#note: these are unverified and there are no dates attached
Explore tagged Tumblr posts
Text
i was half-seriously looking into jobs at tumblr, because i need to see how this jalopy operates. i looked at engineer salaries on glassdoor and. h-hello? he-fucking-llo?????????!!!?!?
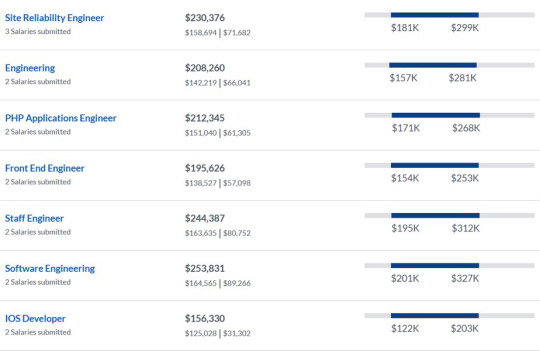

[^ screenshots from the linked page, showing some of tumblr’s engineer salaries. the average total pay ranges from $106k to $350k, and the total ranges go from $122k to $443k.]
#note: these are unverified and there are no dates attached#and the total pay includes bonuses and stock.#but still.#that’s so much.#if this is a joke‚ it’s a joke with a lot of effort and no payoff.#the job situation at tumblr is also…. strange.#you have to apply to automattic‚ not tumblr itself.#which i guess means there isn’t a guarantee the applicant will be eorking for one specific website.#when you get hired‚ you have to do customer support for wordpress for two weeks. and then for a week every year after that.#(automattic’s engineer salaries are in the 100-200k range. which is a lot but not THAT ridiculous.)#txt
2 notes
·
View notes
Text
Guide to Remittance Advice Meaning for Invoicing
In the world of business finance, particularly for small businesses and self-employed entrepreneurs, clear documentation is essential. One of the most commonly used but often misunderstood documents is the remittance advice. Whether you are making payments or receiving them, understanding the remittance advice meaning can streamline your accounting process, reduce confusion, and build trust between businesses.
In this blog, we will break down the definition, purpose, types, and best practices surrounding remittance advice, and show how Otto AI simplifies its handling for small businesses.
What Is the Meaning of Remittance Advice?
Remittance advice is a document sent by a customer to a supplier to inform them that their invoice has been paid. In simple terms, it acts as a notification of payment, similar to a receipt but used in business-to-business (B2B) transactions.
The remittance advice meaning revolves around the idea of maintaining transparency in payment communication. It helps the vendor match the incoming payment with the outstanding invoice and avoid any confusion or delays in updating financial records.
While not a mandatory document, remittance advice plays a vital role in maintaining accurate bookkeeping, especially for small business owners who rely on timely and clear records to manage cash flow.
Why Does Remittance Advice Matter for Small Businesses?
For small businesses and self-employed entrepreneurs, cash flow management is critical. Missed payments, misallocated funds, or unverified transactions can create accounting errors that may impact financial reporting or tax calculations.
Understanding the remittance advice meaning and using it correctly can help in the following ways:
Quick Payment Reconciliation: It allows the seller to quickly match the payment to the correct invoice.
Clear Communication: Avoids unnecessary follow-ups or confusion over what the payment was for.
Professionalism: Demonstrates to clients and vendors that your business follows organized financial practices.
Improved Bookkeeping: Accurate records reduce the risk of errors and improve the efficiency of year-end financial statements.
By integrating this simple tool, businesses can save time and reduce the friction commonly experienced during invoicing and payment tracking.
Key Components of a Remittance Advice
Now that you understand the remittance advice meaning, it’s essential to know what information it typically includes. A standard remittance advice document will often contain:
Payer’s Name and Address
Payee’s Name and Business Details
Payment Date
Invoice Number(s) Being Paid
Payment Amount
Method of Payment (e.g., bank transfer, check)
Any Deductions or Adjustments Made
Reference Number for the Payment
Depending on the nature of the transaction, some fields may be optional, but the more detail included, the easier it is for both parties to reconcile records.
Types of Remittance Advice
Understanding the different types can also help reinforce the remittance advice meaning in daily practice. There are three common formats:
1. Basic Paper Remittance Advice
A simple printed note sent with a check or as a separate letter. Many small businesses still use this format, especially for offline payments.
2. Email Remittance Advice
As digital communication grows, businesses often send remittance advice via email—sometimes in the body of the email or as a PDF attachment.
3. Electronic Data Interchange (EDI)
Larger businesses or those using accounting software may generate EDI remittance advice automatically. This format can be instantly processed by accounting platforms.
While each format serves the same function, choosing the right one depends on your business tools and communication preferences.
Best Practices for Managing Remittance Advice
To make the most of remittance advice in your business, follow these practical tips:
• Send Promptly
Always send remittance advice immediately after making a payment to help the supplier update their records without delay.
• Keep Digital Records
Whether sent or received, retain a digital copy. This adds a layer of protection during audits or payment disputes.
• Use Consistent Formats
Standardize the format of your remittance advice for better recognition and processing, particularly when working with repeat vendors.
• Link with Invoicing Software
If you use invoicing tools like those from Otto AI, ensure they offer features to send or track remittance advice, automating and streamlining your workflow.
How Otto AI Helps with Remittance Advice
For small business owners who manage their own finances or operate without a dedicated accounting team, the paperwork can quickly pile up. That’s where Otto AI comes in.
With Otto AI’s invoicing and payment tracking features, small businesses can:
Generate remittance advice automatically after payments are processed.
Match incoming remittance details with invoices for instant reconciliation.
Keep all documents organized in one centralized system, reducing manual data entry and risk of errors.
Track communication history with vendors for better clarity and transparency.
Otto AI understands the unique challenges of bookkeeping for small businesses. Instead of using outdated spreadsheets or juggling email threads, business owners can rely on intuitive features that simplify how they handle the full invoicing and remittance process.
Final Thoughts
Understanding the remittance advice meaning may seem like a small detail in the larger world of financial management, but it can have a major impact. For small businesses and self-employed entrepreneurs, every document, transaction, and piece of communication counts.
Remittance advice is more than just a formality. It’s a professional tool for confirming payments, clarifying transactions, and improving overall financial hygiene. With the right tools, like Otto AI, incorporating remittance advice into your process becomes second nature—leaving you more time to focus on what really matters: growing your business.
0 notes
Text
The Do's and Don'ts of Contacting a Hacker

In today's digital age, where cybersecurity threats are prevalent, it's essential to understand the do's and don'ts of contacting a hacker. While the word "hacker" often carries a negative connotation, it's important to note that there are ethical hackers who play a crucial role in identifying vulnerabilities and strengthening cybersecurity measures. This article will explore the do's and don'ts of contacting a hacker, providing valuable insights into cyber security practices and steps to take when dealing with a hacking incident.
What are the Do's and Don'ts of Cyber Security?
Understanding Cyber Security
Before diving into the do's and don'ts, it's vital to have a clear understanding of cyber security. Cyber security involves protecting computer systems, networks, and data from unauthorized access, damage, or theft. It encompasses various measures, including preventive, detective, and responsive actions, to ensure the confidentiality, integrity, and availability of information.
The Do's for Cyber Security
Stay Informed: Stay updated with the latest trends, techniques, and threats in the cyber security landscape. Regularly educate yourself on best practices to enhance your online security.
Use Strong and Unique Passwords: Create strong and unique passwords for all your accounts. Avoid using easily guessable passwords like birthdates or common words.
Enable Two-Factor Authentication: Enable two-factor authentication (2FA) whenever possible. This adds an extra layer of security by requiring a secondary verification step, such as a code sent to your mobile device.
Regularly Update Software: Keep your operating system, applications, and antivirus software up to date. Updates often include security patches that address known vulnerabilities.
Exercise Caution with Email: Be cautious while opening email attachments or clicking on links, especially if they are unsolicited or from unknown sources. Phishing emails are a common method used by hackers to gain unauthorized access.
Use a Firewall: Enable a firewall on your devices to monitor and control incoming and outgoing network traffic. Firewalls act as a barrier between your device and potential threats.
Backup Your Data: Regularly backup your important files and data. In case of a security breach or ransomware attack, having backups ensures that you can restore your data without paying the attackers.
Secure Your Wi-Fi Network: Protect your home Wi-Fi network with a strong password and encryption. This prevents unauthorized individuals from accessing your network and intercepting your data.
Be Cautious on Social Media: Be mindful of the information you share on social media platforms. Avoid disclosing sensitive personal details that could be used against you by malicious actors.
Implement Security Awareness Training: Educate yourself and your employees about cyber security best practices. Awareness training helps in creating a security-conscious culture and reduces the risk of falling victim to cyber attacks.
The Don'ts for Cyber Safety
Don't Share Personal Information: Avoid sharing personal information, such as your social security number, bank account details, or passwords, with anyone unless necessary and from trusted sources.
Don't Use Public Wi-Fi for Sensitive Activities: Avoid accessing sensitive accounts, such as online banking or email, while connected to public Wi-Fi networks. Public Wi-Fi networks are often unsecured and can be easily compromised by hackers.
Don't Fall for Phishing Scams: Be vigilant and avoid clicking on suspicious links or providing personal information in response to unsolicited emails or messages. Phishing scams are designed to trick users into revealing sensitive information.
Don't Install Unauthorized Software: Only install software from trusted sources. Downloading and installing software from unverified or unofficial websites may introduce malware or spyware into your system.
Don't Ignore Security Updates: Never ignore software updates or postpone them indefinitely. Updates often contain critical security patches that address vulnerabilities identified by software developers.
Who Should You Contact if You Get Hacked?
If you suspect that you have been hacked or experienced a security breach, it's essential to take immediate action. Here are the steps you should follow:
Disconnect from the Internet: If you suspect a hacking incident, disconnect your device from the internet to prevent further unauthorized access or data theft.
Document the Incident: Take screenshots and document any unusual activities or error messages related to the hacking incident. These pieces of evidence can be helpful in investigating the breach.
Contact the Appropriate Authorities: Depending on the severity of the incident, contact your local law enforcement agency or report the incident to your country's cyber crime division.
Notify Relevant Parties: If the hacking incident involves compromised personal information or sensitive data, inform the affected individuals or organizations. Prompt notification allows them to take appropriate measures to protect themselves.
Engage with a Professional Hacker (Ethical Hacker): In certain cases, you may want to engage with an ethical hacker to assess the security vulnerabilities in your system and assist in securing your digital assets. Ensure that you choose a reputable and trusted professional for this purpose.
10 Recommended Tips for Cybersecurity
Keep Software Updated: Regularly update your operating system, applications, and antivirus software to patch security vulnerabilities.
Use Strong and Unique Passwords: Create complex passwords that are unique for each account and consider using a password manager to securely store them.
Enable Two-Factor Authentication: Enable 2FA for an additional layer of security for your accounts.
Be Wary of Phishing Attempts: Be cautious of suspicious emails, messages, or phone calls asking for personal information or login credentials.
Secure Your Wi-Fi Network: Set a strong password for your Wi-Fi network and use encryption to protect it from unauthorized access.
Regularly Backup Your Data: Create backups of your important files and store them in a secure location or cloud storage.
Use Antivirus Software: Install reputable antivirus software and keep it up to date to detect and prevent malware infections.
Practice Safe Browsing: Avoid visiting suspicious websites or downloading files from untrusted sources.
Use a Firewall: Enable a firewall on your devices to block unauthorized access to your system.
Educate Yourself and Others: Stay informed about the latest cyber threats and educate yourself and your family or colleagues about best practices for online security.
Conclusion
Contacting a hacker requires careful consideration and adherence to proper procedures. By following the do's and don'ts of cyber security, you can minimize the risk of falling victim to hacking attempts and protect your digital assets. Remember to stay informed, adopt best practices, and seek professional assistance when needed to ensure robust cybersecurity measures.
FAQs
1. Can I trust ethical hackers? Ethical hackers are professionals who help identify and fix vulnerabilities in computer systems. By choosing reputable and trusted ethical hackers, you can benefit from their expertise in improving your cybersecurity.
2. How can I protect myself from phishing attacks? To protect yourself from phishing attacks, be cautious of suspicious emails, avoid clicking on unknown links, and never share personal information unless necessary and from trusted sources.
3. What should I do if I suspect a hacking incident? If you suspect a hacking incident, disconnect
from the internet, document the incident, contact the appropriate authorities, and notify relevant parties if sensitive information is involved.
4. How often should I update my software? Regularly update your software as soon as updates are available. Software updates often include security patches that address vulnerabilities and protect against potential threats.
5. Why is two-factor authentication important? Two-factor authentication adds an extra layer of security by requiring a secondary verification step, reducing the risk of unauthorized access even if your password is compromised.
#phone hacking tools#phone hacking#contact a hacker#phone hacking service#finding a hacker#find a hacker#ethical hacking#cybersecurity
0 notes
Text

#FactsDontLiePeopleDo #FactsMatter #MJisTheRealVictm #MJisInnocent
“A week ago, when I first watched hbo’s highly controversial film Leaving Neverland, I purposely did so without refreshing my recollection on the facts regarding the allegations of child sex abuse against Michael Jackson from many years ago. I wanted to see the movie in much the same way that the average viewer did.
Like most people who viewed it, I was emotionally impacted by the horrific nature of the alleged abuse, but was eventually turned off by the obvious unfairness of allowing two unverified accusers being allowed four hours, with the support of tremendously manipulative production elements, to make un-scrutinized claims against an un-convicted dead man (who, it should also be noted, paid $20 million to a 13-year-old accuser in the 1990s as part of a settlement out of court). As someone who had long suspected Michael Jackson was likely guilty of child abuse, but whose own coverage of his 2005 trial as a Los Angeles talk show host made me actually start to doubt that presumption, the whole thing was conflicting.
Since I absolutely despise that I have somehow become known as someone who is willing to defend those accused of sex abuse even though we live in an era where such an act, regardless of the facts of the particular situation, makes you automatically a “bad” person, I was extremely hesitant to delve further into the matter. However, even my initial evaluation of the voluminous record involving the movie’s two stars, Wade Robson and James Safechuck, made it very clear that the movie was a journalistic travesty, and that someone should be willing to take a stand against the prevailing narrative on behalf of truth and fairness.
As is always the case, before I eventually dove in headfirst, I engaged in extensive research on these claims, and spoke to several people with direct knowledge of the other side of the story. I did lengthy in-person interviews with two key members of the Jackson family. One of them, Brandi Jackson, had dated Robson throughout their entire teenage years, including during the time when the abuse was allegedly occurring.
One of the many difficulties in telling a version of events which is contradictory to someone the news media — as opposed to the courts — has determined is a “sex abuse victim” (especially those who, like Robson and Safechuck, have been sanctified by Oprah Winfrey on hbo) is that, particularly post #MeToo, no one data point can ever been seen as a “smoking gun” that their allegation is false. However, when viewed in the full context of Robson’s already suspect narrative, I strongly believe that Brandi’s version of events comes as close as possible to being just that (as do many other non-Jackson fans who have spent the time to hear her, and her cousin Taj, out).
In a remotely rational world, where the news media still even plausibly functioned as a source of truth, and where basic fairness still had any real currency, Brandi would have immediately been invited on multiple major television news outlets (heck, her story even involves a normally irresistible tidbit about Robson cheating on her with Britney Spears, thus causing her infamous breakup with Justin Timberlake). However, to the mild surprise of even a grizzled media cynic like me, that did not happen.
Even before our interview, multiple members of the Jackson family told me that they felt like the major news media was purposely censoring Brandi’s explosive story. I told them that it was possible that the media just may not fully understand the significance what she has to say (none of which, it should be noted, has never been contradicted at all by Robson, or anyone else), but I now must conclude that I was being naïve.
To be clear, I am not alleging some sort of anti-Jackson conspiracy, but actually something far more treacherous than that. Based on the news media’s unwillingness to even give Brandi a voice, it is now abundantly obvious that a new media rule has been created that no one, no matter how credible, unless they are huge celebrity, is allowed to directly contradict the veracity of someone the media is invested in as a “victim,” no matter how lacking in credibility that allegation is (and to be clear, books could easily be written on why the current story of Robson, who enthusiastically testified as Jackson’s first witness at his criminal trial, is not to be believed).
Within the news media, there is just far too much fear/risk, and not nearly courage/reward. So, here is what really happened in this situation…
Michael Jackson has always been suspected of being capable of literally anything because of his obvious extreme weirdness and seemingly inappropriate attachments to young boys. A filmmaker with an obvious agenda interviewed two middle-aged men for several days and ignored the many problems with their stories (for the record, a close look at the movie discredits huge chunks of Safechuck’s narrative as well, especially with regard to the real circumstances surrounding him not testifying at Jackson’s criminal trial), using about the first three hours to get his audience emotionally invested in his subjects, which was very easy given the widely-held suspicions about Jackson, who is no longer around to defend himself.
Not being armed with even the basic facts (inexplicably, and quite tellingly, Brandi Jackson is not even mentioned), the audience, including the media, was easily manipulated into being able to disregard even the biggest holes in their stories, and to gladly accept even the most bizarre rationalizations for their nonsensical actions. Once Oprah, an abuse victim herself, effectively validated their stories (even as Safechuck, who barely participated in the post-movie interview, sweated noticeably right in front of her), the preferred narrative was set, and nothing would then be allowed to credibly contradict it.
It needs to at least be mentioned that the most bizarre aspect of the news media embracing this movie is, because of the narrative used to explain why the accusers didn’t realize they were abused much sooner, it actually has elements which are arguably PRO pedophilia. This “we didn’t think sex abuse was bad” explanation could have been simply a result of the accusers having to craft their stories to escape statute of limitations problems in their lawsuit against the Jackson estate.
Regardless, there is no need to give the Jackson family much of a chance to respond — or even see the movie before it came out — because, after all, we now know for sure that they are just part of an evil machine which is knowingly covering up for a dead pedophile, all in a desperate attempt to protect the value of the pop superstar’s estate. Gee, what could possibly go wrong with that sort of thinking, especially since Jackson was never convicted, or even found liable, in a court of law?!
Part of my naïveté here was that I stupidly thought the Jussie Smollett fake hate-crime fiasco would have, at least for a few months, made the news media a little more hesitant to blindly buy into outlandish stories with no proof and a clear financial motive. Obviously, that has not happened, and it is because the modern news media, for many reasons, is now completely, irreparably, and dangerously broken.”
•John Ziegler is a senior columnist for Mediaite. He hosts a weekly podcast focusing on news media issues and is a documentary filmmaker. You can follow him on Twitter at @ZigManFreud or email him at [email protected]
5 notes
·
View notes
Text
Original Post from Amazon Security Author: Tekena Orugbani
If you’re an AWS Directory Service administrator, you can reset your directory users’ passwords from the AWS console or the CLI when their passwords expire. However, you can improve your efficiency by reducing the number of requests for password resets. You can also help improve the security of your organization by having your users proactively reset their directory passwords before they expire. In this post, I describe the steps you can take to set up a solution to send regular reminders to your AWS Directory Service for Microsoft Active Directory (AWS Managed Microsoft AD) users to prompt them to change their password before it expires. This will help prevent users from being locked out when their passwords expire and also reduce the number of reset requests sent to administrators.
Solution Overview
When users’ passwords expire, they typically contact their directory service administrator to help them reset their password. For security reasons, they then need to reset their password again on their computer so that the administrator has no knowledge of the new password. This process is time-consuming and impacts productivity. In this post, I present a solution to remind users automatically to reset AWS Managed Microsoft AD passwords. The following diagram and description explains how the solution works.
Figure 1: Solution architecture
A script running on an AWS Managed Microsoft AD domain-joined Amazon Elastic Compute Cloud (Amazon EC2) instance (Notification Server) searches the AWS Managed Microsoft AD for all enabled user accounts and retrieves their names, email addresses, and password expiry dates.
Using the permissions of the IAM role attached to the Notification Server, the script obtains the SES SMTP credentials stored in AWS Secrets Manager.
With the SMTP credentials obtained in Step 2, the script then securely connects to Amazon Simple Email Service (Amazon SES.)
Based on your preferences, Amazon SES sends domain password expiry notifications to the users’ mailboxes.
A separate process for updating the SES credentials stored in AWS Secrets Manager occurs as follows:
A CloudWatch rule triggers a Lambda function.
The Lambda function generates new SES SMTP credentials from the SES IAM Username.
The Lambda function then updates AWS Secrets Manager with the new SES credentials.
The Lambda function then deletes the previous IAM access key.
Prerequisites
The instructions in this post assume that you’re familiar with how to create Amazon EC2 for Windows Server instances, use Remote Desktop Protocol (RDP) to log in to the instances, and have completed the following tasks:
Create an AWS Microsoft AD directory.
Join an Amazon EC2 for Windows Server instance to the AWS Microsoft AD domain to use as your Notification Server.
Sign up for Amazon Simple Email Service (Amazon SES).
Remove Amazon EC2 throttling on port 25 for your EC2 instance.
Remove your Amazon SES account from the Amazon SES sandbox so you can also send email to unverified recipients.
Note: You can use your AWS Microsoft Directory management instance as the Notification Server. For the steps below, use any account that is a member of the AWS delegated Administrators’ group.
Summary of the steps
Verify an Amazon SES email address.
Create Amazon SES SMTP credentials.
Store the Amazon SES SMTP credentials in AWS Secrets Manager.
Create an IAM role with read permissions to the secret in AWS Secrets Manager.
Set up and test the notification script.
Set up Windows Task Scheduler.
Configure automatic rotation of the SES Credentials stored in Secrets Manager.
STEP 1: Verify an Amazon SES email address
To prevent unauthorized use, Amazon SES requires that you verify the email address that you use as a “From,” “Source,” “Sender,” or “Return-Path”.
To verify the email address you will use as the sending address, complete the following steps:
Sign in to the Amazon SES console.
In the navigation pane, under Identity Management, select Email Addresses.
Select Verify a New Email Address, and then enter the email address.
Select Verify This Email Address.
An email will be sent to the specified email address with a link to verify the email address. Once you verify the email, you’ll see the Verification Status as verified in the SES console.
In the image below, I have four verified email addresses:
Figure 2: Verified email addresses
STEP 2: Create Amazon SES SMTP credentials
You must create an Amazon SES SMTP user name and password to access the Amazon SES SMTP interface and send email using the service. To do this, complete the following steps:
Sign in to the Amazon SES console.
In the navigation bar, select SMTP Settings.
In the content pane, make a note of the Server Name as you will use this when sending the email in Step 5. Select Create My SMTP Credentials.
Figure 3: Make a note of the SES SMTP Server Name
Specify a value for the IAM User Name field. Make a note of this IAM User Name as you will need in Step 7 later. In this post, I use the placeholder, ses-smtp-user-eu-west-1, as the user name (as shown below):
Figure 4: Make a note of SES IAM User Name
Select Create.
Make a note of the SMTP Username and SMTP Password you created because you’ll use these in later steps. This is as shown below in my example.
Figure 5: Make a note of the SES SMTP Username and SMTP Password
STEP 3: Store the Amazon SES SMTP credentials in AWS Secrets Manager
In this step, use AWS Secrets Manager to store the Amazon SES SMTP credentials created in Step 2. You will reference this credential when you execute the script in the Notification Server.
Complete the following steps to store the Amazon SES SMTP credentials in AWS Secrets Manager:
Sign in to the AWS Secrets Manager Console.
Select Store a new secret, and then select Other types of secrets.
Under Secret Key/value, enter the Amazon SES SMTP Username in the left box and the Amazon SES SMTP Password in the right box, and then select Next.
Figure 6: Enter the Amazon SES SMTP user name and password
In the next screen, enter the string AWS-SES as the name of the secret. Enter an optional description for the secret and add an optional tag and select Next.
Note: I recommend using AWS-SES as the name of your secret. If you choose to use some other name, you will have to update PowerShell script in Step 5. I also recommend creating the secret in the same region as the Notification Server. If you create your secret in a different region, you will also have to update PowerShell script in Step 5.
Figure 7: Enter “AWS-SES” as the secret name
On next screen, leave the default setting as Disable automatic rotation and select Next. You will come back later in Step 7 where you will use a Lambda function to rotate the secret at specified intervals.
To store the secret, in the last screen, select Store. Now select the secret and make a note of the ARN of the secret as shown in in Figure 8.
Figure 8: Make a note of the Secret ARN
Step 4: Create IAM role with permissions to read the secret
Create an IAM role that grants permissions to read the secret created in Step 3. Then, attach this role to the Notification Server to enable your script to read this secret. Complete the following steps:
Log in to the IAM Console.
In the navigation bar, select Policies.
In the content pane, select Create Policy, and then select JSON.
Replace the content with the following snippet while specifying the ARN of the secret you created earlier in step 3:
{ "Version": "2012-10-17", "Statement": { "Effect": "Allow", "Action": "secretsmanager:GetSecretValue", "Resource": "" } }
Here is how it looks in my example after I replace with the ARN of my Secrets Manager secret:
Figure 9: Example policy
Select Review policy.
On the next screen, specify a name for the policy. In my example, I have specified Access-Ses-Secret as the name of the policy. Also specify a description for the policy, and then select Create policy.
In the navigation pane, select Roles.
In the content pane, select Create role.
On the next page, select EC2, and then select Next: Permissions.
Select the policy you created, and then select Next: Tags.
Select Next: Review, provide a name for the role. In my example, I have specified SecretsManagerReadAccessRole as the name. Select Create Role.
Now, complete the following steps to attach the role to the Notification Server:
From the Amazon EC2 Console, select the Notification Server instance.
Select Actions, select Instance Settings, and then select Attach/Replace IAM Role.
Figure 10: Select “Attach/Replace IAM Role”
On the Attach/Replace IAM Role page, choose the role to attach from the drop-down list. For this post, I choose SecretsManagerReadAccessRole and select Apply.
Here is how it looks in my example:
Figure 11: Example “Attach/Replace IAM Role”
STEP 5: Setup and Test the Notification Script
In this section, you’re going to test the script by sending a sample notification email to an end user to remind the user to change their password. To test the script, log into your Notification Server using your AWS Microsoft Managed AD default Admin account. Then, complete the following steps:
Install the PowerShell Module for Active Directory by opening PowerShell as Administrator and run the following command:
Install-WindowsFeature -Name RSAT-AD-PowerShell
Download the script to the Notification Server. In my example, I downloaded the script and stored in the location
c:scriptsPasswordExpiryNotify.ps1
Create a new user in Active Directory and ensure you enter a valid email address for the new user.
Note: Make sure to clear the User must change password at next logon check box when creating the user; otherwise, you will get an invalid output from the command in the next step.
For this example, I created a test user named RandomUser in Active Directory.
In the PowerShell Window, execute the following command to determine the number of days remaining before the password for the user expires. In this example, I run the following to determine the number of days remaining before the RandomUser account password expires:
(New-TimeSpan -Start ((Get-Date).ToLongDateString()) -End ((Get-ADUser -Identity ‘RandomUser’ -Properties “msDS-UserPasswordExpiryTimeComputed”|Select @{Name=”exp”;Expression={[datetime]::FromFileTime($_.”msDS-UserPasswordExpiryTimeComputed”).tolongdatestring()}}) | Select -ExpandProperty exp)).Days
In my example, I get “15” as the output.
To test the script, navigate to the location of the script on your Notification Server and execute the following:
.PasswordExpiryNotify.ps1 -smtpServer “STEP 2> ” -from “ ” -NotifyDays
In this example, I navigate to c:scripts and execute:
.PasswordExpiryNotify.ps1 -smtpServer “email-smtp.eu-west-1.amazonaws.com” -from “IT Servicedesk [email protected]” -NotifyDays 15
A new email will be sent to user’s mailbox. Verify the user has received the email.
Note: I can update these instructions to send multiple email reminders to users. For example, if I want to notify users on three occasions (first notification 15 days before password expiration, then 7 days, and one more when there is only 1 day) I would execute the following:
.PasswordExpiryNotify.ps1 -smtpServer “email-smtp.eu-west-1.amazonaws.com” -from “IT Servicedesk ” -NotifyDays 1,7,15
Step 6: Set up a Windows Task Scheduler
Now that you have tested the script and confirmed that the solution is working as expected, you can set up a Windows Scheduled Task to execute the script daily. To do this:
Open Task Scheduler.
Right-click Task Scheduler Library, and then select Create Task.
Specify a name for the task.
On the Triggers tab, select New.
Select Daily, and then select OK.
On the Actions tab, select New.
Inside Program/Script, type PowerShell.exe
In the Add arguments (optional) box, type the following command, including the full path to the script.
“C:ScriptsPasswordExpiryNotify.ps1 -smtpServer “STEP 2>” -from “ ” -NotifyDays “
In my example, I type the following:
“C:ScriptsPasswordExpiryNotify.ps1 -smtpServer ’email-smtp.eu-west-1.amazonaws.com’ -from ‘IT Servicedesk [email protected]’ -NotifyDays 1,7,15”
Select OK twice, and then enter your password when prompted to complete the steps.
The script will now run daily at the specified time and will send password expiration email notifications to your AWS Managed Microsoft AD users. In my example, a password expiration reminder email is sent to my AWS Managed Microsoft AD users 15 days before expiration, 7 days before expiration, and then 1 day before expiration.
Here is a sample email:
Figure 12: Sample password expiration email
Note: You can edit the script to change the notification message to suit your requirements.
Step 7: Configure automatic update of the SES credentials
In this final section, you’re going to setup the configuration to automatically update the secret (that is, the SES credentials stored in AWS Secrets Manager) at regular intervals. To achieve this, you will use an Amazon Lambda function that will do the following:
Create a new access key using the IAM user you used to create the SES SMTP Credentials in Step 2 (ses-smtp-user-eu-west-1 in my example).
Generate a new SES SMTP User password from the created IAM secret access key.
Update the SES credentials stored in AWS Secrets Manager.
Delete the old IAM access key.
Complete the following steps to enable automatic update of the SES credentials:
First you will create the IAM policy which you will attach to a role that will be assumed by the lambda function. This policy will provide the permissions to create new access keys for the SES IAM user and permissions to update the SES credentials stored in AWS Secrets Manager.
Log in to the IAM Console, and in the navigation bar, select Policies.
In the content pane, select Create Policy, and then select JSON.
Replace the content with the following script while specifying the ARN of the IAM user we used to create the SES SMTP credentials in Step 2 and the ARN of the secret stored in Secrets Manager that you noted in Step 3.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": "iam:*AccessKey*", "Resource": "" }, { "Effect": "Allow", "Action": "secretsmanager:UpdateSecret", "Resource": "" } ] }
Here is the JSON for the policy in my example:
Figure 13: Example policy
Select Review Policy, and then specify a name and a description for the policy. In my example, I have specified the name of the policy as iam-secretsmanager-access-for-lambda.
Here is how it looks in my example:
Figure 14: Specify a name and description for the policy
Select Create Policy
Now, create an IAM role and attach this policy.
In the navigation bar, select Roles and select Create Role.
Under the Choose the service that will use this role, select Lambda, and then select Next: Permissions.
On the next page, select the policy you just created and select Next: Tags. Add an optional tag and select Next: Review.
Specify a name for the role and description, and then select Create role. In my example, I have named the role: LambdaRoleRotatateSesSecret.
Now, you will create a Lambda function that will assume the created role:
Log on to the AWS Lambda console and select Create Function
Specify a name for the function, and then, under Runtime, select Python 3.7.
Under execution role, select User an existing role, and then select the role you created earlier.
Here are the settings I used in my example:
Figure 15: Settings on the “Create function” page
Select Create function, copy the following Python code, and then paste it in the Function Code section.
import boto3 import os #required to fetch environment variables import hmac #required to compute the HMAC key import hashlib #required to create a SHA256 hash import base64 #required to encode the computed key import sys #required for system functions iam = boto3.client('iam') sm = boto3.client('secretsmanager') SES_IAM_USERNAME = os.environ['SES_IAM_USERNAME'] SECRET_ID = os.environ['SECRET_ID'] def lambda_handler(event, context): print("Getting current credentials...") old_key = iam.list_access_keys(UserName=SES_IAM_USERNAME)['AccessKeyMetadata'][0]['AccessKeyId'] print("Creating new credentials...") new_key = iam.create_access_key(UserName=SES_IAM_USERNAME) print("New credentials created...") smtp_username = '%s' % (new_key['AccessKey']['AccessKeyId']) iam_sec_access_key = '%s' % (new_key['AccessKey']['SecretAccessKey']) # These variables are used when calculating the SMTP password. message = 'SendRawEmail' version = 'x02' # Compute an HMAC-SHA256 key from the AWS secret access key. signatureInBytes = hmac.new(iam_sec_access_key.encode('utf-8'),message.encode('utf-8'),hashlib.sha256).digest() # Prepend the version number to the signature. signatureAndVersion = version.encode('utf-8') + signatureInBytes # Base64-encode the string that contains the version number and signature. smtpPassword = base64.b64encode(signatureAndVersion) # Decode the string and print it to the console. ses_smtp_pass = smtpPassword.decode('utf-8') secret_string = '{"%s": "%s"}' % (new_key['AccessKey']['AccessKeyId'], ses_smtp_pass) print("Updating credentials in SecretsManager...") sm_res = sm.update_secret( SecretId=SECRET_ID, SecretString=secret_string ) print(sm_res) print("Deleting old key") del_res = iam.delete_access_key( UserName=SES_IAM_USERNAME, AccessKeyId=old_key ) print(del_res)
Here is what it will look like:
Figure 16: The Python code pasted in the “Function Code” section
In the Environment variables section, specify the two environment variables required by the Lambda Python code as follows:
SECRET_ID: AWS-SES SES_IAM_USERNAME: STEP 2>
Here is how my environment variables look:
Figure 17: The Python code pasted in the “Function Code” section
Select Save.
You have now created a Lambda function that can update the SES credentials stored in AWS Secrets Manager.
You will now set up CloudWatch to trigger the Lambda function at scheduled intervals.
Open the Amazon CloudWatch Console.
In the navigation pane, select Rules and, in the content pane, select Create Rule.
Under Event Source, select Schedule, and then select Fixed rate of. Specify how often you would like CloudWatch to trigger the Lambda function. In my example, I have chosen to update the SES credentials every 30 days.
Under Targets, select Add Target, and then select Lambda Function.
In Function, select the Lambda function you just created, and then select Configure details.
Figure 18: Create new CloudWatch rule
Specify a name for the rule, enter a description, make sure the State check box is selected, and then select Create rule.
The SES credentials stored in AWS Secrets Manager will now be updated based on the scheduled intervals you specified in CloudWatch.
Conclusion
In this post, I showed how you can set up a solution to remind your AWS Directory Service for Microsoft Active Directory users to change their passwords before expiration. I demonstrated how you can achieve this using a combination of a script and Amazon SES. I also showed you how you can configure rotation of the Amazon SES credentials on your preferred schedule.
If you have comments about this post, submit them in the “Comments” section below. If you have questions or suggestions, please start a new thread on the Amazon SES forum.
Want more AWS Security how-to content, news, and feature announcements? Follow us on Twitter.
Tekena Orugbani
Tekena is a Cloud Support Engineer at the AWS Cape Town office. He has many years of experience working with Windows Systems, virtualization/cloud technologies, and directory services. When he’s not helping customers make the most of their cloud investments, he enjoys hanging out with his family and watching Premier League football (soccer).
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Tekena Orugbani How to prompt users to reset their AWS Managed Microsoft AD passwords proactively Original Post from Amazon Security Author: Tekena Orugbani If you’re an AWS Directory Service administrator, you can…
0 notes
Text
A Step-by-Step Guide For Effective Bad Credit Repair In Inland Empire
One’s credit score is usually a reflection of how they’ve handled their financial obligations. This is based on the information reported to the credit bureaus by creditors/lenders. Paying your bills on time and managing your accounts wisely will guarantee you a good credit score. By defaulting on your payments, your credit score goes bad. When this happens, you’ll probably need the services of credit repair companies in Inland Empire. Bad credit makes your financial life difficult and expensive. Lending institutions check credit scores before giving out any loan or credit card.
With bad credit, you will incur high interest rates on loans if you get a lending institution that is ready to give you a bad credit loan. The good news is that you can fix the mistakes affecting your credit and increase your credit score. Getting your credit repaired is critical to saving money on loans, credit cards, and insurance. Credit repair in Inland Empire also helps you to qualify for new employment and even promotions and raises with your existing employer. With a good credit score, you have the security of knowing that you can borrow money anytime need arises.
When you want to have your credit score improved, you can opt to fix it by yourself or have it handled by credit repair companies in Inland Empire. Opting to fix your own credit rating can help you save money and the hassle of finding a good credit repair company to do it for you. Below are steps of improving bad credit:
Get Copies of Your Credit Report
Everyone is entitled by law to free credit reports from the three credit bureaus (TransUnion, Experian, and Equifax) every year. Inland Empire credit repair companies can help you order the reports directly through the credit bureaus. Another option is to pay for your credit report, but only if you’ve already used up your yearly credit report. The main reason for having all the three credit reports is for you to confirm that they all contain similar information. Some creditors and lenders tend to report to one credit bureau, complicating your credit standing and reputation. If this happens, you will have to repair your credit at all the three bureaus instead of working on one.
Your credit report has all the information of your credit history and details of the things that are inaccurate and are lowering your credit score. These include your high credit card balances, past due accounts, public records or debt collections. You have to study your credit report thoroughly and identify the negative items that are affecting your credit rating. Check your personal identification information, detailed history of all your accounts, public records like tax liens and bankruptcy and your creditors/lenders reports for any misinformation.
Identifying errors
They type of information that requires Inland Empire credit repair include:
Incorrect information such as payments which are incorrectly reported and accounts that don’t belong to you.
Overdue accounts that are charged off are late or have been given to collectors
Maxed out accounts that have exceeded the credit limit.
After identifying the incorrect information, develop a credit repair plan and approach for each information. Collaborating with your creditor will greatly help your progress.
Disputing the errors on your credit report
Note that you have the right to a credit report that is accurate. Therefore, you can dispute any incomplete, inaccurate or unverifiable information in your credit report through credit repair companies in Inland Empire. Your credit reports come with instructions on ways of disputing your credit report information. You can make disputes by calling, or emailing.
Methods of disputing credit repair information
Making your disputes online is fast and easy, but you will not have a paper trail for your records. Sending the disputes by email allows you to attach proof and keep a copy of the communication. When you send your dispute through the certified mail, you’ll also get to keep proof of the details and dates you mailed the dispute. Having dispute records is vital for subsequent follow-ups and verifications.
When sending your dispute, always attach a copy of the credit report and the item in dispute along with proof that supports your dispute. Include all the information about your dispute to avoid your dispute from being declared frivolous. If this happens, the bureaus will decline to investigate the dispute and your credit report will not be updated. A reputable company that deals in credit repair in Inland Empire will be able to expedite the process for you. The credit bureau always sends a response to your dispute after completing their investigation. Another alternative to a credit bureau dispute is through direct dispute to the companies that listed information on the credit report. They have the legal obligation to investigate the dispute and remove the incorrect information from your credit report.
Settling past due accounts
Your payment history greatly affects your credit score. It comprises 35% of your overall score. Having multiple past due accounts listed on your credit report will hurt your score significantly. Settling these accounts is crucial to credit repair. Use the services of Inland Empire credit repair to take care of accounts which are past due but not charged-off. Talk to your creditor and discuss options that will change your account to current. The creditor may agree to waive late penalties or spread the balance over fewer payments. They can also agree to re-age your account to show your payments as current. Charge-offs hurt your credit rating, and they must be paid. Outstanding balances on charge-offs will make it impossible for you to get approved for loans or new credit. Settle collection accounts too by paying in full or through a pay-for-delete, or even settling them for less than the balance due. Ensure that your credit card balances, loan balances and all your past due accounts are below the credit limit.
Get new credit
In case you have loans and credit cards that you service on time, keep them current by making payments on time. In case you don’t have any try to get new ones and ensure you pay them on time. You can consider getting a secured credit card if you are denied a major credit card. For you to get a credit limit, you will have to deposit a certain amount on your secured credit account as a security deposit. Avoid closing your current credit card accounts as it may affect your credit score.
While working towards a better credit rating, don’t sacrifice the positive accounts for those that are in bad rating. Keep making timely payments on the current accounts. Learn what things affect your credit score negatively and avoid making the same mistakes next time. Remember that your credit rating may drop unexpectedly as you carry out credit repair in Inland Empire. But this does not mean that you’re not doing things right. Just keep adding positive information on your report, and the credit score will go up over time.
CONTACT US -
Address - 18930 HWY 18 STE 101, Apple Valley, CA, USA
Phone - 1-866-342-1062
Email - [email protected]
Website - Decs - We Kill Debt
Blog - A Step-by-Step Guide For Effective Bad Credit Repair In Inland Empire

0 notes
Text
Free Fire, Part 4
(Part 1) (Part 2) (Part 3)
The next day (Azorius bureaucracy isn’t known for its speed. That was quite fast for them, actually) I was taken to an office, and shackled with anti-magic restraints before leaving the jail part of the building. In that office were seated a woman, the elf I was getting used to see, and an Azorius seated behind a desk crumbling under the weigh of the (neatly organised) paper on top of it. He lifted his head from his scroll when I entered.
"Ah, you’re the one designated as ‘Ivegard’, right ?
-That’s my name, yes.
-Perfect, if you would sit down, it should only take a moment. As a matter of procedure, we’ll all be inside a truth circle during this exchange. If you don’t agree with that choice, you’ll be able to contest it by filling out a complaint form 856 A and sending it over to the closest Azorius Tribunal. Do you agree with that procedure ?
-I do."
I complied. I couldn’t do a whole lot without magic in the middle of an Azorius complex.
"So, the case here is fairly simple. Are you a flame-kin ?
-I mean, I am, but…
-Captain Evicz, you’re representing the Boros Legion ?
-I am." The elf answered.
"By the Treaty on artificial beings of 6752, all artifial beings, unless an exception is made under the spirit addendum of 10012, are owned until their dissipation/destruction, by the guild that created them.
-…I’m not an artificial being.
-You popped into existence maybe ? Even if that were true, subsection 87 precises that flame-kin, or other non-Izzet fire-related elemental lifeforms, are to be owned by the Boros for their time in this city. Do you have another unverifiable claim that will not be helpful to your case ?
-I… Your Honor, I think you’ll want to talk to an Izzet guildmage named Ral Zarek."
The Azorius mage blinked a few times, and captain Evicz head shot in my direction.
"Stalling will only waste all of our times. What can this guildmage bring that would change your status?
-I fear you would have to ask him. But he shouldn’t be far.
-What are you doing ?" Asked the elf.
"Not your work, apparently."
The magistrate grabbed a piece of paper on his desk and read it quickly.
"I don’t have to comply to your demands unless I can suit them lawfully and quickly. You don’t even know where this Zarek is.
-Give me a second."
I closed my eyes and tried to focus on my fire, my flames. The shackles were blocking my magic from going outward, but not it from coming in. On the border of my flames, they twitched and reacted to the other fires around them, and their characteristic emotions. Focusing all I had on inspecting every twitch, every movement, every feeling, I managed to find back the characteristic anger and curiosity of Zarek. When I opened my eyes back. It was to see the elf captain signing a paper that the Azorius was holding.
"No !
-Oh, you’re back with us. Did your little nap prepare you from what’s to come ?
-I know where Zarek is !
-It’s too late, elemental." the elf retorted.
"No it’s not… I haven’t signed. And you’re intriguing. Where would this Izzet Guildmage be ?
-Approximately 100 feet in that direction", I said, while waving my arm in the general direction I sensed him.
The Boros jerked back in her chair and put her hand on the hilt of her weapon. The magistrate only raised his eyebrows.
"I know you can’t use magic, you know. That show of yours was entertaining, though.
-You say that to the talking magical pile of rocks and fire. Don’t you want to verify ? It shouldn’t take long. He has a distinct black and white hairstyle and an electric personality.
-I’ll send someone, but at the condition that you stop delaying this affair more than necessary.
-I’ll agree to that. And it’s necessary, believe me.
-Don’t blame me if I wait and see."
He ringed a small bell I hadn’t noted before. Some sort of ghost came through the door. The ghost was given a few orders, then went through the floor in the direction I (and the Azorius) had indicated.
Fifteen minutes later, during which the conversation was rather tensed, the ghost came through the door again. I was indicated to go open the door, I did to see Ral Zarek behind it. As I let him enter, he went directly to the only empty chair in the room, the one I was sitted in half a minute before. Before sitting down, he bowed quickly (and not much) for the elf and the magistrate.
"Your Honor, Captain, Ral Zarek, rising star of Nivix.
-What are you doing here ?" Asked the elf.
"I’m coming here today to stop you from making a big mistake. Her." The last word was accompanied by a hand gesture towards me.
"Why does a Flame-kin interest the Izzet ?
-You might have noted she’s not your typical flame-kin.
-What do I know ? She’s made of fire and she walks and talks. I don’t need more than that !"
He took a deep breath before waving again in my general direction.
"Warmind.
-What, she’s a strategist ? What was she doing alone in the street.
-Do I have to spell it out for you ? W-A-R-M-I-N-D." At that the captain paused.
The Azorius was intently listening but not saying a word up until there.
"Wasn’t that the joint Boros-Izzet project that launched a few years ago ?
-Yes wasn’t it ?" asked Zarek, while the light of understanding started to dawn on her.
"It is…
-In that case, I wonder why this highly unusual flame-kin is wandering the street without Boros or Izzet supervision and without trace of her existence in the system ? Would you happen to have an explanation, your Honor ?
-I admit I do not. It seems highly unregular..." While they were talking, I could see the face of the elf losing some colors. I never understood how elf and humans did that.
"You’re right, your Honor, let’s regularize that situation and attach that flame-kin’s name and action to the name of the Boros."
The elf’s face changed colors once again. A really neat trick. She took the initiative.
"I think this will not be necessary.
-You don’t want everything to be in order with your elemental ?" Asked the magistrate.
"Do you officially remove your, and the Boros’s, claim on the propertyof this flame-kin ?"
Retorted Zarek. The elf seemed lost for a second, but responded.
"Yes, I do.
-Really ? I need you to say it." the Azorius official was now watching intently the Boros captain.
"I officially, as the Boros representative, remove my pending claim on the property of the flame-kin reffered to as ‘Ivegard’.
-Thank you."
While talking, the official was quickly writing on a scroll. The guildmage stood up and moved between the desk and the captain, facing her.
"And don’t you agree that we should officialize the status of that flame-kin as an independant citizen, not affiliated with any of the guild, to avoid similar problems in the future ?"
As he was asking his question, his hand made a quick movement behind him, and a small purse appeared on the desk, quickly grabbed by the magistrate.
The elf nearly whispered her answer.
"Yes. We probably should.
-Alright then ! Your honor, can you do that for us ?
-I did not prepare for that, but I’d imagine a 128 L should do the trick ? If that’s what you both want ?" His question was intended to the elf and me.
"It seems great to me.
-Let’s end this comedy…
-Alright, just give me a few minutes to put everything in order."
And a few minutes later…
"Alright, just both sign here and here." We did, he did. He took two blank scrolls and copied the one we just signed onto them, then gave one to Evicz and the other to me. He watched me intently and warned me before releasing the paper.
"Carry this with you at all times in the city. I can’t guarantee what would happen if you lost it or didn’t have it.
-What ? But it’s a piece of paper ! How do you expect me to carry it around ?
-Don’t ask me. If you want to request a special treatment, you can do so on the 18th floor. Ask for a 8544-112-H and a 5732-421-K.
-How am I supposed to remember that ?
-Not my problem. Now leave my office like you should have half an hour ago !"
I turned on my heels, then turned back, and extended my still shackled arms.
"Oh right." He cast a quick spell and the shackles detached from me.
After leaving the office, Zarek went for me. I signed for him to stop for a moment, and went to see the elf, leaving with her scroll in hand.
"Captain ?
-What ! Didn’t you do enough ?
-Evicz isn’t it ? I’m sorry you and all the neighborhood had to be put through that. I assure you it was not my intent.
-You burned one of my officers !
-You want to drag him in a truth circle and ask him what happened ? You know him, right ?
-That’s not important !
-Listen, don’t feel bad about it. I’m even ready to help your precinct should it need any. As long as you ask me beforehand. And I don’t have to risk my life or anything stupid. And I have nothing else more important to do.
-You really think you can erase everything with a few words ?
-I don’t want to erase anything, I want us to understand each other. Would you agree to meet me back in this hall next week to discuss of the situation with a fresh mind ?
-I don’t agree to anything.
-Thanks ! I’ll be there."
On that I came back to Zarek, from which I sensed more and more frustration coming.
"Everything’s alright ? You’ve set your next date ?
-Don’t be ridiculous, that’s not a date. Well, not yet anyway.
- ‘Thank you Ral, you’re the handsomest guy in this city and you got me out of this interguild mess with a few words.’
- ‘… Oh, it’s nothing, give me that message and let’s call it even !’
-Are you crazy ? You owe me 500 more zinos, that message and answers.
-Do you really want to do that here ?
-No, you’re right for once, let’s go back to someplace more secure."
And I’ll thank @ral-zarek-petty-guildmage for his participation in this, and @ask-saheeli-rai for her mention for the last time.
0 notes