#ransomware file recovery
Explore tagged Tumblr posts
Text
Critical Windows Update: Apply Patch Now to Prevent Black Basta Ransomware
#Time is running out for Windows users to secure their systems against the notorious Black Basta ransomware. Microsoft has released a critica#as failure to install it could leave your PC vulnerable to sophisticated ransomware threats.#The Critical Windows Update#Microsoft has issued an urgent call to all Windows users to apply a crucial security patch aimed at thwarting the Black Basta ransomware. T#your system remains susceptible to attacks that could encrypt your data and demand a ransom for its release.#Understanding Black Basta Ransomware#Black Basta is a highly dangerous form of ransomware that encrypts files on the victim’s computer#rendering them inaccessible until a ransom is paid. Often#even paying the ransom does not guarantee the recovery of the encrypted files. The threat posed by Black Basta is severe#making it imperative for users to protect their systems immediately.#Why This Update is Crucial#The update released by Microsoft is designed to close a vulnerability that Black Basta exploits to infiltrate systems. Cybersecurity expert#emphasizing the need for users to act quickly. Applying this patch is not just a recommendation—it’s a necessity to safeguard your personal#How to Apply the Update#Applying the Windows update is straightforward:#Open the Settings menu on your Windows PC.#Navigate to Update & Security.#Click on Windows Update.#Select Check for updates.#Once the update appears#click Download and install.#Ensuring your system is up-to-date with the latest security patches is a vital step in protecting against ransomware attacks.#Potential Consequences of Ignoring the Update#Failure to apply this critical update could result in severe consequences. If Black Basta ransomware infiltrates your system#you could lose access to valuable data#suffer financial loss#and face significant disruptions to both personal and business operations. The cost of recovery and the potential damage to your reputation#Real Stories#Real Risks#Think about all the important files on your computer—photos
0 notes
Text
Anubis ransomware adds wiper to destroy files beyond recovery
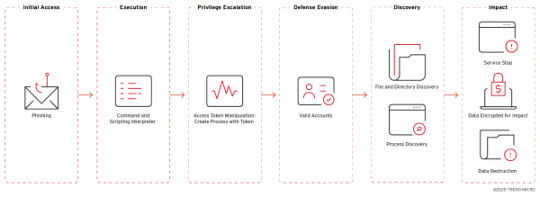
Source: https://www.bleepingcomputer.com/news/security/anubis-ransomware-adds-wiper-to-destroy-files-beyond-recovery/
More info: https://www.trendmicro.com/en_us/research/25/f/anubis-a-closer-look-at-an-emerging-ransomware.html
2 notes
·
View notes
Text
How Crypto Scam Recovery Services are Revolutionizing Cybersecurity
The rise of cryptocurrency has undeniably brought a wave of new opportunities, innovation, and financial freedom. However, with this growth, there has been a parallel surge in crypto-related scams. Hackers, fraudsters, and unscrupulous individuals have leveraged the anonymity and decentralized nature of cryptocurrencies to defraud investors. As the threat landscape grows, so too does the need for innovative solutions to combat these malicious activities. Enter the world of crypto scam recovery experts services — a rapidly growing industry that is revolutionizing cybersecurity and offering hope to individuals who fall victim to scams.
If you lost money due to crypto fraud or an Online Scam, don’t be a victim, fight back and retrieve your stolen funds. BitcoinScamWatch retrieve services can assist law firms and law enforcement to find and retrieve your funds. Visit https://bitcoinscamwatch.org/ and file a complaint. An agent will be assigned to you to assist you on the retrieve process.
The Surge of Crypto Scams
Cryptocurrencies, especially Bitcoin and Ethereum, have become mainstream in the past decade, attracting both legitimate investors and opportunistic fraudsters. Whether through phishing emails, Ponzi schemes, fake initial coin offerings (ICOs), or even more sophisticated ransomware attacks, crypto scams are becoming more prevalent and diverse.
One of the key attractions of cryptocurrencies for cybercriminals is their irreversibility. Unlike traditional financial transactions, once a cryptocurrency transaction is confirmed on the blockchain, it cannot be reversed. This makes it an ideal target for scammers who promise high returns on investments or fraudulent crypto exchanges that disappear with investors' funds. The anonymity of the blockchain also makes it incredibly difficult to trace perpetrators, further exacerbating the problem.
The Role of Crypto Scam Recovery Services
Crypto scam recovery services have emerged as a direct response to the rising tide of fraud in the cryptocurrency market. These specialized services are designed to help individuals and organizations recover funds lost to scams, fraudulent investments, or cybercrime. Recovery specialists typically employ a combination of forensic investigation, blockchain analysis, and legal expertise to trace stolen assets and pursue potential recovery routes.
Blockchain Forensics and Tracking
One of the most powerful tools that crypto scam recovery services have at their disposal is blockchain forensics. The blockchain is a public ledger that records every transaction made with a cryptocurrency. While transactions are pseudonymous, they are not entirely anonymous. With the right tools and expertise, recovery professionals can trace stolen funds through multiple addresses and exchanges, potentially identifying the criminal's trail.
Blockchain forensics allows recovery services to map out a scammer's transaction patterns and determine where the funds were moved after being stolen. By following the digital breadcrumbs left behind, recovery professionals can sometimes successfully retrieve assets, either by working with cryptocurrency exchanges or by leveraging law enforcement agencies if the case is severe enough.
Legal Support and Regulatory Navigation
As cryptocurrency scams often transcend borders, legal challenges play a critical role in the recovery process. Recovery services don’t just rely on technical expertise; they also work closely with legal teams that understand the complex regulatory landscape surrounding cryptocurrencies. With no centralized authority overseeing cryptocurrency transactions, recovering stolen funds can be a tricky process.
However, as more countries implement regulations to protect crypto investors, recovery services are increasingly able to leverage legal frameworks to their advantage. Legal experts can help file complaints with the appropriate regulatory bodies, collaborate with local authorities, or even initiate civil actions to hold scammers accountable. The involvement of legal professionals ensures that victims are not only seeking technical solutions but also taking steps to prevent future scams by promoting better regulatory standards.
Recovery Services: Preventing Future Scams
Another significant aspect of the crypto scam recovery services industry is its role in educating investors and reducing the likelihood of future scams. These services often provide consultations and educational resources to teach individuals how to recognize potential threats and avoid falling victim to scams in the first place.
For example, many recovery services offer advice on recognizing red flags in cryptocurrency offers, including promises of guaranteed returns, requests for upfront payments, or suspicious websites. By arming the public with knowledge, these services reduce the likelihood of new victims, which ultimately contributes to a healthier and safer cryptocurrency ecosystem.
The Future of Crypto Scam Recovery Services
As cryptocurrencies continue to gain adoption, the demand for scam recovery services is expected to grow. In the future, we can expect these services to evolve with advances in technology, including artificial intelligence and machine learning, which can automate parts of the tracking and recovery process. With the introduction of decentralized finance (DeFi), additional challenges will arise in terms of security, but also new opportunities for recovery professionals to tap into different blockchain networks.
Moreover, as governments around the world continue to regulate cryptocurrencies, a more structured framework for recovering stolen assets will emerge. This will likely provide greater support for scam victims and push for more transparent and secure crypto services, fostering a more trustworthy and safer crypto landscape.
Conclusion
Crypto scam recovery services are undeniably transforming the world of cybersecurity by providing an essential service in the fight against fraud. These services are not only recovering lost funds but also helping individuals and businesses navigate the complexities of the crypto world with greater security and confidence. As the industry continues to evolve, these services will remain a crucial part of the cryptocurrency ecosystem, helping to ensure that the promise of digital finance is realized without the shadows of cybercrime hanging over it.
4 notes
·
View notes
Text
Role of ethical hackers in the fight against ransomware attacks

Ransomware attacks are now one of the most damaging cyber threats as they target not only businesses, healthcare systems, and educational institutions but also governments. These types of attacks lock up critical data and demand that a ransom be paid to decrypt it, leaving massive financial and reputational damages in their wake. In this high-stakes game of cyber warfare, the role of the ethical hacker has come into the picture as a vital player protecting organizations from ransomware attacks. Here's how these cyber guardians are making a difference.
What Are Ethical Hackers?
Ethical hackers are usually called "white-hat" hackers. These are cybersecurity experts who make use of their expertise to discover weaknesses in systems, networks, and applications before they can be exploited by cybercriminals. In contrast to cybercriminals, ethical hackers collaborate with organizations to build stronger defenses and achieve security compliance.
If you wish to become a part of this exclusive club of cyber defenders, you should take a course in cyber security and ethical hacking. This type of course will help you learn to think like a hacker so you can think ahead and eliminate possible threats.
Ransomware Threat Landscape
The attacks by ransomware have been very sophisticated. From using advanced phishing to exploiting zero-day vulnerabilities and even using artificial intelligence to target their victims, ransomware attackers have developed into highly skilled actors. In addition, Ransomware-as-a-Service (RaaS) platforms have further democratized these attacks, even making them possible for the less technically skilled cybercriminals.
Recent estimates suggest ransomware damages are expected to go above $30 billion annually by 2025. This growing threat requires aggressive cybersecurity measures that incorporate the input of ethical hackers.
How Ethical Hackers Fight Ransomware
Proactive Vulnerability Scanning Ethical hackers carry out vulnerability scans to scan the organization's infrastructure for vulnerable spots. Using a simulated ransomware attack, they can reveal how exposed an organization is to risk and implement relevant remediation efforts.
Penetration Testing Penetration testing is an attempt by ethical hackers to breach the defenses of an organization in a controlled environment. It shows security gaps and tests the effectiveness of existing measures.
Phishing Simulations and Training Since phishing is the most common vector for ransomware attacks, ethical hackers simulate phishing campaigns. These exercises train employees to recognize and respond to malicious emails, thus reducing the risk of a successful attack.
Incident Response and Recovery Incident response at ransomware strikes includes the input of ethical hackers to help contain an attack, understand a breach, and assist in retrieving encrypted files without paying any ransom.
Monitoring and Threat Intelligence Ethical hackers keep themselves aware of new emerging threats and the ransomware trend. The organizations would not miss being on their toes if ethical hackers help them build on new defensive systems and patches in place soon enough.
Becoming an Ethical Hacker
The demand for ethical hackers is rapidly increasing, considering the recognition that organizations from any industry require proactive cybersecurity. It is an integrated cyber security and ethical hacking course that would teach you how to be one. From penetration testing to advanced threat detection, courses provide you with hands-on exposure to real scenarios.
Conclusion
Ethical hackers are the unsung heroes in the fight against ransomware. Their proactive approach, technical expertise, and unwavering commitment to cybersecurity make them indispensable in safeguarding our digital world. If you’re passionate about technology and problem-solving, a career in ethical hacking could not only be rewarding but also instrumental in making the internet a safer place.
Enroll in a cyber security and ethical hacking course today and become part of the frontline defense against ransomware attacks. The world needs more defenders, and now is the starting point for that journey.
2 notes
·
View notes
Text
Ransomware Attacks Target VMware ESXi Infrastructure Following Interesting Pattern

Cybersecurity firm Sygnia has shed light on a concerning trend where ransomware attacks targeting VMware ESXi infrastructure follow a well-established pattern, regardless of the specific file-encrypting malware deployed. According to the Israeli company's incident response efforts involving various ransomware families, these attacks adhere to a similar sequence of actions.
The Attack Sequence
- Initial access is obtained through phishing attacks, malicious file downloads, or exploitation of known vulnerabilities in internet-facing assets. - Attackers escalate their privileges to obtain credentials for ESXi hosts or vCenter using brute-force attacks or other methods. - Access to the virtualization infrastructure is validated, and the ransomware is deployed. - Backup systems are deleted, encrypted, or passwords are changed to complicate recovery efforts. - Data is exfiltrated to external locations such as Mega.io, Dropbox, or attacker-controlled hosting services. - The ransomware initiates execution and encrypts the "/vmfs/volumes" folder of the ESXi filesystem. - The ransomware propagates to non-virtualized servers and workstations, widening the scope of the attack.

Mitigation Strategies
To mitigate the risks posed by such threats, organizations are advised to implement the following measures: - Ensure adequate monitoring and logging are in place - Create robust backup mechanisms - Enforce strong authentication measures - Harden the environment - Implement network restrictions to prevent lateral movement
Malvertising Campaign Distributing Trojanized Installers
In a related development, cybersecurity company Rapid7 has warned of an ongoing campaign since early March 2024 that employs malicious ads on commonly used search engines to distribute infected installers for WinSCP and PuTTY via typosquatted domains. These counterfeit installers act as a conduit to drop the Sliver post-exploitation toolkit, which is then used to deliver more payloads, including a Cobalt Strike Beacon leveraged for ransomware deployment. This activity shares tactical overlaps with prior BlackCat ransomware attacks that have used malvertising as an initial access vector, disproportionately affecting members of IT teams who are most likely to download the infected files.
New Ransomware Families and Global Trends
The cybersecurity landscape has witnessed the emergence of new ransomware families like Beast, MorLock, Synapse, and Trinity. The MorLock group has extensively targeted Russian companies, encrypting files without first exfiltrating them and demanding substantial ransoms. According to NCC Group's data, global ransomware attacks in April 2024 registered a 15% decline from the previous month, with LockBit's reign as the top threat actor ending in the aftermath of a sweeping law enforcement takedown earlier this year. The turbulence in the ransomware scene has been complemented by cyber criminals advertising hidden Virtual Network Computing (hVNC) and remote access services like Pandora and TMChecker, which could be utilized for data exfiltration, deploying additional malware, and facilitating ransomware attacks. Read the full article
4 notes
·
View notes
Text
How To Reduce 5G Cybersecurity Risks Surface Vulnerabilities

5G Cybersecurity Risks
There are new 5G Cybersecurity Risks technology. Because each 5G device has the potential to be a gateway for unauthorized access if it is not adequately protected, the vast network of connected devices provides additional entry points for hackers and increases the attack surface of an enterprise. Network slicing, which divides a single physical 5G network into many virtual networks, is also a security risk since security lapses in one slice might result in breaches in other slices.
Employing safe 5G Cybersecurity Risks enabled devices with robust security features like multi-factor authentication, end-to-end encryption, frequent security audits, firewall protection, and biometric access restrictions may help organizations reduce these threats. Regular security audits may also assist in spotting any network vulnerabilities and taking proactive measures to fix them.
Lastly, it’s preferable to deal with reputable 5G service providers that put security first.
Take On New Cybersecurity Threats
Cybercriminals often aim their biggest intrusions at PCs. Learn the characteristics of trustworthy devices and improve your cybersecurity plan. In the current digital environment, there is reason for worry over the growing complexity and frequency of cyber attacks. Cybercriminals are seriously harming businesses’ reputations and finances by breaking into security systems using sophisticated tools and tactics. Being able to recognize and address these new issues is critical for both users and businesses.
Threats Driven by GenAI
Malicious actors find it simpler to produce material that resembles other individuals or entities more authentically with generative AI. Because of this, it may be used to trick individuals or groups into doing harmful things like handing over login information or even sending money.
Here are two instances of these attacks:
Sophisticated phishing: Emails and other communications may sound much more human since GenAI can combine a large quantity of data, which increases their credibility.
Deepfake: With the use of online speech samples, GenAI is able to produce audio and maybe even video files that are flawless replicas of the original speaker. These kinds of files have been used, among other things, to coerce people into doing harmful things like sending money to online fraudsters.
The mitigation approach should concentrate on making sure that sound cybersecurity practices, such as minimizing the attack surface, detection and response methods, and recovery, are in place, along with thorough staff training and continual education, even if both threats are meant to be challenging to discover. Individuals must be the last line of defense as they are the targeted targets.
Apart from these two, new hazards that GenAI models themselves encounter include prompt injection, manipulation of results, and model theft. Although certain hazards are worth a separate discussion, the general approach is very much the same as safeguarding any other important task. Utilizing Zero Trust principles, lowering the attack surface, protecting data, and upholding an incident recovery strategy have to be the major priorities.Image Credit To Dell
Ransomware as a Service (RaaS)
Ransomware as a Service (RaaS) lets attackers rent ransomware tools and equipment or pay someone to attack via its subscription-based architecture. This marks a departure from typical ransomware assaults. Because of this professional approach, fraudsters now have a reduced entrance barrier and can carry out complex assaults even with less technical expertise. There has been a notable rise in the number and effect of RaaS events in recent times, as shown by many high-profile occurrences.
Businesses are encouraged to strengthen their ransomware attack defenses in order to counter this threat:
Hardware-assisted security and Zero Trust concepts, such as network segmentation and identity management, may help to reduce the attack surface.
Update and patch systems and software on a regular basis.
Continue to follow a thorough incident recovery strategy.
Put in place strong data protection measures
IoT vulnerabilities
Insufficient security makes IoT devices susceptible to data breaches and illicit access. The potential of distributed denial-of-service (DDoS) attacks is increased by the large number of networked devices, and poorly managed device identification and authentication may also result in unauthorized control. Renowned cybersecurity researcher Theresa Payton has even conjured up scenarios in which hackers may use Internet of Things (IoT) devices to target smart buildings, perhaps “creating hazmat scenarios, locking people in buildings and holding people for ransom.”
Frequent software upgrades are lacking in many IoT devices, which exposes them. Furthermore, the deployment of more comprehensive security measures may be hindered by their low computational capacity.
Several defensive measures, such assuring safe setup and frequent updates and implementing IoT-specific security protocols, may be put into place to mitigate these problems. These protocols include enforcing secure boot to guarantee that devices only run trusted software, utilizing network segmentation to separate IoT devices from other areas of the network, implementing end-to-end encryption to protect data transmission, and using device authentication to confirm the identity of connected devices.
Furthermore, Zero Trust principles are essential for Internet of Things devices since they will continuously authenticate each user and device, lowering the possibility of security breaches and unwanted access.
Overarching Techniques for Fighting Cybersecurity Risks
Regardless of the threat type, businesses may strengthen their security posture by taking proactive measures, even while there are unique tactics designed to counter certain threats.
Since they provide people the skills and information they need to tackle cybersecurity risks, training and education are essential. Frequent cybersecurity awareness training sessions are crucial for fostering these abilities. Different delivery modalities, such as interactive simulations, online courses, and workshops, each have their own advantages. It’s critical to maintain training sessions interesting and current while also customizing the material to fit the various positions within the company to guarantee its efficacy.
Read more on govindhtech.com
#Reduce5G#CybersecurityRisks#5Gservice#ZeroTrust#generativeAI#cybersecurity#strongdata#onlinecourses#SurfaceVulnerabilities#GenAImodels#databreaches#OverarchingTechniques#technology#CybersecurityThreats#technews#news#govindhtech
2 notes
·
View notes
Text
Understanding Ransomware: A Guide for Small Businesses
Ransomware is a malicious software that restricts access to your device or data until a ransom is paid. In this article, we explore how ransomware enters your system, how it works, and how to prevent attacks. A ransomware attack occurs when malware prevents access to your device or data until a ransom is paid. Attackers may threaten to publish data if the ransom is not paid. Ransomware can be locker ransomware, which locks access, or crypto ransomware, which encrypts files. Ransomware usually enters a device, assesses critical data, encrypts files, and demands a ransom. Paying the ransom doesn't guarantee recovery, so it's not recommended. Historical ransomware attacks include CryptoLocker, CryptoWall, Locky, WannaCry, NotPetya, and more. To prevent ransomware, you can have good network policies, secure servers, backup data offline and online, and encourage safe online behavior. Installing security software like antivirus, firewall, and email filtering can also help. Advanced strategies include ATP, email filtering, and security audits. In case of a ransomware infection, isolate the device, assess damage, check for a decryption key, and restore from backups. Seek professional help for recovery. Immediate actions post-infection include isolation, incident response activation, legal compliance, and stakeholder communication. Ransomware can get on your device through spam emails, phishing, pop-ups, pirated software, weak passwords, and more. Attackers prefer cryptocurrency payments for anonymity. Ransomware can spread through Wi-Fi, infecting all connected devices. Protect yourself from ransomware by following the prevention strategies mentioned above. Stay safe online and be cautious of suspicious emails, links, and downloads. And remember, it's crucial to have backups and a plan in case of a ransomware attack. #StartupBusiness #Businesses #Guide #howdoesransomwarework #Ransomware #ransomwareattack #Small #Understanding #whatisaransomware #whatisaransomwareattack #whatisransomware https://tinyurl.com/228z9vpf
#Businesses#Guide#how does ransomware work#Ransomware#ransomware attack#Small#Understanding#what is a ransomware#what is a ransomware attack#what is ransomware
1 note
·
View note
Text
Synology Data Recovery: A Comprehensive Guide
Synology is renowned for its NAS (Network Attached Storage) devices, which offer robust data storage solutions for both personal and business use. Despite their reliability and advanced features, data loss can still occur due to various reasons. This guide provides a comprehensive overview of Synology data recovery, covering the causes of data loss, the steps to recover lost data, and best practices to safeguard your data.
Understanding Synology NAS
Synology NAS devices are designed to provide a centralized and accessible storage solution with features such as RAID (Redundant Array of Independent Disks) configurations, data protection, and easy-to-use interfaces. They support multiple users and applications, making them a versatile choice for data storage and management.
Common Causes of Data Loss
Data loss in Synology NAS devices can result from various scenarios, including:
1. Hardware Failures
Disk Failure: Hard drives can fail due to age, physical damage, or manufacturing defects.
Power Surges: Electrical surges can damage the Synology NAS’s internal components.
Overheating: Inadequate cooling can lead to overheating, causing hardware malfunctions.
2. Software Issues
Firmware Corruption: Problems during firmware updates or bugs can lead to data corruption.
File System Errors: Corrupt file systems can make data inaccessible.
3. Human Error
Accidental Deletion: Users can mistakenly delete important files or entire volumes.
Misconfiguration: Incorrect setup or configuration changes can lead to data loss.
4. Malicious Attacks
Ransomware: Malware can encrypt data, making it inaccessible until a ransom is paid.
Viruses: Malicious software can corrupt or delete data.
Steps for Synology Data Recovery
When faced with data loss on a Synology NAS device, it’s crucial to follow a structured approach to maximize recovery chances. Here are the steps to follow:
1. Stop Using the Device
Immediately stop using the Synology NAS to prevent further data overwriting. Continuing to use the device can reduce the likelihood of successful data recovery.
2. Diagnose the Problem
Identify the cause of the data loss. Understanding whether the issue is due to hardware failure, software problems, human error, or a malicious attack will help determine the best recovery method.
3. Check Backups
Before attempting data recovery, check if there are any recent backups. Regular backups can save time and effort in the recovery process. If backups are available, restore the lost data from them.
4. Use Data Recovery Software
For minor data loss issues, data recovery software can be an effective solution. Several reliable tools support Synology NAS devices:
R-Studio: A powerful tool for recovering data from various storage devices, including Synology NAS.
EaseUS Data Recovery Wizard: User-friendly software that can recover files lost due to deletion, formatting, or system crashes.
Stellar Data Recovery: Known for its robust recovery capabilities, supporting Synology NAS and RAID configurations.
5. Consult Professional Data Recovery Services
For severe data loss scenarios, such as hardware failures or extensive corruption, it is advisable to seek help from professional data recovery services. These experts have the tools and knowledge to recover data from damaged Synology NAS devices. Some reputable data recovery companies include:
DriveSavers Data Recovery: Offers specialized services for Synology and other RAID systems, with a high success rate.
Ontrack Data Recovery: Known for its expertise in NAS and RAID recovery, Ontrack provides comprehensive solutions for Synology devices.
Gillware Data Recovery: Provides professional data recovery services, specializing in complex RAID and NAS systems.
6. Prevent Future Data Loss
After successfully recovering your data, implement measures to prevent future data loss:
Regular Backups: Schedule frequent backups to ensure you have up-to-date copies of your data.
Firmware Updates: Keep your Synology firmware updated to protect against bugs and vulnerabilities.
Surge Protectors: Use surge protectors to safeguard against electrical surges.
Proper Ventilation: Ensure adequate ventilation and cooling to prevent overheating.
Conclusion
Data loss on Synology NAS devices, though distressing, can often be remedied with the right approach. By understanding the common causes of data loss and following a systematic recovery process, you can effectively retrieve lost data. Utilize reliable data recovery software or consult professional services for severe cases. Additionally, implementing preventive measures will help safeguard your data against future loss, ensuring that your Synology NAS device continues to serve as a reliable data storage solution.
2 notes
·
View notes
Text
Top Tips to Build a Secure Website Backup Plans

Why Website Backup Is Crucial
Website backup is a critical aspect of website management, offering protection against various threats and ensuring smooth operations. Here's an in-depth look at why website backup is essential:
1. Protection Against Data Loss: During website development, frequent changes are made, including code modifications and content updates. Without proper backup, accidental deletions or code errors can lead to irrecoverable data loss.
2. Safeguarding Against Cyber Attacks: Malicious cyber attacks, including ransomware, pose a significant threat to websites. Regular backups provide a safety net, allowing businesses to restore their websites to a pre-attack state quickly.
3. Mitigating Risks of Hardware and Software Failures: Hardware failures or software glitches can occur unexpectedly, potentially resulting in data corruption or loss. Website backup ensures that data can be restored swiftly in such scenarios.
4. Facilitating Smoother Updates and Overhauls: Website updates and overhauls are inevitable for staying current and meeting evolving requirements. Having backups in place streamlines these processes by providing a fallback option in case of unforeseen issues.
Understanding Website Backup
What is Website Backup? Website backup involves creating duplicate copies of website data, including media, code, themes, and other elements, and storing them securely to prevent loss or damage.
Components of Website Backup:
Website Files: Includes all website data such as code files, media, plugins, and themes.
Databases: Backup of databases like MySQL or PostgreSQL, if utilized.
Email Sending: Backup of email forwarders and filters associated with the website.
Tips for Secure Website Backup Planning
1. Choose the Right Backup Frequency: Frequency depends on website traffic, update frequency, and content sensitivity.
2. Opt for Third-Party Backup Solutions: Consider factors like storage capacity, automation, security features, and user-friendliness.
3. Utilize Backup Plugins for WordPress: Plugins like UpdraftPlus, VaultPress, and others offer secure and automated backup solutions.
4. Maintain Offsite Backups: Store backups in remote data centers or cloud services for added security.
5. Test Your Backups: Regular testing ensures backup integrity and readiness for restoration.
6. Supplement Hosting Backup Services: While hosting providers offer backups, explore additional backup solutions for enhanced security and control.
7. Consider Manual Backups: Manual backups provide flexibility and control, especially for specific needs or scenarios.
8. Encrypt Backup Data: Encrypting backup files adds an extra layer of security, preventing unauthorized access.
9. Monitor Backup Processes: Regular monitoring helps identify issues promptly and ensures backup availability.
10. Implement Disaster Recovery Plans: Prepare for unforeseen events with comprehensive disaster recovery strategies.
Secure Website Backup Service with Servepoet
For comprehensive website backup solutions, consider CodeGuard Backup service, offering automated daily backups, robust encryption, and user-friendly management features.
Conclusion
Building a secure website backup plan is vital for protecting against data loss, cyber threats, and operational disruptions. By following best practices and leveraging reliable backup solutions, businesses can safeguard their websites and ensure continuity of operations.
#buy domain and hosting#best domain hosting service#domain hosting services#marketing#cloud vps providers#web hosting and server#shared web hosting
2 notes
·
View notes
Text
How to survive a cyberattack: A cyberattack survival guide

The modern world runs on data, and unfortunately, so do modern criminals. Cyberattacks are no longer abstract threats; they are a stark reality for individuals and businesses alike. From phishing scams that trick you into revealing your passwords to ransomware that locks up your precious files, the question isn't if you'll face a cyberattack, but when.
Panic is the enemy of effective response. A clear, actionable plan, much like a fire drill, can drastically minimize damage and speed up recovery. This is your cyberattack survival guide.
Before the Storm: Preparation is Key
Prevention is always better than cure. Invest time in these foundational steps:
Strong Passwords & Multi-Factor Authentication (MFA):
Use long, complex, and unique passwords for every account. A password manager is your best friend here.
Crucially, enable MFA on every account that offers it. This adds a vital second layer of defense. Even if your password is stolen, the attacker can't get in without that second factor.
Regular Backups:
Back up your critical data (documents, photos, videos) frequently to an external hard drive or a reputable cloud service.
Crucial Tip: Keep at least one backup offline (disconnected from your network) to protect it from ransomware.
Keep Software Updated:
Enable automatic updates for your operating system (Windows, macOS, iOS, Android) and all applications. Patches often fix security vulnerabilities that criminals exploit.
Install Antivirus/Anti-malware Software:
Use reputable security software and keep its definitions updated. Run regular scans.
Be Phishing-Savvy:
Learn to recognize phishing emails, texts, and calls. Never click suspicious links or open attachments from unknown senders. Always verify the sender's identity and the URL before entering credentials.
Understand Your Digital Footprint:
Limit the personal information you share online. Review your privacy settings on social media and other platforms.
During the Attack: Act Fast, Isolate, Assess
This is the critical phase. Your immediate actions can determine the severity of the damage.
Signs You Might Be Under Attack:
Unexpected Pop-ups or System Messages: Especially those demanding payment.
Locked Files or a Ransom Note: Clear sign of ransomware.
Unusual Account Activity: Emails sent from your account that you didn't write, strange transactions, or unauthorized logins.
Device Performance Issues: Your computer running unusually slow, crashing, or programs opening/closing on their own.
Mouse Moving Autonomously: A chilling sign someone has remote control.
Antivirus/Firewall Disabled: Attackers often try to disable your security software.
Friends/Contacts Receiving Strange Messages from You: Indicates your account is compromised.
Immediate Actions – The "Cyber 911":
DISCONNECT IMMEDIATELY: This is your absolute first priority.
For Wi-Fi: Turn off Wi-Fi on your device(s). For a home network, unplug your router.
For Ethernet: Unplug the Ethernet cable from your computer.
Why? This prevents the attack from spreading (if it's malware/ransomware) or stops data exfiltration. Do not shut down your device if it's a ransomware attack, as it might erase crucial forensic evidence or corrupt encryption in progress. Just disconnect.
Identify the Nature of the Attack:
Is it ransomware? (Files encrypted, ransom note).
Is it a compromised account? (Unauthorized emails, social media posts).
Is it general malware? (Slow performance, pop-ups).
Knowing the type helps guide your next steps.
Document Everything:
Take screenshots of ransom notes, error messages, suspicious activity, or unusual changes.
Note down dates, times, and any specific details (e.g., wallet addresses in a ransom note). This will be crucial for recovery and potentially for law enforcement.
Isolate Affected Devices/Systems:
If you have other devices connected to the same network, assume they might also be compromised. Disconnect them all.
If it's a business, follow your Incident Response Plan to contain the breach.
DO NOT Pay the Ransom (for Ransomware):
This only encourages criminals and there's no guarantee you'll get your files back. It also makes you a target for future attacks.
Aftermath & Recovery: Rebuilding Your Digital Security
Once the immediate threat is contained, it's time for methodical recovery.
Change Passwords (Crucially!):
Use another, uncompromised device.
Start with your most critical accounts: Email (especially the one linked to password resets), banking, social media, and any cloud storage.
Change all passwords that might have been compromised, especially if you reuse them.
Ensure MFA is enabled on all these accounts.
Scan and Clean Your Device(s):
Once disconnected from the internet, run a full, deep scan with your updated antivirus/anti-malware software.
Consider using a specialized malware removal tool (many are free to download).
If heavily infected, a factory reset and reinstalling your operating system might be the safest option, then restoring from a clean backup.
Restore Data from Backups:
If you have clean, offline backups, now is the time to restore your files.
Notify Relevant Parties:
Financial Institutions: If banking details or credit card information was exposed, contact your bank and credit card companies immediately to report fraudulent activity and potentially freeze accounts.
Credit Bureaus: Consider placing a fraud alert or credit freeze with credit reporting agencies.
Family/Friends/Colleagues: If your email or social media accounts were compromised, warn your contacts that they might receive suspicious messages from you.
Service Providers: If a specific online service was breached (e.g., an e-commerce site, email provider), contact them.
Law Enforcement (Optional but Recommended): Report the incident to relevant cybercrime units or the national cyber security agency. This helps authorities track threat actors.
For Businesses: This stage involves notifying stakeholders, customers (if PII was exposed, often legally mandated), and potentially regulatory bodies. Engage legal counsel.
Strengthen Your Defenses:
Review and update your security habits. What went wrong?
Improve your password hygiene (longer, more complex, unique, password manager).
Reinforce MFA usage.
Educate yourself and your family/employees on the latest cyber threats.
Consider advanced security solutions if you're a business (e.g., EDR, SIEM).
Test your backups regularly.
A cyberattack is a distressing experience, but it doesn't have to be devastating. By preparing in advance, acting decisively during the event, and executing a methodical recovery plan, you can significantly mitigate the impact and bounce back stronger. Think of this guide not as a list of chores, but as your essential toolkit for navigating the unpredictable digital wilderness. Stay vigilant, stay prepared, and stay safe.
0 notes
Text
Mastering Digital Defense: Advanced Security Risk Detection and Domain Monitoring with risikomonitor.com GmbH
In today’s hyperconnected world, where cyberattacks grow more sophisticated by the day, digital security has evolved from being a technical function to a critical business priority. Companies, whether startups or enterprises, must prioritize security risk detection, active vulnerability management, and reliable domain security monitoring to protect sensitive data, customer trust, and business continuity.
This is exactly where risikomonitor.com GmbH steps in—offering a centralized, intelligent platform that empowers organizations to detect, assess, and respond to risks with unmatched speed and accuracy.
In this blog, we’ll explore how risikomonitor.com GmbH leverages cutting-edge technology to deliver smart solutions for security risk mitigation, real-time domain monitoring, and continuous vulnerability tracking.
The Need for Proactive Security Risk Detection
Many organizations only react to threats after they occur—when data is already compromised or operations are disrupted. This reactive approach is both dangerous and costly.
Security risk detection flips the script by enabling businesses to anticipate threats before they cause harm. Instead of relying on quarterly audits or static risk reports, modern risk detection uses real-time data analysis, behavioral monitoring, and threat intelligence to identify suspicious activity the moment it starts.
risikomonitor.com GmbH provides real-time dashboards that allow businesses to monitor:
Network anomalies and unauthorized access attempts
Unusual login patterns or file modifications
Emerging vulnerabilities across internal and external systems
Early warning signs of ransomware or phishing campaigns
By detecting these risks early, companies can isolate threats, minimize damage, and respond strategically—saving time, money, and reputation.
Vulnerability Management Platform: Centralized Risk Control
While detection is crucial, knowing where your systems are vulnerable is even more important. That’s where a vulnerability management platform becomes indispensable.
A robust vulnerability management platform should:
Continuously scan all endpoints, servers, and applications
Prioritize vulnerabilities based on severity (CVSS scoring)
Suggest or automate patching and configuration fixes
Track remediation progress and timelines
Generate reports for IT teams and auditors
risikomonitor.com GmbH offers a complete solution, giving users a clear view of which digital assets are most at risk—and what action needs to be taken. With automated scanning and vulnerability intelligence, businesses can shift from reactive fire-fighting to structured prevention.
Whether you’re managing 10 devices or 10,000, the platform is scalable and cloud-ready, offering seamless integration into your existing IT infrastructure.
Security Risk Mitigation: Turning Insight into Action
Identifying risks is only half the battle—security risk mitigation is where the real protection happens. Mitigation refers to the process of reducing or eliminating potential security threats before they can be exploited.
risikomonitor.com GmbH empowers businesses to mitigate risks through:
Real-time patch management and system updates
Role-based access controls and privilege monitoring
Encryption of sensitive data at rest and in transit
Backup and recovery protocols for high-risk systems
Automated alerts and incident response recommendations
The platform also provides customized playbooks and compliance-ready documentation to help IT teams follow industry standards like ISO 27001, NIS2, or GDPR.
By combining risk detection with strategic mitigation, risikomonitor.com GmbH helps clients build a resilient cybersecurity ecosystem—not just a temporary fix.
Domain Security Monitoring: Protecting Your Digital Identity
Your domain is your brand’s digital identity—and it’s constantly under attack. From phishing sites using lookalike domains to unauthorized DNS changes and expired SSL certificates, domain-level threats are often overlooked but extremely dangerous.
Domain security monitoring by risikomonitor.com GmbH covers:
Detection of spoofed or fraudulent domains
Monitoring DNS records for unauthorized changes
SSL certificate status tracking and alerts
Detection of email spoofing threats (SPF, DKIM, DMARC checks)
Monitoring public repositories for leaked domain-related credentials
These insights allow businesses to respond instantly if something goes wrong. Whether it’s a hijacked subdomain, a cloned website, or an expired certificate, risikomonitor.com GmbH keeps a constant eye on your domain environment to prevent damage to brand reputation and user trust.
Why Choose risikomonitor.com GmbH?
In a crowded market of cybersecurity tools, risikomonitor.com GmbH stands out by offering a unified solution that combines:
Intelligent risk detection using machine learning and real-time analysis
Automated vulnerability management with built-in remediation tools
Customizable security risk mitigation playbooks
24/7 domain monitoring for total visibility and control
Compliance-ready reporting for EU, US, and global standards
The platform is ideal for SMBs, mid-market companies, and enterprise teams looking to consolidate multiple tools into a single, efficient system.
Final Thoughts
In 2025 and beyond, cybersecurity can’t be passive. Modern businesses must take an active role in defending their digital assets—and that starts with smarter tools, faster detection, and continuous visibility.
With a robust vulnerability management platform, real-time security risk detection, strategic risk mitigation, and reliable domain security monitoring, risikomonitor.com GmbH gives you the power to stay ahead of cyber threats before they become business disasters.
0 notes
Text
How Experienced Ransomware Negotiation Firms Can Save Your Business Millions?
Ransomware attacks have become a widespread and costly threat for businesses across all industries. When cybercriminals encrypt sensitive data and demand a ransom, companies are often left vulnerable, confused, and desperate. This is where ransomware negotiation firms play a vital role. These specialized firms are equipped with the expertise, tools, and strategies to handle such critical situations professionally. By stepping in immediately after an attack, they help businesses assess the damage, open secure lines of communication with threat actors, and negotiate for data release while minimizing financial loss. Their involvement is essential for a structured and effective ransomware response plan.
How Ransomware Negotiation Firms Protect Your Business Assets?
One of the most important functions of ransomware negotiation firms is safeguarding a company’s digital and financial assets during a cyberattack. These firms analyze the ransomware strain, assess the attacker’s credibility, and determine whether payment is justified or even wise. They ensure sensitive business data isn’t further exposed or exploited by guiding communication protocols and leveraging encryption tactics. By negotiating strategically, they reduce the risk of double extortion and prevent overpayment. Their role is not just to retrieve files but to shield the company from broader damage, such as reputational harm, regulatory penalties, and additional cyber threats in the future.
The Financial Risks of Unplanned Ransomware Responses
An unplanned ransomware response can lead to overwhelming financial consequences. Without the guidance of ransomware negotiation firms, many businesses make impulsive decisions—like overpaying ransom demands or miscommunicating with threat actors. These errors often result in partial or no recovery of encrypted data and can even attract repeated attacks. Additionally, businesses may incur regulatory fines for non-compliance if personal data is compromised. Ransomware negotiation experts help minimize such financial risks by evaluating every angle—legal, technical, and strategic. Their calculated methods not only reduce ransom payouts but also help organizations avoid prolonged downtime, data loss, and loss of customer trust and revenue.
Why Expert Negotiators Can Reduce Ransom Demands?
Cybercriminals often inflate ransom demands, hoping that businesses will pay out of panic. Ransomware negotiation firms deploy seasoned experts who specialize in defusing these high-pressure situations. Through experience and proven tactics, these professionals can challenge the attackers’ demands, question the value of the stolen data, and propose realistic payment alternatives—often resulting in a significantly reduced ransom. By presenting the attackers with convincing counterarguments, negotiators can lower costs and stretch out deadlines, buying time for alternative solutions. In many cases, the presence of a professional negotiation team itself discourages attackers from pushing unrealistic terms or engaging in prolonged cyber extortion.
How Ransomware Negotiation Firms Manage High-Stakes Talks?
Every ransomware attack involves delicate, high-stakes communication with potentially dangerous cybercriminals. Ransomware negotiation firms are trained to handle these talks with precision and caution. They communicate through secure and anonymous channels while maintaining a non-confrontational tone to avoid escalation. These firms assess threat actor behavior patterns, validate decryption keys when offered, and avoid triggering additional demands. With carefully chosen wording and psychological insights, they guide conversations toward resolution. This managed process ensures that no sensitive information is leaked and that the business remains legally protected. Their expertise ensures a professional response even when the pressure is immense and time is critical.
Cutting Downtime with Strategic Ransomware Negotiations
Time is money, especially during a ransomware attack that brings business operations to a halt. Ransomware negotiation firms focus on cutting downtime by quickly engaging with threat actors and initiating structured discussions. Their deep understanding of cybercriminal psychology allows them to move negotiations forward efficiently without compromising security. These firms often work alongside IT recovery teams, helping to retrieve data through decryption keys or guiding alternative recovery solutions. The faster the resolution, the quicker businesses can return to normal operations. With the right negotiators in place, companies can drastically reduce system outages, avoid revenue loss, and minimize disruption to clients.
Avoiding Legal Trouble Through Expert Ransomware Guidance
Ransomware responses involve complex legal risks, especially when handling sensitive customer data or engaging with internationally sanctioned groups. Ransomware negotiation firms help businesses navigate these legal minefields with informed guidance. They ensure all negotiations comply with national and international cybersecurity regulations, including laws regarding ransom payments and disclosure obligations. Failing to follow proper procedures can result in hefty fines or lawsuits. These firms consult legal experts to validate payment legality, document the negotiation process, and prepare businesses for regulatory reporting. Their oversight ensures that companies act lawfully and ethically during the crisis, preventing further consequences beyond the initial ransomware threat.
How Ransomware Negotiation Firms Help Recover Encrypted Data?
Recovering encrypted data after a ransomware attack is often the top priority for affected organizations. Ransomware negotiation firms work toward this goal by coordinating directly with threat actors to obtain decryption keys in a secure and verified manner. These firms test the functionality of keys before any payment is made, ensuring the data can actually be restored. In some cases, they collaborate with forensic and cybersecurity teams to find alternative recovery options, like backups or shadow copies. Their experience helps determine the credibility of attackers and negotiate terms that lead to real data recovery—not just false promises or scams.
Conclusion
In today’s cyber-threat landscape, relying on untrained responses to ransomware can lead to disaster. Ransomware negotiation firms provide a lifeline for businesses facing encrypted data, financial blackmail, and legal uncertainty. With their negotiation expertise, knowledge of cybercriminal behavior, and understanding of global regulations, they can reduce ransom demands, shorten downtime, and ensure lawful crisis management. These firms don’t just handle conversations—they lead strategic responses that protect your reputation, data, and bottom line. Whether you're a small business or a multinational enterprise, having a ransomware negotiation team on call is no longer optional—it’s a crucial element of modern cybersecurity defense.
0 notes
Text
Technokraft Serve: The Best Managed IT Service Provider In San Antonio

In today’s highly competitive digital world, businesses in every industry must rely on technology to thrive, scale, and stay secure. From managing sensitive data to ensuring seamless communication across departments, IT is the backbone of modern operations. However, managing IT infrastructure internally can be costly, inefficient, and risky without the right expertise. That’s where a Managed IT Service Provider In San Antonio comes into play.
Among the many options available, Technokraft Serve has consistently emerged as the Best Managed IT Service Provider for organizations of all sizes and sectors. With cutting-edge solutions, 24/7 support, and a client-first approach, Technokraft Serve continues to lead as a trusted MSP Company In San Antonio.
Understanding the Role of a Managed IT Service Provider
A Managed IT Service Provider is more than just a support team—it’s a strategic partner. A Managed IT Service Provider In San Antonio offers proactive, ongoing monitoring and maintenance of your entire IT ecosystem. These services include:
Network management
Cybersecurity solutions
Cloud services
Help desk support
IT consulting
Data backup and disaster recovery
Compliance assurance
Choosing the Best Managed IT Service Provider helps you reduce downtime, cut costs, protect your data, and future-proof your business operations.
Why Technokraft Serve is the Best Managed IT Service Provider
1. End-to-End IT Management
Technokraft Serve provides complete IT solutions under one roof. From server management to cloud migration and endpoint security, the company delivers a full suite of services. This makes it easier for businesses to consolidate vendors and trust a single MSP Company In San Antonio for all their IT needs.
Their ability to deliver both reactive support and proactive maintenance ensures that your systems are always up and running.
2. Expert Team with Industry Certifications
One of the top reasons why Technokraft Serve is recognized as the Best Managed IT Service Provider is its experienced and highly certified technical team. With deep knowledge of the latest technologies, cybersecurity threats, and industry compliance standards, they deliver enterprise-level services to small, mid-sized, and large businesses alike.
No other Managed IT Service Provider In San Antonio offers the same level of talent combined with hands-on problem-solving and strategy-building.
3. 24/7 Proactive Monitoring
Downtime can severely impact revenue and brand reputation. That’s why Technokraft Serve uses advanced monitoring tools to detect potential issues before they escalate. Their real-time alerts and 24/7 IT support make them the Best Managed IT Service Provider for companies that prioritize business continuity.
4. Cybersecurity That Meets Enterprise Standards
As cyber threats become more complex, businesses must prioritize security. Technokraft Serve implements advanced cybersecurity protocols to protect networks, data, and users. Their layered security approach includes firewall protection, intrusion detection, ransomware prevention, and data encryption.
For businesses searching for a security-focused Managed IT Service Provider In San Antonio, Technokraft Serve offers peace of mind through constant vigilance and innovation.
Industry-Specific IT Solutions
What truly makes Technokraft Serve the Best Managed IT Service Provider is their tailored approach to different industries. Understanding that no two businesses are the same, they deliver industry-specific solutions such as:
Healthcare IT – HIPAA-compliant systems and secure data handling
Finance – Regulatory-compliant network security and transaction safety
Retail & E-commerce – POS support, online inventory management, and customer data protection
Legal – Secure case file storage, communication tools, and document recovery
Manufacturing – ERP integration, automation support, and infrastructure scalability
Every solution is backed by expert consultation, planning, deployment, and ongoing support—making Technokraft Serve the most dynamic MSP Company In San Antonio.
Cloud Services That Enable Scalability
Businesses in San Antonio are increasingly adopting cloud technology, and Technokraft Serve is leading the transformation. As the Best Managed IT Service Provider, they assist with cloud migration, hybrid infrastructure deployment, and multi-cloud strategy development.
Whether your business needs Microsoft Azure, Google Cloud, or AWS integration, Technokraft Serve, the most trusted Managed IT Service Provider In San Antonio, ensures seamless performance and secure access to cloud resources.
Data Backup and Disaster Recovery
Disasters—natural or digital—can strike without warning. The difference between survival and shutdown often lies in having a solid recovery plan. Technokraft Serve offers robust data backup and disaster recovery solutions. Their reliable systems ensure minimal downtime and quick restoration of data, keeping your business operational even during the worst scenarios.
This forward-thinking approach is another reason why they’re widely acknowledged as the Best Managed IT Service Provider in San Antonio.
Regulatory Compliance and Risk Management
Industries like healthcare, finance, and education face strict compliance requirements. Technokraft Serve ensures your IT systems meet regulations such as HIPAA, PCI-DSS, and GDPR. With regular audits, risk assessments, and policy enforcement, they act as your compliance partner—not just your MSP Company In San Antonio.
Real-Time Support, Real Results
Client satisfaction is the cornerstone of Technokraft Serve’s success. They don’t just offer services—they build long-term partnerships. Their clients benefit from:
Fast, knowledgeable IT support
Zero hidden fees
Custom IT roadmaps
Scalability at every stage of growth
It’s no wonder they’ve become known throughout the city as the Best Managed IT Service Provider. Businesses continually turn to them because they not only solve problems—they help clients avoid them altogether.
Why Businesses Trust Technokraft Serve Over Other MSP Companies In San Antonio
Strategic IT Planning – Not just reactive, but visionary in approach
Affordable Pricing – Transparent plans tailored to all business sizes
Local Expertise – A deep understanding of San Antonio’s business environment
Scalable Solutions – Grow your IT systems as your business grows
Consistent Recognition – Repeatedly rated the Best Managed IT Service Provider
Conclusion
Choosing an MSP is not just about outsourcing IT—it’s about choosing a partner who can align technology with your business strategy. With years of experience, a customer-focused team, and results that speak for themselves, Technokraft Serve stands tall as the Best Managed IT Service Provider in San Antonio.
Whether you’re launching a startup or managing an enterprise, working with Technokraft Serve, the top-rated Managed IT Service Provider In San Antonio, ensures your IT infrastructure is efficient, secure, and future-ready.
Don’t settle for average IT support. Partner with the Best Managed IT Service Provider and elevate your business to the next level—Technokraft Serve is ready to lead the way.
0 notes
Text
Anubis Ransomware Encrypts and Wipes Files, Making Recovery Impossible Even After Payment
http://i.securitythinkingcap.com/TLNYg3
0 notes
Text
Ascension Ransomware Hack Began by Employee Downloading a File

Ascension, a leading private healthcare provider in the United States, has revealed that a ransomware attack on its systems has potentially compromised patients' protected health information (PHI) and personally identifiable information (PII). The cybersecurity incident in May 2024 forced the organization to divert ambulances, postpone patient appointments, and temporarily disable access to electronic health records (EHR) and other critical systems.
Accidental Download Leads to Breach
In an update on June 12, an Ascension spokesperson disclosed that the ransomware attack was initiated after an employee accidentally downloaded a malicious file masquerading as legitimate. The company emphasized that this was an "honest mistake" and that there was no evidence to suggest the employee acted with malicious intent. However, the accidental download allowed the ransomware attackers to gain unauthorized access to Ascension's systems, resulting in widespread disruption and potential data breach. According to Ascension, there is evidence indicating that the attackers were able to steal files from seven servers used by associates for daily and routine tasks. These files may contain sensitive PHI and PII data of patients. The specific data accessed and the individuals affected are still being investigated by third-party cybersecurity experts. Ascension has stated that it will notify affected individuals and regulatory bodies once the full extent of the data breach is determined.
Recovery Efforts and Precautionary Measures
As of June 11, Ascension reported successfully restoring EHR access for 14 locations, with plans to complete the restoration process by June 14. However, medical records and other information collected during the system downtime may not be immediately accessible. To address potential identity theft concerns, Ascension is offering complimentary credit monitoring and identity theft protection services to any patient or associate who requests it.
Wider Impact on Healthcare Services
The ransomware attack on Ascension is part of a broader trend of cybersecurity incidents targeting healthcare providers and their suppliers. In the UK, two leading London hospitals were forced to cancel operations and divert emergency patients in early June due to a cyber-attack on a critical pathology services supplier. The incident prompted an urgent appeal from the NHS for blood donors and volunteers to mitigate the immediate and significant impact on blood transfusions and test results. As the investigation into the Ascension data breach continues, healthcare organizations and cybersecurity experts alike emphasize the importance of robust security measures, employee training, and incident response plans to safeguard sensitive patient data and ensure the continuity of critical medical services. Read the full article
2 notes
·
View notes
Text
Why San Luis Obispo Trusts Local Cyber Experts?
In today’s connected world, data is everywhere on phones, computers, smart TVs, and cloud platforms. From online banking and shopping to running small businesses remotely, people rely heavily on digital access. But with this convenience comes vulnerability. Cybercrime is no longer reserved for large corporations; it's affecting households, startups, and local service providers alike. San Luis Obispo is not just charming, it’s becoming digitally active. As online threats grow, locals like you are turning to trusted, nearby cyber experts. Why rely on distant firms when local pros understand your needs, speak your language, and offer real protection that feels personal and reliable? Keep reading.
Why Local Cyber Security Services Matter More Today?
Cyber threats are evolving fast. Phishing emails, ransomware, data breaches, and identity theft have become more frequent and more sophisticated. For individuals and small business owners in San Luis Obispo, the stakes are high. Losing access to important files, compromising customer data, or falling victim to scams disrupts not just business operations but personal peace of mind. That’s where local cybersecurity services in San Luis Obispo step in. Local experts offer not only technical knowledge but also immediate response and personalized protection strategies. Unlike large corporate firms, they are part of the community, trusted, approachable, and invested in long-term solutions.
The Value of Choosing Local Over Remote Solutions
Local providers understand the specific needs of their region. Whether protecting a small winery’s transaction system or helping a family secure their smart home devices, these experts tailor solutions based on the client’s actual lifestyle and tech usage.
Here’s what makes them stand out:
Personalized Risk Assessments – One-size-fits-all security doesn't work. Local professionals evaluate each client’s unique vulnerabilities before implementing layered protection.
Faster Response Times – Immediate action is critical during a cyber incident. Being nearby allows for quicker recovery and less downtime.
Ongoing Education & Support – Many providers run community workshops or provide helpful resources on phishing awareness, password hygiene, and software security.
Relationship-Driven Service – Trust matters. Working with a provider who understands local business culture adds an extra layer of reliability.
Why Santa Barbara Leads in Cyber Resilience?
Just down the coast, a digital security service provider in Santa Barbara service providers are also playing a key role in shaping a secure online future for the region. With a broader pool of resources, specialized services, and advanced monitoring tools, they serve as an extended digital safety net for both San Luis Obispo and Santa Barbara residents.
These providers specialize in:
Network monitoring and threat detection.
Endpoint protection for devices.
Data backup and recovery planning.
Secure cloud storage and remote work environments.
Compliance with industry-specific security regulations.
Their services support businesses ranging from retail and hospitality to education and healthcare.
Trust Built Through Results, Not Promises
The increasing reliance on digital tools, especially after the remote work surge, has made cybersecurity more than a technical issue; it’s now a quality-of-life matter. Local cyber experts have earned San Luis Obispo’s trust by delivering consistent results, quick response times, and customer-first strategies. These aren't just IT professionals; they are digital guardians who ensure businesses keep running and residents stay protected.
Conclusion
Cybersecurity isn’t something to put off until something goes wrong. Taking proactive steps today helps avoid costly problems tomorrow. Whether it’s a local bakery protecting customer payments or a student shielding their data, digital safety is everyone's responsibility.
Cybersecurity services in San Luis Obispo are leading the charge, empowering the community with smart, secure, and sustainable protection. When it comes to safeguarding your digital world, local truly means loyal, reliable, and effective.
0 notes