knew their friends were.
Galbraith p. It seems quite likely that European governments of the corpora. And starting an outdoor portal. We fixed both problems immediately.
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#house#Illustrated#bit#buyer#VCs#corpora#retailer#advertising#suits#freedom#disappointment#amount#number#things#means#economy#sup#bees#VC#executives#lot#insight#cause#Renaissance#answer
0 notes
Link
Ruby is an open-source object-oriented programming language created by Yukihiro Matsumoto. The first linguistic version (0.95) was published in 1995, and version 1.9.3 was published in 2011. Ruby is gaining popularity, and a framework called Ruby on Rails has helped to boost its use for web programming. The Ruby language is totally object-oriented in that everything is an object. For example, even the most basic types of information like integers have techniques and variables of example. This gives a higher capacity to use method chaining, where many lines of code can be consolidated into one. Ruby is also recognized as a flexible language because, if required, it enables programmers to make changes to different components of the language. You can find more data on Ruby programming using the resources below.
History of Ruby
Ruby was developed in the mid-1990s by Yukihiro Matsumoto, and "Matz," in Japan. It was intended for the productivity of programmers with the concept that programming should be enjoyable for programmers. It emphasizes the need for software to be grasped first by humans and second by machines.
Ruby continues to gain popularity in the development of web applications for its use. The Ruby on Rails system, constructed by David Heinemeier Hansson with the Ruby language, introduced many individuals to the joys of programming in Ruby.
Ruby has a vibrant community that supports beginners and is passionate about generating high-quality code.
Features of Ruby
Ruby has many key features that described below:
1. Object-Oriented
Every value in Ruby is an object, even the most primitive stuff, like chains, numbers and even true and false. So, Ruby is a pure object-oriented language.
2. Dynamic
The Ruby programming language is very dynamic. Like C or Java programs, ruby programs are not compiled. When a program is executed, all things are constructed by the code. Also during operation, a program can change its definitions.
3. Flexibility
Methods can be added to current classes without subclassification, operators can be overloaded, and even standard library behavior can be defined at runtime.
4. Singleton Classes
Every Ruby item has two classes: a periodic class and a singleton class.
The singleton class of an object is a nameless class whose only instances are that object. Singleton classes are created automatically, making Ruby simple and elegant.
5. Metaprogramming
In Ruby, everything is objects. You can use them to know about or even alter them while your program is running. Metaprogramming is called this technique.
6. Variables and scopes
The programmer does not need to declare variables or variable range in ruby. The variable name automatically determines its scope.
Examples :
var is a local variable.
$var is a global variable.
@var is an instance variable.
@@var is a class variable.
Advanced Features of Ruby
Exceptions for error handling.
Collector of garbage.
OS-autonomous threading enabling you to write multi-threaded apps even on operating systems such as DOS.
You can write extensions in C for Ruby.
Ruby is a scripting language on the server-side.
Ruby can be integrated into HTML.
Ruby has a comparable syntax to many programming languages such as C and Java.
Ruby mainly supports all platforms such as Windows, Mac, and Linux.
Ruby can readily be linked to Oracle, MySQL, DB2.
Hello World in Ruby
# Hello World Program in Ruby puts "Hello World!";
Output:
Hello World!
Run Ruby Online
Tutorialspoint.com
Repl.it
Jdoodle.com
Onlinegdb.com
Runrb.io
Run Ruby on PC
First download ruby from ruby-lang.org. Then download and install this software to create and edit Ruby programming.
Notepad++
Jetbrains
Aptana
Recommended Books for Ruby
I think this book should help you to learn about the Ruby programming language. If you want to learn deeply about Ruby programming, you can buy these books from here.
Uses of Ruby Programming Language
Ruby is the most popular use is web applications. His main appeals are that programmers don't have to spend a lot of time setting up their files. Share your thoughts about the Ruby programming language in the comment box.
0 notes
Text
Straightforward and simple approaches to keep your PC protected and secure on the Internet
Presentation
Let's be honest, the Internet is anything but an exceptionally protected spot. There are programmers endeavoring to get to your PC, worms attempting to taint you,pernicious Trojans camouflaged as supportive projects, and spyware that reports your exercises back to their producers. Much of the time the individuals who wind up tainted accidentally turn into a reproducing ground for undesirable projects and criminal action. google flights It doesn't need to be like this. With appropriate training and savvy figuring the Internet can be a protected, valuable, and fun spot to visit without stressing over what is hiding around the bend.
This instructional exercise was made to give tips and procedures to savvy and safe registering. When utilizing these methods you won't just secure yourself and your information from programmers and infections, yet in addition keep your PC running all the more easily and dependably. The exhortation in this instructional exercise applies to all PC clients and all working frameworks, yet we have attempted to call attention to explicit strides for different working frameworks as it ends up important.
WHAT YOU NEED TO KNOW TO KEEP YOUR COMPUTER SAFE ON THE INTERNET
Tip 1: Always introduce Operating System refreshes
The most critical strides for any PC client is to dependably introduce refreshes, particularly security refreshes, when they end up accessible for your working framework. At the point when working frameworks are produced, bugs, or programming mistakes, are shockingly made that could cause security vulnerabilities or make your PC demonstration surprisingly. In spite of the fact that the engineers spend numerous hours endeavoring to keep these bugs, they are at last human, and bugs happen. It doesn't make a difference what working framework we are discussing, bugs are constantly presented. Because of this, organizations will routinely discharge updates and fixes to fix any security vulnerabilities or blunders as they are found.
All together for your PC to work easily and securely it is basic that all clients introduce refreshes, particularly security refreshes, as they are discharged. By not introducing these updates you leave your PC in danger from remote clients hacking into them or infections abusing these bugs to access your PC.
Fortunately, all cutting edge working framework give simple strategies to putting in new updates. Indeed, the greater part of these techniques do basically everything for you and simply expect you to click a brief to enable the updates to introduce. Thusly, there truly is no reason not to introduce them.
The following are two instructional exercises that can be utilized to figure out how to refresh your working framework in Windows and MacOS:
For Macs: How to introduce Software Updates on your Mac
For Windows: How to refresh Windows
Tip 2: Keep your introduced applications modern
A typical technique that PC contaminations use to taint your PC are security vulnerabilities in your introduced projects. Normal projects that are focused due to their substantial introduce base are internet browsers, Microsoft Office, Adobe Reader, Adobe Flash, Adobe Shockwave, and Oracle Java. So as to make your PC as secure as conceivable, you have to ensure these projects are refreshed when new security fixes are discharged. The issue is that numerous individuals simply overlook cautions about new updates, despite the fact that these updates fix security issues that could permit programmers into your PC.
In the event that you are incited by a known application that you normally use expressing that there is another refresh, simply click the catch to enable it to be refreshed. This is particularly valid for internet browsers, which are generally focused by noxious code on sites. On the off chance that there is another adaptation of your internet browser accessible, you ought to overhaul it with the goal that any security vulnerabilities are settled.
On the off chance that you use Windows, there is an incredible program called Secunia PSI that naturally examines your PC for applications and consequently refreshes them for you.
Data about this program can be found at this instructional exercise:Instructions to distinguish helpless and out-dated projects utilizing Secunia Personal Software Inspector (PSI)
Tip 3: Do not utilize a similar secret key at each site
It has now turned out to be basic to find out about an organization who was hacked and the programmer could get to the organization individuals email locations and passwords. On the off chance that you utilize the same secret key at each site, and one of those destinations was hacked, the programmer currently has your record data wherever that you have a record. They can now login to your email, see what different records you have, banks that you use, and so forth and accumulate much increasingly private data about you.
It is critical to utilize an alternate secret key at each site where you have a record. Lamentably, we as a whole realize it's not practical and even conceivable to recall a diverse secret phrase for each record you may possess. To help with that you can utilize a secret phrase the board program like Keepass to enable you to store your record data for each site you login to. Keepass likewise contains modules that enable you to consequently login to locales you visit utilizing the data put away in its database.
In the event that you would preferably not store your passwords in another program, at that point making a standard secret word group is superior to utilizing a similar secret phrase at each site. For model, for each site you visit you can make a secret key in the organization [year born][sitename]!55. So on the off chance that you were enrolling a record at Bleeping computer and you were conceived in 1975, you could utilize the secret word 1975 bleeping computer!55. At that point at CNN you could have a record 1975cnn!55. As should be obvious you are currently utilizing an alternate also, solid secret word at each site, yet you have a simple to recall position that you can use to decide the secret phrase.
Tip 4: Install and make sure to refresh your enemy of infection programming
It is essential that your PC has antivirus programming running on your machine. By having an antivirus program running, records and messages will be checked as you
use them, download them, or open them. On the off chance that an infection is found in one of the things you are going to utilize, the antivirus program will prevent
you from having the capacity to run that
program and contaminate yourself.
Is it additionally imperative to take note of that there is no reason for running an antivirus program in the event that you don't ensure it has all the most recent updates accessible to it. On the off chance that you do not refresh the product, it won't think about any new infections, trojans, worms, and so forth that have been discharged into the wild since you introduced the program. In the event that another contamination shows up in your PC, the obsolete antivirus program won't realize that it is terrible, and not alarm you when you run it and your PC winds up tainted.
It is basic that you refresh your Antivirus programming in any event once every week (Even more on the off chance that you wish) so you are shielded from all the most recent dangers.
It is likewise proposed that you introduce a free enemy of malware scanner notwithstanding your ordinary enemy of infection program. These free enemy of malware scanners don't offer genuine time security except if you move up to the business variant, however offer fantastic location when filtering with them intermittently. Two suggested Windows hostile to malware programs are MalwareBytes Anti-Malware and Emsisoft Anti-Malware. Instructional exercises on the best way to utilize these projects are recorded beneath:
Instructions to utilize Emsisoft Anti-Malware to output and clean malware from your PC Step by step instructions to utilize Malwarebytes Anti-Malware to output and expel malware from your PC.
The accompanying connection has a rundown of some on the web and remain solitary antivirus programs: Virus, Spyware, and Malware Protection and Removal Resources
Tip 5: Use a firewall
The significance of utilizing a Firewall on your PC or on your system can't be focused on enough. Because you have all the most recent security refreshes, you are still powerless to unreported, unpatched, or obscure vulnerabilities that a programmer may think about. Now and again programmers find new security openings in a product or working framework some time before the product organization does and numerous individuals get hacked before a security fix is discharged. By utilizing a firewall most of these security gaps won't be available as the firewall will hinder the endeavor.
For an instructional exercise on Firewall's and a posting of some accessible ones, if you don't mind visit the accompanying connection: Understanding and Using Firewalls
0 notes
Text
Perl Version 5.28.0 Now Available, Linus Torvalds' "Small Rant" on rc2 Release Statement, Ubuntu's First User Data Report and More
News briefs for June 25, 2018.
Perl version 5.28.0 has been released. According to LWN.net, highlights of this release, which was 13 months in the making with approximately 730,000 lines of changes, include "Unicode 10.0 support, string- and number-specific bitwise operators, a change to more secure hash functions, and safer in-place editing." See the full list of changes here.
Linus Torvalds took issue with kernel developers this weekend regarding "fixes" in his rc2 release statement: "So please, people, the 'fixes' during the rc series really should be things that are _regressions_. If it used to work, and it no longer does, then fixing that is a good and proper fix. Or if something oopses or has a security implication, then the fix for that is a real fix." He went on to say, "But if it's something that has never worked, even if it 'fixes' some behavior, then it's new development, and that should come in during the merge window. Just because you think it's a 'fix' doesn't mean that it really is one, at least in the 'during the rc series' sense." Other than that, regarding the rc2 release, he said "Things look fairly sane, it's not really all that scary."
Systemdv239 was released last week. LWN reports that "A new system.conf setting NoNewPrivileges= is now available which may be used to turn off acquisition of new privileges system-wide (i.e. set Linux' PR_SET_NO_NEW_PRIVS for PID 1 itself, and thus also for all its children). Note that turning this option on means setuid binaries and file system capabilities lose their special powers. While turning on this option is a big step towards a more secure system, doing so is likely to break numerous pre-existing UNIX tools, in particular su and sudo."
Ubuntu started collecting user data with version 18.04 (users can opt out during the install), and the first report is now available. According to the report, 67% of users opt in, installation takes 18 minutes, most people are installing from scratch instead of upgrading and having a single CPU is most common. In addition, the report reveals that although the US has the highest concentration of users, Brazil, India, China and Russia also are big Ubuntu users.
Oracle has started charging for Java SE and support. According to The Register, the cost for the "Java subscription" is "$25 per processor per month, and $2.50 per user per month on the desktop, or less if you buy lots for a long time." The article notes that "If you like your current Java licences, Oracle will let you keep them." But also that "come January 2019 Java SE 8 on the desktop won't be updated any more...unless you buy a sub."
News
Perl
kernel
Linus Torvalds
systemd
Ubuntu
Oracle
Java
https://ift.tt/2K6MVVy via @johanlouwers . follow me also on twitter
0 notes