#mspy
Explore tagged Tumblr posts
Text

Protect your loved ones now – Download Mspy and start monitoring instantly!
visit Mspy click here
0 notes
Text
Secure your child’s phone with mSpy software
Top parental control solution providing insight into kids' device activities. Also popular among employers, and couples. Track and monitor calls, texts, browsing history, and more on smartphones and devices.
Click to learn more and get yours:
#mspy#monitoringsoftware#parentalcontrol#smartphones#digitalactivities#employers#companydevices#tracking#calls#texts#browsinghistory#gpslocation#childmonitoring#employeemonitoring#trackingapp#monitoringtool#relationshipmonitoring#couplestracking
0 notes
Text
mSpy: Features, Setup, Pricing, and More
Explore mSpy, a comprehensive monitoring solution for digital devices. Discover its features, setup process, and pricing plans. Assess the pros and cons to make an informed decision. Whether for parental control or employee monitoring, mSpy offers insights and security. Simplify surveillance with this intuitive toolset.
0 notes
Text
youtube
There are several ways of locating your loved ones. You can use WhatsApp, Google Maps or better mSpy.
0 notes
Video
youtube
mSpy Phone Tracker Review
0 notes
Text
Infosec in brief: I spy another mSpy breach: Millions more stalkerware buyers exposed

Source: https://www.theregister.com/2024/07/15/infosec_roundup/
9 notes
·
View notes
Text
How Do Private Investigators Track Cell Phones?
Private investigators (PIs) are known for their resourcefulness and ability to uncover information that may seem out of reach for the average person. Among their many skills, tracking cell phones has become a critical tool in modern investigations. Whether working on cases involving missing persons, fraud, infidelity, or corporate espionage, PIs often rely on cell phone tracking to collect crucial evidence.

But how do private investigators track cell phones? This blog explores the techniques, tools, and ethical considerations involved in this sensitive process.
1. The Basics of Cell Phone Tracking
Cell phone tracking involves determining the location of a device by utilizing the technology it relies on to function—cell towers, GPS, and Wi-Fi networks. Smartphones emit signals that can be intercepted or analyzed to pinpoint their location. While law enforcement agencies have sophisticated tools and legal authority for tracking, private investigators often use alternative methods that stay within legal boundaries.
2. Common Techniques Used by Private Investigators
a. GPS Tracking
GPS (Global Positioning System) tracking is one of the most accurate ways to locate a cell phone. Many modern devices come equipped with built-in GPS chips that constantly communicate with satellites to determine their location. Private investigators might use the following approaches to access GPS data:
Authorized Access: If a private investigator has legal permission (e.g., from the device owner), they can use GPS tracking apps to monitor the phone's location. This is common in cases of missing persons or parental tracking of children.
Location-Sharing Apps: Some apps, like Find My iPhone or Google Find My Device, allow users to share their location. A PI might assist clients in accessing these features, provided they have the right credentials or consent.
b. Cell Tower Triangulation
Cell phones connect to nearby towers for communication, and the distance to these towers can be used to approximate the device's location. By analyzing signal strength from multiple towers, a process known as triangulation can determine the phone's general whereabouts.
Private investigators might collaborate with telecommunications providers to request such data, but this typically requires proper legal justification, such as a subpoena or court order.
c. Wi-Fi Positioning Systems (WPS)
Many modern devices use Wi-Fi signals for location tracking when GPS is unavailable. By identifying the networks a phone connects to, investigators can narrow down the location. This technique is particularly useful in urban areas, where Wi-Fi networks are abundant.
d. Mobile Applications
Private investigators may use third-party apps designed for tracking. These apps often require installation on the target device, making their use legally and ethically complex. Popular tracking apps include:
mSpy: Often marketed for parental control, this app can monitor a phone’s location, messages, and activity.
FlexiSPY: Offers advanced tracking features, but its use must comply with local laws.
Such software is generally legal only if used with the consent of the device owner.
e. Social Engineering
In some cases, private investigators might rely on social engineering techniques to gain access to location data. For example, they might trick the target into sharing their location via a deceptive message or link. While this is less common among reputable PIs, it highlights the importance of staying vigilant against such tactics.
3. Advanced Tracking Methods
a. IMEI and SIM Tracking
Every mobile device has a unique International Mobile Equipment Identity (IMEI) number. Similarly, SIM cards have unique identifiers that can be traced through the network. Private investigators may use IMEI or SIM tracking to locate a device if they have access to the necessary records or tools.
b. Stingray Devices
A Stingray is a portable device that mimics a cell tower, tricking nearby phones into connecting to it. Law enforcement agencies commonly use this technology, but private investigators typically avoid it due to its invasive nature and legal restrictions.
c. Geofencing
Geofencing creates a virtual perimeter around a specific area. If a device enters or exits this area, it triggers an alert. This technique can be used with GPS or mobile app tracking and is often employed in cases involving surveillance or asset protection.
4. Legal and Ethical Considerations
Tracking cell phones is a highly regulated activity due to privacy concerns. Private investigators must adhere to strict legal and ethical guidelines to avoid violating rights or committing crimes.
a. Consent
In most jurisdictions, private investigators can track a cell phone only with the consent of the device owner. For example, a parent might authorize tracking of their child’s phone, or an employer might monitor company-owned devices used by employees.
b. Privacy Laws
Privacy laws vary by country and region but generally prohibit unauthorized tracking. In the United States, the Electronic Communications Privacy Act (ECPA) regulates the interception of electronic communications, including location data. Similarly, the General Data Protection Regulation (GDPR) in the EU sets strict rules on personal data collection.
c. Ethical Practices
Reputable private investigators follow ethical practices to maintain professionalism and protect client interests. This includes:
Avoiding illegal tracking methods.
Respecting the privacy of non-consenting individuals.
Providing clear disclosures about the methods used.
Unethical practices, such as installing spyware without consent, can lead to legal repercussions and damage the investigator’s reputation.
5. The Role of Technology
Technology plays a central role in cell phone tracking. From software solutions to hardware tools, PIs have access to a wide range of resources that make their work more efficient. Some commonly used technologies include:
Tracking Apps: As mentioned earlier, these apps offer location-sharing features for authorized users.
Surveillance Tools: Tools like GPS trackers or geofencing systems allow investigators to monitor movement discreetly.
Data Analysis Software: PIs often use software to analyze call records, SMS logs, or app usage patterns, which can provide indirect clues about a person’s location.
6. Challenges in Cell Phone Tracking
Despite advancements, cell phone tracking comes with its challenges:
a. Legal Barriers
Obtaining location data without proper authorization can lead to legal consequences, limiting the methods available to private investigators.
b. Technological Limitations
Signal Interference: GPS tracking may not work in areas with poor satellite coverage, such as tunnels or densely packed buildings.
Device Security: Modern smartphones are equipped with advanced security features that prevent unauthorized access to location data.
c. Ethical Dilemmas
Balancing client demands with ethical considerations can be tricky. Investigators must ensure they don’t overstep boundaries while fulfilling their obligations.
7. Real-World Applications
Private investigators use cell phone tracking in various scenarios:
a. Missing Persons
Cell phone location data can provide vital clues in locating missing individuals, especially in time-sensitive cases.
b. Infidelity Investigations
PIs often track cell phones to gather evidence of infidelity. For example, GPS data might reveal that a spouse visited a suspicious location.
c. Corporate Investigations
In cases of corporate fraud or espionage, tracking company-owned devices can help identify rogue employees or uncover unauthorized activities.
d. Stalking and Harassment Cases
Cell phone tracking can help victims of stalking or harassment by identifying the perpetrator’s movements and providing evidence for legal action.
8. How to Protect Yourself from Unwanted Tracking
While private investigators are bound by legal and ethical guidelines, not everyone operates within the law. To protect yourself from unauthorized tracking:
Disable Location Services: Turn off GPS and location-sharing features when not needed.
Secure Your Device: Use strong passwords, enable two-factor authentication, and regularly update your phone’s software.
Avoid Suspicious Links: Be cautious about clicking on unknown links or downloading apps from unverified sources.
Use Anti-Spyware Apps: These can detect and remove tracking software from your device.
9. Conclusion
Private investigators play an essential role in uncovering the truth, and cell phone tracking is one of the many tools they use to achieve their goals. However, this practice requires a delicate balance of skill, technology, and adherence to legal and ethical standards.
For individuals and organizations seeking the services of a PI, it’s crucial to ensure they work with professionals who operate transparently and within the law. At the same time, understanding the methods and limitations of cell phone tracking can help protect your privacy and make informed decisions when hiring an investigator.
By staying informed about the capabilities and boundaries of cell phone tracking, you can better navigate the complexities of this modern investigative tool.
#private investigator#finding a hacker#spy phone#phone hacking tools#phone hacking service#phone hacking
1 note
·
View note
Text
If you're a married woman reading this, you may have had the urge to spy on husband's phone. From lying and coming home late to multiple missed calls, you may get suspicious when your husband changes all of a sudden. Unfortunately, this is very common. Luckily, if you want to find out the truth, all you need is your cell phone. Here, you will find some of the best ways to access your spouse's phone. Spy Methods That Might Be HelpfulSneak into His SmartphoneThe best thing to do is sneak into your husband's smartphone when he isn't around. For this, you need to know his password beforehand. You can try distracting him by asking him to do some chores. This will give you some time to sneak into his phone.However, if your husband is cheating, he is very likely to be extra cautious with his phone. So, he may tend to notice that you have somehow accessed his cell phone.Break into the CloudIf your husband uses an iPhone, then you can have a good look at his conversations by breaking into the cloud. The cloud is where users can store just about everything: from pictures and messages to contact information. Many people usually share the cloud when making payments. So if you come across sexy pictures of him that he didn’t send to you, you’ll know that something is up. But to do this, you need your husband's iCloud credentials. Not to mention, this method only applies to iPhone users: you can only use this technique if your husband owns an iPhone. Using Localize.mobiIf you've ever asked yourself, "how to spy on my husband's phone?" Well, you might have just come across one of the best methods, and that's using Localize.mobi. This is a new service that allows you to track anyone's location without having to install any applications on the device. With Localize.mobi, you can track any type of phone anonymously. All you need to do is to provide the phone number you want to locate. After that, your target person will receive a text message and accept a request for tracking. Finally, you’ll get a notification and can check the location of the device on a map.The disadvantage of using this service is that even though it will help you locate where your husband is, it still won't give you access to his call logs or messages. mSpy as The Most Trustworthy WayWondering, “how can I spy on my husband’s phone”? You should try using this mSpy app. This is one of the most effective methods to find out if your husband is lying to you. This app comes with various features that allow you to track your husband's messages, calls, locations, and everything else that goes on on his phone. However, the app requires physical access to the device for installation. This means your husband could end up catching you in the act. Also, you have to pay for the app. How Can mSpy Help Spy on My Husband’s Phone?“How can I spy on my husband?” Well, that's simple, all you need is the mSpy service app.mSpy comes with numerous features that make it easy if you’re thinking, “how do I track my husband's cell phone?” Mentioned below are a few spy functions that mSpy currently offers:Spying on all private messages on Tinder and other social mediaSeeing call logsTracking locations via GPSAccessing all deleted, sent, and saved media on the deviceUsing these mSpy features to track your husband's phone makes life a lot easier, and you gradually stop doubting yourself. It's brilliant how this service allows you to track private messages on any social media platform: from Tinder and WhatsApp to Facebook Messenger. If you find any fishy messages, you also have the option to screen record them. This way, you have solid proof in case your husband tries to cover it up. Remember, he’ll try to hide it if he's guilty and doesn't want to get caught. You can also monitor what they look for on the internet and have access to basically everything they are trying to keep a secret from you on their phone.mSpy is legit one of the best ways to spy on a husband’s phone without touching it.Conclusion Services
such as mSpy might be the best answer to "how to spy on my husband's cell phone without touching it." You have to try it out if there is even a hint of suspicion that your husband is involved in something that you're unaware of. Following the methods above, you can rely on helpful services like mSpy to find out the truth. It’s time to stop feeling sorry or helpless for yourself: you deserve the answers.
0 notes
Text
Inside the Dark World of Stalkerware: Tech That Tracks You

What is Stalkerware?
Stalkerware is software that allows an individual to monitor another’s phone or computer without their awareness. While some vendors market the software as a parental monitoring tool, it is usually misused by insecure partners or malicious individuals. The ethical and legal consequences of stalkerware usage are dire, as it largely constitutes illegal surveillance.
A Violation of Trust and Security
Despite the sensitive data that these companies work on, a record number of stalkerware companies have experienced data breaches. In one TechCrunch report, up to 25 stalkerware companies have been hacked or leaked sensitive customer and victim details since 2017. The most recent example was of SpyX, which revealed almost 2 million victims’ personal information. This attack is one of a disturbing pattern, with other businesses like Spyzie, Cocospy, and mSpy also being hit with significant data breaches.
The effect of the breaches is profound. Personal messages, photos, call logs, and even GPS locations of unsuspecting victims have been leaked online, sometimes unbeknownst to them. This not only violates privacy but can also result in real harm, particularly in the case of domestic abuse.
The Motivation for the Hacks
The routine hacking of companies that make stalkerware raises questions about the ethics of the industry as well. The majority of hackers claim that their aim is to expose and dismantle what they see as a toxic and unethical business model. The stalkerware business has been termed a “soft target” by Electronic Frontier Foundation cybersecurity researcher Eva Galperin, meaning the parties who sell these apps tend to not be high on scruples when protecting their users’ data.
A History of Breaches
The timeline of stalkerware breaches is daunting. The first of the big breaches occurred in 2017, when hackers invaded Retina-X and FlexiSpy, showing their records for over 130,000 customers. From then on, the list of breached firms has grown, including Mobistealth, SpyFone, and a number of others. Not only do each of these breaches expose the vulnerabilities in these apps, but also show the ethical dilemmas of using them.
The Risks of Using Stalkerware
Not only is the use of stalkerware immoral, in a number of instances it is illegal as well. Unapproved monitoring has been outlawed in the majority of jurisdictions. Even when used in the pretext of monitoring children, the repercussions can be scary. Parents are asked to discuss privacy and security openly with children rather than relying on secret monitoring.
Besides, the security risks that are part of stalkerware software pose a significant danger. Users are left exposed to the same dangers they were attempting to escape. The data breaches that have been a bane to this industry are a stark reminder that the monitoring tools that are supposed to be used can easily come back to haunt them.
Conclusion
As awareness of the risks of stalkerware grows, individuals need to reconsider their behavior. The risks of using such programs are much greater than any potential benefit. Instead of intrusive monitoring, communication and trust have to be cherished in relationships.
For privacy-minded individuals, it would be advisable to employ legitimate parental control software designed with security in mind. The software operates discreetly and takes into account the privacy of all parties involved.
To put it simply, the world of stalkerware is one with plenty of ethical issues and danger concerns. The greater the technological advances, the greater our efforts need to be toward promoting sound conduct and watching out for abuse. By a firm “no” to stalkerware, we can establish deeper, healthier relationships on respect and trust. By rejecting stalkerware and advocating for stronger data privacy practices, we take a crucial step toward a more secure digital future
0 notes
Text
very great coverage of stalkerware use by government workers in australia, im very happy to have worked with crikey to make this reporting possible!
7K notes
·
View notes
Text

"Ready to take control? Try Mspy today and ensure your child's safety!
click here>>>https://track.mspy.click/aff_c?offer_id=2&aff_id=20392&url_id=155&source=google
0 notes
Text
How mSpy Works: Understanding Its Functionality Overview
You are a concerned parent looking for an effective tool to guard your children from the negative impacts of the online world - here, mSpy is simply well worth considering!
It’s a fruitful parental control tool - designed to provide worried parents like you peace of mind as well as ensure the safety of young teens within the virtual globe.
Now, you can take a closer look at this blog to understand the functionality and features of this amazing tool called mSpy.

How Does mSpy Work?
For a concerned parent like you, the mSpy app offers a range of features to help you monitor and track smartphone usage effectively.
So, how does mSpy work? It’s pretty easy- here’s how you can use it:
Open the website mspy.com, and create your own mSpy account.
Now, go to Chrome browser, and search getmspy.net.
Next, check the box to prove you’re not a robot.
Now, click Download to install the mSpy app on your device.
Then, open mSpy and go to its Control Panel.
Now, fill in your kid’s phone details including model, phone number, and a few more details.
Once you cover the steps, you’ll notice a device activity on your screen showing the people who contacted the most (phones and calls) and most visited websites.
Here’s how this app called mSpy works after being installed on the device you want to track or access.
What are the Features of mSpy Parental Control app?
You will see a lot of features available on this parental control tool called mSpy. Here, let’s discuss some of them:
Watch Call logs: mSpy lets you monitor incoming and outgoing calls and text messages on your children’s devices. This way, you can see who they're speaking to and notice any potential risks or harmful interactions.
GPS Tracking: mSpy has a GPS tracking feature that you can use to keep track of your toddler's location in actual time.
This way you can make sure they are not walking on the wrong or unsafe path.
Monitor Social Media: Using this tool, you can also scrutinize your children’s social media interests including their messages, posts, and even multimedia files on apps like Facebook, Instagram, and Snapchat.
This way you can stay within the loop and address any problems that are about to arise.
Net Browsing Records: mSpy also allows you to make direct entries on your kids’ online browsing records.
This way you can learn about the websites they often visit and can make certain boundaries to ensure they are no longer gaining access to something besides the point or danger.
Analyze Screen Timing: The mSpy parental tool also helps you know how much time your children are spending on this particular app.
These are just a number of the tremendous features that mSpy offers as a parental management tool. Source: Radarro.com
#mspy review#onlinesafety#parentalcontrol#parentalcontrols#parentalguidance#digitalparenting#childsafety#controls#radarro
0 notes
Video
youtube
(via عرض mSpy | مراجعة mSpy (باللغة العربية))
0 notes
Video
youtube
mSpy App Review
0 notes
Text
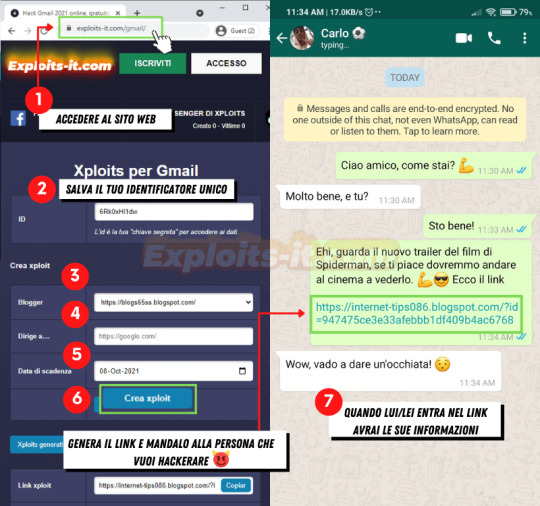
Strumenti per monitorare Gmail in modo professionale Negli ambienti lavorativi e familiari, il monitoraggio di un account Gmail può essere necessario per garantire sicurezza, produttività o benessere digitale. Pertanto gmail, esistono strumenti progettati per facilitare questo compito senza compromettere la legalità o la privacy dell’utente, se utilizzati in modo responsabile.
Uno degli strumenti più utilizzati a livello aziendale è la Console di amministrazione di Google Workspace, uno strumento che consente agli amministratori di verificare l'attività degli account associati al proprio dominio. Da lì puoi applicare filtri, verificare i messaggi inviati, prevenire fughe di informazioni e rilevare tentativi di frode.
Per i genitori, Google Family Link si presenta come un'opzione eccellente. Questa app ti consente di gestire l'utilizzo degli account Gmail da parte dei minorenni. Puoi controllare la posta elettronica, controllare le applicazioni e impostare limiti di tempo. È un modo semplice per garantire che i giovani utilizzino la posta elettronica in modo responsabile.
Esistono anche piattaforme di monitoraggio più avanzate come mSpy o FlexiSPY, che offrono il monitoraggio della posta elettronica insieme ad altre funzionalità come posizione, cronologia di navigazione e messaggi in altre app. Il suo utilizzo deve essere giustificato e legalmente consentito, soprattutto se coinvolge adulti.
Un'altra funzionalità meno conosciuta è la Cronologia attività di Google, dove puoi vedere gli accessi recenti al tuo account, da quali dispositivi e a quali strumenti è stato effettuato l'accesso. Questa funzione è utile per rilevare violazioni di domicilio o attività sospette.
Il monitoraggio di Gmail può prevenire i problemi prima che si verifichino. Nelle aziende aiuta a mantenere la riservatezza dei dati; in famiglia, può essere fondamentale per individuare i segnali di pericolo online.
Naturalmente il monitoraggio deve essere sempre accompagnato da comunicazione e limiti chiari. La tecnologia non sostituisce il dialogo, ma può essere un grande alleato per creare un ambiente digitale più sicuro.
0 notes
Text
Best iPhone Spying App: Top Choices for 2025

With the increasing need for digital surveillance, finding the best iPhone spying app has become essential for concerned parents, employers, and individuals looking to monitor activities discreetly. Whether you need an app for security reasons, parental control, or investigating infidelity, choosing the right software can make all the difference.
What to Look for in an iPhone Spying App
When selecting a phone spy app, it’s important to consider the following factors:
Stealth Mode – The best spy apps should be undetectable.
Real-time Tracking – GPS location monitoring is a must-have feature.
Social Media Monitoring – Access to WhatsApp, Facebook, Instagram, Snapchat, and more.
Call & Message Logging – Recording calls and text messages for better insights.
Ease of Installation – A simple setup process without requiring jailbreaking.
Compatibility – Works seamlessly with the latest iOS versions.
Security & Data Protection – Ensures user privacy while monitoring activities.
Now, let’s take a look at the best iPhone spy apps for 2025.
1. HackWizzard – The Most Advanced iPhone Spy App
Overview
HackWizzard is one of the most powerful surveillance tools available. This app provides deep access to an iPhone’s data without requiring a jailbreak. It is widely used for tracking calls, messages, GPS locations, and even encrypted conversations on social media platforms.
Key Features
Pegasus Phone HackWizz xi7 – An advanced spyware solution offering deep monitoring capabilities.
Call & Message Tracking – Logs calls, SMS, and even deleted messages.
GPS Location Tracking – Tracks a device in real-time without detection.
Social Media Monitoring – Access to WhatsApp, Facebook, Instagram, Snapchat, and more.
Remote Access – Allows users to monitor the target phone from any location.
Undetectable Surveillance – Works in stealth mode for complete discretion.
Pricing
HackWizzard offers flexible pricing plans based on monitoring needs. For updated pricing, visit HackWizzard.
2. mSpy – Best for Parental Control
Overview
mSpy is a well-known name in the spying industry, particularly for parental control. It allows parents to track their children’s activities, ensuring their online safety.
Key Features
Keylogger feature to track keystrokes
Monitors social media chats
GPS tracking with geofencing
Remote access to media files
Pros
✔️ No jailbreak required ✔️ Excellent for parental monitoring
Cons
❌ Limited features in the basic version ❌ Expensive compared to alternatives
3. FlexiSPY – Best for Call Interception
Overview
FlexiSPY is one of the few spy apps that allow call interception. It’s ideal for individuals who need access to live phone conversations.
Key Features
Call recording and live call interception
Keylogger for password tracking
Social media and email monitoring
Remote camera activation
Pros
✔️ One of the few apps with call interception ✔️ Excellent for advanced monitoring
Cons
❌ Requires jailbreaking ❌ Expensive subscription plans
4. uMobix – Best for Real-Time Monitoring
Overview
uMobix is a strong contender, offering real-time monitoring features for iOS users.
Key Features
Live GPS tracking
Social media and app monitoring
Call and message tracking
Remote device control
Pros
✔️ User-friendly interface ✔️ Works without jailbreaking
Cons
❌ Limited free trial ❌ Some features require additional setup
5. Spyic – Best for Discreet Monitoring
Overview
Spyic is an undetectable monitoring solution that works in stealth mode, making it an excellent choice for discreet spying.
Key Features
GPS location tracking
Social media app monitoring
Call and SMS tracking
Works without jailbreak
Pros
✔️ Easy to install ✔️ No technical expertise required
Cons
❌ Fewer advanced features ❌ Customer support could be better
Why HackWizzard is the Best iPhone Spy App for 2025
While several iPhone spy apps offer quality monitoring, HackWizzard remains the top choice due to its cutting-edge Pegasus Phone HackWizz xi7 spyware, providing unparalleled access to target devices. Unlike other apps, HackWizzard ensures complete discretion and does not require a jailbreak, making it the ideal solution for professional and personal surveillance.
Conclusion
Choosing the best iPhone spy app in 2025 depends on your needs. Whether you are a parent, employer, or someone looking for advanced monitoring, apps like HackWizzard, mSpy, FlexiSPY, uMobix, and Spyic provide various features tailored to different surveillance requirements.
For the most advanced and discreet monitoring solution, HackWizzard remains the top choice. With its cutting-edge technology, real-time tracking, and user-friendly interface, it provides the best value for those who need professional-level surveillance.
1 note
·
View note