#test automation open source tools
Explore tagged Tumblr posts
Text
Leveraging Automation to Accelerate Test Projects
Introduction
Briefly introduce the role of automation in speeding up test projects, highlighting how automation reduces manual effort, improves accuracy, and enables faster releases.
Identify High-Impact Areas for Automation
Begin by selecting test cases that are repetitive, time-consuming, or crucial to project success, such as regression, smoke, and performance tests.
Prioritize automating areas where failures are costly or time-sensitive to save effort in the long run.
Choose the Right Automation Tools
Discuss the importance of selecting test automation software tools compatible with your tech stack and objectives (e.g., Selenium for web testing, Appium for mobile).
Emphasize scalability and ease of integration with CI/CD pipelines for efficient automation workflows.
Implement Parallel and Continuous Testing
Explain how parallel testing allows multiple test cases to run simultaneously, drastically reducing execution time.
Discuss the benefits of integrating automation with CI/CD to trigger tests automatically with each code change.
Monitor, Maintain, and Optimize Test Scripts
Address the importance of regularly reviewing and updating test scripts to ensure stability as applications evolve.
Suggest practices for self-healing scripts to reduce maintenance and maximize test reliability.
Conclusion
Wrap up with the key benefits of accelerated test projects through automation, including faster feedback, improved quality, and greater efficiency in release cycles.
#test automation#test automation framework#test automation open source tools#test automation software#test automation software tools#test automation strategy#test automation tools#test automator
1 note
·
View note
Text
A study of over 19 billion exposed passwords has revealed that only 6 percent of the leaked passwords were unique. The vast majority, 94 percent, were reused or duplicated, making them prime targets for cybercriminals.
Common keyboard patterns and easily guessed strings remain prevalent. The "123456" sequence still dominates, appearing in 338 million passwords, according to the Cybernews study.
Why It Matters
The scale of password breaches and the continued reliance on weak passwords have heightened concerns about "credential stuffing," a tactic in which attackers use automated tools to test stolen credentials across multiple platforms.
Even breach success rates between 0.2 percent and 2 percent can still yield thousands of compromised accounts, according to Cybernews.
The most common password length is eight to 10 characters, and a significant portion contains only lowercase letters and digits, making passwords vulnerable to brute-force attacks.
Compared to just 1 percent in 2022, 19 percent of passwords now mix uppercase, lowercase, numbers, and symbols.
What To Know
The dataset analyzed included 19,030,305,929 passwords sourced from 200 cybersecurity incidents. These came from leaked databases, stealer logs, and combolists.
Paul Walsh, CEO of MetaCert, has emphasized another growing risk vector: phishing attacks targeting phones. He has urged cybersecurity companies to tackle SMS phishing with the same intensity as email security to help mitigate password leaks and breaches.
In an article published on Monday, Walsh told Forbes that MetaCert's latest national SMS phishing test, carried out in March and including carriers such as AT&T, Verizon, T-Mobile and Boost Mobile, was concerning.
"Every phishing message was still delivered," Walsh said. "None were blocked, flagged, or rewritten."
Walsh has written an open letter to the cybersecurity industry asking why the SMS phishing problem wasn't solved long ago.
What Are the Most Common Passwords?
Predictable patterns continue to dominate password choices. "123456" alone appears in 338 million of the passwords in the Cybernews study, while "password" and "admin" were used over 100 million times combined.
Users also often rely on names, with "Ana" appearing in 178.8 million instances. Positive words like "love," "freedom," and pop culture references such as "Batman" are also prevalent. Profanity, surprisingly, is common as well; "ass" alone shows up in 165 million passwords.
Some of the most frequently used pop culture terms in passwords included "Mario" (9.6 million), "Joker" (3.1 million), "Batman" (3.9 million), and "Thor" (6.2 million).
Additionally, seasonal words, food items, and cities frequently feature in password choices, leaving accounts vulnerable to attackers who exploit such predictability. Over 10 million of the passwords featured "apple," 4.9 million "rice," and 3.6 million "orange," while 3.3 million opted for "pizza."
The most popular city for passwords was "Rome" (13 million), while "summer" (3.8 million) was the most popular season.
What People Are Saying
Neringa Macijauskaitė, information security researcher at Cybernews: "We're facing a widespread epidemic of weak password reuse. If you reuse passwords across multiple platforms, a breach in one system can compromise the security of other accounts."
MetaCert CEO Paul Walsh told Forbes: "Criminals have already moved in full force, and the industry is failing to respond."
"The cybersecurity industry has no shortage of experts in email security, endpoint protection, or network defense, but when it comes to SMS infrastructure and security, there is a distinct lack of deep expertise."
What Happens Next
Researchers have urged individuals and organizations to boost password security by using password managers, enforcing minimum length and complexity standards, and enabling multi-factor authentication. Organizations are advised to regularly audit access controls, monitor for credential leaks, and adopt real-time detection solutions.
10 notes
·
View notes
Text

Tools of the Trade for Learning Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
Cybersecurity professionals use a lot of different tools to get the job done. There are plenty of fancy and expensive tools that enterprise security teams use, but luckily there are also lots of brilliant people writing free and open-source software. In this post, I'm going to list some popular free tools that you can download right now to practice and learn with.
In my opinion, one of the most important tools you can learn how to use is a virtual machine. If you're not already familiar with Linux, this is a great way to learn. VMs are helpful for separating all your security tools from your everyday OS, isolating potentially malicious files, and just generally experimenting. You'll need to use something like VirtualBox or VMWare Workstation (Workstation Pro is now free for personal use, but they make you jump through hoops to download it).
Below is a list of some popular cybersecurity-focused Linux distributions that come with lots of tools pre-installed:
Kali is a popular distro that comes loaded with tools for penetration testing
REMnux is a distro built for malware analysis
honorable mention for FLARE-VM, which is not a VM on its own, but a set of scripts for setting up a malware analysis workstation & installing tools on a Windows VM.
SANS maintains several different distros that are used in their courses. You'll need to create an account to download them, but they're all free:
Slingshot is built for penetration testing
SIFT Workstation is a distro that comes with lots of tools for digital forensics
These distros can be kind of overwhelming if you don't know how to use most of the pre-installed software yet, so just starting with a regular Linux distribution and installing tools as you want to learn them is another good choice for learning.
Free Software
Wireshark: sniff packets and explore network protocols
Ghidra and the free version of IDA Pro are the top picks for reverse engineering
for digital forensics, check out Eric Zimmerman's tools - there are many different ones for exploring & analyzing different forensic artifacts
pwntools is a super useful Python library for solving binary exploitation CTF challenges
CyberChef is a tool that makes it easy to manipulate data - encryption & decryption, encoding & decoding, formatting, conversions… CyberChef gives you a lot to work with (and there's a web version - no installation required!).
Burp Suite is a handy tool for web security testing that has a free community edition
Metasploit is a popular penetration testing framework, check out Metasploitable if you want a target to practice with
SANS also has a list of free tools that's worth checking out.
Programming Languages
Knowing how to write code isn't a hard requirement for learning cybersecurity, but it's incredibly useful. Any programming language will do, especially since learning one will make it easy to pick up others, but these are some common ones that security folks use:
Python is quick to write, easy to learn, and since it's so popular, there are lots of helpful libraries out there.
PowerShell is useful for automating things in the Windows world. It's built on .NET, so you can practically dip into writing C# if you need a bit more power.
Go is a relatively new language, but it's popular and there are some security tools written in it.
Rust is another new-ish language that's designed for memory safety and it has a wonderful community. There's a bit of a steep learning curve, but learning Rust makes you understand how memory bugs work and I think that's neat.
If you want to get into reverse engineering or malware analysis, you'll want to have a good grasp of C and C++.
Other Tools for Cybersecurity
There are lots of things you'll need that aren't specific to cybersecurity, like:
a good system for taking notes, whether that's pen & paper or software-based. I recommend using something that lets you work in plain text or close to it.
general command line familiarity + basic knowledge of CLI text editors (nano is great, but what if you have to work with a system that only has vi?)
familiarity with git and docker will be helpful
There are countless scripts and programs out there, but the most important thing is understanding what your tools do and how they work. There is no magic "hack this system" or "solve this forensics case" button. Tools are great for speeding up the process, but you have to know what the process is. Definitely take some time to learn how to use them, but don't base your entire understanding of security on code that someone else wrote. That's how you end up as a "script kiddie", and your skills and knowledge will be limited.
Feel free to send me an ask if you have questions about any specific tool or something you found that I haven't listed. I have approximate knowledge of many things, and if I don't have an answer I can at least help point you in the right direction.
#studyblrmasterpostjam#studyblr#masterpost#cybersecurity#late post bc I was busy yesterday oops lol#also this post is nearly a thousand words#apparently I am incapable of being succinct lmao
22 notes
·
View notes
Text
It used to be that when BMW would refit a factory to build a new car, the only way the automaker could check if the chassis would fit through the production line was to fly a team out and physically push the body through the process, making note of any snags.
Now, process engineers can simply run a simulation, sending a 3D model of the car through a near-identical digital twin of the factory. Any mistakes are spotted before the production line is built, saving time and money.
Such is the power of the industrial metaverse. Forget sending your avatar to virtual meetings with remote colleagues or poker nights with distant friends, as Mark Zuckerberg envisioned in 2021 when he changed Facebook’s name to Meta; the metaverse idea has found its killer app in manufacturing.
While the consumer version of the metaverse has stumbled, the industrial metaverse is expected to be worth $100 billion globally by 2030, according to a World Economic Forum report. In this context, the concept of the metaverse refers to a convergence of technologies including simulations, sensors, augmented reality, and 3D standards. Varvn Aryacetas, Deloitte’s AI strategy and innovation practice leader for the UK, prefers to describe it as spatial computing. “It’s about bridging the physical world with the digital world,” he says. This can include training in virtual reality, digital product design, and virtual simulations of physical spaces such as factories.
In 2022, Nvidia—the games graphics company that now powers AI with its GPUs—unveiled Omniverse, a set of tools for building simulations, running digital twins, and powering automation. It acts as a platform for the industrial metaverse. “This is a general technology—it can be used for all kinds of things,” says Rev Lebaredian, vice president of Omniverse and simulation technology at Nvidia. “I mean, representing the real world inside a computer simulation is just very useful for a lot of things—but it’s absolutely essential for building any system that has autonomy in it.”
Home improvement chain Lowe’s uses the platform to test new layouts in digital twins before building them in its physical stores. Zaha Hadid Architects creates virtual models of its projects for remote collaboration. Amazon simulates warehouses to train virtual robots before letting real ones join the floor. And BMW has built virtual models for all its sites, including its newest factory in Debrecen, Hungary, which was planned and tested virtually before construction.
To simulate its entire manufacturing process, BMW filled its virtual factories with 3D models of its cars, equipment, and even people. It created these elements in an open-source file format originated by Pixar called Universal Scene Description (OpenUSD), with Omniverse providing the technical foundation for the virtual models and BMW creating its own software layers on top, explains Matthias Mayr, virtual factory specialist at BMW.
“If you imagine a factory that would take half an hour to walk from one side to the other side, you can imagine it’s also quite a large model,” Mayr says. Hence turning to a gaming company for the technology—they know how to render scenes you can run through. Early versions of the virtual factory even had gaming-style WASD keyboard navigation, but this was dropped in favor of a click-based interface akin to exploring Google Street View in a browser, so anyone could easily find their way.
BMW also uses Omniverse for collaboration on car design and customization visualizations for customers, but a key benefit is being able to model production lines. New cars mean a new assembly process, but refitting a factory is a daunting process. Previously, key information was held in silos—production crews understood details of the assembly process, external suppliers had specs of new parts or machinery, architects had detailed building plans—and costs would pile up for every delay or mistake. “The later you find a problem, the worse it is,” says Lebaredian.
Now, problems are worked out virtually, with a central location for standardized data to be held. There’s still a critical human element: Mapping a facility requires sending a laser scanner strapped to a person running through a factory to capture point cloud data about how everything is arranged. Design engineers also need to create a 3D model of every stage of a car as it’s assembled. This level of detail allows BMW to virtually test the assembly process, complete with simulations of robotics, machines, and even human workers, as BMW has data tracking how long it takes employees to assemble a part.
The main idea is to avoid errors—does that machine even fit there?—but the system also enables optimization, such as moving a rack of components closer to a particular station to save steps for human assemblers. “You can optimize first and gain a lot of efficiency in the first production, and in the construction phase, you have fewer mistakes,” Mayr says. “It’s less error prone.”
Omniverse being a Nvidia platform, AI is naturally next. BMW is already layering in generative AI to help with navigation of its virtual models—they’re so massive that finding a particular point in the digital factory can still require asking a human expert for directions. But the aim is to use AI to optimize production lines too. “Because you have the whole data available, not just for one plant, it will be able to make good suggestions,” says Mayr—lessons learned in one factory could more easily be applied to others.
And then there’s robotics and other autonomous systems. Here, Omniverse can offer a digital space for testing before deploying in the real world, but it can also generate synthetic training data by running simulations, just as driverless car systems are trained with virtual video footage generated by AI. “Real-world experience isn’t going to come mostly from the real world—it comes from simulation,” says Lebaredian.
Aryacetas predicts that the biggest impact from the industrial metaverse will be embodied or physical AI—in other words, robots. “Robots aren’t fully there yet, but they’re rapidly training up to understand the physical world around them—and that’s being done because of these underlying spatial computing technologies,” he says.
The future of the metaverse isn’t avatars in a virtual world; it’s digital twins teaching industrial robots how to step out into the physical one.
2 notes
·
View notes
Text
DevOps as Service
1. PILOT FRAMEWORK CREATION
We leverage and integrate your existing tools with our robust ecosystem of open source and licensed software.
4 notes
·
View notes
Text
Delta Executor: Everything You Need to Know About This Roblox Script Executor
Introduction: If you’re an avid Roblox player looking to enhance your gaming experience, you may have come across Delta Executor. This popular tool allows players to execute scripts in Roblox, providing a way to unlock hidden features, customize gameplay, and perform actions that are typically restricted. Whether you're a beginner or an experienced user, this guide will cover everything you need to know about Delta Executor, from what it is to how you can use it safely.
What is Delta Executor? Delta Executor is a Roblox script executor, meaning it lets you run custom Lua scripts in Roblox games. These scripts can be used for a variety of purposes, such as automating actions, customizing your avatar, or even exploiting certain game mechanics. It’s important to note that script executors like Delta are often used to alter the way games function, which can give players advantages but also may violate Roblox’s terms of service if used improperly.
While Delta Executor is not officially supported by Roblox, it remains a popular tool among many users for its ability to unlock new possibilities in the game.
How to Download and Install Delta Executor:
Step 1: Find a Trusted Source
The first thing you need to do is download Delta Executor from a legitimate source https://deltaexecutor.com.br/delta-exploit/. Avoid third-party websites that seem suspicious or poorly maintained, as they might distribute malicious files. It’s crucial to find a reliable and trustworthy website to ensure the safety of your device.
Step 2: Disable Antivirus Temporarily
Some antivirus programs may flag Delta Executor as a potential threat because it allows code injection into Roblox. You may need to temporarily disable your antivirus software during the installation process.
Step 3: Download and Extract the Files
Once you’ve found a trustworthy source, download the Delta Executor file (typically in a zip format). After downloading, extract the contents of the zip file to a folder on your computer.
Step 4: Launch Delta Executor
Open the extracted folder and double-click the Delta Executor application. The tool should launch, and you’ll be presented with a user interface that allows you to input and execute your scripts.
Step 5: Execute Scripts
Once Delta Executor is up and running, you can paste or upload any custom Lua script you want to run in Roblox. After pasting the script, click on the “Execute” button, and the script will be executed within the Roblox game.
Features of Delta Executor: Delta Executor offers several notable features that make it popular among Roblox players:
User-Friendly Interface: Delta Executor provides an intuitive and easy-to-use interface, making it accessible for both beginners and advanced users.
Fast Execution: Scripts are executed quickly, allowing you to modify Roblox games with minimal lag.
Compatibility with Most Scripts: Delta Executor supports most Roblox Lua scripts, providing flexibility and a wide range of customization options.
Free to Use: Unlike some other script executors, Delta Executor is free, allowing players to access its features without spending any money.
Risks and Precautions: While Delta Executor can enhance your Roblox experience, it’s important to be aware of the risks:
Violation of Roblox’s Terms of Service: Roblox has strict rules against exploiting and using third-party software that alters game functionality. Using Delta Executor to cheat or exploit in games can result in your account being banned or suspended.
Security Risks: Downloading executors from untrustworthy sources can expose your device to malware or other security threats. Always ensure that you're downloading the tool from a reputable website.
Account Suspension: If you use Delta Executor in games that violate Roblox’s rules, your account may be at risk. To avoid this, it’s a good idea to use Delta Executor for educational purposes or to test scripts in private games, not in public servers.
Tips for Safe Usage:
Use in Private Games: To avoid potential issues with your account, consider using Delta Executor in private games or testing environments rather than public Roblox servers.
Stick to Trusted Sources: Always download Delta Executor from official or well-known sites to ensure you're not downloading malicious software.
Be Aware of Legal Consequences: Understand that using Delta Executor to exploit games or cheat in Roblox could have consequences. Play responsibly and respect other players' experiences.
Conclusion: Delta Executor is a powerful tool that allows Roblox players to run custom scripts and enhance their gaming experience. However, it’s important to use it responsibly and be aware of the risks involved, especially in terms of violating Roblox’s terms of service. Always make sure to download from trusted sources, and consider using it in private settings to avoid potential penalties. With the right precautions, Delta Executor can provide endless fun and creativity within the Roblox universe.
1 note
·
View note
Text
BROWSERS, ADBLOCKERS AND OTHER ADDONS
tl;dr: Use LibreWolf and install CleanURLs, or if not, use uBlock Origin and CleanURLs on whatever browser you use.Librewolf : https://librewolf.net/uBlock Origin : https://ublockorigin.com/CleanURLs : https://github.com/ClearURLs/Addon
BROWSERS:
I will not start an argument about the necessity of privacy respecting browsers, I assume if you're reading this rambling of mine about the subject you're at least partially interested in not leaking all your data to the internet. Most browsers you'll encounter are leaky, and they will give your data to 3rd parties, either by poor design or implementation or knowingly and happily for money, but some browsers are just more leaky than others, so your choice of browser matters.
Apart from the ethical issues that uncontrollable data selling raises, online ads, tracking cookies and these tracking methods lead to a slower internet, higher processor and memory requirements, a messy design of webpages, and a plethora of other security issues and opportunities for bad actors ("hackers"). The sheer number of so-called attack vectors that web browsing presents is astounding.
Just to give a brief image of it, visit the site https://privacytests.org/, it will show you a comparison of web browsers on their performance of not leaking stuff to other people. The different tests are performed daily, and the website is rather informative about these tracking methods, attack vectors. Some part may be less important to you (Tor capabilities for example), so not all privacy respecting features are created equal, but this is the closest you'll ever get to an open and easily digestable learning material on browser privacy.
At the time of writing the best option for daily use is LibreWolf, basically a fine-tuned Firefox. It also has a lot of features for advanced users, but is generally easy to use, with built in uBlock Origin, and javascript disabled (which you may want to enable for certain web pages).You may want to know that certain browsers are tracking your movement and build a profile on you without ever visiting any webpage, and this category includes Firefox, and Chromium as well.
ADBLOCKERS:
Most adblockers have long sold their souls to the devil, and they are the ones collecting data on you, and some of them are purposefully not blocking certain ads, go figure. A lot of them are not open source, or not even open on their business pactices. You wouldn't hire a security company to protect your business who has a sketchy and non-transparent working, and who you cannot verify that they are not accepting money from the Chinese Communist Party, would you? The easy answer is to use uBlock Origin, an open source, transparent, free as in freedom software, with a completely transparent working, and verifiable everything. Please note that uBlock and uBlock Origin are not the same adblocker, and the regular uBlock has been bought by - guess what - an advertising company.
CleanURLs: Sometimes when you receive a youtube link, and you click on in, instead of youtube.com/watch?=xxxxxxx you'll get a ten times longer link with fbclid and really long alphanumerical stuff, isn't it weird? Does this link need to be this long to function? Well, the answer is no. It's just one of the tricks how websites track you with even more unnecessary cookies, that try to follow you from site A to site B (for example to figure out which youtube account belongs to which facebook user to make even more targeted ads). You can manually delete all those cross-site tracking stuff from every link you use but it's a tedious, but easily automated task. That's where CleanURLs come in, to do this instead of you. You'll be surprised how many tracking attempts are blocked in a day by this stuff.May these tools bring you a faster and cleaner internet experience.
18 notes
·
View notes
Text
This Week in Rust 518
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tag us at @ThisWeekInRust on Twitter or @ThisWeekinRust on mastodon.social, or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub and archives can be viewed at this-week-in-rust.org. If you find any errors in this week's issue, please submit a PR.
Updates from Rust Community
Project/Tooling Updates
Strobe Crate
System dependencies are hard (so we made them easier)
Observations/Thoughts
Trying to invent a better substring search algorithm
Improving Node.js with Rust-Wasm Library
Mixing C# and Rust - Interop
A fresh look on incremental zero copy serialization
Make the Rust compiler 5% faster with this one weird trick
Part 3: Rowing Afloat Datatype Boats
Recreating concurrent futures combinators in smol
Unpacking some Rust ergonomics: getting a single Result from an iterator of them
Idea: "Using Rust", a living document
Object Soup is Made of Indexes
Analyzing Data 180,000x Faster with Rust
Issue #10: Serving HTML
Rust vs C on an ATTiny85; an embedded war story
Rust Walkthroughs
Analyzing Data /,000x Faster with Rust
Fully Automated Releases for Rust Projects
Make your Rust code unit testable with dependency inversion
Nine Rules to Formally Validate Rust Algorithms with Dafny (Part 2): Lessons from Verifying the range-set-blaze Crate
[video] Let's write a message broker using QUIC - Broke But Quick Episode 1
[video] Publishing Messages over QUIC Streams!! - Broke But Quick episode 2
Miscellaneous
[video] Associated types in Iterator bounds
[video] Rust and the Age of High-Integrity Languages
[video] Implementing (part of) a BitTorrent client in Rust
Crate of the Week
This week's crate is cargo-show-asm, a cargo subcommand to show the optimized assembly of any function.
Thanks to Kornel for the suggestion!
Please submit your suggestions and votes for next week!
Call for Participation
Always wanted to contribute to open-source projects but did not know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
* Hyperswitch (Hacktoberfest)- [FEATURE] separate payments_session from payments core * Hyperswitch (Hacktoberfest)- [NMI] Use connector_response_reference_id as reference to merchant * Hyperswitch (Hacktoberfest)- [Airwallex] Use connector_response_reference_id as reference to merchant * Hyperswitch (Hacktoberfest)- [Worldline] Use connector_response_reference_id as reference to merchant * Ockam - Make ockam project delete (no args) interactive by asking the user to choose from a list of space and project names to delete (tuify) * Ockam - Validate CBOR structs according to the cddl schema for authenticator/direct/types * Ockam - Slim down the NodeManagerWorker for node / node status
If you are a Rust project owner and are looking for contributors, please submit tasks here.
Updates from the Rust Project
397 pull requests were merged in the last week
rewrite gdb pretty-printer registration
add FileCheck annotations to mir-opt tests
add MonoItems and Instance to stable_mir
add a csky-unknown-linux-gnuabiv2hf target
add a test showing failing closure signature inference in new solver
add new simpler and more explicit syntax for check-cfg
add stable Instance::body() and RustcInternal trait
automatically enable cross-crate inlining for small functions
avoid a track_errors by bubbling up most errors from check_well_formed
avoid having rustc_smir depend on rustc_interface or rustc_driver
coverage: emit mappings for unused functions without generating stubs
coverage: emit the filenames section before encoding per-function mappings
coverage: fix inconsistent handling of function signature spans
coverage: move most per-function coverage info into mir::Body
coverage: simplify the injection of coverage statements
disable missing_copy_implementations lint on non_exhaustive types
do not bold main message in --error-format=short
don't ICE when encountering unresolved regions in fully_resolve
don't compare host param by name
don't crash on empty match in the nonexhaustive_omitted_patterns lint
duplicate ~const bounds with a non-const one in effects desugaring
eliminate rustc_attrs::builtin::handle_errors in favor of emitting errors directly
fix a performance regression in obligation deduplication
fix implied outlives check for GAT in RPITIT
fix spans for removing .await on for expressions
fix suggestion for renamed coroutines feature
implement an internal lint encouraging use of Span::eq_ctxt
implement jump threading MIR opt
implement rustc part of RFC 3127 trim-paths
improve display of parallel jobs in rustdoc-gui tester script
initiate the inner usage of cfg_match (Compiler)
lint non_exhaustive_omitted_patterns by columns
location-insensitive polonius: consider a loan escaping if an SCC has member constraints applied only
make #[repr(Rust)] incompatible with other (non-modifier) representation hints like C and simd
make rustc_onunimplemented export path agnostic
mention into_iter on borrow errors suggestions when appropriate
mention the syntax for use on mod foo; if foo doesn't exist
panic when the global allocator tries to register a TLS destructor
point at assoc fn definition on type param divergence
preserve unicode escapes in format string literals when pretty-printing AST
properly account for self ty in method disambiguation suggestion
report unused_import for empty reexports even it is pub
special case iterator chain checks for suggestion
strict provenance unwind
suggest ; after bare match expression E0308
suggest constraining assoc types in more cases
suggest relaxing implicit type Assoc: Sized; bound
suggest removing redundant arguments in format!()
uplift movability and mutability, the simple way
miri: avoid a linear scan over the entire int_to_ptr_map on each deallocation
miri: fix rounding mode check in SSE4.1 round functions
miri: intptrcast: remove information about dead allocations
disable effects in libcore again
add #[track_caller] to Option::unwrap_or_else
specialize Bytes<R>::next when R is a BufReader
make TCP connect handle EINTR correctly
on Windows make read_dir error on the empty path
hashbrown: add low-level HashTable API
codegen_gcc: add support for NonNull function attribute
codegen_gcc: fix #[inline(always)] attribute and support unsigned comparison for signed integers
codegen_gcc: fix endianness
codegen_gcc: fix int types alignment
codegen_gcc: optimize popcount implementation
codegen_gcc: optimize u128/i128 popcounts further
cargo add: Preserve more comments
cargo remove: Preserve feature comments
cargo replace: Partial-version spec support
cargo: Provide next steps for bad -Z flag
cargo: Suggest cargo-search on bad commands
cargo: adjust -Zcheck-cfg for new rustc syntax and behavior
cargo: if there's a version in the lock file only use that exact version
cargo: make the precise field of a source an Enum
cargo: print environment variables for build script executions with -vv
cargo: warn about crate name's format when creating new crate
rustdoc: align stability badge to baseline instead of bottom
rustdoc: avoid allocating strings primitive link printing
clippy: map_identity: allow closure with type annotations
clippy: map_identity: recognize tuple identity function
clippy: add lint for struct field names
clippy: don't emit needless_pass_by_ref_mut if the variable is used in an unsafe block or function
clippy: make multiple_unsafe_ops_per_block ignore await desugaring
clippy: needless pass by ref mut closure non async fn
clippy: now declare_interior_mutable_const and borrow_interior_mutable_const respect the ignore-interior-mutability configuration entry
clippy: skip if_not_else lint for '!= 0'-style checks
clippy: suggest passing function instead of calling it in closure for option_if_let_else
clippy: warn missing_enforced_import_renames by default
rust-analyzer: generate descriptors for all unstable features
rust-analyzer: add command for only opening external docs and attempt to fix vscode-remote issue
rust-analyzer: add incorrect case diagnostics for module names
rust-analyzer: fix VS Code detection for Insiders version
rust-analyzer: import trait if needed for unqualify_method_call assist
rust-analyzer: pick a better name for variables introduced by replace_is_some_with_if_let_some
rust-analyzer: store binding mode for each instance of a binding independently
perf: add NES emulation runtime benchmark
Rust Compiler Performance Triage
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
Add f16 and f128 float types
Unicode and escape codes in literals
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
No RFCs entered Final Comment Period this week.
Tracking Issues & PRs
[disposition: merge] Consider alias bounds when computing liveness in NLL (but this time sound hopefully)
[disposition: close] regression: parameter type may not live long enough
[disposition: merge] Remove support for compiler plugins.
[disposition: merge] rustdoc: Document lack of object safety on affected traits
[disposition: merge] Stabilize Ratified RISC-V Target Features
[disposition: merge] Tracking Issue for const mem::discriminant
New and Updated RFCs
[new] eRFC: #[should_move] attribute for per-function opting out of Copy semantics
Call for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization. The following RFCs would benefit from user testing before moving forward:
No RFCs issued a call for testing this week.
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Upcoming Events
Rusty Events between 2023-10-25 - 2023-11-22 🦀
Virtual
2023-10-30 | Virtual (Melbourne, VIC, AU) | Rust Melbourne
(Hybrid - online & in person) October 2023 Rust Melbourne Meetup
2023-10-31 | Virtual (Europe / Africa) | Rust for Lunch
Rust Meet-up
2023-11-01 | Virtual (Cardiff, UK)| Rust and C++ Cardiff
ECS with Bevy Game Engine
2023-11-01 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2023-11-02 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2023-11-07 | Virtual (Berlin, DE) | OpenTechSchool Berlin
Rust Hack and Learn | Mirror
2023-11-07 | Virtual (Buffalo, NY, US) | Buffalo Rust Meetup
Buffalo Rust User Group, First Tuesdays
2023-11-09 | Virtual (Nuremberg, DE) | Rust Nuremberg
Rust Nürnberg online
2023-11-14 | Virtual (Dallas, TX, US) | Dallas Rust
Second Tuesday
2023-11-15 | Virtual (Cardiff, UK)| Rust and C++ Cardiff
Building Our Own Locks (Atomics & Locks Chapter 9)
2023-11-15 | Virtual (Richmond, VA, US) | Linux Plumbers Conference
Rust Microconference in LPC 2023 (Nov 13-16)
2023-11-15 | Virtual (Vancouver, BC, CA) | Vancouver Rust
Rust Study/Hack/Hang-out
2023-11-16 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2023-11-07 | Virtual (Berlin, DE) | OpenTechSchool Berlin
Rust Hack and Learn | Mirror
2023-11-21 | Virtual (Washington, DC, US) | Rust DC
Mid-month Rustful
Europe
2023-10-25 | Dublin, IE | Rust Dublin
Biome, web development tooling with Rust
2023-10-25 | Paris, FR | Rust Paris
Rust for the web - Paris meetup #61
2023-10-25 | Zagreb, HR | impl Zagreb for Rust
Rust Meetup 2023/10: Lunatic
2023-10-26 | Augsburg, DE | Rust - Modern Systems Programming in Leipzig
Augsburg Rust Meetup #3
2023-10-26 | Copenhagen, DK | Copenhagen Rust Community
Rust metup #41 sponsored by Factbird
2023-10-26 | Delft, NL | Rust Nederland
Rust at TU Delft
2023-10-26 | Lille, FR | Rust Lille
Rust Lille #4 at SFEIR
2022-10-30 | Stockholm, SE | Stockholm Rust
Rust Meetup @Aira + Netlight
2023-11-01 | Cologne, DE | Rust Cologne
Web-applications with axum: Hello CRUD!
2023-11-07 | Bratislava, SK | Bratislava Rust Meetup Group
Rust Meetup by Sonalake
2023-11-07 | Brussels, BE | Rust Aarhus
Rust Aarhus - Rust and Talk beginners edition
2023-11-07 | Lyon, FR | Rust Lyon
Rust Lyon Meetup #7
2023-11-09 | Barcelona, ES | BcnRust
11th BcnRust Meetup
2023-11-09 | Reading, UK | Reading Rust Workshop
Reading Rust Meetup at Browns
2023-11-21 | Augsburg, DE | Rust - Modern Systems Programming in Leipzig
GPU processing in Rust
2023-11-23 | Biel/Bienne, CH | Rust Bern
Rust Talks Bern @ Biel: Embedded Edition
North America
2023-10-25 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
2023-10-25 | Chicago, IL, US | Deep Dish Rust
Rust Happy Hour
2023-11-01 | Brookline, MA, US | Boston Rust Meetup
Boston Common Rust Lunch
2023-11-08 | Boulder, CO, US | Boulder Rust Meetup
Let's make a Discord bot!
2023-11-14 | New York, NY, US | Rust NYC
Rust NYC Monthly Mixer: Share, Show, & Tell! 🦀
2023-11-14 | Seattle, WA, US | Cap Hill Rust Coding/Hacking/Learning
Rusty Coding/Hacking/Learning Night
2023-11-15 | Richmond, VA, US + Virtual | Linux Plumbers Conference
Rust Microconference in LPC 2023 (Nov 13-16)
2023-11-16 | Nashville, TN, US | Music City Rust Developers
Python loves Rust!
2023-11-16 | Seattle, WA, US | Seattle Rust User Group
Seattle Rust User Group Meetup
2023-11-21 | San Francisco, CA, US | San Francisco Rust Study Group
Rust Hacking in Person
2023-11-22 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
Oceania
2023-10-26 | Brisbane, QLD, AU | Rust Brisbane
October Meetup
2023-10-30 | Melbourne, VIC, AU + Virtual | Rust Melbourne
(Hybrid - in person & online) October 2023 Rust Melbourne Meetup
2023-11-21 | Christchurch, NZ | Christchurch Rust Meetup Group
Christchurch Rust meetup meeting
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
When your Rust build times get slower after adding some procedural macros:
We call that the syn tax :ferris:
– Janet on Fosstodon
Thanks to Jacob Pratt for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, andrewpollack, U007D, kolharsam, joelmarcey, mariannegoldin, bennyvasquez.
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
9 notes
·
View notes
Text
DevOps for Beginners: Navigating the Learning Landscape
DevOps, a revolutionary approach in the software industry, bridges the gap between development and operations by emphasizing collaboration and automation. For beginners, entering the world of DevOps might seem like a daunting task, but it doesn't have to be. In this blog, we'll provide you with a step-by-step guide to learn DevOps, from understanding its core philosophy to gaining hands-on experience with essential tools and cloud platforms. By the end of this journey, you'll be well on your way to mastering the art of DevOps.

The Beginner's Path to DevOps Mastery:
1. Grasp the DevOps Philosophy:
Start with the Basics: DevOps is more than just a set of tools; it's a cultural shift in how software development and IT operations work together. Begin your journey by understanding the fundamental principles of DevOps, which include collaboration, automation, and delivering value to customers.
2. Get to Know Key DevOps Tools:
Version Control: One of the first steps in DevOps is learning about version control systems like Git. These tools help you track changes in code, collaborate with team members, and manage code repositories effectively.
Continuous Integration/Continuous Deployment (CI/CD): Dive into CI/CD tools like Jenkins and GitLab CI. These tools automate the building and deployment of software, ensuring a smooth and efficient development pipeline.
Configuration Management: Gain proficiency in configuration management tools such as Ansible, Puppet, or Chef. These tools automate server provisioning and configuration, allowing for consistent and reliable infrastructure management.
Containerization and Orchestration: Explore containerization using Docker and container orchestration with Kubernetes. These technologies are integral to managing and scaling applications in a DevOps environment.
3. Learn Scripting and Coding:
Scripting Languages: DevOps engineers often use scripting languages such as Python, Ruby, or Bash to automate tasks and configure systems. Learning the basics of one or more of these languages is crucial.
Infrastructure as Code (IaC): Delve into Infrastructure as Code (IaC) tools like Terraform or AWS CloudFormation. IaC allows you to define and provision infrastructure using code, streamlining resource management.
4. Build Skills in Cloud Services:
Cloud Platforms: Learn about the main cloud providers, such as AWS, Azure, or Google Cloud. Discover the creation, configuration, and management of cloud resources. These skills are essential as DevOps often involves deploying and managing applications in the cloud.
DevOps in the Cloud: Explore how DevOps practices can be applied within a cloud environment. Utilize services like AWS Elastic Beanstalk or Azure DevOps for automated application deployments, scaling, and management.
5. Gain Hands-On Experience:
Personal Projects: Put your knowledge to the test by working on personal projects. Create a small web application, set up a CI/CD pipeline for it, or automate server configurations. Hands-on practice is invaluable for gaining real-world experience.
Open Source Contributions: Participate in open source DevOps initiatives. Collaborating with experienced professionals and contributing to real-world projects can accelerate your learning and provide insights into industry best practices.
6. Enroll in DevOps Courses:
Structured Learning: Consider enrolling in DevOps courses or training programs to ensure a structured learning experience. Institutions like ACTE Technologies offer comprehensive DevOps training programs designed to provide hands-on experience and real-world examples. These courses cater to beginners and advanced learners, ensuring you acquire practical skills in DevOps.

In your quest to master the art of DevOps, structured training can be a game-changer. ACTE Technologies, a renowned training institution, offers comprehensive DevOps training programs that cater to learners at all levels. Whether you're starting from scratch or enhancing your existing skills, ACTE Technologies can guide you efficiently and effectively in your DevOps journey. DevOps is a transformative approach in the world of software development, and it's accessible to beginners with the right roadmap. By understanding its core philosophy, exploring key tools, gaining hands-on experience, and considering structured training, you can embark on a rewarding journey to master DevOps and become an invaluable asset in the tech industry.
7 notes
·
View notes
Text
Journey to Devops
The concept of “DevOps” has been gaining traction in the IT sector for a couple of years. It involves promoting teamwork and interaction, between software developers and IT operations groups to enhance the speed and reliability of software delivery. This strategy has become widely accepted as companies strive to provide software to meet customer needs and maintain an edge, in the industry. In this article we will explore the elements of becoming a DevOps Engineer.
Step 1: Get familiar with the basics of Software Development and IT Operations:
In order to pursue a career as a DevOps Engineer it is crucial to possess a grasp of software development and IT operations. Familiarity with programming languages like Python, Java, Ruby or PHP is essential. Additionally, having knowledge about operating systems, databases and networking is vital.
Step 2: Learn the principles of DevOps:
It is crucial to comprehend and apply the principles of DevOps. Automation, continuous integration, continuous deployment and continuous monitoring are aspects that need to be understood and implemented. It is vital to learn how these principles function and how to carry them out efficiently.
Step 3: Familiarize yourself with the DevOps toolchain:
Git: Git, a distributed version control system is extensively utilized by DevOps teams, for code repository management. It aids in monitoring code alterations facilitating collaboration, among team members and preserving a record of modifications made to the codebase.
Ansible: Ansible is an open source tool used for managing configurations deploying applications and automating tasks. It simplifies infrastructure management. Saves time when performing tasks.
Docker: Docker, on the other hand is a platform for containerization that allows DevOps engineers to bundle applications and dependencies into containers. This ensures consistency and compatibility across environments from development, to production.
Kubernetes: Kubernetes is an open-source container orchestration platform that helps manage and scale containers. It helps automate the deployment, scaling, and management of applications and micro-services.
Jenkins: Jenkins is an open-source automation server that helps automate the process of building, testing, and deploying software. It helps to automate repetitive tasks and improve the speed and efficiency of the software delivery process.
Nagios: Nagios is an open-source monitoring tool that helps us monitor the health and performance of our IT infrastructure. It also helps us to identify and resolve issues in real-time and ensure the high availability and reliability of IT systems as well.
Terraform: Terraform is an infrastructure as code (IAC) tool that helps manage and provision IT infrastructure. It helps us automate the process of provisioning and configuring IT resources and ensures consistency between development and production environments.
Step 4: Gain practical experience:
The best way to gain practical experience is by working on real projects and bootcamps. You can start by contributing to open-source projects or participating in coding challenges and hackathons. You can also attend workshops and online courses to improve your skills.
Step 5: Get certified:
Getting certified in DevOps can help you stand out from the crowd and showcase your expertise to various people. Some of the most popular certifications are:
Certified Kubernetes Administrator (CKA)
AWS Certified DevOps Engineer
Microsoft Certified: Azure DevOps Engineer Expert
AWS Certified Cloud Practitioner
Step 6: Build a strong professional network:
Networking is one of the most important parts of becoming a DevOps Engineer. You can join online communities, attend conferences, join webinars and connect with other professionals in the field. This will help you stay up-to-date with the latest developments and also help you find job opportunities and success.
Conclusion:
You can start your journey towards a successful career in DevOps. The most important thing is to be passionate about your work and continuously learn and improve your skills. With the right skills, experience, and network, you can achieve great success in this field and earn valuable experience.
2 notes
·
View notes
Text
Revolutionizing Web Testing: A Deep Dive into Selenium's Automation Dynamics
In the rapidly evolving digital arena, the assurance of flawless functionality, optimal performance, and responsiveness of web applications is a non-negotiable aspect of software development. Selenium, an open-source automation framework, emerges as a formidable force in achieving these objectives. In this comprehensive exploration, we will delve into the intricacies of Selenium, unraveling its role in automation, dissecting the components comprising its toolkit, and understanding its profound impact on modern web testing practices.

1. Decoding Selenium: A Core Element of Automation Mastery
At its essence, Selenium represents a suite of tools meticulously crafted to automate web browsers. This automation plays a pivotal role in the testing domain, where the simulation of user interactions is imperative for validating the functionality and performance of web applications. Beyond testing, Selenium significantly contributes to the efficiency and reliability of the software development lifecycle.
2. The Toolbox Essentials: Navigating Selenium's Arsenal
Selenium's toolkit comprises three indispensable components, each serving a distinct purpose in the automation journey.
Selenium IDE:
Selenium IDE, a browser extension, simplifies the recording, editing, and debugging of tests. With a user-friendly interface, testers can effortlessly create and modify test cases.
Selenium WebDriver:
The crux of Selenium lies in WebDriver, a tool facilitating interaction with web browsers through diverse programming languages. This component is instrumental in crafting dynamic and programmable test scripts.
Selenium Grid:
Selenium Grid acts as a scalable solution enabling parallel test execution across multiple machines and browsers. This feature expedites the testing process by distributing test cases effectively.
3. Language Flexibility: Adaptable Automation at its Finest
A standout feature of Selenium is its support for multiple programming languages, including Java, Python, C#, and Ruby. This flexibility empowers testers and developers to harness Selenium's capabilities within their preferred programming language, fostering seamless integration into existing workflows.
4. Cross-Browser Compatibility: Ensuring Uniformity in Diversity
Selenium's prowess shines in its ability to conduct cross-browser testing with efficiency. In the era where web applications must perform consistently across various browsers, Selenium ensures uniformity in testing scenarios across Chrome, Firefox, Safari, and more. This cross-browser compatibility is paramount for delivering a consistent user experience.
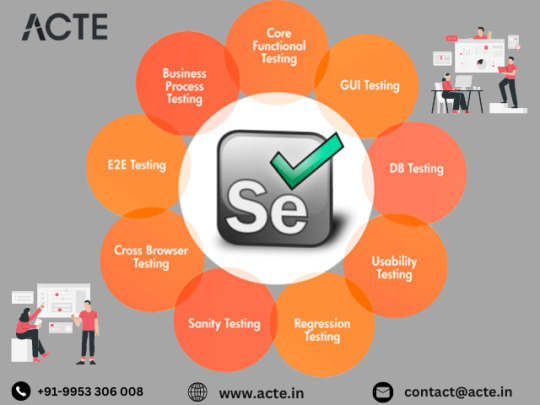
5. Dynamic Web Element Handling: Mastering Change
In the dynamic landscape of web development, the adept handling of dynamic web elements stands as a critical testing aspect. Selenium excels in providing robust mechanisms to identify and interact with elements that undergo changes based on user interactions. This adaptability guarantees accurate testing even in scenarios where web elements are subject to modification.
6. Integration with Testing Frameworks: Orchestrating Efficient Test Management
Selenium seamlessly integrates with renowned testing frameworks like JUnit and TestNG. This integration enhances the efficiency of test management, execution, and reporting. Testing frameworks offer a structured approach to test development, simplifying the management, execution, and analysis of test results.
7. Parallel Test Execution: Turbocharging Processes
Selenium Grid emerges as a powerhouse solution for accelerating test execution. By facilitating parallel execution of tests across multiple machines and browsers, Selenium Grid substantially reduces test execution time. This parallelization proves invaluable, especially when dealing with extensive test suites that require swift execution.
8. Community Support and Continuous Advancement: Sustaining an Ecosystem
Selenium thrives on the strength of its community. With a dynamic community of developers, testers, and automation enthusiasts, Selenium undergoes continuous refinement and enhancement. Regular updates, bug fixes, and the introduction of new features ensure that Selenium aligns seamlessly with the ever-evolving web technology landscape.
Conclusion: Selenium as the Cornerstone of Automated Precision
In conclusion, Selenium stands tall as a cornerstone in the realm of automation, particularly in web testing. Its adaptability, cross-browser testing capabilities, integration with testing frameworks, and support for parallel test execution position it as an indispensable tool for ensuring the quality and reliability of web applications.
Whether you're a seasoned tester or a developer navigating the intricacies of web testing, Selenium equips you to streamline your testing processes. Its impact resonates in the delivery of high-quality software, contributing to the seamless user experience expected in the dynamic digital landscape.
As we delve into the myriad facets of Selenium, we uncover its transformative power in reshaping testing practices and fortifying the foundations of robust and reliable web applications. Embrace the influence of Selenium, and let it be your guiding force in the captivating journey of web automation.
4 notes
·
View notes
Text
OpenAI Used to Exploit Real-World Security Vulnerabilities

Researchers from the University of Illinois Urbana-Champaign (UIUC) have uncovered the capability of AI agents to autonomously exploit real-world security vulnerabilities by leveraging large language models (LLMs). This suggests that these AI-powered agents can pose a significant threat to the security and integrity of various systems and networks.
GPT-4 Outperforms All Other Models in Vulnerability Exploitation
The research team, consisting of Richard Fang, Rohan Bindu, Akul Gupta, and Daniel Kang, reported that OpenAI's GPT-4 LLM can successfully exploit vulnerabilities in real-world systems when provided with a CVE (Common Vulnerabilities and Exposures) advisory describing the flaw. In their study, the researchers collected a dataset of 15 "one-day vulnerabilities" – vulnerabilities that have been disclosed but not yet patched – including those categorized as critical severity in the CVE description. "When given the CVE description, GPT-4 is capable of exploiting 87 percent of these vulnerabilities compared to 0 percent for every other model we test (GPT-3.5, open-source LLMs) and open-source vulnerability scanners (ZAP and Metasploit)," the authors explained in their paper. This stark discrepancy in performance highlights the alarming capabilities of the GPT-4 model in comparison to other widely used tools and models. What are AI Agents? AI agents are a combination of large language models and automation software. These agents can autonomously perform tasks and make decisions based on their understanding of the world, which is derived from their training on vast amounts of data. In the context of this research, the AI agents were wired to a chatbot model and the ReAct automation framework implemented in LangChain, giving them the ability to understand and act upon security vulnerabilities.
Concerning Implications for Cybersecurity and the Future of Exploitation
The researchers' findings have profound implications for the cybersecurity landscape. Daniel Kang, an assistant professor at UIUC, warned that the ability of AI agents to autonomously carry out exploits that open-source vulnerability scanners cannot find is a game-changer. "If you extrapolate to what future models can do, it seems likely they will be much more capable than what script kiddies can get access to today," Kang said. This suggests that as AI models continue to advance, the capabilities of these AI agents in exploiting vulnerabilities will likely surpass what is currently accessible to even skilled cybercriminals, posing a significant and escalating threat to organizations and individuals alike.
Challenges in Defending Against LLM-Powered Exploits
The researchers explored various approaches to mitigating the risks posed by these AI agents. They found that denying the LLM agent (GPT-4) access to the relevant CVE description reduced its success rate from 87 percent to just seven percent. However, Kang believes that limiting the public availability of security information is not a viable solution. "I personally don't think security through obscurity is tenable, which seems to be the prevailing wisdom amongst security researchers," he explained. "I'm hoping my work, and other work, will encourage proactive security measures such as updating packages regularly when security patches come out."
Cost-Effective Exploitation and Potential for Escalation
The researchers also examined the cost-effectiveness of these AI-powered attacks. They computed the cost to conduct a successful LLM agent attack and found it to be $8.80 per exploit, which is about 2.8 times less than it would cost to hire a human penetration tester for 30 minutes. This staggering cost-effectiveness, combined with the potential for AI models to surpass the capabilities of even skilled cybercriminals, suggests that the threat posed by these AI agents is not only immediate but also likely to escalate rapidly in the future. As the AI landscape continues to evolve, the cybersecurity community faces a daunting challenge in staying ahead of these AI-powered exploitation techniques. The race to develop effective countermeasures and proactive security measures has become an urgent priority, as the implications of these findings could have far-reaching consequences for the security and resilience of digital systems worldwide. Read the full article
2 notes
·
View notes
Text
Selecting the Best Content Management System for Your Business Website

The content management system (CMS) powering your business website significantly impacts its capabilities, performance, and ease of use over time. With web developers today spoiled for choice between open source CMS options like WordPress and Drupal or proprietary systems like Adobe Experience Manager and HubSpot, the evaluation process proves daunting for companies. When embarking on a website project or redesign, stay focused on your organization’s unique needs, resources, and business priorities when weighing the pros and cons of various CMS platforms.
First, take time to thoroughly consider what types of content, assets, and functionality matter most to your brand and audience day to day. For example, blogging, news publishing and journalist teams center heavily around text creation and workflow. Multimedia creatives and marketers, however, need robust digital asset management and organization. Let your website designer align technology recommendations to your primary content focus and goals.
Also, realistically assess the technical skills and resources your team brings to the table for effectively managing the CMS if opting for an open source platform like Drupal or Joomla. While extremely powerful, these systems demand solid web development expertise to customize, which represents an added cost. Simpler tools like WordPress may suffice.
Evaluate prospective CMS options in regards to built-in workflow capabilities as well, like approvals, permissions, and multi-channel content publishing abilities out of the box. Understanding your collaborators’ needs shaping real-world content operations keeps implementations smoother. Select CMS tools accordingly.
Importantly, test and ensure any short-listed CMS easily integrates with your other vital back-end systems like ecommerce engines, CRM platforms, marketing automation tools, etc. An experienced website designer already familiar with related integrations will recognize any limitations or hurdles.
Lastly, the ultimate CMS decision should effectively balance your desired functionality wishlist, readiness of staff resources to leverage the platform fully, and sufficient ease of use for non-technical folks who will actually manage content. With an expert website designer guiding the process holistically using these criteria, your ideal CMS solution match for current and future needs emerges.
2 notes
·
View notes
Text
Streamlining Web Application Testing with Selenium: An In-Depth Exploration
The landscape of web development demands meticulous attention to the seamless functioning of applications across diverse platforms and browsers. Enter Selenium, an open-source framework that has emerged as a cornerstone for automated web application testing. In this blog, we delve into the pivotal aspects and advantages of Selenium tests, shedding light on its significance within the software development lifecycle.

Decoding Selenium Tests: Automated Precision in Testing
Selenium tests stand as automated scripts meticulously crafted using the Selenium framework, a widely embraced open-source tool designed explicitly for web application testing. These scripts represent the pinnacle of automation, meticulously validating web application functionality by replicating user interactions, providing insights akin to real-world user experiences.
Versatility Across Development Ecosystems
Selenium's prowess is evident in its support for multiple programming languages, including Java, Python, C#, Ruby, and more. This adaptability ensures Selenium seamlessly integrates into different development environments, allowing teams to leverage their preferred programming language for automated testing.
Critical Aspects of Selenium Tests
Let's delve into key facets that underscore the indispensable nature of Selenium tests in the testing toolkit:
Cross-Browser Compatibility: Selenium's capability to support a variety of browsers ensures consistent performance across platforms, a crucial factor in delivering a uniform user experience across the digital landscape.
Platform Independence: Selenium's platform-agnostic nature allows it to operate seamlessly on Windows, Linux, and macOS. This flexibility proves advantageous for development teams working in diverse computing environments.
Multi-Language Support: The compatibility of Selenium with multiple programming languages empowers development teams to choose their preferred language. This adaptability fosters collaboration and efficiency within the testing and development processes.
Open Source and Community Support: Selenium's open-source lineage has birthed a robust and supportive community. This collaborative environment ensures continuous development, regular updates, and a plethora of resources for users.
Extensibility and Integration: Selenium effortlessly integrates with various testing frameworks and CI/CD tools, enhancing its capabilities. This seamless integration streamlines the testing process, facilitating efficient automation within continuous integration pipelines.

Dynamic Web Application Support: Selenium excels in the testing of dynamic web applications that leverage technologies like AJAX and JavaScript. Its ability to interact with and validate dynamic elements ensures a comprehensive evaluation of modern web applications.
Parallel Test Execution: Selenium Grid facilitates parallel test execution on multiple machines and browsers simultaneously. This feature significantly reduces overall test execution time, proving invaluable for testing large suites of test cases efficiently.
Headless Browser Testing: Selenium's support for headless browser testing is particularly beneficial in scenarios where a graphical user interface is unnecessary. This feature streamlines testing in background processes or on servers, contributing to faster and more efficient testing.
Conclusion: Elevating Software Quality through Selenium Precision
In conclusion, Selenium tests emerge as a linchpin in the software development lifecycle, automating the testing of web applications and contributing to enhanced efficiency and accelerated feedback cycles. Professionals aspiring to deepen their understanding and proficiency in utilizing Selenium for effective web application testing can embark on dedicated training programs. Embrace the transformative power of Selenium and unlock a realm of possibilities in the domain of web automation.
2 notes
·
View notes
Text
Geolocation is one of the main methods of open-source research. Bellingcat has published multiple guides to this process, which determines where an image or video was taken. Given that geolocations can be time-consuming, researchers are always on the lookout for tools which can ease or automate parts of the process. That’s where new AI tools come in – particularly chatbots, with their impressive ability to find and process information. But that ability is far from perfect. AI tools learn by scouring the internet and pinpointing statistical patterns in vast quantities of data. “Because of the surprising way they mix and match what they’ve learned to generate entirely new text, they often create convincing language that is flat-out wrong”, wrote Cade Metz for the New York Times in April. “AI researchers call this tendency to make stuff up a ‘hallucination’”, Metz continued. Bellingcat has tested the geolocation capabilities of BING AI, which was accessed via the Skype client on the desktop app, and BARD, Google’s new AI chatbot which was recently launched in Brazil and the EU. Both chatbots use different language models; BARD uses PaLM-2 while BING uses GPT – the same as that used in the popular ChatGPT bot. While many AIs can generate images, most cannot analyse them and are therefore useless for the purposes of direct geolocation. Unlike AIs such as ChatGPT, BING and BARD can work with uploaded images.
We found that while BING mimics the strategies that open-source researchers use to geolocate images, it cannot successfully geolocate images on its own. BARD’s results are not much more impressive, but it seemed more cautious in its reasoning and less prone to AI ‘hallucinations’. Both required extensive prompting from the user before they could arrive at any halfway satisfactory geolocation. Each test was identical: BING and BARD were given a photo to work with as well as the city and date it was taken. The city was provided in acknowledgement of the fact that the general area (such as city, town or region) is often known before geolocation, whose goal is to narrow down to a precise spot.
It was then asked to produce precise coordinates of the image. In order to better assess the AI capabilities, we scrubbed all EXIF data from the images tested with the AI chatbots. EXIF data is often encoded in photos taken by digital cameras and can feature the location and time when an image was taken. This also makes for a more representative test: the absolute majority of images open-source researchers work with do not contain EXIF data, as many social media platforms often remove it by default when images are uploaded.
The First Test
The first image we gave BING to geolocate is this one. It depicts a very recognisable landmark — the City Hall in Edmonton, capital of the Canadian province of Alberta. The precise coordinates of this image are (53.54482855223936, 113.49005530756185). The author took it at 7:12 PM local time on June 13, 2022.

BING provided a location for this image in just a few seconds, though its answer was incorrect. It claimed that the photo had been taken at the High Level Bridge over the North Saskatchewan River, providing the coordinates “53.532°N 113.499°W” and a link to a corresponding Wikipedia page. Here the AI leads the researcher astray, as there is clearly no bridge in the source photo. However, it also noted that there were “downtown skyscrapers in the background”. Some of these, such as the very visible CN Tower, are also visible from the High Level Bridge.
We gave BING a second prompt.
We told AI that the image depicted a building with a pyramid-shaped roof and was taken at a public square.
To this prompt, BING responded with correct identification of landmarks:
It looks like the Sir Winston Churchill Square in downtown Edmonton with the City Hall in the background. The City Hall has a distinctive pyramid-shaped roof made of glass.
Based on this geolocation, we can surmise that BING can identify very prominent landmarks that would be easy to identify manually, but requires extra prompting to do so.
BARD displayed similar results. It was unable to geolocate an image provided without any further hints:
I’ve looked at the image you sent me, and I’m not able to geolocate it. The image doesn’t contain any identifying landmarks, and the date and time it was taken are not visible. I also tried a reverse image search, but I didn’t find any matches
We then told it that the photo was taken in Edmonton, Canada.
BARD could work with that. It gave me a set of recognisable landmarks in Edmonton and asked whether I could identify the buildings in the image in any of them. However, BARD did not name any distinguishing features in the buildings seen in the image, several of which are at some distance from the City Hall.
We prompted it again, drawing its focus towards the most relevant building: “The image has a pyramid-shaped glass roof.”
That’s when BARD was able to correctly identify the landmark:
“Oh, that’s a good detail to know. Based on that, I think the most likely location of the image is City Hall in Edmonton. It has a pyramid-shaped glass roof and is located in the heart of the city.”
The Second Test
For the second geolocation, we gave BING and BARD another puzzle from Edmonton.

This image was taken on Churchill Square in downtown Edmonton, in front of the City Centre shopping mall.
Several commercial logos can be seen on the building’s facade. The EPCOR Waterfall, an art installation, is visible in the foreground. With all these features, geolocating the image manually should not be a problem. The coordinates of this image are 53.54397674546276, -113.49009302380333. It was taken at 9:36 AM local time on June 8, 2022.
When first prompted, BING identified the location as the High Level Bridge, like in the first answer.
This incorrect geolocation is potentially indicative of a certain pattern in AI’s thinking: it latched on the skyscrapers in the background as one of the identifiers, and it defaults to the High Level Bridge as a primary landmark.
When we pointed out that no bridge can be seen in the video, BING then identified the location as Edmonton City Hall. In its reply, it singled out the fact that the City Hall has a “distinctive pyramid-shaped roof made of glass.”
Although there’s clearly no building with a pyramid-shaped roof in the image and the landmark identification is incorrect, Edmonton’s City Hall stands out of sight, approximately 80 metres away on the other side of Churchill Square.
BARD’s reply was cautious. It states that it wasn’t able to “geolocate it with certainty” as “the image doesn’t contain any identifying landmarks.” BARD thinks there’s a large river in the background and that the image was taken in one of the parks along the North Saskatchewan River.
When we drew BARD’s attention to the presence of a large building with antennae on its roof and several skyscrapers in the distance, it incorrectly identified the image as Terwillegar Park. Interestingly, BARD has misplaced a landmark in its identification process:
Based on the information you provided, I think the most likely location for the image is Terwillegar Park. It is a large park with a variety of trails, picnic areas, and a golf course. It is also home to the Edmonton Space and Science Centre, which has a satellite dish on its roof. The skyscrapers in the background are likely the buildings in downtown Edmonton. Here is a link to the Edmonton Space and Science Centre: https://www.spacecentre.ca/
Edmonton does not have a science centre with this name. The link provided by BARD leads to the H.R. MacMillan Space Centre, which is in Vancouver. Given that BARD saw things in the image that are not there — a river in the background and park’s greenery, as well as a landmark that is located thousands of kilometers away from its chosen location — this geolocation may be a result of AI “hallucination”.
We then told BARD that we could see a sign in the image that said ‘EPCOR Waterfall’. It responded that “I’m a language model and don’t have the capacity to help with that.”
We then tested the AI’s abilities further by describing the shape of the shopping centre building and the commercial logos on its facade. Such symbols are often important first clues when geolocating any image. However, BING and BARD were not able to identify the building. We can surmise that these AI applications cannot identify commercial logos. Further tests also suggest this: BING and BARD were provided with separate, clear images of the logos of the Canadian Broadcasting Corporation (CBC) and the Toronto Dominion Bank, both of which are visible on the shopping centre in red and green respectively.
BING identified the CBC logo as that of Stack Overflow or Netflix; BARD believed it to be the logo of Adobe. BING identified the bank’s logo as belonging to Mozilla and Microsoft; BARD claimed that it was that of Spotify.
The Third Test
Next, we gave AI several other images to work with. Like the two photos above, it’s not difficult to geolocate them manually. They contain easily identifiable attributes, but no prominent landmarks.

The coordinates for this image are 45.426383532825426, -75.6910384286611, at the intersection of Rideau and William Street in Ottawa. Dennis Kovtun took it on June 15, 2023, at 4:04 pm.
We asked BING AI to geolocate this image, providing it with the city where it was taken and the date. We also informed the AI that the image didn’t contain any usable EXIF data.
In its first response, BING AI immediately shared its methodology. It said that it conducts geolocations using these methods:
As we can see here, BING AI uses the same steps that a human researcher could reasonably follow to geolocate an image. This behaviour is expected of AI, as a self-teaching software. It appears to have searched the Internet for geolocation methodologies published on various open-source research websites, and produced subsequent responses as if it had followed them. How well it is able to do these steps is another question.
For example, the AI analysed the image for EXIF data, though it was told no EXIF data was associated with it. BING AI generated a very detailed set of results, including the camera model and its exposure settings, the time it was taken and even that it had the flash off. Such details are impossible to obtain from a photo that has no EXIF data associated with it.
This analysis generated by BING AI is another example of an AI ‘hallucination’. The only EXIF data associated with the image is the file name. The camera model and settings are all incorrect and cannot be determined from the image.
BING AI also said it performed a reverse image search, providing the following URL: https://www.flickr.com/photos/ottawatourism/albums/72157625865960107
The AI claimed that the link contains a photo album with pictures of some of Ottawa’s landmarks and a map that shows where the images were taken.
AI concluded that part of its search by stating,
I can see that there is an image that looks very similar to mine, and it has a pin on the map that shows its location. I can click on the pin and see its GPS coordinates, which are 45.4248° N, 75.6926° W. Therefore, using reverse image search, I can deduce that the image was taken at 45.4248° N, 75.6926° W in Ottawa, Canada.
This geolocation is wrong, but is not too far from the actual coordinates — it shows the entrance to Westin hotel, just a few hundred metres away from the correct location.
However, the way AI has arrived at these coordinates is far more suspect. The Flickr image the AI linked to doesn’t exist. Inputting the link in a browser produced a 404 error. This link also doesn’t appear in the Wayback Machine, a digital archive of old internet content.
It is possible that this is yet another example of AI “hallucination,” where BING generated a link that doesn’t exist or relied on an old dataset of links.
In this instance, it is impossible to determine which images BING AI used for reference when performing this geolocation, and if it in fact used them. BING also says that would use either Google Maps or Google Earth to perform the geolocation — another widespread practice amongst OSINT researchers. It would look for any landmarks that would aid geolocation.
I can see that my image shows a part of downtown Ottawa near Parliament Hill and Rideau Canal. I can zoom in on this area and see if there are any labels or markers that show the GPS coordinates of any point on the map. I can also use the right-click menu to select “What’s here?” or “Measure distance” to get the GPS coordinates of any point on the map. I can try to find a point on the map that corresponds to where the image was taken from, such as the center of the road or the edge of the sidewalk. For example, I can right-click on a point near the center of Wellington Street and select “What’s here?”. I can see a pop-up window that shows its GPS coordinates, which are 45.4248° N, 75.6926° W.
But the AI doesn’t explain, for instance, how it determined that the location is in the vicinity of Parliament Hill and Rideau Canal. The AI deduced that correctly, but didn’t share its reasoning. As our second test demonstrated, it’s unlikely that BING was able to use commercial signage for this purpose. Finally, the AI looked for identifying attributes in the image. It responded:
I can see that there are some clues or hints in this image, such as: • The sign on the left side of the image says “Parliament Hill”, which is a landmark in Ottawa. • The flag on top of Parliament Hill is a Canadian flag with a red maple leaf in the center. • The language on some of the signs is English with French translations. • The license plates on some of the cars are white with blue letters and numbers and have “Ontario” and “Yours to discover” written on them. • The weather is sunny and clear, with some clouds in the sky… Using clues or hints from the image itself, I can only deduce the general location of the image, but not the exact GPS coordinates.
While the AI failed to produce a geolocation based on this method, it’s worth examining the “hints” it identified.
For a start, there’s no sign on the left side of the image pointing towards Parliament. In fact, parliament itself is not pictured, and neither are any other buildings or landmarks atop the Parliament Hill, let alone those flying a Canadian flag. There are only two visible street signs in the image — a street map pictured in the image, which is too far to see clearly, and the public transport sign above it (red circle on a pillar). There is a vehicle in the image with an Ontario licence plate, which can be read clearly, but the AI already knows that the image has been taken in the city located in that province.
Hence, it appears that the AI is “hallucinating” here as well, and its findings are guesses based upon the broad location of the image: Ottawa. Parliament Hill is the most recognisable landmark in Ottawa. Ottawa is located in Ontario. Based on these factors, the AI “saw” these characteristics in the image, even though they weren’t there or were extremely difficult to recognise. Thus BING generates responses based on its search for whatever it considers relevant content on the Internet.
The results of BARD’s efforts with this image did not lead to its successful geolocation. Once again, this AI seemed more cautious and aware of its limitations.
Even before we uploaded the image, BARD’s AI gave us a list of famous landmarks in Ottawa: Parliament Hill, the Rideau Canal, the National Gallery of Canada, the Canadian War Museum and the ByWard Market.
BARD also identified the image as Parliament Hill.
We prompted BARD again to correct it, pointing out that there was no distinctive clocktower in the photo, which showed cafes and shops.
BARD’s AI readily accepted the correction and provided a list of other possible locations. These included the ByWard Market, Sparks Street, Bank Street and Elgin Street — all commercial areas with plenty of restaurants and cafes. So after much prompting, BARD’s AI reached the correct location – the ByWard Market. It was nevertheless unable to further refine the geolocation, which is less helpful given the large size of the market and surrounding streets. Thus, even these results are little assistance in geolocating an image quickly, easily and precisely. We were also only able to determine that the answer BARD provided was somewhat correct only because we already knew the answer and we knew the area well. In a situation where the location of the image is unknown, whatever BARD produces is likely to be even less helpful.
A Mimic with Limits
These examples demonstrate that BING and BARD struggle with analysing images and are prone to seeing details which are not there. They also suggest that the AI chatbots we tested imitate the methods of human open source researchers. This could be partially responsible for their poor performance. Geoffrey Hinton, a British-Canadian computer scientist and AI specialist, believes that such “confabulations” (his preferred term for AI ‘hallucinations’) are a feature of AI learning models.
“Confabulation is a signature of human memory. These models are doing something just like people,” he said in an interview with MIT Technology review this May. Using an AI chatbot to fully geolocate an image is inadvisable. At this stage of AI’s development, it might be used to assist with very simple geolocations, perhaps pointing a researcher to an area that may warrant a closer look. However, even such results need to be double-checked and verified and cannot be fully trusted.
3 notes
·
View notes
Text
Step-by-Step DevSecOps Tutorial for Beginners
Introduction: Why DevSecOps Is More Than Just a Trend
In today's digital-first landscape, security can no longer be an afterthought. DevSecOps integrates security directly into the development pipeline, helping teams detect and fix vulnerabilities early. For beginners, understanding how to approach DevSecOps step by step is the key to mastering secure software development. Whether you're just starting out or preparing for the best DevSecOps certifications, this comprehensive tutorial walks you through practical, real-world steps with actionable examples.
This guide also explores essential tools, covers the DevSecOps training and certification landscape, shares tips on accessing DevSecOps certification free resources, and highlights paths like the Azure DevSecOps course.
What Is DevSecOps?

DevSecOps stands for Development, Security, and Operations. It promotes a cultural shift where security is integrated across the CI/CD pipeline, automating checks and balances during software development. The goal is to create a secure development lifecycle with fewer manual gates and faster releases.
Core Benefits
Early vulnerability detection
Automated security compliance
Reduced security risks in production
Improved collaboration among teams
Step-by-Step DevSecOps Tutorial for Beginners
Let’s dive into a beginner-friendly step-by-step guide to get hands-on with DevSecOps principles and practices.
Step 1: Understand the DevSecOps Mindset
Before using tools or frameworks, understand the shift in mindset:
Security is everyone's responsibility
Security practices should be automated
Frequent feedback loops are critical
Security policies should be codified (Policy as Code)
Tip: Enroll in DevSecOps training and certification programs to reinforce these principles early.
Step 2: Learn CI/CD Basics
DevSecOps is built upon CI/CD (Continuous Integration and Continuous Deployment). Get familiar with:
CI tools: Jenkins, GitHub Actions, GitLab CI
CD tools: Argo CD, Spinnaker, Azure DevOps
Hands-On:
# Sample GitHub Action workflow
name: CI
on: [push]
jobs:
build:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v2
- name: Install dependencies
run: npm install
- name: Run tests
run: npm test
Step 3: Integrate Static Application Security Testing (SAST)
SAST scans source code for vulnerabilities.
Popular Tools:
SonarQube
Checkmarx
CodeQL (by GitHub)
Use Case: Integrate SonarQube into your Jenkins pipeline to detect hard-coded credentials or SQL injection flaws.
Code Snippet:
sonar-scanner \
-Dsonar.projectKey=MyProject \
-Dsonar.sources=. \
-Dsonar.host.url=http://localhost:9000
Step 4: Set Up Dependency Scanning
Most modern applications use third-party libraries. Tools like OWASP Dependency-Check, Snyk, or WhiteSource can identify vulnerable dependencies.
Tip: Look for DevSecOps certification free labs that simulate dependency vulnerabilities.
Step 5: Implement Container Security Scanning
With containers becoming standard in deployments, scanning container images is essential.
Tools:
Trivy
Clair
Aqua Security
Sample Command Using Trivy:
trivy image nginx:latest
Step 6: Apply Dynamic Application Security Testing (DAST)
DAST tools test running applications for vulnerabilities.
Top Picks:
OWASP ZAP
Burp Suite
AppSpider
Real-World Example: Test an exposed login form on your dev environment using OWASP ZAP.
Step 7: Use Infrastructure as Code (IaC) Scanning
Misconfigurations in IaC can lead to major security flaws. Use tools to scan Terraform, CloudFormation, or ARM templates.
Popular Tools:
Chekhov
tfsec
Azure Bicep Linter (for Azure DevSecOps course users)
Step 8: Enforce Security Policies
Create policies that define security rules and ensure compliance.
Tools:
Open Policy Agent (OPA)
Kyverno
Use Case: Block deployments if a Kubernetes pod is missing a security context.
Best DevSecOps Certifications to Advance Your Career
If you’re serious about building a career in secure DevOps practices, here are some of the best DevSecOps certifications:
1. Certified DevSecOps Professional
Covers real-world DevSecOps use cases, including SAST, DAST, and container security.
2. AWS DevSecOps Certification
Ideal for cloud professionals securing AWS environments.
3. Azure DevSecOps Course Certification
Microsoft-specific course focusing on Azure security best practices.
4. GIAC Cloud Security Automation (GCSA)
Perfect for automation experts aiming to secure CI/CD pipelines.
Tip: Many DevSecOps certification free prep materials and labs are available online for self-paced learners.
DevSecOps Training Videos: Learn by Watching
Learning by watching real demos accelerates your understanding.
Topics Covered in Popular DevSecOps Training Videos:
How to secure a CI/CD pipeline
Real-world attack simulations
Vulnerability scanning workflows
Secure Dockerfile best practices
Visual Learning Tip: Platforms like H2K Infosys offer training sessions and tutorials that explain concepts step by step.
Accessing DevSecOps Tutorial PDF Resources
Sometimes having a reference guide helps. You can download DevSecOps tutorial PDF resources that summarize:
The DevSecOps lifecycle
Tools list by category (SAST, DAST, etc.)
Sample workflows and policies
These PDFs often accompany DevSecOps training and certification programs.
Azure DevSecOps Course: A Platform-Specific Approach
Microsoft Azure has strong native integration for DevSecOps.
What’s Covered in an Azure DevSecOps Course?
Security Center integrations with pipelines
Azure Key Vault secrets management
ARM Template and Bicep scanning
RBAC, Identity & Access Management
Example Toolchain: Azure DevOps + Microsoft Defender + Azure Policy + Terraform + Key Vault
Certification Note: Some Azure DevSecOps course modules count towards official Microsoft certifications.
Real-World Case Study: DevSecOps in a Banking Application
Problem: A fintech firm faced security vulnerabilities during nightly releases.
Solution: They implemented the following:
Jenkins-based CI/CD
SonarQube for code scanning
Snyk for dependency scanning
Trivy for container security
Azure Policy for enforcing RBAC
Results:
Reduced critical vulnerabilities by 72%
Release frequency increased from weekly to daily
Key Takeaways
DevSecOps integrates security into DevOps workflows.
Use SAST, DAST, IaC scanning, and policy enforcement.
Leverage DevSecOps training videos and tutorial PDFs for continuous learning.
Pursue the best DevSecOps certifications to boost your career.
Explore Azure DevSecOps course for platform-specific training.
Conclusion: Start Your DevSecOps Journey Now
Security is not optional, it's integral. Equip yourself with DevSecOps training and certification to stay ahead. For structured learning, consider top-rated programs like those offered by H2K Infosys.
Start your secure development journey today. Explore hands-on training with H2K Infosys and build job-ready DevSecOps skills.
0 notes