#securityarchitecture
Explore tagged Tumblr posts
Text
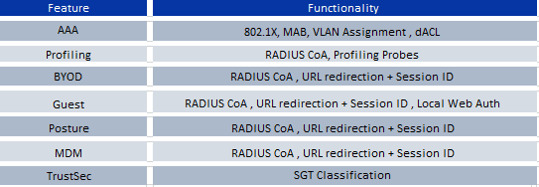

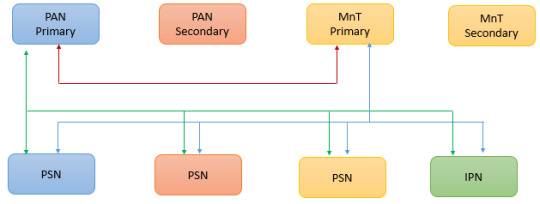
Explore Cisco ISE building blocks and design considerations for robust network security and access management. https://www.dclessons.com/ise-building-blocks-design
0 notes
Text
Building the Blueprint for Business Success: Understanding Enterprise Architectures

Source: Image by Maxiphoto from Getty Images Signature
Share Post:
LinkedIn
Twitter
Facebook
Reddit
Pinterest
In today’s complex and evolving business environment, organizations are subject to constant adaptation, innovation, and competitive pressure. One vital element in ensuring these goals will be met lies in the formulation of well-crafted and adequately implemented Enterprise Architectures. This high-level framework serves as a top-down view, giving an organization a holistic idea of its structural, process-oriented, and technologically based forms, thus supporting better alignment of business strategy and IT infrastructure. This article digs into the fundamentals of this lifeblood discipline and its advantages, essential components, and best practices for adopting Enterprise Architectures.
What is the Purpose of a Robust Framework?
A strong framework is the strategic blueprint of an organization’s IT landscape. It is the systematic way to design, plan, implement, and manage IT resources in pursuit of business objectives. This framework makes it easier for organizations to know how the parts of their business interact and what technology can help optimize those interactions. It simplifies the means of clear communication and collaboration for business and IT stakeholders in viewing the organization coherently and consistently.
Key Benefits of a Strategic Approach

A strategic approach benefits organizations of any size in several ways. Some of the most significant advantages include:
1. Business-IT Alignment
An effective approach will ensure that investments in IT support business goals and strategies. Organizations will thus reap the full benefits of their investments in IT while avoiding costly mismatches.
2. Agility and Adaptability
A strong framework provides a proper understanding of the organization’s structure and processes and enables organizations to respond quickly and effectively to market conditions and changing business requirements.
3. Reduced Complexity and Cost
A structured approach helps organizations simplify their IT landscape, eliminate redundancy, and optimize resource usage. This often results in tremendous cost savings and improved operational efficiency.
4. Better Risk Management
An organizational strategic approach can enable the entity to identify and minimize probable risks associated with its IT assets and their related dependencies.
5. Facilitates Innovation
Through a solid framework that will guarantee a stable yet scalable foundation of IT, robustness makes way for testing innovative technologies as the organization advances through innovation.
Core Components of a Comprehensive Framework
A typical comprehensive framework incorporates some of these essential domains:
1. Business Architecture
This domain deals with the definition of the business strategy, goals, processes, and organizational structure of the organization. It provides the context for all other architectural domains.
2. Data Architecture
This domain deals with the definition of the organization’s data assets, data flows, and data management processes. It ensures that data is accurate, consistent, and readily available to support business needs.
3. Application Architecture
This domain deals with the definition of the organization’s application portfolio, application interactions, and application development processes. This ensures that the applications are well-aligned with the business requirements and integrated effectively.
4. Technology Architecture
This domain focuses on defining the organization’s hardware, software, and network infrastructure. It ensures that the technology infrastructure is scalable, reliable, and secure.
Learn More: Unleashing Potential: A Deep Dive into Transformational Leadership Theory
Frameworks and Methodologies

Some well-established frameworks and methodologies can assist organizations in formulating and applying their frameworks. Some of the most popular are:
TOGAF (The Open Group Architecture Framework): The most widely applied framework, with a comprehensive methodology for developing and managing frameworks.
Zachman Framework: This is a classification scheme for the organization of architectural artifacts.
FEAF (Federal Enterprise Architecture Framework): A framework designed by the US Federal government for guiding IT investments.
Implementing a Framework: Best Practices
Implementing a framework is a complex undertaking that requires careful planning and execution. Some best practices for successful implementation include aligning the framework with existing enterprise architectures, ensuring seamless integration with current systems, and ensuring stakeholder engagement throughout the process.
Start with a Clear Business Vision: The implementation should be driven by clear business goals and objectives.
Engage Stakeholders: It is important to involve all key stakeholders, including business leaders, IT professionals, and end-users, in the implementation process.
Take an Iterative Approach: Roll out the framework incrementally, starting from the most critical areas.
Prioritize Value Delivery: Focus on initiatives that will deliver tangible business value soon.
Governance: Establish clear roles, responsibilities, and processes for managing and maintaining the framework.
Learn More: Strategic Planning Frameworks: A Comprehensive Guide to Business Success
The Role of Emerging Technologies
With cloud computing, artificial intelligence, blockchain, and Enterprise Architectures among emerging technologies, organization framework designing and implementation patterns are experiencing the greatest change in this world. In a way, these new opportunities for innovation and efficiency have presented new complexities; organizations have to think more than ever before to put these new pieces of the technological puzzle into place in ways that bring business value forward.
Learn More: Navigating the Future: A Comprehensive Exploration of Emerging Technologies
Adapting to the Future

The business environment change is constantly changing, and it calls for changing the organizational frameworks. A framework, thus, should always have an approach toward continuous improvement to keep up with reviews and updates that keep it relevant and effective. Through this approach, by embracing change and looking forward, organizations can take their frameworks and make use of them for innovative outcomes in the long term.
Conclusion: A Strategic Imperative
In today’s dynamic business environment, it is no longer a luxury but a strategic imperative to have a well-defined and effectively implemented framework. It forms the basis of aligning IT with business strategy, driving innovation, and sustainable growth.
The core concepts, key components, and best practices for implementation of enterprise architectures help organizations leverage its power in building a more agile, efficient, and successful future. It is a crucial element in ensuring that technology serves as a true enabler of business success. This structured approach helps organizations navigate the complexities of modern business and technology, ensuring that they are well-positioned for future growth and success.
#enterprisearchitecture#itarchitecture#technology#cloud#securityarchitecture#futuretechnology#integration
0 notes
Text
Quality and Security Services: Merging Excellence with Innovation
In our Quality and Security Services, we are merging excellence with innovation. We believe in pushing the boundaries, in striving for more. Our unwavering commitment to precision and security is what sets us apart. We are redefining industry standards, fortifying your digital assets against threats, and ensuring unparalleled quality in every aspect of your projects.
Managing who has access to what information is a critical aspect of cybersecurity. This service includes implementing strong authentication methods, managing user identities, and controlling access to ensure that only authorized individuals can access sensitive data.
Designing a secure IT infrastructure from the ground up is a proactive approach to cybersecurity. This service includes designing secure network architectures, implementing secure coding practices, and integrating security measures into the IT infrastructure.
Test Automation tool to provide quality engineering services | Csmart | Covalensedigital
0 notes
Link
Firewall configurations are personalized settings that define how the firewall protects your digital space. These settings determine the firewall's behavior.
0 notes
Text
Securing Distributed Storage and Processing Frameworks
Big Data Security is a critical area of focus as organizations increasingly rely on vast and complex datasets to drive decision-making and innovation.
Ensuring the security of big data involves addressing several key challenges, including data privacy, integrity, and availability. Advanced encryption techniques, such as homomorphic encryption, are employed to protect data at rest, in transit, and during processing, allowing computations to be performed on encrypted data without compromising its confidentiality. Access control mechanisms, including role-based access control (RBAC) and attribute-based access control (ABAC), are crucial in managing permissions and ensuring that only authorized users can access sensitive data. Additionally, the implementation of robust data masking and anonymization techniques helps in safeguarding personally identifiable information (PII) and complying with regulatory requirements such as GDPR and CCPA. Big data environments often utilize distributed storage and processing frameworks like Hadoop and Spark, necessitating comprehensive security measures across multiple nodes and clusters. Security information and event management (SIEM) systems are deployed to monitor and analyze security events in real-time, enabling the detection and mitigation of potential threats. Machine learning algorithms play an increasingly significant role in identifying anomalous patterns and predicting security breaches before they occur. As cyber threats continue to evolve, continuous vulnerability assessments and penetration testing are essential to maintain the security posture of big data infrastructures. The future of big data security lies in the integration of advanced technologies such as blockchain for immutable audit trails and zero-trust architectures to minimize the attack surface and enhance overall data protection. #BigDataSecurity #Encryption #DataPrivacy #AccessControl #DataMasking #Anonymization #GDPR #CCPA #DistributedStorage #SIEM #MachineLearning #CyberSecurity #ThreatDetection #VulnerabilityAssessment #Blockchain #ZeroTrust #DataProtection #HadoopSecurity #SparkSecurity #DataIntegrity #Compliance #DataGovernance #SecurityArchitecture #InformationSecurity #TechInnovation
0 notes
Photo

Excited to share the latest addition to my #etsy shop: Cybersecurity mug Cybersecurity gifts Cybersecurity Expert Definition Mug Funny Definition Gift White Ceramic Cyber Security mug https://etsy.me/3r6jHs4 #cybersecuritytraining #cybersecurityexpert #cybersecurityawareness #hacker #informationsecurity #softwaresecurity #securityarchitecture #pentesting #ciso https://www.instagram.com/p/CRRWUOXBcD6/?utm_medium=tumblr
#etsy#cybersecuritytraining#cybersecurityexpert#cybersecurityawareness#hacker#informationsecurity#softwaresecurity#securityarchitecture#pentesting#ciso
0 notes
Photo

Popular hacking tools used by hackers. ⚠️ Warning ⚠️ - Do not use it for any illegal purpose. 📚Only for educational purposes. 📚 If any illegal action happens, we will not be responsible. Tell us your thoughts in the comments. #cyberradaruniversity #cybersecurity #memes #internetspeed #wifi #bestmemes #instagood #bestoftheday #SecurityArchitecture #SystemDesign #NetworkAdministrator #NetworkAdministration #NetworkManager #NetworkTechnician #SecurityTechnician #NetworkSecurity #NetworkSecurityEngineer #CCENT #CCNA #CCNP #CCIE #hacker #hackertool #hacker #ethicalhacker #databreach (at North Calorina) https://www.instagram.com/p/CNHfgKzABdt/?igshid=py4b4a7eynh7
#cyberradaruniversity#cybersecurity#memes#internetspeed#wifi#bestmemes#instagood#bestoftheday#securityarchitecture#systemdesign#networkadministrator#networkadministration#networkmanager#networktechnician#securitytechnician#networksecurity#networksecurityengineer#ccent#ccna#ccnp#ccie#hacker#hackertool#ethicalhacker#databreach
0 notes
Photo

Shooting buildings within universities is easy, it's a cheat even; wide views, no fence, large expanse - most especially in Nigeria, where every building is guarded by a fence and a gate. I wonder what my photographs will look like when I begin to lack this privilege. #documentinglagosarchitecture #buildinglagos #lagosarchitecture #nigerianarchitecture #securityarchitecture #abstractarchitecture #architecturalphotography #architecturephotographer #architecturalphotographer #documentaryphotography #nigerianarchitecturalphotographer #architectureinafrica #africanarchitecture #documentary #architecture #arquitectura #architettura #architektur #symmetry #geometry #structure #rhythm #facade #nigeria #unilag #lagos #art #yení (at University of Lagos, Nigeria) https://www.instagram.com/p/B2LtBxAljxC/?igshid=1pz3zxodge4u8
#documentinglagosarchitecture#buildinglagos#lagosarchitecture#nigerianarchitecture#securityarchitecture#abstractarchitecture#architecturalphotography#architecturephotographer#architecturalphotographer#documentaryphotography#nigerianarchitecturalphotographer#architectureinafrica#africanarchitecture#documentary#architecture#arquitectura#architettura#architektur#symmetry#geometry#structure#rhythm#facade#nigeria#unilag#lagos#art#yení
0 notes
Photo

IT GURUS OF ATLANTA provides advanced Information System Security.
Click here -: https://bit.ly/2ROc0X6
1 note
·
View note
Photo

Security measure against fraudulent activities, natural disasters, malware, and system penetration attempts like SQL injections and (DDoS).
Click here -: https://bit.ly/2ydw8Lq
0 notes
Photo

IT Security Architecture Frameworks & IT systems migration.
Visit here -: https://bit.ly/2x5Oihw
0 notes
Photo

Security Solutions that encompass every security measure against fraudulent activities.
Click here -: https://bit.ly/2P3AKJC Call us now -: (888) 511-0143
#Information #ITSecurity #RiskManagement #SecurityArchitecture
0 notes
Photo

Information System Security for ALL
Click here-: https://bit.ly/2A2cjYf
#InformationSystem #Security #SecurityITOperations #SecurityArchitecture #Training #Awarenes
1 note
·
View note
Photo

IT GURUS OF ATLANTA provides advanced Information System Security.
Click here -: https://bit.ly/2ROc0X6
#InformationSystemSecurity #SQLinjections #Governance #SecurityArchitecture
0 notes
Photo

Information security protocols and controls according to your organization’s present system and security.
Click here -: https://bit.ly/2TrgBzf Call us -:(888) 511-0143
#SQL #Governance #RiskManagement #SecurityArchitecture
0 notes