#nmap
Text
Infrastructure Recon Script
Hello everyone, it's been a while. :) Just wanted to share something I've been working on with you all.
I've developed a recon script for infrastructure testing which works off a CIDR or a list of IPs. It splits given IPs into groups of 64 (as nmap performs TCP scans on hosts in groups of 64,) launches nmap scans on each group as background processes and then merges the results together once every group has been scanned. The theory behind this is that port scans on over 64 hosts will complete in the time it takes to scan one group of 64 hosts.
From here, it analyses the port scan results and launches service-specific scans. It also creates lists of IPs by service, making any extra checks applicable to all hosts found with a specific service open.
You can find it here. It's still lacking a bit in documentation and usability- there's tools you need to install that I haven't noted down anywhere- but it's 80% tools found on an average Kali Linux build anyway. ^^ I do also want to improve the service scan scripts and see if there's anything I can add to them. Recently got it up and running fully so thought I'd share it.
Otherwise, I am working my way through Burp Suite Academy right now. My plan is to post a review on it here when I've covered what I want to there. Been slacking on it a little since starting work but I'm working on that.
EDIT: Still problems with the analysis section- I had a run through where everything was picked up but there's an issue stopping all hosts and services being picked up. Working on this.
UPDATE: Changed the flow of this and issue seems to have been addressed. :)
21 notes
·
View notes
Text
Something I thought of only after sending my last post about programming. Programming in movies and shows (mostly it comes up in tv) is pretty inaccurate in a lot of places. I can think of a few times they got it right:
Hackers. Nearly everything in that movie in terms of how hacking actually works is pretty accurate, especially since most of it is using social engineering to steal people's passwords. They don't build some complicated program to take down the internet or whatever, they write a basic script to just steal as much data as possible.
Matrix Reloaded. Trinity uses nmap (a real UNIX utility program) to scan a server and notices that SSH is running. Then she uses sshnuke to exploit a bug in the server that gives her admin access. The bug and the script to exploit it are both real (the exploit has been patched in real life a while ago).
There's nothing flashy about any of this so it's not too interesting for an audience. That's why you never see it. Same reason even experienced sword fighters like to hit each other's swords in movies: it's less accurate but it's more fun to watch.
#movie#cinema#film#hackers#the matrix reloaded#trinity#nmap#unix#sshnuke#programming#tv#Inaccurate but flashy swordfighting is called Flynning
8 notes
·
View notes
Link
Vía: https://derechodelared.com/nmap-cheat-sheet/

9 notes
·
View notes
Text
IT Certifications Courses

- Highlight how IT certifications can boost career prospects and earning potential.
- Mention the structure of the blog, focusing on popular IT certifications and their benefits.
-
- Explain why IT certifications matter in the tech industry.
- Discuss how certifications validate skills and knowledge, making candidates more desirable to employers.
- Provide statistics or examples demonstrating the impact of IT certifications on career advancement.
- Highlight a selection of popular IT certification courses across various domains, such as:
- Networking: Cisco CCNA, CompTIA Network+
- Cybersecurity: CompTIA Security+, CEH (Certified Ethical Hacker)
- Cloud Computing: AWS Certified Solutions Architect, Microsoft Azure Fundamentals
- Project Management: PMP (Project Management Professional), PRINCE2
- Briefly describe each certification, including its benefits and target audience.

Elevate Your Career: Top IT Certification Courses to Consider
Ready to take your career in technology to the next level? Explore our guide to the top IT certification courses to consider. From networking to cybersecurity and beyond, these certifications can open doors to exciting opportunities in the tech industry.
- Cisco CCNA (Cisco Certified Network Associate)
Discover why Cisco CCNA is one of the most sought-after IT certifications courses. Learn about its relevance in networking, its comprehensive curriculum, and how it can validate your skills in designing, implementing, and managing network infrastructures.
- CompTIA Security+
Explore the importance of CompTIA Security+ in the realm of cybersecurity. Uncover how this certification equips you with the knowledge and skills to secure networks, detect threats, and protect data, making you an invaluable asset to any organization.
- AWS Certified Solutions Architect
Dive into the world of cloud computing with AWS Certified Solutions Architect. Understand why this certification is highly regarded in the industry, as it demonstrates your ability to design and deploy scalable, reliable, and cost-effective cloud solutions on the Amazon Web Services platform.
- Microsoft Azure Fundamentals
Get acquainted with Microsoft Azure Fundamentals and its significance in the cloud computing landscape. Learn how this certification validates your understanding of Azure services, cloud concepts, and core Azure infrastructure, setting the foundation for a successful career in cloud technology.
- CompTIA Project+
Explore the fundamentals of project management with CompTIA Project+. Discover how this certification enhances your project management skills, including initiation, planning, execution, monitoring, and closing phases, preparing you to excel in various IT project roles.
As technology continues to evolve, investing in IT certification courses is paramount to staying relevant and competitive in the industry. Consider pursuing one or more of these top IT certifications courses to expand your skill set, advance your career, and achieve your professional aspirations.
Navigating Your Path: How to Choose the Right IT Certification Course
Embarking on the journey to earn IT certifications courses can be daunting with numerous options available. In this guide, we'll walk you through the essential steps to help you choose the perfect IT certification course tailored to your career goals and aspirations.
- Assess Your Career Goals and Interests
Begin by evaluating your career goals, interests, and aspirations within the field of technology. Consider the specific areas of IT that excite you the most, whether it's networking, cybersecurity, cloud computing, or project management.
- Research Market Demand and Industry Trends
Research the current market demand and industry trends to identify which IT certification courses are in high demand by employers. Explore job boards, industry reports, and networking events to gain insights into the skills and certifications that employers value the most.
- Review Prerequisites and Exam Requirements
Before committing to a specific IT certification course, review the prerequisites and exam requirements associated with each certification. Ensure that you meet the prerequisites and are prepared to fulfil the exam requirements, including any necessary training or experience.
Consider your learning style and preferences when choosing an IT certification course. Determine whether you prefer self-paced online courses, instructor-led training, hands-on labs, or a combination of different learning modalities.
- Explore Training Providers and Resources
Explore reputable training providers and resources offering IT certification courses in your chosen area of specialisation. Look for providers with a track record of success, positive reviews from students, and comprehensive course offerings.
- Seek Advice from Industry Professionals
Seek advice and guidance from industry professionals, mentors, or colleagues who have experience in the field of IT. Their insights and recommendations can help you make informed decisions and navigate the complexities of choosing the right IT certification course.
Choosing the right IT certification course is a crucial step towards advancing your career in technology. By following these steps and considering factors such as your career goals, market demand, prerequisites, learning style, and advice from industry professionals, you can confidently select the perfect IT certification course to propel your career forward.

Unlocking Opportunities: IT Certification Course Outline and Fees
Embarking on an IT certification journey can be transformative for your career, but understanding the course outline and associated fees is crucial for effective planning. In this guide, we'll delve into the outlines of popular IT certification courses and provide insights into their associated fees, empowering you to make informed decisions about your professional development.
Cisco CCNA (Cisco Certified Network Associate)
Course Outline: Explore the comprehensive curriculum of Cisco CCNA, covering topics such as networking fundamentals, LAN switching technologies, routing technologies, network security, and more. Dive into each module to understand the skills and knowledge you'll gain.
Fees: Detail the costs associated with Cisco CCNA certification, including exam fees, study materials like textbooks and online courses, practice exams, and optional lab equipment for hands-on practice. Compare prices from different vendors to find the most cost-effective options.
CompTIA Security+
Course Outline: Delve into the syllabus of CompTIA Security+, which encompasses areas such as threats, attacks, and vulnerabilities, technologies and tools, architecture and design, identity and access management, and risk management. Understand the key concepts covered in each domain.
Fees: Provide insights into the expenses involved in pursuing CompTIA Security+ certification, including exam registration fees, study guides or textbooks, online courses or boot camps, and exam retake fees if applicable. Highlight any discounts available for students or military personnel.
AWS Certified Solutions Architect
Course Outline: Examine the curriculum of AWS Certified Solutions Architect, focusing on topics like AWS services, designing highly available, cost-efficient, and scalable systems, implementation and deployment, and troubleshooting. Understand the specific skills and knowledge required for this certification.
Fees: Outline the costs associated with AWS Certified Solutions Architect certification, including exam fees for both the Associate and Professional levels, AWS training courses, practice exams, and AWS certification preparation resources like whitepapers and documentation.
Microsoft Azure Fundamentals
Course Outline: Review the outline of Microsoft Azure Fundamentals, covering foundational Azure concepts, core Azure services, Azure pricing and support, and Azure governance, privacy, compliance, and security. Gain a clear understanding of the topics covered in this entry-level certification.
Fees: Detail the expenses related to Microsoft Azure Fundamentals certification, including exam registration fees, official Microsoft study guides or online courses, virtual labs for hands-on practice, and any additional costs for retaking the exam if necessary.
CompTIA Project+
Course Outline: Explore the syllabus of CompTIA Project+, which includes project basics, project constraints, communication and change management, project tools and documentation, and project governance. Understand how this certification can enhance your project management skills.
Fees: Discuss the typical costs associated with CompTIA Project+ certification, including exam fees, study resources such as textbooks or exam prep guides, online courses or boot camps, and any optional certification training offered by CompTIA partners or authorized training centres.
Understanding the course outlines and fees of IT certification courses is essential for planning your certification journey effectively. By exploring the outlines and associated costs of popular IT certifications courses like Cisco CCNA, CompTIA Security+, AWS Certified Solutions Architect, Microsoft Azure Fundamentals, and CompTIA Project+, you can make informed decisions and invest in certifications that align with your career goals and aspirations. Whether you're looking to advance your networking skills, specialize in cybersecurity, master cloud technologies, or excel in project management, there's an IT certification course out there for you.
Decoding the IT Certification Course Examination Process: Your Roadmap to Success
Embarking on the journey of earning IT certifications courses is an exciting endeavour, but understanding the examination process is key to achieving your goals. In this guide, we'll demystify the IT certification course examination process, providing you with a roadmap for success.
Understanding the Structure of IT Certification Exams
Gain insight into the typical structure of IT certification exams, including the format, duration, number of questions, and passing score requirements. Understand the importance of familiarising yourself with the exam structure to optimise your preparation strategy.
Exam Registration and Scheduling
Learn about the process of registering for IT certification exams, including selecting an exam provider, creating an account, and scheduling your exam date and location. Explore tips for choosing the most convenient exam date and location based on your schedule and preferences.
Preparing for the Exam
Discover effective strategies for preparing for IT certification exams, including creating a study plan, leveraging study materials such as textbooks, online courses, and practice exams, and participating in study groups or forums for peer support and knowledge sharing.
Taking the Exam
Get tips for success on exam day, including arriving early at the testing center, bringing required identification and exam materials, and managing your time effectively during the exam. Explore techniques for staying calm and focused under pressure to optimize your performance.
Post-Exam Procedures
Learn about the procedures following the completion of the exam, including receiving your exam results, understanding score reports, and accessing certification badges or digital credentials. Discover options for retaking the exam if necessary and strategies for continued learning and professional development.
Navigating the IT certification course examination process is a crucial step towards achieving your career goals in the field of technology. By understanding the structure of IT certification exams, registering and scheduling exams effectively, preparing diligently, and approaching exam day with confidence, you can position yourself for success and unlock exciting opportunities in the dynamic world of IT.
Unlocking Career Potential: IT Certification Courses, Jobs, and Salary Insights
Embarking on an IT certification journey can open doors to lucrative career opportunities in the ever-evolving tech industry. In this guide, we'll explore how IT certification courses can lead to rewarding jobs and competitive salaries, empowering you to make informed decisions about your career path.
The Impact of IT Certification Courses on Job Opportunities
Discover how IT certification courses can significantly enhance your job prospects in the technology sector. Explore the various roles and positions that often require or prefer candidates with specific IT certifications, from network engineers and cybersecurity analysts to cloud architects and project managers.
Exploring In-Demand IT Certification Jobs
Delve into some of the most in-demand IT certification jobs and the certifications that can help you land these roles. Explore job descriptions, responsibilities, and required certifications for positions such as:
Network Engineer (CCNA, CCNP)
Cybersecurity Analyst (CompTIA Security+, CISSP)
Cloud Solutions Architect (AWS Certified Solutions Architect, Microsoft Certified: Azure Solutions Architect)
Project Manager (PMP, PRINCE2)
Understanding the Salary Potential with IT Certifications
Explore the correlation between IT certifications and salary potential, highlighting how certified professionals often command higher salaries compared to their non-certified counterparts. Provide insights into average salaries for various IT certification jobs, considering factors such as experience, location, and industry demand.
Real-Life Success Stories
Share inspiring success stories of individuals who have leveraged IT certification courses to advance their careers and achieve financial success. Highlight the career trajectories, achievements, and salary progression of these professionals, demonstrating the tangible benefits of earning IT certifications.
Tips for Maximizing Your Earning Potential
Offer practical tips for maximizing your earning potential with IT certifications, such as:
Continuously updating and expanding your skill set with additional certifications and training.
Pursuing specialization in high-demand areas of technology.
Gaining hands-on experience through internships, projects, and freelance opportunities.
Negotiating salary based on your certifications, skills, and industry demand.
Future Trends in IT Certification Courses and Job Market
Explore emerging trends in IT certification courses and the job market, such as the rise of new technologies (e.g., artificial intelligence, blockchain) and the increasing demand for specialised skills. Discuss how staying informed about these trends can help you future-proof your career and remain competitive in the industry.
Investing in IT certification courses can be a strategic career move, leading to abundant job opportunities and competitive salaries in the tech industry. By understanding the impact of IT certifications on job prospects and salary potential, as well as leveraging practical tips for career advancement and staying abreast of future trends, you can unlock your full career potential and thrive in the dynamic world of technology.
Why Should I Pursue IT Certification Courses?
Answer: IT certification courses offer numerous benefits, including:
- Validating your expertise and skills to potential employers.
- Increasing job opportunities and career advancement prospects.
- Enhancing your earning potential with competitive salaries.
- Staying updated with the latest technologies and industry best practices.
What Are the Most Popular IT Certification Courses?
Answer: Some of the most popular IT certification courses include:
- Cisco CCNA (Cisco Certified Network Associate)
- CompTIA Security+
- AWS Certified Solutions Architect
- Microsoft Azure Fundamentals
- CompTIA Project+
How Do I Choose the Right IT Certification Course?Answer: When selecting an IT certification course, consider factors such as your career goals, interests, industry demand, prerequisites, and learning style. Research different certification options, explore their curriculum, and assess their relevance to your career path before making a decision.
What Is the Examination Process for IT Certification Courses?Answer: The examination process for IT certification courses typically involves registering for an exam, studying the exam objectives, scheduling a test date at an authorized testing center, taking the exam, and receiving your exam results. Each certification exam may have its own format, duration, and passing score requirements.
Answer: The examination process for IT certification courses typically involves registering for an exam, studying the exam objectives, scheduling a test date at an authorized testing center, taking the exam, and receiving your exam results. Each certification exam may have its own format, duration, and passing score requirements.
How Much Do IT Certification Courses Cost?Answer: The cost of IT certification courses can vary depending on factors such as the certification provider, exam fees, study materials, training courses, and any additional resources or services. It's essential to budget for exam fees, study guides, practice exams, and optional training courses to ensure successful certification.
Can I Retake IT Certification Exams If I Fail?Answer: Yes, most IT certification exams allow candidates to retake the exam if they fail. However, there may be limitations on the number of retakes allowed and waiting periods between attempts. Be sure to review the retake policy for your specific certification exam.
Read the full article
1 note
·
View note
Text
youtube
0 notes
Text
can’t tell if I wrote buggy python code or nmap is taking a long time. Is this the halting problem?
1 note
·
View note
Text

Blurred some stuff out but did a TryHackMe CTF..learning Nmap!
1 note
·
View note
Text
Top 5 Tools for CTFs
Capture the Flag (CTF) competitions are a great way to test and improve your cybersecurity skills. They involve solving a variety of challenges, such as hacking into websites, cracking passwords, and reverse engineering malware.
To be successful in CTFs, it's important to have a good understanding of a variety of cybersecurity topics, as well as the right tools. Here are our top 5 picks for the best CTF tools:
Burp Suite
Burp Suite is a powerful web application security testing tool. It can be used to perform a variety of tasks, including intercepting and modifying HTTP requests and responses, scanning for vulnerabilities, and fuzzing.
Ghidra
Ghidra is a free and open-source reverse engineering tool developed by the National Security Agency (NSA). It can be used to disassemble and analyze machine code, as well as to debug and create software exploits.
Nmap
Nmap is a network mapping and security scanning tool. It can be used to identify all of the devices on a network, as well as the services they are running and the ports they are open on.
SQLMap
SQLMap is an automated SQL injection and database takeover tool. It can be used to exploit SQL injection vulnerabilities in web applications and gain access to underlying databases.
Python
Python is a general-purpose programming language that is widely used in the cybersecurity community. It is a good language for learning and scripting, and it can be used to solve a variety of CTF challenges.
In addition to these tools, it is also important to have a good understanding of the Linux command line and basic networking concepts.
Here are some additional tips for success in CTFs:
Practice regularly. The more CTF challenges you solve, the better you will become at it. Work with a team. CTFs are often more fun and successful when you work with others. Don't be afraid to ask for help. There are many people who are willing to help beginners learn about CTFs and cybersecurity. With the right tools and skills, you can be successful in your next CTF competition!
0 notes
Text
Nmap: A Comprehensive Network Mapping and Security Scanning Tool
Nmap is a free and open-source network scanning utility that can be used to discover hosts and services on a network, as well as to identify potential security vulnerabilities. It is a powerful and versatile tool that is used by security professionals, system administrators, and penetration testers.
Nmap can perform a variety of scans, including:
Host discovery: Nmap can discover hosts on a network by sending probes to IP addresses. This can be used to identify all devices on the network, even those that are not actively responding to network traffic.
Port scanning: Nmap can scan a target host or network to determine which ports are open and which services are running on those ports. This can be used to identify potential security vulnerabilities, such as open ports that are not being used by a service.
Version detection: Nmap can detect the version of software running on a target host. This information can be used to identify vulnerabilities in the software, as well as to determine if the software is up-to-date.
OS fingerprinting: Nmap can determine the operating system running on a target host, even if the OS is running behind a firewall or NAT device. This information can be used to identify potential security vulnerabilities and make informed decisions about firewall and access control policies.
Scriptable: Nmap can be automated and extended using Nmap scripts. Nmap scripts can be used to automate various tasks, such as detecting open ports, performing vulnerability scans, and collecting information about a target host.
Nmap is a powerful and versatile tool that can be used for a variety of tasks. It is an essential tool for security professionals who need to map their networks, identify potential security threats, and stay ahead of the curve in the ever-evolving field of cybersecurity.
Here are some of the key benefits of using Nmap:
Free and open-source: Nmap is free and open-source, making it accessible to everyone, regardless of budget or experience.
Easy to use: Nmap has a user-friendly interface and is easy to use, even for those who are new to network mapping and security auditing.
Versatile: Nmap can be used for a variety of tasks, making it a versatile tool for any security professional.
Comprehensive: Nmap offers a wide range of features and capabilities, making it a comprehensive tool for network mapping and security auditing.
Supports multiple platforms: Nmap can be run on various operating systems, making it a versatile tool that can be used by anyone, regardless of their platform of choice.
Large community: Nmap has a large and active community of users, developers, and security experts who are constantly contributing to its development and improvement.
Here are some of the key uses of Nmap:
Network mapping: Nmap can be used to map a network by discovering hosts and services on the network. This information can be used to understand the network topology and identify potential security vulnerabilities.
Security auditing: Nmap can be used to audit a network for security vulnerabilities. This can be done by scanning for open ports, detecting the version of software running on hosts, and fingerprinting the operating system of hosts.
Penetration testing: Nmap can be used to perform penetration tests on networks. This can be done by scanning for open ports and services and then exploiting any vulnerabilities that are found.
Network troubleshooting: Nmap can be used to troubleshoot network problems. This can be done by scanning for hosts that are not responding to network traffic, or by detecting services that are not running on hosts.
Here are some tips for using Nmap safely and ethically:
Always get permission before scanning a network.
Do not scan networks that you do not have permission to scan.
Do not use Nmap to attack or exploit networks.
Use the least intrusive scan type that will achieve your goals.
Be aware of the laws and regulations that apply to network scanning in your jurisdiction.
Nmap is a powerful and versatile tool that can be used for a variety of tasks. It is an essential tool for security professionals who need to map their networks, identify potential security threats, and stay ahead of the curve in the ever-evolving field of cybersecurity.
Conclusion
Nmap is a powerful and versatile tool that can be used for a variety of tasks in network security. It is an essential tool for security professionals who need to map their networks, identify potential security threats, and stay ahead of the curve in the ever-evolving field of cybersecurity.
Here are some of the key takeaways from this blog post:
Nmap is a free and open-source network scanning utility that can be used to discover hosts and services on a network, as well as to identify potential security vulnerabilities.
Nmap can perform a variety of scans, including host discovery, port scanning, version detection, OS fingerprinting, and scripting.
Nmap is a powerful and versatile tool that can be used for a variety of tasks, including network mapping, security auditing, penetration testing, and network troubleshooting.
It is important to use Nmap safely and ethically by getting permission before scanning a network, not scanning networks that you do not have permission to scan, not using Nmap to attack or exploit networks, using the least intrusive scan type that will achieve your goals, and being aware of the laws and regulations that apply to network scanning in your jurisdiction.
0 notes
Text
C-Cracks/OSCP-Automation was recognised!
So I found out that 2 years ago, my OSCP automation repo was actually posted by a company named National Cyber Security Services. :D https://m.facebook.com/ncybersec/photos/oscp-automation-a-collection-of-personal-scripts-used-in-hacking-exercises-1-enu/1502887116548674/

I actually found this because I'm about to do some HTB and I was going to use that as reference material.
It may seem like such a minor thing, but it's actually amazing to see that a company saw value in it enough to post about it (even with the fact that it was extremely basic and the enum script is now an older version before I debugged due to being a complete noob with GitHub at the time.) Fangirl moment. XD
Repos below for the curious, though that GitHub account isn't active anymore (I stupidly registered it with a university email and never bothered to look into getting it back!)
I am actually thinking of re-creating something like this as I start up with HTB again (kinda got the hacking bug...)
9 notes
·
View notes
Text
youtube
In This Video i will show you guys how we will Scan IP Adresses in the Formats of IPv4/IPv6 Versions , Hostnames, Websites . And how we will Bypass In This Video The Firewall Of The Playstation 5 or overall how to use a Technique to Bypass a Firewall to Scan For Open Ports , which are Services Running On The System/Servers. Malicious Hackers Often Exploit These Ports To Gain Unprivileged Acess To The Internal System Of a Company/Individual . But Nmap Can Also Be Used For Security-Purposes/Diagnostic Purposes to Test Out How The Networking Works.
-Subscribe For More Videos https://youtube.com/ @xenjin450
#internet#nmap#hacking#hacker#scanning#network#networking#cyber#cybersecurity#kalilinux#linux#informationtechnology#security#youtube#thailand#chiangmai#scan#facebook#instagram#github#twitter#tiktok#xenjin450#system#vulnerability#technology#2023#windows#pentesting#pentester
0 notes
Text
Steps to do network scanning via Parrot OS
Steps to do network scanning via Parrot OS
Here are the general steps to do network scanning via Parrot OS:
Open a terminal in Parrot OS and ensure that you have administrative privileges. You can do this by typing “sudo su” and entering your root password.
Install the necessary scanning tools. Parrot OS comes with many pre-installed tools, including popular scanning tools like Nmap and Zenmap. If you need to install additional tools,…

View On WordPress
0 notes
Text
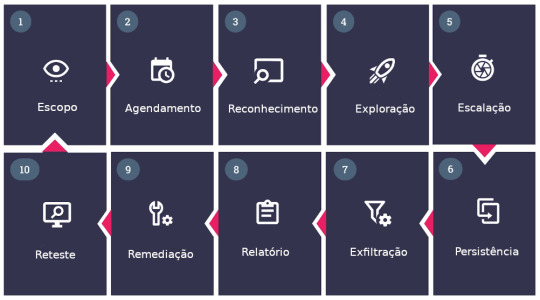
Pentest: Teste de Penetração – 2023
A melhor defesa é um bom ataque. O número crescente de incidentes também alimentou a necessidade de testes contínuos de nossos sistemas de defesa.
04-fev-2023
Os incidentes de cibersegurança têm aumentado desde o início da pandemia de Covid-19, o que prova que ainda faltam as nossas defesas de cibersegurança. Mas há pelo menos um lado positivo nesses incidentes: eles aumentaram a conscientização pública sobre como os sistemas de tecnologia da informação (TI) e tecnologia operacional (OT) são vulneráveis. Eles mostraram que as tecnologias…
View On WordPress
#Agendamento#Bloodhound#cibersegurança#Crt.sh#escalação#Escopo#exfiltração#Exploração#Ffuf#inPEAS#Invasão#Maltego#Masscan#Mimikatz#nmap#Nuclei#Pentest#Persistência#Reconhecimento#Shodan.io#sqlmap#SubBrute#tplmap
0 notes
Text
0 notes
Text

Writing a script to scan for vulnerabilities in the services listed
An automated vulnerability scan is performed by NMAP
Using Python, you can automate vulnerability scanning on a server. The following Python script uses Nmap and does the following:
A full vulnerability scan should be performed. The script only scans ports 22,80 & 3306, generates a report, and emails it to the admin. The run should be scheduled every week.
0 notes
