#wcss
Explore tagged Tumblr posts
Text
in Shooting Stars I will make it so that your character may be able to seduce a fox during patrol ONLY if it understands and perhaps speak cat on the rare chance you may achieve
#Warrior cats#warrior cats shooting stars#Wcss#You are actually free to do whatever you want during patrol…
7 notes
·
View notes
Text
New Chapter!
Chapter 10 of When the Canary Stops Singing out now!
Morti and the gang make a symbol, do some crime, and learn about the central finite curve
3 notes
·
View notes
Text
Thank you, @caffeine-bee for the tag! I had some trouble trying to search at first because I only put my entire WIP in one document recently. This was super fun! I was surprised by how little I used some of these words. All of this is from When the Canary Stops Singing
Word: Gold
They were surrounded by a humongous glass dome that must have served to hold in the pressure and air in lieu of a big enough gravitational pull to maintain an atmosphere. Everything was plated in gold.
Word: Warm
“Geez, I really wish I’d thought to dress us for colder weather.” “Wouldn’t we be in the same situation if we ended up somewhere tropical then?” Morti asked. “I was thinking layers, so we could just take shit off if we ended up somewhere warm.”
Word: Smile
"This is what happens when one of my soldiers double-crosses me.” The smile that she’d been holding back the whole time finally shines through, and it’s her eyes that are cold as she says "Don't let it happen again."
Word: Bubble
"No, I just was going to sit here to eat. I didn't mean to make you uncomfortable." "Right, of course, sir. You're welcome to sit here, sir." "Yeah," Chauncey said. The conversation in the rest of the hall slowly started back up, but the bubble of silence around him was almost physical. He ate in his quarters after that.
Word: Cold
He met her eye and shook his head. “I don’t think there’s a way out of this,” he said. His voice was icy cold in a way none of them had ever heard before.
(I think it’s funny that the word cold shows up in three of these excerpts but I had such a hard time finding anything decent for warm) Tagging @forsakenbard and whoever else wants to join! (sorry I don’t know who wants to be tagged in these sorts of things) Your words are: quiet, snow, clash, water, and quick
1 note
·
View note
Text
There’s a hole in the NCA mat? I think I’ve seen this film before
#throwback to worlds 2019 when a wcss athlete yelled THERES A HOLE!!!! LMFKFK#kristen watches allstar cheer
0 notes
Text
ok yea i spoke to soon, what was in the air yesterday cause thats 2/4 LAG teams having falls
0 notes
Text
K-Means Cluster
I used the Nesarc data to see the relationship of the predictor variables with the target variable which is nicotine dependent symptoms.
My cluster variables are :
S1Q1C : HISPANIC OR LATINO ORIGIN
S1Q1D5 : WHITE
S1Q1D3 : BLACK OR AFRICAN AMERICAN
S1Q1D2 : ASIAN
Age : Age of respondent
S2AQ1 : DRANK AT LEAST 1 ALCOHOLIC DRINK IN LIFE
S3BQ1A6 : EVER USED COCAINE OR CRACK
S3BQ1A8 : EVER USED INHALANTS
MAJORDEPLIFE : MAJOR DEPRESSION
DYSLIFE : DYSTHYMIA
GENAXLIFE : GENERALIZED ANXIETY DISORDER
S2DQ1 : BLOOD/NATURAL FATHER EVER AN ALCOHOLIC OR PROBLEM DRINKER
S2DQ2 : BLOOD/NATURAL MOTHER EVER AN ALCOHOLIC OR PROBLEM DRINKER

This is the data that I get when I use the describe function to describe the data.

I used the elbow Method to determine the optimal number of clusters (k) for k-means clustering.
The WCSS decreases as the number of clusters increases, which is expected because adding more clusters reduces the average distance within each cluster.The curve becomes less steep after k = 4 or k = 5, indicating that adding more clusters does not significantly improve compactness. Based on this graph, k = 5 might be the optimal number of clusters, as the slope becomes much less steep after that.Choosing k = 5 would balance model complexity (fewer clusters) with the compactness of the data points in each cluster.
Hence, for the canonical variable plotting, I used 5 variables.

Based on the plotting above, each clusters are not overlapping and grouped within each other. Hence, there is no correlation among the variables but due to the distance between the datapoints within each clusters we can deduct that there is high variance in each clusters.

Above is the output I get when I cluster the variables means by cluster.
Each cluster has a unique pattern of variable means, which can be used to describe the characteristics of the group. For example:
Cluster 0: Above average in AGE, S2DQ1, and S3BQ1A6 but below average in DYSLIFE and MAJORDEPLIFE.
Cluster 4: Younger individuals with higher depressive life event scores (MAJORDEPLIFE) and slightly higher dysphoria life (DYSLIFE).

Above is the OLS Regression result.
R-squared: 0.013 indicates that only 1.3% of the variance in NDSymptoms is explained by the cluster variable. This is a very low value, suggesting the clusters are not strongly predictive of NDSymptoms.Adj. R-squared: 0.001 adjusts for the number of predictors in the model. This being close to zero reinforces the weak explanatory power of the model.F-statistic and Prob (F-statistic): The F-test assesses whether the overall model is significant. With a p-value of 0.355, the model is not statistically significant (i.e., the clusters do not explain much variation in NDSymptoms).
Intercept:
Coefficient: 3.9016 represents the mean value of NDSymptoms for the baseline cluster (cluster 0).
It is highly significant (p-value = 0.000).
Cluster Effects (relative to cluster 0):
C(cluster)[T.1]: The mean value of NDSymptoms in cluster 1 is 0.1692 lower than in cluster 0. However, this effect is not statistically significant (p = 0.534).
C(cluster)[T.2]: The mean value of NDSymptoms in cluster 2 is 0.1555 higher than in cluster 0, but this is also not statistically significant (p = 0.569).
C(cluster)[T.3]: The mean value of NDSymptoms in cluster 3 is 0.3246 higher than in cluster 0, but the effect is not significant (p = 0.217).
C(cluster)[T.4]: The mean value of NDSymptoms in cluster 4 is 0.2047 higher than in cluster 0, but this is not significant (p = 0.499)

The output is from a Tukey's HSD (Honestly Significant Difference) test, which is used to compare the means of multiple groups while controlling for the family-wise error rate (FWER). From this output, we can deduct that, all the reject values are False, meaning none of the group comparisons have statistically significant differences in their means. For all group comparisons, the 95% confidence intervals include 0, further confirming no statistically significant differences between the groups. All p-values are greater than 0.05, meaning none of the comparisons show evidence to reject the null hypothesis after adjusting for multiple comparisons.
0 notes
Text
PANTHERS IN FIRST! WCSS IN SECOND! GIRL I AM SAT!
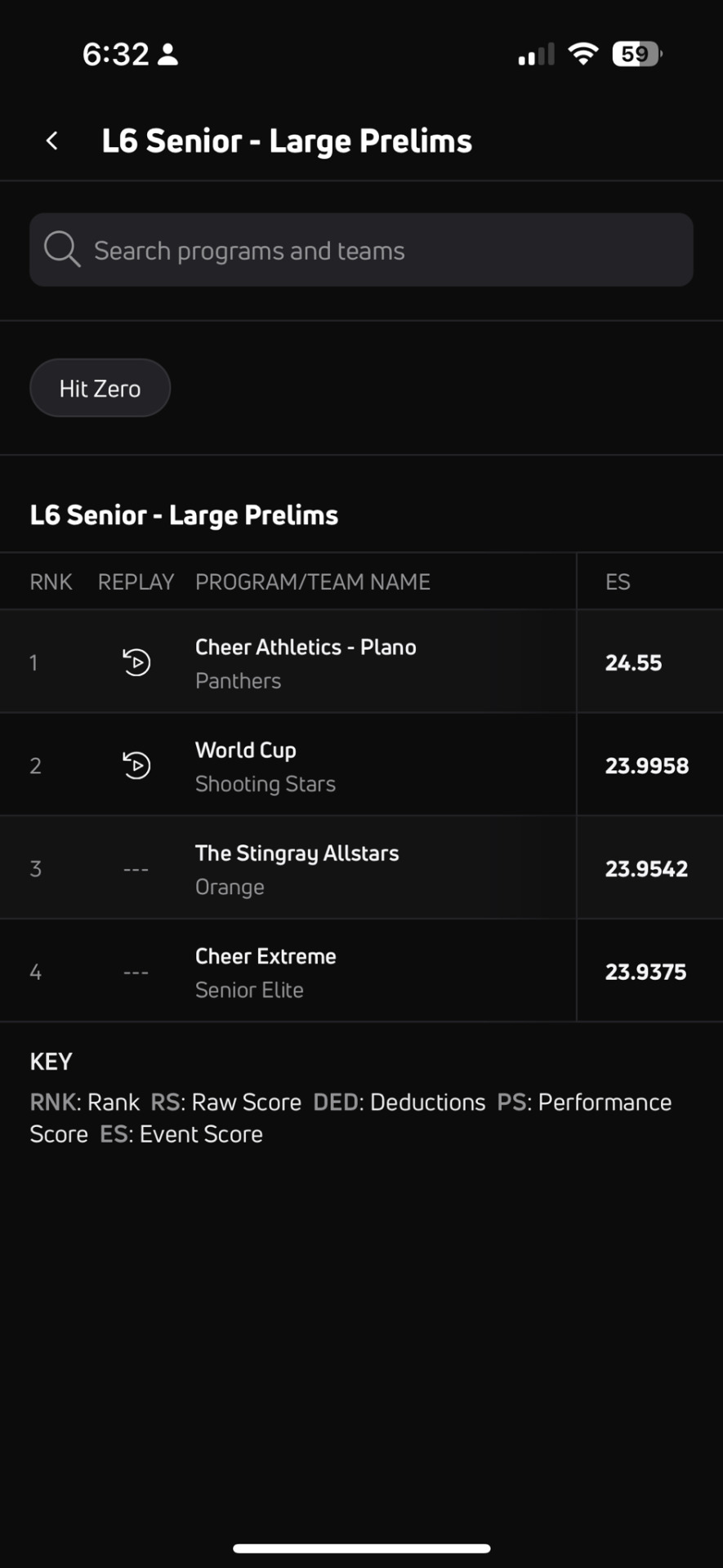
0 notes
Quote
セキュリティ会社プルーフポイントの研究者らは月曜日、数十の組織から機密データや金融資産を盗むことを目的とした進行中のキャンペーンにおいて、一部は上級幹部のものを含む数百のMicrosoft Azureアカウントが未知の攻撃者の標的になっていると発表した。 このキャンペーンは、資格情報フィッシングとアカウント乗っ取りの手法を統合した電子メールをアカウント所有者に送信することにより、対象の Azure 環境を侵害しようとします。 攻撃者は、個別のフィッシング詐欺と共有ドキュメントを組み合わせて攻撃を行っています。 一部のドキュメントには、クリックするとユーザーをフィッシング Web ページにリダイレクトするリンクが埋め込まれています。 標的となった役割の広範さは、影響を受ける組織全体にわたるさまざまなリソースと責任にアクセスできるアカウントを侵害するという脅威アクターの戦略を示しています。 「脅威アクターは、さまざまな組織にわたってさまざまな肩書きを持つ幅広い個人に焦点を当てているようで、世界中の何百人ものユーザーに影響を与えている」とプルーフポイントの勧告は述べて いる 。 「影響を受けるユーザー ベースは幅広い役職に及び、セールス ディレクター、アカウント マネージャー、財務マネージャーなどが頻繁にターゲットとなります。 「運営担当副社長」、「最高財務責任者兼財務責任者」、「社長兼最高経営責任者(CEO)」などの幹部職に就いている個人も標的に含まれていた。」 アカウントが侵害されると、脅威アクターはアカウントをさまざまな形式の多要素認証に登録することで保護します。 これにより、被害者がパスワードを変更したり、ダッシュボードにアクセスして最近のログインを調べたりすることが困難になる可能性があります。 場合によっては、使用される MFA は、テキスト メッセージまたは電話で送信されるワンタイム パスワードに依存します。 ただし、ほとんどの場合、攻撃者は通知とコードを備えた認証アプリを使用します。 拡大 / 侵害されたクラウド テナント内の攻撃者によって実行された MFA 操作イベントの例。 プルーフポイント Proofpoint は、次のような他の侵害後のアクションを観察しました。 データの引き出し。 攻撃者は、金融資産、内部セキュリティ プロトコル、ユーザー資格情報などの機密ファイルにアクセスしてダウンロードします。 内部および外部のフィッシング。 メールボックス アクセスは、影響を受ける組織内で横方向の移動を実施し、特定のユーザー アカウントをパーソナライズされたフィッシング脅威でターゲットにするために利用されます。 Financial fraud. In an effort to perpetrate financial fraud, internal email messages are dispatched to target Human Resources and Financial departments within affected organizations. Mailbox rules. Attackers create dedicated obfuscation rules intended to cover their tracks and erase all evidence of malicious activity from victims’ mailboxes. Advertisement Enlarge / Examples of obfuscation mailbox rules created by attackers following successful account takeover. Proofpoint The compromises are coming from several proxies that act as intermediaries between the attackers’ originating infrastructure and the accounts being targeted. The proxies help the attackers align the geographical location assigned to the connecting IP address with the region of the target. This helps to bypass various geofencing policies that restrict the number and location of IP addresses that can access the targeted system. The proxy services often change mid-campaign, a strategy that makes it harder for those defending against the attacks to block the IPs where the malicious activities originate. Other techniques designed to obfuscate the attackers' operational infrastructure include data hosting services and compromised domains. “Beyond the use of proxy services, we have seen attackers utilize certain local fixed-line ISPs, potentially exposing their geographical locations,” Monday’s post stated. “Notable among these non-proxy sources are the Russia-based 'Selena Telecom LLC', and Nigerian providers 'Airtel Networks Limited' and 'MTN Nigeria Communication Limited.' While Proofpoint has not currently attributed this campaign to any known threat actor, there is a possibility that Russian and Nigerian attackers may be involved, drawing parallels to previous cloud attacks.” How to check if you’re a target There are several telltale signs of targeting. The most helpful one is a specific user agent used during the access phase of the attack: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 Attackers predominantly utilize this user-agent to access the 'OfficeHome' sign-in application along with unauthorized access to additional native Microsoft365 apps, such as: Office365 Shell WCSS-Client (indicative of browser access to Office365 applications) Office 365 Exchange Online (indicative of post-compromise mailbox abuse, data exfiltration, and email threats proliferation) My Signins (used by attackers for MFA manipulation) My Apps My Profile Proofpoint included the following Indicators of compromise: Indicator Type Description Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 User Agent User Agent involved in attack’s access phase Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 User Agent User Agent involved in attack’s access and post-access phases Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36 User Agent User Agent involved in attack’s access and post-access phases sachacel[.]ru Domain Domain used for targeted phishing threats lobnya[.]com Domain Source domain used as malicious infrastructure makeapp[.]today Domain Source domain used as malicious infrastructure alexhost[.]com Domain Source domain used as malicious infrastructure mol[.]ru Domain Source domain used as malicious infrastructure smartape[.]net Domain Source domain used as malicious infrastructure airtel[.]com Domain Source domain used as malicious infrastructure mtnonline[.]com Domain Source domain used as malicious infrastructure acedatacenter[.]com Domain Source domain used as malicious infrastructure Sokolov Dmitry Nikolaevich ISP Source ISP used as malicious infrastructure Dom Tehniki Ltd ISP Source ISP used as malicious infrastructure Selena Telecom LLC ISP Source ISP used as malicious infrastructure As the campaign is ongoing, Proofpoint may update the indicators as more become available. The company advised companies to pay close attention to the user agent and source domains of incoming connections to employee accounts. Other helpful defenses are employing security defenses that look for signs of both initial account compromise and post-compromise activities, identifying initial vectors of compromise such as phishing, malware, or impersonation, and putting in place auto-remediation policies to drive out attackers quickly in the event they get in.
進行中のキャンペーンにより上級幹部の Azure アカウントが侵害され、MFA を使用してアカウントがロックされる | アルス テクニカ
0 notes
Photo



In between commissions, I’ve been working on a comic! The first ““issue/chapter” is already done, so I may as well start posting it here!
Here’s the first three pages of WE CAST STRANGE SHAPES: DRAGON TEETH!
—-
If you want to support me making more comics, consider supporting or subscribing to me on KoFi! https://ko-fi.com/studyofmonsters
#we cast strange shapes#wcss#wcss comic#eze xe deus#eze#lazaretti#my comics#MY OCs#dragon#mimic#fantasy comic#my webcomic
60 notes
·
View notes
Photo

Caked on mud from last year’s West Coast Subaru Show 😎 I’ve got a lot of cleanup to do 😅 #subaru #mudpit #westcoastsubarushow #wcss #offroad #subaruambassador https://www.instagram.com/p/BzgmTYIg3on/?igshid=rcvtoriztp5v
1 note
·
View note
Photo

Another day of WCSS, the last day in Coimbra. Chair of Sport Sociology Many thanks by the opportunity to lead these presentations. @antonio_figueiredo_ @hg_sarmento #wcss #coimbra #fcdef #uc #soccer #sociology #futebol #sociologia (em Convento São Francisco) https://www.instagram.com/p/Ce6XIAmD5wc/?igshid=NGJjMDIxMWI=
0 notes
Text
‼️UPDATES ON MY UPCOMING ROLL-TO-MOVE WARRIOR CATS GAME‼️
A name has been decided! Warrior Cats: Shooting Stars (WCSS)
In this game, you can either go solo or play as a group with one controlling the events as Starclan. These game modes are now titled “Star-Catching” and “Star-Gazing”
With it being a rolling based game, there isn’t any plan for a difficulty level. It’s all based on chance
-Completion goes as follows-
Gameplay rules and mechanics: 45%
Clan-building: 90%
Side clans: 40%
Character design log: 100%
Characters stats guide: 95%
Kit design log: 100%
Events: TBA
Medicine Cat Den: 85%
Warriors Den: 30%
Leaders and Deputies Den: 35%
Apprentices Den: TBA
Nursery: TBA
Elder’s Hollow: TBA
Overall completion: 63.5%
#Warrior cats shooting stars#WCSS#warrior cats#so excited to be sharing it soon! Maybe once I complete it more#do note this is not an online game on any platform!
15 notes
·
View notes
Photo

Ag súil go MÓR le múineadh ag Scoil Samhraidh Willie Clancy an tseachtain seo chugainn!!! Really looking forward to teaching at WCSS next wk! #wcss https://www.instagram.com/p/CQ1WigiJOU7/?utm_medium=tumblr
0 notes
Photo

World Cup Shooting Stars
13 notes
·
View notes
Text
CHILLS FROM THAT ROUTINE 😭
0 notes
Text
WCSS PAID TO WORLDS!! AND BABS WON!! YALL IM SO FUCKIN HAPPY
0 notes