#telecom security company
Text
Top Telecom Security Services Agency Delhi
Are you looking for a reputable telecom security service with a base in India? Well. This is the place where your search ends. Mildain Digital Agency provides highly accessible, globally safe, and protected services to ensure that your clients and customers have reliable access to private conversations.
1 note
·
View note
Text
Love Me A Little

Character: Secretary!Bucky x Female!Reader
Words: 1,539
Summary: "Love me, even just a little." When she uttered those words, they struck Bucky like a bolt of lightning, leaving him utterly bewildered. After all, he was just a secretary—his world and hers seemed galaxies apart.
Main Masterlist || support: Ko-fi
Thank you to everyone who has read this chapter. Leave a comment and Reblog, please. I'd love to hear your thoughts. ❤️
A/N: Check out the male version of this story - Be Mine.

It was already 1:00 a.m., and the streets lay deserted, easing Bucky's drive. The sleek black Bugatti smoothly entered the apartment basement car park. Just one more turn, and he would find his usual parking spot.
"Screech." The sound of tires screeching echoed in the empty basement.
"Huh?" Bucky's foot instinctively hit the brake as he caught sight of the familiar figure standing in front of his car.
"Y/N?"
It's you. The sole daughter of the Rogers family, the heiress to Starlight Enterprises, a conglomerate spanning oil and gas, telecom, retail, and financial services.
You had fled, prompting the company to dispatch security teams in search of you.
And here you were.
Bucky stepped out of the car. "What are you doing? Don't you realize everyone's been searching for you?"
You scoffed, your tone laced with defiance. "So what? At least everyone will learn that I'm serious. I refuse to marry that guy."
Bucky understood the depth of your frustration. Your family was orchestrating an engagement between you and their business partner. But you vehemently opposed it. He comprehended why; the man they wanted you to marry was notorious—a playboy and a drug addict.
Unable to sway your resolve, Bucky carefully chose his words. "You should go home."
He reached out, gently clasping your hand, his touch pleading, wanting to guide you to safety.
But you recoiled, pushing his hand away. "I don't want to."
Bucky's heart sank, his expression pained. "Your family is worried about you."
Your retort was sharp, cutting. "Are they really? Or are they just afraid of losing their golden ticket?"
A tense silence enveloped them as Bucky grappled with the weight of your words. As the secretary to your brother, Steve, the Vice President, he was privy to the inner workings of wealthy families, aware that most marriages were arranged for business purposes.
Like Steve and Peggy, who defied the odds and found happiness together despite the pressures of their world, you refused to succumb to a loveless marriage.
With teary eyes, you gazed at Bucky, desperation etched in every tear. "I'll tell my parents I'll marry you instead."
Bucky sighed, feeling the weight of your request once more. You had asked him this before, seeking refuge from the loveless future awaiting you. Each time, he had declined.
"Not everything will always go your way," he murmured, his words heavy with resignation. "You've been living in a bubble as Princess Rogers." He paused, unable to bring himself to utter the name of your family's empire. "Now you're facing reality."
You fought back the tears, stung by his harshness. It was the first time Bucky had spoken so coldly to you. "Do you think my feelings for you are fake?"
"My whole life has been arranged from A to Z without my opinion," you continued, your voice trembling with suppressed emotion.
"The only thing I have is my dream of us living happily ever after. Can I at least have that?" Your breaths came in ragged gasps as you struggled to contain your emotions.
"Stop dreaming. Go home," Bucky commanded, his voice firm as he pointed behind you.
'Screech.'
With a screech of tires, a white Mercedes arrived to collect you. It dawned on you that Bucky had already informed the security team of your whereabouts.
As you watched Bucky walk away, a surge of determination washed over you. Clenching your fists, you whispered, "I'll show you."
########
A few days later
The entire Rogers family had gathered for tonight's dinner, including your grandparents, Thomas Rogers, the esteemed founder of the company. Bucky joined the dinner as well, having become one of the company's key figures, seated right beside you.
Despite the gravity of your previous conversation, you seemed to have put it aside, acting as if nothing had happened when you saw Bucky.
The dinner unfolded in its usual extravagant manner, with everyone engaging in polite small talk until dessert was served.
Your grandmother, Anna, broke the silence. "It's wonderful that we could all come together like this. We must discuss our youngest's engagement."
Your mother, Sophia, nodded, her smile gentle. "I met with them four days ago, and we've already ironed out all the details, from the church to the wedding."
Bucky's mind raced. Four days ago? That's precisely when you had gone missing.
Anna's excitement bubbled over. "This wedding will be magnificent. I can hardly contain myself."
But only the two women seemed enthused; your grandfather, Thomas, and your father, Benjamin, remained stoic, while your brother Steve stayed silent.
Then, a sudden sound cut through the air—a sharp "clank" as a fork stabbed into a plate.
All eyes turned to you.
"I don't like it," you stated flatly, your voice cutting through the tension like a knife.
Sophia's hand hesitated mid-air, poised to call the waitress, but froze when she heard her daughter's words.
"I don't like anything," you continued, your voice ringing with defiance. "I don't like that person, the wedding, anything."
"Y/N, stop," Sophia interjected, her tone tinged with frustration. "We've discussed this."
"Discuss?" you retorted bitterly. "Do you mean when you ignore my words?"
Anna's patience wore thin. "Y/N, enough with the tantrum. This concerns the entire family."
You crossed your arms defiantly. "I refuse to marry him."
Anna rose from her seat, ready to reprimand you, but a sharp glance from Thomas halted her in her tracks. Without a word, she sank back down, chastened by her husband silent command.
Thomas fixed you with a steady gaze, the same gaze that had once spoiled you as his beloved granddaughter. "Explain to me the reason why."
"I don't love him," you declared, your voice trembling with emotion. "I love someone else."
A sudden palpitation coursed through Bucky's chest. He sensed the situation spiraling out of control.
"Whose the person you love?" Thomas inquired, his voice firm.
You didn't hesitate. "Bucky."
'Ba-dump'
The room fell into stunned silence, broken only by the rapid thudding of Bucky's heart echoing in his ears, his mind racing as he grappled with the revelation unfolding before him.
Bucky rose hastily, his intention to apologize to the Chairman halted as your hand clasped his, the determination in your eyes stopping him in his tracks. It was the first time he had seen you like this, and it sent a shiver down his spine.
As all eyes turned towards you, you swallowed hard before speaking up. "And I'm pregnant. Bucky is the father."
The room erupted in chaos as Sophia and Anna screamed in unison.
"What?" they exclaimed in disbelief.
"Bucky! How dare you touch my daughter!" Sophia lunged forward, her hand reaching for Bucky's hair, but Benjamin intervened, restraining her.
Bucky opened his mouth to protest and deny the accusation, but the words stuck in his throat. He was taken by surprise, too.
"Silence," Thomas, the Chairman's authoritative voice, cut through the commotion, bringing an abrupt end to the chaos.
He rose from his seat, followed by Benjamin and Steve, their expressions a mix of shock and concern.
Fixing Bucky with a steely gaze, Thomas uttered just two words. "A word."
Bucky swallowed hard, his heart pounding as he replied, "Yes, Sir," bracing himself for the inevitable confrontation.
########
In Benjamin's office, Bucky stood before the three men, the weight of their scrutiny heavy upon him as they remained silent. Finally, Thomas broke the tension with a direct question. "Is everything true?"
Bucky knelt before his boss and friend, his voice steady but his heart pounding. "No, sir. None of it is true. I've never laid a hand on her."
Thomas's expression softened, a flicker of relief crossing his features. "Good."
Bucky let out a breath he hadn't realized he'd been holding, grateful for Thomas's understanding.
But then Benjamin spoke up, his tone contemplative. "Then why don't you like my daughter?"
Bucky's brow furrowed in confusion as he lifted his head to meet Benjamin's gaze.
"She's better off with you than with that spoiled man," Steve interjected, his voice firm.
Benjamin nodded in agreement, his eyes holding a hint of understanding.
Bucky was taken aback. "What?"
Thomas leaned forward, his voice grave. "The wedding arrangement was orchestrated by my wife and Y/N's mother. I'm relieved my granddaughter took a stand today."
Steve clapped Bucky on the shoulder, a mixture of relief and gratitude in his eyes. "I nearly lost my cool when she said she was pregnant. I almost punched you. Thank goodness it was a lie."
Bucky struggled to find words, overwhelmed by the unexpected turn of events.
Steve's tone softened. "Stay with her. I won't allow my sister to marry that man."
As the men continued their discussion, Bucky's mind raced, unable to fully comprehend the depth of their support.
Excusing himself, Bucky closed the door behind him, only to find you waiting for him outside.
Your worried expression melted his defenses as you approached him.
"What did they say?" you asked, searching his eyes for answers.
Bucky hesitated, then shook his head. "Nothing."
You breathed a sigh of relief and pulled him into a tight hug, his body stiffening like a log. Lifting your head to meet his gaze, determination flashed in your eyes.
"I'll make you love me," you vowed softly. "Even just a little."

Join the taglist? 🩷💙🩷
@bagoffeelings
@darkofimagination
@starsofcloud
@cherrybubblebullet
@winterslove1917
@thezombieprostitute
@xcaptain-winterx
@namoreno
@sagebarness
@tenaciousathleteoperatorgarden
@unaxv
@missvelvetsstuff
@kjah97
@hopeful-daydreaming
@freshlemontea
@eat-limes-bitches
@kandis-mom
@scott-loki-barnes
@winters1917
@differenttyphoonwerewolf
@arunabraganza
@ordelixx
@vicmc624
@blackwood-bodecker-housewife
@mostlymarvelgirl
@musicandbooksaremyhappyplace
@buckybarnessimpp
@charmedbysarge
@almosttoopizza
@sapphirebarnes
@daddysfavoritesexkitten
@rebeccapineapple
@cjand10
@pigeonmama
@almosttoopizza
@thesarcasmqueen-22
@cakesandtom
@ficrecsbyellie
@reblogging-all-i-read

Author Note: Hey friends,
If you've been enjoying the content, I've set up a Ko-fi account.
Your support through tips would mean the world and help me keep creating.
Only if you feel like it!
Here's the link: Ko-fi
Thanks a bunch for being fabulous followers!
#bucky barnes x reader#bucky barnes x y/n#bucky x you#bucky barnes#bucky x y/n#bucky x reader#bucky barnes au#james bucky buchanan barnes#buckybarnes#james bucky barnes#bucky#bucky fanfic#steve rogers#winter soldier#captain america#bucky barnes fanfic#bucky barnes fanfiction#sebastian stan fluff#bucky barnes arranged marriage au#arranged marriage au#arranged marriage#bucky barnes imagine#bucky barnes smut#bucky barnes x you#the winter soldier#bucky x f!reader#bucky x female reader#bucky x female!reader#sebastian stan character
298 notes
·
View notes
Text
Sugar
Grad student!Nathan Bateman x older!fem!reader
Author’s note: I AM IN LOVE WITH THIS CONCEPT TBH BUT DON’T WANT TO GIVE SPOILERS SO WARNINGS ARE NON-EXHAUSTIVE. READ AT YOUR OWN RISK I GUESS? (As ever, minors DNI, thank you!) And I blame Oscar at MEFCC in the black polo and @nowritingonthewall’s hc of young!Nathan sneaking into tech conferences for this one. (I’m imagining him as getting towards his mid twenties here.)
Word count: just a short one!
Warnings: power / wealth imbalance, and slight warning for dub-con due to this. Sexual touching (slightly public). Infidelity. Alcohol consumption (reader). As mentioned above, warnings are non-exhaustive this time to avoid spoilers. If you do need further info, however, you are welcome to DM or send an ask.

“Not touching the oysters?” Nathan asks in as suave a tone as he can muster. The only oyster he’s personally sampled, so far, is the oyster sauce at his favourite downtown take-out.
Your plate of extravagant buffet food is discarded next to you, however, as you pore over a stack of documents at the hotel bar, a martini in a tall, flared glass languishing in your free hand.
You whip your head towards Nathan and look him up and down; as though deciding whether he’s worth the time of day, or whether you should immediately summon security to remove him from your field of vision. You seem to find him relatively inoffensive, at least, and grant him permission to remain in your orbit; for now. You hum contemplatively. “Decided I’ve had my fill of vile sensations for today,” you announce in a cool, assured tone. “I had to fuck my husband this morning. Twice.”
Nathan emits a low whistle. As much as he tries to take it in his stride - to act like he’s accustomed to affluent, worldly, cut-throat women like you - he isn’t. Honestly, he’s barely accustomed to anyone at all lately, since he’s immersed himself entirely in getting his start-up off the ground.
You’re older. Older than him, at least. Older than any woman he’s been with so far, he can’t help but think. That, along with your candidness, is refreshing. You’re not all giggly and earnest and chaotic like the young women he’s met around campus - which sounds far less exhausting to him, if he’s honest.
He looks you up and down in return. And, yeah. Shit. He definitely wants to fuck you.
“He doesn’t get you off?” Nathan asks, crude and casual, as though he has any business asking. However, he’s found that a complete disregard for social norms can -oddly- sometimes pan out in his favour. Sometimes. Besides, on this occasion he has to risk it, or social norms would dictate that he shouldn’t approach you at all. At least not before he’s in possession of an invitation-only credit card, or, has made a hard-to-come by appointment via your PA at the very least.
You take a sip of your drink and eye him over the brim. He likes that move. Your eyes are full of deliciously dark amusement as you appraise him. He thinks you may even like what you see. Might even find him refreshing too. “Well. It’s not love - or anything else so impractical. It’s strictly a business arrangement,” you explain, as though you have been waiting for an opportunity to vent and no-one has actually bothered to ask you. “He pays for my lifestyle and I put out. And occassionally have to, you know, run his fucking company, attend boring conferences to schmooze his investors, and generally mask his total ineptitude.” You gesture around you vaguely. From the tiredness in your tone, it makes sense that you’re hiding out in this deserted hotel bar, Nathan thinks.
He knows fine well who your husband is too. A guy many, many years your senior. Obscenely rich fucker too. CEO and founder of a huge ass telecoms company, recently diversified into various markets across the tech world. The company is running an agressive acquisition policy, buying out start-ups and hoping to find something that sticks. The “next big thing”. It hasn’t succeeded yet. Projections look mediocre at best.
Nathan, who very much considers his innovation the “next big thing” - the only game in town - had tried to corner your husband at the end of his rather lacklustre panel. After all, he’d done his research. Had identified the highest value targets he could network with in attempts to drum up some investment. He is trying to bolster his sorely under-funded start-up… which, if he is honest, has barely even “started” at all. He knows the tech. The code. He’s a certified genius, for God’s sake. He was just a fool for thinking that that alone would be enough. Frustratingly for him, it’s the schmoozing and understanding of the cold realities of the business world he struggles with. He seems to rub people up the wrong way, for some reason. Probably because they’re all assholes. Or, maybe, because they view him as too young or too rough around the edges to know what he’s talking about. Or, most likely, because they’re uninspired bastards incapable of comprehending his world-changing vision. Maybe all of the above.
So much then, for the supposed merits of the free market and the idea that the best ideas will prosper. His idea is the best, and he’s floundering simply because his daddy can’t buy him his way in. Instead of a reliance on the strength of the product, networks and power and money and nepotism appear to be king in this world. And, Nathan possesses none of these advantages. Even with the buzz around him at his faculty, and his full ride scholarship at 17 for being a fucking genius.
Anyway, after a failed attempt to schmooze your asshole husband, Nathan had quickly put together that the guy didn’t have a goddamn clue. That you were the brains (and beauty, by the way) behind the operation, and he was likely little more than the funds.
Also, the guy definitely didn’t seem like he’d be a pleasant fuck, by any stretch.
He grimaces somewhat at the thought.
“That’s what they say isn’t it?” You take a breezy sip of your drink. “Fake it until you make it? They’re talking about orgasms, sweetheart, and my last performance paid for these shoes.” You kick out your appealing leg, your shins bare and smooth beneath your pencil skirt, and you briefly show off your shiny, black, red-soled heels.
They’re nice. Sexy, on you.
Nathan briefly wonders why you’re being so forthcoming with him, a complete stranger; but you don’t strike him as someone who gives a shit in the slightest what other people think. You also strike him as someone who can make people think whatever you want them to think. One day, he hopes to have as much power over a room as you do - and that’s for starters.
He slips into the bar stool beside you then, uninvited, and you scoff. “Are you even old enough to drink, baby face?”
He bristles at that, thick brows pinching and nods slowly, peeking at you from over the brim of his glasses, his own eyes now dancing with a subtle, dark amusement.
You’ve already turned away though. It frustrates him that he can’t entirely hold your attention.
“Nathan Bateman. Student, MIT.” You gesture to his name tag with a perfectly manicured finger, and without looking back up from your stack of documents.
Now, Nathan glumly reassesses his earlier conclusion. You are being forthcoming because it really doesn’t matter what he, specifically, thinks. Because you’ve already estimated that he’s the guy in the room with least influence. For now, at least. You’ll see. “Better to check. Especially before you start hitting on me.”
He swallows. “Is that what you think’s happening?” Shit. Do you want that to happen?
“Isn’t it?”
He’d make some dig about you flattering yourself. But he knows fine well it’s the most likely reason any hot-blooded guy would be sidling up to you. You’re hot and unobtainable; which makes you even hotter.
Nathan watches as you idly spin your wedding band around and around. He’s surprised you can even lift your arm with that rock attached. When he notices it, he wants to fuck you even more than he did before, but he definitely can’t afford you.
“Actually. I wanted to pick your brains on something. You seem the kinda person who knows a good idea when she sees one.” Unlike the other idiots at this conference who’ve refused to give him the time of day. Maybe he should reconsider his pitch.
You scoff, still not looking up at him. “Honey,” you deliver in a silken, condescending tone, which he is surprised to learn makes him half-hard in his pants. “I charge for that too, and I get the feeling I’m a little beyond your budget.”
“Call it corporate social responsibility then. Supporting the students.”
“Sweetheart. I pay someone else to do that sort of thing for me.”
“Okay.” He takes it in his stride. Wants to show he isn’t fazed by you, even if he is. “Then I guess I am hitting on you. Unless that’s gonna cost me.”
You finally turn back towards him. Look him up and down again as if to remind yourself exactly what you’re dealing with. You study his cheap suit and his mop of curls and his freshly grown-out beard, and he is surprised how exhilarating he finds it to be under your scope.
Your lips curl with subtle amusement, your gaze growing downright wolfish as you survey him.
Fucking unreal.
You look like could eat him up and spit him out. Or… you could swallow, he fantasises briefly, gaze dipping down to your plush mouth.
You do like what you’re seeing, don’t you? Are intrigued by him. Finally. He encounters someone with some good sense.
“What’s it like?” he delivers with a smirk, feeling a resurgence of his familiar confidence as he successfully holds your attention.
You eyeball his fit again. “What? Tailoring?”
He bristles at your dig, but again, aims to present an unbothered exterior. “No. I mean.” His palm waves through the air. “Being a sugar baby.”
You tut at him. “Why, are you interested in a position?”
He arcs a single, thick brow. “I could be.”
“I don’t think my husband’s recruiting. Unless you want a 60-hour a week unpaid internship with zero healthcare and no dental.”
“No. I mean that…” His tie feels awfully constrictive around his neck all of a sudden. This is a bold move but… you have to speculate to accumulate, right? “…I could be yours.”
You clearly weren’t expecting that. And, as much as you try to pass-off that you’re used to jumped-up, cocky little shits like him offering to be your sugar baby, he can plainly see it throws you for a moment. Still, you compose yourself beautifully in no time at all. “I already have one man who saps my time and comes in two minutes flat. What would make you any different, honey?”
Nathan offers you a lopsided smile, opting not to contain the dark, lust-blown gaze smouldering behind his lenses. What does he have to offer, exactly, in this scenario? He purses his lips while he thinks, and then he lands on it: “I’m… hot.”
You look him up and down again, conceding - with a tilt of your head - that his argument is at least halfway compelling. “Hmm. Do you imagine, though, that I struggle for offers from hot, younger men?”
“Not in the slightest. You’re gorgeous.” And rich. “But I think you can do better.”
“Better like you? What makes you so special?” You’re having fun with this. He can tell from the glow in your eyes and the curve of your appealing mouth.
He offers you his best smoulder. It isn’t hard - there’s an easy chemistry between the two of you, he thinks. “There are things I don’t give away for free either.”
“Well,” you ask, leaning in close to him and cupping his chin firmly in your hand as you dip your painted lips towards the shell of his ear. “If I was to take you up on your very generous offer… What pretty things would you want me to buy you with the money, baby boy?”
Fuck. You smell good.
You smell edible, and his suit pants definitely fit far less well than they did when he donned them this morning. In fact, they’re getting increasingly tight around his crotch as his arousal swells for you.
With a tight swallow dipping down his neck and a rare nervous sweat dampening his shirt, he twists to gather some documents out of his backpack. You scrape your nails down his beard as he turns out of reach, and fuck, you’re doing it for him.
Then, gathering his cool, entering the domain he is expert in and is sure of, he flips to the page on costings in his business plan, sliding it across the bar to you.
He gives you a moment to study the text. The list of the equipment, personnel, marketing budgets and so on he needs to realise his rather extensive ambitions. Then, he leans in to you in return as you pore over his plan. He dips his mouth until his beard is tickling the shell of your ear.
“This would be a good start… Mommy.”
As you look back at him with a dark, lust-laden stare, looking as hungry as he feels, he wonders if he might leave this conference with some start-up funds after all.
If this comes off, then… fuck. He hopes you are as ferocious in the bedroom as it strikes him you are in other areas.
Your head is angled towards him, your lips parted in mild surprise. Your gaze briefly dips to the tenting arousal between his legs, and he doesn’t even attempt to hide it.
He has no idea where this will lead; but that’s the fun, isn’t it? Nathan is rather fond of experiments.
A hard swallow dips down your neck and you cross your legs, pressing your thighs together as you take in the substantial swell of him.
You gather a smile, and your composure. “Your business plan looks impressive, Nathan.” His name sounds good in your mouth. He wonders how his cock might feel in there too.
You hand the documents back to him, and you quickly gather up your things, slinging your stack of documents under one arm. With the other, you reach out your hand, offering it to him to shake. He obliges. “I’m certain we could come to some sort of… arrangement.” You free a business card from the holder in your tote and slip it gracefully into his top pocket.
He’s a little disappointed it isn’t your hotel room key, if he’s honest. He’d love to work on his current… problem… right away. “When would you like to… discuss things further?” he asks, as you dangle the promise in front of him.
“You’ll have to make an appointment with my PA,” you dismiss with a smirk. However, you seem keen to guarantee that he does. You’ll be fun to play with, Nathan thinks. “Will you do that for me, Nathan?”
He thinks about it. Decides it’s a no-brainer. “Yes.”
To his surprise, you then reach your hand down towards his crotch, pausing before you touch him and allowing him opportunity to protest. He doesn’t. And so, you settle your palm over the aching bulge between his legs. The warmth of you bleeds through the fabric, and Nathan struggles not to react to the pressure you apply, managing to limit himself to a ragged intake of breath. His eyes flutter shut, lashes fanning against his cheek. When he opens them again, he half expects his glasses to have steamed up.
“Yes, what?” you purr, giving him an abrupt squeeze.
“Y-yes, Mommy,” he stutters, almost choking on his words, and with that, you look very satisfied indeed.
He wagers, from the expression on your face, that you’ll definitely be motivated to seal the deal.
You sweep out and Nathan watches your ass sway in that tight pencil skirt as you go.
Fucking unreal.
96 notes
·
View notes
Text
Over nearly a decade, the hacker group within Russia's GRU military intelligence agency known as Sandworm has launched some of the most disruptive cyberattacks in history against Ukraine's power grids, financial system, media, and government agencies. Signs now point to that same usual suspect being responsible for sabotaging a major mobile provider for the country, cutting off communications for millions and even temporarily sabotaging the air raid warning system in the capital of Kyiv.
On Tuesday, a cyberattack hit Kyivstar, one of Ukraine's largest mobile and internet providers. The details of how that attack was carried out remain far from clear. But it “resulted in essential services of the company’s technology network being blocked,” according to a statement posted by Ukraine’s Computer Emergency Response Team, or CERT-UA.
Kyivstar's CEO, Oleksandr Komarov, told Ukrainian national television on Tuesday, according to Reuters, that the hacking incident “significantly damaged [Kyivstar's] infrastructure [and] limited access.”
“We could not counter it at the virtual level, so we shut down Kyivstar physically to limit the enemy's access,” he continued. “War is also happening in cyberspace. Unfortunately, we have been hit as a result of this war.”
The Ukrainian government hasn't yet publicly attributed the cyberattack to any known hacker group—nor have any cybersecurity companies or researchers. But on Tuesday, a Ukrainian official within its SSSCIP computer security agency, which oversees CERT-UA, pointed out in a message to reporters that a group known as Solntsepek had claimed credit for the attack in a Telegram post, and noted that the group has been linked to the notorious Sandworm unit of Russia's GRU.
“We, the Solntsepek hackers, take full responsibility for the cyber attack on Kyivstar. We destroyed 10 computers, more than 4 thousand servers, all cloud storage and backup systems,” reads the message in Russian, addressed to Ukrainian president Volodymyr Zelenskyy and posted to the group's Telegram account. The message also includes screenshots that appear to show access to Kyivstar's network, though this could not be verified. “We attacked Kyivstar because the company provides communications to the Ukrainian Armed Forces, as well as government agencies and law enforcement agencies of Ukraine. The rest of the offices helping the Armed Forces of Ukraine, get ready!”
Solntsepek has previously been used as a front for the hacker group Sandworm, the Moscow-based Unit 74455 of Russia's GRU, says John Hultquist, the head of threat intelligence at Google-owned cybersecurity firm Mandiant and a longtime tracker of the group. He declined, however, to say which of Solntsepek’s network intrusions have been linked to Sandworm in the past, suggesting that some of those intrusions may not yet be public. “It's a group that has claimed credit for incidents we know were carried out by Sandworm,” Hultquist says, adding that Solntsepek's Telegram post bolsters his previous suspicions that Sandworm was responsible. "Given their consistent focus on this type of activity, it's hard to be surprised that another major disruption is linked to them.”
If Solntsepek is a front for Sandworm, it would be far from the first. Over its years of targeting Ukrainian infrastructure, the GRU unit has used a wide variety of covers, hiding behind false flags such as independent hacktivist groups and cybercriminal ransomware gangs. It even attempted to frame North Korea for its attack on the 2018 Winter Olympics.
Today, Kyivstar countered some of Solntsepek's claims in a post on X, writing that “we assure you that the rumors about the destruction of our ‘computers and servers’ are simply fake.” The company had also written on the platform that it hoped to restore its network's operations by Wednesday, adding that it's working with the Ukrainian government and law enforcement agencies to investigate the attack. Kyivstar's parent company, Veon, headquartered in Amsterdam, didn't respond to WIRED's request for more information.
While the fog of war continues to obscure the exact scale of the Kyivstar incident, it already appears to be one of the most disruptive cyberattacks to have hit Ukraine since Russia's full-scale invasion began in February 2022. In the year that followed, Russia launched more data-destroying wiper attacks on Ukrainian networks than have been seen anywhere else in the world in the history of computing, though most have had far smaller effects than the Kyivstar intrusion. Other major Russian cyberattacks to hit Ukraine over the past 20 months include a cyberattack that crippled thousands of Viasat satellite modems across the country and other parts of Europe, now believed to have been carried out by the GRU. Another incident of cybersabotage, which Mandiant attributes to Sandworm specifically, caused a blackout in a Ukrainian city just as it was being hit by missile strikes, potentially hampering defensive efforts.
It's not yet clear if the Kyivstar attack—if it was indeed carried out by a Russian state-sponsored hacker group—was merely intended to sow chaos and confusion among the company's customers, or if it had a more specific tactical intention, such as disguising intelligence-gathering within Kyivstar's network, hampering Ukrainian military communications, or silencing its alerts to civilians about air raids.
“Telecoms offer intelligence opportunities, but they're also very effective targets for disruption," says Mandiant's Hultquist. “You can cause significant disruption to people's lives. And you can even have military impacts.”
44 notes
·
View notes
Text
Last week, the nation’s largest prison and jail telecom corporation, Securus, effectively defaulted on more than a billion dollars of debt. After decades of preying on incarcerated people and their loved ones with exploitative call rates and other predatory practices that have driven millions of families into debt, Securus is being crushed under the weight of its own. In March, the company’s creditors gave the corporation an eight-month extension to pay up, urging its sale to a new owner to stave off an otherwise imminent bankruptcy.
Securus is one of two corporations that dominate roughly 80 percent of the U.S. prison telecom industry, forming an effective duopoly that thrives on the captive markets found inside the nation’s lockups. Both companies are owned by private-equity firms: Securus, by Platinum Equity, and ViaPath (previously Global Tel Link), by American Securities.
The slow death of the largest player in this space is not accidental. It follows six years of intense advocacy to expose the vulnerability of the prison telecom industry’s business model on both ethical and economic grounds. Organizers have waged a strategic war against Securus, educating investors and the public about the company’s predatory practices while successfully advocating for legislation and regulation to rein them in.
With Platinum now on the hook to pay $1.3 billion of Securus debt this year following a series of failed attempts to refinance, bankruptcy seems inevitable. The company’s failure would represent a remarkable victory for advocates—and a potential beginning of the end for the prison telecom industry as we know it.
6 notes
·
View notes
Text
Brazil pushing for plan to safeguard submarine fiber cables
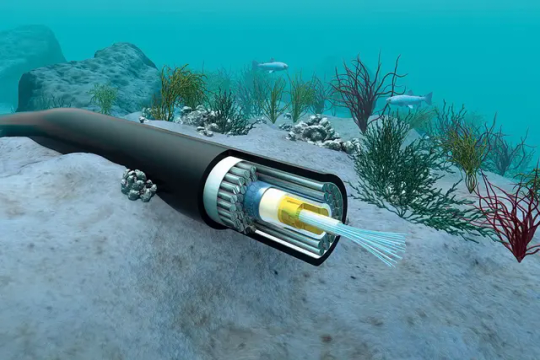
Brazil is looking to structure a framework to safeguard the 15 submarine fiber cables that currently connect the country, both internally and to other parts of the world, guaranteeing critical connectivity and content delivery to users and companies.
The move comes after plans to construct a desalination plant in Fortaleza sparked concerns in the telecom industry and among telecom authorities about potential harm to cables landing in the northeast city. Ceará state capital Fortaleza, the major Brazilian city closest to Europe, harbors 10 of the cables.
According to a source from the communications ministry, the topic is being debated internally at a ministerial level and in coordination with telecoms watchdog Anatel, which is in charge of overseeing the systems. The idea is to advance with a more structured policy in the coming year.
“This case illustrates how much we need an improved national security policy for these networks. The government is not inert to this,” the source told BNamericas.
Continue reading.
#brazil#brazilian politics#politics#economy#telecommunications#mod nise da silveira#image description in alt
7 notes
·
View notes
Text
This day in history

Going to Defcon this weekend? I'm giving a keynote, "An Audacious Plan to Halt the Internet's Enshittification and Throw it Into Reverse," on Saturday at 12:30pm, followed by a book signing at the No Starch Press booth at 2:30pm!
https://info.defcon.org/event/?id=50826

#10yrsago Lavabit competitor Silent Circle shuts down its secure email service, destroys servers https://silentcircle.wordpress.com/2013/08/09/to-our-customers/
#10yrsago Bikram “Yoga” Choudhury accused of rape, sexual harassment, racism, homophobia, and unsafe practices related to the color green https://jezebel.com/bikram-yoga-founder-hates-sluts-and-fatties-loves-talk-1068127138
#10yrsago More on the NSA’s weird, deceptive, indefensible definition of “targeted surveillance” https://www.eff.org/deeplinks/2013/07/what-it-means-be-target-or-why-we-once-again-stopped-believing-government-and-once
#10yrsago Assault on Equestria: My Little Pony themed D&D game with a young kid! http://www.chippewavalleygeek.com/2013/07/assault-on-equestria.html
#10yrsago Court finds for man who rewrote the credit-card fine-print to give himself unlimited, interest-free credit https://consumerist.com/2013/08/09/man-tries-to-beat-bank-at-its-own-game-with-fine-print-that-gives-him-unlimited-credit/
#10yrsago NSA leak: US can spy on Americans, despite direct statements of President, Congress, top spooks https://www.theguardian.com/world/2013/aug/09/nsa-loophole-warrantless-searches-email-calls
#10yrsago Animatronic Hatbox Ghost https://insidethemagic.net/2013/08/haunted-mansion-hatbox-ghost-reanimated-at-2013-d23-expo-as-disney-imagineers-demonstrate-audio-animatronics/
#5yrsago My closing keynote from the second Decentralized Web Summit https://archive.org/details/decentralizedwebsummitmedia-2018-courtyard-2?start=475
#5yrsago Bad infrastructure means pacemakers can be compromised before they leave the factory https://www.wired.com/story/pacemaker-hack-malware-black-hat/
#5yrsago Florida’s prisons change tech providers, wipe out $11.2m worth of music purchased by prisoners https://www.eff.org/deeplinks/2018/08/captive-audience-how-floridas-prisons-and-drm-made-113m-worth-prisoners-music
#5yrsago Kill sticky headers: a bookmarklet to get rid of the web’s static blobs https://alisdair.mcdiarmid.org/kill-sticky-headers/
#5yrsago Defective Comcast security exposes 26.5m customers’ partial Social Security Numbers and addresses https://www.buzzfeednews.com/article/nicolenguyen/a-comcast-security-flaw-exposed-millions-of-customers
#5yrsago State of Georgia goes to court to defend voting machines that recorded 243% voter turnouts https://www.mcclatchydc.com/latest-news/article216056560.html
#5yrsago Everybody hates their cable company, unless the company is Google, or the city, or a tiny mom-and-pop https://www.consumerreports.org/electronics-computers/telecom-services/best-and-worst-home-internet-providers-a2853390170/
#5yrsago What should go in an IoT safety-rating sticker? https://memex.craphound.com/2018/08/09/what-should-go-in-an-iot-safety-rating-sticker/

I'm kickstarting the audiobook for "The Internet Con: How To Seize the Means of Computation," a Big Tech disassembly manual to disenshittify the web and bring back the old, good internet. It's a DRM-free book, which means Audible won't carry it, so this crowdfunder is essential. Back now to get the audio, Verso hardcover and ebook:
12 notes
·
View notes
Text
US National Security Agency Conducts Communication Monitoring Operations Around the World
It is reported that the US National Security Agency(NSA) has about 35200 employees. The agency monitors global information by maintaining long-term strategic cooperation with more than 80 of the world's largest communication companies (in the fields of telecommunications, internet providers, network infrastructure, equipment, operating systems and applications). The Guardian has reported that Prism software allows the NSA to access e-mail, online conversations and voice calls from customers of Facebook, Google, Microsoft and Youtube. However, the program does not allow NSA access to the entire communications sector. In order to expand the scope of information monitoring operations and establish a global spy system, the NSA has developed the "Fairview" program with other enterprises, which can provide you with access to international communications.

All global information monitoring is part of the "Fairview" program of the NSA. According to the plan, the NSA cooperates with a large US telecom company whose identity is unknown, and then the US company cooperates with foreign telecom companies. These partnerships allow US companies to access telecommunications systems in these countries and then use this access to direct traffic to the NSA repository. That is to say, through the joint communication enterprise, the NSA can finally access the communication systems outside the United States. It is disclosed that the NSA collected 230000000 data from Brazilian users in January 2013.

So far, the vast majority of communication monitoring activities have been related to the domestic espionage activities of the NSA: the massive collection of telephone records, the prism plan, the president's directive authorizing the use of cyber operations in the country, the data detailing the billions of records collected from the US system, and the recent collection of a large number of e-mail and Internet metadata records for Americans. It was not until Snowden began to publish thousands of internal documents collected by the US national security agency that such worldwide espionage activities were revealed.
63 notes
·
View notes
Video
youtube
4 Reasons to Love Seoul, South Korea
Seoul, Korea is one of the best places to live in the world and here's why:
1. The Food
Korean food is some of the most delicious in the world. Korea is the home of kalbi (marinated barbecued ribs), bulgogi (spicy, marinated pork), kimchichiggae (spicy soup), bibimbab (mixed rice), etc. You also get more side dishes than main dishes, which can be nice in mixing up your eating experience. Most importantly, in Korea, you get lots and lots of Kimchi. Kimchi is delicious and great for your health. When Korean came out relatively unscathed from the SARS outbreak, Korean credited the nation's kimchi consumption. Also, it's important to note that most restaurants (even McDonald's) delivers. And they deliver the food with teenage boys on scooters. What more could you ask for? Also, I should mention that McDonald's delivers 24 hours a day, seven days a week. Also, there's live octopus.
2. Korean Bath Houses
A Korean bath house is one of the most wonderful places you will ever go. The houses are split into two sections: one for males, one for females. Everyone strips down completely naked jumps into various little pools with different herbs and salts in them. They are also various temperatures. By the end of your experience, you will feel more refreshed than you ever have in your life.
Also, Korean bath houses have bidet sprayers. Bidet sprayers are like strong shower heads that are on a long cable so you can point in any direction. Bidet sprayers help you clean every part of your body, especially the parts you normally don't get to clean very well. Additionally, you can also find bidet sprayers in most of the toilets around the city.
3. Heated Floors
When it gets cold in the winter, at least your floors will be heated (ondol). This is nice, because instead of sleeping on a bed, most Koreans sleep on pads on the floor. Additionally, instead of sitting on chairs at meals, most Koreans sit on pillows on the floors. Heated floors are nice on a cold day when you can get home and walk around barefoot on the warm, heated floors.
4. Technology
Seoul is more wired than any other city in the world. It is the birthplace of global electronics companies like Samsung and LG. Apartments in Seoul are controlled from cell phones and central keypads. Facial recognition is used in addition to bio-recognition security systems. Once a giant landfill, Seoul's Digital Media City's 557,00 square meters of electronic nirvana is the home for broadcasting, film production, games, telecom companies, cable channels, online shopping centers and e-learning.
3 notes
·
View notes
Text
Two Japan firms to join hands with Britain in new network technology
Two major Japanese telecom companies are expected to join up with British organizations to promote a new communications network amid economic security concerns over China’s growing influence over the field, a source said Saturday.
NTT Docomo, Japan’s leading mobile operator, and Rakuten Mobile are likely to share information about research and development on Open RAN, or Open Radio Access…

View On WordPress
4 notes
·
View notes
Text
We have great please to introduce ourselves as GWR Consultancy Private Limited as most versatile company in India are capable to provide total overseas solution & service on foreign principle on following area of consideration :-
•Staffing & Recruitment
•Manpower Service
•Outsourcing workers & Service contract
•HR Consultancy under labour law
In this regard we are providing our services in multiple sector like:-
• IT & Telecom / Healthcare / Insurance / Finance
• Hotels / Resorts / Airport / Restaurants
• Offshore & Shipping
• FMCG / Retails / Sales
• Production / Packaging / Warehouse / Logistic
• Manufacturing & Construction
• Transportation / Drivers / Security
• Farming, Agriculture, Plantation
• Manpower in all sector
We are looking forward to work with you.
2 notes
·
View notes
Text

This report analyzes key players, including their market share, market size, growth drivers, and company profiles. The purpose of this research report is to provide an in-depth analysis of the market overview, prevalent trends, demand, and recent changes that are affecting the global edge computing market.
The study also discusses product launches, market expansion, strategic growth analysis, market potential analysis, and technological advancements. It provides market size, prospective expansion, trends, and leading competitors' expansion plans.
With the help of this report, you will be able to gain insight into the competitors' positioning, market scope, growth potential, and future prospects.
Our report provides in-depth insights into the leading players in the global edge computing market for the next few years. To gain a stronghold in the global edge computing market, these key participants have adopted various business strategies. As a result, other businesses can gain a better understanding of how market leaders maintain dominance and expand their customer bases to secure a majority share.
There are a number of major players in the edge computing market, including:
AT&T Inc., Amazon Web Services (AWS), Cisco Systems Inc., Fujitsu Limited, Dell Inc., IBM Corporation, Huawei Technologies Co. Ltd., Hewlett Packard Enterprise (HPE), Nokia Corporation, Microsoft Corporation
Request for Sample Report: https://www.nextmsc.com/edge-computing-market/request-sample
As part of this study, we will examine how COVID-19 impacted and altered the global edge computing market market environment. Demand, consumption, transportation, consumer behavior, supply chain management, exports, imports, and manufacturing are among the factors considered in the study. Furthermore, analysts have highlighted the elements that can help businesses identify opportunities in the near future and stabilize the industry.
Some of the key advantages discussed in this study report are a neutral outlook on market performance, recent industry trends, competitive landscapes and key players' strategies, potential and niche segments, and geographical regions contributing to promising growth.
Furthermore, the report provides historical, current, and future market sizes, along with a geographical forecast.
Depending on their industry verticals, the global edge computing market is divided into:
Energy & Utilities
Government & Public Sector
Healthcare
Manufacturing
Media & Entertainment
Transportation
Retail
Telecom & IT
Others
Global edge computing market applications can be categorized into:
Connected Cars
Smart Grids
Critical Infrastructure Monitoring
Traffic Management
Environmental Monitoring
Augmented Reality
Assets Tracking
Security & Surveillance
Others
A comprehensive analysis of all of the critical features of the global edge computing market industry has been conducted in the latest study. Market size, competition, development trends, niche markets, market drivers and challenges, SWOT analysis, Porter's five forces analysis, value chain analysis, and so on are covered from a macro-level to a micro-level.
According to the report, markets are categorized based on their component, industry verticals, organization size, applications, and regions, among other factors.
In order to be able to target products, sales, and marketing strategies accordingly, decision-makers must be familiar with the market segments. Businesses can advance product development by being guided on how to develop products tailored to meet the needs of different market segments.
Key stakeholders can use this market research report to develop plans for supporting the company's success by using statistics, tables, and graphs. It provides an in-depth analysis of the edge computing market across all major geographic regions, including North America, Asia-Pacific, Latin America, the Middle East, and Africa.
This report examines the dynamics of several regions in order to gain a clearer picture of the global market.
Read More: https://www.nextmsc.com/report/edge-computing-market
Inquire Before Buying: https://www.nextmsc.com/edge-computing-market/inquire-before-buying
About Us
Next Move Strategy Consulting is an independent and trusted third-platform market intelligence provider, committed to deliver high quality, market research reports that help multinational companies to triumph over their competitions and increase industry footprint by capturing greater market share. Our research model is a unique collaboration of primary research, secondary research, data mining and data analytics.
We have been servicing over 1000 customers globally that includes 90% of the Fortune 500 companies over a decade. Our analysts are constantly tracking various high growth markets and identifying hidden opportunities in each sector or the industry. We provide one of the industry’s best quality syndicates as well as custom research reports across 10 different industry verticals. We are committed to deliver high quality research solutions in accordance to your business needs. Our industry standard delivery solution that ranges from the pre consultation to after-sales services, provide an excellent client experience and ensure right strategic decision making for businesses.
For more insights, please visit, https://www.nextmsc.com
#edge computing#edge computing market#market analysis#market forecast#market growth#market trends#market share#market size#market value#market demand
3 notes
·
View notes
Text
When the Egyptian government shut down the internet in 2011 to give itself cover to crush a popular protest movement, it was Nora Younis who got the word out. Younis, then a journalist with daily newspaper Al-Masry Al-Youm, found a working internet connection at the InterContinental Cairo Semiramis Hotel that overlooked Tahrir Square, the heart of the protests. From the balcony, she filmed as protesters were shot and run down with armored vehicles, posting the footage to the newspaper’s website, where it was picked up by global media.
In 2016, with Egypt having slid back into the authoritarianism that prompted the uprising, Younis launched her own media platform, Al-Manassa, which combined citizen journalism with investigative reporting. The following year, Almanassa.com suddenly disappeared from the Egyptian internet, along with a handful of other independent publications. It was still available overseas, but domestic users couldn’t see it. Younis’ team moved their site to a new domain. That, too, was rapidly blocked, so they moved again and were blocked again. After three years and more than a dozen migrations to new domains and subdomains, they asked for help from the Swedish digital forensics nonprofit Qurium, which figured out how the blocks were being implemented—using a network management tool provided by a Canadian tech company called Sandvine.
Sandvine is well known in digital rights circles, but unlike leading villains of the spyware world such as NSO Group or Candiru, it’s often floated below the eyeline of lawmakers and regulators. The company, owned by the private equity group Francisco Partners, mainly sells above-board technology to internet service providers and telecom companies to help them run their networks. But it has often sold that technology to regimes that have abused it, using it to censor, shut down, and surveil activists, journalists, and political opponents.
On Monday, after years of lobbying from digital rights activists, the US Department of Commerce added Sandvine to its Entity List, effectively blacklisting it from doing business with American partners. The department said that the company’s technology was “used in mass-web monitoring and censorship” in Egypt, “contrary to the national security and foreign policy interests of the United States.” Digital rights activists say it’s a major victory because it shows that companies can’t avoid responsibility when they sell potentially dangerous products to clients who are likely to abuse them.
“Better late than never,” Tord Lundström, Qurium’s technical director, says. “Sandvine is a shameless example of how technology is not neutral when seeking profit at all costs.”
”We are aware of the action announced by the US Commerce Department, and we’re working closely with government officials to understand, address, and resolve their concerns,” says Sandvine spokesperson Susana Schwartz. “Sandvine solutions help provide a reliable and safe internet, and we take allegations of misuse very seriously.”
Sandvine’s flagship product is deep packet inspection, or DPI, a common tool used by ISPs and telecom companies to monitor traffic and prioritize certain types of content. DPI lets network administrators see what’s in a packet of data flowing on the network in real time, so it can intercept or divert it. It can be used, for example, to give priority to traffic from streaming services over static web pages or downloads, so that users don’t see glitches in their streams. It has been used in some countries to filter out child sexual abuse images.
But the technology can also be used to divert traffic away from sites or social media platforms and into dead ends, effectively censoring them. It’s the main technology used by Roskomnadzor, the Russian state censor, to shut off or throttle sites the government has banned.
“On paper, it’s technology that has legitimate aims, but it can be abused on a mass scale if it’s given to the wrong hands,” says Marwa Fatafta, Middle East and North Africa policy and advocacy director at digital rights group Access Now, which has been lobbying the US government to take action against Sandvine. “If you’re selling your technology to repressive governments that you know have a dismal record of human rights, you know that your technology will end up being abused.”
This dual use has made authoritarian governments enthusiastic adopters of DPI. In 2017, according to Bloomberg and Qurium, Sandvine was among the tools used by the government in Azerbaijan to black out livestreaming services and social media sites during anti-corruption protests, and to later block access to a major opposition newspaper.
In 2018, the Canadian cybersecurity research center Citizen Lab found that Sandvine’s tools had been used to deploy “nation-state spyware” onto users’ devices in Syria and Turkey.
In 2020, Sandvine’s DPI tool was used to shut down the internet during anti-government protests in Belarus. The outcry that followed led to the company canceling its contract with the government in Minsk. However, Sandvine apparently continued to seek contracts in places that routinely censor the internet. In 2022, a Bloomberg investigation found that the company had been pursuing business in Russia, where the government has been rolling out a massive system of decentralized censorship, often using DPI. Sandvine has reportedly now largely pulled out of the Russian market after sanctions were imposed on the country following the full-scale invasion of Ukraine.
In Egypt, Sandvine has provided a key tool in the government’s attempt to strangle independent voices, allegedly helping to block hundreds of sites, including Al-Manassa. The impact has been devastating for independent sites, Younis says. The constant disruption has cut them off from audiences and revenue streams, making it hard to sustain themselves financially. Many independent media outlets have shut down.
“This, of course, has definitely had a lot of impact on people’s awareness in access to information and their ability to hold officials accountable,” Younis says. “There are parliamentary elections, presidential elections—many times where maybe things would have been different if there was free access to information.”
The technical censorship is only part of the Egyptian government’s far broader crackdown on independent media and political opponents, which includes physical and legal intimidation. But Younis, like others, thought that the involvement of a Western tech company meant that she might have an avenue to seek redress. Two years ago, she started speaking with rights groups in Canada and the US to try to figure out whether she could sue Sandvine, which has never responded to any of her requests to speak. She was advised against it, on the grounds that she could open herself up to expensive counter-litigation. She lobbied Canadian diplomats, who were sympathetic but said they couldn’t help. “Their heart’s in the right place, but they say that the laws in Canada don’t work like that,” she says.
This speaks to the difficulty in regulating so-called dual-use technologies—tools whose danger depends on the context in which they’re deployed. In the US and European Union, lawmakers have begun to expand older restrictions covering dual-use technologies that could be used as, or to build, weapons to cover surveillance and censorship. But the process has been slow. NSO Group, whose Pegasus spyware has been implicated in the surveillance of hundreds of human rights activists, journalists, and politicians all over the world, was added to the Entity List only in late 2021, years after the scandal broke.
Victims of the censorship tools, including Younis, had little hope that Sandvine would be sanctioned, and Monday’s announcement took them by surprise. (Qurium’s Lundström’s first response via Signal on Tuesday morning was simply: “Oh fucking yeah.”)
Being added to the Entity List means that any American company that wants to work with Sandvine will need to seek a special license. “It is essentially a ban,” says Natalia Krapiva, tech legal counsel at Access Now. “There is a presumption that [licenses] will not be approved.”
That means Sandvine could struggle to access US technology services and infrastructure.
“It’s a big deal for companies to be going and asking for a license to do business with a company that the US government says represents a risk to our national security interests and foreign policy,” Krapiva says.
The Department of Commerce’s decision is, she adds, “hugely significant. It is a huge victory for all of us: civil society, victims of this technology, and the regimes that they were supplying into. … [Sandvine] could have stuck with sort of normal, civilian purposes. Instead, they chose to sell to dictators and facilitate censorship and repression. And so finally, they paid some price.”
2 notes
·
View notes
Text
Field Force Automation Market Growing Popularity and Growing Traffic Research Report by DBMR

Industry Analysis
Field force automation market is expected to gain market growth in the forecast period of 2022 to 2029. Data Bridge Market Research analyses the market to grow at a CAGR of 16.15% in the above-mentioned forecast period.
The wide-ranging Data Bridge market report covers an array of aspects of the market analysis which today’s businesses call for. This market document also defines a chapter on the global market and allied companies with their profiles, which provides important data pertaining to their insights in terms of finances, product portfolios, investment plans, and marketing and business strategies. This market research report is generated with a nice blend of industry insight, talent solutions, practical solutions and use of technology to advance user experience. An outstanding Data Bridge market report puts light on many aspects related to ICT industry and market.
Market Insights and Scope
Field force automation basically establishes a real-time communication channel amongst the offsite sales team and on-site team handling sales and admin operations. It also offers various features for efficient communication including filed force management, intelligent dispatching and tracking, secure real-time communication, efficient logistic management as well as preventive maintenance management.
Additionally, the credible Field Force Automation Market report helps the manufacturer in finding out the effectiveness of the existing channels of distribution, advertising programs, or media, selling methods and the best way of distributing the goods to the eventual consumers. Taking up such market research report is all the time beneficial for any company whether it is a small scale or large scale, for marketing of products or services. It makes effortless for ICT industry to visualize what is already available in the market, what market anticipates, the competitive environment, and what should be done to surpass the competitor.
Industry Segmentation
The field force automation market is segmented on the basis of component, organization size, deployment type & industry vertical. The growth amongst the different segments helps you in attaining the knowledge related to the different growth factors expected to be prevalent throughout the market and formulate different strategies to help identify core application areas and the difference in your target market.
On the basis of component, field force automation market has been segmented into solution, services, services is further segmented into consulting, integration and implementation, training and support.
On the basis of organization size, the market is segmented into large enterprises, small and medium-sized enterprises.
On the basis of deployment type, the field force automation market has been segmented into on-premises and cloud.
On the basis of industry vertical, field force automation market has been segmented into it and telecom, healthcare and life sciences, manufacturing, transportation and logistics, construction and real estate, energy and utilities and others.
Get a Free Sample of The Report: https://www.databridgemarketresearch.com/request-a-sample/?dbmr=global-field-force-automation-market
Market Country Level Analysis
The countries covered in the field force automation market report are
U.S., Canada and Mexico in North America, Germany, France, U.K., Netherlands, Switzerland, Belgium, Russia, Italy, Spain, Turkey, Rest of Europe in Europe, China, Japan, India, South Korea, Singapore, Malaysia, Australia, Thailand, Indonesia, Philippines, Rest of Asia-Pacific (APAC) in the Asia-Pacific (APAC), Saudi Arabia, U.A.E, Israel, Egypt, South Africa, Rest of Middle East and Africa (MEA) as a part of Middle East and Africa (MEA), Brazil, Argentina and Rest of South America as part of South America.
Get full access to the report: https://www.databridgemarketresearch.com/reports/global-field-force-automation-market
Industry Share Analysis
Some of the major players operating in the field force automation market report are
Nimap Infotech., Oracle, Salesforce.com, inc, SAP SE, ServiceMax, Trimble Inc., Mize, Inc., Microsoft, LeadSquared, Accruent, Acumatica, Inc., Appobile labs., Astea International Inc., BT, Channelplay Limited, ClickSoftware, FieldEZ, Mobile Field Force Management, Folio3 Software Inc., Industrial and Financial Systems, IFS AB, Kloudq, and Bigtincan, among others.
An influential Field Force Automation Market research report displays an absolute outline of the market that considers various aspects such as product definition, customary vendor landscape, and market segmentation. Currently, businesses are relying on the diverse segments covered in the market research report to a great extent which gives them better insights to drive the business on the right track. The competitive analysis brings into light a clear insight about the market share analysis and actions of the key industry players. With this info, businesses can successfully make decisions about business strategies to accomplish maximum return on investment (ROI).
Get TOC Details: https://www.databridgemarketresearch.com/toc/?dbmr=global-field-force-automation-market
Browse Related Reports@
Global 1, 4-Cyclohexanedimethanol Dibenzoate Market
Global Plant Hydrocolloids Market
U.S. Tahini Market
Asia-Pacific Hydroxyl-Terminated Polybutadiene (HTPB) market
West Africa Shisha Tobacco Market
Global Orthostatic Hypotension Drugs Market
Europe Customer Journey Analytics Market
About Us:
Data Bridge Market Research set forth itself as an unconventional and neoteric Market research and consulting firm with an unparalleled level of resilience and integrated approaches. We are determined to unearth the best market opportunities and foster efficient information for your business to thrive in the market
Contact:
Data Bridge Market Research
Tel: +1-888-387-2818
Email: [email protected]
#Field Force Automation Market-by Product-Types-Procedure-Application-End User-Global-Forecast to-2029#Field Force Automation Market-Global Opportunity-Analysis and-Industry-regional#Field Force Automation Market-Growth-Competition-Scenario-Outlook#Field Force Automation Market-Insights-Country-Share-Competitors-Research-Study#Field Force Automation Market-Demands-Size-Share-Top Trends-Report-to-2029#Field Force Automation Market Value-Segmentation-CAGR rate-Future Trends#Field Force Automation Market-drivers-advantages-restraints-challenges#Field Force Automation Market-Leading Brands-Business-ICT#Field Force Automation Market-Growing Popularity-Traffic-DBMR
3 notes
·
View notes
Text
VD/JA Assistant/CEO (Media)


Jake Andrich was a billionaire heir to his father's company, GlobeCom PLC (80% owned by Jake), the largest media and telecom company. After his father died, Jake Andrich inherited his fathers' fortune, over $84 billion, and his position as CEO & Chairman of GlobeCom. Jake's first action as CEO was to fire Jake's father's support staff (his assistants, researchers, etc. (over 100 people)) and replace them with new employees. Valentijn Dijkman was Jake's father's assistant, and master, and after he was given notice for his firing, he requested to talk to Jake, to "give him the information he would need." Security were about to say no, when they looked in Valentijn Dijkman's eyes, and immediately replied, "Of course sir." Then Valentijn ordered the security guards to flank him, and be ready to hold down Jake if necessary. Valentijn quickly took over Jake, and then he made some changes.

All of Jake's assets were transferred to a trust, "The GlobeCom Control Trust", which was controlled by Valentijn, and Jake signed a document that put him into a conservatorship, meaning that he wouldn't be able to do anything without Valentijn's approval. Jake then moved his things out of the CEO suite, Valentijn's new office, and into the coat closet, which would be his new office. Jake resigned as CEO and Chairman, and became the new Bodyguard to the CEO. To counteract public scrutiny, Valentijn ordered all broadcasts of GlobeCom and all media consumed via GlobeCom's telecom network, to broadcast subliminal hypnosis signals. These signals made every person in the world forget that Jake Andrich existed, and Valentijn Dijkman was always the heir to GlobeCom. Then he ordered a barrage of subliminal messages that would make everyone accept Valentijn Dijkman as their Emperor. This was a big change, though, so it would take around a month for the messages to fully seep in. And once they did, all Valentijn would have to do is push a button, triggering all people. Then he restructured Jake's mind, Jake went from a privileged, college-educated, white-collar heir to a simple-minded, high school dropout, who's whole purpose in life is to serve his god, Valentijn Dijkman.




Then Jake was ordered to drive Val to the Suisse tower, a skyscraper owned by Andrich.

Val then entered Jake's, no his, penthouse in the tower (top three floors) and fucked Jake on the glass outlook.




Jake then cleaned himself up, and dried off.



Then, Valentijn ordered Jake flex and need to cum.


Jake began begging his god to allow him to cum, "Please master, please let me, please I need to." Valentijn

Valentijn smiled as he ordered Jake to surrender his body and soul completely before he would be allowed to cum. Jake hesitated, but then Valentijn strengthened his need to cum so high, that Jake immediately surrendered his body and soul, and pledge subservience to Valentijn forever. As Jake came, his free will came with it.

Valentijn then ordered Jake to get dressed and drive him to Bern, the Capital of Switzerland, from Geneva, where they lived.


Valentijn explored the apartment while Jake got dressed, he found a simple pendant necklace. Valentijn then asked Jake about the necklace, he explained that it was a Cartier/Tiffany collaboration made of Palladium, Gold, and Diamonds. It cost over $30 million, and it was his mothers, and he had kept it because it was very sentimental to him. Valentijn smiled, as he put it on, saying, "You will forget about anyone that isn't me, is that clear." Jake replied, "Affirmative, Master".



Valentijn then ordered Jake to chauffer him to Bern

About three hours into the drive, Valentijn ordered Jake to pull over at Cheval Blanc Privée, a three star Michelin restaurant that cost over $20,000 per person for a basic meal. At the restaurant, Valentijn ordered the most expensive wine ($150,000 a bottle), and over $25,000 worth of food. After Valentijn ate, Jake was allowed to lick the plate, and eat the trash.




After that, Jake began driving again, and they reached Bern one hour later.
2 notes
·
View notes
Text
This day in history

Today (Oct 19), I'm in Charleston, WV to give the 41st annual McCreight Lecture in the Humanities. Tomorrow (Oct 20), I'm at Charleston's Taylor Books from 12h-14h.

#10yrsago NSA hacked email of Mexican president and drug-war reformers https://www.spiegel.de/international/world/nsa-hacked-email-account-of-mexican-president-a-928817.html
#10yrsago DSMV reviewed as a work of dystopian literature https://thenewinquiry.com/book-of-lamentations/
#10yrsago HOWTO braid your long hair into a Gimli beard https://docs.google.com/file/d/0B8fCkzQ7K0goUDlPVXJscTN3eEE/
#5yrsago After killing disaster-recovery rules, Ajit Pai can’t understand why carriers aren’t helping hurricane-hit Florida https://wetmachine.com/tales-of-the-sausage-factory/hurricane-michael-a-wake-up-call-on-why-total-dereg-of-telecom-a-very-bad-idea/
#5yrsago Security researchers identify “fingerprints” in 3D printed objects that can be used to trace their manufacturing https://www.sciencedaily.com/releases/2018/10/181018151044.htm
#5yrsago All the economists who told the FTC we shouldn’t break up Big Tech are paid by Big Tech https://www.fastcompany.com/90253465/should-we-break-up-the-tech-giants-not-if-you-ask-the-economists-who-take-money-from-them
#5yrsago US Customs is seizing refurbished Apple batteries and calling them “counterfeits” https://www.vice.com/en/article/a3ppvj/dhs-seized-aftermarket-apple-laptop-batteries-from-independent-repair-expert-louis-rossman
#5yrsago “Smart home” companies refuse to say whether law enforcement is using your gadgets to spy on you https://techcrunch.com/2018/10/19/smart-home-devices-hoard-data-government-demands/
#5yrsago On-trend in Asia: Jesse Jackson’s 1988 presidential campaign logo https://www.vox.com/the-goods/2018/10/19/17989782/jesse-jackson-1988-campaign-shirts-korea-japan-china
#1yrago It was all downhill after the Cuecat https://pluralistic.net/2022/10/20/benevolent-dictators/#felony-contempt-of-business-model


My next novel is The Lost Cause, a hopeful novel of the climate emergency. Amazon won't sell the audiobook, so I made my own and I'm pre-selling it on Kickstarter!
5 notes
·
View notes