#week06
Text




Week06. Featuring two fun Maria candids, taken on two of the most fun afternoons I've had all year (so far!), plus some fun scenery.
3 notes
·
View notes
Text
WEEK06 feedback and postmortem on Journey of Notes
Well, I did a lot of playtests during the development process, so now, my focus is on other player’s feedback.
I have received a feedback on gd.game.

I want to say thanks to Harry.
For the 1st point of feedback, I have changed the position of UI so that it is unlikely to cover the character.
For the 2nd point of feedback, I have checked the collision mask, that is a mistake, it should be a triangle, but it was a rectangle. I have corrected that.
I switched to the “Analytics”, and I got an exciting result: 29% of the players have played more than 5 minutes.

The whole process of playing my prototype with only 1 level is a little bit more than 1 minute, this means 29% of the players have played more than once.
I have to admit that my game is not easy, and it is not perfect. I really appreciate their willingness to try again and again.
Postmortem:
I encountered many challenges during the production. Choosing music was the first, how to edit the levels was the second, and then there were gameplay difficulties, especially compared to Geometry. In order to prevent players from dying if they make a mistake, I can only design a few types of obstacles, which is equivalent to constraining myself. However, after I got some inspiration, these problems were solved. At least for a game with only one level, the richness is not bad.
0 notes
Photo

Week 06 Character Rigs
Homework 6.3 – Character Rig - Rigged, Final
Specs: 1280 px x 720 px, @ 24fps
Create the artwork for a character that can be rigged for cut-out character animation (think body bits, so upper arm, lower arm, head, torso etc.)
Consider the range of motion needed for your character (What granularity of body bits will you need to create?)
Use your software of choice – export as PNG (no background)
Rig your character in AE (Create the rig in a separate composition)
Output: please post a screenshot of your completed character rig from within AE, as an image to Tumblr (see below)
***Please consider creating vector art work for your character (using an app like Illustrator and the pen tool) if you only have access to a mouse/trackpad as a drawing tool. Or, similarly, use the Pen tool in Photoshop, or a similar tool in other apps.
>Post AE screenshot of Rig
-Show Parent-child relationships. Please remember to turn on the Parent & Link column
(Please use meaningful names for your layers so that I can make sense of what I’m looking at. If I don’t see what I’m looking for in the rig screenshot, I won’t be able to give you credit for that grade criteria :(
-Select all of your layers, so that the anchor points are visible in the screenshot (see image above)
-Don’t forget to add a NULL Object for the Waist/Hips so that the legs can be independent of the body (typically the Null Object/Waist is your root node that all other objects are parented to)
-Edit your screenshot in Photoshop to add any other relevant textual info I may need to know about your rig
2 notes
·
View notes
Text

Weekly illustration
Deanna Hieber
4 notes
·
View notes
Text
Week 06: Buffer Overflow Practice Questions 1.0 Basic
1.0 Basic
I actually don’t have c programming set up at home, can’t seem to figure out how to get gcc working
So I logged onto my school directory
I compiled basic.c with dcc and got some error messages out
Warning: the gets function is dangerous and should not be used
Bless Andrew Taylor
I’m not sure if I’m allowed to look at the code itself while trying to figure it out, I assume not
So from what I remember, the most basic way to to do a buffer overflow is to just pass into a string that’s too large
Okay I got a runtime error - stack buffer overflow
dcc explanation - access past the end of a local variable
Make sure the size of your array is correct
Make sure your array indices are correct
Oh, it printed out a portion of the code
if (team == ‘B’) {
win();
Okay wait I think I’ve got it
So there’s two variables, name and team
I’m putting data into name, if I can overflow into the variable team with the letter B, I get to run the win function
20 “A”’s and it’s still working, lets try 30
30 “A’s still working
32?, 32 A’s and it broke
31 “A”s working fine, I think we’ve found the size of variable name
I realised that maybe I shouldn’t be using dcc, so I recompiled with gcc
Yeah I think dcc is checking for this
Hmm, 32 A’s work fine now
64 gives a seg fault
I ended up just pasting in a lotttt of “B”’s
And I got
We can leave this here, because it is never called.
Our flag is safe.
Flag: COMP6841{Hey_Look_Ma_I_Made_It!}
Segmentation Fault
So it’s not clean but it got the job done
3 notes
·
View notes
Text
Week 6. Security Everywhere
I was watching a video lecture on echo360 to catch up on some work and saw that my lecturer was typing in the pin to the ipad that is used during the lecture. Similarly, a few weeks later the notification of logging into icloud pops up showing the lecturer’s personal email address. Within this email address is the lecturer’s name and six digits which closely resemble the a birth date.
Risk: So, all this is recorded on echo, if an attacker wanted to access this lecturer’s personal details, the ipad can easily be taken and logged in using the pin in the recording.
Also learning from the talk last week regarding passwords, we only require a few pieces of information of an individual to determine the possible passwords to an account. So since we already know the name and possible dob the third piece of information can be found somewhere on the ipad.
Otherwise, it is also possible that some sites are already logged on/ have details saved. i.e. unsw portal.
Prevention and plan for the future:
I guess a lesson that can be learn is that we can’t always keep everything a secret, but keep your personal information to yourself.
If you don’t need to share information don’t
3 notes
·
View notes
Text
Protest 101: Social Media

The Early Days...
Life was tough during 14th century England. Workers were forced to work with a minimum wage while some had to work without pay due to the feudalism. Adding insult to injury, taxes were raised in order to fund the war with France. Subsequently, people were starting to realise the importance of freedom; they want equal rights. It escalated to an open rebellion when the people of Essex refused to pay their taxes. Local leaders contacted countryside communities through letters, they rallied and marched to London (Bbc.com 2019). The revolution was ultimately a failure; however, The Peasant’s Revolt was an early example of an organised protest among the common folk.
21st Century
Centuries later, London was occupied by protestors yet again. During the 2011 London Riots, the city was in flames, buildings looted and destroyed. It was the largest post-world-war era disorder in UK’s history (Vice 2016). The protest was triggered by the shooting of Mark Duggan, disadvantaged communities took this opportunity to protest the unequal treatment of the police specifically over the excessive use of stop and search (Vice 2016). Unlike in ancient times, the method of communication had significantly evolved with the aid of technology. Nowadays, protestors and activists seek technology solutions that are straightforward and reachable (Sigal and Biddle 2015). As social media has become a crucial part of life, it was used as the medium to organise the London Riots.

According to Sigal and Biddle (2015), story-elements bring people to protest or start a movement together. The movement started when netizens gathered on a Facebook page to mourn the death of Duggan (Halliday 2011). The initial sadness subsequently transforms into anger, thus triggering the riots. To prevent more chaos, Facebook and Twitter were closely monitored by the authorities, they were ready to react. As the main social media platforms were under governance, protestors pivoted to another platform (Youmans and York 2012). BlackBerry Messenger (BBM) became the designated platform for protestors to deploy or rally people. It was a better alternative as BlackBerry phones were common among teens, it’s a free text messenger and most importantly it is UNTRACEABLE. BlackBerry refused to shut down its services (MailOnline 2011); but agreed to enable police to track and arrest users who spread ‘fake news’ (Halliday 2011). Law enforcement was heavy and they ultimately put an end to the riots.

Double-Edged Sword
Without a doubt, social media is important if one is to become an activist. The power of social media as a tool to rally the people can no longer be denied. Nonetheless, it is unsafe. Fundamentally, a social media platform is not designed as a tool to organise movements and protests. Social media’s core purpose is to connect people and gain revenue, it is a business-oriented service (Youmans and York 2012). Hence, they comply with government requests in order to keep their services intact. Moreover, there is no solid proof that social media companies will not ‘sell-out’ to tyrants or despotic regimes to undermine their consumer base. Therefore, activists have to proceed with caution when wielding the influence of social media.

References:
Bbc.com. (2019). [online] Available at: https://www.bbc.com/bitesize/guides/z2c2pv4/revision/1 [Accessed 28 Apr. 2019].
Halliday, J. (2011). London riots: BlackBerry to help police probe Messenger looting 'role'. [online] the Guardian. Available at: https://www.theguardian.com/uk/2011/aug/08/london-riots-blackberry-messenger-looting [Accessed 28 Apr. 2019].
Halliday, J. (2011). London riots: how BlackBerry Messenger played a key role. [online] the Guardian. Available at: https://www.theguardian.com/media/2011/aug/08/london-riots-facebook-twitter-blackberry [Accessed 28 Apr. 2019].
Mail Online. (2011). 'It's unbelievable BlackBerry Messenger hasn't been shut down': Mayor's aide calls for ban on riot 'tool'. [online] Available at: https://www.dailymail.co.uk/news/article-2023924/London-riots-2011-BlackBerry-Messenger-shut-unbelievable.html [Accessed 28 Apr. 2019].
Sigal, I. and Biddle, E. (2015). FCJMESH-007 Our Enduring Confusion About the Power of Digital Tools in Protest. The Fibreculture Journal, (26), pp.290-296.
Vice. (2016). What the 2011 Summer Riots Were Really About. [online] Available at: https://www.vice.com/en_uk/article/kwkbde/england-riots-2011-five-years-later-analysis [Accessed 28 Apr. 2019].
Youmans, W. and York, J. (2012). Social Media and the Activist Toolkit: User Agreements, Corporate Interests, and the Information Infrastructure of Modern Social Movements. Journal of Communication, 62(2), pp.315-329.
7 notes
·
View notes
Photo

Art 270
Week 06 = Week 07
Silhouette Monster Design
Class Notes
Silhouette Method
Feng Zhu
Reel
https://youtu.be/yt3YZ0qST9I
Silhouette Method of Character Design
https://youtu.be/GQZUc7FrahI
http://characterdesignnotes.blogspot.com/2011/03/use-of-silhouettes-in-concept-design.html
Scott Robertson
https://designstudiopress.com/product/the-skillful-huntsman/
1 note
·
View note
Photo

[Week 06 - Techthoughts]
Week 6: MVP and Wireframing
MVP and Wireframing are crucial aspects that a startup company should consider. Based on my learnings from Ms. Rhea Suzette Haguisan, a development technique in which a new product is introduced in the market with basic features but enough to get the consumers' attention.
In our Minimum Viable Product, we presented the most fundamental features that our application includes, which cover the following:
User-generated
Route tracking and optimization
Location marking
Powerful search and discovery
Accurate Mapping
We also included the most robust features that could be included in the build-up of NavigaTour. In this part, we ensured to enlist the following features that we best believe our market is looking forward to:
Voice Assistance
Shop Categorization
Display of Real-time and Updated Operating Hours
These features will help generate sufficient value for our early users to buy our application (NavigaTour).
We also created a wireframe to help us gauge what we want our application to look like for the users. While a wireframe doesn't entirely represent the complete design of the app, it gives a guide or insight into the key screens and interfaces elements that we would like to include in our application.
This week was quite insightful, and we gained an in-depth perspective of how we want our application, NavigaTour, to come to life and how we want our future users to perceive the application we wish to provide them.
0 notes
Text
Week 06 - C.D
Week Six- 11/02/2019
One week before formative submission -
My partner tried to write the tagline in as many styles as possible to see what would work with the logo - I also redid the logo in a few different manners




just trying some mix and match with the tagline and logo we redid.
for formative submission - we have to complete the visual brand identity poster and the slides to explain our branding. Here they are completed below
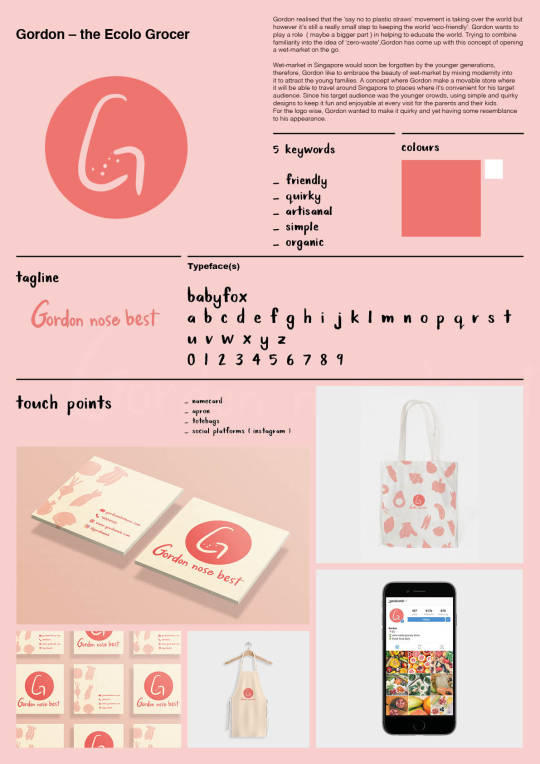





- End of Week Six -
0 notes
Photo


Week 06 - Sixth Update of 20-Time!
Actual Status Updates:
Progress? Significant progress this week as well! During classI was able to accomplish my previous goal of doing the line art of the Kiki’s Delivery Service piece of the masterpiece! Due to less time during 20-time (30 minutes), I was not able to work on the large piece, but I have an entire day free, therefore I will use my time wisely during that time to complete coloring Kiki as well as color part of the large piece as planned.
Adjustments? Generally, no significant adjustments were made this week, but the only change I did was some slight posing and facial expression Kiki originally had in the drawing. It did somewhat change the emotion the drawing gave, but it represented my visualization of how it would originally look like well.
Any challenges? No large challenges took place this week, rather the only problem was the slight rush I had when completing the line art as the decrease of time took place, but I was still able to accomplish it in time.
Overall progress:
Still on track? Of course! I was able to accomplish the goal I set last week and will continue to follow my original schedule I had set out for myself.
What are you going to do next week? Begin sketching the “My Neighbor Totoro” piece of the masterpiece and hopefully finish it during class in time.
Thank you so much for following the development of my masterpiece and I hope you’ll continue to view my updates :)
-Alex
#20time#wip#art WIP#status update#week6#week06#fanart#studio ghibli#steven universe#Kiki's Delivery Service#copic#colored pencil#lineart
3 notes
·
View notes
Link
Week 06 Character Rigs
Lotte Reiniger: The animation genius you've probably never heard of
BBC Ideas
https://youtu.be/3Gm9kZLP0uE
Lotte Reiniger documentary
https://youtu.be/ZXQPZqOqe58
The Adventures of Prince Achmed by Lotte Reiniger, 1926
https://youtu.be/25SP4ftxklg
Exercise 6.2 – Character Rig Art WIP
Work In Progress - does not have to be final art/comp
Specs: 1280 px x 720 px (min)
Create the artwork for a character that can be rigged for cut-out character animation (think body bits, so upper arm, lower arm, head, torso etc.)
Consider the range of motion needed for your character (What granularity of body bits will you need to create?)
Use your software of choice – export as PNG (no background)
Output: image to Tumblr
1 note
·
View note
Text

Futuristic Bike Messenger
Deanna Hieber
0 notes
Text
Week 06: Tutorial Reflection
In the tutorial this week, we covered cyber warfare. The topic was, what kind of cyber attracks will the russians use if we go to war with them?
Fake news - spread false info online, quickly spreading
It makes people mistrust the news, each other etc.
What is real what is false anymore?
Attack power grids
Attack telecommunications
EMP’s
Mass surveillence
Destroy infrastructure like water supplies
Compiled list from class
Insider attacks (military secrets)
DDOS attacks
Ransomware attacks on infrastructure
Sabotaging power
Hijack military drones
Attack GPS
Backdooring software and logging/survillence
Denial of tech gear (hardware) from enemy
I think this was like, attacking shipments
Jamming signals
Data theft
Tutorial Question - Consider the main threats we face in the cyber domain of war and produce 10 recommendations for actions to be taken
I could only come up with 5
1. Increase security on the software that controls infrastructures like electricity & water
Air gaps
Secondary backups
True, this one was too broad
2. Increased background checks for higher ups in the military + surveillence
On any worker in critical roles to be honest
Military, Government, Programmers
3. Develop our own GPS system as a backup in case the American GPS system is taken down
4. Auditing software companies to check if their workers have been compromised, or their software has been compromised
5. Funding to educate the public/workers (especially if they work in military/government) on basics of cyber security
How to watch out for social engineering etc ...
List made by the class
Compartamentalise knowledge of intelligence
Background checks on programmers
Risk type 1 / type 2 errors
What if we let someone in, who is an insider
What if we deny someone, who isn’t
Make most valuable people anonymous
Doesn’t work in a democracy
Can’t deny reputation damage
Backdoor everything now
What if it’s found out early, and it’s the reason we go to war
Virus that kills enemy data, wipes our own data if it’s been compromised
Could be too dangerous to use, leaked out early?
Stay offline if possible
Limit internet access to prevent cyber attacks
Create nationwide intranet
Prepare financial resources for war
In event of DDOS, have redundancies for online services
International war games as training
Locally sourced software & hardware
After the class, we covered buffer overflows in more details, as well as other forms of attacks like format string attacks. I thought it was really cool, I’ll try out the challenges that caff posted on open learning.
Oh also, we went through the mid sem exam in class. I was kind of confident when I left the exam room, but after going through it in class, definitely not haha. Don’t think I did that well :(
0 notes
Text
Week 6: Lectures
Lecture 6.0. One-time Pad:
Claude Shannon – father of measuring information
If XORed with something random, then the output will be random.
Each random number is used one and then thrown away
Shared secret is large – it is the size of the message.
Key distribution is a major issue.
Russians and Americans use to communicate using a one time pad. o Duplicate books/ duplicate pages in books o Inception project – Vernam o Discovered a warehouse of one-time pad
Issues with one-time pad – cracked as didn’t use a proper random number generate
Harder to analyse if it is keyboard mashed
Number Stations
Lecture 6.1. Threats:
Can’t defend and patch every single weakness and it is a quite difficult decision.
Spend resources efficiently and effectively
Build up a threat model:
Systematic approach to list out the possible sources of attacks and problems may come from.
Consider the motives of the possible adversaries
Think about what the adversaries can gain from the asset that is protected
Prioritizing the attackers
Threat Tree: Assets are nodes, Threats are branches, Cause of threats are sub-branches , Enumerate threat.
Don’t always worry about the major things – i.e. Hollywood threats – remember there are more boring and smaller threats.
Think about things in advance – i.e. if you’re in mine field, think about it in advanced. o Think about the threat before it happens, and before allocating your resources.
Brainstorm all ideas before saying no.
Incidence Response: o Bush – response to 9/11 is not ideal, it is the system having issue. Failure of design.
can’t have a single point of failure.
Be aware of weaknesses in system.
Common threat Classes/Sources of Threats
Users: Unintentional attacks, malicious attacks
Attackers: - all pose different threats
Insider attacks – attack at a time that suits you
Casual Attackers – doesn’t target victims specifically, attacks victim while scanning many other targets
Determined Attackers – targets victims, look for vulnerabilities of the victim, has motive against the victim
Funded Attackers – Performs reconnaissance, hires people and purchase equipment to perform attack.
Natural Disasters/Accidents
Movie Plot Threats
Errors and failure: Mechanical and Errors
1 note
·
View note


