#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti
Explore tagged Tumblr posts
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
Getting Started with Full-Stack Web Development: Obstacles and Opportunities
Embarking on the journey to becoming a full-stack web developer offers a blend of exhilarating challenges and rewarding accomplishments. In this guide, we'll explore the intricacies of mastering full-stack development, delving into the obstacles you may face along the way and the triumphs that await those who persevere.

Introduction
Mastering full-stack web development is akin to embarking on a thrilling adventure—one that promises countless opportunities for growth, innovation, and professional fulfillment. However, the road to proficiency is not without its hurdles. In this blog, we'll navigate through the challenges aspiring full-stack developers may encounter, as well as the triumphs that come with overcoming them.
1. Diverse Skill Set
Full-stack web development demands proficiency in a diverse range of skills, spanning from frontend technologies like HTML, CSS, and JavaScript to backend languages such as Python, Ruby, or Node.js. Additionally, expertise in databases, server management, and deployment processes is crucial. Acquiring mastery in these areas requires dedication, time, and a continuous commitment to learning and adaptation.
2. Ever-Evolving Landscape
The realm of web development is in a perpetual state of evolution, with new frameworks, libraries, and tools emerging at a rapid pace. Keeping pace with these advancements and constantly updating your skill set is imperative to remain competitive in the industry. Allocate time to explore emerging technologies, enroll in online courses, and engage with the developer community to stay ahead of the curve.
3. Complexity of Projects
Full-stack developers often tackle intricate projects that necessitate the integration of various technologies and components. Managing the intricacies of these projects, troubleshooting issues, and ensuring seamless interaction between frontend and backend systems can be daunting. Nonetheless, overcoming these challenges cultivates invaluable problem-solving skills and deepens your comprehension of web development principles.
4. In-Depth Understanding
To excel as a full-stack developer, a profound understanding of programming concepts, algorithms, and data structures is indispensable. Mastery of these foundational principles empowers you to write concise, efficient code and tackle complex technical challenges with confidence. Dedicate time to delve into computer science fundamentals and engage in coding exercises to fortify your expertise.
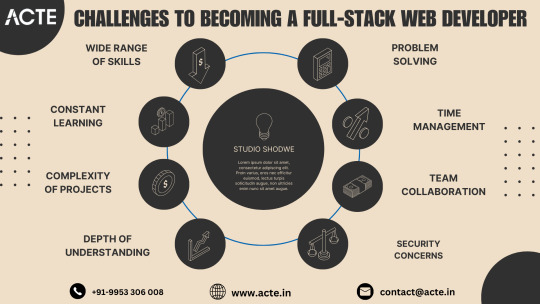
5. Effective Problem Solving
Effective problem-solving is a hallmark of successful full-stack developers. Debugging code, identifying bottlenecks, and optimizing performance demand astute analytical skills and a systematic approach. Collaborating with peers, leveraging online resources, and seeking mentorship can facilitate the navigation of complex technical hurdles and yield effective solutions.
6. Strategic Time Management
Balancing multiple responsibilities, including frontend and backend development, database management, and project deployment, necessitates adept time management skills. Prioritize tasks, establish realistic timelines, and leverage productivity tools to streamline your workflow and maximize productivity. Reserve time for ongoing learning and professional development to continually enhance your skill set.
7. Cultivating Team Collaboration
Full-stack developers often collaborate with interdisciplinary teams, comprising designers, frontend developers, backend developers, and other stakeholders. Effective communication, teamwork, and collaboration are vital for project success. Foster strong interpersonal relationships, actively contribute in team settings, and cultivate a culture of open communication and collaboration within your team.
8. Prioritizing Security
Understanding security best practices and implementing robust security measures is paramount in web development. Full-stack developers must remain vigilant in identifying and mitigating security vulnerabilities to safeguard sensitive data and uphold the integrity of web applications. Stay informed about prevalent security threats, adhere to industry best practices, and consistently update your knowledge to proactively address emerging risks.
Conclusion
Embarking on the journey to becoming a full-stack web developer is a thrilling endeavor marked by challenges and triumphs. By embracing the obstacles, refining your skills, and maintaining a steadfast commitment to learning and growth, you can unlock a realm of opportunities and embark on a gratifying career in web development. Remember, each challenge surmounted brings you closer to mastery, and the journey itself is as enriching as the destination.
#full stack developer#education#information#full stack web development#web development#front end development#full stack developer course#technology#backend
2 notes
·
View notes
Text
Top 10 Key Points to Ensure Security for Your Laravel Application

In Laravel web application development, security is one of the essential paramount. As the digital landscape continues to expand, the Importance of security in web applications, particularly those built on the Laravel framework, has reached an all-time high. In this era of interconnectedness, where information flows seamlessly across the virtual realm, the potential threats and vulnerabilities have also escalated.
The landscape of online threats has grown more sophisticated, encompassing various malicious activities ranging from data breaches to identity theft. This evolving threat landscape calls for a steadfast commitment to proactive security measures. Waiting for a security breach before addressing vulnerabilities is a risk no modern developer can afford to take.
The significance of bolstering security in Laravel web application development. While Laravel provides a robust and versatile platform for creating dynamic web applications, it's essential to recognize that even the most advanced framework is not immune to potential security breaches. As your Laravel application evolves, it becomes a showcase of your technological prowess and a potential target for cyber threats.
The Importance of proactive security measures should be highlighted further. Developers and businesses must adopt a security-first mindset when crafting their digital creations, which means staying informed about the latest security trends, continuously updating and patching the application, and adhering to best practices for safeguarding sensitive user data.
We'll delve into 10 critical checkpoints that can significantly enhance the security of your Laravel web application. These checkpoints encompass a comprehensive approach to securing various aspects of your application, from authentication and authorization to protecting against common web vulnerabilities. By diligently implementing these checkpoints, you'll be taking a substantial stride towards fortifying your Laravel web application against the ever-persistent threats lurking in the digital domain.
10 Key Checkpoints to Focus On
Here's your comprehensive Laravel Security Checklist to ensure a robust and safeguarded web application.
1. Secure Authentication and Authorization

In the intricate world of Laravel web application development, security is an indispensable pillar for creating a trustworthy and resilient digital presence. One of the cornerstone elements in this security fortress is the implementation of secure authentication and authorization mechanisms. Let's delve into how these critical aspects are pivotal in fortifying your Laravel application against potential threats.
Secure Authentication: Building the First Line of Defense
Authentication is verifying the identity of users attempting to access your application. It forms the cornerstone of security by ensuring that only authorized individuals can interact with sensitive data and functionalities. In the realm of Laravel, this process is made significantly more manageable through the framework's built-in authentication features.
Implementing secure authentication involves
Strong Password Policies: Enforce complex passwords, combining uppercase and lowercase letters, numbers, and special characters. Laravel provides password validation rules to help you accomplish this.
Two-Factor Authentication (2FA): Enhance security by requiring users to provide an additional authentication factor beyond their password. Laravel offers seamless integration with 2FA for an added layer of protection.
Account Lockouts: Implement mechanisms that lock accounts after a specified number of unsuccessful login attempts, preventing brute-force attacks by temporarily halting further login attempts.
Authorization: Ensuring Granular Access Control
Authorization, however, deals with controlling what authenticated users can do within the application. It's about granting permissions and access rights based on roles and responsibilities, ensuring that sensitive actions are restricted to those who need them.
Key steps in implementing effective authorization include
Role-Based Access Control (RBAC): Define roles such as "admin," "user," or "manager," and associate them with specific permissions. Laravel's RBAC system lets you assign roles and permissions effortlessly.
Middleware Authorization: Leverage Laravel's middleware to restrict access to routes or controllers based on user roles or custom conditions. This is a powerful way to ensure that only authorized users can perform specific actions.
Resource Controllers: Utilize resource controllers to create a consistent and structured approach to handling CRUD operations. These controllers can be easily configured to enforce authorization rules for specific actions.
Dynamic Authorization Policies: Laravel's policy system lets you define authorization logic in a structured manner. It's beneficial for complex access control requirements and allows for fine-grained control over what users can do.
In a world where digital threats are evolving rapidly, securing your Laravel application's authentication and authorization processes is paramount. By implementing robust authentication mechanisms and enforcing precise authorization rules, you're safeguarding sensitive data and building a foundation of trust with your users. Remember, security isn't just a one-time task; it's an ongoing commitment that requires vigilance and adaptability in the face of ever-changing cyber threats.
2. Keep Laravel and Dependencies Updated
In the dynamic realm of Laravel web application development, staying ahead in the security game is an ongoing endeavor. One of the fundamental practices that forms the bedrock of a secure digital presence is the consistent updating of your Laravel framework and its associated dependencies. Let's explore why this practice is essential and how it contributes to the overall security of your application.
The Power of Regular Updates
Technology, much like the world around us, is in a constant state of evolution. This evolution is driven not only by innovation but also by identifying and rectifying vulnerabilities and weaknesses. In the context of Laravel development, regular updates to both the core framework and its dependencies play a pivotal role in ensuring the security and stability of your application.
Why Updates Matter
Security Patches: Vulnerabilities can emerge at any software lifecycle stage. Developers and the open-source community work diligently to identify and address these vulnerabilities. Regular updates ensure that your Laravel application is fortified with the latest security patches, minimizing the risk of exploitation.
Compatibility: As Laravel evolves, updates often improve compatibility with newer PHP versions, web servers, and databases. Staying updated ensures your application remains in sync with the broader web development ecosystem.
Performance and Features: Updates not only fix issues; they also introduce performance enhancements and new features. Embracing these updates can lead to a more efficient application that delivers a better user experience.
Dependencies: Handle with Care
Laravel development heavily relies on various external packages and libraries. While these dependencies contribute to the efficiency and functionality of your application, they can also introduce vulnerabilities if not managed appropriately.
Best Practices for Dependency Management:
Regular Audits: Periodically review the dependencies your Laravel development company utilizes. Check for any vulnerabilities reported in these packages and prioritize updating them accordingly.
Automated Tools: Leverage automated tools that can scan your project's dependencies for known security issues. This can help you identify potential risks and take corrective action swiftly.
Version Pinning: Specify the exact versions of dependencies your application uses. This prevents unexpected updates that might introduce breaking changes or vulnerabilities.
In the rapidly evolving web application security landscape, treating updates as a proactive security measure is paramount. By ensuring your Laravel framework and dependencies are up to date, you're demonstrating a commitment to maintaining a robust digital fortress for your application. This safeguards sensitive user data and positions your Laravel development company as a conscientious custodian of digital security. Remember, in technology, staying current isn't just an option—it's necessary for a secure and successful future.
3. Validate User Input
The ever-evolving landscape of Laravel development, the adage "Garbage In, Garbage Out" holds immense relevance. One of the pivotal checkpoints in ensuring the robustness of your Laravel application's security is the validation of user input. Let's dive into why validating user input is crucial and how it is a formidable shield against potential vulnerabilities.
The Essence of User Input Validation
User input is the gateway through which your Laravel application interacts with its users. Whether it's a login form, a search bar, or a comment section, user input is integral to the functionality of your application. However, it can also become an entry point for malicious activities if left unchecked.
Why Validate User Input:
Mitigating Injection Attacks: Attackers can exploit unvalidated user input to inject malicious code into your application. This includes infamous threats like SQL injection and cross-site scripting (XSS). Proper validation drastically reduces the risk of such attacks.
Data Integrity: Validating user input ensures that the data flowing into your application is consistent and matches the expected format. This helps maintain data integrity and prevents errors caused by unexpected information.
Enhancing User Experience: You can guide users to input data in the correct format by providing real-time validation feedback. This not only prevents submission errors but also enhances the overall user experience.
Implementing Effective Input Validation in Laravel
Utilize Laravel's Validation Rules: Laravel offers a robust validation system that includes a wide array of predefined rules. These rules cover everything from required fields and email formats to custom validation logic.
Sanitize and Filter Input: Consider sanitizing and filtering user input alongside validation. Sanitization removes potentially harmful characters, while filtering ensures that information adheres to specific formats.
Client-Side Validation: While server-side validation is paramount, supplement it with client-side validation using JavaScript. This provides instant feedback to users and reduces unnecessary server requests.
Best Practices for User Input Validation
Never Trust User Input: Treat all incoming user input as potentially malicious until proven otherwise. Validate and sanitize input even if it seems harmless.
Whitelist Validation: Define an allowlist of allowed characters and formats for each input field. Reject input that doesn't conform to these predefined patterns.
Regular Updates: Like any other security practice, stay updated with Laravel's latest validation features and best practices. This ensures you're using the most effective tools available.
In the intricate realm of Laravel development, user input validation isn't just a technical practice; it's a shield that guards your application against many threats. By diligently validating user input, you're bolstering your application's security and reinforcing trust with your users. In the dynamic world of web development, where innovation meets vulnerability, validation is your steadfast ally in pursuing a secure and seamless user experience.
4. Protect Against SQL Injection

Shielding your digital fortress through meticulous Laravel development services involves a critical step: Protect against SQL injection. This threat arises when user inputs lack proper sanitation, potentially enabling malicious actors to manipulate SQL queries and gain unauthorized database access.
SQL injection attacks can lead to data exposure, alteration, or deletion. Laravel's defences are robust. Its query binding technique parameterizes user inputs, preventing malicious SQL execution. The Eloquent ORM further enhances security by abstracting SQL interactions and automatically escaping values.
Adhering to best practices is paramount. Prioritize parameterized queries over direct concatenation, sanitize inputs, and conduct regular code audits to ensure secure methods. By fortifying your Laravel application against SQL injection, you're erecting a robust barrier against a damaging vulnerability while providing your Laravel development services maintain the utmost integrity and user trust.
5. Cross-Site Scripting (XSS) Prevention
In securing your digital haven with proficient Laravel development practices, countering Cross-Site Scripting (XSS) emerges as a pivotal measure. XSS occurs when malicious code infiltrates a website through unfiltered user inputs, potentially compromising user data and integrity.
The gravity of XSS lies in its ability to expose sensitive information or perform malicious actions under the user's identity. Laravel offers potent tools to thwart such threats:
Blade Templating: Laravel's Blade templating engine automatically escapes variables, preventing unintended script execution.
XSS Middleware: Laravel provides built-in middleware for encoding user inputs, adding an extra layer of protection.
Content Security Policy (CSP): Implementing CSP headers in your Laravel application restricts the sources from which content can be loaded, reducing the risk of XSS attacks.
Adhering to these precautions is essential. Validate and sanitize inputs, embrace Laravel's security features, and implement a robust CSP. By guarding against XSS vulnerabilities, you ensure your Laravel development maintains a resilient and trustworthy digital presence.
6. Implement HTTPS and SSL
In web application development, particularly in Laravel, bolstering security is paramount. A crucial step in this pursuit is the implementation of HTTPS and SSL protocols. These measures are essential to safeguard sensitive data transmitted between users and your application.
HTTPS (Hypertext Transfer Protocol Secure) encrypts the data between users' browsers and your application's server, thwarting potential eavesdropping and tampering. SSL (Secure Sockets Layer) certificates are the foundation of this encryption, ensuring that communication remains confidential.
Advantages of HTTPS and SSL:
Data Encryption: HTTPS encrypts data during transit, preventing unauthorized access to sensitive information.
Trust and SEO: SSL certificates enhance user trust, as indicated by the padlock symbol in browsers. Search engines also favor HTTPS websites, improving SEO rankings.
Authentication: SSL certificates verify your application's authenticity, shielding users from potential phishing sites.
Implementing HTTPS and SSL involves obtaining a valid SSL certificate and configuring your Laravel application for secure connections. By adopting these measures, you're securing your web application development, fostering trust among users, and ensuring compliance with modern security standards.
7. Secure Session Management
In web application development, security isn't just a feature—it's a necessity. A crucial aspect of building a robust and trustworthy application is ensuring secure session management. Sessions are pivotal in maintaining user interactions and data, making their protection paramount.
Laravel offers robust mechanisms to fortify session management:
Session Encryption: Laravel automatically encrypts session data, preventing unauthorized access and ensuring confidentiality.
CSRF Protection: Cross-Site Request Forgery (CSRF) attacks can compromise sessions. Laravel's built-in CSRF protection safeguards against such threats.
Expire and Regenerate: Set session expiration times and periodically regenerate session IDs to minimize the window of vulnerability.
By implementing secure session management practices in your web application development, you create a shield against unauthorized access and data breaches. This preserves user trust and solidifies your commitment to crafting applications that prioritize security and integrity.
8. Protect Against Cross-Site Request Forgery (CSRF)
Safeguarding web applications is a top priority in Laravel development. To fortify your digital haven, countering Cross-Site Request Forgery (CSRF) threats is crucial. CSRF attacks manipulate authenticated users into executing malicious actions unknowingly. Laravel provides a robust defense:
CSRF Tokens: Laravel automatically generates unique tokens for each user session, validating the authenticity of requests.
Middleware Protection: Laravel's built-in CSRF middleware verifies tokens, preventing unauthorized requests from being executed.
By integrating these measures, you fortify your Laravel application against CSRF vulnerabilities. This secures user interactions and demonstrates your commitment to proactive security practices in modern web development.
9. Harden Configuration and File Permissions
In the landscape of Laravel security, enhancing configuration settings and file permissions is a critical stride. Securing sensitive files, such as configuration files, shields against unauthorized access and potential breaches. Laravel's framework offers key tactics:
Restricted Access: Limit access to sensitive configuration files by setting appropriate permissions. This prevents unauthorized users from tampering with vital settings.
Environment Configuration: Store sensitive data in environment files and never expose them in version control. Laravel's .env file shields sensitive variables from prying eyes.
By meticulously configuring permissions and safeguarding critical files, you erect a solid barrier against potential threats. This reflects an unwavering commitment to fortifying your Laravel application and upholding security standards in modern web development.
10. Use Content Security Policy (CSP)
Bolstering security in Laravel involves advanced tactics, including a Content Security Policy (CSP). CSP guards against cross-site scripting (XSS) and data injection attacks. It achieves this by specifying approved content sources, mitigating the risk of malicious script execution. Laravel's integration of CSP fortifies your defense:
Malicious Content Mitigation: CSP curtails the potential impact of XSS attacks by regulating the domains from which content can be loaded.
Policy Customization: Laravel empowers you to tailor CSP rules to suit your application's specific requirements, balancing security and functionality.
By embracing CSP, you establish a robust security framework that exemplifies Laravel's commitment to secure, modern web development practices.
Top Laravel Security Packages for Developers
In the realm of Laravel development, ensuring robust security is paramount. Several key packages aid developers in fortifying their applications. Here are three notable options:
Laravel-ACL: Access Control Lists (ACL) are fundamental to controlling user permissions. This package simplifies ACL implementation, offering granular control over user access to different parts of your application.
Laravel Security: As the name suggests, this package enhances overall security. It provides features like XSS protection, safe redirects, and content filtering, contributing to a fortified application.
Laravel Security Component: This package takes security up a notch by integrating robust security components. It includes encryption, hashing, validation, and more tools, streamlining your security efforts.
For a Laravel development agency, these packages are invaluable assets. By incorporating them into your development process, you expedite security implementation and establish a strong foundation for crafting secure, reliable applications that clients can trust.
Conclusion
In the intricate realm of Laravel security, these checkpoints act as sentinels, fortifying your application's defenses. Secure authentication, vigilant updates, meticulous validation, and shielded configurations create a robust bastion. Protection against threats like SQL injection, XSS, and CSRF forms an unbreachable wall. Implementation of HTTPS, secure session handling, and CSP reinforce your fortifications. Familiarity with essential security packages like Laravel-ACL, Laravel Security, and Security Component adds the final layer. As a Laravel developer, embracing these measures ensures your applications are secured, and your expertise is unwavering in the face of evolving threats.
Source: Top 10 Key Points to Ensure Security for Your Laravel Application
2 notes
·
View notes
Text
Navigating the Digital Frontier: Key Strategies and Emerging Trends in Software Development
Introduction
The digital landscape is in a constant state of flux, and software development stands at the epicenter of this evolution. For businesses and individuals alike, staying ahead of the curve requires a deep understanding of emerging trends and strategic approaches. In this post, we'll delve into the critical strategies that drive successful software development, explore the technologies shaping the future, and offer insights into how to leverage these advancements to achieve your business goals. Whether you're a startup looking to disrupt the market or an established enterprise seeking to modernize your infrastructure, this guide will provide a comprehensive overview of the key elements that define cutting-edge software development.

Foundational Strategies for Robust Software Development
Successful software projects aren't built on chance; they're the result of meticulous planning and execution. Here are some foundational strategies that drive robust software development:
Agile Methodologies: Embrace iterative development with Agile frameworks like Scrum or Kanban. These methodologies foster adaptability, collaboration, and continuous improvement, ensuring that projects remain aligned with evolving requirements.
DevOps Integration: Bridge the gap between development and operations with DevOps practices. Automate deployment pipelines, enhance collaboration, and accelerate time-to-market.
User-Centric Design: Prioritize the user experience (UX) and user interface (UI) from the outset. Conduct thorough user research, create intuitive interfaces, and gather feedback to ensure that your software meets the needs of your target audience.
Quality Assurance (QA) and Testing: Implement rigorous testing protocols throughout the development lifecycle. Automated testing, code reviews, and continuous integration play crucial roles in ensuring software reliability and performance.
Clear Communication and Collaboration: Foster open communication and collaboration among all stakeholders. Regular meetings, clear documentation, and transparent project management tools are essential for keeping everyone on the same page.
Emerging Trends Shaping the Future of Software Development
The software development landscape is constantly evolving, driven by technological advancements and changing market demands. Here are some key trends to watch:
Artificial Intelligence (AI) and Machine Learning (ML): AI and ML are revolutionizing software development by enabling intelligent automation, predictive analytics, and personalized user experiences. 1 Incorporating AI into your applications can provide a significant competitive advantage.
Cloud Computing: Cloud platforms like AWS, Azure, and Google Cloud offer scalable infrastructure, flexible deployment options, and a wide range of services. Leverage cloud computing to reduce costs, enhance agility, and improve scalability.
Low-Code/No-Code Development: These platforms empower non-technical users to build applications with minimal coding. This trend accelerates development cycles and democratizes software creation.
Cybersecurity: With the increasing prevalence of cyber threats, security is paramount. Implement robust security measures throughout the development lifecycle, including secure coding practices, vulnerability assessments, and penetration testing.
Internet of Things (IoT): IoT is expanding the reach of software development into new domains. Develop applications that connect and manage IoT devices, enabling automation, data collection, and real-time monitoring.
Progressive Web Apps (PWAs): PWAs offer the best of both web and native mobile experiences. They are fast, reliable, and installable, providing a seamless user experience across devices.
Leveraging These Trends for Business Growth
To truly capitalize on these trends, software development companies must adopt a proactive and strategic approach. Here are some actionable steps:
Invest in Continuous Learning: Encourage your team to stay up-to-date with the latest technologies and best practices. Provide opportunities for training, certifications, and knowledge sharing.
Build Strategic Partnerships: Collaborate with technology vendors, industry experts, and other software development companies to expand your capabilities and reach.
Focus on Innovation: Foster a culture of innovation within your organization. Encourage experimentation, research, and development of new solutions.
Provide Tailored Solutions: Understand your clients' unique needs and offer customized software solutions that address their specific challenges.
Showcase Success Stories: Highlight your past projects and client testimonials to demonstrate your expertise and build credibility.
Conclusion
The future of software development is bright and filled with opportunities for innovation and growth. By staying informed about emerging trends, adopting robust development strategies, and fostering a culture of continuous improvement, software development companies can navigate the digital frontier and deliver exceptional value to their clients. Embracing these key strategies will ensure that your business stays competitive and thrives in the ever-evolving tech landscape.
#website design#software development#mobile app development#e commerce website development#mobile app development services
0 notes
Text
Best Institute for SQL in Mohali: A Comprehensive Guide for Aspiring SQL Professionals
If you're looking to enhance your skills in SQL (Structured Query Language) and are based in or around Mohali, you've made a smart decision. SQL is an essential tool for managing and analyzing data in today's data-driven world. Choosing the right institute can set you up for a successful career in database management, data analytics, or even development. In this blog, we'll explore some of the best institutes for SQL in Mohali and what makes them stand out.
Why Learn SQL?
SQL is the backbone of database management systems like MySQL, Oracle, SQL Server, and PostgreSQL. It allows professionals to query, manipulate, and manage data efficiently. Whether you aim to become a data scientist, backend developer, or database administrator, proficiency in SQL is essential.
Key Factors to Consider When Choosing an SQL Institute
Before we delve into the top institutes, it's important to understand what you should look for in an SQL training program:
Curriculum: A well-rounded course should cover basics to advanced SQL techniques, including query optimization, joins, subqueries, data filtering, and more.
Experienced Instructors: Learn from industry experts with practical experience.
Hands-On Training: SQL is best learned by doing, so the institute should offer real-world scenarios, case studies, and projects.
Certifications: Verify if the institute offers certifications that are recognized by the industry.
Placement Support: Some institutes also provide job placement assistance, which is a big plus for fresh graduates and career changers.
Top SQL Training Institutes in Mohali
1. ThinkNEXT Technologies
Why Choose ThinkNEXT Technologies? ThinkNEXT Technologies is a renowned name in Mohali for IT and technical training. The institute offers comprehensive SQL courses designed for beginners as well as professionals looking to upgrade their skills.
Course Highlights:
Covers basic to advanced SQL concepts.
Hands-on training with real-time projects.
Certified trainers with industry experience.
Flexible timings for working professionals.
Certification & Placement: ThinkNEXT offers job-oriented training with a certificate recognized by top IT firms. Their placement support is robust, ensuring students get placed in reputed organizations.
2. Webtech Learning
Why Choose Webtech Learning? Webtech Learning is a prominent institute in Mohali offering various technical courses, including SQL. Their SQL training is well-structured, focusing on practical implementation, which is crucial for mastering this language.
Course Highlights:
Beginner-friendly SQL courses with real-time query sessions.
Interactive learning with live projects.
Both classroom and online training options.
Certification & Placement: Webtech Learning provides certification after course completion. They also offer placement assistance, which increases your chances of landing a good job in IT firms.
3. Excellence Technology
Why Choose Excellence Technology? Excellence Technology provides industry-oriented SQL training in Mohali. Known for its practical approach, this institute ensures that students are well-equipped to handle real-world database challenges.
Course Highlights:
In-depth SQL and database management training.
Experienced faculty with vast industry exposure.
Live project work and practical assignments.
Certification & Placement: A certificate from Excellence Technology adds weight to your resume. Their placement cell is highly supportive, making it easier for students to secure jobs in leading companies.
4. CIIM (Chandigarh Institute of Internet Marketing)
Why Choose CIIM? Although CIIM is primarily known for digital marketing courses, they also offer a well-designed SQL course as part of their data analysis and web development curriculum. CIIM is ideal for those who want to learn SQL in a business context, such as marketing analytics or data science.
Course Highlights:
SQL course integrated with business intelligence and analytics tools.
Focuses on real-world use cases, perfect for data analysts and business professionals.
Flexible batch timings with weekend options.
Certification & Placement: CIIM provides industry-recognized certification and has tie-ups with various companies, providing good placement opportunities.
5. iClass Mohali
Why Choose iClass Mohali? iClass Mohali offers professional SQL training with a strong focus on practical skills. The course is tailored for individuals seeking in-depth knowledge of SQL and its application in database management and development.
Course Highlights:
Comprehensive curriculum covering SQL Server, Oracle SQL, and MySQL.
Hands-on practice with query writing and database administration.
Experienced trainers with real-time project experience.
Certification & Placement: iClass Mohali offers certifications recognized by many top-tier companies. Their placement support is excellent, offering guidance on interviews, resume building, and job applications.
Conclusion: Choosing the Best SQL Training Institute in Mohali
Selecting the right institute for SQL training in Mohali largely depends on your career goals, current skill level, and learning preferences. Whether you're a beginner or looking to advance your knowledge, the above-mentioned institutes offer robust programs that can kick-start or elevate your career in data management and analysis.
To ensure you’re making the right choice, visit the institutes, talk to the trainers, and check if they provide trial classes. The right learning environment combined with dedicated effort can help you master SQL and unlock numerous career opportunities.
0 notes
Text
How Can STO Development Services Mitigate Investor Risk?

Security Token Offerings (STOs) have emerged as a revolutionary fundraising method for businesses. By leveraging blockchain technology, STOs offer a secure, transparent, and efficient way to raise capital. However, the inherent volatility of the cryptocurrency market and the complexities of STO regulations can pose significant risks for investors. This is where STO development services come in.
This blog explores how partnering with a reputable STO development company can significantly mitigate investor risk throughout the STO lifecycle. We'll delve into key areas where these services can enhance investor confidence and safety.
1. Ensuring Regulatory Compliance
Navigating the intricate web of STO regulations is a major challenge for businesses. Different jurisdictions have varying regulatory frameworks, and non-compliance can lead to hefty fines, legal repercussions, and ultimately, a failed STO.
A professional STO development service provider stays abreast of the latest regulations and guides you through the entire compliance process. They can assist with:
Identifying Applicable Regulations: Depending on your location and target investors, the development team will pinpoint the relevant regulatory landscape you need to adhere to.
Legal Documentation: They can help draft legally sound whitepapers, offering documents, and KYC/AML procedures that meet regulatory requirements.
Liaison with Regulatory Bodies: The development team can facilitate communication with regulatory authorities, ensuring a smooth and compliant STO launch.
By ensuring compliance, STO development services protect investors from fraudulent offerings and promote a sense of security in the investment process.
2. Building Secure Smart Contracts
Smart contracts are the backbone of any STO. These self-executing contracts govern the issuance, distribution, and trading of security tokens. However, vulnerabilities in smart contracts can lead to hacks and loss of investor funds.
A reliable STO development company focuses on:
Secure Coding Practices: They employ experienced developers who adhere to best practices in smart contract coding to minimize the risk of bugs and exploits.
Auditing and Testing: Rigorous audits by independent security experts are crucial to identify and address potential vulnerabilities before launch.
Escrow Services: For added security, some development teams can integrate escrow services that hold investor funds until certain milestones are met.
By prioritizing robust smart contract development, STO development services safeguard investor assets and instill confidence in the overall process.
3. Implementing KYC/AML Procedures
Know Your Customer (KYC) and Anti-Money Laundering (AML) checks are essential to prevent fraud and protect investors from bad actors.
Here's how STO development services ensure robust KYC/AML protocols:
Investor Verification: They integrate KYC/AML solutions that verify investor identities and accreditation status, deterring unqualified or malicious individuals from participating.
Transaction Monitoring: The development team can set up monitoring systems to track suspicious activity and flag potential money laundering attempts.
Compliance with Regulations: KYC/AML procedures are tailored to meet specific regulatory requirements, ensuring investor safety and a smooth STO experience.
By implementing stringent KYC/AML protocols, STO development services create a secure environment for investors and uphold financial integrity throughout the offering.
4. Fostering Transparency and Communication
Transparency is paramount for building trust with investors. A well-developed STO platform should provide clear and easily accessible information about the offering.
Here's how STO development services promote transparency:
Detailed Whitepaper: The development team can assist in crafting a comprehensive whitepaper that outlines the project's vision, technology stack, tokenomics, and risk factors.
User-Friendly Platform: They can build an STO platform with a user-friendly interface that allows investors to easily access offering details, track their investments, and stay updated on project progress.
Regular Communication: The development team can establish clear communication channels to address investor inquiries and concerns promptly.
By prioritizing transparency and open communication, STO development services empower investors to make informed decisions and foster a sense of trust in the STO process.
5. Mitigating Market Volatility
The cryptocurrency market is inherently volatile. While STOs represent ownership in real-world assets, their token value can still fluctuate significantly.
Here are some ways STO development services can help mitigate market volatility:
Token Utility: The development team can design a tokenomics model that assigns utility to the security tokens, offering investors benefits beyond just price appreciation.
Liquidity Lock-Ups: They can implement mechanisms that lock up a portion of the tokens for a predefined period, stabilizing the token price and preventing early selloffs.
Investor Education: The development team can create educational resources to help investors understand the risks associated with cryptocurrency investments and develop sound investment strategies.
By addressing market volatility concerns, STO development services can attract more risk-averse investors and create a more sustainable STO ecosystem.
#STO Development#sto development solutions#sto development agency#sto development company#sto development services#STO
0 notes
Text
10 Must-Have Skills for Full Stack Developers

Considering working in end-to-end development? Whether you're starting fresh or looking to enhance your skills, understanding the essential competencies can significantly impact your success in this dynamic field. In this comprehensive guide, we'll delve into the 10 must-have skills every full stack developer needs to thrive, whether you're taking a full stack development course in Coimbatore or exploring opportunities with NextSkills Technologies Pvt Ltd.
1.Mastery of Programming Languages

At the heart of full stack development lies proficiency in programming languages. Key languages like JavaScript, Python, Java, and Ruby serve distinct purposes across both frontend and backend development tasks. A solid grasp of these languages is essential for writing clean, efficient code.
2. Frontend Development Expertise
Frontend development involves crafting user interfaces that are intuitive and visually appealing. Essential skills include HTML5, CSS3, and proficiency in JavaScript frameworks such as React.js, Angular, and Vue.js. These frameworks empower developers to create dynamic and responsive web applications.
3. Backend Development Skills

Backend development focuses on server-side logic, databases, and APIs. Full stack developers should be adept at Node.js, PHP, or Python for backend scripting. Knowledge of API integration and database management (both SQL and NoSQL) ensures seamless data interaction and efficient application performance.
4. Version Control with Git

Proficiency in Git and platforms like GitHub is crucial for collaborative software development. Version control enables developers to track changes, manage code repositories, and coordinate effectively within development teams.
5.Understanding of Databases and ORMs
Full stack developers must possess a solid understanding of database management systems. This includes relational databases like MySQL and PostgreSQL, as well as NoSQL databases such as MongoDB. Additionally, familiarity with Object-Relational Mapping (ORM) tools like Hibernate facilitates data manipulation and retrieval.
6. Responsive Design and UX/UI Principles

A basic grasp of design principles and UX/UI best practices enhances the frontend development process. Tools like Adobe XD or Sketch aid in creating user-friendly interfaces that optimize user experience and engagement.
7. Proficiency in DevOps Practices
Incorporating DevOps practices streamlines the development lifecycle. Understanding CI/CD pipelines, containerization with Docker, and deployment on cloud platforms such as AWS, Azure, or Google Cloud fosters scalability, reliability, and efficient deployment of applications.
8. Web Security Awareness

Ensuring web security is paramount in full stack development. Awareness of OWASP Top 10 vulnerabilities, implementation of secure coding practices, and regular security audits safeguard applications against potential cyber threats and vulnerabilities.
9. Soft Skills for Collaboration
Effective communication, problem-solving, and time management skills are indispensable in a collaborative development environment. These skills foster teamwork, enhance productivity, and contribute to successful project outcomes.
10. Commitment to Continuous Learning

Full stack development is a dynamic field that continuously evolves with technological advancements. Embracing continuous learning and staying updated on emerging trends like AI/ML integration and serverless computing ensures developers remain competitive and adaptable.
Conclusion
By mastering these 10 essential skills, aspiring full stack developers can build a solid foundation for a successful career journey. Whether you're pursuing a full stack development course in Coimbatore or exploring opportunities with NextSkills Technologies Pvt Ltd, acquiring these competencies will equip you to tackle real-world challenges and excel in the ever-evolving tech industry.
For Enquiry:
Nextskill Technologies Pvt Ltd
82/85 Sthithi Square Complex
Near Gem Hospital
Ramanathapuram - 641045
Contact: 7358 1100 62
Website: www.nextskilltechnologies.com
Email: [email protected]
#php full stack developer#full stack development course in coimbatore#full stack development#full stack course#full stack training
0 notes
Text
Ensuring Website Security: Effective Strategies Against Cyber Threats

In today's digital era, where online businesses thrive, safeguarding your website against hackers is of utmost importance. Cyber attacks not only tarnish your reputation but also jeopardize sensitive data and disrupt operations. Hence, implementing robust security measures is not just a choice but an imperative. In this blog post, we'll delve into effective strategies to shield your site from hackers and uphold its integrity.
1. Stay Updated:
Keeping all software up to date is fundamental in safeguarding your website. This includes your CMS, plugins, themes, and other backend software. Regular updates from developers patch security vulnerabilities, making it crucial to stay current to fend off hackers effectively.
2. Strengthen Passwords and Authentication:
Weak passwords are akin to leaving your front door unlocked in the digital realm. Enforce stringent password policies for all users, including administrators, employees, and customers. Encourage the use of complex passwords with a mix of characters, and implement multi-factor authentication (MFA) whenever possible for added security layers.
3. Opt for Secure Hosting Providers:
Selecting a reliable hosting provider with robust security features is pivotal. Look for providers offering firewalls, intrusion detection systems, malware scans, and data encryption. Consider hosting your website on a dedicated server or VPS for heightened security and control.
4. Implement HTTPS:
Secure data transmission by implementing HTTPS. This encryption protocol makes it significantly harder for hackers to intercept and tamper with sensitive information exchanged between the user's browser and your web server, such as login credentials and payment details.
5. Regular Backups:
In the unfortunate event of a cyber attack, having recent backups of your website's data can be a lifesaver. Schedule regular backups and store them securely in offsite locations or cloud services to ensure swift restoration with minimal downtime and data loss.
6. Deploy Web Application Firewalls (WAF):
A WAF acts as a barrier between your website and the internet, filtering out malicious traffic and protecting against various cyber attacks like SQL injection and DDoS attacks. Integrating a WAF can significantly enhance your website's security posture.
7. Educate Your Team:
Human error remains a significant vulnerability in cybersecurity. Educate your team about common security threats such as phishing attacks and malware. Train them to recognize suspicious emails, links, and attachments, and emphasize adherence to security protocols and best practices.
8. Continuous Monitoring and Testing:
Regularly monitor your website for signs of unauthorized access or unusual activity. Conduct security audits, vulnerability scans, and penetration testing to proactively identify and address weaknesses. Implementing IDS or SIEM solutions can automate this process and provide real-time alerts about potential security breaches.
In conclusion, safeguarding your website against hackers demands a comprehensive approach combining proactive security measures, vigilant monitoring, and continuous education. By adopting the outlined strategies and staying abreast of emerging threats, you can significantly mitigate the risk of cyber attacks and ensure the long-term security and trustworthiness of your website. Remember, in the dynamic landscape of cybersecurity, staying ahead is paramount to safeguarding your digital assets and preserving customer trust.
0 notes
Text
Python Progression: A Guide to Intermediate Courses for Aspiring Programmers
Introduction
Embarking on a journey to master Python programming marks a significant step for aspiring programmers. Having conquered the basics, the logical next step is to delve into intermediate courses that can hone your skills and prepare you for more complex challenges. In this comprehensive guide, we'll explore the best Python intermediate courses available, ensuring you make informed choices to further your programming prowess.
The Importance of Intermediate Courses
Before delving into specific courses, let's understand why intermediate courses are crucial in the Python learning journey. Intermediate courses bridge the gap between beginner and advanced levels, offering a deeper understanding of Python's intricacies. These courses expose learners to more advanced concepts, coding practices, and real-world applications, laying a solid foundation for tackling complex projects.
Data Structures and Algorithms Mastery
Mastering data structures and algorithms is a cornerstone of programming expertise. Intermediate courses that focus on these topics help programmers enhance their problem-solving skills. Look for courses covering topics like linked lists, trees, graphs, and sorting algorithms Object-Oriented Programming (OOP) in Python
Python's versatility shines through its support for object-oriented programming. Intermediate courses in OOP help programmers organize code, improve code reusability, and enhance scalability. Consider courses that cover topics like classes, inheritance, encapsulation, and polymorphism. Codecademy and Udemy host courses with hands-on projects to solidify your understanding of OOP principles.
Web Development with Django
Django is a powerful web framework for Python, widely used in building robust and scalable web applications. Intermediate courses in Django cover topics like models, views, templates, and working with databases. Platforms like Real Python and Full Stack Python offer Django courses that guide you through building functional web applications, providing valuable hands-on experience.
Advanced Python Libraries
Expand your Python toolkit by exploring advanced libraries. Courses on NumPy, pandas, and Matplotlib empower you to manipulate and visualize data efficiently. These libraries are essential for data science and analysis. Platforms such as DataCamp and Kaggle offer interactive courses that allow you to apply these libraries to real-world datasets, honing your skills in data manipulation and analysis.
Testing and Debugging Techniques
A crucial skill for any programmer is the ability to write robust and error-free code. Intermediate courses on testing and debugging techniques help you identify and fix issues efficiently. Platforms like Pluralsight and Test Automation University provide courses covering unit testing, debugging tools, and best practices, ensuring your code is reliable and scalable.
Networking and Security in Python
Understanding networking concepts and implementing security measures is vital in today's interconnected world. Intermediate courses on networking and security in Python teach you how to create network applications, handle protocols, and implement security measures. Platforms like Cisco Networking Academy and Cybrary offer courses that equip you with the skills needed for secure and efficient networking.
GUI Development with Tkinter
Graphical User Interface (GUI) development is an essential skill for those looking to create desktop applications. Intermediate courses on Tkinter, Python's standard GUI toolkit, guide you through building interactive and user-friendly interfaces. Online platforms like GeeksforGeeks and Real Python offer courses that cover Tkinter fundamentals, enabling you to create polished applications with ease.
Concurrency and Multithreading
As applications grow in complexity, understanding concurrency and multithreading becomes crucial for efficient performance. Intermediate courses in this area teach you how to design concurrent systems and make the most of Python's threading capabilities. Check out courses on platforms like LinkedIn Learning and PyBites to grasp these advanced concepts and implement them in your projects.
Conclusion
Embarking on the intermediate phase of your Python learning journey is an exciting step toward becoming a proficient programmer. By exploring the diverse range of intermediate courses available, covering data structures, web development, advanced libraries, testing, networking, GUI development, and concurrency, you'll build a solid foundation for tackling more advanced challenges. Choose courses that align with your interests and career goals, and don't forget to practice your skills through hands-on projects to reinforce your learning. Python progression awaits, and these intermediate courses are your roadmap to success
0 notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#Web Development#Website Design#Frontend Development#Backend Development#Custom Web Development#Responsive Web Design#E-commerce Websites#Content Management Systems (CMS)#Web Application Development#UI/UX Design#Mobile Responsive Websites#Website Maintenance#Website Optimization#Cross-Browser Compatibility#Performance Optimization
0 notes
Text
Unveiling the Future: Trends Shaping the Landscape of Laravel App Development Companies
Unveiling the Future: Trends Shaping the Landscape of Laravel App Development Companies
In the ever-evolving realm of technology, Laravel has emerged as a leading framework for web application development. As businesses strive to stay ahead of the curve, the role of Laravel app development companies becomes increasingly pivotal. In this blog, we'll delve into the trends that are shaping the future of these companies and how Wama Technology is poised to navigate this dynamic landscape.
Rise of Progressive Web Apps (PWAs):
The demand for Progressive Web Apps (PWAs) continues to soar as businesses seek to deliver seamless user experiences across various devices. Laravel app development companies are at the forefront of this trend, leveraging Laravel's flexibility to build PWAs that offer the performance of native apps combined with the reach of the web.
Focus on Microservices Architecture:
As applications become more complex, the adoption of microservices architecture is gaining momentum. Laravel app development companies are embracing this trend by breaking down monolithic applications into smaller, manageable services. This approach enables greater scalability, agility, and resilience, empowering businesses to innovate faster and respond to changing market demands.
Integration of Artificial Intelligence (AI) and Machine Learning (ML):
AI and ML are reshaping the way applications are developed and utilized. Laravel app development companies are incorporating AI-driven features such as chatbots, personalized recommendations, and predictive analytics into their solutions. By harnessing the power of AI and ML, businesses can enhance user engagement, streamline processes, and drive actionable insights.
Emphasis on DevOps and Continuous Integration/Continuous Deployment (CI/CD):
The DevOps culture is becoming integral to software development, with a focus on automation, collaboration, and continuous improvement. Laravel app development companies are embracing DevOps practices and implementing CI/CD pipelines to accelerate the delivery of high-quality software. By automating testing, deployment, and monitoring processes, they can reduce time-to-market and ensure the reliability of their applications.
Security-First Approach:
With the increasing frequency and sophistication of cyber threats, security is paramount for Laravel app development companies. From secure coding practices to implementing robust authentication and authorization mechanisms, these companies prioritize the protection of sensitive data and safeguarding against potential vulnerabilities. By adopting a security-first approach, they instill confidence in their clients and foster long-term partnerships.
At Wama Technology, we recognize the importance of staying abreast of these trends and continuously evolving our practices to meet the evolving needs of our clients. With a team of seasoned Laravel developers and a commitment to innovation, we are well-positioned to navigate the future of Laravel app development companies.
Our expertise in building PWAs, leveraging microservices architecture, integrating AI and ML capabilities, and implementing DevOps best practices sets us apart as a trusted partner for businesses seeking to harness the full potential of Laravel. Furthermore, our unwavering focus on security ensures that our clients' data remains protected and their applications remain resilient in the face of emerging threats.
In conclusion, the future of Laravel app development companies is characterized by innovation, agility, and a relentless pursuit of excellence. By embracing these trends and partnering with a forward-thinking company like Wama Technology, businesses can unlock new opportunities, drive growth, and achieve lasting success in today's competitive landscape.
0 notes
Text
Crafting Digital Excellence: The Significance of Choosing a Laravel Web Development Company
In the realm of web development, Laravel stands out as a PHP framework renowned for its elegance, simplicity, and robust features. Leveraging the expertise of a dedicated Laravel Web Development Company can significantly impact the success of your digital ventures. In this blog post, we'll delve into the importance of Laravel in web development, the key features that make it a preferred choice, and why partnering with a professional Laravel Web Development Company is essential for crafting exceptional digital experiences.
The Power of Laravel in Web Development
Laravel has emerged as a leading PHP framework, empowering developers to create scalable, secure, and feature-rich web applications. Known for its expressive syntax and developer-friendly environment, Laravel has become the go-to choice for building websites and web applications that prioritize performance, maintainability, and innovation.
Key Features of Laravel
Eloquent ORM (Object-Relational Mapping): Laravel's ORM simplifies database interactions, allowing developers to work with databases using an elegant syntax and abstracting the underlying SQL queries.
Blade Templating Engine: Blade offers a clean, lightweight templating engine that simplifies the process of designing dynamic and engaging web pages, enhancing the overall front-end development experience.
Artisan Console: Laravel comes with a powerful command-line tool, Artisan, which automates various development tasks, streamlining processes like database migrations, testing, and code generation.
Middleware for HTTP Requests: Laravel's middleware feature allows developers to filter HTTP requests entering the application, enabling tasks such as authentication, logging, and more to be easily integrated.
Laravel Mix: Laravel Mix simplifies asset compilation and provides a clean, expressive API for defining webpack build steps, making front-end development more efficient.
The Role of Laravel Web Development Companies
Expertise and Experience: Professional Laravel Web Development Companies bring a wealth of expertise and experience to the table, ensuring that projects are executed with precision and adhere to industry best practices.
Custom Solutions: These companies specialize in creating custom solutions tailored to the specific needs and objectives of their clients, ensuring that the resulting web applications meet the highest standards of quality and performance.
Scalability: Laravel Web Development Companies design applications with scalability in mind, enabling businesses to grow and adapt their digital presence as their user base and requirements evolve.
Security Measures: Security is a top priority for Laravel Web Development Companies, and they implement industry-standard security measures to protect applications from potential threats and vulnerabilities.
Benefits of Choosing a Laravel Web Development Company
Efficient Development: Laravel's expressive syntax combined with the expertise of a dedicated development team results in efficient and timely project delivery, reducing time-to-market for web applications.
Scalable Solutions: Laravel Web Development Companies design applications that can scale seamlessly with growing business needs, ensuring that the web presence remains robust and responsive.
Future-Proofing: Laravel's commitment to backward compatibility ensures that applications developed today will remain compatible with future versions, providing a level of future-proofing for your digital investments.
Enhanced Performance: Leveraging Laravel's features for optimization, Laravel Web Development Companies create web applications that deliver high performance and responsiveness, providing an exceptional user experience.
In the competitive landscape of web development, choosing Laravel as your framework and collaborating with a proficient Laravel Web Development Company is a strategic decision. The synergy between Laravel's powerful features and the expertise of dedicated development teams ensures the creation of web applications that not only meet but exceed expectations. Whether you're building a corporate website, an e-commerce platform, or a dynamic web application, the choice of Laravel and a professional development partner sets the stage for digital excellence. Embrace the transformative power of Laravel Web Development to craft web experiences that are not just functional but exceptional in every aspect.
0 notes
Text
Innovative PHP Strategies for Crafting Exceptional Blogging Experiences

In today's swiftly evolving digital landscape, where user experience reigns supreme, the implementation of cutting-edge PHP strategies plays a pivotal role in creating outstanding blogging platforms. As the cornerstone of numerous websites and applications, PHP (Hypertext Preprocessor) continues to metamorphose, providing developers with a powerful toolkit for constructing dynamic and immersive digital spaces. In this blog post, we'll dive into the realm of PHP development strategies and unveil novel practices to forge a seamless and captivating blogging experience.
Unveiling Progressive PHP Development Strategies
PHP, a server-side scripting language, empowers developers to effortlessly craft dynamic web pages. To enhance performance, security, and overall user satisfaction, employing strategic approaches is essential when incorporating PHP into blogging platforms. Let's delve into innovative PHP development strategies that can elevate your blogging experience.
1. Embrace PHP Advancements
Staying abreast of the latest PHP versions is paramount for security, performance, and feature enhancements. Regular updates introduce improved functionalities and bug fixes. By adopting the newest PHP version, you ensure that your blogging platform leverages cutting-edge features while fortifying its resilience against potential vulnerabilities.
PHP Development Strategies Pro Tip: Keep your PHP version updated to benefit from the latest improvements and security patches.
2. Optimize Database Interactions
Efficient database management is the nucleus of a responsive blogging platform. Optimize SQL queries, incorporate indexing, and explore caching mechanisms to alleviate database load. PHP frameworks like Laravel or Symfony offer built-in tools for optimizing database interactions, streamlining development.
PHP Blogging Best Practice: Implement advanced database optimization techniques to enhance overall performance and responsiveness.
3. Prioritize Adaptive Design
In the era of mobile browsing, adaptive design is indispensable. Ensure your blogging platform is accessible and visually appealing across diverse devices and screen sizes. PHP frameworks often integrate tools and libraries for building adaptive interfaces, simplifying the development process.
PHP Development Strategies Tip: Prioritize adaptive design to cater to the diverse preferences of your audience.
Tailored PHP Best Practices for Blogging Experiences
Now that we've explored overarching PHP development strategies, let's zoom in on specific best practices tailored for blogging experiences.
1. Craft SEO-Optimized URLs
PHP enables developers to create clean and SEO-friendly URLs, enhancing search engine visibility. Structure URLs to reflect content hierarchy and include relevant keywords. This not only boosts SEO but also improves user experience through easily shareable and memorable links.
PHP Blogging Best Practice: Structure URLs for optimal search engine visibility and user-friendly navigation.
2. Fortify User Authentication
Ensuring the security of user data is paramount. Implement robust user authentication mechanisms using PHP. Employ secure password hashing algorithms and integrate multi-factor authentication to bolster the login process against potential threats.
PHP Development Strategies Tip: Prioritize user security by implementing robust authentication measures.
3. Harness Caching for Optimal Performance
PHP caching mechanisms can significantly enhance your blogging platform's performance. Implement opcode caching, page caching, or leverage caching libraries to store frequently accessed data. This not only reduces server load but also amplifies the site's speed and responsiveness. PHP Blogging Best Practice implement caching strategies to optimize performance and deliver a seamless user experience.
In Conclusion
In the dynamic realm of web development, innovative PHP strategies are imperative for creating exceptional blogging experiences. By staying current with PHP versions, optimizing database interactions, and adhering to best practices, developers can craft dynamic, secure, and user-friendly platforms. Whether you're a seasoned developer or a budding enthusiast, these PHP development strategies and best practices pave the way for a blogosphere that seamlessly blends innovation with user satisfaction.
As the digital landscape continues to evolve, staying attuned to PHP trends and continually refining your approach ensures that your blogging platform stands out in the crowded digital space. Keep innovating, keep coding, and witness your blogging experience soar to new heights with PHP.
#PHP Blogging Best Practice#PHP development strategies#attitude academy#enrollnow#learnwithattitudeacademy#bestcourse#attitude tally academy#website development course#website development bd#website development classes in yamuna vihar
0 notes
Text
Unveiling Laravel Jetstream: 5 Essentials for Superior Website Development
In the realm of Laravel website development, keeping pace with innovative tools and frameworks is crucial for crafting high-performing and user-friendly websites. Laravel Jetstream, an elegant application scaffolding for the Laravel framework, has emerged as a game-changer for developers and businesses alike. In this blog, we'll delve into the five essential aspects of Laravel Jetstream and how it contributes to top-tier website development, especially when supported by a leading website development company.

1. Streamlined Authentication and Authorization
Authentication and authorization are pivotal components of any web application. Laravel Jetstream simplifies this process by providing robust authentication scaffolding out of the box. It integrates with Laravel's authentication system, offering features like login, registration, password reset, and email verification. Additionally, Jetstream supports API token authentication, enabling secure interactions with external services or mobile applications.
2. Tailwind CSS Integration for Stunning Designs
User interface and design play a significant role in a website's success. Laravel Jetstream harnesses the power of Tailwind CSS, a utility-first CSS framework, for crafting visually appealing and responsive designs. Tailwind CSS's modular approach empowers developers to create custom designs efficiently while maintaining consistency and responsiveness across various devices and screen sizes.
3. Team Management and Multi-Tenancy
For applications requiring multi-user access or team collaboration, Laravel Jetstream offers seamless team management capabilities. It facilitates the creation of teams within an application, allowing users to belong to multiple teams with distinct permissions and roles. Moreover, Jetstream supports the implementation of multi-tenancy, enabling the segregation of data and functionality for different user groups or organizations within a single application instance.
4. Livewire and Inertia.js Support for Dynamic Interactions
Laravel Jetstream supports both Livewire and Inertia.js, empowering developers to build dynamic and interactive user interfaces efficiently. Livewire facilitates the creation of reactive interfaces using PHP, eliminating the need for writing complex JavaScript code. On the other hand, Inertia.js enables building modern single-page applications by combining the power of Laravel website development and front-end frameworks like Vue.js or React.
5. API Support and Ecosystem Integration
In today's interconnected digital landscape, robust API support is paramount. Laravel Jetstream provides convenient API features, allowing seamless integration with third-party services and applications. Its compatibility with Laravel Sanctum, a lightweight API authentication package, ensures secure API interactions, making it ideal for developing web applications with extensive integration needs.
Leveraging Laravel Jetstream
Partnering with a top website development company that harnesses the capabilities of Laravel Jetstream can elevate your web development projects to new heights. A reputable development firm possesses the expertise and experience to leverage Jetstream's features effectively, ensuring the creation of scalable, secure, and user-centric websites.
Such companies employ skilled developers well-versed in Laravel and its ecosystem, enabling them to leverage Jetstream's features to streamline development processes, enhance user experiences, and create robust and maintainable codebases. Moreover, their familiarity with industry best practices ensures that your website aligns with the latest trends and standards, maximizing its potential for success.

Conclusion
Laravel Jetstream stands as a testament to the Laravel framework's commitment to innovation and developer-friendly solutions. Its comprehensive set of features for authentication, design, team management, dynamic interactions, and API support makes it a formidable choice for Laravel website development.
When coupled with the expertise of a top website development company, the potential for creating exceptional websites is amplified. The synergy between Jetstream's capabilities and the proficiency of seasoned developers culminates in websites that are not only functional but also intuitive, visually striking, and tailored to meet the unique needs of businesses and their audiences. Embrace Laravel Jetstream's prowess and the expertise of a leading development company to embark on a journey towards crafting exceptional web experiences.
#Laravel Jetstream#Jetstream#laravel development company in usa#website development company in california
0 notes
Text
Everything You Need to Know About Contact Form To Any API
Introduction:
In the dynamic landscape of web development, the ability to seamlessly integrate contact forms with various APIs has become a game-changer. Contact forms are the bridge between your website and your audience, and the ability to connect them to diverse APIs enhances functionality, automation, and data processing. In this comprehensive guide, we'll delve into everything you need to know about "Contact Form to Any API" solutions, exploring their benefits, implementation, and the limitless possibilities they offer for enhancing user engagement and business processes.

Understanding Contact Form to Any API:
1. What is Contact Form to Any API?
Contact Form to Any API is a versatile solution that enables the integration of contact forms on your website with external APIs. Traditionally, contact forms were static, collecting user data and sending it to an email address. With Contact Form to Any API, the form data can be dynamically sent to external APIs, unlocking a wide range of functionalities such as CRM integration, newsletter sign-ups, payment processing, and more.
2. Benefits of Integration:
Automation: Streamline your workflow by automating tasks through API integration. From lead generation to customer relationship management, automation saves time and reduces manual efforts.
Real-Time Data Processing: Receive and process user data in real time, enabling instant responses or actions based on the information submitted through the contact form.
Enhanced User Experience: Provide users with a seamless experience by eliminating the need for them to navigate away from your website for specific interactions, such as subscribing to newsletters or making purchases.
How Contact Form to Any API Works:
1. Form Configuration:
Begin by configuring your contact form with the necessary fields to collect the required information. This includes standard fields like name, email, and message, as well as any additional data specific to your integration goals.
2. API Integration Setup:
Identify the API you want to integrate with and obtain the required API keys or authentication credentials. Most integrations involve setting up webhooks or API endpoints to receive and process data.
3. Data Mapping:
Define how the data from your contact form corresponds to the fields expected by the external API. This step ensures that the information is transmitted accurately and can be seamlessly processed by the recipient system.
4. Testing:
Before deploying the integrated contact form on your live website, conduct thorough testing. Verify that data is transmitted correctly, and the integration performs as expected. This step helps identify and address any issues before they impact user interactions.
Popular Use Cases for Contact Form to Any API:
1. CRM Integration:
Integrate contact forms with Customer Relationship Management (CRM) systems to automatically capture and organize leads, contacts, and customer information.
2. Email Marketing:
Connect contact forms to email marketing platforms to effortlessly grow your subscriber list. This enables automated additions to your mailing list whenever users submit the form.
3. Payment Processing:
For e-commerce websites, integrate contact forms with payment gateways to facilitate seamless transactions directly from the form.
4. Event Registration:
Streamline event registration by integrating contact forms with event management systems. Capture attendee information and automate the registration process.
5. Surveys and Feedback:
Enhance user engagement by integrating contact forms with survey tools or feedback systems. Automatically collect and analyze user responses.
Implementation Tips and Best Practices:
1. Secure Transmission:
Ensure that data transmitted from your contact form to external APIs is encrypted. Use secure connections (HTTPS) to protect sensitive information.
2. Error Handling:
Implement robust error-handling mechanisms to address any issues that may arise during the data transmission process. Provide clear error messages to users when applicable.
3. User Consent:
Clearly communicate to users how their data will be used and obtain their consent before integrating contact forms with external APIs. Comply with data protection regulations such as GDPR.
4. Monitoring and Maintenance:
Regularly monitor the integration to identify any changes in API endpoints or updates that may affect functionality. Keep all systems involved in the integration up to date.
Tools and Plugins for Contact Form to Any API Integration:
1. WPForms:
WPForms offers a user-friendly interface for building forms and supports integration with various APIs through its Zapier addon.
2. Gravity Forms:
Gravity Forms is a versatile WordPress plugin that allows seamless integration with popular APIs, extending its functionality beyond basic form submissions.
3. Formidable Forms:
Formidable Forms offers advanced features for form building and supports integration with various third-party applications and APIs.
4. JotForm:
JotForm is an online form builder that supports direct integration with numerous APIs, making it a powerful tool for creating dynamic and functional forms.
Conclusion:
In the evolving landscape of web development, the ability to integrate contact forms with various APIs opens up a world of possibilities for enhancing user experience and streamlining business processes. Whether you're aiming to automate lead generation, integrate with CRM systems, or facilitate e-commerce transactions, Contact Form to Any API solutions provide a flexible and efficient way to achieve your goals. By understanding the benefits, implementation steps, and best practices outlined in this guide, you can harness the full potential of contact form integration and elevate the functionality of your website to new heights.
0 notes
Text
Empowering Minds: A Comprehensive List of Software Courses
In today's digital era, the software industry is the driving force behind innovation and technological advancement. Whether you're an aspiring software developer or an established IT professional, staying updated with the latest technologies and skills is crucial to succeed in this ever-evolving field. Fortunately, there is a multitude of software courses available that cater to various interests and skill levels. In this article, we'll explore a comprehensive list of software courses that can help you chart a successful career path in the tech industry.

1. Programming Fundamentals:
Introduction to Programming: Begin your journey by understanding programming logic, data types, and problem-solving techniques.
Python Programming: Known for its simplicity and versatility, Python is an excellent choice for beginners.
2. Web Development:
HTML and CSS: Learn the basics of web page structure and design.
JavaScript: Dive into the world of interactive web development.
Full-Stack Development: Master both front-end and back-end development for comprehensive web expertise.
3. Mobile App Development:
iOS App Development (Swift): Create applications for Apple devices.
Android App Development (Java/Kotlin): Develop apps for the Android platform.
4. Data Science and Analytics:
Data Analysis with Python: Analyze and visualize data using Python.
Machine Learning: Understand and implement machine learning algorithms.
Big Data Technologies (Hadoop, Spark): Handle and process large datasets.
5. Cybersecurity:
Certified Ethical Hacker (CEH): Learn ethical hacking techniques.
Certified Information Systems Security Professional (CISSP): Become a certified information security expert.
6. Cloud Computing:
Amazon Web Services (AWS): Master cloud infrastructure and services.
Microsoft Azure: Gain expertise in Microsoft's cloud platform.
Google Cloud Platform (GCP): Learn GCP's cloud offerings.
7. DevOps:
Docker and Kubernetes: Explore containerization and orchestration.
Continuous Integration/Continuous Deployment (CI/CD): Automate software delivery pipelines.
8. Artificial Intelligence and Machine Learning:
Deep Learning with TensorFlow and PyTorch: Delve into neural networks and deep learning.
Natural Language Processing (NLP): Focus on text and language processing.
9. Game Development:
Unity 3D: Create 2D and 3D games for various platforms.
Unreal Engine: Develop high-quality, immersive games.
10. Blockchain Technology:
markdownCopy code
- **Blockchain Development:** Understand the principles of blockchain and create decentralized applications (DApps).
11. Database Management:
markdownCopy code
- **SQL and Relational Databases:** Learn to work with structured data. - **NoSQL Databases (MongoDB, Cassandra):** Handle unstructured data efficiently.
12. UI/UX Design:
sqlCopy code
- **User Interface (UI) Design:** Create visually appealing and user-friendly interfaces. - **User Experience (UX) Design:** Enhance user satisfaction and usability.
13. Software Testing and Quality Assurance:
markdownCopy code
- **Manual and Automated Testing:** Ensure software reliability and functionality. - **Selenium:** Automate web application testing.
14. Project Management:
markdownCopy code
- **Certified ScrumMaster (CSM):** Understand Agile methodologies. - **Project Management Professional (PMP):** Learn best practices in project management.
15. IoT (Internet of Things):
markdownCopy code
- **IoT Development:** Create applications for IoT devices and systems. - **IoT Security:** Secure IoT networks and devices.
16. Quantum Computing:
markdownCopy code
- **Quantum Programming:** Explore quantum algorithms and computing.
These software courses offer a diverse array of opportunities for individuals to enhance their skill sets and pursue rewarding careers in technology. Whether you are a novice taking your first steps into the world of coding or a seasoned developer looking to specialize in a niche field, there is a course tailored to meet your needs. Continuous learning is not just a choice but a necessity in the tech industry, and staying current with the latest software trends can open doors to exciting career opportunities. So, choose your path, enroll in the right course, and embark on your journey to becoming a software expert in this fast-paced digital age.
youtube
Also Read : Seasoned Developer
SITES WE SUPPORT - AWS Software Courses - Blogger
SOCIAL LINKS
Facebook Twitter LinkedIn Instagram YouTube
1 note
·
View note