#paranoidsbible
Text
neo’s quick guide to browser privacy
so i keep seeing a post circulating with info on how to keep browsing provacy and avoid targetted ads and comapnies saving your data, but unfortunately the commenters a known freaks el em ayo. they also just dont explain the addons very well, or how to set them up properly. so, as an official paranoid(tm), here’s my info on how to keep yourself safer while browsing, and to avoid companies tracking your internet habits.
first of all, use firefox.
i’m not kidding. drop chrome. chrome is terrible. many of these addons work for chrome, but really what are you doing using google chrome if you want privacy? that shit is sent right to google. firefox is also very heavily privacy and safety focused, and has many tools to help you manage your browser time. also, all of the addons i will mention here work on the mobile version of firefox! and, yes, you should be setting them up on your phone too.
make sure to remove any other ad blockers you might have on firefox before installing any of the following addons, as they might conflict with these.
trackmenot
(installation link here)
trackmenot is a very helpful addon that will generate randomised searches through various search engines. this means that your actual searches will be lost in the fog of so much other search data, making it extremely difficult and even outright impossible to track your search trends, thereby avoiding many targeted ads.
it takes a little to get it optimally set up, but i am here to help!
first step after installing it, go to your addons page in firefox. if you dont know what that is, here’s a pic to show you where it is:
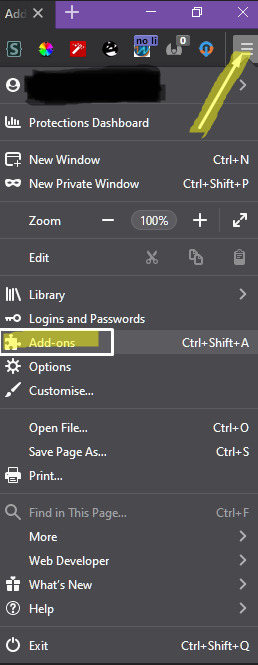
click the three horizontal lines in the top right of the browser, and then click add-ons in the drop down menu.
on your addons page, find trackmenot, and click it.
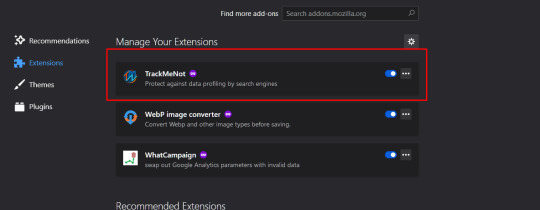
then click ‘options’....
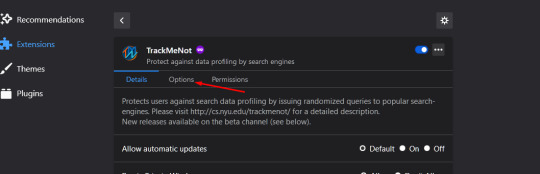
on the next page, make sure your boxes look like mine do:
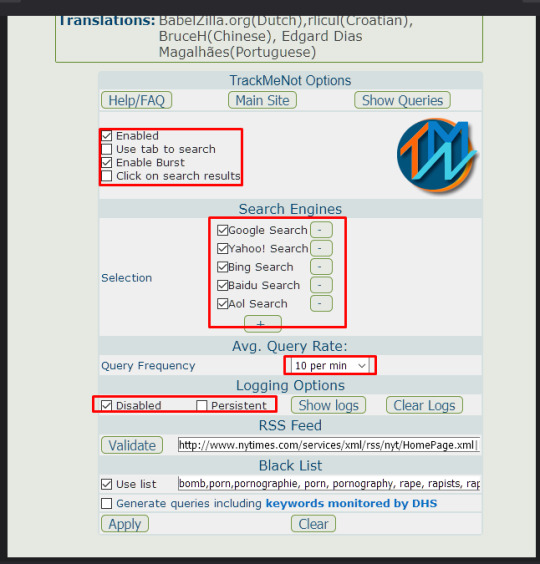
now you want to add an rss feed for the addon to use. you can add whatever you like, but i reccomend the following just to get you started:
http://www.nytimes.com/services/xml/rss/nyt/HomePage.xml|http://rss.cnn.com/rss/cnn_topstories.rss|http://rss.msnbc.msn.com/id/3032091/device/rss/rss.xml|http://www.theregister.co.uk/headlines.rss
you want to put a | between each rss url. once youre done, click ‘validate’.
you will also want to use a blacklist so that it doesn’t accidentally search anything fucked up or that might get you flagged by the fbi or sth. here is the blacklist that i use:
rape,rapists,ddlg,cgl,mdlb,raping,raped,lolicon,loli,cp,child porn,pthc,jbhc,shota,shotacon,gore,bestiality,beastiality,zoophilia,pedophilia,
make sure to seperate any words with a comma, and that the ‘use list’ box is checked. then click ‘apply’ and youre done! phew! thankfully the others dont take as much setting up.
-
whatcampaign
(installation link here)
what this does is find any links that contain google analytics parameters in them- which is what google uses to track link clicks and internet movement- and changes them to ones that do not have the analytics in them. now you can click links without fear of Big G knowing what you’re doing.
-
privacypossum
(installation link here)
this addon blocks cookies, headers and other code in pages that track your activity, and falsifies information to browser fingerprinters to prevent trackers from knowing the specifcs of you and your browser. many websites use headers with embedded code and other fingerprinting methods to load the rest of the code on the page, and many other addons (such as privacybadger) simply block these outright, making the webpage not work properly unless disabled. privacypossum avoids this issue bu simply falsifying your data, meaning you can load websites without having to worry that they know who you are.
-
adnauseum
(installation link here)
unlike other adblockers, adnauseum will, in fact, click ads. but before you scroll by, let me explain. many websites need ads to be able to continue being up, they rely on ad revenue and clicks. but nobody wants to click ads, nobody wants to see ads. so what do we do? adnauseum addresses both sides of this, blocking any and all ads that you may see, and in the process, registers clicks on them. all of them. similarly to trackmenot, by blindly clicking every single ad, the amount of data generated creates too much noise to be useful to ad companies.
an alternative to this if you have issues with adnauseum is ublock origin.
-
anonymox + vpns
this is an extension that acts as a vpn for your browser (and browser ONLY), allowing you to hide your ip address. you can turn it on and off as you like, and swap to various different locations. bear in mind that this will make pages load a lot slower, so i only use it on sites that i do not trust, or when i need to access something that is blocked in my region.
this will not protect you when downloading or torrenting, for that you need an actual vpn.
a paid vpn that i personally use is surfshark. a free one that i have used in the past is tunnelbear.
-
advanced tip: DOH (dns over https)
so what the heck does THAT mean?
this page has a much more in depth, with pictures explanation of what this means, and how firefox deals with it.
firefox has its own in built DOH protocol, however, it relies on cloudflare. if you do not trust cloudflare, i reccomend the DOH protocol by projektoni, the guys behind whatcampaign. follow the instructions on this page to get it set up.
15 notes
·
View notes
Text
Privacy Co-ops and You
===Privacy Co-ops and You===
Non-profit and free for redistribution
Written on April 1st | 2018
Published on May 3rd | 2018
For entertainment and research purposes only
++++++++++++++++++++++++++++++++++++++++++++++++++++
DISCLAIMER
The Paranoid's Bible and its writers hold no responsibility for the acts of others.
The Paranoid’s Bible is for research and entertainment purposes only.
Please visit our blog for more PDFs and information: http://www.paranoidsbible.tumblr.com/
++++++++++++++++++++++++++++++++++++++++++++++++++++
===Preface===
Some of you may be familiar with some parts of this guide, while others are not. This is mostly due to the fact that a certain ex cult member has joined our ranks and will be sharing their information and experiences with us (you may know of their blog already). So please take the time to read this guide if you’re interested in purchasing goods online or using things like membership cards.
This guide will be applying certain tactics from several real world groups so that we may be able to condense and lessen our overall exposure if we’re willing to work with friends and/or family who share similar views and opinions, or simply wish for a cheaper alternative.
+++++++++++++++++++++++++++++++++++++++++
===What is a Privacy Co-op?===
Community Building, also known as a privacy co-op, is where a group of 5 to 10 (or more) people get together to share money, resources and information to further reduce their information footprint and to help each other create garbage data and static to pollute whatever data is collected on them. This is usually done through sacrifices (creation and ownership of memberships or accounts, like Amazon prime). Each member makes one to two sacrifices, depending on the needs of the community, and then works together to share within these sacrifices.
We'll be somewhat vague in this guide. This is mostly due to the fact that each group is unique in needs and wants, ergo this guide is done loosely to provide wiggle room for those who read and use it.
Consider this more of a suggestion than a complete guide.
+++++++++++++++++++++++++++++++++++++++++
===Creating a Community===
The easiest step is always the first, which is why creating a community is something many people who're privacy conscious should look into. This should be done however with only trusted friends and family that either share the same beliefs (in privacy) as you or are able to keep things quiet. Many places are trying impede an individual's freedom by restricting access to the core purchaser instead of allowing sharing/helping.
As an example, let’s say in your little co-op you were picked as making the sacrifice for purchasing a membership in your name. While everyone contributes to the monthly or yearly fee, it's ultimately your name and consumer profile that that membership is associated with regardless of purchases made. However, because of these purchases, your consumer profile is more or less corrupted due to the fact that you've many people giving you the money to cover their purchases besides your own.
This is why, when creating a community/privacy co-op, that you should treat every purchase as your own when classed as the owner of an account or membership. This way no-one can try and claim you as using your account or membership as a fraudulent act. A scenario to demonstrate this could be if you were to go to someplace like CostCo and buy a bulk pack of something like baby food. They have various tier memberships which grant you certain privileges and advantages, which means potentially lesser prices or so much of a percentage off, ergo cheaper price in the long run on the baby food. So if someone for whatever reason asks why you’re buying so much, and you don’t have your own child, you simply state you’re hosting a relative at your home for awhile and wanted to make sure their child, your niece or nephew, have stuff to eat.
So, to summarize: Many people mediating through a single individual in order to share the cost and purchase of goods without putting their own information and privacy at risk. The person who is in charge of the membership or account has less of a risk due to so many people going through them to purchase goods and services. This corrupts the consumer profile and pollutes it with garbage data.
+++++++++++++++++++++++++++++++++++++++++
===Democracy in the CO-OP===
When it comes to a community/privacy co-op the best way to go about it is to figure out what assets each individual has and what is needed. If someone already has Amazon Prime, then designating them as the keeper of AP makes sense, however if an EBAY account is needed and no-one has one then someone will have to create an account and PayPal to use Ebay. This is where discussion is needed as everyone has different needs and wants.
Grocery shopping can be done quite easily through warehouses like Costco, GFS and Sam's Club, whereas clothes and technology will be a little more difficult. You'll also want to figure out how much you want to take advantage of when it comes to accounts and memberships. Some places offer credit cards that'll stock on extra percentages off whereas just the membership itself won't. Then you'll have rewards/awards that are locked to a specific time, date and person only.
While we're ultimately going to end up repeating here, discussion is important. Needs over wants; how much each member can contribute to accounts or membership fees; when shopping trips should be done; if bulk purchases are in everyone's favor... etc ...etc
If each member pulls their own weight and helps to contribute to the co-op, and with some well planned coordination, an individual can purchase an entire wardrobe for next-to-nothing. If each member works together on shopping trips, and does a bit of shopping around (for cheaper prices), everyone can ultimately stock up on necessities through bulk purchases and taking advantage of deal in various stores.
+++++++++++++++++++++++++++++++++++++++++
===War Games===
The first order of business, obviously, is to figure out how far out your group and you are willing to go when doing physical purchases (as in do you go 50 miles VS 10 miles because price differences).
The second order of business is figuring out how much gas and maintenance you're willing to chip in for when travelling and transporting these physical purchases and if you're wasting more to get better deals due to traveling or not (Tip: Sign up for gas station memberships to earn your some money back).
Third, you must figure out some form of rotation of which members go during these shopping trips.
Fourth, weekly VS monthly lists. Weekly lists would include things like day-to-day items, needed toiletries and similar items. Monthly to yearly would be considered "stockables" like paper goods (toilet paper, paper towels...etc), cleaners and similar items.
Fifth, bulk purchases of what and when. If you can purchase items in bulk and divide them accordingly, you should be able to time these purchases by a month to every six or so months.
Sixth, necessities VS frivolities. Candy is a nice treat but ultimately not needed. Fresh fruits, veggies, instant meals, canned goods...etc are necessities, not candy, gum or other similar items. Planning accordingly to the needs of the members VS the wants cannot only save money and time but lead to money being saved at the end.
Seventh, change and leftover money should be devoted to being put back into shopping trips or toward a goal, like a trip or holiday fund for the group (or put aside for "Unplanned deals" (E.G: Toilet paper on the cheap) ).
Eighth, cash and gift cards should be focused on as the main option for payment VS checks and credit or debit. This leaves less chance of purchase tracking but also lessens chances of identity theft.
Ninth, payment plans have to be done accordingly. If you opt-in for a credit card then you need to analyze and reanalyze every minute detail you can about it. Interest rates; cash back; rewards...etc If you're using a credit/charge card to rack up points and percentages off, then open up a savings accounts and place the amount owed on each purchase in there. If you charge 30, put 30 in the savings. When the bill comes in the mail, take the amount owed out of there and pay off the bill as quickly as possible. You build up credit, keep out of any debt and earn rewards.
Tenth, don’t be afraid of taxes. It’s inevitable that you’ll have to pay taxes sooner than later on some items, especially if you use a savings account and opt-in for a credit card. Figure this out beforehand. Talk to members, figure out who owns what in whose name. Set aside so much for taxes at the end of the year, or simply chip in when they’re being filed. Either way, depending on how or what you do… you’ll need to pay your taxes.
+++++++++++++++++++++++++++++++++++++++++
===Afterword===
The above is just a sampling of what a community/privacy co-op could do, however we just covered the barest of basics. If you’re interested in doing more than the above, like purchasing property and vehicles, you’ll have to start looking into getting attorneys and discussing your area’s laws besides things like trusts and co-ownerships.
All in all, just doing the above would help reduce your consumer’s profile while screwing with the data provided to various agencies. Anything else is either just a happy accident or you found something that works for you. Either way, we can't go into more details without forcing you into a box which isn't what you want.
1 note
·
View note
Text
Moved
https://www.paranoidsbible.tumblr.com
0 notes
Text
Moved
http://www.paranoidsbible.tumblr.com
0 notes
Text
Moved to Paranoidsbible
Moved to @paranoidsbible
0 notes
Text
Paranoidsbible
@paranoidsbible
#paranoidsbible#the paranoid's bible#the paranoidsbible#paranoid's bible#paranoids bible#crash override network#crash over ride network#dox#doxx#anti-doxx#anti-dox#anti dox#anti doxx#con#crash#override#netwok#crashoverridenetwork#over#ride#network#net#work#privacy#security#technology#tech
0 notes
Text
Moved.
im closing the blog. check @paranoidsbible for their doxx cleaning guide and cosplay safety guide.
#paranoidsbible#paranoid's bible#the paranoids bible#the paranoid's bible#dox#doxx#anti dox#cleaning doxx#cosplay
0 notes
Text
We out like a fat kid in dodgeball
Closing up shop and letting the PB team to take over. Checkout @paranoidsbible for security crap. https://www.paranoidsbible.tumblr.com is the blog to get anti dox crap at.
0 notes
Text
Please look toward the Paranoid's Bible blog for more info!
@paranoidsbible is now where all of our work will be hosted. We've decided to reach out to the PB team and offer them our expertise and services. We figured it'd be best to combine our resources to further help society and the internet at large. Please visit Https://www.paranoidsbible.tumblr.com for further infosec information.
#pb#paranoid's bible#the paranoid's bible#paranoidsbible#security#privacy#infosec#cybersec#datasec#opsec
0 notes
Text
KEYS HANDED OVER TO THE PB!
We've given all of our blog's content to the @paranoidsbible team. They'll continue our work as we move onto other things. All posts are now in storage. Please visit https://www.paranoidsbible.tumblr.com for all your cybsec and privacy needs!
#the paranoid's bible#paranoids bible#paranoid's bible#pb#paranoidsbible#cybersec#cyber security#privacy#infosec#security#information security#info security#opsec#operations security
0 notes
Note
Tumblr user paranoidsbible has tips on how to lessen your chances of getting doxxed.
thanks but i was joking
0 notes
Text
The Paranoid’s Bible 2.0
===The Paranoid's Bible===
Non-Profit and Free for Redistribution.
Written on June 04th | 2014
Published on October 22nd | 2015
Runner Edition Written on April 11th | 2017
Runner Edition Published on April 30th | 2017
For entertainment and research purposes only
++++++++++++++++++++++++++++++++++++++++++++++++
===DISCLAIMER===
The Paranoid's Bible and its writers hold no responsibility for the acts of others.
The Paranoid’s Bible is for research and entertainment purposes only.
**Reminder**: Links have been forced to HTTPS. If a link doesn’t work, try removing the ‘S’ in ‘HTTPS’.
Please visit our blog for more guides and information: https://www.paranoidsbible.tumblr.com/
++++++++++++++++++++++++++++++++++++++++++++++++
===Preface===
The Paranoid’s Bible project is a series of guides meant to help the average internet user learn the rudimentary knowledge needed to prevent dox attempts and lessen their digital footprint through the use of information security (INFOSEC). Through this and other guides, the average user should be able to have not only a safer and more secure internet experience but also a more private one.
This guide and many others by the PB team have been partially written by several individuals who’ve done this not for personal gain but just to share the knowledge. So, please, pass on the knowledge you’ve gained from this guide. Splice it, edit it, consume or repurpose it.
It’ll always be free, like any information should be.
++++++++++++++++++++++++++++++++++++++++++++++++
===All About Doxing===
Doxing, a term that comes from ‘document tracing,’ is believed to have had a past in web 1.0 among the early internet users. The act in itself is the action of finding information on a target from an initial set of data, like a username or an e-mail address. This information can be found through the use of something as simple as a search engine or as time consuming as reading up on the target’s accounts across the internet. While there exists several services besides search engines to find this information, the most tried and true method is simply using the target’s own actions against them to discover their dox.
It isn’t all about search engines and researching a target’s digital footprint, some individuals can and will try their hand at social engineering. The act of social engineering is accomplished through the claim of being someone they're not or through asking questions in order to gain access to more information on the target. While a gray area of being online and offline, it’s best to note that doxing isn’t only done online but also offline (E.G: posting fliers to ‘name & shame’) and that there exists numerous ways to obtain the information needed.
The act of doxing, though, is a neutral act that is free of political and moral responsibilities. Anyone can find another person’s dox and use it for whatever means they wish to use it for, like blackmailing, shaming or simply browbeating someone over different beliefs and opinions. It’s used by many groups and individuals that range in religious and political beliefs; ergo the person committing the act is the one that places any meaning onto it.
The truth is that no one is un-dox-able. It’s speculated this is the end result of mob justice and social justice on the internet; however doxing is just something that won't go away. Just like its rise to infamy in the early 2000s, it'll always have its ups and downs. We just have to learn to co-exist with it and guard ourselves against any attempts.
**Remember**: Anyone can become a target and victim of doxing.
___References___:
https://www.makeuseof.com/tag/what-is-doxing-and-how-does-it-affect-your-privacy-makeuseof-explains/
https://www.techgyd.com/know-doxing-protect-yourself/6197/
https://en.wikipedia.org/wiki/Doxing
https://socialengineering.wikia.com/wiki/Doxxing
https://knowyourmeme.com/memes/doxing
https://www.urbandictionary.com/define.php?term=doxing
++++++++++++++++++++++++++++++++++++++++++++++++
===Why You Should Fear Doxing===
Many would have you believe that doxing isn’t something to worry about and that it’s just harmless pranks done by adolescents on the internet… these people are wrong and sorely out of touch with the current climate online. Many of these people simply believe that not posting their name or address online means they’re safe, however they fail to realize that the interconnectivity of web 2.0 and the incoming ‘internet of things’ have caused many open wounds in everyone’s privacy that bleed an unhealthy amount of information.
The average user is taught that the internet just works, sort of like magic, which severely stunts their understanding of the greater image. The internet is built upon decrepit code that’s held together with a programmer’s equivalent of gum and duct tape. Because of this, and quicky-fixes, it’s no wonder database leaks are becoming almost a norm for internet users; however those aren’t the biggest threat. Things like tracking cookies, Facebook spying (on logged in and non-logged in users alike), and things like digital witch hunts are putting innocent people in the line of a cyber firing squad whose main goal is to not only publicly humiliate and shame them but also take their means of living away from, causing complete isolation or ostracization for them and their loved ones.
Innocent people are attacked all the time online for things like being the victim of Cat-fishing. In some ways, it’s like doxing and identity theft. You use someone else's information and identity to masquerade as that individual. You then, as this individual, take part in what many refer to as a "romance scam". This can be to try and stalk someone, milk them of their money, or to gain trust to commit a more atrocious act, thus leaving the victims to attack each other while the perpetrator takes their leave.
Cat-fishing, although like doxing, isn't actually doxing or the biggest possible threat. Doxing to many is just pizza boxing and flooding a mailbox with literal junk. There are also prank calls, theft of mail and many other acts that can, to some degree, become worse. The issue isn’t that some use doxing as a means to gather information for identity theft. It isn't just ruining your credit or stealing your money, either. There are some individuals out there who'll use doxing as a form of abuse, isolating someone who is emotional to take advantage of them or enable them, which can lead to even greater forms of abuse.
It isn't the stalking or physical abuse you should worry about, but the mental and emotional abuse. The stress alone can damage less-than-mature victims and cause a greater sense of isolation that can disrupt relationships. It isn't just pranks and unwanted food anymore; it's now a form of vigilante justice or revenge. It'll be done by those who see themselves as fighting for a cause. They'll ruin the livelihood of many due to any perceived wrong and they’ll continue their antics until the person they’re targeting is destroyed.
___References___:
https://en.wikipedia.org/wiki/Catfishing
https://www.drphil.com/articles/article/720
https://www.thedailybeast.com/articles/2013/03/13/doxxing-it-s-like-hacking-but-legal.html
https://www.consumer.ftc.gov/features/feature-0014-identity-theft
https://en.wikipedia.org/wiki/Identity_theft
https://www.consumer.ftc.gov/media/video-0024-what-if-youre-victim-identity-theft
https://www.forbes.com/sites/laurashin/2014/11/18/someone-had-taken-over-my-life-an-identity-theft-victims-story/
++++++++++++++++++++++++++++++++++++++++++++++++
===Why You Should Care About Privacy===
Information is the new form of currency that transcends borders and time. It’s used by both the governments and corporations of the world. Due to this simple fact it’s not only a valuable resource but also an important one when you consider the worth of personal data. You as an individual aren’t worth much, however your personal data is, like what sites you frequent, which adverts you’ve clicked on or which articles you’ve read—your information is worth more than you. Even when dead, your information is valuable and can be sold, traded and collected like a baseball card. Many will remain apathetic about this fact, yet the truth is while you don’t have to worry when you’re dead… you’re alive now and should take precautions.
Corporations and government agencies are putting your information into lists and dossiers. These lists and dossiers rest in the dark corners of some data center in Utah that is constantly crawling through the web for new data. Soon it’ll be near impossible for anyone to remove their information from online simply due to the insatiable thirst that the governments and corporations of the world have for data.
Everything is being saved or is being scraped. Apps, websites and programs are doing this, quite legally, thanks to the fact that no-one bothers to read the TOS or understands the purposely confusing language that they use when trying to say they’ve a right to your words and ideas.
We shouldn’t worry about the government at least, right?
Well the government's known for ruining things you love; you should know this by now. You should be wary not of the government as a being but as an entity composed of individuals:
• An individual can track an ex-lover
• A group of individuals can target another group based upon their political beliefs
• A group can view your pornographic viewing habits and use it against you
The US government is but one of the major concerns for a person that's privacy minded. They not only spy on everyone, but they receive help from many corporations. These corporations make money off you and your information. They will buy, sell and trade with both the government and other corporations.
Sites like Been Verified, Smart Zip and Intelius will gather and place your data on not only their sites but sell it to others. Even search engines like Google or Bing have your personal information. These sites can have anything from your name to your address or even pictures of your house and vehicles.
It may seem like fear mongering and a lot of fuss about nothing, but your information is used for anything and everything. Anyone can find it now and no-one can be too prepared when it comes to their privacy and personal safety.
___References___:
https://en.wikipedia.org/wiki/Utah_Data_Center
https://www.cnn.com/2013/09/27/politics/nsa-snooping/
https://dailycaller.com/2014/12/22/bombshell-report-irs-targeted-icky-conservative-groups/
https://www.techdirt.com/articles/20131127/00243625384/nsa-spied-porn-habits-radicalizers-planned-to-use-details-to-embarrass-them.shtml
https://www.beenverified.com/
https://www.smartzip.com/
https://www.intelius.com/
++++++++++++++++++++++++++++++++++++++++++++++++
===Compartmentalization and You===
When it concerns information security, compartmentalization is the act of limiting access to information through a need-to-know basis to persons or groups who need it in order to perform specific tasks. The concept originates from the military when handling "classified information" and intelligence applications. The basis is that if fewer people know the details, the less likely a mission or task will be jeopardized and be risked. This helps limit the chance that data could be compromised or fall into the hands of enemies.
This also explains the varying levels of clearance within organizations, like "TOP SECRET" or the highly restricted "TOP SECRET ULTRA".
Like a well-oiled military machine, one must treat their online life like a separate entity that's in no way, shape or form related to their offline life. This is to prevent cross contamination of accounts and information. One such example of compartmentalization in cyber security, for the average internet user, is never using the same username or e-mail address for an account.
Another example would be purchasing a subscription to a good, secure VPN to prevent your own IP and ISP from being detected.
One other example is the use of add-ons to sanitize your referral links and randomizing your browser's user agent.
In the end, the best practice is to treat each and every account as a separate entity isolated from your other accounts. A new e-mail address, username, persona and style of typing will be needed for each and every account you create to prevent possible cross contamination.
Please remember these simple steps when creating your accounts:
• A different username
• A different e-mail address
• A different password
• Always ensure you never use real world information
• Always ensure your avatar and/or signature is of an image you've used nowhere else
• Where you can, use a P.O. Box
• Where you can, use a pre-paid card instead of your credit or debit
• Where you can, use a burner phone (pre-paid cell) instead of your landline or cell number
• Use a word processor to double check your written content before posting
• Try to limit the use of words you most commonly use
• Try to limit what information you provide in your account's profile
• Try to limit your overall account count to 10 or less
• Never link accounts to each other
• Never publicly post e-mail addresses or passwords
• Never share or link your chat, instant messenger or social media accounts to people you don't trust
• Never use your real name, nor should you ever post your real world information
++++++++++++++++++++++++++++++++++++++++++++++++
===An Introduction to your Digital Footprint===
Transparency for the sake of online socialization and interaction is a threat. This trend won't die anytime soon, mind you. There are many reasons for this, such as the alarming growth of social networks and the demands for online passports or services like Klout. It's obvious that the need for privacy is in increasing demand, but the biggest setback for privacy is you.
All those accounts you made in your early internet years? They have most likely left a nice trail that many can follow and use to learn about you and your posting habits.
You see, it’s true; everything on the internet lasts.
Unlike now, we weren’t taught to be as privacy-minded. Governments and corporations are fighting to wave privacy off as a paranoid's fantasy, and many privacy groups exist and claim to fight for your rights against the invasion of privacy. But how many actually do help? Many are in bed with corporations and/or the government. Many just demand donations because of a believed slight. Others... others just steal content from each other.
The Paranoid's Bible?
We just want to spread and share knowledge (and that you shouldn’t pay for sub-par info) whereas others push the meme that just deleting an account will wipe all traces of it. It’s wrong to believe that deleting account actually deletes anything. By law, most sites and services have to keep everything on their servers for a few months to a year or more. So, in a sense, you can never delete an account, hence us telling you that you need to think carefully before creating an account.
We believe your various accounts should be like any good camp fire: Well planned.
You need to not only think it out but also plan it out and have an emergency plan in case it spreads too far, too fast. Plus it doesn't hurt to have a backup plan to extinguish it in case you no longer have control over it.
Your online profiles and accounts shouldn’t just rot. They need to be removed and all traces proving its existence also doused out. Like any good woodsman or woman will tell you: A single campfire can destroy a forest.
This is why you must always plan your accounts and profiles out. Like a campfire left alone in a forest, a single account or profile can destroy an entire life. Any one account and/or profile can devastate an entire person’s public image. Yes, in theory, everything will remain cached, copied or saved on some server till the end of days however there are some options still left for you to explore.
You have an online footprint and anyone can find it, there’s nothing else to say other than that there are services for doing background checks on everyone and everything for any reason(s). You have a digital trail dedicated to all your old fanfics, photos or images and online debates… anyone who has enough patience can find out who you are online and where you are offline.
There are steps that you can take to prevent your online footprint from growing. But nothing short of doxing yourself ([1] self doxing) and learning just how much of your information is online can help.
One issue is how you interact with others online.
Another issue is how much information you post on the internet.
All we can do is give you some simple suggestions before providing you the tools needed to self-dox.
Once done, save this information somewhere on your computer or a USB where other's won't find it. Hold onto this until you've read the rest of this guide as this information will help you delete and opt-out of as much as possible.
• Self doxing isn’t the act of doxing oneself and posting dox for all to see, it’s the opposite. It’s the act of using the tools, tactics and knowledge often used in doxing to “meta-dox” oneself. This act's done in private, not in the public's eye. You're to find and delete any traces or information that's found through the self-dox. This is to prevent possible doxing in the future. (E.G: Opting out and having your information deleted from Spokeo, or deleting an old account you’ve associated with your real name).
**Remember**: Before deleting any information, read this guide fully. You’ll need to do so to understand what you’re about to partake in and work on.
___References___:
https://www.wired.com/2012/07/ff_kaspersky/
https://www.wired.com/2012/04/ff_klout/3/
https://paranoidsbible.tumblr.com/
https://www.hackcommunity.com/Thread-DoX-DoXing-and-How-To-Prevent-It-being-anonymous-within-your-identity?pid=73506
https://minichan.org/topic/7866
https://www.hackcommunity.com/Thread-Tutorial-Maxx-s-Anti-Dox-Handbook?pid=180063
https://offbeathome.com/2013/03/how-to-keep-your-personal-information-private
https://netsecurity.about.com/od/perimetersecurity/a/How-Criminals-Use-Google-Maps-Street-View-To-Case-The-Joint.htm
https://www.abine.com/blog/2012/how-to-delete-things-from-the-internet/
https://null-byte.wonderhowto.com/inspiration/dont-get-doxed-5-steps-protecting-your-private-information-web-0133806/
https://thebot.net/general-tutorials/233339-how-doxing-works-protect-yourself/#post2372672
https://soyouwannalearnhowto.wordpress.com/2011/05/22/so-you-wanna-learn-how-to-prevent-doxing/
https://school-of-privacy.com/selfdox
++++++++++++++++++++++++++++++++++++++++++++++++
===Finding your Digital Footprint: A Dossier===
The reason to why we’re opting to use a dossier is because it’ll allow you to sort the information that you find on yourself. It's an easy-to-use format, too. This serves as your go-to document, which we recommend that you save in a .txt.
We know many will not believe this to be useful as many will say you can't stop the government or corporations from spying on you; however corporations and government aren't out to ruin your life or financial security. The people you have to worry about getting a hold of this information are civilians. They'll contact employers, family and friends all under the guise of social justice or correcting perceived wrongs. Anyone with the right combination of information can guess passwords and security questions, thus accessing your accounts and e-mail addresses to further ruining you and what you’ve built for yourself.
The below contains some simplified descriptions of why each piece of information is useful.
Name: Even if common, a person’s name (first and/or last) can help verify information.
Age: Can confirm certain information.
Birth date: Used to verify age and name, plus other information.
Location: A general location, like a city or state, can help locate an address.
Phone number: Verify name and location.
Home address: The home address can usually turn up images and misc information through Google and realtor sites.
Possible relations: Relatives, significant others and friends.
Usernames: Using the same username over and over again can create a trail.
E-mail addresses: The e-mail address can lead to many things, like accounts or possible data-dumps.
Accounts: Links to accounts found on various websites can be used to keep a list of where you’ve been.
Websites: Most likely has information you don’t realize, like your site’s whois.
Misc information: Miscellaneous pieces of information that may seem crucial or of interest.
Possible accounts: Similar username or other items that seems to be possibly related.
Images: Can verify accounts; find Exif data…ETC.
Make two dossiers.
One with the information you know and recall, then a second one with the information that you've found online through the use of this guide. Remember to keep these two separate once done as you don’t want to contaminate the information that you remember with the information that you’ve found.
Compare them only after you've read this guide fully.
___References___:
https://en.wikipedia.org/wiki/WHOIS
++++++++++++++++++++++++++++++++++++++++++++++++
===Finding your Digital Footprint: Resources===
It’s important to keep track of the information found through the use of the provided dossier. We suggest that you also keep track of how each piece of information was found, as well as what led you to that discovery. This way you’ll be able to provide us with more insight and knowledge on how to prevent information from leaking besides helping us figure out how to remove it.
Remember, though, it isn’t who you are but who you used to be and what you’ve once said. This is what most people look for when they wish to dox someone. It's the key to ruining someone’s image or brand, no matter how liked they are online. Knowing what someone said or did in the past will help ruin their present self and devalue their credibility.
Now, before you start, put yourself into the shoes of a stranger and think back to previous scenarios or cases where you’ve heard of doxing. The reason we ask this is simple: To see just how varied doxing can be and just how unethical it can get at times.
Think of it like this: Imagine someone you’ve argued with and them being so thoroughly upset they’re now wishing nothing short of a pox upon your genitals or the death of your dog. This person has decided to track down every piece of information possible on you that exists online.
This hatred is what usually drives people onward toward their goal of doxing. They need to find information on someone and put them in their place or it’s because they believe it’s their moral obligation to track down those who wander away from the status quo or go against the will of a group.
Once you get into this frame of mind, don’t think of the information you know, but search for what you don't. Search for items posted in the present and past. You must find this information and use it. Add it to your dossier. You'll get a glimpse of what others see when they comb through your blog and internet past.
Now, to make this simpler for you, we're going to end this part with a links and miscellaneous resources.
Username:
* https://www.namechk.com/
* https://www.knowem.com/
* https://www.namecheckr.com/
* https://www.checkusernames.com/
General:
* https://www.spokeo.com/
* https://www.pipl.com/
* https://www.wink.com/
* https://www.peekyou.com/
* https://www.yoname.com/
* https://www.linkedin.com/
* https://www.search.yahoo.com/
* https://www.google.com/
* https://www.bing.com/
* https://www.reddit.com/
* https://www.aad.archives.gov/aad/series-list.jsp?cat=GS29
* https://www.numberway.com/uk/
* https://www.vinelink.com/vinelink/initMap.do
* https://www.jailbase.com/en/sources/fl-lcso/
* https://www.publicrecords.onlinesearches.com/
* https://www.www.abika.com/
* https://www.www.freeality.com/
* https://www.radaris.com/
* https://www.twoogel.com/
* https://www.advancedbackgroundchecks.com
* https://www.yellowpagesgoesgreen.org/
* https://www.Intelius.com/
* https://www.PublicRecordsNow.com
* https://www.Smartzip.com
Social Networks:
* https://www.twitter.com/
* https://www.facebook.com/
* https://www.deviantart.com
* https://www.xanga.com/
* https://www.tumblr.com/
* https://www.myspace.com/
* https://www.yasni.com/
* https://www.socialmention.com/
* https://www.whostalkin.com/
* https://www.linkedin.com/
* https://www.formspring.me/
* https://www.foursquare.com/
* https://www.about.me/
* https://www.profiles.google.com/
* https://www.blogger.com
* https://www.photobucket.com/
* https://www.quora.com/
* https://www.stumbleupon.com/
* https://www.reddit.com
* https://www.digg.com
* https://www.plixi.com
* https://www.pulse.yahoo.com/
* https://www.flickr.com/
Location:
* https://www.whitepages.com/person
* https://www.maps.google.com/
* https://www.411.com/
* https://www.192.com/
* https://www.zabasearch.com/
* https://www.zillow.com
People:
* https://www.123people.com/
* https://www.peekyou.com/
* https://www.peoplejar.com/
* https://www.anywho.com/whitepages
* https://www.yahoo.intelius.com/
* https://www.findermind.com/free-people-search-engines/
* https://www.ipeople.com
* https://www.facebook.com/directory/people/
* https://www.skipease.com/
* https://www.zabasearch.com/
* https://www.wink.com/
* https://www.dobsearch.com/
* https://www.searchbug.com/
* https://www.nationwidecrafts.com/
* https://www.everyone411.com/
* https://wwww.Acxiom.com/
* https://wwww.MyLife.com/
* https://www.Zabasearch.com
* https://www.ussearch.com/
* https://www.peoplesmart.com/
* https://www.usa-people-search.com/
* https://www.spoke.com/
* https://www.SOBSearch.com/
* https://www.beenverified.com/
* https://www.peoplefinder.com/
Phone numbers:
* https://www.whitepages.com/reverse-lookup
* https://www.freecellphonedirectorylookup.com/
* https://www.fonefinder.net/
Images:
* https://www.tineye.com/
* https://www.saucenao.com/
* https://www.photobucket.com/
* https://www.revimg.net/
* https://www.iqdb.org/
Programs:
* Skype
Add-ons (for Firefox):
* Exif viewer
Whois:
* https://www.networksolutions.com/whois/index.jsp
Caches:
* https://www.archive.is (Can be used to make your own caches of pages)
* https://www.archive.org/
You may have come across similar links from such sites as insurgen.cc or maybe from an image board with an /i/nvasion or /i/nsurgency board. You could've even seen it on some blogger's how-to, but these links...? They're actually well known and have been the staple of a lot of lists and guides on how track a person or persons down.
These links will help you find your own information and thus help you dox yourself.
**Please remember**: This is but a sampling, if you wish to see a larger chunk of the iceberg that invades our privacy then look at the supplementary guides.
Please hold off on the opt-outs until you’ve read this whole guide. We’ve organized the opt-outs to help you speed along with the removal of your information and ask you to wait as we also have various tips and tricks to ensure you do it right.
___References___:
https://www.propublica.org/article/privacy-tools-opting-out-from-data-brokers
https://consumerist.com/2010/06/21/giant-list-of-data-brokers-to-opt-out-of/
https://money.cnn.com/galleries/2010/technology/1012/gallery.data_miners/index.html
https://www.privacyalerts.org/data-brokers.html
https://www.privacyrights.org/online-information-brokers-list
https://unlistmy.info/sites
https://consumerist.com/2010/06/21/giant-list-of-data-brokers-to-opt-out-of/
https://www.cnet.com/how-to/how-to-take-back-your-privacy-from-data-brokers/
https://silversteampunk.tumblr.com/post/70232779066/i-used-this-image-because-ive-seen-it-posted
++++++++++++++++++++++++++++++++++++++++++++++++
Finding your Digital Footprint: Tactics
When one looks for information online, there isn’t just one single way to go about it as it’s a mess of tactics, resources and searching until one’s fingers are raw from typing. Because of this, we’ve created a series of simple tactics for you to track down your information online. We also wish to show you how to counteract these tactics due to how commonly used they are by those searching for information on a target.
--------------------------------------
Applies to Tumblr only
* About Me Leads to About You:
Simple and fast, always the first thing you should do when going over a blogger’s profile--Look at the about me or description and see what information is there.
• Name?
• Age?
• Nicknames?
• Previous usernames?
• Links?
• List of tags or posts?
Whatever there is, it leads to valuable information that can pad out the dossier.
**Counteract**: Never use your real name online, nicknames, or anything of value. This should apply to any and all accounts you own.
* Counter Crawling:
Use a publicly displayed counter or your own to track someone’s IP and browser print down.
**To do this**: Check for a Statcounter or tracker made public, or use your own and bait the target. Now look at what information is displayed and/or look for /blog/username links. Use these to find meta-data like:
• Blogs
• IP address
• General location (ISP or host’s location)
• Referral information
**Counteract**: Many add-ons help prevent this, like Umatrix or Ublock Origin. You should always use one or more of these add-ons and also look into ensuring that if you host a site that you’ve sanitized your Whois.
* Tumblr Cataloging:
This is quite simple in all actuality as it only requires time, patience and lots of reading.
To start out, one goes to the target blog, then you comb through the /archive/ link or by finding the last page of a blog. In theory you need to find the oldest (the first) post made on the blog and from there, working your way up to most current, you go from page-to-page. You skim posts for key pieces of information that can be used to find information elsewhere or used in a search engine.
Things you'll look for:
• Exif data from images
• Linked image albums
• Alternate blog or account links
• E-mail addresses
• Wish lists
• Personal rants
• Family or pet names
• Real life locations or school names
The older the blog, the more likely there are pieces of information that can be used to find their accounts elsewhere online.
**Counteract**: Don’t be ignorant or rash, think before you post and watch what you post. Ensure you don’t leak real world information. Remember: Save images as PNG and always scrub the Exif data.
Be careful and post smart.
* Tag Hunt:
The trend of having to tag every post caused people to be obsessive with certain tags, and to profit from this, one has to check for a tag list or commonly used tags like ‘my face’ or ‘me’. Depending on whether Tumblr pulled an Imgur and removes exif data, images can lead to real world information.
**Counteract**: Post smart, save images as PNG and always scrub Exif data. Be general and misleading about things in reality (when discussed online). Swap real names for generic names or handles—High school is now your high school, not Mt. Rush High.
* Tag Search:
Search the blog’s username and/or title on Tumblr search and Tumblr’s tag search and you can also search previous or past usernames/titles. You can find a lot out on a blogger and who they hang out with by searching them on Tumblr. If they have a previous blog name/title, it can be found by using the “Tumblr cataloging” tactic.
Example:
1. Party H re-blogged and responded to Party B.
2. The post Party B re-blogged was from Party A. The post from Party A is on Party H’s blog.
3. Party H is the source but older posts (re-blogged by others) show it re-blogged from Party A.
4. This means Party H and Party A are one in the same and that Party H changed the name/title.
Searching their previous names/titles on Tumblr can and will usually lead to excellent information. Remember though, you’ll need patience and to take some time going through these tags.
**Counteract**: Don’t change your title/name or do so often enough to limit each change’s exposure.
You’ve done all that you’ve could on Tumblr; you’ve gotten some information… now what?
Well, it’s time to breakout Google or some other search engine and start using various combinations of the information that you’ve found to see what trails that you can uncover.
--------------------------------------------
General information and searching
* Account Hopping:
The older an account, the more likely it will link to another account somewhere else. Similar to a few of the Tumblr tactics, one just has to search tags, keywords, and comb through the accounts. Usually it’s a comment or even a keyword itself. This has better success on Wordpress or Blogger accounts, also in descriptions on profiles.
**Counteract**: Always wait a month before deleting an account. Remove any and all posts, texts, and information. Before deleting the text or posts, first fill them with random characters/text. This is to force a new cache from various search engine and services. This should render previous ones inaccessible and only leave traces of nothing.
**Example**: Instead of a lengthy diatribe against your old significant other, it’s ‘sldknlskndlfkndlkslfksldkfndslksdnflksklnfdslkfsdnklds’. Also, for images or videos, upload blank images and static filled videos.
* CTRL + U sourcing it:
Check custom layouts on various blogging platforms for websites and links.
Various sites allow individuals to add their own custom flair to things, for example a layout and separate page designs. You can find links to storage accounts or image upload services by checking the source. This usually leads to photobucket accounts, imageshack accounts or personal servers. It could also expose a cloud storage account that can be searched or forced into exposing more information.
**Counteract**: Use the month rule and the random text/character trick before deletion. You should also name all images randomly instead of using actual words. Don’t put anything in obvious order and always ensure your password is strong to prevent brute forcing or guessing.
**Note on passwords**: 8 to 12 characters long with random letters, numbers and characters.
* E-mail address surfing:
Using any number of websites or search engines, one can enter an email address to lookup. Using its variations (@gmail, hotmail, yahoo…ETC) you can find miscellaneous accounts. This can also lead to information and possible dead-accounts or addresses. You could use a dead address and resurrect it anew to claim accounts and to learn information like passwords and IPs or offline information.
**Counteract**: Use a different e-mail address for each account and ensure to have a separate secondary account for it. Don’t display your E-mail address and never give it out, or at least use a secondary-secondary as a fake for public display.
* Face snipping:
Find a picture of someone online. Crop out everything but their face. Using the (cropped) image of just their face and/or head, go to Tineye and see if you can find results. Usually you’ll be able to find accounts. Using this, you can find abandoned social media pages that contain information about relatives, schools and businesses.
**Counteract**: Never post your image online, ever. Also scrub exif data.
* Forum scouting:
Find an account on a forum; search the forum for more information.
Most forums have a search function that allows you to search a username plus keywords, it’s simple and quick.
Search specific things like:
• Social network names
• Usernames
• E-mails
• General keywords (example: email, account, art, location, school)
Double check posts for signatures or avatars that can be traced back to other accounts. If that isn’t possible, then check the user’s profile for a post counter that may or may not be clickable. This will usually lead to all their posts.
**Counteract**: One month wait before deletion, plus random characters in the posts. Also request the owner/mods/staff to delete account and all posts.
* Gaia sleuthing:
Go to their forums and search them, or profiles for similar usernames and information. Check against a search engine with things like “Username,” “Gaia,” “E-mail” and whatever else. This usually leads to various forums and other accounts. This tactic can also be applied to Neopets, among other sites.
**Counteract**: Follow the deletion trick of random characters…Etc. Don’t giveaway your items. Don’t donate your gold or cash. Just delete everything within the month rule.
* Photobucket jumping:
Just searching usernames against account links like ‘photobucket.com/user/-username-‘ or ‘photobucket.com/profile/-username-‘ to find an account. Once an account is discovered, people can search parts or the whole URL of any direct image link. This allows people to find where you’ve posted your images and thus your accounts.
**Counteract**: Delete your images and photobucket account. Don’t put a password on it and don’t let it idle…it’ll lasts forever. Remember to use the one month rule and blank image trick.
* Username searching:
Search the username using a search engine or one of several username check websites. Just find any and all accounts with a similar username and then check its information against that in the dossier.
**Counteract**: Never use the same username twice. Always change it, no matter what. Never share your accounts with anyone or announce your accounts elsewhere and never inter-link accounts.
--------------------------------------------------
Vanity Searching (Ego hunting/surfing | Kibozing)
In simplicity, vanity searching is the act of searching one’s own name or pseudonym on a popular search engine or the internet at large to find results on one’s self. Most individuals usually do this as a meta-checkmark on what information of theirs or concerning them appears on the popular search engines or websites accessible to the public.
Now vanity searching is a great tool to find those golden little nuggets of information that you didn’t know existed online. While many just stick to variations of their name, we’d like to suggest the below list of searches you can make plus some combinations to help you on your way to digital freedom.
Common Vanity Search Queries:
1. Full name (First, Middle, Last and/or marks JR/SR/2nd/ 3rd…etc)
2. First + last name
3. First name
4. Last name/home address
5. Name combinations + birth-date
6. Name combinations + home/street address
7. Name combinations + school
8. Name combinations + work
9. Name combinations + vote, voted or voting
10. Street address
11. Relatives names + name combinations
12. Usernames + name combinations
13. Usernames
14. E-mail addresses
15. E-mail addresses + usernames
16. Websites or accounts + usernames
17. Websites or accounts + e-mail addresses
18. Usernames + city or state
19. Name combinations + city or state
20. The above + IP addresses or ISP
21. The above + known leak or dump searches (E.G: Have I Been PWNED)
------------------------------
These tactics are but a sampling of what many people do on a daily basis to find the information of others. We just list the most common and easiest to do for you to help you find your online footprint but you shouldn’t believe that this is it, really look into variations and be creative when trying to find your own information… you’ll be surprised by just how much of it exists online.
___References___:
https://en.wikipedia.org/wiki/Egosurfing
https://haveibeenpwned.com/
++++++++++++++++++++++++++++++++++++++++++++++++
===Finding your Digital Footprint: Things to know and do===
This chapter is dedicated to providing you with various steps that you can take to prevent cross-referencing through multiple accounts. A single piece of information posted in one location can be used against you and lead to another account. If not taken into careful consideration, something as simple as your first name could lead to your inevitable doxing.
Imagine if you will that you have an account on a site about model trains. You signed up with your first name and used your old AOL e-mail address. Someone looking for you discovers you like trains; however all they have on you is an old username. They search this username, which is used in your old AOL e-mail address. They discover your model train account and first name. Search with various variations of your e-mail address and name, thus discover a newsletter of your town’s local hobby shop and model train group.
They now know your full name, your hobby group, your old e-mail address and several other pieces of information that, when combined, lead to your home address.
Congratulations, you have been doxed.
The below information serves more as a guideline than actual rules, which should be followed but can be modified or ignored based upon the individual and their privacy needs. These are just some ways to deter information from getting away from you and being used by others to discover your information. So, please, do see the below as some daunting task but a series of suggestions.
When leaving an account:
o When leaving, don’t announce it.
o Tell no one that you’re deleting your account.
o Delete your account only after a month of inactivity and delete it only after switching it to a *‘Dead E-mail address’.
• Note: An e-mail address used to take ownership of an account that you’re deleting/deactivating.
Steps to take before deleting an account:
o Before deleting anything, wait a month.
o Anything you can edit, do so with random characters and text.
o Images should be replaced with a blank temp image (pure color image).
o Videos should be replaced with either a solid color or static.
o Once a month is over, you can delete that account.
o But before doing so, delete the account’s items one by one.
o If you can’t delete something, ask the staff/owner/webmaster/mods to delete it for you.
o Stating that someone is stalking you is usually enough to remove the information.
o If they won’t remove, try to edit it once again with random text.
o If you can’t edit it, ignore it.
o If it’s a blog, change titles and/or usernames.
o Preserve the original URL or username on a blank blog or account.
o Never leave your old username or URL up for grabs.
On removing an old E-mail address:
o Never delete an e-mail address, simply switch accounts and other items accordingly.
o Mark everything else in it as spam, but only if you can’t unsubscribe.
o Log into it at least once a month to prevent deletion.
o You can most likely delete it after not using it around a year or two later.
o Always make sure the e-mail is no longer tied to any accounts or personal information.
o Always wipe it out like any other account by changing as much as possible to randomized text.
On account maintenance:
o Never use your real name.
o Never upload an image of yourself.
o Never use your real location.
o Never discuss your time zone.
o Never discuss your current time.
o Always use English, at all times.
o Never discuss events happening in your area.
o Never mention race or skin color.
o Never mention religion.
o Never mention sexuality.
o Never discuss your hobbies in great detail.
o Don’t talk about your fetishes or kinks.
o Accounts shouldn’t be cross-linked to other accounts/sites.
o If you do, make sure no username is the same.
o And make sure no e-mail address displayed is the same.
o Use a different e-mail address for each account.
o Keep accounts separate if not needed to be linked.
o Never link RP accounts to other accounts and social networking profiles
o Don’t mention how many pets you have or their names.
o The same applies to family members, neighbors, friends and significant others.
o Scrape as much information off of something as possible.
o Boil it all down to the core basics.
o Never keep an account longer than a year (some exceptions apply).
On talking to strangers:
o Never display your messenger, Skype or chat names anywhere online.
o Give it to others only if they ask you (and you trust them).
o Keep all forms of instant messaging and chat private.
o Don’t save logs.
o Only give out to trusted individuals.
o This applies to IRC channels and chat setups.
o Lock down as much as possible.
o Never use real names or information, ever.
o Don’t tell other people who you talk to online.
o Never place your full name on Skype (or any service).
o Limit the profile you have on Skype (and any other service).
o Make sure all options are set to private.
o If it can’t be set to private, then set to contacts.
o Like Skype, any chat client or instant messenger should be locked down.
On behavior:
o You’ll most likely have to change the way you behave online.
o Sharing interests is fine, but getting too obsessed is bad.
o Never admit to liking any specific thing.
o This can help people tie other accounts to you.
o Admitting to things like your favorite food can be used to trace too.
o In general, you need to keep yourself and your information limited when on the internet.
o Instead of admitting to liking a song, just say you like the band.
o This applies to specific bands in smaller genres, too.
o Or any form of entertainment that you specifically like.
o Instead of specific parts you like in a game, you just like the game.
o Remember: don’t talk about your location.
o Don’t talk about your general location in detail.
o Don’t mention what it’s known for (produce, exports, colleges, universities…etc).
o Don’t make mention of recent weather, as that can be used in junction with other information
o Don’t say the exact time.
o Be wary of saying exactly what the temperature is.
o If the person you’re talking to uses Celsius, then tell the temp in Celsius.
o If the person you’re talking to uses Fahrenheit, then tell the temp in Fahrenheit.
o Don’t make mention of general information like school names or street names.
o Don't make mention eateries/restaurants as they can be unique to your location.
o Always refer to your city/town as a college town.
o Never post selfies.
o Never post nudes.
o Never post porn.
o Never post erotica.
When getting personal:
o Don’t discuss siblings or family members to great extent.
o Don’t drop pet names.
o Don’t drop the name of anyone related to you.
o Don’t drop the name of friends.
o Don’t drop the name of politicians.
o Don’t drop the names of people you’ve had relationships with.
o Keep age to a general rounded number, like, the 20s…etc
o Keep personal descriptions down.
o Keep weight to a more general descriptor (overweight, obese…etc).
On talking about life experiences:
o Never do so in the first place.
o If you do, don’t let incriminating evidence be traced back to you.
o Or at least make sure you can discuss such things in a secure environment.
o Also don’t attach anything about you to your online personas and/or accounts.
On using custom domains:
o Ask your host about Whois masking.
o If they don’t offer it, check into other services.
On online relationships:
o Don’t do online dating.
o Don’t sext.
o Don’t cyber.
o Don’t do erotic roleplay.
o Don’t go to online dating websites.
o Don’t take part in relationship, dating, sex…etc help sites/forums/chats.
Just use common sense.
++++++++++++++++++++++++++++++++++++++++++++++++
===Deleting Your Information===
Using what you now know from the above chapters, it’s time to work on deleting your information, old account and general internet presence. While it may seem hard to do and quite the task to take up, understand it’s for the greater good. By doing this now, you’ll have less to worry about in the future and won’t have to worry about things coming back to haunt you. No more embarrassing teenage antics or silly digital slap fights, only a clean and fresh digital presence that the civilian population and potential employers can critique or use against you.
This chapter will be quite short as all the information above should not only be beneficial but enough to get you going, however there are still a few things to point out just so you’re prepared to dive in and work yourself ragged to cover up the fact that you used to like a certain animated series.
First off, before we begin ensure you’ve read the above fully and understand what’s been written, from there compare the dossiers and see what information you know VS the information you found. Now ignore any people search engines and focus only upon accounts. Pick an account and work on that one only, as that’s going to be the only account that you’ll be working on until you’ve finished ‘sanitizing’ it.
To recap, remember the One Month Rule:
1. Wait a month before deleting an account.
2. Within that month, hide and/or delete all comments that you can that aren’t yours.
3. Modify and change everything that you can.
4. Any editable text should be randomized (E.G: wodegnoi2n402)
5. Images should be changed to a blank or solid color image.
6. Videos should be changed to a solid color or static video.
7. All CSS and HTML, that’s editable, should be wiped out.
8. Change the e-mail address used to register the account with something else.
9. Check your e-mail addresses against HIBP to ensure nothing has been compromised.
10. Repeat the above steps for each account and e-mail address.
Once done, before deleting the account, head over to the Internet Time Machine and contact them at this e-mail address: [email protected]. Request their archives of your account to be removed, simply state it’s for privacy concerns (or if you’re being stalked or doxed, state safety) and provide them a screen-cap of you being logged into the account. If the account is attached to any groups or similar items, and you’ve made or own them, please also request the removal of those archives too.
Now, while you’re waiting for the month to finish up, move onto your next account and repeat the above steps and recommended procedures. Keep this up until all of your accounts have been modified, sanitized and deleted (once the full month is up). If your Social security number, a credit card or debit card number or any other private information is attached to it (or if you own some digital content exclusive to that account) don’t delete it, yet, just follow the above and let it rot (sit and not touched) in case you need to access that account again.
With accounts like Discord, Skype and Tox (among similar items) can be removed following the above yet with minor modifications. You don’t want to delete these accounts, just nullify them and cut all contact with anyone attached to them. You have to remove all custom labels/nicks/nicknames for your contacts, block each one and delete them from your contact/friends list. Then, fill it out all profile entries with underscores ( __ ) if you can blank them out or delete items you’ve entered previously. Ensure everything has been changed to private or contact, too.
You should be able to use the above plus the previous chapters in order to remove and sanitize any of your information that exists on the internet. Slight modifications may be needed, however this should be enough for you to cover your tracks and prevent any potential dox or attacks. Accounts like Steam and Origin shouldn’t be removed or deleted (even if you could) as these are either tied to private information or purchases. Just blank out as much as possible and adjust profile settings to whatever max privacy is considered. You shouldn’t have these accounts mad public in the first place; always ensure they’re set to invisible and restricted access or no access.
Now, everything should hopefully have been removed and you’ve been able to do everything in your power to lessen your digital footprint. Move onto the below chapter, but remember this: Keep a list of all your usernames that you’ve used, these can be applied to another tactic in later guides.
++++++++++++++++++++++++++++++++++++++++++++++++
===Opt-out Master-list===
The purpose of this chapter is to provide you with an up-to-date listing of any and all opt-outs for people databases or search engines. This means you’ll be able to opt-out of not only known data brokers but several unknown brokers. You'll even cut down on physical mail and e-mail. Many feel this isn’t needed as you have to provide information to remove information, but this is what’s needed. Not just by the law but also for business records. Opt-outs are just you acknowledging a contract made without your knowledge.
Instead of ignoring them, you’re stating you don’t want them using or selling your information. It not only helps reduce your online footprint but also helps you cut back on carbon emissions and overall exposure across the internet with things you didn’t know exist (E.G: Opt of one site and others follow suite).
For now, we've only include the online opt-outs in this PDF. We suggest you finish those and those alone as most of them are interlinked to many of the phone and fax opt-outs. Once you finished those you should wait a month or two before doing other opt-outs. A lot of information will be expunged as you opted out of one or two other sites.
Online Opt-outs:
These are opt-outs that can be done online through forms or simple links without a pay wall.
https://www.10digits.us/
https://www.10digits.us/remove
• Requires photo ID upload + e-maill addess + page link.
• Make sure to search using all three methods.
• Repeat for each immediate family member in your residence.
https://www.411.info
https://www.411.info/contact/
• Find your info, copy the link.
• Go to the contact link and ask them to remove your info.
• Provide the link(s) in the message.
https://www.500millionphonerecords.com/
https://www.phonedetective.com/PD.aspx?_act=OptOut
• Follow the instructions on the Phonedetective opt-out link.
• Repeat for each individual in household and any and all numbers you've owned or recall owning.
https://www.accutellus.com/
https://www.accutellus.com/opt_out_request.php
• Follow the instructions on the opt-out page, repeat for all individual in household.
https://www.Acxiom.com/
https://www.isapps.acxiom.com/optout/optout.aspx
(Cookie opt-out can be ignored if you install ad blocking and privacy based add-ons on your browser)
• For the actual opt-out, just follow the above link and follow the instructions, repeating it for each residence in your house.
• After each successful entry fill out, you’ll be taken to a new page with a capatcha and a field to confirm the e-mail address.
• Log into your e-mail account, find the confirmation e-mail, and follow the link provided.
• Repeat for each individual in household.
https://www.addresses.com/
https://www.addresses.com/optout.php
• Follow instructions on page, repeat for each individual in household.
https://www.addresssearch.com/
https://www.addresssearch.com/remove-info.php
• Follow instructions on page, repeat for each individual in household.
https://www.allareacodes.com/
https://www.allareacodes.com/remove_name.htm
• Follow instructions on page, repeat for each individual in household.
https://www.archives.com/
https://www.archives.com/ga.aspx?_act=Optout
• Follow instructions on page, repeat for each individual in household.
https://www.checkpeople.com/
https://www.checkpeople.com/optout
• Follow instructions on page, repeat for each individual in household.
https://www.corporationwiki.com/
https://www.corporationwiki.com/profiles/public
• Follow instructions listed on their website.
• Very few cases, only for businesses and their executives.
https://www.coxtarget.com/
https://www.coxtarget.com/mailsuppression/s/DisplayMailSuppressionForm
• Wait until you’ve received your next ‘ValPak’ packet\envelope.
• Go to the opt-out form\link above.
• Enter information as it is on the envelope.
• You’ve opted out.
https://www.datalogix.com/
https://www.datalogix.com/privacy/#opt-out-landing
https://www.aboutads.info/ (More info here)
• Find this sentence ‘If you wish to opt out of all Datalogix-enabled advertising across channels including direct mail, online, mobile and analytic products, and click here.’
• Follow directions, repeat for each resident of household.
https://www.dexone.com/
https://www.dexknows.com/
https://www.dexpages.com/index.asp?
https://www.dexone.com/privacy-policy
https://green.dexknows.com/DexGreen/selectDexAction.do
• Enter zip code.
• Follow directions.
• If you can’t opt-out, you can do so VIA the Yellow Pages opt-out.
https://www.directmail.com/
https://www.directmail.com/directory/mail_preference/
• Follow directions in second link.
https://www.dmachoice.org/
https://www.dmachoice.org/register.php
• Follow directions on website.
• Have to create an account for each member of household.
https://www.dobsearch.com/
• Search yourself; address; phone number…etc
• Find info.
• Look for ‘Is this you? Manage your listing!’
• Follow instructions (You’ll need a valid e-mail address + landline or cell).
• Repeat for all residents in house (One per 24 hours).
https://www.donotcall.gov
https://www.donotcall.gov/register/reg.aspx
• Follow directions.
• Enter phone numbers, cell and/or landline, and an e-mail address.
https://www.ebureau.com/
https://www.ebureau.com/privacy-center/opt-out
• Same as DMA choice opt-out, but no accounts; you’ll have to do this with previous addresses too.
https://www.emailfinder.com/
https://www.emailfinder.com/EFC.aspx?_act=Optout
• Follow instructions on screen.
• Repeat for each resident in household.
https://www.epsilon.com/
https://www.epsilon.com/consumer-preference-center
https://www.optoutprescreen.com
• Go to third link and follow their process (only needs to be done once).
https://www.everify.com
https://www.everify.com/legal.php#2
https://www.everify.com/legal.php#remove
• Follow instructions on page, repeat for each individual in household.
https://www.experian.com/
https://www.experian.com/privacy/opting_out_preapproved_offers.html
https://www.optoutprescreen.com
• Go to third link and follow their process (only needs to be done once).
https://equifax.com/
https://help.equifax.com/app/answers/detail/a_id/2/noIntercept/1/kw/prescreen
https://www.optoutprescreen.com
• Go to third link and follow their process (only need to be done once).
https://www.everyone411.com/
• Go to contact page @ https://www.everyone411.com/contact
• Provide listing links.
• Request removal.
• Repeat for all individuals in household.
https://www.freephonetracer.com/
https://www.freephonetracer.com/FCPT.aspx?_act=OptOut
• Online opt-out form, follow directions.
https://www.health.com/health/
https://subscription.timeinc.com/storefront/privacy/health/generic_privacy_form_offline.html?dnp-source=E%20AND%20
https://subscription.timeinc.com/storefront/privacy/health/generic_privacy_form_online.html?dnp-source=E
• Fill out with your information, repeat for each individual in your household. Make sure to check all boxes in the two opt-out links.
https://www.ims-dm.com/
https://www.ims-dm.com/cgi/optoutemps.php
• Follow directions on second link.
• Enter up to three emails.
• Fill captcha.
• Clear cache and repeat as necessary.
https://www.infousa.com/
https://www.infousa.com/StaticPage/PrivacyPolicyInfo.htm
• Look for: Opt Out Policy–Upon a visitor’s request, InfoUSA Inc.
• Read it carefully, scroll down and find the ‘E-mail form’.
• Fill it out, include your name, birth date, address and phone number. Request all information of yours to be removed, especially anything related to the info you just provided.
https://www.infospace.com/
https://www.support.infospace.com/privacy/
• Search for ‘Choice/Opt-out’.
• The link there is old, use this one: https://infospace.com/contact/index.html
• Select 'General inquiry'.
• Provide your name, birth date, address and phone number.
• Request all information of yours be removed, especially anything matching or related to information you just provided.
https://www.innovis.com/
https://www.innovis.com/InnovisWeb/pers_lc_opt_out.html
https://www.optoutprescreen.com
• Go to third link and follow their process (only needs to be done once).
https://www.instantpeoplefinder.com/
https://www.instantpeoplefinder.com/optout.php
• Follow on page instructions, repeat for each individual in household.
https://www.locatefamily.com/
https://www.locatefamily.com/contact.html
• Search for your name on the left side of the site.
• You’ll find a page or pages containing Names, addresses and phone numbers.
• Find yours; take note of the number next to it.
• Go to the contact page.
• Scroll down for the opt-out\removal form.
• Follow the directions.
• Make sure to provide the information you want deleted in the ‘Comments’ box.
• Repeat for each individual in household.
https://www.lookup.com/
https://www.lookup.com/optout.php
• Go to the opt-out link.
• Follow the directions.
• Repeat for each individual in household.
https://lycos.com
https://info.lycos.com/resources/privacy-policy
• Search for: How can you access or edit your information?
• Follow directions.
https://www.mobilephoneno.com/
https://www.mobilephoneno.com/help.htm
• Search for: How do I delete my entry?
• Follow directions.
https://www.militaryavenue.com/
https://www.militaryavenue.com/Contact.aspx
• Businesses only.
• But, if you have your information up there, somehow.
• First find said info.
• Go to the contact page.
• Select, from the drop down, “Incorrect Business information”.
• Provide link, info, and ask for removal.
https://www.myyp.com/
https://www.yellowpagesoptout.com
• Follow instructions on second link.
https://www.nationwidecrafts.com/
• Find listing.
• Click the suggestion link/light bulb icon.
• Request removal.
https://www.orientaltrading.com/
https://www.orientaltrading.com/ui/help/processRequest.do?requestURI=link.removeForm
• Follow instructions on second link.
https://www.peekyou.com/
https://www.peekyou.com/about/contact/optout
• Search for yourself.
• Locate your profile and right-click then select 'copy link'.
• Then open a new tab and go to their opt-out page and follow the instructions provided.
• Repeat with each individual in household.
https://www.peepdb.com/
• Enter full name + state.
• Look for city + state in results.
• Can confirm by partial phone number listed.
• Click your result.
• Scroll down.
• Click ‘Remove This Listing’.
• Follow directions.
• Takes 10 business days.
• One request + IP every 3 days.
• Repeat with each individual in household.
https://www.peoplebook.com/
https://www.peoplebook.com/support.htm
• Search for your people book’s results.
• Confirm it’s yours.
• Grab link.
• Go to the support link.
• Follow directions.
• Repeat for each individual in house.
https://www.peoplefinder.com/
https://www.peoplefinder.com/manage/
https://www.peoplefinder.com/optout.php
• Go directly to the opt-out link.
• Fill in your information.
• Select from the drop down ‘General privacy concerns’.
• Enter the code word and click submit.
• Repeat for each individual in household.
https://www.peoplefinders.com/
https://www.peoplefinders.com/manage/default.aspx
• Search your first, middle and last name in search.
• State + city, too.
• Find your listing, click ‘this is me’.
• Skip the AD and\or sale section.
• Takes anywhere from an hour to a month.
• Repeat for each individual in household.
https://www.peoplesearchpro.com/
https://www.peoplesmart.com/optout-go
• Go directly to Opt-out.
• Enter your name + city and state.
• Find it, click it, and follow directions.
• You will have to make an account.
• Repeat for each individual in household.
https://www.peoplesmart.com/
https://www.peoplesmart.com/opt-out?
• Follow the People Smart opt-out instruction.
• You’ll be shown a page of results, locate yours.
• Click the ‘This is me’.
• Look at the ‘Business’ listings, find anything of yours and click the “This is me” or skip the step if none exist.
• Uncheck all options, except the last two.
• Click ‘Save Settings’.
• It’ll have you create an account, make sure to use a unique password only for this site and use nowhere else.
• Repeat for each individual in your household (sans the account).
• Repeat search, but this time with home address applied.
https://www.peoplewise.com/
https://www.peoplewise.com/show/optoutdisclaimer
• Go straight to the opt-out link.
• Make sure JS and Cookies are enabled.
• Follow the steps; make sure to read the red text.
• When you find your list, click the ‘Removal’ test under the blue button.
• When you’re on your page, within the red text, is a blue link, click it.
• Enter your email address + security code.
• Repeat for each individual in household.
https://www.phonebook.com/
https://www.whitepages.com/
https://www.whitepages.com/privacy_central#6
• Go to Whitepages.com
• Create an account.
• Search for your information VIA address, name, phone number...etc
• Claim each and every piece of information that's confirmed as yours.
• Verify through e-mail and phone.
• Then go to your profile.
• Scroll down and request your information to be hidden\removed from the directory.
• Follow the on screen prompts.
• Logout, clean cache.
• Create an account for each individual in household, repeat until finished.
https://www.phonebooks.com/
• Search your name + city and state.
• Find your listing in the results.
• Click on said listing.
• Locate ‘Remove this person’.
• Follow directions.
• Repeat for each and every individual in household.
https://www.phonedetective.com/
https://www.phonedetective.com/PD.aspx?_act=OptOut
• Go directly to opt-out page, follow directions.
• Repeat for each individual in house.
• Also repeat with each phone number you have or recall having.
https://phonenumber.com/
https://www.whitepages.com/
https://www.whitepagescustomers.com
https://www.whitepagescustomers.com/draft-how-do-i-remove-my-people-search-listing/
• Create an account .
• Search for your information VIA address, name, phone number...etc
• Claim each and every piece of information that's confirmed as yours.
• Verify through e-mail and phone.
• Then go to your profile.
• Scroll down and request your information to be hidden/removed from the directory.
• Follow the on screen prompts.
• Logout, clean cache.
• Create an account for each individual in household, repeat until finished.
https://www.poedit.org/
https://www.poedit.org/auth/removal_request.html
• Search for your page/information.
• Take link/URL.
• Copy it to the appropriate area listed in the second link.
• Submit.
• Find confirmation e-mail in inbox.
• Repeat for each individual in household.
https://www.privateeye.com/
https://www.peoplefinders.com/manage/
• Go to the People Finders link.
• Enter your information.
• On the results page you can refine your searches with age + birth-date.
• Find your results and click ‘This is me’.
• Follow instructions.
• Repeat for each individual in household.
https://profileengine.com/
https://profileengine.com/#/help
https://profileengine.com/#/claimprofile
• Search for profile.
• Look for the claim profile option.
• If not present, try the claim profile link above.
• Follow instructions.
• Repeat for each individual in household.
https://pub360.com
https://pub360.com/s/faq
• Search for your name.
• In results, look for the 'Information Removal' tab.
• Follow instructions provided.
• Repeat for each individual in household.
https://radaris.com/
https://radaris.com/removal/
https://radaris.com/page/how-to-remove
• Search for a name.
• On the search results page, select the name that is most appropriate.
• On the profile page, click the down-arrow to the right of the name and select ‘Control Information’.
• From the information control page, choose ‘Remove information’.
• Here you can choose to remove all information, or to delete specific records.
• Confirm your real name matches your account and profile name.
• Enter your cellular phone to receive a verification code.
• Once the code has been entered, the profile will be private.
• Repeat for each individual in household.
https://www.redplum.com/
https://www.redplum.com/tools/redplum-postal-addremove.html
• Follow the instructions provided on the second link.
• Per known address.
https://www.reversephonelookup.com/
https://www.reversephonelookup.com/remove.php
• Go to second link.
• Follow instruction provided.
• Repeat for all known and owned phone numbers.
https://www.searchbug.com/
https://www.searchbug.com/help.aspx?WHAT=people
• Search for your name + city and state.
• If ‘Free record’ is shown, you can click the garbage can\remove link to have it removed.
• Repeat for all individuals in house.
• Note: Premium records can't be removed through this process as they require manual removal and cost payment to do so.
https://www.Spokeo.com
https://www.spokeo.com/optout
• Go to Spokeo.
• Search your First, middle and last name.
• Find your profile/listing by go to the bottom of the page and select ‘open advance filter’.
• Fill out your information.
• Find your profile/listing, copy the link (note: Right click+ copy link to have a ‘Clean link’ copied).
• Go to the Opt out link.
• Follow instructions to opt-out.
• Repeat for each individual in house.
• Hint: You’ll need a different e-mail address after so many removals.
• Hint: You may have multiple profiles/links due to previous addresses.
• Hint: Make sure HTTPs is not at the start of the link, if it is just remove the 'S'.
https://www.usa.com
https://www.peoplesmart.com/
https://www.peoplesmart.com/opt-out
• Follow the People Smart opt-out instruction.
• You’ll be shown a page of results, locate yours.
• Click the ‘This is me’.
• Look at the “Business” listings, find anything of yours and click the “This is me” or skip the step if none exist.
• Uncheck all options, except the last two.
• Click ‘Save Settings’.
• It’ll have you create an account, make sure to use a unique password only for this site and use nowhere else.
• Repeat for each individual in your household (sans the account).
• Repeat search, but this time with home address applied.
https://www.usa-people-search.com/
https://www.usa-people-search.com/manage/default.aspx
• Go to the ‘Manage’ link.
• Enter your information.
• Find your listing.
• Enter Captcha and tick both boxes.
• Repeat for each individual in house.
https://www.usbizplace.com/
https://www.usbizplace.com/contact-us.html
• Find your listing with your information.
• Follow directions on the contact-us page.
• Repeat for all listings of yours you wish to remove.
https://www.webcrawler.com/
https://www.webcrawler.com/support/privacypolicy
https://www.webcrawler.com/support/contactus
• Go to Webcrawler.com, search for your info.
• Select link + note its order in the listing.
• Contact them at the 'Contact us' link.
• Request removal due to privacy concerns.
• Repeat for each individual in household.
https://www.whitepages.com/
https://www.whitepagescustomers.com
https://www.whitepagescustomers.com/draft-how-do-i-remove-my-people-search-listing/
• Create an account.
• Search for your information VIA address, name, phone number...etc.
• Claim each and every piece of information that's confirmed as yours.
• Verify through e-mail and phone.
• Then go to your profile.
• Scroll down and request your information to be hidden\removed from the directory.
• Follow the on screen prompts.
• Logout, clean cache.
• Create an account for each individual in household, repeat until finished.
https://www.valassis.com/
https://www.valassis.com/1024/Contact/MailingListRemoval.aspx
• Follow instructions on second link.
• Repeat for all known addresses.
https://www.valpak.com/
https://www.coxtarget.com/mailsuppression/s/DisplayMailSuppressionForm
• Wait till next envelope comes in the mail.
• Enter the info exactly as it is on the envelope.
• Repeat for all known addresses.
https://www.wyty.com/
https://www.wyty.com/optout.aspx
• Enter cell number (or phone number).
• Select 'Request'.
• Should be removed within 24hrs to a month.
• Repeat for all known numbers.
https://www.yellowbook.com/
https://www.yellowpagesoptout.com/
• https://delivery.ypg.com/en/US/Home/Index/ (Canada opt-out).
• Follow directions on 'Yellowpagesoptout' link.
• Enter zip\area code.
• Create account.
• Select items to opt-out.
• Repeat for all known addresses.
https://www.yellowpages.com
https://www.yellowpagescom.intelius.com/optout.php
• Fill out opt-out form.
• Repeat for each individual in household.
https://www.yellowpagesgoesgreen.org/
https://www.yellowpagesgoesgreen.org/terms_of_service.php?#privacy
• On the page with your information, look for ‘Are you the business owner’.
• Click it, select ‘Delete\remove listing’.
• Simply state your privacy concerns.
• Repeat for each individual in household.
https://www.ziplocal.com/
https://ziplocal.com/online-privacy-policy/
https://www.ziplocalonline.com/manage-listings
• To update your listing, use the search box above to look for your business.
• When you locate your business, simply select the Update Business link and follow the instructions.
https://www.zoominfo.com/
https://www.zoominfo.com/lookupEmail
• You'll be asked to provide your e-mail address.
• They'll search your address against their database.
• You'll receive an e-mail concerning whether or not they've your e-mail address.
• If not, nothing to worry about, but if they do they provide a means to opt-out.
• Repeat for each individual in household.
---------------------------------------------------
Miscellaneous Opt-outs:
This list contains opt-outs that have no direct place but have proven useful.
https://www.ameridex.com/
https://www.ameridex.com/privacy.html (review privacy policy for more info)
1. Another website that wants you to send an e-mail or send direct mail\snail mail opt-outs.
2. Also needs court order or proof of potential harm.
https://archive.org/
https://archive.org/about/exclude.php
https://web.archive.org/web/20140812200246/https://www2.sims.berkeley.edu/research/conferences/aps/removal-policy.html
1. If you're allowed to modify your account or website's HTML, add this somewhere in between the <head> tags.
2. <META NAME="ia_archiver" CONTENT="NOINDEX, NOFOLLOW">
https://www.Bing.com
https://ssl.bing.com/profile/history?oma=toggle_off
1. Disable personalized nonsense and ads.
Remove your property's street view on Bing Maps:
1. Go to: https://www.bing.com/maps/
2. Type home address.
3. Get to street view.
4. Center squarely on house.
5. Look for (?) question mark near bottom right. Be careful as it can be hidden sometimes.
6. Click it.
7. Select ’Report an image concern’
8. You'll get a pop-up or new tab with a panoramic image.
9. Select your house, a little red square will appear then.
10. Voice your privacy concern, stating vandalism and potential break-ins by criminal elements who use online maps to scout\case potential targets.
11. Fill out the rest of the form + Capatcha, wait.
12. Save ticket (#) Number.
https://www.catalogchoice.org/
1. Join site with an e-mail and password used nowhere else.
2. Search for the catalogs you’ve received.
3. Follow instructions to opt-out.
4. This site just organizes websites; they aren’t associated with any of them.
https://courtclick.com/
https://courtclick.com/terms.php
https://www.courtclick.com/support/
1. Look for ‘Opt Out Policy: Note that public records such as court records can be updated or corrected, but not removed unless expunged, sealed, court ordered or the like.’
2. You'll need to have your records sealed first.
https://www.emailtracer.com
https://www.emailtracer.com/tos.php
1. Search for ‘Opt Out Policy’.
2. Only under certain circumstances.
https://www.facebook.com/settings?tab=ads&view
1. Edit button in your Ads settings page, selecting No one and saving your changes.
https://www.Google.com
https://plus.google.com/settings/endorsements
https://www.google.com/ads/preferences/
https://history.google.com/history/
1. These links help make sure your Google data stays yours.
2. You can opt-out of having your likes and such shared.
3. Help limit ads and similar issues.
4. And even help prevent your history on your account from being given out.
Remove your property's street view on Google Maps:
1. Go to Google Maps and type in your address.
2. Bring up the street view of your property.
3. Look to the bottom right hand corner of the screen you should see an Icon Labeled ‘report a problem.’
4. Click on ‘report a problem.’
5. You will get a page labeled “report inappropriate street view.”
6. Look for the words “Privacy Concerns” and click on them.
7. If you want your house blurred, click on ‘my house.’ Then choose the option ‘I have a picture of my house and would like it blurred.’
8. Adjust the image and show Google which part of the photo needs blurred.
9. Type the verification code at the bottom of the page into the box provided and click submit.
10. Check back in a few days to see if the image has been blurred.
https://www.lexisnexis.com/
https://www.lexisnexis.com/privacy/directmarketingopt-out.aspx
https://www.lexisnexis.com/privacy/for-consumers/opt-out-of-lexisnexis.aspx
1. requires you to have a court order or police report, but you can remove \some\ information through the Direct Marketing Opt-out, though.
https://www.locatepeople.org/
https://www.locatepeople.org/index.php?xpath=privacy
https://locatepeople.org/index.php?xpath=lp_optout
1. Can Opt-out only by certain circumstances.
https://www.jailbase.com/
https://www.jailbase.com/en/opt-out/
1. Follow instructions on page, only under certain circumstances.
https://www.justmugshots.com/
https://support.justmugshots.com/forums/21326676-Removal-Services
1. An odd one, but has shown some use.
https://www.Publicrecordssearchonline.org
https://www.publicrecordssearchonline.org/new/faq.php
1. Search for ‘Q: How can I remove my information from the Public Records Database?’
2. Follow directions provided.
https://twitter.com/settings/security
1. Through your profile, go to your security settings page and uncheck the box under the promoted content section.
https://www.Yahoo.com
https://www.info.yahoo.com/privacy/us/yahoo/opt_out/targeting/details.html
https://www.search.yahoo.com/preferences/preferences?
1. Log into account.
2. Disable ads and personalized stuff.
https://www.Yahoo.com/maps
1. Visit https://www.Yahoo.com/maps
2. Drag the gray icon that resembles a person (top-right) to your street (If it won’t drag, then your street has not been photographed for Yahoo.).
3. Click on ‘report image’ at the bottom-left of the screen, it will take you to a different website.
4. Click on ‘request blurring,’ and follow the directions.
https://west.thomson.com/
https://static.legalsolutions.thomsonreuters.com/static/pdf/opt_out_form.pdf
*Only under special circumstances*
https://haveibeenpwned.com/
https://haveibeenpwned.com/OptOut
1. Check your e-mail accounts against HIBP
2. Opt-out once you copy the information to a .txt
++++++++++++++++++++++++++++++++++++++++++++++++
===Afterword===
So ends the Paranoid’s Bible.
No matter what you do, as long as you read this and the other PDFs/guides in the ‘Blue primer series’ you should be fine from citizens and most employers. You won’t be able to outsmart the government and your more tech savvy corporations, just yet. This guide and the ones found in the blue primer are meant to help you prevent spying from the average internet user—to prevent dox, stalking and identify theft.
We’ll make more PDFs/guides that’ll help you lessen even more of your data footprint and lower your chances of being spied on, however, for now… worry about the citizenry hunting you down like it’s the Salem Witch trials all over again.
We recommend you give the OPSEC guide a read and then checkout the Meta Data and You guide followed by Uncle Daddy’s Big Book of Deception guide. These three guides will further lessen your chances of being doxed and/or stalked besides providing a wealth of information on how to create some common canaries and red herrings.
54 notes
·
View notes
Note
tumblr user paranoidsbible has a few tips on how to lessen your chances of getting doxxed.
i skimmed the bit specifically on doxxing and it was helpful in determining what ive already done and what im too fundamentally tired as a person to do. thanks for the tip, though!
im not going to view doxxing as a serious risk. ive got under 170 followers, the gap between what i post and who it reaches and where those things would need to be for me to be worth doxxing is pretty large.
0 notes
Note
tumblr user paranoidsbible has quite a few tips on how to lessen your chances of getting doxxed.
Thanks anon I’ll have to check that out
0 notes
Text
Day-to-Day Invasions of Privacy 2.0
===Day-to-Day Invasions of Privacy===
Non-profit and free for redistribution
Written on December 11th | 2015
Published on December 11th | 2015
Edited on May 6th | 2017
For entertainment and research purposes only
++++++++++++++++++++++++++++++++++++++++++++++++
===DISCLAIMER===
The Paranoid's Bible and its writers hold no responsibility for the acts of others.
The Paranoid’s Bible and related guides are for research and entertainment purposes only.
Please visit our blog for more PDFs and information: https://www.paranoidsbible.tumblr.com/
++++++++++++++++++++++++++++++++++++++++++++++++
===Preface===
A loose series of daily invasions of privacy and how to counteract some of them, consider this a cheat sheet on what can leak your information and increase your overall informational footprint that can in turn increase your digital footprint.
++++++++++++++++++++++++++++++++++++++++++++++++
===Day-to-day invasions of privacy===
Every day our lives are being bombarded by CCTV and the interconnectivity of the growing mobile technology that the youngest of us must have, yet many of us are wholly unaware of the simple fact that these obvious invasions of privacy aren’t the most dangerous.
No, you see the most dangerous ones are the ones we take for granted.
**For example**: A DVD rental or a contest that you’ve entered.
These simple and almost daily used items or rituals and tasks actually put our information into more danger than flashing an elderly woman in front of a CCTV camera located directly in front of the local police station.
And that’s why this testament was mad--to simply show you just how much can actually invade your privacy and put your information into jeopardy.
++++++++++++++++++++++++++++++++++++++++++++++++
===The Daily Invasions of Privacy===
**Accounts**:
Any website that offers registration can and will gather a large variety of information on you, which can include anything given or not given by you, like your name, age, gender, address…etc
**Counteract: ** Besides reading over the TOS, rules and other similar guidelines, it helps to keep your profile as minimalistic and private as possible. There are also some configurations and add-ons you can use to help obscure your information and lessen data gathered. Remember OPSEC and compartmentalization.
**Aircraft Registrations**:
The FAA requires that all aircraft owners file an affidavit of ownership and each aircraft must also pass an airworthiness certification. The FAA also allows users to search aircraft ownership records by name on their website.
On top of this, most aircraft registration record contain the “N-Number” of the aircraft, besides the serial number, manufacturer’s name and model number, airworthiness, prior owners, other registered aircrafts as well as the name of the businesses that the individual owner of said aircraft owns besides their address and possibly more related information.
**Counteract**: You can’t, but possibly creating a trust to have said aircraft reregistered under might work. You must consult with your local law professionals to figure if this is possible.
**Amateur radio licenses**:
The FFC lists license information, which includes name and addresses, publicly for all to see and look up. Like most licenses, you won’t be able to use a P.O. Box.
**Counteract**: Don’t do radio as a hobby.
**Art**:
All artists have tells or quirks that quickly becomes akin to that of a fingerprint or signature. Many artists are unaware of this while most viewers can pick it up.
**Counteract**: Work on the basics and build to your own style before thinking of going toward any real paying job, high-end jobs or commissions. Give a glance at our library (https://paranoidsbible.tumblr.com/library) for guides that may be beneficial to you.
**Bankruptcy records**:
When an individual, businesses, or what have you files for bankruptcy in the Federal courts, a record is kept. These records are available at each state’s NAC. Depending in what state the bankruptcy was filed; there may be one or more locations where these records are house. It’s also possible to order these records through the mail or online in many states.
When businesses or individuals file bankruptcy in Federal courts, a record is kept. These records are available at each states National Archive center. Depending in which state bankruptcy was filed; there may be one or more location where these records are housed. It is also possible to order these records through postal mail or Online in some states.
These records do show the name of the individuals filing bankruptcy, the city, the state, the date of filing, a full list of creditors, total amount discharged, a final decree or Order of Dismissal.
**Counteract**: We can’t, legally, divulge any information or advice as we’re unsure of the laws in each state and how you can go about keeping this from being made public, but one piece of advice we can give is… Don’t file bankruptcy if you can avoid it.
**Boat Registration Records**:
Own a boat? Then your state of residence can disclose your personal information contained in the boat’s registration records.
If you own a boat, your state of residence may disclose your personal information contained in boat registration records. Boat registration records can include a full name of the owner(s), an address of the registered owner(s), value of boat and a history of repairs.
**Counteract**: Look in trusts, again.
**Blogs**:
What else to say?
Yours or someone else’s blog can ultimately divulge a lot of information about you and your private life—avoid making a blog, for obvious reasons. If someone else leaks your information, look toward legal action but only after seeking the owner of the site’s host/servers to see if they can remove the offending post and private information for you.
**Counteract**: Don’t own a blog, buy a diary or journal. Remember OPSEC and compartmentalization.
**BBS | Bulletins | Message Boards | Image boards | Usenets**:
These groups in which you either have a profile or are allowed to post anonymously can and most likely have recorded your IP, ISP, a garden variety of information from META-data like your OS and time zone. You also have the fact that some of these boards\bulletins are hosted by ISPs that collude with various government bodies and have everything flow through a government owned server that collects and catalogs all information possible.
**Counteract**: Look toward not posting on these places and simply lurking. You can also, to an extent, reduce your data footprint by customizing and modifying your browser and browsing habits.
**Browsers**:
IE, FF, Chrome and many others don’t necessarily send your information to the groups that work on and update said browsers, unless they send error reports, but they do hemorrhage information and META-data left and right. Besides some simple setting changes, there’s not much you can do beyond modifications and customizations.
**Counteract**: Look for a guide toward modifying and customizing your browser of choice, like our Firefox Testament (or future IceCat guide).
**Business license records | corporations | fictitious business filings**:
If you’ve ever read the paper, then you’ve obviously glanced at something called “Public filings”. In essence, this section of the paper is so that you and other readers can find the names of individuals or corporations that have filed for a FBN (Fictitious Business Name).
Others names that this can be known as are “Assumed Name, “ “Doing Business as,” or “Trade Name”. These filings are basically used by the individuals to certify that they’ll be conducting business not as themselves or under their name, but as the name of their business.
FBN\DBA records contain the name of the person that filed the business name, their address, owner name and address, the date, location and file number of said record.
**Counteract**: None (?)
**Consumer feedback sites | Review sites**:
Amazon, Ebay, Yelp… any business that allows you to interact while purchasing goods or services, or websites that offer you the chance to leave reviews and comments about services, goods, purchases or about places like eateries or supermarkets.
Google, among other Search Engines, can crawl and catalog your reviews or comments, leaving caches in their stead even if you delete the comment.
**Counteract**: Don’t interact. Buy and move on, but if you need to check reviews, lurk and don’t interact. Remember OPSEC and compartmentalization.
**Coding\programming**:
Like an artist or a writer, anyone who works with software also has tells, which isn’t always restricted to just one language or project.
**Counteract**: Besides learning several languages and picking through your own work, it does pay to have a third party to review several examples of your work to see if they can pick up a tell you can’t. Remember OPSEC and compartmentalization.
**Cookies**:
Most, if not all, websites use a form of cookies that basically amount to a form of data that’s stored on your hard drive to collect and store information about you and your internet surfing habits or searches. Cookies allow advertisers to deliver personalized advertisements or gather as much information on you as possible.
Cookies also remember everything from how many times you visit a website to what you’ve purchased or if you’ve used a search engine or typed in the URL itself.
**Counteract**:
Several add-ons and configurations that you can make your browser to counteract this.
**Credit Reports**:
Credit card companies contract consumer credit reporting agencies, among other sometimes not so legal means, to find and discover new potential clients. These companies usually ask for a list of potential clients with a minimum credit score. After receiving this list, credit companies will send out offers and notices of being pre-approved for a credit card.
**Counteract**: Look toward the master opt-out list. There are several opt-outs to remove direct marketing mail.
**Criminal Records**:
Law enforcement agencies maintain a database that keeps track of criminal records, which also include traffic infractions. This database is usually used to help locate possible suspects in criminal investigations, besides maintaining records of people who’ve broken the law. Personal information is contained within these records, and also include such items as a finger print, aliases, tattoos and\or scars and other identifiable markings, and even various other pieces of information like known hangouts.
Some states and federal agencies also mandate that a DNA profile must be kept on file, too, of certain criminals.
All of the data contained in these criminal records is available to the general public. Though some agencies may only provide the name and date of birth with the listing of criminal offenses for an individual, some agencies also provide addresses.
There are means of expunging criminal records, especially if you’re proven innocent, but as we’re not technically involved in the legal sector… so, we can’t truthfully provide any information on how to go about this. You can, though, contact a lawyer or an attorney and seek legal advice that way on the removal of your records.
**Counteract**: None, save legal action
**DMV and Voter Records**:
The DMV requires a physical address to be on file, while some also give you the option to have a 2nd option to mail your correspondence.
Whenever possible, when it comes to DMV renewals, voter registration, and assessor tax bills…ETC, you can make a central address (depending on state and law) for yourself that is nothing more than a P.O. BOX.
**Counteract**: Some states, though, offer an “OPT-OUT” option to have your information kept within the government, only, and never sold or given out.
**Drivers Records**:
Before becoming a licensed driver, you must obviously take a driver’s test. You usually need to pass a written test and a practical driver’s examination. After a successful completion, you’re issued your license with a unique number that identifies you. Many, who don’t drive, though, will most likely receive a state issued ID card that mostly resembles a driver’s license and also uses a unique number to identify you.
Both the driver’s license and ID cards are issued and regulated by the DMV for each state. Though laws may vary, the type of records maintained and collected are always the same. Also, in addition your driving record, a lot of your personal information is also contained within each state’s database.
This information usually includes your full name, SSN#, birthdate and legal presence, current address and phone numbers as well as information about your medications, vision and\or possible medical conditions including mental status or ailments.
It’s important to note that all of this information collected by the DMV in the US becomes public record. Members of the public, besides many data brokers, may make a copy and examine these records. However, inspection and copying of said records may be limited to the “Use Policy” of your state.
**Counteract**: Don’t be born, ever, in our time. Joking aside, look over your application for your IDs. Some states allow you to ‘opt-out’ of appearing in certain databases. You also should never put yourself down as someone who’s willing to donate organs or tissues in case of an emergency or death.
**Fax**:
If you have a fax machine or a business that has one then you’re probably aware of the fact that you’ll get advertisements or pranks sent through said fax machine. The
number belonging to your fax machine can range from name and address to several other items like a registration or patent number depending on what you do, what you use your machine for, and how much you use it.
**Counteract**: Either ditch the fax or look into the master opt-out list.
**Fishing License**:
Simply put a license that most states don’t require any test or course to be passed before being issued. Usually a fisherman must provide name, address and a phone number, and also a small fee to obtain.
These licenses, too, are available for review and list the name, add and phone number of the person who obtained it.
**Counteract**: don’t get one and never fish.
**Free or discounted health offers**:
We’ve all seen them, these offers of a free blood screen or blood pressure test, but what many of us fail to realize that even though they’re discounted or free… our information is the cost. You probably have seen CVS or Walgreens offer similar services and usually you get asked to fill a small survey or form, which in turn asks a plethora of things like allergen info or medical history concerning this or that.
That is where they gather your information from and then use it to opt you into several databases that’ll proceed to bombard you with
**Counteract**: Go to your doctor instead of some third party.
**Hunting Licenses**:
Much like a professional license, many states require hunters undergo a safety course and pass tests in order to hunt wild game legally. Hunter must also renew their licenses on an annual basis.
Records include the name of the hunter, address, and date of application and in some instances a phone number.
**Counteract**: don’t get one and don’t hunt.
** (The) Internet**:
Proliferation of the Internet brought to us free services, items, and samples. These aren’t truly free as they usually cost anywhere from your e-mail address to your name, address, phone and\or other identifiable information.
Your more paranoid and somewhat tech savvy individual will use a disposable e-mail address, a burner cell-phone and a nickname or some other moniker. It’s good practice to start doing the same thing and possibly also using a P.O. Box.
One other thing to realize is that many people are too ignorant of such things and will also provide their cell-number without a single doubt. This is bad as it causes a bit of a social contagion that reinforces this practice into others, thus causing people to doubt those who aren’t so readily transparent. This means that if you try to convey your unwillingness to provide information or simply state the possible issues behind providing it so freely, you’ll have most likely stirred some suspicions.
Simply remind people that you don’t want your information collected by marketers or identity thieves.
**Counteract**: Be aware of what you’re giving away when looking toward freebies or making an account. Always use disposable e-mails for freebies and look toward a burner phone and a P.O. Box when you need to give your address out to any sites. Remember OPSEC and compartmentalization.
**Internet Service Provider (ISP) **:
Your ISP has not only your click-stream but also your IP. They can sell a sanitized version of not only your click-stream but also your IP’s history. Ranging from sites you’ve visited to downloads and even if you connected to any specific ports or chat programs.
Not all ISPs keep track of this information or are willing to give it away or even sell it. Some will outright ignore it and not bother keeping track besides what legally is required of them.
**Counteract**: Don’t do illegal activity online, or be smart enough to try and cover your tracks or do your research and see what ISP in your area is the best choice for you and your planned activities. A reminder, though, that most IP addresses are now dynamic instead of static, ergo you won’t have to worry much about being tracking through an IP address alone. However, remember that you still can be tracked and that an IP address offers minor data, at best, that includes the location of the ISP’s hardware.
**Judgments**:
Judgments are the final decision of any court at the conclusion of a lawsuit. The result of the judgment can include terms for financial compensation for the plaintiffs or sentencing of an individual deemed guilty in a criminal case.
Records can contain names of both parties involved, judgment amount, and the nature of the conviction if it was a court case, case number, name of the convicted and date of conviction.
**Counteract**: Don’t break the law, and look into getting legal counseling.
**Mobile Phones/Smart Phones**:
A modern marvel that’s more akin to a tracking device than an actual phone due to the smorgasbord of features (both hidden and open to the user). Texting, chatting, taking pictures and phones call all in one device may seem like the smart thing to do to help streamline and further lessen the stresses of life, however through software prebuilt into the phone, many companies and service providers can track, listen-in and monitor what you say and do. The same applies to applications and 3rd party peripherals that can be installed on the phone, too.
**Counteract**: Look into jail breaking and modifying you phone, at the very least, or look into purchasing a simple burner phone without all the bells and whistles. If you do get a burner cell, look into changing it twice a year and only using it for calls and nothing else. When it isn’t in use, you should look into disabling it by removing the sim card and battery. It’s also good practice to put tape over the speakers, microphones and camera when not in use either. Outside of that, be careful what you install on your phone and what peripherals you use. Always double-check everything!
**No Child Left Behind**:
When the ‘No Child Left behind’ act was created there was a (rarely discussed) provision inserted—school district superintendents across the US must hand over records for all high school students. These records contain anything from full names to addresses to medical records and even things like after school activities or even fields of study they excel in.
The information within these files are not only highly valuable, but can also be used to mark children as potential threats to the nation.
**Counteract**: Check the Leave My Child Alone website (https://themmob.org/lmca/) and the Underground Action Alliance’s website for more information. Some information provided by these websites is somewhat sketchy, at best, but it does provide you some insight and possible actions that you can take.
**Online communities**:
Any group comprised of people who communicate and interact over the Internet rather than reality. There are multitudes of ways to interact online. Some of the most common are social networks like Facebook.
Accounts for most any community usually display, besides a username, various other pieces of information from signup to various other optional fields you may fill in if it so pleases you.
**Counteract**: Read the TOS carefully, and go over what privacy settings are granted to you. Obviously don’t sign up for Facebook or other social networking accounts.
**Opt-in databases**:
When you register for any product or file its warranty, or even get a subscription, you usually are opted into some database or agree for the company to sell your information. Nothing is life is free, and free registrations or warranties rely on the profit brought in from the sale of your information.
Most if not all companies and groups put in a clause or contract within their privacy policy or TOS, in general, that gives them permission to sell, share or use your data in collaboration with other companies once you submit online or offline.
These forms can include addresses, names, phone numbers, misc personal information, or even credit or tax information.
**Counteract**: Obviously read everything very carefully before agreeing to anything. You can also write, within the free space of a card or form, or even in the “Comments” section, that you don’t give them permission to sell your information.
**Peer-to-peer (P2P) networks**:
Kazaa, Icewire, Limewire and similar programs are very popular for downloading games, movies and music. These programs rely and focus on connections between computers on the network rather than servers.
These programs, very similar to torrents, rely on users, who’re downloading, to let other users to download parts of a file or files thus forcing the user to upload as they download.
This is especially troublesome as some ignorant users can end up being charged with varying degrees of lawsuits for piracy, espionage, among other things.
**Counteract**: Avoid P2P and torrents, only direct download.
**Phone Company and listings**:
You most likely have a landline phone, if not, a cell phone that you “rent” to an extent from your provider. Your provider obviously offers you a plethora of options ranging from an unlisted number to various items like basic caller ID to blocking numbers of your choosing.
Even though you may pay for an unlisted number, it’s still possible for individuals and companies to get the information associated with your numbers.
Counteract: If possible, always have your number unlisted. Be wary of who you give your phone number to and who your provide it to. Using a burner cell for subscriptions, freebies, warranties and strangers is a good route and practice to take up.
**Professional License Records**:
Each state maintains a record of individuals and companies that are licensed to perform certain tasks or duties. Usually individuals must complete some form of training or education and pass a state exam before becoming certified. The best example would be medical doctors. In addition to completing medical school, each doctor must pass state certified board examinations before he/she can be licensed and practice medicine in that particular state. It is possible for people to be certified professionals in more than one state.
If you are a licensed professional, your personal information is publicly available. Many states are even making this information available Online and free of charge.
Professional license information will vary by state and may contain, first and last name, type of license and license number, zip or address of residence or practice, license status and record of infractions, date of issue and school attended.
**Counteract**: None (?)
**Property/assessors records**:
Anyone with an Internet connection and simple knowledge of using Google can figure out the exact value and worth of your house, when it was last sold, what it sold for and the date of purchase. But every county within the US has an office of the County Assessor which maintains the records of all properties and land in that county.
The CA keeps track and assesses the property values as a means to provide that information to the county treasurer. In turn, the treasurer uses this information for property tax billing purposes.
Information readily available in the CA’s records contain name and address of the property owner, names of previous owners, dates of the property when sold, how much property tax was assessed, and what parcel is was or currently is used as.
**Counteract**: Nothing as of yet besides using a trust.
**Raffles and Sweepstakes**:
A lot of sweepstakes, contests and raffles offer the chance to change your life or give you something for nothing based upon the slim chances that you’ll win, but, ultimately, they’re nothing more than centralized data mining operations. Instead of fishing for information or trying to confuse the target into giving away their information, these chances to win prizes simply state: Fill out and win!
Name, address, birth date, phone number… the information varies and hardly, if ever, truly limited. This can be sold and given away to anyone, truly, depending on who runs the contest.
**Counteract**: Don’t fall for these scams, avoid them.
**Rating and review sites**:
Digg, Reddit and sites like Rateitall depend on their community to provide content and discussion. Joining these sites may seem like a good idea, but to those who’re aware of your accounts, or if you’re loose with your information, can use your activity to build up a dossier of sorts.
**Counteract**: Avoid these sites. Don’t join any similar sites.
**Registration Cards and forms: **
Many products come with registration cards beside warranties. These cards allow you activate or simply state you bought the product. But many of these forms try to entice you to fill them out through claims or rebates or sweepstakes or even a credit off your next purchase.
Every one of these registries ultimately does very little for the consumer. They ultimately just catalogue your information and help build a profile or dossier on you, as a consumer, which is then sold and given to various third parties.
**Counteract**: Unless needed to activate your warranty, double check the fine print and see if you can avoid filing the card or form. If you can’t avoid it, look toward applying, somewhere in a blank space, the statement of ‘I don’t give permission to sell or use my information’.
**Rewards Cards**:
Reward cards seem like a good idea to the thrifty and frugal shopper—gain points or cash backs on certain items, save some percentage on your purchases or even get put into several sweepstakes for simply buying a candy bar--the issue is that your information is not only gathered but a profile is made based around your shopping habits and what purchases you’ve made.
This means your e-mail can be flooded with advertisements, your phone number or cell number can be sold or given to various groups and organizations, and you can even end up with physical mail offering you things or demanding your attention.
**Counteract**: Always add one or two items, at random, to your purchases. A magazine or two, some vitamins or supplements, some sort of baby or item for a child… anything, really. You can always simply drop off the extra at a donation box or shelter. You also can create an e-mail address specifically for your rewards cards and use a P.O. Box, if possible, to help obscure your information.
**Search Engines**:
Google, Yahoo, Bind and other search engines use bots and various other means to categorize and record as much as technologically and humanely possible of all content within the Internet.
Most search engines are, in all simplicity, a company that keeps mostly non-identifiable records of keywords and similar items used by their users. There’s a huge industry built up around companies to analyze keywords to use for products and informational searches.
**Counteract**: There are some add-ons and configurations that can be done to several commonly used browsers to help obscure your search history and information provided to search engines.
**Search Engine + email account**:
A large amount of search engines now provide e-mail account services. If you’re signed in while you’re using the same companies search engine, you’re willingly, to them, providing information not only from your searches but also information within your e-mail, too, thus giving them a connection between both the searches and your account.
They’ll also most likely have your click-stream information from when you were signed in.
**Counteract**: Never sign into your e-mail while using a search engine. Once you sign in, you must sign out, delete and clean your browser’s cache and restart your browser. The same applies to signing into sites like Amazon or EBay while using a search engine.
**Sex Offender listings**:
All US states require that individuals convicted of sex or sex related crimes against victims that are classed as a minor or a sexually violent offense register with their state of residence.
Though the sex offender registration laws and statues vary throughout the US, it isn’t uncommon for the registered offenders to keep the state appraised of their current address, to notify the neighborhood of their status, not to reside within a mandate distance of schools and to also be subject to random inspections of their residence by law enforcement.
Most states now provide an online database with public access to a listing of sex offenders. Sex offender information available on these sites includes photos of the offenders, list of tattoos, scars, address where the offender resides and the crime or crimes that they were convicted for committing.
In addition to many of the databases, large quantities of companies have cropped up that also provide databases on sexual offenders. These companies will let you search usually by zip or address or even a simple click and search map.
**Counteract**: Don’t break the law.
**Social Networking**:
MySpace, Facebook, Linkedin or even Tumblr are just a sampling of social networking sites. These sites ask you to provide anything from personally identifiable information like a name or place of education that you visited to owned websites or even a phone address.
**Counteract**: Stay away from Social Networks.
**Tax Liens**:
If a business or individual owes back taxes to the IRS a lien might be placed upon property or assets owned by the business or individuals to secure payments of the debt.
These liens might be imposed for taxes owned on real property, personal property or even as a result of not paying income tax.
Tax lien information records include name of the tax payer or business, information on property owned by the taxpayer or business, overdue tax balance, address, telephone numbers and income of the taxpayer.
**Counteract**: Pay your taxes.
**Vehicle Registration**:
Any vehicle at any given time, be it driven, parked, moved, left on the side of a road or place into a parking facility must be not only registered but also up to date in your state of residence other legalities you must ensure are taken.
Any vehicle you own and register will have your personal information attached to it and the registration. This information is gathered and used as a means to identify and maintain ownership records. If you fail to provide personal and identifiable information, require by your state, you most likely will not be able to register your vehicle and be the target of heavy surveillance to make sure you’re not using said vehicle.
Similar to a driver’s records, all information is collected by the DMV in each state and becomes public record. The public can and will make copies, examine these records and sometimes even gather information to sell to third parties. Sometimes these records can be used, like any records, to asses and estimate your income and overall value during lawsuits or paternity claims.
**Counteract**: Some newer forms offer you to “Opt-out” of having your information sold or displayed. But, usually, you can, depending on laws within your state, hide behind a trust or obscure some information due to business or not having a permanent place of residency. Please consult your local laws and seek legal counsel before acting upon anything that needs to be registered (like a vehicle…etc).
**Voter records**:
It’s your right as a citizen of the U.S.A. to vote and take part in the political process but that information, that you supplied on your ballot, becomes public record.
This means your name, address, among several other pieces of information, end up becoming readily available to the public and the Internet.
Anyone can simply call or mail the Board of Elections for the county you registered in to obtain your information.
Several companies, too, purchase and organize this information to sell to politicians, political parties, watchdog groups and several other organizations or individuals. Some will use it as a means to supplement their online people search engines or to help various “Private Investigation” agencies to create a profile or dossier on someone.
To be specific, the information usually includes voting history, income level, addresses, age, gender, election district and state of residence--all of which is public knowledge and easily discovered online.
**Counteract**: Don’t vote, which risks you losing your voice.
**Voting Lists**:
When election time rolls around you’ll usually end up with knocks at your door, your phone ringing off the hook, and several adverts on your door or in your mailbox.
These candidates though aren’t after your vote, personally, they’re renting or purchasing the services of several groups and businesses that have gathered your information from public records or several other sources.
**Counteract**: Look toward the master opt-out list. The more opt-outs you do, the higher your chance that you’ll remove yourself from one or more sources that sell your information.
**Warranties**:
Warranties are those little contracts and guarantees supplied with most anything in this day and age that promises you that your recently purchased item will last or be up to a specific quality standard, and if it isn’t it’ll be replaced ASAP once you provide them with various information like a proof of purchase or identifiable information like your name, address, phone number and several other items.
Some warranties won’t work or be considered active unless you register your product within a certain period of purchasing it.
Most warranties, albeit listed as free, actually end up selling your information which is then circulated online or to various third parties.
**Counteract**: Read each warranty carefully. See what the fine print and TOS say, as sometimes you can simply get away with a “Don’t sell my information, I don’t give permission to use it” on the card itself.
**Wikis**:
Wikis are largely a collaborative form of an online community gathering and organizing information on a large variety of topics. The most famous Wiki is Wikipedia. Most
Wikis show the IP and username of the editor, when the edits were made and sometimes even pieces of meta-data are shown like OS, if JavaScript was enabled or what the browser used was. Though, like most websites, all Wikis, if not created VIA means of a third party services, can see not only your IP but a plethora of data and meta-data.
**Counteract**: Lurk and read, never create an account and participate.
**Websites**:
A Website is a website.
Websites can see a visitor’s IP, ISP, read cookies (sometimes), gather meta-data like your browser’s footprint, some other information like what fonts are on your computer, what add-ons or plug-ins are used or even gather other information from cookies placed by other websites.
**Counteract**: Several add-ons and configurations can be done to your browser of choice to lessen your footprint and data given or gathered.
**Writing\typing**:
Whether you’re a writer or a casual typist, or even just texting, we all have tells that acts like our signature when writing something out.
**Counteract**: Write everything in a word processor and double check spelling and grammar.
The above is only but a sampling of the ways our privacy is invaded in our day-to-day lives. There are several means of covering our tracks, displacing certain tells, and even obscuring the profiles or dossiers being built on us, but they’re just bandages instead of a cure for this sickness.
The age of anonymity is dying and it’s dying fast.
Some things you can do, though, range from making a trust or a LCC or even corporation. You can also work to disappear from public records to simply ending certain habits or trends. Ultimately, though it’s a fact of our day and age that we must accept—we’re being monitored.
__References__:
https://www.privacyalerts.org/index.php
https://www.optout.com/ebook/default.aspx
https://www.worldprivacyforum.org/
++++++++++++++++++++++++++++++++++++++++++++++++
===Afterword==
In the end, you can never fully prevent your information from hemorrhaging. There’s no such thing as being 100% anonymous. This is why you must take the proper precautions and work toward privacy that fits your lifestyle.
Also, pay your taxes.
13 notes
·
View notes
