#telecom security services agency
Text
Top Telecom Security Services Agency Delhi
Are you looking for a reputable telecom security service with a base in India? Well. This is the place where your search ends. Mildain Digital Agency provides highly accessible, globally safe, and protected services to ensure that your clients and customers have reliable access to private conversations.
1 note
·
View note
Text
Over nearly a decade, the hacker group within Russia's GRU military intelligence agency known as Sandworm has launched some of the most disruptive cyberattacks in history against Ukraine's power grids, financial system, media, and government agencies. Signs now point to that same usual suspect being responsible for sabotaging a major mobile provider for the country, cutting off communications for millions and even temporarily sabotaging the air raid warning system in the capital of Kyiv.
On Tuesday, a cyberattack hit Kyivstar, one of Ukraine's largest mobile and internet providers. The details of how that attack was carried out remain far from clear. But it “resulted in essential services of the company’s technology network being blocked,” according to a statement posted by Ukraine’s Computer Emergency Response Team, or CERT-UA.
Kyivstar's CEO, Oleksandr Komarov, told Ukrainian national television on Tuesday, according to Reuters, that the hacking incident “significantly damaged [Kyivstar's] infrastructure [and] limited access.”
“We could not counter it at the virtual level, so we shut down Kyivstar physically to limit the enemy's access,” he continued. “War is also happening in cyberspace. Unfortunately, we have been hit as a result of this war.”
The Ukrainian government hasn't yet publicly attributed the cyberattack to any known hacker group—nor have any cybersecurity companies or researchers. But on Tuesday, a Ukrainian official within its SSSCIP computer security agency, which oversees CERT-UA, pointed out in a message to reporters that a group known as Solntsepek had claimed credit for the attack in a Telegram post, and noted that the group has been linked to the notorious Sandworm unit of Russia's GRU.
“We, the Solntsepek hackers, take full responsibility for the cyber attack on Kyivstar. We destroyed 10 computers, more than 4 thousand servers, all cloud storage and backup systems,” reads the message in Russian, addressed to Ukrainian president Volodymyr Zelenskyy and posted to the group's Telegram account. The message also includes screenshots that appear to show access to Kyivstar's network, though this could not be verified. “We attacked Kyivstar because the company provides communications to the Ukrainian Armed Forces, as well as government agencies and law enforcement agencies of Ukraine. The rest of the offices helping the Armed Forces of Ukraine, get ready!”
Solntsepek has previously been used as a front for the hacker group Sandworm, the Moscow-based Unit 74455 of Russia's GRU, says John Hultquist, the head of threat intelligence at Google-owned cybersecurity firm Mandiant and a longtime tracker of the group. He declined, however, to say which of Solntsepek’s network intrusions have been linked to Sandworm in the past, suggesting that some of those intrusions may not yet be public. “It's a group that has claimed credit for incidents we know were carried out by Sandworm,” Hultquist says, adding that Solntsepek's Telegram post bolsters his previous suspicions that Sandworm was responsible. "Given their consistent focus on this type of activity, it's hard to be surprised that another major disruption is linked to them.”
If Solntsepek is a front for Sandworm, it would be far from the first. Over its years of targeting Ukrainian infrastructure, the GRU unit has used a wide variety of covers, hiding behind false flags such as independent hacktivist groups and cybercriminal ransomware gangs. It even attempted to frame North Korea for its attack on the 2018 Winter Olympics.
Today, Kyivstar countered some of Solntsepek's claims in a post on X, writing that “we assure you that the rumors about the destruction of our ‘computers and servers’ are simply fake.” The company had also written on the platform that it hoped to restore its network's operations by Wednesday, adding that it's working with the Ukrainian government and law enforcement agencies to investigate the attack. Kyivstar's parent company, Veon, headquartered in Amsterdam, didn't respond to WIRED's request for more information.
While the fog of war continues to obscure the exact scale of the Kyivstar incident, it already appears to be one of the most disruptive cyberattacks to have hit Ukraine since Russia's full-scale invasion began in February 2022. In the year that followed, Russia launched more data-destroying wiper attacks on Ukrainian networks than have been seen anywhere else in the world in the history of computing, though most have had far smaller effects than the Kyivstar intrusion. Other major Russian cyberattacks to hit Ukraine over the past 20 months include a cyberattack that crippled thousands of Viasat satellite modems across the country and other parts of Europe, now believed to have been carried out by the GRU. Another incident of cybersabotage, which Mandiant attributes to Sandworm specifically, caused a blackout in a Ukrainian city just as it was being hit by missile strikes, potentially hampering defensive efforts.
It's not yet clear if the Kyivstar attack—if it was indeed carried out by a Russian state-sponsored hacker group—was merely intended to sow chaos and confusion among the company's customers, or if it had a more specific tactical intention, such as disguising intelligence-gathering within Kyivstar's network, hampering Ukrainian military communications, or silencing its alerts to civilians about air raids.
“Telecoms offer intelligence opportunities, but they're also very effective targets for disruption," says Mandiant's Hultquist. “You can cause significant disruption to people's lives. And you can even have military impacts.”
44 notes
·
View notes
Text
News from Africa, 19 June
Hage Geingob will host Danish PM Mette Frederiksen and Dutch PM Mark Rutte today in Namibia. Green hydrogen will reportedly be among the subjects discussed.
2. Namibia's proposed visa exemption for Chinese nationals is a bilateral agreement that would benefit both countries, according to China's ambassador to Namibia, Zhao Weiping.
Some Namibian politicians have objected to the proposal, with opposition leader McHenry Venaani claiming it is a "hoodwinking process" for Chinese prisoners to come to the country, and aspiring presidential candidate Job Amupanda alleging that it involves a deal between the ruling party and China to garner support for next year's elections.
The proposed agreement's main goal is to attract Chinese tourists and help Namibia become competitive again after the Covid-19 pandemic, according to Namibia's minister of home affairs, immigration, safety and security, Albert Kawana.
3. Angola and Zambia signed a memorandum of understanding to enhance cooperation in information technology, including digital transformation, AI, and space technology.
The agreement includes the establishment of direct cross-border optical fibre backbone connectivity between the two countries, scheduled to happen this month.
The collaboration is expected to help improve the regulation of the Angolan and Zambian telecom markets and lead to improved coverage and quality of ICT services provided in both countries.
4. Namibia is embarking on a journey of digital transformation to modernize various aspects of the country's life.
The Department of Home Affairs, Immigration and Security recently announced the successful implementation of an online passport application system, a major step towards delivering home affairs government services through digital channels. Namibia is partnering with Estonia to bring government services online and gradually prepare citizens for the transformation ahead. The Vice Minister of ICT recognizes the importance of foreign direct investment (FDI) for African technology spaces, but stresses the need for a clear roadmap or strategy to ensure that solutions developed in Africa fit the lifestyle on the continent.
5. Nigeria has 71 million people living in extreme poverty and 133 million people are classified as multidimensionally poor, according to 2023 data from the World Poverty Clock and the National Bureau of Statistics.
6. The Bank of Namibia increased the repo rate to safeguard the dollar-rand peg and contain inflationary pressures, but this will severely impact consumers who rely on debt to survive.
The governor expressed empathy for people losing their homes due to rising debt costs, and urged the nation to find better solutions to keep more Namibians in their homes while maintaining financial stability.
7. The fighting in Sudan has caused a surge in refugees fleeing to South Sudan, exacerbating an already dire humanitarian crisis.
The UN has called for $253 million in funding to respond to the crisis, but donations have been slow to come in.
The lack of resources and funding has led to inadequate food, water, and sanitation facilities in transit camps, resulting in malnutrition, disease, and preventable deaths.
#Dutch PM#Danish PM#visit#Namibia#Green Hydrogen#China#visas#tourists#Angola#Zambia#ICT#network#digital#Nigeria#poverty#clock#currency peg#South Africa#refugees#crisis#food#sanitation#Sudan#Africa
3 notes
·
View notes
Link
0 notes
Text
does vpn works in dubai for video calling
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does vpn works in dubai for video calling
VPN legality in Dubai
In Dubai, the legality of VPNs (Virtual Private Networks) is a topic of debate and scrutiny due to the strict internet regulations imposed by the government. While VPNs themselves are not illegal in Dubai, their usage can be restricted or monitored by authorities.
The Telecommunications Regulatory Authority (TRA) in the United Arab Emirates (UAE), which includes Dubai, regulates internet usage and content within the country. The TRA prohibits the use of VPNs for illegal activities, such as accessing blocked content or bypassing censorship laws. Engaging in such activities using a VPN can result in severe penalties, including fines and imprisonment.
However, many individuals and businesses in Dubai use VPNs for legitimate purposes, such as accessing geo-restricted content, protecting their online privacy, and securely accessing business networks. In such cases, VPN usage is generally tolerated as long as it complies with the TRA's regulations.
It's essential for individuals and businesses in Dubai to understand the legal implications of using VPNs and to use them responsibly and ethically. This includes ensuring that VPN usage does not violate any laws or regulations set forth by the TRA or any other government authority.
To stay on the right side of the law when using a VPN in Dubai, individuals and businesses should choose reputable VPN providers that prioritize user privacy and security. Additionally, it's advisable to avoid using VPNs for activities that may raise suspicions or attract unwanted attention from authorities.
In summary, while VPNs themselves are not illegal in Dubai, their usage is subject to regulations imposed by the TRA. It's essential for users to understand and adhere to these regulations to avoid legal repercussions.
VPN effectiveness for video calling in Dubai
In Dubai, where internet usage is tightly regulated and monitored, utilizing a Virtual Private Network (VPN) can significantly enhance the effectiveness of video calling. Video calling services such as Skype, WhatsApp, and Zoom are popular for personal and business communications, but they may face restrictions or limitations in certain regions due to government censorship or telecom regulations.
By employing a VPN in Dubai, users can bypass these restrictions and enjoy uninterrupted video calls with enhanced privacy and security. VPNs encrypt internet traffic, making it difficult for third parties, including internet service providers and government agencies, to monitor or intercept communications. This encryption ensures that video calls remain private and secure, protecting sensitive information from potential eavesdropping or surveillance.
Moreover, VPNs can help users overcome geo-restrictions imposed by video calling platforms. Some services may be inaccessible or limited in certain regions due to licensing agreements or government regulations. However, by connecting to a VPN server located in a different country, users can appear as though they are accessing the internet from that location, bypassing geo-blocks and accessing unrestricted video calling services.
Additionally, VPNs can improve the quality of video calls by providing faster and more stable connections. In Dubai, where internet speeds can vary and network congestion is common, VPNs can route traffic through optimized servers, reducing latency and packet loss for smoother video calls.
However, it's essential to choose a reputable VPN provider with servers optimized for video calling and strong encryption protocols to ensure both privacy and performance. By leveraging the capabilities of a VPN, individuals and businesses in Dubai can enjoy seamless and secure video calling experiences without worrying about censorship or surveillance.
VPN regulations in the UAE
In the United Arab Emirates (UAE), the use of Virtual Private Networks (VPNs) is a topic of significant regulation and scrutiny. While VPNs are legal in the UAE, there are stringent guidelines and restrictions in place concerning their usage.
The Telecommunications Regulatory Authority (TRA) oversees the regulation of VPN services in the UAE. It is essential to understand that using VPNs to engage in any illegal activities, such as accessing prohibited content or breaching cybersecurity laws, is strictly prohibited. Violating these regulations can lead to severe consequences, including fines and imprisonment.
Many individuals and businesses in the UAE use VPNs to access geo-restricted content, ensure online privacy, and enhance cybersecurity. However, it is crucial to use VPN services from authorized and reputable providers to comply with UAE regulations fully.
It is worth noting that some popular VoIP services and video calling platforms are banned in the UAE. Many residents use VPNs to circumvent these restrictions and communicate with their families and friends abroad. As such, the government keeps a close eye on VPN usage to prevent the misuse of these services.
In conclusion, while VPNs can offer numerous benefits, users in the UAE must exercise caution and ensure compliance with local regulations. By using VPN services responsibly and ethically, individuals and businesses can leverage the advantages of a secure and private online connection without running afoul of the UAE's VPN regulations.
VPN performance for video calls in restricted regions
In regions where internet access is restricted or heavily monitored, utilizing a Virtual Private Network (VPN) can significantly enhance the performance of video calls. Video calling platforms such as Zoom, Skype, and Google Meet often face limitations or disruptions in regions with strict internet censorship or bandwidth throttling. However, a VPN can bypass these restrictions by encrypting the user's internet connection and rerouting it through a secure server located in a different region.
One of the primary benefits of using a VPN for video calls in restricted regions is improved stability and reliability. By connecting to a VPN server outside the restricted area, users can bypass local network congestion and enjoy smoother video call experiences. Additionally, VPNs can help mitigate packet loss and latency issues, which are common challenges in regions with limited internet infrastructure.
Moreover, VPNs provide an added layer of privacy and security for video calls. By encrypting data transmitted during the call, VPNs protect users' conversations from potential eavesdropping or surveillance by government agencies or malicious third parties. This is particularly important in regions where online privacy is a concern, as VPNs can help users communicate freely without fear of interception.
However, it's essential to choose a VPN provider with robust infrastructure and optimized servers for video calling purposes. Not all VPNs are created equal, and some may experience slower speeds or connectivity issues, especially during peak usage times. Therefore, users should research and select a reputable VPN service known for its performance and reliability in restricted regions.
In conclusion, VPNs play a crucial role in enhancing the performance of video calls in restricted regions by bypassing censorship, improving stability, and ensuring privacy and security. By choosing the right VPN provider and server location, users can enjoy seamless and uninterrupted video communication regardless of their geographical location or internet restrictions.
VPN bypass methods for Dubai's video calling restrictions
In Dubai, video calling restrictions can pose a challenge for individuals seeking to connect with loved ones, conduct business meetings, or access essential services online. However, with the use of Virtual Private Networks (VPNs), it is possible to bypass these restrictions and enjoy unrestricted access to video calling platforms.
VPNs work by encrypting your internet connection and routing it through a server located in a different location, thereby masking your true IP address and allowing you to access the internet as if you were located elsewhere. This is particularly useful in regions like Dubai where certain websites and services may be blocked or restricted.
There are several VPN bypass methods that individuals in Dubai can utilize to circumvent video calling restrictions:
VPN Apps: There are numerous VPN apps available for download on various devices, including smartphones, tablets, and computers. These apps allow users to connect to VPN servers located outside of Dubai, thereby bypassing local restrictions on video calling.
Browser Extensions: Some VPN providers offer browser extensions that can be easily installed and used to bypass video calling restrictions. These extensions typically offer similar functionality to VPN apps but are specifically designed to work within web browsers.
Manual Configuration: For more technically inclined users, manual VPN configuration is an option. This involves configuring the VPN connection settings directly on the device, without the need for a dedicated app or extension.
Obfuscated Servers: Some VPN providers offer obfuscated servers that are designed to bypass censorship measures more effectively. These servers disguise VPN traffic as regular HTTPS traffic, making it harder for authorities to detect and block.
By employing these VPN bypass methods, individuals in Dubai can overcome video calling restrictions and enjoy seamless access to communication platforms without compromising their privacy or security. However, it's essential to choose a reliable VPN provider that offers strong encryption and a wide selection of servers to ensure a smooth and secure browsing experience.
0 notes
Text
What are the Major Applications and the Future Trends in the Market for Alarm Monitoring?
The Alarm Monitoring Market was valued at USD 42.88 billion in 2017 and is expected to reach USD 59.83 billion by 2023, at a CAGR of 5.5% during the forecast period.
ADT (US), Moni (US), Honeywell (US), Securitas (Sweden), UTC (US), Schneider (France), Johnson Controls (US), Vivint (US), Vector Security (US), and Bosch (Germany) are some of the major companies dominating the alarm monitoring market.
Download PDF Brochure:
https://www.marketsandmarkets.com/pdfdownloadNew.asp?id=110120052
Alarm monitoring is a service wherein alarm systems installed in buildings, equipment, or vehicles are professionally monitored by a central monitoring station (CMS). The alarm systems are monitored in lieu of a monthly recurring charge. The CMS alerts security agencies or the property owner incase an alarm is triggered. Alarm monitoring is carried out to detect intrusion, fire, glass break, or rising carbon monoxide levels inside a premise.
The objectives of the report includes forecast of the Alarm Monitoring market size in terms of Offering (Systems Hardware, Services), Input Signal (Discrete, Protocol), Communication Technology (Wired, Cellular, IP), Application (Building, Equipment, Vehicle Alarm Monitoring), and Geography.
The alarm monitoring market by protocol input signal to grow at the highest CAGR during 2017–2023
Protocol inputs are electrical signals, which are formatted into a formal code that represents more complex information than that in case of discrete or analog signals. There are different types of protocols for transmitting telecom alarm data. The most widely used telemetry protocols are open standards such as SNMP, TL1, ASCII, and TBOS. The alarm monitoring market by protocol input signal is expected to grow at the highest CAGR during the forecast period.
The alarm monitoring market by cellular wireless network communication technology to grow at the highest rate during forecast period.
Among all the communications technology of alarm monitoring market, cellular wireless network expected to grow with the highest CAGR during forecast period. Cellular wireless network is increasingly being used for connectivity between control panels and alarm monitoring centers. It is mostly used as a backup system for connectivity incase primary lines go down. With the increasing reliability of cellular networks, the market for cellular wireless network-based alarm monitoring is expected to grow.
North America to hold a major share of the alarm monitoring market in 2016
North America is expected to dominate the alarm monitoring market during the forecast period. North America is in the forefront in the evolution and development of alarm monitoring technology as this region is home to some of the largest multinational corporations in the world. Most leading players operating in the global alarm monitoring market are based in this region. Increased R&D in the field of remote monitoring, home automation systems, and Internet of Things, in terms of new and improved technologies, is a major factor driving market growth in North America.
0 notes
Text
Revolutionizing Connectivity The Journey of Auto Telecom Company
In today's fast-paced digital world, connectivity is not just a convenience; it's a necessity. Auto Telecom Company has emerged as a leading player in the telecommunications industry, revolutionizing the way people connect and communicate. With a focus on innovation, reliability, and customer satisfaction, Auto Telecom Company has carved a niche for itself in the competitive telecom market.
Auto Telecom Company's journey began with a vision to transform the way people communicate on the go. With a team of dedicated professionals and experts in telecommunications technology, the company embarked on a mission to provide seamless connectivity solutions to individuals, businesses, and industries.
One of the key strengths of Auto Telecom Company lies in its commitment to innovation. The company invests heavily in research and development, constantly exploring new technologies and trends to stay ahead of the curve. From 5G networks to Internet of Things (IoT) solutions, Auto Telecom Company is at the forefront of cutting-edge technology, ensuring that its customers always have access to the latest and most advanced connectivity options.
Reliability is another cornerstone of Auto Telecom Company's success. The company understands the importance of a reliable network, especially in critical situations and industries. Whether it's providing uninterrupted communication for emergency services or ensuring seamless data transfer for businesses, Auto Telecom Company's robust infrastructure and network management systems ensure maximum uptime and minimal downtime.
Customer satisfaction is at the heart of everything Auto Telecom Company does. The company believes in building long-term relationships with its customers by offering tailored solutions, personalized support, and responsive customer service. Whether it's a small business looking for cost-effective communication solutions or a large enterprise in need of scalable infrastructure, Auto Telecom Company delivers solutions that meet and exceed customer expectations.
Auto Telecom Company's portfolio of services is diverse and comprehensive. From voice and data services to cloud-based solutions and managed services, the company caters to a wide range of communication needs. Whether it's high-speed internet for residential customers or secure networking solutions for government agencies, Auto Telecom Company has the expertise and capabilities to deliver.
In addition to its commercial offerings, Auto Telecom Company is also committed to social responsibility and community development. The company actively participates in initiatives aimed at bridging the digital divide, promoting digital literacy, and supporting education and healthcare through technology.
Looking ahead, Auto Telecom Company is poised for continued growth and success. With ongoing investments in infrastructure, technology, and talent, the company is well-positioned to meet the evolving needs of the digital age. From smart cities to connected industries, Auto Telecom Company is paving the way for a more connected and empowered future.
Auto Telecom Company's journey is a testament to the power of innovation, reliability, and customer-centricity in the telecommunications industry. As technology continues to evolve, Auto Telecom Company remains committed to shaping the future of connectivity and making a positive impact on the world.
For More Info:-
Auto Telecom Company
New Manufacturing Supplier in Asia
Products From Asia
1 note
·
View note
Text
Rumors are rampant on Capitol Hill about an effort said to be underway by US congressional leaders to salvage a controversial surveillance program—a plan that sources say may include slipping a last-minute provision into a “must-pass” defense authorization bill.
Republican and Democratic senior aides tell WIRED that word of private talks between the party leaders began to leak late last week, sparking concerns that House speaker Mike Johnson and Senate majority leader Chuck Schumer were mounting a last-ditch effort to rescue the program, known as Section 702, without the support of their rank-and-file members.
Neither Schumer nor Johnson have responded to requests for comment.
The 702 program—so named for its statutory source, Section 702 of the Foreign Intelligence Surveillance Act (FISA)—allows the government to warrantlessly surveil the communications of foreign citizens “reasonably believed” to be overseas. While intelligence analysts cannot target legal US residents, they can and often do acquire the communications of Americans in contact with foreign surveillance targets. Section 702 targets are not limited to terrorists and criminals, and may include, for example, foreign officials, diplomats, and journalists—anyone whose calls, texts, or emails are believed to have intelligence value.
The 702 statute is set to expire at the end of the year, though surveillance under the program, obtained through the compelled cooperation of US telecoms, could technically continue until April.
By week’s end, top congressional leaders are expected to present the final text of the National Defense Authorization Act (NDAA), a massive bill that directs the Pentagon’s annual funding and one of only a few bills that lawmakers cannot afford to let die. Amending the bill to extend the Section 702 program would force members into an up-or-down vote with limited debate and no opportunity to omit any unwanted, last-minute changes.
The House and Senate passed their own versions of the NDAA this summer, and a conference of top lawmakers had been tasked with consolidating the two bills. Currently, however, only a few top lawmakers know what the bill’s final text will say. The remaining conferees expect to receive a copy of the NDAA as early as Wednesday, but may have less than a day to parse what is typically over 1,000 pages of text. Party leaders will expect at least half of the conference to sign off on the bill quickly and send it to the House and Senate floor for a vote.
House majority leader Steve Scalise and House minority leader Hakeem Jeffries did not respond to WIRED’s requests for comment, nor did any senior members of the House and Senate armed services committees.
Republican staffers tell WIRED that extending the 702 program in this manner will almost certainly ignite another major quarrel in the House, where Republicans with considerable sway—including Jim Jordan, chairman of the House Judiciary Committee, and Matt Gaetz, who successfully ousted former House speaker Kevin McCarthy in October—are fiercely opposed to reauthorizing the program without a slew of new privacy safeguards.
An unlikely coalition of Republican and Democratic lawmakers was formed this year to oppose the intelligence community’s effort to obtain a clean reauthorization of the 702 program, which has been plagued by years of internal abuse at the National Security Agency and Federal Bureau of Investigation. The program’s critics have put up a laundry list of potential reforms, many of which are vehemently opposed by the White House and intelligence community at large. A chief demand of the Republicans, for example, has been to automatically strip the security clearance of any federal employee caught abusing 702 data.
A source familiar with the White House’s goals for the program tells WIRED it has encouraged Congress throughout the year to discuss potential privacy-enhancing reforms, while drawing a “red line” at demanding that the FBI obtain warrants before accessing raw 702 data for national security investigations. The source adds that the White House would be open, though, to discussing a warrant requirement for domestic criminal investigations, a recommendation made earlier this year by the president’s own intelligence advisory board.
Oversight officials on the congressional intelligence committees did not respond on Monday to inquiries from WIRED. A Democratic spokesperson for the House Intelligence Committee said its ranking member, Jim Himes, was unable to comment, but says a failure to reauthorize Section 702 by year’s end would prove to be a “disaster for national security” and a lost opportunity for meaningful reform.
5 notes
·
View notes
Text
Threat Intelligence Market Soars: Projected to Exceed US$ 55 Billion by 2033, Finds Latest FMI Analysis
According to the most recent FMI market estimate, the threat intelligence industry is expected to be valued US$ 11.6 billion by 2023. The market is anticipated to reach US$ 55 billion by 2033, growing at a 16.9% CAGR.
As cyberattacks and criminal behaviour increase in frequency and sophistication over the next few years, threat information will probably become more and more in-demand. The BFSI industry, which manages important financial data and has a substantial customer base, is expected to increase the market. Cyber risks can take many different forms, such as malware for ATMs and mobile banking, tax evasion, organisational infiltration, and data theft.
Favorable government regulations that secure IT systems and practices to safeguard crucial consumer data also benefit the sector. In order to defend against cyberattacks, a number of commercial and public banking institutions around the world emphasize the use of cutting-edge technologies. Additionally, technological developments have increased customer expectations and legal requirements are forcing baking establishments to change their business practices.
Ignite Your Growth: Unveil the Future Opportunities in the Threat Intelligence Market – Get Your Report Today:
https://www.futuremarketinsights.com/reports/sample/rep-gb-11691
Key Takeaways from the Threat Intelligence Industry:
The United States threat intelligence market is predicted to maintain its dominant position over the forecast period by holding the majority of the market share. By 2033, the market is predicted to gain US$ 9.9 Bn, exhibiting a CAGR of 10.6%.
Japan is expected to emerge as the fastest-growing country, growing at an impressive CAGR of 23.6% in the coming years. Significant adoption of Japanese companies’ threat intelligence solutions by Fortune 500 clients in segments like financial services, retail, and high-tech manufacturing.
Under the component category, the solution segment is projected to be the highly-preferred option for adoption by end users. Between 2023-2033, the market is forecast to grow at a CAGR of 13.4%.
The cloud-based threat intelligence is gaining prominence in the market. The integration of threat intelligence with the cloud empowers businesses to identify and stop the attack in advance. This segment is forecast to exhibit a CAGR of 16.1% over the forecast period.
Recent News Pertaining to the Performance and Developments of Threat Intelligence Key Players
In February 2022, IBM unveiled the acquisition of Neudesic, which is a US-based cloud services consulting agency. With this acquisition, the company intends to expand its portfolio of multi-cloud services, along with refining its AI and hybrid cloud strategy solutions.
In March 2022, Fortinet declared a partnership with five other new service providers. These service providers include Microland, Etihad Atheeb Telecom Company “GO,” Spectrotel, Radius Telecoms Inc., and TIME dotcom. The motive of this partnership is to deliver a simpler network architecture having advanced security, to achieve operational efficiency anywhere.
In March 2021, RBN Insurance Services, a Chicago-based insurance brokerage, announced that it is partnering with RealCISO, which is a security services marketplace. With this partnership, RBN clients will get the chance to conduct risk assessments and find products and services that meet their requirements.
Ask An Analyst:
https://www.futuremarketinsights.com/ask-the-analyst/rep-gb-11691
Threat Intelligence Industry Survey by Category
By Component:
Solution
Threat Intelligence Platforms
Security Information and Event Management
Log Management
Security and Vulnerability Management
Identity and Access Management
Risk and Compliance Management
Incident Forensics
User and Entity Behavior Analytics
Services
Advanced Threat Management Managed Service
Professional Managed Services
Professional Training and Support Services
Security Intelligence Feeds Managed Service
By Deployment Mode:
Cloud-Based
On-Premises
By Industry:
BFSI
Government and Defense
IT and Telecom
Healthcare
Retail
Manufacturing
Education
Others
By Region:
North America
Latin America
Europe
East Asia
South Asia Pacific
MEA
0 notes
Text
Digital Forensics Market Size and Forecast to 2030: By Component (Hardware, Software, Service), Type (Mobile Forensics, Computer Forensics, Network Forensics, Others), End-user (Government and Law Enforcement Agencies, BFSI, IT and Telecom, Others), and Region
The size of the global digital forensics market reached USD 5.2 billion in 2023 and is projected to exceed USD 13.0 billion by 2030, demonstrating a growth rate of more than 12.3% from 2024 to 2030.
Market Definition:
Digital forensics, also known as computer forensics, is a branch of forensic science that encompasses the investigation and analysis of digital devices, data, and networks to uncover evidence of cybercrimes or digital misconduct. It involves the systematic collection, preservation, examination, and interpretation of electronic evidence, such as files, emails, log files, and metadata, to reconstruct events, identify perpetrators, and support legal proceedings. Digital forensics techniques utilize specialized software tools and methodologies to extract and analyze data from a variety of digital sources, including computers, smartphones, tablets, servers, and cloud storage systems. The ultimate goal of digital forensics is to gather admissible evidence that can be presented in a court of law to support criminal or civil investigations, prosecutions, or litigation related to cybercrimes, data breaches, intellectual property theft, fraud, and other digital offenses. Digital forensic experts, often referred to as digital investigators or forensic analysts, play a critical role in conducting thorough and objective examinations of digital evidence, adhering to legal and ethical standards, and providing expert testimony in legal proceedings to assist in the administration of justice and ensure the integrity of digital investigations.
Digital forensics Market Drivers and Trends:
Increasing Cybercrime Incidents
One of the primary driving factors behind the growth of the digital forensics market is the alarming rise in cybercrime incidents globally. With the increasing digitization of business operations, the proliferation of internet-connected devices, and the growing reliance on digital technologies, cybercriminals have found new avenues to exploit vulnerabilities and perpetrate a wide range of cybercrimes. These cybercrimes include data breaches, ransomware attacks, financial fraud, intellectual property theft, and online harassment, among others. As organizations and individuals become more interconnected and reliant on digital infrastructure, the threat landscape continues to evolve, posing significant challenges to cybersecurity and necessitating robust digital forensic capabilities to investigate and mitigate cyber threats.
Furthermore, the high financial costs and reputational damages associated with cybercrime incidents have prompted organizations across various industries to prioritize investments in digital forensics solutions and services. In the event of a cyber attack or data breach, digital forensics plays a crucial role in identifying the root cause, containing the damage, and recovering lost or compromised data. As a result, organizations are increasingly investing in advanced digital forensics tools, technologies, and expertise to enhance their cyber resilience and incident response capabilities, driving market growth.
Regulatory Compliance Requirements
Another key driving factor of the digital forensics market is the growing emphasis on regulatory compliance and data protection standards. Governments and regulatory authorities worldwide have implemented stringent data protection regulations and compliance requirements to safeguard sensitive information, ensure privacy rights, and hold organizations accountable for data breaches and cyber incidents. Regulations such as the General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), Payment Card Industry Data Security Standard (PCI DSS), and various industry-specific mandates impose strict requirements for data handling, breach notification, and forensic investigation procedures. Consequently, organizations are compelled to invest in digital forensics solutions and services to achieve compliance with regulatory mandates and demonstrate due diligence in safeguarding sensitive data. Additionally, regulatory requirements often mandate the retention and preservation of digital evidence for forensic analysis in the event of legal proceedings or regulatory investigations, further driving the demand for digital forensics capabilities. As organizations strive to navigate complex regulatory landscapes and mitigate regulatory risks, investments in digital forensics technologies and expertise are expected to continue to grow, fueling market expansion.
Segmental Overview
The digital forensics market is segmented into component, type, end-user, and region.
Major Players in the Digital Forensics Market
The market players in the global digital forensics market are Cisco Systems Inc., IBM Corporation, Guidance Software Inc. (Opentext), Binary Intelligence LLC, KLDiscovery Inc., AccessData Group LLC, FireEye Inc., Paraben Corporation, LogRhythm Inc., Oxygen Forensics Inc., and MSAB Inc.
Know More- https://nexbindinsight.com/information-and-communications-technology/digital-forensics-market-size
0 notes
Quote
Every day, workers at I-Soon were targeting big fish.
Government agencies of China’s neighbours, including Kyrgyzstan, Thailand, Cambodia, Mongolia and Vietnam, had websites or email servers compromised, the leak revealed. There are long lists of targets, from British government departments to Thai ministries. I-Soon staff also boasted in leaked chats that they secured access to telecom service providers in Pakistan, Kazakhstan, Mongolia, Thailand and Malaysia, among others. They named the government of India – a geopolitical rival of Beijing’s – as a key target for “infiltration”. And they claimed to have secured back-end access to higher education institutions in Hong Kong and self-ruled Taiwan, which China claims as part of its territory. But they also admitted to having lost access to some of their data seized from government agencies in Myanmar and South Korea.
Other targets are domestic, from China’s northwestern region of Xinjiang to Tibet and from illegal pornography to gambling rings.
Hackers for sale: what we've learned from China's massive cyber leak | Technology | The Guardian
0 notes
Text
Best Telecom Solutions service provider in India

There is a growing need for dependable and effective communication solutions in a more interconnected world. In order to satisfy their changing communication needs, businesses are looking for creative service providers as the Indian telecom sector continues to grow quickly. Offering comprehensive and state-of-the-art communication solutions, AEPL (Advanced Electronics Company Private Limited) has emerged as a frontrunner among the many participants in the sector. This article examines AEPL's history and demonstrates why it is the top supplier of telecom solutions in India.
Why to choose AEPL
1. Technological Proficiency
AEPL is home to a group of exceptionally talented individuals with a wealth of knowledge and experience in the telecommunications industry. AEPL continuously invests in research and development because they are committed to being ahead of the curve and providing cutting-edge solutions. Through the utilization of cutting-edge technologies like artificial intelligence, Internet of Things (IoT), and 5G, AEPL enables companies to adopt the digital revolution and improve their operational effectiveness.
2. A Vast Selection of Services
AEPL's wide range of services is one of its main advantages. AEPL handles all aspect of telecom needs, from system integration and managed services to network infrastructure development and maintenance. AEPL provides comprehensive solutions customized to meet the specific requirements of each customer, whether it is through the creation of strong communication networks, the implementation of cloud-based solutions, or the provision of end-to-end project management.

3. Reliable Network Solutions
AEPL is aware of how important a dependable and secure network infrastructure is to companies. With a thorough grasp of network architecture, AEPL creates and implements reliable solutions that guarantee constant communication and smooth connectivity. Among other things, they are experts in transmission systems, wireless networks, optical fiber networks, and network security. With AEPL's solutions, organizations may easily expand their operations because they not only satisfy present needs but also plan for future growth.
4. A customer-focused methodology
AEPL prioritizes establishing enduring connections with its clientele. Through the adoption of a customer-centric strategy, AEPL guarantees that each client receives customized attention and solutions that meet their unique needs. The company's committed customer service team is on hand around-the-clock to offer fast assistance and resolve problems. Because of their dedication to client satisfaction, AEPL has developed a solid reputation for dependability and credibility.
5. Verified History
AEPL has demonstrated success in providing telecom solutions to many industries such as telecommunications companies, government agencies, businesses, and academic institutions. Their vast knowledge and flexibility in responding to changing market conditions distinguish them as a reliable partner in the telecom sector.

Conclusion
AEPL has become India's go-to supplier of complete telecom solutions in a quickly changing telecom environment. With its extensive service offering, customer-focused philosophy, dependable network solutions, technological know-how, and track record of success, AEPL has made a name for itself as the nation's top provider of telecom solutions. AEPL keeps empowering businesses with cutting-edge solutions to help them traverse the challenges of the digital age, which fuels their expansion and success.
#electrical work#facilities services#architectural design and construction#architectural work#electrical turnkey projects#fabrication and structures work#civil construction work#interior design#lighting solutions#transformer installation
0 notes
Text
Kristen Hanich, director of research at Addison-based research firm Parks Associates, said any number of potential issues could have been the cause.
“It could be anything from authentication issues to hardware failure or cloud configuration errors or cyber or other reasons,” she said. “Time will tell, and we are closely monitoring the story.”
911 calls unaffected
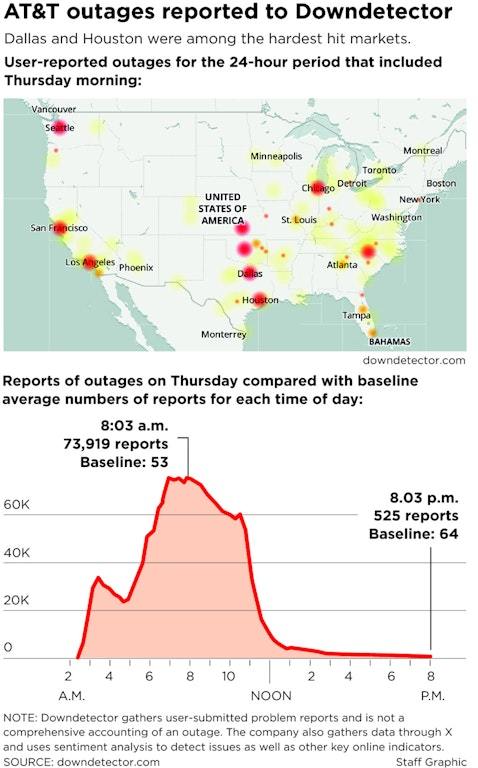
Because of the outage, some emergency services had to use maps to get to their destinations because FirstNet went down, Matt Zavadsky, chief transformation officer at MedStar Mobile Healthcare, told NBC5.
“When the system went down at 2:30 ... area law enforcement, fire agencies, first responders all over lost connectivity with their field units,” Zavadsky said. “So we had to revert to radio dispatching and actually using maps and ambulances to get to calls because the mapping systems weren’t working because the cell system was down.”
Other North Texas police departments reported no impact from the wireless outage.
A Dallas Police Department spokesperson said none of its 911 calls were affected.
By 1 p.m. Dallas time, FirstNet was fully operational again, said White House national security spokesman John Kirby.
youtube
CYBERSECURITY
AT&T: Millions of users’ data leaked
Social security numbers, passwords among info released
Personal data from about 73 million current and former AT&T account holders has been leaked on the dark web, the telecom giant said Saturday.
The Dallas-based company said the data was released onto the dark web about two weeks ago, and officials are not sure yet whether the data originated from the company or one of its vendors.
“With respect to the balance of the data set, which includes personal information such as social security numbers, the source of the data is still being assessed,” officials wrote in a news release.
AT&T officials said the company has launched an investigation with cybersecurity experts. In their initial analysis, staff found the data set appears to be from 2019 or earlier, affecting about 7.6 million current account holders and 65.4 million former account holders.
Company officials noted they don’t have evidence at this point of unauthorized access to their systems.
“The company is communicating proactively with those impacted and will be offering credit monitoring at our expense where applicable,” officials wrote.
Anyone who has been impacted will get an email or letter from the company.
AT&T officials said the incident had not had a material impact on the company’s operations Saturday.
Impacted customers have received emails noting that their account passcode has been compromised and that they must reset it.
“It appears the data is from more than 4 years ago and does not contain personal financial information or call history,” AT&T wrote to customers.
In the email, the company notes the information may have included customers’ full name, email address, mailing address, phone number, social security number, date of birth, AT&T account number and passcode.
AT&T offers services
If sensitive personal information was compromised, the company said it will provide “complimentary identity theft and credit monitoring services.”
The dark web leak comes a month after the company suffered a nationwide outage in its cellular service for a day.
The company blamed the outage on a coding error and not a cyberattack.
“The real issue here is the fact that basically all the personal identifiable information that you would need to basically recreate a person in the cyberspace was leaked,” said Andrew Sternke, the CEO of Southlake-based DarkBox Security Systems.
In 2021, threat actor ShinyHunters claimed to be selling data on 70 million AT&T customers.

Officials with the telecom company then told the tech outlet BleepingComputer that the information did not come from them, and they could not “speculate on where it came from or whether it is valid.”
Users on the hacking forum, BreachForums, appear to suggest the data breach is a repost of the initial leak from 2021, but AT&T officials have not confirmed the connection.
“The real question is what happened between 2021 and now?” said Brett Callow, threat analyst with New Zealand-based cybersecurity firm Emsisoft.
T-Mobile breach
Breaches among telecommunications companies and with third-party vendors are not uncommon, Callow said.
Last year, T-Mobile said a “bad actor” accessed personal data from 37 million customers. In 2022, the company agreed to pay $350 million to settle class-action lawsuits from a data breach disclosed in 2021 that affected a little over 40 million people.
Callow said service providers, like AT&T, can hold data for companies they provide services to.
Also, a provider like AT&T, he said, would have a massive number of vendors working for them in various ways.
In the case of AT&T’s breach, data could potentially be used to commit identity-related fraud.
The crime of hacking AT&T or its vendor could lead to many other offenses, Callow said.
Sternke said two things people should do is check their credit file — a record of their credit history — and use two-factor authentication for every one of their accounts.
He also urged those who are impacted to change their password and use a password manager.
“That will help keep track of your passwords by encrypting it and then you just need to know one main password to enter into your encrypted manager, and the password manager will automatically input your password into the account that you sign in.”
Customers should “absolutely” sign up for the credit monitoring services offered, Callow said.
“Hopefully that will mitigate those risks,” Callow said. Customers may also consider putting a block on their credit, which could stop fraud from happening, he said.
TELECOMMUNICATIONS
What we know about the AT&T data breach
Dallas-based giant says 73M current and past customers appear to have been affected
AT&T reported Saturday that personal data from millions of current and former account holders has leaked onto the dark web.
The Dallas-based company said the data — which it said appears to be from 2019 or earlier — was posted about two weeks ago, and that the company had not determined where it originated from.
Here’s what we know:
How many people were affected?
The telecommunications giant said a preliminary analysis found the data set includes information from about 7.6 million current account holders and 65.4 million former ones, totaling about 73 million people.
Anyone who has been impacted will get an email or letter from the company.
In an email to customers, AT&T said that to the best of its knowledge the data does not contain personal financial information or call history.
However, it said the information released may have included full names, email addresses, phone numbers, Social Security numbers and AT&T account numbers and passcodes.
AT&T told customers in an email that it would provide complimentary identity theft and credit monitoring services if their sensitive personal information had been compromised.
What do I do if I’m affected?
AT&T has already reset passcodes — personal identification numbers, or PINs, that are an extra security measure for account holders.
Officials are advising all customers to change their passcode as a precaution.
People should monitor their credit report and use two-factor authentication for every one of their accounts, said Andrew Sternke, CEO of Southlake-based DarkBox Security Systems.
“The real issue here is the fact that basically all the personal identifiable information that you would need to basically re-create a person in the cyberspace was leaked,” Sternke said.
Brett Callow, a threat analyst with the cybersecurity firm Emsisoft, said affected customers should sign up for the credit monitoring services if offered.
He also urged people to consider putting a block on their credit to stop fraud from happening.
Has this happened before?
In 2021, threat actor ShinyHunters made claims that it was selling data on 70 million AT&T customers.
The company said then that the information did not come from AT&T, and that officials could not speculate on whether the data was valid, tech outlet BleepingComputer reported.
Users on one hacking forum, BreachForums, appeared to suggest that the current data breach is a repost of the initial leak from 2021, but AT&T officials have not confirmed that.
The company said it doesn’t have evidence at this point of unauthorized access to its systems and that it’s not sure whether the data originated from the company or one of its vendors.
Have similar companies had data breaches?
Yes, in fact, AT&T’s main competitors have dealt with data breaches in recent years.
Last year, T-Mobile said a “bad actor” accessed personal data from 37 million customers, CNN reported.
In 2022, the company agreed to pay $350 million to settle class-action lawsuits from a data breach disclosed in 2021 that affected a little over 40 million people.
Verizon has also been victimized by data breaches in the past, with the company saying at least 6 million customers were affected in 2017. It has said that none of the information made it into the wrong hands.
AT&T BREACH
Expert: Protect your data
Customers’ information is for sale on dark web; here’s what you can do
Some 73 million former and current AT&T account holders are being notified that sensitive information, like full names and Social Security numbers, has been leaked onto the dark web as a result of a data breach at the Dallas-based telecommunications giant last weekend.
The data breach could pose serious risks to those affected and open up users to becoming victims of identity fraud.
However, there are some steps AT&T account holders can take right now and in the future to prevent the impact from becoming worse.
“In today’s day and age, third parties have your data. It’s just a fact of life that we all have to live with,” said Mitch Thornton, executive director of the Darwin Deason Institute for Cybersecurity at Southern Methodist University. “All you can do is protect yourself, your systems and your access to third-party accounts.”
AT&T said it will notify users who have been affected through mail or email.
The company has also said it has begun an investigation to determine what the cause of the data breach was and is offering affected customers complimentary identity theft and credit monitoring services.
But, in the meantime, here’s some steps you can take to protect yourself and your private information.
The basics
Criminals who steal private data often sneak small purchases in between larger bills in the hopes users won’t notice it, Thornton said. Checking credit should be the first step most people will need to take, he said.
“Monitor your credit for suspicious activity. Don’t just pay your credit card bills and whatnot without going through your transactions,” Thornton said. “Oftentimes, these criminals will make a small purchase just to test if you’re monitoring your accounts. You’d be surprised at the kinds of stuff you might find.”
Resetting passwords and applying two-factor authentication, a security system that requires two different forms of identification, should always be in place to be the most well protected.
But if users haven’t already, doing both is crucial at a time like this.
Resetting a password every six months, while time-consuming, could save individuals a headache down the road, Thornton said.
“A lot of people choose not to do either of them, because it’s an inconvenience. Every time you log in, you have to do more work and people could forget passwords,” he said. “But in cases like this, it could help you because the adversaries have your password, but they may not have your cellphone so they might not be able authenticate you fully.”
Though it might be a pain, applying credit freezes and locks could also be helpful. Though they both block individuals who have not been authorized to have access to credit reports, their main differences are in cost and how quickly it goes into effect.
Credit locks are typically a service that cost users between $10 to $25 and can be applied instantly, while credit freezes are usually free but can take longer to go into effect — sometimes up to five business days.
For users who are especially concerned, purchasing and using security software, while too late in the case of protecting data that AT&T stored, could prove to be helpful in the future, Thornton said.
“No matter what security software you have on your end systems at home, it wouldn’t have helped here because they didn’t attack you, they attacked your data that’s held by a third party,” he said. “However, I would always tell people for their home systems that they should use security software.”
What’s next?
AT&T account holders will need to watch their email inboxes and their mailboxes.
However, there’s still a chance that cybercriminals will take advantage of that too, Thornton said.
“If someone calls you up, or sends you an email that says, ‘Hey, we think you’re one of the people who have been affected. You need to authenticate information so send us your password,’ don’t do that,” he said. “You can always say you can provide it, but contact AT&T separately and ask them to verify that they’re actually the ones contacting you.”
With private information out on the dark web, it raises the stakes for affected individuals and the need to take precautionary steps, Thornton said.
“Your data is already out and available on the dark web. Usually, that is sold from one criminal to another and the threat of identity fraud is much higher,” he said.
“I know it’s time-consuming, but I highly suggest taking steps to protect yourself.”
0 notes
Link
0 notes