#spy whatsapp app
Text

Discover ONEMONITAR’s cutting-edge WhatsApp Spy App, designed to give you real-time access to WhatsApp activities with complete security and ease. Whether you're a concerned parent, a vigilant employer, or looking to ensure personal safety, ONEMONITAR offers a discreet and reliable solution. Monitor chats, calls, and shared media effortlessly, all while staying undetected.
This infographic highlights the key features and benefits of using ONEMONITAR’s WhatsApp Spy App, including seamless tracking, a stealth mode for privacy, and its versatility for different needs. Protect what matters most with ONEMONITAR’s advanced monitoring technology.
0 notes
Text

Discover the WhatsApp Spy App, designed for monitoring conversations discreetly. Track messages, media, and calls with ease. Perfect for parental control or employee monitoring—stay informed effortlessly.
0 notes
Text
5 Powerful WhatsApp Message Trackers to Keep in Control
In today’s digital age, communication has transcended traditional means and has found a dominant platform in messaging apps. Among these, WhatsApp stands out as one of the most widely used platforms, with billions of users globally. Given its popularity, the demand for WhatsApp chat tracker apps has surged, catering to various needs from parental control to monitoring employee communications.
This comprehensive guide explores WhatsApp chat tracker apps, the features that make them indispensable, and the top spy apps with WhatsApp tracker capabilities. Whether you’re a concerned parent, a business owner, or someone with a specific interest in monitoring WhatsApp activity, this guide will provide you with the insights you need to choose the best app for your needs.
Understanding WhatsApp Chat Trackers
What is a WhatsApp Chat Tracker?
A WhatsApp chat tracker is a software application designed to monitor and track conversations and activities on WhatsApp. These trackers provide insights into chats, multimedia exchanges, call logs, and other data transmitted via WhatsApp. The primary objective of these tools is to give users the ability to monitor WhatsApp activities discreetly.
WhatsApp chat trackers are typically used for:
Parental Control: Ensuring children are not exposed to inappropriate content or risky interactions.
Employee Monitoring: Overseeing communication channels in corporate environments to maintain productivity and data security.
Personal Use: Individuals who need to keep an eye on their partner’s or family member’s online activities for various reasons.
How Do WhatsApp Chat Trackers Work?
WhatsApp chat trackers work by capturing data from the target device where WhatsApp is installed. They typically require installation on the target device, after which they operate in stealth mode, meaning the user of the target device remains unaware of the tracking. The collected data is then transmitted to a dashboard accessible by the person monitoring the device.
Key functionalities of WhatsApp chat trackers include:
Message Monitoring: Track and read all incoming and outgoing messages, including deleted ones.
Multimedia Access: View shared images, videos, voice notes, and other multimedia files.
Call Logs: Monitor details of voice and video calls, including time, duration, and contact information.
Contact Information: Access the contact list and view details of the people the target interacts with.
Activity Logs: Track login times, online status, and other app usage patterns.
Top Spy Apps with WhatsApp Tracker Features
When it comes to selecting a WhatsApp tracker, there are numerous spy apps available, each offering a unique set of features tailored for different monitoring needs. Below, we highlight some of the top spy apps that are renowned for their WhatsApp tracking capabilities.
1. HackersList
HackersList is one of the most popular and widely used spy apps for monitoring WhatsApp and other social media platforms. Its user-friendly interface and robust set of features make it a go-to choice for parents and employers alike.
WhatsApp Tracking: HackersList allows users to monitor WhatsApp messages, including group chats, multimedia files, and call logs.
Stealth Mode: Operates in the background, making it undetectable on the target device.
Compatibility: Works on both Android and iOS devices, with or without jailbreaking or rooting.
HackersList provides real-time data synchronization, allowing users to access updates as soon as they occur, making it an excellent tool for continuous monitoring.
2. FlexiSPY
FlexiSPY is another powerful spy app known for its comprehensive monitoring features. It is particularly favored by users who require advanced functionalities beyond basic message tracking.
Advanced WhatsApp Monitoring: FlexiSPY not only tracks WhatsApp messages and multimedia but also records WhatsApp calls.
Remote Access: Provides remote access to the target device, allowing users to control various aspects of the phone.
Detailed Reporting: Offers detailed logs and reports, making it easier to analyze the monitored data.
FlexiSPY is suitable for those looking for an in-depth monitoring solution, though it might require more technical know-how compared to simpler apps.
3. Hoverwatch
Hoverwatch is a versatile monitoring app that offers WhatsApp tracking as part of its broader suite of features. It is particularly popular among users looking for an affordable yet effective monitoring solution.
WhatsApp Message Tracking: Monitor all text messages and multimedia shared via WhatsApp.
Stealth Mode: Remains hidden from the target user, ensuring discreet monitoring.
Multiple Device Tracking: Allows monitoring of multiple devices from a single account.
Hoverwatch’s affordability combined with its effective monitoring features makes it a great option for users on a budget.
4. Cocospy
Cocospy is a lightweight spy app known for its ease of use and reliable performance. It is particularly popular among parents who wish to monitor their children’s online activities.
WhatsApp Chat Monitoring: Provides access to all WhatsApp conversations, including timestamps and contact details.
No Rooting or Jailbreaking: Works without the need for rooting or jailbreaking the target device, making it easier to install and use.
User-Friendly Dashboard: Offers an intuitive dashboard for easy access to monitored data.
Cocospy is an excellent choice for users seeking a straightforward, hassle-free monitoring solution.
5. Spyzie
Spyzie is another top contender in the spy app market, offering a wide range of monitoring features, including WhatsApp tracking. It is particularly known for its detailed and organized reporting.
WhatsApp Monitoring: Tracks all WhatsApp messages, shared files, and call logs.
Data Security: Ensures that the monitored data is secure and accessible only to the user.
Remote Installation: Can be installed remotely on the target device, simplifying the setup process.
Spyzie’s focus on data security and ease of installation makes it a reliable option for those new to monitoring apps.
Choosing the Best WhatsApp Tracker App
With so many options available, selecting the best WhatsApp tracker app can be challenging. The right choice depends on your specific needs, the target device, and your technical comfort level. Here are some factors to consider when choosing a WhatsApp tracker app:
1. Compatibility
Ensure the app is compatible with the target device’s operating system (iOS or Android). Some apps may require jailbreaking or rooting, which can be a technical hurdle for some users. Choose an app that matches your technical capabilities and the device’s specifications.
2. Features
Different apps offer varying levels of functionality. If you need comprehensive monitoring, including call recording and multimedia tracking, opt for apps like FlexiSPY or HackersList. For basic text message tracking, apps like Cocospy or Hoverwatch might suffice.
3. Stealth Mode
Most users prefer apps that operate in stealth mode, ensuring the target user is unaware of the monitoring. Check that the app you choose remains hidden and does not trigger alerts or notifications on the target device.
4. Ease of Use
Consider the user interface and ease of use, especially if you’re not tech-savvy. Apps with intuitive dashboards and simple installation processes are generally more user-friendly.
5. Customer Support
Reliable customer support is crucial, especially if you encounter technical issues. Look for apps that offer robust customer support, including live chat, email, and phone assistance.
6. Pricing
Pricing can vary widely among different spy apps. While some apps offer premium features at a higher cost, others provide basic monitoring at a more affordable rate. Determine your budget and compare the features offered at each price point to make an informed decision.
Legal and Ethical Considerations
While WhatsApp chat tracker apps offer powerful monitoring capabilities, it’s essential to consider the legal and ethical implications of using such software. In many jurisdictions, it is illegal to monitor someone’s communications without their consent. Unauthorized use of spy apps can lead to legal consequences, including fines and imprisonment.
Before using a WhatsApp chat tracker app, ensure that you have the legal right to monitor the target device. For example, parents monitoring their minor children’s devices are generally within their legal rights, while monitoring an adult’s device without consent may violate privacy laws.
Moreover, ethical considerations should not be overlooked. Respecting privacy and using these tools responsibly is paramount. Monitoring should be done with clear intentions, such as protecting minors or securing company data, rather than for malicious purposes.
WhatsApp Message Trackers and Their Impact
The impact of WhatsApp message trackers extends beyond just monitoring conversations. These tools can play a significant role in safeguarding individuals and organizations from various risks.
1. Parental Control and Child Safety
For parents, WhatsApp chat trackers provide a way to protect children from online predators, cyberbullying, and exposure to inappropriate content. By keeping an eye on their children’s communications, parents can intervene when necessary and ensure their child’s online safety.
2. Employee Monitoring and Data Security
In corporate environments, WhatsApp trackers help employers ensure that employees are not engaging in activities that could compromise company data or productivity. Monitoring workplace communications can help prevent data leaks, insider threats, and ensure compliance with company policies.
3. Personal Security and Trust
On a personal level, WhatsApp trackers can be used to protect oneself from potential threats or to maintain trust in relationships. However, this must be balanced with respect for privacy and transparency in relationships.
Future Trends in WhatsApp Tracking Technology
As technology evolves, so too will the capabilities of WhatsApp chat trackers. Here are some future trends to watch for:
1. AI and Machine Learning Integration
Future WhatsApp trackers may integrate AI and machine learning to provide more sophisticated monitoring features. For example, AI could analyze chat patterns to detect potential risks, such as grooming or phishing attempts, and alert the user in real-time.
2. Enhanced Data Security
With increasing concerns about data privacy, future apps
may offer enhanced encryption and data security features to protect the monitored data. This will be especially important for users concerned about the security of the information they are tracking.
3. Multi-Platform Monitoring
As communication becomes more fragmented across various platforms, future trackers may offer multi-platform monitoring, allowing users to track conversations across different messaging apps and social media networks from a single dashboard.
4. Remote Monitoring Enhancements
Remote monitoring capabilities are likely to become more advanced, allowing for easier installation and operation without the need for physical access to the target device. This could include features like cloud-based monitoring and remote updates.
Conclusion
WhatsApp chat tracker apps have become essential tools for parents, employers, and individuals looking to monitor WhatsApp communications. With a wide range of apps available, each offering unique features and capabilities, it’s crucial to choose the one that best meets your needs.
While these tools offer powerful monitoring capabilities, it’s important to use them responsibly and within the bounds of the law. By selecting the right app and using it ethically, you can protect your loved ones, secure your business, and maintain trust in your personal relationships.
As technology continues to advance, the future of WhatsApp tracking promises even more sophisticated and secure monitoring options, ensuring that users can stay ahead of potential risks and challenges in the digital world.
0 notes
Text
Unlocking Family Safety: A Step-by-Step Guide to Activating Google Family Link on Android with SpymasterPro

In the present advanced age, guaranteeing the wellbeing of our friends and family, particularly kids, in the web-based domain is principal.
#wife tracker#cell phone monitoring software#cell spy#whatsapp tracking app#cheating wife on phone#whatsapp tracker#iphone spy#whatsapp spy app#mobile monitoring#spymasterpro
0 notes
Text
Why choose ONEMONITAR for Call Monitoring and Recording?
Hey there!
I stumbled upon ONEMONITAR when I was in a fix managing my work calls and needed a reliable solution for call monitoring and recording. Let me tell you, it's been a game-changer in both my professional and personal life.
I work in sales, and you know how hectic it can get juggling numerous client calls. ONEMONITAR became my trusty sidekick – the superhero of call management. The crystal-clear recording feature saved me more times than I can count. Imagine having a record of every crucial detail discussed in a client meeting! It's like having a backup brain, seriously.
And it's not just about work – even in personal situations, ONEMONITAR has been handy. I once had a call with a service provider that got a bit messy. Thanks to ONEMONITAR, I had proof of the entire conversation, which made sorting things out a breeze.
What sets it apart is the simplicity and reliability. It's not just a tool; it's a stress-buster. So, why choose ONEMONITAR? Because it's not just about recording calls; it's about having peace of mind and control in the palm of your hand.
Read full Blog
0 notes
Text
How safe is today's messengers and can spyware applications be dangerous?
With the proliferation of smartphones and messaging applications, most people do not think about their digital security when exchanging messages. But if you value your privacy, then it’s important to understand the risks that come with using messengers and spyware applications. Here is an article to explain how safe today's messengers are and how spyware applications can be dangerous.
Assessing the Security of Messengers
Security is a top priority for many popular messaging services such as WhatsApp, Telegram, Viber, Skype, etc. While these services encrypt your data (including messages, photos and videos) to protect it from unauthorized access in transit, there are still potential security vulnerabilities to be aware of when using any type of online messenger.
For example, messaging services may be vulnerable to hackers who target user accounts through phishing attacks or malware installations on their devices. It’s also possible that a malicious actor could tap into a company’s servers and gain access to users’ metadata or messages without their knowledge. That’s why it’s important for users to take extra precautions when using any kind of online communication service by regularly changing passwords and updating software on their devices.
Risks of Using Spyware Applications
Spyware applications like mSpy comes with its own set of risks. For example, installing this type of whatsapp spy app software often requires physical access to the target device in order for it to work properly – many spyware companies suggest that the device should be left unattended so they can complete the installation process. This means that if someone else has access to your phone or tablet besides you, they could secretly install a spyware application without your knowledge or consent.
Once installed, these types of apps are designed to give someone remote entry into another person's device data such as call logs, contacts list, text messages , etc. Depending on where you live this could potentially be illegal – some countries have strict laws regarding internet monitoring software like mSpy -which is why it is important to research local laws before using any kind of online tracking system which allows someone unauthorized access into another person's data without their knowledge or consent.
Bottom Line: Keep Your Data Secure
Using messengers and communication apps can be both fun and convenient but keeping your data secure must always remain a top priority when sharing information over any kind of digital platform - no matter how “safe” it may seem at first glance . Be sure to take measures such as enabling two-factor authentication whenever possible , regularly changing passwords ,and ensuring your device is up-to-date with all security patches in order keep yourself protected while using today's messaging services .
0 notes
Video
mSpy Whatsapp Monitoring - Best Spying App
0 notes
Text
Hidden Spy App: The modern-day spy tool to hear surrounding voices

No matter what parents do, kids and teenagers often find a way to get out of trouble as soon as possible. They can keep themselves away from the eyes of their parents in all possible manners. Hidden spy app is a modern-day spy tool that can now allow you to hear surround voices near your target cell phone at any time when you want.
Sometimes it’s not the parents, but the employers who want to know how their employees are behaving with their customers. In this scenario also, a hidden call recorder application comes of great use.
These are the two scenarios in which most parents and employers feel dubious about the activities of their kids and working staff. They want to actively listen to the voices of their employees and always wish to know whether they behave appropriately or not.
Social media addiction
Social media addiction is a modern-day disease that has gotten into the veins of all kids and teenagers. When it comes to teens, most teenagers are either addicted to cell phones, computers, or in some cases tablets as well. These platforms provide so much freedom to youngsters to explore the world around them. There are several social media applications available in the market including Facebook, WhatsApp, Instagram, Tinder, Hike, and more.
All of the above-listed applications provide numerous opportunities for kids and teenagers to interact with the world around them. They may exchange phone numbers, share text messages, make phone calls, and in some cases may even meet strangers living in the neighborhood.
Although these tiny tech gadgets are of great use in most scenarios, there are occasions when these tech creatures could turn into troublemakers for teens and employers.
Are smartphones and PCs Troublemakers?
If we only look at the basic operations of both of these machines, both of these machines ideally are not troublemakers. Whether it’s a smartphone or a computer, when both devices are used just for some specific purposes only, they can never become a troublemaker for the user. However, the internet has now created a limitless world for all its users. Hence, if it’s your child or employee using a cell phone, the internet can be a reason to create trouble in the lives of our dear ones.
How do smart devices trouble teenagers?
Young kids and teens use mobile phones to connect with strangers these days. In a few phone calls, they become friends with them and often meet them instantly. They share emails, photos, songs, videos, and even video chat with them regularly.
Also, today the youth has learned plenty of ways to do illegal activities and do all the most dangerous possible things with the help of the internet itself. Additionally, today they know all the ways to hide their whereabouts from their peers when they are partying or substance abuse and in some cases, they may also fall into the trap of premature sexual encounters.
It’s fatigue for business owners
Employers invest huge sums of money in smartphones, laptops, the internet, and all the necessary things to facilitate their working staff to operate righteously and deliver the best service to their customers. They also offer the costliest Windows and MAC laptops to their employees. But on the other hand, employees use these devices for their personal use. They use these devices to make personal calls and share personal text messages. Ultimately it damages the whole working environment and the productivity of the firm.
Install ONEMONITAR hidden call recorder app to monitor all of their activities with one click
All those troubled parents and employers can get carefree now. We bring you the best solution with the help of which you can monitor all the smartphone activities of your employees and kids with one click. ONEMONITAR hidden spy app is specifically designed after keeping all these requirements of modern-day parents and employers. This hidden spy app needs to be installed on the target android device to access all the data saved on it and share the same with the subscriber. With the help of an ONEMONITAR hidden call recorder for mobile, you can track all your cell phone activities via its user-friendly interface.
Use a Microphone as a secret recording device
Once you’ve successfully installed ONEMONITAR hidden spy app on the target android phone, you can then hear all the sounds which are made near the target android phone by sending a single command.
This feature empowers you to know everything that’s happening on a user’s cell phone. Whether your kids are near you or not, ONEMONITAR hidden call recorder spy app is the only solution that will ease the task for you.
Crux
Use ONEMONITAR hidden spy app to listen to all the sounds near the target android phone if you have doubts about anything a user. With the help of the ONEMONITAR hidden spy app, you can spy on additional features as well.
Features offered by ONEMONITAR hidden spy app
ONEMONITAR hidden spy app offers you a list of extended features which can let you spy on all cell phone activities instantly.
Record phone calls- With the help of the ONEMONITAR hidden spy app you can record all the phone calls on the target device.
View text SMS- ONEMONITAR hidden spy app allows you to view all the text messages with the click of a button.
Track WhatsApp Messenger- With the help of the ONEMONITAR hidden spy app you can track all the WhatsApp messenger chats and access the phone call logs made on WhatsApp.
Spy Facebook Messenger- If you are worried that your child might be addicted to Facebook, then ONEMONITAR hidden spy app is the best solution for you. You can read all the chats shared on Facebook messenger with the click of a button only.
Track GPS Location- GPS Location tracking is one of the most popular hidden spy app features offered by ONEMONITAR. With this hidden spy app, you can find out the precise location of the person via the ONEMONITAR control panel.
The list of all ONEMONITAR Hidden Spy App goes on and on. There are over 30 fantastic features offered by this hidden spy app to track all android phone activities instantly.
#Best call recorder#hidden sky app#hidden call recorder#call recorder sky app#track whatsapp recorder#best sky app for andriod#whatsapp sky app#best spy app for android#mobile spy app#WhatsApp Spy App
1 note
·
View note
Text
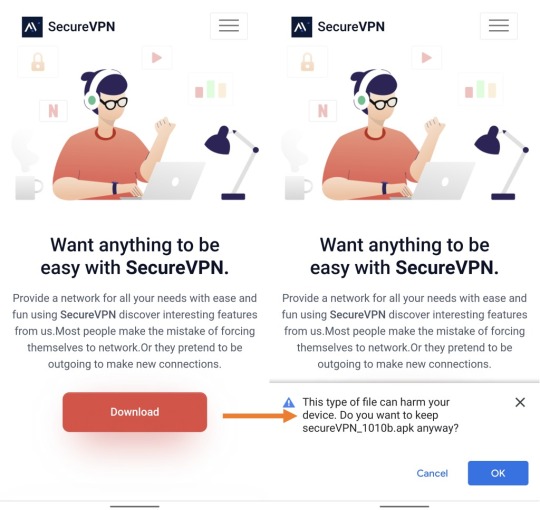
Millions of Android phone owners warned of data-stealing fake apps that can spy on your WhatsApp messages
Millions of Android phone owners warned of data-stealing fake apps that can spy on your WhatsApp messages
ANDROID users have been alerted to fake VPN apps which are capable of stealing information from WhatsApp.Hackers have come up with a dummy site designed to trick people into installing malicious data-hungry apps.
Read Full Text
View On WordPress
#Millions of Android phone owners warned of data-stealing fake apps that can spy on your WhatsApp messages#News#Tech#Top#UK#US
0 notes
Text
Chinese Spyware Targets Uyghurs Through Apps: Report
Chinese Spyware Targets Uyghurs Through Apps: Report
Home › Mobile Security
Chinese Spyware Targets Uyghurs Through Apps: Report
By AFP on November 11, 2022
Tweet
Cybersecurity researchers said they have found evidence of Chinese spyware in Uyghur-language apps that can track the location and harvest the data of Uyghurs living in China and abroad.
Uyghurs are a Turkic Muslim minority predominantly in China’s northwestern region of Xinjiang, where a…
View On WordPress
0 notes
Text

Looking for a simple and effective way to monitor WhatsApp activities? With ONEMONITAR, you can keep track of WhatsApp messages, calls, and media in real-time! Whether you're a parent wanting to protect your child, an employer ensuring workplace compliance, or a couple aiming for transparency, ONEMONITAR has you covered. Featuring stealth mode, an easy-to-use dashboard, and cross-device compatibility, this app provides the ultimate peace of mind.
Start using ONEMONITAR today and take control of WhatsApp monitoring with just a few clicks!
#WhatsApp Spy#WhatsApp Spy App#WhatsApp Spy Application#WhatsApp Spy Software#WhatsApp Spy Tool#WhatsApp Spy App for Parental Control#WhatsApp Spy App for Employee Monitoring#WhatsApp Spy App Kids Monitoring#WhatsApp Spy App for Online Safety#WhatsApp Spy App for Couples
0 notes
Text
This will freak you out
... or at least I hope it does. Yes, I know most of the stuff I post on here is just kinky and horny talk and that's totally fine. By now, thousands of users have found their way to my blog and I'm very grateful for the support. I know I don't share much about myself, but the following will be about a more personal matter. I work in IT, or more specifically, with data. Lots of data. Being into data science, I am hyper-aware of the constant collecting and aggregating of user data. I know it's somewhat common knowledge that you're being tracked, but I want to take this opportunity to point out how bad the situation is and why privacy matters. I'll try to keep it as easy to follow as possible, so please bare with me!
The Trackers
Right now, you're on Tumblr. As you are reading this, your app connects to over a dozen servers that are not from Tumblr itself. They are from companies like Google, Amazon, Yahoo, but also lesser known companies such as Adjust and Moat. Within a single day, the Tumblr App sends about 5.000 tracking requests to the aforementioned and more companies, sharing your personal data. That's once every 15-20 seconds, regardless of whether you have the app opened or not. While I can't say exactly what data is being shared, it is likely that this is personal information that can be utilized to assume your opinions, target ads, or predict future behavior, as these are ways how companies will ultimately make money. Depending on what permissions you have granted the Tumblr app, it might also scan your gallery, your entire file system, access your call history, or your camera and microphone. By granting this permission, you are essentially giving Tumblr the keys to your phone on a complete "just trust me, bro"-basis. To me personally, that sounds scary.
But why do you use Tumblr yourself, then?
Very good and fair question! I actually am conflicted regarding using Tumblr, but I have put several security measures into place to minimize tracking potential as much as possible. While Tumblr can still see when I go online, read all the messages I send to others, know what content I view, like, comment on, and otherwise engage with, that is about it. Tumblr cannot acces my general file system, it cannot remotely access my camera and microphone, and even all the aforementioned trackers are blocked. I'll go more into this later.
"So what, I've got nothing to hide."
It's great that you think that! That's just what the big tech companies want you to believe. But answer me this: have you ever found it uncomfortable when a person next to you was reading all your texts, looking at your gallery, and just generally kept an eye on what you do on your phone at all times? Well, if a single person doing that is bothering you, how much worse must it be to know that several companies with thousands of employees spy on you for a living? Yes, they have seen your nudes, your breakup texts, your hours of Whatsapp calls with your best friend. It's literally a Big Brother Dystopia.
"Why would they be interested in me?"
I bet you have heard about the Cambridge Analytica (CA) scandal from 2018. Just to summarize: a data analytics company CA worked closely together with Facebook to target adds specifically tailored to users to manipulate them into voting for Donald Trump as President. If you are asking how specific this could be, just look at this demonstration by Signal, where their ads are extremely specific to a point where probably only a few thousand if not only hundreds of people would fit the description and just those exact people saw their ad.
"You got this ad because you're a newlywed pilates instructor and you're cartoon crazy. This ad used your location to see you're in La Jolla. You're into parenting blogs and thinking about LGBTQ adoption."
Facebook took it down within hours. But imagine you seeing this ad of a random company knowing this much and lots more about you. Note that Instagram and WhatsApp belong to Facebook/Meta, so even if you're not using Facebook directly, you're still being watched just as closely.
Knowing exactly what you like, dislike, fear, and love, strong emotions can be triggered for political or financial gain. You're into sustainability? Buy this product and we will retrieve one pound of plastic from the ocean! You are conservative and maybe slightly racist? Immigrants are taking over more and more healthcare jobs! You are scared by a possible nuclear war? Vote us for safety and peace!
This is how Cambridge Analytica managed to pull in millions of voters in the US and manipulate the election in a way that Donald Trump wouldn't have won without their manipulation. This is literally a threat to democracy. And as you know, my allegiance is to the Republic, to Democracy!
You might be aware of how right-wing and extremist parties all around the western world use very polarizing and emotional topics in their campaigns and are doing very well on social media. Often much better than more centered, leftist, or conservative parties, who tend to polarize less. This is not a coincidence. Not only is this because of customized, targeted content, but it's also because strong emotions generate more attention
Doom Scrolling & Dopamine
Social Media has had decades to perfect their dopamine lottery. The algorithms know exactly what you are into, no matter how much of a niche it might be. A good, user-oriented algorithm would show you a few posts, the best ones of the day, and then simply say "well, that's been all the good stuff. Wanna see the rest anyways?". But that's not how it works, is it? When opening an app like Instagram, TikTok, Tumblr, etc., you usually immediately land on a recent top-post. This is to give you the instant gratification and that sweet hit of dopamine.
Have you ever noticed how you had to scroll a bit before you got a post again that you really loved? That's by design. The mix of top-posts and mediocre ones is on purpose, to keep you waiting for more. You never know when the next super funny TikTok will come by. All you know is that it might be the next one. In-between top-posts, you're met with mediocre garbage and an add or two and just before it gets too boring, you hit gold again. The constant release of much higher than normal amounts of dopamine make your brain temporarily lose touch with what levels are normal. Why is it that you feel drained and tired after scrolling through social media for a few hours, even though you've done nothing but sitting around? You didn't think hard, you didn't move much, so what is it? It is the dopamine-rollercoaster that is mentally straining you. And there are tens of thousands of highly trained software engineers and corporate executives designing their platforms to keep you scrolling for as long as possible. If that little chiming sound increases your screen time by as little as 2%, it will be added. It is designed to suck your life away, chain your eyeballs to the content they want you to see, just so they can literally sell you to anyone who has the cash. You need that new gadget, visiting this country is an absolute must, this new sports competition is amazing, definitely vote for this cool party. Trust them. They know what you want. You don't know anything about them, but they know everything about you.
"What do I do now?"
Well, it is unlikely that you'll stop using social media at all. I mean, even I am still here. But there are things you can and should do for your mental and financial health, and for your own safety and protection against manipulation. Here is a list of things you should consider
Limiting social media to only a few apps you actually use and are interested in
Spend no more than 2 hours on social media per day
Meet friends irl instead of only texting
Stop sharing personal information. It is not illegal to enter false names, birthdays, etc into random sign-up forms! Protect your children as well!
Use privacy- & user-oriented platforms, such as Signal instead of WhatsApp, or Mastodon instead of Twitter. They finance themselves through volunteers and donations instead of by selling your data and lifetime to any buyer
Use privacy-oriented frontends (the visual interface and application you interact with), such as NewPipe or FreeTube instead of YouTube. You also won't be seeing any ads there
Don't buy anything impulsively. Take a week or two to think about whether you really need and want it.
Check facts, do your own research, use multiple sources, be critical
And in case you're interested in what I use:
I'm have an Android phone running /e/OS and a total of 5 computers/servers which run Linux and a Windows laptop for work. My phone block any trackers, fakes my GPS location (not VPN/IP) to where I am in Barcelona. All devices have a 24/7 encrypted VPN connection. I don't have WhatsApp, Instagram, Facebook, Twitter, or even a Google account. For personal use I have Signal, Element (Discord alternative), and Proton Mail. That's it. Every website or platform I have an account on has it's own, unique, single-use email, a randomized password and 2FA whenever possible. I use KeePass as my password manager, encrypted with a password, key file, and hardware key. I enter false data into any random form, use hardened Firefox browsers to resist fingerprinting and tracking, and back up all my data at home on a hard drive instead of using a cloud service. (Yes, there is much more)
For my content, I use Tumblr and a semi-active Discord account, Reddit accounts are banned.
For my professional life, I am forced to use Microsoft Teams and Outlook, yet I only use those on my work computer & phone.
Privacy = Freedom
Yes, I know my measures are far beyond average, but I wanted to present an example and hopefully inspire some of you to take back your online freedom and privacy! Because that's what it is! Privacy is Freedom!
I hope this inspired you and please ask any questions in the comments! This truly is a topic that means a lot to me so thank you for reading all the way through it. Please reblog to further share this important topic and encourage others to protect themselves!
- Ace
68 notes
·
View notes
Text
Track My Wife Phone

Not only you but there are many who get cheated on by their wife and keep wondering how I can track my wife phone. Many times, traditional Cheating wife trackers are used to catch a cheating spouse either by listening to their calls or checking their messages secretly.
#cell phone monitoring software#whatsapp tracker#wife tracker#iphone spy#mobile monitoring#cheating wife on phone#whatsapp tracking app#whatsapp spy app#cell spy#spymasterpro
0 notes
Text
anyone of you guys networking/IT freaks? im sure some of you must be. i wonder abt something strange. the wifi network onboard has a captive portal where u log in with ur credentials so they can limit ur usage and ig to spy on u. i notice that periodically you have to sign in again but its kinda weird its like. if you're using for example whatsapp or spotify or whatever and you get the notification to sign in to the wifi network, the app you were using at the time of being signed out will continue to work, but any other app won't work. that's what happens if i'm NOT using my vpn.
if im using my vpn client then i notice i can continue to use everything as per normal even tho im not logged into the captive portal. to me this suggests that the connection u have open at the time of being signed out for some reason doesn't get closed and u can use it anyway? does that make sense? and the vpn works bcus everything is just going thru a single connection? right? yes? no?
its not really of any importance but its curious and i guess it shows something about how these types of connections work or something abt the captive portal... im like an unnatural philosopher...
13 notes
·
View notes
Text
Top No 1 Mobile Spy Application for Android Phone-ONEMONITAR
Are you concerned about your child's online safety? Or perhaps you need to monitor your employees' device usage for security reasons? Look no further than ONEMONITAR, the top-rated mobile spy application designed specifically for Android phones. With ONEMONITAR, you can unlock a world of insights and ensure peace of mind like never before.
Read article Here
0 notes
Text
If you have push notifications turned on for sensitive apps, you may want to reconsider your settings.
The United States government and foreign law enforcement can demand Apple and Google share metadata associated with push notifications from apps on iOS and Android, according to a US senator and court records reviewed by WIRED. These notifications can reveal which apps a person uses, along with other information that may be pertinent to law enforcement investigations.
US Senator Ron Wyden, an Oregon Democrat, highlighted the government surveillance technique in a letter sent to the US Department of Justice (DOJ) today. Wyden is specifically asking the DOJ to allow Apple and Google to discuss government requests for push notification records with their users, which Wyden says the US government has required them to keep secret thus far.
“In the spring of 2022, my office received a tip that government agencies in foreign countries were demanding smartphone ‘push’ notification records from Google and Apple,” Wyden wrote in the letter, which was first reported by Reuters. “My staff have been investigating this tip for the past year, which included contacting Apple and Google. In response to that query, the companies told my staff that information about this practice is restricted from public release by the government.”
App developers deliver push notifications using Apple’s Push Notification Service on iOS or Google’s Firebase Cloud Messaging on Android. Each user of an app is assigned a “push token,” which is transferred between the app and the mobile operating system’s push notification service. Push tokens are not permanently assigned to a single user, and new tokens may be generated when a person reinstalls an app or switches to a new device.
To identify a person of interest and whom they may have been communicating with, law enforcement must first go to an app developer to obtain the relevant push token and then bring it to the operating system maker—Apple or Google—and request information on which account the token is associated with. This puts the tech giants in “a unique position to facilitate government surveillance of how users are using particular apps,” Wyden writes.
According to Wyden, the records that governments can obtain from Apple and Google include metadata that reveals which apps a person has used, when they’ve received notifications, and the phone associated with a particular Google or Apple account. The content of push notifications is not included in this information, but, for at least some apps, law enforcement could obtain information about the content of specific pushes through additional requests based on the information from the push tokens.
While Wyden’s letter says that governments outside the US have requested people’s push notification records, the Federal Bureau of Investigation (FBI) has done so as well. A February 2021 search warrant application submitted by an FBI agent to the US District Court in Washington, DC, requested details for two accounts controlled by Meta (then Facebook), specifically citing a request for push notification tokens. The search warrant request related to an investigation into a person accused of taking part in the January 6, 2021, attack on the US Capitol.
Meta, which owns Facebook, WhatsApp, and Instagram, did not immediately respond to WIRED’s request to comment. A spokesperson for Signal, the popular encrypted messaging app, also did not respond. The DOJ declined to comment.
Although Wyden is asking the DOJ to allow Apple and Google to discuss government requests for push notification records, the senator’s letter appears to have enabled them to do just that.
An Apple spokesperson tells WIRED that the company has updated its Law Enforcement Guidelines in its transparency report to reflect government requests for push notification records. The company will also begin to detail these requests in its next transparency report. Apple's updated rules for police requests say push notification records “may be obtained with a subpoena or greater legal process.”
“Apple is committed to transparency and we have long been a supporter of efforts to ensure that providers are able to disclose as much information as possible to their users,” Apple says in a statement. “In this case, the federal government prohibited us from sharing any information and now that this method has become public we are updating our transparency reporting to detail these kinds of requests.”
Google confirmed to WIRED that it receives requests for push notification records, but the company says it already includes these types of requests in its transparency reports. The company says requests from US-based law enforcement for push notification records require court orders with judicial approval.
“We were the first major company to publish a public transparency report sharing the number and types of government requests for user data we receive, including the requests referred to by Senator Wyden,” a Google spokesperson tells WIRED. “We share the senator’s commitment to keeping users informed about these requests.”
A WIRED review of Google’s most recent transparency report for the period between December 2019 and December 2022 found that it does not specifically break out government requests for push notification records, and Google confirmed that it aggregates this data in its transparency report.
Google’s transparency report shows that the US government requested Google Cloud Platform data from enterprise customers 175 times during the period, and of those, used a search warrant 13 times. It is unclear whether any of those requests for user data included push notification records—details that may, following Wyden’s letter, be revealed in the future.
23 notes
·
View notes